Risk Management
Risk Management Regulation and Standards
Risk Management Regulation
C 153/2018 Effective from 27/6/2018Introduction
The Central Bank seeks to promote the effective and efficient development and functioning of the banking system. To this end, banks are required to have a comprehensive approach to risk management, including Board and Senior Management oversight, to ensure their resiliency and enhance overall financial stability.
Risk management, together with internal audit and compliance, comprise key control functions in a bank. The control functions have a responsibility, independent of the management of the bank’s business lines, to provide objective assessment, reporting and/or assurance. The control functions are an essential foundation for effective corporate governance, which is the set of relationships between the bank’s management, board, shareholders and other stakeholders. Collectively these comprise the structure through which the objectives of the bank are set, the means of attaining those established objectives and the monitoring of performance against the established objectives.
In introducing this Regulation and the accompanying Standards, the Central Bank intends to ensure that banks’ approaches to risk management are in line with leading international practices.
This Regulation and the accompanying Standards establish an overarching prudential framework for risk management. Standards and supervisory expectations for selected specific risks are, or will be, established in other Central Bank regulations.
This Regulation and the accompanying Standards are issued pursuant to the powers vested in the Central Bank under the Central Bank Law.
Where this Regulation, or the accompanying Standards, include a requirement to provide information or to take certain measures, or to address certain items listed at a minimum, the Central Bank may impose requirements, which are additional to the list provided in the relevant article.
Objective
The objective of this Regulation is to establish the minimum acceptable standards for Banks’ comprehensive approach to risk management with a view to:
i. Ensuring the soundness of banks; and
ii. Contributing to financial stability.
The accompanying Standards supplement the Regulation to elaborate on the supervisory expectations of the Central Bank with respect to risk management.
Scope of Application
This Regulation and the accompanying Standards apply to all Banks. Banks established in the UAE with significant group relationships, including subsidiaries, affiliates, or international branches, must ensure that the Regulation and Standards are adhered to on a solo and group-wide basis.
Article 1: Definitions
- Affiliate: An entity that, directly or indirectly, controls, is controlled by, or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity, or of the power to direct or cause the direction of the management of another entity.
- Bank: A financial entity that is authorized by the Central Bank to accept deposits as a bank.
- Board: The Bank’s board of directors.
- Central Bank: The Central Bank of the United Arab Emirates.
- Central Bank Law: Union Law No (10) of 1980 concerning the Central Bank, the Monetary System and Organization of Banking as amended or replaced from time to time.
- Central Bank regulations: Any resolution, regulation, circular, rule, standard or notice issued by the Central Bank.
- Group: A group of entities that includes an entity (the 'first entity') and:
- any Parent of the first entity;
- any Subsidiary of the first entity or of any Parent of the first entity; and
- any Affiliate.
- any Parent of the first entity;
- Islamic Financial Services: Shari’a compliant financial services offered by Islamic Banks and Conventional Banks offering Islamic banking products (Islamic Windows).
- Parent: An entity (the 'first entity') which:
- holds a majority of the voting rights in another entity (the 'second entity');
- is a shareholder of the second entity and has the right to appoint or remove a majority of the board of directors or managers of the second entity; or
- is a shareholder of the second entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the second entity.
Or;
- if the second entity is a subsidiary of another entity which is itself a subsidiary of the first entity.
- holds a majority of the voting rights in another entity (the 'second entity');
- Risk appetite: The aggregate level and types of risk a bank is willing to assume, decided in advance and within its risk capacity, to achieve its strategic objectives and business plan.
- Risk limits: Specific quantitative measures that must not be exceeded based on, for example, forward looking assumptions that allocate the bank’s aggregate risk appetite to business lines, legal entities or management units within the bank or group in the form of specific risk categories, concentrations or other measures as appropriate.
- Risk profile: Point in time assessment of the bank’s gross (before the application of any mitigants) or net (after taking into account mitigants) risk exposures aggregated within and across each relevant risk category based on current or forward-looking assumptions.
- Risk governance framework: As part of the overall approach to corporate governance, the framework through which the Board and management establish and make decisions about the bank’s strategy and risk approach; articulate and monitor adherence to the risk appetite and risk limits relative to the bank’s strategy; and identify, measure, manage and control risks.
- Risk management function: Collectively, the systems, structures, policies, procedures and people that measure, monitor and report risk on a bank-wide and, if applicable, group-wide basis.
- Senior Management: The executive management of the Bank responsible and accountable to the Board for the sound and prudent day-to-day management of the Bank, generally including, but not limited to, the chief executive officer, chief financial officer, chief risk officer and heads of the compliance and internal audit functions.
- Subsidiary: An entity (the 'first entity') is a subsidiary of another entity (the 'second entity') if the second entity:
- holds a majority of the voting rights in the first entity;
- is a shareholder of the first entity and has the right to appoint or remove a majority of the board of directors or managers of the first entity; or
- is a shareholder of the first entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the first entity.
Or;
- if the first entity is a subsidiary of another entity which is itself a subsidiary of the second entity.
- holds a majority of the voting rights in the first entity;
- Affiliate: An entity that, directly or indirectly, controls, is controlled by, or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity, or of the power to direct or cause the direction of the management of another entity.
Article 2: Risk Governance Framework
- A Bank must have an appropriate risk governance framework that provides a bank-wide and, if applicable, group-wide view of all material risks. This includes policies, processes, procedures, systems and controls to identify, measure, evaluate, monitor, report and control or mitigate material sources of risk on a timely basis. A bank’s definition and assessment of material risks must take into account its risk profile, nature, size and complexity of its business and structure.
- The Board is in ultimate control of the Bank and bears ultimate responsibility for ensuring that there is a comprehensive risk governance framework appropriate to the risk profile, nature, size and complexity of the Bank’s business and structure.
- The risk governance framework must, at a minimum, provide for the following items:
- A board-approved risk appetite statement including limits for all relevant risk categories and risk concentrations;
- Documentation of the roles and responsibilities of the different parts of the Bank involved in managing risk;
- Policies and procedures to ensure that all material risks are identified, measured, managed, mitigated and reported upon in a timely and comprehensive manner; and
- Contingency arrangements such as business continuity plans and contingency funding plans for risks that may materialize in stress situations.
- A board-approved risk appetite statement including limits for all relevant risk categories and risk concentrations;
- The risk-governance framework, in addition to the risk management function, must include adequately resourced compliance and internal audit functions to assess bank-wide, or if applicable, group–wide adherence, to relevant legislation, policies and procedures and to provide independent assurance regarding the implementation and effectiveness of risk management policies, procedures, systems and controls.
- Senior Management is responsible for the implementation of sound policies, effective procedures and robust systems consistent with the board-approved risk governance framework. The Board remains ultimately accountable, notwithstanding specific responsibilities delegated to Senior Management.
- A Bank must have an appropriate risk governance framework that provides a bank-wide and, if applicable, group-wide view of all material risks. This includes policies, processes, procedures, systems and controls to identify, measure, evaluate, monitor, report and control or mitigate material sources of risk on a timely basis. A bank’s definition and assessment of material risks must take into account its risk profile, nature, size and complexity of its business and structure.
Article 3: Risk Management Function
- A Bank must have an adequately resourced Risk Management Function headed by a chief risk officer or equivalent. The function must be independent of the management and decision-making of the Bank’s risk-taking functions and have a direct reporting line to the Board or a board risk committee.
- The Risk Management Function must include policies, procedures, systems and controls for monitoring and reporting risk and to ensure that risk exposures are aligned with the Bank’s strategy and business plan and consistent with the board-approved risk appetite statement and individual risk limits.
- Exceptions to the Bank’s risk management policies, procedures or limits must be immediately addressed by the appropriate level of management or the Board.
- A Bank must immediately notify the Central Bank when it becomes aware of a significant deviation from its board-approved risk appetite statement, risk management policies or procedures, or that a material risk has not been adequately addressed.
- A Bank must have an adequately resourced Risk Management Function headed by a chief risk officer or equivalent. The function must be independent of the management and decision-making of the Bank’s risk-taking functions and have a direct reporting line to the Board or a board risk committee.
Article 4: Risk Measurement & Use of Models
- A Bank must have systems to measure and monitor risk which are commensurate with the risk profile, nature, size and complexity of its business and structure.
- The Board must have sufficient expertise to understand and oversee the risk measurement systems including any use of models.
- Where a Bank uses models to measure components of risk, it must have appropriate internal processes for the development and approval for use of such models and must perform regular and independent validation and testing of the models. The Board remains ultimately accountable whether the approval for use of models is provided by the Board or through authority delegated to management.
- A Bank must have systems to measure and monitor risk which are commensurate with the risk profile, nature, size and complexity of its business and structure.
Article 5: Stress Testing of Material
- 1. A Bank must implement a forward-looking stress-testing program as part of its comprehensive approach to risk management. Extreme, but plausible, adverse scenarios for a range of material risks must be included in the stress-testing program, commensurate with the size of the Bank’s risk exposures. The results of the stress-testing program must be reflected on an ongoing basis in the Bank’s risk management, including contingency planning and the Bank’s internal assessment of its capital and liquidity.
- A Bank’s internal process for assessing capital and liquidity requirements must take into account the nature and level of risks taken by the Bank. In addition to the specific risks identified in the Central Bank Capital Adequacy and Liquidity Regulations and Standards, a Bank must consider all other material risks.
- 1. A Bank must implement a forward-looking stress-testing program as part of its comprehensive approach to risk management. Extreme, but plausible, adverse scenarios for a range of material risks must be included in the stress-testing program, commensurate with the size of the Bank’s risk exposures. The results of the stress-testing program must be reflected on an ongoing basis in the Bank’s risk management, including contingency planning and the Bank’s internal assessment of its capital and liquidity.
Article 6: Information Systems and Internal Reporting
A Bank must have information systems that enable it to measure, assess and report on the size, composition and quality of risk exposures on a bank-wide and where applicable group-wide, basis across all risk types, products and counterparties. Reports must be provided on a timely basis to the Board and Senior Management, in formats suitable for their use and understanding.
Article 7: Strategic & Operational Decisions
- A Bank must have adequate policies and procedures to ensure that the risks inherent in strategic or major operational initiatives such as changes in systems, business models, or acquisitions are identified, understood and mitigated to the extent possible. At a minimum, policies and procedures must require:
- Approval by the Board, or a board committee, of strategic and major operational decisions; and
- Reporting that enables the Board and Senior Management to monitor and manage these risks on an ongoing basis.
- Approval by the Board, or a board committee, of strategic and major operational decisions; and
- Policies and procedures must establish appropriate levels of approval authority for introducing new products and material modifications to existing products. The Board remains ultimately accountable notwithstanding any delegation of approval authority to Senior Management. At a minimum, policies and procedures must ensure:
- Assessment of the risks and determination that the Bank’s control functions and systems are adequate to measure and mitigate the risks; and
- Reporting that enables the Board and Senior Management to monitor and manage these risks on an ongoing basis.
- Assessment of the risks and determination that the Bank’s control functions and systems are adequate to measure and mitigate the risks; and
- A Bank must appropriately account for risks in its internal pricing, performance measurement and new product approval process, for all significant business activities.
- A Bank must have adequate policies and procedures to ensure that the risks inherent in strategic or major operational initiatives such as changes in systems, business models, or acquisitions are identified, understood and mitigated to the extent possible. At a minimum, policies and procedures must require:
Article 8: Group Risk Management
- Banks, for which the Central Bank is the primary regulator, who have significant group relationships including subsidiaries, affiliates, or international branches, must develop and maintain processes to coordinate the identification, measurement, evaluation, monitoring, reporting and control or mitigation of all internal and external sources of material risk across the group. The process must provide the Board with a solo and group-wide view of all material risks including the roles and relationships of other group entities to one another and to the Bank.
The methods and procedures applied by subsidiaries, affiliates and international branches must support risk management on a group-wide basis. Banks must conduct group-wide risk management and prescribe group policies and procedures, while the boards and Senior Management of subsidiaries and affiliates must have input with respect to the local or regional application of these policies and procedures and the assessment of local or regional risks.
- Where the Central Bank is not the primary regulator of a bank that is part of a Group and any element of its comprehensive approach to risk management is controlled or influenced by another entity in the group, the bank’s risk governance framework must specifically take into account risks arising from the Group relationship and clearly identify:
- Linkages and any significant differences between the Bank’s and the Group’s risk governance framework;
- Whether the bank’s risk management function is derived wholly or partially from Group risk management functions; and
- The process for monitoring by, or reporting to, the Group on risk management.
- Linkages and any significant differences between the Bank’s and the Group’s risk governance framework;
- Banks, for which the Central Bank is the primary regulator, who have significant group relationships including subsidiaries, affiliates, or international branches, must develop and maintain processes to coordinate the identification, measurement, evaluation, monitoring, reporting and control or mitigation of all internal and external sources of material risk across the group. The process must provide the Board with a solo and group-wide view of all material risks including the roles and relationships of other group entities to one another and to the Bank.
Article 9: Disclosure
- A Bank must make publicly available, including through publication in its annual report and on its website, information on its Risk Governance Framework and the nature and extent of its risk exposures.
Article 10: Islamic Banking
- A bank offering Islamic financial services must ensure that its approach to risk management incorporates appropriate measures to comply with Sharī’ah provisions.
- A bank offering Islamic financial services must ensure that its risk governance framework addresses the potential risk exposures arising from Islamic financing instruments with respect to credit, market and liquidity risks as well as equity investment risk and rate of return risk and the operational and reputational risks from failure to adhere to Sharī’ah provisions.
- A bank offering Islamic financial services must ensure that its approach to risk management incorporates appropriate measures to comply with Sharī’ah provisions.
Article 11: Enforcement
- Violation of any provision of this Regulation and the accompanying Standards may be subject to supervisory action as deemed appropriate by the Central Bank.
Article 12: Interpretation of Regulation
- The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
Article 13: Cancellation of Previous Notices
- This Regulation and the accompanying Standards replace all previous Central Bank regulations with respect to risk management.
Article 14: Publication and Application
- This Regulation and the accompanying Standards shall be published in the Official Gazette in both Arabic and English and must come into effect one month from the date of publication.
Risk Management Standards
C 153-2018 STA Effective from 27/6/2018Introduction
- 1. These Standards form part of the Risk Management Regulation. All banks must comply with these Standards, which expand on the Regulation. These Standards are mandatory and enforceable in the same manner as the Regulation.
- 2. A bank's board of directors is in ultimate control of the bank and accordingly, ultimately responsible for the bank’s comprehensive approach to risk management. There is no one-size-fits-all or single best solution. Accordingly, each bank could meet the minimum requirements of the Regulation and Standards in a different way and thus may adopt an organisational framework appropriate to the risk profile, nature, size and complexity of its business and structure. The onus is on the Board to demonstrate that it has implemented a comprehensive approach to risk management. Banks are encouraged to adopt leading practices that exceed the minimum requirements of the Regulation and Standards1.
- 3. The Standards follow the structure of the Regulation, with each article corresponding to the specific article in the Regulation.
1 The Central Bank will apply the principle of proportionality in the enforcement of the Regulation and Standards, whereby smaller banks may demonstrate to the Central Bank that the objectives are met without necessarily addressing all of the specifics cited in the Standards.
Article 1: Definitions
- 1. Affiliate: An entity that, directly or indirectly, controls, is controlled by or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity or of the power to direct or cause the direction of the management of another entity.
- 2. Bank: A financial entity, which is authorized by the Central Bank to accept deposits as a bank.
- 3. Board: The Bank’s board of directors.
- 4. Central Bank: The Central Bank of the United Arab Emirates.
- 5. Central Bank Law: Union Law No (10) of 1980 concerning the Central Bank, the Monetary System and Organization of Banking as amended or replaced from time to time.
- 6. Central Bank regulations: Any resolution, regulation, circular, rule, standard or notice issued by the Central Bank.
- 7. Group: A group of entities that includes an entity (the 'first entity') and:
- 8. Parent: An entity (the 'first entity') which:
- a. holds a majority of the voting rights in another entity (the 'second entity');
- b. is a shareholder of the second entity and has the right to appoint or remove a majority of the Board or managers of the second entity; or
- c. is a shareholder of the second entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the second entity;
Or;
- d. if the second entity is a subsidiary of another entity which is itself a subsidiary of the first entity.
- 9. Risk appetite: The aggregate level and types of risk a bank is willing to assume, decided in advance and within its risk capacity, to achieve its strategic objectives and business plan.
- 10. Risk capacity: The maximum amount of risk a bank is able to assume given its capital base, risk management and control measures, as well as its regulatory constraints.
- 11. Risk culture: A bank’s norms, attitudes and behaviors related to risk awareness, risk taking and risk management and controls that shape decisions on risks, influence the decisions of management and employees during day-to-day activities and is reflected in the risks they assume.
- 12. Risk governance framework: As part of the overall approach to corporate governance, the framework through which the board and management establish and make decisions about the bank’s strategy and approach to risk management; articulate and monitor adherence to the risk appetite and risks limits relative to the Bank’s strategy; and identify, measure, manage and control risks.
- 13. Risk limits: Specific quantitative measures that must not be exceeded based on, for example, forward looking assumptions that allocate the bank’s aggregate risk appetite to business lines, legal entities or management units within the bank or group in the form of specific risk categories, concentrations or other measures as appropriate.
- 14. Risk management function: Collectively, the systems, structures, policies, procedures and people that measure, monitor and report risk on a bank and, if applicable, group-wide basis.
- 15. Risk profile: Point in time assessment of the bank’s gross (before the application of any mitigants) or net (after taking into account mitigants) risk exposures aggregated within and across each relevant risk category based on current or forward-looking assumptions.
- 16. Senior management: The executive management of the bank responsible and accountable to the board for the sound and prudent day-to-day management of the bank, generally including, but not limited to, the chief executive officer, chief financial officer, chief risk officer and heads of the compliance and internal audit functions.
- 17. Subsidiary: An entity (the 'first entity') is a subsidiary of another entity (the 'second entity') if the second entity:
- a. holds a majority of the voting rights in the first entity;
- b. is a shareholder of the first entity and has the right to appoint or remove a majority of the board or managers of the first entity; or
- c. is a shareholder of the first entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the first entity;
Or;
- d. if the first entity is a subsidiary of another entity that is itself a subsidiary of the second entity.
Article 2: Risk Governance Framework
- 1. A bank must establish, implement and maintain a risk governance framework that enables it to identify, assess, monitor, mitigate and control risk. The risk governance framework consists of policies, processes, procedures, systems and controls.
- 2. The risk governance framework must be documented and approved by the Board and must provide for a sound and well-defined framework to address the bank's risks.
- 3. The risk governance framework will vary with the specific circumstances of the bank, particularly the risk profile, nature, size and complexity of its business and structure. A bank must incorporate the following minimum elements into its risk governance framework or demonstrate to the Central Bank that its framework meets the requirements for a comprehensive approach to risk management without the presence of all of the elements set out below:
- a. Board: the board must approve, maintain and oversee the bank’s risk governance framework, including the risk appetite statement, risk limits by legal entity, business line or management units consistent with the risk appetite statement and policies and procedures to implement a comprehensive approach to risk management.
- b. Board risk committee: pursuant to a charter or terms of reference approved by the board, the board risk committee must (a) review and recommend the establishment of and revisions to the bank’s risk governance framework and (b) oversee its implementation by senior management.
- c. Board audit committee: pursuant to a charter or terms of reference approved by the Board, the board audit committee must oversee the independent assessment of the risk governance framework by the internal audit function and the internal audit function’s independent assessment of implementation of the bank’s comprehensive approach to risk management.
- d. Management risk committee: the management risk committee must develop and recommend the overall risk strategy, the risk governance framework and the risk appetite statement to the board or to the board risk committee and must be accountable for an effective bank-wide approach to risk management and for the communication of the comprehensive approach to risk management across the bank.
- e. Risk management function: headed by the chief risk officer (CRO) or equivalent, the risk management function must develop metrics relevant to the risk appetite statement, monitor and report on the risk metrics, escalate breaches and conduct stress tests.
- f. Compliance function: the compliance function must verify that compliance policies are observed and must report to senior management or the board, as appropriate, on how the bank is managing its compliance risk.
- g. Internal audit function: the internal audit function must provide independent assurance to the board and senior management on the quality and effectiveness of a bank’s internal control and risk management policies, procedures and systems, including measurement methodologies and assumptions. It reports directly to the board audit committee.
- h. Business line management: must receive and operationalize risk limits, establish procedures to identify and control risks including monitoring and escalation of breaches and report on risk metrics.
- 4. In defining and assessing risks, a bank must consider both the probability of the risk materializing and its potential impact on the bank. In assessing the potential impact of a risk, a bank must assess factors including but not limited to: (a) potential disruption of the bank’s business operations; (b) effect on profitability, liquidity, capital adequacy and regulatory compliance; and (c) ability of the bank to meet its obligations to its customers or other counterparties.
- 5. A Bank’s risk governance framework must address all material risks, which, at a minimum, must include the following items:
- a. Credit risk;
- b. Market risk;
- c. Liquidity risk
- d. Operational risk;
- e. Risks arising from its strategic objectives and business plans; and
- f. Other risks that singly, or in combination with different risks, may have a material impact on the bank.
- 6. A Board is responsible for the implementation of an effective risk culture and internal controls across the bank and its subsidiaries, affiliates and international branches. The board approved risk governance framework must incorporate a “three lines of defense” approach including senior management of the business lines, the control functions of risk management and compliance and an independent and effective internal audit function:
- a. Business line management - identification and control of risks
- i. Manage and identify risks in the activities of the business line;
- ii. Ensure activities are within the bank’s risk appetite, risk management policies and limits;
- iii. Design, implement and maintain effective internal controls; and
- iv. Monitor and report on business line risks.
- b. Risk management function - sets standards and challenges business lines
- i. Headed by the CRO or equivalent;
- ii. Establish bank-wide or, if applicable, group-wide risk and control strategies and policies;
- iii. Provide oversight and independent challenge of business line accountabilities;
- iv. Develop and communicate risk and control procedures; and
- v. Monitor and report on compliance with risk appetite, policies and limits.
- c. Compliance function - assess bank-wide adherence to requirements
- i. Develop and communicate compliance policies and procedures; and
- ii. Monitor and report on compliance with laws, corporate governance rules, regulations, regulatory codes and policies to which the bank is subject.
- d. Internal audit function - independent assurance
- i. Independently assess the effectiveness and efficiency of the internal control, risk management and governance systems and processes; and
- ii. Independently assess the effectiveness of business line management in fulfilling their mandates and managing risk.
- a. Business line management - identification and control of risks
- 7. The Board must ensure that the risk management, compliance and internal audit functions are properly staffed and resourced and carry out their responsibilities independently and effectively. This includes unrestrained access to all kinds of information needed for the risk management, compliance and internal audit functions to fulfil their tasks.
- 8. The Board must review policies annually and controls on a regular basis with senior management and with the heads of the risk management, compliance and internal audit functions to identify and address significant risks and issues, as well as determine areas that need improvement.
- 9. The Board must provide oversight of senior management. It must hold members of senior management accountable for their actions and enumerate the consequences if those actions are not aligned with the board’s expectations. This includes adhering to the bank’s values, risk appetite and risk culture, regardless of financial gain or loss to the bank.
- 10. Senior management must implement, consistent with the direction given by the board, policies, procedures, systems and controls for managing the risks to which the bank is exposed and for complying with laws, Central Bank regulations and internal policies. This includes comprehensive and independent risk management, compliance and audit functions, as well as an effective overall system of internal controls.
- 11. Senior management must provide the board with the information it needs to carry out its responsibilities, including the supervision of senior management and assessment of the quality of senior management’s performance.
Risk Appetite Statement
- 12. The risk appetite statement is a written articulation of the aggregate level and types of risk that a bank will accept or avoid in order to achieve its business objectives. At a minimum, it must include the following items:
- a. For each material risk, the maximum level of risk that the bank is willing to operate within, expressed as a limit in terms of:
- i. Quantitative measures expressed relative to earnings, capital, liquidity or other relevant measures as appropriate; and
- ii. Qualitative statements or limits as appropriate, particularly for reputation, compliance and legal risks.
- b. Delineation of any categories of risk the bank is not prepared to assume;
- c. The process for ensuring that risk limits are set at an appropriate level for each risk, considering both the probability of loss and the magnitude of loss in the event that each material risk is realized;
- d. The process for monitoring compliance with each risk limit and for taking appropriate action in the event that it is breached; and
- e. The timing and process for review of the risk appetite and risk limits.
- a. For each material risk, the maximum level of risk that the bank is willing to operate within, expressed as a limit in terms of:
- 13. Quantitative risk limits and metrics may include, but are not limited to:
- a. Capital targets beyond regulatory requirements, such as economic capital or capital-at-risk;
- b. Various liquidity ratios and survival horizons;
- c. Net interest income volatility;
- d. Earnings-at-risk;
- e. Value at risk (VaR);
- f. Risk concentrations by internal or external rating;
- g. Expected loss ratios;
- h. Growth ceilings by asset type, business line or type of exposure;
- i. Economic value added; and
- j. Stressed targets for capital, liquidity and earnings.
- 12. The risk appetite statement is a written articulation of the aggregate level and types of risk that a bank will accept or avoid in order to achieve its business objectives. At a minimum, it must include the following items:
Policies and Procedures
- 14. A bank must have a board approved risk management policy, which includes identifying, measuring, evaluating, monitoring, reporting and controlling or mitigating all internal and external sources of material risk. The overarching risk management policy document must reflect an understanding of the risks arising from the bank’s business activities and the relationships among those risks.
- 15. A bank’s documented policies and procedures for risk management must, at a minimum, address the following:
- a. Details of board oversight of risk management, including regular review of risk management policies, review and approval of the risk appetite statement and regular and ad hoc reporting on risk management by senior management, the risk management function, compliance function and internal audit to the Board or committee of the board;
- b. The role and responsibilities of the board risk committee, documented through an appropriate charter or terms of reference;
- c. A process for the identification of material risks, which is likely to be undertaken by a senior management committee overseen by the Board or board risk committee;
- d. A process for ensuring there is a bank-wide or, if applicable, group-wide view that includes identifying, measuring, evaluating, monitoring and controlling risks and that the risk culture is disseminated throughout the bank or, if applicable group, which will involve senior executives, often through a management risk committee or other senior executive committee, as well as the risk management function;
- e. Establishment of an effective control environment including measures embedded in the business lines such as delegated levels of authority, segregation of duties and physical controls such as dual custody, as well as the role of the risk management function in setting standards and challenging the business lines, an independent compliance function to monitor adherence to legal and regulatory requirements as well as internal compliance policies and internal audit to provide independent assurance; and
- f. Ensuring that the bank’s data architecture and information technology systems adequately support the bank’s comprehensive approach to risk management with timely and accurate reporting in readily usable formats.
- 16. A bank must have an appropriate level of granularity in its policies and procedures. Smaller banks with minimal trading activities may address market risks in a single set of policies and procedures, while larger and more complex banks must address market risks in detailed policies and procedures for individual types of market risk. A bank that outsources functions must have specific risk management policies and procedures related to the outsourcing.
Internal Capital Adequacy Assessment Process (ICAAP)
- 17. A bank must have a formal documented process for assessing its overall capital adequacy in relation to its risk profile and a strategy for maintaining its capital levels above regulatory minimum requirements. The assessment must be documented and submitted annually to the Central Bank for review (ICAAP Report).
- 18. A bank must demonstrate the following in its documented ICAAP:
- a. Board and senior management oversight;
- b. Elements of a sound capital assessment process. This includes policies and procedures designed to ensure that the bank identifies, measures and reports all material risks, policies and procedures relating to capital and capital adequacy goals to the level of risk and policies and procedures for internal control to ensure the integrity of the overall management process;
- c. Comprehensive assessment of risks; notably credit, market, operational, interest rate, concentration, liquidity and other;
- d. Monitoring and reporting of risk exposure and related capital needs; and
- e. Internal control review, including the role of internal and external audit where appropriate.
Article 3: Risk Management Function
- 1. The head of the risk management function, the CRO or equivalent, must be of sufficient seniority and stature within the bank, to credibly challenge the heads of business lines and functions. The risk management function is responsible for assisting the Board, board committees, executive committee (including the credit committee) and senior management to develop and maintain the risk governance framework.
- 2. Appointment or dismissal of the CRO must be approved by the Board or board risk committee. If the CRO is removed, the bank must immediately advise the Central Bank of the reasons for such a removal.
- 3. The CRO, or equivalent, must:
- a. Not have a decision-making role in the bank’s risk-taking functions, including credit underwriting, or the finance function;
- b. Have no revenue-generating responsibilities;
- c. Not have remuneration based on the performance of any of the bank’s risk-taking functions;
- d. Not be the chief executive of the bank, or head of the finance, compliance or internal audit function;
- e. Have a direct reporting line to the Board or board risk committee and appropriate reporting lines to senior management; and
- f. Have unfettered access directly to the board risk committee, including the ability to meet without other senior executives present.
- 4. Key activities of the risk management function must include, but are not limited to:
- a. Identifying material individual, aggregate and emerging risks;
- b. Assessing these risks and measuring the bank’s exposure to them;
- c. Supporting the Board in its implementation, review and approval of the bank-wide or if applicable, group-wide risk governance framework;
- d. Ongoing monitoring to ensure risk-taking activities and risk exposures are in line with the board-approved risk appetite, risk limits and corresponding capital or liquidity needs;
- e. Establishing an early warning or trigger system as part of ongoing monitoring to ensure that breaches of the board-approved risk appetite and risk limits are reported on a timely basis to senior management, the Board or board risk-committee as required by board-approved policies;
- f. Influencing and, when necessary, challenging material risk decisions; and
- g. Reporting to senior management and the Board or board risk committee in accordance with the risk governance framework.
Article 4: Risk Measurement and Use of Models
- 1. A bank must use risk measurement methodologies commensurate with the risk profile, nature, size and complexity of the business and the structure of the bank. These could include VaR analysis, scenario analysis and stress testing and single counterparty and concentration limits. Common metrics must be employed on a bank (or group)-wide basis to foster a bank (or group)-wide approach and effective identification and monitoring of risks across the Bank (or Group).
- 2. Risk measurement and modeling techniques must be used in addition to qualitative risk analysis and monitoring. The comprehensive approach to risk management must include policies and procedures for the development and internal approval for use of models or other risk measurement methodologies. Where the models, or data for the models, are supplied by a third party, there must be a process for validation of the model and data relative to the specific circumstances of the bank.
- 3. A bank must perform regular validation and testing of models. This must include evaluation of conceptual soundness, ongoing monitoring including process verification and benchmarking and outcomes analysis, including back-testing. Stress-testing and scenario analysis must be used to take into account the risk of model error and the uncertainties associated with valuations and concentration risks. Widely recognized weaknesses in VaR such as dependence on historical data and inadequate volatility estimates must be explicitly addressed by banks in developing and implementing VaR methodologies. Banks employing VaR or other model methodologies must regularly back-test actual performance against model predictions and adjust their methodologies in light of experience.
- 4. Model-based approaches must be supplemented by other measures. These include qualitative assessment of the logic, judgment and types of information used in models as well as assessments of policies, procedures, risk limits and exposures, especially with respect to difficult to quantify risks such as operational, compliance and reputational.
Article 5: Stress-Testing of Material Risks
- 1. A bank must have a forward looking stress testing program that addresses credit, market and operational risk with the bank taking into account that its risk profile is likely to require capital in excess of the minimum capital requirements. The stress testing program must also include any risk that is material for the bank given the nature of its business. These may include but are not limited to: concentration risk; interest rate risk in the banking book; liquidity risk; currency risk; reputation and compliance risks; contagion risk; country and transfer risks; legal risk; and strategic risk.
- 2. The requirement for a bank to use stress tests and scenario analysis to better understand potential risk exposures under a variety of adverse circumstances is common to both the risk governance framework and ICAAP. A bank must have a comprehensive approach to stress-testing that meets its ICAAP and other risk management requirements. Stress-testing within business lines can be a useful part of the program, however, there must be a means to capture correlations across business lines and obtain a bank-wide or, if applicable, a group-wide overview of performance in stress scenarios.
- 3. A bank’s stress-testing program must be undertaken on a regular basis to facilitate the tracking of trends over time and developments in key risk factors and exposure amounts, in addition to ad hoc stress tests as required. The program must cover a range of scenarios based on reasonable assumptions regarding dependencies and correlations. Senior management and, as applicable, the Board or board risk committee must review and approve the scenarios. The specifics of the program must be tailored to the risk exposures of the bank and, at a minimum, must take into account the following factors:
- a. Bank and Group-specific and system-wide events;
- b. Extreme but plausible shocks as well more gradual changes in key risk parameters such as interest and exchange rates;
- c. Potential reputational risk implications of the bank’s actions in a stress scenario;
- d. Potential for loss of key sources of funding; and
- e. Potential outflows related to customer activity.
- 4. Stress test program results must be periodically reviewed by the Board or the board risk committee. Results must be incorporated into reviews of the risk appetite, the bank’s ICAAP and capital and liquidity planning processes. The risk management function is responsible for recommending any action required, for example adjustments to risk limits or contingency arrangements, based on stress test results. The results of stress tests and scenario analysis must be communicated to the relevant business line management and functional heads within the bank to assist them in understanding and mitigating the risks inherent in their activities. Stress test program results must factor in the bank’s contingency planning, particularly liquidity risk management and contingency funding.
- 5. The identification and management of all material risks must be consistent on a bank-wide and if applicable, group-wide basis. This is of particular importance with respect to a bank’s and, if applicable, a group’s ICAAP, given the significant intersection and mutual reinforcement of risk management and capital adequacy. For example, capital and liquidity implications need to be considered in the determination of risks the bank is prepared to assume and the limits for those risks established in the risk appetite statement. Similarly, the impact on capital and liquidity is an important element of a bank’s procedures for review of new products or business lines or acquisitions.
- 6. From the perspective of capital planning, the ICAAP must explicitly incorporate all material risks, which a bank identifies through its comprehensive approach to risk management. Stress test results must be considered in developing liquidity plans, particularly contingency funding arrangements.
Article 6: Information Systems and Internal Reporting
- 1. A bank’s comprehensive approach to risk management must include policies and procedures designed to provide risk data aggregation and reporting capabilities appropriate for the risk profile, nature, size and complexity of the bank's business and structure. The policies and procedures for risk data aggregation and reporting must provide for the design, implementation and maintenance of a data architecture and information technology infrastructure that supports the bank’s monitoring and reporting needs in normal times and periods of stress.
- 2. A bank’s systems must support supervisory reporting requirements and provision of risk reports to all relevant parties within the bank on a timely basis and in a format commensurate with their needs. The scope of reporting must be proportionate to the business activities and complexity of the bank. Ideally, banks will have a highly automated process, however, certain circumstances may mean that manual intervention is required to aggregate risk data and produce supervisory and internal risk management reports.
- 3. The processes for aggregating the necessary data and producing supervisory and internal risk management reports must be fully documented and establish standards, cutoff times and schedules for report production. The aggregation and reporting process must be subject to high standards of validation through periodic review by the internal audit function using staff with specific systems, data and reporting expertise, particularly where the process requires substantial manual intervention.
- 4. Banks are encouraged to adopt centralized databases with single identifiers and/or uniform naming conventions for legal entities, counterparties, customers and accounts to facilitate accessing multiple records of risk data across the bank or group in a timely manner. Bank systems must be adequate to compile gross and net exposures to institutional counterparties (i.e. interbank, central counterparties) and to capture credit risk concentrations on a bank-wide or, if applicable, group-wide basis, including on and off-balance sheet exposures, for individual counterparties, groups of related counterparties and other concentrations relevant to the bank’s business such as by currency, industry sector or geographic region. Banks are encouraged to have this information available on a daily basis.
Article 7: Strategic and Operational Decisions
- l. A bank must have approval procedures for new products, material modification to existing products and strategic or major operational initiatives such as changes in systems, business models or acquisitions. The procedures must ensure that strategic and major operational decisions require approval by the board or a committee of the board. Approval authority for new products or material changes to existing projects may be delegated by the Board to the appropriate level of management, although the Board remains ultimately responsible.
- 2. In addition to providing for reporting that enables the Board and senior management to monitor the associated risks on an ongoing basis, the procedures must include at a minimum:
- a. An assessment of risks under a variety of scenarios, particularly with more pessimistic assumptions than the base-line case;
- b. An assessment of the extent to which the bank’s risk management, legal and regulatory compliance, information technology, business line and internal control functions have the necessary expertise, systems and other tools to measure and manage the associated risks, if necessary withholding approval if the required measures are not in place; and
- c. An ongoing assessment of risk and performance relative to initial projections and if necessary adapting the risk management treatment in light of experience.
- 3. Mergers and acquisitions, disposals and other changes to bank or group structure can pose special risk management challenges. Risks can arise from conducting insufficient due diligence that fails to identity post-transaction risks or activities conflicting with the bank’s strategic objectives or Risk Appetite. The risk management function must be actively involved in assessing the risks of such transactions and must report its findings directly to the Board or a committee of the board.
Article 8: Group Risk Management
- 1. A bank for which the Central Bank is the primary regulator is required to meet the objectives of the Regulation and Standards on a solo and group-wide basis. Subsidiaries and affiliates, including non-bank entities, must be captured by the bank’s comprehensive approach to risk management and must be part of the overall risk governance framework to ensure that the policies, business strategies, procedures and controls of the subsidiaries and affiliates are aligned with those of the group.
- 2. The boards and senior management of subsidiaries and affiliates remain responsible for their entities’ risk management. The methods and procedures applied by subsidiaries and affiliates must support risk management on a group-wide basis. Parent banks must conduct group-wide risk management and prescribe group policies and procedures, while the boards and senior management of subsidiaries and affiliates must have input with respect to the local or regional application of these policies and procedures and the assessment of local or regional risks.
- 3. Parent banks are responsible for ensuring that the risk management function in subsidiaries and affiliates is adequately resourced and that group reporting lines support the independence of the risk management, compliance and internal audit functions from the risk-taking business lines throughout the group. Parent banks are responsible for ensuring that reporting to the group by subsidiaries and affiliates is sufficiently detailed and timely to support effective group-wide risk management.
- 4. Where the Central Bank is not the primary regulator of a bank that operates a branch in the U.A.E., the branch must have a risk governance framework and risk management function that meets the requirements of the Regulation and Standards. The “three lines of defense” approach must be incorporated within the branch. This will require a senior risk officer, compliance officer and senior internal audit officer with stature within the branch comparable to the business line managers2.
- 5. Reporting relationships between officers of the branch and group business lines and functions must support the independence of the risk management, compliance and internal audit functions from the risk-taking business lines. These branches must provide the Central Bank with unfettered access to any staff of the group involved in the risk management of the branch and any group reports or data that the Central Bank may request.
2 Considering the principle of proportionality and the role of group functions in overseeing the branch, a bank may demonstrate to the Central Bank that it meets the requirements of the Regulation and Standards in some other way.
Article 9: Disclosures
- 1. A Bank must comply with the disclosure requirements. A bank must have a board-approved disclosure policy. A bank must describe in its disclosures its risk management objectives and policies including the following items:
- a. Strategies and processes (for each material risk);
- b. Structure and organization of its risk governance;
- c. Scope and nature of risk reporting and/or measurement systems;
- d. Policies for hedging and/or mitigating risk; and
- e. Strategies and processes for monitoring the continuing effectiveness of hedges/mitigants.
- 1. A Bank must comply with the disclosure requirements. A bank must have a board-approved disclosure policy. A bank must describe in its disclosures its risk management objectives and policies including the following items:
Article 10: Islamic Banking
- 1. The Board offering Islamic financial services must ensure that the comprehensive approach to risk management ensures compliance with Sharī’ah provisions in addition to meeting the other requirements of the Regulation and Standards. The risk governance framework must specifically identify and address for each relevant risk any elements arising from the use of Islamic financial instruments, as well as risks specific to Islamic instruments and agreements. At a minimum, the risk governance framework of a bank offering Islamic financial services must address:
- a. Identifying, monitoring and mitigating potential credit risk exposures that may arise at different stages of the various financing agreements;
- b. Requiring a due diligence review in respect of counterparties prior to deciding on the choice of an appropriate Islamic financing instrument;
- c. Considering separately and on an overall basis liquidity exposures with respect to each category of current account, unrestricted and restricted investment accounts;
- d. Ensuring adequate recourse to Sharī’ah-compliant funds to mitigate liquidity risk;
- e. Identifying and managing equity investment risk including appropriate and consistent valuation methodologies agreed between the bank and its equity investment partners and exit strategies with respect to equity investment activities;
- f. Ensuring compliance with Sharī’ah provisions to mitigate the risk of income having to be donated to charity rather than recognized;
- g. Implementing a comprehensive approach to assessing and reporting on the potential impacts of market factors affecting rates of returns on assets relative to the expected rates of return to investment account holders (rate of return risk);
- h. Using appropriate measures to safeguard the interests of all fund providers which will include but is not limited to ensuring that when investor funds are comingled with the bank’s funds, the basis for asset, revenue, expense and profit allocations are established, applied and reported in a manner consistent with the bank’s fiduciary responsibilities; and
- i. Ensuring that risks arising from the provision of Islamic financial services are appropriately captured in the bank's forward-looking stress-testing program.
- 1. The Board offering Islamic financial services must ensure that the comprehensive approach to risk management ensures compliance with Sharī’ah provisions in addition to meeting the other requirements of the Regulation and Standards. The risk governance framework must specifically identify and address for each relevant risk any elements arising from the use of Islamic financial instruments, as well as risks specific to Islamic instruments and agreements. At a minimum, the risk governance framework of a bank offering Islamic financial services must address:
Standard re Risk Management Requirements for Islamic Banks
CBUAE/BSD N 1198/2021 Effective from 25/2/2021Article (1) Introduction
- 1.1This Standard re risk management requirements for Islamic banks (“the Standard”) forms part of the Risk Management Regulation (Circular 153/2018) issued by the Central Bank on 27th May 2018. Licensed banks that conduct all or part of their activities in accordance with the provisions of Islamic Shari’ah (“Islamic Banks and Banks Housing an Islamic Window” both referred to hereafter as “IBs”) must comply with this Standard. This Standard is mandatory and enforceable in the same manner as the Regulation.
- 1.2Banks housing an Islamic Window should comply with the provisions of this Standard in relation to the Shari’ah compliant businesses and activities. Banks housing an Islamic Window must integrate the risk management requirements stated in this Standard within the existing risk management framework and apply these requirements to the existing modes and contracts within the Islamic Window.
- 1.3This Standard should be read in conjunction with the other risk management standards issued by the Central Bank. The Standard elaborates on risk management aspects pertaining to IBs that have not been specifically addressed in other regulations or standards issued by the Central Bank. IBs should comply with the requirements of this Standard in addition to the requirements stated in the other risk management regulations and standards.
- 1.4It is crucial for IBs to recognize and evaluate the overlapping nature and transformation of risks that exist between and among the categories of the above-mentioned risks. IBs may also face consequential business risks relating to developments in the external marketplace. Adverse changes in IB’ markets, counterparties, or products as well as changes in the economic and political environments in which IBs operate and the effects of different Shari’ah standards are examples of business risk. These changes may affect IBs’ business plans, supporting systems and financial position. In this regard, IBs are expected to view the management of these risks from a holistic perspective.
- 1.5IBs are exposed to reputational risk arising from failures in governance, business strategy and process. Negative publicity about the IBs business practices, particularly relating to Shari’ah non-compliance in their products and services, could have negative impact on their market position, profitability and liquidity.
- 1.6This Standard is issued pursuant to the powers vested in the Central Bank under the provisions of the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities and its amendments (“Central Bank Law”).
- 1.7Where this Standard stipulates to provide information, undertake certain measures, or address certain terms listed as a minimum, the Central Bank may impose requirements, which are additional to those outlined in the relevant article of the Standard.
- 1.8This Standard elaborates on the supervisory expectations of the Central Bank with respect to risk management for Shari’ah compliant businesses and activities.
Article (2) Scope of Application
- 2.1This Standard applies to all IBs. IBs established in the UAE with Group relationships, including Subsidiaries, Affiliates, or international branches, must ensure that the Standard is adhered to on a solo and Group-wide basis.
- 2.3An IB which sets up special purpose vehicles with the objective of conducting specific Shari’ah compliant activity must ensure that the risks arising in the special purpose vehicle are monitored and reported at the group level (risk management on a consolidated basis).
- 2.4This Standard must also be read in conjunction with the Standards and Resolutions issued by the Higher Shari’ah Authority (HSA).
Article (3) Definitions
- a.Affiliate: An entity that, directly or indirectly, controls, or is controlled by, or is under common control with another entity. The term control as used herein to mean the holding, directly or indirectly, of voting rights in another entity, or of the power to direct or cause the direct of the management of another entity.
- b.Board: The Islamic Bank’s board of directors.
- c.Central Bank: The Central Bank of the United Arab Emirates.
- d.Central Bank Law: Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities and its amendments.
- e.Central Bank Regulations: Any resolution, regulation, circular, rule, standard or notice issued by the Central Bank.
- f.Credit Risk: The potential that a counterparty fails to meet its obligations in accordance with agreed terms. Credit risk includes the risk arising in the settlement and clearing transactions.
- g.Compliance with Islamic Shari’ah refers to compliance with Shari’ah in accordance with:
a.resolutions, fatwas, regulations, and standards issued by the Higher Shari’ah Authority in relation to licensed activities and businesses of IBs (“HSA’s Resolutions”), and
b.resolutions and fatwas issued by Internal Shari’ah Supervision Committee (“ISSC”) of the respective IB, in relation to licensed activities and businesses of such institution (“the ISSC’s Resolutions”), provided they do not contradict HSA’s Resolutions.
- h.Displaced Commercial Risk: Risk where the IB may be under market pressure to voluntarily pay a return that exceeds the rate that has been earned on assets financed by Investment Account Holder when the return on assets is under-performing as compared with competitors’ rates.
- i.Equity Investment Risk: Risk arising from entering into a partnership for the purpose of undertaking or participating in a particular financing or general business activity as described in the contract, and in which the provider of finance shares in the business risk.
- j.Fiduciary responsibilities and duties refers to the responsibilities of IB to treat all their fund providers appropriately and in accordance with the terms and conditions of their investment agreements.
- k.Fiduciary Risk: Risk that arises from IBs’ failure to perform in accordance with explicit and implicit Standards applicable to their fiduciary responsibilities.
- l.Fund Providers: Refers to the deposits received by IB and that includes (a) current account holders; and (b) Investment Account Holders.
- m.Group: A group of entities which includes an entity (the ‘first entity’) and:
a.any Controlling Shareholder of the first entity;
b.any Subsidiary of the first entity or of any Controlling Shareholder of the first entity; and
c.any Affiliate, joint venture, sister company and other member of the Group.
- n.Internal Shari’ah Audit: Regular process to inspect and assess the IB’s compliance with Islamic Shari’ah and the level of effectiveness of the IB’s Shari’ah governance systems.
- o.Internal Shari’ah Supervision Committee (ISSC): A body appointed by the IB, comprised of scholars specialized in Islamic financial transactions, which independently supervises the transactions, activities, and products of the IB and ensures they compliance with Islamic Shari’ah in all its objectives, activities, operations, and code of conduct.
- p.Internal Shari’ah Control Division (or Section): Technical division (or section) in the IBs with a mandate to support the ISSC its mandate.
- q.Investment Risk Reserve: Investment risk reserve is the amount appropriated by the IBs out of the income of Investment Account Holder (IAH), after allocating the Mudarib’s share, in order to cushion against future investment losses for IAH.
- r.Investment Account: Refers to the deposits accepted by IBs on the basis of Mudarabah or Wakalah contract or any other profit generating contract.
- s.Islamic Window: Refers to the licensed activities that are conducted in accordance with the Islamic Shari’ah that are carried by financial institutions for their account or for the account of or in partnership with third parties which comply with the regulatory requirements stated in this Standard and other regulations issued by the Central Bank.
- t.Market Risk: Refers to the potential impact of adverse price movements such as benchmark rates, foreign exchange (FX) rates, equity prices and commodity prices, on the economic value of an asset.
- u.Parent: An entity (the ‘first entity’) which:
- a.Holds a majority of the voting rights in another entity (‘the second entity’);
- b.Is a shareholder of the second entity and has the right to appoint or remove the majority of the board of directors or managers of the second entity; or
- c.Is a shareholder of the second entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the second entity; or
- d.If the second entity is a subsidiary of another entity which is itself a subsidiary of the first entity.
- v.Profit Equalization Reserve: The amount appropriated out of the Mudaraba profits, in order to maintain a certain level of return on investment for the Mudarib and unrestricted investment account holders and mitigate displaced commercial risk.
- w.Rate of Return Risk: Overall balance sheet exposures where mismatches arise between assets and balances from fund providers.
- x.Restricted Investment Accounts: The account holders authorize the IBs to invest their funds based on Mudaraba or Wakala contracts with certain restrictions as to where, how and for what purpose these funds are to be invested.
- y.Risk Appetite: The aggregate level and types of risk an IB is willing to assume, decided in advance and approved by the Board and within its risk capacity, to achieve its strategic objectives and business plan.
- z.Risk Limits: Specific quantitative measures that must not be exceeded based on, for example, forward-looking assumptions that allocate the bank’s aggregate risk appetite to business lines, legal entities or management units within the bank or group in the form of specific risk categories, concentrations or other measures as appropriate.
- aa.Risk Profile: Point in time assessment of the bank’s gross (before the application of any risk mitigants) or net (after taking into account risk mitigants) risk exposures aggregated within and across each relevant risk category based on current or forward-looking assumptions.
- bb.Risk Governance Framework: As part of the overall approach to corporate governance, the framework through which the Board and management establish and make decisions about the bank’s strategy and risk approach; articulate and monitor adherence to the risk appetite and risk limits relative to the bank’s strategy; and identify, measure, manage and control risks.
- cc.Risk Management Function: Collectively, the systems, structures, policies, procedures and people that measure, report and monitor risk on a bank-wide and, if applicable, group-wide basis.
- dd.Senior Management: The executive management of the Bank responsible and accountable to the Board for sound and prudent day-to-day management of the Bank, generally including, but not limited to, the chief executive officer, chief financial officer, chief risk officer and heads of the compliance and internal audit functions.
- ee.Shari’ah Non-Compliance Risk: Probability of financial loss or reputational damage that IB might incur or suffer due to not complying with Islamic Shari’ah.
- ff.Subsidiary: An entity (the ‘first entity’) is a subsidiary of another entity (the ‘second entity’) if the second entity:
- a.Holds a majority of the voting rights in the first entity;
- b.Is a shareholder of the first entity and has the right to appoint or remove the majority of the board of directors or managers of the first entity; or
- c.Is a shareholder of the first entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the first entity; or
- d.If the first entity is a subsidiary of another entity which is itself a subsidiary of the second entity.
- gg.Unrestricted Investment Accounts: The account where the holders authorize the IBs to invest their funds based on Mudaraba or Wakala (agency) contracts without laying any restriction on how the investment is to be managed. The IBs can commingle these funds with their own funds and invest them in pooled portfolio.
Article (4) Risk Governance Framework for IB
- 4.1An IB must establish, implement and maintain a risk governance framework that enables it to identify, assess, monitor, mitigate and control risks. The risk governance framework consists of policies, procedures processes, systems, controls and limits. The risk governance framework must be comprehensive and address the specific risks associated with Shari’ah compliant businesses and activities.
- 4.2IBs that are branches of foreign licensed financial institutions must adhere to this Standard or establish equivalent arrangements to ensure regulatory comparability and consistency. The equivalent arrangement, if applicable, should include the matters related to general assembly, the Board and its Committees without contradicting the prevailing laws in the UAE. The equivalent arrangements must be submitted to the Central Bank for approval.
- 4.3IBs must ensure an adequate system of controls with appropriate checks and balances are in place. The controls must (a) comply with the Islamic Shari’ah, (b) comply with applicable regulatory and internal policies and procedures; and (c) take into account the integrity of risk management processes.
- 4.4In addition to the minimum elements of the risk governance framework stated in the Central Bank’s Risk Management Standards (153/2018), IBs must incorporate the following minimum elements into the risk governance framework:
- a.Internal Shari’ah Supervisory Committee,
- b.Internal Shari’ah Compliance, and
- c.Internal Shari’ah Audit.
- 4.5In defining and assessing risks, IBs must consider both the probability of the risk materializing and its potential impact on the IB. In addition to the factors to be assessed in the context of the potential risk impact as stated within Central Bank’s Risk Management Standards (153/2018) the IB must also assess the ability to meet its fiduciary responsibility to Investment Account Holders (IAH), both restricted and unrestricted investment accounts.
- 4.6IBs risk governance framework must address all material risks which at a minimum must include the following items:
- a.Credit Risk;
- b.Market Risk;
- c.Liquidity Risk;
- d.Operational Risk and Shari’ah Non-compliance Risk;
- e.Displaced Commercial Risk;
- f.Equity Investment Risk;
- g.Rate of Return Risk;
- h.Risks arising from its strategic objectives and business plans; and
- i.Other risks that singly, or in combination with different risks, may have a material impact on the IB.
- 4.7The Board is ultimately responsible for developing the IB’s Shari’ah compliant risk governance framework. The framework must incorporate a “three lines of defense” approach. In addition to the stated requirements within the Central Bank’s Risk Management Standards (153/2018) the IB’s approach should also include provisions relating to:
- -Internal Shari’ah Supervision Committee (ISSC);
- -Internal Shari’ah compliance, and
- -Internal Shari’ah Audit.
- 4.8The risk appetite statement must reflect a written articulation of the aggregate level and types of risk that an IB is willing to accept, or avoid, in order to achieve its business objectives. However, an IB should have no tolerance toward Shari’ah non-compliance risk. In addition to the minimum items set-out within Central Bank’s Risk Management Standards (153/2018), an IB’s risk appetite statement must also cover the following risks:
- -Shari’ah Non-Compliance Risk,
- -Displaced Commercial Risk,
- -Rate of Return Risk and
- -Equity Investment Risk.
- 4.9IBs must define and document roles and responsibilities towards IBs’ risk governance framework.
- 4.10The Board’s Risk Committee (“Risk Committee”) is responsible to review and approve the establishment of framework for managing all material risks as part of the overall risk management framework of the IB and must oversee its implementation by the Senior Management.
- 4.11The Risk Committee must supervise and monitor the management of Shari’ah non-compliance risk and set controls in relation to this type of risk, in consultation with the ISSC and through the internal Shari’ah control division, or section.
- 4.12The Risk Committee must ensure there is an information system that enables the IB to measure, assess and report all risks including but not limited to Shari’ah Non-Compliance Risk, Equity Investment Risk and Displaced Commercial Risk. Reports must be provided on a timely manner to the Board and Senior Management, in formats suitable for their use and understanding.
- 4.13In addition to the minimum items set-out within Central Bank’s Risk Management Regulation, IBs must include in its documented ICAAP, within the Internal Control review, provisions relating to the Internal Shari’ah Audit function.
- 4.14IBs should manage risks in accordance with the Shari’ah rules and the scope determined by the contracts IBs use as basis for their financial transactions. IBs may not transfer risks to counterparties, or avoid responsibilities and ownership risks, which result from using specific contracts. IBs may manage these risks by other means that do not conflict with the provisions of Islamic Shari’ah.
Article (5) Risk Management Function of IBs
- 5.1The head of the risk management function, the Chief Risk Officer (CRO) or equivalent is responsible for assisting the Board, board committees, executive committee (including the Internal Shari’ah Supervision Committee), senior management (including Internal Shari’ah Control Division or Section and Internal Shari’ah Audit) to develop and maintain the risk governance framework applicable to its IB.
- 5.2In addition to the key activities set out within the Central Bank’s Risk Management Standards (153/2018), IBs must include identifying, assessing, monitoring and reporting risks associated specifically to Shari’ah compliant business and activities.
Article (6) Risk Measurement and Use of Models for IBs
- 6.1The risk assessment and measurement processes undertaken by IBs must specifically address the risk of loss arising from Mudaraba, Musharaka and Wakala contracts, where applicable. Rigorous risk evaluation (including due diligence) must be adequately conducted in view of the exposure to capital impairment.
Article (7) Stress Testing of Material Risks for IBs
- 7.1IBs must ensure that risks arising from the provision of Shari’ah Compliant business and activities are appropriately captured in the IBs’ forward-looking stress-testing program.
Article (8) Information Systems and Internal Reporting for IBs
- 8.1IBs must ensure that an adequate system of controls with appropriate checks and balances are in place. The controls must:
- a.Ensure compliance with the provisions of Islamic Shari’ah, and
- b.Take into account the integrity of risk management processes.
- 8.1IBs must ensure that an adequate system of controls with appropriate checks and balances are in place. The controls must:
Article (9) Strategic and Operational Decisions
- 9.1As part of the IBs’ overarching approval process, the following at a minimum must be undertaken by IBs:
- a.New Product Approvals must include a risk assessment with a variety of scenarios, particularly with more pessimistic assumptions than the base-line case. The assessment should take into consideration the legal consequences of the underlying Shari’ah structure/contract throughout the life span of the products and services e.g. event of default, restructuring and rescheduling scenarios.
- b.Mergers and acquisitions, disposal and other changes must include adequate due diligence that identifies post-transaction risks or activities conflicting with the IBs’ Governance Framework and other specifities relating to IBs. An IB must have a strategy towards alleviating over-dependence on few types of underlying structures/contracts that may present limitations in terms of tradability and flexibility in the events where risk emerges (e.g. dependence on monetization products).
- 9.1As part of the IBs’ overarching approval process, the following at a minimum must be undertaken by IBs:
Article (10) Disclosures of IBs
- 10.1In addition to the requirements set out within Central Bank’s Risk Management Standards (153/2018) regarding disclosures, IBs must make appropriate and timely disclosure of information to Investment Account Holders. The disclosure should include information related to Profit Equalization Reserves and Investment Risk Reserves, if applicable, so that the investors are able to assess the potential risks and rewards of their investments and to protect their own interests in their decision-making process. Applicable international financial reporting standards must be used for this purpose.
Article (11) Credit Risk
- 11.1IBs must have in place:
- -an appropriate credit strategy, including pricing and tolerance for undertaking credit risks exposures;
- -a risk management structure with effective oversight of credit risk management; credit policies and operational procedures including credit criteria and credit review processes, acceptable forms of risk mitigation, and limit setting;
- -an appropriate measurement and careful analysis of exposures, including market and liquidity-sensitive exposures; and
- -a system (a) to monitor the condition of ongoing individual credits to ensure the financings are made in accordance with the IBs’ policies and procedures, (b) to manage credit challenges according to an established remedial process; and (c) to ensure adequate provisions are allocated.
- 11.2IBs must have in place an appropriate framework for credit risk management and reporting in respect to all assets. This includes credit risk related to different stages of the Shari’ah compliant products and investments. IBs must apply the credit risk principles to credit risks associated with securitization and investment activities.
- 11.3The risk assessment and measurement processes undertaken by IBs must also be applicable to profit sharing assets (Mudaraba and Musharaka) which are classified under equity investments. Rigorous risk evaluation (including due diligence) and controls of these investments are necessary in view of their exposure to capital impairment. This must not contradict the risk sharing nature in these instruments as prescribed by Islamic Shari’ah.
- 11.4IBs must have in place a strategy for financing, using various instruments in compliance with Shari’ah, whereby the strategy recognizes the potential credit exposures that may arise at different stages of the various financing agreements.
- 11.5IBs must manage and account for the credit risk arising from Shari’ah compliant instruments where:
- -no Shari’ah compliant compensation can be imposed, and/or
- -the profit cannot be increased/continued.
- 11.6IBs must have a policy for carrying out a due diligence review in respect of counterparties prior to deciding on the choice of an appropriate Shari’ah compliant financing instrument.
This has to be carried in particular, for transactions involving:
- New ventures with multiple financing modes: IBs should carry out due diligence processes on customers using multiple financing modes to meet specific financial objectives designed to address Shari’ah, legal or tax issues of customers.
- Creditworthiness that may be influenced by external factors: Where significant investment risks are present in participatory instruments, especially in the case of Mudarabah financings, additional counterparty reviews and evaluations will focus on the business purpose, operational capability, enforcement and economic substance of the proposed project including the assessment of realistic forecasts of estimated future cash flows. IBs should put in place risk mitigating structures in place to the extent possible. - 11.7IBs must have in place Shari’ah compliant credit risk mitigating techniques appropriate for each Islamic financing instrument. IBs must be aware of the commencement of exposure to credit risk inherent in different financing instruments such as the non-binding nature of certain contracts. Risk management techniques should not change the nature or the Shari’ah aspects of the contract in order to mitigate the risk.
- 11.8IBs should clearly define their credit risk-mitigating techniques including, but not limited to, having in place:
- -a methodology for setting mark-up rates according to the risk rating of the counterparties, where expected risks should be taken into account in the pricing decisions;
- -permissible and enforceable collateral and guarantees;
- -stipulating the counter party’s commitment to donate in case of default in the legal documentations in accordance with the applicable Shari’ah resolutions and standards;
- -clear documentation as to whether or not purchase orders are cancellable; and
- -clear procedures for taking account of governing laws for contracts relating to financing transactions.
- 11.9In a financing involving several related agreements, IBs must be aware of the binding obligations arising in connection with credit risks associated with the underlying assets for each agreement. IBs must ensure that all components of a financial structure comply with the Shari’ah parameters applicable to combination of contracts.
- 11.10IBs must establish limits on the degree of reliance and the enforceability of collateral and guarantees subject to the provisions set-out within the relevant rules of Islamic Shari’ah.
- 11.11IBs must have appropriate credit management systems and administrative procedures in place to undertake early remedial action in the case of financial distress of a counterparty or, in particular, for managing bad credits, potential and defaulting counterparties. This system should be reviewed on a regular basis. Remedial actions will include both administrative and financial measures.
Administrative measures may inter alia include:- -negotiating and following-up pro-actively with the counterparty through maintaining frequent contact with the counterparty;
- -setting an allowable timeframe for payment or to offer rescheduling (without an increase in the amount of the debt in debt based instruments) or Shari’ah compliant restructuring arrangements;
- -using a debt-collection agency;
- -resorting to legal action, including the attachment of any credit balance belonging to defaulters according to the agreement between them; and
- -making a claim under Shari’ah-compliant insurance as applicable.
Financial measures may include, among others:
- -invoking commitment to donate clauses, where applicable, in accordance with the relevant Shari’ah parameters,; and
- -establishing the enforceability of collateral or third party guarantees.
- 11.12IBs must set appropriate measures for early settlements.
- 11.13IBs must have policies to define adequately the action to be taken by the IB when a customer cancels a non-binding purchase order.
- 11.14IBs should assess and establish appropriate policies and procedures pertaining to the risks associated with their own exposures in parallel transactions.
- 11.15IBs must ensure, whenever possible or applicable, that there is sufficient Shari’ah-compliant insurance coverage of the value of the assets.
- 11.16IBs must have in place an appropriate policy for determining and allocating provisions for (a) non-performing debt categories, including counterparty exposures; and (b) estimated impairment in value of assets.
- 11.1IBs must have in place:
Article (12) Market Risk
- 12.1Requirements on market risk must be read in conjunction with the Market Risk Regulation and accompanying Standards (Circular 164/2018).
IBs must have in place an appropriate framework for market risk management in each stage of the contract, including reporting in respect of all assets held, particularly those that do not have a ready market and/or are exposed to high price volatility. - 12.2IBs must establish a sound and comprehensive market risk management process and information system, which (among others) comprises:
- -a conceptual framework to assist in identifying underlying market risks;
- -guidelines governing risk taking activities in different portfolios of restricted IAH and their market risk limits;
- -appropriate frameworks for pricing, valuation and income recognition; and
- -a strong management information system for controlling, monitoring and reporting market risk exposure and performance to appropriate levels of senior management.
Given that all the required measures are in place (e.g. pricing, valuation and income recognition frameworks, strong MIS for managing exposures, etc.), the applicability of any market risk management framework that has been developed should be assessed taking into account consequential business and reputation risks.
- 12.3IBs must adhere to the fiduciary duty to apply the same risk management policies and procedures to assets held on behalf of restricted Investment Account Holders as they do for assets held on behalf of shareholders and unrestricted Investment Account Holders.
- 12.4IBs must be able to quantify market risk exposures and assess exposure to the probability of future losses in their net open asset positions.
- 12.5IBs must take into consideration the specifics of each Shari’ah compliant instrument in the following manner:
- a.In operating Ijarah contracts, a lessor is exposed to market risk on the residual value of the leased asset at the term of the lease or if the lessee terminates the lease earlier (by defaulting), during the contract
- b.In Salam, an IB as a buyer is exposed to commodity price fluctuations on a long position after entering into a contract and while holding the subject matter until it is disposed of. In the case of parallel Salam, there is also the risk that a failure of delivery of the subject matter by the counterparty which exposes the IBs to commodity price risk as a result of the need to purchase a similar asset in the market in order to honor the parallel Salam contract.
- c.Before acquisition of financial assets not actively traded with the intention of selling them, an IB must analyze and assess the factors attributable to changes in liquidity of the markets in which the assets are traded and which give rise to greater market risk.
IBs may hedge foreign exchange fluctuations arising from general FX spot rate changes in both cross-border transactions and the resultant foreign currency receivables and payables using Shari’ah compliant methods.
- 12.6In the valuation of assets where no direct market prices are available, IBs must incorporate in their own product program a detailed approach to valuing their market risk positions. IBs may employ appropriate forecasting techniques to assess the potential value of these assets.
Where available valuation methodologies are deficient, IBs must assess the need (a) to allocate funds to cover risks resulting from illiquidity and uncertainty in assumptions underlying valuation and realization; and (b) to establish a contractual agreement with the counterparty specifying the methods to be used in valuing the assets
- 12.1Requirements on market risk must be read in conjunction with the Market Risk Regulation and accompanying Standards (Circular 164/2018).
Article (13) Equity Investment Risk
- 13.1IBs must establish an adequate framework towards the management of market risks inherent in the holding of Mudaraba, Musharaka, and Wakala instruments for investment purposes. This includes consideration of quality of the partner, underlying business activities and ongoing operational matters.
- 13.2IBs must have in place appropriate mechanisms to safeguard the interests of all fund providers. Where IAH funds are commingled with the IBs’ own funds, the IBs must ensure that the bases for asset, revenue, expense and profit allocations are established, applied and reported in a manner consistent with the IB’s fiduciary responsibilities.
- 13.3In performing the due diligence review, IBs must consider in evaluating the risk in Mudarabah, Musharakah, and Wakala instruments and the capabilities and risk profiles of potential partners (Mudarib or Musharakah partner). Such due diligence is essential to an IBs’ fiduciary responsibilities as an investor of IAH funds in profit sharing and loss-bearing instruments (such as Mudarabah, Musharkah and Wakala).
- 13.4IBs must consider factors relating to the legal and regulatory environment affecting the equity investment performance during risk evaluation. These factors include policies pertaining to tariffs, quotas, taxation or subsidies and any sudden policy changes affecting the quality and viability of an investment.
- 13.5IBs risk mitigation techniques attaching to lack of reliable information must require its investor to take an active role in monitoring the investment, or the use of specific risk mitigating structures.
- 13.6IBs must define and set the objectives of, and criteria for, investments before using profit-sharing and loss-bearing instruments (such as Mudarabah, Musharkah and Wakala), including the types of investment, tolerance for risk, expected returns and desired holding periods.
- 13.7IBs must have, and keep under review, policies, procedures and an appropriate management structure for evaluating and managing the risks involved in the acquisition of, holding and exiting from loss bearing investments. IBs must ensure proper infrastructure and capacity are in place to monitor continuously the performance and operations of the entity in which IB invest as partners. These should include evaluation of Shari’ah compliance, adequate financial reporting by, and periodical meetings with, partners and proper recordkeeping of these meetings.
- 13.8IBs must identify and monitor the transformation of risks at various stages of investment lifecycles, for example, where the investee’s business involves innovative or new products and services in the marketplace.
- 13.9IBs must analyze and determine possible factors affecting the expected volume and timing of cash flows for both returns and capital gains arising from equity investments.
- 13.10IBs must use Shari’ah compliant risk-mitigating techniques, which reduce the impact of possible capital impairment of an investment. This may include the use of Shari’ah permissible security from the partner.
- 13.11IBs must ensure that their valuation methodologies are appropriate and consistent and must assess the potential impacts of their methods on profit calculations and allocations. The methods must be mutually agreed between the IB and the Mudarib and/or Musharaka partners.
- 13.12IBs must assess and take measures to deal with the risks associated with potential manipulation of reported results leading to overstatements or understatements of partnership earnings.
- 13.13IBs must define and establish exit strategies in respect of their equity investment activities, including extension and redemption conditions for Mudaraba, Musharaka and Wakala investments, subject to the approval of the institution’s Internal Shari’ah Supervision Committee.
- 13.14IBs must be aware that the risks arising from the use of profit-sharing instruments for financing purposes do not include credit risk in the conventional sense but share a crucial characteristic of credit risk because of the risk of capital impairment.
Article (14) Rate of Return Risk
- 14.1Requirements in this area must be read in conjunction with the Interest Rate and Rate of Return Risk in the Banking Book Regulation and accompanying Standards (Circular No. 165/2018). IBs must establish a comprehensive risk management and reporting process to assess the potential impacts of market factors affecting rates of return on assets in comparison with the expected rates of return for IAH.
- 14.2IBs must take necessary steps to ensure that the management processes relating to the identification, measurement, monitoring, reporting and control of the rate of return risk (including appropriate structure) are in place.
- 14.3IBs must be aware of the factors that give rise to rate of return risk. The primary form of rate of return risk to which IBs are exposed comprises increasing long-term fixed rates in the market. IBs must have in place appropriate systems for identifying and measuring the factors, which give rise to rate of return risk.
- 14.4IBs must employ a gapping method for allocating positions into time bands with remaining maturities or repricing dates, whichever is earlier.
- 14.5IBs’ rate of risk return measurement must highlight the importance of cash flow forecasting for instruments and contracts where IBs are required to simulate and assess their behavioral maturity, underlying assumptions and parameters, which must be reviewed periodically for reliability. The materiality of potential threats to future earnings and the usefulness of the resulting information must be considered in determining the type and extent of forecasted behavior for IBs.
- 14.6IBs are encouraged to employ balance sheet techniques to minimize their exposures using the following strategies, among others:
- a.determining and varying future profit ratios according to expectations of market conditions;
- b.developing new Shari’ah-compliant instruments; and
- c.issuing securitization tranches of Shari’ah permissible assets.
Article (15) Displaced Commercial Risk
- 15.1IBs must have in place an appropriate framework for managing displaced commercial risk, where applicable.
- 15.2IBs must have in place a policy and framework for managing the expectations of their shareholders and IAH.
- 15.3IBs must develop and maintain an informed judgement about an appropriate level of the balances of Profit Equalization Reserve, bearing in mind that its essential function is to provide mitigation of displaced commercial risk.
Article (16) Operational and Shari’ah Non-Compliance Risk
- 16.1IBs must have in place an appropriate framework, adequate systems, controls and limits for Operational and Shari’ah Non-Compliance Risk management.
- 16.2IBs must consider the full range of material operational risks affecting their operations, including the risk of loss resulting from inadequate or failed internal processes, people and systems or from external events. IBs must also incorporate possible causes of loss resulting from Shari’ah non-compliance and the failure in their fiduciary responsibilities.
- 16.3IBs must be aware of being exposed to risks relating to Shari’ah non-compliance and risks associated with the IBs’ fiduciary responsibilities towards different fund providers. These risks expose IBs to fund providers’ withdrawals, loss of income or voiding of contracts leading to a diminished reputation or the limitation of business opportunities.
- 16.4IBs’ must be prudent towards Shari’ah compliance and such compliance requirements must permeate throughout the organization and their products and activities. The perception regarding IBs’ compliance with Shari’ah rules and principles is of great importance to their sustainability.
In this regard, Shari’ah compliance is considered as falling within a higher priority category in relation to other identified risks. If IBs do not comply with Shari’ah rules and principles, the impacted transactions should be referred to the ISSC to decide on the appropriate treatment (remedy of contracts, derecognition of profit, etc.) and if needed such incidents may be escalated to the HSA. - 16.5IBs must ensure that their contract documentation complies with Shari’ah with regard to formation, termination and elements possibly affecting contract performance such as fraud, misrepresentation, duress or any other rights and obligations.
- 16.6IBs must keep track of income not recognized due to Shari’ah non-compliance and assess the probability of similar cases arising in the future and ensure that appropriate controls are in place to avoid recurrences. This may include monitoring of income not recognized due to origination from Shari’ah non-compliant activities.
- 16.7IBs must establish and implement a clear and formal policy for undertaking their different and potentially conflicting roles in respect of managing different types of investment accounts. The policy relating to safeguarding the interests of their IAH may include the following:
- -identification of investing activities that contribute to investment returns and taking reasonable steps to carry on those activities in accordance with the IB’s fiduciary and agency duties and to treat all their fund providers appropriately and in accordance with the terms and conditions of their investment agreements;
- -allocation of assets and profits between the IB and their IAH will be managed and applied appropriately to IAH having funds invested over different investment periods;
- -determination of appropriate reserves at levels that do not discriminate against the right for better returns of existing IAH; and
- -limiting the risk transmission between current and investment accounts.
- 16.8IBs must adequately disclose information on a timely basis to their IAH and the markets in order to provide a reliable basis for assessing their risk profiles and investment performance.
Article (17) Compliance with the Standard
- 17.1The IBs should comply fully with these standard requirements within 180 days from publishing this Standard.
- 17.2The Regulatory Development Division of the Central bank shall be the reference for interpretation of the provisions of this Standard.

Standard Regarding Profit Equalization for Islamic Banks
N 1382/2022Article (1)
Introduction
1.1 This Standard Regarding Profit Equalization for Islamic Banks (“the Standard”) constitutes additional requirements to the Standards Re Risk Management Requirements for Islamic Banks issued by the Central Bank. This Standard is mandatory and enforceable.
1.2 This Standard is issued by virtue of the powers conferred by the Central Bank under the provisions of Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities and its amendments (“the Central Bank Law”).
1.3 This Standard elaborates on the supervisory expectations of the Central Bank with respect to profit equalization in Islamic Banks and it must be read in conjunction with the regulations, standards and resolutions issued by the Central Bank and the Higher Shari’ah Authority (“HSA”).
1.4 For the Shari’ah aspects related to profit equalization, all Islamic Banks and banks housing an Islamic Window operating in the UAE (“Islamic Banks or “IBs”) are required to comply with the Shari’ah requirements issued by the HSA.
Article (2)
Scope of Application
2.1 This Standard applies to all IBs. Islamic Banks established in the UAE with Group relationships, including Subsidiaries, Affiliates, or international branches, must ensure that the Standard is adhered to on a solo and group-wide basis.
2.2 Islamic Banks may maintain more than one investment pool for different Investment Account Holders (“IAHs”). Each investment pool may earn a different return depending on the yield of the allocated and/or tagged portfolio of assets. The IBs must maintain the separation of accounts for each investment pool.
Article (3)
Profit Equalization Techniques
3.1 The preponderant portion of the profit-generating funds raised by IBs is based on Mudaraba and Wakala contracts. The funds raised are further deployed into the pool that the IB manages in its capacity as Mudarib or Wakil (“Fund Manager”), for both of which the IB enjoys certain rights and undertakes certain responsibilities. IAHs bear the commercial risk associated with the underlying investments made using their funds unless there is negligence, misconduct or breach of contract from the IB. Nevertheless, the return to be distributed to the IAHs can only be ascertained at the end of the investment period. Contractually, IAHs are only entitled to profits or returns if the pool’s underlying assets perform. The profit sharing and loss bearing contracts expose IBs to different risks, which require adherence to strong risk management governance and a high degree of transparency.
3.2 Therefore, one of the key risks IBs are exposed to is Displaced Commercial Risk (“DCR”) whereby the IB may be under market pressure to voluntarily pay a return that exceeds the rate that has been earned on the assets financed by IAHs’ funds, when the return on assets is underperforming when compared with competitors’ returns.
3.3 IBs are expected to develop and implement a sound methodology to identify, monitor, measure and report the impact of DCR and the amount needed to mitigate the exposure. The methodology must be applied systematically and reviewed regularly. Any changes to the adopted methodology must be justified and approved at the appropriate management level and the Board, if applicable.
3.4 In managing this risk, IBs may adopt the following profit equalization techniques:
- Establish an Investment Risk Reserve (“IRR”). This reserve represents the amount appropriated by the IBs out of the income of IAHs, after allocating the Mudarib’s profit, in order to cushion IAHs against future investment losses. IBs must develop models to determine the size of the IRR and the periodic contributions to be made to build up the IRR over time.
- Establish a Profit Equalization Reserve (PER) by setting aside amounts from the profits before allocation between the IAH and IB. IBs may fully or partly utilize the amount of the PER to improve the returns for IAHs during periods when the investment pool’s profits are below market expectations.
- Unconditionally, and based on the IB’s absolute discretion:
- Forgo part of or its entire profit as the Mudarib, in favor of the IAH in order to increase the profit attributed to the IAH; and/or
- Transfer the IB’s current profits or retained earnings to the IAH on the basis of Hibah / gift.
3.5 IBs may combine more than one technique in order to equalize the profit payout to IAH so as to match the current market returns. The techniques applied must be duly disclosed and compliant with the applicable laws and regulations, including HSA resolutions.
3.6 Subject to 3.1, the IRR and PER must be reflected in the audited financial statements in accordance with the appropriate accounting treatment and must be invested in Shari’ah compliant activities only. Any return from such investment must be credited back to the IRR and PER as applicable.
3.7 IBs must set limits for the amounts transferred to the IRR and PER and must distribute the rest to the IAHs.
3.8 If the IB has various Investment Accounts (“IA”) (with different categories/types/tiers), the IB must ensure that any accumulated reserve (appropriated from a specific category/type/tier) will benefit only the respective IAs, avoiding, in the process, any cross funding.
Article (4)
Governance Requirements
4.1 The Board is responsible for providing robust oversight and a sound monitoring function to ensure that IAs are managed in the best interests of IAH.
4.2 The Board must ensure that profit equalization internal policies, procedures and controls are developed and periodically updated in order to ensure adequate and prudent profit equalization. The Board must ensure that the internal policies, procedures and controls are adequate and duly approved by the Internal Shari’ah Supervision Committee (“ISSC”).
4.3 The Board must review and approve the policies and strategies of the investments, and strategies for the management of DCR, and conduct regular reviews of the investment policies and the performance of the asset portfolio in which IAHs funds are invested.
The broad policies and strategies must address, inter alia, the following areas:
- The management of DCR, including the limits to and tolerance level of DCR;
- the policies and mechanisms used in respect of the IB forgoing its share of profits in favor of the IAH; and
- appropriations to reserves and provisioning, in accordance with the agreed contractual terms and conditions for IAH.
4.4 In order to ensure that profit equalization, including utilization of reserves such as PER and IRR, are appropriately checked and monitored, the Board must form an independent committee (“the Committee”) mandated to scrutinize the utilization of such reserves and to make appropriate recommendations to the Board. The Committee shall coordinate and integrate the implementation of the governance policy framework, with the primary objective of protecting the interests of stakeholders, other than the shareholders, in line with the HSA and ISSC resolutions.
4.5 The Committee shall comprise of at least three members:
- an independent non-executive director (preferably chairing the Committee);
- a member of the Board; and
- a member of the ISSC.
Any increase of membership in the Committee must be filled by independent non-executive directors.
4.6 The Board or its committees must ensure rigorous and diligent oversight policy, process and procedures over the following:
- the financing and investment activities undertaken by the IB using IAH’s funds;
- the fiduciary duties performed by the IB, which must be in accordance with the terms and conditions of the Mudarabah and Wakala contracts between the IB and its IAH; and
- the level of reserve allocation, ensuring that it is appropriate and fair to both existing and new IAHs.
Further, as a part of systems and controls, compliance, internal Shari’ah compliance, internal audit and internal Shari’ah audit functions of the IB must verify the compliance of the IB to approved policies and procedures relating to profit calculation and equalization.
4.7 The Committee shall also evaluate the disclosures made by the IB regarding its asset allocation and investment strategies in respect of IA, in order to monitor closely the performance of IB as managers of such accounts.
4.8 The ISSC must ensure that all IB’s practices related to profit equalization are Shari’ah compliant. This includes reviewing and approving the establishment and any changes to:
- the internal policies and procedures related to profit equalization,
- the contractual arrangements between IAHs and the IB, including terms and conditions and the profit equalization arrangements,
- the profit distribution mechanisms as well as the profit distributed, including appropriation to the PER and IRR,
- the maintenance of the PER and IRR and their deployment, and
- the policy regarding liquidation of PER and IRR.
Article (5)
Disclosure Requirements
5.1 IBs must clearly demonstrate, in IA related contracts and agreements to IAH, any equalization practices that are employed by the IB, including the approach towards allocating a portion of income which is appropriated for building up reserves such as PER and IRR.
5.2 IBs must explicitly disclose the following requirements within IA contracts entered with IAH:
- the rights and liabilities of both parties - in particular, with respect to the circumstances where losses are to be borne by the IAH and the implications on contractual rights of the IAHs with regard to early withdrawal and early redemption;
- the extent of management’s right to appropriate IAH’s share of investment profits in order to build up PER and/or IRR, to use these reserves to equalize profit payouts to IAH, and the deployment of unused balances on these accounts when the relevant Mudarabah contract matures;
- the accountability and responsibility of the IB to disclose accurate, relevant and timely information to the IAH on the investment of their funds, including its performance, investment policies, valuation, and frequency of valuation of the IAH funded assets; and
- the rights of IAH in the event that the IB fails to perform its fiduciary obligations in accordance with the applicable IA contract, that is, in the event of proven negligence or misconduct or breach of contract by the IBs whereby the IBs will have to compensate the IAH for any loss.
5.3 IBs must make adequate and timely public disclosures in their annual report, website and any other means used by the IBs, of any material changes to their policies regarding profit calculation, asset allocation, investment strategies and mechanics of equalization of the returns (if any) in respect of the IAs that they manage. The IB must allocate appropriate time between the announcement and the changes being effective.
5.4 The utilization of PER for equalizing the returns to IAH and shareholders, as well as the use of IRR for covering losses (if any), is an issue of public interest and must be publicized via the usual means used by the IB as well as in the annual report of the IB.
5.5 IBs must disclose information on policies, procedures, product design/type, profit allocation basis and differences between restricted and unrestricted IAH in addition to the clarity and transparency regarding the rates of return and associated risks that are applicable to IA.
5.6 Disclosures on the IBs’ websites and notice boards in branches / client-facing offices must include:
- Percentage of Mudarib Share for the concerned period and at least two previous financial periods in each category of IA.
- Weightages assigned to each category of IAs for the concerned period and at least two previous financial periods.
- The actual monthly/periodic profit/loss distributed to each category of IA during the last 2 years.
- Key highlights of PER and IRR policies.
5.7 IAH disclosures must contain information to reflect, with the appropriate level of detail, the direct and indirect fees, expenses, taxes deducted and the net amount received by the IAH based on the profit calculation and allocation methods adopted by the IB.
5.8 The IB shall be encouraged to provide simplified disclosures, using simple language, and easy- to-understand measures of risk and risk-sharing.
Article (6)
Liquidation Requirements
6.1 In the event of voluntary liquidation, the IBs must dispose the outstanding IRR and PER in accordance with the agreed terms and conditions at the time of establishing the reserves.
6.2 The ownership over the profit equalization reserves, including the IAHs’, must be clearly stated and publicized.
Article (7)
Reporting
Periodic reports must be shared by the Board with the Board committees, ISSC and the Central Bank, stating the current state of the reserve, amount used for the equalization of the profit, and the amount allocated for investment.
Article (8)
Compliance with the Standard
8.1 The IBs must comply fully with the requirements stated in this Standard within 180 days from publishing this Standard.
8.2 The Regulatory Development Division of the Central Bank shall be the reference for the interpretation of the provisions of this Standard.
Appendix: List of disclosures
The disclosures indicated may be made as part of the periodic financial reporting (marked “F” in Tables 1, and 2), or as part of product information published in connection with new products or changes in existing products - for example, prospectuses and offer documents (marked “P” in Tables 1, and 2). Some disclosures may be made under both headings.
Table 1: Investment Accounts (both Unrestricted and Restricted IAH)
F P General Qualitative Disclosures 1. Written procedures and policies applicable to the IAs, including a synopsis of the following: - range of investment products available from the IB;
- characteristics of investors for whom various investment accounts may be appropriate;
- purchase, redemption and distribution procedures; experience of portfolio managers, investment advisors and trustees;
- governance arrangements for the IAH funds; and
- procedures for trading and origination of assets.
√ 2.
Disclosure that IAH funds are invested and managed in accordance with Shari’ah requirements. √ √ 3. Product information and the manner in which the products are made available to investors. √ 4. Bases of allocation of assets, expenses and profit in relation to IAH funds. √ 5. Disclosure on the policies governing the management of both unrestricted and restricted IAH funds, which covers the approaches to the management of the investment portfolio, establishment of reserves, and the calculation, allocation and distribution of profits. √ √ General Quantitative Disclosures 6. PER-to-IA ratio - that is: Amount of total PER / Amount of Aby type of IAH. √ 7. IRR-to-IA ratio - that is: Amount of total IRR / Amount of IA by type of IAH. √ 8. Return on Assets (ROA) - that is: Amount of total net income (before distribution of profit to unrestricted IAH) / Total amount of assets financed by shareholders’ equity and minority interests, unrestricted IAH, and current accounts and other liabilities. √ 9. Return on Equity (ROE) - that is, Amount of total net income
(after distribution of profit to IAH) / Amount of shareholders ’ equity.√ 10. Ratios of profit distributed to IA by type of IAH. √ √ 11. Ratios of financing to IA by type of IAH. √ Table 2: Unrestricted Investment Accounts
F P Additional Qualitative Disclosures 1. General investment objectives and policies that are offered to the unrestricted IAH based on the general business strategy and risk-sharing policies of the IB (including commingling of funds). √ 2. Disclosure on the major changes in the investment strategies that affect the investment accounts (including commingling of funds). √ √ 3. Method for calculation and distribution of profits. √ 4. Rules governing the transfer of funds to or from PER andIRR. √ √ 5. Bases applied for charging expenses to unrestricted IAH. √ √ 6. Description of total administrative expenses charged to unrestricted IAH. √ Additional Quantitative Disclosures 7. Total amount of unrestricted IAH funds, and sub-totals by asset category. √ 8. Share of profits earned by unrestricted IAH, before transfers to or from reserves (amount and as a percentage of funds invested). √ 9. Share of profits paid out to unrestricted IAH, after transfers to or from reserves (amount and as a percentage of fundsinvested). √ 10. Changes on PER during the year. √ 11. Changes on IRR during the year. √ 12. Disclosure of the utilization of PER and/or IRR during theperiod. √ 13. Profits earned and profits paid out over the past three to fiveyears (amounts and as a percentage of funds invested). √ 14. Amount of total administrative expenses charged to unrestricted IAH. √ 15. Average declared rate of return or profit rate on unrestricted IA by maturity (3-month, 6-month, 12-month, 36-month). √ 16. Changes in asset allocation in the last six months. √ 17. Off-balance sheet exposures arising from investment decisions, such as commitments and contingencies. √ 18. Disclosure of limits imposed on the amount that can be invested in any one type of asset. √ √ Credit Risk
Credit Risk Management
Large Exposures Regulation
C 1/2023 Effective from 26/7/2023Introduction
The Central Bank seeks to promote the effective and efficient development and functioning of the banking system. To this end, the Central Bank is issuing this regulation setting large exposure limits for Banks.
The regulation is aimed at banks' management of risk concentrations, and in particular the risk that the default of a single counterparty or Group Of Connected Counterparties would endanger the solvency of the Bank.
Scope
This regulation applies to all Banks, including branches of foreign banks, operating in the UAE.
The requirements apply at every tier within a banking group, meaning at solo and consolidated level, and all levels of sub-consolidation.
Objective
This regulation is seeking to manage concentrations and limit the maximum possible loss a Bank could incur due to the failure of a single counterparty or Group Of Connected Counterparties.
Article (1): Definitions
1.1 Bank: Any juridical person licensed in accordance with the provisions of the Central Bank Law, to primarily carry on the activity of taking deposits, and any other Licensed Financial Activities.
1.2 Branch Capital: shall mean the fully paid-up capital at branch level as defined in the Minimum Capital for Banks Regulation.
1.3 Central Bank: The Central Bank of the United Arab Emirates.
1.4 Central Bank Law: Decretal Federal Law No. (14) of 2018 regarding the Central Bank & Organization of Financial Institutions and Activities as amended.
1.5 ECAI: External Credit Assessment Institution.
1.6 Intraday: funds which can be accessed during the business day, usually to enable financial institutions to make payments in real time.
1.7 Group Of Connected Counterparties: a group of connected counterparties as defined in Article 4 of this regulation.
1.8 Qualifying Central Counterparty: A qualifying central counterparty as defined in the Capital Adequacy Standards.
1.9 Related Parties: the Group and its Controlling Shareholders, members of the board and senior management (and their Relatives) and persons with control, joint control or significant influence over the Bank (and their Relatives).
1.10 Relatives: The individual's parents, siblings and children.
1.11 Sovereign: for the purpose of this regulation, sovereign refers to the UAE Federal Government and any other foreign sovereign with a long term credit rating of at least AA- (or its equivalent) issued by an ECAI recognized by the Central Bank.
1.12 The Unknown Client: where the counterparty of an exposure is unknown to the Bank, for example because a structure does not disclose exposures below a certain threshold, the exposure should be assigned to “the unknown client', to which the large exposure limit applies. For the avoidance of doubt, the exposure to the unknown client is the aggregate of all exposures across all such transactions, regardless of whether they are related in any way.
Article (2): Definition of a Large Exposure
2.1 The sum of all exposure values of a Bank to a counterparty or to a Group Of Connected Counterparties is considered a large exposure if it is equal to or exceeds 10% of the Bank's Tier 1 capital.
2.2 The exposure value must be calculated in accordance with the provisions of this regulation.
Article (3): Large Exposure Limits
3.1 The sum of all the exposure values of a Bank to a single counterparty or to a Group Of Connected Counterparties must not be higher than 25% of the Bank's Tier 1 capital at all times.
3.2 For a global systemically important Bank's exposures to another global systemically important bank, the large exposure limit is 15%. When a bank is identified by the Financial Stability Board as a global systemically important bank, Banks must apply the 15% limit within 12 months of publication of the list by the Financial Stability Board.
3.3 For exposures to the UAE local governments and their public sector entities, the large exposure limits as set out in Article 12 of this regulation apply.
3.4 Additional restrictions apply to exposures to Related Parties as set out in Article 18 of this regulation.
3.5 Breaches of the limits described in Article 3.1 to 3.4 must be communicated immediately to the Central Bank and must be rapidly rectified.
3.6 For any breaches of the limits described in Article 3.1 to 3.4, the Tier 1 capital will be reduced by the amount by which the limit is breached.
3.7 The Central Bank may in exceptional cases, if it deems the risk to be low, waive the application of Article 3.6 for exposures to a particular counterparty or Group of Connected Counterparties, and determine a risk-weight to be applied to the amount by which the limit is breached instead.
Article (4): Connected Counterparties
4.1 Two or more counterparties shall be considered a Group Of Connected Counterparties if at least one of the following criteria is satisfied:
4.1.1 Control relationship: one of the counterparties, directly or indirectly, has control over the other(s).
4.1.2 Economic interdependence: if one of the counterparties were to experience financial problems, in particular funding or repayment difficulties, the other(s), as a result, would also be likely to encounter funding or repayment difficulties.
4.2 Banks must assess the relationship amongst counterparties against the criteria listed in Article 4.1 and take into account at least the criteria listed below in Article 4.3 and 4.4.
4.3 The following criteria must be considered to assess the control relationship between counterparties:
4.3.1 If one counterparty owns more than 50% of the voting rights of the other counterparty, Banks must consider the control relationship established;
4.3.2 Voting agreements whereby a majority of voting rights in one counterparty are controlled by another counterparty pursuant to an agreement with other shareholders;
4.3.3 Significant influence on the appointment or dismissal of an entity's board or senior management, such as the right to appoint or remove a majority of members in those bodies, or the fact that a majority of members have been appointed solely as a result of exercising an individual entity's voting rights;
4.3.4 Significant influence on senior management, such as where a counterparty has the power, through a contract or otherwise, to exercise a controlling influence over the management or policies of another counterparty, for example through consent rights over key decisions.
4.3.5 Control relationships as established by the applicable accounting standards.
4.4 The following criteria must be considered to assess the economic interdependence between counterparties:
4.4.1 Where at least half of one counterparty's annual gross receipts or gross expenditures is derived from transactions with the other counterparty. For example, the owner of a real estate portfolio rented out for the most part to a single tenant;
4.4.2 Where one counterparty has guaranteed an exposure of the other counterparty, or is liable by other means, and the exposure is so significant that the guarantor is likely to default if a claim occurs;
4.4.3 Where a significant part of one counterparty's output is sold to another counterparty, and that counterparty cannot easily be replaced by other customers;
4.4.4 When the expected source of funds to repay the loans of both counterparties is the same and neither counterparty has another independent source of income from which the loan may be serviced and fully repaid;
4.4.5 Where it is likely that the financial problems of one counterparty would cause difficulties for another counterparty in terms of full and timely repayment of liabilities;
4.4.6 Where the insolvency or default of one counterparty is likely to be associated with the insolvency or default of another counterparty;
4.4.7 When two or more counterparties rely on the same source for the majority of their funding and, in the event of the common provider's default, an alternative provider cannot be found and funding problems of one counterparty are likely to spread to another counterparty due to one-way or twoway dependence on the same main funding source.
4.5 Where a control relationship has been established based on the criteria set out in Article 4.3 above, a Bank may still approach the Central Bank to demonstrate and seek agreement that such control does not result in the entities concerned constituting a Group Of Connected Counterparties, for example due to specific circumstances and corporate governance safeguards.
4.6 Where economic interdependence has been established based on the criteria in Article 4.4 above, a Bank may still approach the Central Bank to demonstrate and seek agreement that a counterparty, while economically closely related to another counterparty, may still overcome financial difficulties, including the other counterparty's default.
4.7 Banks may apply proportionality and apply a risk-based approach when assessing economic interdependence. However, Banks must identify the Group Of Connected Counterparties on the basis of economic interdependence in all cases where the sum of all exposures to one individual counterparty exceeds 5% of Tier 1 capital.
4.8 The Central Bank may at its own discretion determine that certain exposures must be considered a Group Of Connected Counterparties.
Article (5): Reporting Requirements
Banks must report the following to the Central Bank in the manner established by the Central Bank:
5.1 All exposures measured in accordance with the provisions of this regulation, taking into account the effects of credit risk mitigation, equal to or above 10% of the Bank's Tier 1 capital;
5.2 All exposures measured in accordance with the provisions of this regulation without the effects of credit risk mitigation taken into account equal to or above 10% of the Banks' Tier 1 capital;
5.3 All the exempted exposures with values equal to or above 10% of the Bank's Tier 1 capital;
5.4 The largest 20 exposures to counterparties measured in accordance with Article 6 of this regulation and included in the scope of application, irrespective of the values of these exposures to the Bank's Tier 1 capital;
5.5 All exposures subject to additional restrictions as set out in Article 18 of this regulation, regardless of their size; and
5.6 Exposures by sector, country, and currency.
Article (6): Measurement of Exposures
6.1 As a general principle, the exposure values that must be considered to identify large exposures are the exposures defined under the risk-based capital framework, including both on- and off- balance sheet exposures, both in the banking and the trading book, and including instruments with counterparty credit risk.
6.2 Exposure amounts that are deducted from Tier 1 capital must not be added to the exposures to that counterparty for the purpose of the large exposure framework. This exclusion does not apply to 1,250% risk-weighted exposures.
6.3 As a general principle, the exposure value is the accounting value of the exposure, i.e. reduced by the specific provisions and value adjustments.
6.4 For instruments that give rise to counterparty credit risk, but are not securities financing transactions, the exposure value must be the exposure at default in accordance with the standardized approach for counterparty credit risk.
6.5 The exposure value for securities financing transactions must be calculated using the comprehensive approach with standard supervisory haircuts for credit risk mitigation as set out in the capital adequacy regulation.
6.6 The exposure amount for off-balance sheet exposures is calculated by converting the off- balance sheet items into credit exposure equivalents through the use of credit conversion factors as set out in the standardized approach for credit risk. For the purpose of the large exposures framework, the minimum credit conversion factor applied for off-balance sheet items is 10%.
Article (7): Credit Risk Mitigation Techniques
7.1 Only the following credit risk mitigation techniques are considered eligible for the purposes of the large exposure framework:
7.1.1 Unfunded credit protection meeting the minimum requirements and eligibility criteria for the recognition of unfunded credit protection under the standardized approach; and
7.1.2 Financial collateral qualifying as eligible financial collateral under the standardized approach.
7.2 Other forms of collateral that are only eligible under the internal-ratings based approach are not eligible to reduce exposure values for the purposes of the large exposure framework.
7.3 A Bank must recognize eligible credit risk mitigation techniques in the calculation of an exposure whenever it has used this technique to calculate the risk-based capital requirements, provided the technique also meets the conditions for recognition under the large exposures framework.
7.4 Hedges with maturity mismatches are recognized in accordance with the risk-based capital framework.
7.5 In case of a maturity mismatch in respect of credit risk mitigants that are recognised in the risk-based capital requirements, the adjustment of the credit protection to calculate the large exposure is determined using the same approach as in the risk-based capital requirements.
7.6 Where legally enforceable netting arrangements are in place for loans and deposits, the exposure values for large exposures purposes may be calculated according to the same calculation the Bank uses for capital requirements purposes.
Article (8): Credit risk mitigation techniques that reduce the original exposure
8.1 A Bank must reduce the value of the exposure to the original counterparty by the amount of the eligible credit risk mitigation technique recognised for risk-based capital requirements purposes.
8.2 The recognised amount mentioned in Article 8.1 is:
8.2.1 The value of the protected portion in the case of unfunded credit protection;
8.2.2 The value of the portion of claim collateralised by the market value of the recognised financial collateral when the Bank uses the simple approach for risk-based capital requirements purposes;
8.2.3 The value of the collateral as recognised in the calculation of the counterparty credit risk exposure value for any instruments with counterparty credit risk, such as over-the-counter derivatives;
8.2.4 The value of collateral adjusted after applying the required haircuts, in the case of financial collateral when the Bank applies the comprehensive approach. The haircuts used to reduce the collateral amount are the supervisory haircuts under the comprehensive approach - internally modelled haircuts must not be used.
Article (9): Recognition of Exposures to Credit Risk Mitigation Providers
9.1 Whenever a Bank recognises a reduction of the exposure to the original counterparty due to an eligible credit risk mitigation technique, it must also recognise an exposure to the credit risk mitigation providers. The amount assigned to the CRM provider is the amount by which the exposure to the original counterparty is reduced.
Article (10): Calculation of Exposure Value for Trading Book Positions
10.1 A Bank must add any exposures to a single counterparty arising in the trading book to any other exposures to that counterparty in the banking book to calculate its total exposure to that counterparty.
10.2 Trading book positions not corresponding to concentration risk associated with the default of a single counterparty are out of the scope of the large exposure framework. As such, concentrations in commodities or currencies are not subject to the large exposures limit. Banks must nevertheless appropriately evaluate and manage concentrations in exposures to commodities and currencies.
10.3 The exposure value of straight debt instruments and equities is defined as the accounting value of the exposure.
10.4 Instruments such as swaps, futures, forwards and credit derivatives must be converted into positions following the risk-based capital requirements. Such instruments are decomposed into their individual legs; and only the legs representing exposures in scope of the large exposures framework must be considered. This implies that legs that do not entail any risk due to the default of the counterparty are not considered.
10.5 In the case of credit derivatives that represent sold protection, the exposure to the referenced name must be the amount due in case the respective referenced name triggers the instrument, minus the absolute value of the credit protection. In the case of credit-linked notes, the protection seller needs to consider positions both in the bond of the note issuer and in the underlying referenced by the note. For positions hedged by credit derivatives, see Articles 11.3 to 11.6 of this regulation.
10.6 The exposure value for options is the change in option price that would result from a default of the underlying instrument.
Hence, the exposure value of a long call option is its market value.
The exposure value of a short put option is equal to its strike price minus its market value.
The exposure value of a short call option equals a negative exposure equal to the market value.
The exposure value of a long put option equals a negative exposure equal to the strike price of the option reduced by its market value.
The resulting positions are aggregated with those from other exposures. After this aggregation, negative net exposures are set to zero.
10.7 Exposure values of a Bank's investments in transactions, such as index positions, securitisations, hedge funds or investment funds, must be calculated in accordance with the same rules as for similar instruments in the banking book. This implies that the amounts invested in such a structure may be assigned to the structure itself, defined as a counterparty distinct from the counterparties corresponding to the underlying assets or to the unknown client, following the rules described in Articles 15.1 to 15.6 of this regulation.
10.8 Covered bonds held in the trading book are subject to the general treatment for covered bonds described in Article 14 of this regulation.
Article (11): Offsetting Long and Short Positions in the Trading Book
11.1 Banks may offset long and short positions in the same issue and consider only the net position in that issue for the purpose of calculating a Bank's exposure to that particular counterparty.
Two issues are defined as the same if the issuer, coupon, currency and maturity are all identical.
11.2 Positions in different issues from the same counterparty may be offset only when the long position is senior to the short position, or if the positions are of the same seniority.
11.3 For positions hedged by credit derivatives, the hedge may be recognised provided the underlying of the hedge and the position hedged fulfil the requirements of Article 11.2, i.e. that the long position is senior or of equivalent seniority to the short position.
11.4 To determine the relative seniority of positions, securities may be allocated into broad buckets of degrees of seniority, such as for example “equity”, “subordinated debt”, and “senior debt”.
11.5 Offsetting of long and short positions in different issues relating to the same counterparty is not allowed in case the Bank chooses not to allocate securities to seniority buckets as described in Article 11.4.
11.6 For positions hedged by credit derivatives, the provisions of Article 9.1 of this regulation apply and a new exposure to the credit protection provider must be recognised.
11.7 In case the credit protection takes the form of a credit default swap, and either the provider of the credit default swap or the referenced entity is not a financial entity, the amount to be assigned to the credit protection provider is the counterparty credit risk exposure value as calculated under the standardized approach for counterparty credit risk.
11.8 Financial entities, for this purpose, includes regulated financial institutions, including nonbank financial institutions and foreign financial institutions, as well as unregulated financial institutions whose main business includes the management of financial assets, lending, factoring, leasing, provision of credit enhancements, securitisation, investments, financial custody, central counterparty services, proprietary trading and other financial services activities identified by supervisors.
11.9 Netting across the banking and trading books is not permitted.
11.10 When the result of offsetting is a net short position with a single counterparty, this net exposure need not be considered as an exposure for the purposes of the large exposure framework.
Article (12): Sovereign Exposures and Public Sector Entities
12.1 Banks' exposures to the UAE Federal Government, the Central Bank of the UAE, and exposures to other foreign sovereigns rated at least AA- and their central banks are exempted from the large exposure limit.
12.2 A Banks' aggregate exposure to the Emirates Governments, meaning the exposure to all of the Emirates Governments combined and inclusive of exposures to their non-commercial public sector entities, is subject to an aggregate limit of 150% of Tier 1 capital. Exposures directly to the Emirates Governments are not restricted at individual level, but exposures to their non-commercial entities are restricted at individual level to 25% of Tier 1 capital.
12.3 Exposures to the commercial entities of UAE Federal and Emirates Governments are subject to an individual limit of 25% and an aggregate limit of 100% of Tier 1 capital.
12.4 A commercial public sector entity that is selfsustainable, meaning, at a minimum, that it is profitable and can service its debt from its own resources without a need for any implicit or explicit government support, can be considered as a counterparty separate from its government parent subject to Central Bank approval. This public sector entity, and the Group Of Connected Counterparties it belongs to, is then subject to the general large exposure limit, but not to the aggregate limits described in Article 12.2 and 12.3.
12.5 Exposures or parts thereof guaranteed by, or secured by instruments issued by, the counterparties listed in Article 12.1 are exempted from the large exposure limit to the extent that the eligibility criteria for the recognition of credit risk mitigation are met.
12.6 Where two or more entities that are outside the scope of the exemption described in Article 12.1 are controlled by or economically dependent on an entity that falls within the scope of Article 12.1, but are otherwise not connected, those entities need not be deemed to constitute a Group Of Connected Counterparties.
12.7 While the exposures described in Article 12.1 are exempted from the large exposure limit, these exposures must nevertheless be reported if these exposures meet the criteria for definition as a large exposure.
12.8 Where an exposure to an exempted entity is hedged by a credit derivative, an exposure to the provider of the credit protection must nevertheless be recognised in accordance with Articles 9.1 and 11.7 of this regulation.
12.9 Non-commercial public sector entities of the UAE Federal Government are subject to the general large exposure limit as set out in Article 3.1 of this regulation, with the exception of those ‘treated as sovereign' under the credit risk standards.
12.10 The Central Bank may, on an exceptional, temporary and case-by-case basis, increase the aggregate limit set out in Article 12.2. Such an exception will detail the new maximum permissible limits, and the risk-weight add-on applicable to the amounts by which the normal limits as set out in Article 12.2 are exceeded.
12.11 The exemption set out in Article 12.1 also applies to multilateral development banks for which a 0% risk weight applies under the Central Bank's credit risk standards.
Article (13): Interbank Exposures
13.1 Intraday interbank exposures are exempted from the large exposure framework.
13.2 Any other interbank exposures are subject to the large exposure limit set out in Article 3 of this regulation.
13.3 Banks incorporated in the UAE must limit the aggregate exposure to their foreign branches to 30% of Tier 1 capital, where those branches are located in a jurisdiction which requires them to hold capital in that jurisdiction. The exposure value is equal to the sum of all of the branch's liabilities where the head office is the counterparty, including the dotation capital. The denominator is the entity's Tier 1 capital.
Article (14): Covered Bonds
14.1 For covered bonds, an exposure to the issuing Bank must be assigned equal to 100% of the nominal value of the Bank's covered bond holding, or, where the covered bond satisfies the conditions set out in Article 14.2 below, an exposure to the issuing Bank of at least 20% of the nominal value of the Bank's covered bond holding.
14.2 To be eligible to be assigned an exposure of less than 100%, a covered bond must satisfy all of the following conditions:
14.2.1 It must meet the definition of a covered bond: Covered bonds are bonds issued by a bank or mortgage institution and are subject by law to specific supervision designed to protect bond holders. Proceeds deriving from the issue of these bonds must be invested in conformity with the law in assets which, during the whole period of the validity of the bonds, are capable of covering claims attached to the bonds and which, in the event of the failure of the issuer, would be used on a priority basis for the reimbursement of the principal and payment of the accrued interest.
14.2.2 The pool of underlying assets must consist exclusively of:
14.2.2.1 Claims on, or guaranteed by, sovereigns, their central banks, public sector entities or multilateral development banks;
14.2.2.2 Claims secured by mortgages on residential real estate that would qualify for a 35% or lower risk weight under the standardized approach for credit risk and having a loan-to-value ratio of 80% or lower; and/or
14.2.2.3 Claims secured by commercial real estate that would qualify for the 100% or lower risk-weight under the standardized approach for credit risk and with a loan-to-value of 60% or lower.
14.2.3 The nominal value of the pool of assets assigned to the covered bond by its issuer should exceed its nominal outstanding value by at least 10%. This requirement can be met also in jurisdictions where the former 10% is not required by law, however in that case the issuing bank needs to regularly publicly disclose that their covered pool meets the 10% requirement in practice.
This 10% additional collateral may also include substitution assets, such as cash or short term secure assets, and derivatives entered into to hedge risks arising in the covered bond programme.
14.2.4 The requirements regarding maximum loan-to-value ratio for residential and commercial real estate referred to in Article 14.2.2 must be met following an objective market value of the collateral and frequent revaluation of the collateral.
Article (15): Collective Investment Undertakings, Securitisation Vehicles, and other Structures
15.1 Banks must consider exposures even when a structure lies between the Bank and the exposures, that is, even when the Bank invests in structures through an entity which itself has exposures to assets (hereafter referred to as the "underlying assets"). Banks must assign the exposure amount, i.e. the amount invested in a particular structure, to specific counterparties following the approach described below. Such structures include funds, securitisations and other structures with underlying assets.
15.2 A Bank may assign the exposure amount to the structure itself, defined as a distinct counterparty, if it can demonstrate that the Bank's exposure amount to each underlying asset of the structure is smaller than 0.25% of its Tier 1 capital, considering only those exposures to underlying assets that result from the investment in the structure itself and using the exposure value calculated according to Article 15.8 and 15.9. This condition is always considered fulfilled whenever a Bank's whole investment in a structure is less than 0.25% of the Bank's Tier 1 capital. In this case, a Bank is not required to look through the structure to identify the underlying assets.
15.3 A Bank must look through the structure to identify those underlying assets for which the underlying exposure value is equal to or above 0.25% of its Tier 1 capital. In this case, the counterparty corresponding to each of the underlying assets must be identified so that these underlying exposures can be added to any other direct or indirect exposure to the same counterparty. The Bank's exposure amount to the underlying assets that are below 0.25% of the Bank's Tier 1 capital may be assigned to the structure itself (ie partial look- through is permitted).
15.4 If a Bank is unable to identify the underlying assets of a structure:
15.4.1 Where the total amount of its exposure is less than 0.25% of its Tier 1 capital, the total exposure amount of the Bank's investment must be assigned to the structure;
15.4.2 In other cases, the total exposure amount of the Bank's investment must be assigned to “The Unknown Client”.
15.5 The Bank must aggregate all unknown exposures as if they related to a single counterparty, referred to as “The Unknown Client”, to which the large exposure limit applies.
15.6 Banks must not circumvent the large exposure limit by investing in multiple structures with identical underlying assets that represent individually immaterial transactions.
15.7 If the look-through approach does not need to be applied, a Bank's exposure to the structure must be the nominal amount invested in the structure.
15.8 When the look-through approach is required in accordance with this Article, the exposure value assigned to the counterparty is equal to the pro rata share that the Bank holds in the structure multiplied by the value of the underlying asset in the structure. Thus, a Bank holding a 1% share of a structure that invests in 20 assets each with a value of 5 must assign an exposure of 0.05 to each of the counterparties. These exposures to these counterparties must be added to any other direct or indirect exposures the Bank has to these counterparties.
15.9 When the look-through approach is required in accordance with this Article, the exposure value to a counterparty is measured for each tranche within the structure, assuming a pro rata distribution of losses amongst investors in a single tranche. To compute the exposure value to the underlying asset, a Bank must:
(1) First, consider the lower of (a) the value of the tranche in which the Bank invests, and, (b) the nominal value of each underlying asset included in the underlying portfolio of assets
(2) Second, apply the pro rata share of the Bank's investment in the tranche to the value determined in the first step above.
15.10 Banks must identify third parties that may constitute an additional risk factor inherent in a structure itself rather than in the underlying assets. Such a third party could be a risk factor for more than one structure that a Bank invests in. Examples of such third parties include the originator, fund manager, liquidity provider, and protection provider. There may be multiple such common risk factors, all of which must be recognised separately.
15.11 Based on the common risk factor identified in accordance with Article 15.10, a Bank must form a distinct Group Of Connected Counterparties that is subject to the large exposure limit.
15.12 Banks must assess whether the exposure to the common risk factor is also an exposure to the entity representing that common risk factor. In the case of a credit protection provider, this will be the case, however it may not be the case for the originator or fund manager where the structures can operate independently. If the latter can be demonstrated by the Bank, the exposure to the common risk factor need not be added to the exposure to the entity representing that common risk factor.
Article (16): Exposures to Central Counterparties
16.1 Banks' exposures to Qualifying Central Counterparties related to clearing activities are exempted from the large exposures limit, however, these exposures are subject to the reporting requirements as defined in Article 5 of this regulation.
16.2 Banks' exposures to non-Qualifying Central Counterparties must be measured as the sum of the clearing exposures described in Article 16.4 and the non-clearing exposures described in Article 16.6, and is subject to the large exposure limit set out in Article 3 of this regulation.
16.3 The requirement related to connected counterparties set out in Article 4 of this regulation does not apply to exposures to central counterparties specifically related to clearing activities. For non-clearing exposures, the provisions related to connected counterparties fully apply.
16.4 Banks must calculate the following types of exposure as set out below:
16.4.1 Trade exposures: the exposure value of trade exposures must be calculated following the relevant provisions of this regulation (as for any other counterparty).
16.4.2 Segregated initial margin: the exposure value is zero.
16.4.3 Non-segregated initial margin: the exposure value is the nominal amount of the initial margin posted.
16.4.4 Pre-funded default fund contributions: the exposure value is the nominal amount of the funded contribution.
16.4.5 Unfunded default fund contributions: the exposure value is zero.
16.4.6 Equity stakes: the exposure value is the nominal amount.
16.5 For exposures where the Bank acts as a clearing member or where the Bank acts as client of a clearing member, the Bank must determine the counterparty to which the exposures must be assigned in accordance with the capital adequacy standards.
16.6 Any other exposure types not directly related to clearing services provided by the central counterparty must be measured according to the rules set out in this regulation, as for any other counterparty, and are subject to the large exposure limit.
Article (17): Risk Management and Governance
17.1 A Bank must have policies and processes that provide a comprehensive, Bank-wide view of significant sources of concentration risk, including also sources of concentration risk not captured by the large exposure limit as described in this regulation, such as exposures to a single industry, economic sector, geographic region, as well as exposures to a particular asset class, product, collateral or currency.
17.2 A Bank's information systems must be able to identify and aggregate risk concentrations in a timely manner, and facilitate the active monitoring and management of all risk concentrations as described in Article 17.1.
17.3 A Bank's risk appetite statement must include thresholds for acceptable concentrations of risk reflecting the Bank's risk appetite. These thresholds must be appropriately integrated into a Bank's processes and procedures, and well understood by any relevant staff.
17.4 All material risk concentrations must be regularly reviewed and reported to the Board. Such reports must highlight any current, near or expected breaches of the risk appetite and of the regulatory requirements.
17.5 Senior management must monitor the large exposure limits described in this regulation for the purposes of risk management and to detect any breaches. In the case of breaches, senior management must comply with Article 3.5 of this regulation immediately. Immediate communication means that this communication cannot be subject to Board approval, review, or any other form of confirmation by the Board.
17.6 A Bank must include in its stress testing programmes the impact of significant risk concentrations.
17.7 A Bank must cover in its Internal Capital Adequacy Assessment Process (ICAAP) and Internal Liquidity Adequacy Assessment Process (ILAAP) all forms of concentration risk.
17.8 New or additional exposures resulting in a large exposure may only be granted following approval by the Board of the Bank, or following approval by a designated Board committee.
17.9 Where an existing exposure becomes a large exposure for any reason other than the Bank granting an additional exposure, the Board must be informed immediately. Such a large exposure must also be approved by the Board or a designated Board committee, but it may be done ex-post within a reasonable timeframe.
17.10 A large exposure must be subject to increased monitoring, proportional to its size and risks, in terms of all associated risks, including also risks other than credit risk such as legal, compliance, market and interest rate risk. This should also be reflected in the frequency, detail, and the granularity of reporting to the Board.
Article (18): Exposures to Related Parties
18.1 In addition to the large exposure limits, additional limits apply to the Related Parties as set out below:
Aggregate Individual 18.1.1 Shareholders who own 5% or more of a Bank’s capital, the Group Of Connected Counterparties they belong to, and their Related Parties 50% 20% 18.1.2 Bank’s non-bank subsidiaries and affiliates 25% 10% 18.1.3 Bank’s Board Members 25% 5% 18.1.4 Bank’s external auditors Prohibited 18.2 In Article 18.1.1 above, the individual limit for shareholders applies to an independent shareholder, the Group Of Connected Counterparties they belong to, and their Related Parties. The aggregate limit applies to multiple such Groups of Connected Counterparties and Related Parties, which are otherwise not identified as a Group Of Connected Counterparties.
18.3 Where a Board Member constitutes a Group Of Connected Counterparties with a shareholder who owns 5% or more of the Bank's capital, the lower limits applicable to Board Members apply to that Group Of Connected Counterparties. However, a natural person nominated by a shareholder need not be considered a Group Of Connected Counterparties with that shareholder based on his nomination alone.
Article (19): Application to Branches of Foreign
19.1 The general large exposure limit applicable to branches of foreign banks is equal to the lower of 250% of the Branch Capital and 25% of the entity level capital. This is instead of the limit set in Article 3.1 of this regulation.
19.2 A branch's head office and its head office's branches are always considered a single counterparty, and, based on the criteria set out in Article 4 of this regulation, will normally constitute a Group Of Connected Counterparties with its group, including all subsidiaries of the ultimate parent, to which the large exposure limits apply.
19.3 A branch of a foreign bank must limit its exposures to its head office, which includes exposures to other branches of the head office, to maximum 30% of the Branch Capital for funded exposures and 300% of the Branch Capital for unfunded exposures.
19.4 For the large exposure limits for which the application to branches is not specified, the same limits apply as for Banks incorporated in the UAE, and the limits are applied to the Branch Capital.
Article (20): Enforcement & Sanctions
20.1 Violation of any provision of this regulation and any accompanying Standards may be subject to supervisory action and administrative and financial sanctions as deemed appropriate by the Central Bank.
20.2 Supervisory action and administrative and financial sanctions by the Central Bank may include withdrawing, replacing or restricting the powers of Senior Management or members of the Board, providing for the interim management of the Bank, imposition of fines or barring individuals from the UAE banking sector.
Article (21): Interpretation of Regulation
The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this regulation.
Article (22): Cancellation of Previous Circulars and Notices
This regulation repeals and replaces the following Central Bank Circulars and Notices:
22.1 Circular No. 32 of 2013 regarding “Monitoring of Large Exposure Limits” and its annexes (including the “Guidelines to Monitoring of Large Exposures”);
22.2 Notice No. 300/2013 dated 17/11/2013 regarding “Regulations Re Monitoring of Large Exposure Limits”; and,
22.3 Notice No. 226/2018 dated 1/10/2018 regarding “Large Exposures - Credit Concentrations Above Limits”.
Article (23): Publication & Effective Date
23.1 This regulation shall be published in the Official Gazette in both Arabic and English and shall come into effect (1) one month from the date of publication.
23.2 A grandfathering scheme will apply to any breaches that are due to the change in regulation, as set out in this Article.
23.3 The ‘grandfathered basis' is equal to the breach recorded as of 31 December 2022 when applying the requirements of this regulation, deducted by the breach recorded as of the same date when applying the requirements of Circular No. 32/2013 regarding “Monitoring of Large Exposure Limits” and its annexes (including the “Guidelines to Monitoring of Large Exposures”). The aforementioned requirements include the change in capital base, large exposure limits, and calculation methods.
The grandfathered basis is tied to a specific exposure and counterparty, which will be referred to as the ‘grandfathered exposure', and cannot be used to apply grandfathering to any other exposures or counterparties. For the avoidance of doubt, where the aggregate of multiple exposures to the same counterparty (or Group Of Connected Counterparties) leads to a breach, the grandfathering applies to that specific group of exposures only.
The grandfathered basis is fixed and does not change over time.
23.4 The grandfathering basis will determine the ‘grandfathered amount', which is the amount by which a grandfathered exposure may be reduced when applying the requirements of this regulation. The grandfathered amount is determined by multiplying the grandfathered basis with the following percentage:
23.4.1 100%, upon this regulation coming into force until 30 December 2023;
23.4.2 75%, from 31 December 2023 until 30 December 2024;
23.4.3 50%, from 31 December 2024 until 30 December 2025;
23.4.4 25%, from 31 December 2025 until 30 December 2026;
23.4.5 0%, from 31 December 2026 and onwards.
On 31 December 2026, the grandfathering scheme will cease having any effect.
23.5 Article 3.5 and 3.6 of this regulation do not apply to the grandfathered amount; but apply fully to the exposures in breach after applying the grandfathering scheme.
23.6 The reporting requirements set out in Article 5 of this regulation fully apply to any grandfathered exposures. Banks that have grandfathered exposures will however be required to attach additional information to their regular reporting to the Central Bank providing an overview of:
23.6.1 The grandfathering basis as per Article 23.3;
23.6.2 The percentage applied for the current period as per Article 23.4;
23.6.3 The grandfathered amount as per Article 23.4;
23.6.4 The current exposure amount without deduction of the grandfathered amount;
23.6.5 The amount by which the above (Article 24.6.4) breaches the applicable limits;
23.6.6 The current exposure amount after deduction of the grandfathered amount;
23.6.7 The amount by which the above (Article 24.6.6) breaches the applicable limits.
The Central Bank may issue further instructions on how the above should be reported, including both in terms of content and in terms of format.
23.7 For interbank exposures, the grandfathering scheme set out above does not apply, and Banks must comply fully by 31 December 2023.
Annex 1
Large Exposures Regulation 1 Annex 1
Summary of regulatory large exposure limitsExposure type Aggregate limit Individual limit General large exposure limit
Applies to any exposure unless specifically stated otherwise.1.1 A single borrower or group of related borrowers n/a 25% Exposures with specific limits
Limits overriding the general large exposure limit.Sovereign and UAE public sector entity exposures 1.2 UAE federal government and their non-comm. PSEs treated as sovereign n/a 1.3 Foreign sovereigns rated at least AA- 1.4 UAE local governments 150% n/a 1.5 Non-commercial entities of UAE local governments 25% 1.6 Commercial entities of UAE federal and local governments 100% 25% 1.7 Self-sustainable commercial entities of UAE federal and local governments n/a 25% Interbank exposures 1.8 Intraday interbank exposures n/a 1.9 UAE incorporated bank's exposure to its foreign branches (Art. 13.3) 30% n/a 1.10 G-SIB's exposure to another G-SIB n/a 15% Transactions with related parties 1.11 Shareholders who own 5% or more of a Bank's capital, the Group of Connected Counterparties they belong to, and their Related Parties 50% 20% 1.12 Bank's non-bank subsidiaries and affiliates 25% 10% 1.13 Bank's board members 25% 5% 1.14 Bank's external auditors Prohibited Application to branches of foreign banks
(lower of branch capital limit and entity Tier 1 capital limit)Entity Tier 1 capital Branch capital 1.15 General large exposure limit 25% 250% 1.16 Funded exposures to own head office, its subsidiaries, affiliates and branches n/a 30% 1.17 Unfunded exposures to own head office and its branches n/a 300% Operational Risk
Operational Risk Regulation
C 163/2018 Effective from 29/8/2018Introduction
The Central Bank seeks to promote the effective and efficient development and functioning of the banking system. To this end, Banks must have appropriate policies, processes, procedures, systems and controls to identify, monitor and mitigate operational risks.
In introducing this Regulation and the accompanying Standards, the Central Bank intends to ensure that Banks’ approaches to operational risk are in line with leading international practices.
This Regulation and the accompanying Standards are issued pursuant to the powers vested in the Central Bank under the Central Bank Law.
Where this Regulation or its accompanying Standards, include a requirement to provide information or to take certain measures, or to address certain items listed at a minimum, the Central Bank may impose requirements, which are additional to the list provided in the relevant article.
Objective
The objective of this Regulation is to establish minimum acceptable standards for Banks’ approach to managing operational risks, with a view to:
i Ensuring the soundness of Banks; and
ii Enhancing financial stability
The accompanying Standards supplement the Regulation to elaborate on the supervisory expectations of the Central Bank with respect to operational risk management.
Application
This Regulation and the accompanying Standards apply to all Banks. Banks established in the UAE with significant Group relationships, including Subsidiaries, Affiliates, or international branches, must ensure that the Regulation and Standards are adhered to on a solo and Group-wide basis.
This Regulation and Standards must be read in conjunction with the Risk Management Regulation and Standards, which establish the requirements for Banks’ overarching approach to risk management.
Article 1: Definitions
- Affiliate: An entity that, directly or indirectly, controls, is controlled by or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity, or of the power to direct or cause the direction of the management of another entity.
- Bank: A financial entity, which is authorized by the Central Bank to accept deposits as a Bank.
- Board: The Bank’s Board of Directors.
- Central Bank: The Central Bank of the United Arab Emirates.
- Central Bank Law: Union Law No (10) of 1980 concerning the Central Bank, the Monetary System and Organization of Banking as amended or replaced from time to time.
- Central Bank regulations: Any resolution, regulation, circular, rule, standard or notice issued by the Central Bank.
- Group: A group of entities that includes an entity (the 'first entity') and:
- a) any Parent of the first entity;
- b) any Subsidiary of the first entity or of any Parent of the first entity; and
- c) any Affiliate.
- a) any Parent of the first entity;
- Islamic Financial Services: Shari’a compliant financial services offered by Islamic Banks and Conventional Banks offering Islamic banking products (Islamic Windows).
- Operational risk: The risk of loss resulting from inadequate or failed internal processes, people and systems or from external events. This definition includes legal risk but excludes strategic and reputational risk.
- Parent: An entity (the 'first entity') which:
- a) holds a majority of the voting rights in another entity (the 'second entity');
- b) is a shareholder of the second entity and has the right to appoint or remove a majority of the Board of directors or managers of the second entity; or
- c) is a shareholder of the second entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the second entity.
Or; - d) if the second entity is a subsidiary of another entity which is itself a subsidiary of the first entity.
- a) holds a majority of the voting rights in another entity (the 'second entity');
- Risk appetite: The aggregate level and types of risk a Bank is willing to assume, decided in advance and within its risk capacity, to achieve its strategic objectives and business plan.
- Risk limits: Specific quantitative measures that must not be exceeded based on, for example, forward looking assumptions that allocate the Bank’s aggregate risk appetite to business lines, legal entities or management units within the Bank or Group in the form of specific risk categories, concentrations or other measures as appropriate.
- Risk profile: Point in time assessment of the Bank’s gross (before the application of any mitigants) or net (after taking into account mitigants) risk exposures aggregated within and across each relevant risk category based on current or forward-looking assumptions.
- Risk governance framework: As part of the overall approach to corporate governance, the framework through which the Board and management establish and make decisions about the Bank’s strategy and risk approach; articulate and monitor adherence to the risk appetite and risk limits relative to the Bank’s strategy; and identify, measure, manage and control risks.
- Senior Management: The executive management of the Bank responsible and accountable to the Board for the sound and prudent day-to-day management of the Bank, generally including, but not limited to, the chief executive officer, chief financial officer, chief risk officer, and heads of the compliance and internal audit functions.
- Subsidiary: An entity (the 'first entity') is a subsidiary of another entity (the 'second entity') if the second entity:
- a) holds a majority of the voting rights in the first entity;
- b) is a shareholder of the first entity and has the right to appoint or remove a majority of the Board of directors or managers of the first entity; or
- c) is a shareholder of the first entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the first entity.
Or; - d) if the first entity is a subsidiary of another entity which is itself a subsidiary of the second entity.
- a) holds a majority of the voting rights in the first entity;
- Affiliate: An entity that, directly or indirectly, controls, is controlled by or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity, or of the power to direct or cause the direction of the management of another entity.
Article 2: Operational Risk Governance Framework
- A Bank must have appropriate operational risk management strategies, policies and processes to identify, assess, evaluate, monitor, report and control or mitigate operational risk on a timely basis.
- The members of the Board bear ultimate responsibility for ensuring that a Bank has an adequate operational risk governance framework, which must be fully integrated into the Bank’s overall risk governance framework.
- A Bank must ensure that its operational risk strategy, policies and processes are consistent with its risk profile, systemic importance, risk appetite and capital strength and take account of market and macroeconomic conditions.
- A Bank must address all major aspects of operational risk prevalent in the business of the Bank on a bank-wide and if applicable Group-wide basis.
- A Bank must have appropriate operational risk management strategies, policies and processes to identify, assess, evaluate, monitor, report and control or mitigate operational risk on a timely basis.
Article 3: Board of Directors
- The Board must approve and thereafter review at least annually, the Bank’s operational risk strategies, policies and processes, including disaster recovery and business continuity plans.
- The Board must establish a formal process to oversee Senior Management and ensure that the strategies, policies and processes are implemented effectively at all decision levels.
- The Board must approve and thereafter review at least annually, the Bank’s operational risk strategies, policies and processes, including disaster recovery and business continuity plans.
Article 4: Senior Management
- Senior Management must ensure that the Board-approved operational risk management strategy and significant policies and processes are implemented effectively and fully integrated into the Bank’s overall risk management process.
- Senior Management must ensure that the Board-approved operational risk management strategy and significant policies and processes are implemented effectively and fully integrated into the Bank’s overall risk management process.
Article 5: Identification and Assessment
- The Board-approved operational risk management strategy must provide for the identification and assessment of the operational risks inherent in all material products, activities, processes and systems.
Article 6: Control and Mitigation
- The Board-approved operational risk management strategy must foster a strong control environment that utilizes policies, processes and systems, appropriate internal controls and appropriate risk mitigation and transfer.
Article 7: Disaster Recovery and Business Continuity Management
- A Bank must have disaster recovery and business continuity plans in place to ensure its ability to operate on an ongoing basis and limit losses in the event of a severe business disruption. Such plans must be commensurate with the risk profile, nature, size and complexity of the Bank’s business and structure and take into account different scenarios to which the Bank may be vulnerable.
- Disaster recovery and business continuity plans must ensure that critical business functions can be maintained or recovered in a timely manner to minimize the financial, legal, regulatory, reputational and other risks that may arise from a disruption.
- The Board must ensure there is a periodic independent review of the Bank’s disaster recovery and business continuity plans to ensure adequacy and consistency with current operations, risks and threats, recovery levels and priorities.
- A Bank must have disaster recovery and business continuity plans in place to ensure its ability to operate on an ongoing basis and limit losses in the event of a severe business disruption. Such plans must be commensurate with the risk profile, nature, size and complexity of the Bank’s business and structure and take into account different scenarios to which the Bank may be vulnerable.
Article 8: Information Technology
- A Bank must establish appropriate information technology policies and processes to identify, assess, monitor and manage technology risks.
- A Bank must have appropriate information technology infrastructure to meet its current and projected business requirements under normal circumstances and in periods of stress. This infrastructure must ensure data and system integrity, security and availability and support integrated and comprehensive risk management.
- A Bank must establish appropriate information technology policies and processes to identify, assess, monitor and manage technology risks.
Article 9: Systems and Internal Reporting
- A Bank must have appropriate and effective information systems to:
- a) Monitor operational risk;
- b) Compile and analyze operational risk data; and
- c) Facilitate appropriate reporting mechanisms at the Bank’s Board, Senior Management and business line levels that support proactive management of operational risk.
- a) Monitor operational risk;
- A Bank must have appropriate and effective information systems to:
Article 10: Reporting Requirements and Disclosure
- A Bank must promptly notify the Central Bank when it becomes aware of a significant deviation from its Board-approved operational risk appetite statement, policies or procedures, or becomes aware that a material operational risk has not been adequately addressed.
- A Bank must provide, upon request, any specific information with respect to operational risk that the Central Bank may require.
- A Bank’s publicly disclosed information must be appropriate to permit stakeholders to assess the Bank’s approach to operational risk management in the context of the Bank’s size, risk profile, complexity of operations and evolving industry practice.
- A Bank must promptly notify the Central Bank of any operational risk event that triggers, or is likely to trigger disaster recovery or business continuity plans, or has, or is likely to have, a material impact on the Bank’s operations, profitability or capital.
- A Bank must promptly notify the Central Bank when it becomes aware of a significant deviation from its Board-approved operational risk appetite statement, policies or procedures, or becomes aware that a material operational risk has not been adequately addressed.
Article 11: New Businesses, Products and Systems
- The approval procedures for new businesses, products or systems or material modification of existing businesses, products or systems required by the Risk Management Regulation and Standards must explicitly address operational risk.
- The approval procedures for new businesses, products or systems or material modification of existing businesses, products or systems required by the Risk Management Regulation and Standards must explicitly address operational risk.
Article 12: Islamic Banking
- A Bank offering Islamic financial services must ensure that its operational risk management framework addresses any operational risks arising from potential non-compliance with Shari’a rules and principles.
- A Bank offering Islamic financial services must ensure that its operational risk management framework addresses any operational risks arising from potential non-compliance with Shari’a rules and principles.
Article 13: Enforcement
- Violation of any provision of this Regulation and the accompanying Standards shall be subject to supervisory action as deemed appropriate by the Central Bank.
- Violation of any provision of this Regulation and the accompanying Standards shall be subject to supervisory action as deemed appropriate by the Central Bank.
Article 14: Interpretation of Regulations
- The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
- The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
Article 15: Cancellation of Previous Notices
- This Regulation and the accompanying Standards replace all previous Central Bank regulations with respect to operational risk.
- This Regulation and the accompanying Standards replace all previous Central Bank regulations with respect to operational risk.
Article 16: Publication and Application
- This Regulation and the accompanying Standards shall be published in the Official Gazette in both Arabic and English and shall come into effect one month from the date of publication.
Operational Risk Standards
C 163/2019 STAIntroduction
- 1.These Standards form part of the Operational Risk Regulation. All Banks must comply with these Standards, which expand on the Regulation. These Standards are mandatory and enforceable in the same manner as the Regulation.
- 2.Operational risk is inherent in all dimensions of a Bank, including all banking products, activities, processes and systems. Accordingly, the effective management of operational risk is a fundamental element of a Bank’s risk management program. Banks with a sound operational risk management framework, a strong risk management culture and ethical business practices, are less likely to experience potentially damaging operational risk events and better placed to deal effectively with those events that do occur.
- 3.A Bank’s Board is in ultimate control of the Bank and accordingly ultimately responsible for operational risk management. There is no one-size-fits-all or single best solution. Accordingly, each Bank could meet the minimum requirements of the Regulation and Standards in a different way and thus may adopt an organizational framework appropriate to the risk profile, nature, size and complexity of its business and structure. The onus is on the Board to demonstrate that it has implemented an appropriate approach to operational risk management. Banks are encouraged to adopt leading practices that exceed the minimum requirements of the Regulation and Standards.1
- 4.The Standards follow the structure of the Regulation, with each article corresponding to the specific article in the Regulation.
1 The Central Bank will apply the principle of proportionality in the enforcement of the Regulation and Standards, whereby smaller banks may demonstrate to the Central Bank that the objectives are met without necessarily addressing all of the specifics cited in the Standards.
Article 1: Definitions
- 1. Affiliate: An entity that, directly or indirectly, is controlled by, or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity, or of the power to direct or cause the direction of the management of another entity.
- 2. Bank: A financial entity, which is authorized by the Central Bank to accept deposits as a Bank.
- 3. Board: The Bank’s Board of Directors.
- 4. Central Bank: The Central Bank of the United Arab Emirates.
- 5. Central Bank Law: Federal Law No (10) of 1980 concerning the Central Bank, the Monetary System and Organization of Banking as amended or replaced from time to time.
- 6. Central Bank regulations: Any resolution, regulation, circular, rule, standard or notice issued by the Central Bank.
- 7. Group: A group of entities that includes an entity (the 'first entity') and:
- a.any Parent of the first entity;
- b.any Subsidiary of the first entity or of any Parent of the first entity; and
- c.any Affiliate.
- 8. Higher Shari’a Authority: The Higher Shari’a Authority for Islamic banking and financial activities that was established by the Cabinet Resolution no. 2016 (1/و5/102) at the Central Bank.
- 9. Inherent risk: The risk existing if no controls or other mitigating factors are in place.
- 10. Islamic Financial Services: Shari’a compliant financial services offered by Islamic Banks and Conventional Banks offering Islamic banking products (Islamic Windows).
- 11. Operational risk: The risk of loss resulting from inadequate or failed internal processes, people and systems or from external events. This definition includes legal risk but excludes strategic and reputational risk.
- 12. Parent: An entity (the 'first entity') which:
- a.holds a majority of the voting rights in another entity (the 'second entity');
- b.is a shareholder of the second entity and has the right to appoint or remove a majority of the Board or managers of the second entity; or
- c.is a shareholder of the second entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the second entity;
Or; - d.If the second entity is a subsidiary of another entity which is itself a subsidiary of the first entity.
- 13. Residual risk: The risk exposure after controls are considered.
- 14. Risk appetite: The aggregate level and types of risk a Bank is willing to assume, decided in advance and within it risk capacity, to achieve its strategic objectives and business plan.
- 15. Risk governance framework: As part of the overall approach to corporate governance, the framework through which the Board and management establish and make decisions about the Bank’s strategy and approach to risk management; articulate and monitor adherence to the risk appetite and risks limits relative to the Bank’s strategy; and identify, measure, manage and control risks.
- 16. Risk limits: Specific quantitative measures that may not be exceeded, based on, for example, forward looking assumptions that allocate the Bank’s aggregate risk appetite to business lines, legal entities or management units within the Bank or Group in the form of specific risk categories, concentrations or other measures, as appropriate.
- 17. Risk Management function: Collectively, the systems, structures, policies, procedures and people that measure, monitor and report risk on a Bank-wide and, if applicable, Group-wide basis.
- 18. Senior Management: The executive management of the Bank responsible and accountable to the Board for the sound and prudent day-to-day management of the Bank, generally including, but not limited to, the chief executive officer, chief financial officer, chief risk officer and heads of the compliance and internal audit functions.
- 19. Subsidiary: An entity (the 'first entity') is a subsidiary of another entity (the 'second entity') if the second entity:
- a.holds a majority of the voting rights in the first entity;
- b.is a shareholder of the first entity and has the right to appoint or remove a majority of the Board or managers of the first entity; or
- c.is a shareholder of the first entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the first entity;
Or; - d.If the first entity is a subsidiary of another entity that is itself a subsidiary of the second entity.
Article 2: Operational Risk Governance Framework
- 1.The fundamental premise of sound risk management is that the Board and the management of a Bank understand the nature and complexity of the risks inherent in the portfolio of the Bank’s products, services and activities. This is particularly important for operational risk.
- 2.A Bank must establish, implement and maintain an operational risk governance framework, which enables it to identify, assess, evaluate, monitor, mitigate and control operational risk. The operational risk governance framework consists of policies, processes, procedures, systems and controls.
- 3.The operational risk governance framework must be documented and approved by the Board of the Bank, must provide for a sound and well-defined framework to address the Bank's operational risk and must include definitions of operational risk and material operational loss.
- 4.A Board is responsible for establishing, maintaining and overseeing a robust operational risk governance framework that must take into account the risk profile, nature, size and complexity of the Bank's business and structure.
- 5.A Board must approve and subsequently review, at least annually, a risk appetite statement for operational risk that articulates the nature, types and levels of operational risk that the Bank is willing to assume and that sets appropriate limits and thresholds.
- 6.The operational risk governance framework must be fully integrated into the Bank’s overall risk governance framework and risk management processes. This applies to all levels and areas of the Bank including to business lines and, if applicable, to Group levels, as well as new business initiatives, products, activities, processes and systems.
- 7.The operational risk governance framework must clearly:
- a.Identify the governance structures used to manage operational risk, including reporting lines, responsibilities and accountabilities;
- b.Establish operational risk reporting and management information systems;
- c.Provide for periodic independent review and assessment of operational risk; and
- d.Require policies to be reviewed and revised as appropriate, whenever a material change in the operational risk profile of the Bank occurs.
- 8.Larger or more complex Banks must have an Operational Risk Committee or other designated committee that addresses operational risk.
- 9.A Bank must measure operational risks for capital purposes using the approach most appropriate to the risk profile, nature, size and complexity of the Bank's business and structure. Holding capital against operational risks, however, is not a substitute for effective operational risk management.
- 10. A Bank must meet the following minimum criteria or demonstrate to the Central Bank that its framework meets the requirements for a comprehensive approach to operational risk management without the presence of all of the criteria enumerated below.
- a.A Bank must have an operational risk management system with clear responsibilities assigned to an operational risk management function. These responsibilities must include, but not be limited to, developing strategies to identify, assess, monitor and control or mitigate operational risk; codifying bank-level policies and procedures concerning operational risk management and controls; the design and implementation of the Bank’s operational risk assessment methodology; and the design and implementation of a risk-reporting system for operational risk.
- b.A Bank must systematically track relevant operational risk data including material losses by business line. Its operational risk assessment system must be closely integrated into the risk management processes and procedures of the Bank. Its output must be an integral part of the process of and procedures for monitoring and controlling the Banks operational risk profile. For instance, this information must play a prominent role in risk reporting, management reporting and risk analysis. The Bank must have techniques for creating incentives to improve the management of operational risk throughout the Bank.
- c.There must be regular reporting of operational risk exposures, including material operational losses, to business unit management, Senior Management and to the Board. The Bank must have procedures for taking appropriate action according to the information within the management reports.
- d.A Bank’s operational risk management system must be well documented. A Bank must have a routine in place for ensuring compliance with a documented set of internal policies, controls and procedures concerning the operational risk management system, which must include policies for the treatment of non-compliance issues.
- e.A Bank’s operational risk management processes and assessment system must be subject to regular internal audit review. These reviews must include both the activities of the business units and of the operational risk management function.
Article 3: Board of Directors
- 1.The Board must establish and maintain a strong operational risk management culture, which has to be guided by strong operational risk management that supports and provides appropriate standards and incentives for professional and responsible behaviour. The Board must ensure that a strong control environment is established and maintained.
- 2.The Board must establish and maintain a code of conduct or an ethics policy that sets clear expectations for integrity and ethical values of the highest standard and identifies acceptable business practices and prohibits conflicts of interest.
Article 4: Senior Management
- 1.Senior Management must consistently implement and maintain throughout the Bank (and, if applicable, Group) policies, processes and systems for managing operational risk in all material products, activities, processes and systems, consistent with the risk appetite statement.
- 2.Senior Management must clearly assign authority, responsibility and reporting relationships to encourage and maintain accountability and to ensure that the necessary resources are available to manage operational risk in line with the Bank’s risk appetite statement. The management oversight process for operational risk must be appropriate to the risks inherent in a business unit’s activities.
- 3.Senior Management must ensure that the control environment provides for appropriate independence and segregation of duties. The approach to operational risk management must incorporate the “three lines of defence” approach:
- a.Business line management responsible for identification and control of risks;
- b.Control functions of risk management and compliance; and
- c.Internal audit to provide independent assurance.
- 4.Senior Management must implement a process to regularly monitor operational risk profiles and material exposures to losses. Appropriate reporting mechanisms must be in place at the Board, senior management and business line levels that support proactive management of operational risk.
- 5.Senior Management must ensure that an appropriate level of operational risk training is available at all levels throughout the Bank. Training that is provided must reflect the seniority, role and responsibilities of the individuals for whom it is intended.
Article 5: Identification and Assessment
- 1.A Bank must identify and assess the operational risk inherent in all material products, activities, processes and systems. Effective identification and assessment considers both internal and external factors. This must include any operational risk arising from common points of exposure, such as a single external service provider serving the Bank.2
- 2.A Bank’s approach to assessment of operational risk at a minimum must address the following items:
- a.Determining which operational risk assessment tools will be employed by the Bank and how they are to be used;
- b.Establishing and monitoring thresholds or limits for inherent and residual risk exposure;
- c.Calibration of identified risks against operational risk appetite limits, as well as thresholds or limits for inherent and residual risk and approved risk mitigation strategies and instruments; and
- d.Providing for common operational risk terminology to ensure consistency of risk identification and assessment on a bank-wide or, if applicable, Group-wide basis.
- 3.A Bank must take into account its assessment of operational risk in its internal pricing and performance monitoring mechanisms.
2 Appendix 1 provides examples of tools that may be used for identifying and assessing operational risk.
Article 6: Control and Mitigation
- 1.A Bank must have a strong control environment, including but not limited to, appropriate segregation of duties and dual control. Areas of potential conflicts of interest must be identified, minimized and be subject to careful independent monitoring3 and review.
- 2.A Bank, in addition to segregation of duties and dual control, must ensure that other traditional internal controls are in place. Such controls include but are not limited to:
- a.Clearly established authorities and/or processes for approval;
- b.Close monitoring of adherence to assigned risk thresholds or limits;
- c.Safeguards for access to and use of, Bank assets and records;
- d.Appropriate staffing level and training to maintain expertise;
- e.Ongoing processes to identify business lines or products where returns appear to be out of line with reasonable expectations;
- f.Regular verification and reconciliation of transactions and accounts; and
- g.A vacation policy that requires officers and employees to take a minimum leave of absence as determined by the Bank.
- 3.Risk transfer and mitigation tools such as insurance are imperfect substitutes for sound controls and risk management so Banks must utilize risk transfer tools as complementary to, rather than a replacement for, internal operational risk control.
3 Independent monitoring may be done by the internal audit function or an external consultant, subject to the party having the appropriate skills to do so. The Central Bank will expect the Bank to explain and evidence its decision of how it chose an independent party and how their skills were assessed.
Article 7: Disaster Recovery and Business Continuity Management
- 1.Disaster recovery and business continuity planning must consider the whole of the Bank or Group, if applicable, to identify, assess and mitigate potential business continuity risks and ensure that the Bank is able to meet its financial and service obligations in the event of business disruptions.
- 2.A Bank’s business continuity management (BCM) policy must be documented, set out its objectives and approach to BCM and be up-to-date. The BCM policy must clearly state the roles, responsibilities and authorities to act in relation to the BCM policy.
- 3.A Bank must conduct business impact analysis (BIA) and risk assessment on an ongoing basis. A BIA involves identifying all critical business functions and assessing the impact of a disruption on these.
- 4.Critical business functions are the business operations, resources and infrastructure that may, if disrupted, have a material impact on the Bank’s business functions, reputation, profitability or customers.
- 5.When conducting the BIA, a Bank must consider at a minimum:
- a.Disruption scenarios over varying periods of time;
- b.The period of time for which the Bank could not operate without each of its critical business operations;
- c.The extent to which a disruption to the critical business operations might have a material impact on customers of the Bank; and
- d.The financial, legal, regulatory and reputational impact of a disruption to a Bank’s critical business operations over varying periods.
- 6.A Bank must identify and document appropriate recovery objectives and implementation strategies based on the results of the BIA, taking into account the risk profile, nature, size and complexity of the Bank's business and structure. Recovery objectives are pre-defined goals for restoring critical business operations to a specified level of service (recovery level) within a defined period (recovery time) following a disruption.
- 7.A Bank must maintain at all times a documented business continuity plan (BCP) that meets the objectives of the BCM policy. The BCP must reflect the specific requirements of the Bank and must identify:
- a.Critical business operations;
- b.Recovery levels and time targets for each critical business operation;
- c.Recovery strategies for each critical business operation;
- d.Infrastructure and resources required to implement the BCP;
- e.Roles, responsibilities and authorities to act in relation to the BCP; and
- f.Communication plans with staff and external stakeholders.
- 8.A Bank must review and test its BCP at least annually or more frequently if there are material changes to business operations, to ensure that staff can effectively execute contingency plans and that recovery and resumption objectives and timeframes can be met. The results of the testing must be reported formally to the Board or to designated Senior Management in line with the BCM policy. The BCP must be updated if shortcomings are identified as a result of the review and testing.
Article 8: Information Technology
- 1.A Bank’s effective use and sound implementation of technology can contribute to the control environment. However, use of technology-related products, activities, processes and delivery channels exposes a Bank to strategic, operational and reputational risks and the possibility of material financial loss. Automated processes introduce risks that must be addressed through technology governance and infrastructure risk management programmes, including an information security management system.
- 2.A Bank must have an integrated approach to identifying, measuring, monitoring and managing technology risk. Technology risk management includes but is not limited to:
- a.Governance and oversight controls that ensure technology, including outsourcing arrangements, are aligned with and supportive of the Bank’s business objectives;
- b.Establishment and maintenance of appropriate information technology policies, procedures and processes to identify, assess, monitor and manage technology risks;
- c.Establishment of a risk appetite statement and limits as well as performance expectations to assist in controlling and managing risk;
- d.Implementation of an effective control environment;
- e.Monitoring processes that test for compliance with policy thresholds or limits; and
- f.Establishment and maintenance of appropriate and sound information technology infrastructure to meet the current and projected business requirements of the Bank under normal circumstances and in periods of stress and which ensures data and system integrity, security and availability.
Article 9: Systems and Internal Reporting
- 1.A Bank must have information systems that enable accurate and timely monitoring of and reporting on operational risk. The level of sophistication of a Bank’s operational risk information system must be calibrated to the risk profile, complexity and systemic importance of the Bank.
- 2.The processes for aggregating the necessary data and producing operational risk management reports must be fully documented. These must include standards, cut-off times and schedules for report production. The aggregation and reporting process must be subject to high standards of validation through periodic review by the internal audit function using staff with specific systems, data and reporting expertise, particularly where the process requires substantial manual intervention.
- 3.Operational risk reports to Senior Management and the Board must provide aggregate information as well as sufficient supporting detail to enable Senior Management and the Board to understand and assess the Bank’s operational risk exposures.
Article 10: Reporting Requirements and Disclosure
- 1.A Bank must notify the Central Bank promptly and no later than 24 hours after experiencing an operational risk event that triggers, or is likely to trigger, disaster recovery or business continuity plans, or has, or is likely to have, a significant impact on the Bank’s operations, profitability or capital. The Bank must explain to the Central Bank the nature of the event, actions being taken, the likely effect and the timeframe for returning to normal operations, where applicable. The Bank must notify the Central Bank when normal operations resume.
- 2.A Board-approved disclosure policy must provide for the Bank’s publication of sufficient information on operational risk and controls to allow stakeholders to assess its approach to operational risk management and to determine whether the Bank identifies, assesses, evaluates, monitors and controls and mitigates operational risk effectively. In addition, a Bank must implement a process for assessing the appropriateness of its operational risk disclosures.
- 3.Branches and Subsidiaries of foreign Banks operating in the UAE may largely rely on the Group’s disclosures, supplemented by disclosure, at least annually through their websites that are dedicated to their activities in the UAE, of a summary of the local branch or Subsidiary’s operational risk management framework.
- 4.A Bank’s public disclosures must be commensurate with the size, risk profile and complexity of a Bank’s operations and evolving industry practice. A Bank’s disclosures must be consistent with how Senior Management and the Board assess and manage the operational risk of the Bank.
Article 11: New Businesses, Products and Systems
- 1.In general, a Bank’s operational risk exposure is increased when a Bank engages in new activities, develops new products, enters unfamiliar markets, implements new business processes or technology systems and/or engages in businesses that are geographically distant from its head office. A Bank must ensure that its risk management control infrastructure is appropriate and that it keeps pace with the development of or changes to its products, activities, processes and systems.
- 2.A Bank must have policies and procedures that address the process for review and approval of new products, activities, processes and systems. The review and approval process must consider at a minimum:
- a.Inherent risks, including but not limited to legal risks, in the new product, service or activity;
- b.Changes to the Bank’s risk profile and operational risk appetite, including the risk of existing products or activities;
- c.The necessary controls, risk management processes and risk mitigation strategies;
- d.Residual risk;
- e.Changes to relevant risk thresholds or limits;
- f.Procedures and metrics to measure, monitor and manage the risk of the new product or activity; and
- g.Whether appropriate investment has been made for human resources and technology infrastructure before new products are introduced.
- 3.A Bank must ensure that the implementation of new products, activities, processes and systems is monitored in order to identify any material differences to the expected operational risk profile and to manage any unexpected risks.
Article 12: Islamic Banking
- 1.A Bank offering Islamic financial services must have in place adequate systems and controls, including a Shari’a Control Committee, to ensure compliance with Shari’a provisions. This includes policies and procedures for the approval of Islamic products, contracts and activities.
- 2.A Bank offering Islamic financial services must keep track of income not recognized arising from Shari’a non-compliance and assess the probability of similar cases arising in the future. Based on historical reviews and potential areas of Shari’a non-compliance, the Bank must assess potential profits that cannot be recognized as eligible Islamic Banking profits.
- 3.A Bank offering Islamic financial services must undertake a Shari’a compliance review at least annually, performed either by a separate Shari’a Audit function or as part of the existing internal and external audit function by persons having the required knowledge and expertise. The objective must be to ensure that the nature of the Bank’s financing and equity investment and its operations are executed in adherence to the applicable Shari’a rules and principles as per the fatwa, policies and procedures approved by the Shari’a Control Committee in accordance with the requirements set by the Central Bank and the Higher Shari’a Authority.
- 4.A Bank offering Islamic financial services must establish and implement a clear and formal policy for undertaking its different and potentially conflicting roles in respect of managing different types of investment accounts. The policy relating to safeguarding the interests of its investment account holders may include but is not limited to:
- a.Identification of investing activities that contribute to investment returns and taking reasonable steps to carry on those activities in accordance with the Bank’s fiduciary and agency duties and to treat all its fund providers appropriately and in accordance with the terms and conditions of its investment agreements;
- b.Allocation of assets and profits between the Bank and its investment account holders must be managed and applied appropriately to investment account holders having funds invested over different investment periods;
- c.Determination of appropriate reserves at levels that do not discriminate against the right for better returns of existing investment account holders; and
- d.Limiting the risk transmission between current and investment accounts.
- 5.A Bank offering Islamic financial services must adequately disclose information on a timely basis to its investment account holders and the markets in order to provide a reliable basis for assessing its risk profile and investment performance.
- 6.A Bank offering Islamic financial services must maintain separate accounts in respect of the Bank’s operations undertaken for restricted investment account holders and ensure proper maintenance of records for all transactions in investments.
Appendix 1: Tools for Identifying and Assessing Operational Risk
Examples of tools4 that may be used for identifying and assessing operational risk include:
- Internal loss data collection and analysis: Internal operational loss data provides meaningful information for assessing a Bank’s exposure to operational risk and the effectiveness of internal controls. Analysis of loss events can provide insight into the causes of large losses and information on whether control failures are isolated or systematic. Banks may also find it useful to capture and monitor operational risk contributions to credit and market risk related losses in order to obtain a more complete view of their operational risk exposure.
- External data collection and analysis: External data elements consist of gross operational loss amounts, dates, recoveries and relevant causal information for operational loss events occurring at organizations other than the Bank. External loss data can be compared with internal loss data, or used to explore possible weaknesses in the control environment or consider previously unidentified risk exposures.
- Risk assessments: In a risk assessment, often referred to as a risk self-assessment, a Bank assesses the processes underlying its operations against a library of potential threats and vulnerabilities and considers their potential impact. A similar approach, risk control self-assessments (RCSA), typically evaluates inherent risk (the risk before controls are considered), the effectiveness of the control environment and residual risk (the risk exposure after controls) are considered. Scorecards built on RCSAs by weighting residual risks provide a means of translating the RCSA output into metrics that give a relative ranking of the control environment.
- Business process mapping: Business process mappings identify the key steps in business processes, activities and organizational functions. They also identify the key risk points in the overall business process. Process maps can reveal individual risks, risk interdependencies and areas of control or risk management weakness. They also can help prioritize subsequent management action.
- Risk and performance indicators: Risk and performance indicators are risk metrics and/or statistics that provide insight into a Bank’s risk exposure. Risk indicators, often referred to as Key Risk Indictors (KRIs), provide insight into the status of operational processes, which in turn may provide insight into operational weaknesses, failures and potential loss. Risk and performance indicators are often paired with escalation triggers to warn when risk levels approach or exceed thresholds or limits and prompt mitigation plans.
- Scenario analysis: Scenario analysis is a process of obtaining expert opinion of business line and risk managers to identify potential operational risk events and assess their potential outcome. Scenario analysis is an effective tool to consider potential sources of significant operational risk and the need for additional risk management controls or mitigation solutions. Given the subjectivity of the scenario process, a robust governance framework is essential to ensure the integrity and consistency of the process.
- Models: Larger Banks may find it useful to quantify their exposure to operational risk by using the output of the risk assessment tools as inputs into a model that estimates operational risk exposure. The results of the model can be used in an economic capital process and can be allocated to business lines to link risk and return.
- Comparative analysis: Comparative analysis consists of comparing the results of the various assessment tools to provide a more comprehensive view of the Bank’s operational risk profile. For example, comparison of the frequency and severity of internal data with RCSAs can help the Bank determine whether self-assessment processes are functioning effectively. Scenario data can be compared to internal and external data to gain a better understanding of the severity of the Bank’s exposure to potential risk events.
- Audit findings: While audit findings primarily focus on control weaknesses and vulnerabilities, they can also provide insight into inherent risk due to internal or external factors. Banks must not solely rely on internal audit to identify operational risks.
4 Banks are encouraged to use a range of tools to gain an understanding of their operational risks, in a manner consistent and proportional with the size and complexity of the bank and the operational risks it faces.
IRRBB
Interest Rate and Rate Of Return Risk in the Banking Book Regulation
C 165/2018 Effective from 29/8/2018Introduction
The Central Bank seeks to promote the effective and efficient development and functioning of the banking system. To this end, Banks exposed to interest rate and rate of return risk in the banking book (IRRBB) must have appropriate policies, processes, procedures, systems and controls to identify, measure, monitor, report on, control and mitigate such risks.
In introducing this Regulation and the accompanying Standards, the Central Bank intends to ensure that Banks’ approaches to the management of (IRRBB) are in line with leading international practices.
This Regulation and the accompanying Standards are issued pursuant to the powers vested in the Central Bank under the Central Bank Law.
Where this Regulation or its accompanying Standards, include a requirement to provide information or to take certain measures, or to address certain items listed at a minimum, the Central Bank may impose requirements, which are additional to the list provided in the relevant article.
Objective
The objective of these Regulations is to establish minimum requirements for (IRRBB) management for Banks, with a view to:
i. Ensuring the soundness of Banks; and
ii. Enhancing financial stability.
The accompanying Standards supplement the Regulation to elaborate on the supervisory expectations of the Central Bank with respect to the management of (IRRBB).
Scope of Application
This Regulation and the accompanying Standards apply to all Banks. Banks established in the UAE with significant Group relationships, including Subsidiaries, Affiliates, or international branches, must ensure that the Regulation and Standards are adhered to on a solo and Group-wide basis.
This Regulation and Standards must be read in conjunction with the Risk Management Regulation and Standards, which establish the requirements for a Bank’s overarching approach to risk management.
Article 1: Definitions
- Affiliate: An entity that, directly or indirectly, controls is controlled by or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity or of the power to direct or cause the direction of the management of another entity.
- Bank: A financial entity, which is authorized by the Central Bank to accept deposits as a Bank.
- Board: The Bank’s Board of Directors.
- Banking Book: Positions in financial instruments that are expected to be held to maturity.
- Central Bank: The Central Bank of the United Arab Emirates.
- Central Bank Law: Union Law No (10) of 1980 concerning the Central Bank, the Monetary System and Organization of
- Central Bank regulations: any resolution, regulation, circular, rule, standard or notice issued by the Central Bank.
- Group: a group of entities which includes an entity (the ‘first entity’) and:
- a) any Parent of the first entity;
- b) any Subsidiary of the first entity or of any Parent of the first entity; and
- c) any Affiliate.
- a) any Parent of the first entity;
- Islamic Financial Services: Shari’a compliant financial services offered by Islamic Banks and Conventional Banks offering Islamic banking products (Islamic Windows).
- Parent: an entity (the ‘first entity’) which:
- a) holds a majority of the voting rights in another entity (the ‘second entity’);
- b) is a shareholder of the second entity and has the right to appoint or remove a majority of the board or managers of the second entity; or
- c) is a shareholder of the second entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the second entity.
Or;
d) if the second entity is a subsidiary of another entity which is itself a subsidiary of the first entity.
- a) holds a majority of the voting rights in another entity (the ‘second entity’);
- Risk appetite: The aggregate level and types of risk a Bank is willing to assume, decided in advance and within its risk capacity, to achieve its strategic objectives and business plan.
- Risk governance framework: As part of the overall approach to corporate governance, the framework through which the Board and management establish and make decisions about the Bank’s strategy and risk approach; articulate and monitor adherence to the risk appetite and risk limits relative to the Bank’s strategy; and identify, measure, manage and control risks.
- Risk limits: Specific quantitative measures that must not be exceeded based on, for example, forward looking assumptions that allocate the Bank’s aggregate risk appetite to business lines, legal entities or management units within the Bank or Group in the form of specific risk categories, concentrations or other measures as appropriate.
- Risk profile: Point in time assessment of the Bank’s gross (before the application of any mitigants) or net (after taking into account mitigants) risk exposures aggregated within and across each relevant risk category based on current or forward-looking assumptions.
- Senior Management: The executive management of the Bank responsible and accountable to the Board for the sound and prudent day-to-day management of the Bank, generally including but not limited to the chief executive officer, chief financial officer, chief risk officer and heads of the compliance and internal audit functions.
- Subsidiary: an entity (the ‘first entity’) is a subsidiary of another entity (the ‘second entity’) if the second entity:
- a) holds a majority of the voting rights in the first entity;
- b) is a shareholder of the first entity and has the right to appoint or remove a majority of the board or managers of the first entity; or
- c) is a shareholder of the first entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the first entity.
Or;
d) if the first entity is a subsidiary of another entity which is itself a subsidiary of the second entity.
- a) holds a majority of the voting rights in the first entity;
- Trading Book: Positions in financial instruments and commodities held either with trading intent or in order to hedge other elements of the trading book.
- Affiliate: An entity that, directly or indirectly, controls is controlled by or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity or of the power to direct or cause the direction of the management of another entity.
Article 2: Risk Governance Framework
- A Bank must have an appropriate IRRBB strategy and risk governance framework that provides a bank-wide and if applicable Group-wide view of IRRBB. This includes policies and processes to identify, measure, evaluate, monitor, report and control or mitigate material sources of IRRBB on a timely basis.
- A Bank’s IRRBB strategy, policies and processes must be consistent with the risk appetite statement, risk profile and systemic importance of the Bank, taking into account market and macroeconomic conditions.
- A Bank’s IRRBB strategy, policies, and processes must be reviewed at least annually and appropriately adjusted, where necessary, in line with the Bank’s changing risk profile and market developments.
- A Bank’s strategy, policies and processes for IRRBB must be approved and reviewed at least annually by the Board.
- The Senior Management must ensure that the strategy, policies and processes are developed and implemented effectively.
- A Bank’s policies and processes must establish an appropriate and properly controlled IRRBB environment, including, at a minimum, the following items:
- Comprehensive and appropriate interest rate risk measurement systems;
- Regular review and independent (internal or external) validation of any models used by the functions tasked with managing IRRBB, including review of key model assumptions;
- Appropriate limits that are approved by the Board and Senior Management and that reflect the Bank’s risk appetite, risk profile and capital strength, and are understood by and regularly communicated to, relevant staff;
- Effective processes for exception tracking and reporting which ensure prompt action at the appropriate level of the Senior Management or Board, where necessary; and
- Effective information systems for accurate identification, aggregation, monitoring and timely reporting of IRRBB exposure to the Board and Senior Management.
- Comprehensive and appropriate interest rate risk measurement systems;
- A Bank must have an appropriate IRRBB strategy and risk governance framework that provides a bank-wide and if applicable Group-wide view of IRRBB. This includes policies and processes to identify, measure, evaluate, monitor, report and control or mitigate material sources of IRRBB on a timely basis.
Article 3: Risk Management Function
- A Bank’s risk management function must include policies, procedures and systems for monitoring and reporting to ensure that IRRBB exposures are aligned with the Bank’s strategy and business plan and consistent with the Board approved risk appetite statement and individual risk limits, as well as the systemic importance of the Bank, taking into account market and macroeconomic conditions.
- A Bank’s risk management function must include policies, procedures and systems for monitoring and reporting to ensure that IRRBB exposures are aligned with the Bank’s strategy and business plan and consistent with the Board approved risk appetite statement and individual risk limits, as well as the systemic importance of the Bank, taking into account market and macroeconomic conditions.
Article 4: Risk Measurement and Use Of Models
- A Bank must have comprehensive and appropriate interest rate risk measurement systems, which generate a quantification of the threat to earnings and economic value from IRRBB.
- A Bank must ensure that there is a regular review and independent (internal or external) validation of any models used by the functions tasked with managing interest rate risk (including review of key model assumptions).
- A Bank must have comprehensive and appropriate interest rate risk measurement systems, which generate a quantification of the threat to earnings and economic value from IRRBB.
Article 5: Stress Testing
- A Bank must include appropriate scenarios in its stress testing programs to measure its vulnerability to loss under adverse interest rate movements, including but not limited to the impact on the banking book of a standardized interest rate shock as prescribed by the Central Bank.
- A Bank must ensure that its internal capital measurement systems adequately capture IRRBB.
- A Bank must include appropriate scenarios in its stress testing programs to measure its vulnerability to loss under adverse interest rate movements, including but not limited to the impact on the banking book of a standardized interest rate shock as prescribed by the Central Bank.
Article 6: Information Systems and Internal Reporting
- A Bank must have information systems that enable it to identify, accurately aggregate, monitor and report IRRBB to the Board and Senior Management on a timely basis, in formats suitable for their use.
- A Bank must have information systems that enable it to identify, accurately aggregate, monitor and report IRRBB to the Board and Senior Management on a timely basis, in formats suitable for their use.
Article 7: Reporting Requirements
- Banks must report to the Central Bank on their IRRBB exposure in the format and frequency prescribed in the Standards.
- A Bank must provide upon request any specific information with respect to IRRBB that the Central Bank may require.
- A Bank must promptly notify the Central Bank when it becomes aware of a significant deviation from the Board-approved IRRBB risk limits, policies or procedures or becomes aware that a material interest rate risk has not been adequately addressed.
- Banks must report to the Central Bank on their IRRBB exposure in the format and frequency prescribed in the Standards.
Article 8: Islamic Banking
- A Bank offering Islamic financial services must apply the provisions of this Regulation, subject to such adjustments as are necessary, in relation to its RoRR (rate of return risk).
- A Bank offering Islamic financial services must establish a comprehensive risk management and reporting process to assess the potential impacts of market factors affecting rates of return on assets in comparison to rates paid on its liabilities.
- A Bank offering Islamic financial services must have in place an appropriate framework for managing displaced commercial risk, where applicable.
- A Bank offering Islamic financial services must apply the provisions of this Regulation, subject to such adjustments as are necessary, in relation to its RoRR (rate of return risk).
Article 9: Enforcement
- Violation of any provision of this Regulation and the accompanying Standards shall be subject to supervisory action as deemed appropriate by the Central Bank.
Article 10: Interpretation of Regulations
- The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
Article 11: Cancellation of Previous Notices
- These Regulation and the accompanying Standards replace all previous Central Bank Regulations and Notices with respect to IRRBB.
Article 12: Publication and Application
- This Regulation and the accompanying Standards shall be published in the Official Gazette in both Arabic and English and shall come into effect one month from the date of publication.
Interest Rate and Rate of Return Risk in the Banking Book Standards
C 165/2019 STAIntroduction
- 1.These Standards form part of the Interest Rate and Rate of Return Risk in the Banking Book (IRRBB) Regulation. All Banks must comply with these Standards, which expand on the Regulation. These Standards are mandatory and enforceable in the same manner as the Regulation.
- 2.Banks offering Islamic financial services must apply the same principles to address rate of return risk.
- 3.IRRBB is a normal part of banking and can be an important source of profitability and shareholder value to a bank. However, excessive IRRBB can pose a significant threat to a Bank’s earnings and capital base. Changes in interest rates affect a Bank’s earnings by changing its net interest income and the level of other interest-sensitive income and operating expenses. Changes in interest rates also affect the underlying value of a Bank’s assets, liabilities and off-balance sheet items, as the present value of future cash flows change. Accordingly, an effective risk management process that maintains IRRBB within prudent levels is essential to the safety and soundness of a Bank.
- 4.A Bank’s Board is in ultimate control of the bank and accordingly ultimately responsible for the bank’s approach to IRRBB. There is no one-size-fits-all or single best solution. Accordingly, each bank could meet the minimum requirements of the Regulation and Standards in different ways and thus may adopt an organizational framework appropriate to the risk profile, nature, size and complexity of its business and structure. The onus is on the Bank’s Board to demonstrate that it has implemented an approach that adequately addresses IRRBB. Banks are encouraged to adopt leading practices that exceed the minimum requirements of the Regulation and Standards.1
- 5.The Standards follow the structure of the Regulation, with each article corresponding to the specific article in the Regulation.
1 The Central Bank will apply the principle of proportionality in the enforcement of the Regulation and Standards, whereby smaller banks may demonstrate to the Central Bank that the objectives are met without necessarily addressing all of the specifics cited in the Standards.
Article 1: Definitions
- 1.Affiliate: An entity that, directly or indirectly, controls, is controlled by, or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity, or of the power to direct or cause the direction of the management of another entity.
- 2.Bank: A financial entity, which is authorized by the Central Bank to accept deposits as a bank.
- 3.Basis risk: The risk of loss arising from imperfect correlation in changes of the rates earned and paid on different instruments with otherwise similar re-pricing characteristics.
- 4.Board: The Bank’s Board of Directors.
- 5.Central Bank: The Central Bank of the United Arab Emirates.
- 6.Central Bank Law: Union Law No (10) of 1980 concerning the Central Bank, the Monetary System and Organization of Banking as amended or replaced from time to time.
- 7.Central Bank regulation: Any resolution, regulation, circular, rule, standard or notice issued by the Central Bank.
- 8.Displaced commercial risk: Market pressure to pay a return that exceeds the rate earned on assets financed by the investment account holders of a Bank offering Islamic financial services in order to attract or retain funds provided by investment account holders.
- 9.Group: a group of entities that includes an entity (the ‘first entity’) and:
- a.any Parent of the first entity;
- b.any Subsidiary of the first entity or of any Parent of the first entity; and
- c.any Affiliate.
- 10.Interest rate risk (IRR): The risk of loss arising from changes in interest rates. Interest rate risk has a number of manifestations, including basis risk, optionality, re-pricing risk and yield curve risk and can present itself in a Bank’s banking book and in its trading book.
- 11.Interest rate risk in the banking book (IRRBB): The risk of loss in the banking book caused by changes in interest rates.
- 12.Islamic Financial Services: Shari’a compliant financial services offered by Islamic Banks and Conventional Banks offering Islamic banking products (Islamic Windows).
- 13.Option risk: The risk of loss arising from the exercise by a counterparty of an option to re-price, redeem or change maturity of bank assets, liabilities or off balance sheet items.
- 14.Parent: an entity (the ‘first entity’) which:
- a.holds a majority of the voting rights in another entity (the ‘second entity’);
- b.is a shareholder of the second entity and has the right to appoint or remove a majority of the Board or managers of the second entity; or
- c.is a shareholder of the second entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the second entity;
Or; - d.If the second entity is a subsidiary of another entity which is itself a subsidiary of the first entity.
- 15.Rate of return risk: The risk that unexpected changes in market rates of return adversely affect the earnings of a Bank offering Islamic financial services.
- 16.Re-pricing risk: The risk of loss arising from timing differences in the maturity (for fixed-rate) and re-pricing (for floating-rate) of Bank assets, liabilities and off-balance sheet positions.
- 17.Risk governance framework: As part of the overall approach to corporate governance, the framework through which the Board and management establish and make decisions about the Bank’s strategy and approach to risk management; articulate and monitor adherence to the risk appetite and risks limits relative to the Bank’s strategy; and identify, measure, manage and control risks.
- 18.Risk limits: Specific quantitative measures, which may not be exceeded, based on, for example, forward looking assumptions that allocate the Bank’s aggregate risk appetite to business lines, legal entities or management units within the Bank or Group in the form of specific risk categories, concentrations or other measures as appropriate.
- 19.Risk Management function: Collectively, the systems, structures, policies, procedures and people that measure, monitor and report risk on a Bank and if applicable Group-wide basis.
- 20.Senior Management: The executive management of the Bank responsible and accountable to the Board for the sound and prudent day-to-day management of the Bank, generally including but not limited to the chief executive officer, chief financial officer, chief risk officer and heads of the compliance and internal audit functions.
- 21.Subsidiary: an entity (the ‘first entity’) is a subsidiary of another entity (the ‘second entity’) if the second entity:
- a.holds a majority of the voting rights in the first entity;
- b.is a shareholder of the first entity and has the right to appoint or remove a majority of the Board or managers of the first entity; or
- c.is a shareholder of the first entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the first entity;
Or; - d.If the first entity is a subsidiary of another entity that is itself a subsidiary of the second entity.
- 22.Yield curve risk: The risk of loss arising from unanticipated shifts of the yield curve adversely effecting a Bank’s earnings or economic value.
Article 2: Risk Governance Framework
- 1.A Bank must establish, implement and maintain an interest rate and rate of return risk governance framework, which enables it to identify, assess, monitor, mitigate and control interest rate risk. The interest rate and rate of return risk governance framework consists of policies, processes, procedures, systems and controls.
- 2.The interest rate and rate of return risk governance framework must be documented and approved by the Board of the Bank and must provide for a sound and well-defined framework to address the Bank’s interest rate and rate of return risk.
- 3.A Bank’s Board is responsible for establishing, maintaining and overseeing a robust interest rate and rate of return risk governance framework which must take into account the risk profile, nature, size and complexity of the Bank’s business and structure.
- 4.A Bank’s interest rate and rate of return risk governance framework must address the following with respect to IRRBB:
- a.Effective oversight by the Board;
- b.Adequate risk management policies and procedures;
- c.Larger and more complex Banks must address IRRBB as part of the asset and liability management process, which must include an Assets and Liability Management Committee (ALCO) or other designated committee;
- d.Capturing all material sources and accurately measuring IRRBB;
- e.Effective processes for analyzing and assessing IRRBB;
- f.Regular monitoring of the IRRBB profile;
- g.Monitoring and enforcement of IRRBB limits;
- h.Stress-testing of IRRBB and use of results in decision-making;
- i.Oversight by the risk management function;
- j.Independent assurance by the internal audit function; and
- k.Regular reporting to Senior Management and the Board.
- 5.The Board-approved risk appetite statement must specify authorized activities, investments and instruments and specify any activities, investments and instruments, which are not consistent with the Bank’s risk appetite.
- 6.A Bank must clearly define the individuals, functions and/or committees responsible for managing interest rate risk and must ensure that there is adequate separation of duties in the risk management process to avoid conflicts of interest.
- 7.A Bank must have risk measurement, monitoring and control functions with clearly defined duties that are sufficiently independent from position-taking functions and the finance function and which report interest rate risk exposures directly to Senior Management and the Board.
Article 3: Risk Management Function
- 1.Larger or more complex banks must have an ALCO or other designated committee, which addresses IRRBB. The control functions carried out by the ALCO or other designated committee, such as administering the risk limits are part of the overall risk management and internal control system.
- 2.The personnel charged with measuring, monitoring and controlling interest rate risk must have a well-founded understanding of all types of interest rate risk faced throughout the Bank.
- 3.The goal of a Bank’s interest rate risk management must be to maintain a Bank’s interest rate risk exposure within self-imposed parameters over a range of possible changes in interest rates. The limits must be appropriate to the size, complexity and capital adequacy of the Bank, as well as its ability to measure and manage its risk.
Article 4: Interest Rate Risk Measurement and Use of Models
- 1.A Bank must have an interest rate risk measurement systems that assesses the effects of rate changes on both earnings and economic value. These systems must provide meaningful measures of a Bank’s current levels of interest rate risk exposure and must be capable of identifying any excessive exposures that might arise.
- 2.As a general rule, a Bank’s measurement systems must incorporate interest rate risk exposures arising from the full scope of a Bank’s activities, including both trading and non-trading sources, to enable management to have an integrated view of interest rate risk across products and business lines. This does not preclude different measurement systems and risk management approaches being used for different activities.
- 3.A Bank’s interest rate risk measurement system must address all material sources of interest rate risk, including re-pricing, yield curve, basis and options risk exposures. While all of a Bank’s holdings must receive appropriate treatment, concentrations and instruments which might significantly affect a Bank’s aggregate position, must receive rigorous treatment. Instruments with significant embedded or explicit option characteristics must receive special attention.
- 4.At a minimum on a monthly basis, a Bank must prepare a maturity/re-pricing schedule with indicators of the interest rate risk sensitivity of both earnings and economic value, based on both a contractual and behavioral basis. Systemically important Banks must employ more sophisticated interest rate risk measurement systems, including simulation techniques.
- 5.In designing interest rate risk measurement systems, a Bank must ensure that the degree of detail about the nature of their interest-sensitive positions is commensurate with the complexity and risk inherent in these positions.
- 6.A Bank must also consider its dependency on various funding sources since a sudden withdrawal of these funds can have an adverse effect on earnings and economic value through basis risk, re-pricing risk and yield curve risk.
Article 5: Stress Testing
- 1.A Bank must, at a minimum, include in its stress test scenarios the impact of a 200 basis point upward and downward parallel change in interest rates in addition to other scenarios which the Bank determines are appropriate considering the risk profile, nature, size and complexity of its business and structure. A Bank, which is exposed to an economic value decline exceeding 20 percent of total capital from this standardized 200 basis point interest rate shock (or some other level determined by the Central Bank) will be required by the Central Bank to reduce its risk and/or hold additional capital.
- 2.Other stress scenarios which a Bank may use include, but are not limited to, more severe changes in the general level of interest rates, changes in the relationships among key market rates (basis risk), changes in the slope and shape of the yield curve (yield curve risk), changes in the liquidity of key financial markets or changes in the volatility of market rates. In addition, stress scenarios must include conditions under which key business assumptions and parameters break down. A Bank’s Internal Capital Assessment Process must address IRRBB exposures as part of Pillar 2.
Article 6: Information Systems and Internal Reporting
- 1.A Bank’s systems must support supervisory reporting requirements for IRRBB as provided in these Standards as well as provision of IRRBB reports to all relevant parties within the Bank on a timely basis and in a format commensurate with their needs.
- 2.The processes for aggregating the necessary data and producing supervisory and internal IRRBB management reports must be fully documented. These must include standards, cut-off times and schedules for report production. The aggregation and reporting process must be subject to high standards of validation through periodic review by the internal audit function using staff with specific systems, data and reporting expertise, particularly where the process requires substantial manual intervention.
- 3.Interest rate risk reports to Senior Management and the Board must provide aggregate information as well as sufficient supporting detail to enable Senior Management and the Board to assess the sensitivity of the Bank to changes in market conditions and other important risk factors.
Article 7: Reporting Requirements
- 1.A Bank must submit to the Central Bank the Report on Interest Rate in the Banking Book’ on a quarterly basis.
- 2.A bank offering Islamic financial services must submit to the Central Bank the Report on Rate of Return Risk on a quarterly basis.
Article 8: Islamic Banking
- 1.A Bank providing Islamic financial services must be aware of the factors that give rise to rate of return risk (RoRR), primarily increasing long-term fixed profit rates. (RoRR) is generally associated with overall balance sheet exposures of Banks offering Islamic financial services where mismatches arise between assets and balances from fund providers.
- 2.Cash flow forecasting is central to the measurement and management of RoRR. Banks offering Islamic financial services must consider behavioural maturity in addition to contractual maturity and re-pricing dates for instruments and contracts, and other relevant parameters. Depending on the size and complexity of the Bank, measurement techniques may include simple gap analysis, more advanced simulations or dynamic approaches to assess future cash flow variability and the impact on economic value and income.
- 3.A Bank offering Islamic financial services must assess, monitor and manage its dependency on current account holders funds, as a sudden withdrawal of these funds can have an adverse impact on the overall potential rate of return for the holders of the Bank.
- 4.A consequence of RoRR may be displaced commercial risk. As part of an appropriate framework for the management of displaced commercial risk, a Bank offering Islamic financial services must have in place a policy and framework for managing the expectations of its shareholders and investment account holders and monitoring the market rates of returns of competitors.
Country and Transfer Risk
Country and Transfer Risk Regulation
C 154/2018 Effective from 27/5/2018Article 1: Definitions
- Affiliate: An entity that, directly or indirectly, controls, is controlled by, or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity, or the power to direct or cause the direction of the management of another entity.
- Bank: A financial entity which is authorized by the Central Bank to accept deposits as a bank.
- Board: The Bank’s board of directors.
- Central Bank: The Central Bank of the United Arab Emirates.
- Central Bank Law: Union Law No (10) of 1980 concerning the Central Bank, the Monetary System and Organization of banking as amended or replaced from time to time.
- Central Bank regulations: Any resolution, regulation, circular, rule, standard or notice issued by the Central Bank.
- Country risk: The risk of loss caused by events in a foreign country, which may include changes in economic, social, political or regulatory conditions that affect obligors in that country and, potentially, obligations denominated in that country’s currency.
- Group: A group of entities that includes an entity (the ‘first entity’) and:
- any Parent of the first entity;
- any Subsidiary of the first entity or of any Parent of the first entity; and
- any Affiliate.
- any Parent of the first entity;
- Parent: An entity (the ‘first entity’) which:
- holds a majority of the voting rights in another entity (the ‘second entity’);
- is a shareholder of the second entity and has the right to appoint or remove a majority of the board or managers of the second entity; or
- is a shareholder of the second entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the second entity;
Or;
- if the second entity is a subsidiary of another entity which is itself a subsidiary of the first entity.
- holds a majority of the voting rights in another entity (the ‘second entity’);
- Risk governance framework: As part of the overall approach to corporate governance, the framework through which the Board and management establish and make decisions about the bank’s strategy and risk approach, articulate and monitor adherence to the risk appetite and risk limits relative to the bank’s strategy; and identify, measure, manage and control risks.
- Risk limits: Specific quantitative measures that may not be exceeded, based on, for example, forward-looking assumptions that allocate the bank’s aggregate risk appetite to business lines, legal entities or management units within the bank or group in the form of specific risk categories, concentrations, or other measures, as appropriate.
- Risk management function: Collectively, the systems, structures, policies, procedures and people that measure, monitor and report risk on a bank-wide and, if applicable, group-wide basis.
- Senior management: The executive management of the bank responsible and accountable to the Board for the sound and prudent day-to-day management of the bank, generally including, but not limited to, the chief executive officer, chief financial officer, chief risk officer and heads of the compliance and internal audit functions.
- Subsidiary: An entity (the ‘first entity’) is a subsidiary of another entity (the ‘second entity’) if the second entity:
- holds a majority of the voting rights in the first entity;
- is a shareholder of the first entity and has the right to appoint or remove a majority of the board or managers of the first entity; or
- is a shareholder of the first entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the first entity.
Or;
- if the first entity is a subsidiary of another entity, which is itself a subsidiary of the second entity.
- holds a majority of the voting rights in the first entity;
- Transfer risk: The risk that a borrower will not be able to convert local currency into foreign exchange and so be unable to make debt service payments in foreign currency.
- Affiliate: An entity that, directly or indirectly, controls, is controlled by, or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity, or the power to direct or cause the direction of the management of another entity.
Objective
The objective of the Regulation is to establish the minimum acceptable standards for banks’ approach to managing country and transfer risks with a view to:
- Ensuring the soundness of banks; and
- Contributing to financial stability.
The accompanying Standards supplement the Regulation to elaborate on the supervisory expectations of the Central Bank with respect to the management of country and transfer risks.
- Ensuring the soundness of banks; and
Scope of Application
The Regulation and the accompanying Standards apply to all Banks. Banks established in the UAE with significant Group relationships, including subsidiaries, affiliates, or international branches, must ensure that the Regulation and Standards are adhered to on a solo and group-wide basis.
The Regulation and Standards must be read in conjunction with the Risk Management Regulation and Standards, which establish the requirements for Banks’ overarching approach to risk management.
Introduction
The Central Bank seeks to promote the effective and efficient development and functioning of the banking system. To this end, banks exposed to country and transfer risks are required to have appropriate policies, processes, procedures, systems and controls to identify, monitor and mitigate such risks.
In introducing this Regulation and the accompanying Standards, the Central Bank intends to ensure that Banks’ approach to managing country and transfer risks are in line with leading international practices.
The Regulation and the accompanying Standards are issued pursuant to the powers vested in the Central Bank under the Central Bank Law.
Where the Regulation, or their accompanying Standards, include a requirement to provide information or to take certain measures, or to address certain items listed at a minimum, the Central Bank may impose requirements that are additional to the list provided in the relevant Article.
Article 2: Risk Governance Framework
- A Bank’s risk governance framework must include policies and procedures for the identification, measurement, monitoring and reporting on country and transfer risk in the Bank’s international funding, lending and investments on a timely basis.
- The risk governance framework must provide a bank-wide, or if applicable, group-wide view of country and transfer risks, including, where relevant, intra-group exposures.
- For Banks with material exposure to country and transfer risks, the risk governance framework must, at minimum, provide for the following items:
- Country and transfer risk limits established in the board-approved risk appetite statement;
- Documentation of the roles and responsibilities of the different parts of the Bank involved in managing country and transfer risk;
- Definition of material country and transfer risks taking into account the size and nature of cross-border exposures relative to the total business of the Bank;
- Policies and procedures to ensure that all material country and transfer risks are identified, measured, managed, mitigated and reported upon in a timely and comprehensive manner;
- Policies and procedures to ensure that developments affecting country and transfer risks are monitored, and where required, appropriate countermeasures such as reducing exposure limits or other techniques are employed; and
- Policies and procedures to ensure that provisioning reflects prudent minimums based on internal standards for exposure to each relevant country or through explicit consideration of country and transfer risk in the provisioning for individual exposures.
- Country and transfer risk limits established in the board-approved risk appetite statement;
- A Bank’s risk governance framework must include policies and procedures for the identification, measurement, monitoring and reporting on country and transfer risk in the Bank’s international funding, lending and investments on a timely basis.
Article 3: Risk Management Function
- The risk management function must include policies, procedures, systems and controls for monitoring and reporting to ensure that country and transfer risk exposures are aligned with the Bank’s strategy and business plan and consistent with the board-approved risk appetite and individual risk limits.
Article 4: Stress Testing
- A Bank with material country and transfer risks exposure must include in its stress testing program appropriate scenarios reflecting potential shocks such as introduction of capital and exchange controls in relevant foreign jurisdictions, taking into account the impact on all exposures, domestic or cross-border, affected by such shocks.
Article 5: Information Systems and Internal Reporting
- A Bank must have information systems that enable it to accurately aggregate, monitor and report country exposures. Reports must be provided on a timely basis to the Board and Senior Management, in formats suitable for their use.
Article 6: Reporting Requirements
- Banks must report to the Central Bank on their country and transfer risks exposure in the format and frequency prescribed by the Central Bank.
- A Bank must provide upon request any specific information with respect to country and transfer risks that the Central Bank may require.
- A Bank must immediately notify the Central Bank when it becomes aware of a significant deviation from the country and transfer risk limits established in its board-approved policies, or becomes aware that a material country or transfer risk has not been adequately addressed.
- Banks must report to the Central Bank on their country and transfer risks exposure in the format and frequency prescribed by the Central Bank.
Article 7: Enforcement
- Violation of any provision of this Regulation and the accompanying Standards may be subject to supervisory action as deemed appropriate by the Central Bank.
Article 8: Interpretation of Regulation
- The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
Article 9: Cancellation of Previous Notices
- This Regulation and the accompanying Standards replace all previous Central Bank Regulations with respect to country and transfer risks.
Article 10: Publication and Application
- This Regulation and the accompanying Standards shall be published in the Official Gazette, in both Arabic and English, and shall come into effect one month from the date of publication.
Country and Transfer Risk Standards
C 154/2018 STAIntroduction
- 1.These Standards form part of the Country and Transfer Risks Regulation. All Banks must comply with these Standards, which expand on the Regulation. These Standards are mandatory and enforceable in the same manner as the Regulation.
- 2.Banks engaged in international activities are exposed to the risk that conditions and events in a foreign country will adversely affect their financial performance. They are further exposed to the risk that capital controls or foreign exchange restrictions may limit the ability of a foreign counterparty, branch or subsidiary to make contractual payments. These country and transfer risks could threaten the soundness of a bank if not monitored and controlled.
- 3.A Bank’s board of directors is in ultimate control of the bank and accordingly, ultimately responsible for the bank’s approach to country and transfer risk. Country and transfer risks may not be material for all banks. The Board is responsible for ensuring that country and transfer risks exposures are identified and if required, that appropriate policies and procedures are in place to manage those risks. There is no one-size-fits-all or single best solution. Accordingly, each Bank could meet the minimum requirements of the Country and Transfer Risks Regulation and Standards in a different way and thus may adopt a country and transfer risk framework appropriate to the risk profile, nature, size and complexity of its business and structure. The onus is on the bank’s board to demonstrate that it has implemented an approach that adequately addresses country and transfer risks. Banks are encouraged to adopt leading practices that exceed the minimum requirements of the Regulation and Standards1.
- 4.The Standards follow the structure of the Regulation, with each article corresponding to the specific article in the Regulation.
1 The Central Bank will apply the principle of proportionality in the enforcement of the Regulation and Standards, whereby smaller banks may demonstrate to the Central Bank that the objectives are met without necessarily addressing all of the specifics cited in the Standards.
Article 1: Definitions
- 1.Affiliate: An entity that, directly or indirectly, controls, is controlled by or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity or of the power to direct or cause the direction of the management of another entity.
- 2.Bank: A financial entity, which is authorized by the Central Bank to accept deposits as a bank.
- 3.Central Bank: The Central Bank of the United Arab Emirates.
- 4.Central Bank Law: Union Law No (10) of 1980 concerning the Central Bank, the Monetary System and Organization of Banking as amended or replaced from time to time.
- 5.Central Bank regulations: Any resolution, regulation, circular, rule, standard or notice issued by the Central Bank.
- 6.Country risk: The risk of loss caused by events in a foreign country that may include changes in economic, social, political or regulatory conditions that affect obligors in that country and obligations denominated in that country’s currency.
- 7.Group: A group of entities that includes an entity (the ‘first entity’) and:
- a.any Parent of the first entity;
- b.any Subsidiary of the first entity or of any Parent of the first entity; and
- c.any Affiliate.
- 8.Parent: An entity (the ‘first entity’) which:
- a.holds a majority of the voting rights in another entity (the ‘second entity’);
- b.is a shareholder of the second entity and has the right to appoint or remove a majority of the board of directors or managers of the second entity; or
- c.is a shareholder of the second entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the second entity;
Or;
- d.if the second entity is a subsidiary of another entity which is itself a subsidiary of the first entity.
- 9.Risk governance framework: As part of the overall approach to corporate governance, the framework through which the board and management establish and make decisions about the bank’s strategy and approach to risk management; articulate and monitor adherence to the risk appetite and risks limits relative to the bank’s strategy; and identify, measure, manage and control risks.
- 10.Risk limits: Specific quantitative measures which may not be exceeded, based on, for example, forward looking assumptions that allocate the bank’s aggregate risk appetite to business lines, legal entities or management units within the bank or group in the form of specific risk categories, concentrations or other measures as appropriate.
- 11.Risk management function: Collectively, the systems, structures, policies, procedures and people that measure, monitor and report risk on a bank and, if applicable, group-wide basis.
- 12.Senior management: The executive management of the bank responsible and accountable to the board for the sound and prudent day-to-day management of the bank, generally including, but not limited to, the chief executive officer, chief financial officer, chief risk officer and heads of the compliance and internal audit functions.
- 13.Subsidiary: An entity (the ‘first entity’) is a subsidiary of another entity (the ‘second entity’) if the second entity:
- a.holds a majority of the voting rights in the first entity;
- b.is a shareholder of the first entity and has the right to appoint or remove a majority of the board of directors or managers of the first entity; or
- c.is a shareholder of the first entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the first entity;
Or;
- d.if the first entity is a subsidiary of another entity that is itself a subsidiary of the second entity.
- 14.Transfer risk: The risk that a borrower will not be able to convert local currency into foreign exchange and so be unable to make debt service payments in foreign currency.
Article 2: Risk Governance Framework
- 1.The risk governance framework varies with the specific circumstances of each bank, particularly the risk profile, nature, size and complexity of its business and structure. For a bank with material country and transfer risk exposures, its risk governance framework must address the following:
- a.Effective oversight by the board of directors;
- b.Adequate risk management policies and procedures;
- c.An accurate system for reporting country exposures;
- d.An effective process for analyzing country risk;
- e.A country risk-rating system;
- f.Country risk exposure limits;
- g.Regular monitoring of country conditions;
- h.Provisioning policies that explicitly consider country and transfer risks;
- i.Periodic stress-testing of foreign exposures;
- j.Oversight by the risk management function; and
- k.Independent assurance by the internal audit function.
- 2.A bank’s definition and identification of material country and transfer risks must take into account the risk profile, nature, size and complexity of its business and structure. The Central Bank will generally consider as material an aggregate exposure to any single foreign jurisdiction exceeding five percent, or an aggregate exposure to all foreign jurisdictions exceeding 10 percent, of any relevant metric which may include but is not limited to total loans, total liabilities, interest income, interest expense and non-interest income. Banks are encouraged to establish lower thresholds for materiality if required for consistency with the board-approved risk appetite statement.
- 3.A bank must establish and maintain a board-approved risk appetite statement that specifies the types of country risk the bank is prepared to assume in pursuit of its business strategy and objectives and limits for those risks. For banks with moderate country risk exposure it may be appropriate to address these risks under a single grouping of cross-border exposures, but depending on the business of the bank, it may be appropriate to specifically address some or all of the below:
- a.Sovereign risk — a foreign government’s capacity and willingness to repay its direct and indirect foreign currency obligations;
- b.Contagion risk — adverse developments in one country lead to a downgrade and/or difficulty accessing international markets not only for that country but for others in a region or investment class, notwithstanding that the other countries may be more credit worthy;
- c.Currency risk — a borrower’s domestic currency holdings and cash flow become inadequate to service its foreign currency denominated debt due to changes in exchange rates2;
- d.Indirect country risk — the repayment ability of a domestic borrower is affected by adverse developments in a country where the borrower has significant business interests;
- e.Liquidity risk — developments in a country where the bank raises a significant portion of its deposits or other funding may adversely affect the bank’s liquidity and funding profile; and
- f.Macroeconomic risks — a foreign counterparty may be adversely affected by high interest rates, currency depreciation or broader macroeconomic instability, affecting its repayment capacity.
- 4.The board-approved risk appetite statement must specify authorized activities, investments and instruments and delineate any types of country and transfer risk that the bank is not prepared to assume and, where appropriate, specify any activities, investments and instruments that are not consistent with the bank’s risk appetite. Risk limits are typically established on a country basis, but banks must also consider whether regional or other limits such as aggregate exposures to lesser developed countries are appropriate.
- 5.A bank must also consider whether different limits may be established for different types of exposure in a specific country.
- 6.Country exposure limits, sub-limits and regional or other limits with respect to country and transfer risk as established in the board-approved risk appetite statement must take into account the following:
- 7.A bank’s provisioning policies must expressly consider country and transfer risks. Provisions for country and transfer risks may be made on an aggregate basis by country in addition to specific provisions against individual exposures, or by factoring an element of provision for each country risk into the specific provisioning for each individual exposure. Regardless of the approach, banks must ensure adequate provisioning for country and transfer risks based on their assessment of the probability of losses on their cross-border exposures.
2 Note that this is in addition to transfer risk — the risk that official restrictions on currency conversion and/or cross-border remittances may affect the counterparty’s ability to make payments.
- 1.The risk governance framework varies with the specific circumstances of each bank, particularly the risk profile, nature, size and complexity of its business and structure. For a bank with material country and transfer risk exposures, its risk governance framework must address the following:
Article 3: Risk Management Function
- 1.The specific requirements for the risk management function will vary with the specific circumstances of each bank, particularly the risk profile, nature, size and complexity of its business and structure. For banks with material country and transfer risks exposure, the risk management function must address the following:
- a.Quantitative and qualitative ongoing assessment of the risks associated with each country in which the institution has or is planning to have exposure;
- b.Formal analysis of country risk completed at least annually, with an effective system for monitoring developments in the interim;
- c.Conclusions reported to Senior Management and the board in a manner that provides a bank-wide and, if applicable, group-wide view of country and transfer risks exposures; and
- d.Verification that individual and aggregate country and transfer risks exposure limits are adhered to, with a process for escalating breaches to senior management, the board or the board risk committee, as appropriate.
- 2.A bank with material country and transfer risks exposures must have a country risk rating system reflecting a structured approach to assessing country and transfer risk. Banks may use external country ratings as part of their internal approach. A bank’s country risk-rating system must be linked to its country and transfer risk provisioning methodology. A bank is encouraged to compare for reasonableness the results of their internal country risk-rating process to one or more external rating systems, such as export credit agencies classifications, OECD country risk assessments3, or ratings agencies sovereign ratings.
3 Country risk classifications of the OECD Participants to the Arrangement on Officially Supported Export Credits are available at http://www.oecd.org/tad/xcred/crc.htm.
- 1.The specific requirements for the risk management function will vary with the specific circumstances of each bank, particularly the risk profile, nature, size and complexity of its business and structure. For banks with material country and transfer risks exposure, the risk management function must address the following:
Article 4: Stress-Testing
- 1.A bank with material country and transfer risks exposure must include in its stress testing program appropriate scenarios for country and transfer risk. This does not necessarily require sophisticated modelling tools, but does require the bank to evaluate the potential impact of various scenarios affecting countries, regions or types of foreign exposures, as appropriate considering the bank’s business. Scenarios may include, but are not limited to, macro-economic shocks such as interest rate and exchange rate movements, GDP contraction and the introduction of exchange or capital controls.
Article 5: Information Systems and Internal Reporting
- 1.A bank’s systems must support supervisory reporting requirements for country and transfer risks as provided in this Regulation and Standards as well as provision of country and transfer risks reports to all relevant parties within the bank on a timely basis and in a format commensurate with their needs.
- 2.The processes for aggregating the necessary data and producing supervisory and internal country and transfer risks management reports must be fully documented and must establish standards, cut-off times and schedules for report production. The aggregation and reporting process must be subject to high standards of validation through periodic review by members of the internal audit function with specific systems, data and reporting expertise, particularly where the process requires substantial manual intervention.
Article 6: Reporting Requirements
- 1.A bank must submit to the Central Bank on a quarterly basis the Report on Country and Transfer Risks in a format specified by the Central Bank.
Market Risk
Market Risk Regulation
C 164/2018 Effective from 29/8/2018Introduction
The Central Bank seeks to promote the effective and efficient development and functioning of the banking system. To this end, Banks must have a comprehensive approach to market risk management, including Board and Senior Management oversight, to ensure their resiliency and enhance overall financial stability.
In introducing this Regulation and the accompanying Standards, the Central Bank intends to ensure that Banks’ approaches to the management of market risk are in line with leading international practices.
This Regulation and the accompanying Standards are issued pursuant to the powers vested in the Central Bank under the Central Bank Law.
Where this Regulation, or its accompanying Standards, include a requirement to provide information or to take certain measures, or to address certain items listed at a minimum, the Central Bank may impose requirements, which are additional to the list provided in the relevant article.
Objective
The objective of this Regulation is to establish the minimum acceptable standards for Banks’ approach to market risk management, with a view to:
i. Ensuring the soundness of Banks; and
ii. Enhancing financial stability.
The accompanying Standards supplement the Regulation to elaborate on the supervisory expectations of the Central Bank with respect to market risk management.
Scope of Application
This Regulation and the accompanying Standards apply to all Banks. Banks established in the UAE with significant Group relationships, including Subsidiaries, Affiliates or international branches must ensure that the Regulation and Standards are adhered to on a solo and group-wide basis.
This Regulation and the accompanying Standards must be read in conjunction with the Risk Management Regulation and Standards issued by the Central Bank, which establish the requirements for a Bank’s overarching approach to risk management.
Article 1: Definitions
- Affiliate: An entity that, directly or indirectly, controls, is controlled by, or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity, or of the power to direct or cause the direction of the management of another entity.
- Bank: A financial entity, which is authorized by the Central Bank to accept deposits as a Bank.
- Board: The Bank’s Board of Directors.
- Banking Book: Positions in financial instruments that are expected to be held to maturity.
- Central Bank: The Central Bank of the United Arab Emirates.
- Central Bank Law: Union Law No (10) of 1980 concerning the Central Bank, the Monetary System and Organization of Banking as amended or replaced from time to time.
- Central Bank regulations: Any resolution, regulation, circular, rule, standard or notice issued by the Central Bank.
- Group: A group of entities that includes an entity (the 'first entity') and:
- any Parent of the first entity;
- any Subsidiary of the first entity or of any Parent of the first entity; and
- any Affiliate.
- any Parent of the first entity;
- Islamic Financial Services: Shari’a compliant financial services offered by Islamic Banks and Conventional Banks offering Islamic banking products (Islamic Windows).
- Market risk: The risk of losses in on and off-balance sheet positions arising from movements in market prices.
- Parent: An entity (the 'first entity') which:
- holds a majority of the voting rights in another entity (the 'second entity');
- is a shareholder of the second entity and has the right to appoint or remove a majority of the board of directors or managers of the second entity; or
- is a shareholder of the second entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the second entity.
Or; - if the second entity is a subsidiary of another entity which is itself a subsidiary of the first entity.
- holds a majority of the voting rights in another entity (the 'second entity');
- Risk appetite: The aggregate level and types of risk a Bank is willing to assume, decided in advance and within its risk capacity, to achieve its strategic objectives and business plan.
- Risk governance framework: As part of the overall approach to corporate governance, the framework through which the Board and management establish and make decisions about the Bank’s strategy and risk approach; articulate and monitor adherence to the risk appetite and risk limits relative to the Bank’s strategy; and identify, measure, manage and control risks.
- Risk limits: Specific quantitative measures that must not be exceeded, based on, for example, forward looking assumptions that allocate the Bank’s aggregate risk appetite to business lines, legal entities or management units within the Bank or Group in the form of specific risk categories, concentrations or other measures, as appropriate.
- Risk profile: Point in time assessment of the Bank’s gross (before the application of any mitigants) or net (after taking into account mitigants) risk exposures aggregated within and across each relevant risk category based on current or forward-looking assumptions.
- Senior Management: The executive management of the Bank responsible and accountable to the Board for the sound and prudent day-to-day management of the Bank, generally including, but not limited to, the chief executive officer, chief financial officer, chief risk officer and heads of the compliance and internal audit functions.
- Subsidiary: An entity (the 'first entity') is a subsidiary of another entity (the 'second entity') if the second entity:
- holds a majority of the voting rights in the first entity;
- is a shareholder of the first entity and has the right to appoint or remove a majority of the board of directors or managers of the first entity; or
- is a shareholder of the first entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the first entity.
Or;
if the first entity is a subsidiary of another entity which is itself a subsidiary of the second entity.
- holds a majority of the voting rights in the first entity;
- Trading Book: Positions in financial instruments and commodities held either with trading intent or in order to hedge other elements of the trading book.
- Affiliate: An entity that, directly or indirectly, controls, is controlled by, or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity, or of the power to direct or cause the direction of the management of another entity.
Article 2: Risk Governance Framework
- A Bank must have an appropriate market risk strategy and market risk governance framework that provides a Bank-wide and, if applicable, Group-wide view of market risk. This includes policies, processes, procedures, systems and controls to identify, measure, evaluate, monitor, report and control or mitigate material sources of market risk on a timely basis.
- The Board must approve the Bank’s strategies, policies and processes for the management of market risk, which must be reviewed annually.
- The Board must ensure that the Bank has in place adequate systems to identify, measure and manage market risk. Roles and responsibilities must be clearly articulated and provisions must be made for adequate separation of duties and avoiding conflicts of interest.
- The Board must ensure that the Bank has appropriate market risk management processes that provide a bank-wide and, if applicable, Group-wide view of market risk exposure. These must be consistent with the risk appetite statement, risk profile, systemic importance and capital strength of the Bank, take into account market and macroeconomic conditions and the risk of a significant deterioration in market liquidity.
- Senior Management must ensure that the strategy, policies and procedures are developed and implemented effectively. The Board must oversee the Senior Management to ensure that the strategies, policies and processes are implemented effectively and fully integrated into the Bank’s overall risk management process.
- A Bank’s policies and processes must establish an appropriate and properly controlled market risk environment, including, at a minimum, the following items:
- Effective information systems for accurate and timely identification, aggregation, monitoring and reporting of market risk exposure to the Board and Senior Management;
- Appropriate market risk limits consistent with the Bank’s risk appetite, risk profile and capital strength and with the management’s ability to manage market risk and which are understood by and regularly communicated to, relevant staff;
- Exception tracking and reporting processes that ensure prompt action at the appropriate level of the Senior Management or Board, where necessary;
- Effective controls around the use of models to identify and measure market risk and set limits; and
- Sound policies and processes for allocation of exposures to the trading book.
- Effective information systems for accurate and timely identification, aggregation, monitoring and reporting of market risk exposure to the Board and Senior Management;
- A Bank must ensure that intra-day exposures are managed within limits established by the Board-approved market risk policies.
- A Bank wishing to establish a trading book must submit for the Central Bank’s review a trading book policy statement that specifies those activities that belong in the trading book. Any significant change in a Bank’s existing trading book policy must be promptly submitted to the Central Bank for review.
- A Bank must have an appropriate market risk strategy and market risk governance framework that provides a Bank-wide and, if applicable, Group-wide view of market risk. This includes policies, processes, procedures, systems and controls to identify, measure, evaluate, monitor, report and control or mitigate material sources of market risk on a timely basis.
Article 3: Systems and Controls
- A Bank’s market risk measurement systems, monitoring and controls must enable it to maintain capital adequacy on a continuous basis and remain within its intra-day and other market risk limits.
- An independent review of a Bank’s market risk measurement system and the overall market risk management process must be earned out at least annually, as part of the Bank’s own internal auditing process, by functionally independent, appropriately trained and competent personnel.
- A Bank must capture all transactions on a timely basis.
- A Bank’s internal models must be validated internally by suitably qualified parties independent of the model development process, to ensure that they are conceptually sound and adequately capture all material market risks.
- A Bank must have its internal models validated externally by an independent and suitably qualified party on a regular basis and, in addition, on an as-needed basis.
- A Bank’s back-testing program must consist of periodic comparisons of its model results with the realized profit or loss (trading income) relating to corresponding periods.
- A Bank’s market risk measurement systems, monitoring and controls must enable it to maintain capital adequacy on a continuous basis and remain within its intra-day and other market risk limits.
Article 4: Valuation
- A Bank must have systems and controls to ensure that the Bank’s mark-to-market positions, whether in the banking book or trading book, are revalued frequently.
- A Bank’s valuation process must use consistent and prudent practices and reliable market data, or, in the absence of market prices, internal or industry-accepted models, verified by a function independent of the relevant risk-taking business units.
- A Bank that relies on modelling for the purposes of valuation must ensure that the model is validated by a function independent of the relevant risk-taking business units.
- A Bank must establish and maintain policies and processes for considering valuation adjustments for positions that otherwise cannot be prudently valued, including concentrated, less liquid and stale positions.
- A Bank must make appropriate valuation adjustments for uncertainties in determining the fair value of assets and liabilities.
- A Bank operating a trading book must establish an appropriate valuation methodology and measurement model.
- A Bank must have systems and controls to ensure that the Bank’s mark-to-market positions, whether in the banking book or trading book, are revalued frequently.
Article 5: Capital
- A Bank must at all times hold appropriate levels of capital against unexpected losses, which may arise from its market risk exposures.
- A Bank must ensure that market risk capital requirements are met on a continuous basis.
- A Bank must at all times hold appropriate levels of capital against unexpected losses, which may arise from its market risk exposures.
Article 6: Stress Testing
- A Bank must include market risk exposure in its forward-looking stress-testing programs as part of its comprehensive approach to risk management.
Article 7: Reporting Requirements
- A Bank must inform the Central Bank of all significant changes in its market risk measurement systems and in its market risk profile.
- A Bank must promptly notify the Central Bank when it becomes aware of a significant deviation from its Board-approved market risk limits, policies or procedures, or becomes aware that material market risks have not been adequately addressed.
- Banks must report to the Central Bank on market risk in the format and frequency prescribed in the Standards.
- A Bank must inform the Central Bank of all significant changes in its market risk measurement systems and in its market risk profile.
Article 8: Islamic Banking
- A Bank offering Islamic financial services must ensure that its comprehensive approach to market risk management incorporates appropriate measures to comply with Shari’a rules and principles and related Shari’a control functions.
Article 9: Enforcement
- Violation of any provision of this Regulation and the accompanying Standards shall be subject to supervisory action as deemed appropriate by the Central Bank.
Article 10: Interpretation of Regulations
- The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
Article 11: Cancellation of Previous Notices
- This Regulation and the accompanying Standards replace all previous Central Bank regulations with respect to market risk.
Article 12: Publication and Application
- This Regulation and the accompanying Standards shall be published in the Official Gazette in both Arabic and English and shall come into effect one month from the date of publication.
Market Risk Standards
C 164/2018 Effective from 29/9/2018Introduction
- 1. These Standards form part of the Market Risk Regulation. All Banks must comply with these Standards, which expand on the Regulation. These Standards are mandatory and enforceable in the same manner as Regulation.
- 2. A Bank’s Board is in ultimate control of the Bank and accordingly ultimately responsible for market risk management. There is no one-size-fits-all or single best solution. Accordingly, each Bank could meet the minimum requirements of the Regulation and Standards in different ways and thus may adopt an organizational framework appropriate to the risk profile, nature, size and complexity of its business and structure. The onus is on the Board to demonstrate that it has implemented an approach that adequately addresses market risk. Banks are encouraged to adopt leading practices that exceed the minimum requirements of the Regulation and Standards.1
- 3. The Standards follow the structure of the Regulation, with each article corresponding to the specific article in the Regulation.
1 The Central Bank will apply the principle of proportionality in the enforcement of the Regulation and Standards, whereby smaller Banks may demonstrate to the Central Bank that the objectives are met without necessarily addressing all of the specifics cited in the Standards.
Article 1: Definitions
- 1. Affiliate: An entity that, directly or indirectly, controls, is controlled by, or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity, or of the power to direct or cause the direction of the management of another entity.
- 2. Bank: A financial entity, which is authorized by the Central Bank to accept deposits as a Bank.
- 3. Banking book: Positions in financial instruments that are available for sale or expected to be held to maturity. The following instruments must be assigned to the banking book:
- a. Unlisted equities;
- b. Instruments designated for securities warehousing;
- c. Real estate holdings;
- d. Retail and small and medium-sized enterprise credit;
- e. Equity instruments in a fund in which the Bank cannot look through the fund daily or obtain daily prices for its investment in that fund;
- f. Derivative instruments that have instruments of the type specified in 1.3.a through 1.3.e above as underlying assets;
- g. Instruments held for the purpose of hedging a particular risk of a position in the types of instruments of the type specified in 1.3.a through 1.3.e above; and
- h. Any other instrument as may be determined by the Central Bank.
- 4. Board: The Bank’s Board of Directors.
- 5. Central Bank: The Central Bank of the United Arab Emirates.
- 6. Central Bank Law: Union Law No (10) of 1980 concerning the Central Bank, the Monetary System and Organization of Banking as amended or replaced from time to time.
- 7. Central Bank regulations: Any resolution, regulation, circular, rule, standard or notice issued by the Central Bank.
- 8. Financial instrument: Any contract that gives rise to both a financial asset of one entity and a financial liability of another entity. Financial instruments include primary financial instruments (or cash instruments) and derivative financial instruments. A financial asset is any asset that is cash and or, the right to receive cash or another financial instrument. A financial liability is a contractual obligation to deliver cash or another financial asset or to exchange financial liabilities under conditions that are potentially unfavourable.
- 9. Group: A group of entities that includes an entity (the ‘first entity’) and:
- a. any Parent of the first entity;
- b. any Subsidiary of the first entity or of any Parent of the first entity; and
- c. any Affiliate.
- 10. Independent price verification: The process by which market prices or model inputs are regularly verified for accuracy. Independent price verification is distinct from daily marking-to-market. Independent price verification entails a higher standard of accuracy in which the market prices or model inputs are used to determine profit and loss figures, whereas daily marks are collected primarily for management reporting in between reporting dates.
- 11. Islamic Financial Services: Shari’a compliant financial services offered by Islamic Banks and Conventional Banks offering Islamic banking products (Islamic Windows).
- 12. Market risk: The risk of losses in on- and off-balance sheet positions arising from movements in market prices. For the purposes of these Standards, these risks are,
- a. In the trading book of the bank, the risks pertaining to interest rate related instruments and equities, and
- b. Throughout the bank, the risks pertaining to foreign exchange and commodities.
- 13. Marking-to-market: Valuation of positions at readily available close-out prices in orderly transactions that are sourced independently. Examples of readily available close-out prices include exchange prices, screen prices, or quotes from several independent reputable brokers. Marking-to-market may be performed by dealers. Daily marking-to-market is distinct from independent price verification.
- 14. Marking-to-model: Any valuation, which has to be benchmarked, extrapolated or otherwise calculated from a market input.
- 15. Parent: An entity (the ‘first entity’) which:
- a. holds a majority of the voting rights in another entity (the ‘second entity’);
- b. is a shareholder of the second entity and has the right to appoint or remove a majority of the Board of directors or managers of the second entity; or
- c. is a shareholder of the second entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the second entity;
Or;
- d. If the second entity is a subsidiary of another entity which is itself a subsidiary of the first entity.
- 16. Residual risk: The risk exposure after controls are considered.
- 17. Risk appetite: The aggregate level and types of risk a Bank is willing to assume, decided in advance and within it risk capacity, to achieve its strategic objectives and business plan.
- 18. Risk governance framework: As part of the overall approach to corporate governance, the framework through which the Board and management establish and make decisions about the Bank’s strategy and approach to risk management; articulate and monitor adherence to the risk appetite and risks limits relative to the Bank’s strategy; and identify, measure, manage and control risks.
- 19. Risk limits: Specific quantitative measures that may not be exceeded, based on, for example, forward-looking assumptions that allocate the Bank’s aggregate risk appetite to business lines, legal entities or management units within the Bank or Group in the form of specific risk categories, concentrations, or other measures, as appropriate.
- 20. Risk Management function: Collectively, the systems, structures, policies, procedures and people that measure, monitor and report risk on a Bank-wide and, if applicable, Group-wide basis.
- 21. Senior Management: The executive management of the Bank responsible and accountable to the Board for the sound and prudent day-to-day management of the Bank, generally including, but not limited to, the chief executive officer, chief financial officer, chief risk officer and heads of the compliance and internal audit functions.
- 22. Subsidiary: An entity (the ‘first entity’) is a subsidiary of another entity (the ‘second entity’) if the second entity:
- a. holds a majority of the voting rights in the first entity;
- b. is a shareholder of the first entity and has the right to appoint or remove a majority of the board of directors or managers of the first entity; or
- c. is a shareholder of the first entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the first entity;
Or; - d. If the first entity is a subsidiary of another entity that is itself a subsidiary of the second entity.
- 23. Trading book: Positions in financial instruments and commodities held either with trading intent or in order to hedge other elements of the trading book. Any instrument held for one or more of the following purposes must be assigned to the trading book:
- a. Short-term resale;
- b. Profiting from short-term price movements;
- c. Locking in arbitrage profits;
- d. Hedging risks that arise from instruments meeting criteria 3.16.a through 3.16.c above; and
- e. Any other instrument as may be determined by the Central Bank.
Article 2: Risk Governance Framework
- 1. A Bank must establish, implement and maintain a market risk governance framework, which enables it to identify, assess, monitor, mitigate and control market risk. The market risk framework consists of policies, processes, procedures, systems and controls.
- 2. The market risk governance framework must be documented and approved, maintained and overseen by the Board and must provide for a sound and well-defined framework to address the Bank’s market risks.
- 3. A Bank’s market risk management processes must be integrated with the Bank’s overall risk management processes. Banks that have trading books must develop separate and specific trading book policy statements and risk frameworks.
- 4. The Board and Senior Management must be actively involved in the market risk control process and must regard risk control as an essential aspect of the business to which significant resources need to be devoted. In this regard, the daily reports prepared by the market risk management function must be reviewed by a level of management with sufficient seniority and authority to enforce both reductions of positions taken by individual traders and reductions in the Bank’s overall risk exposure.
Article 3: Systems & Controls
General
- 1. The Board must ensure compliance with a documented set of internal policies, controls and procedures concerning the operation of the market risk measurement system. Documentation in the form of a market risk manual or policy must provide a useable and understandable overview of the basic principles of the market risk management system and an explanation of the empirical techniques used to measure market risk.
Risk Factors
- 2. A Bank must specify in its market risk measurement system an appropriate set of market risk factors (market rates and prices that affect the value of the Bank’s market-related positions) that are sufficient to capture the risk inherent in the Bank’s portfolio of on- and off-balance sheet trading positions.
Interest Rates
- 3. A Bank must specify a set of risk factors corresponding to interest rates in each currency in which the Bank has interest-rate-sensitive on- or off-balance sheet positions. The number of risk factors used must be driven by the nature of the Bank’s trading strategies and must include, at a minimum, the following:
- a. Modelling of the yield curve using one of a number of generally accepted approaches, for example, by estimating forward rates of zero coupon yields.
- b. Dividing the yield curve into various maturity segments in order to capture variation in the volatility of rates along the yield curve. There typically will be one risk factor corresponding to each maturity segment.
- c. For material exposures to interest rate movements in the major currencies and markets, modelling the yield curve using a minimum of six risk factors. The number of risk factors used ultimately must be driven by the nature of the Bank’s trading strategies. For instance, a Bank with a portfolio of various types of securities across many points of the yield curve and that engages in complex arbitrage strategies would require a greater number of risk factors to capture interest rate risk accurately.
- 4. The risk measurement system must incorporate separate risk factors to capture spread risk (e.g. between bonds and swaps). These include but are not limited to specifying a completely separate yield curve for non-government fixed-income instruments (for instance, swaps or municipal securities) and estimating the spread over government rates at various points along the yield curve.
- 3. A Bank must specify a set of risk factors corresponding to interest rates in each currency in which the Bank has interest-rate-sensitive on- or off-balance sheet positions. The number of risk factors used must be driven by the nature of the Bank’s trading strategies and must include, at a minimum, the following:
Exchange Rates
- 5. A Bank must specify risk factors corresponding to the exchange rate between the domestic currency and individual foreign currencies in which its positions are denominated.
Equities
- 6. For equity prices, there must be risk factors corresponding to each of the equity markets in which the Bank holds significant positions. The sophistication and nature of the modelling technique for a given market must correspond to the Bank’s exposure to the overall market as well as its concentration in individual equity issues in that market.
- 7. At a minimum, there must be a risk factor that is designed to capture market-wide movements in equity prices (e.g. a market index). Positions in individual securities or in sector indices could be expressed in “beta-equivalents”2 relative to this market-wide index. Alternatively, a Bank may identify risk factors corresponding to various sectors of the overall equity market (for instance, industry sectors or cyclical and non-cyclical sectors), or specify risk factors corresponding to the volatility of individual equity issues.
2 A “beta-equivalent” position would be calculated from a market model of equity price returns (such as the Capital Asset Pricing Model) by regressing the return on the individual stock or sector index on the risk-free rate of return and the return on the market index.
Commodities
- 8. A Bank must specify risk factors corresponding to each of the commodity markets in which it holds significant positions. A Bank’s commodity risk factors must, at a minimum, include the following:
- a. Directional risk, to capture the exposure from changes in spot prices arising from net open positions;
- b. Forward gap and interest rate risks, to capture the exposure to changes in forward prices; and
- c. Basis risk, to capture the exposure to changes in the price relationships between two similar, but not identical, commodities.
- 9. For a Bank with relatively limited positions in commodity-based instruments, a less complex specification of risk factors would be acceptable. Such a specification would likely entail one risk factor for each commodity price to which the Bank is exposed. In cases where the aggregate positions are quite small, it might be acceptable to use a single risk factor for a relatively broad sub-category of commodities (for instance, a single risk factor for all types of oil.) For more active trading, the model must also take account of variation in the “convenience yield” between derivatives positions such as forwards and swaps and cash positions in the commodity.
- 8. A Bank must specify risk factors corresponding to each of the commodity markets in which it holds significant positions. A Bank’s commodity risk factors must, at a minimum, include the following:
Options
- 10. If a Bank’s risk appetite statement includes taking option positions, the market risk measurement system must specify risk factors corresponding to the implied volatilities of those options, to capture the risk of gain or loss resulting from changes in volatility of those positions.
- 11. The following criteria apply to the measurement of options risk:
- a. Bank’s models must capture the non-linear price characteristics of options positions; and
- b. Each Bank’s risk measurement system must have a set of risk factors that captures the volatilities of the rates and prices underlying option positions, including Vega risk. Banks with relatively large and/or complex options portfolios must have detailed specifications of the relevant volatilities.
Internal Review
- 12. The Board-approved policies must provide for an independent review by the internal audit function of the market risk measurement system at least annually. The review must include both the activities of the business trading units and of the independent risk management function. At a minimum, a review must specifically address the following:
- a. The organization of the market risk management function, adequacy of the documentation of the market risk management system and process and the approval process for risk pricing models and valuation systems used by front-and back-office personnel;
- b. The scope of the market risks captured by the market risk measurement system’s models; the accuracy and appropriateness of the risk measurement system (including any significant changes); the accuracy and completeness of position data; the accuracy of calculation and risk transformation calculations; integration of market risk measures into daily risk management; accuracy and appropriateness of volatility and correlation assumptions and (if using the historical simulation approach) calculations of historical rate movements; and the integrity of the management information system with respect to market risk;
- c. The verification of the consistency, timeliness and reliability of the data sources used to run internal models, including the independence of such data sources;
- d. The validation of any significant change in the market risk measurement process, including the evaluation of conceptual/methodological soundness, as well as developmental evidence;
- e. Evidence of ongoing model monitoring, including process verification and benchmarking;
- f. The verification of the model’s accuracy through frequent back-testing of outcomes analysis, including key internal parameters; and
- g. The process used to produce the calculation of market risk capital.
- 12. The Board-approved policies must provide for an independent review by the internal audit function of the market risk measurement system at least annually. The review must include both the activities of the business trading units and of the independent risk management function. At a minimum, a review must specifically address the following:
Models
- 13. The Board must ensure that Board-approved policies adequately provide for market risk measurement methodologies commensurate with the risk profile, nature, size and complexity of the Bank’s business and structure. A Bank that has a trading book must have a robust modelling framework. Development, internal approval and ongoing use of models and other market risk management methodologies must be governed by Board-approved policies and procedures, which at a minimum must address initial and ongoing validation, valuation and independent review by the internal audit function.
- 14. The risk management function must produce and analyse daily reports on the output of the Bank’s market risk measurement models, including an evaluation of the relationship between measures of risk exposure and trading limits. This function must be independent from business trading units and must report directly to Senior Management.
- 15. A Bank’s internal risk measurement models must be closely integrated into the day-to-day risk management process of the Bank. Model output must be an integral part of the process of planning monitoring and controlling the Bank’s Market Risk profile.
- 16. The Market Risk measurement system must be used in conjunction with internal trading and exposure limits. In this regard, trading limits must be related to the Bank’s risk measurement model in a manner that is consistent over time and that it is well understood by both traders and Senior Management.
- 17. A Bank must include in its internal models risk factors deemed relevant for pricing. Any proxies used must show a good track record of the actual position held; for example, an equity index for a position in an individual stock.
Internal Validation
- 18. A Bank using models must provide for initial and on-going validation by a risk management function independent of the risk-taking functions of the internal model and when any significant changes are made to the model. More frequent validation is required where there have been significant structural changes in the market or changes to the composition of the portfolio which might lead to the model no longer being adequate.
- 19. A Bank’s model validation must not be limited to profit or loss attribution and back-testing, but, at a minimum, also must include tests to demonstrate that any assumptions made within the internal model are appropriate and do not underestimate risk. This may include normal distribution assumption, the use of the square root of time to scale from a one day holding period to a 10 day holding period or where extrapolation or interpolation techniques are used, or pricing models.
- 20. Testing for model validation must use hypothetical changes in portfolio value that would occur were end-of-day positions to remain unchanged. It therefore excludes fees, commissions, bid-ask spreads, net interest income and intra-day trading.
- 21. Additional tests are required, which may include but are not limited to:
- a. Testing carried out for longer than required for the regular back-testing program (for instance 3 years). The longer period generally improves the power of the back-testing. A longer time period may not be desirable if the model or market conditions have changed to the extent that historical data is no longer relevant;
- b. Testing carried out using confidence intervals in addition to the 97.5 percent and 99 percent interval required under the Basel quantitative standards;
- c. Testing of portfolios below the overall Bank level;
- d. The use of hypothetical portfolios to ensure that the model is able to account for particular structural features that may arise, for example, where data histories for a particular instrument do not meet the quantitative standards and where the Bank has to map these positions to proxies;
- e. Ensuring that material basis risks are adequately captured. This may include mismatches between long and short positions by maturity or by issuer; and
- f. Ensuring that the model captures concentration risk that may arise in an undiversified portfolio.
External Validation
- 22. The validation of the accuracy of a Bank’s models by an independent appropriately qualified specialist at a minimum (e.g. an external auditor) must include the following steps:
- a. Verifying that the internal validation processes are operating in a satisfactory manner;
- b. Ensuring that the formulae used in the calculation process as well as for the pricing of options and other complex instruments are validated by a qualified unit, which in all cases must be independent from the trading area;
- c. Checking that the structure of internal models is adequate with respect to the Bank’s activities and geographical coverage;
- d. Checking the results of the Bank’s back testing of its internal measurement system (for example, comparing model estimates with actual profits and losses) to ensure that the model provides a reliable measure of potential losses over time. A Bank must make the results as well as the underlying inputs to its model calculations available to the independent specialist; and
- e. Making sure that data flows and processes associated with the risk measurement system are transparent and accessible. In particular, it is necessary that the independent specialist has access as required to the model’s specifications and parameters.
- 22. The validation of the accuracy of a Bank’s models by an independent appropriately qualified specialist at a minimum (e.g. an external auditor) must include the following steps:
Article 4: Valuation
- 1. A Bank must mark-to-market at least on a daily basis its market risk positions. The more prudent side of bid/offer must be used, unless the Bank is a significant market maker in a particular position type and it can close-out at mid-market. A Bank must maximize the use of relevant observable inputs and minimize the use of unobservable inputs when estimating fair value using a valuation technique. However, observable inputs or transactions may not be relevant, such as in a forced liquidation or distressed sale, or transactions may not be observable, such as when markets are inactive. In such cases, the observable data must be considered, but may not be determinative.
- 2. A Bank may use mark-to-model only where marking-to-market is not possible, but it must be able to demonstrate to the Central Bank that this approach is prudent. When marking-to-model, an extra degree of conservatism is appropriate. The Central Bank will consider the following in assessing whether a mark-to-model valuation is prudent:
- a. Senior Management must be aware of the elements of the trading book or of other fair-valued positions which are subject to mark-to-model and must understand the materiality of the uncertainty this creates in the reporting of the risk/performance of the business;
- b. Market inputs must be sourced, to the extent possible, which show satisfactory track record of the actual position held. The appropriateness of the market inputs for the particular position being valued must be reviewed regularly;
- c. Where available, generally accepted valuation methodologies for particular products must be used as far as possible;
- d. A Bank’s model must be based on appropriate assumptions which have been assessed and challenged by suitably qualified parties independent of the development process. This can take the form of a Technical Committee. The model must be developed or approved independently of the risk-taking functions and must be independently tested;
- e. There must be formal change control procedures in place and a secure copy of the model must be held and periodically used to check valuations;
- f. The independent risk management function must be aware of the weaknesses of the models used and how best to reflect those in the valuation output;
- g. The model must be subject to periodic review to determine the accuracy of its performance (e.g. assessing continued appropriateness of the assumptions, analysis of profit and loss versus risk factors, comparison of actual close out values to model outputs); and
- h. Valuation adjustments must be made as appropriate (for example, to cover the uncertainty of the model valuation).
- 3. As part of its procedures for marking-to-market, a Bank must establish and maintain procedures for considering valuation adjustments. A Bank using third-party valuations must consider whether valuation adjustments are necessary. Such considerations are also necessary when marking-to-model.
- 4. A Bank must, at a minimum, formally consider credit valuation adjustments, unearned credit spreads, close-out costs, operational risks, early termination, investing and funding costs, future administrative costs and, where appropriate, model risk.
- 5. The Board-approved polices must provide for independent verification of market prices or model inputs by a unit independent of the risk taking functions, at least monthly and depending on the nature of the market/trading activity, more frequently. Senior Management must take appropriate action to ensure the elimination of inaccurate daily marks.
- 6. Where pricing sources are more subjective, such as when only one available broker quote is provided, prudent measures, such as valuation adjustments must be taken as appropriate.
Back-Testing
- 7. The independent risk management function must conduct a regular back-testing program and profit and loss attribution program including but not limited to comparison of the risk measure and profit or loss values generated by the model against actual daily changes in portfolio value, as well as hypothetical changes based on static positions.
- 8. A Bank’s back-testing program must cover a minimum period of 250 business days.
- 9. A Bank’s back-testing program must include a formal evaluation of instances where trading outcomes are not covered by the risk measures (termed ‘exceptions’) on at least a quarterly basis, using the most recent twelve months modelled results and profit data. The Bank must document all exceptions generated from its ongoing back-testing program, including an explanation for the exceptions. A Bank must have the capacity to perform back-testing analysis both at the level of the whole portfolio and at the level of sub-portfolios or books that contain material risk.
- 10. A Bank must perform back-tests using both actual trading outcomes and hypothetical trading outcomes. Hypothetical trading outcomes are calculated by applying the day’s price movements to the previous day’s end-of-day portfolio. When performing back-tests using actual trading outcomes, a Bank must use clean trading outcomes, i.e. actual trading outcomes adjusted to remove the impact of income arising from factors other than market movements alone, such as fees and commissions, brokerage, additions to and releases from reserves which are not directly related to market risk (such as administration reserves).
Article 5: Capital
- 1. A Bank must calculate a capital charge for interest rate risk, options risk and equity positions in the trading book. Equity exposure, foreign exchange risk and commodity risk and options risk must be calculated on the Bank’s entire positions. Options risk must also be calculated for options on foreign exchange or commodities positions not belonging to the trading book. In addition, a Bank must take into account other relevant market risk exposures, including but not limited to interest rate risk in the Banking book, as part of the Internal Capital Adequacy Assessment Process to ensure that it holds adequate capital against all market risks.
Article 6: Stress Testing
- 1. A Bank must have a forward-looking stress-testing program that addresses market risks as well as other Pillar 1 risks and any relevant Pillar 2 risks. Consideration of market risks must include liquidity implications as well as impacts on earnings and capital.
- 2. A Bank’s stress scenarios must cover a range of market risk factors that can create extraordinary losses or gains in trading portfolios, or make the control of risk in those portfolios very difficult. Stress scenarios need to shed light on the impact of such events on positions that display both linear and nonlinear price characteristics (for instance options and instruments that have options-like characteristics).
- 3. A Bank’s stress tests must be both of a quantitative and qualitative nature, incorporating both market risk and liquidity aspects of market disturbances. Quantitative criteria must identify plausible stress scenarios to which a Bank could be exposed. Qualitative criteria must emphasize that the two major goals of stress testing are to evaluate the capacity of the Bank’s capital to absorb potential large losses and to identity steps the Bank can take to reduce its risk and conserve capital. This assessment is integral to setting and evaluating the Bank’s management strategy and the results of stress testing routinely must be communicated to Senior Management and periodically to the Board.
- 4. From time to time, the Central Bank may require Banks to carry out stress tests based on Central Bank prescribed scenarios. A Bank must combine the use of stress scenarios as prescribed by the Central Bank with internally developed stress tests to reflect the specific risk characteristics of its portfolio. A Bank must submit the following information on stress testing to the Central Bank:
- a. Supervisory scenarios requiring no simulations by a Bank: A Bank must make information on the largest losses experienced during the reporting period available to the Central Bank. This loss information must be compared to the level of capital that results from a Bank’s internal measurement system. For example, it could provide the Central Bank with a picture of how many days of peak day losses would have been covered by a given value-at-risk or expected shortfall estimate;
- b. Supervisory scenarios requiring simulations by a Bank: A Bank must subject its portfolios to a series of simulated stress scenarios and provide the Central Bank with the results. These scenarios could include testing the current portfolio against past periods of significant disturbance. A second type of scenario would evaluate the sensitivity of the Bank’s market risk exposure to changes in the assumptions about volatilities and correlations. Applying this test would require an evaluation of the historical range of variation for volatilities and correlations and evaluation of the Bank’s current positions against the extreme values of the historical range. Due consideration must be given to the sharp variation that at times has occurred in a matter of days in periods of significant market disturbance. (for example, the global financial crisis and earlier major market disturbances involved correlations within risk factors approaching the extreme values of 1 or −1 for several days at the height of the disturbance); and
- c. Scenarios developed by the Bank itself to capture the specific characteristics of its portfolio: A Bank must develop its own stress tests which it identifies as most adverse based on the characteristics of its portfolio (such as adverse regional developments combined with a sharp move in oil prices). The market shocks applied in the tests must reflect the nature of portfolios and the time it could take to hedge or manage risks under severe market conditions. The Bank must provide the Central Bank with a description of the methodology used to select and carry out the scenarios as well as with a description of the results derived from these scenarios. The stress tests must also address:
- i. Illiquidity/gapping of prices;
- ii. Concentrated positions (in relation to market turnover);
- iii. One-way markets;
- iv. Non-linear products/deep out-of-the-money positions;
- v. Events and jumps-to-defaults; and
- vi. Other risks that may not be captured appropriately in the models (in the case of VaR models for example, these may include but are not limited to: recovery rate uncertainty, implied correlations, skew risk, default risk, migration risks and shocks to the exchange rate regime).
- 5. Senior Management must review the stress test results periodically, but at least monthly and such results must be reflected in the policies and limits set by management and the Board. Stress test results must be used in the internal assessment of capital adequacy. The Bank must take prompt steps to manage vulnerabilities identified in stress testing, which can include but are not limited to hedging against identified outcomes, reducing the size of exposures or increasing capital.
Article 7: Reporting
- 1. A Bank must submit to the Central Bank on a quarterly basis the Report on Market Risk Exposures. A Bank must calculate the number of exceptions in back-tests using trading outcomes and provide this information to the Central Bank in such form and frequency as the Central Bank may specify.
Article 8: Islamic Banking
- 1. A Bank offering Islamic financial services must have in place an appropriate framework for market risk management, including reporting, in respect of all assets held, particularly those that do not have a ready market and/or are exposed to high price volatility.
- 2. A Bank offering Islamic financial services must develop a market risk strategy including the level of acceptable market risk appetite taking into account contractual agreements with fund providers, types of risk-taking activities and target markets in order to maximize returns while keeping exposures at or below the pre-determined levels. The strategy must be reviewed at least annually, communicated to relevant staff and disclosed to fund providers. The strategy must provide for guidelines governing risk-taking activities in different portfolios of restricted investment account holders and applicable market risk limits.
- 3. A Bank offering Islamic financial services must ensure that its strategy includes a definition of its risk appetite for tradable assets and that its risk appetite is adequately supported by capital held for that purpose.
- 4. A Bank offering Islamic financial services must be able to quantify market risk exposures and assess exposure to the probability of future losses in its net open asset positions. The Bank must incorporate a detailed approach to valuing its market risk positions where no direct market prices are available. This may include appropriate forecasting techniques to assess the potential value of these assets.
- 5. Where available valuation methodologies are deficient, a Bank offering Islamic financial services must assess the need to:
- a. allocate funds to cover risks resulting from illiquidity, new assets and uncertainty in assumptions underlying valuation and realization; and
- b. establish a contractual agreement with the counterparty specifying the methods to be used in valuing the assets.
- 6. A Bank offering Islamic financial services must apply the same risk management policies and procedures to assets held on behalf of restricted investment account holders as it does to assets held on behalf of shareholders and unrestricted investment account holders.
- 7. Where a Bank offering Islamic financial services plays the role of market maker to restricted investment account holders, the resultant liquidity risk must be managed appropriately.
Model Management Standards
Definitions and Interpretations
The following terms shall have the meaning assigned to them for the purpose of interpreting these Standards and the related Guidance:1. Board: As defined in the CBUAE’s Corporate Governance Regulation for Banks. 2. Causality (written in lower case as “causality”): Relationship between cause and effect. It is the influence of one event on the occurrence of another event. 3. CBUAE: Central Bank of the United Arab Emirates. 4.
Correlation (written in lower case as “correlation”): Any statistical relationship between two variables, without explicit causality explaining the observed joint behaviours. Several metrics exist to capture this relationship. Amongst others, linear correlations are often captured by the Pearson coefficient. Linear or non-linear correlation are often captured by the Spearman’s rank correlation coefficient. 5.
Correlation Analysis (written in lower case as “correlation analysis”): Correlation analysis refers to a process by which the relationships between variables are explored. For a given set of data and variables, observe (i) the statistical properties of each variable independently, (ii) the relationship between the dependent variable and each of the independent variables on a bilateral basis, and (iii) the relationship between the independent variables with each other. 6.
CI (Credit Index): In the context of credit modelling, a credit index is a quantity defined over (-∞,+∞) derived from observable default rates, for instance through probit transformation. CI represents a systemic driver of creditworthiness. While this index is synthetic, (an abstract driver), it is often assimilated to the creditworthiness of specific industry or geography. 7.
Default (written in lower case as “default”): The definition of default depends on the modelling context, either for the development of rating models or for the calibration and probabilities of default. For a comprehensive definition, refer to the section on rating models in the MMG. 8.
Deterministic Model (written in lower case as “deterministic model”): A deterministic model is a mathematical construction linking, with certainty, one or several dependent variables, to one or several independent variables. Deterministic models are different from statistical models. The concept of confidence interval does not apply to deterministic models. Examples of deterministic models include NPV models, financial cash flow models or exposure models for amortizing facilities. 9.
DMF (Data Management Framework): Set of policies, procedures and systems designed to organise and structure the management of data employed for modelling. 10.
DPD (Days-Past-Due): A payment is considered past due if it has not been made by its contractual due date. The days-past-due is the number of days that a payment is past its due date, i.e. the number of days for which a payment is late. 11.
DSIB (Domestic Systemically Important Banks): These are UAE banks deemed sufficiently large and interconnected to warrant the application of additional regulatory requirements. The identification of the institutions is based upon a framework defined by the CBUAE. 12.
EAD (Exposure At Default): Expected exposure of an institution towards an obligor (or a facility) upon a future default of this obligor (or its facility). It also refers to the observed exposure upon the realised default of an obligor (or a facility). This amount materialises at the default date and can be uncertain at reporting dates prior to the default date. The uncertainty surrounding EAD depends on the type of exposure and the possibility of future drawings. In the case of a lending facility with a pre-agreed amortisation schedule, the EAD is known. In the case of off-balance sheet exposures such as credit cards, guarantees, working capital facilities or derivatives, the EAD is not certain on the date of measurement and should be estimated with statistical models. 13. EAR (Earning At Risk): Refer to NII. 14.
ECL (Expected Credit Loss): Metric supporting the estimation of provisions under IFRS9 to cover credit risk arising from facilities and bonds in the banking book. It is designed as a probability-weighted expected loss. 15.
Economic Intuition (written in lower case as “economic intuition”): Also referred to as economic intuition and business sense. Property of a model and its output to be interpreted in terms and metrics that are commonly employed for business and risk decisions. It also refers to the property of the model variables and the model outputs to meet the intuition of experts and practitioners, in such a way that the model can be explained and used to support decision-making. 16.
Effective Challenge: Characteristic of a validation process. An effective model validation ensures that model defects are suitably identified, discussed and addressed in a timely fashion. Effectiveness is achieved via certain key features of the validation process such as independence, expertise, clear reporting and prompt action from the development team. 17.
EVE (Economic Value of Equity): It is defined as the difference between the present value of the institution’s assets minus the present value of liabilities. The EVE is sensitive to changes in interest rates. It is used in the measurement of interest rate risk in the banking book. 18.
Expert-Based Models (written in lower case as “expert-based models”): Also referred to as judgemental models, these models rely on the subjective judgement of expert individuals rather than on quantitative data. In particular, this type of model is used to issue subjective scores in order to rank corporate clients. 19.
Institutions (written in lower case as “institution(s)”): All banks licenced by the CBUAE. Entities that take deposits from individuals and/or corporations, while simultaneously issuing loans or capital market securities. 20.
LGD (Loss Given Default): Estimation of the potential loss incurred by a lending institution upon the default of an obligor (or a facility), measured as a percentage of the EAD. It also refers to the actual loss incurred upon past defaults also expressed as a percentage of EAD. The observed LGD levels tend to be related to PD levels with various strength of correlation. 21.
Limits and limitations (written in lower case as “limits” and “limitations”): Model limits are thresholds applied to a model’s outputs and/or its parameters in order to control its performance. Model limitations are boundary conditions beyond which the model ceases to be accurate. 22.
LSI (Large and/or Sophisticated Institutions): This group comprises DSIBs and any other institutions that are deemed large and/or with mature processes and skills. This categorisation is defined dynamically based on the outcome of regular banking supervision. 23.
Macroeconomic Model (written in lower case as “macroeconomic model” or “macro model”): Refers to two types of models. (i) A model that links a set of independent macro variables to another single dependent macro variable or to several other dependent macro variables or (ii) a model that links a set of independent macro variables to a risk metric (or a set of risk metrics) such as probabilities of default or any other business metric such as revenues. 24.
Market Data: Refers to the various data attributes of a traded financial instrument reported by a trading exchange. It includes the quoted value of the instrument and/or the quoted parameters of that instrument that allow the derivation of its value. It also includes transaction information including the volume exchanged and the bid-ask spread. 25.
Materiality: The materiality of a model represents the financial scope covered by the model in the context of a given institution. It can be used to estimate the potential loss arising from model uncertainty (see Model Risk). Model materiality can be captured by various metrics depending on model types. Typically, total exposure can be used as a metric for credit models. 26. MMG: CBUAE’s Model Management Guidance. 27. MMS: CBUAE’s Model Management Standards. 28.
Model (written in lower case as “model”): A quantitative method, system, or approach that applies statistical, economic, financial, or mathematical theories, techniques, and assumptions to process input data into quantitative estimates. For the purpose of the MMS and MSG, models are categorised in to three distinct groups: statistical models, deterministic models and expert-based models. 29.
Model Calibration (written in lower case as “model calibration”): Key step of the model development process. Model calibration means changing the values of the parameters and/or the weights of a model, without changing the structure of the model, i.e. without changing the nature of the variables and their transformations. 30.
Model Complexity (written in lower case as “model complexity”): Overall characteristic of a model reflecting the degree of ease (versus difficulty) with which one can understand the model conceptual framework, its practical design, calibration and usage. Amongst other things, such complexity is driven by, the number of inputs, the interactions between variables, the dependency with other models, the model mathematical concepts and their implementation. 31.
Model Construction (written in lower case as “model construction”): Key step of the model development process. The construction of a model depends on its nature, i.e. statistical or deterministic. For the purpose of the MMS and the MMG, model construction means the following: for statistical models, for a given methodology and a set of data and transformed variables, it means estimating and choosing, with a degree of confidence, the number and nature of the dependent variables along with their associated weights or coefficients. For deterministic models, for a given methodology, it means establishing the relationship between a set of input variables and an output variable, without statistical confidence intervals. 32.
Model Development (written in lower case as “model development”): Means creating a model by making a set of sequential and recursive decisions according to the steps outlined in the dedicated sections of the MMS. Model re-development means conducting the model development steps again with the intention to replace an existing model. The replacement may, or may not, occur upon re-development. 33.
Modelling Decision (written in lower case as “modelling decision”): A modelling decision is a deliberate choice that determines the core functionality and output of a model. Modelling decisions relate to each of the steps of the data acquisition, the development and the implementation phase. In particular, modelling decisions relate to (i) the choice of data, (ii) the analysis of data and sampling techniques, (iii) the methodology, (iv) the calibration and (v) the implementation of models. Some modelling decisions are more material than others. Key modelling decisions refer to decisions with strategic implications and/or with material consequences on the model outputs. 34.
Model Risk: Potential loss faced by institutions from making decisions based on inaccurate or erroneous outputs of models due to errors in the development, the implementation or the inappropriate usage of such models. Losses incurred from Model Risk should be understood in the broad sense as Model Risk has multiple sources. This definition includes direct quantifiable financial loss but also any adverse consequences on the ability of the institution to conduct its activities as originally intended, such as reputational damage, opportunity costs or underestimation of capital. In the context of the MMS and the MMG, Model Risk for a given model should be regarded as the combination of its materiality and the uncertainty surrounding its results. 35.
Model Selection (written in lower case as “model selection”): This step is part of the development process. This means choosing a specific model amongst a pool of available models, each with a different set of variables and parameters. 36.
Model Uncertainty (written in lower case as “model uncertainty”): This refers to the uncertainty surrounding the results generated by a model. Such uncertainty can be quantified as a confidence interval around the model output values. It is used as a component to estimate Model Risk. 37.
Multivariate Analysis (written in lower case as “multivariate analysis”): For a given set of data and variables, this is a process of observing the joint distribution of the dependent and independent variables together and drawing conclusions regarding their degree of correlation and causality. 38.
NII (Net Interest Income): To simplify notations, both Net Interest Income (for conventional products) and/or Net Profit Income (for Islamic Products) are referred to as “NII”. In this context, ‘profit’ is assimilated as interest. It is defined as the difference between total interest income and total interest expense, over a specific time horizon and taking into account hedging. The change in NII (“?NII”) is defined as the difference between the NII estimated with stressed interest rates under various scenarios, minus the NII estimated with the interest rates as of the portfolio reporting date. ?NII is also referred to as earnings at risk (“EAR”). 39.
NPV (Net Present Value): Present value of future cash flows minus the initial investment, i.e. the amount that a rational investor is willing to pay today in exchange for receiving these cash flows in the future. NPV is estimated through a discounting method. It is commonly used to estimate various metrics for the purpose of financial accounting, risk management and business decisions. 40.
PD (Probability of Default): Probability that an obligor fails to meet its contractual obligation under the terms of an agreed financing contract. Such probability is computed over a given horizon, typically 12 months, in which case it is referred to as a 1-year PD. It can also be computed over longer horizons. This probability can also be defined at several levels of granularity, including, but not limited to, single facility, pool of facilities, obligor, or consolidated group level. 41.
PD Model (written as “PD model”): This terminology refers to a wide variety of models with several objectives. Amongst other things, these models include mapping methods from scores generated by rating models onto probability of defaults. They also include models employed to estimate the PD or the PD term structure of facilities, clients or pool of clients. 42.
PD Term Structure (written as “PD term structure”): Refers to the probability of default over several time horizons, for instance 2 years, 5 years or 10 years. A distinction is made between the cumulative PD and the marginal PD. The cumulative PD is the total probability of default of the obligor over a given horizon. The marginal PD is the probability of default between two dates in the future, provided that the obligor has survived until the first date. 43.
PIT (Point-In-Time) and TTC (Through-The-Cycle): A point-in-time assessment refers to the value of a metric (typically PD or LGD) that incorporates the current economic conditions. This contrasts with a through-the-cycle assessment that refers to the value of the same metric across a period covering one or several economic cycles. 44.
Qualitative validation: A review of model conceptual soundness, design, documentation, and development and implementation process. 45.
Quantitative validation: A review of model numerical output, covering at least its accuracy, degree of conservatism, stability, robustness and sensitivity. 46.
Rating / Scoring (written in lower case “rating or scoring”): For the purpose of the MMS and the MMG, a rating and a score are considered as the same concept, i.e. an ordinal quantity representing the relative creditworthiness of an obligor (or a facility) on a predefined scale. ‘Ratings’ are commonly used in the context of corporate assessments whilst ‘scores’ are used for retail client assessments. 47.
Restructuring (written in lower case “restructuring”): The definition of restructuring / rescheduling used for modelling in the context of the MMS and MMG should be understood as the definition provided in the dedicated CBUAE regulation and, in particular, in the Circular 28/2010 on the classification of loans, with subsequent amendments to this Circular and any new CBUAE regulation on this topic. 48.
Rating Model (written in lower case “rating model”): The objective of such model is to discriminate ex-ante between performing clients and potentially non-performing clients. Such models generally produce a score along an arbitrary scale reflecting client creditworthiness. This score can subsequently mapped to a probability of default. However, rating models should not be confused with PD models. 49.
Retail Clients (written in lower case as “retail clients”): Retail clients refer to individuals to whom credit facilities are granted for the following purpose: personal consumer credit facilities, auto credit facilities, overdraft and credit cards, refinanced government housing credit facilities, other housing credit facilities, credit facilities against shares to individuals. It also includes small business credit facilities for which the credit risk is managed using similar methods as applied for personal credit facilities. 50.
Segment (written in lower case as “segment”): Subsets of an institution’s portfolio obtained by splitting the portfolio by the most relevant dimensions which explain its risk profile. Typical dimensions include obligor size, industries, geographies, ratings, product types, tenor and currency of exposure. Segmentation choices are key drivers of modelling accuracy and robustness. 51. Senior Management: As defined in the CBUAE’s Corporate Governance Regulation for Banks. 52.
Statistical Model (written in lower case as “statistical model”): A statistical model is a mathematical construction achieved by the application of statistical techniques to samples of data. The model links one or several dependent variables to one or several independent variables. The objective of such a model is to predict, with a confidence interval, the values of the dependent variables given certain values of the independent variables. Examples of statistical models include rating models or value-at-risk (VaR) models. Statistical models are different from deterministic models. By construction, statistical models always include a degree of Model Risk. 53. Tiers: Models are allocated to different groups, or Tiers, depending on their associated Model Risk. 54.
Time series analysis (written in lower case as “time series analysis”): For a given set of data and variables, this is a process of observing the behaviour of these variables through time. This can be done by considering each variable individually or by considering the joint pattern of the variables together. 55.
UAT (User Acceptance Testing): Phase of the implementation process during which users rigorously test the functionalities, robustness, accuracy and reliability of a system containing a new model before releasing it into production. 56.
Variable Transformation (written in lower case as “variable transformation”): Step of the modelling process involving a transformation of the model inputs before developing a model. Amongst others, common transformations include (i) relative or absolute differencing between variables, (ii) logarithmic scaling, (iii) relative or absolute time change, (iv) ranking, (v) lagging, and (vi) logistic or probit transformation. 57.
Wholesale Clients (written in lower case as “wholesale clients”): Wholesale clients refer to any client that is not considered as a retail client as per the definition of these Standards.
Introduction
1 Context and Objectives
1.1 Regulatory Context
1.1.1
The Risk Management Regulation (Circular No. 153/2018) issued by the Central Bank of the UAE (“CBUAE”) on 27th May 2018, states that banks must have robust systems and tools to assess and measure risks. In particular, when models are used, they must be managed appropriately to support decision-making.
(i)
Article 2.1: “A bank must have an appropriate risk governance framework that provides a bank-wide view of all material risks. This includes policies, processes, procedures, systems and controls to identify, measure, evaluate, monitor, report and control or mitigate material sources of risk on a timely basis (…).” (ii)
Article 4.1: “A bank must have systems to measure and monitor risks which are commensurate with the risk profile, nature, size and complexity of its business and structure.” (iii)
Article 4.3: “Where a Bank uses models to measure components of risks, it must have appropriate internal processes for the development and approval for use of such models and must perform regular and independent validation and testing of the models (…).”
1.1.2
Consequently, the Model Management Standards (“MMS”) present modelling practices that must be implemented by banks in the UAE, if they decide to employ models for decision-making. These standards are based upon practices deemed appropriate within the financial industry internationally with consideration of local circumstances. The MMS therefore represent the minimum requirements to be met within the UAE.
1.2 Objectives
1.2.1
Models are an integral part of decision-making within UAE banks for risk management, business decisions and accounting. Banks employ models to comply with several regulatory and accounting requirements, including, but not limited to: (i) IFRS9 accounting requirements, (ii) capital forecasting, (iii) Pillar II capital assessment, (iv) regulatory stress testing requirements, (v) risk management of capital market activities and (vi) valuation adjustments. In addition, banks employ models to manage their business effectively, for instance with pricing models, portfolio management models and budgeting models.
1.2.2
When using models to support decisions, banks are exposed to potential losses occurring from making decisions based on inappropriate models or the incorrect usage of models. This potential loss and the associated adverse consequences are referred to as Model Risk. Further details are provided in the definition section.
1.2.3
In light of this large and complex landscape, the MMS has three key objectives. The first objective is to ensure that models employed by UAE banks meet quality standards to adequately support decision-making and reduce Model Risk. The second objective is to improve the homogeneity of model management across UAE banks. The third objective is to mitigate the risk of potential underestimation of provisions and capital across UAE banks.
1.3 Document Structure
1.3.1
The MMS are accompanied by the Model Management Guidance (“MMG”), which expands on technical aspects by model type. Both the MMS and MMG should be read jointly as they constitute a consistent set of requirements and guidance, as follows:
(i)
Part I of the MMS outlines general standards applicable to all models. They represent the key components of the Model Management Standards. (ii)
Part II of the MMS outlines specific requirements for the application of the standards. Both Part I and Part II constitute the minimum requirements to be met by a model and its management process so that the model can be used effectively for decision-making. (iii)
The MMG expands on technical aspects that are expected to be implemented by UAE banks for certain types of models. Given the wide range of models and the complexity of some models, the CBUAE recognises that alternative approaches can be envisaged on specific technical points. However, deviations from the MMG should be clearly justified and will be subject to CBUAE supervisory review.
1.3.2
The MMS is constructed in such a way that all points are mentioned sequentially and each point is a unique reference across the entire MMS. Throughout the document, the requirements associated with ‘must’ are mandatory, while those associated with ‘should’ are strongly recommended as they are regarded as robust modelling practice. The articles of the MMG are all articulated with ‘should’.
1.3.3
Both the MMS and the MMG contain an appendix summarising the main numerical limits included throughout each document, respectively. The summary is expected to ease the implementation and monitoring of these limits by institutions and the CBUAE.
2 Implementation
2.1 Scope of Application
2.1.1
The MMS and the MMG apply to all licensed banks in the UAE, which are referred to herein as “institutions”. This scope covers Islamic institutions.
2.1.2
All institutions must ensure that their models meet minimum quality standards. Simple models must not be confused with poorly designed models. Poorly designed models can be misleading and interfere with sound decision-making. Consequently, the MMS and the MMG apply to all institutions irrespective of their size or sophistication. Small and/or unsophisticated institutions can employ simple models that are properly designed.
2.1.3
At a minimum, UAE branches or subsidiaries of foreign institutions must apply the MMS and the MMG. Where certain elements of the requirements of the parent company’s regulator are more stringent, then these requirements should be implemented. The degree of conservatism must be assessed for each model individually and the associated calibration. The compliance of the UAE branch or subsidiary with the MMS / MSG may require the operational support of their parent company.
2.1.4
An institution that is a parent company incorporated in the UAE must ensure that all its branches and subsidiaries, that are also institutions, comply with the MMS and the MMG.
2.2 Requirements and Implementation Timeframe
2.2.1
The MMS and the MMG will be effective one day after their publication date.
2.2.2
All institutions are expected to identify gaps between their practice and the MMS and MMG and, if necessary, establish a remediation plan to reach compliance. The outcome of this self-assessment and the plan to meet the requirements of the MMS and the MMG must be submitted to the CBUAE no later than six (6) months from the effective date of the MMS.
2.2.3
Institutions must work towards compliance in a proactive manner. They must demonstrate continuous improvements towards meeting these requirements within a reasonable timeframe. This timeframe will be approved by the CBUAE following a review of the self-assessments. The CBUAE will take a proportionate view in its assessment of the proposed time to reach compliance, taking into consideration the size and complexity of each institution. The remediation plan and the associated timing must be detailed, transparent, and justified. The plan must address each gap at a suitable level of granularity.
2.2.4
Institutions, which repeatedly fall short of the requirements and/or do not demonstrate continuous improvement, will face greater scrutiny and could be subject to formal enforcement action by the CBUAE. In particular, continuously structurally deficient models must be replaced and must not be used for decision-making and reporting.
2.2.5
The path to remediation may involve reducing the number and/or complexity of models in order to improve the quality of the remaining models. Subsequently, and subject to remediation needs, the institution could increase the number of models and/or their complexity while maintaining their quality.
2.2.6
Institutions must achieve and maintain full compliance with respect to the general principles described in Part I and Part II of the MMS. For the MMG, whilst alternative approaches can be considered, the focus is on the rationale and the thought process behind modelling choices. Institutions must avoid material inconsistencies, cherry-picking, reverse-engineering and positive bias, i.e. modelling approaches that deliberately favour a desired outcome. Evidence of an institution defying the general principles in this way will warrant a supervisory response ranging from in-depth scrutiny to formal enforcement action.
2.2.7
For statistical models in particular, institutions must focus on the suitability of their calibration, whether these models are relying on internal data or external data. Lack of data will not be an acceptable reason for material models to fall short of these requirements. Instead, institutions must implement temporary solutions to mitigate Model Risk until models based on more robust data sets are implemented. Institutions must avoid excessive and unreasonable generalisations to compensate for lack of data.
2.3 Reporting to the CBUAE
2.3.1
Once a plan to reach full compliance is decided and approved, institutions must report their remediation progress to the CBUAE at regular intervals, as agreed upon with the CBUAE. The CBUAE expects continued and iterative dialogue on this matter during the implementation of the plan and thereafter as modelling requirements evolve.
2.3.2
From the effective date of the MMS, institutions must comply with all CBUAE reporting requirements related to model management. The nature, depth and scope of this reporting may evolve with modelling techniques and economic conditions.
2.4 Scope of Models
2.4.1
The MMS applies to all types of models employed by institutions to support decision-making. Therefore it covers, amongst others, risk models, pricing models and valuation models. The scope of the MMS includes, at a minimum, the non-exhaustive list in Table 1 below, that represents the most commonly employed model types in UAE institutions.
Table 1: List of most commonly employed model types in UAE institutions
Field Model Type Field Model Type Credit risk Rating and scorecard models Stress Testing (ST) Credit risk ST Score-to-PD models Market risk ST LGD models Counterparty risk ST Provision computation for credit ris PIT PD term structure models Liquidity risk ST PIT LGD models Other types of ST models PIT EAD models Operational risk Ops risk scorecards ECL models Ops risk capital models Macro models Pricing and finance Derivative pricing models Market risk VaR and related models Bond pricing models Valuation models RAROC models Counterparty risk Exposure models NPV models xVA models Asset and Liability Management EVE models Capital management Capital forecasting models EAR and NII models Concentration models Liquidity risk models Funding cost models Business management Artificial Intelligence Economic capital models Budgeting, forecasting AML Fraud alert and other models Marketing models Part I – General Standards
The MMS is constructed in such a way that the numbering of each article is sequential and each article is a unique reference across the entire MMS. Therefore the numbering continues from the previous Part.
3 General Standards
This Part outlines the general principles of the MMS, that is, the key components of the Standards. Part I must be read in conjunction with Part II, which explains how these principles must be applied. Both Part I and Part II must be regarded as minimum requirements. The key components of model management are as follows: (i) model governance, (ii) data management, (iii) model development, (iv) model implementation, (v) model usage, (vi) performance monitoring and (vii) independent validation. The timeframes and minimum frequencies of model review are addressed in Part II.
3.1 Model Governance
3.1.1
Model governance must reinforce the continuous improvement of modelling practices in order for institutions to comply with the requirements of the MMS. Institutions must establish a clear plan to comply.
3.1.2
Institutions must define a comprehensive model management framework to ensure that models are used effectively for decision-making and that Model Risk is appropriately understood and mitigated. The scope of the model governance must cover all models used to make decisions within the institution.
3.1.3
Model Risk must be incorporated in institutions’ risk framework alongside other key risks faced by institutions, as inherent consequences of conducting their activities. Consequently, Model Risk must be managed through a formal process incorporating the institution’s appetite for model uncertainty. The framework must be designed to identify, measure, monitor, report and mitigate this risk. A large appetite for Model Risk should be mitigated by counter-measures such as conservative buffers on model results, additional provisions and/or potentially a Pillar II capital add-on.
3.1.4
The model management framework must be structured around key components to be effective. First, the responsibilities of the stakeholders must be clearly defined with a transparent process for modelling decisions, oversight, escalation and for managing relationships with third parties. Second, a limit framework must be established to control and mitigate Model Risk. Third, the nature, objective and priorities of the modelling tasks must be defined. Fourth, appropriate systems, tools and data must be established to support model management. Fifth, the framework must include a granular reporting process to support pro-active management of Model Risk.
3.1.5
Institutions must manage each model according to a defined life-cycle composed of specific steps, from model design to re-development. The roles and responsibilities of stakeholders must be defined for each step of the life cycle. To facilitate model management and prioritisation, models must be grouped according to their associated Model Risk, or at least based on their associated materiality, as defined in the MMS.
3.1.6
Institutions must establish a Model Oversight Committee which must be accountable for all significant modelling decisions related to each step of the model life-cycle. The committee must ensure that these decisions are transparent, justified and documented. The committee’s main objective is to optimise the ability of models to support decision-making throughout the institution, covering all model types. The Model Oversight Committee is accountable to Senior Management and to the Board, who must ensure that the Model Oversight Committee manages Model Risk appropriately and meets the requirements articulated in the MMS.
3.1.7
The Chief Risk Officer (“CRO”) must ensure that the design and usage of models is appropriate to support decision-making throughout the institution, in order to minimise Model Risk. Therefore, the scope of the CRO’s responsibility in this matter must cover the whole institution and must not be limited to the risk function. The CRO must ensure that Model Risk is fully managed with suitable identification, measurement, monitoring, reporting and mitigation.
3.1.8
In accordance with Article 2.2 of the Risk Management Regulation 153/2018, the Board bears the responsibility for the suitability of the risk management framework. In addition, Article 4.3 states that the Board is ultimately accountable for the appropriate usage and management of models, whether the approval for the use of models is provided directly by the Board or through authorities delegated to Senior Management. Consequently:
(i)
The Board bears the responsibility of all modelling decisions with material implications for the institution and it must define the appetite of the institution for Model Risk. Consequently, the Model Oversight Committee must refer decisions with material consequences to the Board (or the Board Risk Committee). If a Board decision is not deemed necessary, the Board (or the Board Risk Committee) must nonetheless be informed of key decisions taken by the Model Oversight Committee, with appropriate rationale. (ii)
To support the appropriate management of models, the Board must ensure that institutions have a sufficient number of internal employees with robust technical expertise. The Board must also ensure that Senior Management possess an adequate level of technical knowledge to form a judgement on the suitability of material modelling decisions.
3.1.9
The internal audit function is also a stakeholder in model governance. It must assess the regulatory compliance and the overall effectiveness of the model management framework as part of its regular auditing process. For this purpose, the internal audit function must be familiar with the requirements articulated in the MMS and review the model management framework against these requirements. The internal audit function must not be involved in the validation of specific models.
3.1.10
Institutions can use third parties to support the design, implementation and management of models. However, institutions must take responsibility for all modelling decisions, model outputs and related financial consequences, even if third parties are involved.
3.1.11
To achieve and maintain the quality of models, institutions must ensure that a sufficient number of internal technical resources are hired, trained and retained. Each institutions’ designated human resource function is responsible for supporting this requirement, operationally and strategically.
3.1.12
One of the key elements to manage Model Risk is a robust process for model review and challenge. Such review must be independent to be effective. Consequently, institutions must clearly define the roles and responsibilities of the development and the validation teams to ensure this independence. The validation team must communicate its findings to Senior Management and the Board on a yearly basis. The management and reporting of Model Risk must also be independent from the development teams.
3.1.13
Dedicated and consistent documentation must be produced for each step of the model life-cycle. Institutions must therefore develop model documentation standards. The documentation must be sufficiently comprehensive to ensure that any independent party has all the necessary information to assess the suitability of the modelling decisions.
3.1.14
The management of models must be supported by a comprehensive reporting framework reviewed and analysed at several levels of the organisation, from the development and validation teams, up to the Board. This reporting must be designed to support the management of Model Risk, covering the identification, measurement, monitoring and mitigation of this risk. Reporting must be clear, comprehensive, specific and actionable.
3.2 Data Management
3.2.1
Accurate and representative historical data is the backbone of financial models. Institutions must implement a rigorous and formal data management framework (“DMF”) to support the development and validation of accurate models.
3.2.2
The management of data sets used for modelling should not be confused with the management of data used for the production of regular risk analysis and reporting. While these two data sets may overlap, they are governed by two different processes and priorities. The construction of data for modelling focuses on consistency through long time periods, while risk analysis and reporting relies more on point-in-time data. In addition, numerous data points needed for modelling are often not included in the scope of reporting.
3.2.3
The DMF must be constructed to fully support each step of the model life-cycle process. The DMF must not be the responsibility of the model development or validation teams. The DMF must be organised by a separate dedicated function / team within the institution, with its dedicated set of policies and procedures.
3.2.4
The DMF must be comprehensive to adequately support the scope of models employed by the institution. It must be coherent with the breadth and depth of models used in production. In particular, sophisticated models with numerous parameters and complex calibration requirements must be supported by an equally sophisticated DMF.
3.2.5
At a minimum, the DMF must include the following components: (i) systematic identification of sources, (ii) regular and frequent collection, (iii) rigorous data quality review and control, (iv) secure storage and controlled access and (v) robust system infrastructure.
3.2.6
The data quality review is a key component of the DMF. It must incorporate standard checks to assess the data completeness, accuracy, timeliness, uniqueness and traceability.
3.3 Model Development
3.3.1
The development process must support the construction of the most appropriate models in order to meet the objectives assigned to these models.
3.3.2
The development process must be structured with sequential logical steps that take into consideration multiple factors, including but not limited to, the business and economic context, the data available, the development techniques, the implementation options and the future usage. Consequently, institutions are expected to employ judgement and critical thinking in the execution of this process, rather than run it in a mechanistic fashion.
3.3.3
Model development requires human judgement at each step of the process to ensure that the assumptions, design and data meet the objective of the model. Judgement is also required to ensure that development methodology is adequate, given the data available. Therefore, institutions must identify where judgment is needed in the development process. Suitable governance must be implemented to support a balanced and controlled usage of human judgement.
3.3.4
Each of these components must be regarded as an essential part to complete the whole process because each step involves key modelling decisions that can materially impact the model outcome and the financial decisions that follow. The process must be iterative. This means that if one step is not satisfactory, some prior steps must be repeated.
3.3.5
The development process must incorporate a degree of conservatism to mitigate Model Risk. Any material degree of uncertainty associated with the development steps, in particular related to data, must be compensated by conservative choices. For instance, conservatism can be reflected during the model selection process or by the usage of buffers at any point during the development process. However, conservatism should not be employed to hide defects and deprioritise remediation. When conservatism is applied, institutions must justify the reasons for it, identify the uncertainty being addressed and define the conditions for model improvement.
3.3.6
The choice of methodology for model development must be the result of a concerted structured process. This choice should be made upon comparing several options derived from common industry practice and/or relevant academic literature. Methodologies must be consistent across the organisation, transparent and manageable.
3.3.7
Institutions must pay particular attention to the model selection process for all types of models. When several models are available, institutions must put in place a documented process to select a model amongst several available options.
3.3.8
The pre-implementation validation must be considered an integral part of the development process. This step must ensure that the model is consistent, fit for purpose and generates results that can be explained and support decision-making appropriately. The depth of the pre-implementation validation should be defined based on model materiality.
3.4 Model Implementation
3.4.1
Institutions must consider model implementation as a separate phase of the model life-cycle process, with its own set of principles.
3.4.2
The implementation of a model must be treated as a project with clear governance, planning, funding and timing. It must include comprehensive user acceptance testing with record keeping and associated documentation. Upon request, these records shall be made available to the CBUAE, other regulators and auditors to assess whether a particular model has been implemented successfully.
3.4.3
The system infrastructure supporting the ongoing usage of models must be carefully designed and assessed before the model implementation phase, to adequately address the needs of model usage. It must cope with the demand of the model sophistication and the volume of regular production.
3.4.4
After the model implementation, institutions must regularly assess the suitability of their system infrastructure for their current and future usage of models. This assessment must be made in light of (i) evolving model design and methodologies, (ii) rapid technology developments and (iii) growing volume of transactions to be processed.
3.4.5
Institutions should avoid spreadsheets for the implementation of large and complex models. Where this is unavoidable, and preferably on a temporary basis, institutions must implement rules and rigorous validation to mitigate the risks posed by spreadsheet tools which are highly susceptible to operational errors. Institutions must implement internal policies and guidelines for the development of spreadsheet tools used in production.
3.5 Model Usage
3.5.1
The conditions for using models must be defined, monitored and managed. Model usage must be treated as an integral part of model management because the appropriate usage of a model is independent from the quality of such model.
3.5.2
Institutions must develop policies to manage model usage. At a minimum, the following must be included: (i) the definition of the expected usage, (ii) the process to control this usage, (iii) the governance surrounding the override of model inputs and outputs, and (iv) the management of user feedback.
3.5.3
Institutions must pay particular attention to circumstances under which model results are overridden. They must establish a clear, approved and controlled policy to govern overrides. This requirement is applicable to all models.
3.6 Model Performance Monitoring
3.6.1
Institutions must implement a process to and monitor the performance of their models on a regular basis, as part of their model life-cycle management. The monitoring frequency must depend on model types. The required minimum frequencies are set in Part II of the MMS.
3.6.2
Prior to engaging in performance monitoring, institutions must ensure that models are used appropriately. This means that the analysis of model usage must have been completed successfully.
3.6.3
The objective of performance monitoring is to assess whether exogenous changes in the economic and business environment have impacted the assumptions of the model and therefore its performance. The monitoring process must be organised with specific responsibilities, monitoring metrics, limits associated with these metrics and required reporting for each model and/or model type. The process must incorporate a clear decision-making and escalation mechanism.
3.6.4
The responsibility for the execution of model monitoring must be clearly defined. This can be assigned to the development team, the validation team or any independent third party. If model monitoring is not performed by the validation team, then the validation team must review the quality and relevance of the monitoring reports during the validation cycle. Monitoring reports must be presented to the Model Oversight Committee on a regular basis, at least every quarter.
3.6.5
Metrics and limits must be designed to appropriately track the performance of each model based on its specific characteristics and its implementation.
3.6.6
Monitoring reports must be comprehensive, transparent and contain explanations regarding the nature of metrics, their acceptable range and respective interpretation. These reports must be designed in such way that non-technical readers can understand the implications of the observations. Each monitoring report must contain an explicit conclusion on the model performance. The report should also include suggestions for defect remediation, when deemed appropriate.
3.6.7
Upon the production of monitoring reports, a clear process must be followed to decide whether to either continue using a model (with further monitoring) or suspend it and work on remediation. This decision must be made by the Model Oversight Committee.
3.6.8
The monitoring process is a key preceding step towards the validation process. The results of the monitoring process must be used as inputs to the validation process (when available), if the monitoring reports are deemed of sufficient quality and relevance by the validator.
3.7 Independent Validation
3.7.1
The independent validation must be established as a key step of the model lifecycle management and is the basis upon which Model Risk can be assessed and managed. Institutions must implement a process to validate independently all their models on a regular basis based on model types, as part of their model life-cycle management. Minimum frequencies are mentioned in Part II of the MMS.
3.7.2
In the context of model management, the model owner acts as the first line of defence, the independent validator acts as a the second line of defence and the internal audit function acts as the third line of defence.
3.7.3
The validation process must be organised with specific responsibilities, metrics, limits and reporting requirements for each model type. The validation process must be constructed to ensure an effective identification and remediation of model defects to manage Model Risk appropriately. This is referred to as the Effective Challenge principle.
3.7.4
Model validation can be performed either by an internal independent team or by a third party. In all cases, the validation process must remain independent from the development process. If model validation is assigned to a third party, institutions remain the owners of validation reports and remain responsible for taking appropriate actions upon the issuance of these reports. If the institution has an internal validation team and also uses third party validators, the internal validation team must maintain oversight of all validation exercises conducted by third parties. If the institution does not have an internal validation team, all validation reports produced by third parties should be owned by an appropriate internal control function separate from the model owner.
3.7.5
The validation must be independent by virtue of excluding the development team from involvement in the assessment of the model. The development team may be involved in the validation process once a set of observations has been produced, in particular for the remediation of these observations. Institutions must be able to demonstrate to the Central Bank, the appropriate arm’s length independence of the validator. Consequently, if a third party provides a methodology to develop a model for an institution, any subsequent validation exercise must be performed by a party different from the original provider. Validation teams must not report to the business lines.
3.7.6
The validation team must possess sufficient technical skills and maturity to formally express its opinion without the interference of the development team or from the business lines. The business lines may be consulted during the validation process, but the conclusion of such process must be formed independently from business line interests.
3.7.7
The validation scope must cover both a qualitative validation and a quantitative validation. A qualitative validation alone is not sufficient to be considered as a complete validation. If insufficient data is available to perform the quantitative validation of a model, the validation process must be flagged as incomplete and the institution must recognise and account for the uncertainty and thus the Model Risk related to such model.
3.7.8
A validation exercise must result in a full articulated judgement regarding the suitability of the model to support decision-making. The analyses and tests performed during the validation of a model must be rigorously documented in a validation report, such that (i) management is able to form a view on the performance of the model, and (ii) an independent party is able to repeat the process on the basis of the report.
3.7.9
Institutions must put in place an effective process to manage and remedy findings arising from validation exercises. Observations and findings across all models must be documented, recorded, tracked and reported to Senior Management and the Board at least once a year. Findings must be classified into groups based on their associated severity, in order to drive the prioritisation of remediation.
3.7.10
Institutions must ensure that model defects are understood and remedied within an appropriate time-frame. They must implement an effective process to prioritise and address model defects based on their materiality and/or associated Model Risk. High severity findings must be remedied promptly. If necessary, such remediation may rely on temporary adjustments and/or manual override. Such adjustments and overrides must not become regular practice, in that they must have an expiry horizon and must be coupled with a plan to implement more robust remediation. Further requirements and minimum remediation timings are mentioned in Part II.
3.7.11
Models employed by institutions must be fit for purpose to support decision-making. Therefore, institutions must aim to resolve all model defects associated with high and medium severity and aim to minimise the number of defects with low severity. If an institution decides not to address some model defects, it must identify, assess and report the associated Model Risk to Senior Management and the Board. Such decision may result in additional provisions and/or capital buffers and will be subject to review by the CBUAE.
3.7.12
The internal audit function is responsible for verifying that the model validation process is performed appropriately and meets the MMS requirements. This review must be planned as part of regular audit cycles. The audit team must comment on the degree of independence of the internal validation process. For technical matters, the audit team may decide to be assisted by third party experts. Where third party assistance is utilised, the internal audit function remains the sole owner of the conclusions of the audit report.
Part II – Application of the Standards
The MMS is constructed in such a way that the numbering of each article is sequential and each article is a unique reference across the entire MMS. Therefore the numbering continues from the previous Part.
4 Model Governance
4.1 Overview
4.1.1
Institutions must develop and maintain policies and procedures that support their model management framework. In addition, they must regularly ensure that these policies and procedures are correctly implemented.
4.1.2
In addition to the elements mentioned in Part I, institutions must include the following components in their model governance framework, at a minimum: (i) the definition of model objectives, (ii) steps of model life-cycle, (iii) model inventory, (iv) model ownership, (v) identification of key stakeholders involved in decision-making, (vi) relations with third parties, (vii) adequacy of internal skills, (viii) comprehensive model documentation, and (ix) reporting.
4.2 Model Objectives and Strategy
4.2.1
Institutions must assign a clearly defined objective to each model and include it in the model development documentation.
4.2.2
If stakeholders disagree on the objective of a model, the model must remain under development or be removed from production until the disagreement is resolved.
4.2.3
Institutions must have a defined strategy to meet the objectives of their models. Institutions must distinguish between short term tactical solutions from longer term solutions. Such strategies must be documented and approved by the stakeholders involved in model management, including Senior Management and the Board.
4.2.4
The modelling strategy must clearly articulate the potential contribution of third party consultants to the development, management and validation of models. The outsourcing strategy must be defined and justified, in particular regarding data, systems, calibration and methodology design. If a quantity of portion of modelling work is outsourced, institutions must implement mechanisms to retain controls control over the key elements of modelling.
4.3 Model Life-Cycle
4.3.1
Institutions must manage each model according to a cycle that includes, at a minimum, the following steps.
(i) Development, (ii) Pre-implementation validation, (iii) Implementation, (iv) Usage and monitoring, (v) Independent validation, and (vi)
Recalibration, redevelopment or retirement, if deemed necessary.
4.3.2
The duration and frequency of each step must be specified in advance for each model and documented accordingly.
4.3.3
Upon independent validation and the response from the development team, the following decisions must be considered by the Model Oversight Committee, which must all be thoroughly justified:
(i) Leave the model unchanged, (ii) Use a temporary adjustment while establishing a remediation plan, (iii) Recalibrate the model, (iv) Redevelop or acquire a new model, or (v)
Withdraw the model without further redevelopment.
4.4 Model Inventory and Grouping
4.4.1
Institutions must maintain a comprehensive inventory of all their models employed in production to support decision-making. The inventory must cover internal models and models provided by third parties. It must contain sufficient relevant information to support model management and mitigate Model Risk.
4.4.2
The inventory must cover models both currently in use and employed in the past for production (starting from the implementation of this MMS). Institutions must ensure that they can refer and/or roll back to previously employed models, if necessary. Consequently, institutions must have a model archiving mechanism in place supported by appropriate documentation and IT system infrastructure.
4.4.3
Each model must have a unique nomenclature and identification number that must be explicitly mentioned in any related model documentation. A model with a new calibration must carry a different identification number. Any variation of a model requiring a separate validation or approval should be identified as a separate model.
4.4.4
The model inventory must include, for each model, all the references and documents pertaining to each step of the life-cycle. Amongst others: (i) the dates of each step, including past and planned steps, (ii) the internal party responsible for each step, and (iii) previous validation exercises and audit reviews plus any reference to their respective outcome. Third-party consultants must not be considered as responsible for any step but only considered as supporting their execution. Where consultants have been involved, the details of the consultants must be recorded.
4.4.5
Models must be grouped based on their associated Model Risk.
(i)
At a minimum, institutions must create two groups referred to as Tier 1 and Tier 2 models, with Tier 1 models being more critical than Tier 2 models. If institutions already employ more than two groups, those can be retained for internal purpose. In the context of the MMS and for regulatory purpose, the models deemed less material than Tier 2, must be regarded Tier 2. (ii)
Whilst the grouping decisions are left to the discretion of each institution, they will be reviewed by the CBUAE as part of its supervisory duty. At a minimum, IFRS9 models for large portfolios (measured by exposure) and capital forecasting models must be classified as Tier 1. (iii)
Institutions may prioritise model management by tier once they have established a clear grouping framework based on Model Risk. In the MMS, in the absence of specific reference to model tiers, the requirements apply to all models irrespective of their materiality, as these requirements must be regarded as fundamental building blocks of model management. Where needed, the MMS explicitly refers to model Tier 1 and Tier 2.
4.5 Model Ownership
4.5.1
The concept of model ownership is fundamental to model management. Institutions must ensure that an internal owner with a sufficient level of seniority is assigned to each model at all times.
4.5.2
The owner of a model is accountable for all modelling decisions and for ensuring that the model goes through all the steps of its life-cycle in a timely fashion. In other words, a model owner is not responsible for executing all the steps; however, a model owner must ensure that the steps are performed.
4.5.3
Risk models involving statistical calibration must be owned by the risk department and must not be owned by the business lines to avoid conflicts of interest. Pricing and valuation models used for commercial decisions can be owned by the business lines. Other financial models with no statistical calibration can be owned by the finance department, at the discretion of each institution.
4.6 Stakeholders and Decision Process
4.6.1
A modelling decision is defined as a deliberate choice that relates to each step of the model life-cycle. In particular, key modelling decisions relate to (i) the model strategy, (ii) the choice of data, (iii) the analysis of data, (iv) the methodology and the development process, (v) the calibration, and (vi) the implementation of models. Such decision have material impacts on model outcomes and have financial implications. Consequently, institutions must implement a clear governance process around these decisions.
4.6.2
All parties involved in making decisions required at any step of the model life-cycle must be identified and recorded in the model documentation. Within an institution, individuals may hold several of these roles (i.e. several responsibilities), with the exception of model validation which must remain independent from the other roles. At a minimum, the following roles must be identified for each model:
(i) Model owner, (ii) Model developer, (iii) Model validator, (iv) Model user, (v) Modelling data owner, and (vi)
Model Oversight Committee members.
4.6.3
Institutions must establish a Model Oversight Committee, to whom the stakeholders mentioned at 4.6.2 are accountable. This committee must be established separately from existing risk management committees. Its scope must cover all models across the institution, with the view to manage Model Risk in its entirety. The committee must convene regularly and at a minimum every quarter.
4.6.4
The Model Oversight Committee must provide substantiated decisions related to each step of the model life-cycle and in particular, strategic modelling options. Consequently, the committee members must have a minimum level of technical understanding to be able to contribute to those decisions.
4.6.5
The Model Oversight Committee must be accountable to Senior Management and the Board. The committee must provide an impartial view of the best modelling approach for the institution. It must remain independent from actual, potential or perceived interests of business lines. Therefore, the majority of the Committee members must not be from the business lines. If business views and risk management views related to modelling choices are irreconcilable, Senior Management must make a decision, be accountable for it and provide a clear rationale for it. The final decision must be in compliance with the requirements outlined in the MMS.
4.6.6
At a minimum, the Model Oversight Committee must hold the following responsibilities.
(i) Design the institution’s appetite for Model Risk to be approved by the Board, (ii) Ensure that Model Risk is managed appropriately across the institution, (iii) Escalate modelling decisions when necessary, (iv) Oversee the objective and strategy of each model, (v) Approve the development of new models, (vi) Request the development of new models when necessary, (vii) Approve material modelling decisions throughout the model life-cycle, (viii)
At the end of each cycle, review the validation results and make a choice amongst the options presented in the section 4.3 on model life-cycle.
Whilst some technical aspects of these responsibilities can be delegated to subcommittees, working groups and/or individuals, the Model Oversight Committee must remain the centralised forum where modelling decisions for the whole institution are discussed, made or proposed for escalation. Material modelling decisions must be ultimately approved by the Board.
4.6.7
Other subject matter experts across the institution and third party experts can contribute to each step of the model life-cycle depending on their field of expertise. They can be involved in model design, development and testing. However, their involvement must be viewed as consultative only.
4.6.8
The CRO is responsible for ensuring that Model Risk is managed appropriately. Consequently, as part of his/her duty, the CRO must ensure that:
(i)
Model Risk is appropriately identified, understood, estimated, reported and mitigated across the institution. (ii)
The governance for model management is efficient and appropriate to the size and complexity of the institution. (iii)
The Model Oversight Committee is functioning appropriately and meets the responsibilities outlined in article 4.6.6. (iv)
Material modelling decisions are approved by the Board (or the Board Risk Committee). The Board is adequately informed of Model Risk, the status of model management and the performance of models. (v) A suitable escalation process is in place through the institution and up to the Board. (vi)
The institution employs adequate resources to meet the demands of model management and, where required, escalate identified gaps to Senior Management and/or the Board. (vii) He/she is fully familiar with the requirements articulated in the MMS. (viii)
He/she has sufficient technical understanding to form an opinion about the modelling decisions with material financial implications. (ix)
He/she is sufficiently informed of material modelling decisions, in such a way that he/she can articulate a view about the suitability of these decisions. (x)
Particular attention is given to the quality, completeness and accuracy of the data used to make decisions based on models.
4.7 Third Party Provider
4.7.1
Institutions must remain the owners of their models at all times, under all circumstances. They must remain accountable for all modelling choices, even in the case of support from a third party consultant for any of the steps in the life-cycle.
4.7.2
If modelling support is provided by a third party, institutions must take the necessary steps to transfer knowledge from that third party to internal employees within a given time frame. This requirement applies to any of the steps of the model life-cycle.
4.7.3
Third party providers may offer a range of modelling contributions covering, amongst others, methodological support, system infrastructure, validation services and ready-made calibrations based on external data. Institutions must take the necessary action to fully understand the contributions provided by third parties. This requirement applies to all models and to all risk types.
4.7.4
In the case of methodological support, whilst institutions must operate within the constraints of the acquired model, they must demonstrate that the method is adequate to their portfolios. If a methodology acquired from a third party is not fully understood by the institution, then it must not be considered fit for purpose. If a third party provides a methodology to an institution, any subsequent validation exercise must be performed by an internal or external party independent from the original provider.
4.7.5
If a third party provides a ready-made calibrated model based on external data, such a solution must be justified, based on the following specific circumstances:
(i)
For portfolios and metrics for which an institution is not able to collect sufficient internal data, then externally calibrated models are acceptable. For instance, this applies in the case of low default portfolios or small portfolios for which data collection may not lead to statistically representative samples. (ii)
For portfolios and metrics for which an institution is in a position to collect internal data, then externally calibrated models must not be used. Externally calibrated models are acceptable, only temporarily over the short term until sufficient data is collected. In this case, immediately after the model implementation, institutions must take the necessary actions to (i) collect historical internal data from internal systems and (ii) collect future internal data in order to develop a model internally.
4.8 Internal Skills
4.8.1
Institutions must ensure that they acquire and retain adequate internal knowledge and core competences about modelling techniques. Full model ownership requires that institutions must have an appropriate number of internal employees with technical skills to understand and own models, even with the contribution of third parties. The contribution of external consultants cannot justify a lack of internal technical employees.
4.8.2
All institutions must ensure that they have a minimum number of technical employees to manage models independently of third parties. The skills of these employees must sufficient to cope with the complexity of the models implemented at the institution. If an institution does not have the required internal skills to manage complex models, these models should be simplified or replaced.
4.8.3
For branches or subsidiaries of foreign institutions, the internal technical expertise may reside at the parent group level, which are responsible for the oversight of the local implementation and/or usage of models. The technical experts from the parent entity must also oversee any third parties employed to deliver models for the local entity. The local branches or subsidiaries must nonetheless have employees with sufficient skills to ensure that models are suitably calibrated to the UAE context and meet the CBUAE requirements in this regard.
4.8.4
Knowledge about a model must not be restricted to a single individual in the organisation. Instead, knowledge must be shared amongst several staff members. This is necessary for the purpose of sound decision-making related to modelling choices and to minimise the impact of staff departure on the smooth continuation of model life-cycle execution.
4.8.5
Institutions are expected to recognise the scarcity of technical staff able to genuinely understand and own models. Therefore, they must put in place development plans and initiatives to retain and manage their technical employees appropriately. The strategic management of technical resources must include full and adequate cooperation of the institutions’ human resources function.
4.9 Model Documentation
4.9.1
Dedicated and consistent documentation must be produced for each step of the model life-cycle. The documentation must be sufficiently comprehensive to ensure that an independent party has all the necessary information to assess the suitability of the modelling decisions. In particular, the documentation must make a clear distinction between theoretical considerations, calibration choices and practical implementation considerations.
4.9.2
All model documentation, model management policies and procedures must be an accurate reflection of the institution’s practice and usage. In other words, institutions must ensure that the model attributes described in a modelling document are actually implemented. Any gaps and partial implementation must be recorded, tracked and reported to Senior Management and the Board by the modelling stakeholders. Institutions must have a remediation plan in place to address each of these gaps within an appropriate timeframe.
4.9.3
Institutions must develop internal standards for model documentation across all model types, with rigorous document control. This requirement is particularly relevant for the development and the validation steps. The documentation must be adapted to the type of model, the business context and the step of the life-cycle. At a minimum, all model development documentation must include the following information:
(i)
Document control including the model reference, owners, contributors and key dates of each life-cycle step, (ii) Model materiality in relation to the institution’s risk profile, (iii) Overview of the model strategy, structure and expected usage, (iv) Data set description, when applicable, (v) Methodology and modelling choices related to all the key modelling decisions, (vi) Modelling assumptions, weaknesses and limitations, (vii) Expert judgement inputs if any, (viii) Impact analysis of the new modelling decisions, and (ix)
Implementation process and timing of the new modelling decisions.
4.10 Performance Reporting
4.10.1
Institutions must implement a comprehensive reporting framework to ensure that Model Risk is analysed and assessed for the purpose of implementing risk mitigating measures.
4.10.2
Reporting must be implemented at several levels of the organisation, including to the Model Oversight Committee, the institution’s Risk Committee and the Board. Reporting must be specific and adapted to the nature of the stakeholders. The status of model management and Model Risk across the entire organisation must be presented to the Model Oversight Committee and the institution’s Risk Committee at a minimum on a quarterly basis, and to the Board or a specialised sub-committee of the Board at least on a yearly basis.
4.10.3
Reporting must be designed to support Model Risk management covering the identification, measurement, monitoring and mitigation of these risks. In particular, reporting must cover (i) the status of the model lifecycle for each model, (ii) the results of model performance assessment, (iii) the risks arising from the uncertainty surrounding certain modelling decisions, and (iv) the status and estimation of Model Risk throughout the organisation.
4.10.4
Institutions must comply with model reporting requirements from the CBUAE, as they evolve through time.
4.11 Mergers, Acquisitions and Disposals
4.11.1
If an institution merges with or acquires another institution, it must re-visit all the elements of the model management framework, as part of the integration process. The modelling framework and all the principles of model life-cycle management must be applied consistently across the newly formed institution. In particular, model ownership must be clearly defined. The newly formed institution must have sufficient resources to fully manage the new scope of models.
4.11.2
The scope of models must be re-visited to assess whether there is a degree of overlap between models. Depending on circumstances, models may need to be recalibrated or redeveloped. Models must be representative of the risk profile of the newly formed institution. In the case of overlap between two similar models, a new single model must be developed based on a larger data sample. This new development must occur promptly after the completion of the merger or the acquisition.
4.11.3
Institutions must pay particular attention to the integration of historical data, and future data collection, subsequent to the merger or the acquisition. This requirement applies to all data fields used as inputs to the existing models and to the future models to be developed, in particular, default rates and recovery information. Historical data time series must be reconstructed to reflect the characteristics and risk profile of the newly formed institution. Upon the implementation of the MMS, this requirement applies retroactively to cover, at a minimum, a full economic cycle in the UAE, and where possible covering the 2008 global financial crisis. Future data collection must be performed for the entire scope of the newly formed institution.
4.11.4
In the case of the disposal of an entity, a subsidiary, a branch and/or a large portfolio, institutions must ensure that the modelling framework and all the principles of model life-cycle management are adjusted to fit the needs of the reduced scope of portfolios, products, obligors and/or exposures.
5 Data Management
5.1 Data Governance
5.1.1
For the avoidance of doubt, the scope under consideration in this section includes the data employed for modelling and validation purposes, not the data employed for regular risk analysis and reporting. This section focuses on the construction of historical data sets for the purpose of modelling.
5.1.2
Accurate and representative historical data is the backbone of financial models. Institutions must implement rigorous and a comprehensive formal data management framework (“DMF”) to ensure the development of accurate models. Institutions must consider DMF as a structured process within the institution, with dedicated policies and procedures, and with the adequate amount of resources and funding. The DMF core principles are as follows:
(i) It must be approved by Senior Management and the Board, (ii) It must be thoroughly documented with indication of limitations and assumptions, (iii) Its coverage must include the whole institution and all material risk types, and (iv)
It must be independently validated.
5.1.3
The DMF must include, at a minimum, the following steps:
(i) Identification of sources, (ii) Regular and frequent collection, (iii) Rigorous data quality review and control, (iv) Secure storage and controlled access, and (v)
Robust system infrastructure. 5.1.4
The roles and responsibilities of the parties involved or contributing to the DMF must be defined and documented. Each data set or data type must have an identified owner. The owner is accountable for the timely and effective execution of the DMF steps for its data set or data type. The owner may not be responsible for performing each of the DMF steps, but she/he must remain accountable for ensuring that those are performed by other parties with high quality standards.
5.2 Identification of Data Sources
5.2.1
The DMF must include a process to identify and select relevant data sources within the institution for each type of data and model. If an institution recently merged or acquired another entity, it must carry out the necessary steps to retrieve historical data from these entities.
5.2.2
If internal sources are lacking in data quality or quantity, institutions may rely on external sources. However, if an institution decides to rely on external data for modelling, it must demonstrate that the data is relevant and suitably representative of its risk profile and its business model. External data sources must be subject to an identification and selection process. The DMF governance and quality control also apply to external data employed for modelling.
5.2.3
Once a source has been selected, institutions are expected to retain this source long enough to build consistent time series. Any change of data source for the construction of a given data set must be rigorously documented.
5.3 Data Collection
5.3.1
Each institution must collect data for the estimation of all risks arising from instruments and portfolios where it has material exposures. The data collection must be sufficiently granular to support adequate modelling. This means that data collection must be (i) sufficiently specific to be attributed to risk types and instrument types, and (ii) sufficiently frequent to allow the construction of historical time series.
5.3.2
The data collection process must cover, amongst others, credit risk, market risk (in both the trading and banking books), concentration risk, liquidity risk, operational risk, fraud risk and financial data for capital modelling. A justifiable and appropriate collection frequency must be defined for each risk type.
5.3.3
The data must be organised such that the drivers and dimensions of these risks can be fully analysed. Typical dimensions include obligor size, industries, geographies, ratings, product types, tenor and currency of exposure. For credit risk in particular, the data set must include default events and recovery events by obligor segments on a monthly basis.
5.3.4
The data collection must be documented. The data collection procedure must include clear roles and responsibilities with a maker-checker review process, when appropriate.
5.3.5
Institutions must seek to maximise automated collections and reduce manual interventions. Manual interventions must be avoided as much as possible and rigorously documented to avoid operational errors.
5.3.6
The data collection process must ensure the accuracy of metadata such as units, currencies, and date/time-stamping.
5.4 Data Quality Review
5.4.1
Prior to being used for modelling purposes, the extracted data must go through a cleaning process to ensure that data meets a required quality standard. This process must consider, at a minimum, the following data characteristics:
(i) Completeness: values are available, where needed, (ii) Accuracy: values are correct and error-free, (iii) Consistency: several sources across the institution lead to matching data, (iv) Timeliness: values are accurate as of the reporting date, (v) Uniqueness: values are not incorrectly duplicated in the same data set, and (vi)
Traceability: the origin of the data can be traced.
5.4.2
Institutions must put in place process to accomplish a comprehensive data quality review. In particular, the quality of data can be improved by, amongst others, replacing missing data points, removing errors, correcting the unit basis (thousands vs. millions, wrong currency, etc.) and reconciling against several sources.
5.4.3
Institutions must put in place tolerance levels and indicators of data quality. These indicators must be mentioned in all model documentation. Data quality reports must be prepared regularly and presented to Senior Management and the Board as part of the DMF governance, with the objective to monitor and continuously improve the quality of data over time. Considering the essential role of data quality in supporting risk management and business decisions, institutions must also consider including data quality measures in their risk appetite framework.
5.5 Data Storage and Access
5.5.1
Once a data set has been reviewed and is deemed fit for usage, it must be stored in a defined and shared location. Final data sets must not be solely stored on the computers of individual employees.
5.5.2
The access to a final data set must be controlled and restricted to avoid unwarranted modifications.
5.5.3
Appropriate measures must be taken to ensure that data is stored securely to mitigate operational risks such as cyber-attacks and physical damage.
5.6 System Infrastructure
5.6.1
Institutions must ensure that an appropriate IT system infrastructure is in place to support all the steps required by the DMF.
5.6.2
The system infrastructure must be sufficiently scalable to support the DMF requirements.
5.6.3
The system infrastructure must be in the form of strategic long-term solutions, not tactical solutions. Spreadsheet solutions must be not considered as acceptable long term solutions for data storage.
5.6.4
Employment of staff with data science knowledge and expertise is encouraged in order to undertake appropriate data management oversight.
5.6.5
Institutions must minimise key person risk related to the management of modelling data. They must ensure that several members of staff have the suitable technical expertise to fully manage data for modelling purposes.
6 Model Development
6.1.1
The development of internal models must follow a documented and structured process with sequential and logical steps, supporting the construction of the most appropriate models to meet the objectives assigned to these models. At a minimum, institutions must consider the following components. More components can be added depending on the type of model. If a component is not addressed, then clear justification must be provided.
(i) Data preparation, (ii) Data exploration (for statistical models), (iii) Data transformation, (iv) Sampling (for statistical models), (v) Choice of methodology, (vi) Model construction, (vii) Model selection, (viii) Model calibration (for statistical models), (ix) Pre-implementation validation, and (x)
Impact analysis.
6.1.2
This process must be iterative, in that, if one step is not satisfactory, some prior steps must be repeated. For instance, if no model can be successfully constructed, additional data may be needed or another methodology should be explored.
6.1.3
Each of these steps must be fully documented to enable an independent assessment of the modelling choices and their execution. This requirement is essential to support an adequate, independent model validation. Mathematical expressions must be documented rigorously to enable replication if needed.
6.1.4
For the purpose of risk models, a sufficient degree of conservatism must be incorporated in each of the development step to compensate for uncertainties. This is particularly relevant in the choice of data and the choice of methodology.
6.2 Data Preparation and Representativeness
6.2.1
Institutions must demonstrate that the data chosen for modelling is representative of the key attributes of the variables to be modelled. In particular, the time period, product types, obligor segments and geographies must be carefully chosen. The development should not proceed further if the data is deemed not representative of the variable being modelled. The institution should use a conservative buffer instead of a model, until a robust model can be built.
6.2.2
For the purpose of preparation and accurate representation, the data may need to be filtered. For instance, specific obligors, portfolios, products or time periods could be excluded in order to focus on the relevant data. Such filtering must be supported by robust documentation and governance, such that the institution is in a position to measure the impact of data filtering on model outputs. The tools and codes employed to apply filters must be fully transparent and replicable by an independent party.
6.3 Data Exploration
6.3.1
The data exploration phase must be used to confirm whether the data set is suitable for modelling purposes. The objective is to understand the nature and composition of the data set at hand and to identify expected or unusual patterns in the data. In this process, critical thinking and judgement is expected from the modelling team.
6.3.2
Descriptive statistics should be produced across both the dependent and independent variables. For instance, for credit risk modelling, such exploration is relevant to identify whether obligors have homogeneous features per segment and or market risk modelling, such exploration is relevant to assess whether the market liquidity of the underlying product is sufficient to ensure a minimum reliability of the market factor time series.
6.3.3
Institutions must clearly state the outcome of the data exploration step, that is, whether the data is fit for modelling or not. In the latter case, the development process must stop and additional suitable data must be sourced. Consequently, data unavailability must not excuse unreliable and inaccurate model output.
6.3.4
The exploration of data can lead to unusual, counterintuitive or even illogical patterns. Such features should not be immediately accepted as a mere consequence of the data. Instead, the modelling team is expected to analyse further these patterns at a lower level of granularity to understand their origin. Subsequently, either (i) the pattern should be accepted as a matter of fact, or (ii) the data should be adjusted, or (iii) the data set should be replaced. This investigation must be fully documented because it has material consequences on model calibration.
6.4 Data Transformation
6.4.1
Institutions must search for the most appropriate transformation of the dependent and the independent variables, in order to maximise the explanatory power of models. If some variables do not need to be transformed, such conclusion must be clearly stated and justified in the model development documentation.
6.4.2
The choice of variable transformation must neither be random nor coincidental. Transformations must be justified by an economic rationale. Amongst others, common transformations include (i) relative or absolute differencing between variables, (ii) logarithmic scaling, (iii) relative or absolute time change, (iv) ranking and binning, (v) lagging, and (vi) logistic or probit transformation. Quadratic and cubic transformations are possible but should be used with caution, backed by robust economic rationale, and should be used with a clear purpose in mind.
6.5 Sampling
6.5.1
For all types of statistical models, institutions must ensure that samples used for modelling are representative of the target variable to be modelled. Samples must meet minimum statistical properties to be eligible for modelling including, amongst others, a minimum size and a minimum number of data points.
6.5.2
Once a modelling data set has been identified, institutions should use sampling techniques to increase the likelihood of model stability, when possible. The sampling technique must be appropriate to the data set and a justification must be provided. Amongst others, common techniques include dividing data sets into a development sample and a validation sample.
6.6 Choice of Methodology
6.6.1
Each methodology employed for modelling must be based upon a conscious, rigorous and documented choice made under the model governance framework, and guided by the model objective. Methodology options can be suggested by third parties, however, the choice of a specific methodology remains a decision made within each institution. The ownership of a methodology must be assigned to a specific team or function within the institution, with sufficient level of seniority. The choice of methodology must be clearly stated and justified in the model development documentation.
6.6.2
The choice of methodology must be made upon comparing several options derived from common industry practice and/or relevant academic literature. Institutions must explicitly list and document the benefits and limitations of each methodology.
6.6.3
The choice of methodology must follow the following principles, which must be included in the model documentation:
(i)
Consistency: Methodologies must be consistent and comparable across the institution, across risk metrics and risk types. For instance, two similar portfolios should be subject to similar modelling approaches, unless properly justified. (ii)
Transparency: Methodologies must be clear and well-articulated to all stakeholders, including management, internal audit and the CBUAE. Mathematical formulation must be documented with all parameters clearly mentioned. (iii)
Manageability: A methodology must be chosen only if all the steps of the model life-cycle can support it. Complex methodologies must be avoided if any step of the model life-cycle cannot be performed. The choice of methodology must be based upon its ability to be implemented and successfully maintained.
6.6.4
When choosing the most suitable methodology, institutions must avoid excessive and unreasonable generalisations to compensate for a lack of data.
6.7 Model Construction
6.7.1
Statistical models:
(i)
The construction of statistical models must be based upon robust statistical techniques to reach a robust assessment of the coefficients. The statistical techniques should be chosen amongst those commonly employed in the industry for financial modelling and/or those supported by academic scientific literature. (ii)
Institutions must demonstrate that they have undertaken best efforts to understand the characteristics of the data and the nature of the relationships between the dependent and independent variables. In particular, institutions should analyse and discuss the observed correlations between variables and expected economic causations between them. Institutions should discuss the possibility of non-linear relationships and second order effects. Upon this set of analysis, a clear conclusion must be drawn in order to choose the best-suited approach for the model at hand. The analyses, reasoning and conclusions must be all documented. (iii)
Statistical indicators must be computed and reported in order to support the choice of a model. Thresholds should be explicitly chosen upfront for each statistical indicator. The indicators and associated thresholds should be justified and documented. (iv)
The implementation of statistical techniques is expected to lead to several potential candidate models. Consequently, institutions should identify candidates and rank them by their statistical performance as shown by the performance indicators. The pool of candidate models should form part of the modelling documentation. All model parameters must be clearly documented.
6.7.2
Deterministic models:
(i)
Deterministic models, such as financial forecasting models or valuation models, do not have statistical confidence intervals. Instead, the quality of their construction should be tested through (a) a set of internal consistency and logical checks and (b) comparison of the model outputs against analytically derived values. (ii)
Amongst other checks, one form of verification consists of computing the same quantity by different approaches. For instance, cash flows can be computed with a financial model through the direct or the indirect methods, which should both lead to the same results. Institutions must demonstrate and document that they have put in place a set of consistency checks as part of the development process of deterministic models. (iii)
Several deterministic models can be constructed based on a different set of assumptions. These models should constitute the pool of candidate models to be considered as part of the selection process.
6.7.3
Expert-based models:
(i)
Expert-based models, also referred to as ‘judgemental models’, must be managed according to a comprehensive life-cycle as for any other model. The construction of such models must follow a structured process, irrespective of the subjective nature of their inputs. The documentation must be sufficiently comprehensive to enable subsequent independent validations. In particular, the relationship between variables, the model logic and the rationale for modelling choices should all be documented and approved by the Model Oversight Committee. (ii)
The collection of subjective inputs must be treated as a formal data collection process. This means that the input data must be part of the DMF, with suitable quality control. Expert-based models provided by third parties must be supported by an appropriate involvement of internal subject matter experts. (iii)
Institutions are expected to develop several candidate models based on different assumptions. For all candidates, they should assess the uncertainty of the outputs, which will be a key driver of the model selection. (iv)
Institutions must be mindful of the high Model Risk associated with expert-based models. They must be in a position to justify that appropriate actions have been taken to manage such Model Risk. An additional degree of conservatism should be employed for the design, calibration and usage of expert-based models. The usage of such models for material portfolios could result into additional provisions and/or capital upon reviews from the CBAUE.
6.8 Model Selection
6.8.1
For statistical models, institutions must choose a final model amongst a pool of constructed models. Institutions must implement an explicit mechanism to filter out models and select a final model amongst several available options. It is recommended to select a main model and a challenger model up to the pre-implementation validation step. The selection of a model should include, at a minimum, the criteria outlined below. Institutions should consider all criteria together. Statistical performance should not be the only decisive factor to choose a model.
(i)
The chosen model must demonstrate adequate performance, statistical stability and robustness as shown by the statistical indicators and their thresholds. (ii)
The chosen model must be based on appropriate causal relationships, i.e. it should be constructed with variables and relationships that meet economic intuition and make logical business sense, as per the definition section of the MMS. For that purpose, causal diagrams are encouraged. (iii)
The chosen model must also lead to outcomes that meet economic intuition, can be explained easily and can support decision-making appropriately. (iv)
The chosen model must be implementable.
6.8.2
For deterministic and expert-based models, institutions must choose a final model amongst the pool of constructed models based on various assumptions. Institutions must put in place an explicit mechanism to prioritise certain assumptions and therefore choose a model amongst several candidates. In particular, the selection process should incorporate the following criteria:
(i)
The relationships between variables should be based on established causal links. The assumptions and limitations of these links should be assessed thoroughly. (ii)
The chosen model should lead to outcomes that make meet economic intuition as defined in the MMS, can be explained easily and can support decision-making appropriately. (iii)
The chosen model should be implementable.
6.9 Model Calibration
6.9.1
Model calibration is necessary to ensure that models are suitable to support business and risk decisions. Institutions must ensure that model calibration is based on relevant data that represents appropriately the characteristics and the drivers of the portfolio subject to modelling. This also applies to decisions to override or adjust inputs, coefficients and/or variables. Calibration choices must be fully documented and their assessment must also form part of the validation process. Models should be re-calibrated when deemed necessary, based on explicit numerical indicators and pre-established limits.
6.9.2
The choice of calibration requires judgement and must be closely linked to the objective of each model. In particular, the time period employed for calibration must be carefully justified depending on model types. Pricing models should be accurate. Provision models should be accurate with a degree of conservatism and should reflect the current and future economic conditions. Capital models should be conservative and reflect long term trends. Stress testing models should focus on extreme economic conditions.
6.10 Pre-implementation Validation
6.10.1
The pre-implementation validation of a model is the first independent validation that takes place after the model development. The objective of such validation must ensure that the model is fit for purpose, meets economic intuition as defined in the MMS and generates results that are assessed as reasonable by expert judgement. The depth of such validation must be defined based on model materiality and follow the institution’s model management framework. Tier 1 models must be subject to comprehensive pre-implementation validation.
6.10.2
For the qualitative review, the pre-implementation validation must cover the elements presented in Article 10.3 pertaining to the scope of the independent post-implementation validation. For the quantitative review, the pre-implementation validation must assess the model accuracy, stability and sensitivity as explained in Article 10.4.3 also pertaining to the scope of the independent post-implementation validation.
6.10.3
Institutions must document the scope, limitations and assumptions of models as part of the pre-implementation validation.
6.11 Impact Analysis
6.11.1
The objective of the impact analysis is to quantify the impact of using a newly-developed model or a newly-recalibrated model on the production of financial estimates. Where applicable, the impact analysis should be documented as part of the model development phase and reported to the Model Oversight Committee.
7 Model Implementation
7.1.1
Institutions must consider model implementation as a separate phase within the model life-cycle process. The model development phase must take into account the potential constraints of model implementation. However, successful model development does not guarantee a successful implementation. Consequently, the implementation phase must have its own set of documented and approved principles.
7.2 Project Governance
7.2.1
The implementation of a model must be treated as a project with clear governance, planning, funding, resources, reporting and accountabilities.
7.2.2
The implementation of a model must be approved by Senior Management and must only occur after the model development phase is complete and the model is fully approved.
7.2.3
The implementation project must be fully documented and, at a minimum, must include the following components:
(i) Implementation scope, (ii) Implementation plan, (iii) Roles and responsibilities of each party, (iv) Roll-back plan, and (v)
User Acceptance Testing with test cases.
7.2.4
The roles and responsibilities of the parties involved in the model implementation must be defined and documented. At a minimum, the following parties must be identified: (i) the system owner, (ii) the system users, and (iii) the project manager. All parties must be jointly responsible for the timely and effective implementation.
7.2.5
For model implementation, institutions should produce the following key documents, at a minimum:
(i)
User specification documentation: this document should specify requirements regarding the system functionalities from the perspective of users. (ii)
Functional and technical specification documentation: this document should specify the technological requirements based on the user specifications. (iii)
A roll back plan: this document should specify the process by which the implementation can be reversed, if necessary, so that the institution can rely on its previous model.
7.3 Implementation Timing
7.3.1
Institutions must be conscious that models are valid for a limited period of time. Any material delay in implementation diminishes the period during which the model can be used. Newly developed models must be implemented within a reasonable timeframe after the completion of the development phase. This timeframe must be decided upfront and fully documented in the implementation plan.
7.4 System Infrastructure
7.4.1
The IT system infrastructure must be designed to cope with the demand of the model sophistication and the volume of regular production. Institutions must assess that demand during the planning phase. Institutions should be in a position to demonstrate that the technological constraints have been assessed.
7.4.2
The IT system infrastructure should include, at a minimum, three environments: (i) development, (ii) testing, and (iii) production.
7.4.3
Institutions must have a management plan for systems failure. A system that does not comply with the business requirements must be replaced.
7.4.4
In the case of systems provided by a third party, institutions must have a contingency plan to address the risks that may arise if the third party is no longer available to support the institution.
7.4.5
If a system is designed to produce a given set of metrics, then institutions must use that system for the production and reporting of those metrics. If a system is not fit for purpose despite being implemented, institutions must not use a shadow system or a parallel system to produce the metrics that the original system was meant to produce, while maintaining the deficient original system. Instead, institutions must decommission any deficient system and fully replace it by a functioning system.
7.5 User Acceptance Testing
7.5.1
Institutions must ensure that a User Acceptance Testing (“UAT”) phase is performed as part of the system implementation plan. The objective of this phase is to ensure that the models are suitably implemented according to the agreed specifications.
7.5.2
The model implementation team must define a test plan and test cases to assess the full scope of the system functionalities, both from a technical perspective and modelling perspective. The test cases should be constructed with gradually increasing complexity. In particular, the test cases should be designed in order to assess each functionality, first independently and then jointly. The test cases should also capture extreme and erroneous inputs. Partial model replication must be used as much as possible.
7.5.3
There must be at least two (2) rounds of UAT to guarantee the correct implementation of the model. Generally, the first round is used to identify issues, while the second round is used to verify that the issues have been remediated.
7.5.4
The UAT test cases and results must be fully documented as part of the model implementation documentation. The test case inputs, results and computation replications must be stored and must be available for as long as the model is used in production.
7.5.5
Institutions must ensure that UAT tests and results are recorded and can be presented to the CBUAE, other regulators and/or auditors to assess whether a model has been implemented successfully. In particular, all rounds of UAT test cases and results must be available upon request from the CBUAE, as long as a model is used in production.
7.5.6
The UAT must be considered successful only upon the sign-off from all identified stakeholders on the UAT results. The UAT plan and results must be approved by the Model Oversight Committee.
7.5.7
Institutions must ensure that the model being implemented remains unchanged during the testing phase.
7.6 Production Testing
7.6.1
Institutions must ensure that a production testing phase is performed as part of the system implementation plan. The objective of this phase is to guarantee the robustness of the system from a technology perspective according to the functional and technical specification documentation.
7.6.2
In particular, the production testing phase must ensure that systems can cope with the volume of data in production and can run within an appropriate execution time.
7.7 Spreadsheet Implementation
7.7.1
It is not recommended that institutions use spreadsheet tools for the usage of material models and the production of metrics used for regular decision-making. More robust systems are preferred. Nevertheless, if spreadsheets are the only possible modelling environment available initially, the standards in 7.7.2 must apply, at a minimum.
7.7.2
Spreadsheet implementation should follow a quality standard as follows:
(i) The spreadsheet should be constructed with a logical flow, (ii) Formulae should be easily traceable, (iii)
Formulae should be short and constructed in a way that they are easily interpreted. It is recommended to split long formula into separate components, (iv) Tables should include titles, units and comments, (v)
Inputs should not be scattered across the sheets but they should be grouped in one worksheet/table, (vi) Hardcoded entries (i.e. fixed inputs) should be clearly identified, (vii)
Tabs should be clean, i.e. when the implementation is completed, all work in progress should be removed, (viii) Instructions should be included in one or several tabs, and (ix)
Wherever suitable, cells should be locked and worksheets protected, preferably by password.
7.7.3
Models implemented in spreadsheets that deviate from the above criteria must not be employed for regular production.
7.7.4
To ensure their robust implementation, spreadsheet tools must include consistency checks. Common consistency checks include: (i) computing the same results through different methods, (ii) ensuring that a specific set of inputs leads to the correct expected output values, and (iii) ensuring that the sensitivities of outputs to changes in inputs are matching expected values.
7.7.5
If an institution employ spreadsheets for regular production, a rigorous maker-checker process must be implemented and documented. The review of spreadsheet tools must be included in the scope of the independent validation process. In addition, a clear version control should be implemented.
8 Model Usage
8.1.1
Model usage is an integral part of model management. Model usage must be defined, documented, monitored and managed according to the following principles.
8.2 Usage Definition and Control
8.2.1
As part of the definition of model strategy and objectives, institutions must articulate and document upfront the expected usage of each model. Model usage must cover, at a minimum, the following components:
(i) The users identified either as individuals or teams, (ii) The expected frequency of model utilisation, (iii) The specific source and nature of the inputs in the production environment, (iv) The destination of the outputs in terms of IT system and operational processes, (v)
The interpretation of the outputs, that is a clear guidance on how the outputs should be used, their meaning and the decisions that they can support, (vi)
The limits of the outputs, associated uncertainty and the decisions that can be supported by the model versus those that should be supported, and (vii)
The governance of output overrides.
8.2.2
Institutions must produce indicators to actively monitor the realisation of the components in 8.2.1 and compare them against initial expectations. These must be documented and reported as part of the monitoring and validation steps of the model life-cycle.
8.2.3
Any deviation between the real usage of a model and the expected usage of a model must be documented in the monitoring and validation phases and remedied promptly, by reverting to the intended usage of the model.
8.3 Responsibilities
8.3.1
The management of model usage is shared between several parties. The model owner is responsible to define the usage of his/her models. The usage of each model should then be approved by the Model Oversight Committee. If the model owner and model user are different parties, the owner is responsible to provide documentation and training to the user. The model user must therefore follow appropriately the guidance provided by the owner.
8.3.2
The monitoring of model usage can be performed by the model owner, by the validator, or both, depending on the institution’s circumstances. Irrespective of the party performing the monitoring process, the validator must conduct an independent assessment of the appropriate usage of models as part of the validation process. For this purpose, the validator should refer to the monitoring reports, when available.
8.3.3
It may happen that the model owner has limited control over the usage of a model by other parties. In this case, the model owner is responsible to report to the Model Oversight Committee any model misuse or usage without his consent.
8.4 Input and Output Overrides
8.4.1
This section refers to all model types including, but not limited to, rating models. Manual overrides of model inputs and outputs are possible and permitted but within limits. For this purpose, institutions must put in place robust governance to manage these overrides. Such governance must be reviewed by the internal audit function. Institutions must implement limits and controls on the frequency and magnitude of overrides. Models whose input and/or outputs that are frequently and materially overridden must not be considered fit for purpose and must be recalibrated or replaced.
8.4.2
During the execution phase, input and/or output overrides must be documented, justified and approved at the appropriate authority level. When necessary, an opinion from technical subject matter experts should be produced. Overrides used by the business lines must be subject of review by the risk management function before being implemented.
8.4.3
The development and validation teams must analyse and understand the reasons for input and/or output overrides and assess whether they are caused by model weaknesses. Overrides must be tracked and reported to the Model Oversight Committee, Senior Management and the Board as part of the monitoring and validation processes.
8.4.4
If a model has been approved and is deemed suitable for production, its outputs must not be ignored. This also applies when model outputs are not meeting commercial expectations. Model outputs must be considered objectively and independently from actual, potential or perceived business line interests.
8.5 User Feedback
8.5.1
Institutions must have a process in place to ensure that model functionalities are working as expected during ongoing utilisation. The objective is to ensure that models have been designed, calibrated and implemented successfully.
8.5.2
The user feedback must cover the model functionalities, stability and consistency of output against economic and business expectations. The user feedback must be documented and reported as part of the monitoring and validation steps of the model life-cycle. If model users are different from model developers, institutions must have a process in place to collect feedback from the identified model users.
8.6 Usage of Rating Models
8.6.1
Institutions must pay particular attention to the usage of rating models due to their material impacts on financial reporting, provisions, risk decisions and business decisions. Specific policies and procedures must be designed to govern overrides, including the scope of usage, the responsibilities and the conditions of output overrides.
8.6.2
At a minimum, a rating must be assigned to each obligor on a yearly cycle. In the case of exceptional circumstances related to the obligor, the industry or the wider economy, ratings may need to be assigned more frequently.
8.6.3
Consistently with Article 8.6.2, upon the roll-out of a new rating model and/or a newly recalibrated (optimised) rating model, institutions must update client ratings as soon as possible and within a period no longer than twelve (12) months. Further details are provided in the MMG on this matter.
9 Model Performance Monitoring
9.1 Objective
9.1.1
Institutions must implement a process to monitor the performance of their models on a regular basis, as part of their model life-cycle management. The relationship between model performance and usage is asymmetric. A robust model does not guarantee relevant usage. However, an improper usage is likely to impact the model performance. Consequently, institutions must ensure that models are used appropriately prior to engaging in performance monitoring.
9.1.2
The objective of the monitoring process is to assess whether changes in the economic environment, market conditions and/or business environment have impacted the performance, stability, key assumptions and/or reliability of models.
9.1.3
Institutions must implement a documented process with defined responsibilities, metrics, limits and reports in order to assess whether models are fit for purpose, on an ongoing basis. Upon this assessment, there must be a clear decision-making process to either (i) continue monitoring or (ii) escalate for further actions.
9.2 Responsibility
9.2.1
The responsibility for the execution of model monitoring must be clearly defined. Institutions have the flexibility to assign this task to the development team, the validation team or to a third party. If model monitoring is assigned to the development team, the monitoring reports must be included in the scope of review of the independent validation process. If model monitoring is assigned to a third party, institutions remain the owners of monitoring reports and remain responsible to take appropriate actions upon the issuance of these reports. Institutions are expected to fully understand and control the content of monitoring reports produced by third party providers.
9.2.2
Monitoring reports must be presented regularly to the Model Oversight Committee. All reports containing limit breaches of monitoring metrics must be discussed by the committee.
9.2.3
The internal audit function must verify that model monitoring is performed appropriately by the assigned party. In particular, the internal audit function must review the relevance, frequency and usability of the monitoring reports.
9.3 Frequency
9.3.1
Model monitoring must be undertaken on a frequent basis and documented as part of the model life-cycle management. Institutions must demonstrate that the monitoring frequency is appropriate for each model. The minimum frequency is indicated in the Article (10) of the MMS, which covers the independent validation process.
9.4 Metrics and Limits
9.4.1
Institutions must develop metrics and limits to appropriately track model performance. The metrics must be carefully designed to capture the model performance based on its specific characteristics and its implementation. At a minimum, the monitoring metrics must capture the model accuracy and stability as explained in Article 10.4.3 pertaining to the scope of the post-implementation validation. In addition, the monitoring metrics must track the model usage to assess whether the model is used as intended.
9.5 Reporting and Decision-Making
9.5.1
Institutions must implement a regular process to report the results of model monitoring to the Model Oversight Committee, the CRO and to the model users.
9.5.2
Reports must be clear and consistent through time. For each model, monitoring metrics must be included along with their respective limits. Times series of the metrics should be provided in order to appreciate their volatility and/or stability through time and therefore help make a view on the severity of limit breaches. Explanations on the nature and meaning of each metric must be provided, in such a way that the report can be understood by the members of the Model Oversight Committee and by auditors.
9.5.3
Regardless of the party responsible for model monitoring, all reports must be circulated to both the development team and the independent validation team, as soon as they are produced. For some models, monitoring reports can also be shared with the model users.
9.5.4
In each report, explanations on the significance of limit breaches must be provided. Sudden material deterioration of model performance must be discussed promptly between the development team and the validation team. If necessary, such deterioration must be escalated to the Model Oversight Committee and the CRO outside of the scheduled steps of the model life-cycle. The Committee and/or the CRO may decide to suspend the usage of a model or accelerate the model review upon the results of the monitoring process.
9.5.5
Institutions must define the boundaries of model usage. These are the limits and conditions upon which a model is immediately subject to adjustments, increased margins of conservatism, exceptional validation and/or suspension. Specific triggers must be clearly employed to identify abnormalities in model outputs.
10 Independent Validation
10.1 Objective and Scope
10.1.1
The independent validation of models is a key step of their life-cycle management. The objective is to undertake a comprehensive review of models in order to assess whether they are performing as expected and in line with their designed objective. While monitoring and validation are different processes run at different frequencies, the content of the monitoring process forms a subset of the broader scope covered by the validation process. Therefore, when available, the results of the monitoring process must be used as inputs into the validation process.
10.1.2
Institutions must put in place a rigorous process with defined responsibilities, metrics, limits and reporting in order to meet the requirements of independent model validation. Part of the metrics must be common between the monitoring process and the validation process. Independent validation must be applied to all models including statistical models, deterministic models and expert-based models whether they have been developed internally or acquired from a third party provider.
10.1.3
The validation scope must cover both a qualitative validation and a quantitative validation. Both validation approaches complement each other and must not be considered separately. A qualitative validation alone is not sufficient to be considered as a complete validation since it does not constitute an appropriate basis on which modelling decisions can be made. If insufficient data is available to perform the quantitative validation, the validation process should be flagged as incomplete to the Model Oversight Committee, which should then make a decision regarding the usage of the model in light of the uncertainty and the Model Risk associated with such partially validated model.
10.1.4
The scope of the validation must be comprehensive and clearly stated. The scope must include all relevant model features that are necessary to assess whether the model produces reliable outputs to meet its objectives. If a validation is performed by a third party, institutions must ensure that the validation scope is comprehensive. It may happen that an external validator cannot fully assess all relevant aspects of a model for valid reasons. In this case, institutions are responsible to perform the rest of the validation and to ensure that the scope is complete.
10.1.5
A validation exercise must result in an independent judgement with a clear conclusion regarding the suitability of the model. A mere description of the model features and performance does not constitute a validation. Observations must be graded according to an explicit scale including, but not limited to, ‘high severity’, ‘medium severity’ and ‘low severity’. The severity of model findings must reflect the degree of uncertainty surrounding the model outputs, independently of the model materiality, size or scope. As a second step, this degree of uncertainty should be used to estimate Model Risk, since the latter is defined as the combination of model uncertainty and materiality.
10.1.6
In addition to the finding severity, institutions must create internal rating scales to assess the overall performance of each model. This performance rating should be a key input in the decision process in each model step of the model life-cycle.
10.2 Responsibilities
10.2.1
Institutions must put in place a rigorous process to ensure that models are independently validated either by an internal dedicated team or by a third party provider, or both. If model validation is assigned to a third party, institutions remain the owners of validation reports and must take appropriate action upon the issuance of these reports.
10.2.2
In order to ensure its independence and efficiency, the party responsible for model validation (“validator”) must be able to demonstrate all the following characteristics. If the validator does not possess all of those, the validation reports must not be considered independent and/or robust enough and therefore must not be used for decision-making.
(i) Advanced understanding of model methodologies and validation techniques, that is sufficiently mature to allow the formulation of independent judgement. (ii)
The expertise and freedom to express, hold and defend views that are different from the development team and from management. The ability to present those views to the Model Oversight Committee, Senior Management and the Board. (iii)
The ability to perform independent research and articulate alternative proposals.
10.2.3
The internal audit function is responsible to verify that model validation is performed appropriately by the assigned party, following a regular audit cycle. At a minimum, the audit function must cover the following scope:
(i)
Review the governance surrounding the internal validation process and assess its independence in light of the MMS. (ii)
Form a view regarding the suitability of the depth and scope of the work performed by the validation team, also in light of the MMS. (iii)
Review the relevance, frequency and effectiveness of the validation process. At a minimum, the auditor must review the list of findings issued by the validator and assess if the timing necessary for remediation is appropriate.
10.2.4
The internal audit function should employ third party experts to assist on technical matters until it can demonstrate that it can perform an adequate review of the model validation process without technical support. If the audit team employs supporting experts, it remains the sole owner of the conclusions of the audit report.
10.3 Qualitative Validation
10.3.1
The independent validation process must include a review of the model conceptual soundness, design and suitability of the development process. The scope of the qualitative validation varies depending on the statistical or deterministic nature of the model. This must include, at a minimum, a review of the following elements:
(i) The model governance and decision process, (ii) The model conceptual soundness, purpose and scope, (iii) The methodology including the mathematical construction, (iv)
The suitability of the output in terms of economic intuition and business sense as defined in the MMS, and (v) The suitability of the implementation (when the model is implemented) In addition, for statistical models: (vi) The choice of variables and their respective transformation, (vii) The suitability of the data in terms of sources, filters and time period, and (viii)
The suitability of the sampling techniques, if any.
10.4 Quantitative Validation
10.4.1
The quantitative validation must assess the suitability of the model output with respect to the objective initially assigned to the model. This process must rely on numerical analyses to derive its conclusions. Such validation should include a set of dedicated research to arrive at an independent judgement. Under certain circumstances, partial model replication and/or a challenger model may be necessary to form a judgement.
10.4.2
The set of metrics employed for model validation must at least include those employed for monitoring. As a first step, the validator must make a review of the monitoring reports and their observations. In addition, institutions should employ a broader spectrum of performance metrics to fully assess model performance, since the scope of the validation process is larger than that of monitoring.
10.4.3
The assessment of model performance must cover, at a minimum, the following components, applicable to both statistical and deterministic models:
(i)
Accuracy and conservatism: The ability of a model to generate predictions that are close to the realised values, observed before and after the model development phase. For models whose results are subject to material uncertainty, the validator should assess if sufficient conservatism included in the model calibration. (ii)
Stability and robustness: Whilst there are theoretical differences between stability and robustness, for the purpose of this MMS, this refers to the ability of a model to withstand perturbations, i.e. maintain its accuracy despite variability in its inputs or when the modelling assumptions are not fully satisfied. In particular, this means the ability of a model to generate consistent and comparable results through time. (iii)
Controlled sensitivity: This relates to the model construction. Model sensitivity refers to the relationship between a change in the model inputs and the observed change in the model results. The sensitivity of the output to a change in inputs must be logical, fully understood and controlled.
10.4.4
The quantitative validation process should include a review of the suitability, relevance and accuracy of following components.
For both statistical and deterministic models: (i) The implementation, (ii) The adjustments and scaling factors, if any, (iii) The ‘hard-coded’ rules and mappings, (iv) The extrapolations and interpolations, if any, and (v) The sensitivities to changes in inputs, In addition for statistical models only: (vi) The model coefficients, (vii) The statistical accuracy of the outputs, (viii) The raw data as per the DMF requirements, and (ix) The historical time series, In addition, for deterministic models only: (x) A decomposition of the model drivers and their associated sensitivity, and (xi)
A partial replication, when possible.
10.5 Review Frequency
10.5.1
All models must be validated at regular frequencies appropriate to model types and tiers. The review periods should not be longer than the ones presented in Table 2 below. More frequent reviews can be implemented at the discretion of institutions, depending on model types and complexity. More frequent reviews may also be necessary in the case of unforeseen circumstances, for instance related to changes in model usage and/or changes in the economic environment. Less frequent reviews are possible in certain circumstances, but they should be justified and will be subject to assessment from the CBUAE.
10.5.2
The dates corresponding to the last monitoring and validation exercises must be tracked rigorously, included in the model inventory and reported to the Model Oversight Committee at least every quarter. The internal audit function must ensure that this process is implemented effectively by the model owner and the validator.
Table 2: Minimum monitoring and validation frequencies for most common models
Tier 1 models Tier 2 models Portfolio Model Type Monitoring Validation Monitoring Validation Wholesale Rating 1 year 3 years 2 years 5 years Wholesale PD term structure 1 year 3 years 2 years 5 years Wholesale Macro-PD 1 year 2 years 2 years 3 years Wholesale LGD 1 year 3 years 2 years 5 years Wholesale Macro-LGD 1 year 2 years 2 years 3 years Retail Scorecard 3 months 1 year 6 months 3 years Retail PD term structure 1 year 2 years 2 years 3 years Retail Macro-PD 1 year 2 years 2 years 3 years Retail LGD 1 year 2 years 2 years 3 years Retail Macro-LGD 1 year 2 years 2 years 3 years EAD EAD 1 month 3 years 2 years 5 years Trading Book VaR and related models 3 months 3 years* 6 months 4 years* Trading Book Exposure and xVA 1 year 3 years* 6 months 4 years* Multiple Valuation 1 year 3 years* n/a 4 years* Multiple Concentration 1 year 3 year** n/a n/a Multiple IRRBB 1 year 3 year** n/a n/a Multiple Other Pillar II models 1 year 3 year** n/a n/a Multiple Capital forecasting 1 year 3 year** n/a n/a Multiple Liquidity 1 year 3 year** n/a n/a 10.5.3
Where [*] is indicated in table 2 above: For pricing and traded risk models such as VaR, exposure and xVA models, a distinction should be made between (i) the model mechanics, (ii) the calibration and (iii) the associated market data. The mechanics should be reviewed at least every 3 to 4 years ; however the suitability of the calibration and the market data should be reviewed more frequently as part of the model monitoring process. In addition to these frequencies, any exceptional market volatility should trigger a revision of all model decisions.
10.5.4
Where [**] is indicated in table 2 above: For deterministic models such as capital forecasting, concentration and IRRBB models, a distinction should also be made between (i) the model mechanics and (ii) the input data. Whilst the mechanics (methodology and system) can be assessed every 3 years, the calibration must be reviewed yearly in order to assess the appropriate usage of the model with a new set of inputs. This yearly frequency is motivated by the strategic usage of such models in the ICAAP.
10.5.5
For models other than those mentioned in table 2 above, institutions must establish a schedule for monitoring and validation that is coherent with their nature and their associated Model Risk.
10.6 Reporting of Findings
10.6.1
The analyses and tests performed during the validation of a model must be rigorously documented in a validation report. Validation reports must be practical, action orientated, focused on findings and avoid unnecessary theoretical digressions. A validation report should include, at a minimum, the following components:
(i) The model reference number, nomenclature, materiality and classification, (ii) The implementation date, the monitoring dates and the last validation date, if any, (iii) A clear list of findings with their associated severity, (iv) Suggestions for remediation, when appropriate, (v) The value of each performance indicator with its associated limit, (vi) The results of the qualitative review as explained above, (vii) The results of the quantitative review as explained above, (viii) The model risk rating, and (ix)
A conclusion regarding the overall performance.
10.6.2
The model validation report must refer to the steps of the model life-cycle. Its conclusion should be one of the following possible outcomes, as mentioned in the model governance section:
(i) Leave the model unchanged, (ii) Use a temporary adjustment while establishing a remediation plan, (iii) Recalibrate the model, (iv) Redevelop a new model, or (v)
Withdraw the model without further redevelopment.
10.7 Remediation Process
10.7.1
Institutions must put in place effective processes to manage observations and findings arising from independent validation exercises. The remediation process must be structured and fully documented in the institution’s policy. The findings need to be clearly recorded and communicated to all model stakeholders including, at least, the development team, the members of the Model Oversight Committee and Senior Management. The members of the committee must agree on a plan to translate the findings into actionable items which must be addressed in a timely fashion.
10.7.2
If an institution decides not to address some model defects, it must identify, assess and report the associated Model Risk. It must also consider retiring and/or replacing the model or implement some other remediation plan. Such decision may result in additional provisions and/or capital buffers and will be subject to review by the CBUAE.
10.7.3
Upon completion, the validation report must be discussed between the validator and the development team, with the objective to reach a common understanding of the model weaknesses and their associated remediation. Both parties are expected to reach a conclusion on the validation exercise, its outcomes and its remediation plan. The following must be considered:
(i)
The views expressed by both parties must be technical, substantiated and documented. The development team and/or the model owner should provide a response to all the observations and findings raised by the validator. (ii)
The views expressed by both parties must aim towards a practical resolution, with the right balance between theoretical requirements vs. practical constraints. (iii)
The resolution of modelling defects must be based on minimising the estimated Model Risk implicit in each remediation option. (iv)
Outstanding divergent views between both parties should be resolved by the Model Oversight Committee.
10.7.4
For each finding raised by the validator, the following must be submitted to the Model Oversight Committee for consideration: (i) substantiated evidence from the validator, (ii) the opinion of the development team, (iii) a suggested remediation, if deemed necessary, and (iv) a remediation date, if applicable. The Model Oversight Committee must decide to proceed with one of the options listed in the Article 10.6.2 above. When making a choice amongst the various options, the Committee must consider their respective Model Risk and associated financial implications.
10.7.5
The validator must keep track of the findings and remediating actions and report them to the Model Oversight Committee and Senior Management on a quarterly basis, and to the Board (or to a specialised body of the Board) on a yearly basis. Such status reports must cover all models and present the outstanding Model Risk. The reports must be reviewed by the internal audit function as part of their audit review. Particular attention should be given to repeated findings from one validation to the next.
10.7.6
If the institution does not have an internal validation team, then reporting of model findings and remediation can be performed by another function within the institution. However, the internal audit function must regularly review the reporting process to ensure that such reporting is an accurate representation of the status of model performance.
10.7.7
Institutions must aim to resolve model findings promptly in order to mitigate Model Risk. For that purpose, institutions must develop a process to manage defect remediation effectively. This process must include the following principles:
(i)
High severity findings must be addressed immediately with tactical solutions, irrespective of the model Tier. Such solutions can take the form of temporary adjustment, overlay and/or scaling in order to reduce the risk of inaccurate model outputs and introduce a degree of conservatism. Tactical solutions must not become permanent, must be associated with an expiration date and must cease after the implementation of permanent remediation. (ii)
Institutions must establish maximum remediation periods per finding severity, per model Tier and per model type. The remediation period must start from the date at which the Model Oversight Committee reaches an agreement on the nature and severity of the finding. For findings requiring urgent attention, an accelerated approval process must be put in place to start remediation work. (iii)
Tactical solutions must only be temporary in nature and institutions should aim to fully resolve high severity findings within six (6) months. At a maximum, high severity findings must be resolved no later than twelve (12) months after their identification. High severity findings, not resolved within 6 months must be reported to the Board and to the CBUAE. (iv)
When establishing maximum remediation periods, institutions must take into account model types in order to mitigate Model Risk appropriately. For instance, defects related to market risk / pricing models should be remedied within weeks, while defect remediation for rating models could take longer. (v)
For each defect, a clear plan must be produced in order to reach timely remediation. Priority should be given to models with greater financial impacts. The validator should express its view on the timing and content of the plan, and the remediation plan should be approved by the Model Oversight Committee.
10.7.8
At the level of the institution, the timing for finding resolution is a reflection of the effectiveness of the validation process and the ability of the institution to manage Model Risk. This will be subject to particular attention from the CBUAE. Exceptions to the time frame defined by institutions must be formally approved by Senior Management upon robust justification and will be reviewed by the CBUAE as part of regular supervision.
Appendix
NUMERICAL THRESHOLDS INCLUDED IN THE MMS
The MMS contains several numerical thresholds.The following table indicates the relevant Articles to facilitate their implementation.
Table 3: Numerical thresholds included in the MMS
Article Topic Threshold Threshold 2.2.2 Self-assessment and plan to meet the MMS and MMG requirements 6 months from the effective date of the MMS Mandatory 4.6.3 Model Oversight Committee meeting Quarterly Mandatory 4.10.2 Reporting model life-cycle and associated Model Risk to the Model Oversight Committee and to the Board Quarterly and yearly, respectively Mandatory 8.6.2 and 8.6.3 Rating frequency Annually Mandatory 10.5.2 Reporting of monitoring & validation results to the Model Oversight Committee Quarterly Mandatory 10.5.2 Maximum periods of model validation and monitoring See table in the corresponding section Strongly recommended 10.7.5 Reporting of findings and remediation to Senior Management Quarterly and yearly, respectively Mandatory 10.7.7 Maximum remediation period for high severity findings 12 months Mandatory Model Management Guidance
Definitions and Interpretations
The following terms shall have the meaning assigned to them for the purpose of interpreting these Standards and the related Guidance:
1. Board: As defined in the CBUAE’s Corporate Governance Regulation for Banks. 2.
Causality (written in lower case as “causality”): Relationship between cause and effect. It is the influence of one event on the occurrence of another event. 3. CBUAE: Central Bank of the United Arab Emirates. 4.
Correlation (written in lower case as “correlation”): Any statistical relationship between two variables, without explicit causality explaining the observed joint behaviours. Several metrics exist to capture this relationship. Amongst others, linear correlations are often captured by the Pearson coefficient. Linear or non-linear correlation are often captured by the Spearman’s rank correlation coefficient. 5.
Correlation Analysis (written in lower case as “correlation analysis”): Correlation analysis refers to a process by which the relationships between variables are explored. For a given set of data and variables, observe (i) the statistical properties of each variable independently, (ii) the relationship between the dependent variable and each of the independent variables on a bilateral basis, and (iii) the relationship between the independent variables with each other. 6.
CI (Credit Index): In the context of credit modelling, a credit index is a quantity defined over (-∞,+∞) derived from observable default rates, for instance through probit transformation. CI represents a systemic driver of creditworthiness. While this index is synthetic, (an abstract driver), it is often assimilated to the creditworthiness of specific industry or geography. 7.
Default (written in lower case as “default”): The definition of default depends on the modelling context, either for the development of rating models or for the calibration and probabilities of default. For a comprehensive definition, refer to the section on rating models in the MMG. 8.
Deterministic Model (written in lower case as “deterministic model”): A deterministic model is a mathematical construction linking, with certainty, one or several dependent variables, to one or several independent variables. Deterministic models are different from statistical models. The concept of confidence interval does not apply to deterministic models. Examples of deterministic models include NPV models, financial cash flow models or exposure models for amortizing facilities. 9.
DMF (Data Management Framework): Set of policies, procedures and systems designed to organise and structure the management of data employed for modelling. 10.
DPD (Days-Past-Due): A payment is considered past due if it has not been made by its contractual due date. The days-past-due is the number of days that a payment is past its due date, i.e. the number of days for which a payment is late. 11.
DSIB (Domestic Systemically Important Banks): These are UAE banks deemed sufficiently large and interconnected to warrant the application of additional regulatory requirements. The identification of the institutions is based upon a framework defined by the CBUAE. 12.
EAD (Exposure At Default): Expected exposure of an institution towards an obligor (or a facility) upon a future default of this obligor (or its facility). It also refers to the observed exposure upon the realised default of an obligor (or a facility). This amount materialises at the default date and can be uncertain at reporting dates prior to the default date. The uncertainty surrounding EAD depends on the type of exposure and the possibility of future drawings. In the case of a lending facility with a pre-agreed amortisation schedule, the EAD is known. In the case of off-balance sheet exposures such as credit cards, guarantees, working capital facilities or derivatives, the EAD is not certain on the date of measurement and should be estimated with statistical models. 13. EAR (Earning At Risk): Refer to NII. 14.
ECL (Expected Credit Loss): Metric supporting the estimation of provisions under IFRS9 to cover credit risk arising from facilities and bonds in the banking book. It is designed as a probability-weighted expected loss. 15.
Economic Intuition (written in lower case as “economic intuition”): Also referred to as economic intuition and business sense. Property of a model and its output to be interpreted in terms and metrics that are commonly employed for business and risk decisions. It also refers to the property of the model variables and the model outputs to meet the intuition of experts and practitioners, in such a way that the model can be explained and used to support decision-making. 16.
Effective Challenge: Characteristic of a validation process. An effective model validation ensures that model defects are suitably identified, discussed and addressed in a timely fashion. Effectiveness is achieved via certain key features of the validation process such as independence, expertise, clear reporting and prompt action from the development team. 17.
EVE (Economic Value of Equity): It is defined as the difference between the present value of the institution’s assets minus the present value of liabilities. The EVE is sensitive to changes in interest rates. It is used in the measurement of interest rate risk in the banking book. 18.
Expert-Based Models (written in lower case as “expert-based models”): Also referred to as judgemental models, these models rely on the subjective judgement of expert individuals rather than on quantitative data. In particular, this type of model is used to issue subjective scores in order to rank corporate clients. 19.
Institutions (written in lower case as “institution(s)”): All banks licenced by the CBUAE. Entities that take deposits from individuals and/or corporations, while simultaneously issuing loans or capital market securities. 20.
LGD (Loss Given Default): Estimation of the potential loss incurred by a lending institution upon the default of an obligor (or a facility), measured as a percentage of the EAD. It also refers to the actual loss incurred upon past defaults also expressed as a percentage of EAD. The observed LGD levels tend to be related to PD levels with various strength of correlation. 21.
Limits and limitations (written in lower case as “limits” and “limitations”): Model limits are thresholds applied to a model’s outputs and/or its parameters in order to control its performance. Model limitations are boundary conditions beyond which the model ceases to be accurate. 22.
LSI (Large and/or Sophisticated Institutions): This group comprises DSIBs and any other institutions that are deemed large and/or with mature processes and skills. This categorisation is defined dynamically based on the outcome of regular banking supervision. 23.
Macroeconomic Model (written in lower case as “macroeconomic model” or “macro model”): Refers to two types of models. (i) A model that links a set of independent macro variables to another single dependent macro variable or to several other dependent macro variables or (ii) a model that links a set of independent macro variables to a risk metric (or a set of risk metrics) such as probabilities of default or any other business metric such as revenues. 24.
Market Data: Refers to the various data attributes of a traded financial instrument reported by a trading exchange. It includes the quoted value of the instrument and/or the quoted parameters of that instrument that allow the derivation of its value. It also includes transaction information including the volume exchanged and the bid-ask spread. 25.
Materiality: The materiality of a model represents the financial scope covered by the model in the context of a given institution. It can be used to estimate the potential loss arising from model uncertainty (see Model Risk). Model materiality can be captured by various metrics depending on model types. Typically, total exposure can be used as a metric for credit models. 26. MMG: CBUAE’s Model Management Guidance. 27. MMS: CBUAE’s Model Management Standards. 28.
Model (written in lower case as “model”): A quantitative method, system, or approach that applies statistical, economic, financial, or mathematical theories, techniques, and assumptions to process input data into quantitative estimates. For the purpose of the MMS and MSG, models are categorised in to three distinct groups: statistical models, deterministic models and expert-based models. 29.
Model Calibration (written in lower case as “model calibration”): Key step of the model development process. Model calibration means changing the values of the parameters and/or the weights of a model, without changing the structure of the model, i.e. without changing the nature of the variables and their transformations. 30.
Model Complexity (written in lower case as “model complexity”): Overall characteristic of a model reflecting the degree of ease (versus difficulty) with which one can understand the model conceptual framework, its practical design, calibration and usage. Amongst other things, such complexity is driven by, the number of inputs, the interactions between variables, the dependency with other models, the model mathematical concepts and their implementation. 31.
Model Construction (written in lower case as “model construction”): Key step of the model development process. The construction of a model depends on its nature, i.e. statistical or deterministic. For the purpose of the MMS and the MMG, model construction means the following: for statistical models, for a given methodology and a set of data and transformed variables, it means estimating and choosing, with a degree of confidence, the number and nature of the dependent variables along with their associated weights or coefficients. For deterministic models, for a given methodology, it means establishing the relationship between a set of input variables and an output variable, without statistical confidence intervals. 32. Model Development (written in lower case as “model development”): Means creating a model by making a set of sequential and recursive decisions according to the steps outlined in the dedicated sections of the MMS. Model re-development means conducting the model development steps again with the intention to replace an existing model. The replacement may, or may not, occur upon re-development. 33.
Modelling Decision (written in lower case as “modelling decision”): A modelling decision is a deliberate choice that determines the core functionality and output of a model. Modelling decisions relate to each of the steps of the data acquisition, the development and the implementation phase. In particular, modelling decisions relate to (i) the choice of data, (ii) the analysis of data and sampling techniques, (iii) the methodology, (iv) the calibration and (v) the implementation of models. Some modelling decisions are more material than others. Key modelling decisions refer to decisions with strategic implications and/or with material consequences on the model outputs. 34.
Model Risk: Potential loss faced by institutions from making decisions based on inaccurate or erroneous outputs of models due to errors in the development, the implementation or the inappropriate usage of such models. Losses incurred from Model Risk should be understood in the broad sense as Model Risk has multiple sources. This definition includes direct quantifiable financial loss but also any adverse consequences on the ability of the institution to conduct its activities as originally intended, such as reputational damage, opportunity costs or underestimation of capital. In the context of the MMS and the MMG, Model Risk for a given model should be regarded as the combination of its materiality and the uncertainty surrounding its results. 35.
Model Selection (written in lower case as “model selection”): This step is part of the development process. This means choosing a specific model amongst a pool of available models, each with a different set of variables and parameters. 36.
Model Uncertainty (written in lower case as “model uncertainty”): This refers to the uncertainty surrounding the results generated by a model. Such uncertainty can be quantified as a confidence interval around the model output values. It is used as a component to estimate Model Risk. 37.
Multivariate Analysis (written in lower case as “multivariate analysis”): For a given set of data and variables, this is a process of observing the joint distribution of the dependent and independent variables together and drawing conclusions regarding their degree of correlation and causality. 38.
NII (Net Interest Income): To simplify notations, both Net Interest Income (for conventional products) and/or Net Profit Income (for Islamic Products) are referred to as “NII”. In this context, ‘profit’ is assimilated as interest. It is defined as the difference between total interest income and total interest expense, over a specific time horizon and taking into account hedging. The change in NII (“∆NII”) is defined as the difference between the NII estimated with stressed interest rates under various scenarios, minus the NII estimated with the interest rates as of the portfolio reporting date. ∆NII is also referred to as earnings at risk (“EAR”). 39.
NPV (Net Present Value): Present value of future cash flows minus the initial investment, i.e. the amount that a rational investor is willing to pay today in exchange for receiving these cash flows in the future. NPV is estimated through a discounting method. It is commonly used to estimate various metrics for the purpose of financial accounting, risk management and business decisions. 40.
PD (Probability of Default): Probability that an obligor fails to meet its contractual obligation under the terms of an agreed financing contract. Such probability is computed over a given horizon, typically 12 months, in which case it is referred to as a 1-year PD. It can also be computed over longer horizons. This probability can also be defined at several levels of granularity, including, but not limited to, single facility, pool of facilities, obligor, or consolidated group level. 41.
PD Model (written as “PD model”): This terminology refers to a wide variety of models with several objectives. Amongst other things, these models include mapping methods from scores generated by rating models onto probability of defaults. They also include models employed to estimate the PD or the PD term structure of facilities, clients or pool of clients. 42.
PD Term Structure (written as “PD term structure”): Refers to the probability of default over several time horizons, for instance 2 years, 5 years or 10 years. A distinction is made between the cumulative PD and the marginal PD. The cumulative PD is the total probability of default of the obligor over a given horizon. The marginal PD is the probability of default between two dates in the future, provided that the obligor has survived until the first date. 43.
PIT (Point-In-Time) and TTC (Through-The-Cycle): A point-in-time assessment refers to the value of a metric (typically PD or LGD) that incorporates the current economic conditions. This contrasts with a through-the-cycle assessment that refers to the value of the same metric across a period covering one or several economic cycles. 44.
Qualitative validation: A review of model conceptual soundness, design, documentation, and development and implementation process. 45.
Quantitative validation: A review of model numerical output, covering at least its accuracy, degree of conservatism, stability, robustness and sensitivity. 46.
Rating/Scoring (written in lower case “rating or scoring”): For the purpose of the MMS and the MMG, a rating and a score are considered as the same concept, i.e. an ordinal quantity representing the relative creditworthiness of an obligor (or a facility) on a predefined scale. ‘Ratings’ are commonly used in the context of corporate assessments whilst ‘scores’ are used for retail client assessments. 47.
Restructuring (written in lower case “restructuring”): The definition of restructuring / rescheduling used for modelling in the context of the MMS and MMG should be understood as the definition provided in the dedicated CBUAE regulation and, in particular, in the Circular 28/2010 on the classification of loans, with subsequent amendments to this Circular and any new CBUAE regulation on this topic. 48.
Rating Model (written in lower case “rating model”): The objective of such model is to discriminate ex-ante between performing clients and potentially non-performing clients. Such models generally produce a score along an arbitrary scale reflecting client creditworthiness. This score can subsequently mapped to a probability of default. However, rating models should not be confused with PD models. 49.
Retail Clients (written in lower case as “retail clients”): Retail clients refer to individuals to whom credit facilities are granted for the following purpose: personal consumer credit facilities, auto credit facilities, overdraft and credit cards, refinanced government housing credit facilities, other housing credit facilities, credit facilities against shares to individuals. It also includes small business credit facilities for which the credit risk is managed using similar methods as applied for personal credit facilities. 50.
Segment (written in lower case as “segment”): Subsets of an institution’s portfolio obtained by splitting the portfolio by the most relevant dimensions which explain its risk profile. Typical dimensions include obligor size, industries, geographies, ratings, product types, tenor and currency of exposure. Segmentation choices are key drivers of modelling accuracy and robustness. 51. Senior Management: As defined in the CBUAE’s Corporate Governance Regulation for Banks. 52.
Statistical Model (written in lower case as “statistical model”): A statistical model is a mathematical construction achieved by the application of statistical techniques to samples of data. The model links one or several dependent variables to one or several independent variables. The objective of such a model is to predict, with a confidence interval, the values of the dependent variables given certain values of the independent variables. Examples of statistical models include rating models or value-at-risk (VaR) models. Statistical models are different from deterministic models. By construction, statistical models always include a degree of Model Risk. 53. Tiers: Models are allocated to different groups, or Tiers, depending on their associated Model Risk. 54.
Time series analysis (written in lower case as “time series analysis”): For a given set of data and variables, this is a process of observing the behaviour of these variables through time. This can be done by considering each variable individually or by considering the joint pattern of the variables together. 55.
UAT (User Acceptance Testing): Phase of the implementation process during which users rigorously test the functionalities, robustness, accuracy and reliability of a system containing a new model before releasing it into production. 56.
Variable Transformation (written in lower case as “variable transformation”): Step of the modelling process involving a transformation of the model inputs before developing a model. Amongst others, common transformations include (i) relative or absolute differencing between variables, (ii) logarithmic scaling, (iii) relative or absolute time change, (iv) ranking, (v) lagging, and (vi) logistic or probit transformation. 57.
Wholesale Clients (written in lower case as “wholesale clients”): Wholesale clients refer to any client that is not considered as a retail client as per the definition of these Standards.
1 Context and Objective
1.1 Regulatory Context
1.1.1
The Risk Management Regulation (Circular No. 153/2018) issued by the Central Bank of the UAE (“CBUAE”) on 27th May 2018 states that banks must have robust systems and tools to assess and measure risks.
1.1.2
To set out modelling requirements for licenced banks, the CBUAE has issued Model Management Standards (“MMS”) and Model Management Guidance (“MMG”). Both MMS and MMG should be read jointly as they constitute a consistent set of requirements and guidance, as follows:
(i)
The MMS outline general standards applicable to all models and constitute minimum requirements that must be met by UAE banks.
(ii)
The MMG expands on technical aspects that are expected to be implemented by UAE banks for certain types of models. Given the wide range of models and the complexity of some, the CBUAE recognises that alternative approaches can be envisaged on specific technical points. Whilst this MMG neither constitutes additional legislation or regulation nor replaces or supersedes any legal or regulatory requirements or statutory obligations, deviations from the MMG should be clearly justified and will be subject to CBUAE supervisory review.
1.2 Objectives
1.2.1
Both the MMS and MMG share three key objectives. The first objective is to ensure that models employed by UAE banks meet quality standards to adequately support decision-making and reduce Model Risk. The second objective is to improve the homogeneity of model management across UAE banks. The third objective is to mitigate the risk of potential underestimation of provisions and capital across UAE banks.
1.2.2
The MMG outlines techniques based on commonly accepted practices by practitioners and academics, internationally. The majority of its content has been subject to consultation with numerous subject matter experts in the UAE and therefore it also reflects expected practices amongst UAE institutions.
1.3 Document Structure
1.3.1
Each section of the MMG addresses a different type of model. The MMG is constructed in such a way that the numbering of each article is sequentially and each article is a unique reference across the entire MMG.
1.3.2
Both the MMS and the MMG contain an appendix summarising the main numerical limits included throughout each document respectively. Such summary is expected to ease the implementation and monitoring of these limits by both institution and the CBUAE.
1.4 Scope of Application
1.4.1
The MMG applies to all licensed banks in the UAE, which are referred to herein as “institutions”.
1.4.2
The scope of institutions is consistent across the MMS and the MMG. Details about the scope of institutions are available in the MMS.
1.4.3
Branches or subsidiaries of foreign institutions should apply the most conservative practices between the MMG and the expectations from their parent company’s regulator.
1.4.4
Institutions with a parent company incorporated in the UAE should ensure that all their branches and subsidiaries comply with the MMG.
1.5 Requirements and Timeframe
1.5.1
The implementation timeframe is consistent across the MMS and the MMG. Further details are available in the MMS.
1.6 Scope of Models
1.6.1
The MMG focuses on the main credit risk models entering the computation of the Expected Credit Loss in the context of the current accounting requirements, due to their materiality and their relevance across the vast majority of institutions. The MMG also provides guidance on other models used for the assessment of interest rate risk in the banking book and net present values.
1.6.2
The MMG does not impose the use of these models. The MMG outlines minimum expected practices if institutions decide to use such models, in order to manage Model Risk appropriately.
1.6.3
As model management matures across UAE institutions, additional model types may be included in the scope of the MMG in subsequent publications.
Table 1: List of model types covered in the MMG
Model type covered in the MMG Rating Models PD Models LGD Models Macro Models Interest Rate Risk In the Banking Book Models Net Present Value Models 2 Rating Models
2.1 Scope
2.1.1
The vast majority of institutions employ rating models to assess the credit worthiness of their obligors. Rating models provide essential metrics used as foundations to multiple core processes within institutions. Ratings have implications for key decisions, including but not limited to, risk management, provisioning, pricing, capital allocation and Pillar II capital assessment. Institutions should pay particular attention to the quality of their rating models and subsequent PD models, presented in the next section.
2.1.2
Inadequate rating models can result in material financial impacts due to a potentially incorrect estimation of credit risk. The CBUAE will pay particular attention to suitability of the design and calibration of rating and PD models. Rating models that are continuously underperforming even after several recalibrations should be replaced. These models should no longer be used for decision making and reporting.
2.1.3
For the purpose of the MMG, a rating and a score should be considered as identical concepts, that is a numerical quantity without units representing the relative creditworthiness of an obligor or a facility on predefined scale. The main objective of rating models is to segregate obligors (or facilities) that are likely to perform under their current contractual obligations from the ones that are unlikely to perform, given a set of information available at the rating assessment date.
2.1.4
The construction of rating models is well documented by practitioners and in academic literature. Therefore, it is not the objective of this section to elaborate on the details of modelling techniques. Rather, this section focuses on minimum expected practices and the challenging points that should attract institutions’ attention.
2.2 Governance and Strategy
2.2.1
The management of rating models should follow all the steps of the model life-cycle articulated in the MMS. The concept of model ownership and independent validation is particularly relevant to rating models due to their direct business implications.
2.2.2
It is highly recommended that institutions develop rating models internally based on their own data. However, in certain circumstances such as for low default portfolios, institutions may rely on the support from third party providers. This support can take several forms that are presented below through simplified categorisation. In all cases, the management and calibration of models should remain the responsibility of institutions. Consequently, institutions should define, articulate and justify their preferred type of modelling strategy surrounding rating models. This strategy will have material implications on the quality, accuracy and reliability of the outputs.
2.2.3
The choice of strategy has a material impact on the methodology employed. Under all circumstances, institutions remain accountable for the modelling choices embedded in their rating models and their respective calibrations.
2.2.4
Various combinations of third party contributions exist. These can be articulated around the supplier’s contribution to the model development, the IT system solution and/or the data for the purpose of calibration. Simplified categories are presented hereby, for the purpose of establishing minimum expected practices:
(i)
Type 1 – Support for modelling: A third party consultant is employed to build a rating model based on the institution’s own data. The IT infrastructure is fully developed internally. In this case, institutions should work in conjunction with consultants to ensure that sufficient modelling knowledge is retained internally. Institutions should ensure that the modelling process and the documentation are compliant with the principles articulated in the MMS. (ii)
Type 2 – Support for modelling and infrastructure: A third party consultant provides a model embedded in a software that is calibrated based on the institution’s data. In this case, the institution has less control over the design of the rating model. The constraints of such approach are as follows:
a.
Institutions should ensure that they understand the modelling approach being provided to them. b.
Institutions should fully assess the risks related to using a system solution provided by external parties. At a minimum, this assessment should be made in terms of performance, system security and stability. c.
Institutions should ensure that a comprehensive set of data is archived in order to perform validations once the model is implemented. This data should cover both the financial and non-financial characteristics of obligors and the performance data generated by the model. The data should be stored at a granular level, i.e. at a factor level, in order to fully assess the performance of the model.
(iii)
Type 3 – Support of modelling, infrastructure and data: In addition to Type 2 support, a third party consultant provides data and/or a ready-made calibration. This is the weakest form of control by institutions. For such models, the institution should demonstrate that additional control and validation are implemented in order to reduce Model Risk. Immediately after the model implementation, the institution should start collecting internal data (where possible) to support the validation process. Such validation could result in a material shift in obligors’ rating and lead to financial implications. (iv)
Type 4 – Various supports: In the case of various supports, the minimum expected practices are as follows:
a.
If a third party provides modelling services, institutions should ensure that sufficient knowledge is retained internally. b.
If a third party provides software solutions, institutions should ensure that they have sufficient controls over parameters and that they archive data appropriately. c.
If a third party provides data for calibration, institutions should take the necessary steps to collect internal data in accordance with the data management framework articulated in the MMS.
2.2.5
In conjunction with the choice of modelling strategy, institutions should also articulate their modelling method of rating models. A range of possible approaches can be envisaged between two distinct categories: (i) data-driven statistical models that can rely on both quantitative and qualitative (subjective) factors, or (ii) expert-based models that rely only on views from experienced individuals without the use of statistical data. Between these two categories, a range of options exist. Institutions should consciously articulate the rationale for their modelling approach.
2.2.6
Institutions should aim to avoid purely expert based models, i.e. models with no data inputs. Purely expert-based models should be regarded as the weakest form of models and therefore should be seen as the least preferable option. If the portfolio rated by such a model represents more than 10% of the institution’s loan book (other than facilities granted to governments and financial institutions), then the institution should demonstrate that additional control and validation are implemented in order to reduce Model Risk. It should also ensure that Senior Management and the Board are aware of the uncertainty arising from such model. Immediately after the model implementation, the institution should start collecting internal data to support the validation process.
2.3 Data Collection and Analysis
2.3.1
Institutions should manage and collect data for rating models, in compliance with the MMS. The data collection, cleaning and filtering should be fully documented in such way that it can be traced by any third party.
2.3.2
A rigorous process for data collection is expected. The type of support strategy presented in earlier sections has no implications on the need to collect data for modelling and validation.
2.3.3
For the development of rating models, the data set should include, at a minimum, (i) the characteristics of the obligors and (ii) their performance, i.e. whether they were flagged as default. For each rating model, the number of default events included in the data sample should be sufficiently large to permit the development of a robust model. This minimum number of defaults will depend on business segments and institutions should demonstrate that this minimum number is adequate. If the number of defaults is too small, alternative approaches should be considered.
2.3.4
At a minimum, institutions should ensure that the following components of the data management process are documented. These components should be included in the scope of validation of rating models.
(i) Analysis of data sources, (ii) Time period covered, (iii) Descriptive statistics about the extracted data, (iv) Performing and non-performing exposures, (v) Quality of the financial statements collected, (vi) Lag of financial statements, (vii) Exclusions and filters, and (viii)
Final number of performing and defaulted obligors by period.
2.4 Segmentation
2.4.1
Segmentation means splitting a statistical sample into several groups in order to improve the accuracy of modelling. This concept applies to any population of products or customers. The choice of portfolio, customer and/or product segmentation has a material impact on the quality of rating models. Generally, the behavioural characteristics of obligors and associated default rates depend on their industry and size (for wholesale portfolios) and on product types (for retail portfolios). Consequently, institutions should thoroughly justify the segmentation of their rating models as part of the development process.
2.4.2
The characteristics of obligors and/or products should be homogeneous within each segment in order to build appropriate models. First, institutions should analyse the representativeness of the data and pay particular attention to the consistency of obligor characteristics, industry, size and lending standards. The existence of material industry bias in data samples should result in the creation of a rating model specific to that industry. Second, the obligor sample size should be sufficient to meet minimum statistical performance. Third, definition of default employed to identify default events should also be homogeneous across the data sample.
2.5 Default Definition
2.5.1
Institutions should define and document two definitions of default, employed in two different contexts: (i) for the purpose of rating model development and (ii) for the purpose of estimating and calibrating probabilities of defaults. These two definitions of default can be identical or different, if necessary. The scope of these definitions should cover all credit facilities and all business segments of the institution. In this process, institutions should apply the following principles.
2.5.2
For rating models: The definition of default in the context of a rating model is a choice made to achieve a meaningful discrimination between performing and non-performing obligors (or facilities). The terminology ‘good’ and ‘bad’ obligors is sometimes employed by practitioners in the context of this discrimination. Institutions should define explicitly the definition of default used as the dependent variable when building their rating models.
(i)
This choice should be guided by modelling considerations, not by accounting considerations. The level of conservatism embedded in the definition of default used to develop rating models has no direct impact on the institution’s P&L. It simply supports a better identification of customers unlikely to perform. (ii)
Consequently, institutions can choose amongst several criteria to identify default events in order to maximise the discriminatory power of their rating models. This choice should be made within boundaries. At a minimum, they should rely on the concept of days-past-due (“DPD”). An obligor should be considered in default if its DPD since the last payment due is greater or equal to 90 or if it is identified as defaulted by the risk management function of the institution. (iii)
If deemed necessary, institutions can use more conservative DPD thresholds in order to increase the predictive power of rating models. For low default portfolios, institutions are encouraged to use lower thresholds, such as 60 days in order to capture more default events. In certain circumstances, restructuring events can also be included to test the power of the model to identify early credit events.
2.5.3
For PD estimation: The definition of default in the context of PD estimation has direct financial implications through provisions, capital assessment and pricing.
(i)
This choice should be guided by accounting and regulatory principles. The objective is to define this event in such a way that it reflects the cost borne by institutions upon the default of an obligor. (ii)
For that purpose, institutions should employ the definition of default articulated in the CBUAE credit risk regulation, separately from the MMS and MMG. As the regulation evolves, institutions should update the definition employed for modelling and recalibrate their models.
2.6 Rating Scale
2.6.1
Rating models generally produce an ordinal indicator on a predefined scale representing creditworthiness. The scores produced by each models should be mapped to a fixed internal rating scale employed across all aspects of credit risk management, in particular for portfolio management, provision estimation and capital assessment. The rating scale should be the result of explicit choices that should be made as part of the model governance framework outlined in the MMS. At a minimum, the institution’s master rating scale should comply with the below principles:
(i)
The granularity of the scale should be carefully defined in order to support credit risk management appropriately. An appropriate balance should be found regarding the number of grades. A number of buckets that is too small will reduce the accuracy of decision making. A number of buckets that is too large will provide a false sense of accuracy and could be difficult to use for modelling. (ii)
Institutions should ensure that the distribution of obligors (or exposures) spans across most rating buckets. High concentration in specific grades should be avoided, or conversely the usage of too many grades with no obligors should also be avoided. Consequently, institution may need to redefine their rating grades differently from rating agencies’ grades, by expanding or grouping certain grades. (iii)
The number of buckets should be chosen in such a way that the obligors’ probability of default in each grade can be robustly estimated (as per the next section on PD models). (iv)
The rating scale from external rating agencies may be used as a benchmark, however their granularity may not be the most appropriate for a given institution. Institutions with a large proportion of their portfolio in non-investment grade rating buckets should pay particular attention to bucketing choices. They are likely to require more granular buckets in this portion of the scale to assess their risk more precisely than with standard scales from rating agencies. (v)
The choice of an institution’s rating scale should be substantiated and documented. The suitability of rating scale should be assessed on a regular basis as part of model validation.
2.7 Model Construction
2.7.1
The objective of this section is to draw attention to the key challenges and minimum expected practices to ensure that institutions develop effective rating models. The development of retail scorecards is a standardised process that all institutions are expected to understand and implement appropriately on large amounts of data. Wholesale rating models tend to be more challenging due to smaller population sizes and the complexity of the factors driving defaults. Consequently, this section related to model construction focuses on wholesale rating models.
2.7.2
Wholesale rating models should incorporate, at a minimum, financial information and qualitative inputs. The development process should include a univariate analysis and a multivariate analysis, both fully documented. All models should be constructed based on a development sample and tested on a separate validation sample. If this is not possible in the case of data scarcity, the approach should be justified and approved by the validator.
2.7.3
Quantitative factors: These are characteristics of the obligors that can be assessed quantitatively, most of which are financial variables. For wholesale rating models, institutions should ensure that the creation of financial ratios and subsequent variable transformations are rigorously performed and clearly documented. The financial variables should be designed to capture the risk profile of obligors and their associated financing. For instance, the following categories of financial ratios are commonly used to assess the risk of corporate lending: operating performance, operating efficiency, liquidity, capital structure, and debt service.
2.7.4
Qualitative subjective factors: These are characteristics of the obligor that are not easily assessed quantitatively, for instance the experience of management or the dependency of the obligors on its suppliers. The following categories of subjective factors are commonly used to assess the risk of corporate lending: industry performance, business characteristics and performance, management character and experience, and quality of financial reporting and reliability of auditors. The assessment of these factors is generally achieved via bucketing that relies on experts’ judgement. When using such qualitative factors, the following principles should apply:
(i)
Institutions should ensure that this assessment is based upon a rigorous governance process. The collection of opinions and views from experienced credit officers should be treated as a formal data collection process. The data should be subject to quality control. Erroneous data points should also be removed. (ii)
If the qualitative subjective factors are employed to adjust the outcome of the quantitative factors, institutions should control and limit this adjustment. Institutions should demonstrate that the weights given to the expert-judgement section of the model is appropriate. Institutions should not perform undue rating overrides with expert judgement.
2.7.5
Univariate analysis: In the context of rating model development, this step involves assessing the discriminatory power of each quantitative factor independently and assessing the degree of correlation between these quantitative factors.
(i)
The assessment of the discriminatory power should rely on clearly defined metrics, such as the accuracy ratio (or Gini coefficient). Variables that display no relationship or counterintuitive relationships with default rates should preferably be excluded. They can be included in the model only after a rigorous documentation of the rationale supporting their inclusion. (ii)
Univariate analysis should also involve an estimation of the correlations between the quantitative factors with the aim to avoid multicolinearity in the next step of the development. (iii)
The factors should be ranked according to their discriminatory power. The development team should comment on whether the observed relationship is meeting economic and business expectations.
2.7.6
Multivariate analysis: This step involves establishing a link between observed defaults and the most powerful factors identified during the univariate analysis.
(i)
Common modelling techniques include, amongst others, logistic regressions and neural networks. Institutions can chose amongst several methodologies, provided that the approach is fully understood and documented internally. This is particularly relevant if third party consultants are involved. (ii)
Institutions should articulate clearly the modelling technique employed and the process of model selection. When constructing and choosing the most appropriate model, institutions should pay attention to the following:
(a)
The number of variables in the model should be chosen to ensure a right balance. An insufficient number of variables can lead to a sub-optimal model with a weak discriminatory power. An excessive number of variables can lead to overfitting during the development phase, which will result in weak performance subsequently. (b)
The variables should not be too correlated. Each financial ratio should preferably be different in substance. If similar ratios are included, a justification should be provided and overfitting should be avoided. (c)
In the case of bucketing of financial ratios, the defined cut-offs should be based on relevant peer comparisons supported by data analysis, not arbitrarily decided.
2.8 Model Documentation
2.8.1
Rigorous documentation should be produced for each rating model as explained in the MMS. The documentation should be sufficiently detailed to ensure that the model can be fully understood and validated by any independent party.
2.8.2
In addition to the elements articulated in the MMS, the following components should be included:
(i)
Dates: The model development date and implementation date should be explicitly mentioned in all rating model documentation. (ii)
Materiality: The model materiality should be quantified, for instance as the number of rated customers and their total corresponding gross exposure. (iii)
Overview: An executive summary with the model rating strategy, the expected usage, an overview of the model structure and the data set employed to develop and test the model. (iv)
Key modelling choices: The default definition, the rating scale and a justification of the chosen segmentation as explained in earlier sections. (v)
Data: A description of the data employed for development and testing, covering the data sources and the time span covered. The cleaning process should be explained including the filter waterfall and/or any other adjustments used. (vi)
Methodology: The development approach covering the modelling choices, the assumptions, limits, the parameter estimation technique. Univariate and multivariate analyses discussing in detail the construction of factors, their transformation and their selection. (vii)
Expert judgement inputs: All choices supporting the qualitative factors. Any adjustments made to the variables or the model based on expert opinions. Any contributions from consulted parties. (viii)
Validation: Details of testing and validation performed during the development phase or immediately after.
2.9 Usage of Rating Models
2.9.1
Upon the roll-out of a new rating model and/or a newly recalibrated (optimised) rating model, institutions should update client ratings as soon as possible. Institutions should assign new ratings with the new model to 70% of the existing obligors (entering the model scope) within six (6) months and to 95% of the existing obligors within nine (9) months. The assignment of new ratings should be based on financials that have been updated since the issuance of the previous rating, if they exist. Otherwise prior financials should be used. This expectation applies to wholesale and retail models.
2.9.2
In order to achieve this client re-rating exercise in a short timeframe, institutions are expected to rate clients in batches, performed by a team of rating experts, independently from actual, potential or perceived business line interests.
2.9.3
Institutions should put in place a process to monitor the usage of rating models. At a minimum, they should demonstrate that the following principles are met:
(i)
All ratings should be archived with a date that reflects the last rating update. This data should be stored in a secure database destined to be employed on a regular basis to manage the usage of rating models. (ii)
The frequency of rating assignment should be tracked and reported to ensure that all obligors are rated appropriately in a timely fashion. (iii)
Each rating model should be employed on the appropriate type of obligor defined in the model documentation. For instance, a model designed to assess large corporates should not be used to assess small enterprises. (iv)
Institutions should ensure that the individuals assigning and reviewing ratings are suitably trained and can demonstrate a robust understanding of the rating models. (v)
If the ratings are assigned by the business lines, these should be reviewed and independently signed-off by the credit department to ensure that the estimation of ratings is unbiased from short term potential or perceived business line interests.
2.10 Rating Override
2.10.1
In the context of the MMG, rating override means rating upgrade or rating downgrade. Overrides are permitted; however, they should follow a rigorously documented process. This process should include a clear governance mirroring the credit approval process based on obligor type and exposure materiality. The decision to override should be controlled by limits expressed in terms of number of notches and number of times a rating can be overridden. Eligibility criteria and the causes for override should be clearly documented. Causes may include, amongst others: (i) events specific to an obligor, (ii) systemic events in a given industry or region, and/or (iii) changes of a variable that is not included in the model.
2.10.2
Rating overrides should be monitored and be included in the model validation process. The validator should estimate the frequency of overrides and the number of notches between the modelled rating and the new rating. A convenient approach to monitor overrides is to produce an override matrix.
2.10.3
In some circumstances, the rating of a foreign obligor should not be better than the rating of its country of incorporation. Such override decision should be justified and documented.
2.10.4
A contractual guarantee of a parent company can potentially result in the rating enhancement of an obligor, but conditions apply:
(i)
The treatment of parental support for a rating enhancement should be recognised only based on the production of an independent legal opinion confirming the enforceability of the guarantee upon default. The rating enhancement should only apply to the specific facility benefiting from the guarantee. The process for rating enhancement should be clearly documented. For the avoidance of doubt, a sole letter of intent from the parent company should not be considered as a guarantee for enforceability purpose. A formal legal guarantee is the only acceptable documentation. (ii)
For modelling purpose, an eligible parent guarantee can be reflected in the PD or the LGD of the facility benefiting from this guarantee. If the rating of the facility is enhanced, then the guarantee will logically be reflected in the PD parameter. If the rating of the obligor is not enhanced but the guarantee is deed eligible, then the guarantee can be reflected in the LGD parameter. The rationale behind such choice should be fully documented.
2.11 Monitoring and Validation
2.11.1
Institutions should demonstrate that their rating models are performing over time. All rating models should be monitored on a regular basis and independently validated according to all the principles articulated in the MMS. For that purpose, institutions should establish a list of metrics to estimate the performance and stability of models and compare these metrics against pre-defined limits.
2.11.2
The choice of metrics to validate rating models should be made carefully. These metrics should be sufficiently granular and capture performance through time. It is highly recommended to estimate the change in the model discriminatory power through time, for instance by considering a maximum acceptable drop in accuracy ratio.
2.11.3
In addition to the requirement articulated in the MMS related to the validation step, for rating models in particular, institutions should ensure that validation exercises include the following components:
(i)
Development data: A review of the data collection and filtering process performed during the development phase and/or the last recalibration. In particular, this should cover the definition of default and data quality. (ii)
Model usage: A review of the governance surrounding model usage. In particular, the validator should comment on (a) the frequency of rating issuance, (b) the governance of rating production, and (c) the variability of ratings produced by the model. The validator should also liaise with the credit department to form a view on (d) the quality of financial inputs and (e) the consistency of the subjective inputs and the presence of potential bias. (iii)
Rating override: A review of rating overrides. This point does not apply to newly developed models. (iv)
Model design: A description of the model design and its mathematical formulation. A view on the appropriateness of the design, the choice of factors and their transformations. (v)
Key assumptions: A review of the appropriateness of the key assumptions, including the default definition, the segmentation and the rating scale employed when developing the model. (vi) Validation data: The description of the data set employed for validation. (vii)
Quantitative review: An analysis of the key quantitative indicators covering, at a minimum, the model stability, discriminatory power, sensitivity and calibration. This analysis should cover the predictive power of each quantitative and subjective factor driving the rating. (viii)
Documentation: A review on the quality of the documentation surrounding the development phase and the modelling decisions. (ix)
Suggestions: When deemed appropriate, the validator can make suggestions for defect remediation to be considered by the development team.
3 PD Models
3.1 Scope
3.1.1
The majority of institutions employ models to estimate the probability of default of their obligors (or facilities), for risk management purpose and to comply with accounting and regulatory requirements. These models are generally referred to as ‘PD models’, although this broad definition covers several types of models. For the purpose of the MMG, and to ensure appropriate model management, the following components should be considered as separate models:
(i) Rating-to-PD mapping models, and (ii)
Point-in-Time PD Term Structure models.
3.1.2
These models have implications for key decisions including, but not limited to, risk management, provisioning, pricing, capital allocation and Pillar II capital assessment. Institutions should manage these models through a complete life-cycle process in line with the requirements articulated in the MMS. In particular, the development, ownership and validation process should be clearly organised and documented.
3.2 Key Definitions and Interpretations
3.2.1
The following definitions are complementing the definitions provided at the beginning of the MMG. The probability of default of a borrower or of a facility is noted “PD”. The loss proportion of exposure arising after default, or “loss given default” is noted “LGD”.
3.2.2
A point-in-time assessment (“PIT”) refers to the value of a metric (typically PD or LGD) that incorporates the current economic conditions. This contrasts with a through-the-cycle assessment (“TTC”) that refers to the value of the same metric across a period covering one or several economic cycles.
3.2.3
A PD is associated with a specific time horizon, which means that the probability of default is computed over a given period. A 1-year PD refers to the PD over a one year period, starting today or at any point in the future. A PD Term Structure refers to a cumulative PD over several years (generally starting at the portfolio estimation date). This contrasts with a marginal forward 1-year PD, which refers to a PD starting at some point in the future and covering a one year period, provided that the obligor has survived until that point.
3.2.4
A rating transition matrix is a square matrix that gives the probabilities to migrate from a rating to another rating. This probability is expressed over a specific time horizon, typically one year, in which case we refer to a ‘one-year transition matrix’. Transitions can also be expressed over several years.
3.3 Default Rate Estimation
3.3.1
Prior to engaging in modelling, institutions should implement a robust process to compute time series of historical default rates, for all portfolios where data is available. The results should be transparent and documented. This process should be governed and approved by the Model Oversight Committee. Once estimated, historical default rates time series should only be subject to minimal changes. Any retroactive updates should be approved by the Model Oversight Committee and by the bank’s risk management committee.
3.3.2
Institutions should estimate default rates at several levels of granularity: (i) for each portfolio, defined by obligor type or product, and (ii) for each rating grade within each portfolio, where possible. In certain circumstances, default rate estimation at rating grade level may not be possible and institutions may only rely on pool level estimation. In this case, institutions should justify their approach by demonstrating clear evidence based on data, that grade level estimation is not deemed sufficiently robust.
3.3.3
Institutions should compute the following default ratio, based on the default definition described in the previous section. This ratio should be computed with an observation window of 12 months to ensure comparability across portfolios and institutions. In addition, institutions are free estimate this ratio for other windows (e.g. quarterly) for specific modelling purposes.
(i)
The denominator is composed of performing obligors with any credit obligation, including off and on balance sheet facilities, at the start of the observation window. (ii) The numerator is composed of obligors that defaulted at least once during the observation window, on the same scope of facilities.
Formally the default rate can be expressed as shown by the formula below, where t represented the date of estimation. Notice that if the ratio is reported at time t, then the ratio is expressed as a backward looking metrics. This concept is particularly relevant for the construction of macro models as presented in subsequent sections. The frequency of computation should be at least quarterly and possibly monthly for some portfolios.
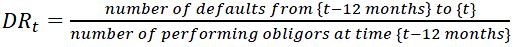
3.3.4
When the default rate is computed by rating grade, the denominator should refer to all performing obligors assigned to a rating grade at the beginning of the observation window. When the default rate is computed at segment level, the denominator should refer to all performing obligors assigned to that segment at the beginning of the observation window.
3.3.5
For wholesale portfolios, this ratio should be computed in order to obtain quarterly observations over long time periods covering one or several economic cycles. For wholesale portfolios, institutions should aim to gather at least 5 years of data, and preferably longer. For retail portfolios or for portfolios with frequent changes in product offerings, the period covered may be shorter, but justification should be provided.
3.3.6
Institutions should ensure that default time series are homogeneous and consistent through time, i.e. relate to a portfolio with similar characteristics, consistent lending standards and consistent definition of default. Adjustments may be necessary to build time series representative of the institution current portfolios. Particular attention should be given to changes in the institution’s business model through time. This is relevant is the case of rapidly growing portfolios or, conversely, in the case of portfolio run-off strategies. This point is further explained in the MMG section focusing on macro models.
3.3.7
If an obligor migrates between ratings or between segments during the observation period, the obligor should be included in the original rating bucket and/or original segment for the purpose of estimating a default rate. Institutions should document any changes in portfolio segmentation that occurred during the period of observation.
3.3.8
When the default rate is computed by rating grade, the ratings at the beginning of the observation window should not reflect risk transfers or any form of parent guaranties, in order to capture the default rates pertaining to the original creditworthiness of the obligors. The ratings at the start of the observation window can reflect rating overrides if these overrides relate to the obligors themselves, independently of guarantees.
3.3.9
When default rate series are computed over long time periods, it could happen that obligors come out of their default status after a recovery and a cure period. In subsequent observation windows, such obligors could be performing again and default again, in which case another default event should be recorded. For that purpose, institutions should define minimum cure periods per product and/or portfolio type. If a second default occurs after the end of the cure period, it should be recorded as an addition default event. These cure periods should be based on patterns observed in data sets.
3.3.10
Provided that institutions follow the above practices, the following aspects remain subject to the discretion of each institution. First, they may choose to exclude obligors with only undrawn facilities from the numerator and denominator to avoid lowering unduly the default rate of obligors with drawn credit lines. Second, institutions may also choose to estimate default rates based on exposures rather than on counts of obligors; such estimation provides additional statistical information on expected exposures at default.
3.4 Rating-to-PD
3.4.1
For the purpose of risk management, the majority of institutions employ a dedicated methodology to estimate a TTC PD associated with each portfolio and, where possible, associated with each rating grade (or score) generated by their rating models. This estimation is based on the historical default rates previously computed, such that the TTC PD reflects the institution’s experience.
3.4.2
This process results in the construction of a PD scale, whereby the rating grades (or scores) are mapped to a single PD master scale, often common across several portfolios. This mapping exercise is referred to as ‘PD calibration’. It relies on assumptions and methodological choices separate from the rating model, therefore it is recommended to considered such mapping as a standalone model. This choice is left to each institution and should be justified. The approach should be tested, documented and validated.
3.4.3
Institutions should demonstrate that the granularity of segmentation employed for PD modelling is an appropriate reflection of the risk profile of their current loan book. The segmentation granularity of PD models should be based on the segmentation of rating models. In other words, the segmentation of rating models should be used as a starting point, from which segments can be grouped or split further depending on portfolio features, provided it is fully justified. This modelling choice has material consequences on the quality of PD models; therefore, it should be documented and approved by the Model Oversight Committee. Finally, the choice of PD model granularity should be formally reviewed as part of the validation process.
3.4.4
The rating-to-PD mapping should be understood as a relationship in either direction since no causal relationship is involved. The volatility of the grade PD through time depends on the sensitivity of the rating model and on the rating methodology employed. Such volatility will arise from a combination of migrations across rating grades and changes in the DR observed for each grade. Two situations can arise:
(i)
If rating models are sensitive to economic conditions, ratings will change and the exposures will migrate across grades, while the DR will remain stable within each grade. In this case, client ratings will change and the TTC PD assigned to each rating bucket will remain stable. (ii)
If rating models are not sensitive to economic conditions, then the exposures will not migrate much through grades but the DR of each grade will change. In this case, client ratings will remain stable but the observed DR will deviate from the TTC PD assigned to each rating bucket.
3.4.5
Institutions should estimate the degree to which they are exposed to each of the situations above. Institutions are encouraged to favour the first situation, i.e. implement rating models that are sensitive to economic conditions, favour rating migrations and keep the 1-year TTC PD assigned to each rating relatively stable. For the purpose of provisioning, economic conditions should be reflected in the PIT PD in subsequent modelling. Deviation from this practice is possible but should be justified and documented.
3.4.6
The estimation of TTC PD relies on a set of principles that have been long established in the financial industry. At a minimum, institutions should ensure that they cover the following aspects:
(i)
The TTC PD associated with each portfolio or grade should be the long-run average estimation of the 1-year default rates for each corresponding portfolio or grade. (ii)
The DR time series should be homogeneous and consistent through time, i.e. relate to a portfolio with similar characteristics and grading method. (iii)
TTC PDs should incorporate an appropriate margin of conservatism depending on the time span covered and the population size. (iv)
TTC PDs should be estimated over a minimum of five (5) years and preferably longer for wholesale portfolios. For retail portfolios, changes in product offerings should be taken into account when computing TTC PD. (v)
The period employed for this estimation should cover at least one of the recent economic cycles in the UAE: (i) the aftermath of the 2008 financial crisis, (ii) the 2015-2016 economic slowdown after a sharp drop in oil price, and/or (iii) the Covid-19 crisis. (vi)
If the estimation period includes too many years of economic expansion or economic downturn, the TTD PD should be adjusted accordingly.
3.4.7
For low default portfolios, institutions should employ a separate approach to estimate PDs. They should identify an appropriate methodology suitable to the risk profile of their portfolio. It is recommended to refer to common methods proposed by practitioners and academics to address this question. Amongst others, the Pluto & Tasche method or the Benjamin, Cathcart and Ryan method (BCR) are suitable candidates.
3.4.8
For portfolios that are externally rated by rating agencies, institutions can use the associated TTC PDs provided by rating agencies. However, institutions should demonstrate that (i) they do not have sufficient observed DR internally to estimate TTC PDs, (ii) each TTC PD is based on a blended estimation across the data provided by several rating agencies, (iii) the external data is regularly updated to include new publications from rating agencies, and (iv) the decision to use external ratings and PDs is reconsidered by the Model Oversight Committee on a regular basis.
3.5 PIT PD and PD Terms Structure
3.5.1
Modelling choices surrounding PIT PD and PD term structure have material consequences on the estimation of provisions and subsequent management decisions. Several methodologies exist with benefits and drawbacks. The choice of methodology is often the result of a compromise between several dimensions, including but not limited to: (i) rating granularity, (ii) time step granularity and (iii) obligor segmentation granularity. It is generally challenging to produce PD term structures with full granularity in all dimensions. Often, one or two dimensions have to be reduced, i.e. simplified.
3.5.2
Institutions should be aware of this trade-off and should choose the most appropriate method according to the size and risk profile of their books. The suitability of a methodology should be reviewed as part of the validation process. The methodology employed can change with evolving portfolios, risk drivers and modelling techniques. This modelling choice should be substantiated, documented and approved by the Model Oversight Committee. Modelling suggestions made by third party consultants should also be reviewed through a robust governance process.
3.5.3
For the purpose of the MMG, minimum expected practices are articulated for the following common methods. Other methodologies exist and are employed by practitioners. Institutions are encouraged to make research and consider several approaches.
(i) The transition matrix approach, (ii) The portfolio average approach, and (iii)
The Vasicek credit framework.
3.5.4
Irrespective of the modelling approach, institutions should ensure that the results produced by models meet business sense and economic intuition. This is particularly true when using sophisticated modelling techniques. Ultimately, the transformation and the adjustment of data should lead to forecasted PDs that are coherent with the historical default rates experienced by the institution. Deviations should be clearly explained.
3.6 PIT PD with Transition Matrices
3.6.1
This section applies to institutions choosing to use transition matrices as a methodology to model PD term structures.
3.6.2
Transition matrices are convenient tools; however, institutions should be aware of their theoretical limitations and practical challenges. Their design and estimation should follow the decision process outlined in the MMS. Institutions should assess the suitability of this methodology vs. other possible options as part of the model development process. If a third party consultant suggests using transition matrices as a modelling option, institutions should ensure that sufficient analysis is performed, documented and communicated to the Model Oversight Committee prior to choosing such modelling path.
3.6.3
One of the downsides of using transition matrices is the excessive generalization and the lack of industry granularity. To obtain robust matrices, pools of data are often created with obligors from various background (industry, geography and size). This reduces the accuracy of the PD prediction across these dimensions. Consequently, institutions should analyse and document the implications of this dimensionality reduction.
3.6.4
The construction of the TTC matrix should meet a set of properties, that should be clearly defined in advance by the institution. The matrix should be based on the institution’s internal data as it is not recommended to use external data for this purpose. If an institution does not have sufficient internal data to construct a transition matrix, or if the matrix does not meet the following properties, then other methodologies should be considered to develop PD term structures.
3.6.5
At a minimum, the following properties should be analysed, understood and documented:
(i)
Matrix robustness: Enough data should be available to ensure a robust estimation of each rating transition point. Large confidence intervals around each transition probabilities should be avoided. Consequently, institutions should estimate and document these confidence intervals as part of the model development phase. These should be reviewed as part of the model validation phase. (ii)
Matrix size: The size of the transition matrix should be chosen carefully as for the size of a rating scale. A number of buckets that is too small will reduce the accuracy of decision making. A number of buckets that is too large will lead to an unstable matrix and provide a false sense of accuracy. Generally, it is recommended to reduce the size of the transition matrix compared to the full rating scale of the institution. In this case, a suitable interpolation method should be created as a bridge from the reduced matrix size, back to the full rating scale. (iii)
Matrix estimation method: Amongst others, two estimation methods are commonly employed; the cohort approach and the generator approach. The method of choice should be tested, documented and reviewed as part of the model validation process. (iv)
Matrix smoothing: Several inconsistencies often occur in transition matrices, for instance (a) transition probabilities can be zero in some rating buckets, and/or (b) the transition distributions for a given origination rating can be bi-modal. Institutions should ensure that the transition matrix respect Markovian properties.
3.6.6
If the institution decides to proceed with the transition matrix appraoch, the modelling approach should be clearly articulated as a clear sequence of steps to ensure transparency in the decision process. At a minimum, the following sequence should be present in the modelling documentation. The MMG does not intend to elaborate on the exact methodology of each step. Rather, the MMG intends to draw attention to modelling challenges and set minimum expected practices as follows:
(i)
TTC transition matrix: The first step is the estimation of a TTC matrix that meets the properties detailed in the previous article. (ii)
Credit Index: The second step is the construction a Credit Index (“CI”) reflecting appropriately the difference between the observed PIT DR and TTC DR (after probit or logit transformation). The CI should be coherent with the TTC transition matrix. This means that the volatility of the CI should reflect the volatility of the transition matrix through time. For that purpose the CI and the TTC transition matrix should be based on the same data. If not, justification should be provided. (iii)
Forecasted CI: The third step involves forecasting the CI with a macroeconomic model. However, a segmentation issue often arises. If the matrix was created by pooling obligors from several segments, then only one blended CI will be estimated. This may be insufficient to capture the relationship between macroeconomic variables and the creditworthiness of obligors at segment level for the purpose of PIT modelling. Institutions should be cognisant of such limitation and provide solutions to overcome it. An option is to adjust the blended forecasted CI to create several granular CIs that would reflect the behaviour of each segment. (iv)
Adjusted transition matrix: The fourth step is the development of a mechanism to adjust the TTC transition matrix with the forecasted CI or the adjusted CIs. Several forward PIT transition matrices should be obtained at several points in the future. (v)
PD term structure: Finally, a PD term structure should be created based on the forward PIT transition matrices. Methodologies based on matrix multiplication techniques should be robust and consistently applied.
3.6.7
As part of the development process, several pre-implementation validation checks should be performed on the TTC transition matrix in order to verify that the above properties are met. In addition, for each segment being modelled, the matrix should be constructed such that two logical properties are met by the PD outputs:
(i)
The weighted average TTC PD based on the default column of the TTC transition matrix should be reasonably close to the long term default rate of the obligors from the same segment(s) employed to build the matrix. (ii)
The weighted average PIT PD based on the default column of the PIT transition matrix for the next few time steps, should be coherent with the current default rate of the obligors from the same segment(s) employed to build the matrix or the segment(s) employed to derived the adjusted CIs.
3.7 Portfolio Scaling Approach
3.7.1
This section applies to institutions using a portfolio-level scaling approach to model the term structure of PIT PD. This approach is simpler to implement than transition matrices and is suitable for portfolios with smaller data sets. In this method, average PD across ratings are being modelled, instead of all transition points between ratings. This approach tends to be preferred for smaller segments. The obligor segmentation granularity is preserved at the expense of a simplification of the rating granularity.
3.7.2
In order to ensure transparency in the decision process, the modelling approach should be clearly articulated as a clear sequence of steps. It is not the object of the MMG to elaborate on the exact methodology of each step. Rather, the MMG intends to draw attention to modelling challenges and set minimum expected practices. At a minimum, the following sequence should be present in the modelling documentation:
(i) Forecast portfolio average PIT PD per segment based on macro-PD models. (ii) Estimate the deviation of the portfolio PIT PD from its long term average PD. (iii)
Apply this deviation to PDs at lower granularity levels, for instance pools or rating grades. This can be achieved by scaling in logit or probit space. (iv)
Construct a PIT PD term structure. It is highly recommended to compare several methods and test their impacts on PD outcomes and risk metrics.
3.7.3
The drawback of this method is the generalisation of the PD volatility across grades (or pools) with the use of scalers. Certain rating grades are more prone to volatility than others, which is not reflected in this type of model. Therefore this method could result in an underestimation of the PIT PD of the lowest rating grades. Consequently, institutions should demonstrate that they assess and understand this effect.
3.7.4
Institutions should ensure that scalers lead to explainable shifts of the PD curve across rating grades and across time steps. The scalers will not be static. They will change through the forecasted time steps, since they follow the path of the PD forecasts.
3.7.5
Institutions should be aware of the theoretical and practical limitations of this approach. Its design and estimation should follow the decision process outlined in the MMS. As for any other models, institutions should assess the suitability of this methodology vs. other possible options as part of the model development process.
3.8 The Vasicek Credit Framework
3.8.1
The Vasicek credit framework is sometimes used to model PIT PD term structures. Institutions should be cognisant of the material challenges arising from using the Vasicek one-factor credit model (or similar derivations) for the purpose of ECL estimation, for the following reasons:
(i)
This model has been originally designed to model economic capital and extreme losses at portfolio level. It is designed to replicate the behaviour of credit risk for a granular and homogeneous portfolio. Whilst it is an elegant modelling construction, it might not be the most suitable approach to model expected loss behaviours at the level of individual obligors. (ii)
It relies on parameters that are challenging to calibrate, in particular the asset correlation representing the correlation between (a) obligors’ asset value and (b) a non-observable systemic factor - generally assimilated to an industry factor for practical reasons. The model results are highly sensitive to the choice of this parameter. When modelling PIT PD, the introduction of this correlation parameter tends to reduce the impact of macroeconomic factors. (iii)
When it is used for ECL, the Vasicek model is often combined with a macroeconomic regression model. In this case, the non-observable systemic factor is not a given input. Rather, it is partially driven by macro variables. Consequently, the commonly used one- factor model should be adjusted to account for the variance of the residuals, i.e. the part of the systemic factor that is not explained by the macro variables.
3.8.2
If an institution decides to use this methodology, this choice should be approved by the Model Oversight Committee, with a clearly documented rationale. The asset correlation parameters should be chosen carefully, bearing in mind the following principle: the lower the PD, the higher the asset correlation because the obligor’s performance is expected to be mostly driven by systemic factors rather than by idiosyncratic factors.
3.8.3
It is common practice to calibrate the asset correlation based on the values suggested by the Basel Framework employed for capital calculation. However, institutions should consider the possibility that the interconnectedness of corporates in the UAE could lead to higher systemic correlations for some industries. Consequently, institutions should, at a minimum, perform sensitivity analysis to assess the implications of this calibration uncertainty on PDs.
3.9 Validation of PD Models
3.9.1
Irrespective of their choice of methods, institutions should validate PD models according to the principles articulated in the MMS. In particular for PD models, both qualitative and quantitative assessments are required.
3.9.2
Institutions should ensure that the following metrics represent accurately the risk profile of their books at segment-level: TTC 1y PD, PIT 1y PD and PD term structure. For that purpose, these metrics should be validated at several granularity levels (e.g. rating grades, segments, industries). Statistical tests alone are generally not sufficient to conduct appropriate validation of PD at segment level. Consequently, institutions should combine statistical tests, judgement and checks across several metrics to ensure that the calibration of these metrics are meaningful and accurate.
3.9.3
Comprehensive techniques should be developed in order to validate PIT PDs. At a minimum, institutions and their supporting third parties should cover the comparisons articulated in the following table. This logical cross-check approach involves comparing variables estimated via several methods. In addition to these comparisons, institutions should design and compute other metrics to suit their specific PD methodology.
3.9.4
If insufficient data is available to estimate some of the metrics in the below table, institutions should demonstrate that actions are taken to collect data to produce these metrics. Given the lack of data, they should also explain their approach to assess the suitability of the PIT PD calibration currently used in production.
Table 2: Metrics used to validate PD models
Segment level metrics Point-in-Time metrics (PIT) Through-the-Cycle metrics (TTC) 1-year Default Rate
(“1y DR”)PIT 1y DR are historically observed default rates per segment. Should be in a form a rolling time series, preferably with monthly intervals. TTC 1y DR are computed as the average of PIT 1y DR through time. They can be weighted by the number of performing obligors in each time step. Cumulative Default Rate
(“CDR”)PIT CDR are historically observed default rates over several performance windows, covering for instance 2, 3 and 4 years. The result should be several term-structures of defaults, observed at several points in time. Also computed per segment. TTC CDR is the average of the CDR through time, per performance window, covering for instance 2, 3 and 4 years. The result should be a single PD term structure of default per segment. 1-year Probability of Default
(“1y PD”)PIT 1y PD estimated based on score-to-PD calibration and macro models. Estimated at segment level as the average across rating grades (exposure-weighted or count-weighted). TTC 1y PD can be computed with several methods. For instance as: (i) weighted average PD based on the bank’s master scale, or (ii) if transition matrices are used, weighted average across the default column of the TTC matrix. Cumulative Probability of Default (“CPD”)
Terms structure of PIT PD per segment and rating grades produced by models. Estimated per segment as the average across rating grades (exposure-weighted or count-weighted). Not always available, depending on the methodology. In the case of transition matrices, it should be based on the TTC matrix computed over several time horizons. 3.9.5
Upon the estimation of the above metrics, institutions should perform the following comparisons at segment level. Institutions should implement acceptable limits to monitor each of the following comparison, i.e. the difference between each two quantities. These limits should be included in the model validation framework and agreed by the Model Oversight Committee. Frequent and material breaches should trigger actions as articulated in the governance section of the MMS.
(i)
TTC 1y DR vs. TTC 1y PD per segment: The objective is to verify that the central tendency observed historically is in line with the PD estimated based on the institution’s master-scale. (ii)
PIT 1y DR vs. PIT 1y PD estimated over the same historical period, per segment: This is a back testing exercise. The objective is to verify that the default rates observed historically are falling within a reasonable confidence interval around the PD forecasted over the same period. (iii)
PIT 1y DR recently computed vs. PIT 1y PD estimated over the next 12 months: The objective is to verify that the default rate recently observed is coherent with the PD forecasted from the reporting date over the next 12 months. These two quantities can diverge due to the effect of economic forecasts. There should be a logical and intuitive link between the two and material differences should be explained. (iv)
TTC CDR vs. PIT CPD per segment: The objective is to verify that the shape of the cumulative default rates observed historically is similar with the shape of the cumulative default rate forecasted by the model from the portfolio reporting date. The shape can be expressed as a multiplier of the 1-year PD. (v)
TTC CDR vs. PIT PD derived analytically: A PD term structures can be estimated simply by using survival probabilities derived from the institution’s PD mater scale. This is referred as the analytical PD term structure, that serves as a theoretical benchmark. The objective is to compare this analytical benchmark vs. (a) observed CDR and (b) the PD term structure generated by the model. Material deviations should be understood and documented. If CDR and CPD are materially lower than the analytical approach, adjustments should be considered.
3.9.6
In addition to segment level validation, institutions should ensure that the PIT PD profile across rating grades is logical and consistent. This is particularly relevant in the case of transition matrices. PIT adjustments should be coherent across different ratings. Technically, for a given segment and a given horizon forecast, the log-odd ratio of the PIT PD for a given rating over the TTC PD for the same rating, should be of similar magnitude between ratings.
3.9.7
Finally, economic consistency between segments is also part of the validation process of PD models. Institutions should ensure that such considerations are included in the scope of model validation. PIT PDs generated by models should be coherent between industries and between segments. For instance, if a given portfolio displayed high historical PD volatility, then such volatility is expected to be reflected in the forecasted PIT PD. Material deviations from coherent expectations should be explained and documented.
4 LGD Models
4.1 Scope
4.1.1
For risk management purpose and to comply with accounting and regulatory requirements, the majority of institutions develop models to estimate the potential loss arising in the event of the default of a facility or obligor. These are referred to as Loss Given Default models (“LGD”). These models serve several purposes including, but not limited to provision estimation, credit portfolio management, the economic capital estimation and capital allocation. For the purpose of the MMG, and to ensure appropriate model management, the following components are considered as separate models:
(i) TTC LGD models, and (ii) PIT LGD models.
The definitions of through-the-cycle (“TTC”) and point-in-time (“PIT”) are similar to those used under the section on PD models.
4.1.2
Institutions should develop and manage these models through a complete life-cycle process in line with the requirements articulated in the MMS. In particular, the development, ownership and validation process should be clearly managed and documented.
4.1.3
Institutions are expected to meet minimum expected practices for the development of LGD models. For that purpose, the construction of LGD models should include, at a minimum, the following steps:
(i) Regular and comprehensive collection of data, (ii) Accurate computation of realised historical LGD, (iii) Analysis of the LGD drivers and identification of the most relevant segmentation, (iv) Development of TTC LGD model(s), and (v)
Development of PIT LGD model(s).
4.1.4
This section elaborates on the concepts and methods that institutions should incorporate in their modelling practice. In particular, institutions should pay attention to the appropriate estimation of recovery and losses arising from restructured facilities. Restructuring should not always be considered as a zero-sum game leading to no financial impact. In some cases the present value (“PV”) mechanics can lead to limited impact; however, restructuring events generate execution costs, delays and uncertainty that should be fully identified and incorporated into LGD modelling.
4.1.5
Institutions are strongly recommended to apply floors on TTC LGD and PIT LGD across all portfolios for several reasons. There is limited evidence that default events lead to zero realised losses. An LGD of zero leads to zero expected loss and zero capital consumption, thereby creating a biased perception of risk and misguided portfolio allocation. LGD floors contribute to sound decision making for risk management and lead to more realistic provisioning. The value of the floor should be five percent (5%) for all facilities, except in the following circumstances:
(i)
The facility is fully secured by cash collateral, bank guarantees or government guarantees, and/or (ii) The institution provides robust evidence that historical LGDs are lower than 5%.
In all circumstances, LGD should not be lower than one percent (1%).
4.2 Data Collection
4.2.1
A robust data collection process should be put in place in order to support the estimation of LGD parameters. This process should follow the requirements pertaining to the Data Management Framework articulated in the MMS. If the data listed below is not currently available in the institution’s data bases, a formal project should be put in place in order to collect and store this data from the date of the MMG issuance.
4.2.2
Governance: The data types to be collected for the estimation of LGD are often spread across several teams and departments within institution. Consequently, close collaboration is expected between departments to (i) fully retrieve historical default cases, (ii) understand the reasons and the context for default and (iii) reconstruct long recovery processes that can last several years. In particular, close collaboration is expected between the risk analytics department in charge of model development and the department in charge of managing non-performing credit facilities.
4.2.3
Default definition: Institutions should ensure consistency between (i) the default definition used to collect data for LGD estimation and (ii) the default definition used to estimate PD for the same segment. PD and LGD are necessarily linked to each other and their estimation should be coherent. This is particularly relevant in the context of facility restructuring. If restructured facilities are included in the estimation of LGD, they should also be included in the estimation of PD.
4.2.4
Data types: The collection of data should cover all the elements necessary to estimate recoveries and historical LGDs, following each default event. At a minimum, the data collection process should include the following elements:
(i)
Default events: An exhaustive list of default events should be collected to support a robust estimation of LGD. They should be consistent with the default events employed for PD modelling. Institutions are expected to collect as many default events as possible covering at least one economic cycle. (ii)
Exposure At Default: As per the definition section. For non-contingent facilities, the EAD should be the outstanding amount at the date of default. For contingent facilities, the EAD should be the outstanding amount at the date of default plus any other amounts that become due during the recovery process. This should include any additional drawings that occurred after default and before foreclosure or cure. It should also include any part of the original exposure that had been written-off before the default event was recorded. (iii)
Outcome categorisation: Each default event should be linked to the categories presented in the next article, depending on the outcome of the recovery process, namely (i) cured & not restructured, (ii) cured & restructured, (iii) not cured & secured, and (iv) not cured & not secured. (iv)
Obligor information: For each default event, client related information should be collected including, at a minimum, client segment, industry and geography. (v)
Facility details: This should include the type of facility and the key elements of the facility terms such as the tenor, the seniority ranking and the effective interest rate. (vi)
Restructuring: Each restructuring and rescheduling event should be identified and used in the categorisation of outcomes presented in the next articles. (vii)
Collateral: For each default event related to collateralised facilities, institutions should collect all relevant collateral information, including, but not limited to, the type of collateral, the last valuation prior to the default event and the associated valuation date, the liquidation value after default and the associated liquidation date, the currencies of collateral values and unfunded credit protections. If several valuations are available, institutions have a method to estimate a single value. (viii)
Historical asset prices: In order to estimate collateral haircut, historical time series should be collected, including amongst others, real estate prices, traded securities and commodity prices. (ix)
Collected cash flows: For each default event, the data set should include the cash flow profile received through time, related to this specific default event. Provided that collected cash inflows are related to the specific default event, they can arise from any party, including the obligor itself, any guarantor or government entities. (x)
Direct costs: These costs are directly linked to the collection of the recovery cash flows. They should include outsourced collection costs, legal fees and any other fees charged by third parties. If the facility is secured, the data set should include costs associated with the sale of collateral, including auction proceedings and any other fees charges by third party during the collateral recovery process. (xi)
Indirect costs: Institutions are encourage to collect internal and external costs that cannot be directly attributed to the recovery process of a specific facility. Internal costs relate to the institution’s recovery process, i.e. mostly the team that manages non-performing credit facilities and obligors. External costs relate mostly to overall costs of outsourced collection services.
4.2.5
Categorisation: The outcome of default events should be clearly categorised. Institutions are free to define these categories, provided that these include, at a minimum, the below concepts.
Table 3: Typical outcomes of default events
Outcome Description Detailed outcome Category Cured The obligor has returned to a performing situation after a cure period-as defined in the CBUAE Credit Risk regulation. No restructuring / rescheduling Cured & not restructured Restructuring / rescheduling Cured & restructured Not cured The obligor has not returned to a performing status after defaulting. The facility is secured by collateral Not cured & secured The facility is not secured Not cured & unsecured Unresolved The outcome remains uncertain until a maximum recovery period beyond which all cases should be considered closed for LGD estimation. Unresolved 4.3 Historical Realised LGD
4.3.1
The next step in the modelling process involves the computation of historical realised LGD based on the data previously collected. The objective is to estimate the recovery and loss through a ‘workout’ approach for each of the identified default event.
4.3.2
The computation of LGD relies on the appropriate identification and quantification of the total recoveries and expenses linked to each default event. Institutions should implement a robust process to perform the necessary computation to estimate LGD at the lowest possible granularity level.
4.3.3
Institutions can develop their own methodologies for the estimation of historical realised LGD. However, their approach should incorporate, at a minimum, the components listed in this section and the corresponding categories of workout outcomes.
4.3.4
Institutions are expected to compute LGD at the time default (t) as the ratio of the total loss incurred divided by the Exposure At Default. When modelling LGD time series, the time of reference should be the date of default. We note LGD as a function of time t, as LGDt, then t is the date of default, which is different from the time at which the recovery cash flows where collected. The total recovery is noted Recoveryt and the total loss is noted Losst. Institutions should therefore estimate realised LGD for each default event with the following formula:
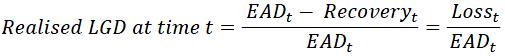
4.3.5
The recovery is derived from all cash inflows and expenses occurring at future times after the default event and discounted back to the default date. The recovery cash flows should not be higher than the amount of recoveries that can legally be obtained by the institution. The discount rates should reflect the time-value of money plus the uncertainty surrounding the cash flows. Additional considerations for restructured facilities are presented at the end of this section. If several facilities are secured by one or several collaterals, institutions should implement a clear collateral allocation mechanism from the obligor level to each facility. The computations of Recoveryt and Losst depend on the workout outcome. The estimation method should incorporate the following components.
Table 4: Recovery and costs per type of outcome
Outcome Components of recovery and costs (1) Cured & not restructured (a)
Indirect costs, as defined in the data collection section.
(2) Cured & restructured (a) Potential reduction in present value upon restructuring the facility. (b) Direct costs, as defined in the data collection section. (c)
Indirect costs, as defined in the data collection section.
(3) Not cured & secured (a) When applicable, present value of discounted collateral proceedings back to the default date (b) Direct costs, as defined in the data collection section. (c) Indirect costs, as defined in the data collection section. (d)
Cash flows received but not associated with collateral liquidation.
(4) Not cured & unsecured (a) Recovered cash flows. Effect of discounting these cash flows back to the default date, function of the time to recovery. (b)
Indirect costs, as defined in the data collection section.
(5) Unresolved These should be treated as per the following article. 4.3.6
The treatment of unresolved default cases (incomplete workouts) creates a material bias in the estimation of LGD. Consequently, institutions should establish a clear process for the treatment of these cases and understand their impact on the estimation of historical realised LGD.
(i)
Institutions should define criteria to decide on whether the recovery process of a default case should be considered closed. A degree of conservativeness should be included in this estimation to reflect the uncertainty of the recovery process. This means that if doubts persist regarding the possibility of future cash inflows, the recovery process should be considered closed. (ii)
Institutions should put in place clear criteria to include or exclude unresolved cases in their estimation samples. For that purpose, a maximum length of resolution period (from the date of default) should be established by obligor segment. The objective is to choose a duration that is sufficiently short to maximise the number of recovery cases flagged as ‘closed’ and sufficiently long to capture a fair recovery period. (iii)
It is recommended that open default cases with a recovery period longer than four (4) years should be included in the LGD estimation process, irrespective of whether they are considered closed. For the avoidance of doubt, all closed cases with a shorter recovery period should, of course, be included. Banks are free to use a shorter maximum duration. Longer maximum duration, however, should be avoided and can only be used upon robust evidence provided by the institution. (iv)
Default cases that are still unresolved within the maximum length of the recovery process (i.e. shorter than 4 years) should preferably be excluded for the purpose of estimating historical LGDs. Institutions have the option to consider adjustments by extrapolating the remaining completion of the workout process up to the maximum resolution period. Such extrapolation should be based on documented analysis of the recovery pattern by obligor segment and/or product type observed for closed cases. This extrapolation should be conservative and incorporate the possibility of lower recovered cash-flows.
Table 5: Treatment of unresolved default cases
Recovery status Shorter recovery than the maximum recovery period Longer recovery than the maximum recovery period Closed cases Included. All discounted cash-flows taken into account. Included. All discounted cash-flows taken into account. Open cases Excluded. Possible inclusion if cash-flows are extrapolated. Included. All discounted cash-flows taken into account. 4.3.7
Institutions should not assume that restructuring and rescheduling events necessarily lead to zero economic loss. For restructuring associated with material exposures, an estimation of their associated present value impact should be performed. If no PV impact is readily available, then the terms of the new and old facilities should be collected in order to estimate a PV impact, according to the methodology outlined in the dedicated section of the MMG. In particular, if the PV impact of the cash flow adjustment is compensated for by a capitalisation of interest, institutions should include an incremental credit spread in discounting to reflect the uncertainty arising from postponing principal repayments at future dates. Such credit spread should then lead to a negative PV impact.
4.3.8
For low default portfolios, institutions may not have enough data to estimate robust historical recovery patterns. In this case, institutions should be in a position to demonstrate that data collection efforts have taken place. They should also justify subsequent modelling choices based on alternative data sources and/or comparables. Furthermore, portfolios with high frequency of cure via restructuring should not be considered as portfolios with low default frequency. Restructured facilities could be recognised as defaults depending on circumstances and in compliance with the CBUAE credit risk regulation.
4.4 Analysis of Realised LGD
4.4.1
Once institutions have estimated and categorised realised LGD, they should analyse and understand the drivers of realised LGD in order to inform modelling choices in the subsequent step.
4.4.2
At a minimum, institutions should analyse and understand the impact of the following drivers on LGD:
(i)
The time at which LGD was observed in the economic cycle. The profile of the recovery pattern and the effect of the economic cycle on this pattern. (ii)
The effect of collateral on the final LGD including the time to realise the collateral, the impact of the type of collateral, the difference between the last valuation and the liquidation value. (iii)
The link between LGD and the obligor’s credit worthiness at the time of default captured by its rating or its PD. (iv) The type of facility and its seniority ranking, where applicable. (v) The obligor segments expressed by size, industry, and/or geography. (vi)
Any change in the bankruptcy legal framework of the jurisdiction of exposure.
4.4.3
Institutions should identify the most appropriate segmentation of historical realised LGD, because this choice will subsequently inform model segmentation. Portfolio segmentation should be based upon the characteristics of the obligors, its facilities and its collateral types, if any.
4.4.4
Institutions should be cautious when using ‘Secured LGD’ and ‘Unsecured LGDs’ as portfolio segments. A secured LGD is a loss obtained from a facility secured by a collateral. It is based upon the estimation of a collateral coverage (defined as the ratio of the collateral value to the exposure). The loss resulting from such coverage can spread across a large range: from low values in the case of over-collateralization, up to high values in the case of small collateral amounts. An average (referred as Secured LGD) across such large range of values is likely to suffer from a lack of accuracy. Thus, it is preferable to employ collateral as a direct continuous driver of LGD, rather than use it to split a population of obligors.
4.4.5
Once segments have been identified, institutions should produce three types of LGD per segment to support the estimation of ECL as per accounting principles. These estimates should be used to calibrate the TTC LGD and PIT LGD models in subsequent modelling steps. The estimation of averages can be exposure-weighted or count-weighted. This choice depends on each portfolio and thus each institution.
(i)
The long run average by segment, through time across business cycles, estimated as the average of realised LGDs over the observation period. (ii) The LGD during economic downturns. (iii)
The LGD during periods of economic growth.
4.4.6
When analysing the effect of collateral on LGD outcomes, institutions should consider, at a minimum, the following collateral types. Note that personal guarantees should not be considered as eligible collateral for the purpose of modelling LGD. This list may evolve with the CBUAE regulation.
Table 6: Types of eligible collateral
Collateral types Cash (or cash equivalent) Federal Government (security or guarantee) Local Government (security or guarantee) Foreign sovereign government bonds rated BBB- or above UAE licensed Bank (security or guarantee) Foreign bank rated AA- or above (security or guarantee) Foreign bank rated BBB- but below AA- (security or guarantee) Listed Shares on a recognized stock exchange Bonds or guarantees from corporations rated above BBB- Residential Real Estate Commercial Real Estate All other banks bonds or guarantees Cars, Boats, Machinery and other movables All other corporate bonds or guarantees (not including cross or personal guarantees) 4.5 TTC LGD Modelling
4.5.1
The objective of TTC LGD models is to estimate LGD, independently of the macroeconomic circumstances at the time of default. Therefore, these models should not depend on macroeconomic variables. These models can take several forms depending on the data available and the type of portfolio. Institutions are free to choose the most suitable approach, provided that it meets the minimum expectations articulated in this section.
4.5.2
Defaulted vs. non-defaulted cases: LGD should be modelled and estimated separately between defaulted obligors (or facilities) and non-defaulted obligors. Whilst the methodology should be similar between these two cases, several differences exist:
(i)
Upon a default event, the estimation of recovery relies on assumptions and on a live process with regular information updates. Therefore, for defaulted obligors (or facilities), as the recovery process unfolds, institutions should collect additional information to estimate recovery rates with further accuracy and thus obtain more specific LGD estimation. (ii)
For defaulted obligors (or facilities), particular attention should be given to PV modelling as per the dedicated section of the MMG. Discount factors should reflect the circumstances of default and the uncertainty surrounding the recovery process. (iii)
One of the major differences between LGD from defaulted vs. non-default exposures is that the former is estimated only as of the date of default, while the latter is estimated at several point in time, depending on the needs of risk management and financial reporting.
4.5.3
Properties: At a minimum, LGD models should meet the following properties.
(i)
The modelled LGD should be based upon the historical realised LGD observations previously estimated. (ii)
The methodology should avoid excessive and unreasonable generalisations to compensate for a lack of data. (iii)
The model performance should be validated based on clear performance measurement criteria. For instance, model predictions should be compared against individual observations and also against segment average. (iv)
There should be enough evidence to demonstrate that in-sample fit and out-of-sample performance are reasonable. (v) The choice of parameters should be justified and documented. (vi)
The model inputs should be granular and specify enough to generate a LGD distribution that is a fair and accurate reflection of the observed LGDs.
4.5.4
Functional form: Institutions are free to use LGD models with any functional form provided that the model output is an accurate reflection of the observed LGD. Institutions should aim to build LGD models that incorporate the suitable drivers enabling the model to reflect the main possible outcomes of the workout process.
4.5.5
Parameters: Institutions should aim to incorporate the following drivers in their LGD models. This means that any model using less granular inputs should be considered as a first generation model that requires improvement as further data becomes available.
(i) The probability of cure without restructuring, (ii) The probability of cure through restructuring, (iii) The collateral coverage, (iv) Direct and indirect recovery costs, (v) Collateral liquidation values including haircuts, and (vi)
Recovered cash flows
The quantitative drivers above should be analysed (segmented) by qualitative drivers, including but not limited to:
(vii) Industry or obligor type, (viii) Facility type, and (ix)
Seniority ranking.
4.5.6
The parameters listed above should drive the estimation of LGD. The mathematical construction of the LGD model can take several forms, that institutions are free to choose. The form presented below serves as illustration. Institutions are not expected to use this expression literally; rather, they should ensure that their final LGD model respects the principles of this expression with a suitable estimation of each component. If institutions employ a different functional form, they are encouraged to use the following expression as a challenger model.
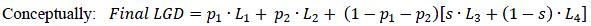
Table 7: Typical components of LGD models
Component Definition P1 Probability of cure without restructuring P2 Probability of cure through restructuring S Collateral coverage defined as 𝐶𝑜𝑙𝑙𝑎𝑡𝑒𝑟𝑎𝑙 𝑉𝑎𝑙𝑢𝑒 ⁄𝐸𝐴D L1 Loss (cost) from managing delinquent clients that were cured without restructuring L2 Loss from managing delinquent clients through restructuring or rescheduling, including direct and indirect costs plus NPV impacts. L3 Loss from the realisation of collateral including haircuts, direct and indirect costs plus NPV impact. Estimated across all collateral types. L4 Loss arising from the incomplete recovery of the portion of exposure not covered by collateral, also including indirect management costs and NPV impacts. (Referred to as unsecured LGD.)
The loss arising from the unsecured portion (L4) is often called "unsecured LGD". The final LGD after taking collateral into accounts is often referred to as the "secured LGD". Irrespective of the semantic employed, LGD models should reconcile conceptually against the expression above.
4.5.7
Granularity: Institutions should aim to develop TTC LGD models to estimate LGD at a low level of granularity. The following minimum expected practices apply:
(i)
Institutions should aim to model LGD at facility level, i.e. the LGD should incorporate facility characteristics. If this is not possible for practical reasons, LGD should be computed at obligor level. This means that LGD should be driven by parameters specific to each obligor and the associated collaterals if any. (ii)
If several facilities are secured by one or several collaterals, institutions should implement a clear collateral allocation mechanism from the obligor to each facility. (iii)
If institutions do not have the required data to build such granular models, they should put in place a formal project in order to collect the necessary data as a stepping stone towards accurate LGD modelling.
4.5.8
Segmentation: The portfolio segmentation employed to estimate LGDs should be justified and documented. In theory, LGD segments do not have to be identical to those employed for PD modelling. However, in practice, it is recommended to use similar portfolio segmentation across PD and LGD models, where possible, in order to ease the interpretation of LGD and subsequent usage in provision and capital estimation.
4.5.9
Collateral haircuts: The last valuation of an asset is unlikely to reflect the resale value of a repossessed asset. Consequently, institutions should estimate appropriate haircuts based on the assumption that they intend to sell the repossessed asset as soon as reasonably possible. Haircuts should be estimated based on historical data by type of collateral.
4.5.10
Bimodal distribution: Institutions should identify whether the distribution of observed LGD is bimodal, i.e. a distribution with two peaks of high frequency. In this case, specific modelling constraints apply. Institutions should be cautious when using an average value between these two peaks. Such average can be misleading and should not be employed to assign LGD at facility level since it does not correspond to an observable LGD at facility level.
4.5.11
Logical features: Following on from the conceptual framework presented above, some logical characteristics should be respected: (i) the final LGD should be equal or smaller than the unsecured LGD, (ii) the LGD should decrease with the presence of collateral, all other parameters being kept constant, and (iii) the longer the recovery period, the higher the recovery, the lower the LGD. The logical features should be tested as part of the model validation process.
4.6 PIT LGD Modelling
4.6.1
There is general evidence that LGD levels tend to be higher during economic downturns. This intuitive relationship is supported by numerous publications from academics and practitioners based on data from the US and European markets. In the UAE, whilst this relationship is more difficult to prove, there are objective reasons to believe it exists. In any case, this should be investigated as part of current accounting requirements. Consequently, institutions should implement a process to analyse the relationship between LGD and macro factors. This should be done at a relevant level of granularity.
4.6.2
This analysis should drive the modelling strategy of PIT LGD. Several modelling options can be envisaged and institutions should articulate explicitly their approach based on their preliminary analysis. While making a strategic decision, institutions should remain conservative. A portfolio may not be large enough to capture this relationship despite the existence of such relationship at larger scale. In doubt, it is preferable to include some degree of correlation between LGD and macro factors for the estimation of ECL. Once a mechanism is in place, the strength of the relationship can be adjusted in calibration exercises, upon further evidence proving or refuting it.
4.6.3
The objective of PIT LGD models is to estimate LGD as a function of the economic circumstances at the time of default and during the recovery process. Therefore, these models should depend on macroeconomic variables. Institutions are free to choose the most suitable methodology, provided that it meets the minimum expected practices articulated in this section.
4.6.4
PIT LGD models can be constructed by (i) adjusting TTC LGD or (ii) developing models independently from TTC LGD. For consistency purpose, the former is recommended over the latter. If institutions chose the second approach, they should ensure that both PIT LGD output and TTC LGD outputs are coherent.
4.6.5
The properties of the PIT LGD models should be similar to that of TTC LGD models. At a minimum, these models should meet the following:.
(i)
The modelled LGD should be based upon the historical realised LGD observations previously estimated. (ii)
The methodology should avoid excessive and unreasonable generalisations to compensate for a lack of data. (iii)
The model performance should be validated based on clear performance measurement criteria. For instance, model predictions should be compared against individual observations (or relevant groups) and also against segment average. (iv) The choice of parameters should be justified and documented. (v)
There should be enough evidence to demonstrate that in-sample fit and out-of-sample performance are reasonable. (vi)
The model inputs should be granular and specify enough to generate a PIT LGD distribution that is a fair and accurate reflection of the observed LGDs.
4.6.6
PIT LGD models can take several forms depending on the data available and the type of portfolio. Several broad categories of models can be defined as follows, ranked by increasing granularity and accuracy:
(i)
Option 1: Most granular approach. The LGD parameters are directly linked to the macro forecasts and used as inputs to compute the losses (L1,L2,L3,L4). The final LGD is subsequently computed based on these losses, as defined in the TTC LGD section. For instance, collateral values at facility level can be directly linked to the macro forecasts, then secured LGDs are derived. (ii)
Option 2: Intermediate granular approach. The losses (L1,L2,L3,L4) are linked to the macro forecasts and used as input to estimate the final LGD, as defined in the TTC LGD section. For instance, the segment level secured and unsecured LGDs can be linked to the macro forecasts. (iii)
Option 3: Non-granular approach. The final LGD is directly linked to the macro forecasts. In this case the PIT LGD models does not use the LGD parameters. (iv)
Option 4: Alternative approach. The final LGD is linked to the obligor's PD, itself linked to macro forecasts. In this case, the LGD response to macroeconomic shocks is constructed as a second order effect through correlation rather than structural causation.
4.6.7
Institutions should articulate and document explicitly their preferred modelling option. All these options are acceptable; however institutions should be aware of their theoretical and practical limitations, in particular the potential accuracy issues arising from options 3 and 4. Institutions should aim to model PIT LGD via option 1. Consequently, institutions should understand and assess the financial implications of their modelling choice. This choice should be approved by the Model Oversight Committee.
4.6.8
If the PIT LGD model uses PIT PD as a sole driver of macro adjustment, then the model segmentation should be identical between PIT LGD and PIT PD. If institutions decide to develop dedicated PIT LGD-macro models, those should follow the minimum expectations articulated in the section of the MMG dedicated to macro models.
4.7 Validation of LGD Models
4.7.1
Institutions should validate all LGD models according to the validation principles articulated in the MMS. Both qualitative and quantitative assessments should be conducted for an appropriate validation.
4.7.2
Institutions should ensure that segment-level LGD values represent the risk profile of their books. Statistical tests alone are not sufficient to conduct appropriate validation of LGD at segment level. Consequently, institutions should combine statistical tests, judgement and checks across comparable metrics to ensure that the calibration of these metrics are meaningful and accurate.
4.7.3
The scope of the validation should be comprehensive. If the validation is performed by a third party consultant, institutions should ensure that the validation effort is comprehensive in scope and substance.
4.7.4
The validation scope should include, at a minimum, the following components:
(i)
The data quality, comprehensiveness and collection process. This should cover the analysis of unusual features observed in historical data and their subsequent treatment for modelling. (ii)
The definition of default. This should cover the treatment of technical defaults and restructured accounts. (iii)
The methodology employed to compute historical LGD. This should cover in particular the possible outcomes as described earlier in this section. Partial replication of the historical LGD for a sample of facilities should be performed. (iv)
The methodology employed to estimate TTC LGD and subsequent PIT adjustments. This should cover the model fit, functional form, robustness, properties and sensitivities. (v)
The treatment of collateral. The treatment of LGD segmentation granularity. The quality of the model output in terms of economic and business meaning. This can rely on comparables based on data available outside of the institution. (vi)
The existence of spurious accuracy and excessive generalisation. In particular, the validation process should report the excessive usage of average LGD employed across a large population of heterogeneous obligors. (vii)
Back-testing of modelled LGD, estimated separately for defaulted and non-defaulted obligors.
5 Macroeconomic Models
5.1 Scope
5.1.1
Macroeconomic models (“macro models”) are primarily employed by UAE institutions for the estimation of Expected Credit Loss (“ECL”) and for internal and regulatory stress testing purpose. The objective of this section is to provide guidance and set the Central Bank’s expectation applicable to all macroeconomic models used by institutions. The practices described in this section are in compliance with current accounting principles.
5.1.2
In this context, macro models are defined as statistical constructions linking macro variables (“independent variables”) to an observed risk or business metrics, typically PD, Credit Index, LGD, cost of funds, or revenues (“dependent variables”). Several types of macro models exist. A common approach relies on time series regression techniques, which is the main focus of this section on macro models. Other approaches include (i) for retail clients, vintage-level logistic regression models using directly macroeconomic drivers as inputs and (ii) for corporate clients, structural models using macro variables as inputs.
5.1.3
Irrespective of the methodology employed, institutions should use judgement and critical thinking, where statistical techniques are coupled with causality analysis. Institutions should justify and balance (i) statistical performance, (ii) business intuition, (iii) economic meaning, and (iv) implementation constraints. Statistical methods and procedures will only provide part of the solution. Therefore, rigorous modelling techniques should be coupled with sound economic and business judgement in order to build and choose the most appropriate models. The key modelling choices and the thought process for model selection should be rigorously documented and presented to the Model Oversight Committee.
5.1.4
The modelling decision process should be driven by explorations, investigations, and comparisons between several possible methods. Note that time series regression models have been proven to yield the most intuitive results over other techniques.
5.1.5
When developing macro models, institutions should follow a clear sequential approach with a waterfall of steps. Depending on the outcome, some steps may need to be repeated. Each step should be documented and subsequently independently validated. In particular, for time series regression models, the process should include, at a minimum, the steps presented in the table below.
Table 8: Sequential steps for the development of macro models
# Step 1 Data collection 2 Analysis of the dependent variables 3 Analysis of the macro variables 4 Variable transformations 5 Correlation analysis 6 Model construction 7 Statistical tests 8 Model selection 9 Monitoring and validation 10 Scenario forecasting 5.2 Data Collection
5.2.1
In order to proceed with macroeconomic modelling, institutions should collect several types of time series. This data collection process should follow the requirements articulated in the MMS.
5.2.2
At a minimum, these time series should be built with monthly or quarterly time steps over an overall period of five (5) years covering, at least, one economic cycle. Institutions should aim to build longer data series. The following data should be collected.
5.2.3
Macro variables: Institutions should obtain macro variables from one or several external reliable sources.
(i)
The scope of variables should be broad and capture appropriately the evolution of the economic environment. They will typically include national accounts (overall and non-oil, nominal and real), oil production, real estate sector variables, CPI, crude oil price and stock price indexes. (ii)
Institutions should collect macro data pertaining to all jurisdictions where they have material exposures (at least greater than ten percent (10%) of the total lending book, excluding governments and financial institutions). (iii)
Institutions should document the nature of the collected variables, covering at a minimum, for each variable, a clear definition, its unit, currency, source, frequency, and extraction date. (iv)
Institutions should ensure that all variables employed for modelling will also be available for forecasting.
5.2.4
Historical default rates: Macro-PD models (or macro-to-credit index models) stand at the end of a chain of models. They are employed to make adjustments to the output of TTC PD models, themselves linked to rating models. Therefore the default data used for macro-PD modelling should reflect the institution’s own experience. If external default data points are used, justification should be provided. Finally, institutions are encouraged to also include restructuring and/or rescheduling events in their data to better capture the relationship between obligor creditworthiness and the economic environment.
5.2.5
Historical recovery rates: Macro-LGD models are designed to adjust the output of TTC LGD models. Consequently, the recovery data employed for macro-LGD modelling should reflect the institution’s own experience. If external recovery data points are used, justification should be provided.
5.2.6
Macro data series are mostly available with quarterly or even annual data points and rarely with monthly time intervals. Consequently, interpolation techniques may need to be developed. Institution should include interpolation methodology as part of the data transformation step. Such interpolation should be documented and included in the validation process.
5.3 Analysis of the Dependent Variables
5.3.1
Institutions should demonstrate that default series are suitable for modelling and are representative of their current portfolio. For that purpose, they should employ judgement and critical thinking when analysing the data. At a minimum, they should perform an analysis of the dependent variables through descriptive statistics, covering the distribution followed by each dependent variable and the identification of outliers, if any. Upon this analysis, a clear statement should be made regarding the suitability of the data for macro modelling. Consideration should be given to (i) the data quality, (ii) length, and (iii) representativeness. This analysis should be fully described in the model development documentation.
Business consistency: Institutions should pay attention to the business significance of the historical data related to the dependent variable. One possible conclusion is that historical data of a given variable is no longer an appropriate representation of the current institution’s portfolio because the segment business strategy has changed materially. In the case of default and recovery rates, conservatism prevails.
(i)
The institution may believe that its current portfolio is less risky than its historical portfolio and that it expects to experience lower default rates and/or losses in the future. In that case, the existing historical default series should be used for a reasonable period until there is enough evidence supporting the new risk profile. Subsequently, adjustments are permitted on the forecasted values, for instance in the form of scalers. (ii)
The institutions may believe that its current portfolio is more risky than its historical portfolios and that it will consequently experience higher default rates in the future. In that case, forecasts should be immediately adjusted, i.e. forecasted PDs and LGDs should be shifted upward.
5.3.2
Regime shifts: Institutions should identify the presence of regime shifts in all times series. These can be clearly identified by the presence of sudden permanent jumps in the data. Regime shifts tend to occur in default and recovery series due to changes in the data collection process, definition of default, recovery process or business strategies. For modelling, it is strongly recommended to avoid using time series with regime shifts as direct model inputs. Instead, adjustments should be implemented such as a truncation of the series or the use of specific econometrics techniques (the introduction of a dummy variable in the model).
5.3.3
Segmentation consistency: Segmentation means splitting a statistical sample into several groups in order to improve the accuracy of modelling. This concept applies to any population of products or customers. In particular, for the construction of PD and LGD macro models, the choice of portfolio, customer and/or product segmentation has a material impact of the quality of macro models. The economic behaviours of obligors and/or products should be homogeneous within each segment in order to build appropriate models. As mentioned in the data collection section, a degree of consistency is required between macro models and other models. For macro-PD models in particular, such consistency should be analysed and documented as follows:
(i)
The granularity of segments for macro modelling should be equal or greater than the granularity of segments employed for (i) rating models, and (ii) PD term structures models. If this alignment is not possible, institutions should provide robust justifications and document them accordingly. (ii)
Institutions may decide to increase the segmentation granularity of macro models. An increase in the number of segments will lead to a reduction in segment size and in the number of observed defaults, could, in turn, reduce the statistical significance of the default rate. Therefore, increasing the segmentation granularity is permitted, provided that there is no material loss in the representativeness of the default rates.
5.3.4
Institutions should analyse and assess the impact of segmentation choices as part of the development of macro models. Several segmentation options should be considered and subject to the entire model development process described hereby. Institutions should then choose the best segmentation by assessing the quality and robustness of the macro models across several segmentation options.
5.4 Analysis of the Macro Variables
5.4.1
Institutions should perform a robust analysis of the macro variables through descriptive statistics. At minimum, this analysis should examine, amongst others, the shape of distribution to identify outliers, shape of tails, multimodality. Upon this analysis, a clear statement should be made regarding the suitability of the data for macro modelling. In particular, the analysis should consider the data quality, length and representativeness. This analysis should be fully described in the model development documentation.
5.4.2
Regime shift: Institutions should identify the presence of regime shifts in all macro time series. Regime shifts can occur in macro time series due to economic decisions such as the introduction of VAT or a large shift in interest rates. Similarly to the dependent variables, macro time series with regime shifts should be avoided or adjusted accordingly.
5.4.3
Economic consistency: Institutions should pay attention to the economic significance of the macro variables. Some macro variables provide consistently better explanatory power of risk metrics in the banking book. Conversely some variables are more challenging to interpret, consequently institutions should be cautious when using those variables for PD and LGD macro models. Particular attention is needed for the following:
(i)
Employment rate: A large proportion of employees leave the UAE upon losing their employment. Consequently, the UAE employment rate incorporates a material bias, hence it is preferable to avoid this variable to model business or risk metrics. (ii)
Interest rates: The relationship between interest rates and default rates is ambiguous. Institutions should ensure that an appropriate interpretation of the estimates is provided upon modelling PDs and LGDs. (iii)
Abu Dhabi and Dubai stock indices: These indices can suffer from a lack of liquidity therefore institutions should ensure that an appropriate interpretation of the estimates is provided upon modelling PDs and LGDs. (iv)
UAE account balances (e.g. fiscal balance, current account): By construction these variables can oscillate between positive and negative values. Consequently, a relative time differencing can lead to very high returns and uncontrollable spikes. Instead, it is recommended to normalise these variables by nominal GDP prior to using them for modelling.
5.5 Variable Transformations
5.5.1
The principles of variable transformation articulated in the MMS also apply to macro models. Variable transformations have a material impact on macro models and on ECL. Therefore, institutions should test, choose and document the most appropriate transformations applied to both the macro variables and to the dependent variable.
5.5.2
Stationarity: Modelled economic relationship should be stable over time. In the context of time series regression model, variables should be stationary in order to construct robust and meaningful econometric models. Stochastic trends, seasonality and structural breaks are most common sources of non-stationarity. This property should be tested for both the dependent and independent variables, according to the following principles:
(i)
Macroeconomic variables should meet stationarity criteria prior to be used for modelling. The absence of stationarity has adverse material consequences on macro models because it often leads to spurious correlations. Macro variables that are not stationary should either be transformed to obtain stationary series or should be excluded from the modelling process. (ii)
Even after transformations, in some circumstances full stationarity is challenging to obtain if series are short and data is scarce. In this case, institutions should use judgement and critical thinking to balance economic significance and stationarity requirement in order to assess if modelling can proceed. In this assessment, institutions should pay particular attention to the presence of trends, that often leads to spurious correlations. (iii)
To test for stationarity, standard unit root test may be used, including the Augmented Dickey-Fuller test, the Phillips-Perron test, the Kwiatkowski-Phillips-Schmidt-Shin (KPSS test). In case there is evidence of the presence of stochastic trend, standard transformations can be applied such as quarter-on-quarter or year-on-year log differencing. (iv)
Seasonality may be checked using X12 or X13 seasonal adjustment algorithms. Year-on-year differencing could also be used to remove stable seasonal patterns. Formal structural breaks tests (e.g. Chow test) may be employed if there is visual evidence of break in the series. (v)
Common stochastic trends between two variables may be explicitly modelled using the rigorous application of standard co-integration models (e.g. Engle-Granger two step method or Johansen approach). (vi)
The absence of stationarity of the dependent variable can also be addressed by a first order time differencing or by autoregressive models. However, this can potentially lead to further complexity in implementation. Institutions should use judgement in this choice provided that it is justified and clearly documented.
5.5.3
Differencing: Time differencing should be based upon the following principle. Let Xt be a time series of the macroeconomic variable X at regular time steps t. Formally we can define two types of changes: (i) backward looking returns that estimate the change of the variable over a previous horizon h and (ii) forward looking returns that estimate the change of the variable over a coming horizon h. Formally:
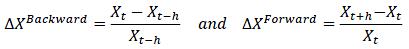
It is recommended to build macro models based on backward looking returns as these are more intuitive to interpret and easier to implement. It is also recommended to compute backward looking default rates in order to ensure that both the dependent and independent variables are homogeneous.
5.5.4
Horizon of differencing: Institutions should choose carefully the horizon of return applied to macro variables, i.e. the period used to compute the change of a variable through time. Institutions should take notes of the following principles:
(i)
For macroeconomic models, common return horizons include quarterly, half-yearly and yearly. The most appropriate return horizon should be chosen to maximize the explanatory power of the macro variables. (ii)
Note that the return horizon is not necessarily equal to the granularity of the time series. For instance, rolling yearly returns can be computed on quarterly time steps. (iii)
Institutions should be aware of the degree of noise in high frequency data. Consequently judgement should be used when using high frequency returns.
5.5.5
Lags: Variable lags should be considered in the modelling process to capture delayed effects of macro drivers. The use of large lags (more than 6 quarters) should be justified since long lags delay the impact of macro shocks on the dependent variable. For each macro variable, the choice of the most appropriate lag should be based on its statistical performance and economic meaning.
5.5.6
Smoothing: This means reducing the presence of spikes and outliers in times series. This is commonly addressed by the usage of moving average. Such practice is permitted but should be employed with caution and documented. The right balance of smoothing needs to be found. No smoothing (too much noise) in time series can lead to weak models. Alternatively, too much smoothing can dilute the strength of correlations. Smoothing techniques should be documented when applied.
5.5.7
Standard and intuitive transformations should be used. For example, the growth rate of a variable that can be zero or negative is not a meaningful measure.
5.6 Correlation Analysis
5.6.1
The objective of the correlation analysis is to assess the strength of the relationship between (i) each of the transformed dependent variable (e.g. PD) and (ii) each of the transformed macro variables, on a bilateral basis. Consequently such univariate analysis should be performed for each obligor segment. This analysis should include both statistical and causality perspectives. Relationships should make economic sense and meet business intuitions.
5.6.2
Institutions should pay attention to the strength and sign of correlations (positive vs. negative relationships) and assess whether they meet business intuitions. At a minimum, the following components should be documented: (i) the top macro variables ranked by correlation strength and (ii) comments and analysis on the observed statistical relationships vs. expected business intuitions.
5.6.3
A cut-off should be establish to eliminate the transformed macro variables that display weak and/or incoherent correlations with the independent variables. This reduced population of transformed macro variables should be used to perform multivariate analysis.
5.7 Model Construction
5.7.1
The objective of this step is to construct relevant and robust relationships between a single transformed dependent variable (e.g. PD) and several macro variables. The choice of the macro variables entering each model should be based upon the results of the correlation analysis. This process results in the construction of a range of multifactor models for each dependent variable.
5.7.2
In the context of time series regressions, institutions should choose the most appropriate methodology to perform multifactor regressions. Amongst others, it is recommended to perform multifactor regressions with or without autoregressive terms. It is recommended that institutions include several modelling forms as part the pool of possible model candidates.
5.7.3
The estimation of model coefficients should be performed with recognised professional statistical software and packages. The entire process should be fully documented and replicable by an independent party.
5.7.4
Several performance metrics should be used to rank and choose models. As these metrics depend on the type of models, institutions should use judgements to employ the most appropriate performance metrics per model type. At a minimum, the adjusted R-square should be used for multifactor regression models. For models based on the ARIMA form, a pseudo R-square should be employed as the square of the correlation between the fitted variable and the original dependent variable.
5.8 Statistical Tests
5.8.1
Standard post-estimation tests should be used to check that the underlying assumptions are appropriate for all types of macro models. The set of appropriate tests should be based on best practices in the relevant field / literature. The model development documentation should clearly indicate (i) the chosen test for each property, (ii) the nature of the H0 hypothesis, (iii) the cut-off values chosen upfront to determine the rejection or non-rejection.
5.8.2
In the context of time series regression, regression coefficients should be significant and residuals should be tested for autocorrelation and normality. The table below indicates properties that should be tested, at a minimum. Other tests may be considered, if necessary.
Table 9: Typical statistical tests for models based on time series regression
Property to be tested Description of the property to be rejected Suggested test (others may exist) Stationarity Absence of stationarity in each time series Augmented Dickey-Fuller (ADF) Co-integration Absence of stationarity in a linear combination of the dependent variable and each independent variable Engle-granger two-step method Multicolinearity High correlation between the independent variables Variance Inflation Factor Coefficient significance The coefficients are not statistically significantly different from zero Coefficient p-value on a t-distribution Autocorrelation High correlation between the error terms of the model Ljung-Box test Heteroscedasticity Absence of relationship between independent variables and residuals Breusch-Pagan or White test Normality Normal distribution of the residuals Shapiro Wilk 5.9 Model Selection
5.9.1
The model and macroeconomic variable selection should be based on clearly defined performance criteria using a transparent selection algorithm. The final model should be able to (i) generate values that fit the historical values of the dependent variable and (ii) generate accurate predictions.
5.9.2
For each segment, institutions should choose a final model from the list of candidate models generated from the model construction step. Statistical performance should not be the only decisive factor to choose a model. Instead, the choice of the final model should be based upon the combination of various factors. At a minimum, institutions should use the criteria outlined below. It is essential that institutions include all these criteria in the selection process. The absence of one criteria could be materially detrimental to the choice of the most relevant model.
(i)
Statistical performance:
a.
The chosen model should meet minimum requirements of performance, statistical stability and robustness as shown by the statistical indicators and their associated thresholds. Model parameters and forecasts should remain stable over time. b.
In addition, at the model development stage, it is important to examine the stability of models: out-of-sample performance and in-sample fit should be tested and compared across candidate models. A common metric employed to express model performance is the root mean square error, for which limits should be established.
(ii)
Model sensitivity: Quantitative response of the dependent variable to independent variables should be meaningful and statistically significant - both quantitatively and qualitatively. This can be examined through simulating one standard deviation change in individual dependent variables or by considering the forecast differences across alternative scenarios. (iii)
Business intuition: The chosen model should be constructed with variables and relationships that meet logical business and economic intuitions. This means that the model should be explained by causal relationships. (iv)
Realistic outcomes: Projected values should be consistent with historical observations and meet economic intuition. Any material jump and/or disconnect between historical values and forecasted should be explained. (v)
Implementation: When choosing a model, institutions should be mindful of the implementation and maintenance constraints, which should form part of the choice of the most appropriate models. For instance, some variables may not be available as frequently as expected for forecasting. Also, some model formulations may require autoregressive terms that need specific treatment during implementation.
5.9.3
In order to test the business intuition, for each candidate model, institutions should forecast the dependent variables (e.g. PD, Credit Index) under a severe downside scenario. The outcome will therefore be a range of projected dependent variables (one for each model) under the same scenario. It may become apparent that some candidate models should be excluded as they generate outputs that deviate too much from economic and business expectations.
5.9.4
Forecast Uncertainty: Projected forecast are based on mean or median values, around which uncertainty (i.e. confidence interval) inherently exists. Institutions should ensure that the model forecast uncertainty are clearly estimated, documented and reported to the Model Oversight Committee. In the context of time series regression, the confidence interval around the mean can be estimated empirically or based on the standard deviation of the residuals under the assumption of normally distributed residuals.
5.10 Validation of Macro Models
5.10.1
The validation of macro models should be performed by a different and independent party from the development team, according to the validation principles articulated in the MMS. If macro models are developed by a third party consultant, then a team within the institution or another consultant should therefore perform these independent validations.
5.10.2
Monitoring macro models may be challenging due to the low frequency of macroeconomic data. Institutions are expected to monitor the performance of macro models once a year. However, exceptional monitoring is required in the case of exceptional macroeconomic events.
5.10.3
Pre-implementation validation: This step involves the validation of the chosen macro models immediately after their development, prior to using them in production. The objective is to ensure that macro models meet a minimum level of quality and that they are fit for purpose. At a minimum, the following validation steps should be performed.
(i)
Development process: The validator should review the development process as per the principles articulated in the MMS. (ii)
Replication: The validator should replicate the final chosen model per segment and ensure that the coefficients are correctly estimated. (iii)
Statistical tests: The validator should ensure that statistical tests are correct, that cut-offs are reasonable and that statistical assumptions are correctly interpreted. This may necessitate partial replication. Additional statistical tests may be needed. (iv)
Model sensitivity: The validator should measure the elasticity of the model output to changes in each input variable. The model user and validator should be aware of the presence of independent variables that dominates other variables in a given model. (v)
Model stability: The validator should test the model stability, for instance by removing data points from the original time series (at the start or the end), re-run the regressions and re-project the dependent variable. The validator should also examine the stability of the model coefficients. (vi)
Conclusion: When deemed appropriate, the validator can make suggestions for defect remediation to be considered by the development team.
5.10.4
Post-usage validation: This is otherwise referred to as back-testing, whereby the validator should compare the realized values of the dependent variable (e.g. PD, LGD, Credit Index) against the forecasted values based on the macroeconomic scenarios employed at the time of the forecast. A conclusion should be made based pre-defined confidence intervals.
5.10.5
Upon the post-usage validation, the validator should make a clear statement regarding the suitability of the model to be used for another cycle. When deemed appropriate, the validator can make suggestions for defect remediation to be considered by the development team.
5.11 Scenario Forecasting
5.11.1
The expected practices articulated in this section relate to the regular estimation of ECL. As per current accounting requirements, institutions should estimate an unbiased and probability weighted ECL by evaluating a range of possible outcomes. Consequently, institutions should forecast economic conditions over the lifetime of their portfolio. All the macroeconomic variables employed as input in macro models should be forecasted until the longest maturity date of the institutions’ portfolio.
5.11.2
Institutions are encouraged to disclose macroeconomic scenarios in their annual reports. For this information to be meaningful, institutions should provide the values of the main economic drivers over the next three (3) years with the weight of each scenario.
5.11.3
Institutions should use the most recent set of models to forecast PD and LGD. If the most recent models are not used in the computation of ECL, this should be mentioned in monitoring and validation reports and reported to internal and external auditors because it has direct impacts on financial reporting.
5.11.4
Governance: Institutions can either develop macroeconomic forecasts internally or rely on third party providers. In both cases, a governance process should be put in place to guarantee the quality of forecasts.
(i)
If scenarios are developed internally, they should be constructed by subject matter experts with robust economic knowledge, within the institution. The scenarios should be reviewed by the Model Oversight Committee and the committee in charge of ECL oversight. (ii)
If scenarios are developed externally, institutions should put in place an internal validation process, by which the forecasts are checked, errors are adjusted and economic consistency is ensured. Even if scenarios are provided by an external party, each institution remains the owner of the economic forecasts and therefore remains accountable for inconsistencies present in those scenarios. (iii)
To support the adequate estimation of ECL, institutions should produce regular reports to present the aspects of macro scenario calibration discussed in this section. The report should address the source of scenarios, their economic consistency, their severity, weights and potential adjustments.
5.11.5
Weights and severity: As per current accounting requirements, institutions should use several weighed scenarios. At a minimum, institutions should employ one base, one upside and one downside scenario for each macro variable. In order to obtain an unbiased estimation of ECL, both the scenario weights and their associated severity should be jointly calibrated. For each variable, institutions should pay attention to the relative weight and severity of the downside scenario vs. the weight and severity of the upside scenario. Finally, it is recommended to estimate the ECL under each scenario in order to convey possible ECL volatility and support appropriate risk management.
5.11.6
Forward looking information: As per current accounting requirements, ECL should be based on forward looking information that is relevant reasonable and supportable. This should be understood as follows:
(i)
The economic information should be based on consensus, when possible, rather than a single source. (ii)
The economic forecasts should be realistic in terms of trend, level and volatility. For instance, economic forecasts assuming a constant positive inflation should not push asset prices to excessive and unrealistic levels in the long term. This feature is particularly relevant for real estate collaterals. (iii)
The divergence between the scenarios (base, upside, downside) should meet economic intuition and business sense. Such divergence should follow a logical economic narrative.
5.11.7
Benchmarks: Aside from ECL measurement, institutions employ existing scenarios for planning purposes, with varying severity and probability of occurrence. Amongst others, dedicated scenarios are used for the ICAAP, the recovery and resolution plan, and for stress testing purpose. These scenarios should not be employed as input for ECL computation because they do not represent an unbiased probability-weighted set of scenarios. Similarly, the macroeconomic scenarios provided by the CBUAE as part of regulatory enterprise-wide stress testing exercises should not be used as input for ECL computation. All these alternative scenarios can only be used as distant comparables for the ECL scenarios. However, this comparison should be made with caution because the calibration (severity, likelihood) of the ECL scenarios is likely to be different.
5.11.8
The construction of the scenarios should be economically coherent and therefore should follow a set of rules to be consistent. Let Xt be a time series of the macroeconomic variable X at regular time steps t. For the purpose of articulating this point, we will use three scenarios. The time series of X corresponding to each scenario are noted Xtbase, XtUp and XtDown .
(i)
Scenarios should be constructed in such way that their values diverge after a given date, called the forecasting date, noted ?. The time series for the three scenarios should be identical prior to the date of forecast and diverge after the date of forecast. Formally:
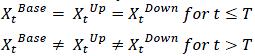
(ii)
The portfolio date noted K employed in loss computation should be close to the forecasting date. Therefore, institutions should keep updating the macroeconomic forecasts along with the portfolio date, in order to minimize the time difference between T and K. It may happen that ECL reporting is done at a higher frequency than the update of macroeconomic forecasts. In this case, the time step at which scenarios start diverging occurs before the portfolio date K. Formally, for T<K:
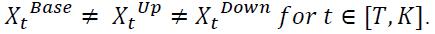
This misalignment is likely to create unwarranted effects in particular if scalers are used in PD modelling. Therefore, the maximum delay between the two dates should be no more than three months: K - T ≤ 3 months. If this difference is greater than three (3) months, the impact on the forecasted PD and LGD should be analysed and documented by the independent model validation team. (iii)
Beyond the forecasting start date, the upside and downside scenarios should not be constructed by a constant parallel shift (or scaling) of the base scenarios. Rather, the upside and downside scenarios should be constructed such that they display a gradual divergence from the base scenario through time (in growth rate terms if growth rates are applied). This property should apply to the stationary transformed macroeconomic variable. Consequently, the forecasted PD and LGD should follow the same pattern. Formally:
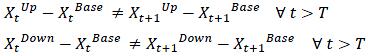
(iv)
Any scaler subsequently constructed based on these scenarios should follow the same pattern: a gradual divergence from the base scenario.
5.11.9
The principles articulated in this section about scenario forecast should also be included in the scope of review of the validation process. The validation process should test, assess and document practices for scenarios forecasts, including the governance, scenario construction and calibration.
6 Interest Rate Risk in the Banking Book
6.1 Scope
6.1.1
For the purpose of this section, and in order to simplify technical considerations, both interest rate risk (for conventional products) and profit rate risk (for Islamic products) will be referred to as Interest Rate Risk in the Banking Book (“IRRBB”). Both lead to a similar structural risk on institutions’ balance sheet.
6.1.2
Institutions should implement models to address the requirements articulated in “Interest rate and rate of return risk in the banking book Standards” issued by the CBUAE in 2018 (notice 165/2018), hereby referred to as the “CBUAE Standards on IRRBB”. In addition to the CBUAE Standards, institutions should refer to the Standards articulated by the Basel Committee on Banking Supervision in April 2016: “Interest rate risk in the banking book”, hereby referred as the “Basel Standards on IRRBB”.
6.1.3
According to the CBUAE Standards on IRRBB, interest rate risk should be captured through changes in both (i) expected earnings and (ii) the economic value of the balance sheet. In order to ensure more homogeneity in the methodology employed by institutions across the UAE, the MMG hereby presents some guidance on IRRBB modelling. The IRRBB requirements related to governance, management, hedging and reporting are covered in a separate CBUAE Standards on IRRBB.
6.2 Metrics
6.2.1
Institutions should identify all positions in interest sensitive instruments including:
(i)
All assets, which are not deducted from Common Equity Tier 1 (“CET1”) capital, and which exclude (a) fixed assets such as real estate or intangible assets and (b) equity exposures in the banking book. (ii) All liabilities, including all non-remunerated deposits, other than CE1 capital ; and (iii)
Off-balance sheet items.
6.2.2
Institutions should reconcile their exposures against their general ledger and their published financials. Differences may arise for valid reasons, which should be documented. This reconciliation process should be included in the model documentation and should be verified by the finance team on a yearly basis.
6.2.3
Changes in expected earnings and economic value can be captured through several possible metrics. At a minimum, the following metrics should be computed. These are referred as “IRRBB metrics”:
(i)
Gap risk: It is defined as the difference between future cash in-flows and cash-outflows generated by both assets and liabilities. The cash in-flows and out-flows are derived from the allocation of all relevant interest rate sensitive instruments into predefined time buckets according to their repricing or their maturity dates. These dates are either contractually fixed or based upon behavioural assumptions. The resulting metrics is the net position (gap) of the bank per future time bucket. (ii)
Gap risk duration: Also referred to as partial duration or partial “PV01”. It is defined as the modified duration of the gap per maturity bucket. The modified duration is the relative change in the present value of the position caused by a 1 basis point change in the discount factor in a specific maturity bucket. The resulting metrics is a term structure of PV01 per maturity bucket. (iii)
Economic value of equity: Also referred to as “EVE”. It is defined as the difference between the present value of the institution’s assets minus the present value of liabilities. The change in EVE (“∆EVE”) is defined as the difference between the EVE estimated with stressed discount factors under various scenarios, minus the EVE estimated with the discount factors as of the portfolio reporting date. (iv)
Net interest income: For the purpose of the MMG, and in order to simplify notations, both Net Interest Income (for conventional products) and/or Net Profit Income (for Islamic Products) are referred to as “NII”, defined as the difference between total interest (profit) income and total interest (profit) expense, over a specific time horizon and taking into account hedging. The change in NII (“∆NII”) is defined as the difference between the NII estimated with stressed interest rates under various scenarios, minus the NII estimated with the interest rates as of the portfolio reporting date. ∆NII is also referred to as earning at risk (“EAR”).
6.3 Modelling Requirements
6.3.1
The models employed to compute the metrics above should follow the principles articulated in the MMS. In particular all IRRBB models should follow the steps in the model life-cycle. The assumptions and modelling choices surrounding IRRBB models should not be the sole responsibility of the ALM function nor the market risk function. Rather, these assumptions should be presented to and discussed at the appropriate governance forum reporting to the Model Oversight Committee.
6.3.2
The modelling sophistication of the EVE should depend upon the size and complexity of institutions. For that purpose, different requirements are defined in function of their systemically important nature. The modelling requirements presented hereby should be regarded as minimum standards. To remain coherent with Basel principles, higher standards apply to large and/or sophisticated institutions (“LSI”). However, the other institutions may choose to implement models with higher standards than the one prescribed for them. This proportionality is an exception to the MMG due to the prescriptive nature of the Basel methodology surrounding IRRBB.
6.3.3
The requirements below refer to the methodology articulated in section IV (“The standardised framework”) of the Basel Standards on IRRBB. All institutions are requirements to fully understand this framework.
Table 10: Components of IRRBB models
Component LSIs Other institutions Computation
granularityFacility level or facility type if groups of facilities are homogeneous Summation of facilities within buckets, according to the Basel Standards Time buckets Granular bucketing depending on the composition of the books Standardised bucketing according to the Basel Standards on IRRBB Option risk Included in both EVE and NII Included in EVE
Optional from NIICommercial margins Optional from EVE
Included in NIIOptional from EVE
Included in NIIBasis risk Included Optional Currency Estimation for each material currency Estimation for each material currency Scenarios Standard plus other scenarios defined by institutions Standard six scenarios IT-system Dedicated system Spreadsheets can be used if the model and its implementation are independently validated 6.3.4
The estimation of EVE should be based upon the following principles: (a) it includes all banking book assets, liabilities and off-balance sheet exposures that are sensitive to interest rate movements, (b) it is based on the assumption that positions roll off, and (c) it excludes the institution’s own equity. The approach subsequently depends on the type of institutions.
(i)
LSIs should compute EVE as the difference between discounted assets and liabilities at a granular level. Institutions should aim to perform this computation at a facility level. For practical reasons, some facilities could be aggregated, provided that they are homogeneous and share the same drivers and features. All inputs including, but not limited to, cash-flows, time buckets, risk-free rates, option risk and basis risk should also be estimated at a granular level. (ii)
It should be noted that the Gap risk and the Gap risk duration are not directly used to estimate EVE in the context of a granular full revaluation. However, the Gap risk and Gap risk duration should be estimated and reported in order to manage IRRBB. (iii)
Non-LSI can compute EVE at a higher level of granularity, according to the principles outlined in the Basel Standards on IRRBB and in particular according to article 132. The methodology is based upon the summation of discounted Gap risk across time buckets, rather than a granular NPV estimation at facility level. Institutions should pay particular attention to the cash flow allocation logic in each time bucket. (iv)
Irrespective of their size, all institutions should compute ?EVE as the difference between EVE estimated under interest rate scenarios and the EVE under the current risk-free rates. The final EVE loss and the standardised risk measure employed in Pillar II capital should be computed according to the method explain in the article 132 (point 4) of the Basel Standards on IRRBB, whereby EVE loss should be aggregated across currencies and scenarios in a conservative fashion.
6.3.5
The estimation of NII should be based upon the following principles: (a) it includes all assets and liabilities generating interest rate revenue or expenses, (b) it includes commercial margins and (c) no discounting should be used when summing NII across time buckets. The approach subsequently depends on the type of institutions.
(i)
LSIs should compute NII at a granular level, both for facilities and maturity time steps. NII should be based on expected repricing dates upon institutions’ business plan of future volume and pricing. Therefore LSIs should estimate ∆NII as the difference in NII under the base and the stress scenarios. Such granular computation should include option risk and basis risk. (ii)
Non-LSIs can compute ?NII by allocating interest revenue and interest expenses in the standardised time buckets used for EVE. Non-LSI institutions can compute ?NII by estimating directly their earning at risk on each expected repricing date. (iii)
For the purpose of risk management, institutions are free to model NII based on static or dynamic balance sheet assumptions (although LSIs are recommended to employ the latter). Institutions can also choose the NII forecasting horizon. However, for Pillar II assessment as part of the ICAAP and for reporting to the CBAUE, the following, institutions should compute NII over 1 year; in addition LSIs should also compute NII over 3 years.
6.3.6
Institution’s own equity: For NII estimation, institutions should include interest-bearing equity instruments. For EVE, in the context of the MMG, institutions should compute two sets of metrics by first including and then excluding instruments related their own equity. These two types of EVE will be used for different purposes.
(i)
CET1 instruments should be excluded at all times to avoid unnecessary discrepancies related to the choice of behavioural maturity associate to this component. (ii)
Some institutions have a large proportion of interest-sensitive instruments, in particular in the AT1 components. Consequently, these institutions should estimate and report a first set of EVE sensitivities by including these instruments. This type of EVE is useful for proactive management of IRRBB. (iii)
Conversely, one of the objectives of assessing IRRBB is to ensure that institutions hold enough capital to cover such risk, which is articulated through the ICAAP. Institutions should not use part of their capital to cover a risk that is itself generated from capital. Therefore, institutions should also compute and report EVE by excluding their own equity entirely. This type of EVE is useful to estimate the Pillar II capital charge arising from IRRBB.
6.3.7
Commercial margins: The treatment of commercial margins is different between NII and EVE. However, the recommendation is similar for both LSIs and non-LSIs.
(i)
All institutions should include commercial margins in NII estimation. Margins should be adjusted based on business plans and expected customer behaviour in a given interest rate environment. For instance, it might be assumed that margins will be increased to retain depositors in a falling interest rate environment. (ii)
All institutions have the option to include or exclude commercial margins in EVE estimation. However, institutions should also aim to estimate the impact of commercial margins on EVE. For consistency, if margins are included in the cash flows (numerator), then discount factors should also reflect the corresponding credit spread of the obligors (denominator). Such estimation should be done at homogeneous pools obligors with similar credit risk profiles.
6.3.8
Basis risk: This risk arises when assets and liabilities with the same tenor are discounted with different ‘risk-free’ interest rates. Potential credit risk embedded in these rates makes them not entirely risk-free, hence the existence of bases. A typical example is an asset priced with the US LIBOR curve but funded by a liability priced with the US Overnight Index Swap (“OIS”) curve, thereby creating an LIBOR-OIS basis leading to different NPV and NII from both the asset and the liability. Another example is the recent introduction of USD Secured Overnight Financing Rate (“SOFR”) creating a LIBOR-SOFR basis. LSIs are required to fully identify and assess basis risk. They should employ the appropriate risk-free rate for each instrument type, thereby capturing basis risk in all the IRRBB metrics. While non-LSIs are not expected to fully quantify basis risk on a regular basis, they should perform an approximation of this risk to assess whether further detailed quantification is necessary.
6.3.9
Currency risk: The currencies of assets and liabilities have a material impact on the resulting IRRBB, therefore this dimension should be fully addressed by institutions’ modelling practice.
(i)
All the IRRBB metrics should be estimated for each currency in which the institution has material exposures, i.e. when the gross exposure accounts for more than five percent (5%) of either the gross banking book assets or gross liabilities. For those, the interest rate shocks should be currency-specific. (ii)
For the estimation of the capital charge, the Basel Standards on IRRBB suggests to sum the maximum change in EVE across currencies without offsetting. While the CBUAE recognises that no offsetting is conservative for pegged currencies, (typically USD/AED), institutions should manage basis risk appropriately since material bases have been observed between USD rates and AED rates. Consequently, each institution has the option to offset ?EVE between pegged currencies, only if it can demonstrate that it does capture the basis risk between these currencies with dedicated stress scenarios.
6.3.10
Non-performing assets (“NPA”): Institutions should define clearly the treatment of non-performing assets in their modelling practice, according to the following principles.
(i)
NPA (net of provisions) should be included in the estimation of EVE. In most default cases, LGD>0% therefore a recovery is estimated at some point in the future. The LGD is estimated by discounting expected recoveries with a discount rate generally based on the effective interest rate of the facility. In the context of IRRBB, a change in the interest rate environment should have an impact the present value of discounted recoveries and therefore on LGD. This effect could likely impact EVE. Finally, consideration should also be given to rescheduled facilities and/or forbearance with payment holidays where interests are accrued. The postponement could results in lower PV under scenarios with increasing rates. (ii)
The treatment of NPA (net of provisions) for NII computation is left to the discretion of banks. Under a static balance sheet assumption, non-performing assets will not generate cash inflows. A change in rates would have no impact the NII from such assets. However, under dynamic a balance sheet assumption, some NPA could return to a performing status and therefore impact NII.
6.4 Option Risk
6.4.1
Option risk constitutes a fundamental building block of IRRBB. Option risk is defined as the potential change of the future flows of assets and liabilities caused by interest rate movements. In the context of the MMG, option risk refers to deviations from either contractual maturity or expected behavioural maturity. Consequently, these options can be explicit or implicit. The exercise of these options are a function of the contractual features of the product, the behaviour of the parties, the current interest rate environment and/or the potential interest shocks. All institutions should capture option risks, irrespective of their size and sophistication.
Table 11: Categories of option risk
Financial product Risk Behavioural trigger Automatic trigger Non-maturing deposits Early redemption risk Yes No Fixed rate loans Prepayment risk and restructuring risk Yes No Term deposits Early redemption risk Yes No Automatic interest rate options Early redemption risk and prepayment risk No Yes 6.4.2
In order to model option risk appropriately, all institutions should, at a minimum, undertake the following steps:
(i) Identify all material products subject to embedded options, (ii) Ensure that assumptions employed in modelling are justified by historical data, (iii)
Understand the sensitivity of the IRRBB metrics to change in the assumptions related to option risk, and (iv) Fully document the method and assumptions used to model option risk.
6.4.3
LSIs should incorporate option risks at a granular level and undertake the necessary analysis to substantiate their assumptions. Option risk can be modelled and estimated at an aggregated level that displays similar behavioural characteristics, but the model results should be applied as a granular level. For that purpose, LSIs can use the standardised approach as a starting point and elaborate on it, in such a way that the approach meets the size and complexity of the institution. Ultimately, cash flows from assets and liabilities should be conditional upon the level of interest rates in each scenario. The methodology and assumptions employed to model optionality should be fully documented.
6.4.4
Non-LSIs should use the EVE approach articulated in the Basel Standards on IRRBB, whereby option risk is incorporated via the dependency of cash flows on interest rate levels by using conditional scalers. Subsequently, under each stress scenario with specific interest rate shocks, institutions should employ a different set of netted cash flows per bucket to compute EVE. In other words and using the Basel formulation, the cash flow CFi,c(tk) should vary for each interest rate scenario, where i, c and tk are respectively the interest rate scenario, the currency and the time bucket. The below steps explain further the standardised approach.
6.4.5
Non-maturity Deposits (“NMD”): All institutions should model option risk for NMD, as described in the Basel Standards on IRRBB, from article 110 to 115. The objective is to assess the behavioural repricing dates and cash flow profiles of NMD. In particular, institutions should undertake the following steps:
(i)
Segregate NMD into categories of depositors, considering at a minimum, retail clients, wholesale clients and Islamic products.
(ii)
Identify stable and core deposits, defined as those that are unlikely to be repriced, even under significant changes in the interest rate environment. For that purpose, institutions should analyse historical patterns and observe the change in volume of deposits over long periods. Institutions should describe the data sample and the statistical methodology used for this analysis. (iii)
For each segment, apply the caps mentioned in Table 2 of the Basel Standards on IRRBB and allocate the cash flows in the appropriate time bucket based on their estimated maturity. (iv)
Construct assumptions regarding the proportion of core deposits and their associated maturity under each interest rate scenario and in particular the potential migrations between NMD and other types of deposit. These assumptions should reflect the most likely client behaviour but with a degree of conservatism. Institutions should bear in mind the importance of portfolio segmentation on behavioural modelling.
6.4.6
Fixed rate loans: Such instruments are subject to prepayment risk because a drop in interest rates is susceptible to accelerate their early prepayment. In addition, restructuring events can also change their expected cash flow profiles. Consequently, all institutions should implement the approach mentioned in articles 120 to 124 of the Basel Standards on IRRBB. In particular, institutions should proceed as follows.
(i) Business-as-usual prepayment ratios should be estimated per product type and per currency. (ii)
These ratios should be multiplied by the scalers in Table 3 of the Basel Standards on IRRBB, that depend on the interest rate shock scenarios, in order to derive adjusted prepayment rates. If the institution has already defined prepayment rates under each scenario based on its own internal historical data, then it can use these rates, provided that they are fully documented and justified. Portfolio concentration and segmentation should be taken into account when performing such behavioural modelling. (iii)
The adjusted prepayment rates should be employed to construct the repayment schedule under a given scenario. The choice of the time buckets where the prepayments are made, should also be justified and documented.
6.4.7
Term deposits: Such instruments are subject to redemption risk because an increase in interest rates is susceptible to accelerate their early withdrawal. Consequently, all institutions should implement the approach mentioned in the articles 125 to 129 of the Basel Standards on IRRBB. In particular, institutions should proceed as follows:
(i) Business-as-usual redemption ratios should be estimated per product type and per currency. (ii)
These ratios should be multiplied by the scalers in Table 4 of the Basel Standards on IRRBB, that depend on the interest rate shock scenarios, in order to derive adjusted redemption rates. (iv)
The adjusted redemption rates should be used to derive the proportion of outstanding amount of term deposits that will be withdrawn early under a given scenario. If the institution has already defined redemption rates under each scenario based on its own internal historical data, then it can use these rates, provided that they are fully documented and justified. Portfolio concentration and segmentation should be taken into account when performing such behavioural modelling. (iii)
That proportion is finally allocated to the overnight time bucket, per product type and per currency, as per article 127 of the Basel Standards on IRRBB. (iv)
Finally, institutions should take into consideration off-balance sheet exposures in the form of future loans and expected drawings on committed facilities.
6.4.8
Automatic interest rate options: All institutions should follow the methodology articulated in the Basel Standards on IRRBB in articles 130 to 131. Automatic interest rate options should be fully taken into account in the estimation of both EVE and NII.
6.5 Interest Rate Scenarios
6.5.1
All institutions should compute ∆EVE and ∆NII under the six scenarios prescribed in Annex 2 of the Basel Standards on IRRBB and pasted in the following table. The interest rate shocks for AED can be directly derived from those corresponding to USD. For convenience, the AED shocks have been computed and provided below. For other currencies, all institutions should compute themselves the corresponding interest shocks based on the methodology outlined in the Basel Standards on IRRBB. The six interest rate shocks are as follows:
(i) Parallel shock up, (ii) Parallel shock down, (iii) Steepener shock (short rates down and long rates up), (iv) Flattener shock (short rates up and long rates down), (v) Short rates shock up, and (vi)
Short rates shock down.
6.5.2
In addition to the standard shocks prescribed by the Basel Standards on IRRBB, LSIs should define other scenarios combining shift of yield curves with changes in basis and commercial margins in order to comprehensively capture the risk profile of their balance sheet structure. These institutions should ensure that scenarios are commensurate with the nature, and complexity of their activities.
The choice of scenarios should be supported by an appropriate governance and fully documented. All institutions should integrate the IRRBB scenarios and results in their stress testing framework and in enterprise-wide stress testing exercises.
Table 12: Standard shocks per scenario (bp) for AED prescribed by the BIS method
Time Buckets (M: months ; Y: Years) Tenors
(years)(i) (ii) (iii) (iv) (v) (vi) Short-Term t = Overnight (O/N) 0.0028 200 -200 -195 240 300 -300 O/N < t <= 1M 0.0417 200 -200 -192 237 297 -297 1M < t <= 3M 0.1667 200 -200 -182 227 288 -288 3M < t <= 6M 0.375 200 -200 -165 210 273 -273 6M < t <= 9M 0.625 200 -200 -147 192 257 -257 9M < t <= 1Y 0.875 200 -200 -130 175 241 -241 1Y < t <= 1.5Y 1.25 200 -200 -106 151 219 -219 1.5Y < t <= 2Y 1.75 200 -200 -78 123 194 -194 Medium-Term 2Y < t <= 3Y 2.5 200 -200 -42 87 161 -161 3Y < t <= 4Y 3.5 200 -200 -3 48 125 -125 4Y < t <= 5Y 4.5 200 -200 28 17 97 -97 5Y < t <= 6Y 5.5 200 -200 52 -7 76 -76 6Y < t <= 7Y 6.5 200 -200 70 -25 59 -59 Long-Term 7Y < t <= 8Y 7.5 200 -200 84 -39 46 -46 8Y < t <= 9Y 8.5 200 -200 96 -51 36 -36 9Y < t <= 10Y 9.5 200 -200 104 -59 28 -28 10Y < t <= 15Y 12.5 200 -200 121 -76 13 -13 15Y < t <= 20Y 17.5 200 -200 131 -86 4 -4 t > 20Y 25 200 -200 134 -89 1 -1 6.5.3
Institutions should consider the possibility of negative interest rates and understand the impact on their balance sheet and business models. For each asset and liability, if the legal documentation of the contract stipulates a certain treatment of negative rates, then this treatment should be used. If the legal documentation is silent on the treatment of negative rates, then such negative rates should be used to price assets, but they should be floored at 0% for deposits (liabilities) because there is little evidence supporting the assumption that both retail and corporate clients would accept being charged for depositing their funds in UAE banks.
6.6 Validation of EVE and NII Models
6.6.1
Institutions should validate all EVE and NII models according to the principles articulated in the MMS and in particular related to model life cycle management.
6.6.2
The validation of EVE and NII models should be based upon the principles articulated for both deterministic and statistical models. The validation exercise should ensure that modelling decisions are justified and documented and cover all the model components presented in the previous sections. In particular, the appropriate use of data input should also be reviewed by the validator.
(i)
The validator should ensure that the mechanistic construction of these models is sound. This should be tested with partial replication and internal consistency checks. (ii)
The validator should ensure that the financial inputs are correctly flowing into these models. This step may require the join work between several teams including the risk and finance teams. (iii)
The validator should ensure that the results produced by these models are coherent. For that purpose sensitivity analysis can be performed. (iv)
Finally, some of the inputs are derived from statistical models, including the behavioural patterns observed for non-maturity deposits, fixed rate loans and term deposits. Consequently, the validation should consider the robustness, stability and accuracy of the ancillary statistical models employed to derived inputs to EVE and NII models.
6.6.3
Overall, the validation process of EVE and NII models should focus on the economic meaning and business intuition of the model outputs. The development and validation processes should not be dominated by the mechanistic aspect of these models, but also ensure that those are suitably designed to support robust decision making and the appropriate management of interest rate risk in the banking book.
7 NET Present Value Models
7.1 Scope
7.1.1
The concept of Net Present Value (“NPV”) is commonly used to estimate various metrics for the purpose of financial accounting, risk management and business decisions. This section focuses on standalone NPV models employed for the purpose of general asset valuation, covering, amongst others, investment valuation, collateral valuation and financial modelling to estimate the cost of facility rescheduling (or restructuring). The discounting component embedded in ECL, LGD and CVA models is discussed in other sections.
7.2 Governance
7.2.1
Standalone NPV models should be included in the scope of models managed by institutions. These models should be included in the model inventory and subject to the life-cycle management articulated in the MMS. The management of these models should be governed by the Model Oversight Committee.
7.2.2
These models are deterministic in substance as they do not need statistical calibrations. Therefore the recalibration step of the life-cycle does not apply to them. However, the suitability of inputs and the assumptions embedded in the model construction should be reviewed on a regular basis, or whenever there is a significant change in assumptions.
7.2.3
Institutions should establish a general consistent methodology for standalone NPV computation that follows the entire model life-cycle management, including the validation step. Independent model validation should follow the principles articulated in the MMS.
7.2.4
In addition to the regular generic validation of the approach and usage, institutions should define materiality thresholds, beyond which the valuation of specific transactions should be subject to modelling review by an independent model validator. The threshold of materiality should be clearly documented.
7.2.5
For NPV computation in the context of facility rescheduling (restructuring), the choice of methodology, inputs and assumptions should follow accounting principles.
7.3 Methodology
7.3.1
The methodology surrounding NPV computation can be split into two parts: (i) the mathematical mechanistic considerations and (ii) the choice of inputs. The mathematical considerations surrounding NPV computation are well documented in accounting rulebooks, practitioner guidelines and academic literature. Consequently, institutions have limited room to deviate from these rules and are expected to apply rigorously these principles in a transparent fashion. Institutions can exercise some judgement regarding the choice of inputs, although a tight framework is generally provided by accounting standards.
7.3.2
Mechanics: In addition to generally accepted principles, institutions should pay attention to the following:
(i)
The cash-flows from the facility or asset to be valued should reflect the contractual obligations of all parties. (ii) Contractual mechanical optionality should be reflected in the cash flow structure. (iii) Behavioural optionality should be tested. (iv)
The granularity of the time buckets should closely reflect the granularity of the cash flows. This is particularly relevant for large facility restructuring, for which cash-flows occurring at different dates cannot be grouped in the same time bucket. (v)
For the purpose of estimating the present cost of rescheduling a facility, institutions should compute the difference between the NPV of the original and the newly issued facility. The modelling mechanics described above should be identical for both the original facility and the new facility.
7.3.3
Inputs: For a given set of mechanistic rules in place, the choice of inputs has a materia impact on the NPV values produced by the model. In particular:
(i)
The discount factor should be chosen to reflect the opportunity cost of lending or investing the same notional elsewhere at a similar level of risk. It should reflect the contractual obligations of all parties involved in the transaction. (ii)
In the context of facility rescheduling (or restructuring), the discount factor employed to compute the NPV of the original and the new facilities should be based on the same effective interest rate as the contractual obligations of the original facility. (iii)
In addition, if there is evidence that the creditworthiness of the obligor has deteriorated, a credit premium should be added to the discount factor of the newly rescheduled facility. The calibration of this credit premium should be substantiated by market analysis and comparables. If no credit premium is added, justification should be provided. (iv)
In the context of facility rescheduling (or restructuring), the cash-flows of the original and new facilities should reflect the original and the new contractual obligations, respectively. This is applicable to the principal repayment flows and interest rate payments. In particular, if the interest of a restructured facility has been dropped, the received cash-flows should include lower interest payments. (v)
In the case of assets and facilities with floating interest rates or resetting rates, the source of the input rates should be clearly identified. Assumptions regarding forward rates should be based upon the term structure or interest rate at the date of valuation. (vi)
In the context of facility restructuring (or rescheduling) with floating rates or resetting rates, the reference interest rates should be identical for both the original facility and the new facility. (vii)
If several choices of inputs are envisaged for the same asset, institutions should perform several valuations under a different set of inputs and choose the most appropriate one. This choice should be clearly justified, documented and validated. The chosen set of assumptions are not necessarily those leading to the lower P&L impact.
7.4 Documentation
7.4.1
All standalone NPV models should be fully documented. The documentation should address the methodology, the assumptions and the principles behind the choice of inputs.
7.4.2
For each valuation exercise deemed material, institutions should produce dedicated documentation at the time of the exercise in order to justify the model inputs. Institutions should provide the business rationale, the economic context and the background for such valuations in order to justify the choice of inputs. This is particularly relevant for facility rescheduling (or restructuring).
7.5 Validation of NPV Models
7.5.1
All NPV models should be included in the scope of the validation exercise undertaken by the institution and in line with the principles articulated in the MMS and, in particular, the validation checks related to deterministic models.
7.5.2
The validation process should cover, at a minimum, the assumptions, inputs and usage of the general NPV methodology. In addition, the review should cover specific valuations deemed material on a sample basis to ensure that the choice of inputs are coherent with the principles articulated in the general NPV methodology documentation.
7.5.3
The general principles of the NPV computation methodology should be reviewed on a regular basis. The choice of inputs and assumptions in the context of material valuations should be reviewed for each material restructuring events.
7.5.4
The validation exercise should ensure that the model inputs reflect accurately the legal terms of both the original agreement and the new agreement. It should also ensure that the model outputs meet economic and business intuitions. This is particularly relevant for restructurings over a long time horizon where material uncertainty arises. Finally, the validation exercise should pay particular attention to the calibration of the credit spread premium in the context of a deterioration in the obligor’s creditworthiness.
Appendix
NUMERICAL THRESHOLDS INCLUDED IN THE MMG
The MMG contains several numerical thresholds that institutions should follow.The following table indicates the relevant Articles to facilitate their implementation.
Table 13: Strongly recommended practices
Section Topic Threshold Strength 2.5.2 Number of days past due used for default definition used in rating models 90 days Strongly recommended 2.9.1 Re-rating of customers upon the roll-out of a new and/or recalibrated rating model 70% within 6 months
95% within 9 monthsStrongly recommended 3.4.6 Minimum time period for the estimation of TTC PDs 5 years Strongly recommended 4.1.5 LGD floor 5% for all collaterals, unless demonstrated otherwise.
1% for cash collateral, bank guarantees and government guarantees.Strongly recommended 5.2.2 Minimum period of time series used for macro modelling 5 years Strongly recommended 6.5.2 IRRBB standard shocks See table in the corresponding section Strongly recommended Table 14: Recommended and suggested practices
Section Topic Threshold Strength 2.5.2 Number of days-past-due for default definition of low default portfolios used in rating models 60 days Suggested 4.3.6 Maximum period of recovery for incomplete default cases to be included in LGD estimation 4 years Recommended 5.2.3 Minimum size of the exposure (to total exposure) in jurisdictions where macro data should be collected. 10% Recommended 5.11.2 Period of macro-economic scenarios disclosed in annual reports 3 years Suggested 5.11.8 Maximum misalignment between the date of the portfolio and the date of the start of the macro scenarios (in ECL) 3 months Recommended 6.3.9 Minimum exposure (to total exposure) in a given currency, for which IRRBB metrics should be computed 5% of gross banking book assets or liabilities Recommended