2. Overview of Digital ID Systems and Participants
2.1. Terminology and Definitions
For the purposes of this Guidance, in relation to identifying and verifying the identity of a customer as part of the customer due diligence (“CDD”) process, identity (“ID”) refers to the specification of a unique natural person that is:
• Based on characteristics (attributes or identifiers) of the person that establish a person’s uniqueness in the population or particular context(s); and • Recognized by the state for regulatory and other official purposes.
Proof of identity generally depends on some form of government-provided or issued registration, documentation, or certification (such as a birth certificate, identity card, or digital ID credential) that constitutes evidence of core attributes (such as name and date and place of birth) for establishing and verifying identity. Proof of identity may be provided through general-purpose ID systems (such as national ID and civil registration systems) or various limited-purpose ID systems (such as taxpayer identification numbers, driver’s licenses, passports, voter registration cards, social security numbers, and refugee identity documents).
Digital ID systems use electronic means to assert and prove a person’s identity online and/or in in-person environments, including through the use of:
• Electronic databases, including distributed databases and/or ledgers, to obtain, confirm, store, and/or manage identity evidence; • Digital credentials to authenticate identity for accessing mobile, online, and offline applications; • Biometrics to help identify and/or authenticate individuals; and • Digital application program interfaces (“APIs”), platforms, and protocols that facilitate online identification and the verification and authentication of identity.
Identification Systems in the UAELFIs should understand and utilize national-level identification systems and processes currently in place or under development in the UAE, including but not limited to:
• UAE Pass, the UAE’s first national digital identity and signature solution that enables users to identify themselves to government service providers in all emirates through a smartphone-based authentication protocol and to sign documents digitally with a high level of security. The UAE Pass app uses biometric facial recognition software to verify and register users without requiring an in-person visit to a government services center. The UAE Pass also includes a “digital vault” for storing users’ digital documents and sharing them with government departments, as well as a “digital signature” function to complete official transactions without the need for paper documents or physical signatures.
• Emirates ID, the mandatory, government-issued identity card for all UAE citizens and residents. While issued as a physical card, the Emirates ID card uses public key infrastructure to attach individual identities to digital certificates that can be used to sign and encrypt data, as well as fingerprint biometrics. When verifying an Emirates ID card, LFIs should use the online validation gateway of the Federal Authority for Identity and Citizenship and should keep a copy of the Emirates ID and its digital verification in their records.
• Emirates Facial Recognition, an initiative launched by the UAE Ministry of Interior and Federal Authority for Identity, Citizenship, Customs & Port Security, together with private sector partners. The facial recognition initiative includes a “face fingerprint” system for digital verification of digital transactions and remote identities.
Digital ID systems involve two basic components and an optional third component:
• Identity proofing and enrollment answers the question: Who are you? It involves collecting, validating, and verifying identity evidence and information about a person, establishing an identity account, and binding the individual’s unique identity to authenticators possessed and controlled by this person.
• Authentication and identity lifecycle management answers the question: Are you the person who has been identified and verified? It establishes, based on possession and control of authenticators, that the person asserting the identity is the same person who was identity proofed and enrolled, and ensures that adequate controls are in place to manage events that can occur over the identity lifecycle that affect the use, security, and trustworthiness of authenticators.
• Portability and interoperability mechanisms, where used, enable proof of identity to be portable, so that an individual’s digital ID credentials can be used to prove identity for new customer relationships at unrelated private-sector or governmental entities, without their having to obtain and verify personal data and conduct customer identification and verification each time. Portability and interoperability are optional components of any digital ID system.
Not all elements of a digital ID system are necessarily digital. Some elements of identity proofing and enrollment can be either digital or physical, or a combination; however, binding, credentialing, authentication, and portability/federation (where applicable) are always and necessarily digital. These concepts are explained further in the following sections.
Digital ID systems can enable remote customer identification and verification, support remote financial transactions, and otherwise facilitate non-face-to-face business relationships and transactions, defined as interactions in which the parties are not in the same physical location and conduct activities by digital or other non-physically present means, such as mail or telephone. Under international standards, non-face-to-face business relationships and transactions are included as an example of a potentially higher-risk situation in undertaking CDD.3 However, given the evolution of digital ID technology, architecture, and processes, and the emergence of consensus-based open-source digital ID technical standards, non-face-to-face interactions that rely on reliable, independent digital ID systems with appropriate risk mitigation measures in place may present a standard level of risk, and may even present a lower level of risk where higher assurance levels are implemented and/or appropriate control measures are present.4 See section 4 below for specific risk mitigation measures and strategies that can help ensure that a digital ID system is suitably “reliable” and “independent” in this sense.
3 See The FATF Recommendations, Interpretive Note to Recommendation 10, at 68, available at: fatf- gafi.org/media/fatf/documents/recommendations/pdfs/FATF%20Recommendations%202012.pdf.
4 FATF, Guidance on Digital Identity, at 30, available at: fatf-gafi.org/media/fatf/documents/recommendations/Guidance- on-Digital-Identity.pdf.
2.2. Identity Proofing and Enrollment
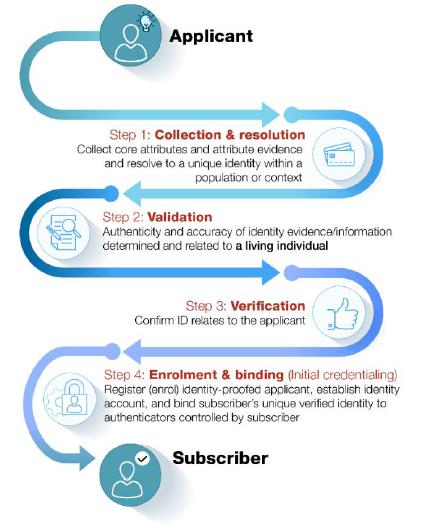
Identity proofing and enrollment (with initial binding/credentialing) constitute the first stage of a digital ID system. This component is directly and most immediately relevant to LFIs’ customer identification and verification obligations under Article 8 of the AML-CFT Decision. For illustrative purposes only, Figure 1 below presents a sample process flow for identity proofing and enrollment; the discussion that follows explains each step in greater detail.
Figure 1. Identity Proofing and Enrollment
 Source: The Financial Action Task Force5
Source: The Financial Action Task Force5Identity proofing comprises three actions: (1) collection and resolution, (2) validation, and (3) verification. Examples of each of these actions are included in the discussion below for illustrative purposes only; there is no expectation that LFIs employing a digital ID system for CDD use any particular method of identity proofing unless otherwise required.
1. Collection and resolution involves obtaining attributes, collecting attribute evidence, and resolving identity evidence and attributes to a single unique identity within a given population or context (a process known as “de-duplication”).6
○ Attribute evidence may be either physical (documentary) or purely digital, or a digital representation of physical attribute evidence (such as a digital representation of a paper or plastic driver’s license). Identity evidence has traditionally taken a physical form and been physically presented by the person seeking to prove his or her identity (known as a “claimant”) to an identity service provider (“IDSP”). However, with the development of digital technology, identity evidence may now be generated digitally (or converted from physical to digital form) and stored in electronic databases, allowing the identity evidence to be obtained remotely and/or identity evidence to be remotely verified and validated against a digital database. ○ Attributes may also be inherent, that is, based on an individual’s personal biometric characteristics, including:
• Biophysical biometrics, such as fingerprints, iris patterns, voiceprints, and facial recognition—all of which are static;
• Biomechanical biometrics, such as keystroke mechanics, which are the product of unique interactions of an individual’s muscles, skeletal system, and nervous system—all of which are dynamic; and
• Behavioral biometrics, such as email or text message patterns, mobile phone usage, geolocation patterns, and file access log, which are based on an individual’s patterns of movement and usage in what are known as “geospatial temporal data streams.”
○ Under Article 8.1 of the AML-CFT Decision and section 6.3.1 of the AML/CFT Guidelines for Financial Institutions, required identity attributes for CDD under UAE regulations and guidance include, for a natural person, the name (as in the passport or identity card, number, country of issuance, date of issuance and expiration date of the identity card or passport), the nationality, the address (i.e., the permanent residential address), the date and place of birth, and the name and address of employer (if applicable).
When verifying the Emirates ID card, either physically or by way of digital or electronic Know Your Customer (“e-KYC”) solutions, LFIs should use the online validation gateway of the Federal Authority for Identity, Citizenship, Customs & Port Security, the UAE Pass Application, or other UAE Government-supported solutions, and keep a copy of the Emirates ID and its digital verification record. Where passports, other than Emirates IDs, are used in the KYC process, a copy should be physically obtained from the original passport, which should be certified as “Original Sighted and Verified” under the signature of the employee who carries out the CDD process and retained.
2. Validation involves determining that the evidence is genuine (i.e., not counterfeit, forged, or misappropriated) and that the information the evidence contains is accurate. Validation is performed by checking the identity information and evidence against an authoritative and reliable source to establish that the information matched reliable, independent source data or records.
○ For instance, in order to assess whether an individual’s physical identity evidence (such as a driver’s license or passport), or the digital images thereof, is genuine, an IDSP may review the evidence to determine that there have been no alterations, that the identification numbers follow standard formats, and that the physical and digital security features are valid and intact.
• When utilizing a physical or digital copy of identity evidence such as an Emirates ID card for purposes of validation, LFIs are expected to review the evidence for physical or digital abnormalities or possible alterations and to make a determination as to whether the evidence has been altered or forged.
○ In order to assess whether such evidence is accurate, the IDSP may query the government issuing sources for the license or passport and confirm that the information matches.
• As noted above, LFIs should use the online validation gateway of the Federal Authority for Identity, Citizenship, Customs & Port Security, the UAE Pass Application, or other UAE Government-supported solutions, to ensure that the information presented for validation purposes matches the information included in reliable databases or other sources.
3. Verification involves confirming that the validated identity relates to the specific individual being identity-proofed, including (but not limited to) through the use of biometric solutions like facial recognition or liveliness detection.
○ For example, if performing verification remotely, an LFI or other IDSP could ask the applicant to take and send a mobile phone video or photo with other liveliness checks, compare the submitted photos to the photos on the applicant’s Emirates ID, passport, or other valid documents, and determine that they match to a given level of certainty.
○ To tie this identity evidence to the actual (real-person) applicant, the IDSP could then send an enrollment code to the applicant’s validated phone number, email address, or another address that is tied to the identity, require the applicant to provide the enrollment code to the IDSP, and confirm that the submitted code matches the code sent. Such measures would verify that the applicant is a real person, in possession and control of the validated phone number. At this point, the applicant will have been identity proofed.
The fourth and final action in the first stage of a digital ID system is enrollment and binding.
4. Enrollment is the process by which an IDSP registers (or “enrolls”) an identity-proofed applicant as a “subscriber” and establishes their identity account. This process authoritatively binds the subscriber’s unique verified identity (i.e., the subscriber’s attributes/identifiers) to one or more authenticators possessed and controlled by the subscriber, using an appropriate binding protocol. The process of binding the subscriber’s identity to authenticator(s) is also referred to as “credentialing.”
○ An authenticator is something the claimant possesses and controls—typically, a cryptographic module, one-time code generator, or password—that is used to confirm or “authenticate” that the claimant is the individual to whom a credential was issued and therefore is (to a given degree of likelihood) the actual subscriber and accountholder. The likelihood that the claimant to whom a credential was issued is in fact the actual subscriber is a function, in part, of the strength of the authentication component; stronger authenticators, such as longer and more complex passwords, can increase an IDSP’s confidence that the claimant is in fact the actual subscriber.
○ A credential is a physical object or digital structure, such as a physical or electronic ID card, that authoritatively binds a subscriber’s proofed identity (via one or more identifiers) to at least one authenticator possessed and controlled by the subscriber. When a digital IDSP issues an authenticator (such as a password or PIN) and authoritatively binds the authenticator to the subscriber’s identity, the physical object or digital structure that results (such as an ID card) is a credential.
Typically, an IDSP issues one or more authenticators (such as a password or auto-generated code) to the subscriber and registers the authenticators in a way that ties them to the subscriber’s proofed identity at enrollment. However, the IDSP can also bind the subscriber’s account to authenticators provided by the subscriber that are acceptable to the IDSP. For example, users of the UAE Pass app are prompted to create a signing password while completing the verification step at a UAE Pass kiosk or through the mobile app. The IDSP can also bind a subscriber’s credentials to additional or alternative authenticators at a later point in time, as part of identity lifecycle management (discussed immediately below). 5 Available at: fatf-gafi.org/media/fatf/documents/recommendations/Guidance-on-Digital-Identity.pdf.
6 Some government-provided ID solutions include a de-duplication process as part of identity proofing, which may involve checking the applicant’s specific biographical attributes (such as name, age, or gender), biometrics (such as fingerprints, iris scans, or facial recognition images), and/or government-assigned attributes (such as driver’s license, passport, or taxpayer identification numbers) against the identity system’s database of enrolled individuals and their associated attributes and identity evidence to prevent duplicate enrollment.
2.3. Authentication and Identity Lifecycle Management
Authentication and identity lifecycle management constitute the second stage of a digital ID system. Authentication answers the question: Are you the person who has been identified and verified? It establishes the individual seeking to access an account (or other services or resources) is the same person who has been identity proofed, enrolled, and credentialed and has possession and control of the binding credentials and other authenticators, if applicable. In other words, it establishes that the claimant is the onboarded customer. Authentication can rely on various types of authentication factors and processes, with the trustworthiness of the authentication depending on the type of authentication factors used and the security of the authentication processes:
• Authentication factors fall into three basic categories:
○ Knowledge factors, that is, something you know, such as a shared secret (e.g., username, password, or passphrase), a personal identification number (“PIN”), or a response to a pre-selected security question;
○ Ownership factors, that is, something you have, such as a cryptographic key stored in hardware (e.g., in a mobile phone, tablet, computer, or USB-dongle) or software that the subscriber controls; a one-time password (“OTP”) generated by a hardware device; or a software OTP generator installed on a digital device, such as a mobile phone; and
○ Inherence factors, i.e., something you are, including biophysical biometrics, biomechanical biometrics, and behavioral biometrics (as discussed in section 2.2 above).
• Authentication processes have historically been assessed by the number and type of authentication factors the process requires, on the assumption that the more factors an authentication process employs, the more robust and trustworthy the authentication system is likely to be. As authentication technology and processes have evolved, however, this assumption has been revised, and the strength of the authentication component is no longer assumed to depend on how many factors (or types of factors) it uses but rather on whether its authentication processes are secure: that is, resistant to compromise by commonly executed and evolving attacks, such as phishing and man-in-the-middle attack vectors. In this revised paradigm, multifactor authentication (“MFA”)—where an IDSP uses two or more independent authenticators from at least two different authentication factor categories (knowledge/possession/inherence) to authenticate the claimant’s identity—is typically assumed.
○ As detailed in the Guidance for Financial Institutions adopting Enabling Technologies, LFIs should implement MFA using a biometric factor where possible to authorize high-risk activities and protect the integrity of customer account data and transaction details. High-risk activities include changes to personal data (e.g., customer office or home address, email address, or telephone contact details), registration of third-party payee details, high-value funds transfers, and revisions to funds transfer limits.
• LFIs deploying MFA at login that includes a biometric factor should consider employing phishing-resistant authenticators where at least one factor relies on public key encryption to secure the customer authentication process.
○ Digital ID authentication has traditionally been conducted at a particular point in time: namely, when the claimant asserts the customer’s/subscriber’s identity and seeks authorization to begin a digital or in-person interaction to access his or her account or other financial services or resources. Today, however, many regulated entities augment traditional authentication at the beginning of an online interaction with continuous authentication solutions that leverage biomechanical biometrics, behavioral biometrics, and/or dynamic transaction risk analysis.
• Instead of relying on something the claimant has/knows/is to establish at the beginning of the interaction that the claimant is the onboarded customer and is in control of the authenticators issued to that customer, continuous authentication focuses on ensuring that certain data points collected throughout the course of an online interaction—such as geolocation, Media Access Control (“MAC”) and Internet Protocol (“IP”) addresses, typing cadence, and mobile device angle— match what should be expected during the entire session.
• However, ways of measuring the effectiveness of continuous authentication technology in mitigating authentication risks have not reached maturity, and the digital ID technical standards, such as the U.S. National Institute of Standards and Technology (“NIST”) Digital Identity Guidelines, do not currently address them.
• Finally, identity lifecycle management refers to the actions IDSPs should take in response to events that can occur over the lifecycle of a subscriber’s authenticator that affect the use, security, and trustworthiness of the authenticator. The attributes associated with an identity may change from year to year, and analytics systems may uncover risk signals suggesting an identity is being used in a manner consistent with fraud or account compromise. Key identity lifecycle events may include:
○ Issuing and recording credentials: At customer onboarding, the IDSP issues the credential and records and maintains the credential and associated enrollment data in the subscriber’s identity account throughout the credential’s lifecycle.
○ Binding: Throughout the digital ID lifecycle, the IDSP should also maintain a record of all authenticators that are, or have been, associated with the identity account of each of its subscribers, as well as the information required to control authentication attempts. When an IDSP binds a new authenticator to the subscriber’s account post-enrollment, it should require the subscriber to first authenticate at the assurance level (or higher) at which the new authenticator will be used.
○ Compromised authenticators: If a subscriber loses or otherwise experiences compromise of all authenticators of a factor required for MFA, the subscriber should repeat the identity proofing process, confirming the binding of the authentication claimant to previously proofed evidence, before the IDSP binds a replacement for the lost authenticator to the subscriber’s identity account. If the subscriber has MFA and loses one authenticator, the IDSP should require the claimant to authenticate, using the remaining authentication factors.
○ Expiration and renewal: Where an IDSP has issued an authenticator that expires, the IDSP should bind an updated authenticator prior to expiration, using a process that conforms to the initial authenticator binding process and protocol, and then revoke the expiring authenticator.
○ Revocation or termination: IDSPs should promptly revoke the binding of authenticators when an identity ceases to exist (e.g.., because the subscriber has died or is discovered to be fraudulent); when requested by the subscriber; or when the IDSP determines that the subscriber no longer meets its eligibility requirements. 2.4. Portability and Interoperability Mechanisms
Digital ID systems can—but need not—include a component that allows proof of identity to be portable. An individual’s identity is portable when his or her digital ID credentials can be used to prove identity for new customer relationships at unrelated private sector or government entities, without their having to obtain and verify personally identifiable information (“PII”) and conduct customer identification and verification each time. Portability requires developing interoperable digital identification products, systems, and processes, including through the use of federated digital architecture and assertion protocols to convey identity and authentication information across a set of networked systems or through APIs that do not use federated architecture and protocols.
Portability and interoperability can potentially save relying parties (e.g., financial institutions and government entities) time and resources in identifying, verifying, and managing customer identities, including for account opening and authorizing customer account access, and may reduce the risk of identity theft stemming from the repeated exposure of PII. However, as discussed below, portability and interoperability are optional components of a digital ID system and will not be a focus of this Guidance.
2.5. Focus of this Guidance
This Guidance focuses on the use of digital ID systems for CDD, specifically for customer identification and verification at onboarding or account opening and for ongoing CDD monitoring, thus enabling LFIs to fulfill their obligations under Articles 8 and 7, respectively, of the AML-CFT Decision. The Guidance emphasizes, however, that customer identification and verification and ongoing monitoring of the business relationship are only two components of LFIs’ wider CDD obligations, which include identifying and verifying the identities of a legal entity customer’s beneficial owners and understanding the nature of the customer’s business and the nature and purpose of the customer’s business relationship with the LFI. LFIs are also separately required under Article 24 of the AML-CFT Decision to maintain all records and documents obtained through CDD measures for a period of no less than five years from the date of termination of the business relationship with the customer; under FATF standards and UAE regulation, such recordkeeping requirements are technology neutral, meaning they apply equally to records kept in digital and physical (documentary) form.
The Guidance focuses primarily on identity proofing and enrollment and secondarily on authentication; it does not address portability and interoperability, as these components are regarded as optional under international AML/CFT standards and are less directly relevant to the application of CDD measures by LFIs. Particular emphasis will be placed on the use of third-party sources or providers to verify and authenticate customer identity through digital means.
Finally, the Guidance focuses on the use of digital ID systems to identify and verify the identity of customers that are individuals (natural persons). It does not examine the use of digital ID systems to help identify and verify the identity of a legal person’s representative(s) or beneficial owner(s) or to understand and obtain information on the nature and intended purpose of the business relationship—although reliable, independent digital ID systems are important for all of these CDD functions.