All Licensed Financial Institutions
Laws
Central Bank & Organization of Financial Institutions and Activities Law
Fed Law 14/2018 Effective from 31/10/2018This law has been amended by The Decretal Federal Law No. (1) of 2020 Decretal Federal law No. (25) of 2020, Decretal Federal law No. (2) of 2021, Decretal Federal Law No. (9) of 2021, Decretal Federal Law (23) of 2022 and Decretal Federal Law (54) of 2023 respectively. You are viewing the latest version. Please find the PDFs of previous versions on the versioning table below.VersionsVersion 7 (consolidated as of 11/01/2023) pdf download Version 6 (consolidated as of 02/01/2023) pdf download Version 5 (consolidated as of 26/07/2021) pdf download Version 4 (consolidated as of 08/03/2021) pdf download Version 3 (consolidated as of 02/01/2021) pdf download Version 2 (consolidated as of 09/07/2020) pdf download Version 1 (effective from 31/10/2018) pdf download Decretal Federal Law No (14) of 2018 Regarding the Central Bank and Organization of Financial Institutions and Activities, and its Amendments
We, Khalifa Bin Zayed Al Nahyan, President of the United Arab Emirates,
Having perused the Constitution;
Federal Law No (1) of 1972, Regarding Jurisdictions of Ministries and Powers of Ministers, and amendments thereto;
Federal Law No (5) of 1975, Regarding the Commercial Register;
Federal Law No (10) of 1980, Regarding the Central Bank, the Monetary System and Organization of Banking, and amendments thereto;
Federal Law No (5) of 1985, Promulgating the UAE Civil Transactions Law and amendments thereto;
Federal Law No (6) of 1985, Regarding Islamic Banks, Financial Institutions and Investment Companies;
Federal Law No (3) of 1987, Promulgating the UAE Penal Code and amendments thereto;
Federal Law No (10) of 1992, Promulgating the Evidence Law in Civil and Commercial Transactions and amendments thereto;
Federal Law No (11) of 1992, Promulgating the Civil Procedures Law and amendments thereto;
Federal Law No (18) of 1993, Promulgating the Commercial Transactions Law and amendments thereto;
Federal Law No (4) of 2000, Regarding the UAE Securities and Commodities Authority and Market and amendments thereto;
Federal Law No (4) of 2002, Regarding Criminalization of Money Laundering and amendments thereto;
Federal Law No (8) of 2004, Regarding Financial Free Zones;
Federal Law No (17) of 2004, Regarding combating of Commercial Cover-up;
Federal Law No (1) of 2006, Regarding Electronic Transactions and Commerce;
Decretal Federal Law No (4) of 2007, Regarding Establishment of The Emirates Investment Authority, and amendments thereto;
Federal Law No (6) of 2007, Regarding Establishment of The Insurance Authority and Organization of its Business, and amendments thereto;
Federal Law No (6) of 2010, Regarding Credit Information;
Federal Law No (1) of 2011, Regarding the State Public Revenues;
Decretal Federal Law No (5) of 2011, Regarding Organization of Boards of Directors, General Secretariats and Committees in the Federal Government;
Federal Law No (8) of 2011, Regarding Re-organization of the State Audit Bureau;
Decretal Federal Law No (8) of 2011, Regarding Rules for Preparation of the State Budget and Final Account;
Federal Law No (4) of 2012, Regarding Organization of Competition;
Decretal Federal Law No (5) of 2012, Regarding Combating of IT Offences;
Decretal Federal Law No (7) of 2014, Regarding Combating of Terrorist Offences;
Federal Law No (12) of 2014, Regarding Reorganization of Accounts Auditors Profession;
Federal Law No (2) of 2015, Regarding Commercial Companies;
Decretal Federal Law No (9) of 2016, Regarding Bankruptcy;
Federal Law No (20) of 2016, Regarding Pledge of Movable Properties in Guarantee of Debt.
Federal Law No (7) of 2017, Regarding Tax Procedures;
Decretal Federal Law No (9) of 2018, Regarding Public Debt;
Decretal Federal Law No (10) of 2018, Regarding Netting;
And based on the proposal of the Finance Minister and approval of the Cabinet.
Promulgated the following Decretal Law:
Article (1): Definitions
In the implementation of provisions of this Decretal Law, and unless the context otherwise requires, the following words and expressions shall have the meanings cited against each:
The State: The United Arab Emirates.
The Government: The UAE Federal Government.
The Ministry: The Ministry of Finance.
The Minister: The Minister of Finance.
The Central Bank: The Central Bank of the United Arab Emirates.
The Regulatory Authorities in the State: The Central Bank, the Securities and Commodities Authority.
The Board of Directors: The Board of directors of the Central Bank.
The Governor: The Governor of the Central Bank.
The Public Sector: The Federal Government, governments of Union member emirates, and their fully owned agencies and public institutions and companies, which provide public services and do not, primarily, carry on any activities relating to money and financial markets.
Government Related Entities: A Juridical person wherein the Government, any of the governments of the Union member emirates, or any of their respective subsidiaries, owns more than fifty percent (50%) of its capital.
Financial Free Zones: Financial free zones subject to the provisions of Federal Law No (8) of 2004, Regarding Financial Free Zones, and amending laws.
Licensed Financial Institutions: Banks and Other Financial Institutions licensed in accordance with the provisions of this Decretal Law, to carry on a Licensed Financial Activity or more, including those which carry on the whole or a part of their business in compliance with the provisions of Islamic Shari’ah, and are either incorporated inside the State or in other jurisdictions, or have branches, subsidiaries or Representative Offices inside the State.
Banks: Any juridical person licensed in accordance with the provisions of this Decretal Law, to primarily carry on the activity of taking deposits, and any other Licensed Financial Activities.
Other Financial Institutions: Any juridical person, other than Banks, licensed, in accordance with the provisions of this Decretal Law, to carry on a financial activity or more, of the Licensed Financial Activities.
Higher Shari’ah Authority: The Authority referred to in Article (17) of this Decretal Law.
Exchange House: A juridical person licensed in accordance with the provisions of this Decretal Law to carry on money exchange activity, and conduct funds transfers within and outside the State, and any other businesses determined by the Central Bank.
Representative Office: An office licensed in accordance with the provisions of this Decretal Law, to carry on representation of a financial institution incorporated in other jurisdictions.
Licensed Financial Activities: The financial activities subject to Central Bank licensing and supervision, which are specified in Article (65) of this Decretal Law.
Authorized Individual: Any natural person authorized in accordance with the provisions of this Decretal Law, to carry on any of the Designated Functions.
Designated Functions: Functions of the Authorized Individual at, or for the benefit of, a Licensed Financial Institution of influential nature on the institution’s activities.
Own Funds: The Central Bank’s capital and reserves referred to in Article (5) of this Decretal Law.
Foreign Reserves: Foreign assets held by the Central Bank denominated in any reserve currency and deployed to back its liabilities.
Primary Dealers: Any bank which, acting as a principal or on behalf of another Person, purchases, sells or redeems any securities issued inside the State by the Public Sector, in accordance with the terms and conditions set by the Central Bank.
Standing Facilities: Monetary Policy tools made available to Licensed Financial Institution, to enable management of its liquidity in accordance with the controls and instructions issued by the Central Bank, in accordance with the provisions of this Decretal Law.
Financial Infrastructure System: Means either (1) a Clearing and Settlement System or (2) a Retail Payment System, established, operated, licensed, or overseen by any of the Regulatory Authorities in the State.
Designated System: Any Financial Infrastructure System designated by the Central Bank as systemically important, in accordance with the provisions of this Decretal Law.
Clearing and Settlement System: Any system established for the following purposes: (1) Clearing or settlement of payment obligations or (2) Clearing or settlement of obligations to transfer specific book-entry securities, or transfer of such securities.
Retail Payment System: Any fund transfer system and related instruments, mechanisms, and arrangements that typically handles a large volume of relatively low-value payments in such forms as cheques, credit transfers, direct debit, or card payment transactions.
Stored Value Facilities: non-cash facilities, in electronic or magnetic form, which is purchased by a user to be used as means of making a payment for goods and services.
Participant Person: In respect of a Financial Infrastructure System, shall mean any Person who is party to the arrangements for which the system has been established.
Settlement Institution: In respect of a Financial Infrastructure System, shall mean a Person (1) providing settlement accounts to the Participant Persons and to any Central Counterparty, in a Clearing and Settlement System, in order to settle Transfer Orders through the system, and provide credit facilities for settlement purposes, if necessary or (2) providing settlement services for any Retail Payment System.
Default Arrangements: In respect of a Financial Infrastructure System, means the arrangements in place within the system for limiting systemic and other types of risk in the event of a participant appearing to be, or likely to become, unable to meet his obligations in respect of a Transfer Order; and would include any arrangements that have been enforced by the system’s operator or its Settlement Institution for the following: (1) the Netting of obligations owed to or by a Participant Person; (2) the closing out of open financial position of a Participant Person, or (3) the realization of collateral securities to secure payment of obligations owed by the Participant Person.
Transfer Order: In respect of a Financial Infrastructure System, shall mean any of the following instructions: (1) instructions by a Participant Person to make funds available to another Participant Person, to be transferred, on a book-entry basis, in the accounts of the Settlement Institution for a Clearing and Settlement System; (2) or otherwise put funds within the control of a Participant Person in accordance with the rules and procedures of the Financial Infrastructure System, (3) instructions for discharge from obligation to pay, for the purposes of the operational rules of a Clearing and Settlement System; or (4) instructions by a Participant Person to either settle an obligation by transferring a book-entry security, or transferring those securities; or (5) instructions by a Participant Person that result in the assumption or discharge of retail operations payment obligation.
Netting: In respect of a Clearing and Settlement System, means the conversion of the various obligations owed to or by a Participant Person towards all the other Participant Persons in the system, into one net obligation owed to or by the Participant Person.
Reserve Requirements: The percentage of deposits held by deposit- taking licensed financial institutions, which the Board of Directors may decide to keep with the Central Bank, as per the terms and conditions it may determine.
Eligible Securities: Securities approved by the Central Bank, which Licensed Financial Institution may present as collateral for drawing from the Central Bank funds in accordance with the controls and instructions issued by the Central Bank, in accordance with the provisions of this Decretal Law.
Currency: The State’s official national currency in notes, coins, and digital form, units of which are referred to as the “Dirham”.
Monetary Base: It includes the following: (1) Issued Currency; (2) Aggregate balances of current accounts of Licensed Financial Institutions with the Central Bank, including the Reserve Requirements, in addition to any other funds deposited with the Central Bank for the purpose of clearing and settlement operations; and (3) the outstanding balance of securities and financial instruments issued by the Central Bank.
Grievances and Appeals Committee: The committee referred to in Article (136) of this Decretal Law.
Person: A natural or juridical person, as the case may be.
Year: The Gregorian calendar year.
This article has been amended by Decretal Federal Law No. (25) of 2020, and Decretal Federal Law No. (9) of 2021 and Decretal Federal Law No. (54) of 2023 respectively. You are viewing the latest version. To view previous versions, click the version boxes below.Version 3(effective from 26/07/2021 to 01/11/2023)In the implementation of provisions of this decretal law, and unless the context otherwise requires, the following words and expressions shall have the meanings cited against each:
The State: The United Arab Emirates
The Government: The UAE Federal Government
The Ministry: The Ministry of Finance
The Minister: The Minister of Finance
The Central Bank: The Central Bank of the United Arab Emirates
The Regulatory Authorities in the State: The Central Bank, the Securities & Commodities Authority.
The Board of Directors: Board of directors of the Central Bank
The Governor: The Governor of the Central Bank
The Public Sector: The Federal Government, governments of Union member emirates, and their fully owned agencies and public institutions and companies, which provide public services and do not, primarily, carry on any activities relating to money and financial markets
Government Related Entities: A Juridical person wherein the Government, any of the governments of the Union member emirates, or any of their respective subsidiaries, owns more than fifty percent (50%) of its capital
Financial Free Zones: Financial free zones subject to the provisions of Federal Law No (8) of 2004, Regarding Financial Free Zones, and amending laws
Licensed Financial Institutions: Banks and Other Financial Institutions licensed in accordance with the provisions of this decretal law, to carry on a Licensed Financial Activity or more, including those which carry on the whole or a part of their business in compliance with the provisions of Islamic Shari`ah, and are either incorporated inside the State or in other jurisdictions, or have branches, subsidiaries or Representative Offices inside the State
Banks: Any juridical person licensed in accordance with the provisions of this decretal law, to primarily carry on the activity of taking deposits, and any other Licensed Financial Activities
Other Financial Institutions: Any juridical person, other than Banks, licensed, in accordance with the provisions of this decretal law, to carry on a financial activity or more, of the Licensed Financial Activities
Higher Shari`ah Authority: The Authority referred to in Article (17) of this decretal law
Exchange House: A juridical person licensed in accordance with the provisions of this decretal law to carry on money exchange activity, and conduct funds transfers within and outside the State, and any other businesses determined by the Central Bank
Representative Office: An office licensed in accordance with the provisions of this decretal law, to carry on representation of a financial institution incorporated in other jurisdictions
Licensed Financial Activities: The financial activities subject to Central Bank licensing and supervision, which are specified in article (65) of this decretal law
Authorized Individual: Any natural person authorized in accordance with the provisions of this decretal law, to carry on any of the Designated Functions
Designated Functions: Functions of the Authorized Individual at, or for the benefit of, a Licensed Financial Institution of influential nature on the institution's activities
Own Funds: Central Bank’s capital and reserves referred to in Article (5) of this decretal law
Foreign Reserves: Foreign assets held by the Central Bank denominated in any reserve currency and deployed to back its liabilities
Primary Dealers: Any bank which, acting as a principal or on behalf of another Person, purchases, sells or redeems any securities issued inside the State by the Public Sector, in accordance with the terms and conditions set by the Central Bank
Standing Facilities: Monetary Policy tools made available to deposit-taking Licensed Financial Institution, to enable management of its liquidity in accordance with the controls and instructions issued by the Central Bank, in accordance with the provisions of this Decretal Law
Financial Infrastructure System: Means either (1) a Clearing and Settlement System or (2) a Retail Payment System, established, operated, licensed, or overseen by any of the Regulatory Authorities in the State
Designated System: Any Financial Infrastructure System designated by the Central Bank as systemically important, in accordance with the provisions of this decretal law
Clearing and Settlement System: Any system established for the following purposes: (1) Clearing or settlement of payment obligations or (2) Clearing or settlement of obligations to transfer specific book-entry securities, or transfer of such securities
Retail Payment System: Any fund transfer system and related instruments, mechanisms, and arrangements that typically handles a large volume of relatively low-value payments in such forms as cheques, credit transfers, direct debit, or card payment transactions
Stored Value Facilities: A non-cash facility, in electronic or magnetic form, which is purchased by a user to be used as means of making a payment for goods and services
Participant Person: In respect of a Financial Infrastructure System, shall mean any Person who is party to the arrangements for which the system has been established
Settlement Institution: In respect of a Financial Infrastructure System, shall mean a Person (1) providing settlement accounts to the Participant Persons and to any Central Counterparty, in a Clearing and Settlement System, in order to settle Transfer Orders through the system, and provide credit facilities for settlement purposes, if necessary or (2) providing settlement services for any Retail Payment System
Default Arrangements: In respect of a Financial Infrastructure System, means the arrangements in place within the system for limiting systemic and other types of risk in the event of a participant appearing to be, or likely to become, unable to meet his obligations in respect of a Transfer Order; and would include any arrangements that have been enforced by the system’s operator or its Settlement Institution for the following: (1) the Netting of obligations owed to or by a Participant Person; (2) the closing out of open financial position of a Participant Person, or (3) the realization of collateral securities to secure payment of obligations owed by the Participant Person
Transfer Order: In respect of a Financial Infrastructure System, shall mean any of the following instructions: (1) instructions by a Participant Person to make funds available to another Participant Person, to be transferred, on a book-entry basis, in the accounts of the Settlement Institution for a Clearing and Settlement System; or (2) instructions for discharge from obligation to pay, for the purposes of the operational rules of a Clearing and Settlement System; or (3) instructions by a Participant Person to either settle an obligation by transferring a book-entry security, or transferring those securities; or (4) instructions by a Participant Person that result in the assumption or discharge of retail operations payment obligation
Netting: In respect of a Clearing and Settlement System, means the conversion of the various obligations owed to or by a Participant Person towards all the other Participant Persons in the system, into one net obligation owed to or by the Participant Person
Reserve Requirements: The percentage of deposits held by deposit-taking financial institutions, which the Board of Directors may decide to keep with the Central Bank, as per the terms and conditions it may determine
Eligible Securities: Securities approved by the Central Bank, which Licensed Financial Institution may present as collateral for drawing from the Central Bank funds in accordance with the controls and instructions issued by the Central Bank, in accordance with the provisions of this Decretal Law
Currency: The State’s official national currency notes and coins, which its unit is referred as the “Dirham”
Monetary Base: It includes the following: (1) Issued Currency; (2) Aggregate balances of current accounts of Licensed Financial Institutions with the Central Bank, including the Reserve Requirements, in addition to any other funds deposited with the Central Bank for the purpose of clearing and settlement operations; and (3) the outstanding balance of securities and financial instruments issued by the Central Bank
Grievances & Appeals Committee: The committee referred to in Article (136) of this decretal law
Person: A natural or juridical person, as the case may be
Year: The Gregorian calendar year
Version 2(effective from 02/01/2021 to 26/07/2021)In the implementation of provisions of this decretal law, and unless the context otherwise requires, the following words and expressions shall have the meanings cited against each:
The State: The United Arab Emirates
The Government: The UAE Federal Government
The Ministry: The Ministry of Finance
The Minister: The Minister of Finance
The Central Bank: The Central Bank of the United Arab Emirates
The Regulatory Authorities in the State: The Central Bank, the Securities & Commodities Authority
The Board of Directors: Board of directors of the Central Bank
The Governor: The Governor of the Central Bank
The Public Sector: The Federal Government, governments of Union member emirates, and their fully owned agencies and public institutions and companies, which provide public services and do not, primarily, carry on any activities relating to money and financial markets
Government Related Entities: A Juridical person wherein the Government, any of the governments of the Union member emirates, or any of their respective subsidiaries, owns more than fifty percent (50%) of its capital
Financial Free Zones: Financial free zones subject to the provisions of Federal Law No (8) of 2004, Regarding Financial Free Zones, and amending laws
Licensed Financial Institutions: Banks and Other Financial Institutions licensed in accordance with the provisions of this decretal law, to carry on a Licensed Financial Activity or more, including those which carry on the whole or a part of their business in compliance with the provisions of Islamic Shari`ah, and are either incorporated inside the State or in other jurisdictions, or have branches, subsidiaries or Representative Offices inside the State
Banks: Any juridical person licensed in accordance with the provisions of this decretal law, to primarily carry on the activity of taking deposits, and any other Licensed Financial Activities
Other Financial Institutions: Any juridical person, other than Banks, licensed, in accordance with the provisions of this decretal law, to carry on a financial activity or more, of the Licensed Financial Activities
Higher Shari`ah Authority: The Authority referred to in Article (17) of this decretal law
Exchange House: A juridical person licensed in accordance with the provisions of this decretal law to carry on money exchange activity, and conduct funds transfers within and outside the State, and any other businesses determined by the Central Bank
Representative Office: An office licensed in accordance with the provisions of this decretal law, to carry on representation of a financial institution incorporated in other jurisdictions
Licensed Financial Activities: The financial activities subject to Central Bank licensing and supervision, which are specified in article (65) of this decretal law
Authorized Individual: Any natural person authorized in accordance with the provisions of this decretal law, to carry on any of the Designated Functions
Designated Functions: Functions of the Authorized Individual at, or for the benefit of, a Licensed Financial Institution of influential nature on the institution's activities
Own Funds: Central Bank’s capital and reserves referred to in Article (5) of this decretal law
Foreign Reserves: Foreign assets held by the Central Bank denominated in any reserve currency and deployed to back its liabilities
Primary Dealers: Any bank which, acting as a principal or on behalf of another Person, purchases, sells or redeems any securities issued inside the State by the Public Sector, in accordance with the terms and conditions set by the Central Bank
Standing Facilities: Monetary Policy tools made available to deposit-taking Licensed Financial Institutions, to enable management of their liquidity
Financial Infrastructure System: Means either (1) a Clearing and Settlement System or (2) a Retail Payment System, established, operated, licensed, or overseen by any of the Regulatory Authorities in the State
Designated System: Any Financial Infrastructure System designated by the Central Bank as systemically important, in accordance with the provisions of this decretal law
Clearing and Settlement System: Any system established for the following purposes: (1) Clearing or settlement of payment obligations or (2) Clearing or settlement of obligations to transfer specific book-entry securities, or transfer of such securities
Retail Payment System: Any fund transfer system and related instruments, mechanisms, and arrangements that typically handles a large volume of relatively low-value payments in such forms as cheques, credit transfers, direct debit, or card payment transactions
Stored Value Facilities: A non-cash facility, in electronic or magnetic form, which is purchased by a user to be used as means of making a payment for goods and services
Participant Person: In respect of a Financial Infrastructure System, shall mean any Person who is party to the arrangements for which the system has been established
Settlement Institution: In respect of a Financial Infrastructure System, shall mean a Person (1) providing settlement accounts to the Participant Persons and to any Central Counterparty, in a Clearing and Settlement System, in order to settle Transfer Orders through the system, and provide credit facilities for settlement purposes, if necessary or (2) providing settlement services for any Retail Payment System
Default Arrangements: In respect of a Financial Infrastructure System, means the arrangements in place within the system for limiting systemic and other types of risk in the event of a participant appearing to be, or likely to become, unable to meet his obligations in respect of a Transfer Order; and would include any arrangements that have been enforced by the system’s operator or its Settlement Institution for the following: (1) the Netting of obligations owed to or by a Participant Person; (2) the closing out of open financial position of a Participant Person, or (3) the realization of collateral securities to secure payment of obligations owed by the Participant Person
Transfer Order: In respect of a Financial Infrastructure System, shall mean any of the following instructions: (1) instructions by a Participant Person to make funds available to another Participant Person, to be transferred, on a book-entry basis, in the accounts of the Settlement Institution for a Clearing and Settlement System; or (2) instructions for discharge from obligation to pay, for the purposes of the operational rules of a Clearing and Settlement System; or (3) instructions by a Participant Person to either settle an obligation by transferring a book-entry security, or transferring those securities; or (4) instructions by a Participant Person that result in the assumption or discharge of retail operations payment obligation
Netting: In respect of a Clearing and Settlement System, means the conversion of the various obligations owed to or by a Participant Person towards all the other Participant Persons in the system, into one net obligation owed to or by the Participant Person
Reserve Requirements: The percentage of deposits held by deposit-taking financial institutions, which the Board of Directors may decide to keep with the Central Bank, as per the terms and conditions it may determine
Eligible Securities: Securities approved by the Central Bank, which deposit-taking Licensed Financial Institutions may present as collateral for drawing from the Central Bank funds
Currency: The State’s official national currency notes and coins, which its unit is referred as the “Dirham”
Monetary Base: It includes the following: (1) Issued Currency; (2) Aggregate balances of current accounts of Licensed Financial Institutions with the Central Bank, including the Reserve Requirements, in addition to any other funds deposited with the Central Bank for the purpose of clearing and settlement operations; and (3) the outstanding balance of securities and financial instruments issued by the Central Bank
Grievances & Appeals Committee: The committee referred to in Article (136) of this decretal law
Person: A natural or juridical person, as the case may be
Year: The Gregorian calendar year
Version 1(effective from 31/10/2018 to 02/01/2021)In the implementation of provisions of this decretal law, and unless the context otherwise requires, the following words and expressions shall have the meanings cited against each:
The State: The United Arab Emirates
The Government: The UAE Federal Government
The Ministry: The Ministry of Finance
The Minister: The Minister of Finance
The Central Bank: The Central Bank of the United Arab Emirates
The Regulatory Authorities in the State: The Central Bank, the Securities & Commodities Authority, and the Insurance Authority
The Board of Directors: Board of directors of the Central Bank
The Governor: The Governor of the Central Bank
The Public Sector: The Federal Government, governments of Union member emirates, and their fully owned agencies and public institutions and companies, which provide public services and do not, primarily, carry on any activities relating to money and financial markets
Government Related Entities: A Juridical person wherein the Government, any of the governments of the Union member emirates, or any of their respective subsidiaries, owns more than fifty percent (50%) of its capital
Financial Free Zones: Financial free zones subject to the provisions of Federal Law No (8) of 2004, Regarding Financial Free Zones, and amending laws
Licensed Financial Institutions: Banks and Other Financial Institutions licensed in accordance with the provisions of this decretal law, to carry on a Licensed Financial Activity or more, including those which carry on the whole or a part of their business in compliance with the provisions of Islamic Shari`ah, and are either incorporated inside the State or in other jurisdictions, or have branches, subsidiaries or Representative Offices inside the State
Banks: Any juridical person licensed in accordance with the provisions of this decretal law, to primarily carry on the activity of taking deposits, and any other Licensed Financial Activities
Other Financial Institutions: Any juridical person, other than Banks, licensed, in accordance with the provisions of this decretal law, to carry on a financial activity or more, of the Licensed Financial Activities
Higher Shari`ah Authority: The Authority referred to in Article (17) of this decretal law
Exchange House: A juridical person licensed in accordance with the provisions of this decretal law to carry on money exchange activity, and conduct funds transfers within and outside the State, and any other businesses determined by the Central Bank
Representative Office: An office licensed in accordance with the provisions of this decretal law, to carry on representation of a financial institution incorporated in other jurisdictions
Licensed Financial Activities: The financial activities subject to Central Bank licensing and supervision, which are specified in article (65) of this decretal law
Authorized Individual: Any natural person authorized in accordance with the provisions of this decretal law, to carry on any of the Designated Functions
Designated Functions: Functions of the Authorized Individual at, or for the benefit of, a Licensed Financial Institution of influential nature on the institution's activities
Own Funds: Central Bank’s capital and reserves referred to in Article (5) of this decretal law
Foreign Reserves: Foreign assets held by the Central Bank denominated in any reserve currency and deployed to back its liabilities
Primary Dealers: Any bank which, acting as a principal or on behalf of another Person, purchases, sells or redeems any securities issued inside the State by the Public Sector, in accordance with the terms and conditions set by the Central Bank
Standing Facilities: Monetary Policy tools made available to deposit-taking Licensed Financial Institutions, to enable management of their liquidity
Financial Infrastructure System: Means either (1) a Clearing and Settlement System or (2) a Retail Payment System, established, operated, licensed, or overseen by any of the Regulatory Authorities in the State
Designated System: Any Financial Infrastructure System designated by the Central Bank as systemically important, in accordance with the provisions of this decretal law
Clearing and Settlement System: Any system established for the following purposes: (1) Clearing or settlement of payment obligations or (2) Clearing or settlement of obligations to transfer specific book-entry securities, or transfer of such securities
Retail Payment System: Any fund transfer system and related instruments, mechanisms, and arrangements that typically handles a large volume of relatively low-value payments in such forms as cheques, credit transfers, direct debit, or card payment transactions
Stored Value Facilities: A non-cash facility, in electronic or magnetic form, which is purchased by a user to be used as means of making a payment for goods and services
Participant Person: In respect of a Financial Infrastructure System, shall mean any Person who is party to the arrangements for which the system has been established
Settlement Institution: In respect of a Financial Infrastructure System, shall mean a Person (1) providing settlement accounts to the Participant Persons and to any Central Counterparty, in a Clearing and Settlement System, in order to settle Transfer Orders through the system, and provide credit facilities for settlement purposes, if necessary or (2) providing settlement services for any Retail Payment System
Default Arrangements: In respect of a Financial Infrastructure System, means the arrangements in place within the system for limiting systemic and other types of risk in the event of a participant appearing to be, or likely to become, unable to meet his obligations in respect of a Transfer Order; and would include any arrangements that have been enforced by the system’s operator or its Settlement Institution for the following: (1) the Netting of obligations owed to or by a Participant Person; (2) the closing out of open financial position of a Participant Person, or (3) the realization of collateral securities to secure payment of obligations owed by the Participant Person
Transfer Order: In respect of a Financial Infrastructure System, shall mean any of the following instructions: (1) instructions by a Participant Person to make funds available to another Participant Person, to be transferred, on a book-entry basis, in the accounts of the Settlement Institution for a Clearing and Settlement System; or (2) instructions for discharge from obligation to pay, for the purposes of the operational rules of a Clearing and Settlement System; or (3) instructions by a Participant Person to either settle an obligation by transferring a book-entry security, or transferring those securities; or (4) instructions by a Participant Person that result in the assumption or discharge of retail operations payment obligation
Netting: In respect of a Clearing and Settlement System, means the conversion of the various obligations owed to or by a Participant Person towards all the other Participant Persons in the system, into one net obligation owed to or by the Participant Person
Reserve Requirements: The percentage of deposits held by deposit-taking financial institutions, which the Board of Directors may decide to keep with the Central Bank, as per the terms and conditions it may determine
Eligible Securities: Securities approved by the Central Bank, which deposit-taking Licensed Financial Institutions may present as collateral for drawing from the Central Bank funds
Currency: The State’s official national currency notes and coins, which its unit is referred as the “Dirham”
Monetary Base: It includes the following: (1) Issued Currency; (2) Aggregate balances of current accounts of Licensed Financial Institutions with the Central Bank, including the Reserve Requirements, in addition to any other funds deposited with the Central Bank for the purpose of clearing and settlement operations; and (3) the outstanding balance of securities and financial instruments issued by the Central Bank
Grievances & Appeals Committee: The committee referred to in Article (136) of this decretal law
Person: A natural or juridical person, as the case may be
Year: The Gregorian calendar year
Part I – The Central Bank –
Chapter One: Organization of the Central Bank and its Objectives
Article (2): Independence of the Central Bank
1) The Central Bank shall be considered a Federal public institution having legal personality, enjoying financial and managerial independence, and the required juridical capacity to conduct all businesses and activities, which ensure attainment of its objectives.
2) The Central Bank shall not be subject to the provisions of laws relating to public finance, tenders and auctions, public accounts and civil service, and its own regulations in these respects, shall apply.
3) The functions of State Audit Institution as per Federal Law No. (8) of 2011, Regarding Re-organization of the State Audit Institution, shall be confined to post-audit, and it shall have no right to interfere in the running of the Central Bank business, or challenge its policies.
Article (3): The Central Bank Headquarters
Headquarters of the Central Bank and its official address, along with its main branch shall be located in the State’s capital and may, upon Board of Directors approval, establish affiliated entities and open branches, offices and agencies inside and outside the State, and appoint agents and correspondents inside and outside the State.
Article (4): Principal Objectives and Functions of the Central Bank
1) Maintain the stability of the national Currency within the framework of the monetary system.
2) Contribute to the promotion and protection of the stability of the financial system in the State.
3) Ensure prudent management of the Central Bank’s Foreign Reserves.
4) Provide appropriate environment to develop and enhance the role of the insurance industry in insuring people, property and liabilities against risks to protect the national economy, encourage fair and effective competition, provide the best insurance services at competitive prices and coverage, and localize jobs in the insurance market.
For the purpose of achieving its objectives, the Central Bank shall undertake the following functions and competences:
- a. Establish and implement monetary policy while considering the State’s general strategy.
- b. Exercise the privilege of Currency issuance.
- c. Organize Licensed Financial Activities, establish the foundations for carrying them on, and determine the standards required for developing and promoting prudential practices in accordance with the provisions of this decretal law and international standards.
- d. Issuance of appropriate regulations and standards for protection of consumers of Licensed Financial institutions.
- e. Monitor the credit condition in the State, in order to contribute to the achievement of balanced growth in the national economy.
- f. Manage foreign reserves to maintain, at all times, sufficient foreign currency assets to cover the Monetary Base as per the provisions of this decretal law.
- g. Regulate, develop, oversee and maintain soundness of the Financial Infrastructure Systems in the State, including electronic payment systems, digital currency, and Stored Value Facilities.
- h. Regulate, develop and oversee the insurance sector and business, propose and implement regulating legislation in this regard.
- i. Receive requests for establishing and opening branches and representative offices for insurance and reinsurance companies, insurance agents and the professions associated therewith, and issuing the necessary licenses for them in accordance with the regulating legislation in this regard.
- j. Protect the rights of the insured and the beneficiaries of the insurance business and monitor the financial solvency of insurance companies to provide adequate insurance coverage to protect these rights.
- k. Work to raise the performance and efficiency of insurance companies and oblige them to the rules and ethics of the profession to increase their ability to provide better services to the beneficiaries of insurance, and to achieve positive competition among them.
This article has been amended by Decretal Federal Law No. (25) of 2020. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 02/01/2021)The Central Bank aims at achieving the following objectives:
1) Maintain stability of the national Currency within the framework of the monetary system.
2) Contribute to the promotion and protection of the stability of the financial system in the State.
3) Ensure prudent management of the Central Bank’s Foreign Reserves.
For the purpose of achieving its objectives, the Central Bank shall undertake the following functions and jurisdictions:
a. Draw up and implement monetary policy while considering the State’s general strategy.
b. Exercise the privilege of Currency issuance.
c. Organize Licensed Financial Activities, establish the foundations for carrying them on, and determine the standards required for developing and promoting prudential practices in accordance with the provisions of this decretal law and international standards.
d. Set up appropriate regulations and standards for protection of customers of Licensed Financial institutions.
e. Monitor the credit condition in the State, in order to contribute to the achievement of balanced growth in the national economy.
f. Manage foreign reserves to maintain, at all times, sufficient foreign currency assets to cover the Monetary Base as per the provisions of this decretal law.
g. Regulate, develop, oversee and maintain soundness of the Financial Infrastructure Systems in the State, including electronic payment systems, digital currency, and Stored Value Facilities.
Chapter Two: Capital, Reserves and Accounts of the Central Bank
Article (5): Capital and Reserves
1) The capital of the Central Bank shall be Twenty Billion (20,000,000,000) Dirhams.
2) A sum of Seventeen Billion Five Hundred Million (17,500,000,000) Dirhams shall be transferred from the General Reserve Account, to increase the capital to the amount referred to in item (1) of this article.
3) The capital may be increased by a federal decree based on a proposal of the Board of Directors, presented by the Minister, and approved by the Cabinet. Such increase shall be paid either by transfer from the General Reserve Account or directly by the Government.
4) The capital of the Central Bank may only be reduced by law.
5) The Central Bank shall establish a General Reserve Account that should not exceed four (4) times the paid up capital referred to in item (1) of this article. All net profit shall, after that, automatically devolve to the Government.
6) The Board of Directors shall, at the end of each financial year, determine the Central Bank’s annual net profits after deducting administrative and operational expenses, and allocating necessary funds for depreciation of assets and reserves, provisions for bad and doubtful debts and end of service indemnity for the staff of the Central Bank, along with the contingencies and/or other purposes the Board of Directors may determine, and in general, all other financial expenses normally deducted from net profits by banks, and the resulting net profits for each financial year shall be posted to the General Reserve Account.
7) The Cabinet shall issue a resolution specifying the percentage of profits to be retained by the Central Bank until the total balance of the General Reserve Account reaches the four (4) times limit referred to in item (5) hereof.
8) Should the balance of the General Reserve Account, at end of any financial year, be insufficient to cover the losses of the Central Bank; the deficit shall be met by the Government.
Article (6): Financial Year
The financial year for the Central Bank shall commence on the first day of January and end on the thirty-first day of December of each Year.
Article (7): Organization of Operations and Accounts
Operations of the Central Bank shall be conducted, and its balance sheet and accounts shall be organized in accordance with international standards and banking rules and customs. The Central Bank’s operations with third parties shall be deemed commercial.
Article (8): Accounts Auditing
The accounts of the Central Bank shall be audited by an auditor or more, selected, periodically, by the Board of Directors. The Board of Directors shall determine the auditors’ annual remunerations.
Article (9): Required Statements and Accounts Reports
1) Within three (3) months from end of the financial year, the Central Bank shall submit to the President of the State an annual report on the following:
- a. The Central Bank’s final accounts of the year, certified by the auditors. Such accounts shall be published in the Official Gazette.
- b. Central Bank’s activities and businesses during the financial year.
- c. An overview of monetary, banking and financial developments in the State.
2) The Central Bank shall submit the following to the Minister:
Copy of the annual report referred to in item (1) of this article.
The information the Minister may request on monetary, banking and financial developments in the State, along with semi-annual reports covering all aspects related to such developments.
A quarterly statement on the Central Bank’s assets and liabilities, which shall be published in the Official Gazette.
Chapter Three: Management of the Central Bank
Section One: The Board of Directors
Article (10): Members of the Board of Directors
The Central Bank shall be managed by a Board of Directors of seven (7) members, including the Chairman and the Governor.
This article has been amended by Decretal Federal Law No. (02) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 08/03/2021)The Central Bank shall be managed by a Board of Directors of seven (7) members, including the Chairman, Deputy Chairman and the Governor
Article (11): Members Appointment
1) Members of the Board of Directors shall be appointed by a federal decree based on recommendation of the Cabinet, and shall serve for a four (4) year term renewable for similar periods. The Decree designates from among the members of the Board of Directors one or more deputy chairman.
2) The Chairman, his Deputies and the Governor, shall each have the rank of Minister.
3) The Chairman issues a decision defining the powers of his Deputies.
4) Subject to item three (3) of this article, should the Chairman be absent or his post became vacant, the Deputy Chairman shall replace him; and should both the Chairman and his Deputies be absent or their posts became vacant, the Governor shall replace them both.This article has been amended by Decretal Federal Law No. (02) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 08/03/2021)1) Members of the Board of Directors shall be appointed by a federal decree based on recommendation of the Cabinet, and shall serve for a four (4) year term renewable to similar periods.
2) The Chairman, the Deputy Chairman and the Governor, shall each have the rank of Minister. Should the Chairman be absent or his post became vacant, the Deputy Chairman shall replace him; and should both the Chairman and his Deputy be absent or their posts became vacant, the Governor shall replace them both
Article (12): Membership Conditions
1) Be of UAE nationality.
2) Have experience in economic, financial or banking affairs.
3) Not have been declared bankrupt or ceased repaying his debts.
4) Not have been convicted of a felony or a misdemeanor involving moral turpitude or dishonesty, unless rehabilitated.
5) Not an active minister, excluding the Chairman of the Board of Directors.
6) Not a member of the Federal National Council.
7) Not holding any position, a job or board of directors’ membership of any institution licensed by any of the Regulatory Authorities in the State or by any of the regulatory authorities in the Financial Free Zones.
8) Not a controller or auditor of accounts of a Licensed Financial Institution, nor owner, agent, or partner in any accounts audit firm.
This article has been amended by Decretal Federal Law No. (1) of 2020.You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 09/07/2020)A member of the Board of Directors shall satisfy the following conditions:
1) Be of UAE nationality.
2) Have experience in economic, financial or banking affairs.
3) Not have been declared bankrupt or failed to repay his debts.
4) Not have been convicted, of a felony or a misdemeanor involving moral turpitude or dishonesty, unless rehabilitated.
5) Not an active minister or member of the Federal National Council.
6) Not holding any position, a job or board of directors’ membership of any institution licensed by any of the Regulatory Authorities in the State or by any of the regulatory authorities in the Financial Free Zones.
7) Not a controller or auditor of accounts of a Licensed Financial Institution, nor owner, agent, or partner in any accounts audit firm.
Article (13): Resignation or Vacancy of Office
Should a member of the Board of Directors resign, or his seat becomes vacant for any reason whatsoever prior to the expiry of his tenure, a successor shall be appointed, in accordance with the membership conditions referred to in Article (12) of this decretal law, for the remaining term of the Board of Directors.
Article (14): Termination of Membership
1) Membership of the Board of Directors terminates upon end of the term without renewal, or through death, or resignation. Membership of the Board of Directors may also be terminated by a federal decree, based on the Cabinet approval, in any of the following cases:
- a. If the member committed grave mistakes in the management of the Central Bank, or committed serious breach of his duties.
- b. If the member absented himself from three (3) consecutive meetings of the Board of Directors without the Board of Directors’ approval, unless such absence was due to being on an official assignment, annual or sick leave, or due to any other acceptable reason.
- c. If the member no longer satisfies any of the membership conditions referred to in Article (12) of this decretal law.
- d. If the member was rendered incapable of performing his functions, for any reason whatsoever.
2) Where term of the membership of the Board of Directors has expired without renewal, members of the Board of Directors shall continue to perform their functions until such time new members are appointed.
Section Two: Competences of the Board of Directors and its Meetings
Article (15): Powers and Functions of the Board of Directors
The Board of Directors shall, within the limitations imposed by the provisions of this decretal law, exercise all powers required for achieving the objectives for which the Central Bank has been established.
The Board of Directors shall, in particular, exercise the following:
1) Approve regulations, rules, standards, instructions and business controls to perform its functions and competences, and take all measures and actions necessary to enforce the provisions of this decretal law.
2) Establish and oversee implementation of polices for deployment and management of the Central Bank’s Own Funds and assets.
3) Decide on matters relating to issuance of the Currency and its withdrawal from circulation.
4) Issue regulations relating to organization of Licensed Financial Activities and decide on related matters, including regulations and procedures relating to supervision and oversight thereof, and determine conditions and rules for granting licenses to Licensed Financial Institutions to carry on Licensed Financial Activities and authorizations to undertake Designated Functions.
5) Approve regulations, rules, standards, instructions and business controls for insurance and reinsurance companies, insurance agents and the professions associated therewith.
6) Establish policies, and approve regulations relating to prudential supervision, and the standards and guidelines relating to Licensed Financial Activities.
7) Establish regulations and standards for protection of consumers of Licensed Financial Institutions.
8) Approve regulations, controls, and procedures for countering money laundering and combating terrorism financing and unlawful organizations.
9) Take necessary actions, procedures and impose administrative penalties against any Person violating the provisions of this Decretal Law, and regulations issued in implementation thereof.
10) Approve rules and regulations for maintaining integrity and efficiency of Financial Infrastructure Systems licensed, established, developed, or operated by the Central Bank.
11) Approve risk management and compliance policies at the Central Bank.
12) Approve Central Bank’s bylaws, issue the organizational structure and the administrative, financial and technical regulations, and determine powers and competencies, within the limitations of the provisions of this Decretal Law.
13) Approve human resources policies at the Central Bank.
14) Approve rules for the Central Bank institutional governance, including a set of rules and regulations aimed at achieving performance quality and excellence, in line with the Government’s strategic plans and objectives.
15) Decide on loans and advances granted to the Government, in accordance with the provisions of this Decretal Law.
16) Approve settlements and reconciliations relating to Central Bank’s businesses.
17) Approve the Central Bank’s annual budget and any variations thereof during the year.
18) Approve the Central Bank’s annual final accounts and the amount of net annual profits.
19) Regulate the mechanism of objections related to the insurance activity.
20) Deal with all other matters deemed within its powers, and are conducive to achievement of the objectives of the Central Bank and the discharge of its functions, in accordance with the provisions of this Decretal Law.
This article has been amended by Decretal Federal Law No. (25) of 2020, and Decretal Federal Law No. (9) of 2021 respectively. You are viewing the latest version. To view previous versions, click the version boxes below.Version 2 (effective from 02/01/2021 to 26/07/2021)The Board of Directors shall, within the limitations imposed by the provisions of this decretal law, exercise all powers required for achieving the objectives for which the Central Bank has been established. The Board of Directors shall, in particular, exercise the following:
- Issue regulations, rules, standards, instructions and business controls to perform its functions and jurisdictions, and take all measures and actions necessary to enforce the provisions of this decretal law.
- Establish and oversee implementation of polices for deployment and management of the Central Bank’s Own Funds and assets.
- Decide on matters relating to issuance of the Currency and its withdrawal from circulation.
- Issue regulations relating to organization of Licensed Financial Activities and decide on related matters, including regulations and procedures relating to supervision and oversight thereof, and determine conditions and rules for granting licenses to Licensed Financial Institutions to carry on Licensed Financial Activities and authorizations to undertake Designated Functions.
- Issue regulations, rules, standards, instructions, and work controls for insurance, reinsurance, insurance agents, and the professions and activities associated therewith.
- Establish regulations and standards for protection of customers of Licensed Financial Institutions.
- Issue regulations, controls, and procedures for encountering money laundering and combating terrorism financing and unlawful organizations.
- Take necessary actions, procedures and impose administrative penalties against any Person violating the provisions of this decretal law, and regulations issued in implementation thereof.
- Approve rules and regulations for maintaining integrity and efficiency of Financial Infrastructure Systems licensed, established, developed, or operated by the Central Bank.
- Approve risk management and compliance policies at the Central Bank.
- Approve Central Bank’s bylaws, issue the organizational structure and the administrative, financial and technical regulations, and determine powers and competencies, within the limitations of the provisions of this decretal law.
- Approve human resources policies at the Central Bank.
- Approve rules for the Central Bank institutional governance, including a set of rules and regulations aimed at achieving performance quality and excellence, in line with the Government’s strategic plans and objectives.
- Decide on loans and advances granted to the Government, in accordance with the provisions of this decretal law.
- Approve settlements and reconciliations relating to Central Bank’s businesses.
- Approve the Central Bank’s annual budget and any variations thereof during the year.
- Approve the Central Bank’s annual final accounts and the amount of net annual profits.
- Regulate the mechanism of objections related to the insurance activity in accordance with the regulating legislations in this regard.
- Deal with all other matters deemed within its powers, and are conducive to achievement of the objectives of the Central Bank and the discharge of its functions, in accordance with the provisions of this decretal law.
Version 1 (effective from 31/10/2018 to 02/01/2021)The Board of Directors shall, within the limitations imposed by the provisions of this decretal law, exercise all powers required for achieving the objectives for which the Central Bank has been established.
The Board of Directors shall, in particular, exercise the following:
1) Issue regulations, rules, standards, instructions and business controls to perform its functions and jurisdictions, and take all measures and actions necessary to enforce the provisions of this decretal law.
2) Establish and oversee implementation of polices for deployment and management of the Central Bank’s Own Funds and assets.
3) Decide on matters relating to issuance of the Currency and its withdrawal from circulation.
4) Issue regulations relating to organization of Licensed Financial Activities and decide on related matters, including regulations and procedures relating to supervision and oversight thereof, and determine conditions and rules for granting licenses to Licensed Financial Institutions to carry on Licensed Financial Activities and authorizations to undertake Designated Functions.
5) Establish policies, and issue regulations relating to prudential supervision, and the standards and guidelines relating to Licensed Financial Activities.
6) Establish regulations and standards for protection of customers of Licensed Financial Institutions.
7) Issue regulations, controls, and procedures for encountering money laundering and combating terrorism financing and unlawful organizations.
8) Take necessary actions, procedures and impose administrative penalties against any Person violating the provisions of this decretal law, and regulations issued in implementation thereof.
9) Approve rules and regulations for maintaining integrity and efficiency of Financial Infrastructure Systems licensed, established, developed, or operated by the Central Bank.
10) Approve risk management and compliance policies at the Central Bank.
11) Approve Central Bank’s bylaws, issue the organizational structure and the administrative, financial and technical regulations, and determine powers and competencies, within the limitations of the provisions of this decretal law.
12) Approve human resources policies at the Central Bank.
13) Approve rules for the Central Bank institutional governance, including a set of rules and regulations aimed at achieving performance quality and excellence, in line with the Government’s strategic plans and objectives.
14) Decide on loans and advances granted to the Government, in accordance with the provisions of this decretal law.
15) Approve settlements and reconciliations relating to Central Bank’s businesses.
16) Approve the Central Bank’s annual budget and any variations thereof during the year.
17) Approve the Central Bank’s annual final accounts and the amount of net annual profits.
18) Deal with all other matters deemed within its powers, and are conducive to achievement of the objectives of the Central Bank and the discharge of its functions, in accordance with the provisions of this decretal law.
Article (16): Formation of Committees and Delegation of Authorities
1) The Board of Directors may form the committees it deems appropriate to assist in the discharge of its functions and competences in accordance with the provisions of this decretal law. Such committees may be formed from within the Board of Directors, or from outside the Board of Directors. The Board of Directors may also form committees and advisory boards, which include in their membership Persons from outside the Central Bank, and shall determine the remunerations of members of such committees and boards.
2) The Board of Directors may delegate some of its powers to the Chairman, to the Governor, or to any committee derived from the Board of Directors.
3) The Board of Directors may, annually, review the terms of reference and performance of the committees formed in accordance with item (1) of this article, and may take necessary actions to ensure compliance with professional and international standards, codes of conduct and governance.
Article (17): Higher Shari’ah Authority
1) Pursuant to this decretal law, a Shari’ah authority referred to as “Higher Shari’ah Authority” affiliated to the Central Bank shall be established with a membership of not less than five (5) members and not exceeding seven (7) members, with knowledge and experience in the jurisprudence of Islamic financial transactions.
2) The Board of Directors shall approve the authority’s charter, its functions and competencies, and the mechanism for financing the costs of its establishment and continuity of work.
3) The Governor shall issue a decision to form the authority and appoint its members.
4) Licensed Financial Institutions, which carry on the whole or part of their business and activities in compliance with the provisions of Islamic Shari’ah shall bear all expenses of the Authority referred to in item (1) of this article, including remunerations, allowances and expenses of its members according to the decision issued by the Board of Directors.
5) The Higher Shari’ah Authority shall determine the rules, standards, and general principles applicable to Shari’ah-compliant Licensed Financial Activities and business, and shall undertake supervision and oversight of the internal Shari’ah supervisory committees of Licensed Financial Institutions, referred to in Article (79) of this decretal law.
6) The Higher Shari’ah Authority shall approve Islamic monetary and financial tools issued and developed by the Central Bank to manage monetary policy operations within the State, and provide its opinion regarding the specific regulatory rules and instructions relating to the operations and activities of Licensed Financial Institutions which conduct the whole or part of their business and activities in accordance with the provisions of Islamic Shari’ah.
7) The Fatawa and opinions of the Higher Shari’ah Authority shall be binding on the internal Shari’ah supervisory committees, referred to in Article (79) of this decretal law, and on Licensed Financial Institutions which conduct the whole or part of their business and activities in accordance with the provisions of Islamic Shari’ah.
8) The Higher Shari’ah Authority may seek assistance of a specialized entity, if deemed necessary, to conduct a Shari’ah external audit of the business of any Licensed Financial Institution, which carry on the whole or part of their business and activities in accordance with the provisions of Islamic Shari’ah, and the conditions and procedures determined by the Authority, at the expense of the concerned institution.
This article has been amended by Decretal Federal Law No. (09) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 26/07/2021)1) Pursuant to this decretal law, an authority named “Higher Shari`ah Authority” shall be established with a membership not less than five (5) members and not exceeding seven (7) members, of sufficient knowledge and experience in the jurisprudence of Islamic financial transactions.
2) The Board of Directors shall issue a decision to form the authority and appoint its members. The decision shall determine the work mechanism of the authority, its functions, and responsibilities of its members and their term of office. This authority shall be affiliated to the Central Bank.
3) Licensed Financial Institutions, which carry on the whole or part of their businesses and activities in compliance with Islamic Shari`ah shall bear all expenses of the Authority referred to in item (1) of this article, including remunerations, allowances and expenses of its members and the mechanism of funding its establishment and continuity of its functioning, as determined by the Board of Directors.
4) The Higher Shari`ah Authority shall determine the rules, standards, and general principles applicable to Shari`ah-compliant businesses and Licensed Financial Activities, and shall undertake supervision and oversight of the internal Shari`ah supervisory committees of Licensed Financial Institutions, referred to in Article (79) of this decretal law.
5) The Higher Shari`ah Authority shall approve Islamic monetary and financial tools issued and developed by the Central Bank to manage monetary policy operations in the State, and provide its opinion regarding the specific regulatory rules and instructions relating to the operations and activities of Licensed Financial Institutions which conduct the whole or part of their business and activities in accordance with the provisions of Islamic Shari`ah.
6) The Fatwas and opinions of the Higher Shari`ah Authority shall be binding on the internal Shari`ah supervisory committees, referred to in Article (79) of this decretal law, as well as on Licensed Financial Institutions which conduct the whole or part of their business and activities in accordance with the provisions of Islamic Shari`ah.
7) The Higher Shari`ah Authority may seek assistance of a specialized party, if necessary, to conduct Shari`ah external audit of the business of any Licensed Financial Institution, which carry on the whole or part of their businesses and activities in accordance with the provisions of Islamic Shari`ah, and the conditions and procedures determined by the Authority, at the expense of the concerned institution.
Article (18): Appointment of Senior Central Bank Executives
The Board of Directors may, upon recommendation of the Governor, appoint senior Central Bank executives, with titles of deputy, assistant governors, or any other titles the Board of Directors deems appropriate. The decision appointing the deputies and assistants shall determine their competences, salaries, and remunerations.
Article (19): Working Full Time for the Central Bank
1) The Governor, his deputies and assistants shall devote their full time to their work at the Central Bank, and none of them may hold any paid or unpaid position, or be a member of the Board of Directors of any of the Regulatory Authorities in the State, or in the Financial Free Zones or the Board of Directors of any Licensed Financial Institution, or enter, directly or indirectly, in any contracts concluded by the Public Sector.
2) The prohibition referred to in item (1) of this article shall not apply to assignments entrusted to any of them by the Government in the Public Sector, including representation in international conferences, or representation of the Public Sector in the various committees, subject to the approval of the Board of Directors.
Article (20): Remunerations and Entitlements
The Board of Directors shall set up a regulation regarding remunerations of the Governor and his other entitlements, and the remunerations of the Chairman and members of the Board of Directors. A federal decree, in this respect, shall be issued.
Article (21): Meetings of the Board of Directors
1) The Board of Directors shall, upon invitation by the Chairman, hold an ordinary meeting, at least once every sixty (60) days.
2) The Chairman of the Board of Directors may call the Board of Directors to convene whenever the need arises.
3) The Chairman of the Board of Directors shall convene the Board of Directors upon request of, at least, three (3) members of the Board of Directors.
Article (22): Meetings Quorum
Five (5) members of the Board of Directors including the Chairman of the Board of Directors, one of his deputies, or the Governor, shall constitute quorum for any meeting.
Decisions of the Board of Directors shall be adopted by a majority vote of the members present. In case of a tie, the Chairman of the session shall have the casting vote.
This article has been amended by Decretal Federal Law No. (02) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 08/03/2021)1) Five (5) members of the Board of Directors including the Chairman of the Board of Directors, his deputy, or the Governor, shall constitute quorum for any meeting.
2) Decisions of the Board of Directors shall be adopted by a majority vote of the members present. In case of a tie, the Chairman of the session shall have the casting vote
Section Three: Powers of the Chairman and the Governor
Article (23): Powers of the Chairman
Without prejudice to the powers and competencies of the Chairman of the Board of Directors, the Governor shall be the legal representative of the Central Bank, and shall sign, on its behalf, all instruments, contracts and documents.
This article has been amended by Decretal Federal Law No. (25) of 2020. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 02/01/2021)The Chairman of the Board of Directors shall be the legal representative of the Central Bank and shall sign, on its behalf, all instruments, contracts and documents. The Chairman may delegate some of his powers and competencies to the Governor
Article (24): Responsibilities of the Governor
Without prejudice to any competencies established for the Board of Directors or the Chairman of the Board of Directors, the Governor shall conduct and manage all the affairs of the Central Bank, and issue regulations, systems and policies approved by the Board of Directors. The Governor shall be responsible for the implementation of this Decretal Law, the regulations of the Central Bank and decisions of the Board of Directors. He may delegate some of his powers and competencies to any of his deputies, assistants, or some senior staff of the Central Bank.
This article has been amended by Decretal Federal Law No. (09) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 26/07/2021)The Governor shall be responsible for the implementation of this decretal law, the regulations of the Central Bank and decisions of the Board of Directors. He may delegate some of his powers and competencies to any of his deputies, assistants, or some senior staff of the Central Bank
Section Four: Other Provisions
Article (25): Exemption from Liability
1) The Central Bank, members of the Board of Directors, members of committees formed by the Board of Directors, whether from within its membership or from outside, staff of the Central Bank and its duly authorized representatives, shall be exempt from civil liability towards third parties, in respect of the following:
- a. Exercise, or failure to exercise, the functions, powers, authorities and businesses of the Central Bank, or their own functions, competencies and powers, authorities, and all related practices;
- b. Instructions, guidelines, declarations, data, statements and opinions given by them in relation to the practice of the Central Bank’s functions, powers, authorities and businesses, or their own functions, competencies, authorities and businesses – unless bad faith, with intent to harm third parties, was established.
2) The Central Bank shall bear all charges, costs, expenses, and attorney fees relating to the defense of the Persons referred to in item (1) of this article, in lawsuits pertaining to discharge of their functions at the Central Bank.
Article (26): Confidential Information
1) Any member of the Board of Directors, any member of the committees formed by the Board of Directors, any employees or representatives of the Central Bank; any experts, technical personnel, or academics the Central Bank deals with, shall not disclose any information that is confidential, unless such disclosure is consistent with the provisions of item (3) of this article. This prohibition shall remain effective even after the expiry of membership or termination of the service or the function.
2) Confidential information shall include all information received by any of the Persons referred to in item (1) of this article, by virtue of their positions, or in the course of discharging their functions, as long as such information were not made available to the public through official or legal means.
3) Without prejudice to the provisions of Article (28) of this Decretal Law, confidential information may be disclosed where such disclosure is permitted, legally enforced, or addressed to authorities and agencies within the State or in other jurisdictions.
Article (27): Declaration of Conflict of Interest
1) A member of the Board of Directors shall, upon his appointment, declare his interests, which may conflict with his membership at the Board of Directors, and whenever a conflict of interest arises. Should any member of the Board of Directors have a personal interest in any contract or dealing to which the Central Bank is party, such member must declare those interest prior to the discussion of the subject; withdraw from the meeting when such dealing or contract is discussed, and should not participate in voting pertaining thereto, in accordance with the code of conduct and governance rules issued by the Board of Directors.
2) Every employee or representative of the Central Bank shall disclose to his manager, or his immediate superior, any interest which may be in conflict with the discharge of his functions, and he may not participate in exchange of opinions, and decisions or measures, taken in this regard.
3) The Board of Directors shall establish codes of conduct for employees and representatives of the Central Bank, as well as disclosure procedures, compliance, and governance.
Article (28): Cooperation with Local and International Authorities
1) The Central Bank may, within the scope of its jurisdiction and in accordance with the Law, cooperate with the concerned regulatory authorities in other countries, and with international institutions, in providing assistance and exchanging information, subject to the following:
- a. The request is made on basis of reciprocity.
- b. The request does not contravene any of the State’s established laws and regulations.
- c. The request is serious and important.
- d. The request is not in conflict with the public interest and public order requirements.
2) The Central Bank shall, in coordination and collaboration with the concerned regulatory authorities, within applicable laws, exercise its powers on Licensed Financial Institutions operating outside the State or in Financial Free Zones.
Article (29): Engagement of Experts, Technical Personnel and Academics
The Central Bank may seek the assistance of experts, technical personnel and academics, determine their remunerations and entitlements. The Board of Directors may also invite to its meetings whomever it wishes to hear their opinion on a specific issue, and such invitee to the meeting shall have no counted vote in deliberations.
Article (30): Publication of Draft Rules and Regulations
1) The Central Bank may publish the draft regulations and rules it intends to issue in relation to organization of businesses of Licensed Financial Institutions and Licensed Financial Activities, for their feedback, via a public notice to the concerned parties.
2) The Central Bank may invite concerned parties to provide their feedback on the draft rules and regulations referred to in item (1) of this article, within the period prescribed by the Central Bank.
3) The Central Bank may decide not to publish the draft regulations referred to in item (1) of this article, if it deems such publication contrary to public interest, or to the achievement of the Central Bank’s objectives and discharge of its functions.
Chapter Four: Monetary Policy and Financial Stability
Article (31): Objectives of Monetary Policy
1) Monetary policy aims at maintaining soundness and stability of the monetary system in the State, in order to ensure stability and required confidence in the national economy.
2) The Central Bank shall determine monetary tools and operational means for achievement of monetary policy objectives, including policies relating to management of the exchange rate of the national Currency and money markets in the State.
3) The Central Bank shall, on the basis of a proposal by the Board of Directors and approval of the Cabinet, determine the national Currency’s exchange rate regime.
4) The Central Bank may, for operational purposes, take necessary measures to manage and control the official exchange rate of the national Currency, as per the guiding principles set by the Board of Directors.
Article (32): Reserve Requirements
1) The Central Bank may, in line with monetary policy objectives and the current and forecasted status of liquidity, determine minimum Reserve Requirements for each type of deposits, or on the total of deposits held with deposit-taking Licensed Financial Institutions. The Board of Directors shall determine the manner in which ratio of the Reserve Requirements is calculated, as it deems appropriate.
2) The Central Bank shall specify all operational arrangements related to the maintenance of the Reserve Requirements referred to in item (1) of this article.
Article (33): Credit Conditions Surveillance
The Central Bank may set regulations which determine limits of credit facilities extended by Licensed Financial Institutions to their customers, compared to the total of their stable resources or to the total deposits of their customers. Such limits may be prescribed for a specific Licensed Financial Institution or for all Licensed Financial Institutions.
Article (34): Coordination between Monetary Policy and Fiscal Policy
The Central Bank and the Ministry shall establish a mechanism for coordinating monetary policy and fiscal policy for the purpose of achieving balanced growth in the national economy. Such coordination shall take place before the beginning of each financial year, and whenever necessary, and shall be in respect of volume of government expenditure, the Government’s debt, and debts of governments of emirates members of the Union, along with debts of Government Related Entities, companies and institutions which they own, hold shares in, or manage, and their plans regarding domestic and foreign public debt.
Article (35): Designating Systemically Important Licensed Financial Institutions
The Central Bank shall solely have the authority to designate any Licensed Financial Institution as systemically important. For such purpose, the Central Bank may require the designated Licensed Financial Institution to take the needed measures and procedures.
Article (36): Domestic Market Statistics
1) The Public Sector and other agencies as the Board of Directors deems necessary, shall provide the Central Bank with all the information and statistics it requires for the purpose of performing its functions under the provisions of this Decretal Law. Such information and statistics shall include all monetary and economic statistics, as well as balance of payments statistics and consumer prices. The Central Bank may publish the statistics it deems appropriate, in whole or in part.
2) The Central Bank shall obtain the approval of other Regulatory Authorities in the State regarding provision and/or publication of non- public information and statistics in relation to institutions under the supervision of those authorities.
Article (37): Research
1) The Central Bank may conduct research and analyses in areas of macro-economy, conduct of monetary policy, and banking and financial operations, as deemed of strategic importance to the State economy.
2) The Central Bank shall publish and issue regular statistical reports, quarterly and annual reviews of the Central Bank, policy briefs and working papers that contain analyses of the relevant data to ensure the soundness and effectiveness of policy decisions.
Chapter Five: Central Bank Operations
Section One: Operations with the Public Sector
Article (38): Advisor to the Government
The Central Bank shall advise the Government on matters falling within its jurisdiction, and shall provide its opinion on monetary, banking, and financial affairs as requested by the Government.
Article (39): Financial Agent for the Government
1) The Central Bank shall participate in negotiations relating to the Government’s international monetary and financial agreements, and it may be assigned implementation of provisions of such agreements.
2) The Central Bank may, directly or through Primary Dealers, sell and manage securities issued or secured by the Government or governments of emirates members of the Union, in accordance with an agreement with the concerned government.
Article (40): Bank for the Government
1) For the purposes of achieving objectives of its monetary policy, and in order to provide the Government and governments of emirates members of the Union with their needs for national Currency and/or foreign currencies, the Central Bank shall buy or sell foreign currencies to the concerned government, at prevailing exchange rates.
2) The Central Bank shall conduct banking operations and services for the Government, whether in the State or in other jurisdictions, against fees. The Central Bank may also perform banking operations and services for governments of member emirates of the Union, against fees.
3) The Government and governments of emirates members of the Union, shall open accounts in national Currency and foreign currencies with the Central Bank, and conduct transfers through such accounts.
4) Government funds in national Currency or foreign currencies shall be deposited with the Central Bank, and the latter shall pay or charge interest thereon in view of the prevailing market rates. Governments of emirates members of the Union may also deposit funds in national Currency or foreign currencies with the Central Bank, on which the latter shall pay or charge interest thereon in view of the prevailing market rates.
5) Public Sector entities, other than the Government, and governments of emirates members of the Union, may deposit their funds in national Currency or foreign currencies with the Central Bank. The Central Bank shall pay or charge interest thereon as determined by the Central Bank.
6) The Central Bank may grant advances or other credit facilities to the Government, at interest rates set in accordance with the terms and conditions of the agreement signed between the Central Bank and the Ministry in this regard, provided such advances and credit facilities are for the purpose of covering a temporary, unforeseen deficit in Government revenues, compared to its expenses. The Government may not relend or grant such advances to any other party. Granted advances shall at no time exceed ten percent (10%) of the government’s average revenues realized in the budgets of the last three (3) years. The Government shall repay these advances within a period not exceeding one (1) year from date of granting thereof. In case advances were not repaid at the specified date, the outstanding balance should be subject to an interest charge, as specified in the agreement signed between the Central Bank and the Ministry.
7) The Central Bank may subscribe to securities and debt instruments issued by the Government for maturities exceeding one (1) year, only in cases designated by the Board of Directors. The Government shall repay the amounts due, including interest, on maturity dates. In case of late or early payment an interest charge shall be imposed, as specified in the debt agreement.
Article (41): Investment and Deployment of Government Funds
Apart from the funds deposited with the Central Bank in accordance with the provisions of Article (40) of this Decretal Law, the Central Bank may not interfere in the investment and deployment of Government funds or funds of governments of emirates, members of Union, unless it has been assigned to do so per the agreement concluded between the concerned government and the Central Bank.
Section Two: Operations with Financial Institutions, Monetary Authorities, and other Central Banks
Article (42): Opening of Accounts and Maintaining Financial Balances in Digital Currency
First: The Central Bank may open the following accounts:
1) Currency or foreign currencies accounts for Licensed Financial Institutions, and accept deposits from them. The Central Bank shall pay or charge agreed interest on such deposits.
2) Accounts for monetary authorities, other Central Banks, foreign banks, international financial and monetary institutions, as well as Arab and international monetary funds. The Central Bank may pay or charge interest on such accounts, and act as agent or correspondent for these parties.
3) Accounts with monetary authorities, other Central Banks, foreign banks, international financial and monetary institutions, as well as Arab and international monetary funds.
4) The Central Bank may open any other accounts within the limits and in accordance with the rules and regulations issued by the Board of Directors.
Second: The Central Bank may maintain other forms of digital currency financial balances, whatever their type, within the limits and in accordance with the rules and regulations issued by the Board of Directors.
This article has been amended by Decretal Federal Law No. (54) of 2023. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 01/11/2023)1) The Central Bank may open the following accounts:
a. National Currency or foreign currencies accounts for Licensed Financial Institutions, and accept deposits from them. The Central Bank shall pay or charge agreed interest on such deposits.
b. Accounts for monetary authorities, other Central Banks, foreign banks, international financial and monetary institutions, as well as Arab and international monetary funds. The Central Bank may pay or charge interest on such accounts, and act as agent or correspondent for these parties.
2) The Central Bank may open accounts with monetary authorities, Central Banks, foreign banks or international financial and monetary institutions, as well as Arab and international monetary funds
Article (43): Money and Capital Markets Operations
The Central Bank may conduct the following money and capital markets operations:
1) Purchase, re-purchase, sell, and accept and place deposits of gold bullion or coins and precious metals.
2) Accept and place monetary deposits and pay or charge interest thereon, subject to the provisions of Article (62) of this Decretal Law.
3) Issue bills payable upon demand and other types of payable financial transfers, at its head office, branches, and offices of its agents or correspondents.
4) Conduct all foreign currency operations and external transfer operations with the Government, governments of emirates members of the Union, public entities, local and foreign banks, licensed Exchange Establishments, other monetary authorities and Central Banks, and other Arab and international financial institutions and funds.
5) Issue securities in the name of the Central Bank, and sell and re- purchase, discount and rediscount, redeem such securities for the purposes of managing monetary policy operations.
6) Purchase, re-purchase, sell, discount and rediscount Eligible Securities and other securities related to the management of its Own Funds and/ or Foreign Reserves as per established terms and conditions.
7) Purchase, re-purchase, and sell Shari’ah-compliant commodities and securities, in order to develop liquidity management instruments for Licensed Financial Institutions, which carry on the whole or part of their business and activities in compliance with the provisions of Islamic Shari’ah.
8) Grant collateralized loans, advances, other credit facilities, and Shari’ah- compliant funding facilities to Licensed Financial Institutions, for the purpose of managing monetary policy operations, in accordance with the terms and conditions the Central Bank deems appropriate and determines from time to time.
9) Grant collateralized loans and advances to monetary authorities, Central Banks, foreign banks, and international financial institutions, and obtain loans and advances therefrom, provided there is consistency of such operations with the Central Bank’s functions and jurisdictions. Interest or commission may be paid or charged for this purpose.
10) Obtain, guarantee or secure loans and advances or issue credit, in any currency inside the State or in other jurisdictions, in accordance with the terms and conditions the Central Bank deems appropriate for the purpose of conducting its own business.
11) Conduct all other operations deemed conducive to the achievement of Central Bank’s objectives.
Article (44): Protection of Licensed Financial Institutions
1) The Central Bank shall take all measures it deems appropriate to maintain conduct of operations of deposit-taking Licensed Financial Institutions, within the frameworks and limits set by the Board of Directors.
- For this purpose, the Central Bank shall:
- a) Request to hold a meeting of the general assembly of the licensed financial institution to discuss any issue the Central Bank deems important.
- b) Request to include any item that the Central Bank deems necessary into the agenda of the general assembly meeting of the licensed financial institution.
- c) Suspending the implementation of any decision issued by the general assembly of the licensed financial institution in the event that it violates the laws or regulations in force.
2) The Central Bank, according to its own discretion, in cases of necessity during which the deposit-taking licensed financial institution is exposed to liquidity pressures or is subject to crisis management procedures, may provide loans to that establishment, in order to contribute to strengthening and protecting the stability of the financial system and protecting the monetary system in the state.
This article has been amended by Decretal Federal Law No. (09) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 26/07/2021)The Central Bank shall take all necessary measures to ensure proper and effective conduct of operations of deposit-taking Licensed Financial Institutions, within the frameworks and limits set by the Board of Directors.
Article (45): Appointment of Primary Dealers
1) The Central Bank shall set-up rules to regulate securities issued by the Central Bank or the Government in coordination with the various stakeholders. Such rules shall include all aspects of these securities issuance, custody, trading in the State.
2) The Central Bank may appoint Primary Dealers for securities issued inside the State by the Central Bank or the Public Sector, in accordance with the terms and conditions set by the Central Bank.
3) For the purpose of listing securities issued by the Public Sector in the State’s financial markets, the Central Bank shall appoint Primary Dealers it approves who comply with the requirements of the concerned regulator.
Section Three: Investment of Central Bank’s Foreign Reserves and Own Funds
Article (46): Foreign Reserves
The Central Bank may, in accordance with the instructions and rules stipulated in the investment policy and guidelines approved by the Board of Directors, invest its Foreign Reserves in all or any of the following instruments:
1) Gold bullions, gold coins and other precious metals.
2) Currency notes and coins, call money, and placements in foreign countries.
3) Securities issued or secured by governments of foreign countries and related entities, or by international monetary and financial institutions.
4) Derivatives and other financial instruments required for the management of Central Bank’s exposure to interest rates, currencies, credit, gold, and other precious metals.
5) Any other financial assets the Central Bank deems appropriate for investment as foreign assets, subject to approval of the Board of Directors.
Article (47): Own Funds
The Central Bank may, in accordance with the investment policy and guidelines set by the Board of Directors, deploy or invest part of its Own Funds in the following:
1) Purchase and sell securities, and subscribe to loans issued or guaranteed by the Public Sector, or buy shares in any entity wherein the Government or governments of emirates members of the Union hold shares, or is granted a concession in the State.
2) Invest in projects, investment funds and financial institutions not licensed by the Central Bank.
3) Acquire real estate, equity and movable properties and all related matters.
Article (48): Appointment of External Parties to Manage Foreign Reserves and Own Funds
The Central Bank may appoint external parties to manage its Foreign Reserves and Own Funds, in accordance with the investment policy and guidelines set by the Board of Directors.
Chapter Six: Miscellaneous Provisions
Article (49): Establishment of Companies and Commercial or Financial Institutions
The Central Bank may, for the purpose of achieving its objectives and discharging its functions, as per provisions of Article 4 of this Decretal Law, establish, or partner with any other agency in establishing companies and commercial or financial institutions, or for any specific purpose, inside the State or in other jurisdictions, and may carry on any commercial activity, own moveable and immoveable property, as per the regulations issued by the Board of Directors.
Article (50): Privilege and Guarantee of Own Rights
1) Debts of the Central Bank shall enjoy the privilege Government debts have, over property of its debtors. The Central Bank’s debts shall be collected in the same manner and by the same means prescribed for collection of Government debts and property.
2) Save for the Reserve Requirements referred to in Article (32) hereof, the Central Bank shall have privilege over the property of Licensed Financial Institutions for payment of all its claims and dues of cash balances or assets which constitute guarantees for these claims and dues, upon maturity thereof.
3) The Central Bank may purchase, by agreement or by forced sale, or acquire real estate and movable property in settlement of its debts. Such property must be sold within the shortest possible period of time, unless the Central Bank decided to use it for the conduct of its business, in accordance with this Decretal Law.
4) The Central Bank must obtain sufficient guarantees to ensure the fulfillment of its rights, including mortgage, pledge or waiver.
5) In case its secured rights were not paid upon maturity thereof, the Central Bank may, after ten (10) days from the date its debtor was duly notified, proceed with sale of any pledged assets, without prejudice to Central Bank’s right to initiate other legal proceedings against the debtor, until its secured rights were fully paid.
6) Sale of pledged property pursuant to provisions of item (5) of this article shall be carried out by the competent court upon request of the Central Bank.
7) The Central Bank shall collect its dues from proceeds of the sale carried out pursuant to provisions of item (6) of this article. Should such proceeds exceed the Central Bank’s dues; the surplus shall be deposited with the Central Bank, at the debtor’s disposal, without paying any interest.
This article has been amended by Decretal Federal Law No. (09) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 26/07/2021)1) Debts of the Central Bank shall enjoy the privilege Government debts have, over property of its debtors. The Central Bank’s debts shall be collected in the same manner and by the same means prescribed for collection of the Government debts and property.
2) Save for the Reserve Requirements referred to in Article (32) hereof, the Central Bank shall have privilege over the property of Licensed Financial Institutions for payment of all its claims and dues of cash balances or assets which constitute guarantees for these claims and dues, upon maturity thereof.
3) The Central Bank may purchase, by agreement or by forced sale, or acquire immovable property in settlement of its debts. Such property must be sold within the shortest possible period of time, unless the Central Bank decided to use it for the conduct of its business, in accordance with this decretal law.
4) The Central Bank may accept, by way of mortgage, pledge or assignment, real estate and movable property, as collateral for payment of its rights.
5) In case its secured rights were not paid upon maturity thereof, the Central Bank may, after ten (10) days from the date its debtor was duly notified, proceed with sale of any pledged assets, without prejudice to Central Bank’s right to initiate other legal proceedings against the debtor, until its secured rights were fully paid.
6) Sale of pledged property pursuant to provisions of item (5) of this article shall be carried out by the competent court upon request of the Central Bank.
7)The Central Bank shall collect its dues from proceeds of the sale carried out pursuant to provisions of item (6) of this article. Should such proceeds exceed the Central Bank’s dues; the surplus shall be deposited with the Central Bank, at the debtor’s disposal, without paying any interest
Article (51): Financial Exemptions
1) The Central Bank shall be exempt from the following:
- a. Taxes, fees, and payments relating to its capital, reserves, Currency issuance, or income.
- b. Taxes, fees, and payments relating to its contribution, shares, or profits originating from companies and establishments it owns part of its capital.
2) The Central Bank and the companies and establishments it owns the majority of its shares shall be exempt from Court fees and bail bonds required by law.
Article (52): Security of Premises and Safe Transport of Funds and Valuables
The Government shall provide security for the Central Bank’s premises, and the security escort needed for the safe transport of funds and valuables, free of charge.
Article (53): Dissolution of the Central Bank
The Central Bank shall not be dissolved except by a law specifying the manner and timing of its liquidation.
Part II – Currency –
Chapter One: Currency Unit and Issuance
Article (54): Currency Unit
The official Currency of the State “The Dirham” shall be referred as (إ هـ د) in Arabic letters and as (AED) in Latin letters and is subdivided into one hundred (100) fills.
Article (55): Currency Issuance
Issuance of Currency shall be the exclusive right of the State. This right shall be exercised solely and exclusively by the Central Bank.
No Person shall issue or put into circulation Currency, Currency coins, or any instrument or token payable to bearer on demand having the appearance of, or purporting to be, or are likely to pass as, or be confused with legal tender in the State or in any other country.
This article has been amended by Decretal Federal Law No. (54) of 2023. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 02/10/2023)1) Issuance of Currency shall be the exclusive right of the State. This right shall be exercised solely and exclusively by the Central Bank.
2) No Person shall issue or put into circulation Currency notes, Currency coins, or any instrument or token payable to bearer on demand having the appearance of, or purporting to be, or are likely to pass as, or be confused with legal tender in the State or in any other country.
Article (56): Currency Legal Tender
Currency notes and digital currency issued by the Central Bank shall be legal tender for payment of any amount up to their full face value.
Currency coins issued by the Central Bank shall be legal tender in the State for payment of any amount with its full face value, and not exceeding fifty (50) Dirhams. Nevertheless, should such Currency coins be presented to the Central Bank, the latter must accept them without any limitation to its quantity.
This article has been amended by Decretal Federal Law No. (54) of 2023. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 01/11/2023)1) Currency notes issued by the Central Bank shall be legal tender for payment of any amount up to their full face value.
2) Currency coins issued by the Central Bank shall be legal tender in the State for payment of any amount with its full face value, and not exceeding fifty (50) Dirhams. Nevertheless, should such Currency coins be presented to the Central Bank, the latter must accept them without any limitation to its quantity.
Article (57): Currency Specifications, Features and Denominations
1) Currency notes issued by the Central Bank shall be of such denominations, designs, and specifications, and bear such features as shall be decided by the Board of Directors. Currency notes shall bear the signature of the Chairman of the Board of Directors.
2) The Board of Directors shall determine the weight, composition, mix ratios, allowed variation, and all other specifications of Currency coins as well as the quantities of each denomination to be minted.
3) The Central Bank shall make necessary arrangements for printing of Currency notes referred to in item (1) of this article, and minting of Currency coins referred to in item (2) of this article, along with all matters relating to such printing, minting and safekeeping of such Currency notes and coins and the relative plates and dies.
4) The Central Bank shall issue the forms, designs, and specifications of the digital currency, the conditions and controls for its possession, and other features determined by the Board of Directors.
5) The Central Bank shall publish decisions to issue Currency by the specifications, designs and all other features, in the Official Gazette.
This article has been amended by Decretal Federal Law No. (09) of 2021.and Decretal Federal Law No. (54) of 2023 respectively. You are viewing the latest version. To view the previous versions, click the version box below.Version 2(effective from 26/07/2021 to 01/11/2023)1) Currency notes issued by the Central Bank shall be of such denominations, designs, and specifications, and bear such features as shall be decided by the Board of Directors. Currency notes shall bear the signature of the Chairman of the Board of Directors.
2) The Board of Directors shall determine the weight, composition, mix ratios, allowed variation, and all other specifications of Currency coins as well as the quantities of each denomination to be minted.
3) The Central Bank shall make necessary arrangements for printing of Currency notes referred to in item (1) of this article, and minting of Currency coins referred to in item (2) of this article, along with all matters relating to such printing, minting and safekeeping of such Currency notes and coins and the relative plates and dies.
4) The Central Bank shall publish decisions to issue Currency by the specifications, designs and all other features, in the Official Gazette.
Version 1(effective from 31/10/2018 to 26/07/2021)1) Currency notes issued by the Central Bank shall be of such denominations, designs, and specifications, and bear such features as shall be decided by the Minister upon the proposal of the Board of Directors. Currency notes shall bear the signature of the Minister and the Chairman of the Board of Directors.
2) The Minister shall, upon proposal of the Board of Directors, determine the weight, composition, mix ratios, allowed variation, and all other specifications of Currency coins as well as the quantities of each denomination to be minted.
3) The Central Bank shall make necessary arrangements for printing of Currency notes referred to in item (1) of this article, and minting of Currency coins referred to in item (2) of this article, along with all matters relating to such printing, minting and safekeeping of such Currency notes and coins and the relative plates and dies.
4) The Central Bank shall publish decisions to issue Currency by the specifications, designs and all other features, in the Official Gazette.
Article (58): Gold and Silver Coins and Commemorative Coins
1) The Board of Directors shall determine conditions for sale and purchase of gold and silver coins at the Central Bank.
2) The Central Bank may issue commemorative Currency notes or coins for any wishing party, in accordance with the rules and conditions set by the Board of Directors.
3) The Board of Directors, determine the denominations, fineness, and weights, measurements, allowed variation, and all other specifications of gold and silver coins, as well as the quantities of each denomination to be minted.
4) The Central Bank shall make necessary arrangements for minting of gold and silver coins referred to in this article, along with all matters relating to such minting and safekeeping of such coins and the relative plates and dies.
This article has been amended by Decretal Federal Law No. (09) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 26/07/2021)1) The Board of Directors shall determine conditions for sale and purchase of gold and silver coins at the Central Bank.
2) The Central Bank may issue commemorative Currency notes or coins for any wishing party, in accordance with the rules and conditions set by the Board of Directors.
3) The Minister shall, upon proposal of the Board of Directors, determine the denominations, fineness, and weights, measurements, allowed variation, and all other specifications of gold and silver coins, as well as the quantities of each denomination to be minted.
4) The Central Bank shall make necessary arrangements for minting of gold and silver coins referred to in this article, along with all matters relating to such minting and safekeeping of such coins and the relative plates and dies.
Chapter Two: Currency Circulation and Withdrawal
Article (59): Currency Notes
1) New Currency notes shall be put in circulation by a Board of Directors decision specifying their denominations and quantities. Such decision shall be published in the Official Gazette and communicated to the public through appropriate media.
2) The Board of Directors may, after approval of the Cabinet, withdraw from circulation any denomination of Currency notes against payment of their face value. Such decision shall be published in the Official Gazette and communicated to the public through appropriate media.
3) The withdrawal decision shall specify the time limit allowed for exchange, which shall not be less than three (3) months from date of publication of the decision in the Official Gazette. Such time limit may, if necessary, be reduced to fifteen (15) days.
4) Currency notes not presented for exchange prior to expiry of the time limit stated in item (3) of this article shall cease to be legal tender and may not be negotiated. However, holders of such Currency notes shall have the right to redeem them, at face value, at the Central Bank, within ten (10) years from the effective date of the withdrawal decision. Currency notes not exchanged upon expiry of said ten-year period must be taken out of circulation and their value shall be credited to Central Bank account.
5) The Central Bank shall, in pursuance to the provision of item (4) of this article, destroy the Currency notes withdrawn from circulation in accordance with the instructions issued by the Central Bank in this respect.
6) The Central Bank shall be under no obligation to refund the value of any lost or stolen Currency notes, or to accept or pay for counterfeit Currency notes.
7) The Central Bank shall pay value of torn, mutilated or imperfect Currency notes, which satisfy the requirements to be prescribed by the Central Bank in this regard. Currency notes not satisfying those requirements shall be withdrawn from circulation without any compensation to bearers.
Article (60): Currency Coins
1) Currency coins of various denominations shall be put into circulation by a Board of Directors decision specifying their respective quantities. This decision shall be published in the Official Gazette and communicated to the public through appropriate media.
2) Any denomination of the Currency coins referred to in item (1) of this article may be withdrawn, by a decision of the Board of Directors, against payment of their face value. Such decision shall be published in the Official Gazette and communicated to the public through appropriate media.
3) The withdrawal decision shall specify the time limit for exchange, which shall not be less than six (6) months from date of publication of the decision in the Official Gazette.
4) Currency coins not exchanged prior to expiry of the period referred to in item (3) of this article shall cease to be legal tender and may not be negotiated and must be taken out of circulation and their value shall be credited to Central Bank account.
5) Should Currency coins lose their features, become deformed, diminished or changed in shape for any reason other than normal use, the Central Bank must withdraw such coins from circulation without compensating their holders.
Article (60) bis:
Digital Currency
1) The Board of Directors shall issue a decision for the types of Digital Currency to be put in circulation and redeemed in exchange for payment of its face value, such decision shall be published in the Official Gazette and broadcasted to the public through appropriate media.
2) The Central Bank shall be under no obligation to refund the value of any digital currency that is lost, seized or tampered with, or to accept or pay for any counterfeit currency.
Article (60) Bis. has been added as per the Decretal Federal Law No. (54) of 2023.
Article (61): Currency Mutilation, Destruction and Shredding
No Person is permitted to mutilate/deform, destroy or shred Currency, in whichever manner. The Board of Directors shall issue regulations on replacement of mutilated, destroyed or shredded Currency.
Chapter Three: Monetary Base
Article (62): Monetary Base Cover
The Central Bank shall, at all times, hold reserves of foreign assets, to cover the Monetary Base, in accordance with provisions of Article (63) of this Decretal Law. Such reserves of foreign assets shall consist of one or more than one of the following items:
1) Gold bullion and other precious metals.
2) Cash, deposits and other monetary and payment instruments denominated in foreign currencies, freely convertible in global financial markets, including digital currencies issued by central banks and other monetary authorities.
3) Securities denominated in foreign currencies and issued or guaranteed by foreign governments and their related companies, entities, institutions, and agencies, or by international monetary and financial institutions, or by multinational corporations, and are tradable in global financial markets.
This article has been amended by Decretal Federal Law No. (54) of 2023. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 01/11/2023)The Central Bank shall, at all times, hold reserves of foreign assets, to cover the Monetary Base, in accordance with provisions of Article (63) of this decretal law. Such reserves of foreign assets shall consist of one or more than one of the following items:
1) Gold bullion and other precious metals.
2) Cash, deposits and other monetary and payment instruments denominated in foreign currencies, freely convertible in global financial markets.
3) Securities denominated in foreign currencies and issued or guaranteed by foreign governments and their related companies, entities, institutions, and agencies, or by international monetary and financial institutions, or by multinational corporations, and are tradable in global financial markets.
Article (63): Foreign Reserves for the Monetary Base Cover
1) The market value of balance of the Foreign Reserves referred to in Article (62) of this Decretal Law, shall not, at any time, be less than seventy percent (70%) of the value of the Monetary Base.
2) The Board of Directors may reduce the Monetary Base cover ratio, referred to in item (1) of this article for a period not exceeding twelve (12) months.
Part III – Organization of Licensed Financial Institutions and Activities
Chapter One: General Provisions
Article (64): Prohibition of Carrying on or Promoting Financial Activities Without a License
1) Licensed Financial Activities may only be carried on, in or from within the State, in accordance with the provisions of this Decretal Law, and the rules and regulations issued in implementation thereof.
2) Promotion of any of the Licensed Financial Activities and financial products may only be carried on in or from within the State, in accordance with the provisions of this Decretal Law, and the rules and regulations issued in implementation thereof. The promotion referred to in this item shall mean any form of communication, by any means, aimed at inviting or offering to enter into any transaction, or offering to conclude any agreement related to any of the Licensed Financial Activities.
3) The Board of Directors may issue the rules, regulations, standards and directives relating to the prohibition to carry on Licensed Financial Activities without prior licensing and to the prohibition to promote Licensed Financial Activities and financial products, and shall take all necessary measures and actions in this regard.
4) The Board of Directors may exempt any activities or practices, or exempt natural or juridical persons, either generally or in particular, from the prohibition to carry on or promote Licensed Financial Activities.
Chapter Two: Licensing
Section One: Licensed Financial Activities
Article (65): Financial Activities
1) The following activities shall be considered financial activities subject to Central Bank licensing and supervision in accordance with the provisions of this Decretal Law:
- a. Taking deposits of all types, including Shari’ah-compliant deposits.
- b. Providing credit facilities of all types.
- c. Providing funding facilities of all types, including Shari’ah-compliant funding facilities.
- d. Providing currency exchange and money transfer services.
- e. Providing monetary intermediating services.
- f. Providing stored values services, electronic retail payments and digital money services.
- g. Providing virtual banking services.
- h. Arranging and/or marketing for Licensed Financial Activities.
- i. Acting as a principal in financial products that affect the financial position of the Licensed Financial Institution, including but not limited to foreign exchange, financial derivatives, bonds and sukuk, equities, commodities, and any other financial products approved by the Central Bank.
2) The Board of Directors shall:
- a. Classify and define Licensed Financial Activities and the practices relating thereto.
- b. Add activities or practices to the list of Licensed Financial Activities mentioned in item (1) of this article, or delete activities or practices from the list, or amend them, following coordination and agreement with the Regulatory Authorities in the State, through the Financial Activities Committee referred to in Article (66) of this Decretal Law.
3) In case a Licensed Financial Institution wishes to carry on activities licensed by Regulatory Authorities in the State or the regulatory authorities in other jurisdictions, other than the activities referred to in item (1) of this article, such institution must obtain approval of the Central Bank, prior to obtaining licensing from the concerned regulatory authority.
Article (66): Financial Activities Committee
1) A technical committee named the ‘Financial Activities Committee’ shall be established in the Ministry by a Cabinet resolution, chaired by the Ministry and include in its membership a representative of each of the Regulatory Authority in the State. The mentioned committee shall look into and provide opinion on any proposal to regulate a financial activity other than those mentioned in the laws of regulatory authorities. The resolution shall specify the committee’s terms of reference and the mechanism for discharge of its functions.
2) The approval of the concerned Regulatory Authority shall be obtained in case the financial activities committee suggest adding a specific financial activity not mentioned in its law to the list of activities under its licensing and regulation.
Section Two: Licensing of Financial Institutions
Article (67): Application for Licensing
1) Any Person may, in accordance with the regulations issued by the Board of Directors, submit to the Central Bank an application for a license to carry on one or more Licensed Financial Activities or the addition of one or more Licensed Financial Activities to an already issued license.
2) The Board of Directors shall issue rules, regulations and standards, and determine conditions for granting license to carry on Licensed Financial Activities, including the following:
- a. Fit and proper criteria.
- b. Resources required for carrying on the activity.
- c. Control and monitoring systems.
3) The Board of Directors may add any requirements or conditions to be fulfilled by the applicant for license, at its own discretion and as it deems appropriate for safeguarding public interest.
Article (68): Compliance with Scope of the License
1) A licensed financial institution must carry on its business within the scope of the license granted to it.
2) No Person may represent that it is a Licensed Financial Institution, if such is not the case.
Article (69): Deciding on Licensing Application or Extension of License Scope
1) Deciding on licensing application or extension thereof shall be within a period not exceeding sixty (60) working days from date of meeting all conditions and requirements for licensing. The lapse of this period without decision on the application shall be considered a rejection thereof.
2) The Central Bank may require the applicant to fulfill licensing requirements and conditions within such period as specified by the Central Bank.
3) The Central bank may reject an application for a license, or an application to add any financial activity based on the capacity of the financial sector in the State and the needs of the local market. Such decision issued in this regard shall be final and not subject to appeal before the Grievances and Appeals Committee.
4) The applicant shall be notified, officially, of the reasoned rejection decision within a period not exceeding twenty (20) working days from date of its issue.
This article has been amended by Decretal Federal Law No. (23) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 02/01/2023)1) Deciding on licensing application or extension thereof shall be within a period not exceeding sixty (60) working days from date of meeting all conditions and requirements for licensing. The lapse of this period without decision on the application shall be considered an implicit rejection thereof.
2) The Board of Directors may reject an application for a license, or an application to add any financial activity based on the capacity of the financial sector in the State and the needs of the local market.
3) The Board of Directors may, before issuing the rejection decision, request the applicant to fulfill licensing requirements and conditions within such period as specified by the Board of Directors.
4) The applicant shall be notified, officially, of the reasoned rejection decision within a period not exceeding twenty (20) working days from date of its issue. Such notice shall include the following:
- a. Content of the rejection decision.
- b. Reasons for rejection.
- c. A statement advising the applicant of his right to submit a grievance against the rejection decision, by applying to the Grievances & Appeals Committee, in accordance with the provisions of this decretal law.
Article (70): Imposing Conditions and Restrictions on a License
1) The Board of Directors may impose conditions or restrictions, or otherwise change or cancel conditions or restrictions imposed on a license for carrying on Licensed Financial Activities.
2) The Board of Directors may, before issuing the decision mentioned in item (1) of this article, request the concerned financial institution to provide its opinion on the reasons for the decision, within such period as specified.
3) The licensed financial institution shall be notified, officially, of the reasoned decision within a period not exceeding twenty (20) working days from date of its issue. The notice shall include the following:
- a. Content of the decision.
- b. Reasons for the decision.
- c. Effective date of the decision.
- d. A statement advising the licensed financial institution of its right to submit a grievance against the decision, by applying to the Grievances and Appeals Committee, in accordance with the provisions of this Decretal Law.
Article (71): Suspension, Withdrawal, or Revocation of License
1) The Board of Directors may suspend, withdraw, or revoke a license issued to a Licensed Financial Institution, in the following cases:
- a. If the Licensed Financial Institution ceased to meet, or breached one or more of the conditions or restrictions imposed on the license.
- b. If the Licensed Financial Institution breached any of the State’s established laws and regulations, or the regulations, rules, standards, instructions, and guidelines issued by the Central Bank.
- c. If the Licensed Financial Institution failed to take any measures or actions determined or prescribed by the Central Bank.
- d. If the Licensed Financial Institution ceased to carry on one or more of the Licensed Financial Activities, for a period exceeding one year.
- e. If the business or operations were ceased for a period exceeding one year.
- f. If the Central Bank considered, at its own discretion, that the full or partial withdrawal, revocation, or suspension of the license, was necessary for achieving its objectives and discharging its functions.
- g. If the concerned Licensed Financial Institution submitted an application for full or partial suspension or revocation of the license.
- h. If the Licensed Financial Institution’s liquidity or solvency was at risk.
- i. If the capital of the Licensed Financial Institution fell below the minimum required in accordance with the provisions of this Decretal Law, or the regulations, rules, or standards issued by the Central Bank.
- j. If the Licensed Financial Institution merged with another financial institution.
- k. If the Licensed Financial Institution was declared bankrupt.
- l. If the Licensed Financial Institution’s officers, employees, or representatives refused to cooperate with Central Bank officers, representatives, or examiners or abstained from providing required information, statements, documents, or records.
- m. If the license of a foreign Licensed Financial Institution was revoked, or if it was put under liquidation at its domicile, or if the businesses of its branch, companies or Representative Offices in the State were wound down.
2) The Licensed Financial Institution shall be notified, officially, of the reasoned withdrawal, cancellation or suspension decision within a period not exceeding twenty (20) working days from date of its issue. The notice shall include the following:
- a. Content of the decision.
- b. Reasons for the decision.
- c. Effective date of the decision.
- d. A statement advising the Licensed Financial Institution of its right to submit a grievance against the decision, by applying to the Grievances and Appeals Committee, in accordance with the provisions of this Decretal Law.
3) The decision issued by the Central Bank shall, following decision on the grievance or appeal, if presented to the Grievances and Appeals Committee, or expiry of the period specified in item (2) of this article, be published in two local newspapers, one in Arabic and another in English, and on the Central Bank’s official website. Such decision may also be announced by any other means if necessary.
Article (72): Use of Term “Bank” or “Masraf”
1) Entities other than Banks licensed in accordance with the provisions of this decretal law may not use, in their business addresses or advertisements, the expressions “Bank”, “Masraf” or any other expression derived therefrom or similar thereto, in any language, and in any way which may mislead the public as to the nature of their business.
2) The following entities shall be not be subject to the provisions of item (1) of this article:
- a. Monetary authorities and Central Banks.
- b. Any federation or association established for protection of Banks’ interests.
- c. Any other institution exempted by the Board of Director.
Article (73): Entry to the Register
1) An electronic register named “Register of Licensed Financial Institutions” shall be created in the Central Bank, to which names of Licensed Financial Institutions and all their data and any amendments thereto, shall be entered. A decision setting the rules and conditions for entry to such register shall be issued by the Board of Directors. Decision to license such institutions and any amendments thereto, shall be published in the Official Gazette. This register shall be published on the Central Bank’s official website.
2) A Licensed Financial Institution may not commence any Licensed Financial Activity except after its name was entered to the register.
3) Proceeds of licensing and entry to the register fees shall be deposited in a special account with the Central Bank. A decision shall be issued by the Board of Directors organizing operation of the account, and setting rules for withdrawing funds from it.
Article (74): Legal Form
1) Banks shall take the form of public joint- stock companies, with incorporating law or decree so permits. Branches of foreign banks operating in the State, and specialized banks with low risks that are determined according to the conditions and rules set by the Board of Directors shall be exempt from this requirement.
2) Other Financial Institutions may take the form of joint- stock companies or limited liability companies, in accordance with the rules and conditions issued by the Board of Directors.
3) Exchange Houses and monetary intermediaries may be a sole proprietorship, or take any other legal form in accordance with the rules and conditions issued by the Board of Directors.
This article has been amended by Decretal Federal Law No. (25) of 2020. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 02/01/2021)1) Banks shall take the form of public joint- stock companies, with incorporating law or decree so permits. Branches of foreign banks operating in the State shall be exempt from this requirement.
2) Other Financial Institutions may take the form of joint- stock companies or limited liability companies, in accordance with the rules and conditions issued by the Board of Directors.
3) Exchange Houses and monetary intermediaries may be a sole proprietorship, or take any other legal form in accordance with the rules and conditions issued by the Board of Directors
Article (75): Minimum Capital Requirements
The Board of Directors shall establish regulations on the minimum capital requirement for Licensed Financial Institutions, and conditions and instances of increase or decrease of capital, and shall determine its risk-based requirements, and the necessary actions to be taken in case of capital shortfall, in addition to the measures taken by the Central Bank in this regard.
Article (76): Shareholding and Ownership in Licensed Financial Institutions
1) Without prejudice to the financial and commercial activities restricted to UAE nationals prescribed in any other law, the Board of Directors shall determine the conditions and controls for ownership of shares of Banks incorporated in the State and shareholdings contribution in their capital, and in all cases the national shareholding must not be less than sixty percent (60%).
2) The Board of Directors may determine the conditions, controls for percentage of ownership of shares and shareholdings contribution in the capital of Other Financial Institutions incorporated in the State by nationals and foreigners.
Article (77): Amendment of the Memorandum and Articles of Association
1) Licensed Financial Institutions shall request the Central Bank’s approval for amendments they wish to introduce to their memorandum or articles of association. Such amendments shall only take effect after they were entered into the register.
2) The Central Bank shall decide on the application. Should the Central Bank decided to reject the application to enter the amendment, the matter shall be submitted to the Board of Directors whose decision in that respect shall be final.
Section Three: Provisions for Islamic Licensed Financial Institutions
Article (78): Scope of Activity
1) Licensed Financial Institutions that carry on all or part of their activities and business in accordance with the provisions of Islamic Shari’ah may carry on the Licensed Financial Activities mentioned in Article (65) of this decretal law, whether for themselves or on behalf of others or in partnership with third parties, provided such business and activities are in compliance with the provisions of Islamic Shari’ah. The Board of Directors shall issue regulations specifying the activities, conditions, rules, and operating standards for these institutions, in a manner commensurate with the nature of the license granted to them.
2) Licensed Financial Institutions mentioned in item (1) of this article shall, in respect of their Shari’ah-compliant business and activities initiated on behalf of their customers and not for themselves, be exempted from:
- a. Provisions of item (1) of Article (93) of this decretal law.
- b. Provisions of item (2) of Article (93) of this decretal law, insofar as such exemption does not contradict the provisions of local legislations applicable in the relevant member Emirate of the Union.
Article (79): Internal Shari’ah Supervision
1) An independent committee referred to as “Internal Shari’ah Supervisory Committee” shall be established within each Licensed Financial Institution that conducts all or part of its activities and business in accordance with the provisions of Islamic Shari’ah. Membership of this committee shall consist of experienced specialists in jurisprudence of Islamic financial and banking transactions. The said committee shall undertake Shari’ah supervision of all business, activities, products, services, contracts, documents, and business conduct charters of the concerned institution and shall approve them and establish the necessary Shari’ah requirements applicable to them, within the framework of the rules, principles and standards set by the Higher Shari’ah Authority, in order to ensure compliance with the provisions Islamic Shari’ah. Fatawa or opinions issued by the Committee shall be binding.
2) The Internal Shari’ah Supervisory Committee shall be appointed by the general assembly of the concerned Licensed Financial Institution, in accordance with the provisions of the referenced Commercial Companies law. Names of members of the Internal Shari’ah Supervisory Committee shall be presented to the Higher Shari’ah Authority for approval, prior to presentation to the general assembly and issuance of decision approving their appointment.
3) Members of the Internal Shari’ah Supervisory Committee are prohibited from holding any executive position in the institution referred to in item (1) of this article, or provide services to it outside of the scope of the committee’s assigned scope of work, nor hold shares or have for themselves or for any of their relatives up to the second degree, any interests associated with it.
4) In cases where disagreement arises, over a Shari’ah opinion, between members of the Internal Shari’ah Supervisory Committee, or disagreement between the Internal Shari’ah Committee and the Board of Directors of the concerned financial institution, over the compliance or non-compliance of a particular matter with the provisions of Shari’ah, the disagreement shall be referred to the Higher Shari’ah Authority, whose opinion on the matter shall be final.
5) There shall be established, in each institution referred to in item (1) of this article, a division or internal section, of a size commensurate with the business and activities of the concerned institution, to undertake internal Shari’ah audit and monitor compliance of the concerned institution with the fatawa and opinions of the Internal Shari’ah Supervisory Committee. Such division or section shall report to the Board of Directors of the concerned institution, and its employees shall not have any executive powers or any responsibilities towards the business, activities and contracts which they review or audit from a Shari’ah perspective. The said division or section shall be headed by a Shari’ah controller appointed by the Board of Directors of the concerned institution.
Article (80): Report of the Internal Shari’ah Supervision Committee
1) The Internal Shari’ah Supervisory Committee shall prepare an annual report to be presented to the general assembly of the Licensed Financial Institution, which conducts on all or part of its activities and businesses in accordance with the provisions of Islamic Shari’ah. The report shall take the form specified by the Higher Shari’ah Authority, and shall indicate the extent the management of the concerned institution is compliant with the provisions of Islamic Shari’ah, in all activities, business it conducts, the products it offers, contracts it enters into, and the documentation it uses. The said report shall include the following:
- a. A statement on the extent of independence of the Internal Shari’ah Supervisory Committee when discharging its mandates.
- b. A statement on compliance with the provisions of Islamic Shari’ah during the financial year ending in regards to policies, accounting standards, financial products and services, operations and activities in general, together with the memorandum, articles of association, and financial statements of the relevant institution.
- c. A statement on the compliance of distribution of profits, bearing of losses, costs, and expenses among the shareholders and investment account holders, with the fatawa and opinions of the Internal Shari’ah Supervisory Committee.
- d. A statement on any other breaches of Shari’ah provisions and the controls established by the Higher Shari’ah Authority.
2) The Internal Shari’ah Supervisory Committee shall provide the Higher Shari’ah Authority with copy of its report, no later than two (2) months from end of the financial year, in order for the Authority to express its remarks prior to the meeting of the general assembly of the concerned institution.
Article (81): State Audit Supervision
Where a Licensed Financial Institution, which conducts all or part of its business and activities in accordance with the provisions of Islamic Shari’ah, is subject to the supervision of the State Audit Institution, pursuant to the referenced Re-organization of the State Audit Institution law, the function of the audit institution shall be restricted to post- audit, and shall not interfere in the conduct of business or policies of these institutions.
Article (82): Non-Compliance with the Provisions of Islamic Shari’ah
Where it is established that a financial institution, which conducts on all or part of its business and activities in accordance with the provisions of Islamic Shari’ah, has conducted business that is not compliant with such provisions, as per fatawa and opinions of the Internal Shari’ah Supervisory Committee, and the fatawa and opinions of the Higher Shari’ah Authority, the Central Bank shall inform the concerned institution accordingly, after consulting with the Higher Shari’ah Authority, and shall ask the institution to reconcile its position, under the supervision of the Internal Shari’ah Supervisory Committee, within thirty (30) working days from date of notification. The Central Bank shall take the appropriate corrective measures and corrective actions in case the concerned institution’s inability to reconcile its position.
Section Four: Provisions Relating to Undertaking Designated Functions Subject to Central Bank Authorization
Article (83): Designated Functions
1) The Board of Directors may issue regulations, rules, standards, conditions, and instructions, specifying Designated Functions subject to Central Bank authorization and the individuals who shall be required to obtain Central Bank authorization to undertake them, including fit and proper conditions, and cases of exemption of such conditions and standards.
2) Without prejudice to the provisions of item (1) of this article, Designated Functions subject to Central Bank authorization include those carried out by members of the boards of directors of Licensed Financial Institutions, and their chief executive officers, senior managers, executives, and Authorized Individuals.
3) No individual may undertake any Designated Functions at a Licensed Financial Institution, without obtaining Central Bank’s prior authorization.
4) Licensed Financial Institutions shall take all measures and actions, which ensure that no officer, employee, or any other individual representing them, shall exercise any of the Designated Functions without obtaining prior authorization from the Central Bank.
5) Any Authorized Individual in accordance with the provisions of this article shall abide with limits of powers stated in the authorization.
6) No individual shall introduce himself as an Authorized Individual unless he is authorized by the Central Bank.
Article (84): Application for Authorization to Undertake Designated Functions
1) A Licensed Financial Institution may submit an application to the Central Bank for authorization of any individual to undertake any of the Designated Functions or to undertake additional Designated Functions.
2) The Central Bank may require the applicant to provide all information necessary for enabling it to decide on the application.
3) A Licensed Financial Institution shall notify the Central Bank of any material changes relating to the conditions for granting authorization to undertake the Designated Functions.
Article (85): Deciding on Application for Authorization to Undertake
1) Deciding on application for authorization or extension thereof shall be within a period not exceeding twenty (20) working days from date of meeting all conditions and requirements for authorization. The lapse of this period without decision on the application shall be considered an implicit rejection thereof.
2) The Board of Directors may reject an application for authorization or addition of other Designated Functions to an Authorized Individual if it considered that such rejection would serve public interest or that conditions and requirements for authorization were not fulfilled.
3) The applicant shall be notified, officially, of the rejection decision within a period not exceeding twenty (20) working days from date of its issue. The notice shall include the following:
- a. Content of the decision.
- b. Reasons for the decision.
- c. A statement advising the applicant of his right to submit a grievance against the rejection decision, by applying to the Grievances and Appeals Committee, in accordance with the provisions of this Decretal Law.
Article (86): Imposing Conditions and Restrictions to an Authorization to Undertake Designated Functions
1) The Central Bank may decide to add conditions or restrictions to an authorization to undertake Designated Functions.
2) Before issuing the decision referred to in item (1) of this article, the Central Bank may request the concerned Licensed Financial Institution to provide its comments on the reasons for the decision, within such period as it specifies.
3) The Licensed Financial Institution shall be notified, officially, of the decision within a period not exceeding twenty (20) working days from date of its issue. Such notice shall include the following:
- a. Content of the decision.
- b. Reasons for the decision.
- c. Effective date of the decision.
- d. A statement advising the Licensed Financial Institution of its right to submit a grievance against the decision, by applying to the Grievances and Appeals Committee, in accordance with the provisions of this Decretal Law.
Article (87): Suspension, Withdrawal, or Revocation of Authorization to Undertake Designated Functions
1) The Central Bank may suspend, withdraw, or revoke the authorization issued to an individual undertaking Designated Functions, by an official notice, in the following cases:
- a. If the Authorized Individual ceased to meet, or breached one or more of the fit and proper criteria and other conditions or restrictions imposed on the authorization to undertake Designated Functions.
- b. If the Authorized Individual violated any of the State’s established laws and regulations or the regulations, rules, standards, or guidelines issued by the Central Bank.
- c. If the Authorized Individual failed to take any measures or actions prescribed by the Central Bank.
- d. If the Central Bank considered, that full or partial withdrawal, revocation, or suspension of the authorization, was necessary for achieving its objectives and discharging its functions.
- e. If the Authorized Individual was declared bankrupt.
- f. If the Authorized Individual refused to cooperate with the officials, representatives, or examiners of the Central Bank, or failed to submit required information or records.
2) In all cases, the authorization shall be revoked in case a cancellation application was submitted by the Licensed Financial Institution where the Authorized Individual works or in case of termination of his relationship with such institution.
3) The Licensed Financial Institution, where the Authorized Individual works shall be notified, in writing, of the decision to withdraw, revoke, or suspend the authorization, within a period not exceeding twenty (20) working days from date of its issue. Such notice shall include the following:
- a. Content of the decision.
- b. Reasons for the decision.
- c. Effective date of the decision.
- d. A statement advising the concerned Licensed Financial Institution and the Authorized Individual of their right to submit a grievance against the decision, by applying to the Grievances and Appeals Committee, in accordance with the provisions of this Decretal Law.
Article (88): Prohibition of Undertaking Designated Functions at Licensed Financial Institutions
1) The Central Bank may prohibit any individual from working, or undertaking Designated Functions related to Licensed Financial Activities if it considered that the concerned individual was not fit and proper to work or undertake such Designated Functions.
2) The concerned Licensed Financial Institution shall be notified, officially, of the decision to prohibit the concerned individual from working or undertaking Designated Functions at it, within a period not exceeding twenty (20) working days from date of its issue. Such notice shall include the following:
- a. Content of the decision.
- b. Reasons for the decision.
- c. Effective date of the decision.
- d. A statement advising the Licensed Financial Institution and the concerned individual of their right to submit a grievance against the decision, by applying to the Grievances and Appeals Committee, in accordance with the provisions of this Decretal Law.
Chapter Three: Responsibilities of Deposit-Taking Licensed Financial Institutions
Article (89): Compliance with Central Bank’s Instructions
1) Deposit-taking Licensed Financial Institutions shall comply with all rules, regulations, standards, circulars, and directives and instructions issued by the Central Bank with regard to lending or other matters it deems necessary for achieving its objectives.
2) The Central Bank may take all necessary measures and actions, and use means, which would ensure proper conduct of business at deposit-taking Licensed Financial Institutions. Such instructions, directives, measures, procedures, or means, may either be general or individual.
Article (90): Central Bank Risk Bureau
The Risk Bureau at the Central Bank shall undertake compilation, exchange and processing of credit information from Licensed Financial Institutions or any party the Central Bank deems necessary. The said bureau shall operate within the conditions and controls determined by the Board of Directors.
Article (91): Protection of Depositors’ Interests
1) Each deposit-taking Licensed Financial Institution shall prepare a quarterly statement, in the form specified by the Central Bank, indicating all the credit and funding facilities granted by the Licensed Financial Institution to:
- a. Any member of its board of directors.
- b. Any establishment or company where the concerned institution is a partner, manager, agent, guarantor or sponsor.
- c. Any company where a member of the board of directors of the concerned institution is a manager or agent.
- d. Any company where an employee, expert or representative of the concerned institution is a manager, executive officer, agent, guarantor, or sponsor.
- e. Any Person holding controlling interest in the concerned institution, or a related company, as per provisions of Article (95) of this Decretal Law.
- f. Any subsidiary of the group, which owns the concerned institution.
- g. Any company related to the concerned institution, as per the controls set by the Board of Directors.
- h. Any Person, directly or indirectly related to any member of the board of directors of concerned institution, as per the controls set by the Board of Directors.
- i. Any other Person specified by the Board of Directors as per the rules it sets in this regard.
2) The Central Bank shall be provided with copy of the statement referred to in item (1) of this article, within a period of ten (10) days from end of each quarter of the financial year, or date of a request made by the Central Bank in this regard.
3) The Central Bank may take one or more of the actions listed hereunder, If it decided, following review of the statement referred to in item (1) of this article, that any of the credit or funding facilities extended by the Licensed Financial Institution or any exposure to a particular Person may result in damage to the interests of depositors of the concerned Licensed Financial Institution:
- a. Require the concerned institution to allocate provisions for these facilities, or reduce its exposure to a particular Person, within such period and as per such mechanism as it determines.
- b. Prohibit the concerned institution from extending further credit facilities to the concerned Person, or impose specific restrictions on facilities extended to the concerned Person, as it deems appropriate.
Chapter Four: Prohibitions
Article (92): Prohibition of Conducting Specific Operations
1) The Central Bank may prohibit Licensed Financial Institutions from conducting all or some of the following:
- a. Dealing in specific assets, investments, or monetary and financial instruments.
- b. Closing deals, or conduct specific operations or commercial transactions.
- c. Dealing with specific Persons.
2) The Board of Directors may issue rules, regulations and standards relating to the operations referred to in item (1) of this article, and take necessary measures and actions it deems appropriate.
3) The concerned Licensed Financial Institution shall be notified, officially, of Central Bank’s decision within a period not exceeding twenty (20) working days from date of its issue. The notice shall include the following:
- a. Content of the decision.
- b. Reasons for the decision.
- c. Effective date of the decision.
4) A statement advising the Licensed Financial Institution of its right to submit a grievance against the decision, by applying to the Grievances and Appeals Committee, in accordance with the provisions of this Decretal Law.
Article (93): Prohibition of Carrying on Non-Banking Activities
Banks shall not carry on any non-banking activities, particularly the following activities:
1) Carry on, for its account, commercial or industrial activities or acquire, own or trade in goods, unless the acquisition of such goods was in settlement of debts due from third parties, in which case the goods must be disposed of within the period specified by the Central Bank.
2) Purchase real estate for its own account, except in the following cases:
- a. Real estate that its value does not exceed the ratio set by the Board of Directors relative to its total capital and reserves.
- b. Real estate owned in direct settlement of debt exceeding the ratio mentioned in paragraph (a) of this item and in such a case the sale of these properties within (3) years, and this may be extended by an approval from the Central Bank based on the guidelines set by the Board of Directors.
3) Purchase or acquire or deal in shares of the Bank, in excess of the ratios set by the Board of Directors, unless the excess has devolved to it in settlement of a debt, in which case the Bank must sell the shares in excess of the said ratio, within a period of two (2) years from date of acquisition.
4) Purchase shares of commercial companies, except within the ratio of the Bank’s own funds, as set by the Board of Directors, unless acquired in settlement of a debt, in which case the excess must be sold within two (2) years from date of acquisition.
5) The Board of Directors shall issue regulations to Banks regarding limits for purchasing and dealing in securities issued by any foreign government or their related entities, or by any foreign commercial company. These limits shall not apply to securities issued or guaranteed by the Public Sector.
Article (94): Restrictions on Provision of Credit Facilities
1) As an exception to the provisions of Article (153) of the referenced Commercial Companies Law, Licensed Financial Institutions may extend credit facilities to members of their boards of directors, their employees, and relatives of such Persons as determined by the Board of Directors.
2) The Board of Directors shall determine conditions and requirements for credit facilities, which may be granted to the categories referred to in item (1) of this article.
3) A deposit-taking Licensed Financial Institution shall not offer credit facilities to its customers against their shares therein.
4) The Board of Directors shall issue regulations, to deposit-taking Licensed Financial Institutions, regarding the limits for credit facilities extended for the purpose of constructing residential or commercial buildings.
Chapter Five: Supervision and Oversight of Licensed Financial Institutions
Section One: Provisions Relating to Supervision and Oversight
Article (95): Provisions relating to Holders of Controlling Interests
1) A Person shall not hold controlling interest, or increase controlling interest in any Licensed Financial Institution, nor exercise powers, which render him a de facto holder of controlling interest, at the discretion of the Central Bank, unless he obtains Central Bank’s prior approval.
2) A Licensed Financial Institution shall also not allow any Person to hold controlling interest therein, unless it obtains Central Bank’s prior approval.
3) The Board of Directors shall issue regulations, rules, standards, conditions, instructions, and restrictions relating to interests and instances of control.
Article (96): Opening Branches Inside the State and in Other Jurisdictions
A Licensed Financial Institution shall not establish any branch or representative office inside the State or in other jurisdictions, or relocate or closedown any existing branch without Central Bank’s prior approval.
Article (97): Providing the Central Bank with Information and Reports
1) Licensed Financial Institutions shall:
- a. Provide the Central Bank with reports, information, statements and other documents, which it determined and considered necessary for achieving its objectives and discharge its functions.
- b. Appoint qualified employees and assign them the task of preparing the reports required by the Central Bank.
- c. Take appropriate measures to ensure that the Person assigned, in accordance with the paragraph (b) of this item, obtains the information required for preparation of the reports.
2) Licensed Financial Institutions are prohibited from issuing instructions or directives, or agree with any manager, officer, an employee working for it, an agent representing it, or auditor of its accounts, to decline to provide the Central Bank with the requirements referred to in item (1) of this article.
3) The Central Bank shall establish rules and guidelines for periodical compilation of information from Licensed Financial Institutions.
4) The Central Bank shall determine the nature, forms and frequency of submission of information. Licensed Financial Institutions shall provide such information in accordance with the instructions issued by the Central Bank in this regard.
5) The provisions of this article shall apply to branches of foreign Licensed Financial Institutions operating in the State.
6) The Board of Directors shall issue regulations, rules, standards, and instructions regarding provision of the requirements referred to in this article, and may take all the measures and actions against the concerned institution or any of its employees referred to in paragraph (b) of item (1) of this article.
Article (98): Reporting of Violations
1) Licensed Financial Institutions, along with their legal representatives, compliance officers, and auditors of accounts shall be responsible for, immediate reporting of any of the following to the Central Bank:
- a. Occurrence of any material or crucial developments, which may impact its activities, structure, or overall position.
- b. Occurrence of any violation to the provisions of this Decretal Law or the decisions, regulations, or instructions issued in implementation thereof.
2) The aforementioned Persons referred to in item (1) of this article shall not be considered to have breached any of their obligations if they, acting in good faith, filed a report as per provisions of this article, or provided information or opinion to the Central Bank. The Licensed Financial Institution shall not dismiss those mentioned in item (1) of this article without obtaining approval of the Central Bank.
3) The Central Bank shall establish a mechanism for accepting notifications concerning violations referred to in item (1) of this article.
Article (99): Submission of Data on Financial Position, Required by the Central Bank
1) Each Licensed Financial Institution shall be required to provide the Central Bank with the statements and reports relating to its financial position.
2) Each Licensed Financial Institution shall be required to provide the Central Bank, within a period not exceeding three (3) months from end of the financial year, or within such period as the Central Bank may specify, with the following:
- a. Copy of the audited balance sheet, showing use of assets and liabilities arising from operations of the concerned institution.
- b. Copy of the audited profit and loss account, and any related notes.
- c. Copy of report of auditors of accounts of the concerned institution.
- d. Copy of report of the board of directors of the concerned institution.
3) The Central Bank may also require the Licensed Financial Institution to provide the following:
- a. Copy of the interim profit and loss account, on semi-annual basis, or for other periods specified by the Central Bank.
- b. Any other additional reports, data or information it deems necessary.
Article (100): Merger and Acquisition
1) A Licensed Financial Institution shall not merge with or acquire any other institution, regardless of its type of activity, nor transfer any part of its liabilities to another Person, without obtaining Central Bank’s prior approval.
2) Without prejudice to the established legislation in the State concerning merger and acquisition, the Board of Directors may issue all regulations, rules, standards, conditions, instructions, and directives pertaining to merger and acquisition.
3) The Licensed Financial Institution shall be notified, officially, of the Central Bank’s decision rejecting the proposed merger or acquisition within a period not exceeding twenty (20) working days from date of its issue. The notice shall include the following:
- a. Content of the decision.
- b. Reasons for the decision.
- c. Effective date of the decision.
- d. A statement advising the concerned Licensed Financial Institution of its right to submit a grievance against the decision, by applying to the Grievances and Appeals Committee, in accordance with the provisions of this Decretal Law.
Article (101): Cessation of Business
A Licensed Financial Institution shall not cease to operate, fully or partially or suspend its operations, or cease to carry-on all or part of its Licensed Financial Activities without approval of the majority of its shareholders and approval of the Central Bank.
Article (102): Authority to Issue Instructions and Directives for Prudential Purposes
1) The Board of Directors shall, for the purposes of prudential supervision, issue necessary instructions and directives to a particular Licensed Financial Institution, or to a number of Licensed Financial Institutions within a specific category, relating to:
- a. Compliance with Central Bank instructions and directives relating to prudential ratios determined by the Board of Directors, regarding capital adequacy and liquidity or any other purposes.
- b. Compliance with the required provisions, or processing of specific assets.
- c. Adherence to limits of credit exposures.
- d. Adherence to limits of exposures to related parties.
- e. Satisfying any additional requirements relating to reporting.
2) The Central Bank may take any additional actions to those mentioned in item (1) of this article.
3) The Central Bank may instruct any subsidiary of a Licensed Financial Institution to take particular actions, or refrain from carrying on particular activities, in the following cases:
- a. If the Central Bank is the consolidated regulatory authority of the entities referred to in this item.
- b. If the Central Bank decided that such instruction is necessary for the exercise of effective and consolidated prudential supervision of the entities referred to in this item.
4) The instructions and directives referred to in item (3) of this article may include the following:
- a. Require the subsidiary of the concerned Licensed Financial Institution to suspend provision of particular services, or carrying on particular businesses or activities, or even closing down any of its offices or branches outside the State, if such services, businesses or activities may expose the concerned Licensed Financial Institution to additional risk, or to risks that cannot be managed effectively and appropriately.
- b. Require the subsidiary of the concerned Licensed Financial Institution to take all necessary actions to remove any impediments that may hinder effective consolidated supervision.
Article (103): Maximum Limits of Operations
The Central Bank may set maximum limits to which deposit-taking Licensed Financial Institutions shall adhere to in their operations, which include the following:
1) The maximum amount of total deduction operations or loans and advances the Licensed Financial Institution is allowed to conduct, as of a certain date.
2) The maximum amount the Licensed Financial Institution may lend to a single Person, relative to the Person’s own funds.
3) Any other limits the Central Bank may determine.
Article (104): Governance of Licensed Financial Institutions
1) The Central Bank shall establish a general framework for governance of Licensed Financial Institutions, and shall issue rules and regulations relating to organization of works of their boards of directors and shall determine the conditions to be met by nominees for membership of their boards of directors, and the requirements and conditions for appointment of their senior staff; provided that Licensed Financial Institutions listed in the State’s financial markets shall adhere to the minimum requirements of corporate governance set by the concerned regulatory authority.
2) Licensed Financial Institutions must obtain Central Bank’s prior approval for appointment, nomination of any Person for membership of their boards of directors or renewal of his membership, and appointment or renewal of the employment contract of any of their senior staff.
3) The Board of Directors may, as may be required to safeguard public interest, reject any Person’s nomination, appointment, or renewal of his membership in the board of directors of a Licensed Financial Institution, and may also reject appointment or renewal of the employment contract of any of its senior staff.
Article (105): Rulebook
The Central Bank shall prepare an electronic guide, which includes all regulations, rules, standards, decisions, and circulars issued by the Central Bank in accordance with the provisions of this decretal law. Such guide shall be published and regularly updated on the Central Bank’s website.
Article (106): Retroactive Effect of Central Bank Regulations and Decisions
The regulations, decisions, and circulars issued by the Central Bank in accordance with the provisions of this Decretal Law shall have no retroactive effect, and shall not prevent implementation of agreements concluded between Licensed Financial Institutions and their customers prior to their issuance. The Central Bank shall determine the required transitional period for Licensed Financial Institutions to reconcile their respective positions, according to the provisions of this Decretal Law.
Article (107): Examination
1) The Central Bank may, at any time, dispatch any of its staff or any third party authorized to act on its behalf to Licensed Financial Institutions and their owned companies or subsidiaries, if it deemed necessary to ensure soundness of their financial positions, and their compliance with the provisions of this Decretal Law and the regulations and decisions issued in implementation thereof, and other established laws and regulations in the State.
2) In case of the conduct of examination of companies owned by Licensed Financial Institutions and their subsidiaries, which are regulated by any of the Regulatory Authorities in the State or in other jurisdictions, the Central Bank shall coordinate with the concerned regulatory authority in this regard.
3) The Central Bank may, in coordination with the concerned agencies in the State, inspect premises of any Person suspected of carrying on any of the financial activities referred to in Article (65) of this Decretal Law, without a license. The Central Bank may, in this respect, require the suspected Person to provide all information, documents, and records relating to the unlicensed financial activities, and may seize such information, documents, and records.
4) Licensed Financial Institutions, their owned companies and subsidiaries shall provide the staff referred to in item (1) of this article with all information, records, books, accounts, documents and data relating to the subject of examination, along with any information he may ask for, on timely basis.
5) Central Bank staff may, within the framework of the examination process, summon any related Person, on the time and place they may determine, to provide information, data, documents, or records relating to the examination process.
6) The Board of Directors may issue regulations, rules, standards, directives and instructions relating to mechanisms and procedures for examination of Licensed Financial Institutions.
7) The Central Bank may take all measures and actions it deems appropriate for achieving its objectives and discharging its functions, and may particularly take the following actions, if it was found that a violation to the provisions of this Decretal Law, or the regulations and decisions issued in implementation thereof, has occurred:
- a. Impose restrictions on some of the operations or activities carried on by the concerned Licensed Financial Institution.
- b. Require the concerned Licensed Financial Institution to take necessary actions to rectify the situation immediately.
- c. Appoint a specialized expert, or a qualified Central Bank employee, to advice the concerned Licensed Financial Institution or supervise, or oversee some of its operations, for a period specified by the Central Bank. The concerned Licensed Financial Institution shall pay remunerations of such appointee if he is an expert from outside the Central Bank.
- d. Take any other action or measure, or impose any penalties it deems appropriate.
8) Licensed Financial Institutions shall be required to pay all costs of examination and investigations process outsourced, by the Central Bank, to a third party, in case its violation to the provisions of this Decretal Law, and the regulation and decisions issued in implementation thereof, has been established.
Article (108): Examination of Entities of National Licensed Financial Institutions Operating in Other Jurisdictions
The Central Bank may dispatch one or more of its examiners or experts, to undertake examination of entities of national Licensed Financial Institutions operating abroad, in collaboration and coordination with the concerned regulatory authorities in those jurisdictions;
Such would include entities of national Licensed Financial Institutions operating in Financial Free Zones in the State, in cooperation and coordination with the supervisory authorities of the concerned Financial Free Zone.
Article (109): Expert Report
The Central Bank may assign an expert or a Person qualified in the area of Licensed Financial Activities, to provide it with a report on any subject specified by the Central Bank, relating to direct and indirect businesses and activities of a particular Licensed Financial Institution, in accordance with the conditions and procedures established by the Central Bank, and at the expense of the entities referred to in this article.
Article (110): Judicial Officer Capacity
Central Bank staff designated per decision issued by the Minister of Justice, in coordination with the Governor, shall, in establishing acts occurring in violation of the provisions of this decretal law, have the capacity of judicial officers.
Article (111): Requesting Intervention in Lawsuits and Judicial Proceedings and Notification of Investigations
1) Without prejudice to the provisions of the Civil Procedures Law, the Central Bank may request intervention in any lawsuit filed before judicial authorities to which a Licensed Financial Institution is party.
2) Law enforcement and other concerned authorities shall notify the Central Bank of any investigations or proceedings initiated against Licensed Financial Institutions. The Central Bank may provide such authorities with any clarifications, statements, or information it deems appropriate in this regard.
Section Two: Financial Accounts
Article (112): Financial Year of Licensed Financial Institutions
The financial year for a Licensed Financial Institution shall begin on the first of January and end on the thirty first of December of each year, except for the first financial year, which begins from date of registration of the institution and shall end at the end of the following financial year.
Article (113): Accounts of Licensed Financial Institutions
1) Branches of foreign Licensed Financial Institutions shall maintain separate accounts for all their operations in the State, including the balance sheet and profit and loss account.
2) Branches and sections of a local or foreign Licensed Financial Institution operating in the State, shall, for the purposes of bookkeeping, constitute one financial institution.
Article (114): Auditors of Accounts of Licensed Financial Institutions
1) Each Licensed Financial Institution operating in the State shall, every year, appoint an auditor or more, from amongst the auditors approved by the Central Bank, to audit its accounts. Should the concerned Licensed Financial Institution fail to appoint the auditor, the Central Bank shall appoint an auditor for the concerned institution and determine its remuneration, which shall be paid by the concerned institution.
2) The functions of the auditors shall include preparation of a report on the balance sheet and the profit and loss accounts for the shareholders. The auditors shall state in their report whether the annual balance sheet and profit and loss accounts are true and fair, and whether the concerned Licensed Financial Institution has provided them with all the information and clarifications requested for the performance of their mission. The concerned Licensed Financial Institution shall, at least twenty (20) working days before convening of the general assembly, provide the Central Bank with copy of the auditors’ report, along with copy of the balance sheet and the profit and loss account.
3) The general assembly of a Licensed Financial Institution may not be convened prior to receipt of Central Bank’s remarks on the report. The Central Bank may, within ten (10) working days from date of receipt of the report referred to in item (2) of this article, issue a decision not to approve the profits proposed for distribution to shareholders, if a shortfall in provisions was found, or a decline in the capital adequacy ratio from the established minimum requirement was established, or any reservation indicated in the auditors’ report or from the Central Bank, and deemed to have impact on distributable profits.
4) The auditors’ report, together with the report of the board of directors of the Licensed Financial Institution shall be read to the shareholders at the annual general assembly where the concerned institution is incorporated in the State. Such institution shall provide the Central Bank, within twenty (20) work days from date of convening of the general assembly, with three (3) copies of each report. If the concerned Licensed Financial Institution was incorporated in another jurisdiction, a copy of the auditors’ report shall be forwarded to its head office, and three (3) copies thereof shall be submitted to the Central Bank within twenty (20) working days from date of its issue.
5) The auditors shall not be represented in the board of directors of the Licensed Financial Institution, which appointed it to audit its accounts, nor have one of its staff appointed as employee, or act as advisor to the same institution.
6) A Licensed Financial Institution shall not extend credit facilities, of any type, to the auditors of its accounts. An auditor approved by the Central Bank may not commence its functions at a Licensed Financial Institution, unless any obligations it may have towards such institution were settled.
7) The auditors shall be responsible for the contents of their report on the financial statements of the concerned Licensed Financial Institution. If failure to properly perform their assigned duties or violation of provisions of this Decretal Law and the regulations and decisions issued in implementation thereof was established, the Central Bank may take any necessary measures or procedures, in collaboration and coordination with the concerned authorities in the State to strike their names from the established registers. The Central Bank may, at its own discretion, take any administrative or legal actions against the negligent or violating auditors.
8) The Central Bank may, at its discretion, require the auditors of a Licensed Financial Institution, or its subsidiaries or affiliates, to submit a report, at the expense of the concerned Licensed Financial Institution, establishing their compliance with the provisions of this Decretal Law and the regulations issued in implementation thereof.
9) The Board of Directors shall issue regulations and establish a register for approved auditors, authorized to audit the accounts of Licensed Financial Institutions.
Article (115): Publication and Posting of Accounts Information
1) Each Licensed Financial institution shall publish and post the following information and statements on its website, and in each of its offices and branches in the State:
- a. Copy of its audited balance sheet and profit and loss account, and copy of the auditors’ report. Where a Licensed Financial Institution is incorporated in other jurisdictions, publication of such statements may be carried out in the manner consistent with laws of the concerned jurisdiction.
- b. List of names of members of the board of directors, senior executives and their deputies and assistants.
- c. Names of all wholly or partially owned subsidiaries, or entities related to the concerned Licensed Financial Institution.
2) The Central Bank may, require any Licensed Financial Institution to publish or post any information or statements relating to its accounts, in addition to the requirements stated in item (1) of this article, as it deems appropriate.
Section Three: Resolution and Liquidation of Licensed Financial Institutions
Article (116): Deficiency of Financial Position
Deficiency of Financial Position
1) The Board of Directors shall establish a resolution framework for deposit-taking Licensed Financial Institutions in order to minimize the effect that a deficiency in their financial position may have on the financial system in the State. This includes the effects related to a deficiency in the financial position of companies owned by those Licensed Financial Institutions or their subsidiaries.
2) The resolution framework shall include a set of triggers, both prudential as well as qualitative, which signal material risks that would result in the deficiency of the financial position of the institutions referred to in item (1) of this article. In order to achieve this, the Central Bank shall, at its own discretion, decide any of the following measures and actions for the protection of the concerned institution and its depositors:
- a. Impose a minimum ratio for liquidity of the concerned institution, commensurable with the risks associated with its activities.
- b. Require the concerned institution to provide, as per terms and conditions set by the Board of Directors, additional financial resources for support of its paid-up capital.
- c. Issue a decision to merge the concerned institution with another Licensed Financial Institution.
- d. Permit any Financial Institution to acquire the concerned institution.
- e. Form an interim committee to manage the concerned institution, and authorize such committee to take whatever actions it deems appropriate, as per conditions and controls determined by the Board of Directors, including the possibility of taking the decision to impose a moratorium on all or some of the activities of the concerned institution with immediate effect or within another timeframe as well as consequential actions.
- f. Undertake, over a period specified by the Board of Directors, direct management of the concerned institution, and shall, in this case, substitute management of the concerned institution in exercising all powers, including financial and administrative powers; and the powers and authorities of its board of directors, and its general assembly shall immediately be frozen until expiry of the period of interim management.
- g. Request competent authorities in the State to place the concerned institution under interim custody and seize its assets, property and shareholders rights.
- h. Adopt a decision to request the competent court to pass a decision to liquidate the concerned institution, prepare a plan for liquidation or transfer of its assets and liabilities, as it deems appropriate, along with all related settlements and releases and implement or oversee implementation of the liquidation plan, or adopt a resolution decision, or request the competent court to declare bankruptcy, in accordance with established laws.
- i. Where a decision to merge or liquidate of a Licensed Financial Institution incorporated in another jurisdiction and has a branch operating in the State, the same procedures applicable in the concerned jurisdiction of incorporation shall apply if they provide better protection for customers consumers in the State, unless otherwise agreed with the concerned authority.
- j. Any other measures or actions in accordance with a decision by the Board of Directors.
3) The Central Bank may coordinate with the relevant federal and local authorities before issuance of any decision by the Board of Directors, as per provisions of this article, if necessary. The Central Bank may request the competent judicial authorities to take protective and urgent measures and actions, which would ensure protection of property and interest of investors and depositors, or serve public interest.
Article (117): Publication of Resolution or Liquidation Announcement
1) In case of resolution or liquidation of a Licensed Financial Institution, such an announcement shall be published in the Official Gazette, and in, at least, two local Arabic and English daily newspapers, and for a period not less than three (3) business days.
2) The announcement shall include the following:
- a. A grace period, not be less than three (3) months, allowed to customers consumers of the concerned Licensed Financial Institution to take necessary actions to protect their rights.
- b. Details of the entity assigned for the resolution and its functions or the liquidator and his functions.
3) If the resolution or liquidation occurred as a result of the Licensed Financial Institution being struck-off the Licensed Financial Institution Register, the Chairman of the Board of Director or his deputized representative shall specify, in the decision to strike- off name of the concerned institution, the date of closing down of the concerned institution, and the entity assigned for resolution or liquidation of any outstanding operations on such date.
Article (118): Surveillance of Licensed Financial Institutions under Resolution or Liquidation
The Central Bank shall continue surveillance of operations of any Licensed Financial Institution under resolution or liquidation, until final closure of its offices.
Article (119): Non-Prejudice to Provisions of Other Laws Relating to Resolution or Liquidation
Chapter Six: Consumers’ Protection
Article (120): Confidentiality of Banking and Credit Information
1) All data and information relating to customers’ accounts, deposits, safe deposit boxes and trusts with Licensed Financial Institutions and related transactions shall be considered confidential in nature, and may not be perused, or directly or indirectly disclosed to any third party without the written permission of owner of the account or deposit, his legal attorney or authorized agent, and in legally authorized cases.
2) Such prohibition shall remain valid, even until end of the business relationship between the customer and the Licensed Financial Institution for any reason.
3) Chairmen and members of boards of directors, managers and employees of Licensed Financial Institutions, and experts, consultants and technicians assigned to perform functions therein, are prohibited from disclosing any information or data on their customers; their accounts or deposits or transactions relating thereto, or enable third parties to peruse them, except in legally authorized cases.
4) Such prohibition shall apply to all agencies and Persons, and whoever, by virtue of his profession, position or nature of work, is able to, directly or indirectly, peruse such information and data.
5) The Central Bank shall establish rules and conditions organizing exchange of banking and credit information, in its capacity as the competent Regulatory Authority in the State in this regard.
6) The provisions of item nos. (1) and (2) of this article shall be without prejudice to the following:
- a. The powers legally vested on security and judicial authorities, the Central Bank and its employees.
- b. The duties assigned to auditors of accounts of the concerned institutions.
- c. The obligation of the concerned institutions to issue, upon request of the beneficiary, a certificate of the reasons for declining to cash a check.
- d. The obligation of the concerned institutions to issue a certificate of partial payment of value of a check, where the consideration for payment is less than the value of the check, pursuant to the provisions of the referenced Commercial Transactions Law.
- e. The right of the concerned institutions to disclose whole or part of the data relating to the customer’s transactions, in order to establish its right in a legal dispute in respect of such transactions, with its customer.
- f. Provisions of established laws and international agreements in the State, in addition to anti-money laundering, terrorist financing and illegal organizations provisions.
Article (121): Protection of Consumers of the Licensed Financial Institutions
1) The Central Bank shall establish regulations relating to protection of consumers of Licensed Financial Institutions, in line with the nature of activities the latter carry on and the services and products they provide.
2) The Central Bank may establish a unit that enjoys independent legal personality, to receive and decide on complaints of customers of licensed financial institutions. The Board of Directors shall issue a resolution establishing this unit, specifying its tasks, charter, powers and the human resources and financial regulations applicable thereto.
3) The Central Bank and Licensed Financial Institutions shall work together to raise public awareness of the types of banking services and financial products, and their inherent risks, through all means of communication and media, in accordance with the rules set by the Central Bank in this regard.
4) Licensed Financial Institutions may not charge interest on accrued interest- compound interest- in relation to facilities extended to customers, and shall, in this regard, follow the rules and controls prescribed in regulations issued by the Central Bank.
Article (121) bis:
Credit Facilities Guarantees
1) Licensed Financial Institutions must obtain adequate guarantees for all types of facilities provided to natural persons and sole proprietorships customers, commensurable with the customer’s income, or the guarantee, if any, and the size of required facilities, as determined by the Central Bank.
2) A claim or a lawsuit or a plea shall not be admissible before competent judicial authorities or arbitration tribunals if filed by a licensed financial institution in respect of credit facilities extended to a natural person or a sole proprietorship, in case such institution had failed to obtain the guarantees referred to in paragraph (1) hereinabove.
3) The Central Bank may impose the administrative or financial sanctions it deems appropriate on licensed financial institutions that violate the provision of paragraph (1) hereinabove, in accordance with Article (137) of this Decretal Federal Law.
This article has been amended by Decretal Federal Law No. (09) of 2021 and Decretal Federal Law No. (23) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 2(effective from 26/07/2021 to 02/01/2023)1)The Central Bank shall establish regulations relating to protection of customers of Licensed Financial Institutions, in line with the nature of activities the latter carry on and the services and products they provide. The Central Bank may establish a unit that enjoys independent legal personality, and is in charge of receiving and handling complaints of clients of licensed financial institutions. The Unit’s system of work, its powers, regulations and regulations related to human resources and its financial affairs shall be issued by a decision of the Board of Directors.
2)The Central Bank and Licensed Financial Institutions shall work together to raise public awareness of the types of banking services and financial products, and their inherent risks, through all means of communication and media, in accordance with the rules set by the Central Bank in this regard.
3)Licensed Financial Institutions are not permitted to charge interest on accrued interest charged on any credit or funding facilities granted to customers.
Version 1(effective from 31/10/2018 to 26/07/2021)1) The Central Bank shall establish regulations relating to protection of customers of Licensed Financial Institutions, in line with the nature of activities the latter carry on and the services and products they provide.
2) The Central Bank and Licensed Financial Institutions shall work together to raise public awareness of the types of banking services and financial products, and their inherent risks, through all means of communication and media, in accordance with the rules set by the Central Bank in this regard.
3) Licensed Financial Institutions are not permitted to charge interest on accrued interest charged on any credit or funding facilities granted to customers.
Article (122): Deposits Guarantee Scheme
The Board of Directors may issue regulations for protection of deposits and the rights of depositors of Licensed Financial Institutions in coordination with the Ministry. Such regulation may include establishment of a compensation fund and determination of its structure.
Article (123): Financial Inclusion
The Board of Directors shall establish necessary regulations and mechanisms to ensure that every natural Person shall have the right to access all or part of the banking and financial services and products from Licensed Financial Institutions suited to his/her need.
Part IV – Financial Infrastructure –
Chapter One: Funds Transfer and Settlement of Securities
Article (124): Clearing and Settlement Operations
1) The Central Bank may:
- a. Establish, develop, and/or operate one or more clearing or settlement systems for transfer of funds, and settlement of securities issued by the Central Bank or the Public Sector and other obligations between Participant Persons in such systems, and may conduct such on its own or in partnership with any other party, or by outsourcing to third parties.
- b. Link the systems referred to in paragraph (a) of this item, to similar systems inside and outside the State.
- c. Establish and/or operate central securities depository for securities issued by the Central Bank or the Public Sector and data repository systems for monetary and financial transactions in the State, and link such systems to similar systems inside and outside the State.
2) The Central Bank shall coordinate with concerned other regulatory authorities and bodies in the State, in relation to the establishment of data repository systems for monetary and financial transactions referred to in paragraph (c) of item (1) of this article.
3) The Board of Directors shall issue the regulations related to the systems referred to in item (1) of this article, the rules of participation in these systems, and the rules to execute related operations.
Articles (124) Bis. (1) and (124) Bis. (2) have been added as per the Decretal Federal Law No. (23) of 2022.Article (124) bis. (1):
Application for Licensing Financial Infrastructure System or Extension of License Scope
1) Any juridical person may, in accordance with the regulations issued by the Board of Directors, submit to the Central Bank an application for licensing a Financial Infrastructure System, or extension of the scope of a previously issued license.
2) The Board of Directors shall issue the rules, regulations, standards and conditions relating to licensing a Financial Infrastructure System, including:
- a. Fit and proper criteria;
- b. The resources required for the system
- c. Control and monitoring systems
3) The Board of Directors may, at its own discretion and as it deems appropriate to safeguarding public interest, add any requirements or conditions to be fulfilled by the applicant.
Article (124) bis. (2):
Deciding on Application for Licensing Financial Infrastructure System or Extension of License Scope
1) Deciding on licensing of Financial Infrastructure System or extension of its scope shall be within a period not exceeding sixty (60) working days from date of meeting all licensing conditions and requirements. Expiry of this period without decision on the application shall be considered an implicit rejection thereof.
2) The Central Bank may require the applicant to fulfill licensing requirements and conditions within such period as specified by the Central Bank.
3) The Central Bank may reject an application for licensing of a Financial Infrastructure System or extension of its scope, at its own discretion and based on the capacity of the financial sector in the State, and the needs of the local market. The Central Bank’s decision in this regard shall be final and not subject to appeal before the Appeals and Grievances Committee.
4) The applicant shall be notified, officially, of the reasoned rejection decision within a period not exceeding twenty (20) working days from date of its issue.
Article (125): Retail Payment Operations and Related Electronic Services
The Central Bank shall solely:
1) Have the authority to issue regulations, rules, and procedures relating to electronic banking operations, digital money, Stored Value Facilities, and shall regulate Retail Payment Systems and related electronic banking and financial services.
2) Take all measures and procedures it deems appropriate to reduce risks to the State’s financial and economic systems associated with operations and systems referred to in item (1) of this article.
Chapter Two: Powers and Functions of the Central Bank Pertaining to Financial Infrastructure Systems
Article (126): Designation of Systems
1) The Central Bank may designate any Financial Infrastructure System as systemically important if it considers, at its own discretion, that any malfunction or inefficiency in the operation of such system would negatively impact processing of the daily operations of financial institutions operating in the State, or the stability of the financial system in the State.
2) For a Financial Infrastructure System to be designated, it shall meet one of the following conditions:
- a. The concerned system is operating in the State;
- b. The concerned system has the capacity to accept clearing and settlement of financial Transfer Orders denominated in national Currency, without prejudice to the provisions of Article (28) of this decretal law; or
- c. The concerned system has the capacity to provide transfer, clearing or settlement of financial Transfer Orders, for retail payment activities, denominated in any currency.
3) Should the Central Bank intend to designate any of the Financial Infrastructure Systems it licenses as systemically important, it shall:
- a. Notify the operator of the system, or its Settlement Institution, officially, of its intention to designate this system as systemically important, clarify grounds of such intention, in addition to other terms and conditions attached to such designation.
- b. Allow such period as specified in the notice referred to in paragraph (a) of this item, which shall not be less than ten (10) working days from date of notification, within which the system’s operator or its Settlement Institution may provide their opinions, or make representations, as to why the system should not be designated.
- c. Issue its decision on designation of the system, within a period not exceeding twenty (20) working days from date of receipt of responses from concerned parties, or expiry of the period stated in the notice, without response.
4) The operator of the Designated System or the Settlement Institution may submit a grievance against the designation decision referred to in item (3) of this article by applying to the Grievances and Appeals Committee, in accordance with the provisions of Part V of this Decretal Law.
5) The Clearing and Settlement Systems established, developed, and/ or operated, in accordance with the provisions of Article (124) of this Decretal Law shall be deemed as Designated Systems.
6) Should the Central Bank intend to designate any of the Financial Infrastructure Systems licensed by any of the other Regulatory Authorities in the State or in other jurisdictions as systemically important, it shall submit its opinion in this regard to the concerned regulatory authority. Should the concerned regulatory authority have no objection to such designation, it shall:
- a. Notify the operator of the system, or its Settlement Institution, officially of the intention to designate this system as systemically important, clarify grounds of such intention, in addition to other terms and conditions attached to such designation.
- b. Allow such period as specified in the notice referred to in paragraph (a) of this item, which shall not be less than ten (10) working days from date of notification, within which the system’s operator or its Settlement Institution may provide their opinions, or make representations, as to why the system should not be designated.
- c. Issue its final approval or disapproval decision on the Central Bank’s request to designate the concerned system, within a period not exceeding twenty (20) working days from date of receipt of responses from concerned parties, or expiry of the period stated in the notice, without response.
7) The Central Bank may revoke designation of a particular Financial Infrastructure System it licenses or request such action from the concerned regulatory authority, if it considered, at its own discretion, that the system is no longer of systemic importance. The concerned regulatory authority, the operator of the system, or its Settlement Institution shall be notified, officially, of such decision, as the case may be.
Article (127): Oversight of Systems
1) The Central Bank shall solely have oversight powers over operations of systems which it licenses and shall ensure their soundness, in accordance with relevant international standards. For such purpose, the Central Bank may require the operators of systems or their Settlement Institutions to take required measures and procedures.
2) The Central Bank shall be responsible for monitoring the implementation of required additional oversight measures and procedures on Designated Systems, licensed by any of the other Regulatory Authorities, in the State or in other jurisdictions in collaboration and coordination with the concerned regulatory authority, and may request in this regard from the concerned regulatory authority:
- a. Require operators of the Designated Systems or their Settlement Institutions to comply with the instructions it issues in this respect and any relevant international standards.
- b. Ensure proper and regular functioning of Designated Systems.
- c. Ensure soundness of financial positions of operators of Designated Systems and their Settlement Institutions, when deemed necessary.
- d. Require the operators of the Designated Systems or their Settlement Institutions to provide it, with the information it deems appropriate for achievement of its objectives and discharge of its functions.
3) The Central Bank may appoint any person it deems fit amongst experts and advisers specialized in financial infrastructure to assist the Central Bank in performing its duties and functions in accordance with the provisions of Part IV of this decretal law, and to keep up with best international standards and practices in this area.
Article (128): Suspension or Revocation of a License
1) The Central Bank may suspend or revoke the license granted to a Financial Infrastructure System, in accordance with the provisions of Article nos. (124) and (125) of this decretal law, by way of an official notice to the operator or the Settlement Institution of the concerned system and take necessary actions in this respect, as the case may be, if it considered that the system is no longer capable of conducting its operations. The Central Bank shall allow such period as specified in the notice referred to in this item, which shall not be less than twenty (20) working days from the date of notice, within which the concerned system operator or its Settlement Institution may object to the Central Bank’s decision to suspend or revoke the license and provide their justifications for such objection, in accordance with the provisions of Part V of this decretal law.
2) The Central Bank, if it considers that any Designated System licensed by any of the Regulatory Authorities in the State or in other jurisdictions is no longer capable of conducting its operations, may request the concerned regulatory authority, by way of an official notice, to suspend or revoke the license of this system and take necessary actions in this respect, as the case may be. The concerned regulatory authority shall have the right to approve or reject the request of the Central Bank. In case of approval, the procedures and controls in force by the concerned authority shall be applicable.
3) In all cases, the suspension or revocation of a license granted to a Designated System in accordance with the provisions of this article, shall not affect any transaction cleared or settled in the concerned system prior to the effective date of suspension or revocation.
This article has been amended by Decretal Federal Law No. (09) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 26/07/2021)1) The Central Bank may suspend or revoke a license granted to a Financial Infrastructure System, in accordance with the provisions of article nos. (124) and (125) of this decretal law, via an official notice to the operator or the Settlement Institution of the concerned system and take necessary actions in this respect, as the case may be, if it considered that the system is no longer capable of conducting its operations. The Central Bank shall allow such period as specified in the notice referred to in this item, which shall not be less than twenty (20) working days from date of notification, within which the concerned system operator or its Settlement Institution may object to the Central Bank’s decision to suspend or revoke the license and provide their justifications for such objection, in accordance with the provisions of Part Four of this decretal law.
2) The Central Bank, if it considers that any Designated System licensed by any of the Regulatory Authorities in the State or in other jurisdictions is no longer capable of conducting its operations, may request the concerned regulatory authority, via an official notice, to suspend or revoke the license of this system and take necessary actions in this respect, as the case may be. The concerned regulatory authority shall have the right to approve or reject the request of the Central Bank. In case of approval, the procedures and controls in force by the concerned authority shall be applicable.
3) In all cases, the suspension or revocation of a license granted to a Designated System in accordance with the provisions of this article, shall not affect any transaction cleared or settled in the concerned system prior to the effective date of suspension or revocation.
Article (129): Authority to Issue Regulations and Instructions
1) The Board of Directors shall issue regulations, instructions, rules, directives, and codes of conduct as it deems appropriate for the implementation of the provisions of Part IV of this decretal law, and to achieve the objectives of the Central Bank and discharge its functions, including:
- a. Regulations, conditions and rules relating to licenses, granted by the Central Bank in accordance with the provisions of Article nos. (124) and (125) of this Decretal Law, to operators of Financial Infrastructure Systems or the Settlement Institutions for such systems and their Participant Persons.
- b. Regulations, rules and standards relating to the designation and oversight of Financial Infrastructure Systems, as per the provisions of Article nos. (126) and (127) of this Decretal Law, monitoring operations of such systems and enforcing compliance requirements on Participant Persons thereof.
2) The Central Bank may exempt operators of Financial Infrastructure Systems it licenses, the Settlement Institutions of such systems or Participant Persons, in a general or specific manner, from the provisions of any of the regulations, instructions, rules, directives, and controls issued by it.
Article (130): Determining Violations
1) The Board of Directors shall issue regulations specifying types of violations pertaining to Financial Infrastructure Systems licensed by the Central Bank, and any of the following instances shall be considered a violation to the terms and conditions relating thereto:
- a. Violation of operational requirements of systems and related settlement rules and procedures.
- b. Failure of an operator of a system or its Settlement Institution to comply with a Central Bank request for information or documents.
- c. Failure to comply with Central Bank’s decisions and instructions, and failure to take a particular action, which the Central Bank considers necessary to render the system compliant with the criteria it sets.
- d. Failure, on the part of an operator of a system or its Settlement Institution to report any action taken under the systems Default Arrangements, in respect of a Participant Person.
- e. Failure, on the part of a Participant Person, to notify the system operator, its Settlement Institutions, and the Central Bank of issuance of judgement to declare it bankrupt or place it under liquidation.
- f. Operating a system without obtaining a license in accordance with the provisions of Article nos. (124) and (125) of this Decretal Law.
- g. Failure of an operator of a system or its Settlement Institution to comply with any request from the Central Bank or any other government agency, relating to default, within a specified time period.
- h. Failure of an operator of a system to notify the Central Bank of issuance of judgment regarding declaration of bankruptcy or liquidation of any Participant Person.
- i. Providing the Central Bank with incorrect or misleading information.
- j. Adding an incorrect entry to any registration book or in any document related to a particular system, or causing alteration, deletion or obliteration of such entry.
- k. Any other related action to the clearing and settlement operations or to the retail payment operations the Central Bank considers a violation.
2) The Central Bank may take whatever actions it deems appropriate to correct any violations referred to in item (1) of this article, and determine settlement thereof.
3) The Central Bank shall officially notify the violating Person, in accordance of item (1) of this article, of any actions that shall be undertaken against it. The violating Person shall be allowed a period not exceeding ten (10) working days from date of notification to submit a grievance against the Central Bank decision. In case the grievance was rejected, the violating Person may escalate the matter to the Grievances and Appeals Committee in accordance with the provisions of this Decretal Law. The decision of the Grievances and Appeals Committee shall be final. Should the violating Person not respond to Central Bank’s decision within the period prescribed in this item, the decision of the Central Bank shall be final and binding.
Chapter Three: Finality of Transactions and Proceedings
Article (131): Finality of Payment and Settlement
1) All transactions conducted through a Financial Infrastructure System, which meets one of the designation conditions referred to in item (2) of Article (126) of this Decretal Law shall be final, irrevocable and irreversible, in any of the following cases:
- a. Transfer of funds from or to the account of a Participant Person.
- b. Settlement of a payment obligation.
- c. Settlement of an obligation to transfer, or the actual transfer of book- entry securities.
2) No transfer or settlement pertaining to the transactions referred to in item (1) of this article shall be cancelled, set aside, re-paid, or reversed, nor shall it be rectified, whether by a court judgement order, or by law.
Article (132): Precedence of Implementation of a Financial Infrastructure Systems’ Rules and Procedures, over the General Insolvency and Bankruptcy Rules and Procedures
1) None of the following operations and procedures carried out through Financial Infrastructure Systems, which meet one of designation conditions referred to in item (2) of Article (126) of this Decretal Law, shall be regarded, as to any extent, invalid on the grounds of commencement of realization of assets of a Person under liquidation, insolvency, financial restructuring, or bankruptcy:
- a. A Transfer Order.
- b. Any disposition of property in pursuance of such Transfer Order.
- c. The Default Arrangements of such systems.
- d. The rules of such systems as to the settlement of Transfer Orders not dealt with under their Default Arrangements.
- e. Any arrangements for the purpose of realizing collateral security in connection with participation in such systems, other than its Default Arrangements.
2) The relevant insolvency officer or any Person appointed to manage the insolvency procedures in cases of bankruptcy or liquidation, shall not take any actions or procedures contrary to the provisions of this Decretal Law, or preclude or interfere with Default Arrangements of systems referred to in item (1) of this article.
3) An obligation arising out of a Transfer Order, which is the subject of an action taken under Default Arrangements of systems referred to in item (1) of this article, shall not be proved in a bankruptcy or liquidation procedures, until completion of the transfer or payment order.
4) A debt or other liability, which by virtue of item (3) of this article may not be proved, shall not be taken into account for the purposes of any set-off, offset, or net out of debt or obligations until the completion of the action taken under the Default Arrangements of such systems.
Article (133): Netting of Obligations of Insolvent or Bankrupt Parties
1) The operator of a Financial Infrastructure System, which meets any of the designation conditions referred to in item (2) of Article (126), may effect Netting of all obligations owed to or by a Participant Person in this System, which incurred before the point of time where the competent court has made an order for bankruptcy or liquidation of the concerned Participant Person.
2) In case Netting has been effected as provided in item (1) of this article, then:
- a. The obligations that are netted shall be disregarded in the bankruptcy or liquidation proceedings and
- b. Any net obligation owed to or by the Participant Person that has not been discharged is payable to the Participant Person and may be recovered for the benefit of his creditors or is provable in the bankruptcy or liquidation, as the case may be.
3) Netting operations processed by the concerned system’s operator in accordance with item (1) of this article shall not be cancelled during a bankruptcy or liquidation process, nor any financial transfers already paid in accordance with paragraph (a) of item (2) of this article.
Article (134): Preservation of Rights in Underlying Transactions
1) Except to the extent that it expressly provides, this Decretal Law shall not operate to limit, restrict or otherwise affect:
- a. Any right, title, interest, privilege, obligation or liability of a Person resulting from the underlying transaction in respect of a Transfer Order that has been entered into a Financial Infrastructure System, which meets any of the designation conditions referred to in item (2) of Article (126).
- b. Any investigation, legal proceedings or remedy in respect of any such right, title, interest, privilege, obligation or liability.
2) Nothing in item (1) of this article shall be construed to require:
- a. The unwinding of any Netting done by the operator of the concerned system, whether pursuant to its Default Arrangements or otherwise;
- b. The revocation of any Transfer Order given by a Participant Person which is entered into the concerned system; or
- c. The reversal of a payment or settlement made under the operating rules of the concerned system.
Article (135): Obligation of Participant Person to Notify of Insolvency
1) A Participant Person in a Financial Infrastructure System, which meets any of the designation conditions referred to in item (2) of Article (126) shall notify the operator of the system or its Settlement Institution, the concerned regulatory authority, and the Central Bank, as soon as practicable if there comes to his knowledge any of the following events occurring in the State or in other jurisdictions:
- a. Presentation of a plea for declaration of his bankruptcy or liquidation;
- b. Issuance of a judgement for declaration of his bankruptcy or liquidation; or
- c. The making of owners, shareholders, or management of a Participant Person voluntary winding up statement in his respect.
2) A Participant Person failing to notify of a relevant event referred to in item (1) of this article within the required timeframe is not in contravention if:
- a. He took reasonable steps to comply with the provisions of item (1) of this article or
- b. The agencies referred to in item (1) of this article were already aware of the relevant event by the time the Participant Person was required to notify the operator under the provisions of this article.
Part V – Grievances and Appeals –
Article (136): Grievances and Appeals Committee
1) Under the provisions of this Decretal Law, an independent committee named “Grievances and Appeals Committee” shall be established. The Cabinet shall issue a resolution, based on a proposal by the Board of Directors, establishing the committee’s formation, duration, system of work, and all procedures and rules related to adjudication of grievances and appeals, including fees due for consideration.
2) In the formation of the committee, the presence of one or more judges and two experts with competence in financial and banking matters should be taken into consideration.
3) A nominated committee member may not be a member of the Board of Directors, nor holder of any position at the Central Bank or at any of the Licensed Financial Institution.
4) The chairman of the committee or any of its members shall have no interest with any party to the dispute, otherwise he shall be required to disclose such interest, and in such case another member shall be temporarily appointed to hear the presented dispute.
5) With the exception of the regulations, directives, instructions, policies, and regulatory and supervisory decisions of a general nature, the Committee, shall solely and exclusively have jurisdiction to decide on grievances and appeals against any decisions related to financial and banking activities issued by the Central Bank in accordance to the provision of this Decretal Law, and may, for such purposes take all or some of the following actions:
- a. Require any Person to appear in front of the Committee to present any evidence, testimony, information or statement.
- b. Hear the testimony of any witnesses under oath.
- c. Commission any experts it deems appropriate to provide opinion on any matter relating to the dispute.
- d. Take whichever actions and procedures it deems appropriate for discharge of its mandate.
6) Appeals against decisions that fall within the competence of the committee in accordance with the provisions of this article are not accepted before the grievance or appeal thereon before the committee, and the grievance is decided according to the circumstances.
7) If the Committee decided to reject or not accept the grievance of appeal, the Committee may impose on the applicant a fine, not exceeding (200,000) two hundred thousand Dirhams.
8) The Committee may suspend the appealed decision, if necessary, until it reached a decision on the dispute.
9) The grievance or appeal against any decision before the committee shall not be accepted after the lapse of (15) fifteen working days from the date on which the concerned person is notified of it, or if his knowledge of it is proven with certainty.
10) A decision issued by the Committee on the grievance or appeal shall be final and shall only be challenged at the Higher Federal Court within a period of (20) twenty work days from date of its notification. The Higher Federal Court may, upon request of the appellant, suspend the decision issued by the Committee until it reached its decision on the subject, if it considered that the appeal is based on genuine grounds and that implementation of the Committee’s decision shall have irreversible consequences.
This article has been amended by Decretal Federal Law No. (25) of 2020, and Decretal Federal Law No. (9) of 2021 respectively. You are viewing the latest version. To view previous versions, click the version boxes below.Version 2(effective from 02/01/2021 to 26/07/2021)1) Under the provisions of this Decretal Law, a committee within the Central Bank, named “Grievances & Appeals Committee” shall be established. The Cabinet shall issue a resolution, based on a proposal by the Board of Directors, establishing the committee’s formation, duration, system of work, and all procedures and rules related to adjudication of grievances and appeals, including fees due for consideration.
2) In the formation of the committee, the presence of one or more judges and two experts with competence in financial and banking matters should be taken into consideration.
3) A nominated committee member may not be a member of the Board of Directors, nor holder of any position at the Central Bank or at any of the Licensed Financial Institution.
4) The chairman of the committee or any of its members shall have no interest with any party to the dispute, otherwise he shall be required to disclose such interest, and in such case another member shall be temporarily appointed to hear the presented dispute.
5) The Committee shall have the jurisdiction to decide on grievances and appeals against any decisions related to financial and banking activities issued by the Central Bank related to licensing, authorization of individuals, and licensing and designation of Financial Infrastructure Systems, and may, for such purposes take all or some of the following actions:
- a. Require any Person to appear in front of the Committee to present any evidence, testimony, information or statement.
- b. Hear the testimony of any witnesses under oath.
- c. Commission any experts it deems appropriate to provide opinion on any matter relating to the dispute.
- d. Take whichever actions and procedures it deems appropriate for discharge of its mandate.
6) If the Committee rejected the grievances or appeal on the grounds that it was filed by a party of no capacity or interest, the Committee may impose on the applicant a fine, not exceeding two hundred thousand (200,000) Dirhams.
7) The Committee may suspend the appealed decision, if necessary, until it reached a decision on the dispute.
8) A decision issued by the Committee on the grievance or appeal shall be final and shall only be challenged at the Higher Federal Court within a period of twenty (20) work days from date of its notification. The Higher Federal Court may, upon request of the appellant, suspend the decision issued by the Committee until it reached its decision on the subject, if it considered that the appeal is based on genuine grounds and that implementation of the Committee’s decision shall have irreversible consequences
Version 1(effective from 31/10/2018 to 02/01/2021)1) An independent committee, named “Grievances & Appeals Committee” shall be established in accordance with the provisions of this decretal law under the chairmanship of a Court of Appeal judge, and membership of two (2) judges from the same court, in addition to two (2) experts nominated by the Board of Directors.
2) The Cabinet shall issue a resolution naming the chairman and members of the committee, based on the nomination of the Higher Judicial Council, with respect to the chairman of the committee and its member judges.
3) The Cabinet shall issue a resolution, based on a proposal by the Board of Directors, establishing the committee’s charter, which would include:
- a. All rules and procedures relating to settlement of grievances and appeals, including payable fees.
- b. Remunerations of members of the committee.
4) Membership of the committee shall be for a term of four (4) years, renewable to similar period(s). In case the seat of a member became vacant before expiry of the membership term, for whatever reason, a successor shall be appointed for the remaining term, in the same manner in which the previous member was selected.
5) A nominated committee member may not be a member of the Board of Directors, nor holder of any position at the Central Bank or at any of the Licensed Financial Institution.
6) The chairman of the committee or any of its members shall have no interest with any party to the dispute, otherwise he shall be required to disclose such interest, and in such case another member shall be temporarily appointed to hear the presented dispute.
7) The Committee shall have the sole and exclusive jurisdiction to decide on grievances and appeals against any decisions by the Central Bank related to licensing, authorization of individuals, and licensing and designation of Financial Infrastructure Systems, and may, for such purposes take all or some of the following actions:
- a. Require any Person to appear in front of the Committee to present any evidence, testimony, information or statement.
- b. Hear the testimony of any witnesses under oath.
- c. Commission any experts it deems appropriate to provide opinion on any matter relating to the dispute.
- d. Take whichever actions and procedures it deems appropriate for discharge of its mandate.
8) If the Committee rejected the grievances or appeal on the grounds that it was filed by a party of no capacity or interest, the Committee may impose on the applicant a fine, not exceeding two hundred thousand (200,000) Dirhams.
9) The Committee may suspend the appealed decision, if necessary, until it reached a decision on the dispute.
10) A decision issued by the Committee on the grievance or appeal shall be final and shall only be challenged at the Higher Federal Court within a period of twenty (20) work days from date of its notification. The Higher Federal Court may, upon request of the appellant, suspend the decision issued by the Committee until it reached its decision on the subject, if it considered that the appeal is based on genuine grounds and that implementation of the Committee’s decision shall have irreversible consequences
Part VI – Administrative and Financial Sanctions and Penalties –
Chapter One: Administrative and Financial Sanctions
Article (137)
1) Without prejudice to other sanctions stated in any other laws in the State, and upon establishment of a violation by any Licensed Financial Institution or by any Authorized Individual of any of the provisions of this Decretal Law or the regulations, decisions, rules, standards or instructions issued by the Central Bank in implementation thereof, or any measures taken by the Central Bank, including procedures for encountering money laundering, combating terrorist financing, and illegal organizations, the Central Bank shall, at its own discretion, decide to impose one or more of the following sanctions or take any of the following measures:
- a. Issue, by any means, a caution to the violator.
- b. Require the violating Licensed Financial Institution to take the necessary actions and measures that the Central Bank deems appropriate to rectify the violation.
- c. Prohibit violating Licensed Financial Institution from conducting some operations, or carrying on some Licensed Financial Activities, or impose any restrictions, conditions or limitations on all or certain operations and activities.
- d. Impose conditions or restrictions on the license of the violating Licensed Financial Institution.
- e. Reduce or suspend the ability of the violating Licensed Financial Institution to draw on the Central Bank’s funds through the Standing Facilities.
- f. Require the violating Licensed Financial Institution to deposit funds with the Central Bank without return and for the period Central Bank deems appropriate, in addition to the credit balance referred to in Article (32) of this Decretal Law.
- g. Impose a fine of four hundred (400) basis points over the prevailing base interest rate of the Central bank on any shortfall in the Reserve Requirements referred to in Article (32) of this Decretal Law.
- h. Require the violating Licensed Financial Institution to return to customers the funds it obtained as a result of its violation of the provisions of this Decretal Law and any excess funds including revenue and profits shall devolve to the Central Bank.
- i. Impose a fine between one time and ten times the value of unjust enrichment as determined by the Central Bank, which the violating Licensed Financial Institution has, unlawfully acquired, as a result of the violation.
- j. Impose a fine on the violating Licensed Financial Institution not exceeding (200,000,000) two hundred million Dirhams.
- k. Delink the violating Licensed Financial Institution from one or all Financial Infrastructure Systems.
- l. Withdraw the license of the violating Licensed Financial Institution and strike off its name from the Register.
- m. Impose conditions or restrictions on the authorization of the violating Authorized Individual.
- n. Impose a fine on the violating Authorized Individual not less than (100,000) one hundred thousand Dirhams and not exceeding (2,000,000) two million Dirhams.
- o. Prohibit the violating Authorized Individual from undertaking any Designated Function at the Licensed Financial Institution he works for, or any other Licensed Financial Institution.
- p. Any other financial or administrative measures or sanctions issued by a decision of the Board of Directors. The decision specifies the authority entrusted with imposing these sanctions or measures.
2) Decisions to impose the sanctions referred to under item (1) if this article shall be made by the Governor except for the sanction stipulated in item (I) herein shall be made by the Board of Directors.
3) In all cases, the violator shall be notified, officially, of the reasoned decision within fifteen (15) working days from date of its issue. Such notice shall include the following:
- a. Content of the decision.
- b. Reasons for the decision.
- c. Effective date of the decision.
- d. A statement advising the violator of its right to submit a grievance against the decision in front of the Grievances and Appeals Committee, in accordance with the provisions of this Decretal Law.
This article has been amended by Decretal Federal Law No. (09) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 26/07/2021)1) Without prejudice to other sanctions stated in any other laws in the State, and upon establishment of a violation by any Licensed Financial Institution or by any Authorized Individual of any of the provisions of this decretal law or the regulations, decisions, rules, standards or instructions issued by the Central Bank in implementation thereof, or any measures taken by the Central Bank, including procedures for encountering money laundering, combating terrorist financing, and illegal organizations, the Central Bank shall, at its own discretion, decide to impose one or more of the following penalties or take any of the following measures:
- a. Issue by any means, a caution to the violator.
- b. Require the violating Licensed Financial Institution to take necessary actions and measures that the Central Bank deems appropriate to rectify the violation.
- c. Prohibit violating Licensed Financial Institution from conducting some operations, or carrying on some Licensed Financial Activities, or impose any restrictions, conditions or limitations on all or certain operations and activities.
- d. Impose conditions or restrictions on the license of the violating Licensed Financial Institution.
- e. Reduce or suspend the ability of the violating Licensed Financial Institution to draw on the Central Bank’s funds through the Standing Facilities.
- f. Require the violating Licensed Financial Institution to deposit funds with the Central Bank without return and for the period Central Bank deems appropriate, in addition to the credit balance referred to in Article (32) of this decretal law.
- g. Impose a fine of four hundred (400) basis points over the prevailing base interest rate of the Central bank on any shortfall in the Reserve Requirements referred to in Article (32) of this decretal law.
- h. Require the violating Licensed Financial Institution to return to customers the funds it obtained as a result of its violation of the provisions of this decretal law and any excess funds including revenue and profits shall devolve to the Central Bank.
- i. Impose a fine between one (1) time and ten (10) times the value of unjust enrichment as determined by the Central Bank, which the violating Licensed Financial Institution has, unlawfully acquired, as a result of the violation.
- j. Impose a fine on the violating Licensed Financial Institution not less than two million (2,000,000) Dirhams and not exceeding two hundred million (200,000,000) Dirhams.
- k. Delink the violating Licensed Financial Institution from one or all Financial Infrastructure Systems.
- l. Withdraw the license of the violating Licensed Financial Institution and strike off its name from the Register.
- m. Impose conditions or restrictions on the authorization of the violating Authorized Individual.
- n. Impose a fine on the violating Authorized Individual not less than one hundred thousand (100,000) Dirhams and not exceeding two million (2,000,000) Dirhams.
- o. Prohibit the violating Authorized Individual from undertaking any Designated Function at the Licensed Financial Institution he works for, or any other Licensed Financial Institution.
2) Decisions to impose the sanctions referred to under paragraphs (a, b, c, e, f, g, and h) shall be made by the Governor and decisions concerning other sanctions shall be made by the Board of Directors.
3) In all cases, the violator shall be notified, officially, of the reasoned decision within fifteen (15) working days from date of its issue. Such notice shall include the following:
- a. Content of the decision.
- b. Reasons for the decision.
- c. Effective date of the decision.
- d. A statement advising the violator of its right to submit a grievance against the decision in front of the Grievances & Appeals Committee, in accordance with the provisions of this decretal law
Chapter Two: Penalties
Article (138)
Without prejudice to any harsher punishment provided for in any other law, the offences referred to in the following articles shall be punishable by the respective penalties stated therein.
Article (139)
An employee or representative of the Central Bank or any member of the committees formed within the Central Bank, or any member of the Board of Directors, who discloses any confidential information in breach of provisions of Article (26) of this Decretal Law, shall be punished by imprisonment for a term not exceeding three (3) months and a fine not exceeding one hundred thousand (100,000) Dirhams, or by either of these two punishments.
Article (140)
Whoever issues Currency in contravention to the provisions of this Decretal Law, shall be punished by imprisonment for a term not exceeding twenty (20) years and a fine not exceeding one hundred million (100,000,000) Dirhams, or by either of these two punishments.
Article (141)
Whoever, publicly and intentionally mutilates, destroys or tears up Currency, shall be punished by imprisonment and a fine of not less than (10,000) ten thousand dirhams, or by one of these two penalties.
This article has been amended by Decretal Federal Law No. (54) of 2023. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 01/11/2023)Whoever, publicly and intentionally mutilates, destroys or tears up Currency, shall be punished by a fine, which shall be the greater of one thousand (1,000) Dirham and ten (10) times the value of the mutilated, destroyed or torn Currency.
Article (142)
1) Whoever contravenes the provisions of item (1) of Article (68) of this Decretal Law shall be punished by imprisonment and with a fine not less than two hundred thousand (200,000) Dirhams and not exceeding ten million (10,000,000) Dirhams, or by either of these two punishments.
2) Whoever contravenes the provisions of item (2) of Article (68) of this Decretal Law shall be punished by imprisonment for a period not exceeding six (6) months and with a fine not less than one hundred thousand (100,000) Dirhams and not exceeding five million (5,000,000) Dirhams, or by either of these two punishments.
Article (143)
Whoever violates the conditions and restrictions imposed on a license to carry on Licensed Financial Activities, shall be punished by a fine not less than two hundred thousand (200,000) Dirhams and not exceeding ten million (10,000,000) Dirhams.
Article (144)
Whoever contravenes the Central Bank’s instructions regarding deficiency in the financial position, referred to in Article (116) of this Decretal Law, shall be punished by imprisonment for a term not less than one (1) year, and a fine of not less than one million (1,000,000) Dirhams and not exceeding ten million (10,000,000) Dirhams, or by either of these two punishments.
Article (145)
Article (146)
Whoever violates any of the provisions of Article (83) of this decretal law, shall be punished by imprisonment for a term of not less than one (1) year and a fine of not less than five hundred thousand (500,000) Dirhams with a further fine of fifty thousand (50,000) Dirhams per day in case of continuing breach, which cumulatively shall not exceed five million (5,000,000) Dirhams, or by either of these two punishments.
Article (147)
Whoever commits any of the following violations shall be punished by imprisonment for a term not exceeding two (2) years and a fine of not less than five hundred thousand (500,000) Dirhams and not exceeding five million (5,000,000) Dirhams, or by either of these two punishments:
1) Provides incorrect or incomplete facts, information, or data in any statements or documents presented to the Central Bank.
2) Conceals any facts from the statements, information, minutes, papers, or other documents submitted to the Central Bank or to its representatives, employees, and auditors.
3) Destroys, mutilates or alters any document relating to a matter, which is the subject of an investigation by the Central Bank or sends, or causes to be sent out of the State such a document.
4) Obstructs, resists, or causes the delay of the conduct of an investigation by the Central Bank or the furnishing of information to the Central Bank.
5) Acts complicitly with another Person to commit any of the acts referred to in items (1) to (4) of this article.
Article (148)
Whoever intentionally discloses the confidential banking and credit information referred to in Article (120) of this Decretal Law shall be punished by imprisonment and a fine of not less than one hundred thousand (100,000) Dirhams and not exceeding five hundred thousand (500,000) Dirhams.
Article (149)
1) Where a violation was committed by a juridical Person, the official in charge of management shall be punished by the same penalties prescribed for actions committed in violation of the provisions of this decretal law, whenever his knowledge of the violation was established, or if the violation was a result of his negligence or failure to perform his duties.
2) The juridical Person shall be jointly liable with the official in charge of actual management with respect to the imposed financial fines and compensation, in case the violation was committed, in the name of the juridical person and on its behalf, by one of its employees.
Article (150)
Whoever commits any of the violations relating to Financial Infrastructure Systems referred to in Article (130) of this Decretal Law shall be punished by imprisonment and a fine of not less than one hundred thousand (100,000) Dirhams and not exceeding ten million (10,000,000) Dirhams, or by either of these two punishments.
Part VII – General Provisions –
Article (151): Scope of Application of the Decretal Law
The provisions of this Decretal Law apply to the Central Bank, financial institutions, financial activities, and Persons subject to it; and does not apply to the Financial Free Zones and the financial institutions regulated by the authorities of these zones.
Article (152): Enforceability of Applicable Regulations
Current regulations, decisions and circulars, issued in accordance with the provisions of Federal Law No (10) of 1980, Regarding the Central Bank, the Monetary System and Organization of Banking, and amendments thereto, and Federal Law No (6) of 1985, Regarding Islamic Banks, Financial Institutions and Investment Companies shall remain in force, until regulations, decisions and circulars are issued in replacement thereof, within a period not exceeding three (3) years from the date this Decretal Law comes into force.
Article (153): Reconciliation of Positions
All agencies and persons subject to the provisions of this Decretal Law shall reconcile their respective positions with its provisions, within the period determined by the Board of Directors.
Article (154): Annulment of Conflicting Provisions
Any provision contravening or conflicting with the provisions of this Decretal Law shall be annulled; and Federal Law No (10) of 1980 Regarding the Central Bank, The Monetary System and Organization of Banking, along with Federal Law No (6) of 1985, Regarding Islamic Banks, Financial Institutions and Investment companies shall be annulled.
Article (155): Fees and Charges
The Central Bank may impose fees and charges for providing the service, issuing licenses and authorizations, as deemed appropriate, in accordance with the nature and scope of functions, activities, and controls determined by the Board of Directors. A decision to such effect shall be issued by the Board of Directors and shall be published in the Official Gazette and the Central Bank’s official website.
Article (156): Enforceability of Judgments of Foreign Judicial Authorities
Judgments and decisions issued by foreign judicial and law enforcement authorities in respect of national Licensed Financial Institutions and branches of foreign Licensed Financial Institutions operating in the State shall apply, in accordance with applicable legal proceedings of effective laws in the State.
Article (157): Interpretation of the Technical Terms Referred to in this Decretal Law
1) If there is a reference in any legislation in force in the country to the “UAE dirham”, “currency”, “cash”, “money”, or any similar term, this includes digital currency in accordance with the provisions of this decree law unless the context requires otherwise.
2) Virtual assets as defined in the applicable laws in the Country, shall not be considered as Currency according to this decree law. Where virtual assets and currencies are used as a means or tool for payment or exchange, any regulations, rules and controls issued by the Central Bank in this regard shall be followed
3) The Central Bank may issue a glossary interpreting the technical terms referred to in this decretal law. This glossary shall be published on its official website.
This article has been amended by Decretal Federal Law No. (54) of 2023. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 01/11/2023)The Central Bank may issue a glossary interpreting the technical terms referred to in this decretal law. This glossary shall be published on its official website.
Article (158): Decretal Law Publication and Application
This decretal law shall be published in the Official Gazette, and shall come into force on the day following date of its publication, without prejudice to the provisions of Article (152) hereof.
AML/CFT
Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations Laws
Decree Federal Law No. (20) of 2018 on Anti-money Laundering and Combating the Financing of Terrorism and Illegal Organisations
DFL 20/2018 Effective from 23/10/2018The Decree Federal Law No. (20) of 2018 on Anti-money Laundering and Combating the Financing of Terrorism and Illegal Organisations has been amended by Federal Decree-Law No. (26) of 2021 and Federal Law by Decree No. (7) of 2024 respectively, You are viewing the latest version. Please find the PDFs of versions on the table below.Version 2 (consolidated as of 13/09/2021) Version 1 (effective from 23/10/2018) Article (1)
In application of the provisions of the present Decree-Law, the following terms and expressions shall have the following meanings assigned to them unless the context requires otherwise:
State: United Arab Emirates
Ministry: Ministry of Finance
Minister: Minister of Finance
Central Bank: Central Bank of the UAE
Governor. Governor of Central Bank
Committee: National Committee for Combating Money Laundering and the Financing of Terrorism and Illegal Organizations
Unit: Financial intelligence Unit
Supervisory Authority: Federal and local authorities which are entrusted by legislation to supervise financial institutions, designated non-financial businesses professions, Virtual Asset Service Providers and non-profit organizations or the competent authority in charge of approving the pursuit of an activity or a profession in case a supervisory authority is not assigned by legislations.
Law-enforcement Authorities: Federal and local authorities which are entrusted under applicable legislation to combat, search, investigate and collect evidences on the crimes including AML/CFT crimes and financing illegal organizations.
Competent Authorities: The competent government authorities in the State entrusted with the implementation of any provision of this Decree Law.
Predicate Offence: Any act constituting a felony or misdemeanor under the applicable laws of the State whether this act is committed Inside or outside the State when such act is punishable In both countries.
Money Laundering: Any of the acts mentioned in Clause (1) of Article (2) of the present Decree-Law.
Financing of Terrorism: Any of the acts mentioned in Articles (29, 30) of Federal Law no. (7) of 2014.
Illegal Organizations: Organizations whose establishment is criminalized or which exercise a criminalized activity.
Financing Illegal Organizations: Any physical or legal action aiming at providing funding to an illegal organization, or any of its activities or its members.
Crime: Money laundering crime and related predicate offences, or financing of terrorism or Illegal organizations.
Funds: Assets, whatever the method of acquisition, type and form, tangible or intangible, movable or Immovable, electronic, digital or encrypted, Including local and foreign currencies, legal documents and instruments of whatever form, including electronic or digital form that proves ownership of such assets, shares or related rights and economic resources that are assets of any kind, including natural resources, as well as bank credits, cheaques, payment orders, shares, securities, bonds, bills of exchange, letters of credit, and any interest, profits or other incomes derived or resulting from these assets, and can be used to obtain any financing or goods or services.
Virtual Assets: A digital representation of the value that can be digitally traded or transferred, and can be used for payment or investment purposes, and otherwise, as specified in the Executive Regulation of this Decree-Law.
Proceeds: Funds generated directly or Indirectly from the commitment of any felony or misdemeanor including profits, privileges, and economic interests, or any similar funds converted wholly or partly into other funds.
Means: Any means used or intended to be used to commit a felony or misdemeanor.
Suspicious Transactions: Transactions related to funds for which there are reasonable grounds to believe that they are earned from any felony or misdemeanor or related to the financing of terrorism or of Illegal organizations, whether committed or attempted.
Freezing or seizure: Temporary attachment over the moving, conversion, transfer, replacement or disposition of funds in any form, by an order issued by a competent authority.
Confiscation: Permanent expropriation of private funds or proceeds or instrumentalities by a ruling issued by a competent court.
Financial Institutions: Anyone who conducts one or several of the financial activities or transactions defined In the Executive Regulation of the present Decree Law for the account of /or on behalf of a client.
Designated Nonfinancial Businesses and Professions: Anyone who conducts one or several of the commercial or professional activities defined in the Executive Regulation of this Decree Law.
Non-Profit Organizations: Any organized group, of a continuing nature set for a temporary or permanent time period, comprising natural or legal persons or not for profit legal arrangements for the purpose of collecting, receiving or disbursing funds for charitable, religious, cultural, educational, social, communal or any other charitable activities.
Legal Arrangement: A relationship established by means of a contract between two or more parties, including but not limited to trust funds or other similar arrangements.
Client: Any person involved in or attempts to carry out any of the activities specified in the Executive Regulations of this Decree Law with one of the financial institutions or designated nonfinancial businesses and professions or Virtual Asset Service Providers
Beneficial Owner: The natural person who owns or exercises effective ultimate control over the client or the natural person on whose behalf a transaction is being conducted or, the natural person who exercises effective ultimate control over a legal person or legal arrangement, whether directly or through a chain of ownership, control or other indirect means.
Virtual asset service providers: Any natural or legal person, who practices any activity of commercial business, conducts one or more of the activities of virtual assets specified in the Executive Regulation of this Decree-Law, or the operations related there to for the benefit or on behalf of another natural or legal person.
Transaction: All disposal or use of Funds or proceeds including for example: deposits, withdrawals, transfer, sale, purchase, lending, swap, mortgage, and donation.
Registrar: The entity in charge of supervising the register of commercial names for all types of establishments registered In the State.
Customer Due Diligance (CDD): The process of identifying or verifying the Information of a Client or Beneficial owner, whether a natural, legal person or a legal arrangement, the nature of its activity, the purpose of the business relationship, the ownership structure, control over it for the purpose of this Decree-Law and its Executive Regulation.
Controlled Delivery: The process by which a competent authority allows the entering or transferring of illegal or suspicious funds or crime revenues to and from the State for the purpose of Investigating a crime or identifying the identity of Its perpetrators.
Undercover Operation: The process of search and Investigation conducted by one of the judicial impoundment officer by impersonating or playing a disguised or false role in order to obtain evidence or information related to the Crime.
This article has been amended by Federal Decree-Law No. (26) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 23/10/2018 to 13/09/2021)In application of the provisions of the present Decree law, the following terms and expressions shall have the following meanings assigned to them unless the context requires otherwise:
- State: United Arab Emirates.
- Ministry: Ministry of Finance.
- Minister: Minister of Finance.
- Central Bank: Central Bank of the UAE.
- Governor: Governor of Central Bank.
- Committee: National Committee for Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations.
- FIU: Financial Intelligence Unit.
- Supervisory Authority: Federal and local authorities which are entrusted by legislation to supervise Financial Institutions, Designated Non-Financial Businesses and Professions and Non-Profit Organisations or the Competent Authority in charge of approving the pursuit of an activity or a profession in case a supervisory authority is not assigned by legislations.
- Law-Enforcement Authorities: Federal and local authorities, which are entrusted under applicable legislation to combat, search, investigate and collect evidences on the crimes including ML/FT and financing illegal organisations crimes.
- Competent Authorities: The competent government authorities in the State entrusted with the implementation of any provision of this Decree law.
- Predicate Offence: Any act constituting a felony or misdemeanour under the applicable laws of the State whether this act is committed inside or outside the State when such act is punishable in both countries.
- Money Laundering: Any of the acts mentioned in Clause (1) of Article (2) of the present Decree law.
- Financing of Terrorism: Any of the acts mentioned in Articles (29 and 30) of Federal Law no. (7) of 2014.
- Illegal Organisations: Organisations whose establishment is criminalized or which pursue a criminalized activity.
- Financing Illegal Organisations: Any physical or legal action aiming at providing funding to an illegal organisation, or any of its activities or its members.
- Crime: Money laundering crime and related predicate offences, or financing of terrorism or financing of illegal organisations.
- Funds: Assets in whatever form, whether tangible or intangible, movable or immovable including national currency, foreign currencies, documents or notes evidencing the ownership of those assets or associated rights in any form including electronic or digital forms or any interests, profits or income originating or earned from these assets.
- Proceeds: Funds generated directly or indirectly from the commitment of any felony or misdemeanour including profits, privileges, and economic interests, or any similar funds converted wholly or partly into other funds.
- Instrumentalities: Any item used or intended to be used in any way to commit a felony or misdemeanour.
- Suspicious Transactions: Transactions related to funds for which there are reasonable grounds to suspect that they are earned from any felony or misdemeanour, related to the financing of terrorism or of illegal organisations, whether committed or attempted.
- Freezing or seizure: Temporary restriction over the moving, conversion, transfer, replacement or disposition of funds in any form, by an order issued by a Competent Authority.
- Confiscation: Permanent expropriation of private funds or proceeds or instrumentalities by an injunction issued by a competent court.
- Financial institutions: Anyone who conducts one or several of the activities or operations defined in the Executive Regulation of the present Decree law for the account of /or on behalf of a customer.
- Designated Nonfinancial Businesses and Professions: Anyone who conducts one or several of the commercial or professional activities defined in the Executive Regulation of this Decree Law.
- Non-Profit Organisations: Any organized group, of a continuing nature set for a temporary or permanent time period, comprising natural or legal persons or not for profit legal arrangements for the purpose of collecting, receiving or disbursing funds for charitable, religious, cultural, educational, social, communal or any other charitable activities.
- Legal Arrangement: A relationship established by means of a contract between two or more parties which does not result in the creation of a legal personality such as trust or other similar arrangements.
- Customer: Anyone involved in or attempts to carry out any of the activities specified in the Executive Regulations of this Decree Law with one of the Financial Institutions or Designated Nonfinancial Businesses and Professions.
- Beneficial Owner: The natural person who owns or exercises effective ultimate control, directly or indirectly over a Customer, or the natural person on whose behalf a Transaction is being conducted or, the natural person who exercises effective ultimate control over a legal person or Legal Arrangement
- Transaction: All disposal or use of Funds or proceeds including for example: deposits, withdrawals, conversion or transfer, sales, purchases, lending, swap, mortgage, and donation.
- Registrar: The entity in charge of supervising the register of commercial names for all types of establishments registered in the State.
- Customer Due Diligence (CDD): The process of identifying or verifying the information of a Customer or Beneficial Owner, whether a natural or legal person or a legal arrangement, and the nature of its activity and the purpose of the business relationship and the ownership structure and control over it for the purpose of this Decree Law and its Executive Regulation.
- Controlled Delivery: The process by which a Competent Authority allows under its supervision the entering or transferring of illegal or suspicious funds or Crime revenues to and from the UAE for the purpose of investigating a Crime or identifying the identity of its perpetrators.
- Undercover Operation: The process of search and investigation conducted by one of the judicial impoundment officers by impersonating or playing a disguised or false role in order to obtain evidence or information related to a crime.
Article (2)
- Any person, having the knowledge that the funds are the proceeds of a felony or a misdemeanour, and who wilfully commits any of the following acts, shall be considered a perpetrator of the crime of Money Laundering:
- Transferring or moving proceeds or conducting any transaction with the aim of concealing or disguising their Illegal source.
- Concealing or disguising the true nature, source or location of the proceeds as well as the method involving their disposition, movement, ownership of or rights with respect to said proceeds.
- Acquiring, possessing or using proceeds upon receipt
- Assisting the perpetrator of the predicate offense to escape punishment
- Transferring or moving proceeds or conducting any transaction with the aim of concealing or disguising their Illegal source.
- The crime of Money Laundering is considered as an independent crime. The punishment of the perpetrator for the predicate offence shall not prevent his punishment for the crime of Money Laundering
- Proving the illicit source of the proceeds should not constitute a prerequisite to sentencing the perpetrator of the predicate offence
This article has been amended by Federal Decree-Law No. (26) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 23/10/2018 to 13/09/2021)1- Any person, having the knowledge that the Funds are the proceeds of a felony or a misdemeanour, and who wilfully commits any of the following acts, shall be considered a perpetrator of the crime of Money Laundering:
a- Transferring or moving Proceeds or conducting any transaction with the aim of concealing or disguising their illegal source.
b- Concealing or disguising the true nature, source or location of the Proceeds as well as the method involving their disposition, movement, ownership of or rights with respect to said Proceeds.
c- Acquiring, possessing or using Proceeds upon receipt.
d- Assisting the perpetrator of the Predicate Offence to escape punishment.
2- The crime of Money Laundering is considered as an independent crime. The punishment of the perpetrator for the Predicate Offence shall not prevent his punishment for the crime of Money Laundering.
3- A conviction with a Predicate Offence shall not be deemed as a condition to prove the illicit source of the Proceeds.
- Any person, having the knowledge that the funds are the proceeds of a felony or a misdemeanour, and who wilfully commits any of the following acts, shall be considered a perpetrator of the crime of Money Laundering:
Article (3)
Without prejudice to the provisions of Federal Law No. (3) of 1987 referred to herein, and Federal Law No. (7) of 2014 referred to herein:
1- The crime of Financing Terrorism shall be committed by whoever intentionally commits any of the following:
a- Any of the acts specified in Clause (1) of Article (2) of the present Decree Law, if he is aware that the Proceeds are wholly or partly owned by a terrorist organisation or terrorist person or intended to finance a terrorist organisation, a terrorist person or a terrorism crime, even if it without the intention to conceal or disguise their illegal source.
b- Providing, collecting, preparing or obtaining Proceeds or facilitating their obtainment by others with intent to use them, or while knowing that such Proceeds will be used in whole or in part for the commitment of a terrorist offence, or if he has committed such acts on behalf of a terrorist organisation or a terrorist person while aware of their true background or purpose.
2- A person shall be guilty of financing illegal Organisations crime if he intentionally commits any of the following:
a- Any of the acts specified in Clause (1) of Article (2) of this Decree Law, if he is aware that the Proceeds are wholly or partly owned by an Illegal Organisation or by any person belonging to an Illegal Organisation or intended to finance such Illegal Organisation or any person belonging to it, even if it without the intention to conceal or disguise their illicit origin.
b- Providing, collecting, preparing, obtaining Proceeds or facilitating their obtainment by others with intent to use such Proceeds, or while knowing that such Proceeds will be used in whole or in part for the benefit of an Illegal Organisation or of any of its members, with knowledge of their true identity or purpose.
Article (4)
The legal person shall be criminally responsible for the Crime if it is committed in its name or for its account intentionally, without prejudice to the personal criminal responsibility of the perpetrator and the administrative penalties as prescribed by law.
Article (5)
1- The Governor or his delegate shall have the right to freeze suspicious Funds deposited at financial institutions for no more than (7) seven working days, in accordance with the rules and controls stipulated in the Executive Regulation of the present Decree Law and it may be, renewed by order of the public prosecutor or his delegate.
2- The public prosecution and the competent court, as the case may be, shall request the identification, tracking, or evaluation of suspicious Funds, Proceeds and Instrumentalities or of whatever is of equivalent value or seizing or freezing them if they are the result of, or in connection with, the Crime without pre-advising the owner and issuing a travel ban until the investigation or trial is completed.
3- The public prosecution and the competent court, as the case may be and when necessary, shall take the necessary decision to prohibit trading or disposing of such Funds, Proceeds and Instrumentalities and take the necessary actions to prevent any act aiming at evading related freezing or seizing orders, without prejudice to the rights of bona fide third parties.
4- All freezing orders of funds held by financial institutions licensed by the Central Bank may be only be executed through the Central Bank.
5- Any grievance against the public prosecution's decision to freeze or seize in accordance with the provisions of the present Article shall be filed before the competent court in whose jurisdiction the public prosecution issuing the decision is located. If the grievance is rejected, a new one may be lodged only after the expiry of three months from the date of rejection of the previous one, unless there is a serious reason to do so before the expiry of that period.
6- The grievance shall be filed by submitting a report to the competent court. The president of the court shall set a date to review the report and notify the plaintiff of the date. The public prosecution shall submit a memorandum expressing its opinion on the grievance. The court shall issue its decision on this grievance within no more than (14) fourteen business days from the date of its submission.
7- The public prosecution and the competent court, as the case may be, shall appoint whomever they find suitable to manage the Funds, Proceeds and Instrumentalities seized, frozen or subject to confiscation, also allowing selling or disposing it, even before the issuance of a court decision if needed. The proceeds of the sale shall be transferred to the UAE treasury in case of a final judgment of conviction. These Funds shall be earmarked to any rights awarded legally to any party acting in good faith, proportionately to its value.
8- The Executive Regulation of the present Decree Law shall define the rules and procedures for implementing the dispositions of the present Article.
Article (6)
- Without prejudice to the provisions of Article (5) of this Decree-Law, no criminal proceedings shall be Instituted against the perpetrator of money laundering, financing terrorism, or financing of illegal organizations in accordance with the provisions of this Decree-Law except by the public prosecutor or his delegate
- The Public prosecutor or his delegate and the competent court as the case may be shall issue a decision to take the necessary procedures to protect the intelligence Information and the means and methods of obtaining such information or Instruct the competent authorities to protect the witnesses, or the undisclosed sources, the accused or other parties involved in the case if there is a serious threat to their safety.
This article has been amended by Federal Decree-Law No. (26) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 23/10/2018 to 13/09/2021)1- Without prejudice to the provisions of Article (5) of this Decree Law, no criminal proceedings shall be instituted against the perpetrator of Money Laundering or Financing of Terrorism, or Financing of Illegal Organisations in accordance with the provisions of this Decree Law except by the Attorney General or his delegate.
2- The Attorney General or his delegate and the competent court as the case may be, shall issue a decision to take the necessary procedures to protect the intelligence information and the means and methods of obtaining such information or instruct the competent authorities to protect the witnesses, or the undisclosed sources, the accused or other parties involved in the case if there is a serious threat to their safety.
Article (7)
1- The public prosecution may, sua sponte or upon the request of the Law Enforcement Authorities, should there be sufficient evidence of the occurrence of the Crime, request direct access to accounts, records and documents held by third parties and request access to the stored data in the computer system and information technology programs, memorandums, correspondences and packages, identify track and seize the Funds, monitor the accounts, issue travel bans and other procedures aiding in uncovering the Crime and its perpetrators without prejudice to the legislations applicable in the UAE.
2- The Law Enforcement Authorities may conduct undercover operations and adopt other investigative methods and initiate the controlled delivery operation aimed at detecting the Crime or its evidence or identifying the source and destination of the Funds, Proceeds or Instrumentalities or arresting the perpetrators without prejudice to the legislation applicable in the UAE.
3- Any person involved in an undercover operation or a controlled delivery operation by Law Enforcement Authorities shall not be held criminally responsible unless such person has instigated the perpetration of the Crime or exceeded the powers granted to him.
4- The Competent Authorities in the UAE shall keep comprehensive statistics on the reports of Suspicious Transactions, investigations and Crime-related judgments, seized, frozen or confiscated funds, international cooperation requests and any statistics related to the efficiency and sufficiency of Crime combating procedures.
Article (8)
Any person shall declare whenever he brings into the UAE or take out any currency or bearer negotiable instruments or precious metals or stones of value, in accordance with the declaration system issued by the Central Bank.
Article (9)
Central Bank of the UAE shall establish an independent “Financial Intelligence Unit” to which suspicious transaction reports, Information on all financial institutions and designated nonfinancial businesses and professions Virtual Asset Service Providers shall be sent exclusively for consideration, analysis, and referral to the competent authorities, either automatically or upon request The Financial Intelligence Unit shall have competence over the following:
- Requesting financial Institutions and designated nonfinancial businesses and professions. Virtual Assets Service Providers and the competent authorities to submit any information or further documentation related to received reports and information and other information deemed necessary for Financial intelligence Unit to perform its duties on schedule and in the form determined by the Unit.
- Exchanging information with its counterparts in other countries, with respect to Suspicious Transactions Reports or any other information to which the Financial Intelligence Unit has exclusive access or is the exclusive recipient, whether directly or Indirectly, according to international agreements to which the State is a party or bilateral agreements signed by the Financial Intelligence Unit with its counterparts governing bilateral cooperation or conditional upon reciprocity, the financial intelligence unit may communicate to its counterparts its findings derived from the use of the information provided by its counterparts and the results of the analysis conducted based on this information. Such Information shall be used only for the purposes of combating the crime and shall not be disclosed to third parties without the Financial Intelligence Unit’s permission.
- Establishing a database or a special register to record all available information and to implement data privacy and data security procedures to protect this information including procedures for handling, archiving transferring and accessing the data, and make sure that access to its premises, its database and its technology systems is restricted.
- Any other competencies to be specified in the Executive Regulation attached to the present Decree-Law.
This article has been amended by Federal Decree-Law No. (26) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 23/10/2018 to 13/09/2021)An independent “Financial Intelligence Unit” shall be established in the Central Bank, to which Suspicious Transaction reports and related information from all Financial Institutions and Designated Nonfinancial Businesses and Professions shall be sent exclusively for consideration and analysis and referral to the competent authorities, spontaneously or upon request. The FIU shall have competence over the following:
1- Requesting Financial Institutions and Designated Nonfinancial Businesses and Professions and the competent authorities to submit any information or additional documentation related to received reports and information, and other information deemed necessary for the FIU to perform its duties, on schedule and in the form determined by the Unit.
2- Exchanging information with its counterparts in other countries, with respect to Suspicious Transactions Reports or any other information to which the FIU has access or is the recipient, whether directly or indirectly, according to international agreements to which the State is a party or bilateral agreements signed by the FIU with its counterparts governing bilateral cooperation or conditional upon reciprocity. The FIU may communicate to its counterparts its findings derived from the use of the information provided by its counterparts and the results of the analysis conducted based on this information. Such information shall be used only for the purposes of combating the Crime and shall not be disclosed to third parties without the FIU’s permission.
3- Establishing a database or a special register to record all available information and to implement data privacy and data security procedures to protect this information including procedures for handling, archiving and transferring and make sure that access to its premises, its database and its technology systems is restricted.
4- Any other competences to be specified in the Executive Regulation to the present Decree Law.
- Requesting financial Institutions and designated nonfinancial businesses and professions. Virtual Assets Service Providers and the competent authorities to submit any information or further documentation related to received reports and information and other information deemed necessary for Financial intelligence Unit to perform its duties on schedule and in the form determined by the Unit.
Article (10)
1- The public prosecution may seek the opinion of the FIU about incoming reports it receives related to cases of Money Laundering, Financing of Terrorism and of Illegal Organisations.
2- Law Enforcement Authorities shall be responsible for receiving and following-up on suspicious transactions reports received from the FIU and gathering related evidence.
3- Law Enforcement Authorities may obtain the information that it deems necessary to perform its duties from the relevant authorities as stipulated under the Executive Regulation of the present Decree Law.
Article (11)
A committee chaired by the Governor, called "National Committee for Anti-Money Laundering and Combating the Financing of Terrorism and Financing of Illegal Organisations", shall be established by virtue of the provisions of this Decree Law. A decision on the formation of the Committee shall be issued by the Minister.
Article (12)
The Committee shall have the following competences:
- Preparing and developing a national strategy to combat crime and proposing related regulations, policies and procedures in coordination with the competent authorities, and monitoring their implementation.
- Determining and assessing the risks of the crime on the national level.
- Coordinating with the relevant authorities and referring to related international sources of information in order to identify high-risk countries in addition to the countries that their combat systems in relation to money laundering and financing of terrorism are weak, Moreover, to identify the necessary countermeasures to be taken and other measures commensurate with the degree of risk, and instructing the supervisory authorities to ensure the adherence to the required due diligence procedures by financial institutions, designated nonfinancial businesses and professions, virtual asset service providers and non-profit organizations which are under their supervision in order to implement the said measures.
- Facilitating the exchange of information and coordination among the various bodies represented therein.
- Collecting and analyzing statistics and other information provided by the Competent Authorities to assess the effectiveness of their Regulations on combating Money laundering. Terrorism financing and financing of illegal organizations.
- Representing the State in International forums related to AML/CTF.
- Proposing the Regulation covering the work of the Committee, and submitting it to the Minister for approval.
- Any other matters referred to the Committee by Competent Authorities in the State.
This article has been amended by Federal Decree-Law No. (26) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 23/10/2018 to 13/09/2021)The Committee shall have the following competences:
1- Preparing and developing a national strategy to combat Crime and proposing related regulations, policies and procedures in coordination with the competent authorities, and monitoring their implementation.
2- Determining and assessing the risks of the Crime on the national level.
3- Coordinating with the relevant authorities and referring to related international sources of information in order to identify high-risk countries in relation to Money Laundering and Financing of Terrorism and instructing the supervisory authorities to ensure the adherence to the required due diligence procedures by Financial Institutions, Designated Nonfinancial Businesses and Professions, and non-profit organisations which are under their supervision.
4- Facilitating the exchange of information and coordination among the various bodies represented therein.
5- Assess the effectiveness of the system on combating Money Laundering, Terrorism Financing and Financing of Illegal Organisations based on collecting and analysing statistics and other information provided by the Competent Authorities.
6- Representing the State in international forums related to Anti-Money Laundering and combating Financing of Terrorism.
7- Proposing the Executive Regulation covering the work of the Committee, and submitting it to the Minister for approval.
8- Any other matters referred to the Committee by Competent Authorities in the UAE.
- Preparing and developing a national strategy to combat crime and proposing related regulations, policies and procedures in coordination with the competent authorities, and monitoring their implementation.
Article (13)
The Supervisory Authorities shall, each within the scope of its competence, carry out supervision, monitoring and follow up to ensure compliance with the provisions provided for in the present Decree-Law and its executive regulation, regulatory decisions in addition to any other related decisions and shall have in particular, the following competences
- Conduct a risk assessment on the likelihood of the perpetration of a Crime within the financial institutions, designated nonfinancial businesses and professions, and activities of virtual assets and activities of virtual asset service providers and non-profit organizations
- Conduct Control and audit inspections over financial institutions, designated nonfinancial businesses and professions, virtual assets service providers and non-profit organizations, both remotely and on site.
- Issue the decisions related to the administrative penalties in accordance with the provisions of this Decree-Law and its Executive Regulation, the grievance mechanism, and keep statistics of measures taken and penalties Imposed.
- Any other competencies stipulated in the Executive Regulation of the present Decree-Law
This article has been amended by Federal Decree-Law No. (26) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 23/10/2018 to 13/09/2021)The Supervisory Authorities shall, each within the scope of its competence, carry out supervision, monitoring and follow up to ensure compliance with the provisions provided for in the present Decree Law and its Executive Regulation and shall have in particular, the following competences:
1- Conduct a risk assessment on the likelihood of the perpetration of a Crime within the Financial Institutions, Designated Nonfinancial Businesses and Professions and Non-Profit Organisations.
2- Conduct supervision and examination over financial institutions, designated nonfinancial businesses and professions and non-profit organisations, both off-site and on-site.
3- Issue the decisions related to the administrative penalties in accordance with the provisions of this Decree Law and its Executive Regulation, the grievance mechanism, and keep statistics of measures taken and penalties imposed.
4- Any other specialized activities stipulated in the Executive Regulation of the present Decree Law.
- Conduct a risk assessment on the likelihood of the perpetration of a Crime within the financial institutions, designated nonfinancial businesses and professions, and activities of virtual assets and activities of virtual asset service providers and non-profit organizations
Article (14)
- Without prejudice to any more severe administrative penalty provided by any other legislation, the Supervisory authority shall impose the following administrative penalties on the financial institutions, designated nonfinancial businesses and professions, and virtual assets service providers and non-profit organizations in case they violate the present Decree-Law and its Executive Regulation or regulatory decisions in addition to any other related decisions:
- Warning
- Administrative fine of no less than AED 50,000 (fifty thousand dirham) and no more than AED 5,000,000 (five million dirham) for each violation.
- Banning the violator from working in the sector related to the violation for the period determined by the supervisory authority.
- Constraining the powers of the Board members, supervisory or executive management members, managers or owners who are proven to be responsible of the violation Including the appointment of temporary supervisor.
- Arresting Managers, board members and supervisory and executive management members who are proven to be responsible of the violation for a period to be determined by the Supervisory Authority or request their removal.
- Arrest or restrict the activity or the profession for a period to be determined by the supervisory authority
- Cancel the License.
- Warning
- Except for paragraph (g) of Clause (1) of this Article, The Supervisory Authority may upon imposing the administrative penalties, request regular reports on the measures taken to correct the violation.
- In any case, the Supervisory Authority shall publish the administrative penalties through various means of publication.
This article has been amended by Federal Decree-Law No. (26) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 23/10/2018 to 13/09/2021)1- The Supervisory Authority shall impose the following administrative penalties on the Financial Institutions, Designated Nonfinancial Businesses and Professions and Non-Profit Organisations in case they violate the present Decree Law and its Executive Regulation:
a) Warning
b) Administrative fines of no less than AED 50,000 (fifty thousand dirham) and no more than AED 5,000,000 (five million dirham) for each violation.
c) Banning the violator from working in the sector related to the violation for the period determined by the supervisory authority.
d) Restricting the powers of the Board members, supervisory or executive management members, managers or owners who are proven to be responsible of the violation including the appointment of temporary inspector.
e) Suspending managers, board members and supervisory and executive management members who are proven to be responsible of the violation for a period to be determined by the Supervisory Authority or request their removal.
f) Suspending or restricting the practice of the activity or the profession for a period to be determined by the supervisory authority
g) Cancelling the License.
2- Except for paragraph (g) of Clause (1) of this Article, The Supervisory Authority may upon imposing the administrative penalties, request regular reports on the measures taken to correct the violation.
3- In any case, the Supervisory Authority shall publish the administrative penalties through various means of publication.
- Without prejudice to any more severe administrative penalty provided by any other legislation, the Supervisory authority shall impose the following administrative penalties on the financial institutions, designated nonfinancial businesses and professions, and virtual assets service providers and non-profit organizations in case they violate the present Decree-Law and its Executive Regulation or regulatory decisions in addition to any other related decisions:
Article (15)
The Financial institutions and designated nonfinancial businesses and professions in addition to the virtual assets service providers shall, upon suspicion or if they have reasonable grounds to suspect a transaction or funds representing all or some proceeds, or suspicion of their relationship to the Crime or that they will be used regardless of their value, to inform the Unit without delay, directly and provide the Unit with a detailed report Including all the data and information available regarding that transaction and the parties involved, and to provide any additional Information required by the Unit, with no right to object under the confidentiality provisions.
However, Lawyers, notaries, other legal professionals and independent legal auditors shall be exempted from this provision if the information related to these operations have been obtained subject to professional confidentiality
The Executive Regulation of the present Decree-Law shall determine the rules, controls and cases of the obligation to report suspicious transactions
This article has been amended by Federal Decree-Law No. (26) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 23/10/2018 to 13/09/2021)The Financial Institutions and Designated Nonfinancial Businesses and Professions shall, upon suspicion or if they have reasonable grounds to suspect a transaction or Funds representing all or some a Proceeds, or suspicion of their relationship to the Crime or that they will be used regardless of their value, to inform the FIU directly and without delay, and provide the FIU with a detailed report including all the data and information available regarding that transaction and the parties involved, and to provide any additional information required by the FIU, with no right to object under the confidentiality provisions. Lawyers, notaries, other legal professionals and independent legal auditors shall be exempted from this provision if the information related to these Transactions have been obtained subject to professional confidentiality. The Executive Regulation of the present Decree Law shall determine the rules, controls and cases of the obligation to report suspicious transactions.
Article (16)
1- Financial Institutions and Designated Nonfinancial Businesses and Professions shall:
a) Identify the Crime risks within its scope of work as well as continuously assess, document, and update such assessment based on the various risk factors established in the Executive Regulation of this Decree Law and maintain a risk identification and assessment analysis with its supporting data to be provided to the Supervisory Authority upon request.
b) Take the necessary due diligence measures and procedures and define their scope, taking into account the various risk factors and the results of the national risk assessment and retain the records received during the implementation of this process. The Executive Regulation of the present Decree Law shall specify the cases in which such procedures and measures are applied, and the conditions for deferring the completion of a Customer or a Beneficial Owner identity verification.
c) Refrain from opening or conducting any financial or commercial transaction under an anonymous or fictitious name or by pseudonym or number, and maintaining a relationship or providing any services to it.
d) Develop internal policies, controls and procedures approved by senior management to enable them to manage the risks identified and mitigate them, and to review and update them continuously, and apply this to all subsidiaries and affiliates in which they hold a majority stake; the Executive Regulations of this Decree Law shall specify what should be included in said policies, controls and procedures.
e) Immediate implementation of the directives issued by the Competent Authorities in the State for implementing the resolutions issued by the United Nations Security Council under Chapter (7) of UN Charter for the Prohibition and Suppression of the Financing of Terrorism, and Proliferation of weapons of mass destruction and their financing, and other related directives.
f) Maintain all records, documents, and data for all transactions, whether local or international, and make this information available to the competent authorities promptly upon request, as stipulated in the Executive Regulation of this Decree Law.
g) Any other obligations stipulated in the Executive Regulation of this Decree Law.
2- For the purposes of this Decree Law, the Executive Regulation of this Decree Law shall regulates the following:
a) The obligations of Non-Profit Organisations.
b) Retaining information and records by the registrar, to be provided upon request and taking procedures for access by the public.
c) Retaining information and records by the legal person and legal arrangement, and making it available upon request.
Article (16) bis*
1. Any natural or legal person may not engage in the activities of virtual assets service providers or any of the financial activities without a license, registration or registration, as the case may be, from the competent supervisory authorities.
2. For the purposes of this Decree-Law, the Executive Regulations shall regulate the obligations of virtual assets service providers.
*Article (16) bis has been added by Federal Decree-Law No. (26) of 2021.
Article (17)
All authorities shall abide by the confidentiality of the information obtained in relation to suspicious transaction or the crimes provided for in this Decree-Law, and such information may not be disclosed except to the extent necessary for use in investigations, prosecutions or cases in violation of the provisions of this Decree-Law.
This article has been amended by Federal Decree-Law No. (26) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 23/10/2018 to 13/09/2021)All entities shall abide by the confidentiality of the information obtained in relation to Suspicious Transaction or the Crimes provided for in this Decree Law, and not disclose them except to the extent necessary for use in investigations, prosecutions or cases in violation of the provisions of this Decree Law.
Article (18)
1- The competent judicial authority shall, upon request of a judicial authority of another country bound by an enforceable agreement with the State or by virtue of the reciprocity principle, provide judicial assistance in relation to investigation, court trials or procedures relevant to the Crime and issue orders as follows:
a) Identify, freeze, seize or confiscate any Funds, Proceeds, or Instrumentalities or their equivalent, generated from the Crime or used or intended to be used in the Crime or take any other procedures applicable under the enforceable legislation in the State, including, to provide records retained by Financial Institutions, or Designated Nonfinancial Businesses and Professions or Non-Profit Organisations, and to inspect persons and buildings, and to collect witnesses’ statements, gather evidence, and use investigative methods including undercover operations, intercepting communications, collecting electronic data and controlled delivery.
b)Handover and handback persons and items relevant to the Crime in a prompt manner in accordance with the legislations applicable in the State.
2- The Competent Authorities shall exchange information related to the Crime promptly with the foreign counterparts, respond to requests made by any competent entity in the foreign countries which are bound by an applicable convention with the State or in accordance with the reciprocity principle. The Competent Authorities shall gather information from the relevant authorities in the State and take the necessary action to ensure the confidentiality of the information and used it only for its intended purpose stated in the request for information and in accordance with applicable legislations in the State.
Article (19)
- Competent Authorities shall give priority to requests for international cooperation related to countering money laundering and combating terrorism financing and ensure prompt handling of those requests and take efficient measures to ensure the confidentiality of the information received
- In application of the present Decree-Law, the request for international cooperation shall not be rejected based on any of the following grounds:
- That the crime involves tax and financial affairs
- That the crime is political or related to politics.
- That the confidentiality provisions apply to financial Institutions and designated nonfinancial businesses and professions without prejudice to the legislations applicable in the State.
- That the request is connected to a crime under investigation or Judicial prosecution in the UAE unless the request win impede on the investigation or prosecution.
- Any other cases mentioned in the Executive Regulation hereof.
- That the crime involves tax and financial affairs
- The rules, controls and procedures governing international cooperation are contained in the Executive Regulation of this Decree-Law
This article has been amended by Federal Decree-Law No. (26) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 23/10/2018 to 13/09/2021)1- Competent Authorities shall give priority to requests for international cooperation related to Anti-Money Laundering and Combating Financing of Terrorism and ensure prompt execution of those requests and take efficient measures to ensure the confidentiality of the information received.
2- In application of the present Decree Law, the request for international cooperation shall not be rejected based on any of the following grounds:
a) That the Crime involves tax and financial affairs
b) That the Crime is political or related to politics.
c) That the confidentiality provisions apply to Financial Institutions and Designated Nonfinancial Businesses and professions without prejudice to the legislation applicable in the State.
d) That the request is connected to a Crime under investigation or judicial prosecution in the State unless the request will impede on the investigation or prosecution.
e) Any other cases mentioned in the Executive Regulation of this Decree Law.
3- The rules, controls and procedures governing international cooperation are contained in the Executive Regulation of this Decree Law.
- Competent Authorities shall give priority to requests for international cooperation related to countering money laundering and combating terrorism financing and ensure prompt handling of those requests and take efficient measures to ensure the confidentiality of the information received
Article (20)
Any court injunction or court decision providing for the confiscation of Funds, Proceeds or Instrumentalities relating to Money-Laundering, Financing of Terrorism or Financing Illegal Organisations may be recognised if issued by a court or judicial authority of another state with which the State has entered into a ratified convention.
Article (21)
The imposition of penalties provided for in this Decree Law shall not prejudice any harsher penalty provided for in any other law.
Article (22)
- Any person who commits or attempts to commit any of the acts set forth in Clause (1) of Article 2 of this Decree-Law shall be sentenced to imprisonment for a period not exceeding ten years and to a fine of no less than (100,000) AED one hundred thousand and not exceeding (5,000,000) AED five Million or either one of these two penalties.
- A temporary imprisonment and a fine of no less than AED 300,000 (three hundred thousand dirham) and no more than AED 10,000,000 (ten million dirham) shall be applied If the perpetrator of a money laundering crime commits any of the following acts:
- If he abuses his influence or the power granted to him by his profession or professional activities
- If the crime is committed through a non-profit organization
- If the crime is committed through an organized crime group
- In case of Recidivism
- An attempt to commit a money laundering offense shall be punishable by the full penalty prescribed for it
- A life imprisonment sanction or temporary imprisonment of no less than (10) ten years and penalty of no less than AED 300,000 (three hundred thousand dirham) and no more than AED 10,000,000 (ten million dirham) is applied to anyone who uses Proceeds for terrorist financing.
- A temporary imprisonment sanction and a penalty of no less than AED 300,000 (three hundred thousand dirham) and no more than AED 10,000,000 (ten million dirham) shall be applicable to anyone who uses the Proceeds in financing illegal organizations.
- The Court may at the request of the Attorney General, his delegate, or on its own initiative commute or exempt from the sentence imposed on the offenders if they provide the Judicial or administrative authorities with information relating to any of the offenses punishable in this article, when this leads to the disclosure, prosecution, arrest the perpetrators or seizure Its proceeds.
This article has been amended by Federal Decree-Law No. (26) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 23/10/2018 to 13/09/2021)1- Any person who commits any of the acts set forth in Clause (1) of Article (2) of this Decree Law shall be sentenced to imprisonment for a period not exceeding ten years and to a fine of no less than (100,000) one hundred thousand dirham and not exceeding (5,000,000) five million dirham or either one of these two penalties.
A temporary imprisonment and a fine of no less than (300,000) three hundred thousand dirham and no more than (10,000,000) ten million dirham shall be applied if the perpetrator commits Money Laundering Crime in any of the following situations:
a) If he abuses his influence or the power granted to him by his employment or professional activities.
b) If the Crime is committed through a Non-Profit Organisation.
c) If the Crime is committed through an organized crime group.
d) In case of recidivism
2- An attempt to commit a Money Laundering offense shall be punishable by the full penalty prescribed for it
3- A life imprisonment sanction or temporary imprisonment of no less than (10) ten years and penalty of no less than (300,000) three hundred thousand dirham and no more than (10,000,000) ten million dirham is applied to anyone who uses Proceeds for Financing of Terrorism.
4- A temporary imprisonment sanction and a penalty of no less than (300,000) three hundred thousand dirham and no more than (10,000,000) ten million dirham shall be applicable to anyone who uses the Proceeds in Financing Illegal Organisations.
5- The Court may commute or exempt from the sentence imposed on the offenders if they provide the judicial or administrative authorities with information relating to any of the offenses punishable in this Article, when this leads to the disclosure of the Crime or its perpetrators, or the verification of the Crime against them or arrest of any of the perpetrators.
- Any person who commits or attempts to commit any of the acts set forth in Clause (1) of Article 2 of this Decree-Law shall be sentenced to imprisonment for a period not exceeding ten years and to a fine of no less than (100,000) AED one hundred thousand and not exceeding (5,000,000) AED five Million or either one of these two penalties.
Article (23)
- A penalty of no less than AED 500,000 (five hundred thousand) and no more than AED 50,000,000 (fifty million dirham) shall apply to any legal person whose representatives or managers or agents commit for its account or its name any of the crimes mentioned In this Decree-Law
- If the legal person is convicted with terrorism financing crime or financing illegal organizations, the court will order its dissolution and closure of its offices where its activity is performed.
- Should a legal person is convicted of any of the crimes stipulated In Clause (1) of Article (2) or Article (8) of this Decree-Law, the court may prevent him from practicing his activity for a specified period, or cancel the license, restriction or registration to practice activity.
- Upon issuance of the indictment, the court shall order the publishing of a summary of the judgment by the appropriate means at the expense of condemned party
This article has been amended by Federal Decree-Law No. (26) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 23/10/2018 to 13/09/2021)1- A penalty of no less than (500,000) five hundred thousand dirham and no more than (50,000,000) fifty million dirham shall apply to any legal person whose representatives or managers or agents commit for its account or its name any of the Crimes mentioned in this Decree Law.
2- If the legal person is convicted with crime of Financing of Terrorism, the court shall order its dissolution and closure of its offices where its activity is performed.
3- Upon issuance of the indictment, the court shall order the publishing of a summary of the judgment by the appropriate means at the expense of condemned party.
- A penalty of no less than AED 500,000 (five hundred thousand) and no more than AED 50,000,000 (fifty million dirham) shall apply to any legal person whose representatives or managers or agents commit for its account or its name any of the crimes mentioned In this Decree-Law
Article (24)
Imprisonment and a fine of no less than (100,000) one hundred thousand dirham and no more than (1,000,000) one million dirham or any of those two sanctions is applied to anyone who violates on purpose or by gross negligence the provision of Article (15) of this Decree Law.
Article (25)
Imprisonment for no less than one year and a penalty of no less than AED 100,000 (one hundred thousand dirham) and no more than AED 500,000 (five hundred thousand dirham) or any of these two sanctions shall apply to anyone who notifies or warns a person or reveals any transaction under review in relation to suspicious transactions or being investigated by the Competent Authorities or to investigate them or any Information related to a violation of the provisions of Article (17) of this Decree-Law
Article (25) bis
Imprisonment for no less than (3) three months and a penalty of no less than AED 50,000 (fifty thousand dirham) or any of these two sanctions shall apply to whoever possesses, conceals or performs any operation of funds when there is sufficient evidence or presumption of the illegality of its source.
Upon conviction, the court shall rule for confiscation in accordance with the provisions of Article 26 of this Decree-Law.
This article has been amended by Federal Decree-Law No. (26) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 23/10/2018 to 13/09/2021)Imprisonment for no less than six months and a fine of no less than (100,000) one hundred thousand dirham and no more than (500,000) five hundred thousand dirham or any of these two sanctions shall apply to anyone who notifies or warns a person or reveals transaction under review in relation to Suspicious Transactions or being investigated by the Competent Authorities.
Article (26)
The court shall, once the perpetration of the crime is verified, confiscate the following:
a. Funds subject matter of the crime, proceeds and instrumentalities.
b. Any funds owned by foe perpetrator with an equivalent value to the funds, Proceeds and instrumentalities mentioned in paragraph (a) of this clause if it fails to confiscate those funds.
If it is not possible to rule for the confiscation of funds, proceeds or instrumentalities due to their failure to seize them or because they are related to the rights of bona fide third parties, the court shall pass a fine equivalent to its value at the time of the crime.
- The confiscation shall be Imposed Irrespective of whether the funds, Proceeds, or Instrumentalities are owned by or in possession of the perpetrator or a third party without prejudice to the rights of third party acting in good faith.
- The fact that the offender is unknown, lack of his criminal responsibility, or the criminal case for a crime punishable under the provisions of this Decree-Law is elapsed does not preclude the competent court from ruling on its own or at the request or the Public Prosecution, as the case may be, to confiscate the seized funds, proceeds and instrumentalities if it is proven mat they are related to the same.
- Without prejudice to the rights of bona fide third parties, any contract or act where the parties, or any one of them or otherwise are aware that such contract or act aims at impacting the ability of the competent authorities to enforce the seizure, freezing or the execution of the confiscation order, shall be void.
Article (26) bis:
Imprisonment for no less than six months and a penalty of no less than AED 200,000 (two hundred thousand dirham) and no more than AED 5,000,000 (five million dirham) or any of these two sanctions shall apply to anyone who violates the provisions of Article (16) bis of this Decree-Law
This article has been amended by Federal Decree-Law No. (26) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 23/10/2018 to 13/09/2021)1- The court shall, once the perpetration of the Crime is verified, confiscate the following:
a) Funds of the Crime, proceeds and instrumentalities used or intended to be used in the Crime.
b) Any Funds owned by the perpetrator with an equivalent value to the Funds and Proceeds mentioned in paragraph (a) of this clause if it fails to confiscate those funds.
2- The confiscation shall be imposed irrespective of whether the Funds, Proceeds, or Instrumentalities are owned by or in possession of the perpetrator or a third party without prejudice to the rights of third party acting in good faith.
3- In the cases of the death of the accused in a Crime punishable under the Decree Law or the perpetrator’s identity being unknown shall not prevent the public prosecution from referring the case file to the competent court to issue an order to confiscate the seized Funds, Proceeds and Instrumentalities if it is established that they were related to the Crime.
4- Without prejudice to the rights of bona fide third parties, any contract or act where the parties, or any one of them or otherwise are aware that such contract or act aims at impacting the ability of the competent authorities to enforce the seizure, freezing or the execution of the confiscation order, shall be void.
Article (27)
Supervisory authorities, FIU, Law Enforcement Authorities, Financial Institutions, Designated Nonfinancial Businesses and Professions, their board members, employees and legally authorized representatives are exempted from criminal, civil or administrative responsibility in relation to their providing any requested information or violating any obligation under legislative, contractual and administrative directives aimed at securing confidentiality of information unless the disclosure is made in bad faith or with the intent of causing damages to others.
Article (28)
Imprisonment of no less than a year and no more than (7) seven years, or a fine of no less than AED 50,000 (fifty thousand dirham) and no more than AED 5,000,000 (five million dirham) shall be applied to any person who violates the instruction issued by the Competent authority in the State for the implementation of the directives of UN Security Council under Chapter (7) of UN Convention for the Suppression of the Financing of Terrorism and Proliferation of Weapons of Mass Destruction and other related decisions
This article has been amended by Federal Decree-Law No. (26) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 23/10/2018 to 13/09/2021)Imprisonment or a fine of no less than (50,000) fifty thousand dirham and no more than AED (5,000,000) five million dirham shall be applied to any person who violates the instruction issued by the Competent Authority in the State for the implementation of the resolutions of United Nations Security Council under Chapter (7) of UN charter for the Suppression of the Financing of Terrorism and Proliferation of Weapons of Mass Destruction and its financing and other related decisions.
Article (29)
- If any foreigner is convicted of a money laundering crime or any felonies mentioned in this Decree-Law, and is given a sanction restricting his freedom, he must be deported from the UAE
- Without prejudice to Clause (1) of this article, if any foreign person is convicted for other criminal offences provided hereunder this Decree-Law, and is given a sentence restricting his freedom, the court may decide to deport him from the UAE or order him to be deported instead of Imposing a sanction restricting his freedom
- The criminal case shall not be subject to the statute of limitations for money laundering or financing terrorism or illegal organizations crimes. The sanctions shall not lapse with time or with the lapse of any related civil legal cases due to statute of limitations
- This Decree Law shall not prejudice the provisions of refereed Federal Law (7) of 2014
- The Financing of Illegal organizations is considered a crime if its purpose is to undermine the internal security of the State or its vital interests thereof and terrorism financing crime and the offense punishable in Article (28) of this Decree-Law are considered as crimes Intended to undermine the internal and external security of the State
This article has been amended by Federal Decree-Law No. (26) of 2021. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 23/10/2018 to 13/09/2021)1- If any foreigner is convicted of a Money Laundering Crime or any felony mentioned in this Decree Law, and is given a sanction restricting his freedom, he must be deported from the State.
2- Without prejudice to Clause(1) of this Article, if any foreign person is convicted for other offences provided hereunder this Decree Law, and is given a sentence restricting his freedom, the court may decide to deport him from the State or order him to be deported instead of imposing a sanction restricting his freedom.
3- The criminal case shall not be subject to the statute of limitations for Money Laundering or Financing of Terrorism or Financing Illegal Organisations Crimes. The sanctions shall not lapse with time or with the lapse of any related civil legal cases due to statute of limitations.
4- This Decree Law shall not prejudice the provisions of refereed Federal Law no. (7) of 2014.
5- The Financing of Illegal Organisations is considered a Crime if its purpose is to undermine the internal security of the State or its vital interests thereof and Financing of Terrorism Crimes are considered as crimes intended to undermine the internal and external security of the State.
- If any foreigner is convicted of a money laundering crime or any felonies mentioned in this Decree-Law, and is given a sanction restricting his freedom, he must be deported from the UAE
Article (30)
Imprisonment and a fine or one of the two penalties shall be imposed on anyone who intentionally fails to declare or refrains from providing additional information upon request, from him or deliberately conceals information that must be declared or deliberately presents incorrect information, in violation of the provisions provided for in Article (8) of this Decree Law. Upon conviction, the Court may rule on the confiscation of seized Funds without prejudice to the rights of others acting in good faith
Article (31)
Imprisonment or a fine of no less than (10,000) ten thousand dirhams and no more than (100,000) one hundred thousand dirhams shall be applied to any person who violates any other provision of this Decree Law.
Article (32)
Employees designated per decision issued by the Minister of Justice, in coordination with the Governor, shall, in establishing acts occurring in violation of the provisions of this Decree Law or its Executive Regulation or the decisions issued thereunder, have the capacity of judicial officers.
Article (33)
The Cabinet of Ministers shall issue the Executive Regulation of this Decree Law based upon the proposal of Minister.
Article (34)
1- Any provision that violates or conflicts with the provisions of this Decree Law shall be revoked.
2- Federal Law no. (4) of 2002 on the criminalization of money laundering shall be abrogated.
Article (35)
The present Decree Law shall be published in the Official Gazette and to be entered into effect one month from the date of publication.
Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations
Fed Res Cab 10/2019 Effective from 10/2/2019The Cabinet Decision No. (10) of 2019 has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version.The Cabinet,
- Pursuant to the perusal of the Constitution;
- Federal Law No. (1) of 1972 concerning the Competencies of Ministries and Powers of the Ministers and its amendments;
Based on the proposal of the Minister of Finance and the approval of the Cabinet,
Has issued the following:
Chapter 1 Definitions
Article (1)
In application of the provisions of this Resolution, the following terms and expressions shall have the following meanings assigned to them unless the context requires otherwise:
State: United Arab Emirates
Minister: Minister of Finance
Central Bank: Central Bank of the United Arab Emirates
Governor: Governor of the Central Bank
Committee: National Committee for Combating Money Laundering and the Financing of Terrorism and Illegal Organizations
Unit: Financial Intelligence Unit.
Supervisory Authority: Federal and local authorities entrusted by legislation to supervise the Financial Institutions, the designated non-financial businesses professions, Virtual Asset Service Providers and non-profit organizations or the competent authority in charge of approving the exercise of an activity or a profession if the legislation does not specify the relevant regulatory authority
Law-enforcement Authorities: Federal and local authorities entrusted under applicable legislation to conduct combat, search, investigate and collect evidences on crimes including AML/CFT crimes and financing illegal organizations.
Competent Authorities: Concerned government authorities that are in charge of implementing any provision of the Decree Law in the State.
Predicate Offence: Any act constituting a felony or misdemeanor under the applicable legislation of the State, whether committed inside or outside the State, when such act is punishable in both countries.
Money Laundering: Any of the acts mentioned in Clause (1) of Article (2) of the Decree-Law.
Financing of Terrorism: Any of the acts mentioned in Articles nos. (29 and 30) of Federal Law no. (7) of 2014 on Combating Terrorism Offences.
Illegal Organizations: Organizations whose establishment is criminalized, or which exercise a criminalized activity.
Financing Illegal Organizations: Any physical or legal action aiming at providing funding to an illegal organization, or any of its activities or its members.
Crime: Money laundering crime and related predicate offences, or financing of terrorism or illegal organizations.
Funds: Assets, regardless of the manner in which they are earned, their type or their form, whether tangible or intangible, movable or immovable, electronic, digital or encrypted, including national and foreign currencies, legal documents and instruments of whatever form, including electronic or digital forms that prove the ownership of these assets, shares or related rights and economic resources that are assets of any kind, including natural resources. As well as bank credits, cheques, payment orders, shares, securities, bonds, bills of exchange, letters of credit, and any interest, dividends or other incomes derived or resulting from these assets, and can be used to obtain any financing or goods or services.
Virtual Assets: A digital representation of the value that can be digitally traded or transferred, and can be used for payment or investment purposes, and do not include digital representations of fiat currencies, securities, or other funds.
Proceeds: Funds generated directly or indirectly from the commitment of any felony or misdemeanor including profits, benefits, and economic interests, or any similar funds converted wholly or partly into other funds.
Means: Any means used or intended to be used to commit a felony or misdemeanor.
Suspicious Transactions: Transactions related to funds for which there are reasonable grounds to believe that they are earned from any felony or misdemeanor or related to the financing of terrorism or of illegal organizations, whether committed or attempted.
Freezing or seizure: Temporary attachment over the moving, conversion, transfer, replacement or disposition of funds in any form, by an order issued by a competent authority.
Confiscation: Permanent expropriation of private funds or proceeds or instrumentalities by a judgment issued by a competent court.
Financial Institutions: Whoever conducts one or more of the financial activities or transactions in for or on behalf of a client.
Financial Intermediary: The financial institution that receives and transfers a wire transfer between the financial institution issuing the transfer and the beneficiary financial institution or another financial intermediary.
The beneficiary financial institution: the financial institution that receives a wire transfer from the financial institution issuing the transfer directly or through an financial intermediary institution, and provides the money available to the beneficiary.
Financial activities or operations: any activity or operation or more of what is stipulated in Article no. (2) of this Resolution.
Designated Nonfinancial Businesses and Professions: Whoever conducts one or more of the commercial or professional activities defined in Article no. (3) of this Resolution.
Non-Profit Organizations: Any organized group, of a continuing nature set for a temporary or permanent period, comprising natural or juridical persons or a legal arrangement not seeking profit, that collects, receives or disburses funds for charitable, religious, cultural, educational, social, communal or any other charitable activities.
Legal Arrangement: the relationship established by means of a contract concluded between two or more parties, including but not limited to trust funds or other similar arrangements.
Trust Fund: A legal relationship whereby the trustee places funds under which the trustor places the funds under the control of the trustee for the account of a beneficiary or for particular purpose , and deemed to be Funds independent of the trustee's property. The right of the trustor’s Funds remains in the name of the trustor or in the name of another person on behalf of the trustor.
Trustor: A natural or juridical person who transfers the management of his funds to a trustee under a document.
Trustee: A natural or juridical person enjoying the rights and powers granted to it by the Trustor, under which he manages, uses and disposes of the trustor’s funds in accordance with the terms imposed on him by either of them.
Client: Any person who carries out or attempts to carry out any of the activities specified in Articles nos. (2) and (3) of this Resolution with a Financial Institutions or designated non-financial businesses and professions or Virtual Asset Service Providers
Transaction: Any disposal or use of Funds or proceeds including for example: deposits, withdrawals, transfer, sale, purchase, lending, swap, mortgage, and donation.
Real Beneficiary : The natural person who owns or exercises effective ultimate control, whether directly or indirectly, over a client or the natural person on whose behalf a transaction is being conducted or a person who exercises effective ultimate control over a juridical person or legal arrangement, whether directly or through a chain of ownership, or control or other indirect means.
Virtual Asset Service Providers: Any natural or juridical person, who conducts any activity of commercial business, conducts one or more of the activities of virtual assets for the benefit or on behalf of another natural or legal person in any of the following activities:
1- Exchange between virtual assets and fiat currencies.
2- Exchange between one or more types of virtual assets.
3- Transfer of virtual assets.
4- Saving or managing virtual assets or tools that enable control of virtual assets.
5- Providing financial services or activities related to an issuer’s offer or, selling or participating in virtual assets.
Business relationship: Any ongoing business or financial relationship arising between Financial Institutions or Designated Non-Financial Business or Professions, and their client related to the activities or services they provide thereto.
Correspondent banking relationship: relationship between a correspondent financial institution and a recipient institution through a current account, or any other type of account or any other associated service therewith, including the correspondent relationship arising for securities transactions or money transfer.
Intermediary Payment Accounts: correspondent account used directly by a third party to perform transactions for its account.
Financial Group: A group of Financial Institutions consisting of a holding company or other juridical person that exercises control over the rest of the group and coordinates the functions in order to control at the level of the group and its branches and subsidiaries, in accordance with the international basic principles of financial control and the policies and procedures for AML/CFT.
Fundamental Principles of International Financial Control: Principles of the Basel Committee for Effective Banking Supervision Nos. (1, 2, 3, 5 to 9, 11 to 15, 26 and 29), the Principles of the International Association of Insurance Supervisors (IAIS). (1, 3 to 11, 18, 21 to 23, 25), and the Principles of the International Organization of Securities Commissions (IOSCO) Nos. (24, 28, 29 and 31) and Responsibilities (A, B, C, and D).
Wire Transfer: A financial transaction carried out by a financial institution itself or through an intermediary institution, on behalf of a sender, through which funds are delivered to a beneficiary in another financial institution, whether the sender and the beneficiary are the same person or others.
Fictitious Bank: A bank registered or licensed in a state that has no physical presence therein, does not belong to a regulated and supervised financial group..
Registrar: entity in charge of supervising the register of commercial names for all types of establishments registered in the State.
Due Diligence Measures: The process of identifying or verifying the information of the Client or the real Beneficiary owner, whether a natural, juridical person or a legal arrangement, and the nature of its activity, and the purpose of the business relationship, and the ownership structure, control over it for the purpose of the Decree-Law and this Resolution.
Controlled Delivery: process by which a competent authority allows the entery or transferring of illegal or suspicious funds or crime revenues to and from the State for the purpose of investigating a crime or identifying the identity of its perpetrators.
Undercover Operation: process of search and investigation conducted by one of the judicial officer by impersonating or playing a disguised or false role in order to obtain evidence or information related to the Crime.
High Risk Client: A Client who represents a risk, either in person , or through his activity, business relationship, its nature or his geographical area, such as a Clientclient from high-risk countries, or non-resident in a country for which does not have an identity card, or of a complex structure, or who carries out complex or unclear operations with an economic or legal purpose, or carries out intensive cash transactions, operations with an unknown third party, or conduct operations without direct confrontation, or any other high-risk operations specified by Financial Institutions, Designated Non-Financial Businesses and Professions, or the Regulatory authority.
Politically exposed persons: Natural persons who are or have been entrusted with prominent functions in the State or in any other State, such as heads of State or Government, senior politicians, high-ranking government officials, judicial or military officials, senior executives of State-owned enterprises, senior officials of political parties, and persons who are or have been entrusted with the management or any other prominent function of international organizations. The definition shall include the following:
- The immediate family members of the politically exposed person, namely spouses, children, their spouses, and parents.
- Partners known to be close to the Politically Exposed Person, namely:
- Persons having joint ownership of a juridical person, or legal arrangement or any close business relationship with the politically exposed person.
- Persons having the exclusive ownership of a single of a juridical person or legal arrangement established for the benefit of the politically exposed person.
- Persons having joint ownership of a juridical person, or legal arrangement or any close business relationship with the politically exposed person.
Decree-Law: Federal Decree-Law No. (20) of 2018 on Combating Money Laundering and the Financing of Terrorism and Illegal Organizations, and its amendments.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)In application of the provisions of the present Decision, the following terms and expressions shall have the meanings assigned to them unless the context requires otherwise:
State: United Arab Emirates
Minister: Minister of Finance
Central Bank: Central Bank of United Arab Emirates
Governor: Governor of the Central Bank
Committee: National Committee for Anti- Money Laundering and Combating the Financing of Terrorism and Illegal Organisations.
FIU: Financial Intelligence Unit
Supervisory Authority: Federal and local authorities, which are entrusted by legislation to supervise Financial Institutions, Designated Non-Financial Businesses and Professions and Non-Profit Organisations or the competent authority in charge of approving the pursuit of an activity or a profession in case a supervisory authority is not assigned by legislations.
Law Enforcement Authorities: Federal and local authorities which are entrusted under applicable legislation to combat, search, investigate and collect evidences on the crimes including ML/FT and financing illegal organisations crimes.
Competent Authorities: The competent government authorities entrusted with the implementation of any provision of the Decretal-Law in the State.
Predicate Offence: Any act constituting an felony or misdemeanour under the applicable laws of the State whether this act is committed inside or outside the State when such act is punishable in both countries.
Money Laundering: Any of the acts mentioned in Clause (1) of Article (2) of the Decretal-Law.
Financing of Terrorism: Any of the acts mentioned in Articles (29) and (30) of Federal Law no. (7) of 2014 on combating terrorism offences.
Illegal Organisations: Organisations whose establishment is criminalised or which pursue a criminalised activity.
Financing of Illegal Organisations: Any physical or legal action aiming at providing funding to an illegal organisation, or any of its activities or members.
Crime: Money laundering crime and related Predicate Offences, or Financing of Terrorism or Illegal Organisations.
Funds: Assets in whatever form, whether tangible, intangible, movable or immovable including national currency, foreign currencies, documents or notes evidencing the ownership of those assets or associated rights in any form including electronic or digital forms or any interests, profits or income originating or earned from these assets.
Proceeds: Funds generated directly or indirectly from the commitment of any felony or misdemeanour including profits, privileges, and economic interests, or any similar funds converted wholly or partly into other funds.
Means: Any means used or intended to be used for the commission of an offence or felony.
Suspicious Transactions: Transactions related to funds for which there are reasonable grounds to suspect that they are earned from any felony or misdemeanour related to the financing of terrorism or of illegal organisations, whether committed or attempted.
Freezing or Seizure: Temporary restriction over the moving, conversion, transfer, replacement or disposition of funds in any form, by an order issued by a Competent Authority.
Confiscation: Permanent expropriation of private funds or proceeds or instrumentalities by an injunction issued by a competent court.
Financial Institutions: Anyone who conducts one or several of the financial activities or operations of /or on behalf of a Customer.
Intermediary Financial Institution: The Financial Institution that receives and sends wire transfer between the Ordering Financial Institution and the Beneficiary Financial institution or another Intermediary Financial Institution.
Beneficiary Financial Institution: The Financial Institution that receives a wire transfer from an Ordering Financial Institution directly or indirectly via an Intermediary Financial Institution and makes funds available to the beneficiary.
Financial Transactions or Activities: Any activity or transaction defined in Article (2) of the present Decision.
Designated Nonfinancial Businesses and Professions (DNFBPs): Anyone who conducts one or several of the commercial or professional activities defined in Article (3) of the present Decision.
Non-Profit Organisations (NPOs): Any organised group, of a continuing nature set for a temporary or permanent time period, comprising natural or legal persons or not for profit legal arrangements for the purpose of collecting, receiving or disbursing funds for charitable, religious, cultural, educational, social, communal or any other charitable activities.
Legal Arrangement: A relationship established by means of a contract between two or more parties which does not result in the creation of a legal personality such as trusts or other similar arrangements.
Trust : A legal relationship in which a settlor places funds under the control of a trustee for the interest of a beneficiary or for a specified purpose. These assets constitute funds that are independent of the trustee's own estate, and the rights to the trust assets remain in the name of the settlor or in the name of another person on behalf of the settlor.
Settlor: A natural or legal person who transfers the control of his funds to a Trustee under a document.
Trustee: A natural or legal person who has the rights and powers conferred to him by the Settlor or the Trust, under which he administers, uses, and acts with the funds of the Settlor in accordance with the conditions imposed on him by either the Settlor or the Trust.
Customer: Anyone who performs or attempts to perform any of the acts defined in Articles (2) and (3) of the present Decision with any Financial Institution or Designated Non-Financial Business or Profession.
Transaction: All disposal or use of Funds or proceeds including for example: deposit, withdrawal, conversion, sale, purchase, lending, swap, mortgage, and donation.
Beneficial Owner: The natural person who owns or exercises effective ultimate control, directly or indirectly, over a Customer or the natural person on whose behalf a Transaction is being conducted or, the natural person who exercises effective ultimate control over a legal person or Legal Arrangement.
Business Relationship: Any ongoing commercial or financial relationship established between financial institutions, designated non-financial businesses and professions, and their Customers in relation to activities or services provided by them.
Correspondent Banking Relationship: Relationship between a correspondent financial institution and a respondent one through a current account or any other type of account(s) or through a service related to such an account and includes a corresponding relationship established for the purpose of securities transactions or transfer of funds.
Intermediary Account: Corresponding account used directly by a third party to conduct a transaction on its own behalf.
Financial Group: A group of financial institutions that consists of holding companies or other legal persons exercising the control over the rest of the group and coordinating functions for the application of supervision on the group, branch, and subsidiary level, in accordance with the international core principles for financial supervision, and AML/CFT policies and procedures.
Core Principles for Financial Supervision: Basel Committee on Banking Supervision (BCBS) Principles 1-3, 5-9, 11-15, 26, and 29; International Association of Insurance Supervisors (IAIS) Principles 1, 3-11, 18, 21-23, and 25; and International Organisation of Securities Commission (IOSCO) Principles 24, 28, 29 and 31; and Responsibilities A, B, C and D.
Wire Transfer: Financial transaction conducted by a financial institution or through an intermediary institution on behalf of a transferor whose funds are received by a beneficiary in another financial institution, whether or not the transferor and the beneficiary are the same person.
Shell Bank: Bank that has no physical presence in the country in which it is incorporated and licensed, and is unaffiliated with a regulated financial group that is subject to effective consolidated supervision.
Registrar: The entity in charge of supervising the register of commercial names for all types of establishments registered in the State.
Customer Due Diligence (CDD): Process of identifying or verifying the information of a Customer or Beneficial Owner, whether a natural or legal person or a legal arrangement, and the nature of its activity and the purpose of the business relationship and the ownership structure and control over it for the purposes of the Decretal-Law and this Decision.
Controlled Delivery: The process by which a competent authority allows the entering or transferring of illegal or suspicious funds or crime revenues to and from the UAE for the purpose of investigating a crime or identifying the identity of its perpetrators.
Undercover Operation: The process of search and investigation conducted by one of the judicial impoundment officers by impersonating or playing a disguised or false role in order to obtain evidence or information related to the Crime.
High Risk Customer: A Customer who represents a risk either in person, activity, business relationship, nature of geographical area, such as a Customer from a high-risk country or non-resident in a country in which he does not hold an identity card, or a costumer having a complex structure, performing complex operations or having unclear economic objective, or who conducts cash-intensive operations, or operations with an unknown third party, or operations without directly confronting any other high risk operations identified by financial institutions, or designated non-financial businesses and professions, or the Supervisory Authority.
Politically Exposed Persons (PEPs): Natural persons who are or have been entrusted with prominent public functions in the State or any other foreign country such as Heads of States or Governments, senior politicians, senior government officials, judicial or military officials, senior executive managers of state-owned corporations, and senior officials of political parties and persons who are, or have previously been, entrusted with the management of an international organisation or any prominent function within such an organisation; and the definition also includes the following:
- Direct family members (Of the PEP, who are spouses, children, spouses of children, parents).
- Associates known to be close to the PEP, which include:
- Individuals having joint ownership rights in a legal person or arrangement or any other close business relationship with the PEP.
- Individuals having individual ownership rights in a legal person or arrangement established in favour of the PEP.
- Individuals having joint ownership rights in a legal person or arrangement or any other close business relationship with the PEP.
Decretal- Law: Federal Decretal-Law No. (20) of 2018 on Anti- Money Laundering and Combating the Financing of Terrorism and Illegal Organisations.
- The immediate family members of the politically exposed person, namely spouses, children, their spouses, and parents.
Chapter 2 Financial Institutions, Designated Non-Financial Businesses and Professions, Virtual Asset Service Providers and Non-Profit Organizations
This title has been amended by Cabinet Resolution No. (24) of 2022.Part 1 Financial Institutions and DNFBPs
Section 1
Article (2) Activities and Transactions of Financial Institutions and DNFBPs
The following shall be considered as Financial Activities and Operations:
1- Receipt of deposits and other payable funds by the public, including Shariah-compliant deposits.
2- Provision of private banking services.
3- Provision of credit facilities of all types.
4- Provision of Financing facilities of all types, including Shariah-complaint Financing facilities.
5- Provision of monetary intermediary services.
6- Financial transactions in securities, financing and financial leasing.
7- Provision of exchange and money transfer services.
8- Issuance and management of means of payment, guarantees or obligations.
9- Provision of stored values services, retail e-payments and digital cash services.
10- Provision of virtual banking services.
11- Trading in, investment, operation or management of funds, options and future financial contracts, exchange rate and interest rate operations, and other financial derivatives or negotiable instruments.
12- Participation in issuing securities and providing of financial services related to these issues
13- Management of funds and portfolios of all kinds
14- Custody of Funds
15- Preparing or marketing financial activities.
16- Direct insurance operations, reinsurance operations for the type and branches of personal insurance, and money making operations in insurance companies, insurance brokers and agents.
17- Any other financial activity or transaction specified by the Supervisory Authority.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)The following are considered financial activities and transactions:
- Receiving deposits and other funds that can be paid by the public, including deposits in accordance with Islamic Sharia
- Providing private banking services
- Providing credit facilities of all types
- Providing credit facilities of all types, including credit facilities in accordance with Islamic Sharia
- Providing cash brokerage services
- Financial transactions in securities, finance and financial leasing
- Providing currency exchange and money transfer services
- Issuing and managing means of payment, guarantees or obligations
- Providing stored value services, electronic payments for retail and digital cash.
- Providing virtual banking services
- Trading, investing, operating or managing funds, option contracts, future contracts, exchange rate and interest rate transactions, other derivatives or negotiable financial instruments
- Participating in issuing securities and providing financial services related to these issues
- Managing funds and portfolios of all kinds
- Saving funds
- Preparing or marketing financial activities
- Insurance transactions, in accordance with Federal Law No. (6) of 2007 concerning the Establishment of the Insurance Authority and the Organisation of its Operations
- Any other activity or financial transaction determined by the Supervisory Authority
- Receiving deposits and other funds that can be paid by the public, including deposits in accordance with Islamic Sharia
Article (3)
Anyone who is engaged in the following trade or business activities shall be considered a DNFBP:
- Brokers and real estate agents when they conclude operations for the benefit of their Customers with respect to the purchase and sale of real estate
- Dealers in precious metals and precious stones in carrying out any single monetary transaction or several transactions that appear to be interrelated or equal to more than AED 55,000.
- Lawyers, notaries, and other independent legal professionals and independent accountants, when preparing, conducting or executing financial transactions for their Customers in respect of the following activities:
- Purchase and sale of real estate.
- Management of funds owned by the Customer.
- Management of bank accounts, saving accounts or securities accounts.
- Organising contributions for the establishment, operation or management of companies.
- Creating, operating or managing legal persons or Legal Arrangements.
- Selling and buying commercial entities.
- Purchase and sale of real estate.
- Providers of corporate services and trusts upon performing or executing a transaction on the behalf of their Customers in respect of the following activities:
- Acting as an agent in the creation or establishment of legal persons;
- Working as or equipping another person to serve as director or secretary of a company, as a partner or in a similar position in a legal person.
- Providing a registered office, work address, residence, correspondence address or administrative address of a legal person or Legal Arrangement.
- Performing work or equipping another person to act as a trustee for a direct Trust or to perform a similar function in favour of another form of Legal Arrangement.
- Working or equipping another person to act as a nominal shareholder in favour of another person.
- Acting as an agent in the creation or establishment of legal persons;
- Other professions and activities which shall be determined by a decision of the Minister
- Brokers and real estate agents when they conclude operations for the benefit of their Customers with respect to the purchase and sale of real estate
Section 2 Identification and Mitigation of Risks
Article (4)
- Financial Institutions and Designated Non-Financial Businesses and Professions shall identify, evaluate and understand their crime risks, in a manner commensurate with the nature and size of their business and shall abide by the following:
- Observing all relevant risk factors such as risks of Clients, countries or geographical areas, products, services, operations and their delivery channels before determining the overall risk level and the appropriate level of risk reduction measures to be applied Client.
- Documenting and continually updating risk assessments and providing them upon request.
- Observing all relevant risk factors such as risks of Clients, countries or geographical areas, products, services, operations and their delivery channels before determining the overall risk level and the appropriate level of risk reduction measures to be applied Client.
- Financial Institutions and Designated Non-Financial Businesses and Professions shall undertake to reduce the risks identified under Clause no 1) of this Article, taking into account the results of the national risk assessment, through the following:
- Developing internal policies, controls and procedures commensurate with the nature and size of its business approved by the senior management, which enable it to manage the identified risks and follow up their implementation and strengthen them if necessary, in accordance with Article no. (20) of this Resolution.
- Taking enhanced due diligence measures to manage high risks when identified, including the following for example:
- Obtaining and verifying further information as information on the identity of the Client, the beneficial owner, his/ her profession, and the amount of funds and information available through public databases and open sources.
- Obtaining additional information about the purpose of the business relationship or the reasons for the operations expected or actually performed.
- Updating Client Due Diligence (CDD) information in a more regular manner about the Client and the beneficial owner.
- Applying reasonable measures to determine the source of funds and wealth of the Client and the beneficial owner.
- Increasing the degree and level of continuous monitoring of the business relationship in order to determine whether they look unusual or suspicious, and to select patterns of operations that need further examination and review.
- Make the first payment through an account in the Client's name at a financial institution subject to similar due diligence standards.
- Obtain senior management approval to start or continue the business relationship with the Clientclient.
- Obtaining and verifying further information as information on the identity of the Client, the beneficial owner, his/ her profession, and the amount of funds and information available through public databases and open sources.
- Developing internal policies, controls and procedures commensurate with the nature and size of its business approved by the senior management, which enable it to manage the identified risks and follow up their implementation and strengthen them if necessary, in accordance with Article no. (20) of this Resolution.
- If the requirements indicated in clauses nos. (1) and (2) of this Article are met, the Financial Institutions and Designated Non-Financial Businesses and Professions may apply simplified due diligence measures to manage and reduce risks when low risks are identified, unless there is a suspicion of a crime has been committed. Simplified due diligence measures must be commensurate with low risk elements, including the following for example:
- Verifying the Clientclient’s identity and the real beneficiary owner after starting the business relationship.
- Updating Clientclients’ data at intervals.
- Reducing the rate of continuous monitoring rate and examination operations.
- Inferring the purpose and nature of the business relationship from the type of the established transactions or business relationship, without the need to collect information or undertake specific procedures.
- Verifying the Clientclient’s identity and the real beneficiary owner after starting the business relationship.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)- Financial institutions and DNFBPs are required to identify, assess, and understand their crime risks in concert with their business nature and size, and comply with the following:
- Considering all the relevant risk factors such as customers, countries or geographic areas; and products, services, transactions and delivery channels, before determining the level of overall risk and the appropriate level of mitigation to be applied.
- Documenting risk assessment operations, keeping them up to date on on-going bases and making them available upon request.
- Considering all the relevant risk factors such as customers, countries or geographic areas; and products, services, transactions and delivery channels, before determining the level of overall risk and the appropriate level of mitigation to be applied.
- Financial Institutions and DNFBPs shall commit to take steps to mitigate the identified risks mentioned as per Clause (1) herein, taking into consideration the results of the National Risk Assessment, by the following:
- Developing internal policies, controls and procedures that are commensurate with the nature and size of their business and are approved by senior management, to enable them to manage the risks that have been identified, and if necessary, to monitor the implementation of such policies, controls and procedures and enhance them as per Article (20) of the present Decision.
- Applying CDD measures to enhance high risks management once identified. Examples include:
- Obtaining more information and investigating this information such as information relating to the Customer and Beneficial Owner identity, or information relating to the purpose of the business relationship or reasons of the transaction.
- Updating the CDD information of the Customer and Beneficial Owner more systematically.
- Taking reasonable measures to identify the source of the funds of the Customer and Beneficial Owner.
- Increasing the degree and level of ongoing business relationship monitoring and examination of transactions in order to identify whether they appear unusual or suspicious.
- Obtaining the approval of senior management to commence the business relationship with the Customer.
- Obtaining more information and investigating this information such as information relating to the Customer and Beneficial Owner identity, or information relating to the purpose of the business relationship or reasons of the transaction.
- Developing internal policies, controls and procedures that are commensurate with the nature and size of their business and are approved by senior management, to enable them to manage the risks that have been identified, and if necessary, to monitor the implementation of such policies, controls and procedures and enhance them as per Article (20) of the present Decision.
- In case the requirements stipulated in Clauses (1 and 2) above are met, the Financial Institutions and DNFBPs shall be permitted to apply simplified CDD measures to manage and limit the identified low risks, unless there is suspicion of a committed Crime. The simplified CDD measures should be commensurate with the low risk factors. These include the following, as examples:
- Verifying the identity of the Customer and Beneficial Owner after establishing the business relationship.
- Updating the Customer’s data based on less frequent intervals.
- Reducing the rate of ongoing monitoring and transaction checks.
- Concluding the purpose and nature of the business relationship based on the type of transactions or the business relationship that has been established, without the need to gather information or performing specific procedure.
- Verifying the identity of the Customer and Beneficial Owner after establishing the business relationship.
- Financial Institutions and Designated Non-Financial Businesses and Professions shall identify, evaluate and understand their crime risks, in a manner commensurate with the nature and size of their business and shall abide by the following:
Section 3 Customer Due Diligence (CDD)
Article (5)
- Financial Institutions and DNFBPs are required to undertake CDD measures to verify the identity of the Customer and the Beneficial Owner before or during the establishment of the business relationship or opening an account, or before executing a transaction for a Customer with whom there is no business relationship. And in the cases where there is a low crime risk, it is permitted to complete verification of Customer identity after establishment of the business relationship, under the following conditions:
- The verification will be conducted in a timely manner as of the commencement of business relationship or the implementation of the transaction.
- The delay is necessary in order not to obstruct the natural course of business.
- The implementation of appropriate and effective measures to control the risks of the Crime.
- The verification will be conducted in a timely manner as of the commencement of business relationship or the implementation of the transaction.
- Financial Institutions and DNFBPs are required to take measures to manage the risks in regards to the circumstances where Customers are able to benefit from the business relationship prior to completion of the verification process.
- Financial Institutions and DNFBPs are required to undertake CDD measures to verify the identity of the Customer and the Beneficial Owner before or during the establishment of the business relationship or opening an account, or before executing a transaction for a Customer with whom there is no business relationship. And in the cases where there is a low crime risk, it is permitted to complete verification of Customer identity after establishment of the business relationship, under the following conditions:
Article (6)
Financial Institutions and DNFBPs should, as the case may be, undertake CDD measures in the following cases:
- Establishing the business relationship;
- Carrying out occasional transactions in favour of a Customer for amounts equal to or exceeding AED 55,000, whether the transaction is carried out in a single transaction or in several transactions that appear to be linked;
- Carrying out occasional transactions in the form of Wire Transfers for amounts equal to or exceeding AED 3,500.
- Where there is a suspicion of the Crime.
- Where there are doubts about the veracity or adequacy of previously obtained Customer's identification data.
- Establishing the business relationship;
Article (7)
Financial Institutions and DNFBPs should undertake CDD measures and ongoing supervision of business relationships, including:
- Audit transactions that are carried out throughout the period of the business relationship, to ensure that the transactions conducted are consistent with the information they have about Customer, their type of activity and the risks they pose, including - where necessary - the source of funds
- Ensure that the documents, data or information obtained under CDD Measures are up-to-date and appropriate by reviewing the records, particularly those of high-risk customer categories
- Audit transactions that are carried out throughout the period of the business relationship, to ensure that the transactions conducted are consistent with the information they have about Customer, their type of activity and the risks they pose, including - where necessary - the source of funds
Article (8)
- Financial Institutions and Designated Non-Financial Businesses and Professions shall recognize the identity of Client the client, whether permanent or occasional, and whether he/ she is a natural or juridical person or a legal arrangement they must also verify his/ her identity, using original documents, data or information from a reliable and independent source, as follows:
- As for natural persons:
Name as shown in the identity or travel document, the nationality, the address, the place of birth and, where applicable, the name and address of the employer, with an attached original copy of the valid identity card or travel document.
- As for juridical persons and legal arrangements:
- the Name, the legal form, and Articles of Incorporation.
- The address of the head office or the principal place of business, and if the person is a foreigner, the name and address of his/ her legal representative in the state, if any, shall be stated and the relevant supporting documents shall be submitted.
- Articles of Association or any other similar approved documents.
- The names of the relevant persons who hold senior management positions with the juridical person or legal arrangement.
- the Name, the legal form, and Articles of Incorporation.
- As for natural persons:
- Financial Institutions and Designated Non-Financial Businesses and Professions shall verify that any person who is acting on behalf of the ClientClient is authorized to do so, and shall identify such person in the manner provided for in clause no. (1) of this article.
- Financial Institutions and Designated Non-Financial Businesses and Professions shall understand the purpose and nature of the business relationship and obtain information related to this purpose when needed.
- Financial Institutions and Designated Non-Financial Businesses and Professions shall understand the nature of the Clientclient's business and the ownership and control structure of the Client.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)- Financial Institutions and DNFBPs should identify the Customer’s identity, whether the Customer is permanent or walk-in, and whether the Customer is a natural or legal person or legal arrangement, and verify the Customer’s identity and the identity of the Beneficial Owner. This should be done using documents, data or information from a reliable and independent source or any other source to verify the identity verification as follows:
- For Natural Persons:
The name, as in the identification card or travel document, nationality, address, place of birth, name and address of employer, attaching a copy of the original and valid identification card or travel document, and obtain approval from the senior management, if the Customer or the Beneficial Owner is a PEP.
- For Legal Persons and Legal Arrangements:
- The name, Legal Form and Memorandum of Association
- Headquarter office address or the principal place of business; if the legal person or arrangement is a foreigner, it must mention the name and address of its legal representative in the State and submit the necessary documents as a proof.
- Articles of Association or any similar documents, attested by the competent authority within the State.
- Names of relevant persons holding senior management positions in the legal person or legal arrangement.
- The name, Legal Form and Memorandum of Association
- For Natural Persons:
- Financial institutions and DNFBP’s are required to verify that any person purporting to act on behalf of the Customer is so authorised, and verify the identity of that person as prescribed in Clause (1), of this Article.
- Financial institutions and DNFBP’s are required to understand the intended purpose and nature of the business relationship, and obtain, when necessary, information related to this purpose.
- Financial institutions and DNFBP’s are required to understand the nature of the Customer’s business as well as the Customer’s ownership and control structure.
- Financial Institutions and Designated Non-Financial Businesses and Professions shall recognize the identity of Client the client, whether permanent or occasional, and whether he/ she is a natural or juridical person or a legal arrangement they must also verify his/ her identity, using original documents, data or information from a reliable and independent source, as follows:
Article (9)
Financial Institutions and Designated Non-Financial Businesses and Professions shall take reasonable measures that take the risks of crime arising from the client Client and business relationship into account, to identify and verify the beneficial owner of juridical persons and legal arrangements, using documents, data or information obtained from a reliable and independent source, as follows:
1. ClientClients from among juridical persons :
a- Obtaining the identity of the natural person, whether he/ she works alone or with another person who has an actual controlling share or equity in the juridical person by (25%) or more. b- In case of doubt as to the identity of the natural person in accordance with the preceding clause, or as to whether the natural person who has a controlling share or equity is the beneficial owner, or where no natural person exercises control through the equity, the natural person who exercises actual or legal control over the juridical person or legal arrangement shall be identified through any other direct or indirect means. c- If no natural person is identified under paragraphs nos. (a) and (b) of this clause, the natural person in question holding the position of Senior Management Officer, whether one or more persons, shall be identified.
2. ClientClients from among Legal arrangements:
Determing the Trustor or trustee, the beneficiaries or classes of beneficiaries, and any other natural person who exercises ultimate effective control, including through a series of controls or ownership over the trust directly or indirectly, and obtain sufficient information about the real beneficial owner so that he/ she can be identified at the time of payment or when he/ she intends to exercise his / her legally acquired rights.
With respect to other legal arrangements, they shall recognize the identity of the natural persons holding equivalent or similar positions.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)Financial Institutions and DNFBP’s are required to take reasonable measures to verify the identity of the Beneficial Owners of legal persons and Legal Arrangements, by using information, data, or statistics acquired from a reliable source, by the following:
1. For Customers that are legal persons:
(a) Obtaining and verifying the identity of the natural person, who by himself or jointly with another person, has a controlling ownership interest in the legal person of 25% or more, and in case of failing or having doubt about the information acquired, the identity shall be verified by any other means.
(b) In the event of failing to verify the identity of the natural person exercising control as per paragraph (a) of this Clause, or the person(s) with the controlling ownership interest is not the Beneficial Owner, the identity shall be verified for the relevant natural person(s) holding the position of senior management officer, whether one or more persons.
2. For Customers that are Legal Arrangements:
Verifying the identity of the Settlor, the Trustee(s), or anyone holding a similar position, the identity of the beneficiaries or class of beneficiaries, the identity of any other natural person exercising ultimate effective control over the legal arrangement, and obtaining sufficient information regarding the Beneficial Owner to enable the verification of his/her identity at the time of payment, or at the time he/she intends to exercise his/her legally acquired rights.
Article (10)
Financial Institutions and Designated Non-Financial Businesses and Professions and virtual assets services providers shall be exempt from determining and verifying the identity of the shareholder or partner or the Real Beneficiary, provided that such information is obtained from reliable sources in cases where the Client or owner of the controlling interest is of any of the following:
- A company that is listed on a regulated securities market and that is subject to disclosure requirements under any means that impose the requirements of adequate transparency for the Real Beneficiary.
- A subsidiary company whose majority of shares or stocks are owned by a holding company.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)Financial Institutions and DNFBPs shall be exempted from identifying and verifying the identity of any shareholder, partner, or the Beneficial Owner, if such information is obtainable from reliable sources where the Customer or the owner holding the controlling interest are as follow:
- A company listed on a regulated stock exchange subject to disclosure requirements through any means that require adequate transparency requirements for the Beneficial Owner.
- A subsidiary whose majority shares or stocks are held by the shareholders of a holding company.
- A company that is listed on a regulated securities market and that is subject to disclosure requirements under any means that impose the requirements of adequate transparency for the Real Beneficiary.
Article (11)
- In addition to the Due Diligence measures required for the ClientClient and the beneficial owner, Financial Institutions must take Due Diligence measures and continuous supervision towards the beneficiary of personal insurance policies and money making operations, including life insurance products, family takaful insurance and other investment insurance products, as soon as the beneficiary is identified or named as follows:
- As for the named beneficiary, the name of the person must be obtained, whether he/she is a natural or legal person or a legal arrangement.
- As for the beneficiary identified by category or description such as family relationship such as spouse, children or any other means such as will or estate, sufficient information about the beneficiary must be obtained to ensure that the financial institution will be able to identify the beneficiary when disbursing compensation or benefits.
- Verifying the identity of the beneficiary in the two previous cases when paying compensation or dues or exercising any rights related to those documents.
- As for the named beneficiary, the name of the person must be obtained, whether he/she is a natural or legal person or a legal arrangement.
- In all cases, Financial Institutions must consider the clientClient and beneficiary of life insurance policies and family takaful insurance as risk factors when determining the applicability of enhanced due diligence procedures. Moreover, if they find that the beneficiary is a high risk legal person or arrangement, they must take enhanced due diligence measures, which must include reasonable procedures to identify and verify the beneficial owner of the policy beneficiary when paying compensation or dues or exercising any rights related to those policies.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)- In addition to the CDD measures required for the Customer and the Beneficial Owner, Financial Institutions shall be required to conduct CDD measures and ongoing monitoring of the beneficiary of life insurance policies and funds generating transactions, including life insurance products relating to investments and family Takaful insurance, as soon as the beneficiary is identified or designated as follows:
- For the beneficiary identified by name, the name of the person, whether a natural person a legal person or a legal arrangement, shall be obtained.
- For a beneficiary designated by characteristics or by class– such as a family relation like parent or child, or by other means such as will or estate – it shall be required to obtain sufficient information concerning the beneficiary to ensure that the Financial Institution will be able to establish the identity of the beneficiary at the time of the pay-out.
- For the beneficiary identified by name, the name of the person, whether a natural person a legal person or a legal arrangement, shall be obtained.
- In all cases – the Financial Institutions should verify the identity of the beneficiary at the time of the payout as per the insurance policy or prior to exercising any rights related to the policy. If the Financial Institution identifies the beneficiary of the insurance policy to be a high-risk legal person or arrangement, then it should conduct enhanced CDD measures to identify the Beneficial Owner of that beneficiary, legal person, or legal arrangement.
- In addition to the Due Diligence measures required for the ClientClient and the beneficial owner, Financial Institutions must take Due Diligence measures and continuous supervision towards the beneficiary of personal insurance policies and money making operations, including life insurance products, family takaful insurance and other investment insurance products, as soon as the beneficiary is identified or named as follows:
Article (12)
Financial Institutions and DNFBPs should apply CDD measures to Customers and the ongoing business relationship on the effective date of the present Decision, within such times as deemed appropriate based on relative importance and risk priority. It should also ensure the sufficiency of data acquired, in case CDD measures were applied before the effective date of the present Decision.
Article (13)
- Financial Institutions and DNFBPs shall be prohibited from establishing or maintaining a business relationship or executing any transaction should they be unable to undertake CDD measures towards the Customer and should consider reporting a suspicious transaction to the FIU.
- Even if they suspect the commission of a Crime, financial institutions and DNFBPs should not apply CDD measures if they have reasonable grounds to believe that undertaking such measures would tip-off the Customer and they should report a Suspicious Transaction to the FIU along with the reasons having prevented them from undertaking such measures.
- Financial Institutions and DNFBPs shall be prohibited from establishing or maintaining a business relationship or executing any transaction should they be unable to undertake CDD measures towards the Customer and should consider reporting a suspicious transaction to the FIU.
Article (14)
Financial Institutions and DNFBP’s shall commit to the following:
- Not to deal in any way with Shell Banks, whether to open bank accounts in their names, or to accept funds or deposits from them.
- Not to create or keep records of bank accounts using pseudonyms, fictitious names or numbered accounts without the account holder’s name.
- Not to deal in any way with Shell Banks, whether to open bank accounts in their names, or to accept funds or deposits from them.
Section 4 Politically Exposed Persons (PEPs)
Article (15)
Financial Institutions and Designated Non-Financial Businesses and Professions must, in addition to implementing ClientClient Due Diligence (CDD) in accordance with the third part of the first section of this chapter, adopt the following:
First: As for Foreign Politically exposed person (PEPs),
- Developing the appropriate risk management systems to determine whether the Client or the beneficial owner is a Foreign Politically exposed person.
- Obtaining senior management approval before establishing or continuing the business relationship for current Clients who are Foreign Politically exposed persons.
- Taking reasonable measures to determine the sources of funds and wealth of Clients, and the beneficial owners who have been identified as politically exposed persons.
- Carrying out continuous and enhanced follow-up of the business relationship.
Second: As for local politically exposed persons and persons who have already been assigned a prominent position in an international organization:
- Taking sufficient measures to determine whether the Client or the beneficial owner is one of these persons.
- Taking the measures mentioned in paragraphs nos. (b), (c) and (d) of article “First”, when there is a high-risk business relationship with such persons.
- Developing the appropriate risk management systems to determine whether the Client or the beneficial owner is a Foreign Politically exposed person.
- Subject to clause no. (1) of this article, the Financial Institutions concerned with life and family takaful insurance policies must take reasonable measures to determine whether the beneficiary or beneficial owner is a politically exposed person before paying compensation or dues or exercising any rights related to those policies. When there are higher risks, they must inform senior management before paying compensation or dues or exercising any rights related to them, conduct a thorough examination of the overall business relationship, and consider reporting a suspicious transaction report to the Unit.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)- In addition to undertaking CDD measures required under Section 3, Part 1 of this Chapter, Financial Institutions and DNFBPs shall be required to carry out the following:
First: For Foreign PEPs:
- Put in place suitable risk management systems to determine whether a Customer or the Beneficial Owner is considered a PEP.
- Obtain senior management approval before establishing a business relationship, or continuing an existing one, with a PEP.
- Take reasonable measures to establish the source of funds of Customers and Beneficial Owners identified as PEPs.
- Conduct enhanced ongoing monitoring over such relationship.
Second: For Domestic PEPs and individuals previously entrusted with prominent functions at international organisations:
- Take sufficient measures to identify whether the Customer or the Beneficial Owner is considered one of those persons.
- Take the measures identified in Clauses (b), (c), and (d) under the first paragraph of this Article, when there is a high-risk business relationship accompanying such persons.
- Put in place suitable risk management systems to determine whether a Customer or the Beneficial Owner is considered a PEP.
- Financial Institutions shall be required to take reasonable measures to determine the beneficiary or Beneficial Owner of life insurance policies and family takaful insurance. If identified as a PEP, Financial institutions shall inform senior management before the pay-out of those policies, or prior to the exercise of any rights related to them, in addition to thoroughly examining the overall business relationship, and consider reporting to the Unit a suspicious transaction report.
Section 5 Suspicious Transaction Reports (STRs)
Article (16)
Financial Institutions and DNFBPs shall put in place indicators that can be used to identify the suspicion on the occurrence of the Crime in order to report STRs, and shall update these indicators on an ongoing basis, as required, in accordance with the development and diversity of the methods used for committing such crimes, whilst complying with what the Supervisory Authorities or FIU may issue instructions in this regard.
Article (17)
- In the case of suspecting, or if they have reasonable grounds to suspect, that an Operation or an attempt to carry out an Operation or that Funds representing Proceeds, in whole all or in part, are related to the Crime or that they will be used for such purpose regardless of their value, Financial Institutions and Designated Non-Financial Businesses and Professions shall comply with the following without invoking bank secrecy or professional or contractual confidentiality:
- Report directly Suspicious Transaction Reports (STRs) to the Unit without delay through its electronic system or any other means approved by the Unit.
- Respond to all additional information requested by the Unit.
- Report directly Suspicious Transaction Reports (STRs) to the Unit without delay through its electronic system or any other means approved by the Unit.
- Lawyers, notaries and other independent legal professionals and independent legal auditors shall be exempt from the provision of Clause no. (1) of this Article if obtaining information relating to such operations on their assessment of the legal status of the client, defending or representing him/ her, before the courts, arbitration or mediation proceedings, or the provision of legal opinion in a matter relating to a judicial proceeding. This includes providing advice on the commencement or avoidance of such proceedings whether the information was previously obtained, during or after the proceedings or in other circumstances in which they are subject to professional secrecy.
- Financial Institutions, Designated Non-Financial Businesses and Professions, Virtual Asset Service Providers, members of their boards of directors, employees and legally authorized representatives shall not incur any administrative, civil or criminal responsibility resulting from the disclosure of any secret, when informing the unit or providing it with information in good faith, even if they do not know exactly what the crime is or whether it actually occurs.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)- If Financial Institutions and DNFBPs have reasonable grounds to suspect that a Transaction, attempted Transaction, or funds constitute crime proceeds in whole or in part, or are related to the Crime or intended to be used in such activity, regardless of the amount, they shall adhere to the following without invoking bank secrecy or professional or contractual secrecy:
- Directly report STRs to the FIU without any delay, via the electronic system of the FIU or by any other means approved by the FIU
- Respond to all additional information requested by the FIU.
- Directly report STRs to the FIU without any delay, via the electronic system of the FIU or by any other means approved by the FIU
- Lawyers, notary publics, other legal stakeholders and independent legal auditors shall be exempt from Clause (1) of this Article, if obtaining this information regarding such Transactions relates to the assessment of their Customers’ legal position, or defending or representing them before judiciary authorities or in arbitration or mediation, or providing legal opinion with regards to legal proceedings, including providing consultation concerning the initiation or avoidance of such proceedings, whether the information was obtained before or during the legal proceedings, or after their completion, or in other circumstances where such Customers are subject to professional secrecy.
- Financial Institutions and DNFBPs, their board members, employees and authorised representatives shall not be legally liable for any administrative, civil or criminal liability for reporting when reporting to the Unit or providing information in good faith.
- In the case of suspecting, or if they have reasonable grounds to suspect, that an Operation or an attempt to carry out an Operation or that Funds representing Proceeds, in whole all or in part, are related to the Crime or that they will be used for such purpose regardless of their value, Financial Institutions and Designated Non-Financial Businesses and Professions shall comply with the following without invoking bank secrecy or professional or contractual confidentiality:
Article (18)
- Financial Institutions and Designated Non-Financial Businesses and Professions, their directors, officials and employees shall not disclose, directly or indirectly, to the Client or any other person, their reporting, or that they are about to report suspicious operations or information and data related to them. They shall not also disclose the existence of an investigation. This does not prevent sharing of information with branches and subsidiaries at the level of the financial group in accordance with the provisions of Article no. (31) of this decision.
- An attempt by lawyers, notaries pubic, other independent legal professionals, or independent legal auditors to dissuade the Client from performing an act that is contrary to the law shall not be considered as disclosure.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)- Financial Institutions and DNFBPs, their managers, officials or staff, shall not disclose, directly or indirectly, to the Customer or any other person(s) that they have reported, or are intending to report a Suspicious Transaction, nor shall they disclose the information or data contained therein, or that an investigation is being conducted in that regard.
- When lawyers, notaries, other independent legal professionals, and legal independent auditors attempt to discourage their Customers from committing a violation, they shall not be considered to have made a disclosure.
- Financial Institutions and Designated Non-Financial Businesses and Professions, their directors, officials and employees shall not disclose, directly or indirectly, to the Client or any other person, their reporting, or that they are about to report suspicious operations or information and data related to them. They shall not also disclose the existence of an investigation. This does not prevent sharing of information with branches and subsidiaries at the level of the financial group in accordance with the provisions of Article no. (31) of this decision.
Section 6 Reliance on a Third Party
Article (19)
- Taking into account the countries that the Committee identifies as high risk and the countries that suffer from weaknesses in AML/CFT systems, the Financial Institutions and the Designated Non-Financial Businesses and Professions may rely on a third party to carry out Client Due Diligence (CDD) in accordance with the third part of the first section of this chapter. The financial institution and the Designated Non-Financial Businesses and Professions shall be responsible for the validity of these measures, and shall do the following:
- Immediately obtain the identification data and necessary information collected during the Client Due Diligence (CDD) measures from the third party, and ensure that copies of the necessary documents for these measures can be obtained without delay upon request.
- Ensure that the third party is subject to regulation and control, and complies with the requirements of Client Due Diligence and keeps the registers provided for in this Decision.
- Immediately obtain the identification data and necessary information collected during the Client Due Diligence (CDD) measures from the third party, and ensure that copies of the necessary documents for these measures can be obtained without delay upon request.
- The financial institution and the Designated Non-Financial Businesses and Professions that that engage a third party who is part of the same Financial Group shall ensure the following:
- Ensure that the Group applies the Client Due Diligence Measures towards Clients and Politically Exposed Persons, that records are kept and that anti-Crime programmes are implemented in accordance with Parts 3, 4 and 11 of Section 1 of this Chapter and Article (31) of this Decision; .
- Sufficiently reduce any high risks related to countries through the Group-related anti-Crime policies and controls.
- Ensure that the Group applies the Client Due Diligence Measures towards Clients and Politically Exposed Persons, that records are kept and that anti-Crime programmes are implemented in accordance with Parts 3, 4 and 11 of Section 1 of this Chapter and Article (31) of this Decision; .
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)- Taking into consideration the high-risk countries identified by the Committee, the Financial Institutions and DNFBPs shall be permitted to rely on a third party to undertake the necessary CDD measures towards Customers as per Section 3 of Part 1 of this Chapter, and each of the Financial Institution and the DNFBP shall be responsible for the validity of these CDD measures, and shall do the following:
- Immediately obtain, from third parties, the necessary identification data and other necessary information collected through the CDD measures and ensure that copies of the necessary documents for such measures can be obtained without delay and upon request.
- Ensure that the third party is regulated and supervised, and adheres to the CDD measures towards Customers and record-keeping provisions of the present Decision.
- Immediately obtain, from third parties, the necessary identification data and other necessary information collected through the CDD measures and ensure that copies of the necessary documents for such measures can be obtained without delay and upon request.
- Financial Institutions and DNFBPs, who rely on third parties that are part of the same Financial Group,shall ensure that:
- The Financial Group applies the CDD, PEP, and record-keeping requirements and implements programs for combating the Crime in accordance with Sections 3, 4, 11 of Part 1 of this Chapter and Article (31) of this Decision, and the Financial Group is subject to supervision in that regard.
- The Financial Group sufficiently mitigates any high risks linked to countries through its own policies and controls for combating the Crime.
- The Financial Group applies the CDD, PEP, and record-keeping requirements and implements programs for combating the Crime in accordance with Sections 3, 4, 11 of Part 1 of this Chapter and Article (31) of this Decision, and the Financial Group is subject to supervision in that regard.
- Taking into account the countries that the Committee identifies as high risk and the countries that suffer from weaknesses in AML/CFT systems, the Financial Institutions and the Designated Non-Financial Businesses and Professions may rely on a third party to carry out Client Due Diligence (CDD) in accordance with the third part of the first section of this chapter. The financial institution and the Designated Non-Financial Businesses and Professions shall be responsible for the validity of these measures, and shall do the following:
Section 7 Internal Supervision and Foreign Branches and Subsidiaries
Article (20)
Financial Institutions and DNFBPs shall have internal policies, procedures and controls for combating the Crime, that should be commensurate with the Crime risks, and with the nature and size of their business, and to continuously update them, and to apply them to all its branches and subsidiaries in which it holds majority interest, including the following:
- CDD measures towards Customers as required in accordance with the Decretal-Law and the present Decision, including procedures for the risk management of business relationships prior to completing the verification process.
- Procedures for the reporting of Suspicious Transactions.
- Appropriate arrangements for compliance management for combating the Crime, including appointing a compliance officer
- Screening procedures to ensure the availability of high competence and compatibility standards when hiring staff
- Preparation of periodic programs and workshops in the field of combatting the Crime to build the capabilities of compliance officers and other competent employees.
- An independent audit function to test the effectiveness and adequacy of internal polices, controls and procedures relating to combating the Crime.
- CDD measures towards Customers as required in accordance with the Decretal-Law and the present Decision, including procedures for the risk management of business relationships prior to completing the verification process.
Section 8 Compliance Officer Tasks
Article (21)
Financial Institutions and Designated Non-Financial Businesses and Professions shall undertake to appoint a compliance officer, who shall have the appropriate competence and experience under its responsibility, to carry out the following tasks:
- Controlling of the Crime-Related Transactions.
- Accessing records and receiving, examining and studying data on Suspicious Transactions and taking the decision to notify the Unit or to retain such records and data while stating the reasons, under complete confidentiality.
- Reviewing the internal systems and procedures for anti-money laundering and combating the financing of terrorism and financing of illegal organizations, and their consistency with the provisions of the decree-law and this resolution. This is in addition to assessing the extent of the institution's commitment to its application and proposing what is necessary to update and develop it, and prepare periodic reports thereon to be submitted to the senior management. This is in addition to sending a copy to the concerned regulatory authority at its request, including the observations and decisions of the senior management.
- Developing, implementing and documenting ongoing programs and training and qualification plans for employees working for the organization on all matters related to anti-money laundering and combating the financing of terrorism and financing of illegal organizations and ways to confront them.
- Cooperating with the Regulatory Authority and the Unit, providing them with the data they request, and enabling their assigned employees to view the records and documents necessary to exercise their competencies.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)Financial Institutions and DNFBPs shall appoint a compliance officer. The compliance officer shall have the appropriate competencies and experience and under his or her own responsibility, shall perform the following tasks:
- Detect Transactions relating to any Crime.
- Review, scrutinise and study records, receive data concerning Suspicious Transactions, and take decisions to either notify the FIU or maintain the Transaction with the reasons for maintaining while maintaining complete confidentiality.
- Review the internal rules and procedures relating to combating the Crime and their consistency with the Decretal-Law and the present Decision, assess the extent to which the institution is committed to the application of these rules and procedures, propose what is needed to update and develop these rules and procedures, prepare and submit semi-annual reports on these points to senior management, and send a copy of that report to the relevant Supervisory Authority enclosed with senior management remarks and decisions.
- Prepare, execute and document ongoing training and development programs and plans for the institution’s employees on Money Laundering and the Financing of Terrorism and Financing of Illegal Organisations, and the means to combat them.
- Collaborate with the Supervisory Authority and FIU, provide them with all requested data, and allow their authorised employees to view the necessary records and documents that will allow them to perform their duties.
- Controlling of the Crime-Related Transactions.
Section 9 High-Risk Countries
Article (22)
- Financial Institutions and Designated Non-Financial Businesses and Professions shall apply enhanced due diligence measures in proportion to the degree of risk that may arise from business relationships or transactions with a natural or legal person from the countries that the Committee identifies as high risk or countries that suffer from weaknesses in AML/CFT systems.
- Financial Institutions and Designated Non-Financial Businesses and Professions shall apply countermeasures and any other measures requested by the regulatory Authorities on their own or on the basis of what the Committee determines with regard to high-risk countries and countries that suffer from weaknesses in AML/CFT systems.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)- Financial Institutions and DNFBPs shall implement enhanced CDD measures based on the level of risk that might arise from business relationships and Transactions with natural or legal persons from high-risk countries.
- Financial Institutions and DNFBPs shall implement CDD measures as defined by the Committee regarding High Risk Countries.
- Financial Institutions and Designated Non-Financial Businesses and Professions shall apply enhanced due diligence measures in proportion to the degree of risk that may arise from business relationships or transactions with a natural or legal person from the countries that the Committee identifies as high risk or countries that suffer from weaknesses in AML/CFT systems.
Section 10 Requirements relating to New Technologies
Article (23)
- Financial institutions and DNFBPs shall identify and assess the risks of money laundering and terrorism financing that may arise when developing new products and new professional practices, including means of providing new services and using new or under-development techniques for both new and existing products.
- Financial Institutions and DNFBPs shall assess risks prior to the release of products, practices or techniques, and take appropriate measures to manage and mitigate such risks
- Financial institutions and DNFBPs shall identify and assess the risks of money laundering and terrorism financing that may arise when developing new products and new professional practices, including means of providing new services and using new or under-development techniques for both new and existing products.
Section 11 Record-keeping
Article (24)
- Financial Institutions and Designated Non-Financial Businesses and Professions shall keep all records, documents, papers and data, for all financial operations and local or international commercial and cash transactions, for a period of no less than (5) years from the completion date of the transaction or the end of the business relationship with the Client.
- Financial Institutions and Designated Non-Financial Businesses and Professions must keep all records and documents obtained through Client due diligence measures, continuous supervision, accounts files, commercial correspondence, and copies of personal identity documents, including suspicious transaction reports and the results of any conducted analysis. This shall be for a period of no less than (5) years from the end date of the business relationship or from the closure date of the account for Clients who maintain accounts with these institutions. In addition, after the completion of an occasional process, from the date after the completion of the inspection by the supervisory authorities, from the completion date of the investigation, or from the date of a final judgment issued by the competent judicial authorities, all as the case may be.
- The operations and the documents records and the kept documents shall be so organized as to be sufficient to permit the reconstitution or re-arrangement of individual operations, the analysis of data and the tracking of financial operations, in such a manner as to provide, where appropriate, evidence of claim against criminal activity.
- Financial Institutions and Designated Non-Financial Businesses and Professions shall ensure all Client information related to Client due diligence, ongoing control and the results of their analysis, records, files, documents, correspondence and forms thereof immediately available to the concerned authorities upon their request.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)- Financial Institutions and DNFBPs shall maintain all records, documents, data and statistics for all financial transactions and local or international commercial and cash transactions for a period of no less than five years from the date of completion of the transaction or termination of the business relationship with the Customer.
- Financial institutions and DNFBPs shall keep all records and documents obtained through CDD measures, ongoing monitoring, account files and business correspondence, and copies of personal identification documents, including STRs and results of any analysis performed , For a period of no less than five years from the date of termination of the business relationship or from the closing date of the account to Customers who maintain accounts with these institutions or after the completion of a casual transaction or from the date of completion of the inspection by the Supervisory authorities, or from the date of issuance of a final judgment of the competent judicial authorities, all depending on the circumstances.
- The records, documents and documents kept shall be organised so as to permit data analysis and tracking of financial transactions.
- Financial Institutions and DNFBPs shall make all Customer information regarding CDD towards Customers, ongoing monitoring and results of their analysis, records, files, documents, correspondence and forms available immediately to the competent authorities upon request.
- Financial Institutions and Designated Non-Financial Businesses and Professions shall keep all records, documents, papers and data, for all financial operations and local or international commercial and cash transactions, for a period of no less than (5) years from the completion date of the transaction or the end of the business relationship with the Client.
Part 2 Requirements for Financial Institutions
Section 1 Correspondent Banking Relationship
Article (25)
- Before entering into correspondent banking or any other similar relationship, financial institutions shall take the following measures:
- Refrain from entering into or maintaining a correspondent banking relationship with Shell Banks or with an institution that allows their accounts to be used by Shell Banks.
- Collect sufficient information about any receiving correspondent banking institution for the purpose of identifying and achieving a full understanding of the nature of its work, and to make available, through publicly available information, its reputation and level of control, including whether it has been investigated.
- Evaluate anti-crime controls applied by the receiving institution.
- Obtain approval from senior management before establishing new correspondent banking relationships.
- Understand the responsibilities of each institution in the field of combatting Crime.
- Refrain from entering into or maintaining a correspondent banking relationship with Shell Banks or with an institution that allows their accounts to be used by Shell Banks.
- With respect to intermediate payment accounts, the financial institution should be required to ensure that the receiving institution has taken CDD measures towards Customers who have direct access to those accounts and that it is able to provide CDD information to the relevant Customers upon request of the correspondent institution.
- Before entering into correspondent banking or any other similar relationship, financial institutions shall take the following measures:
Section 2 Money or Value Transfer Services
Article (26)
- Providers of money or value transfer services shall be licensed by or registered with the competent Supervisory Authority. The Supervisory Authority shall take the necessary measures to punish those who provide such services without a licence or registration in accordance with their effective legislation and to ensure compliance of licensed or registered providers with the Crime combating controls.
- Providers of money or value transfer services shall keep an up-to-date list of their agents and make them available to the relevant authorities within the country in which the money or value transfer services providers and their agents operate, and shall engage their agents in combatting the Crime control programs and monitor them for compliance with these programs.
- Providers of money or value transfer services shall be licensed by or registered with the competent Supervisory Authority. The Supervisory Authority shall take the necessary measures to punish those who provide such services without a licence or registration in accordance with their effective legislation and to ensure compliance of licensed or registered providers with the Crime combating controls.
Section 3 Wire Transfers
Article (27)
- Financial Institutions shall ensure that all international wire transfers equal to or more than (AED 3.500) are always accompanied by the following data:
- The full name of the sender and the beneficiary.
- The account number of the sender and the beneficiary, and in the absence of such account, the transfer must include a unique reference number that allows Financial Institutions to track it.
- The sender's address, identification number, travel document, date and place of birth, or Client identification number with the transferring financial institution, which shall refer to a record containing these data.
- The full name of the sender and the beneficiary.
- In case of several international wire transfers are collected from one being combined in a transfer file to be sent to the beneficiaries, the transfer file shall include accurate data about the sender, and full information about the beneficiaries, which can be fully tracked in the beneficiary's country. Hence, the financial institution is required to include the sender's account number, or a unique reference number for the process.
- Financial Institutions shall ensure that all international wire transfers that are less than the amount of AED (3.500) are accompanied by the data contained in Clause no. (1) of this Article, without the need to verify the validity of the referred data, unless there are doubts about the commission of the crime.
- Financial Institutions transferring local wire transfers shall ensure that the information attached to the wire transfers includes the same data on the transferor referred to in Clause no. (1) of this Article, unless such data is available to the beneficiary Financial Institutions and the concerned parties by other means.
- When the data attached to the local wire transfer is available to the beneficiary Financial Institutions and the concerned authorities through other means, the transferring financial institution is required to include the account number or the unique reference number of the transaction only, provided that this number allows the tracking of transactions to the transferor or the beneficiary. Moreover, the transferring financial institution must provide such data within three (3) working days of receiving the request from the beneficiary financial institution or the concerned authorities.
- Financial Institutions are prohibited from executing wire transfers if they do not comply with the conditions set out in this article.
- The transferring Financial Institutions must keep all the collected information about the transferor and the beneficiary, in accordance with the provisions of Article No. (24) of this Resolution.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)- Financial institutions shall ensure that all international wire transfers equal to or exceeding AED (3,500) are always accompanied by the following data:
- The name of the originator, his or her identity number or travel document, date and place of birth, address and account number. In the absence of an account, the transfer must include a unique transaction reference number which allows the process to be tracked.
- The name of the beneficiary and his account number used to make the transfers. In the absence of the account, the transfer must include a unique transaction reference number which allows the process to be tracked.
- The name of the originator, his or her identity number or travel document, date and place of birth, address and account number. In the absence of an account, the transfer must include a unique transaction reference number which allows the process to be tracked.
- In the event that several individual cross-border wire transfers from a single originator are bundled in a batch file for transmission to beneficiaries, the batch file shall contain required and accurate originator information, and full beneficiary information, that is fully traceable within the beneficiary country; and the financial institution shall be required to include the originator’s account number or unique transaction reference number.
- Financial institutions shall ensure that all cross-border wire transfers less than AED 3,500 are always accompanied by the data in Clause (1) of this Article, without the need to verify the accuracy of the data referred to, unless there are suspicions about committing the Crime.
- For domestic wire transfers, the ordering financial institution shall ensure that the information accompanying the wire transfer includes originator information as indicated in Clause (1) of this Article, unless this information can be made available to the beneficiary financial institution and competent authorities by other means.
- Where the information accompanying the domestic wire transfer can be made available to the beneficiary financial institution and competent authorities by other means, the ordering financial institution shall be only required to include the account number or a unique transaction reference number, provided that this number or identifier will permit the transaction to be traced back to the originator or the beneficiary. The ordering financial institution shall make the information available within three business days of receiving the request either from the beneficiary financial institution or from competent authorities.
- Financial institutions shall not carry out wire transfers if they fail to comply with the conditions set out in this article.
- Ordering financial institutions shall keep all information about the originator and the beneficiary collected in accordance with the provisions of Article (24) of this Decision.
- Financial Institutions shall ensure that all international wire transfers equal to or more than (AED 3.500) are always accompanied by the following data:
Article (28)
- An intermediary financial institution shall ensure that all originator and beneficiary information that accompanies a wire transfer is retained with it for cross-border wire transfers.
- Where technical limitations prevent the required originator or beneficiary information accompanying a cross-border wire transfer from remaining with a related domestic wire transfer, the Intermediary Financial Institution shall keep a record of all the information received from the ordering financial institution or another cross-border Intermediary Financial Institution, in accordance with the provisions of Article (24) of the present Decision.
- Intermediary Financial Institutions shall take reasonable measures, which are consistent with straight-through processing, to identify cross-border wire transfers that lack required originator information or required beneficiary information and shall have risk-based policies and procedures for determining when to execute, reject, or suspend a wire transfer; and the appropriate follow-up action.
- An intermediary financial institution shall ensure that all originator and beneficiary information that accompanies a wire transfer is retained with it for cross-border wire transfers.
Article (29)
- Beneficiary Financial Institutions shall take reasonable measures, to identify cross-border wire transfers that lack required originator information or required beneficiary information, which may include real-time monitoring where feasible or post-event monitoring.
- For cross-border wire transfers of AED 3,500 or more, a Beneficiary Financial Institution shall verify the identity of the beneficiary, if the identity has not been previously verified.
- Beneficiary Financial Institutions shall have risk-based policies and procedures determining when to execute, reject, or suspend a wire transfer lacking required originator or required beneficiary information; and for determining the appropriate follow-up action.
- Beneficiary Financial Institutions shall maintain records of all required originator and required beneficiary information collected, in accordance with the provisions of Article (24) of this Decision.
- Beneficiary Financial Institutions shall take reasonable measures, to identify cross-border wire transfers that lack required originator information or required beneficiary information, which may include real-time monitoring where feasible or post-event monitoring.
Article (30)
- Providers of Money or Value Transfer Services shall comply with all of the relevant requirements of Articles (27), (28), and (29) of this Decision, whether they operate directly or through their agents.
- In the case of a provider of money or value transfer services that controls both the ordering and the beneficiary side of a cross-border wire transfer, the provider of money or value transfer services shall:
- Take into account all information from both the ordering and beneficiary sides in order to determine whether an STR is to be filed; and
- If it is decided to file STR regarding the Transaction, the STR shall be sent to the Financial Intelligence Unit in the relevant country, attaching all relevant transaction information.
- Take into account all information from both the ordering and beneficiary sides in order to determine whether an STR is to be filed; and
- Providers of Money or Value Transfer Services shall comply with all of the relevant requirements of Articles (27), (28), and (29) of this Decision, whether they operate directly or through their agents.
Section 4 Financial Group
Article (31)
The financial groups shall implement anti-crime programs at the group level, that shall be applicable to all branches and subsidiaries in which the group has a majority. In addition, these programs include the following, in addition to the measures stipulated in Article no. (20) of this Resolution:
- Information exchange policies and procedures required for Client due diligence and crime risk management purposes.
- Provision of information related to Clients, accounts and operations from branches and subsidiaries to the AML/CFT officials at the level of the financial group, when necessary. This shall be for the purposes of countering crime, including information on analyzing operations or activities that seem unusual or suspicious, in addition to suspicious transaction reports, their basic information, or an evidence on filing a report of a suspicious transaction. In all cases, branches and subsidiaries are provided with this information when appropriate and necessary to risk management.
- Provision of adequate guarantees on confidentiality and use of exchanged information.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)Financial Groups shall implement group-wide programs with respect to combating the Crime. Such programs shall be applicable and appropriate to all its branches and majority-owned subsidiaries. In addition to the measures mentioned in Article (20) of this Decision, these programs should also include the following:
- Policies and procedures for the exchange of information required for the purposes of CDD and risk management of the Crime;
- The provision of Customer information, accounts, and Transactions from the branches and subsidiaries to the compliance officers at a Financial Group level, whenever necessary for the purpose of combating the Crime.
- Provision of adequate safeguards on the confidentiality and use of the information exchanged.
- Information exchange policies and procedures required for Client due diligence and crime risk management purposes.
Article (32)
- Financial Institutions should ensure that their foreign branches and majority-owned subsidiaries apply Crime-combating measures that are consistent with the requirements of the Decretal-Law and the present Decision when the minimum Crime-combating requirements of the other country are less strict than those applied in the State, to the extent permitted by that other country’s laws and regulations.
- If the other country does not permit the appropriate implementation of measures for combating the Crime that are consistent with the requirements of the Decretal-Law and the present Decision, then Financial Institutions shall take additional measures to manage AML/CFT risks related to their operations abroad and reduce them appropriately, inform the other country of the matter, and abide by the instructions received from the Country in this regard.
- Financial Institutions should ensure that their foreign branches and majority-owned subsidiaries apply Crime-combating measures that are consistent with the requirements of the Decretal-Law and the present Decision when the minimum Crime-combating requirements of the other country are less strict than those applied in the State, to the extent permitted by that other country’s laws and regulations.
Part 3 Requirements of Non-Profitable Organisations
Article (33)
Non-Profit Organisations, in collaboration with the competent Supervisory Authority, shall commit to the following:
- Apply best practices adopted by the competent Supervisory Authority to mitigate their vulnerabilities so that they can protect themselves from being abused for Financing of Terrorism and of Illegal Organisations.
- Put in place clear policies to promote transparency, integrity, and public confidence in its own administration.
- Conduct Transactions through official financial channels, taking into consideration the different capabilities of financial sectors in other countries.
- Apply best practices adopted by the competent Supervisory Authority to mitigate their vulnerabilities so that they can protect themselves from being abused for Financing of Terrorism and of Illegal Organisations.
Part 4 Virtual Asset Service Providers
Part 4 has been added pursuant to Cabinet Resolution No. (24) of 2022.Article no. (33) bis (1)
This article has been added pursuant to Cabinet Resolution No. (24) of 2022.- Every natural or legal person who carries out any of the activities of Virtual Asset Service Providers, provides their products or services or carries out their operations from the state must be licensed, enrolled or registered, as the case may be, by the competent Supervisory Authority.
- The Supervisory Authority on Virtual Asset Service Providers, each according to its competence, may issue the necessary decisions, circulars and procedures for the purposes of adequate organization thereof, taking into account the identified risks in a manner that achieves compliance with the provisions of the Decree-Law and this Resolution.
In all cases, the Supervisory Authority on Virtual Asset Service Providers shall, on its own or in coordination with the concerned authorities, take the necessary measures to determine who carries out any of the activities of the Virtual Asset Service Providers in violation of Clause No. (1) of this Article. It shall also apply the appropriate sanctions against them. These procedures may include the following:
a. Reviewing public and open-source databases to identify relevant ads over the information network or potential business requests by a person who is not licensed, enrolled, nor registered.
b. Establishing feedback channels with Concerned authorities, or communication channels to receive public comments from the public in this regard.
c. Coordinating with the Unit to obtain information available to it such as suspicious transaction reports or the results of other information collection it carried out.
d. Reviewing non-public information, such as information related to the denial, suspension, restriction or revocation of a license, enrollment or registration of virtual asset service provider activities, and any relevant information with law enforcement authorities.
- Subject to the provisions of Chapter (7) of this Resolution, the concerned authorities may, pursuant to the legislation in force in the State and the international agreements to which the State is a party or based on the condition of reciprocity, execute international cooperation requests related to predicate offenses, money laundering crimes, financing of terrorism, or financing of Illegal Organizations related to virtual assets and Virtual Asset Service Providers as expeditiously and effectively as possible. This shall be applied regardless of the nature and difference in the names of the supervisory Authorities or the status of the Virtual Asset Service Providers in other countries.
- Every natural or legal person who carries out any of the activities of Virtual Asset Service Providers, provides their products or services or carries out their operations from the state must be licensed, enrolled or registered, as the case may be, by the competent Supervisory Authority.
Article no. (33) bis (2)
This article has been added pursuant to Cabinet Resolution No. (24) of 2022.Virtual Asset Service Providers must identify, assess, manage and reduce their risks related to money laundering and terrorist financing, as stated in clauses nos. (1) and (2) of Article no. (4) of this Resolution.
Article no. (33) bis (3)
This article has been added pursuant to Cabinet Resolution No. (24) of 2022.Virtual Asset Service Providers must comply with the provisions of Articles nos.(5-9), (12-15/1), (16, 17/1, 18/1, 19-32, 35, 38, 39), and (60) of this Resolution, and consider the following:
- Taking Client Due Diligence (CDD) measures when conducting casual operations equal to or more than (AED 3.500).
- Obtaining and keeping the required transfer information precisely by the Virtual asset service provider, the transfer originator.
This is in addition to requesting the information of the beneficiary of the transfer. It must provide such information to the virtual asset service provider, the beneficiary or the financial institution - if any, immediately and safely. It must also make it available to the competent authorities upon request.
- Obtaining and keeping the required transferor information and the beneficiary precisely by the virtual asset service provider obtains. It must also make it available to the competent authorities upon request.
- All requirements contained in this part of this resolution shall apply to Financial Institutions when they send or receive virtual asset transfers on behalf of the Client.
- Taking Client Due Diligence (CDD) measures when conducting casual operations equal to or more than (AED 3.500).
Chapter 3 Transparency and Beneficial Owner
Part 1 Requirements of Company Registrar and Companies
Article (34)
- The Registrar shall provide information regarding legal persons in the State and make it available to the public as follows:
- The types, different forms and basic features of legal persons
- The processes for the creation of those legal persons
- The processes for obtaining its basic information as stipulated in paragraph (b), Clause (1), of Article (8) of this Decision
- The processes for obtaining information about the Beneficial Owner.
- The types, different forms and basic features of legal persons
- The Registrar shall undertake to maintain and keep the up-to-date basic information defined in paragraph (b), Clause (1), of Article (8) of this Decision, ensure its accuracy and make it available to the public
- Upon registering companies, the Registrar shall commit to receive the data of the Beneficial Owner of the company as stipulated in Clause (1), of Article (9) of this Decision and make sure it remains up to date accurate, and available to the Competent Authorities.
- The Registrar shall provide information regarding legal persons in the State and make it available to the public as follows:
Article (35)
- Companies shall be required to maintain the information set out in paragraph (b), Clause (1) of Article (8) of this Decision and a register of all their shareholders containing the number of shares held by each shareholder and categories of shares, if any, including the voting rights and providing this register to the Registrar after ensuring its accuracy.
- Companies shall undertake to maintain and make available the data mentioned in Clause (1) of Article (9) of this Decision to the Registrar at all times and upon request, update such data within 15 business days upon its amendment or change and ensure to keep this information up-to-date and accurate on an ongoing basis and assist the Registrar in documenting such information if so required.
- Companies shall have one or more natural persons residents of the State and authorised to disclose to the Registrar all information contained in Clauses (1) and (2) of this Article
- Any company established or registered in the State shall be prohibited from issuing share warrants to bearer.
- Companies that permit the issuance of nominee shares in the name of individuals or members of the board of directors shall be required to disclose those shares and the identities of the members of the board of directors to the Registry for the purpose of registering them.
- Companies shall be required to maintain the information set out in paragraph (b), Clause (1) of Article (8) of this Decision and a register of all their shareholders containing the number of shares held by each shareholder and categories of shares, if any, including the voting rights and providing this register to the Registrar after ensuring its accuracy.
Article (36)
The Registrar and the companies, or the administrators or liquidators or any other stakeholder involved in the dissolution of the company, shall maintain records and all information as mentioned in Article (34) and Article (35) for at least five years from the date in which the company is dissolved or otherwise ceased to exist.
Part 2 Requirements of Legal Arrangements
Article (37)
- Trustees in legal arrangements shall keep information about the real beneficial owner as stated in clause no. (2) of Article no. (9) of this Resolution.
- Trustees in legal arrangements must keep basic information about supervised intermediaries and service providers, including investment advisors, managers, accountants, and tax advisors.
- Trustees in legal arrangements must disclose their status to Financial Institutions, Designated Non-Financial Businesses and Professions, and Virtual Asset Service Providers, when they establish a business relationship or carry out an occasional transaction that exceeds the specified limit under the provisions of this resolution. They must also provide them with information related to the beneficial owner and the assets that will be kept or managed under the terms of the business relationship, if requested.
- The information mentioned in clauses nos. (1) and (2) of this Article shall be accurately kept and updated within fifteen (15) working days upon any amendment or variation therein. The representatives of the legal arrangements shall retain such information for a period of five (5) years from the date of termination of their dealings with the legal arrangement.
- The concerned authorities, in particular law enforcement authorities, may request and obtain without delay the information kept by trustees, Financial Institutions, Designated Non-Financial Business or Professions or virtual assets services providers related to the following:
- The real beneficial owner of legal arrangements.
- place of residence of the Trustee.
- The Funds held or managed by the Financial Institution or the Designated Non-Financial Business in respect of any Trustee with whom they have a Business Relationship or for whose account they perform a casual transaction.
- The real beneficial owner of legal arrangements.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)- The Trustees in Legal arrangements are required to information about the Beneficial Owner as prescribed in Clause (Error! Reference source not found.) of Article (9) of this Decision.
- The Trustees in Legal Arrangements are required to maintain basic information relating to intermediaries, who are subject to supervision, and service providers, including consultants, investors, directors, accountants and tax advisors.
- The information mentioned in Clauses (1) and (2) of this Article shall be maintained accurately and updated within 15 days if it is amended or changed and legal arrangement representatives shall be required to maintain this information for at least five years from the date of the end of their involvement with the legal arrangement.
- The Competent Authorities, and in particular Law Enforcement Authorities, shall request and obtain information held by trustees, Financial Institutions, or DNFBPs, without delay, relating to the following:
- The Beneficial Ownership of legal arrangements
- The residence of the Trustee
- The funds that are held or managed by the Financial Institution or DNFBP in relation to any trustees with which they have a Business Relationship, or for which they undertake an occasional Transaction.
- The Beneficial Ownership of legal arrangements
- Trustees in legal arrangements shall keep information about the real beneficial owner as stated in clause no. (2) of Article no. (9) of this Resolution.
Part 3 Prohibition of Invocation of Banking, Professional or Contractual Secrecy
Article (38)
It is prohibited to invoke banking, professional or contractual secrecy as a pretext to prevent application of the provisions of the Decretal-Law and this Decision in the following cases:
- Exchange of information among Financial Institutions whenever it is related to Correspondent Banking or Wire Transfers and the reliance on regulated third party relationships in accordance with Articles (19), (25), and (27) to (30) of this Decision.
- Exchange of information among Competent Authorities at the domestic or international level in relation to the combating of the Crime.
- Exchange of information among Financial Institutions whenever it is related to Correspondent Banking or Wire Transfers and the reliance on regulated third party relationships in accordance with Articles (19), (25), and (27) to (30) of this Decision.
Part 4 Confidentiality of information
Article (39)
- Any person who obtains information related to a suspicious transaction or any of the crimes stipulated in the Decretal-Law shall be bound by its confidentiality and not disclosed except to the extent necessary for its use in investigations, prosecutions or cases in violation of the provisions of the Decretal-Law and this Decision.
- In all cases, it is not permissible to contact the Customer directly or indirectly to notify him of the actions taken, except at the written request of the competent Supervisory Authority.
- Any person who obtains information related to a suspicious transaction or any of the crimes stipulated in the Decretal-Law shall be bound by its confidentiality and not disclosed except to the extent necessary for its use in investigations, prosecutions or cases in violation of the provisions of the Decretal-Law and this Decision.
Chapter 4 Financial Intelligence Unit
Section 1 Independence of the FIU
Article (40)
- The FIU shall be operationally independent in order to carry out its functions effectively, and the Central Bank shall provide it with the required technical, financial and human resources.
- The main headquarter for the FIU shall be the capital of the State and it may open branches within the Central Bank’s branches in the Emirates of the State.
- The FIU shall operate as national centre to receive STR’s and other information related to the Crime.
- The FIU shall be operationally independent in order to carry out its functions effectively, and the Central Bank shall provide it with the required technical, financial and human resources.
Section 2 Powers of the FIU
Article (41)
The FIU shall have the following powers:
- Putting in place the FIU’s departments and internal regulations for approval by the Central Bank’s Board of Directors. The internal regulations shall include procedures to ensure the competency and integrity of its employees and the awareness of their responsibilities in dealing with confidential information.
- Establishing a database or special register to hold any information it has available and securing this information by establishing rules that govern information security and confidentiality, including procedures for processing, storing, disseminating and setting procedures to ensure limited access to the FIU’s facilities, information and technical systems and to the review or disclosure of information, except by those authorised to do so.
- Providing courses and programs to train and develop the employees working in it and any other authority, be it inside or outside the State.
- Preparing studies, research and statistics related to the Crime, and following up on any studies, research or statistics conducted domestically or internationally in this regard.
- Preparing annual reports about its Crime-combatting activities that include specifically general analysis of STRs and notifications received as well as activities and trends of the Crime, and preparing a brief of this report for dissemination purposes.
- Putting in place the FIU’s departments and internal regulations for approval by the Central Bank’s Board of Directors. The internal regulations shall include procedures to ensure the competency and integrity of its employees and the awareness of their responsibilities in dealing with confidential information.
Article (42)
In the course of performing its duties as regards suspicious transaction reports, the Unit shall have competence to carry out the following:
- Receive, study and analyse reports from Financial Institutions, Designated Non-Financial Businesses and Virtual Asset Service Providers according to the models approved thereby, and save the same in its database.
- Request Financial Institutions, Designated Non-Financial Businesses, Virtual Asset Service Providers and the Competent Authorities to provide it with any additional information or documents relating to the reports and information it has received and other information it deems necessary for the performance of its functions, including information on customs reforms, on the date and the form specified by the Unit.
- Analyse reports and information available thereto as follows:
- Conduct an operational analysis using available information and data that can be obtained to identify specific targets such as persons, money or criminal networks, track the course of specific activities or Operations, and identify linkages between these objectives, activities or Operations and the potential Proceeds of the Crime.
- Conduct a strategic analysis using available information and information that can be obtained, including data provided by the Competent Authorities, to identify the trends and patterns of the Crime.
- Conduct an operational analysis using available information and data that can be obtained to identify specific targets such as persons, money or criminal networks, track the course of specific activities or Operations, and identify linkages between these objectives, activities or Operations and the potential Proceeds of the Crime.
- Providing Financial Institutions, Designated Non-Financial Businesses and Professions and Virtual Asset Service Providers with the results of the analysis of the information provided on the reports received by the Unit, in order to enhance the effectiveness of the implementation of procedures to confront crime and detect suspicious transactions.
- Cooperating and coordinating with the Supervisory Authorities by referring the results of the analyzes they conduct related to the quality of the received reports, in order to ensure the compliance of Financial Institutions, Designated Non-Financial Businesses and Professions, and Virtual Asset Service Providers with the procedures for confronting crime.
- Refer the data related to the reports and the results of the analysis it conducts and other relevant information to Law Enforcement Authorities, when there are sufficient grounds to suspect their connection with the Crime, so as to take the necessary action in their respect.
- Provide judicial and Law Enforcement Authorities with Crime-related information and other information that they can be obtain from Financial Intelligence Units in other countries automatically or upon request.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)The FIU shall be responsible for carrying out its duties with regards to STRs as follows:
- Receiving STRs relating to the Crime from Financial Institutions and DNFBPs on the FIU’s approved templates, then studying, analysing and storing them in its database.
- Requesting Financial Institutions, DNFBPs, and Competent Authorities to provide any additional information and documents relating to the STRs and information received, and any other information that it might deem necessary to perform its duties, including information relating to customs’ disclosures, in the time and form specified by the FIU
- Analysing available reports and information as follows:
- Operational analysis by using available and obtainable information, to identify specific targets, such as persons, funds, or criminal networks, track activities or specific Transactions, and determine the links between those targets, activities or transactions and potential proceeds of the Crime.
- Strategic analysis by using available and obtainable information, including data provided by Competent Authorities, to identify trends and patterns of the Crime.
- Operational analysis by using available and obtainable information, to identify specific targets, such as persons, funds, or criminal networks, track activities or specific Transactions, and determine the links between those targets, activities or transactions and potential proceeds of the Crime.
- Providing the Financial Institutions and DNFBPs with the analysis results of the information provided in the reports received by the FIU in order to enhance the effectiveness of the measures for combating the Crime and detecting STRs.
- Cooperating and coordinating with the Supervisory Authorities by disseminating the outcomes of its own analysis, specifically with respect to the quality of STRs, to ensure the compliance of Financial Institutions and DNFBPs with the procedures for combating the Crime
- Sending the data relating to the reports, the outcomes of its analyses and any other relevant data to Law Enforcement Authorities, when there are sufficient grounds to suspect its connection to the Crime, to take required actions in that regard.
- Providing to judiciary authorities and Law Enforcement Authorities information related to the Crime and information it can obtain from foreign FIUs, spontaneously or upon request.
- Receive, study and analyse reports from Financial Institutions, Designated Non-Financial Businesses and Virtual Asset Service Providers according to the models approved thereby, and save the same in its database.
Article (43)
The FIU shall be responsible for carrying out its duties at the international level as follows:
- Exchanging information with its FIU counterparts in other countries on STRs or any other information the FIU has the power to obtain or access, whether directly or indirectly, as per the international agreements to which the State is a party or any memorandums of understanding the FIU has entered into with FIU counterparts to regulate its cooperation with them or on the condition of reciprocity.
- Reporting to its FIU counterparts the outcomes of using the submitted information and analysis conducted based on that information.
- The information specified in Clauses (1) and (2) of this Article may not be used except for Crime-combatting purposes and may not be disclosed to any third party without the FIU’s approval.
- Following up on the developments relating to Money Laundering and Terrorism Financing crimes through the relevant regional and international organisations and bodies and participating in related meetings.
- Following up with the requirements of the Egmont Group, as well as participating and attending its meetings as a member of the group.
- Exchanging information with its FIU counterparts in other countries on STRs or any other information the FIU has the power to obtain or access, whether directly or indirectly, as per the international agreements to which the State is a party or any memorandums of understanding the FIU has entered into with FIU counterparts to regulate its cooperation with them or on the condition of reciprocity.
Chapter 5 Supervisory Authorities
Section 1 The Supervisory Authority for Financial Institutions, Designated Non-Financial Businesses and Professions and Virtual Asset Service Providers
This title has been amended by Cabinet Resolution No. (24) of 2022.Article (44)
The Regulatory Authorities of Financial Institutions, Designated Non-Financial Businesses and Professions and Virtual Asset Service Providers, each according to its competence, shall undertake the tasks of supervision, control and follow-up to ensure compliance with the provisions stipulated in the Decree-Law, this Resolution, the supervisory decisions and any other relevant decisions. They shall also be concerned with the following:
- The identification, evaluation and updating of the potential risk of the crime in legal persons, including Financial Institutions, Designated Non-Financial Businesses and Professions, virtual assets activities and Virtual Asset Service Providers activities.
- The application of a risk-based approach to ensure that the money laundering and terrorist financing prevention or mitigation measures are commensurate with the identified risks.
- The development of instructions, systems and models to counter crime for those under its control when necessary.
- The development of the policies, procedures and controls necessary to verify the compliance of those under its control with the provisions of the Decree-Law, this resolution and any other legislation related to confronting crime in the state, and requesting information related to the implementation of this commitment.
- The development of merit and eligibility regulations, rules and standards and applying them to anyone who seeks to own, control, participate in the management or operation of Financial Institutions, Designated Non-Financial Business or Professions or virtual assets services providers, directly or indirectly, or who is the beneficial owner thereof.
- Office and field supervision and inspection of Financial Institutions, Designated Non-Financial Businesses and Professions, and Virtual Asset Service Providers on the basis of a risk-based approach.
- Determining the periodicity of the supervision and inspection of Financial Institutions, financial groups, Designated Non-Financial Businesses and Professions and Virtual Asset Service Providers based on the following:
- National Risk Assessment
- The distinctive features of Financial Institutions, financial groups, Designated Non-Financial Businesses and Professions and Virtual Asset Service Providers, in terms of their diversity, size and degree of freedom of disposal granted to them according to the risk-based approach.
- Crime risks and understanding them and the policies, internal controls and procedures applied by Financial Institutions, financial groups, Designated Non-Financial businesses or Professions or Virtual Asset Service Providers, as defined in the Supervisory Authority's assessment of their respective risk structure.
- National Risk Assessment
- Taking all necessary measures to ensure full compliance with the Financial Institutions, Designated Non-Financial Businesses and Professions and Virtual Asset Service Providers by implementing the Security Council resolutions relating to the prevention and suppression of terrorism and its financing and the prevention, suppression and cessation of the proliferation of weapons of mass destruction (WMD) and their financing. This is in addition to other relevant resolutions, through field visits and continuous follow-up, and imposing appropriate administrative penalties when violating or failing to apply the instructions.
- Verifying that the establishments under its control adopt and apply the controls, procedures and measures prescribed in accordance with the provisions of the Decree-Law and this resolution, and implementing them in its foreign branches and subsidiaries in which it owns the majority share to the extent permitted by the regulations of the state in which these branches and companies are located.
- Verify the extent to which the Financial Institutions subject to the international basic principles of financial control are subject to regulation and control in accordance with those principles. Such principles shall include the application of consolidated control at the level of the financial group for AML/CFT purposes. This is in addition to ascertain the extent to which they are subject to regulation, control or follow-up, with regard to other Financial Institutions, in accordance with the degree of ML/FT risks.
- Reviewing the assessment of the Establishment and the financial group of the crime risk structure, including the risk of non-compliance, periodically or when there are significant developments in the management of the Establishment or the financial group and its operations.
- Establishing adequate controls and procedures to ensure that Financial Institutions, Designated Non-Financial Businesses and Professions, and Virtual Asset Service Providers are informed of the Committee's decisions related to the following:
- Enhanced due diligence and countermeasures identified by the Committee.
- Any concerns related to weaknesses in AML/CFT systems in other countries.
- Any other resolutions issued by the Committee.
- Enhanced due diligence and countermeasures identified by the Committee.
- Providing those under its control with guidance and feedback to enhance the effectiveness of its implementation of anti-crime measures.
- Maintaining an updated list of the names and data of compliance officials of the establishments under its control and informing the unit of it. In addition, it has the right to oblige those establishments to obtain its prior approval before appointing compliance officials.
- Organizing awareness programs and campaigns on anti-crime.
- Issuing decisions to impose administrative sanctions in accordance with the provisions of the Decree-Law, this Resolution, the supervisory decisions and any other relevant decisions and the mechanism of filing complaints against them.
- Keeping statistics on the measures taken and the sanctions imposed.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)The Supervisory Authorities, each in accordance with its specialisations, shall assume the functions of supervision, monitoring and follow-up to ensure compliance with the provisions of the Decretal-Law and this Decision and shall be specialised in the following:
- Conducting a risk assessment for any potential occurrence of the Crime in legal persons, including Financial Institutions and DNFBPs.
- Putting in place the Crime-Combating regulations, instructions and forms for the entities subject to their supervision, when necessary.
- Putting in place the required procedures and controls to assess the compliance of supervised institutions with the provisions of the Decretal-Law and this Decision and any other legislation related to combating the Crime in the State, as well as to request the information relating to such compliance.
- Setting and applying the regulations, controls, standards of merit to anyone who seeks to acquire, control, participate in management or operation, whether directly or indirectly, or to be the beneficiary of Financial Institutions and DNFBPs.
- Conducting onsite and offsite supervision and inspections over Financial Institutions and DNFBPs.
- Determining the frequency of supervision and inspection over Financial Institutions, Financial Groups, and DNFBPs based on the following:
- National Risk Assessment
- Distinctive characteristics of Financial Institutions, Financial Groups and DNFBPs in terms of their diversities, numbers and the degree of discretion provided to them under the risk-based approach.
- Risks of the Crime as well as internal policies, controls and procedures associated with Financial Institutions, Financial Groups, or DNFBPs as identified by the Supervisory Authority’s assessment of each’s risk profile.
- National Risk Assessment
- Undertaking all measures to ensure full compliance of the Financial Institutions and DNFBPs in implementing Security Council Resolutions relating to the prevention and suppression of terrorism and Terrorism Financing, and the prevention and suppression of the proliferation of weapons of mass destruction and its financing, and other related decisions, by conducting onsite visits and on-going monitoring, and imposing appropriate administrative sanctions when there is a violation or shortcoming in implementing the instructions.
- Ensuring that the prescribed measures are adopted by the supervised institutions in accordance with the provisions of the Decretal-Law and this Decision, and that these measures are implemented in their foreign branches and majority-owned subsidiaries to the extent permitted by the laws of the country, where those branches and subsidiaries exist.
- Periodically reviewing the assessment of the Crime risk profile of a Financial Institution and Financial Group (including the risks of non-compliance), and when there are major events or developments in the management and operations of the Financial Institution or Group.
- Ensuring the compliance of Financial Institutions and DNFBPs subject to their supervision in implementing enhanced CDD measures on Customers and ongoing monitoring of the business relationship related to High-Risk Countries.
- Providing Financial Institutions and DNFBPs with guidelines and feedback to enhance the effectiveness of implementation of the Crime-combatting measures.
- Maintaining an up-to-date list of the names and data of compliance officers of the institutions under their Supervision, and notifying the FIU thereof; and requiring those institutions to obtain their prior consent before appointing their compliance officers.
- Conducting programs and outreach campaigns on combating the Crime.
- Issuing decisions of imposing administrative sanctions in accordance with the provisions of the Decretal-Law and the present Decision, and the mechanism for submitting relevant grievance.
- Maintaining statistics about the measures taken and sanctions imposed.
- The identification, evaluation and updating of the potential risk of the crime in legal persons, including Financial Institutions, Designated Non-Financial Businesses and Professions, virtual assets activities and Virtual Asset Service Providers activities.
Section 2 Supervisory Authority for Non-Profit Organisations
Article (45)
The Competent Supervisory Authority for NPOs shall commit to the following:
- Obtaining, in a timely manner, all information available with all Competent Authorities regarding NPO activities for the purpose of determining the size, features and types of NPOs, and identifying the threats posed against them by terrorism organisations, and the extent to which they are exposed to the risk of being misused for supporting Financing of Terrorism and Financing of Illegal Organisations, and then taking all appropriate and effective measures to combat these identified risks and reviewing them on a periodic basis to ensure their adequacy.
- Reviewing the relevance and adequacy of legislation relating to NPOs to stop their misuse for supporting the Financing of Terrorism and of Illegal Organisations, and working to improve them when necessary.
- Periodically reassessing NPOs by reviewing updated information on their potential vulnerabilities, which may be exploited in support of Financing of Terrorism.
- Promoting and conducting awareness outreach and educational programs in order to raise awareness of NPOs and their donators on their potential vulnerabilities, which may expose them to risks of being misused for supporting and financing of Terrorism, and measures that can be taken by NPOs to protect themselves from such risks.
- Supervising and monitoring NPOs using a risk-based approach to prevent their misuse in the Support and Financing of Terrorism and ensure compliance with their requirements.
- Cooperating, coordinating and exchanging information at the local level with Competent Authorities that hold relevant information on NPOs.
- Possessing experience in the field of investigations and the ability to examine NPOs that are suspected of being misused for supporting and financing of terrorism.
- Fully reviewing the information relating to the administration and management of any NPO, including financial information and information relating to its programs.
- Establishing mechanisms to ensure the prompt exchange of information with Competent Authorities for the purpose of taking preventive measures or investigative action when there is suspicion or reasonable grounds to suspect that the NPO is:
- A front for the raising of funds on behalf of a terrorist organisation.
- Being exploited as a conduit for the Financing of Terrorism or for the evasion of asset freezing measures or any other form of terrorism support.
- Concealing or disguising the flow of funds intended for legitimate purposes, but redirected for the benefit of terrorists or terrorist organisations.
- A front for the raising of funds on behalf of a terrorist organisation.
- Determining the appropriate points of contact and procedures required to respond to international requests for information regarding NPOs suspected of Financing of Terrorism or is being exploited for the Financing of Terrorism or other forms of terrorism support.
- Obtaining, in a timely manner, all information available with all Competent Authorities regarding NPO activities for the purpose of determining the size, features and types of NPOs, and identifying the threats posed against them by terrorism organisations, and the extent to which they are exposed to the risk of being misused for supporting Financing of Terrorism and Financing of Illegal Organisations, and then taking all appropriate and effective measures to combat these identified risks and reviewing them on a periodic basis to ensure their adequacy.
Chapter 6 Provisional Measures and Investigative Procedures
Section 1 Provisional Measures
Article (46)
- The Governor, or whoever is acting in his place, shall order the Freezing of funds, which are suspected to be linked to the Crime, with Financial Institutions licensed by the Central Bank for a period of no more than (7) seven working days, in the case of the FIU’s requests based on its analysis of STRs and other information received.
- The FIU shall, in the event of taking the decision mentioned in Clause (1) of this Article, do the following:
- Notify the concerned Financial Institution to perform the Freezing order without prior notice to the owner of the funds.
- Notify the public prosecutor, in case the Governor requests extending the Freezing order, including the justifications of such extension.
- Notify the concerned Financial Institution to perform the Freezing order without prior notice to the owner of the funds.
- The FIU, after presenting to the Governor, shall notify the concerned Financial Institution of the cancelation of the Freezing order in case the public prosecutor refuses the extension or after expiry of the period specified in Clause (1) of this Article without receiving a response from the public prosecutor
- The Financial Institution, which holds the frozen funds, shall notify the owner of the frozen funds of the Freezing order and its sources, and shall request the owner to provide the required documents that prove the legitimacy of the source of these funds and refer these documents to the FIU to take the required actions.
- The Governor shall submit a proposal to the public prosecutor to cancel the extension of the Freezing order once there are no grounds to such freeze in order for the public prosecutor to take actions as he deems appropriate.
- The fund freezing orders shall not be executed by Financial Institutions licensed by the Central Bank unless they are issued by it.
- The Governor, or whoever is acting in his place, shall order the Freezing of funds, which are suspected to be linked to the Crime, with Financial Institutions licensed by the Central Bank for a period of no more than (7) seven working days, in the case of the FIU’s requests based on its analysis of STRs and other information received.
Article (47)
- The Public Prosecution and the competent court shall, as the case may be, order the identification, tracing, and valuation of the Funds, Proceeds and Means under suspicion, or their equivalent value, or order their Seizing or Freezing, if they were the result of or linked to the Crime, and that is without prior notice to the owner, and shall issue a travel ban for the owner until the completion of the investigation or trial.
- The Public Prosecution or the competent court shall, as the case may be and when deemed necessary, take decisions to prevent the dealing with or disposing of such Funds, Proceeds or Means, and take the necessary measures to prevent any action intended to evade the Freezing and Seizing order issued in that regard, without violating the rights of bona fide third parties.
- Any interested party shall have the right to contest the public prosecution’s Freezing or Seizing decision before the competent court of first instance, which is located within the jurisdiction of the order public, or the competent court specialised in criminal claims.
- The contest shall be submitted as a report to the competent court. The president of the court shall, then, schedule a hearing session with the knowledge of the defendant, and the public prosecution shall be required to lodge a memorandum with its opinion on the defendant’s grievance. The court then issues its final decision within a period of no more than 14 working days as of the date of submission of the appeal.
- The decision to dismiss the contest request is not subject to appeal; if the contest was rejected, it is not permissible to lodge a new contest except after a duration of three months from the date of rejecting the contest, unless a serious reason occurs before the period passes.
- The Public Prosecution and the competent court shall, as the case may be, order the identification, tracing, and valuation of the Funds, Proceeds and Means under suspicion, or their equivalent value, or order their Seizing or Freezing, if they were the result of or linked to the Crime, and that is without prior notice to the owner, and shall issue a travel ban for the owner until the completion of the investigation or trial.
Article (48)
The public prosecution and the competent court shall, as the case may be, appoint whomever they deem suitable to manage the seized and frozen Funds, Proceeds and Means or those subject to Confiscation, and permit them to dispose or sell the Funds, Proceeds and Means in public auction, even before the issuance of the verdict, if necessary, if they are concerned about their depreciation or devaluation over time. The amount of the sale shall be deposited in the State’s treasury in the event of a final verdict of conviction. Such funds shall remain within the limits of their value for any rights legitimately determined to any bona fide third parties.
Section 2 Investigation Procedures
Article (49)
- The public prosecution and Law Enforcement Authorities shall, when launching an investigation and collecting evidence for a Predicate Offense, when necessary, take into consideration the extent to which the financial aspects of the criminal activity are connected with Money Laundering, Financing of Terrorism, or the Financing of Illegal Organisations, in order to determine the scope of the crime, identify and track proceeds and any other funds that may be subject to confiscation and strengthen evidence of the crime.
- The public prosecution shall request the opinion of the FIU on the notifications received in relation to Money Laundering, Financing of Terrorism or Financing of Illegal Organisations cases.
- Law Enforcement Authorities shall be responsible for receiving, and following up on, the results of STR analysis from the FIU and for gathering the related evidence.
- The public prosecution and Law Enforcement Authorities shall promptly identify, trace and seize Funds, Proceeds and Means that might be subject to Confiscation and linked to the Crime.
- Law Enforcement Authorities shall obtain the information directly from Competent Authorities, even if it is subject to banking secrecy or professional confidentiality, as they deem fit so they can perform their duties in detecting the Crime or its perpetrator(s) and collecting evidence about them, and the authority, who is the recipient of the information request, shall execute the request without delay.
- The public prosecution and Law Enforcement Authorities shall, when launching an investigation and collecting evidence for a Predicate Offense, when necessary, take into consideration the extent to which the financial aspects of the criminal activity are connected with Money Laundering, Financing of Terrorism, or the Financing of Illegal Organisations, in order to determine the scope of the crime, identify and track proceeds and any other funds that may be subject to confiscation and strengthen evidence of the crime.
Chapter 7 International Cooperation
Section 1 General Provisions for International Cooperation
Article (50)
Competent Authorities, for the purpose of implementation of International Cooperation requests on the Crime, to conclude, negotiate and sign agreements in a timely manner with foreign counterpart authorities, in a manner that does not contradict the legislation in force in the State
Article (51)
The Competent Authorities shall give priority to all requests for international cooperation in criminal matters, particularly those related to the Crime and implement them expeditiously through clear and secure mechanisms and channels. The confidentiality of the information received, subject-matter of such request, shall be observed if so stipulated in the request. Should it be impossible to observe confidentiality, the requesting authority shall be notified thereof.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)Competent authorities shall give priority to all International cooperation requests related to the Crime and implement them expeditiously through clear and secure mechanisms and channels. The confidentiality of the information received shall be subject to the request, if required. If the confidentiality of the information cannot be kept, then the requesting authority shall be informed of the matter.
Article (52)
Within the scope of the implementation of the provisions of the Decree-Law and this Resolution, a request for international cooperation should not be refused on the basis of any of the following:
- The crime includes financial, tax or customs matters.
- Binding confidentiality provisions for Financial Institutions, Designated Non-Financial Businesses and Professions and Virtual Asset Service Providers in a manner that does not violate the legislation in force in the country, unless the relevant information has been obtained in the circumstances in which legal professional privileges or professional confidentiality apply.
- The crime is political or related thereto.
- The request relates to a crime under inquiry or judicial investigation in the state, unless the request will hinder such inquiry or investigations.
- The act on which the request is based does not constitute an offence in the State or has no common features to an offence provided for therein, unless it includes compulsory measures, or pursuant to the legislation in force in the State.
- The criminal act in the State is listed under a different name or description or its elements differ in the requesting State.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)Within the scope of implementing the provisions of the Decretal-Law and this Decision, an International Cooperation request regarding the Crime shall not be rejected on the basis of any of the following:
- The crime involves financial, tax or customs matters.
- Secrecy provisions are binding upon Financial Institutions and DNFBPs, providing that they do not violate the applicable laws in the State, unless the relevant information was obtained under the circumstances where professional legal privileges or professional secrecy apply.
- The crime is political or related to a political crime.
- The request is connected with a crime subject of an ongoing investigation or prosecution in the State, unless the request impedes the investigation or the prosecution.
- The act, on which the assistance is based, does not constitute a crime in the State, or the act does not have similar attributes to a crime set out in the State, unless it involves constraining, coercive measures or its in accordance with the applicable laws in the State.
- The criminal act in the State is listed under a different name or description or that its structure varies from that of the requesting country.
- The crime includes financial, tax or customs matters.
Section 2 Exchange of Information between Competent Authorities and Counterparts
Article (53)
In accordance with the legislation and agreements in force in the State or on the condition of reciprocity, the competent authorities shall:
- Execute requests received from any foreign entity and exchange information on the Crime at the appropriate speed with foreign counterparts, and obtain any other requested information on its behalf, even if such requests change in nature, whether spontaneously or upon request.
- Provide feedback to foreign counterparts on the use of the information obtained and the extent to which it was beneficial, if requested to do so.
- Obtain a declaration or undertaking from the foreign counterpart that international cooperation information will only be used for the intended purpose, unless prior approval has been obtained.
- Use international cooperation information obtained for the intended purpose, unless the foreign counterpart grants its approval for use for another purpose.
- Refuse to provide information in the event that it is not effectively protected by the foreign counterpart requesting international cooperation.
- Execute requests received from any foreign entity and exchange information on the Crime at the appropriate speed with foreign counterparts, and obtain any other requested information on its behalf, even if such requests change in nature, whether spontaneously or upon request.
Article (54)
- The Competent Authorities commit to provide the means for international cooperation with respect to the basic information and Beneficial Owners of companies and legal arrangements, whereby such cooperation shall include the following:
- Facilitating the access of foreign competent authorities to basic information held by the registries of companies and legal arrangements;
- Exchanging information on legal arrangements and the shareholders in companies;
- Using their powers to obtain all the information on Beneficial Owners on behalf of foreign counterparts.
- Facilitating the access of foreign competent authorities to basic information held by the registries of companies and legal arrangements;
- The Competent Authorities shall supervise the implementation quality for the international cooperation requests received from other countries in relation to basic company information and Beneficial Ownership for companies and legal arrangements, as well as the requests for international cooperation relating to determining the location of the Beneficial Owner from companies abroad.
- The Competent Authorities commit to provide the means for international cooperation with respect to the basic information and Beneficial Owners of companies and legal arrangements, whereby such cooperation shall include the following:
Article (55)
In accordance with the legislation in force in the State, and the provisions of the agreements to which they are a party, and on the condition of reciprocity, the Supervisory Authorities of the Financial Institutions shall:
- Exchange information relating to the appropriate Crime that it maintains and which is available to it directly or indirectly, with foreign counterparts, regardless of their nature, and consistent with the relevant international financial control principles relevant to anti money-laundering and combating the financing of terrorism applicable to each of them, including information on:
- The regulatory framework of the financial sectors and the general information related to them.
- Preventive financial control measures such as information related to the activities and works of financial institutions, their real beneficiaries, their management, and information of merit and eligibility.
- Internal policies of financial institutions in the field of combatting the Crime, CDD information of Customers, and of information related to accounts and transactions.
- The regulatory framework of the financial sectors and the general information related to them.
- Obtaining prior approval of the foreign supervisory authority, where the information is required for transmission or use, other than for the intended purpose, and to informing it of the matter in the event of disclosure of such information whenever it is the result of a legal obligation.
- Requesting or facilitating access to information on behalf of the foreign supervisory authority, for the purposes of enhancing supervision on the financial group.
- Exchange information relating to the appropriate Crime that it maintains and which is available to it directly or indirectly, with foreign counterparts, regardless of their nature, and consistent with the relevant international financial control principles relevant to anti money-laundering and combating the financing of terrorism applicable to each of them, including information on:
Article (56)
Without prejudice to the provisions of the treaties and conventions to which the State is a party and subject to reciprocity; and without prejudice to the legislation in force in the State, Law Enforcement Authorities, in coordination with the Competent Authority, may:
- Exchange information held by it, either directly or indirectly, with foreign counterparts for purposes of investigation or collection of inferences relating to Crime, identification and tracking of proceeds and intermediaries.
- Use the powers conferred upon it in accordance with the legislation in force in the State to conduct investigations and obtain information on behalf of the foreign counterpart, and coordinate the formation of bilateral or multilateral teams to conduct joint investigations.
- Exchange information held by it, either directly or indirectly, with foreign counterparts for purposes of investigation or collection of inferences relating to Crime, identification and tracking of proceeds and intermediaries.
Section 3 International Legal Assistance
Article (57)
The competent judicial authority may, at the request of a judicial authority in another State with which the State has a convention in force, or on the condition of reciprocity in acts punishable in accordance with the legislation in force in the State, provide judicial assistance in investigations, trials or procedures related to the offence. Moreover, it may order the following:
- The identification, freezing, seizure or confiscation of funds, proceeds or means resulting from the offence used or attempted to be used in it or its equivalent. As well, if the accused is unknown, refuses his/ her criminal responsibility or in case of the expiry of the penal case, this does not prevent taking these procedures.
- Any other measures that can be applied in accordance with the legislation in force in the country, including providing records kept by Financial Institutions, designated non-financial businesses or professions, Virtual Asset Service Providers or non-profit organizations. Such measures also include inspecting persons and buildings, collecting witness statements, obtaining evidence, and using investigation techniques such as undercover operations, interception of communications, electronic data and information collection, and controlled delivery.
- Extradition and recovery of persons and objects related to the crime in accordance with the legislation in force in the State.
This article has been amended by Cabinet Resolution No. (24) of 2022. You are viewing the latest version. To view the previous version, click the version box below.Version 1(effective from 10/02/2019 to 01/04/2022)Upon request from another judiciary authority in another country, with whom there is a valid agreement in place with the State, or on the basis of reciprocity concerning any acts that are punishable as per the applicable laws in the State, the competent judiciary authority shall provide legal assistance in investigations, trials or measures linked to the Crime and it shall order the following:
- Locating, Freezing, Seizing or Confiscation of Funds, Proceeds or Means that have been used, or intended for use in the Crime, or their equivalent. The death or anonymity of the suspect shall not prevent undertaking such measures.
- Any other measures applicable in accordance with the enforceable laws in the State, including the provision of records maintained by Financial Institutions, DNFBPs or NPOs, the search of persons and buildings, gathering statements from witnesses, collecting evidence, using investigative methods such as Undercover Operations, wiretapping, communications, obtaining electronic data and information and Controlled Delivery.
- Extradition and repatriation of persons and things related to the Crime in accordance with the laws applicable in the State.
- The identification, freezing, seizure or confiscation of funds, proceeds or means resulting from the offence used or attempted to be used in it or its equivalent. As well, if the accused is unknown, refuses his/ her criminal responsibility or in case of the expiry of the penal case, this does not prevent taking these procedures.
Article (58)
It is permitted to recognise any judgement or judicial order that provides for the confiscation of Funds, Proceeds or Means relating to Money Laundering, the Financing of Terrorism or the Financing of Illegal Organisations issued by a competent court or judiciary authority in another country, with whom there is an attested agreement in place with the State.
Article (59)
Taking into consideration the applicable laws in the State, the implementation of the judgement or judicial order mentioned in Article (58) of the present Decision shall not contradict a judgment or order previously issued by a court in the State, there shall not be an ongoing charge in the State regarding the same judgment issued from the requesting country, and the request shall also include the following documents and information:
- An attested copy of the judgment or judicial order for Confiscation along with the law on which it is based, and a statement of the reasons for issuing the confiscation order, if not mentioned in the judgment or the order itself.
- A statement establishing that the sentenced person has been duly summoned and represented, and has been able to defend himself.
- A document confirming that the judgement or judicial order is enforceable and not subject to appeal through ordinary methods.
- Description of the Funds, Proceeds and Means for Confiscation, their estimated value, their potential location and information regarding any persons who might be holding or possessing these funds.
- Statement of the amount to be repatriated from the funds for Confiscation.
- Any information relating to third party rights on the Funds, Proceeds or Means.
- Statement of the procedures undertaken in the requesting country to protect bona fide third parties.
- An attested copy of the judgment or judicial order for Confiscation along with the law on which it is based, and a statement of the reasons for issuing the confiscation order, if not mentioned in the judgment or the order itself.
Section 4 Implementation of the Security Council Resolutions
Article (60)
Every natural or legal person shall immediately comply with the instructions issued by the Competent Authorities in the State concerning the implementation of the resolutions issued by UN Security Council under Chapter VII of the Charter of the United Nations regarding the prevention and suppression of terrorism and Terrorism Financing, and the prevention and suppression of the proliferation of Weapons of Mass Destruction and its financing, and any other related decisions.
Chapter 8 Final Provisions
Article (61)
Any provision that contradicts or violates the provisions of the present Decision shall be considered void.
Article (62)
The present Decision shall come into force as of the date of its issuance and shall be published in the Official Gazette.
Procedures for Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations
CBUAE-BOD 59/4/2019 Effective from 13/7/2019Central Bank Board of Directors’ Decision No. 59/4/2019 Regarding Procedures for Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations
CBUAE-BOD 59/4/2019 Effective from 13/7/2019Chairman of the Board,
Having perused the provisions of the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities;
Circular No. 24/2000 - Regulation concerning Procedures for Anti-Money Laundering and its amendments.
The Central Bank's Board of Directors has issued the following resolution:
Article (1):
Definitions
UAE: United Arab Emirates.
Decree Federal Law: Decree Federal Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations.
Executive Regulation: Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Federal Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations.
The Central Bank: Central Bank of the UAE.
Financial Institution: Anyone, licensed or registered by the Central Bank, who conducts one or several of the financial activities or operations, defined in Article (2) of the Executive Regulation, of or on behalf of a customer.
Article (2):
Financial Institution and its concerned persons must comply with the requirements mentioned in the Decree Federal Law, the Executive Regulation, instructions, guidelines and notices issued by the Central Bank relating to implementation of the Decree Federal Law and the Executive Regulation.
Article (3):
The Central Bank shall supervise and examine, periodically or unexpectedly, without prior notice to the Financial Institution, to verify the Financial Institution’s compliance with the Decree Federal Law, the Executive Regulation, relevant instructions, guidelines and notices issued by the Central Bank and shall identify any violations resulting from the examination.
The Central Bank shall request all information and documents it deems necessary for the purpose of supervision and verification from the Financial Institution or its employees.
Article (4):
Without prejudice to any of the sanctions or measures contained in any other legislation, the Central Bank may, upon the violation by any Financial Institution of any of the provisions referred to in Article (2) of this Decision, impose any of the administrative sanctions specified in the Decree Federal Law.
Article (5):
The violator may appeal against the decision on the violation, in accordance with the procedures prescribed by the Central Bank in this regard.
Article (6):
The Central Bank may publish its administrative sanctions in the various means of publication.
Article (7):
Circular No. 24/2000 - Regulation concerning Procedures for Anti-Money Laundering and its amendments shall be canceled.
Article (8):
This Decision shall be communicated to whomsoever is concerned for implementation, and shall be published in the Official Gazette in both Arabic and English.
Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations Guidelines for Financial Institutions
Effective from 13/7/2023Part I—Overview
1. Introduction
1.1 Purpose and Scope
The purpose of these Anti-Money Laundering and Combating the Financing of Terrorism and the Financing of Illegal Organisations Guidelines for Financial Institutions (FIs) (Guidelines) is to provide guidance and assistance to supervised institutions that are FIs, in order to assist their better understanding and effective performance of their statutory obligations under the legal and regulatory framework in force in the United Arab Emirates (UAE or State).
These Guidelines have been prepared as a joint effort between the Supervisory Authorities of the UAE, and set out the minimum expectations of the Supervisory Authorities regarding the factors that should be taken into consideration by each of the supervised financial institutions which fall under their respective jurisdictions, when identifying, assessing and mitigating the risks of money laundering (ML), the financing of terrorism (FT), and the financing of illegal organisations.
Nothing in these Guidelines is intended to limit or otherwise circumscribe additional or supplementary guidance, circulars, notifications, memoranda, communications, or other forms of guidance or feedback, whether direct or indirect, which may be published on occasion by any of the Supervisory Authorities in respect of the supervised institutions which fall under their respective jurisdictions, or in respect of any specific supervised institution.
Finally, it should be noted that, guidance on the subject of the United Nations Targeted Financial Sanctions (TFS) regime, and the related Cabinet Decision No. (74) of 2020 Regarding Terrorism Lists Regulation and Implementation of UN Security Council Resolutions On the Suppression and Combating of Terrorism, Terrorists Financing & Proliferation of Weapons of Mass Destruction, and Related Resolutions is outside of the scope of these Guidelines.
1.2 Applicability
Unless otherwise noted, these Guidelines apply to all Financial Institutions, and the members of their boards of directors, management and employees, established and/or operating in the territory of the UAE and their respective Financial and Commercial Free Zones, whether they establish or maintain a Business Relationship with a Customer, or engage in any of the financial activities and/or transactions or the trade and/or business activities outlined in Articles (2) and (3) of Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 On Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations.
Specifically, they are applicable to all such natural and legal persons in the following categories:
• Banks, finance companies, exchange houses, money service businesses (including hawaladar or other monetary value transfer services);
• Insurance companies, agencies, and brokers;
• Securities and commodities brokers, dealers, advisors, investment managers;
• Virtual asset service providers (VASPs);
• Other financial institutions not mentioned above.
1.3 Legal Status
Article 44.11 of Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 On Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations charges Supervisory Authorities with “providing Financial Institutions…with guidelines and feedback to enhance the effectiveness of implementation of the Crime-combatting measures.”
As such, these Guidelines do not constitute additional legislation or regulation, and are not intended to set legal, regulatory, or judicial precedent. They are intended rather to be read in conjunction with the relevant laws, cabinet decisions, regulations and regulatory rulings which are currently in force in the UAE and their respective Free Zones, and supervised institutions are reminded that the Guidelines do not replace or supersede any legal or regulatory requirements or statutory obligations. In the event of a discrepancy between these Guidelines and the legal or regulatory frameworks currently in force, the latter will prevail. Specifically, nothing in these Guidelines should be interpreted as providing any explicit or implicit guarantee or assurance that the Supervisory or other Competent Authorities would defer, waive, or refrain from exercising their enforcement, judicial, or punitive powers in the event of a breach of the prevailing laws, regulations, or regulatory rulings.
These Guidelines, and any lists and/or examples provided in them, are not exhaustive and do not set limitations on the measures to be taken by supervised institutions in order to meet their statutory obligations under the legal and regulatory framework currently in force. As such, these Guidelines should not be construed as legal advice or legal interpretation. Supervised institutions should perform their own assessments of the manner in which they should meet their statutory obligations, and they should seek legal or other professional advice if they are unsure of the application of the legal or regulatory frameworks to their particular circumstances.
1.4 Organisation of the Guidelines
These Guidelines are organized into five (5) parts, roughly corresponding to the following major themes:
Part I—Overview (including background information on the UAE’s AML/CFT legislative and strategy framework, and highlights of key provisions of the law and regulations affecting Financial Institutions);
Part II—Identification and Assessment of ML/FT Risks;
Part III—Mitigation of ML/FT Risks;
Part IV—AML/CFT Compliance Administration and Reporting (including guidance on governance, suspicious transaction reporting, and record-keeping);
The various sections and sub-sections of each part are organized according to subject matter. In general, each section or subsection includes references to the articles of the AML-CFT Law and/or the AML-CFT Decision to which it pertains. While it has been kept to a minimum, users may find that there are instances of repetition of some content throughout various sections of the Guidelines. This has been done in order to ensure that each section or sub-section pertaining to a specific subject matter is comprehensive, and to minimize the need for cross-referencing between sections.
In some cases, the requirements or provisions of specific sections of the relevant legal and regulatory frameworks are deemed sufficiently clear with regard to the statutory obligations of supervised institutions such that no additional guidance on those sections is provided for in these Guidelines. In other cases, guidance is provided with regard to subjects which are not covered explicitly in the AML-CFT Law or the AML-CFT Decision, but which are nevertheless addressed either implicitly or by reference to international best practices.
In certain instances in which there are meaningful differences between the relevant legal and regulatory framework currently in force and previous laws or regulations, or in which there are differences in specific regulatory requirements between various Supervisory Authorities, the Guidelines may or may not highlight these differences. In the event of such differences or discrepancies, supervised institutions seeking further clarification on matters related to those sections are invited to contact their relevant Supervisory Authority through the established channels.
It is the Supervisory Authorities’ intention to update or amend these Guidelines from time to time, as and when it is deemed appropriate. Supervised institutions are reminded that these Guidelines are not the only source of guidance on the assessment and management of ML/FT risk, and that other bodies, including international organisations such as FATF,
MENAFATF and other FATF-style regional bodies (FSRBs), the Egmont Group, and others also publish information that may be helpful to them in carrying out their statutory obligations. It is the sole responsibility of supervised institutions to keep apprised and updated at all times regarding the ML/FT risks to which they are exposed, and to maintain appropriate risk identification, assessment, and mitigation programmes, and to ensure their responsible officers, managers and employees are adequately informed and trained on the relevant policies, processes, and procedures.
Text from the AML-CFT and the AML-CFT Decision are quoted, or otherwise summarized or paraphrased, from time to time throughout these Guidelines. For the sake of convenience, unless specifically noted to the contrary, all references in the text to the term “financing of terrorism” also encompass the financing of illegal organisations. In general, capitalized terms in the text of these Guidelines have the meanings provided in the Glossary of Terms (see Appendix 11.1). However, in the event of any inconsistency or discrepancy between the text or definitions provided for in the Law and/or the Cabinet Decision and such quotations, summaries or paraphrases, or such defined terms, the former shall prevail.
2. Overview of the AML/CFT Legal, Regulatory, and National Strategy Frameworks of the United Arab Emirates
2.1 National Legislative and Regulatory Framework
The legal and regulatory structure of the UAE is comprised of a matrix of federal civil, commercial and criminal laws and regulations, together with the various regulatory and Supervisory Authorities responsible for their implementation and enforcement, and various local civil and commercial legislative and regulatory frameworks in the Financial and Commercial Free Zones. As criminal legislation is under federal jurisdiction throughout the State, including the Financial and Commercial Free Zones, the crimes of money laundering, the financing of terrorism, and the financing of illegal organisations are covered under federal criminal statutes and the federal penal code. Likewise, federal legislation and implementing regulations on the combating of these crimes are in force throughout the UAE, including the Financial and Commercial Free Zones. Their implementation and enforcement are the responsibility of the relevant regulatory and Supervisory Authorities in either the federal or local jurisdictions.
The principal AML/CFT legislation within the State is Federal Decree-Law No. (20) of 2018 On Anti-Money Laundering and Combating the Financing of Terrorism and Financing of Illegal Organisations (the “AML-CFT Law” or “the Law”) and implementing regulation, Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 On Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations (the “AML-CFT Decision” or “the Cabinet Decision”).
The UAE issued Cabinet UBO Resolution No. 58 of 2020 on the Regulation of the Procedures of the Real Beneficiary (UBO Resolution) which came into effect on 28 August 2020 and replaced Cabinet Resolution No. 34 of 2020 issued earlier this year.
The UBO Resolution introduces the requirement for a beneficial ownership register in the UAE mainland and unifies the minimum disclosure requirements for corporate entities incorporated in the UAE mainland and in the non-financial free zones. Financial free zones (Abu Dhabi Global Market (ADGM) and Dubai International Financial Centre (DIFC) and companies owned by the Federal Government and their subsidiaries are not covered by the UBO Resolution.
2.2 International Legislative and Regulatory Framework
The AML/CFT legislative and regulatory framework of the UAE is part of a larger international AML/CFT legislative and regulatory framework made up of a system of intergovernmental legislative bodies and international and regional regulatory organisations. On the basis of international treaties and conventions in relation to combating money laundering, the financing of terrorism and the prevention and suppression of the proliferation of weapons of mass destruction, intergovernmental legislative bodies create laws at the international level, which participating member countries then transpose into their national counterparts. In parallel, international and regional regulatory organisations develop policies and recommend, assess and monitor the implementation by participating member countries of international regulatory standards in respect of AML/CFT.
Among the major intergovernmental legislative bodies, and international and regional regulatory organisations, with which the government and the Competent Authorities of the State actively collaborate within the sphere of the international AML/CFT framework are:
• The United Nations (UN): The UN is the international organization with the broadest range of membership. Founded in October of 1945, there are currently 191 member states of the UN from throughout the world. The UN actively operates a program to fight money laundering, the Global Programme against Money Laundering (GPML), which is headquartered in Vienna, Austria, is part of the UN Office of Drugs and Crime (UNODC).
• The Financial Action Task Force (FATF): The Financial Action Task Force (FATF) is an intergovernmental body established in 1989, which sets international standards and promotes effective implementation of legal, regulatory and operational measures for combating money laundering, terrorist financing and other related threats to the integrity of the international financial system. FATF also monitors the implementation of its standards, the 40 FATF Recommendations and 11 Immediate Outcomes, by its members and members of FSRBs, ensures that the ‘FATF Methodology’ for assessing technical compliance with the FATF Recommendations and the effectiveness of AML/CFT systems is properly applied.
• The Middle East and North Africa Financial Action Task Force (MENAFATF): Recognizing the FATF 40 Recommendations on Combating Money Laundering and the Financing of Terrorism and Proliferation, and the related UN Conventions and UN Security Council Resolutions, as the worldwide-accepted international standards in the fight against money laundering and the financing of terrorism and proliferation, MENAFATF was established in 2004 as a FATF Style Regional Body (FSRB), for the purpose of fostering co-operation and co-ordination between the countries of the MENA region in establishing an effective system of compliance with those standards. The UAE is one of the founding members of MENAFATF.
• The Egmont Group of Financial Intelligence Units: In 1995, a number of FIUs began working together and formed the Egmont Group of Financial Intelligence Units (Egmont Group) (named for the location of its first meeting at the Egmont-Arenberg Palace in Brussels). The purpose of the group is to provide a forum for FIUs to improve support for each of their national AML/CFT programs and to coordinate AML/CFT initiatives. This support includes expanding and systematizing the exchange of financial intelligence information, improving expertise and capabilities of personnel, and fostering better communication among FIUs through technology, and helping to develop FIUs worldwide.
2.3 AML/CFT National Strategy Framework
Money laundering and the financing of terrorism are crimes that threaten the security, stability and integrity of the global economic and financial system, and of society as a whole. The estimated volume of the proceeds of crime, including the financing of terrorism, that are laundered each year is between 2-5% of global GDP. Yet, by some estimates, the volume of criminal proceeds that are actually seized is in the range of only 2% of the total, while roughly only half of that amount eventually ends up being confiscated by competent judicial authorities. Combating money laundering and the financing of terrorist activities is therefore an urgent priority in the global fight against organised crime.
The UAE is deeply committed to combating money laundering and the financing of terrorism and illegal organisations. To this end, the Competent Authorities have established the appropriate legislative, regulatory and institutional frameworks for the prevention, detection and deterrence of financial crimes, including ML/FT. They also continue to work towards reinforcing the capabilities of the resources committed to these efforts, and towards improving their effectiveness by implementing the internationally accepted AML/CFT standards recommended and promoted by FATF, MENAFATF and the other FSRBs, as well as by the United Nations, the World Bank and the International Monetary Fund (IMF).
As part of these efforts, the Competent Authorities of the UAE have taken a number of substantive actions, including among others:
• Enhancing the federal legislative and regulatory framework, embodied by the introduction of the new AML/CFT Law and Cabinet Decision, which incorporate the FATF standards;
• Conducting the National Risk Assessment (NRA) to identify and assess the ML/FT threats and inherent vulnerabilities to which the country is exposed, as well as to assess its capacity in regard to combating ML/FT at the national level;
• Formulating a National AML/CFT Strategy and Action Plan that incorporate the results of the NRA and which are designed to ensure the effective implementation, supervision, and continuous improvement of a national framework for the combating of ML/FT, as well as to provide the necessary strategic and tactical direction to the country’s public and private sector institutions in this regard.
The National Strategy on Anti-Money Laundering and Countering the Financing of Terrorism of the United Arab Emirates is based on four pillars, each of which is associated with its own strategic priorities. These strategic priorities in turn inform and shape the key initiatives of the country’s National Action Plan on AML/CFT.
The pillars of the National Strategy, together with their strategic priorities are summarised in the table below:
National AML/CFT Strategic Pillars Strategic Priorities Legislative & Regulatory Measures Increase effectiveness and efficiency of legislative and regulatory policies and ensure compliance Transparent Analysis of Intelligence Leverage the use of financial databases and the development of information analysis systems to enhance the transparent analysis and dissemination of financial intelligence information Domestic and International Cooperation & Coordination Promote the efficiency and effectiveness of domestic and international coordination and cooperation with regard to the availability and exchange of information Compliance and Law Enforcement Ensure the effective investigation and prosecution of ML/FT crimes and the timely implementation of TFS The National Committee for Combating Money Laundering and the Financing of Terrorism and Illegal Organisations has identified a number of key drivers of success in achieving the goals of the National AML/CFT Strategy. These include, among other things, ensuring:
• Effective coordination between the Financial Intelligence Unit, Law Enforcement Authorities, Public Prosecutors, Supervisory Authorities, and other Competent Authorities within the country;
• Effective compliance with the laws and regulations governing banking activities and other financial services;
• Awareness by FIs of the relevant ML/FT risks facing the UAE in general, and their sectors in particular, as informed by the results of the NRA, as well as their awareness of their statutory obligations in regard to the management and mitigation of those risks.
The present Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations Guidelines for Financial Institutions are thus intended to advance the efforts of the Committee, the Supervisory Authorities, and the other Competent Authorities of the State in this direction.
3. Highlights of Key Provisions Affecting Financial Institutions
The AML-CFT Law and the AML-CFT Decision contain numerous provisions setting out the rights and obligations of supervised institutions, including Financial Institutions, as well as their senior managers and employees. This section highlights some of the key provisions affecting FIs that are of immediate concern. FIs are reminded that it is their sole responsibility to adhere to all provisions of the AML-CFT Law, the AML-CFT Decision, and all regulatory notices, rulings and circulars affecting them.
3.1 Summary of Minimum Statutory Obligations of Supervised Institutions
The AML-CFT Law and the AML-CFT Decision set out the minimum statutory obligations of supervised institutions as follows:
• To identify, assess, understand risks (AML-CFT Law Article 16.1(a), AML-CFT Decision Article 4.1);
• To define the scope of and take necessary due diligence measures (AML-CFT Law Article 16.1(b), AML-CFT Decision Article 4.1(a) and 2);
• To appoint a compliance officer, with relevant qualification and expertise and in line with the requirements of the relevant Supervisory Authority (AML-CFT Decision Article 21, 44.12);
• To put in place adequate management and information systems, internal controls, policies, procedures to mitigate risks and monitor implementation (AML-CFT Law Article 16.1(d), AML-CFT Decision Article 4.2(a));
• To put in place indicators to identify suspicious transactions (AML-CFT Law Article 15, AML-CFT Decision Article 16);
• To report suspicious activity and cooperate with Competent Authorities (AML-CFT Law Article 9.1, 15, 30, AML-CFT Decision Article 13.2, 17.1, 20.2);
• To promptly apply directives of Competent Authorities for implementing UN Security Council decisions under Chapter 7 of the UN Convention for the Prohibition and Suppression of the FT and Proliferation (AML-CFT Law Article 16.1(e), AML-CFT Decision Article 60);
• To maintain adequate records (AML-CFT Law Article 16.1(f), AML-CFT Decision Article 7.2, 24).
Specific guidance on these and other provisions of the AML-CFT Law and the AML-CFT Decision is provided in the following sections.
3.2 Confidentiality and Data Protection
(AML-CFT Law Article 15; AML-CFT Decision Articles 17.2, 21.2, 31.3, 39)
Financial Institutions are obliged to report to the UAE’s Financial Intelligence Unit (FIU) when they have reasonable grounds to suspect a transaction or funds representing all or some proceeds, or suspicion of their relationship to a Crime (see Section 7, Suspicious Transaction Reporting). In reporting their suspicions, they must maintain confidentiality with regard to both the information being reported and to the act of reporting itself, and make reasonable efforts to ensure the information and data reported are protected from access by any unauthorised person.
It should be noted that the confidentiality requirement does not pertain to communication within the FI or its affiliated group members (foreign branches, subsidiaries, or parent company) for the purpose of sharing information relevant to the identification, prevention or reporting of a Crime. However, under no circumstances are FIs, or their managers or employees, permitted to inform a Customer or the representative of a Business Relationship, either directly or indirectly, that a report has been made, under penalty of sanctions (see Section 3.9, Sanctions against Persons Violating Obligations). This is the so-called “tipping off” requirement. This also extends to any related information that might be provided to the FIU or information that is being requested by the FIU.
FIs are not permitted to object to the statutory reporting of suspicions on the grounds of Customer confidentiality or data privacy, under penalty of sanctions. Moreover, data protection laws include provisions that allow the FI to report to the authorities. (see Section 3.9, Sanctions against Persons Violating Obligations).
3.3 Protection against Liability for Reporting Persons
(AML-CFT Law Article 27; AML-CFT Decision Article 17.3)
The AML-CFT Law and the AML-CFT Decision provide Financial Institutions, as well as their board members, employees and authorised representatives, with protection from any administrative, civil or criminal liability resulting from their good-faith performance of their statutory obligation to report suspicious activity to the FIU. This protection is also applicable if they did not know precisely what the underlying criminal activity was, and regardless of whether illegal activity actually occurred.
3.4 Statutory Prohibitions
(AML-CFT Law Article 16.1(c); AML-CFT Decision Articles 13.1, 14, 35.4, 38)
Financial Institutions are prohibited from the following activities:
• Establishing or maintaining any Customer or Business Relationship, conducting any financial or commercial transactions, keeping any accounts under an anonymous or fictitious name or by pseudonym or number;
• Establishing or maintaining a Business Relationship or executing any transaction in the event they are unable to complete adequate risk-based CDD measures in respect of the Customer for any reason;
• Dealing in any way with Shell Banks, whether to open (correspondent) bank accounts in their names, or to accept funds or deposits from them;
• Invoking banking, professional or contractual secrecy as a pretext for refusing to perform their statutory reporting obligation in regard to suspicious activity;
• Issuing or dealing in bearer shares or bearer share warrants.
3.5 Money Laundering
(AML-CFT Law Articles 2.1-3, 4, 29.3, AML-CFT Decision Article 1)
The AML-CFT Law defines money laundering as engaging in any of the following acts willfully, having knowledge that the funds are the proceeds of a felony or a misdemeanour (i.e., a predicate offence):
• Transferring or moving proceeds or conducting any transaction with the aim of concealing or disguising their Illegal source;
• Concealing or disguising the true nature, source or location of the proceeds as well as the method involving their disposition, movement, ownership of or rights with respect to said proceeds;
• Acquiring, possessing or using proceeds upon receipt;
• Assisting the perpetrator of the predicate offense to escape punishment.
Both the AML-CFT Law and the AML-CFT Decision define “funds” in a very broad sense as “assets in whatever form, whether tangible, intangible, movable or immovable including national currency, foreign currencies, documents or notes evidencing the ownership of those assets or associated rights in any forms including electronic or digital forms or any interests, profits or income originating or earned from these assets.” They likewise define “proceeds” as “funds generated directly or indirectly from the commitment of any crime or felony including profits, privileges, and economic interests, or any similar funds converted wholly or partly into other funds.”
Therefore, in order to be considered money laundering, it is not necessary for any of the above-stipulated acts to involve only money or monetary instruments per se, but any number of tangible or intangible assets such as, but not limited to:
• Funds bank or other financial accounts, including so-called virtual or crypto currencies;
• Financial instruments or securities, such as shares, bonds, notes, commercial paper, promissory notes, IOUs, share warrants, options, rights (including land rights), or other transferrable securities or bearer negotiable instruments;
• Contracts, loan instruments, titles, claims, insurance policies, or their assignment;
• Intellectual property (including but not limited to patents or registered trademarks), royalties, licenses, or the rights thereto;
• Physical property, including but not limited to commodities, land, precious metals and stones, motor vehicles or vessels, works of art, or any other goods exchanged as payment-in-kind.
The size or monetary value of the financial or commercial transaction, the timeframe during which it took place, and the nature of the funds or proceeds (whether in liquid funds or some other tangible or intangible asset) are irrelevant to the suspicion and reporting of a suspicious transaction.
The AML-CFT Law designates money laundering as a criminal offence. Its prosecution is independent of that of any predicate offence to which it is related or from which the proceeds are derived. The suspicion of money laundering is not dependent on proving that a predicate offence has actually occurred or on proving the illicit source of the proceeds involved, but can be inferred from certain information, including indicators or behavioural patterns.
According to the 2018 National Risk Assessment, professional third-party money laundering has been identified as one of the top ML/FT threats in the UAE.
3.6 Predicate Offences
The AML-CFT Law defines a predicate offence as “any act constituting an offence or misdemeanour under the applicable laws of the State whether this act is committed inside or outside the State when such act is punishable in both countries.” A predicate offence is therefore any crime, whether felony or misdemeanour, which is punishable in the UAE, regardless of whether it is committed within the State or in any other country in which it is also a criminal offence.
FATF has designated 21 (twenty-one) categories of predicate offences. Each of these categories of predicate offences has been criminalised in the legislative framework of the State. FIs are reminded that this is not an exhaustive list of predicate offences, but simply a convenient categorisation, since in the UAE according to the AML-CFT Law, even crimes that do not appear on this list, whether felonies or misdemeanours, can be predicate offences to money laundering.
Based on expert analysis of these categories conducted on behalf of the UAE’s Competent Authorities for the 2018 National Risk Assessment, the top (highest) threats to the State in relation to money laundering have been identified as: fraud, counterfeiting and piracy of products, illicit trafficking in narcotic drugs and psychotropic substances, and professional third-party money laundering.
Similarly, other (medium-high) threats of particular concern to the UAE in relation to money laundering have been identified as the categories of: insider trading and market manipulation, robbery and theft, illicit trafficking in stolen and other goods, forgery, smuggling (including in relation to customs and excise duties and taxes), tax crimes (related to direct taxes and indirect taxes), and terrorism (including terrorist financing).
While FIs should pay special attention to the most serious threats identified in the NRA and any topical risk assessment when performing their own ML/FT business risk assessments, they are reminded that their risk assessment operations should consider all categories of risk for applicability to their own particular circumstances.
3.7 Financing of Terrorism
(AML-CFT Law Articles 3.1, 4, 29.3, AML-CFT Decision Article 1)
The AML-CFT Law designates the financing of terrorism as a criminal offence, which is not subject to the statute of limitations. It defines the financing of terrorism as:
• Committing any act of money laundering, being aware that the proceeds are wholly or partly owned by a terrorist organisation or terrorist person or intended to finance a terrorist organisation, a terrorist person or a terrorism crime, even if it without the intention to conceal or disguise their illicit origin; or
• Providing, collecting, preparing or obtaining proceeds or facilitating their obtainment by others with intent to use them, or while knowing that such proceeds will be used in whole or in part for the commitment of a terrorist offense, or committing such acts on behalf of a terrorist organisation or a terrorist person while aware of their true background or purpose.
There are numerous risk factors that FIs should consider important when assessing their exposure to the risk of terrorist financing (see Section 4.1.1, Risk Factors), including geographic-, sector-, channel-, product-, service- and customer-specific risks.
In a 2019 report by MENAFATF, an assessment of the global threat posed by the financing of terrorism stated:
“The number, type, scope, and structure of terrorist actors and the global terrorism threat are continuing to evolve. Recently, the nature of the global terrorism threat has intensified considerably. In addition to the threat posed by terrorist organisations such as ISIL, Al-Qaeda and other groups, attacks in many cities across the globe are carried out by individual terrorists and terrorist cells ranging in size and complexity. Commensurate with the evolving nature of global terrorism, the methods used by terrorist groups and individual terrorists to fulfil their basic need to generate and manage funds is also evolving.
Terrorist organisations use funds for operations (terrorist attacks and pre-operational surveillance); propaganda and recruitment; training; salaries and member compensation; and social services. These financial requirements are usually high for large terrorist organisations, particularly those that aim to, or do, control territory. In contrast, the financial requirements of individual terrorists or small cells are much lower with funds primarily used to carry out attacks. Irrespective of the differences between terrorist groups or individual terrorists, since funds are directly linked to operational capability, all terrorist groups and individual terrorists seek to ensure adequate funds generation and management.”1
1 Social Media and Terrorism Financing: A joint project by Asia/Pacific Group on Money Laundering & Middle East and North Africa Financial Action Task Force, APG/MENAFATF, January 2019, p.4.
3.8 Financing of Illegal Organisations
(AML-CFT Law Articles 3.2, 4, 29.3, AML-CFT Decision Article 1)
Like the financing of terrorism, the AML-CFT Law designates the financing of illegal organisations as a criminal offence that is not subject to the statute of limitations. The Law defines the financing of illegal organisations as:
• Committing any act of money laundering, being aware that the proceeds are wholly or partly owned by an illegal organisation or by any person belonging to an illegal organisation or intended to finance such illegal organisation or any person belonging to it, even if without the intention to conceal or disguise their illicit origin.
• Providing, collecting, preparing, obtaining proceeds or facilitating their obtainment by others with intent to use such proceeds, or while knowing that such proceeds will be used in whole or in part for the benefit of an Illegal organisation or of any of its members, with knowledge of its true identity or purpose.
• When assessing their risk exposure to the financing of illegal organisations, FIs should pay special attention to the regulatory disclosure, accounting, financial reporting and audit requirements of organisations with which they conduct Business Relationships or transactions. This is particularly important where non-profit, community/social, or religious/cultural organisations are involved, especially when those organisations are based, or have significant operations, in jurisdictions that are unfamiliar or in which transparency or access to information may be limited for any reason.
3.9 The ML Phases
To identify, understand and accurately assess the ML/FT risks to which FIs are exposed at both the enterprise and business relationship levels, FIs should be aware of the three phases of money laundering. By determining for which ML/FT phase a certain product can be misused or the FI itself can be misused, will help the FI understand its specific inherent ML/FT risks. The paragraphs below describe the crime of money laundering as consisting of three distinct (though sometimes overlapping) phases:
Placement. In this phase, criminals attempt to introduce Funds or the Proceeds of Crime into the financial system using a variety of techniques or typologies (see Section 3.10, ML/FT Typologies).
Examples of placement transactions include the following:
• Blending of funds: Commingling of illegitimate funds with legitimate funds, such as placing the cash from illegal narcotics sales into cash-intensive, locally owned businesses. • Foreign exchange: Purchasing of foreign exchange with illegal funds. • Breaking up amounts: Placing cash in small amounts and depositing them into numerous bank accounts in an attempt to evade attention or reporting requirements. • Currency smuggling: Cross-border physical movement of cash or monetary instruments. • Loans: Repayment of legitimate loans using laundered cash.
Layering. Once the Funds or Proceeds are introduced, or placed, into the financial system, they can proceed to the next phase of the process; often, this is accomplished by placing the funds into circulation through formal financial institutions, and other legitimate businesses, both domestic and international.” In this layering phase, criminals attempt to disguise the illicit nature of the Funds or Proceeds of Crime by engaging in transactions, or layers of transactions, which aim to conceal their origin.
Examples of layering transactions include:
• Electronically moving funds from one country to another and dividing them into advanced financial options and/or markets; • Moving funds from one financial institution to another or within accounts at the same institution; • Converting the cash placed into monetary instruments; • Reselling high-value goods and prepaid access/stored value products; • Investing in real estate and other legitimate businesses; • Placing money in stocks, bonds or life insurance products; and • Using shell companies to obscure the ultimate beneficial owner and assets.
Integration. In this phase, criminals attempt to return, or integrate, their “laundered” Funds or the Proceeds of Crime back into the economy, or to use it to commit new criminal offences, through transactions or activities that appear to be legitimate.
A key objective for criminals engaged in money laundering—and therefore a key generic risk underlying the specific risks faced by FIs—is the exploitation of situations and factors (including products, services, structures, transactions, and geographic locations) which favour anonymity and complexity, thereby facilitating a break in the “paper trail” and concealment of the illicit source of the Funds.
Although the sizes of transactions related to the financing of terrorism and illegal organisations can be (much) smaller than those involved in money laundering operations, and some of the typologies and specific techniques used may differ, the overall principles and generic risks are the same. The terrorists and criminals involved in these acts attempt to exploit situations and factors favouring anonymity and complexity, in order to obscure and conceal the illicit source of the Funds, or the illicit destination or purpose for which they are intended, or both. FIs should remain careful that their services are not being used either directly or indirectly to facilitate Money Laundering or the Financing of Terrorism or Illegal Organisations in any of the three stages described above.
3.10 ML/FT Typologies
The methods used by criminals for money laundering, the financing of terrorism, and the financing of illegal organisations are continually evolving and becoming more sophisticated. It is therefore critical in combating these crimes for FIs to ensure that their personnel are kept up-to-date on the latest ML/FT trends and typologies.
There are numerous useful sources of research and information related to ML/FT typologies, including by the Supervisory Authorities, the FATF, MENAFATF and other FSRBs, the Egmont Group, and others. FIs should incorporate the regular review of ML/FT trends and typologies into their compliance training programmes (see Section 8.2, Staff Screening and Training), as well as into their risk identification and assessment procedures.
Examples of some of the key ML/FT typologies with which FIs should be familiar include (but are not limited to):
• Currency exchanges / cash conversion: used to assist with smuggling to another jurisdiction or to exploit low reporting requirements on currency exchange houses to minimize risk of detection – e.g., purchasing of travellers cheques to transport value to another jurisdiction. • Cash couriers / currency smuggling: concealed movement of currency to avoid transaction / cash reporting measures. • Structuring (smurfing): A method involving numerous transactions (deposits, withdrawals, transfers), often various people, high volumes of small transactions and sometimes numerous accounts to avoid detection threshold reporting obligations. • Use of credit cards, cheques, promissory notes, etc.: Used as instruments to access funds held in a financial institution, often in another jurisdiction. • Purchase of portable valuable commodities (gems, precious metals, etc.): A technique to purchase instruments to conceal ownership or move value without detection and avoid AML/CFT measures – e.g., movement of diamonds or gold to another jurisdiction. • Purchase of valuable assets (real estate, race horses, vehicles, etc.): Criminal proceeds are invested in high-value negotiable goods to take advantage of reduced reporting requirements to obscure the source of proceeds of crime. • Commodity exchanges (barter): Avoiding the use of money or financial instruments in value transactions to avoid AML/CFT measures - e.g., a direct exchange of heroin for gold bullion. • Use of wire transfers: to electronically transfer funds between financial institutions and often to another jurisdiction to avoid detection and confiscation. • Underground banking / unlicensed remittance services: Illegal mechanisms based on networks of trust used to remit monies, without the proper license or registration. Often work in parallel with the traditional banking sector and exploited by money launderers and terrorist financiers to move value without detection and to obscure the identity of those controlling funds. • Trade-based money laundering and terrorist financing: usually involves invoice manipulation and uses trade finance routes and commodities to avoid financial transparency laws and regulations. • Abuse of non-profit organizations (NPOs): May be used to raise terrorist funds, obscure the source and nature of funds and to distribute funds for terrorist activities. • Investment in capital markets: to obscure the source of proceeds of crime to purchase negotiable instruments, often exploiting relatively low reporting requirements. • Mingling (business investment): A key step in money laundering involves combining proceeds of crime with legitimate business monies to obscure the illegal source of the funds. • Use of shell companies/corporations: a technique to obscure the identity of persons controlling funds and exploit relatively low reporting requirements. • Use of offshore banks/businesses, including trust company service providers: to obscure the identity of persons controlling funds and to move monies away from interdiction by domestic authorities. • Use of nominees, trusts, family members or third parties, etc: to obscure the identity of persons controlling illicit funds. • Use of foreign bank accounts: to move funds away from interdiction by domestic authorities and obscure the identity of persons controlling illicit funds. • Identity fraud / false identification: used to obscure the identity of those involved in many methods of money laundering and terrorist financing. • Use “gatekeepers” professional services (lawyers, accountants, brokers, etc.): to obscure the identity of beneficiaries and the illicit source of funds. May also include corrupt professionals who offer ‘specialist’ money laundering services to criminals. • New Payment technologies: use of emerging payment technologies for money laundering and terrorist financing. Examples include cell phone-based remittance and payment systems. • Virtual assets: (VA) and related services have the potential to spur financial innovation and efficiency, but their distinct features also create new opportunities for money launderers, terrorist financiers, and other criminals to launder their proceeds or finance their illicit activities. FIs may refer to the FATF Recommendations that place AML/CFT requirements on Virtual Assets (VA) and Virtual Asset Service Providers (VASPs). The FATF has also issued a document on Guidance on Risk Based Approach to VAs and VASPs. FIs should be familiar with the AML/CFT risks of dealing with VAs and VASPs in accordance with the FATF guidance. • Life insurance products can be for instance be used for money laundering when they have saving or investment features which may include the options for full or partial withdrawals or early surrenders. • General insurance product: there are several cases where the early cancellation of policies with return of premium has been used to launder money.
○ A number of policies entered into by the same insurer/intermediary for small amounts and then cancelled at the same time; ○ Return premium being credited to an account different from the original account; ○ Requests for return premiums in currencies different from the original premium; ○ Regular purchase and cancellation of policies. • Overpayment of premiums: arranging for excessive numbers or excessively high values of insurance reimbursements by cheque or wire transfer to be made, in this method, the launderer may arrange for insurance of the legitimate assets and ‘accidentally’ but on a recurring basis, significantly overpay his premiums and request a refund for the excess.
The UAE FIU releases reports on Trends and Typologies of Money Laundering which is an analysis based on the information extracted from the suspicious transaction reports (STRs) filed by reporting entities. This is a very useful resource for FIs for understanding the prevalent typologies of ML and FT crimes as well as getting information on the latest trends on these crimes in the country. This report is released on the FIU’s GoAML System for STR reporting and therefore, is accessible to registered users of this system.
Links to some other official sources, which may be useful in keeping up-to-date with regard to ML/FT typologies, may be found in Appendix 11.2.
3.11 Sanctions against Persons Violating Reporting Obligations
(AML-CFT Law Articles 15, 24, 25)
The AML-CFT Law provides for the following sanctions against any Financial Institutions, their managers or their employees, who fail to perform, whether purposely or through gross negligence, their statutory obligation to report a suspicion of money laundering or the financing of terrorism or of illegal organisations:
• Imprisonment and fine of no less than AED100,000 and no more than AED1,000,000; or
• Any of these two sanctions.
According to Article 15 of the AML-CFT Law, the requirement to report is in the case of suspicion or reasonable grounds to suspect a Crime. It should also be noted that the transactions or funds that are the subject of the suspicion may represent only part of the proceeds of the criminal offence, regardless of their value.
Likewise, the AML-CFT Law provides for sanctions against anyone who warns or notifies a person of a suspicious transaction report or reveals that a transaction is under review or investigation by the Competent Authorities, as follows:
• Imprisonment for no less than six months and a penalty of no less than AED100,000 and no more than AED500,000; or
• Any of these two sanctions.
Part II—Identification and Assessment of ML/FT Risks
4. Identification and Assessment of ML/FT Risks
(AML-CFT Law Article 16.1; AML-CFT Decision Article 4.1)
Both the AML-CFT Law and the AML-CFT Decision provide that FIs may utilize a risk-based approach with respect to the identification and assessment of ML/FT risks.
FIs are obliged to assess and to understand the ML/FT risks to which they are exposed, and how they may be affected by those risks. Specifically, the AML-CFT Law provides that they shall:
“…continuously assess, document, and update such assessment based on the various risk factors established in the Implementing Regulation of this Decree-Law and maintain a risk identification and assessment analysis with its supporting data to be provided to the Supervisory Authority upon request.”
Furthermore, the AML-CFT Decision charges supervised institutions with:
“…Documenting risk assessment operations, keeping them up to date on on-going bases and making them available upon request.”
Guidance on these subjects is provided in the following sections.
4.1 Risk-Based Approach (RBA)
A risk-based approach (RBA) is central to the effective implementation of the AML/CFT legislation. It means that FIs identify, assess, and understand the ML/TF risks to which they are exposed, and implement the most appropriate mitigation measures. An RBA requires financial institutions to have systems and controls that are commensurate with the specific risks of money laundering and terrorist financing facing them. Assessing this risk is, therefore, one of the most important steps in creating a good AML/CFT compliance program and will enable FIs to focus their resources where the risks are higher. In this regard, FIs can take into account their business nature, size and complexity.
(AML-CFT Law Article 16.1; AML-CFT Decision Article 4.1-3)
Implicit in both the AML-CFT Law and the AML-CFT Decision is the well-established concept of a risk-based approach (RBA) to the identification and assessment of ML/FT risks. Specifically, the AML-CFT Law states that FIs should “identify crime risks within (their) scope of work” and should update their risk assessments on the basis of the various risk factors set out in the AML-CFT Decision. Likewise, the AML-CFT Decision states that FIs’ identification, assessment and understanding of the risks should be carried out “in concert with their business nature and size,” and that various risk factors should be considered in determining the level of mitigation required. The AML-CFT Decision further provides that enhanced due diligence should be performed in cases where high risks are identified, while simplified due diligence may be performed in certain cases where low risk is identified, unless there is a suspicion of ML/FT.
An RBA to AML/CFT means that FIs should identify, assess and understand the ML/TF risks to which they are exposed and take AML/CFT measures commensurate to those risks in order to mitigate them effectively. This will require an understanding of the ML/TF risk faced by UAE (national risks), risks by the sector and the FI as well as specific products and services, customer base, the capacity in which customers are operating, jurisdictions in which they operate , the delivery channel and the effectiveness of risk controls put in place.
The use of an RBA thus allows FIs to allocate their resources more efficiently and effectively, within the scope of the national AML/CFT legislative and regulatory framework, by adopting and applying preventative measures that are targeted at and commensurate with the nature of risks they face.
While there are limits to any risk-management approach, and no RBA can be considered as completely failsafe; there may be occasions where an FI has taken all reasonable measures to identify and mitigate ML/TF risks, but it is still used for ML/TF in isolated instances. FIs should nevertheless understand that a risk-based approach is not a justification for ignoring certain ML/FT risks, nor does it exempt them from taking reasonable and proportionate mitigation measures, even for risks that are assessed as low. Their statutory obligations require them to identify, assess and understand the level of (inherent) risks presented by their (types of) customers, products and services, transactions, geographic areas and delivery channels, and to be in a position to apply sufficient AML/CFT mitigation measures on a risk-appropriate basis at all times.
In order to do so, they should identify and assess their exposure to ML/FT risks on the basis of a variety of risk factors (see Section 4.1, Risk Factors), some of which are related to the nature, size, complexity and operational environment of their businesses, and others of which are customer- or relationship-specific. Furthermore, they should take reasonable and proportionate risk mitigation measures based on the severity of the risks identified.
Conducting an ML/TF business risk assessments can assist FIs to understand their risk exposure and the areas they should give priority in combating ML/FT. The extent of business-wide risks to which an FI is exposed may require different levels of AML/CFT resources and mitigation strategies.
The following picture is a schematic overview of the RBA process from an ML/TF business risk assessments to developing policies, procedures and measures to CDD and the reporting of suspicious transactions.
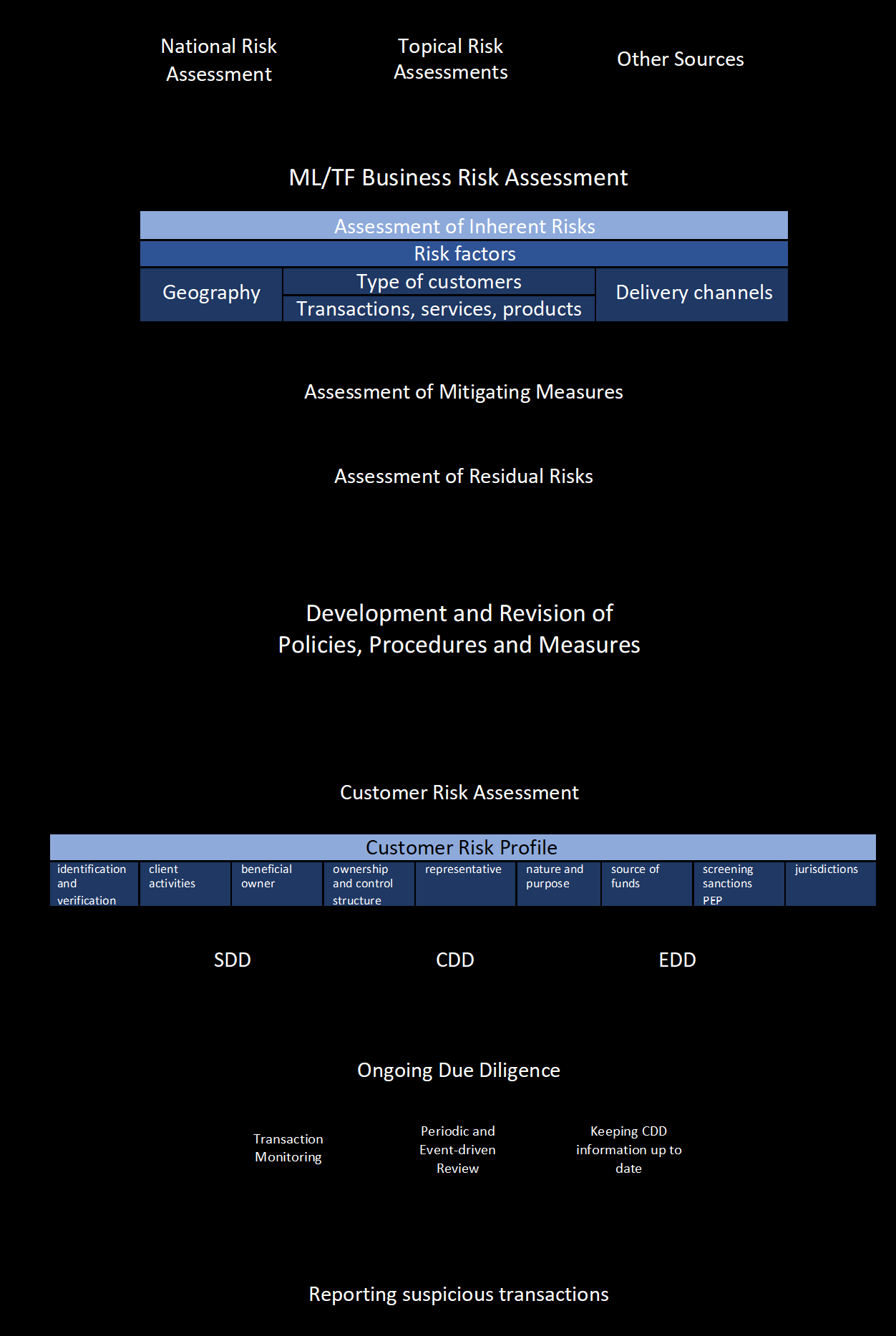
4.1.1 Assessing Business-wide Risks
(AML-CFT Law Article 16.1; AML-CFT Decision Article 4.1)
An important first step in applying an RBA is to identify, assess and understand the ML/FT risks by way of an ML/FT risk assessment of the entire business. The purpose of such an ML/FT business risk assessment is to improve the effectiveness of ML/FT risk management, by identifying the inherent ML/FT risks faced by the enterprise as a whole, determining how these risks are effectively mitigated through internal policies, procedures and controls, and establishing the residual ML/FT risks and any gaps in the controls that should be addressed.
Thus, an effective ML/TF business risk assessment can allow FIs to identify gaps and opportunities for improvement in their framework of internal AML/CFT policies, procedures and controls, as well as to make informed management decisions about risk appetite, allocation of AML/CFT resources, and ML/FT risk-mitigation strategies that are appropriately aligned with residual risks.
The first step of conducting an ML/TF business risk assessment for FIs is to identify, assess and understand the inherent ML/FT risks (i.e., the risks that an FI is exposed to if there were no control measures in place to mitigate them) across all business lines and processes with respect to the following risk factors: customers, products, services and transactions, delivery channels, geographic locations, and any other risk factors.
With the inherent risks as a basis, the FI can determine the nature and intensity of risk mitigating controls to apply to the inherent risks. The level of inherent ML/FT risks influence the kinds and levels of AML/CFT resources and mitigation strategies which FIs require to put in place. The assessment of inherent ML/FT risks and of the effectiveness of the risk mitigation measures will result in a residual risk assessment, i.e., the risks that remain when effective control measures are in place. In case the residual risk falls outside the risk appetite of the FI, additional control measures will need to be implemented to ensure that the level of ML/FT risk is acceptable to the FI.
FIs may utilise a variety of models or methodologies to analyse their risks, in keeping with the nature and size of their businesses. FIs should decide on both the frequency and methodology of an ML/FT business risk assessment, including baseline and follow-up assessments, that are appropriate to their particular circumstances, taking into consideration the nature of the inherent and residual ML/FT risks to which they are exposed, as well as the results of the NRA and Topical Risk Assessments. In most cases, FIs should consider performing the ML/FT business risk assessment at least annually; however assessments that are more frequent or less frequent may be justified, depending on the particular circumstances. They should also decide on policies and procedures related to the periodic review of their ML/TF business risk assessment methodology, taking into consideration changes in internal or external factors. These decisions should be documented, approved by senior management, and communicated to the appropriate levels of the organisation.
As part of the model or methodology, FIs should consider including in their ML/FT risk assessment the following elements:
• Likelihood or probability of occurrence of identified inherent risks;
• Timing of identified inherent risks;
• Impact on the organisation of identified inherent risks.
The result of an effective ML/FT business risk assessment will be the classification of identified risks into different categories, such as high, medium, low, or some combination of those categories (such as medium-high, medium-low). Such classifications may assist FIs to prioritise their ML/FT risk exposures more effectively, so that they may determine the appropriate types and levels of AML/CFT resources needed, and adopt and apply reasonable and risk-proportionate mitigation measures.
4.1.2 Risk Factors
As part of the business-wide ML/TF risk assessment, a proper identification of risk factors is crucial to the effective assessment of ML/FT risk. Risks will often occur as combinations of these risk factors. A risk can for instance occur because of the interrelationship between a customer and the jurisdictions where the customer is from or is active, or because of the connection between a product and the delivery channel.
Identified risk factors are used for the accurate categorisation of inherent risks, as well as for the application of appropriate mitigation measures. At the enterprise level, this includes adopting and applying adequate policies, procedures, and controls to business processes (see Section 5.1, Internal Policies, Controls and Procedures). The policies, procedures, and controls will in turn address the risks at the individual customer level, including assigning appropriate risk classifications to customers and applying due diligence measures that are commensurate with the identified risks (see Section 6, Customer Due Diligence).
The AML-CFT Decision outlines several risk factors which FIs must consider, when identifying and assessing their ML/FT risk exposure. FIs may also consider a wide array of additional risk factors, utilising various sources, such as:
• ML/FT red-flag indicators;
• Input and information from relevant internal sources, including the designated AML/CFT compliance officer;
• Information from national sources, including the results of the NRA or any Topical Risk Assessment with regard to ML/FT trends and sectoral threats and notices or circulars from the relevant Supervisory Authorities;
• Information from publications of relevant international organisations, such as FATF, MENAFATF and other FSRBs, the Egmont Group, UNODC, and others. (Links to some of these sources may be found in Appendix 11.2.)
In keeping with the ever-evolving nature of ML/FT risks, and in order to ensure that FIs implement a model for conducting the ML/TF business risk assessment that is appropriate to the nature and size of their businesses, FIs should continuously update the risk factors which they consider, in order to reflect new and emerging ML/FT risks and typologies.
A good practice to assess the inherent risk factors, is for FIs to formulate risk scenarios and assess the likelihood that a scenario occurs and the impact should a scenario materialize. The likelihood can be assessed based on the number of times per year that a risk scenario can occur. The impact can be assessed based on the possible financial and reputational effects that can result if a scenario indeed occurs. In this way, the FI can determine the inherent risks of a risk factor.
When assessing the inherent risks, an FI should make an inventory of the customers it services, the products and services it offers, define the scope of business areas to assess, including business units, legal entities, divisions, countries and regions. For this, an FI should make use of up-to-date quantitative and qualitative information on for instance, the types and number of customers, the volume of operations for the types of customers, volume of business per product and services and geographic locations.
Examples with regard to some of the major risk factors that should be taken into account by FIs when conducting the ML/TF business risk assessment are provided in the sections below. Even though some of these risk factors will also be relevant for the risk assessment of an individual Customer or Business Relationship, for the ML/TF business risk assessment, FIs are reminded that they should take a holistic view when evaluating exposure to these categories of customers.
4.1.3 Customer Risk
The customer risk factors relate to types or categories of customers. Certain customer or business relationship categories pose a risk that should be taken into account when assessing the overall level of inherent customer risk. When identifying certain categories of customers as inherently high risk, FIs should also consider the results of the NRA or any Topical Risk Assessment, as well as information from official sources, including the Supervisory Authorities, the FIU, the FATF, MENAFATF and other FSRBs, the Egmont Group, etc.
When assessing the customer risk factors with respect to the business-wide ML/FT risk assessment, an FI can take into account:
• Type of customers: The risks related to retail customers in combination with their product/service needs may be different from those related to high net worth or corporate customers and their respective product/service needs. Likewise, the risks associated with resident customers may be different from those associated with non-resident customers.
• Customer base. FIs with small, homogenous customer bases may face different risks from those with larger, more diverse customer bases. Similarly, FIs targeting growing or emerging markets may face different customer risks than those with more established customer bases.
• Maturity of relationship. FIs that rely on more transactional, occasional, or one-off interactions with their customers may be exposed to different risks from institutions with more repetitive or long-term business relationships.
The specific customer risk factors that FIs should consider, include:
• Categories of business relationships with complex legal, ownership, or direct or indirect group or network structures, or with less transparency with regard to Beneficial Ownership, effective control, or tax residency, may pose different ML/FT risks than those with simpler legal/ownership structures or with greater transparency.
• Categories of Customers involved in highly regulated and supervised activities and those involved in activities that are unregulated.
• Customers associated with higher-risk persons or professions (for example, foreign PEPs and/or their companies), or those linked to sectors associated with higher ML/FT risks.
• Non-resident entities particularly those with connections to offshore and high risk jurisdictions.
• Professionals (e.g., lawyers, accountants and TCSPs) acting as introducer or intermediary on behalf of customers or groups of customers (whereby there is no direct contact with the customer).
• High net worth individuals.
• Respondent banks from high risk countries.
Some of these customer risk factors are also relevant when determining the customer risk classification of an individual customer and the type and extent of customer due diligence to be performed (see Section 6, Customer Due Diligence).
4.1.4 Geographic Risk
FIs should consider geographic ML/FT risk factors both from domestically and cross-border sources. These risks arise from: (i) the locations where the FI has offices, branches and subsidiaries and (ii) locations in which the customers reside or conduct their activities. Examples of some of these factors include:
• Regulatory/supervisory framework. Countries with stronger AML/CFT controls present a different level of risk than countries with weaker regulatory and supervisory frameworks, for instance countries identified by the FATF as jurisdictions with weak AML/CFT measures.
• International Sanctions. FIs should consider whether the countries or jurisdictions they deal with are the subject of international sanctions, such as targeted financial sanctions (TFS), UAE, OFAC, UN and EU restrictive measures, that could impact their ML/FT risk exposure and mitigation requirements.
• Reputation. FIs should consider whether the countries or jurisdictions they deal with are associated with higher or lower levels of ML/FT, corruption, and (lack of) transparency (particularly as regards financial and fiscal reporting, criminal and legal matters, and Beneficial Ownership, but also including such factors as freedom of information and the press).
• Combination with customers’ inherent risk factors. FIs should consider the countries risk in combination with customers risks, including principal residential or operating locations of customers.
4.1.5 Product-, Service-, Transaction-Related Risk
When assessing the inherent ML/FT risks associated with product, service, and transaction types, an FI should take stock of its lines of business, products and services that are more vulnerable to ML/FT abuse. FIs should assess the inherent ML/FT risks of abuse of the products and services by their customers taking into account a number of factors such as their ease for holding and transferring value or their complexity and transparency. Some of the risk factors that FIs should consider, among others, are:
• Typology. FIs should consider whether the product, service, or transaction type is associated with any established ML/FT typologies (see Section 3.10, ML/FT Typologies).
• Complexity. Products, services, or transaction types that favour complexity, especially when that complexity is excessive or unnecessary, can often be exploited for the purpose of money laundering and/or the financing of terrorism or illegal organisations. FIs should consider the conceptual, operational, legal, technological and other complexities of the product, service, or transaction type. Those with higher complexity or greater dependencies on the interactions between multiple systems and/or market participants may expose FIs to different types and levels of ML/FT risk than those with lower complexity or with fewer dependencies on multiple systems and/or market participants.
• Transparency and transferability. Situations that favour anonymity can often be exploited for the purpose of ML/FT. FIs should consider the level of transparency and transferability of ownership or control of products, services, or transaction types, particularly in respect of the ability to monitor the identities and the roles/responsibilities of all parties involved at each stage. Special attention should be given to products, services, or transaction types in which funds can be pooled or co-mingled, or in which multiple or anonymous parties can have authority over the disposition of funds, or for which the transferability of Beneficial Ownership or control can be accomplished with relative ease and/or with limited disclosure of information.
• Size/value. Products, services, or transaction types with different size or value parameters or limits may pose different levels of ML/FT risk.
4.1.6 Delivery Channel-Related Risk
Different delivery channels for the acquisition and management of customers and business relationships, as well as for the delivery of products and services, entail different types and levels of ML/FT risk.
When evaluating delivery channel-related risk, FIs should pay particular attention to those channels, whether related to customer acquisition and/or relationship management, or to product or service delivery, which have the potential to favour anonymity. Among others, these may include non-face-to-face channels (especially in cases where there are no safeguards in place such as electronic identification means), such as internet-, phone-, or other remote-access services or technologies; the use of third-party business introducers, intermediaries, agents or distributors; and the use of third-party payment, or other transaction intermediaries.
4.1.7 Other Risk Factors
Given the ever-evolving nature of ML/FT risks, new risks are constantly emerging, while existing ones may change in their relative importance due to legal or regulatory developments, changes in the marketplace, or as a result of new or disruptive products or technologies. For this reason, no list of risks can ever be considered as exhaustive.
Nevertheless, additional factors that may present specific risks are, e.g., the introduction of new products or services, new technologies or delivery processes or the establishment of new branches and subsidiaries locally and abroad.
In order to ensure, therefore, that FIs are in a position to review and update the ML/TF business risk assessment as well as mitigation measures, FIs should take into consideration the results of the NRA or any Topical Risk Assessment. They should also consult publications from official sources on a regular basis, including those of the relevant Supervisory Authorities, the FIU, the FATF, MENAFATF and other FSRBs, the Egmont Group, and others. Links to some of these sources may be found in Appendix 11.2.
Examples of some of the types of additional risk factors which FIs may consider in identifying and assessing their ML/FT risk exposure include:
• Novelty/innovation. FIs should consider the depth of experience with and knowledge of the product, service, transaction, or channel type. Products, services, transaction, or delivery channel types that are new to the market or to the enterprise may not be as well understood as, and may therefore pose a different level of ML/FT risk than, more established ones. Likewise, products, services, transaction, or delivery channel types which are unexpected or unusual with respect to a particular type of customer may indicate a different level of potential ML/FT risk exposure than would more traditional or expected product, service, transaction, or channel types in regard to that same type of customer.
• Cyber security/distributed networks. FIs may consider evaluating the degree to which their operational processes and/or their customers expose them to the risk of exploitation for the purpose of professional third-party money laundering and/or the financing of terrorism or of illegal organisations, through cyber-attacks or through other means, such as the use of distributed technology or social networks. An example of such a risk is the recent dramatic increase in the global incidence of so-called CEO fraud, in which fraudsters troll companies with phishing e-mails that are purportedly from the CEO or other senior executives, and attempt to conduct fraudulent transactions or obtain sensitive data that can be used for criminal purposes.
4.1.8 Assessing New Product and New Technologies Risks
As part of their obligation to update their ML/FT risk assessments on an ongoing basis, the AML-CFT Decision specifically requires FIs to “identify and assess the risks of money laundering and terrorism financing that may arise when developing new products and new professional practices, including means of providing new services and using new or under-development techniques for both new and existing products.”
FIs must complete the assessment of such risks, and take the appropriate risk management measures, prior to launching new products and services, practices or techniques, or technologies. In general, they should integrate these ML/FT risk assessment and mitigation requirements into their new product, service, channel, or technology development processes.
For the purpose of assessing the ML/FT risks associated with new products, services, practices, techniques, or technologies, FIs may consider utilising the same or similar risk assessment models or methodologies as those utilised for their ML/FT business risk assessments, updated as necessary for the particular circumstances. They should also document the new product, service, practice, technique, or technology risk assessments, in keeping with the nature and size of their businesses (see Section 4.6.1, Documentation, Updating and Analysis).
4.2 Risk Assessment Methodology and Documentation
(AML-CFT Law Article 16.1(a) and AML-CFT Decision Article 4.1)
A well-documented assessment of the identified inherent risk factors (see Section 4.1, Risk Factors) is fundamental to the adoption and effective application of reasonable and proportionate ML/FT risk-mitigation measures. Thus, the result of such an ML/TF business risk assessment allows for a systematic categorisation and prioritization of inherent and residual ML/FT risks, which in turn allows FIs to determine the types and appropriate levels of AML/CFT resources needed for mitigation purposes.
An effective ML/TF business risk assessment is not necessarily a complex one. The principle of a risk-based approach means that FIs’ risk assessments should be commensurate with the nature and size of their businesses. FIs with smaller or less complex business models may have simpler risk assessments than those of institutions with larger or more complex business models, which may require more sophisticated risk assessments.
4.2.1 Risk Assessment Methodology
(AML-CFT Decision Article 4.1(b))
The AML-CFT Decision obliges FIs to document their risk assessment operations. FIs may utilise a variety of models or methodologies in assessing their ML/FT risk. FIs should determine the type and extent of the risk assessment methodology that they consider to be appropriate for the size and nature of their businesses, and should document the rationale for these decisions.
To be effective, a risk assessment should be based on a methodology that:
• Is based on quantitative and qualitative data and information and makes use of internal meetings or interviews; internal questionnaires concerning risk identification and controls; review of internal audit reports;
• Reflects the FI’s management-approved AML/CFT risk appetite and strategy;
• Takes into consideration input from relevant internal sources, including input and views from the designated AML/CFT compliance officer and other relevant units like risk management and internal control;
• Takes into consideration relevant information (such as ML/FT trends and sectoral risks) from external sources, including the NRA or any Topical Risk Assessment, Supervisory and other Competent Authorities, and the FATF, MENAFATF and other FSRBs, the Egmont Group, and others where appropriate;
• Describes the weighting of risk factors, the classification of risks into different categories, and the prioritisation of risks.
• Evaluates the likelihood or probability of occurrence of identified ML/FT risks, and determining their timing and impact on the organization.
• Takes into account whether the AML/CFT controls are effective, specifically whether there are adequate controls to mitigate risks concerning customers, products, services, or transactions.
• Determines the effectiveness of the AML/CFT risk mitigating measures in place by using information such as audit and compliance reports or management information reports.
• Determines the residual risk as a result of the inherent risks and the effectiveness of the AML/CFT risk mitigating measures.
• Establishes based on the residual risk and the risk appetite, whether additional AML/CFT controls have to be put in place.
• Determines the rationale and circumstances for approving and performing manual interventions or exceptions to model-based risk weightings or classifications.
• Is properly documented and maintained, regularly evaluated and updated, and communicated to management and relevant personnel within the organisation.
• Is tested and audited for the effectiveness and consistency of the risk methodology and its output with regard to statutory obligations.
4.2.2 Documentation and Updating
(AML-CFT Law Article 16.1(a) and AML-CFT Decision Article 4.1(a)-(b))
Documentation
FIs are obliged to document their ML/TF business risk assessment, including methodology, analysis, and supporting data, and to make them available to the Supervisory Authorities upon request. FIs should incorporate into their documentation, the information used to conduct the ML/TF business risk assessment in order to demonstrate the effectiveness of their risk assessment processes. Examples of such information include, but are not limited to:
• Organization’s overall risk policies (for example, risk appetite statement, customer acceptance policy, and others, where applicable).
• ML/FT risk assessment model, methodology and procedures, including such information as organizational roles and responsibilities; process flows, timing and frequency; internal reporting requirements; and review, testing, and updating requirements.
• Risk factors identified, and input received from relevant internal sources, including the designated AML/CFT compliance officer.
• Details of the inherent and residual risk-factor analysis that constitutes the risk assessment.
The documentation measures taken by FIs should be reasonable and commensurate with the nature and size of their businesses.
Updating
FIs are obliged to keep their ML/TF business risk assessment up-to-date on an ongoing basis. In fulfilling this obligation, they should review and evaluate their ML/FT business risk assessment processes, models, and methodologies periodically, in keeping with the nature and size of their businesses. FIs should also update their ML/TF business risk assessment whenever they become aware of any internal or external events or developments which could affect their accuracy or effectiveness.
Such developments may include, among other things, changes in business strategies or objectives, technological developments, legislative or regulatory developments, or the identification of material new ML/FT threats or risk factors. In this regard, FIs should take into consideration the results of the most recent NRA or any Topical Risk Assessment, as well as circulars, notifications and occasional published information from official sources, such as the Supervisory Authorities; other national Competent Authorities; or relevant international organisations, such as FATF, MENAFATF and other FSRBs, the Egmont Group, and others. Links to some of these sources may be found in Appendix 11.2.
Part III—Mitigation of ML/FT Risks
The Elements of an AML/CFT Program
Commonly referred to as the three lines of defense, the basic elements that must be addressed in an AML/ CFT program are
• A system of internal policies, procedures and controls, including an ongoing employee training program (first line of defense);
• A designated compliance function with a compliance officer or money laundering reporting officer (second line of defense); and
• An independent audit function to test the overall effectiveness of the AML program (third line of defense).
In setting up these three lines of defense, FIs can take into account their business nature, size and complexity.
(AML-CFT Law Article 16.1(b), 16.1(d); AML-CFT Decision Articles 4.2 , 4.3)
FIs are obliged to take the necessary measures to manage and mitigate the ML/FT risks to which they are exposed. Both the AML-CFT Law and the AML-CFT Decision provide that FIs may utilize a risk-based approach with respect to mitigation of ML/FT risks.
5. Internal Policies, Controls and Procedures
Policies:
Clear and simple high-level statements that are uniform across the entire organization (sets the tone from the top).
Procedures:
Translates the AML/CFT policies into an acceptable and workable practice, tasking the stakeholders with their respective responsibilities.
Controls:
The internal technology or tools the financial institution utilizes to ensure the AML/CFT program is functioning as intended and within predefined parameters.
(AML-CFT Law Article 16.1(d); AML-CFT Decision Articles 4.2(a), 20)
The AML-CFT Law and the AML-CFT Decision require FIs to implement internal policies, controls and procedures that enable them to manage and mitigate the ML/FT risks they have identified in their ML/TF business risk assessment, in keeping with the nature and size of their businesses. Such policies, controls and procedures must be approved by senior management, reviewed for effectiveness and continuously updated, and must apply to all branches, subsidiaries and affiliated entities in which FIs hold a majority interest (see Section 8.3, Group Oversight for more guidance). They must also take into consideration the results of the NRA and Topical Risk Assessments.
Additionally, FIs should ensure that the policies, controls and procedures they implement to manage and mitigate ML/FT risks are reasonable, proportionate to the risks involved, and consistent with the results of their ML/TF business risk assessments.
Such policies, procedures and methodologies should be reasonable and proportionate to the risks involved, and, in formulating them, FIs should consider the results of the NRA and any Topical Risk Assessment as well as their own ML/FT business risk assessment. Commensurate with the nature and size of the FIs’ businesses, the policies, procedures and methodologies should also be documented, approved by senior management, and communicated at the appropriate levels of the organisation.
In developing the internal AML/CFT control systems, FIs should also take into account their IT infrastructure and management information systems capabilities. FIs should consider how well their technical infrastructure, including their data management and management information reporting capabilities, are suited to the ML/FT risk mitigation requirements of the types of customers they deal with, particularly in respect of the size and growth dynamics of their customer base.
The internal policies, controls and procedures that FIs design to prevent, detect and deter ML/FT risks can be categorised broadly as those related to:
• The identification and assessment of ML/FT risks (see Section 4.5, Business-wide Risk Assessment).
• Customer due diligence (CDD), including enhance due diligence (EDD), and simplified due diligence (SDD) (see Section 6, Customer Due Diligence), including its review and updating, and reliance on third parties in regard to it.
• Customer and transaction monitoring, and the reporting of suspicious transactions (see Section 7, Suspicious Transaction Reporting).
• AML/CFT governance, including compliance staffing and training, senior management responsibilities, and the independent auditing of risk mitigation measures (see Section 8, Governance).
• Record-keeping requirements (see Section 9, Record Keeping).
Guidance in relation to these categories is provided in the above-referenced sections.
6. Customer Due Diligence (CDD)
MAIN ELEMENTS OF A CUSTOMER DUE DILIGENCE PROGRAM
- Customer Identification; - Profiles; - Customer Acceptance; - Risk rating; - Monitoring; - Investigation; and - Documentation
(AML-CFT Law Article 16.1(b); AML-CFT Decision Articles 4.2(b), 4.3, 5-13, 14, 15, 19, 20.1, 22, 24.2-4, 25, 27, 29.2, 30, 31.1, 35.1-2 and 5, 37.1-2, 44.10, 55.1)
6.1 Risk-Based Application of CDD Measures
The AML-CFT Law implicitly recognises the need for an RBA to customer due diligence measures, by obliging FIs to “take the necessary due diligence measures and procedures and define their scope, taking into account the various risk factors and the results of the national risk assessment….” This principle is further emphasised by the AML-CFT Decision, which explicitly provides for the application of enhanced due diligence (EDD) measures to manage identified high risks (see Section 6.4, Enhanced Due Diligence (EDD) Measures), and of simplified due diligence (SDD) to manage identified low risks in the absence of a suspicion of ML/FT (see Section 6.5, Simplified Due Diligence (SDD) Measures).
FIs are reminded, that each customer’s ML/FT risk profile is dynamic and subject to change depending on numerous factors, including (but not limited to) the discovery of new information or a change in behaviour, and the appropriate level of due diligence should be applied in keeping with the specific situation and risk indicators identified. In that regard, FIs should always be prepared to increase the type and level of due diligence exercised on a customer of any ML/FT risk category whenever the circumstances require, including situations in which there are any doubts as to the accuracy or appropriateness of the customer’s originally designated ML/FT risk category. This means that the CDD measures are not to be taken as a static formula but that depending on the risk of a customer the intensity and depth of the CDD measures should vary.
6.1.1. Assessing Customer and Business Relationship Risk
(AML-CFT Law Article 16.1; AML-CFT Decision Article 4.1)
A customer can be anyone who performs a one-off or occasional financial activity or transaction or anyone who establishes an ongoing commercial or financial relationship with the FI.
The accurate assessment of customer or business relationship risk is fundamental to the risk classification of customers and the effective application of appropriate risk-based customer due diligence measures. FIs should take the necessary steps to ensure that their customer or business relationship risk assessment processes are robust and reliable, and that they incorporate the results of the NRA, any Topical Risk Assessment and their own ML/TF business risk assessment, as well as the input of relevant internal stakeholders, including the designated AML/CFT compliance officer.
In assessing customer or business relationship risk, FIs should analyse customers on the basis of the identified risk factors in order to arrive at a risk classification. FIs may utilize different methodologies to accomplish their risk classification, depending on the nature and size of their businesses, and of the risks involved. For example, some entities with smaller or less complex businesses, or with more homogenous customer bases, may elect to assess business relationship risk and assign customer risk classifications on the basis of generic profiles for customers of the same type. Other larger or more complex FIs may elect to assess business relationship risk and assign customer risk classifications using more sophisticated models or scorecards based on weightings of various risk factors.
Regardless of the methodologies they choose, FIs should ensure that their business relationship risk assessment processes and the rationale for their methodologies are well-documented, approved by senior management, and communicated at the appropriate levels of the organisation. They should also decide on policies and procedures related to both the periodic review of their business relationship risk assessment processes, and to the frequency for updating the individual business relationship risk assessments and customer risk classifications produced by them, taking into consideration changes in internal or external factors.
6.1.2 Establishing a Customer Risk Profile
(AML-CFT Decision Articles 7.1, 8.3-4)
FIs should establish a risk profile for their customers, commensurate with the types and levels of risk involved. Such risk profiles allow FIs to compare a customer’s actual activity with the expected activity more effectively, and thus contribute to their capacity to discover unusual circumstances or potentially suspicious transactions.
Where legal persons or legal arrangements are concerned, FIs are obliged to identify any natural person who owns or controls an interest of 25% or more. In order to achieve an effective understanding of the ownership and control structure of a customer that is a legal person or arrangement, FIs should obtain from the customer and including in the risk profile a detailed explanation or a company structure chart providing the details of any ownership interests of 25% or more, and tracing them through any intermediate entities (whether legal persons or arrangements, or natural persons who are nominee stakeholders) to the natural persons who ultimately own or control them.
Furthermore, in order to understand the nature of the business of a legal person or Legal Arrangement, FIs should obtain and include in the profile a detailed explanation or company structure chart showing the entity’s internal management structure, identifying the persons holding senior management positions, or other positions of control. They should also obtain information about the legal person’s or arrangement’s majority-owned or controlled operating subsidiaries, including the nature of the business and the operating locations of those subsidiaries.
FIs are also required to understand the intended purpose and nature of the Business Relationship, and, for legal persons or arrangements, the nature of the customer’s business and its ownership and control structure.
Based on the risk profile, FIs should carry out ongoing due diligence of their Business Relationships, so as to be able to ensure that the transactions conducted are consistent with the information they have about the customer, the type of activity they are engaged in, the risks they entail, and, where necessary, their source of funds.
When dealing with higher-risk or more complex customers, in addition to the type of information referred to above, FIs may obtain and include in the customer’s risk profile more detailed information about their customers’ activities, such as:
• Anticipated size and/or turnover of account balances or transactional activity;
• Expected types and volumes of transactions;
• Known or expected counterparties or third-party intermediaries with whom the customer conducts transactions;
• Known or expected locations related to transactional activity;
• Anticipated timing or seasonality of transactional activity.
Where lower-risk customers are concerned, FIs may consider applying more generic risk profiles in order to compare actual and expected types and levels of activity.
6.2 Circumstances and Timing for Undertaking CDD Measures
(AML-CFT Decision Article 5.1)
Under normal circumstances, FIs are obliged to undertake CDD measures (including verifying the identity of customers, Beneficial Owners, beneficiaries, and controlling persons) either prior to or during the establishment of a Business Relationship or the opening of an account, or prior to the execution of a transaction for a customer with whom there is no Business Relationship. Guidance in regard to these requirements and certain exceptional circumstances provided for in the AML-CFT Decision is provided in the sub-sections below.
6.2.1 Establishment of a Business Relationship
FIs establish a Business Relationship with a customer when they perform any act for, on behalf of, or at the direction or request of the customer, with the anticipation that it will be of an ongoing or recurring nature, whether permanent or temporary. Such acts may include, but are not limited to:
• Assigning an account number or opening an account in the customer’s name;
• Effecting any transaction in the customer’s name or on their behalf, or at the customer’s direction or request for the benefit of someone else;
• Providing any form of tangible or intangible product or service (including but not limited to granting credits, guarantees, or other forms of value) to or on behalf of the customer, or at the customer’s direction or request for the benefit of someone else;
• Signing any form of contract, agreement, letter of intent, memorandum of understanding, or other document with the customer in relation to the performance of a transaction or series of transactions, or to the provision of any form of tangible or intangible product or service as described above;
• Accepting any form of compensation or remuneration (including a promise of future payment) for the provision of tangible or intangible products or services, as described above, from or on behalf of the customer;
• Receiving funds or proceeds of any kind (including those held on a fiduciary basis, for safekeeping, or in escrow) from or on behalf of the customer, whether for their account or for the benefit of someone else;
• Any other act performed by FIs in the course of conducting their ordinary business, when done on behalf of, or at the request or direction of, a customer.
In such cases, and other than in the exceptional circumstances described below (see Section 6.2.3, Exceptional Circumstances), FIs are required to undertake appropriate risk-based CDD measures (see Section 6.3, Customer Due Diligence (CDD) Measures, Section 6.4, Enhanced Due Diligence (EDD) Measures, and Section 6.5, Simplified Due Diligence (SDD) Measures for further guidance).
In addition, CDD also needs to be conducted when
• there is a ML/FT suspicion (see Section 7.2, Identification of Suspicious Transactions);
• there are doubts about the veracity or adequacy of identification data previously obtained with regard to the customer.
Among other things, the CDD measures should include verifying the identity of the customer as well as the Beneficial Owners, beneficiaries, and controlling persons, and understanding the nature of their business and the purpose of the Business Relationship.
6.2.2 Occasional Transactions
During the course of business, FIs may be called upon to perform occasional or non-recurring transactions for customers with whom there is no ongoing account or Business Relationship. Examples of such transactions include, but are not limited to:
• Exchange of currencies;
• Issue or cashing/redemption of traveler’s cheques;
• Transfer of money or other value for a walk-in customer;
On such occasions, and other than in the exceptional circumstances described below (see Section 6.2.3, Exceptional Circumstances), FIs are required to identify the customer and verify the customer’s identity as well as that of the Beneficial Owners, beneficiaries, and controlling persons. Furthermore, FIs are required to undertake appropriate risk-based CDD measures (see Section 6.3, Customer Due Diligence (CDD) Measures, Section 6.4, Enhanced Due Diligence (EDD) Measures, and Section 6.5, Simplified Due Diligence (SDD) Measures for further guidance), including among other things understanding the nature of the customer’s business and the purpose of the transaction, in the cases specified in Article 6 of the AML-CFT Decision, as follows:
• When carrying out occasional transactions in favour of a Customer for amounts equal to or exceeding AED 55,000 (or equivalent in any other currency), whether the transaction is carried out in a single transaction or in several transactions that appear to be linked;
• When carrying out occasional transactions in the form of Wire Transfers for amounts equal to or exceeding AED 3,500 (or equivalent in any other currency) (see Section 6.3.2, CDD Requirements Concerning Wire Transfers);
• When there is a ML/FT suspicion (see Section 7.2, Identification of Suspicious Transactions);
• When there are doubts about the veracity or adequacy of identification data previously obtained with regard to the customer.
Some of the indicators of transactions that may appear to be linked include, but are not limited to the following:
- Multiple transactions with the same or similar customer reference codes; - Transactions executed sequentially or in close time proximity, and involving the same or related counterparties; - Multiple transactions attempted by a customer with whom there is no Business Relationship at different branches of the same FI on the same day.
6.2.3 Exceptional Circumstances
(AML-CFT Decision Articles 4.3, 5.1(a)-(c), 10, 11.1(b), 13.2)
From time to time, certain situations may arise which fall outside of the normal course of CDD processes. Under these circumstances, described below, FIs are permitted to handle the timing, customer identification, and other aspects of customer due diligence procedures exceptionally. Specifically:
• When there is no ML/FT suspicion, and the ML/FT risks are identified as low, FIs may complete the verification of the customer’s identity after establishing the Business Relationship under the conditions specified in the relevant provisions of the AML-CFT Decision. In such circumstances, the verification of the identity must be conducted in a timely fashion, and FIs must ensure that they implement appropriate and effective measures to manage and mitigate the risks of crime and of the customer benefiting from the Business Relationship prior to the completion of the verification process. Examples of such measures which FIs may consider taking in this regard are, among others:
- Holding funds in suspense or in escrow until the verification of the identity is completed; - Making the completion of the verification of the identity a condition precedent to the closing of a transaction.
• In the case of Legal Arrangements, such as Trusts or foundations, or of life insurance policies (including funds-generating transactions, such as life insurance products relating to investments and family Takaful insurance) in which there are beneficiaries who are not named, but instead belong to a designated class of future or contingent beneficiaries, FIs are required to obtain sufficient information about the details of the class of beneficiaries so as to be in a position to establish the identity of each beneficiary at the time of the settlement, pay-out, or exercise of their legally acquired rights. Furthermore, FIs must verify the identity of the beneficiaries at the time of settlement or pay-out and prior to the exercise of any related legally acquired rights. They should also ensure that they implement appropriate and effective measures to manage and mitigate the risks of crime and of the customer benefiting from the Business Relationship prior to the completion of the verification process. Examples of such measures which FIs may consider taking in this regard are, among others:
- Holding funds in suspense or in escrow until the verification of the identity is completed; - Making the completion of the verification of the identity a condition precedent to the closing of a transaction.
• When a legal entity customer or its controlling stakeholder meets the conditions specified in Article 10.1-2 of the AML-CFT Decision with regard to publicly listed companies (including the condition that information concerning the identity of the shareholders, partners, or Beneficial Owners with an interest of 25% or more is available from reliable sources), FIs are exempted from taking the normally required identity verification measures. In this regard, FIs should ensure that the disclosure and transparency requirements of the regulated stock exchange are at least equivalent to those of the State, and should document the evidence they obtain concerning the relevant disclosure and transparency requirements.
It is important to note that, while FIs are exempted in such situations from identifying and verifying the identity of the shareholders, partners or Beneficial Owners (or in the event that no such person can be identified, of the relevant senior management officers), they are not exempted from ascertaining the identity of senior management.
Examples of reliable information sources in this regard include, but are not limited to:
- Stock exchange disclosure reports or websites; - Corporate annual reports, websites, or other forms of official public disclosure; - Official or public registries; - Credit reporting agencies; - Recognized, well-established media outlets.
• When FIs suspect that a customer or Beneficial Owner is involved in the commitment of a crime related to money laundering, the financing of terrorism, or the financing of illegal organisations, and they have reasonable grounds to believe that undertaking customer due diligence measures would tip off the customer, then they should not apply CDD measures, but should instead report their suspicion to the FIU along with the reasons that prevented them from carrying out the CDD measures.
6.3 Customer Due Diligence (CDD) Measures
The application of risk-based CDD measures is comprised of several components, in keeping with the customer’s ML/FT risk classification and the specific risk indicators that are identified. Generally, these components include, but are not limited to, the following categories:
• Identification of the customer, Beneficial Owners, beneficiaries, and controlling persons; and the verification of their identity on the basis of documents, data or information from reliable and independent sources (see Section 6.3.1, Customer and Beneficial Owner Identification/Verification).
• Screening of the customer, Beneficial Owners, beneficiaries, and controlling persons, to screen for the applicability of targeted or other international financial sanctions, and, particularly in higher risk situations, to identify any potentially adverse information such as criminal history (see Section 6.4, Enhanced Due Diligence (EDD) Measures).
• Obtaining an understanding of the intended purpose and nature of the Business Relationship, as well as, in the case of legal persons or arrangements, of the nature of the customer’s business and its ownership and control structure (see Section 6.3.3, Establishing a Customer Due Diligence Profile).
• Monitoring and supervision of the Business Relationship, to ensure consistency between the transactions or activities conducted and the information that has been gathered about the customer and their expected behaviour (see Section 6.3.4, Ongoing Monitoring of the Business Relationship).
• Scrutinising transactions undertaken throughout the course of that relationship to ensure that the transactions being conducted are consistent with the FI’s knowledge of the customer, their business and risk profile, including where necessary, the source of funds.
• Ensuring that documents, data or information collected under the CDD process is kept up-to-date and relevant, by undertaking reviews of existing records, particularly for higher risk categories of customers.
In cases involving higher levels of risk, FIs are generally required to exercise enhanced levels of customer due diligence, such as identifying and/or verifying the customer’s source of funds and taking other appropriate risk-mitigation measures (see Section 6.4, Enhanced Due Diligence (EDD) Measures).
As part of their overall AML/CFT framework, FIs should take a risk-based approach in developing the internal CDD policies, procedures and controls. Factors to take into account, include:
• The outcomes of the ML/TF business risk assessment;
• Circumstances, timing, and composition in regard to the application of CDD measures;
• Frequency of reviews and updates in relation to CDD information;
• Extent and frequency of ongoing supervision of the Business Relationship and monitoring of transactions in relation to customers to which CDD measures are applied.
Such policies, procedures and methodologies should be reasonable and proportionate to the risks involved, and, in formulating them, supervised institutions should consider the results of both the NRA and any Topical Risk Assessment. Commensurate with the nature and size of the FIs’ businesses, the policies, procedures and methodologies should also be documented, approved by senior management, and communicated at the appropriate levels of the organisation.
Additional guidance related to these and other key aspects of risk-based CDD measures is provided in the following sub-sections.
6.3.1 Customer and Beneficial Owner Identification and Verification of the Identity
(AML-CFT Decision Articles 4.2(b), 3(a), 5.1, 8.1, 9, 10, 11.2, 13.1, 14.2)
Grounded on the principles of “Know Your Customer” and risk-based CDD, the identification and verification of the identity of customers is a fundamental component of an effective ML/FT risk management and mitigation programme. In accordance with Cabinet Resolution no. 58 of 2020 regulating the Beneficial Owner Procedures (the UBO Resolution), FIs are obliged to identify customers, including the Beneficial Owners, beneficiaries, and controlling persons, whether permanent or walk-in, and whether a natural or legal person or Legal Arrangement, and to verify their identity using documents, data or information obtained from reliable and independent sources.
The specific requirements concerning the timing, extent, and methods of identifying and verifying the identity of customers and Beneficial Owners depend in part on the type of customer (whether a natural or legal person) and on the level of risk involved (also see Sections 6.4, Enhanced Due Diligence (EDD) Measures, and 6.5, Simplified Due Diligence (SDD) Measures). Thus, the type and nature of the customer (including Beneficial Owners, beneficiaries, and controlling persons) should be considered as risk factors in determining the type of CDD that should be applied, whether standard CDD, EDD or SDD. However, the core components of a customer’s identification generally remain the same in all cases. They are:
• Personal data, including details such as the name, passport or identity card number, country of issuance, date issuance and expiry date of the identity card or passport, nationality, date and place of birth (or date and place of establishment or incorporation, in the case of a legal person or arrangement); and
• Principal address, including evidence of the permanent residential address of a natural person, or the registered address of a legal person or arrangement.
In taking adequate CDD measures, FIs are obliged at a minimum to identify and verify the identity of the customer as specified in the relevant articles of the AML-CFT Decision. In fulfilling these requirements, FIs should use a risk-based approach to determine the internal policies, procedures and controls they implement in relation to the identification and verification of customers (including the Beneficial Owners, beneficiaries, and controlling persons). The CDD policies and procedures that FIs apply should be reasonable and proportionate to the risks involved, and, in formulating them, entities should consider the following guiding principles.
In relation to natural persons:
• The verification of a customer’s identity, including their address, should be based on original, official (i.e. government-issued) documents whenever possible. When that is not possible, FIs should augment the number of verifying documents or the amount of information they obtain from different independent sources. In particular, when verifying the UAE ID card, FIs licensed by the Central Bank must use the online validation gateway of the Federal Authority for Identity & Citizenship and keep a copy of the UAE ID and its digital verification. They should also identify the lack of official documents and the use of alternative means of verification as risk factors when assessing the customer’s ML/FT risk classification.
An example of alternative verification means is verification by way of digital identification systems. Such a digital identification systems should rely upon technology, adequate governance, processes and procedures that provide appropriate levels of confidence that the system produces accurate results. The FATF Guidance on Digital Identity of March 2020 provides further information on how to making a risk-based determination of whether a particular digital ID system provides an appropriate level of reliability and independence.
• The identification data should include the name, nationality, date of birth and place of birth, and national identification number of a natural person.
• With regard to the identification and verification of the identity of foreign nationals, whether customers or Beneficial Owners, beneficiaries or controlling persons, FIs should take steps to understand and request only those types of identification documents that are legally valid in the relevant jurisdictions. Furthermore, when verifying the identity of foreign nationals associated with high-risk factors, FIs should validate the authenticity of customer identification documents obtained. Some of the methods that FIs may consider in order to do so, commensurate with the nature and size of their businesses, include but are not limited to:
- Relying on information from the relevant foreign embassy or consulate, or the relevant issuing authority; - Using commercially available applications to validate the information in machine-readable zones (MRZs) or biometric data chips of foreign identification documents.
• The types of address verification that may generally be considered acceptable include, but are not limited to, the following categories of documents issued in the name of the customer:
- Bills or account statements from public utilities, including electricity, water, gas, or telephone line providers; - Local and national government-issued documents, including municipal tax records; - Registered property purchase, lease or rental agreements; - Documents from supervised third-party financial institutions, such as bank statements, credit or debit card statements, or insurance policies.
In situations where natural persons do not have this documentation in their own name, for instance because they share accommodation or do not (yet) have a permanent or own residence, other evidence of address may be used as long as this evidence gives the FI reasonable confidence. Where the FI has determined that an individual has a valid reason for being unable to produce the usual documentation to verify the address and who would otherwise be excluded from establishing a business relationship with the FI, the address can be verified by other means, provided the FI is satisfied that the method employed adequately verifies the address of the natural person and any additional risk has been appropriately mitigated.
This can for instance be evidence of entitlement to a state or local authority-funded benefit, pension, educational or other grant, or a letter from a reputable employer or school stating the address.
In relation to legal persons and legal arrangements:
• In addition to the identifying and verifying the identity of customers, Beneficial Owners, beneficiaries, and controlling persons, FIs should verify the identity of any person legally empowered to act or transact business on behalf of the customer, whether the customer is a legal or natural person. Such persons may include:
- Signatories or other authorized persons, or persons with authorised remote access credentials to an account, such as internet or phone banking users; - Parents or legal guardians of a minor child, or legal guardians of a physically or mentally disabled or incapacitated person; - Attorneys or other legal representatives, including liquidators or official receivers of a legal person or arrangement.
In the event that a legally empowered representative is also a legal person or Legal Arrangement, the normal CDD procedures for such entities should be applied.
• When verifying that a person purporting to act on behalf of a customer is so authorised, the following types of documents may generally be considered to be acceptable:
- A legally valid power-of-attorney; - A properly executed resolution of a legal person’s or Legal Arrangement’s governing board or committee; - A document from an official registry or other official source, evidencing ownership or the person’s status as an authorised legal representative; - A court order or other official decision.
• As part of their procedures for identifying and verifying the identity of customers, and for authenticating the original documents upon which the verification is based, FIs should include procedures for the certification of the customer identification and address documentation they obtain. Such procedures may encompass certification by employees of the FI (for example, by including the name, title of position, date and signature of the verifying employee(s) on the copies of documents maintained on file), as well as by reputable third parties (for example, by including the name, organization, title of position, date and signature of the verifying person, along with a statement representing that the copy of the document is a “true copy of the original”). In cases where documents are obtained from foreign sources in countries which are members of The Hague Apostille Convention, consideration should be given to requesting documents certified by Apostille seal.
• Whenever possible, FIs should incorporate a “four-eyes” principle (review by at least two people) into their procedures with regard to the verification of customer identification documentation and other CDD information, as well as with regard to the entry of the relevant data into their information systems.
6.3.2 CDD Measures Concerning Wire Transfers
(AML-CFT Decision Articles 27-30)
Financial institutions are obliged to undertake certain CDD measures concerning wire transfers, as laid out in detail in the above-referenced articles of the AML-CFT Decision. In particular, these measures relate to the identification of the originators and beneficiaries; the maintenance of information in regard to the same; and the implementation of risk-based policies and procedures for handling the disposition of wire transfers and for taking appropriate follow-up action.
The purpose of these measures are to ensure that information on the originator and the beneficiary shall accompany (meaning sent at the same time but not necessarily in the same message) cross-border wire transfers at all stages of its execution in case the amount of the transfer of funds equals or exceeds AED 3,500 or equivalent in any other currency.
The FI of the originator (or payer) shall ensure that the transfer of funds is accompanied by the information on the originator and beneficiary (or payee) as follows:
Information on the originator:
• The name of the originator (in case of natural person – the name and surname);
• The originator’s account number (or in absence thereof the transfer shall be accompanied by a unique transaction reference number);
• The originator’s address, identification document number or customer identification number, and date and place of birth.
Information on the beneficiary:
• The name of the beneficiary (in case of natural person – the name and surname); • The beneficiary’s account number (or in absence thereof, a unique transaction reference number).
In case of cross-border wire transfers of less than AED 3,500 or equivalent it not required to verify the accuracy of the above-mentioned information, unless there are suspicions of ML or TF.
Also for domestic wire transfers, the FI of the originator shall ensure that above-mentioned information is included, unless this information can be made available to the FI of the and by other means.
The FI of the originator shall not execute the transfer if it has not verified the identity of the originator. The FI of the beneficiary shall not credit the beneficiary’s account or make the funds available for the beneficiary if it has not conducted verification of the beneficiary’s identity.
The FI of the beneficiary is required to implement effective procedures to identify the received transfers that lack information about the originator and the beneficiary, in real-time or as part of the post-event monitoring process. This will include risk-based procedures whether transactions that lack the required information are to be executed, returned, suspended or transferred to the account of the beneficiary, as well as procedures related to the follow-up actions regarding these transfers, including to request the information on the originator and the beneficiary.
An intermediary FI ensures that all information about the originator and the beneficiary accompanied with the cross-border wire transfer is transferred to the beneficiary or other intermediary provider. Should there be technical limitations that prevent the required information accompanying a cross-border wire transfer from remaining with a related domestic wire transfer, the intermediary FI shall keep a record of all the information received from the ordering FI or another cross-border intermediary FI.
The intermediary FI is required to implement effective risk-based procedures to identify the received transfers that lack information about the originator and the beneficiary, in real-time or as part of the post-event monitoring process.
The procedures can include defining and documenting specific AML/CFT system parameters (such as transaction value, aggregate transaction amounts at the customer level, customer risk classification, or others) which would trigger an exception to straight-through processing and require manual review and intervention. This will also include procedures for determining when to execute, reject, or suspend a wire transfer lacking required information and the appropriate follow-up action.
Where an FI repeatedly fails to provide the required information on the originator and the beneficiary, the beneficiary’s or intermediary FI, taking into consideration the risks and frequency of the violations by the FI of the originator, shall take steps, which may initially include the issuing of warnings and setting deadlines. These steps can ultimately consist of rejecting any future transactions from the FI or restricting or terminating its business relationship with that FI.
Similar requirements apply to VASPs. Originating VASPs obtain and hold required and accurate originator information and required beneficiary information on virtual asset transfers, submit the above information to the beneficiary VASP or FI (if any) immediately and securely. Beneficiary VASPs obtain and hold required originator information and required and accurate beneficiary information on virtual asset transfers. For the purposes of applying the wire transfer requirements to VASPs, all virtual asset transfers are to be treated as cross-border.
In addition to the above, as part of their ongoing account monitoring procedures, FIs should also review the purpose of wire transfers, as indicated in their description fields, for potential red-flag indicators (see Section 7.2, Identification of Suspicious Transactions).
6.3.3 CDD Measures Concerning Legal Persons and Arrangements
(AML-CFT Decision Articles 8, 9, 37.1-3)
FIs are obliged to undertake CDD measures concerning legal persons and Legal Arrangements, including identification and verification of the identity of the Beneficial Owners, beneficiaries, and other controlling persons, in accordance with the provisions of the AML-CFT Decision. In fulfilling these requirements, they should take the following guidance into consideration:
• Without prejudice to the provisions of Article 9.1(b) of the AML-CFT Decision, when customers that are legal persons are owned or controlled by other legal persons or Legal Arrangements (for example, when customers are subsidiaries of a parent company or a Trust), FIs should make reasonable efforts to identify and verify the Beneficial Owners by looking through each layer of legal persons or Legal Arrangements (intermediate entities) until the natural persons with owning or controlling interests of 25% or more in aggregate are identified. Furthermore, in the event of multiple legal persons or arrangements with ownership or controlling interests, even where each legal person or Legal Arrangement owns or controls less than 25%, FIs should consider whether there are indications that the entities may be related by common ownership, which could reach or surpass the Beneficial Ownership threshold level of 25% in aggregate.
• When undertaking CDD measures on Legal Arrangements which allow funds or other forms of assets to be added or contributed to the arrangement after the initial settlement and by any persons other than the identified settlor(s), FIs should take the necessary steps to ascertain and verify the identity of the Beneficial Owners, and to understand the nature of their relationship with the Legal Arrangement. For customers that are trusts or other legal arrangements, the FI should verify the identity of beneficial owners, being the settlor, the trustee(s), the protector (if any), the beneficiaries or class of beneficiaries, and any other natural person exercising ultimate effective control over the trust (including through a chain of control/ownership), or equivalent or similar positions for other legal arrangements. For beneficiaries of trusts or other legal arrangements that are designated by characteristics or by class, the FI should obtain sufficient information concerning the beneficiary to satisfy the FI that it will be able to establish the identity of the beneficiary at the time of the payout or when the beneficiary intends to exercise vested rights.
• The AML-CFT Decision obliges trustees in Legal Arrangements to maintain basic information relating to intermediaries, who are subject to supervision, and service providers, including consultants, investors or investment advisors, directors, accountants and tax advisors, who have responsibilities in relation to its management. In order to understand the control structure of a customer that is a Legal Arrangement, FIs should obtain this information from the trustees, representatives, or governing or managing officials and including it in the customer’s CDD profile. They should also give the same consideration to other forms of Legal Arrangements and their controlling persons (such as, for example, foundations, membership clubs, religious institutions, or others, along with their founders, representatives and other governing or managing officials).
6.3.4 CDD Measures for Life Insurance Activities
For life or other investment-related insurance business, FIs should, in addition to the CDD measures required for the customer and the beneficial owner, conduct the following CDD measures on the beneficiary(ies) of life insurance and other investment related insurance policies, as soon as the beneficiary(ies) are identified/designated:
(a) For beneficiary(ies) that are identified as specifically named natural or legal persons or legal arrangements – taking the name of the person;
(b) For beneficiary(ies) that are designated by characteristics or by class (e.g. spouse or children at the time that the insured event occurs) or by other means (e.g. under a will) – obtaining sufficient information concerning the beneficiary to satisfy the financial institution that it will be able to establish the identity of the beneficiary at the time of the payout. The information collected under (a) and/or (b) should be recorded and maintained.
For both the cases referred to above, the verification of the identity of the beneficiary(ies) should occur at the time of the payout.
In determining whether enhanced CDD measures are applicable, an FI should take into account as a factor the beneficiary of a life insurance policy. If an FI determines that a beneficiary who is a legal person or a Legal Arrangement presents a higher risk, then the enhanced CDD measures should include reasonable measures to identify and verify the identity of the beneficial owner of the beneficiary, at the time of payout.
In case an FI cannot comply with this, the FI should consider filing an STR with the FIU.
6.3.5 Ongoing Monitoring of the Business Relationship
(AML-CFT Decision Article 4.2(b), Article 4.3(c), 7.1)
With regard to established Business Relationships, FIs are obliged to undertake ongoing supervision of customers’ activity, including monitoring of transactions executed throughout the course of the relationship to ensure that they are consistent with the information, types of activity, and the risk profiles of the customers. FIs should use a risk-based approach to determine the policies, methods, procedures and controls they implement in relation to monitoring customers’ transactions and activities, as well as in regard to the extent of monitoring for specific customers or categories of customers.
As part of a risk-based approach to AML/CFT, in the case of customers or Business Relationships identified as high risk, FIs are expected to investigate and obtain more information about the purpose of transactions, and to enhance ongoing monitoring and review of transactions in order to identify potentially unusual or suspicious activities. In the case of customers or Business Relationships that are identified as low risk, FIs may consider monitoring and reviewing transactions at a reduced frequency.
Thus, in keeping with the level of risk involved, FIs should monitor and examine transactions in relation to the CDD information and risk profile of the customer (see Section 6.3, Customer Due Diligence (CDD) Measures, Section 6.4, Enhanced Due Diligence (EDD) Measures, and Section 6.5, Simplified Due Diligence (SDD) Measures). Where necessary, FIs should also obtain sufficient information on the counterparties and/or other parties involved (including but not limited to information from public sources, such as internet searches), in order to determine whether the transactions appear to be:
• Normal (consideration should be given as to whether the transactions are typical for the customer, for the other parties involved, and for similar types of customers);
• Reasonable (consideration should be given as to whether the transactions have a clear rationale and are compatible with the types of activities that the customer and the counterparties are usually engaged in);
• Legitimate (consideration should be given as to whether the customer and the counterparties are permitted to engage in such transactions, such as when specific licenses, permits, or official authorisations are required).
Examples of some of the methods that may be employed for the ongoing monitoring of transactions include, but are not limited to:
• Threshold-based rules, in which transactions above certain pre-determined values, numerical volumes, or aggregate amounts are examined;
• Transaction-based rules, in which the transactions of a certain type are examined;
• Location-based rules, in which the transactions involving a specific location (either as origin or destination) are examined;
• Customer-based rules, in which the transactions of particular customers are examined.
FIs may use all or any combination of the above methods, or any others that are appropriate to their particular circumstances, to effect ongoing monitoring of the Business Relationship. Furthermore, monitoring systems and methods may be automated, semi-automated, or manual, depending on the nature and size of their businesses. Whichever methods FIs elect to use, however, FIs should document them (see Section 9, Record Keeping), obtain senior management approval for them, and periodically review and update them to ensure their effectiveness. FIs should also establish specific monitoring procedures for customers and business relationships which have been reported as suspicious to the FIU (see Section 7.11, Handling of Transactions and Business Relationships after Filing of STRs).
6.3.6 Reviewing and Updating the Customer Due Diligence Information
(AML-CFT Decision Articles 4.2(b), 4.3(b), 7.2, 12)
The timely review and update of CDD information is a fundamental component of an effective ML/FT risk management and mitigation programme. FIs are obliged to maintain the CDD documents, data and information obtained on customers, and their Beneficial Owners or beneficiaries in the case of legal persons or arrangements, up to date. The AML-CFT Decision provides that FIs should update the CDD information on High Risk Customers more frequently, and that, in the absence of a ML/FT suspicion, FIs may update the CDD information of identified low-risk customers less frequently.
In order to be able to update the CDD information of customer in a risk-based manner, FIs should develop internal policies, procedures and controls in relation to the periodic or event-driven review and updating of CDD information. These policies and procedures should be reasonable and proportionate to the risks involved, and, in formulating them, FIs are advised to consider parameters such as:
• Circumstances, timing and frequency of reviews and updates. Generally, FIs should establish clear rules per customer risk category with respect to the maximum period of time that should be allowed to elapse between CDD reviews and updates of customer records. The expiry of a customer’s or Beneficial Owner’s identification documents is a circumstance that call for updating the customer information. Changes in legislation or internal procedures are also a cause for reviewing and updating customer files.
• Additionally, FIs should also establish clear rules with respect to circumstances that would trigger an interim or event-driven review, or the acceleration of a particular customer’s review cycle. Circumstances or events that might trigger an interim review include:
- Discovery of information about a customer that is either contradictory or otherwise puts in doubt the appropriateness of the customer’s existing risk classification or the accuracy of previously gathered CDD information; - Material change in ownership, legal structure, or other relevant data (such as name, registered address, purpose, capital structure) of a legal person or arrangement; - Initiation of legal or judicial proceedings against a customer or Beneficial Owner; - Finding materially adverse information about a customer or Beneficial Owner, such as media reports about allegations or investigations of fraud, corruption or other crimes; - Qualified opinion from an independent auditor on the financial statements of a legal entity customer; - Transactions that indicate potentially unusual or suspicious transactions or activities.
• Components and extent of reviews and updates. In keeping with the nature and size of their businesses, FIs should clearly define the moments, contents and extent of CDD reviews for Business Relationships in different risk categories, including which data elements, documents, or information should be examined and updated if necessary. In this regard, FIs are advised that tools such as checklists and procedural manuals will help to enhance the effectiveness of CDD reviews and updates. Examples of procedures might include, but are not necessarily limited to:
- When the source of wealth or the source funds of a customer should be verified; - When additional inquiries or investigations should be made pertaining to the nature of a customer’s business, the purpose of a Business Relationship, or the reasons for a transaction; - How much of a customer’s transactional history, including how many and which specific transactions or transaction types, should be reviewed as part of a periodic or an interim review.
• Organisational responsibilities. In keeping with the nature and size of their businesses, FIs should consider clearly defining the relevant organisational arrangements in relation to the CDD review and update process. Examples of such responsibilities might include, but are not necessarily limited to:
- Carrying out reviews and updates; - Escalating and/or reporting situations in which risk classifications should be changed, Business Relationships should be suspended or terminated, or potentially unusual or suspicious activities should be further investigated; - Approving or rejecting reviews of Business Relationships (including senior management involvement with regard to PEPs and other High Risk Customers); - Undertaking CDD file remediation measures when necessary; - Auditing the quality of CDD reviews and updates; - Maintaining records with regard to CDD reviews and updates, in accordance with statutory record-keeping requirements (see Section 9, Record Keeping).
6.4 Enhanced Due Diligence (EDD) Measures
(AML-CFT Decision Articles 4.2(b), 7.2, 15, 22, 25)
In keeping with a risk-based approach to CDD, FIs are obliged to enhance their CDD measures with regard to customers identified as high-risk, including the specific categories of customers as provided for in the relevant articles of the AML-CFT Decision, such as politically exposed persons (PEPs) (see Section 6.4.1, Requirements for Politically Exposed Persons), customers associated with high-risk countries (see Section 6.4.3, Requirements for High-Risk Countries), and correspondent relationships (see Section 6.4.4, Requirements for Correspondent Relationships).
Generally speaking, EDD involves a more rigorous application of CDD measures, including elements such as:
• Increased scrutiny and higher standards of verification and documentation from reliable and independent sources with regard to customer identity;
• More detailed inquiry and evaluation of reasonableness in regard to the purpose of the Business Relationship, the nature of the customer’s business, the customer’s source of funds and source of wealth, and the purpose of individual transactions;
• Increased supervision of the Business Relationship, including the requirement for higher levels of management approval, more frequent monitoring of transactions, and more frequent review and updating of customer due diligence information.
EDD means that FIs should intensify their measures, specifically by obtaining further evidence and supporting documentation. FIs should obtain additional information and evidence from high-risk customers such as:
○ Source of funds (revenue) and source of wealth; ○ Identifying information on individuals with control over the customer (legal person or arrangement) or account, such as signatories or guarantors; ○ Occupation or type of business; ○ Financial statements; ○ Banking references; ○ Domicile; ○ Proximity of the customer’s residence, place of employment or place of business to the FI; ○ Description of the customer’s primary trade area and whether international transactions are expected to be routine; ○ Description of the business operations, the anticipated volume of currency and total sales, and a list of major customers and suppliers; and ○ Explanations for changes in account activity.
In addition, FIs should also apply specific EDD measures in case there are doubts about the accuracy or appropriateness of a customer’s ML/FT risk classification in order to determine the appropriate risk classification. EDD should also be applied when there are red-flag indicators of potentially unusual or suspicious transactions or activities. In all cases in which EDD is applied, FIs should ensure that they take reasonable measures to obtain adequate, substantiated, information about the customer, commensurate with the level of the risks identified.
As part of their overall AML/CFT framework, FIs should develop risk-based internal policies, procedures and controls in connection with the application of EDD measures. Examples of the some of the factors they should consider when developing the risk-based policies include:
• the ML/FT risks identified in the ML/TF business risk assessment;
• Circumstances, timing, and composition regarding the application of EDD measures;
• Frequency of reviews and updates in relation to information on high-risk customers;
• Extent and frequency of ongoing monitoring of the Business Relationship and monitoring of transactions in relation to high-risk customers.
Such policies, procedures and methodologies should be reasonable and proportionate to the risks involved, and, in formulating them, FIs should consider the results of the NRA, any Topical Risk Assessment and their own ML/FT business risk assessments. Commensurate with the nature and size of the FIs’ businesses, the policies, procedures and methodologies should also be documented, approved by senior management, and communicated at the appropriate levels of the organisation.
Additional guidance regarding the application of EDD measures to statutory high-risk Business Relationship categories is provided in the following sub-sections.
6.4.1 Requirements for Politically Exposed Persons (PEPs)
Due to their potential ability to influence government policies, determine the outcome of public funding or procurement decisions, or obtain access to public funds, politically exposed persons (PEPs) are classified as high-risk individuals from an AML/CFT perspective. The AML-CFT Law and the AML-CFT Decision define PEPs as:
“Natural persons who are or have been entrusted with prominent public functions in the State or any other foreign country such as Heads of States or Governments, senior politicians, senior government officials, judicial or military officials, senior executive managers of state-owned corporations, and senior officials of political parties and persons who are, or have previously been, entrusted with the management of an international organisation or any prominent function within such an organisation; and the definition also includes the following:
• Direct family members (of the PEP, who are spouses, children, spouses of children, parents).
• Associates known to be close to the PEP, which include:
- Individuals having joint ownership rights in a legal person or arrangement or any other close Business Relationship with the PEP. - Individuals having individual ownership rights in a legal person or arrangement established in favour of the PEP.
FIs are obliged to put in place appropriate risk management systems to determine whether a customer, Beneficial Owner, beneficiary, or controlling person is a PEP. In addition to undertaking standard CDD procedures, FIs are also required to take reasonable measures to establish the source of funds and the source of wealth of customers and Beneficial Owners identified as PEPs. In this regard, and commensurate with the nature and size of their businesses, FIs should take measures that include:
• Implementing automated screening systems which screen customer and transaction information for matches with known PEPs;
• Incorporating thorough background searches into their CDD procedures, using tools such as:
- Manual internet search protocols; - Public or private databases; - Publicly accessible or subscription information aggregation services; - Commercially available background investigation services.
If a customer, Beneficial Owner, beneficiary, or controlling person is identified as a PEP, FIs are required to take reasonable measures to establish the PEP’s source of funds and source of wealth. In this regard, they should also evaluate the legitimacy of the source of funds and source of wealth, including making reasonable investigations into the individual’s professional and financial background.
Furthermore, FIs are also required to obtain senior management approval before establishing a Business Relationship with a PEP, or before continuing an existing one. In regard to the latter, senior management should be notified and their approval should be obtained for the continuance of a PEP relationship each time any of the following situations occur:
• An existing customer, Beneficial Owner, beneficiary, or controlling person becomes, or is newly identified as, a PEP;
• An existing PEP Business Relationship is reviewed and the CDD information is updated, either on a periodic or an interim basis, according to the organisation’s internal policies and procedures;
• A material transaction that appears unusual or illogical for the PEP Business Relationship is identified;
• The beneficiary or Beneficial Owner of a life insurance policy or family takaful insurance policy is identified as a PEP, and in case higher risks are identified, the overall Business Relationship should also be thoroughly examined and consideration given to filing an STR. Senior management should be informed before the payout of the policy proceeds.
With regard to identified Domestic PEPs and individuals who were previously (but are no longer) entrusted with prominent functions at international organisations, the AML-CFT Decision provides that FIs should implement the measures described above when, apart from their PEP status, the Business Relationships associated with such persons could be classified as high-risk for any other reason.
The handling of a customer who is no longer entrusted with a prominent public function should be based on an assessment of risk. This risk based approach requires that FIs assess the ML/FT risk of a PEP who is no longer entrusted with a prominent public function, and take effective action to mitigate this risk. Possible risk factors are the level of (informal) influence that the individual could still exercise; the seniority of the position that the individual held as a PEP; or whether the individual’s previous and current function are linked in any way (e.g., formally by appointment of the PEPs successor, or informally by the fact that the PEP continues to deal with the same substantive matters).
6.4.2 EDD Measures for High-Risk Customers or Transactions
(AML-CFT Decision Article 4.2(b))
FIs are obliged to apply EDD measures to manage and mitigate the risks associated with identified High Risk Customers and/or transactions. The AML-CFT Decision defines a High Risk Customers as including those who represent a risk:
“…either in person, activity, Business Relationship, nature or geographical area, such as a customer from a high-risk country or non-resident in a country that does not hold an identity card, or a customer having a complex structure, performing complex operations or having unclear economic objective, or who conducts cash-intensive operations, or operations with an unknown third party...”
Examples of the EDD measures that should be taken by FIs are laid out in the relevant article of the AML-CFT Decision. When carrying out such measures (especially as regards obtaining and investigating more information about the nature of the customer’s business, purpose of the Business Relationship, or reason for the transaction), FIs should pay particular attention to the reasonableness of the information obtained, and should evaluate it for possible inconsistencies and for potentially unusual or suspicious circumstances. Examples of factors that FIs should take into consideration in this regard include, but are not limited to:
• An illogical reason for a foreign customer’s or Beneficial Owner’s presence, or establishment of a Business Relationship, in the UAE;
• Consistency between the nature of the customer’s business and transactions and the customer’s or Beneficial Owner’s professional background and employment history, in regard to which FIs may find it helpful to obtain background information from reliable and independent sources, as well as from internet and social media searches, and from the customer’s or Beneficial Owner’s CV;
• The level of complexity and transparency of the customer’s transactions, especially in comparison with the customer’s or Beneficial Owner’s educational and professional background;
• The level of complexity and transparency of the customer’s legal structure of legal persons or arrangements;
• The nature of any other business interests of the customer or Beneficial Owner, including any other legal persons or arrangements owned or controlled;
• Consistency between the customer’s line of business and that of the counterparty to the customer’s transactions (as identified, for example, through internet searches).
Additionally, and commensurate with the nature and size of their businesses, when carrying out EDD measures in respect of High Risk Customers or Beneficial Owners, FIs should take appropriate risk-mitigation measures such as, but not limited to:
• Performing background checks (among other via internet searches, public databases, or subscription information aggregation services) to screen for possible matches with targeted and other international financial sanctions lists, indications of criminal activity (including financial crime), or other adverse information;
• Using more rigorous methods for the verification of the customer’s or Beneficial Owner’s identity in regard to High Risk Customers (see Section 6.3.1, Customer and Beneficial Owner Identification/Verification for more information).
6.4.3 Requirements for High-Risk Countries
(AML-CFT Law Article 16.1(e); AML-CFT Decision Article 22, 44.7, 60)
FIs are obliged to implement EDD measures commensurate with the ML/FT risks associated with Business Relationships and transactions with customers from high-risk countries subject to a Call for Action and Jurisdictions under Increased Monitoring and the countries identified by NAMLCFTFC. In the case of legal persons and arrangements, their Beneficial Owners, beneficiaries and other controlling persons from high-risk countries.
FIs can obtain guidance on high risk countries from NAMLCFTFC, from the FATF list of High-Risk Jurisdictions subject to a Call for Action and Jurisdictions under Increased Monitoring, and from NRA report. In addition, reference can also be made to the Organisation for Economic Cooperation and Development (OECD) list of jurisdictions classified as tax havens. The Basel AML index can be a useful source to determine the risk of a country.
Examples of some of the measures FIs should apply in this regard include:
• Increased scrutiny and higher standards of verification and documentation from reliable and independent sources with regard to the identity of customers, Beneficial Owners, beneficiaries and other controlling persons;
• More detailed inquiry and evaluation of reasonableness in regard to the purpose of the Business Relationship, the nature of the customer’s business, the customer’s source of funds, and the purpose of individual transactions;
• Increased investigation to ascertain whether the customers or related persons (Beneficial Owners, beneficiaries and other controlling persons, in the case of legal persons and arrangements) are foreign PEPs;
• Increased supervision of the Business Relationship, including the requirement for higher levels of internal reporting and management approval, more frequent monitoring of transactions, and more frequent review/ updating of customer due diligence information.
Additionally, FIs are obliged to implement all specific CDD measures and countermeasures regarding High Risk Countries as defined by the National Committee for Combating Money Laundering and the Financing of Terrorism and Illegal Organisations, including those related to the implementation of the decisions of the UN Security Council under Chapter VII of the Charter of the United Nations, the International Convention for the Suppression of the Financing of Terrorism and the Treaty on the Non-Proliferation of Nuclear Weapons, and other related directives, and those called for by the Financial Action Task Force (FATF) and/or other FSRBs.
In order to fulfil these obligations, and commensurate with the nature and size of their businesses and the risks involved, FIs should establish adequate internal policies, procedures and controls in relation to the application of EDD measures and risk-proportionate effective countermeasures to customers and Business Relationships associated with high-risk countries. Some of the factors to which FIs should give consideration when formulating such policies, procedures and controls, include but are not limited to the following:
• The organisation’s risk appetite with respect to Business Relationships involving high-risk countries;
• Methodologies and procedures for assessing and categorising country risk, and identifying high-risk countries, including the statutorily defined High Risk Countries as established by the NAMLCFTC, and taking into consideration advice or notifications of concerns about weaknesses in the AML/CFT system of other countries issued by the relevant Supervisory Authorities and/or Competent Authorities;
• Determination and implementation of appropriate risk-based controls (for example, certain product or service restrictions, transaction limits, or others) with regard to customers and Business Relationships associated with high-risk countries;
• Organisational roles and responsibilities in relation to the monitoring, management reporting, and risk management of high-risk country Business Relationships;
• Appropriate procedures for the enhanced investigation of Business Relationships involving high-risk countries in relation to their assessment for possible PEP associations;
• Independent audit policies in respect of EDD procedures pertaining to customers/Business Relationships involving high-risk countries and the business units that deal with them.
For all countries identified as high-risk, the FATF calls on all members and urges all jurisdictions to apply EDD, and in the most serious cases, countries are called upon to apply countermeasures to protect the international financial system from the ongoing money laundering, terrorist financing, and proliferation financing risks emanating from the country. However, specific countermeasures which need to be applied by FIs shall be advised by the corresponding supervisory authorities, the FIU or the NAMLCFTC.
6.4.4 Requirements for Correspondent Relationships
Financial Institutions are obliged to fulfil certain due diligence requirements with regard to the correspondent banking relationships and other similar relationships they maintain, regardless of whether these involve foreign or domestic financial institutions. Additional guidance in respect of the measures specified in the relevant article of the AML-CFT Decision is provided below. Similar relationships to which FIs should apply the guidance below include, for example those established for securities transactions or funds transfers.
FIs are prohibited from entering into or maintaining correspondent relationships with shell banks, or with institutions that allow their accounts to be used by shell banks. The AML-CFT Decision defines a shell bank as a “bank that has no physical presence in the country in which it is incorporated and licensed, and is unaffiliated with a regulated financial group that is subject to effective consolidated supervision.”
• FIs are required to collect sufficient information about any receiving correspondent institution for the purpose of identifying and achieving a full understanding of the nature of its business, and to determine, through publicly available information, its reputation and level of AML/CFT controls, including whether it has been subject to a ML/FT investigation or regulatory action.
• FIs are obliged to evaluate the AML/CFT controls applied by the receiving correspondent institution.
• FIs are required to obtain approval from senior management before establishing new correspondent relationships.
• FIs are obliged to understand the responsibilities of each institution in the field of combating the crimes of money laundering, the financing of terrorism and of illegal organisations.
Regulatory and supervisory environments governing the operation of financial institutions around the world vary greatly. Thus, not all foreign financial institutions are subject to the same AML/CFT requirements as FIs in the UAE; and as a consequence, some of these foreign institutions may pose a higher ML/FT risk. To mitigate against these risks, FIs that maintain correspondent relationships with foreign financial institutions should consider implementing adequate procedures to assess and periodically review the relevant regulatory and supervisory frameworks of the countries concerned.
Furthermore, when gathering information about financial institutions with which they maintain correspondent relationships, whether foreign or domestic, FIs should take appropriate steps to assess the nature, size and extent of their businesses in the countries where they are incorporated and licensed, as well as their ownership and management structures (taking into consideration the nature and extent of any PEP involvement), in order to evaluate whether they exhibit the characteristics of shell banks, and whether they offer downstream correspondent services (also known as “nested accounts”) to other banks. If they do offer downstream correspondent services, FIs should also take reasonable steps to understand the types of services offered, the number and types of financial institutions they are offered to, the types of customers those institutions serve, and to identify the associated ML/FT risk issues.
In order to collect sufficient information about the nature of a financial institution and the AML/CFT controls it applies, and to assess the ML/FT risks associated with it, FIs should take appropriate measures such as implementing a suitable correspondent relationships questionnaire and, when necessary, conducting follow-up interviews. (FIs may find the correspondent banking questionnaire which has been developed by the Wolfsberg Group, as well as the Wolfsberg Anti-Money Laundering Principles for Correspondent Banking, instructive in this regard. See Appendix 11.2, Useful Links.)
In addition to obtaining senior management approval prior to establishing new correspondent relationships, FIs should also periodically review and update their due diligence information in relation to the financial institutions with which they maintain correspondent relationships, commensurate with the risks involved (see 6.3.6 Reviewing and Updating the Customer Due Diligence Information). In the event of a deterioration in the risk profile of a financial institution with which a correspondent relationship is maintained, including the discovery of material adverse information concerning the institution, FIs should ensure that senior management is informed and appropriate risk-based measures are taken to assess and mitigate the ML/FT risks involved.
FIs should also maintain agreements or contracts with financial institutions with which they maintain correspondent relationships. In addition to operational details concerning the products and services covered, these agreements should clearly describe each party’s responsibilities in regard to ML/FT risk mitigation, due diligence procedures, and the detailed conditions related to any permitted third-party usage of the correspondent account.
6.4.5 Requirements for Money or Value Transfer Services
(AML-CFT Decision Articles 26, 30)
As part of a risk-based AML/CFT approach, FIs that enter into or maintain Business Relationships with Money or Value Transfer Services (MVTSs) should take adequate CDD measures that are commensurate with the risks involved (see Sections 6.3, Customer Due Diligence (CDD) Measures and 6.4, Enhanced Due Diligence (EDD) Measures). Examples of measures that FIs should consider in this regard include, but are not limited to:
• Ensuring that the MVTS is properly licensed or registered; in particular, when opening any accounts for Hawala Providers, FIs licensed by the Central Bank must physically check the original Hawala Provider registration certificate issued by the Central Bank and keep a copy thereof;
• Obtaining information about and assessing the adequacy of the MVTS’s AML/CFT policies, procedures and controls, including those related to Wire Transfers as stipulated in the relevant provisions of the AML-CFT Decision;
• Obtaining the MVTS’s list of agents, and identifying and assessing the associated ML/FT risks, especially with regard to high-risk countries or other identified high-risk factors;
• Obtaining sufficient information about the MVTS’s ownership and management structure (including taking into consideration the possibility of PEP involvement), the nature and scope of its business, the nature of its customer base, and the geographic areas in which it operates, so as to be in a position to identify, assess, and manage or mitigate the associated ML/FT risks.
FIs that enter into or maintain relationships with MTVSs should also use a risk-based approach to determine the appropriate internal AML/CFT policies, procedures and controls FIs implement in relation to the risk assessment, risk classification, and the type and extent of CDD they perform on the MVTSs. The policies and procedures that FIs apply should be reasonable and proportionate to the risks involved, and should be adequately documented, senior management approved, and communicated to the relevant employees of the organisation.
6.4.6 Requirements for Non-Profit Organisations
Non-Profit Organisations (NPOs) can often pose increased risks in regard to money laundering, the financing of terrorism, and the financing of illegal organisations. As part of an effective risk-based approach to AML/CFT, FIs that enter into or maintain Business Relationships with NPOs should take adequate CDD measures that are commensurate with the risks involved (see Sections 6.3, Customer Due Diligence (CDD) Measures and 6.4, Enhanced Due Diligence (EDD) Measures). Examples of measures that FIs should consider include, but are not limited to:
• Ensuring that the NPO is properly licensed or registered; in particular, when opening any accounts for Non-Profit Organisations, FIs licensed by the Central Bank must obtain an original signed letter from the Ministry of Community Development for opening accounts to collect donations and an authorization from the UAE Red Crescent for conducting financial transfers out of the UAE through some of these accounts;
• Obtaining information about and assessing the adequacy of the NPO’s AML/CFT policies, procedures and controls;
• Obtaining sufficient information about the NPO’s legal, regulatory and supervisory status, including requirements relating to regulatory disclosure, accounting, financial reporting and audit (especially where community/social or religious/cultural organisations are involved, and when those organisations are based, or have significant operations, in jurisdictions that are unfamiliar or in which transparency or access to information may be limited for any reason);
• Obtaining sufficient information about the NPO’s ownership and management structure (including taking into consideration the possibility of PEP involvement); the nature and scope of its activities; the nature of its donor base, as well as of that of the beneficiaries of its activities and programmes; and the geographic areas in which it operates, so as to be in a position to identify, assess, and manage or mitigate the associated ML/FT risks;
• Performing thorough background checks (including but not limited to the use of internet searches, public databases, or subscription information aggregation services) on the NPO’s key persons, such as senior management, branch or field managers, major donors and major beneficiaries, to screen for possible matches with targeted and other international financial sanctions lists, indications of criminal activity (including financial crime), or other adverse information.
FIs that enter into or maintain relationships with NPOs should also use a risk-based approach to determine the appropriate internal AML/CFT policies, procedures and controls the FIs implement in relation to the risk assessment, risk classification, and the type and extent of CDD they perform on NPOs. The policies and procedures that FIs apply should be reasonable and proportionate to the risks involved, and should be adequately documented, senior management approved, and communicated to the relevant employees of the organisation.
6.5 Simplified Due Diligence (SDD) Measures
(AML-CFT Decision Articles 4.3, 5, 10)
In keeping with a risk-based approach to CDD, under certain circumstances and in the absence of a ML/FT suspicion, FIs are only permitted to exercise simplified customer due diligence measures (SDD) with regard to customers identified as low-risk through an adequate analysis of risks.
SDD generally involves a more lenient application of certain aspects of CDD measures, including elements as:
• A reduction in verification requirements with regard to customer or Beneficial Owner identification;
• Fewer and less detailed inquiries in regard to the purpose of the Business Relationship, the nature of the customer’s business, the customer’s source of funds, and the purpose of individual transactions;
• More limited supervision of the Business Relationship, including less frequent monitoring of transactions, and less frequent review/updating of customer due diligence information.
Specifically, the AML-CFT Decision permits the application of SDD in the following circumstances:
• Identified low-risk customers. When the customer or Beneficial Owner is identified as posing a low risk of ML/FT, FIs are permitted to complete the verification of their identity after the establishment of a Business Relationship under the conditions specified in the relevant provisions of the AML-CFT Decision. In this regard, FIs are required to implement appropriate and effective measures to control the risks of ML/FT, including the risks in regard to the customer or Beneficial Owner benefitting from the Business Relationship prior to the completion of the verification process. Examples of such measures which FIs may consider taking in this regard are, among others:
- Holding funds in suspense or in escrow until the verification of the identity is completed; - Making the completion of verification of the identity a condition precedent to the closing of a transaction.
It should be noted that the provision allowing a relaxation of the timing for the completion of the identity verification procedures does not imply that FIs are permitted to establish a Business Relationship without any customer identification at all. On the contrary, in all cases, the basic identification information in relation to the customer (whether a natural or legal person or arrangement) should be obtained; however under the specified conditions, FIs are permitted to establish the Business Relationship prior to the completion of the verification process, which may include such steps as: obtaining appropriate supporting documentation, certifications or attestations, when necessary (for example, as regards the corporate documents of a legal person); or obtaining all the necessary information related to the relevant parties of a legal person or Legal Arrangement, such as Beneficial Owners, settlors, trustees or executors, protectors, beneficiaries, or other controlling persons.
• Listed companies. FIs are exempted from identifying and verifying the identity of any shareholder, partner or Beneficial Owner of a legal person under the conditions specified in the relevant provisions of the AML-CFT Decision. Namely:
- When the relevant information on the shareholder, partner or Beneficial Owner is obtained from reliable sources; and - When the customer, or the owner holding the controlling interest of the customer, is a company listed on a regulated stock exchange subject to adequate disclosure and transparency requirements related to Beneficial Ownership; or when the customer, or the owner holding the controlling interest of a legal entity customer, is the majority-held subsidiary of such a listed company.
Without prejudice to the above, in the case of foreign stock exchanges, FIs should take steps to adequately assess and document the relevant disclosure and transparency requirements related to Beneficial Ownership, and to ensure that they are at least equivalent to those of the UAE.
In addition, FIs should be aware that, regardless of the exemption mentioned above, FIs are required with respect to listed companies to verify that any person purporting to act on behalf of the customer is so authorised, and verify the identity of that person.
As part of their overall AML/CFT framework, FIs should use a risk-based approach to determine the internal policies, procedures and controls they implement in connection with the application of SDD procedures. Examples of some of the factors they should consider when developing their risk-based policies include:
• the ML/FT risks identified in the ML/TF business risk assessment, especially with regard to low-risk categories of customers;
• Circumstances, timing, and composition in regard to the application of SDD measures;
• Frequency of reviews and updates in relation to customer SDD information;
• Extent and frequency of ongoing supervision of the Business Relationship and monitoring of transactions in relation to customers to which SDD measures are applied.
Such policies, procedures and methodologies should be reasonable and proportionate to the risks involved, and, in formulating them, FIs should consider the results of both the NRA and any Topical Risk Assessment and their own ML/FT business risk assessments. Commensurate with the nature and size of the FIs’ businesses, the policies, procedures and methodologies should also be documented, approved by senior management, and communicated at the appropriate levels of the organisation.
6.6 Reliance on a Third Party
(AML-CFT Decision Articles 19)
Under certain conditions, the AML-CFT Decision permits FIs to rely on third parties to undertake the required CDD measures, including those measures specifically laid out in regard to identified high-risk countries (see Section 6.4.3, Requirements for High-Risk Countries), with the responsibility for the validity of the measures resting directly with the FIs. Among the conditions set forth in the AML-CFT Decision concerning the reliance on third parties, it is stipulated that FIs shall:
“Ensure that the third party is regulated and supervised, and adheres to the CDD measures towards Customers and record-keeping provisions of the present Decision.”
In order to fulfil this obligation, FIs that rely on third parties to undertake CDD measures on their behalf should implement adequate measures, in keeping with the nature and size of their businesses, to ensure the third party’s adherence to the requirements of the AML-CFT Law and the AML-CFT Decision in relation to CDD measures. Examples of such measures include:
• Clearly defined procedures for determining the adequacy of a third-party’s CDD and record-keeping measures, including the evaluation of such factors as the comprehensiveness and quality of its AML/CFT policies, procedures and controls; the number of personnel dedicated to CDD; and its audit and/or quality assurance policies in regard to CDD. In this regard, FIs are advised that tools such as questionnaires, scorecards, and on-site visits may be useful in evaluating the adequacy of a third party’s adherence.
• Service-level agreements, clearly setting out the roles and responsibilities of the FI and the third party and specifying the nature of the CDD and record-keeping requirements to be fulfilled.
• Procedures for the certification by third parties of documents and other records pertaining to the CDD measures undertaken.
In addition to the above, when relying on foreign third parties for the undertaking of CDD measures, FIs should take steps to ensure that the AML/CFT regulatory and supervisory framework under which the third party operates is at least equivalent to that of the State. This means that FIs should ensure that the third party is regulated and supervised for AML/CFT purposes, and adheres to the equivalent CDD and record-keeping measures.
Whichever methods are utilized to ensure the adherence of third parties to the statutory CDD and record-keeping requirements, FIs should document and periodically review them for effectiveness.
Reliance on a third party refers to an FI’s reliance on a third party of the entire or part of the CDD process as well as reliance on a third party when to introducing business. FIs should therefore take adequate steps to satisfy themselves that copies of identification data and other relevant documentation relating to the CDD requirements will be made available from the third party upon request without delay. This includes the identification and verification of the identity of customers and Beneficial Owners, beneficiaries or controlling persons of legal entities or arrangements, as well as the investigation and assembly of other relevant customer documents, information and data, as per the statutory CDD and record-keeping requirements. Nevertheless, FIs remain ultimately responsible for the outcome of the CDD process. Furthermore, FIs should themselves assess the risks of the customer, including the customer’s risk profile. FIs should thus document their rationale for the assignment of relevant customer risk classifications, as well as their analysis of the CDD information obtained from the third parties. Moreover, FIs remain themselves responsible for conducting ongoing due diligence on the business relationship and scrutiny of transactions undertaken throughout the course of that relationship.
For the purpose of this guidance, it is important to note that FIs are expected to use documents, data or information from reliable and independent sources in carrying out their CDD obligations, which include, among other things, verifying the identity of customers and Beneficial Owners, beneficiaries or controlling persons of legal entities or arrangements.
Reliable and independent sources may include, but are not necessarily limited to, official bodies such as Competent Authorities, governmental departments or agencies, governmental or state-sponsored business registries, public utilities or similar official enterprises; as well as non-official organisations, such as publicly accessible free or subscription information aggregation services, credit reporting agencies, and others.
FIs are reminded that simply obtaining CDD documents and supporting information from reliable and independent sources during the course of performing their own CDD procedures is not necessarily considered as reliance on a third party. On occasion that FIs during the course of carrying out their own CDD procedures, receive certain documents, information or data from a third-party, FIs should obtain evidence of the third party’s regulatory and supervisory status and good standing, and they should also consider obtaining the third party’s certification that any CDD documents provided by them (such as identification documents, proof of address, or documents corroborating a customer’s source of funds) are true copies of the originals.
Part IV—AML/CFT Administration and Reporting
7. Suspicious Transaction Reporting
(AML-CFT Law Articles 9.1, 15, 30; AML-CFT Decision Articles 16-18)
Under the AML/CFT legal and regulatory framework of the UAE, all FIs are obliged to promptly report to the Financial Intelligence Unit (FIU) suspicious transactions and any additional information required in relation to them, when there are suspicions, or reasonable grounds to suspect, that the proceeds are related to a crime, or to the attempt or intention to use funds or proceeds for the purpose of committing, concealing or benefitting from a crime. FIs are required to put in place and update indicators that can be used to identify possible suspicious transactions.
In order to fulfil these obligations, FIs should implement adequate internal policies, procedures and controls in relation to the identification and the immediate reporting of suspicious transactions. The following sub-sections provide additional guidance in this regard.
7.1 Role of the Financial Intelligence Unit
(AML-CFT Law Articles 9-10; AML-CFT Decision Articles 13, 16, 17.1, 21.2 and 5, 40-43, 46.1-4, 49.2-3)
The FIU of the UAE is established within the premises of the Central Bank, however, the FIU operates independently by legal and regulatory mandate as the central national agency with sole responsibility for performing the following functions:
• Receiving and analysing STRs from FIs and DNFBPs, and disseminating the results of its analysis to the Competent Authorities of the State;
• Receiving and analysing reports of suspicious cases from the Federal Customs Authority;
• Requesting additional information and documents relating to STRs, or any other data or information it deems necessary to perform its duties, from FIs, DNFBPs, and Competent Authorities, including information relating to customs disclosures;
• Cooperating and coordinating with Supervisory Authorities by disseminating the outcomes of its analysis, specifically with respect to the quality of STRs, to ensure the compliance of FIs and DNFBPs with their statutory AML/CFT obligations;
• Sending data relating to STRs and the outcomes of its analyses and other relevant data, including information obtained from foreign FIUs, to national Law Enforcement Authorities, prosecutorial authorities and judiciary authorities when actions are required by those authorities in relation to a suspected crime;
• Exchanging information with its counterparts in other countries, with respect to STRs or any other information to which it has access.
Under the aegis of the National Committee for Combating Money Laundering and the Financing of Terrorism and Illegal Organisations, and for the effective performance of its functions, the FIU maintains operational protocols with numerous national and international Competent Authorities.
The FIU has launched the GoAML system for the purposes of facilitating the filing of STRs by all FIs. FIs shall register themselves on the GoAML system by following the procedure manual and maintain their registration in an active status. The Compliance Officer of the company can register as the user of the system. GoAML provides a secure link of each FI to the FIU through their respective supervisory authorities. The system hosts processes for facilitating filing of STRs. It also has an .xml schema for filing batches of STRs. The guidance documents for filing of STRs are posted on the dashboard of this system. All new licensed FIs shall register themselves immediately after obtaining their financial services license so as to confirm their readiness for filing of STRs from the beginning.
The STRs are received by the FIU and processed for any required further information or documents or for further action by Law Enforcement or Supervisory Authorities. The FIU maintains a record of these STRs, performs a trend analysis to understand the prevailing trends in transactions and sectors or Institutions where possibility of ML or FT exists and this trend analysis is shared with all the registered users of GoAML through the system by means of a periodic trends and typologies report.
7.2 Processing of STRs by the FIU
(AML-CFT Law Articles 9-10; AML-CFT Decision Articles 42, 43.1-3, 49.3)
A core function of the FIU is to conduct operational analysis on STRs and information received from FIs, DNFBPs, as well as from Competent Authorities, and to support the investigations of Law Enforcement Authorities. It does so by identifying specific targets (such as persons, funds, or criminal networks) and by following the trail of specific transactions in order to determine the linkages between those targets and the possible proceeds of crime, money laundering, predicate offences and terrorist financing.
Upon the receipt of STRs or information from reporting institutions or other sources, the FIU assesses the information, prioritises the risk, and performs its own analyses using a variety of information sources and analytical techniques.
In certain cases, the FIU may request additional information from the reporting entity, Competent Authorities, or even from other FIs which also have a business relationship with the subject of its analysis or investigation, through the Integrated Enquiries Management System (IEMS). Upon concluding its analysis or investigation, the FIU may disseminate information about the case to Law Enforcement Authorities or foreign FIUs, and may, at its own discretion, also provide feedback to the reporting entity in the form of instructions regarding required actions to be taken, or recommendations and guidance.
In addition to the above, the FIU also performs strategic analysis, using data aggregated from the STRs and other information it receives, including from national and international Competent Authorities and FIUs of other countries, to identify trends and patterns relating to ML/FT. As a result of this analysis, the FIU may from time to time disseminate enhanced due diligence and fraud alerts to FIs as a preventive measure, and may also disseminate information to FIs about prevalent or new and emerging ML/FT typologies, or other specific risks which FIs should take into consideration.
7.3 Meaning of Suspicious Transaction
(AML-CFT Law Article 16; AML-CFT Decision Article 17.1)
Within the meaning of the AML-CFT Law and its implementing AML-CFT Decision, a suspicious transaction refers to any transaction, attempted transaction, or funds which an FI has reasonable grounds to suspect as constituting—in whole or in part, and regardless of the amount or the timing—any of the following:
• The proceeds of crime (whether designated as a misdemeanour or felony, and whether committed within the State or in another country in which it is also a crime);
• Being related to the crimes of money laundering, the financing of terrorism, or the financing of illegal organisations;
• Being intended to be used in an activity related to such crimes.
It should be noted that the only requirement for a transaction to be considered as suspicious is “reasonable grounds” in relation to the conditions referenced above. Thus, the suspicious nature of a transaction can be inferred from certain information, including indicators, behavioural patterns, or CDD information, and it is not dependent on obtaining evidence that a predicate offence has actually occurred or on proving the illicit source of the proceeds involved. FIs do not need to have knowledge of the underlying criminal activity nor any founded suspicion that the proceeds originate from a criminal activity; reasonable grounds are sufficient.
FIs should also note that transactions need not be completed, in progress or pending completion in order to be considered as suspicious. Attempted transactions, transactions that are not executed and past transactions, regardless of their timing or completion status, which are found upon review to cause reasonable grounds for suspicion, must be reported in accordance with the relevant requirements.
7.4 Identification of Suspicious Transactions
FIs are obliged to put in place indicators that can be used to identify suspicious transactions, and to update those indicators on an ongoing basis in accordance with the instructions of the Supervisory Authorities or the FIU, as well as in keeping with relevant developments concerning ML/FT typologies. FIs should also consider the results of the NRA, any Topical Risk Assessment and their own ML/FT business risk assessments in this regard.
As part of their overall AML/CFT framework, and commensurate with the nature and size of their businesses, FIs should determine the internal policies, procedures and controls they apply in connection with the identification, implementation, and updating of indicators, as well as with the identification and evaluation of potentially suspicious transactions. Some factors that should be considered include, but are not limited to:
• Organisational roles and responsibilities with respect to the implementation and review/updating of the relevant indicators, especially in relation to obligatory indicators required by the Supervisory Authorities or the FIU;
• Operational and IT systems procedures and controls in connection with the application of relevant indicators to processes such as transaction handling and monitoring, customer due diligence measures and review, and alert escalation;
• Staff training in relation to the identification and reporting of suspicious transactions (including attempted transactions), the appropriate use and assessment of the relevant indicators, and the degree and extent of internal investigation that is appropriate prior to the reporting of a suspicious transaction.
FIs should ensure that they have an adequate process and dedicated, experienced staff for the investigation of and dealing with alerts. The investigation of alerts and the conclusion of the investigation should be documented, including the decision to close the alert or to promptly report the transaction as suspicious.
Prompt reporting to the FIU is one of the key elements of the AML/CFT process. This means that FIs must report to the FIU the transaction immediately once the suspicious nature of the transaction becomes clear. This will be the case when from an objective point of view, taking the available information into account, there is a reason to believe that a transaction is suspicious. This means that FIs expeditiously investigate alerts and possible indications of ML/FT and immediately report the transaction upon determining that the transaction should be reported to the FIU. FIs therefore need to able to show that from the moment of the alert immediate and continuous action has been taken.
In this respect, FIs must have a procedure in place that defines the reporting process, and what steps to take in such cases. When investigating alerts it is important to examine the customer’s earlier and related transactions, and to reconsider the customer’s risk profile.
When identifying suspicious transactions, FIs, and their management and employees, should be aware of the facts that, in relation to ML/FT crimes, there is no minimum threshold or monetary value for reporting, and that no amount or transaction size should be considered too small for suspicion. This is of particular significance where the crimes of the financing of terrorism and of illegal organisations is concerned, since typologies related to them may often involve very small amounts of money.
Furthermore, with the exception of obligatory indicators for which reporting is required by the relevant Supervisory Authorities or the FIU, FIs should note that the presence of an indicator means that a transaction needs to be immediately investigated in order to determine whether the transaction needs to be reported. When determining whether a transaction is suspicious or whether there is reasonable ground for a suspicion, FIs should give consideration to the nature of the specific circumstances, including the products or services involved, and the details of the customer in the context of its risk profile. In some cases, patterns of activity or behaviour that might be considered as suspicious in relation to a specific customer or a particular product type, might not be suspicious in regard to another. For this reason, clear internal policies and procedures with regard to alert escalation and investigation, and internal suspicious transaction reporting are critical to an effective ML/FT risk-mitigation programme. This includes an adequate training program that will allow staff to detect possible unusual or suspicious transactions.
While it is impossible to list all the indicators of suspicion in these Guidelines, some useful links to sources of AML/CFT suspicious transaction indicators are provided in Appendix 11.2, Useful Links. A few examples of potentially suspicious transaction types that FIs should take into consideration include:
• Transactions or series of transactions that appear to be unnecessarily complex, that make it difficult to identify the Beneficial Owner, or that do not appear to have an economic or commercial rationale;
• Numbers, sizes, or types of transactions that appear to be inconsistent with the customer’s expected activity and/or previous activity;
• Transactions that appear to be exceptionally large in relation to a customer’s declared income or turnover;
• Large unexplained cash deposits and/or withdrawals, especially when they are inconsistent with the nature of the customer’s business;
• Loan repayments that appear to be inconsistent with a customer’s declared income or turnover;
• Early repayment of a loan followed by an application for another loan;
• Third-party loan agreements, especially when there are amendments to or assignments of the loan agreement;
• Requests for third-party payments, including those involving transactions related to loans, investments, or insurance policies;
• Transactions involving high-risk countries, including those involving “own funds” transfers, particularly in circumstances in which there are no clear reasons for the specific transaction routing;
• Frequent or unexplained changes in ownership or management of Business Relationships;
• Illogical changes in business activities, especially where high-risk activities are involved;
• Situations in which CDD measures cannot be performed, such as when the customers or Beneficial Owners refuse to provide CDD documentation, or provide documentation that is false, misleading, fraudulent or forged.
When reporting an STR in the GoAML system, the user is required to select the most appropriate reason for reporting available from the menu selection provided. More than one reason may also be provided, if deemed necessary. In order to select the appropriate indicator, click ‘Add’ to select the appropriate reason for the report.
Select the reason(s) applicable and then press ‘Close’. Alternatively, the user may search for reasons using the search bar available on the top left when expanding the form. It is imperative that a minimum of one reason for reporting must be selected to avoid rejection of the report by the GoAML system.
7.5 Requirement to Report
(AML-CFT Law Articles 9.1, 15, 24; AML-CFT Decision Articles 13.2, 17.1, 20.2)
FIs are obliged to report transactions to the FIU without delay when there are suspicions, or reasonable grounds to suspect, that the proceeds are related to a crime, or to the attempt or intention to use funds or proceeds for the purpose of committing, concealing or benefitting from a crime. There is no minimum reporting threshold; all suspicious transactions, including attempted transactions, should be reported regardless of the amount of the transaction. There is also no statute of limitations with regard to when the possible crimes or the suspicious transaction took place.
Under federal law and regulations, whether the FI operates in the mainland UAE or in a Financial or Commercial Free Zone, the designated Competent Authority for the reporting of suspicious transactions is the FIU.
Failure to – immediately - report a suspicious transaction, whether intentionally or by gross negligence, is a federal crime. Any person, including FIs or their managers and employees, who fails to perform their statutory obligation to report a suspicion of money laundering, or the financing of terrorism or of illegal organisations, is liable to a fine of no less than AED100,000 and no more than AED1,000,000 and/or imprisonment.
There are no exemptions from the statutory reporting requirement provided for FIs under the AML-CFT Law or AML-CFT Cabinet Decision.
7.6 Procedures for the Reporting of Suspicious Transactions
(AML-CFT Law Article 9; AML-CFT Decision Articles 17.1(a), 21.2)
As the designated Competent Authority for receiving and analysing STRs from all FIs, it is within the purview of the FIU to determine the procedures for the reporting of suspicious transactions. As stated in the AML-CFT Decision, FIs shall report STRs “via the electronic system of the FIU or by any other means approved by the FIU”, which is the FIU’s GoAML system.
Without prejudice to the above, it should be noted that the AML-CFT Decision provides for the reporting of STRs to be effected by the designated compliance officer of the FI. Specifically, the Cabinet Decision states that the duty of a compliance officer is to:
“Review, scrutinise and study records, receive data concerning Suspicious Transactions, and take decisions to either notify the FIU or maintain the Transaction with the reasons for maintaining while maintaining complete confidentiality.”
In this regard, as part of their overall risk-based AML/CFT framework and commensurate with the nature and size of their businesses, FIs should establish appropriate policies, procedures and controls pertaining to the internal reporting by their managers and employees of potentially suspicious transactions, including the provision of the necessary records and data, to the designated AML/CFT compliance officer for further analysis and reporting decisions, as well as to the reporting of STRs by the compliance officer to the FIU. The relevant policies, procedures and controls should take into consideration such factors as:
• Policies and procedures for the internal investigation of potentially suspicious transactions prior to the reporting of STRs;
• Conditions, timing, and methods for filing internal potentially suspicious transactions;
• Content requirements and format of internal potentially suspicious transactions;
• Appropriate controls for ensuring confidentiality and the protection of data from unauthorized access (also see Section 7.8, Confidentiality and Prohibition against “Tipping Off”);
• Procedures related to the provision of additional information, follow-up actions pertaining to the transactions, and the handling of Business Relationships after the filing of STRs;
• Policies and procedures for the analysis and decision-making of suspicious transactions by the compliance officer in regard to reporting to the FIU;
• Other conditions deemed appropriate by the AML/CFT compliance officer.
Such policies, procedures and controls should be documented, approved by senior management, and communicated to the appropriate levels of the organisation, in keeping with the nature and size of the FI’s business.
7.7 Timing of Suspicious Transaction Reports (STRs)
(AML-CFT Law 9; AML-CFT Decision 17.1(a), 21.2)
FIs are obliged to report STRs to the FIU without delay. Since it is the responsibility of the designated AML/CFT compliance officer to “review, scrutinise and study records, receive data concerning suspicious transactions, and take decisions to either notify the FIU or maintain the transaction,” (see Section 8.1, Compliance Officer) it follows that the STRs should be immediately reported once the suspicious nature of the transaction becomes clear. This means that the internal reporting of suspicious transactions to the compliance officer should be done directly once the suspicion or reasonable grounds for suspicion are established, and immediately the designated AML/CFT compliance officer has confirmed that the transaction (whether pending, in progress, or past) is suspicious, it should be reported.
Without prejudice to the above, FIs should note that, with the exception of any obligatory indicators for which immediate reporting to the FIU is required by the relevant Competent Authorities, some potentially suspicious transactions or indicators of suspicion may require a degree of internal investigation before a suspicion or reasonable grounds for suspicion are established and an internal STR is reported to the designated AML/CFT compliance officer. The FI should however be able to demonstrate that this investigation is started immediately and has been ongoing continuously until the transaction is reported to the FIU. In this regard, and commensurate with the nature and size of their businesses, FIs should establish clear policies, procedures and staff training programmes pertaining to the identification, investigation and internal reporting of suspicious transactions (including attempted transactions), and the degree and extent of investigations that are appropriate prior to the internal reporting of a suspicious transaction (also see Section 7.2, Identification of Suspicious Transactions). These policies and procedures should be documented, approved by senior management, and communicated to the appropriate levels of the organisation.
7.8 Confidentiality and Prohibition against “Tipping Off”
(AML-CFT Law Article 25; AML-CFT Decision Articles 17.2, 21.2, 31.3, 39)
When reporting suspicious transactions to the FIU, FIs are obliged to maintain confidentiality with regard to both the information being reported and to the act of reporting itself, and to make reasonable efforts to ensure the information and data reported are protected from access by any unauthorized person.
As part of their risk-based AML/CFT framework, and in keeping with the nature and size of their businesses, FIs, and their foreign branches or group affiliates where applicable, should establish adequate policies, procedures and controls to ensure the confidentiality and protection of information and data related to STRs. These policies, procedures and controls should be documented, approved by senior management, and communicated to the appropriate levels of the organisation.
FIs must ensure that all relevant information relating to STRs is kept confidential, with due regard to the conditions and exceptions provided for in the law, and the guiding principles for this must be established in policies and procedures. FIs need to ensure that policy and procedures are reflected in for example, appropriate access rights with regard to core systems used for case management and notifications, secure information flows and guidance/training to all staff members involved. This guidance and training is primarily important for the first-line staff who have contact with customers. It is essential that these staff know when there may be cases of suspicious transactions, what questions they have to ask the customer and which information they must not under any circumstances disclose to the customer.
It should be noted that the confidentiality requirement does not pertain to communication within the FI or its affiliated group members (foreign branches, subsidiaries, or parent company) for the purpose of sharing information relevant to the identification, prevention or reporting of suspicious transactions and/or crimes related to ML/FT.
It is a federal crime for FIs or their managers, employees or representatives, to inform a customer or any other person, whether directly or indirectly, that a report has been made or will be made, or of the information or data contained in the report, or that an investigation is under way concerning the transaction. Any person violating this prohibition is liable to a penalty of no less than AED100,000 and no more than AED500,000 and imprisonment for a term of not less than six months.
7.9 Protection against Liability for Reporting Persons
(AML-CFT Law Article 27; AML-CFT Decision Article 17.3)
FIs, as well as their board members, employees and authorised representatives, are protected by the relevant articles of the AML-CFT Law and AML-CFT Decision from any administrative, civil or criminal liability resulting from their good-faith performance of their statutory obligation to report suspicious activity to the FIU. This is also the case even if they did not know precisely what the underlying criminal activity was, and regardless of whether illegal activity actually occurred. However, it should be noted that such protections do not extend to the unlawful disclosure to the customer or any other person, whether directly or indirectly, that they have reported or intend to report a suspicious transaction, or of the information or data the report contains, or that an investigation is being conducted in relation to the transaction.
7.10 Handling of Transactions and Business Relationships after Filing of STRs
Once a Suspicious Transaction or other suspicious information related to a Customer or Business Relationship has been reported to the FIU, there are two immediate consequences:
• FIs are obliged to follow the instructions, if any, of the FIU in relation to both the specific transaction and to the business relationship in general.
• The Customer or Business Relationship should immediately be classified as a High Risk Customer and appropriate risk-based enhanced due diligence and ongoing monitoring procedures should be implemented in order to mitigate the associated ML/FT risks (see Sections 6.4, Enhanced Due Diligence (EDD) Measures, especially 6.4.2, EDD Measures for High-Risk Customers or Transactions, and 6.3.5 Ongoing Monitoring of the Business Relationship). It is however not required to terminated the relationship.
Further guidance on both of these topics is provided below.
FIU Instructions
After receiving an STR from an FI, the FIU may or may not revert to the reporting institution with specific instructions, requests for additional information, feedback or further guidance related to the STR or to the business relationship in general. In such cases, these communications will generally be directed to the designated AML/CFT compliance officer of the FI.
Confidentiality of FIU’s Instructions
The responsibility for coordinating the FI’s prompt compliance with the FIU’s instructions or requests lies with the designated AML/CFT compliance officer. It should be noted that, depending on the nature of the case, the FIU may require the compliance officer to maintain certain information related to its instructions or requests privileged and/or confidential within the FI’s organisation. In other words, in some cases, the compliance officer could be restricted from divulging information about a transaction or business relationship to anyone other than certain members of senior management or the board of directors of the FI. Regardless of the circumstances surrounding the FIU’s instructions or requests, including whether or not the compliance officer is permitted to provide explanations to the staff of the FI, the FI is obliged at all times to follow the compliance officer’s instructions in regard to any follow-up actions required in relation to an STR.
Timing of FIU’s Instructions
Whether or not the FIU issues instructions or requests for additional information to a reporting institution, or how quickly this may occur after the STR is initially reported, both depend on numerous factors. These may include the prioritisation of the incoming STR among all of the STRs received by the FIU, the results of the ensuing analysis, or the possible need for information to be exchanged with other Competent Authorities or international FIUs, as well as the timing and the results of such exchanges.
When an STR involves an anticipated, pending, or already in-progress transaction, FIs should use their best efforts to delay the execution or completion of the transaction, in order to allow for a reasonable amount of time in which to receive feedback, instructions, or additional information requests from the FIU. In taking such measures, FIs should take the necessary steps to avoid “tipping off” or arousing the customer’s suspicion that the transaction is being investigated or reported. Examples of some of the measures FIs may consider taking, either singly or in combination, in order to delay the execution or completion of transactions include but are not limited to:
• Delaying processing of the transaction without explanation for as long as possible;
• Advising the customer that the transaction has been delayed due to an unspecified operational, technical or other problem, and that efforts are underway to resolve it;
• Requesting additional information and/or supporting documentation (for example, evidence of relevant licences or authorisations, shipping or customs documents, additional identification documents, bank or other references) relating to the transaction, the customer, or the counterparty;
• Advising the customer that paperwork related to the transaction has been lost and requesting that it be resubmitted;
• Advising the customer that the transaction is pending an internal approval process;
• Any other reasonable delaying tactics, bearing in mind the obligation to avoid “tipping off” the customer.
During the time interval during which an anticipated, pending, or in-progress STR that has already been reported to the FIU is being delayed by the FI, any additional suspicions that may arise should also be immediately reported to the FIU as a follow-up to the original STR. Examples of such additional suspicions may include, but are not limited to:
• New adverse information obtained in relation to the transaction, the business relationship, or the counterparty to the transaction;
• Unusual behaviour of the customer as a result of the transaction being delayed, such as but not limited to:
- Sudden material amendments or changes to the circumstances or details of the transaction; - Excessive pressure, intimidation, displays of anger (beyond what would normally be expected) or threats of any kind, aimed at forcing the FI or its employees to complete the transaction; - Abrupt cancellation of the transaction, termination of the business relationship, or sudden attempts to close out the customer’s account and/or withdraw the balance of funds or other assets held by the FI; - Any other indication or reasonable grounds to suspect that the customer has become aware that the transaction is being investigated or reported as suspicious.
If a reasonable amount of time has not yet elapsed before the receipt of feedback, instructions, or requests for additional information from the FIU in regard to an STR, and it becomes impossible for the FI to delay the execution or completion of the reported transaction any longer without arousing the customer’s suspicion that the transaction is being investigated or reported, then the FI should request specific instructions or permission from the FIU in regard to executing or rejecting the transaction.
No Instructions, Feedback or Additional Information Requests from the FIU
Due to the factors previously mentioned, FIs may not receive instructions, additional information requests, or other feedback from the FIU in regard to STRs that have been filed; or the receipt of such communications may be delayed beyond what they consider to be a reasonable time period. In such instances, FIs should determine the appropriate handling of the STR and of the business relationship in general, taking into consideration all of the risk factors involved.
In particular, FIs are reminded that, unless they are specifically instructed by the FIU to do so, they are under no obligation to carry out transactions they suspect, or have reasonable grounds to suspect, of being related to a Crime. Furthermore, unless they are specifically instructed by the FIU to maintain the business relationship (for example, so that the Competent Authorities may monitor the customer’s activity), FIs should take appropriate steps in order to decide whether or not to maintain the business relationship. These steps may include, but are not limited to:
• Reassessing the business relationship risk and re-evaluate the customer’s risk profile, where necessary;
• Initiating an enhanced customer due diligence review;
• Considering the performance of an enhanced background investigation (including, if appropriate, the use of a third-party investigation service);
• Any other reasonable steps, commensurate with the nature and size of their businesses, and bearing in mind the obligation to avoid “tipping off” the customer.
FIs should be aware that filing an STR does not automatically mean that the relationship with the customer needs to be terminated. However, when deciding to terminate a business relationship for which an STR has been filed and no feedback has been received from the FIU after a reasonable time period, FIs should formally advise the FIU of their intention to do so unless there is an official objection.
Reasonable Time Period for Receiving Feedback from the FIU
FIs should note that there are no pre-established processing times, and no statute of limitations, in regard to the time interval during which the FIU may provide feedback, including instructions or requests for additional information in response to an STR. Furthermore, the time period that may be considered reasonable in relation to such feedback depends on numerous factors, including but not limited to the:
• Type, size and circumstances of the transaction;
• Normal average processing times for the specific transaction type;
• Type of customer or business relationship;
• Nature and size of the FI’s business;
• Precise nature of the suspicion.
The time period considered to be reasonable could thus vary widely from one case to another.
As a general guideline, the reasonable time periods for feedback from the FIU concerning transaction types that are less complex, more routine, and have faster average processing times (such as account-to-account or wire transfers, the exchange of currencies, or over-the-counter purchases of precious metals or stones, for example) would normally be expected to be shorter than those for more complex, less routine transaction types (such as, for example, purchases of real estate or other complex assets, trade finance transactions, or various forms of loan or credit agreements). FIs that require further assistance in determining reasonable time periods should consult with the FIU or the relevant Supervisory Authorities.
High-Risk Classification of Reported Business Relationships
When a transaction or other information about a business relationship is reported to the FIU as suspicious, it means that, by definition, the customer or business relationship to which it pertains should be classified as high risk (in case the business relationship has not yet been classified as such). In situations in which no feedback or instructions have been received from the FIU, FIs that determine to maintain the business relationship should, commensurate with the nature and size of their businesses:
• Document the process by which the decision was made to maintain the business relationship, along with the rationale for, and any conditions related to, the decision;
• Implement adequate EDD measures to manage and mitigate the ML/FT risks associated with the business relationship.
In such cases, beyond the EDD measures described in previous sections (see Sections 6.4, Enhanced Due Diligence (EDD) Measures and 6.3.5, Ongoing Monitoring of the Business Relationship), FIs should also implement additional control measures such as, but not limited to:
• Requiring additional data, information or documents from the customer in order to carry out transactions (for example, evidence of relevant licenses or authorisations, customs documents, additional identification documents, bank or other references);
• Restricting the customer’s use of certain products or services;
• Placing restrictions and/or additional approval requirements on the processing of the customer’s transactions (for example, transaction size and/or volume limits, or limits to the number of transactions of certain types that can be executed during a given time period).
FIs should also document the specific EDD, ongoing monitoring, and additional control measures to be taken. In this regard, FIs should obtain senior management approval for the plan, including its specific conditions, duration and any requirements for its removal, as well as the roles and responsibilities for its implementation, monitoring and reporting, commensurate with the nature and degree of the ML/FT risks associated with the business relationship.
8. Governance
(AML-CFT Law Article 16.1(d); AML-CFT Decision Articles 4.2(a), 20, 21, 44.4)
In order for the AML/CFT framework of any organisation to be effective, it must be based on the foundation of a sound governance structure, and held together by a strong compliance culture.
The governance structure should take the following into consideration:
• Establish clear accountability lines and responsibilities to ensure that there is appropriate and effective oversight of staff who engage in activities which may pose a greater AML/CFT risk. • Have the mechanism to inform the board of directors (or a committee of the board) and senior management of compliance initiatives, compliance deficiencies, STRs filed and corrective actions taken; • Develop and maintain a system of reporting that provides accurate and timely information on the status of the AML/CFT program, including statistics on key elements of the program, such as the number of transactions monitored, alerts generated, cases created and STRs filed; • Develop and implement quality assurance testing programs to assess the effectiveness of the AML/CFT program’s implementation and execution of its requirements.
FIs should also make sure to have management structures which are accountable for clear ML/FT risk management and mitigation measures, as well as appropriate independent control functions. Implicit in both the AML-CFT Law and the AML-CFT Decision are the elements of both, concerning which additional guidance is provided in the sections below.
8.1 Compliance Officer
8.1.1 Appointment and Approval
FIs are obliged to appoint a compliance officer (CO) with the appropriate competencies and experience to perform the statutory duties and responsibilities associated with this role. The AML-CFT Decision stipulates that the CO performs these duties “under his or her own responsibility”, referring to the independent nature of the function and from which it should be understood that the position should be at a management level.
FIs must take all appropriate steps to identify and to prevent or manage confilicts of interests between:
• The FI, its’ personnel including its CO, or any other representatives, including any person who is directly or indirectly associated with the organization and who has control to make decisions, and the FI’s customer. • The CO and senior management of the organization including the Board of Directors. The CO must be independent and must hold a position of sufficient seniority within the organization, to ensure informed decisions are made without undue pressure to challenge decisions that are considered ill-suited, to protect the organization from possible ML/TF abuse. The MLRO’s independence of judgement is required to be free from conflicts of interest, whether it is pecuniary or otherwise.
The AML-CFT Decision further provides that the appointment of a person to the position of CO requires the prior consent of the relevant Supervisory Authority. Some FIs might also have appointed a Money Laundering Reporting Officer (MLRO).
In determining the competencies, level of experience, and organizational reporting structures that are appropriate for their COs, FIs should take several factors into consideration, including but not limited to:
• The results of the NRA and any topical risk assessment
• The nature, size, complexity, and risk profile of their industries and businesses, as well as those associated with the products and services they offer and the markets and customer segments they serve;
• The organisation’s governance framework and management structure, with particular consideration given to the independent nature of compliance as a control function;
• The specific duties and responsibilities of the CO’s role (described below).
Where appropriate, FIs may also consider engaging in dialogue with Supervisory Authorities, professional associations in their sectors, and industry peers, in relation to the competencies, experience, and governance structures that make for an effective compliance officer and an effective AML/CFT programme.
8.1.2 Responsibilities
(AML-CFT Decision Article 21.1-5)
The specific tasks of the CO are detailed in the relevant provisions of the AML-CFT Decision. In general, the CO will collaborate with the relevant Supervisory Authority and the FIU to ensure that these can perform their respective duties. The CO’s tasks can be grouped broadly into the following categories:
• ML/FT Reporting. The compliance officer is FI’s officer in charge of reviewing, scrutinizing and reporting STRs. In this capacity, the CO is ultimately responsible for the detection of transactions related to the crimes of money laundering and the financing of terrorism and of illegal organisations, for reporting suspicions to the FIU, and for cooperating with the Competent Authorities in relation to the performance of their duties in regard to AML/CFT.
• AML/CFT Programme Management. The CO should ensure the quality, strength and effectiveness of the FI’s AML/CFT programme. As such, the CO should be a stakeholder with respect to the FI’s ML/FT business risk assessment, and the overarching AML/CFT risk mitigation framework, including its AML/CFT policies, controls and CDD measures. The CO is in charge of informing and reporting to senior management on the level of compliance and report on that to the relevant Supervisory Authority.
• AML/CFT Training and Development. The CO is responsible for helping to establish and maintain a strong and effective AML/CFT compliance culture within the FI. This duty includes working with senior management and other internal and external stakeholders to ensure that the FI’s staff are well-qualified, well-trained, well-equipped, and well-aware of their responsibility to combat the threat posed by ML/FT.
8.2 Staff Screening and Training
(AML-CFT Decision Articles 20.4-5, 21.4)
In order for their ML/FT risk assessment and AML/CFT mitigation measures to be effective, FIs should ensure that their employees have a clear understanding of the ML/FT risks that the FI is exposed to and can exercise sound judgment, both when adhering to the FI’s AML/CFT risk mitigation measures and when identifying suspicious transactions. Furthermore, due to the ever-evolving nature of ML/FT risks, FIs should ensure that their employees are kept up to date on an ongoing basis in relation to emerging ML/FT typologies and new internal and external risks. . Depending on the nature, size and level of complexity of an FI, an FI should also screen staff to ensure high standards when hiring employees.
Thus, to ensure a high level of competence and AML/CFT programme effectiveness, FIs should formulate and implement appropriate policies, procedures and controls with regard to staff screening and training. An effective training program should not only explain the relevant AML/CFT laws and regulations, but also cover the institutions’ policies and procedures used to mitigate ML/FT risks, scope of target employees such as but not limited:
• Customer-facing staff. • AML/CFT compliance staff. • Senior management and board of directors
These measures should be applied across organisations and financial groups, including their foreign branches and majority-owned subsidiaries. Examples of some of the factors that should be considered when determining appropriate staff screening and training measures include, but are not limited to:
• The results of the NRA and any topical risk assessment
• The nature, size, complexity, and risk profile of FIs’ sectors and businesses, as well as those associated with the products and services they offer and the markets and customer segments they serve;
• Effective screening and selection methods in relation the AML/CFT cultural compatibility of their employment candidates;
• Assessment of staff AML/CFT competency in relation to training and development needs;
• The type, frequency, structure, content, and delivery channels of AML/CFT training programmes and development opportunities;
• The effective identification, deployment and management of both internal and external training resources;
• Appropriate methods and tools for assessing the effectiveness of staff hiring, training, and development programmes, including screening procedures to ensure high standards when hiring employees.
8.3 Group Oversight
(AML-CFT Decision Articles 20, 31, 32)
When an FI is part of a group, the FI is obliged to implement appropriate group-wide AML/CFT programmes, and to apply them in relation to all branches and majority-owned subsidiaries of the financial group. The specific requirements that must be met by FIs with respect to their foreign branches and majority-owned subsidiaries are set out in the relevant provisions of the AML-CFT Decision, and reflect those to which FIs are subject within the State.
In meeting these obligations with regard to their branches and majority-owned subsidiaries in foreign countries, FIs, and in particular FIs that are members of financial groups, should ensure that the measures they apply are consistent with the requirements of the AML-CFT Law and AML-CFT Decision. In this regard, FIs should establish appropriate policies and procedures for the exchange and sharing of data and information, including those required for the purposes of CDD and ML/FT risk management, between the foreign branches and subsidiaries and the head office, for the purpose of combating the crimes of money laundering and the financing of terrorism and of illegal organisations, and for reporting suspicious transactions.
In situations where these measures are not possible due to legislative or regulatory restrictions in the foreign countries in which their branches and majority-owned subsidiaries operate, FIs (including those which are members of Financial Groups) should implement the necessary additional measures, commensurate with the nature and size of their businesses, that will enable them to manage and mitigate appropriately the ML/FT risks that relate to their foreign operations. Examples of some of the measures that should be considered include but are not limited to:
• Assessing the effectiveness of foreign branches and majority-owned subsidiaries’ AML/CFT measures, including evaluating such factors as the comprehensiveness and quality of their policies, procedures and controls, and performing gap analyses in relation to the requirements of the AML-CFT Law and AML-CFT Decision;
• Establishing clear policies, procedures and controls in relation to the type and extent of access which managers and employees of foreign branches and majority-owned subsidiaries have to the FIs’ IT and operational systems, including CDD and transaction processing systems;
• Establishing clear policies, procedures and controls in relation to the type and extent of access which customers and Business Relationships of foreign branches and majority-owned subsidiaries have to the FIs’ products, services and transactional processing capabilities;
• Establishing clear policies, procedures and controls in relation to the type of CDD and transaction-related information, data, and analysis FIs accept from their foreign branches and majority-owned subsidiaries in relation to customer or Business Relationship referrals, and the extent of their reliance on such information (see Section 6.6, Reliance on a Third Party);
• Implementing service-level agreements, clearly setting out the roles and responsibilities of the parties and specifying the nature of the CDD and record-keeping requirements to be fulfilled in relation to customer or Business Relationship referrals;
• Establishing protocols for the certification by the foreign branches and subsidiaries of documents and other records pertaining to the CDD measures undertaken in relation to customer or Business Relationship referrals.
In particular, in cases in which the minimum AML/CFT requirements of host countries in which FIs maintain foreign operations are less strict than those of the State, FIs should take the necessary measures to ensure that their foreign branches and/or majority-owned subsidiaries in those countries implement requirements consistent with those of the State, to the extent permitted by the laws and regulations of the host countries. If such host countries do not permit the proper implementation of the AML/CFT requirements consistent with those of the State, FIs should apply appropriate additional measures to manage and mitigate the ML/FT risks (including but not limited to those described above). They should also inform the relevant Supervisory Authorities of the circumstances and comply with any additional supervisory actions, controls, or requirements of the Competent Authorities of the State (up to and including, if requested, terminating their operations in the host countries).
8.4 Independent Audit Function
(AML-CFT Decision Article 20.6)
A robust and independent audit function is a key component to a well-functioning governance structure and an effective AML/CFT framework. FIs are obliged to have in place an independent audit function to test the effectiveness and adequacy of their internal polices, controls and procedures relating to combating the crimes of money laundering and the financing of terrorism and of illegal organisations. In this regard, FIs should ensure that their independent audit function is appropriately staffed and organized, and that it has the requisite competencies and experience to carry out its responsibilities effectively, commensurate with the ML/FT risks to which the FIs are exposed, and with the nature and size of their businesses.
It should be noted that, while most FIs are expected to have the capacity to meet these requirements internally, depending on the nature and size of their businesses, some FIs (particularly smaller ones) may not necessarily have the resources to maintain a fully functioning and effective internal audit unit. In such cases, those FIs should ensure that they take adequate measures to obtain the necessary capabilities from qualified external sources. They should also ensure that they have in place adequate internal capabilities to provide sufficient coordination with and oversight of any external resources they may utilise, and that such external resources are adequately regulated and supervised by relevant Competent Authorities.
FIs should ensure that the periodic inspection and testing of all aspects of their AML/CFT compliance programmes, including ML/FT business risk assessment and AML/CFT mitigation measures, and CDD policies, procedures and controls, is incorporated into their regular audit plans. They should also ensure that all their branches and the subsidiaries in which they hold a majority interest, whether domestic or foreign, are part of an independent audit testing programme that covers the effectiveness and adequacy of their internal AML/CFT polices, controls and procedures.
Some of the factors FIs should consider in determining the appropriate frequency and extent of audit testing of their AML/CFT programmes by their independent audit functions include but are not limited to:
• The results of the NRA and any topical risk assessment;
• The nature, size, complexity, and geographic scope of the FIs’ businesses, and the results of their ML/TF business risk assessments;
• The risk profile associated with the products and services they offer and the markets and customer segments they serve;
• The frequency of supervision and inspection by, and the nature of the feedback (including the imposition of administrative sanctions) they receive from, Supervisory Authorities, relative to enhancing the effectiveness of their AML/CFT measures;
• Internal and external developments in relation to ML/FT risks, as well as developments pertaining to the management and operations of the FIs.
The scope of such audits should include but not be limited to:
• Examine the adequacy of AML/CFT and CDD policies, procedures and processes, and whether they comply with regulatory requirements.
• Assess training adequacy, including its comprehensiveness, accuracy of materials, training schedule, attendance tracking and escalation procedures for lack of attendance.
• Review all the aspects of any AML/CFT compliance function that have been outsourced to third parties, including the qualifications of the personnel, the contract and the performance and reputation of the company.
• Review case management and STR systems, including an evaluation of the research and referral of unusual transactions, and a review of policies, procedures and processes for referring unusual or suspicious activity from all business lines to the personnel responsible for investigating unusual activity
8.5 Responsibilities of Senior Management
(AML-CFT Decision Articles 4.2(a), 4.2(b)(5), 8.1(a), 15.1(b) and 15.2, 17.3, 21.3, 25.1(d))
A cornerstone of any sound governance structure, including those related to AML/CFT compliance, is senior management involvement and accountability. The members of an FI’s senior management (together with the members of the board of directors in those organisations that have one) are ultimately responsible for the quality, strength and effectiveness of the FI’s AML/CFT framework, as well as for the robustness of its compliance culture. In this regard, an FI’s senior management should set the ML/FT risk appetite and a proper “tone at the top,” by demonstrating their commitment to ensuring an effective AML/CFT compliance programme is in place, and by clearly articulating their expectations with regard to the responsibilities and accountability of all staff members in relation to it.
Under the AML/CFT legal and regulatory framework of the UAE, the senior management of all FIs are responsible for performing certain functions related to the assessment, management and mitigation of the ML/FT risks to which their organisations are exposed. These responsibilities can be grouped broadly into categories which include:
• Implementation of governance, control, and operating systems. These include such elements as:
- Appointing a qualified compliance officer in line with the requirements of the relevant Supervisory Authority; - Ensuring a robust and effective independent audit function is in place; - Putting in place and monitoring the implementation of adequate management and information systems, internal controls, and policies, procedures to mitigate risks.
• Approval of internal policies, procedures and controls. These include such elements as the FI’s overall ML/FT risk appetite as well as the framework of AML/CFT policies, procedures and controls related to areas such as:
- Identification, assessment, understanding, management and mitigation of ML/FT risks; - Performance, review and updating of CDD (including EDD and SDD) measures; - Identification and implementation of indictors to identify suspicious transactions; - Record retention and data protection; - Staff screening, training and development.
• Oversight of the AML/CFT compliance programme. This includes such elements as:
- Reviewing and providing comments in relation to the compliance officer’s semi-annual reports to the relevant Supervisory Authority; - Approving the establishment and continuance of High Risk Customer Business Relationships and their associated transactions, including those with PEPs; - Approving the establishment and continuance of Business Relationships involving high-risk countries; - Approving the establishment and continuance of relationships with correspondent institutions; - Ensuring the adequate application of the appropriate components of the AML/CFT compliance programme to all branches and majority-owned subsidiaries, including those operating in foreign jurisdictions.
• Application of the directives of Competent Authorities. This includes such elements as:
- Applying the directives of Competent Authorities for implementing UN Security Council decisions under Chapter VII of the Charter of the United Nations, and other related directives, including Cabinet Decision (74) of 2020 Regarding Terrorism Lists Regulation and Implementation of UN Security Council Resolutions On the Suppression and Combating of Terrorism, Terrorists Financing & Proliferation of Weapons of Mass Destruction, and Related Resolutions; - Implementing CDD measures defined by the National Committee for Combating Money Laundering and the Financing of Terrorism and Illegal Organisations, regarding High Risk Countries.
8.6 Governance Issues of Small Organisations
Some FIs may operate as small or mid-sized businesses, without large staff organisations or sophisticated IT infrastructures. In such cases, individual managers and employees may often be called upon to undertake multiple roles and responsibilities in the course of day-today business activities, and it may be difficult at times to maintain a clear separation of duties or functions. While an FI’s small size does not in any way exempt it from fulfilling its obligations under the AML-CFT Law and AML-CFT Decision, and without prejudice to guidance provided in the previous sections, the following additional considerations are of particular importance to small and mid-sized FIs.
• In situations in which the responsibilities of the AML/CFT compliance officer are delegated to a manager or staff member who also has other responsibilities, FIs should undertake their best efforts to ensure that the designated AML/CFT compliance officer does not have day-to-day responsibility for sales and/or customer business relationship management.
• When an adequate separation of responsibilities is not possible due to the small size of an FI’s organisation, FIs should take the necessary steps to ensure that operational and AML/CFT policies and procedures (particularly those pertaining to CDD, the identification and reporting of Suspicious Transactions, and the monitoring and updating of required High Risk Country CDD measures, and Local and Sanctions Lists—see Sections 6, Customer Due Diligence (CDD), 6.4.3 Requirements for High-Risk Countries, and 10, International Financial Sanctions) are clearly formulated, documented, and adhered to during the establishment and ongoing monitoring of business relationships and the carrying out of transactions.
• In such cases, FIs should ensure that they clearly document the rationale for any policy and/or procedural exceptions they make, along with any additional AML/CFT risk mitigation measures they implement, and that these records are properly retained in accordance with the statutory record-keeping requirements (see Section 9, Record Keeping). FIs should also consider referring to any significant policy or procedural exceptions, along with their rationale, associated additional AML/CFT risk mitigation measures, and senior management comments, in the AML/CFT compliance officer’s required semi-annual reports to the relevant Supervisory Authorities.
• FIs that are unable to ensure a clear and effective separation of AML/CFT responsibilities from those related to the day-to-day management of their businesses, including but not limited to sales and customer business relationship management functions, due to the small size of their organisation should also consider taking additional measures to enhance the application of their independent audit controls (see Section 8.4, Independent Audit Function). Examples of such measures include but are not limited to:
- Incorporating the audit of policies, procedures (particularly those pertaining to CDD, the identification of Suspicious Transactions, and the monitoring and updating of required High Risk Country CDD measures, and Local and Sanctions Lists), and records related to exceptions made to them, as part of their audit plans and/or their service-level agreements with their external providers of independent audit services; - Increasing the frequency of independent audits and random audit inspections; - Applying stricter criteria with regard to the review of past transactions, such as increasing the number of transactions reviewed for a given time period, reducing size threshold limits for transactions to be reviewed, or taking other reasonable measures in this regard.
9. Record Keeping
9.1 Obligations and Timeframe for the Retention and Availability of Records
(AML-CFT Law Articles 16.1(a),(f); AML-CFT Decision Articles 7.2, 24, 36, 37.3)
FIs are obliged to maintain detailed records, documents, data and statistics for all transactions, all records obtained through CDD measures, account files and business correspondence, and results of any analysis undertaken, as well as a variety of record types and documents associated with their ML/FT risk assessment and mitigation measures, as specified in the relevant provisions of the AML-CFT Decision (see Section 9.2, Required Record Types). FIs are required to maintain the records in an organized fashion so as to permit data analysis and the tracking of financial transactions, and to make the records available to the Competent Authorities immediately upon request. They should be sufficient to permit reconstruction of individual transactions so as to provide, if necessary, evidence for prosecution of criminal activity. All CDD information and transaction records should be available swiftly to Competent Authorities upon appropriate authority.
The statutory retention period for all records is at least five (5) years, depending on the circumstances, from the date of the most recent of any of the following events:
• Termination of the Business Relationship or the closing of a customer’s account with the FI;
• Completion of an occasional transaction (in respect of a customer with whom no Business Relationship is established);
• Completion of an inspection of the records by the Supervisory Authorities;
• The issue date of a final judgment by the competent judicial authorities;
• Liquidation, dissolution, or other form of termination of a legal person or arrangement.
Without prejudice to the above, FIs should note that it is the prerogative of the Competent Authorities to require the retention of the records of any FI, whether data, statistics, or records pertaining to a specific customer or transaction or to general categories of customers or transactions which they deemed to be of interest, for a longer period of time at their own discretion.
In order to fulfil their record-keeping obligations, and commensurate with the nature and size of their businesses, FIs should determine the appropriate policies, procedures and controls related to the adequate retention, organisation, and maintenance of records. The policies, procedures and controls should be documented, approved by senior management, and communicated to appropriate levels of the organisation. Examples of the factors which FIs should give consideration to when formulating the relevant policies, procedures and controls, include but are not limited to:
• Organisational roles and responsibilities in regard to the ML/TF business risk assessment, implementation, review and updating of AML/CFT policies, procedures and controls related to record-keeping and data protection, including appropriate business contingency and escalation procedures;
• Organisational roles and responsibilities in relation to record-keeping (including logging, cataloguing and organisation, archiving, handling and transferring of records and documents, as well as of the destruction of expired records) of CDD information and transactions;
• Physical and cyber security, and the protection of active and archived data and records from unauthorised access;
• Appropriate audit and quality assurance testing policies.
9.2 Required Record Types
(AML-CFT Law Articles 16.1(a),(b),(f); AML-CFT Decision Articles 7.2, 24)
The AML-CFT Law and AML-CFT Decision oblige FIs to retain several types of records, which can be classified broadly into the following categories:
• Transaction Records. This category relates to operational and statistical records, documents and information concerning all transactions executed or processed by the FI, whether domestic or international in nature.
• CDD Records. This category relates to records, documents, and information about customers, their due diligence, and the investigation and analysis of their activities, and can be further divided into sub-categories such as records pertaining to:
- Customer Information, including account files and business correspondence, and results of any analysis undertaken - Company Information - Reliance on Third Parties to Undertake CDD - Ongoing Monitoring of Business Relationships - Suspicious Transaction Reports (STRs)
Additional guidance related to these record types is provided in the following sub-sections.
9.2.1 Transactions
(AML-CFT Law Articles 16.1(f); AML-CFT Decision Articles 24.1-3, 28.1-2, 29.4)
FIs are obliged to retain the operational and statistical records, documents and information concerning all transactions executed or processed by the FI, whether domestic or international in nature, and irrespective of the type of customer and whether or not a Business Relationship is maintained, for a minimum period of five (5) years. Some examples of the type of records, documents and information which must be retained include but are not limited to:
• Customer credit or debit advices, and transaction orders or applications (including those for cash deposits or withdrawals, currency exchange transactions);
• Credit-related documentation, including loan or guarantee applications, agreements, amendments and supporting documents, disbursement or repayment records, collateral pledges, letter of credit documentation, promissory notes;
• Deal tickets, trade blotters and ledgers, settlement and dividend payment records related to foreign exchange, securities dealing or investing transactions;
• Escrow or fiduciary account transaction records;
• Insurance policy premiums, pay-outs, and related transaction records and documents;
• Money transfer records, including book transfers orders, and domestic and cross-border wire transfer orders, and their related originator and beneficiary records;
• Statistics and analytical data related to customers’ financial transactions, including their monetary values, volumes, currencies, interest rates, and other information.
In addition to the above, FIs should compile notes on any particularly large or unusual transactions, and keep these notes as part of their records. In particular, FIs licensed by the Central Bank must examine the background and purpose of all complex, unusual large transactions and all unusual patterns of transactions, which have no apparent economic or lawful purpose, and document their findings in writing. This includes transactions that are not considered necessary to be reported as suspicious. These findings must be maintained for inspection by the Central Bank for a period of at least five years.
9.2.2 Customer Information
(AML-CFT Law Articles 16.1(b); AML-CFT Decision Articles 24.2-4, 27.7, 28.1-2, 29.4, 37.1-3)
FIs are required to retain all customer records and documents obtained through the performance of CDD measures in relation to Business Relationships, including customers, Beneficial Owners, beneficiaries, or other controlling persons. Examples of such records include but are not limited to:
• Customer account information and files;
• Customer correspondence (including email and fax correspondence), call reports or meeting minutes (including where applicable recordings, transcripts or logs of telephone or videophone calls);
• Copies of personal identification documents, CDD (including EDD and SDD) forms, profiles and supporting documentation, and results of due diligence background searches, queries and investigations;
• Customer risk assessment and classification records.
9.2.3 Company Information
(AML-CFT Law Articles 16.1(b); AML-CFT Decision Articles 8.1(b), 9.1, 34-36)
The AML-CFT Decision provides that the administrators, liquidators, or any other stakeholders involved in the dissolution of a company are obliged to retain the records, documents and information specified in the relevant articles for a minimum period of five (5) years from the date of its dissolution, liquidation or termination. These records pertain to corporate documents as well as to information on Beneficial Owners, legal shareholders, and senior managers. Such records include but are not limited to documents and information concerning:
• Company formation, registration, deregistration, liquidation, dissolution or expiry, including documents such as share registers, memoranda and articles of association, deeds of settlement and foundation charters, or similar documents, along with any amendments to them (whether the organisation is for-profit or not-for-profit);
• Changes to company information, such as name, registered address, legal representatives and corporate officers (directors, company secretary), or legal form;
• Identification and identity verification documents related to Beneficial Owners, shareholders, nominee shareholders, directors and senior management officers and, in the case of Legal Arrangements, settlors or founders, protectors, beneficiaries, trustees or executors, governing council or committee members, or similar controlling persons.
In order to fulfil their statutory record-keeping obligations in this regard, FIs should determine the appropriate policies, procedures and controls related to the adequate retention, organisation, and maintenance of records when they dissolve or liquidate companies in which they hold a controlling interest. The policies, procedures and controls should be documented, approved by senior management, and communicated to appropriate levels of the organisation (see Section 9.1, Obligations and Timeframe for the Retention and Availability of Records for additional guidance concerning policies, procedures, controls and statutory retention periods related to record-keeping and data protection).
9.2.4 Reliance on Third Parties to Undertake CDD
(AML-CFT Law Article 16.1(b); AML-CFT Decision Articles 24.2-4, 19.1(b)-2(a))
FIs that rely on third parties, whether unaffiliated or members of their own financial groups, are obliged to ensure that copies of all the necessary documents collected through the performance of CDD measures can be obtained upon request and without delay, and that the third parties adhere to the record-keeping provisions of the AML-CFT Decision. See Section 9.2.2, Customer Information above for examples of such records.
In order to fulfil their statutory obligations, and commensurate with the nature and size of their businesses, FIs should determine the appropriate policies, procedures and controls related to the assessment, monitoring, and testing of third parties’ record-retention frameworks. The policies, procedures and controls should be documented, approved by senior management, and communicated to appropriate levels of the organisation. Some of the factors to which FIs should give consideration when formulating relevant policies, procedures and controls include but are not limited to:
• Organisational roles and responsibilities in regard to the assessment, monitoring and testing of the third party’s policies, procedures and controls related to record-keeping and data protection, including appropriate business contingency and escalation procedures;
• Organisational roles and responsibilities for the implementation of service-level agreements with third parties governing the provision of record-keeping services;
• Operational procedures related to request and transfer of records and documents, as well as their physical and cyber security, and the protection of active and archived data and records from unauthorised access;
• Appropriate audit and quality assurance testing policies related to the monitoring and testing of the third-party’s record-retention framework.
9.2.5 Ongoing Monitoring of Business Relationships
(AML-CFT Law Article 16.1(b),(f); AML-CFT Decision Article 24.2-4)
FIs are required to retain all customer records and documents obtained through the ongoing monitoring of Business Relationships. Examples of such records include but are not limited to:
• Transaction review, analysis, and investigation files, with their related correspondence;
• Customer correspondence (including email and fax correspondence), call reports or meeting minutes (including where applicable recordings, transcripts or logs of telephone or videophone calls) related to those transactions or their analysis and investigation;
• CDD records, documents, profiles or information gathered in the course of reviewing, analysing or investigating transactions, as well as transaction-related supporting documentation, including the results of background searches on customers, Beneficial Owners, beneficiaries, controlling persons, or counterparties to transactions;
• Transaction handling decisions, including approval or rejection records, together with related analysis and correspondence.
9.2.6 Suspicious Transaction Reports (STRs)
(AML-CFT Law Article 16.1(f); AML-CFT Decision Articles 24.2-4)
FIs are required to retain all records and documents pertaining to STRs and the results of all analysis or investigations performed. Such records relate to both internal STRs and those filed with the FIU, and include but are not limited to:
• Suspicious transaction indicator alert records, logs, investigations, recommendations and decision records, and all related correspondence;
• Competent authority request for information, correspondent bank requests for assistance, and their related investigation files and correspondence;
• CDD and Business Relationship monitoring records, documents and information obtained in the course of analysing or investigating potentially suspicious transactions, and all internal or external correspondence or communication records associated with them;
• STRs (internal and external), logs, and statistics, together with their related analysis, recommendations and decision records, and all related correspondence;
• Notes concerning feedback provided by the FIU with respect to reported STRs, as well as notes or records pertaining to any other actions taken by, or required by, the FIU.
10. International Financial Sanctions
The UAE is a member of several multinational and international organisations and governing bodies, including the United Nations. As such, the UAE is a party to many international agreements and conventions pertaining to the combating of money laundering and the financing of terrorism, as well as to the prevention and suppression of the proliferation of weapons of mass destruction. These conventions include, among others, the International Convention for the Suppression of the Financing of Terrorism and the Treaty on the Non-Proliferation of Nuclear Weapons.
FIs are obliged to comply with the directives of the Competent Authorities of the State in relation to the agreements and conventions referred to above, including but not limited to Cabinet Decision No. (74) of 2020 Regarding Terrorism Lists Regulation and Implementation of UN Security Council Resolutions On the Suppression and Combating of Terrorism, Terrorists Financing & Proliferation of Weapons of Mass Destruction, and Related Resolutions.
Because it is outside of the scope of these Guidelines to provide detailed guidance on this, reference is made to the guidance on TFS issued by the Executive Office for the Import and Export of Goods. Due to the significance, complexity and extent of the subject matter of international financial sanctions, it is deemed appropriate that this material be covered in depth in separate guidance materials.
Part V—Appendices
11 Appendices
11.1 Glossary of Terms
Term Definition Beneficial Owner: Natural person who owns or exercises effective ultimate control, directly or indirectly, over a customer or the natural person on whose behalf a transaction is being conducted or, the natural person who exercises effective ultimate control over a legal person or Legal Arrangement. Beneficiary Financial Institution The Financial Institution that receives a wire transfer from an Ordering Financial Institution directly or indirectly via an Intermediary Financial Institution and makes funds available to the beneficiary. Business Relationship Any ongoing commercial or financial relationship established between Financial Institutions, Designated Non-Financial Businesses and Professions, and their customers in relation to activities or services provided by them. Committee: National Committee for Combating Money Laundering and the Financing of Terrorism and Illegal Organisations. Competent Authorities: The competent government authorities in the State entrusted with the implementation of any provision of the Decree-Law and the present Decision. Correspondent Relationship: Relationship between a correspondent financial institution and a respondent one through a current account or any other type of account or through a service related to such an account and includes a corresponding relationship established for the purpose of securities transactions or transfer of funds. Crime: Money laundering crime and related Predicate Offences, or Financing of Terrorism or Illegal Organisations. Customer Due Diligence (CDD): Process of identifying or verifying the information of a Customer or Beneficial owner, whether a natural or legal person or a Legal Arrangement, and the nature of its activity and the purpose of the Business Relationship and the ownership structure and control over it for the purposes of the Decree-Law and this Decision. Customer: Any person involved in or attempts to carry out any of the activities specified in the Implementing Regulations of this Decree Law (Articles 2 and 3 the Cabinet Resolution) with one of the Financial Institutions or Designated Non-Financial Businesses and Professions. Decree-Law (or “AML-CFT Law”): Federal Decree-Law No. (20) of 2018 On Anti-Money Laundering and Combating the Financing of Terrorism and Financing of Illegal Organisations. Decision (or “AML-CFT Decision” or “Cabinet Decision”): Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 On Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations. Designated Nonfinancial Businesses and Professions (DNFBPs): Anyone who conducts one or several of the commercial or professional activities defined in Article 3 of the Cabinet Decision, being anyone who is engaged in the following trade or business activities:
1. Brokers and real estate agents when they conclude operations for the benefit of their Customers with respect to the purchase and sale of real estate
2. Dealers in precious metals and precious stones in carrying out any single cash transaction or several transactions that appear to be interrelated or equal to more than AED 55,000.
3. Lawyers, notaries, and other independent legal professionals and independent accountants, when preparing, conducting or executing financial transactions for their Customers in respect of the following activities:
(a) Purchase and sale of real estate.
(b) Management of funds owned by the Customer.
(c) Management of bank accounts, saving accounts or securities accounts.
(d) Organising contributions for the establishment, operation or management of companies.
(e) Creating, operating or managing legal persons or Legal Arrangements.
(f) Selling and buying commercial entities.
4. Providers of corporate services and trusts upon performing or executing a transaction on the behalf of their Customers in respect of the following activities:
(a) Acting as an agent in the creation or establishment of legal persons.
(b) Working as or equipping another person to serve as director or secretary of a company, as a partner or in a similar position in a legal person.
(c) Providing a registered office, work address, residence, correspondence address or administrative address of a legal person or Legal Arrangement.
(d) Performing work or equipping another person to act as a trustee for a direct Trust or to perform a similar function in favour of another form of Legal Arrangement.
(e) Working or equipping another person to act as a nominal shareholder in favour of another person.
5. Other professions and activities which shall be determined by a decision of the MinisterEgmont Group: The Egmont Group is an intergovernmental body of 159 Financial Intelligence Units (FIUs), which provides a platform for the secure exchange of expertise and financial intelligence to combat money laundering and the financing of terrorism (ML/FT). FATF: The Financial Action Task Force is an intergovernmental body that sets international standards and promotes effective implementation of legal, regulatory and operational measures for combating money laundering, terrorist financing and other related threats to the integrity of the international financial system. FSRBs: FATF-Style Regional Bodies are regional intergovernmental organisations which promote and assess the implementation of internationally accepted AML/CFT policies and regulations. Financial Group: A group of financial institutions that consists of holding companies or other legal persons exercising the control over the rest of the group and coordinating functions for the application of supervision on the group, branch, and subsidiary level, in accordance with the international core principles for financial supervision, and AML/CFT policies and procedures. Financial Institution: Anyone who conducts one or several of the financial activities or operations of /or on behalf of a Customer. Financial Transactions or Activities: Any activity or transaction defined in Article (2) of the Cabinet Decision. Financing of Illegal Organisations: Any physical or legal action aiming at providing funding to an illegal organisation, or any of its activities or members. Financing of Terrorism: Any of the acts mentioned in Articles (29, 30) of Federal Law no. (7) of 2014 on combating terrorism offences. FIU: Financial Intelligence Unit. Funds: Assets in whatever form, whether tangible, intangible, movable or immovable including national currency, foreign currencies, documents or notes evidencing the ownership of those assets or associated rights in any forms including electronic or digital forms or any interests, profits or income originating or earned from these assets. High Risk Customer: A customer who represents a risk either in person, activity, Business Relationship, nature or geographical area, such as a customer from a high-risk country or non-resident in a country that does not hold an identity card, or a costumer having a complex structure, performing complex operations or having unclear economic objective, or who conducts cash-intensive operations, or operations with an unknown third party, or operations without directly confronting any other high risk operations identified by Financial Institutions, or Designated Non-Financial Businesses and Professions, or the Supervisory Authority. Illegal Organisations: Organisations whose establishment is criminalised or which exercise a criminalised activity. Intermediary Account: Corresponding account used directly by a third party to conduct a transaction on its own behalf. Intermediary Financial Institution: The Financial Institution that receives and sends wire transfer between the Ordering Financial Institution and the Beneficiary Financial institution or another Intermediary Financial Institution. Law Enforcement Authorities: Federal and local authorities which are entrusted under applicable legislation to combat, search, investigate and collect evidences on the crimes including AML/CFT crimes and financing illegal organisations. Legal Arrangement: A relationship established by means of a contract between two or more parties which does not result in the creation of a legal personality such as Trusts or other similar arrangements. MENAFATF: MENAFATF is a FATF-Style Regional Body (FSRB), for the purpose of fostering co-operation and co-ordination between the countries of the MENA region in establishing an effective system of compliance with international AML/CFT standards. The UAE is one of the founding members of MENAFATF. Means: Any means used or intended to be used for the commitment of an offence or felony. Minister: Minister of Finance Money Laundering: Any of the acts mentioned in Clause (1) of Article (2) of the Decree-Law. Non-Profit Organisations (NPOs): Any organized group, of a continuing nature set for a temporary or permanent time period, comprising natural or legal persons or not for profit Legal Arrangements for the purpose of collecting, receiving or disbursing funds for charitable, religious, cultural, educational, social, communal or any other charitable activities. Politically Exposed Persons (PEPs): Natural persons who are or have been entrusted with prominent public functions in the State or any other foreign country such as Heads of States or Governments, senior politicians, senior government officials, judicial or military officials, senior executive managers of state-owned corporations, and senior officials of political parties and persons who are, or have previously been, entrusted with the management of an international organisation or any prominent function within such an organisation; and the definition also includes the following:
1. Direct family members (Of the PEP, who are spouses, children, spouses of children, parents).
2. Associates known to be close to the PEP, which include:
a- Individuals having joint ownership rights in a legal person or arrangement or any other close Business Relationship with the PEP.
b- Individuals having individual ownership rights in a legal person or arrangement established in favour of the PEP.Predicate Offense: Any act constituting an offense or misdemeanour under the applicable laws of the State whether this act is committed inside or outside the State when such act is punishable in both countries. Proceeds: Funds generated directly or indirectly from the commitment of any crime or felony including profits, privileges, and economic interests, or any similar funds converted wholly or partly into other funds. RBA: A Risk-Based Approach is a method for allocating resources to the management and mitigation of ML/FT risk in accordance with the nature and degree of the risk. Registrar: Entity in charge of supervising the register of commercial names for all types of establishments registered in the State. Sanctions Committee: The UN Security Council Committee established as per resolution nos. 1988 (2011), 1267 (1999), 1989 (2011), 2253 (2015), 1718 (2006) and all other related resolutions. Sanctions List: A list wherein individuals and terrorist organizations, which are subject to the Sanctions imposed as per the Security Council Sanctions Committee are listed, along with their personal data and the reasons for Listing. Settlor: A natural or legal person who transfers the control of his funds to a Trustee under a document. Shell Bank Bank that has no physical presence in the country in which it is incorporated and licensed, and is unaffiliated with a regulated financial group that is subject to effective consolidated supervision. State: United Arab Emirates Supervised institutions: Financial institutions (FIs) and Designated Non-Financial Businesses and Professions (DNFBPs) which fall under the scope of Federal Decree-Law No. (20) of 2018 on Facing Money Laundering and Combating the Financing of Terrorism and Illegal Organisations, and of Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 On Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations. Supervisory Authority: Federal and local authorities, which are entrusted by legislation to supervise Financial Institutions, Designated Non-Financial Businesses and Professions and non-profit organisations or the Competent Authority in charge of approving the pursuit of an activity or a profession in case a supervisory authority is not assigned by legislations. Suspicious Transactions: Transactions related to funds for which there are reasonable grounds to believe that they are earned from any misdemeanour or felony or related to the Financing of Terrorism or of illegal organisations, whether committed or attempted. TFS: Targeted Financial Sanctions are part of an international sanctions regime issued by the UN Security Council under Chapter (7) of the United Nations Convention for the Prohibition and Suppression of the Financing of Terrorism and Proliferation of Weapons of Mass Destruction. Transaction: Any business of either dealing, structuring, advising, drafting, appearing, arranging for funding or investing, preparing documentation or disposal or use of Funds or proceeds including for example: deposit, withdrawal, conversion, sale, purchase, lending, swap, mortgage, and donation. Trust: A legal relationship in which a settlor places funds under the control of a trustee for the interest of a beneficiary or for a specified purpose. These assets constitute funds that are independent of the trustee's own estate, and the rights to the trust assets remain in the name of the settlor or in the name of another person on behalf of the settlor. Trustee: A natural or legal person who has the rights and powers conferred to him by the Settlor or the Trust, under which he administers, uses, and acts with the funds of the Settlor in accordance with the conditions imposed on him by either the Settlor or the Trust. Wire Transfer: Financial transaction conducted by a Financial Institution or through an intermediary institution on behalf of a transferor whose funds are received by a beneficiary in another financial institution, whether or not the transferor and the beneficiary are the same person. 11.2 Useful Links
Institution URL Abu Dhabi Global Market https://www.adgm.com/ Abu Dhabi Securities Exchange http://www.adx.ae/ Basel Committee on Banking Supervision (BCBS) http://www.bis.org/bcbs/index.htm Central Bank of the UAE https://www.centralbank.ae Dubai Financial Market http://www.dfm.ae/ Dubai Financial Services Authority (DFSA) http://www.dfsa.ae/ Egmont Group https://egmontgroup.org FATF http://www.fatf-gafi.org Gulf Cooperation Council For The Arab States (GCC) http://www.gcc-sg.org/ International Organisation of Securities Commissions (IOSCO) http://www.iosco.org/ Interpol/Money Laundering http://www.interpol.int/Public/FinancialCrime/MoneyLaundering/default.asp MENAFATF http://www.menafatf.org/ Securities and Commodities Authority http://www.sca.ae/ United Nations http://www.un.org/ United Nations Office on Drugs & Crime – Global Programme Against Money Laundering http://www.unodc.org/unodc/money-laundering/index.html Wolfsberg Group https://www.wolfsberg-principles.com/ Guidance for Licensed Financial Institutions on Suspicious Transaction Reporting
Effective from 7/6/20211. Introduction
1.1. Purpose
Article 44.11 of the Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations charges Supervisory Authorities with “providing Financial Institutions…with guidelines and feedback to enhance the effectiveness of implementation of the Crime-combatting measures.”
The purpose of this Guidance is to assist the understanding and effective performance by the United Arab Emirates Central Bank’s (“CBUAE”) licensed financial institutions (“LFIs”) of their statutory obligations under the legal and regulatory framework in force in the UAE. It should be read in conjunction with the CBUAE's Procedures for Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations (issued by Notice No. 74/2019 dated 19/06/2019) and Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations for Financial Institutions (issued by Notice 79/2019 dated 27/06/2019) and any amendments or updates thereof.1 As such, while this Guidance neither constitutes additional legislation or regulation nor replaces or supersedes any legal or regulatory requirements or statutory obligations, it sets out the expectations of the CBUAE for LFIs to be able to demonstrate compliance with these requirements. In the event of a discrepancy between this Guidance and the legal or regulatory frameworks currently in force, the latter will prevail. This Guidance may be supplemented with additional separate guidance materials, such as outreach sessions and thematic reviews conducted by the Central Bank.
Furthermore, this Guidance takes into account standards and guidance issued by the Financial Action Task Force (“FATF”), industry best practices and red flag indicators. These are not exhaustive and do not set limitations on the measures to be taken by LFIs in order to meet their statutory obligations under the legal and regulatory framework currently in force. As such, LFIs should perform their own assessments of the manner in which they should meet their statutory obligations.
This Guidance comes into effect immediately upon its issuance by the CBUAE with LFIs expected to demonstrate compliance with its requirements within one month from its coming into effect.
1 Available at https://www.centralbank.ae/en/cbuae-amlcft
1.2. Applicability
Unless otherwise noted, this guidance applies to all natural and legal persons, which are licensed and/or supervised by CBUAE, in the following categories:
• National banks, branches of foreign banks, exchange houses, finance companies, payment service providers, registered hawala providers and other LFIs; and • Insurance companies, agencies, and brokers.
1.3. Legal Basis
(AML-CFT Law Articles 9.1, 15, 24, 25, 27; AML-CFT Decision Articles 16-18, 20.2, 21.2, 40-43)
The requirement to submit Suspicious Transaction Reports (“STRs”) to the Financial Intelligence Unit ("FIU”) is outlined in the (i) Federal Decree-Law No. (20) of 2018 on Anti-Money Laundering (“AML”) and Combatting the Financing of Terrorism (“CFT”) and Financing Illegal Organisations and Federal Decree law No. (26) of 2021 To amend certain provisions of Federal Decree-law No. (20) of 2018, on anti-money laundering and combating the financing of terrorism and financing of illegal organisations (the “AML-CFT Law”); (ii) Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation for Decree-Law No. (20) of 2018 on AML and CFT and Financing of Illegal Organisations (the “AML-CFT Decision”); and (iii) Cabinet Decision No. (74) of 2020 Regarding Terrorism Lists Regulation and Implementation of UN Security Council Resolutions on the Suppression and Combating of Terrorism, Terrorist Financing, Countering the Proliferation of Weapons of Mass Destruction and its Financing and Relevant Resolution.
Under the UAE AML-CFT legal and regulatory framework, all LFIs are obliged to promptly report to the FIU suspicious transactions and any additional information when there are suspicions, or reasonable grounds to suspect, that the proceeds are related to a crime, or to the attempt or intention to use funds or proceeds for the purpose of committing, concealing, or benefitting from a crime. “Crime” is defined in Article 1 of the AML-CFT Law as “money laundering crime and related predicate offences, or financing of terrorism or illegal organisations.” There is no minimum reporting threshold; all suspicious transactions, including attempted transactions, should be reported regardless of the amount of the transaction. LFIs are also required to put in place and update indicators that can be used to identify possible suspicious transactions.
Although the AML-CFT Law uses the term “STRs” to mean both suspicious transactions and activity, for the purposes of this Guidance document, suspicious activity involving transactions should be reported (in the first instance) to the FIU as STRs; suspicious activity that does not involve transactions, on the other hand, should be reported (in the first instance) to the FIU as Suspicious Activity Reports (“SARs”). Examples of scenarios that warrant a SAR filing include, but are not limited to: the customer is the subject of material adverse media; the customer alerts as a positive sanctions match; the prospective customer acts in a manner that is suspicious upon account opening (e.g., refusing to answer account opening questions; providing falsified or counterfeit documentation; exhibiting reluctance to provide detailed information about a business account, etc.); or the customer exhibits other suspicious behavior (e.g., inquiring about ways to circumvent certain reporting thresholds). STRs, SARs, and other report types (referenced in greater detail in Section 3.2 (“Basic Structure of an STR or SAR”)) align with the FIU’s current reporting regime and utilization of the goAML system.
Under federal law and regulations, whether the LFIs operate in the mainland UAE or in a Financial or Commercial Free Zone, the designated competent authority for receiving report of suspicious transactions or activity is the FIU. The UAE’s minimum statutory obligations that apply to LFIs are covered in the following requirements:
• To put in place indicators to identify suspicious transactions (AML-CFT Law Article 15, AML-CFT Decision Article 16). • To report suspicious activity to the FIU and cooperate with relevant authorities, including to not disclose the information or data in an STR (AML-CFT Law Articles 9.1, 15, 24, 25, 27, AML-CFT Decision Articles 13.2, 17.1, 18.1, 20.2, 42.1/2).
1.3.1. Consequences for Failure to Disclose Suspicious Activity
Failure to report a suspicious transaction (STR, SAR, or other report types) without delay, whether intentionally or by gross negligence, is a federal crime in the UAE. The AML-CFT Law provides for the following sanctions against any person, including an LFI, or their managers and employees, who fail to perform, whether purposely or through gross negligence, their statutory obligation to report a suspicion of money laundering and related predicate offences or the financing of terrorism or of illegal organisations:
• Imprisonment and fine of no less than AED100,000 and no more than AED1,000,000; or • Any of these two sanctions (i.e., imprisonment or fine of no less than AED100,000 and no more than AED1,000,000), according to Article 24 of the AML-CFT Law.
According to Article 15 of the AML-CFT Law, the requirement to report is in the case of suspicion or reasonable grounds to suspect a crime.
1.3.2. Protection for Individuals Disclosing Suspicious Activity
LFIs as well as their board members, employees, and authorized representatives, are protected by Article 15 of the AML-CFT Law and Article 17.3 of the AML-CFT Decision from any administrative, civil, or criminal liability resulting from their good-faith performance of their statutory obligation to report suspicious activity to the FIU. This is also the case even if they did not know precisely what the underlying criminal activity was, and regardless of whether illegal activity actually occurred. This covers cases when an employee files an STR, SAR, or other report types that its employer did not want to file.
However, it should be noted that such protections do not extend to the unlawful disclosure to the customer or any other person, whether directly or indirectly, that they have reported or intend to report a suspicious transaction, or of the information or data the report contains, or that an investigation is being conducted in relation to the transaction.
1.3.3. Meaning of Suspicious Transaction
Within the AML-CFT Law and its AML-CFT Decision, a suspicious transaction refers to any transaction, attempted transaction, or funds for which an LFI has reasonable grounds to suspect as constituting—in whole or in part, and regardless of the amount or the timing - any of the following:
• The proceeds of crime (Money laundering and related predicate offenses, or financing of terrorism or illegal organisations); • Being related to the crimes of money laundering and related predicate offences, the financing of terrorism or illegal organisations; and • Being intended to be used in an activity related to such crimes.
The AML-CFT Law and its AML-CFT Decision define a predicate offence as “any act constituting an offense or misdemeanour under the applicable laws of the State whether this act is committed inside or outside the State when such act is punishable in both countries.”
It should be noted that the only requirement for a transaction to be considered as suspicious is “reasonable grounds” in relation to the conditions referenced above. Thus, the suspicious nature of a transaction can be inferred from certain information, including indicators; financial/transactional and behavioral patterns; Customer Due Diligence (“CDD”) information; or adverse media information, and it is not dependent on obtaining evidence that a predicate offense has actually occurred or on proving the illicit source of the proceeds involved. LFIs do not need to have knowledge of the underlying criminal activity nor any founded suspicion that the proceeds originate from a criminal activity; reasonable grounds to suspect any such criminal activity are sufficient.
LFIs should also note that suspicious transactions need not be completed, in progress, or pending completion. Attempted transactions, transactions that are not executed and past transactions, regardless of their timing or completion status, which are found upon review to cause reasonable grounds for suspicion, must be reported in accordance with the relevant requirements.
1.4. Acronyms
Terms Description AIF Additional Information File without Transactions AIFT Additional Information File with Transactions AML / CFT Anti-Money Laundering / Combatting the Financing of Terrorism and Illegal Organisations CBUAE Central Bank of the United Arab Emirates CDD Customer Due Diligence EDD Enhanced Due Diligence FATF Financial Action Task Force FIU Financial Intelligence Unit HRC High Risk Country Transaction Report HRCA High Risk Country Activity Report KYC Know Your Customer QC Quality Control Report Any STR, SAR, AIF, AIFT, RFI, or RFIT based report RFI Request for Information without Transactions RFIT Request for Information with Transactions RFR Reason For Reporting SAR Suspicious Activity Report STR Suspicious Transaction Report 2. Identification of Suspicious Transactions
2.1. Role of the First Line of Defens
Employees within the first line of defense (e.g., relationship managers, business executives, and backoffice operations functions) should understand the AML/CFT risks posed to the business in which they work. First line of defense employees are central to the management of customer and third-party risk and the timely escalation of potentially suspicious activity. LFIs should not rely solely on transaction monitoring systems to identify unusual and potentially suspicious activity in their customer population. First line of defense employees play a critical role in the detection and prevention of money laundering and the financing of terrorism and illegal organisations. Appropriately trained employees are in fact well-placed to identify suspicious transactions and assess that information once deemed reasonable—collected through interactions with a customer—now appears suspicious. They should therefore be trained regarding potential risk and risk mitigation and reporting within their business area. Employees should understand the regulatory requirements within the scope of their role; red flags associated with their customers, products, services, delivery channels, and geographies; and the appropriate escalation procedure both to their management and to the second line of defense without compromising their responsibility to report suspicious transactions.
2.2. Role of the Second Line of Defense
The second line of defense (e.g., compliance employees) provides policy advice, guidance, assurance, oversight, and challenge to the first line of defense. While employees in Financial Crime Operations Units (possibly in the first line of defense) can investigate suspicious transactions and document the resultant investigation, the ultimate filing of the STR or SAR must be made by the Compliance Officer or the MLRO (in the second line of defense). To this end, the second line of defense is charged with overseeing the investigations programme comprised of both automated and manual monitoring processes. The second line of defense is also charged with monitoring risks facing the LFI, such as noncompliance with UAE laws and regulations, and reporting directly to senior management on the LFI’s risk exposure, including through financial crime-related metrics. Specifically, the second line of defense and first line of defense (as applicable) should generate financial crime-related metrics (e.g., STRs or SARs filed, alert backlogs) to provide senior management with an adequate overview of the LFI’s compliance program, including the timeliness and quality of the LFI’s handling and resolution of transaction monitoring alerts and the STR or SAR filing process. The second line of defense should retain records of all information relating to transaction monitoring and suspicious activity reporting for a period of no less than five (5) years as provided in Article 24 of the AML-CFT Decision.
2.2.1. Role of the Compliance Officer / MLRO
According to Article 21 of the AML-CFT Decision, LFIs are required to appoint a Compliance Officer with the appropriate competencies and experience to perform the necessary tasks to:
• Detect transactions relating to any crime as defined in Article 1 of the AML-CFT Decision. • Review, scrutinize, and study records; receive data concerning suspicious transactions; and make decisions to either notify the FIU or maintain the transaction with a documented rationale for maintaining the transaction while upholding confidentiality requirements. • Review the internal rules and procedures relating to combating the crime and their consistency with relevant laws and regulations; assess the extent to which the LFI is committed to the application of these rules and procedures; propose what is needed to update and develop these rules and procedures; prepare and submit semi-annual reports on these points to senior management; and send a copy of that report to the relevant supervisory authority with senior management remarks and decisions. • Prepare, execute, and document ongoing training and development programs and plans for the LFI’s employees on money laundering and the financing of terrorism and financing of illegal organisations, and the means to combat them. • Collaborate with the supervisory authority and FIU, provide them with all requested data, and allow their authorized employees to view the necessary records and documents that will allow them to perform their duties.
According to CBUAE’s Guidelines, the Compliance Officer is the LFI’s money laundering reporting officer (“MLRO”) charged with reviewing, scrutinizing, and reporting STRs and other reports pertaining to suspicious activity. In this capacity, the Compliance Officer or MLRO is ultimately responsible for the detection of transactions related to money laundering and financing of terrorism and illegal organisations; for reporting suspicions to the FIU; implementing the appropriate actions following an STR, SAR, or other report filing (e.g., ensuring the STR or SAR subject is input into the relevant list for close monitoring or internal watchlists/blacklists; changing the customer risk rating; etc.); and for cooperating with the relevant authorities on AML/CFT matters. The Compliance Officer or MLRO is ultimately responsible to ensure that an appropriate programme exists in the LFI and that the LFI effectively deploys a risk-based approach to detect and report suspicious activity.
The Compliance Officer or MLRO should also act as the primary point of contact with law enforcement agencies for their requests and investigations. The Compliance Officer or MLRO is responsible for liaising with regulators and external bodies on financial crime issues in order to share knowledge, report cases, develop best practices, and where possible, to improve coordination within the financial sector.
2.3. Role of the Third Line of Defense
The independent testing function is responsible for evaluating the design and operational effectiveness of an LFI’s compliance program controls, including technical compliance with AML/CFT policies and procedures. This function serves as a “third line of defense” to identify gaps, deficiencies, and weaknesses in operational controls owned or overseen by an LFI’s business, operations, and compliance functions. Independent testing should be conducted by an internal audit department, outside auditors, consultants, and/or other qualified, independent third parties. At a minimum, employees responsible for conducting independent testing should not be involved in the function being tested or in other AML/CFT functions that could compromise their independence. Risk-based auditing assists an LFI’s Board of Directors and senior management in identifying areas of weakness, prioritizing those areas for remediation, and ensuring the provision of adequate resources, oversight, and training for affected employees.
2.4. Purpose of Transaction Monitoring
The purpose of transaction monitoring is the ongoing, retrospective monitoring of customers’ and prospective customers’ transactions or activity to identify activity anomalous from normal behavior. This may, on further investigation, generate knowledge or reasonable suspicion of financial crime and thereby require reporting to the appropriate law enforcement and/or regulatory authority as an STR, SAR, or equivalent local report in line with AML/CFT regulatory and/or UAE FIU reporting requirements. LFIs may choose to use a combination of automated transaction monitoring scenarios and exception-based (manual) transaction reports to monitor for potentially suspicious activity. The aim of the alert review process is to identify and respond to potential indicators of money laundering, associated predicate offenses, financing of terrorism and illegal organisations , financing of proliferation, and any potentially unusual activity that does not align to a customer’s or account's profile including by deploying a risk-based approach. An LFI’s transaction monitoring systems and manual processes should be reviewed, assessed, and revised periodically—at least annually—and otherwise as appropriate, justified by the required circumstances. Additionally, this review should include both an evaluation of transaction monitoring system thresholds and a fine tuning of the LFI’s transaction monitoring system as well as an evaluation of its effectiveness. The individuals responsible for the review should have a proper understanding of the LFI’s framework-including the LFI's business and customer base—to generate a meaningful output.
2.5. Internal Organization
In order for an LFI’s transaction monitoring and suspicious activity reporting program to be effective, it must be based on the foundation of a sound governance structure. Namely, an LFI’s internal organization is important to appropriately identifying unusual or potentially suspicious activity. Internal organization comprises an LFI’s policies, procedures, and processes designed to oversee and manage risks and to achieve compliance with UAE AML/CFT laws and regulations. In particular, an LFI’s internal organization addresses the core organizational elements of an LFI’s compliance program: governance and management oversight; policies and procedures; clear lines of responsibility and reporting; and ongoing training to account for changes in the UAE’s legislative and regulatory frameworks.
• Governance and Management Oversight: Governance and management oversight helps to ensure that an LFI’s compliance program is appropriately funded, staffed, and equipped with the requisite technology, including to identify and report suspicious activity. An LFI’s Board of Directors also ensures that the compliance program has an appropriately prominent status within the organization and is operationally independent. In this capacity, senior management, inclusive of the Compliance Officer, within a compliance program should have the appropriate authority; independence; access to employees and information within the organization; and appropriate resources to conduct their activities—including the identification and reporting of suspicious activity—effectively. The compliance program should have access to the Board of Directors or a designated board committee to raise any issues or risks; report on the status of ongoing compliance; and escalate any other pertinent AML/CFT-related information. • As part of an LFI’s risk management framework, senior management and an LFI’s Board of Directors should oversee the design, implementation, and maintenance of a transaction monitoring and suspicious activity reporting program based on an LFI’s AML/CFT risks and in accordance with all applicable laws and regulations. Senior management should likewise oversee a vendor selection process (as applicable) if a third-party vendor is used to acquire, install, implement, or test a transaction monitoring program or any aspect of identifying and reporting suspicious activity, among other responsibilities. The Compliance Officer (or MLRO) shall periodically update the Board of Directors (or a committee of the Board) on the overall capability framework (that includes technology and process aspects of suspicious activity identification, investigation and reporting aspects). • Policies and Procedures: An LFI should have policies and procedures that govern changes to its transaction monitoring program which ensures that changes are defined, managed, controlled, reported, and audited. Namely, LFIs should have governance protocols surrounding the design and implementation of new detection scenarios; periodic assessment and validation of existing detection scenarios; and retiring of detection scenarios. In addition, an LFI should develop a procedure for the investigation and processing of transaction monitoring alerts in order to file an STR, SAR, or other report type promptly and qualitatively. These policies and procedures should cover the key processes for drafting and filing an STR, SAR, or other report type and other regulatory reports. More broadly, policies and procedures work to manage key AML/CFT risks and create processes for adherence across an LFI. • Clear Lines of Responsibility and Reporting: In relation to suspicious transactions, an LFI should have clear roles, responsibilities, and reporting lines, including reporting and escalations to the Board of Directors and senior management. These roles, responsibilities, and reporting lines should be clearly documented across all three lines of defense. Clear lines of responsibility help with effectively identifying and reporting suspicious activity in a timely manner while ensuring that there is appropriate and effective oversight of employees who engage in activities which may pose greater AML/CFT risk. LFIs should also have a mechanism to inform senior management and the Board of Directors (or a committee of the Board) of compliance initiatives, compliance deficiencies, STRs or SARs (or other reports) filed, and corrective actions taken. • Ongoing Training: Training should be provided on an ongoing basis to an LFI’s employees and should include changes to the UAE’s legislative and regulatory frameworks; internal policies or procedures; and understanding of evolving risk issues with respect to an LFI’s transaction monitoring and suspicious activity reporting program. Training topics can include, but are not limited to, thematic analysis of STRs or SARs; regulatory requirements and best practices related to STR or SAR reporting; noteworthy STRs or SARs (or other reports) filed during the prior quarter; and controls related to emerging financial crime risks. Training should be customized to include any other internal data that would be beneficial to both the first line and second line of defense.
2.5.1. Considerations for Institutions with Foreign Branches and Subsidiaries
For LFIs operating in an international context, FATF Recommendation 18 recommends that financial groups are required to implement group-wide AML/CFT programs applicable to foreign branches and majority-owned subsidiaries. Recent major enforcement actions taken by supervisors in key jurisdictions have highlighted the need to ensure that systems and controls are aligned across a financial group and that foreign branches and majority-owned subsidiaries align AML/CFT measures with a financial group’s home country requirements. As a result, LFIs have implemented global AML/CFT policies that outline a group risk appetite and are managed in each jurisdiction to align to local regulatory or legislative requirements. To support alignment of controls, LFIs operating across jurisdictions may seek to leverage the same control solutions for key processes, such as customer screening or transaction monitoring, though there may be different rules for different jurisdictions. For example, if the LFI operates in an economy which is known to be more cash-based than another, the cash trigger rules in transaction monitoring may vary appropriately. Centralized controls with operational centers of excellence also provide a means of ensuring alignment across the group around systems and controls.
2.6. Transaction Monitoring Methods
The five key components to an effective transaction monitoring and reporting system are: (i) identification of unusual or suspicious activity; (ii) managing alerts with an alert risk scoring model; (iii) STR or SAR decision making; (iv) STR or SAR completion and filing; and (v) monitoring and STR or SAR filing on continuing activity. To effectively identify unusual or potentially suspicious activity, LFIs should first maintain a transaction monitoring program based on an underlying AML/CFT risk-based assessment. The transaction monitoring program should take into account the AML/CFT risks of the LFI’s customers, prospective customers, counterparties, businesses, products, services, delivery channels, and geographic markets in addition to helping prioritize high-risk alerts. However, the sophistication of monitoring systems can differ based on an LFI’s AML/CFT risks. Monitoring systems typically include employee identification or referrals, transaction-based (manual) systems, surveillance (automated) systems, or a combination of these. Overall, LFIs must adopt monitoring processes and procedures to monitor customer activity that are commensurate with the size and nature of the line of business and the money laundering and the financing of terrorism and illegal organisations’ risks posed by their relevant customer base. The monitoring system and/or manual processes must reasonably demonstrate that transactions that carry the highest risk of money laundering and financing of terrorism and illegal organisations are subject to enhanced scrutiny.
As part of a risk-based approach to AML/CFT, in the case of customers or Business Relationships identified as high-risk, LFIs are expected to investigate and obtain more information about the purpose of transactions, and to enhance ongoing monitoring and review of transactions in order to identify potentially unusual or suspicious activities. In the case of customers or Business Relationships that are identified as low-risk, LFIs may consider monitoring and reviewing transactions at a reduced frequency.
Examples of some of the methods that may be employed for the ongoing monitoring of transactions include, but are not limited to:
• Threshold-based rules, in which transactions above certain pre-determined values, numerical volumes, or aggregate amounts are examined; • Transaction-based rules, in which the transactions of a certain type are examined; • Location-based rules, in which the transactions involving a specific location (either as origin or destination) are examined; and • Customer-based rules, in which the transactions of particular customers are examined.
2.6.1. Manual Monitoring
An LFI may seek to utilize a manual transaction monitoring system, which typically targets specific categories of transactions (e.g., those involving large amounts of cash, those to or from certain geographies) and includes a manual review of various reports generated by the LFI’s systems in order to identify unusual activity. The type and frequency of reviews and resulting reports used should be commensurate with the LFI’s AML/CFT risk profile—including the nature, size, and complexity of its operations—and properly cover customers, counterparties, businesses, products, services, delivery channels, and geographic markets. System-generated reports typically use a certain currency threshold to detect unusual activity. An LFI’s responsible senior employee should periodically evaluate the appropriateness of filtering criteria and thresholds used in the monitoring process and periodically appraise Senior Management and where required, notify the Board of Directors (as part of periodic updates), on the appropriateness of design of manual monitoring reports. LFIs should be alert to the fact that complex and evolving financial crime risks can undermine the effectiveness of manual monitoring systems, and therefore, manual monitoring systems should also be independently reviewed for reasonable filtering criteria.
2.6.2. Automated Transaction Monitoring
Automated transaction monitoring systems can cover multiple types of transactions and use different rules to identify potentially suspicious activity. In addition, many systems can adapt over time based on historical activity, trends, or internal peer comparison. After parameters and filters have been developed, they should be reviewed before implementation to identify any gaps in coverage to address potential financial crime schemes that may not have been addressed. LFIs should also seek to have appropriate case management systems so that such funds or transactions are scrutinized in a timely manner and a determination is made as to whether the funds or transaction are suspicious.
Once established, the LFI should review and test system capabilities and thresholds on a periodic basis, commensurate to its risk profile. This review should focus on specific parameters or filters in order to ensure that intended information is accurately captured, and that the parameter or filter is appropriate for the LFI’s particular risk profile, including the applicability of the detection scenarios, underlying rules, threshold values, and assumptions used. An LFI should also aim to review its transaction monitoring program at least annually to account for changes in the LFI’s internal procedures; local laws and regulations; and best practices.
Relatedly, the authorization to establish or alter expected activity profiles should be clearly defined through policies and procedures. An LFI’s internal controls should ensure limited access to the monitoring systems, and changes should require the approval of the Compliance Officer, MLRO, or senior management. The LFI should implement a robust end-to-end, pre- and post-implementation testing procedure of its transaction monitoring program with documentation detailing current detection scenarios and the underlying assumptions, parameters, and thresholds applied.
Employees appointed by the LFI should also be responsible for the design, planning, implementation, operation, testing, validation, and on-going analysis of the transaction monitoring program, which may extend to assessing the timely review and decision-making of generated alerts and potential STR or SAR filings. Such employees should be responsible for independently validating an LFI’s transaction monitoring system's programming methodology and effectiveness to ensure that the LFI’s automated transaction monitoring system is effectively detecting potentially suspicious activity. These appointed employees should also ensure that customer segments, customer types, and transactions/transaction codes are mapped into the transaction monitoring system, and that the transaction monitoring system is integrated with the LFI’s core banking and other relevant system. Independent validation should also take place of an LFI’s policies with an aim to assess if employees are adhering to these policies. This is especially important to validate the proper use of automated tools and to ensure that the application of information technology instruments or algorithms—often leveraged by LFIs to reduce the number of false positives in their transaction monitoring programs—is not inadvertently suppressing instances of reportable suspicious activity. Where appropriate, the LFI, in lieu of maintaining full time employees to perform aforementioned functions, may hire qualified specialist consultants or external vendors to provide such review services.
2.6.3. Intelligence-led Transaction Monitoring Approach
LFIs have begun to invest in forming and developing their own intelligence units or capabilities. By establishing such units or capabilities, these units seek to maximize the use of data and information available both internally—within the LFI—and externally—across jurisdictions and businesses—in order to tackle money laundering, the financing of terrorism and illegal organisations, and fraud schemes, as well as to consolidate analytical capacity and remove any jurisdictional and business silos. This has led some LFIs to shift from a pure transaction-level monitoring approach towards adopting a “customer-level” or “network” monitoring approach. Under this approach, previous investigations can be applied to inform and refine risk models, which can then be used to customize monitoring for different business lines and customer types. These enhancements are focused on looking beyond single transactions or single customers to identify the wider network in which a customer operates—looking at the customer as an entity—enabling LFIs to manage networks of accounts and report on these networks, that in turn, increases opportunities to disrupt that network. This model moves reporting away from reports of single suspicious transactions towards suspicious entities and networks with a view on how the funds flow between them.
3. Procedures for the Reporting of Suspicious Transactions
All customers and accounts should be subject to monitoring under a risk-based approach in order to identify potentially suspicious transactions, patterns, as well as behavior that is inconsistent with past behavior on the account or with the anticipated activity on the account as determined at onboarding. Alerts on such behavior are risk relevant indicators of potentially suspicious activity. Upon identifying unusual or potentially suspicious activity, an LFI’s employees must review and, as appropriate, escalate the activity for further investigation or immediate action.
Although the process for reviewing unusual or potentially suspicious activity for further investigation or immediate action is not outlined in this guidance, LFIs should establish a process to investigate such activity, including developing policies and procedures that document the process for deciding whether to close the alert or to promptly report the transaction as suspicious and should include guidance on capturing detailed descriptions for the manner in which the alerts were either disposed of by reporting or closure of the alerts. For the purposes of this guidance, best practices are discussed once activity is determined to meet one or more of the regulatory definitions of suspicious activity and when an LFI decides to report such activity to the FIU by filing an STR, SAR, or other report type.
3.1. Importance of Filing an STR and SAR
The information generated from an STR, SAR, and other report type is important for identifying and combatting financial crime. First, the quality of STRs, SARs, and other report types is imperative for increasing the FIU’s analytical function to identify vulnerabilities and threats to the UAE financial system and develop an overall understanding of money laundering and the financing of terrorism and illegal organisations’ risks based on emerging trends and patterns. Relatedly, STRs, SARs, and other report types also assist law enforcement in detecting criminal actors and preventing the flow of illicit funds through the UAE financial system. Law enforcement uses the intelligence generated from STRs, SARs, and other report types to initiate and supplement money laundering or terrorist financing investigations and other criminal cases. As a result, it is critical that the information provided in all reports of suspicious activity be as accurate, timely, and complete as possible.
3.2. Basic Structure of an STR or SAR
The Compliance Officer or MLRO and other concerned employees responsible for using the goAML system must be aware of the different report types. As such, the LFI should select the correct report type when filing a report through the goAML system. The STR and SAR are the primary (or first instance) reports which must be used to report a new suspicion, whereas Additional Information File without Transactions (“AIF”) and Additional Information File with Transactions (“AIFT”) report types are supplementary reports which can be used to escalate additional information or transactions that correspond to a previously filed STR or SAR. When filing an AIF or AIFT, the LFI should input the Reference Number that corresponds to the STR or SAR.
• STR: If, during the establishment or course of the customer relationship, or when conducting transactions on behalf of a customer or an occasional customer, an LFI suspects transactions are related to money laundering, related predicate offenses, or the financing of terrorism or illegal organisations, then the LFI should submit an STR to the FIU within the timelines established in this guidance. • SAR: If, during the establishment or course of the customer relationship, an LFI suspects any activity or an attempted transaction (i.e., a non-executed transaction) can be related to money laundering, related predicate offenses, or the financing of terrorism or illegal organisations, then the LFI should submit a SAR to the FIU within the timelines established in this guidance. • Additional Information File (“AIF”) without Transactions: Should the FIU require any further details while reviewing an STR or SAR, then the LFI that originally submitted the report may be solicited for further information by receiving an AIF request from the FIU through the Message Board. Should such a situation arise, the LFI is required to submit an AIF based report through the goAML platform. Please note that an AIF is a supplemental report that does not contain transactional details. • Additional Information File with Transactions (“AIFT”): Should the FIU require any further details including transactions while processing an STR or SAR, then the LFI that originally submitted the said report may be solicited for further information including transactions by receiving an AIFT request from the FIU through the Message Board. Should such a situation arise, then the LFI is required to submit an AIFT report through the goAML. Please note that an AIFT is a supplemental report that contains transactional details. • Request for Information (“RFI”) without Transactions: Should the FIU require further information from multiple LFIs rather than just the entity responsible for submitting the STR or SAR, then an RFI request will be sent out to the concerned LFIs through the goAML Message Board. Should such a situation arise, then the LFI is required to submit an RFI report through the goAML portal. • Request for Information with Transactions (“RFIT”): The ‘RFI with Transaction(s)’ report is similar to the structure of an RFI request, with the exception that this report type supports the use of transactions. • High Risk Country Transaction Report (“HRC”): If, during the establishment or course of the customer relationship, or when conducting transactions on behalf of a customer or a potential customer, an LFI identifies transactions related to high-risk countries as defined by the National Anti-Money Laundering and Combating the Financing of Terrorism and financing of Illegal Organizations Committee2, then the LFI should submit an HRC to the FIU. Such reported transaction(s) may only be executed three working days after reporting such to the FIU, and if the FIU does not object to conducting the transaction within the set period. • High Risk Country Activity Report (“HRCA”): If, during the establishment or course of the customer relationship, or when conducting an activity on behalf of a customer or a potential customer, a reporting entity identifies activities related to high-risk countries as defined by the National Anti- Money Laundering and Combating the Financing of Terrorism and financing of Illegal Organizations Committee3, then the entity should submit an HRC to the FIU. Such reported activity(ies) may only be executed three working days after reporting such to the FIU, and if the FIU does not object to conducting the activity within the set period.
When all applicable information is collected, analyzed, and documented and the LFI decides that an STR or SAR is required, the information should be described in the narrative within an investigative narrative report template in a concise and chronological format. The LFI should divide the narrative into three sections: an introduction, a body, and a conclusion. The investigative narrative report template is considered as an addition to the goAML report (due to the potential text limitation within the “goAML description of the report” field).
• Introduction
The introductory paragraph should provide:
• A brief statement addressing the purpose of the report with a general description of the known or alleged violation. • The name(s) of the subject against whom the report is filed. • Any linked/ previous STRs, SARs, or other reports, including the date of any STR(s) / SAR(s) filed (or other reports) previously on the suspect or related suspects and the reason why the previous STR(s) / SAR(s) (or other report) was filed.
Additional Guidance:
• Whether the activity is associated with any sanctioned countries or contained on government lists for individuals or organisations. • A summary of the “red flags” and suspicious patterns of activity that initiated the report. (This information should be provided either in the introduction or conclusion of the narrative).
• Body
The next paragraph or paragraphs of the narrative can provide all pertinent information documenting why the STR, SAR, or other report was filed and might include:
• Details of parties facilitating the suspicious activity or transactions. If the subject is an entity, details of the subject can include the entity’s trade license number, date established, line of business, licensing authority, and ownership structure. • Involved suspected transactions (usually identified in chronological order by date and amount) [To be included only for an STR and supplementary reports involving transactions]. • The review period for the suspicious activity or transactions. • The source of funds, destination of funds, and total of suspected amounts. This can include the transactor and beneficiary information, providing as much detail as possible, including the name and location of any involved domestic and/or international financial institution(s); names, addresses, account numbers, and any other available identifiers of originator and beneficiary transactor(s); and/or third parties or business entities on whose behalf the conductor was acting; the date(s) of the transaction(s); and amount(s). • Explain in detail the reason for the suspicion, and why the activity or transaction is determined to be illegal or suspicious. • Description of the method of operation (i.e., modus operandi).
Additional Guidance:
• A breakdown of larger volumes of financial activity into categories of credits and debits, and by date and amount. [To be included only for an STR and supplementary reports involving transactions]. • An explanation of any observed relationships among the transactors (e.g., shared accounts, addresses, employment, known or suspected business relationships and/or frequency of transactions occurring amongst them; appearing together at the LFI and/or counter). [To be included only for an STR and supplementary reports involving transactions]. • Specific details on cash transactions that identify the branch(es) where the transaction(s) occurred, the type of transaction(s), and how the transaction(s) occurred (e.g., night deposit, on-line banking, ATM, etc.). [To be included only for an STR and supplementary reports involving transactions]. • Any factual observations or incriminating statements made by the suspect.
• Conclusion
The final paragraph will be covered under “Action Taken by Reporting Entity” field. The final paragraph of the narrative can summarize the report and might also include:
• Any planned/initiated mitigating steps, including information about any follow-up actions conducted by the LFI (e.g., intent to close or closure of accounts, ongoing monitoring of activity, etc.).
Additional Guidance:
• Names and telephone numbers of other contacts at the LFI if different from the point of contact indicated in the report. • A general description of any additional information related to the LFI that may be made available to law enforcement by the LFI. • Names of any law enforcement or department/unit investigating the case who are not already identified in another section of the report.
2 https://www.namlcftc.gov.ae/en/high-risk-countries.php
3 Idem note3.3. Best Practices for Drafting an STR or SAR
In general, a narrative should identify the five core components - who? what? when? where? and why? -of the suspicious activity being reported to the FIU. The method of operation/modus operandi (or how?) is also important and should be included in the report narrative. An LFI should ensure that the following five questions are answered prior to submitting an STR, SAR, or other report in the FIU’s goAML system.
Who is conducting the suspicious activity or transaction?
• Describe the subject of the STR, SAR, or other report, otherwise known as the suspect(s), including the conductor, beneficiary, and accountholders involved in the transaction or activity. • Provide identifying information on the parties involved in the transaction, such as the suspect’s occupation and position or title within the business. • List beneficial owners, directors, officers, and those with signing authority, if possible. If the transaction or activity involves an entity, include information on the ownership, control, and structure of the business. • Provide details about each individual or entity's role in each of the financial transactions described. It is important to understand who is sending and receiving the funds. [To be included only for an STR and supplementary reports involving transactions]. • If more than one individual or entity is involved in the suspicious activity, explain the relationships among the individuals or entities (if known).
Even though information may not always be available, information should be included to the extent possible. For instance, addresses for suspects are important; filing LFIs should note not only the suspect’s primary street addresses, but also, other known addresses. Any identification numbers associated with the suspect(s) such as passport and driver’s license numbers are also important to document.
What instruments or mechanisms are being used to facilitate the suspicious activity or transaction(s)?
• Review the instruments or mechanisms used in the suspicious activity (e.g., wire transfers, foreign currency, Wages Protection System (WPS), letters of credit and other trade instruments, correspondent accounts, money orders, credit/debit cards, etc.). • Understand the number of different methods employed for initiating the negotiation of funds, such as the Internet, phone access, mail, night deposit box, remote dial-up, couriers, or others. • Describe the source of the funds (as originator) or use of the funds (as beneficiary). In documenting the movement of funds, identify all account numbers at the LFI affected by the suspicious activity or transaction and when possible, provide any account numbers held at other LFIs and the names/locations of the other LFIs involved in the reported activity.
When did the suspicious activity or transaction take place?
• If the activity takes place over a period of time, provide the date when the suspicious activity or transaction was first observed and describe the duration of the activity. • To better understand the history and nature of the activity, and the flow of funds, LFIs should provide information on each individual transaction in a chronological order (e.g., individual dates and transaction amounts, rather than only the aggregated amount). [To be included only for an STR and supplementary reports involving transactions]. • Provide information on when the transaction was completed or attempted. If the transaction was not completed, the LFI should indicate this in the narrative. [To be included only for an STR and supplementary reports involving transactions].
Where did the suspicious activity or transaction take place?
• Explain if multiple offices of a single LFI were involved in the suspicious activity or transaction being reported. Provide the addresses of those locations. • Specify if the suspected activity or transaction(s) involves a foreign jurisdiction. In this case, list the foreign jurisdiction, LFI, address, and any account numbers involved in, or affiliated with the suspected activity or transaction(s). • This information should include any location involved in the full transaction chain, including ultimate originators and beneficiaries to the extent this can be ascertained. [To be included only for an STR and supplementary reports involving transactions].
Why does the LFI think the activity or transaction is suspicious?
• Describe the industry or business and why the activity or transaction is unusual for the customer. Consider the types of products and services involved in the activity and the expected activities of similar customers. • Assess why the activity created a red flag for the LFI or triggered an alert within the system.
These answers will vary based on the LFI type (for example, a depository institution versus an insurance company) and an LFI should also consider such factors as:
• The types of products and services the LFI offers; • The types of accounts the customer has with the LFI; • The normally expected business activity of the customer (if they are a customer of the LFI), and why this is not normal or expected activity; • The purpose of the payment or transaction, to the extent known, reported, alleged, or questioned; and • If the activity resulted from an automated alert, the scenario or rule that generated the alert.
How did the suspicious activity or transaction occur?
• Describe how the transaction or pattern of transactions was committed (i.e., the “modus operandi” or the method of operation). [To be included only for an STR and supplementary reports involving transactions]. • For example, if there appear to be multiple cheques deposited matched with outgoing wire transfers from the accounts, the narrative should include information about both the cheques and outbound transfers (including dates, destinations, amounts, accounts, frequency, and beneficiaries of the funds transfers).
3.3.1. Defensive STR or SAR Filings4
Defensive filing is the practice of filing STRs or SARs on transactions or activity(ies) that LFIs do not deem truly suspicious in order to reduce the risk of regulatory penalties for non-filing of STRs or SARs.5 Although there may be some aspect of the transaction or activity creating potential suspicion, defensive filings do not report on activity that the LFI truly considers suspicious. As such, defensive filings are generally discouraged given that such filings diminish the value of STRs and SARs, including by leading to an increase in non-valuable filings. An STR, SAR, and other report types should be of the best possible quality, including in that it should have a clearly written narrative with sufficient detail that comprehensively articulates the factors involving the reported suspicious transaction or activity. As a result, the CBUAE considers defensive STR or SARs as indicative of an inefficient transaction monitoring system and an LFI’s weak system of internal controls. An LFI may be asked to correct such deficiencies as part of broader supervisory measures provided by applicable law, including administrative sanctions, temporary limitation to business activities, etc. If, for any reason, an LFI needs additional data to assess whether unusual activity is truly suspicious, the LFI should review other mechanisms—such as expanding the time period for reviewing alerted transactions (e.g., from 30 days to 90 days) or reviewing threshold-based reports—to make the determination that an STR or SAR is required.
4 The UAE FIU has noted instances where SAR or STRs are reported due to the LFI not receiving supporting documents that would justify the transaction or activity. However, upon the FIU raising a request to the same LFI in the form of an AIF, supporting documents were subsequently provided for the same subjects and report. This documentation in some instances removed the suspicion of the transaction and in others, helped explain the transaction or action. Submitting reports to the FIU without first conducting a thorough investigation and looking at all available evidence creates a situation where non-suspicious transactions may be reported to the FIU. LFIs are reminded that internal investigations into the suspicious transaction or activity should be conducted to the fullest extent possible prior to raising an STR or SAR and that related documentation, when available or easily retrievable, should be included with the STR or SAR.
5 Egmont Group, Enterprise-wide STR Sharing: Issues and Approaches, Pg. 173.4. How to Submit an STR and Other Report Types
LFIs are required to submit suspicious transaction and activity reports directly to the FIU using the “goAML” portal, and registration in the system is mandatory for all entities under CBUAE’s supervision. According to the Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations for Financial Institutions, the FIU has launched the goAML system for the purposes of facilitating the filing of STRs, SARs, and other report types by all LFIs. LFIs should register themselves on the goAML system by following the “GoAML Registration Guide” and maintaining their registration in an “active” status. An entity’s Compliance Officer or MLRO can register as the user of the system. GoAML provides a secure link from each LFI to the FIU through their respective supervisory authorities. The system also has an .xml schema for filing batches of STRs. All newly licensed LFIs should register themselves immediately after obtaining their financial services license. Failure to register within the goAML system may result in a breach of the LFI’s AML/CFT obligations and will be dealt with in accordance with the prevailing legal provisions related to non-compliance.
According to the “goAML XML Submission Guide,” the goAML system reflects multiple mandatory fields, business rules, and various binding scenarios. Combined, the system only accepts reports that pass through the minimum requirements set by the FIU. Mandatory fields for submitting a report in the goAML system are noted below:
1. Select the Report Type [4.2.1 GoAML XML Submission Guide]: A Compliance Officer or MLRO should select a report type and populate all available details in the ‘Report Cover’ as depicted below:
- Reporting Entity ID - Entity name as per the registration (auto-generated)
- Internal STR/SAR # - Internal STR/SAR number
- Submission Date* - Date of escalating the Report to the FIU (auto-generated)
- Description/Summary of the Report* - Brief overview for the suspicion/reason for submitting this report to the FIU. This field is only mandatory for STR and SAR report types
- Reporting Entity Branch - Branch where the main subject(s) of the report were identified
- Report Type* - Report type relevant to the suspicion/reason for submission to the FIU
- FIU Reference - Only applicable in the case of AIF/RFI/ AIFT/RFIT type reports. Provide the corresponding case number as specified in the Message Board communication sent by the FIU
- Action Taken by Reporting Entity* - The action(s) taken by the reporting entity post- identifying the reason for suspicion/submission
2. MLRO Details [4.2.2 GoAML XML Registration Guide]: This section of the report includes details on the Compliance Officer, MLRO, or individual filing the report, which is automatically populated using the details provided during the registration phase.6 3. Location of the Incident [4.2.3 GoAML XML Registration Guide]: The location of the incident requires the location where the suspicious incident/transaction originated from. This is mandatory for STR and SAR report types. 4. Reason for Reporting [4.2.4 GoAML XML Registration Guide]: The LFI is expected to select the most appropriate reason for reporting available from the menu selection provided. If necessary, more than one reason may also be provided. It is imperative that the correct Reason for Reporting (“RFR”) is chosen for STRs or SARs submitted in the goAML system.7 5. Transactions [4.2.5 GoAML XML Registration Guide]: If the reported activity involves transaction(s), the LFI should populate the following transaction details:
- Transaction Ref. Number* - Kindly use the auto-generate button to generate a unique identification number if the LFI is not a Bank/Exchange House
- Reporting Entity Internal Reference Number*- Reporting entity's internal transaction reference number
- Type of Transaction* - The mode used to conduct the transaction being reported
- Late Deposit - Does this transaction account as a late deposit? (Yes or No)
- Total Suspected Amount* (AED) - Suspected amount in AED
- Date* - Date when transaction was initiated
- Indemnified for Repatriation* - If the reporting entity has received an indemnity for repatriation
- Transaction Executed by (Staff Name) - Name of the staff member who executed the transaction
- Authorizer - Name of the staff member responsible for authorizing the transaction
- Branch executing the transaction* - Branch where the transaction was executed
- Date of receipt for recall request* (that field will only show if ‘Yes’ was selected for Indemnified for Repatriation) - The date when the reporting entity received the fund recall request
- Purpose of the Transaction* - Purpose for executing the transaction
- Transactions Comments - Comments (if any)
6. Transaction Type, From Type / To Type, My Client / Not My Client, Foreign Currency, Conductor, [4.2.5.1-4.2.5.5 GoAML XML Registration Guide]: Additional transaction details should be added according to the transaction type; transaction type (to/from) (i.e., my client, not my client); and foreign currency type (if applicable); and the amount. These fields should be populated by the LFI according to the GoAML XML Registration Guide’s instructions. Please refer to Party Type: Person (below) to populate information on the conductor of the transaction for 4.2.5.6. 7. Phone, Address, Identification, Email, and Employer Address and Employer Phone [4.2.5.7-4.2.5.11 GoAML XML Registration Guide]: These fields should be populated by the LFI according to the GoAML XML Registration Guide’s instructions. 8. Party Type [4.2.5.12 GoAML XML Registration Guide]: The Party Type’ refers to the initiating source (source of funds) and beneficiary/destination party in relation to the report being filed. The initiating source and beneficiary/destination party can be either a Person, Account, or Entity.
• Party Type: Person [4.2.5.6, 4.2.5.13 GoAML XML Registration Guide]: Where the subject initiating or receiving the transaction is a person, clicking the ‘Person’ radio button will generate the following form and fields.
- Title - e.g., Mr./Mrs./Dr.
- Prefix - Prefix Name e.g., Von, Jr.
- First Name* - First name of the person
- Middle Name - Middle name of the person
- Last Name* - Last name of the person
- Gender - Male / Female
- Birth Date - Date of birth of the subject person
- Birthplace - Location where the person was born
- Mother’s Name - Name of the person’s mother (if available)
- Alias - A known alias for the person (if applicable)
- Emirates ID - Emirates ID number; input the number without using any spaces/hyphens
- Nationality 1 - First nationality of the person
- Nationality 2 - Second nationality of the person
- Nationality 3 - Third nationality of the person
- ID Number - ID number; input the number without using any spaces/hyphens
- Tax Number - Tax number for outside UAE without hyphens/spaces (e.g., FATCA number for US citizens)
- Residence - Country of residence
- Occupation - Known occupation of the subject
- Employer Name - Name of the person’s current employer
- PEP (Y/ N) - Specify if the person is a politically exposed person. Input “Y” or “N” accordingly
- Source of funds - Primary source of funds used for the reported transaction
- Passport* - Select if the passport details are available (Y/N)
- Passport Number* - Input the passport number without any spaces/hyphens only in the absence of an Emirates ID
- Passport Country* - Country of the passport provided
- Deceased - Is the person deceased? (Y/N)
- Date of Death - Date when the person died (applicable only if “Y” was provided in the ‘Deceased’ field)
• Party Type: Account [4.2.5.14 GoAML XML Registration Guide]: If the transaction was initiated or received through an Account, clicking the ‘Account’ radio button will generate the following form and fields: - Account Number* - Account number without any spaces/ hyphens
- Status Code (is mandatory for My Client) - Account status when transaction was initiated
- Institution Name - Name of the institution where the account was created
- UBO* - Who is the beneficial owner of the account?
- Non-Banking Institution - Is the mentioned account held in a bank or otherwise (Y/N)
- Client Number - Client Number as per reporting entity’s records
- Account Type - Drop-down menu for type of account
- Currency Code - Currency of the account
- I BAN - I BAN as per standard format (no spaces/hyphens)
- Opened* - Date of account opening
- Closed - Date of account closure
- Balance* (Y/N) - Input "Y" or "N” on whether there is a credit / debit in the account
- Balance (if the ‘Yes’ radio button is selected (above)) - The current balance of the account in AED
- Date of balance - Date when the balance was recorded
• Please note that LFIs should also add a ‘Signatory(ies)’ form for reports involving accounts that are classified as ‘My Client.’ When the accountholder is a person, the LFI is required to enter all involved signatories. If the accountholder is an entity, the LFI is required to populate the entity details. For instances where an account has multiple signatories, all of the signatory details need to be captured in the goAML system. • Party Type: [4.2.5.15 GoAML XML Registration Guide]: If the transaction was initiated through an Entity, clicking the 'Entity radio button will generate the following form and fields. - Name* - Legal name as per documentation
- Commercial Name - Commercial name as per documentation
- Business Activity - Business activity of entity (drop-down)
- Licensing Authority - Regulatory authority responsible for licensing the entity
- Trade License Number Authority
- Place of incorporation - Specify the city (Emirate in case of a UAE entity)
- Establishment Date - Date when entity was established
- Incorporation Country - Country where the entity was incorporated (drop-down)
- Email - Registered email for the entity (if any)
- Website - Website for the entity (if any)
- Tax Number - Tax number for outside UAE without hyphens/spaces (e.g., FATCA number for US citizens)
- Comments - Comments (if any)
- PEP (Y/ N) - Specify if the person is a politically exposed person. Input "Y" or "N" accordingly
- Latest date of trade license issuance/renewal - Date of trade license issuance/renewal
- Latest date of trade license issuance/renewal - Date of trade license issuance/renewal
- **Phones, Addresses, and Controlling Persons/Beneficial Owners can also be added. Addresses and Controlling Persons/Beneficial Owners section are mandatory only when the entity is classified as ‘My Client.’
9. Involved Parties [4.2.5.16 GoAML XML Registration Guide]: If there are multiple parties involved in the reported activity, the ‘Involved Parties’ form should be populated with the following fields.
- Role* - Nature of association with the transaction
- Funds Code* - The type of funds
- Country* - Country of the involved party
- Significance - Rate the significance of the concerned subject from 0 - 10 (0 being the lowest and 10 being the highest score
- Funds comment - Comments on use of funds (if any)
- Comments - Comments (if any)
- **Foreign Currency can also be added
10. Good and Services [4.2.5.17 GoAML XML Registration Guide]: This section corresponds to transactions involving the exchange of goods and services. - Item Type* - The type of item (e.g., Vehicle)
- Description - Description of the item (e.g., Luxury Car)
- Manufacturer - Item maker (e.g., if the item is a car - BMW)
- Presently Registered To - Name of current owner
- Previously Registered To - Name of previous owner
- Status Code - Stats code (e.g., Bought, Hired)
- Estimated Value - Estimated value of the item
- Currency Code - Used to report service conducted in foreign currency
- Disposed Value - Effective value for property transfer (value must be in AED)
- Size UOM - Unit of measurement (e.g. square meters)
- Size - Size of the property
- Registration Number - Official registration number (e.g., Car VIN Number)
- Registration Date - Official registration date (in MM/DD/ YYYY format)
- Identification Number - Any number that can identify the item (e.g., Car Plate Number)
- Comments - If applicable
- **Addresses can be added
11. Activity [4.2.6 GoAML XML Registration Guide]: If the report does not contain any transaction(s), then the activity details may be captured in the report. The activity details should include the significance of a concerned subject (scale of 0-10), the reason for reporting the party, and any comments. The ‘Activity’ tab will be shown only in the case the reporting entity is submitting an “SAR”, “RFI without transaction(s)” or an “AIF without transaction(s)” based report file.
Upon completion of all the mandatory fields (noted above) and submission of the report in the goAML system, the report will be provided to the FIU. It is mandatory for the LFI’s filer to attach supplemental documents to accompany the submission—including but not limited to—Know Your Customer (“KYC”) documentation, copies of identification documentation, account opening forms, transaction receipts, financial statements, and other documents relevant to the investigation. In the instance that the LFI conducted due diligence or internal investigations, the corresponding documents must also be attached. This will assist the FIU in reviewing the report with all the appropriate documentation to support its review and analysis.
6 The UAE FIU has noted that there have been instances of reports being received whereby upon review, the LFI’s MLRO and related team members’ contact details were not updated in the goAML system, which included email addresses and phone numbers. Keeping contact information updated helps with the two-way communication between LFIs and the FIU while helping to shorten the turnaround time of report analysis. It also enhances the ability of the FIU to analyze and subsequently process reports in a timely manner. The contact information should be kept updated at all times.
7 The UAE FIU has noted that in some cases LFIs file reports while choosing RFRs that, upon closer examination, are not linked to the actual suspicions of the report. As an example, reports have been received with RFRs related to the financing of terrorism and illegal organisations with no evidence of any activity connected to the financing of terrorism and illegal organisations. Selecting incorrect RFRs hinders the FIU’s analysis, and the LFI should expect multiple requests by the FIU for further clarification in these cases. LFIs should be prudent and diligent when choosing RFRs and submitting reports to the UAE FIU. RFRs should be chosen correctly and in relation to the actual suspicions of the STR or SAR being submitted.3.5. Amendments to Submitted Reports
Once a report is submitted and accepted in the system, neither the Compliance Officer, MLRO, nor FIU employees can apply any changes and amendments to the report for missing or incorrect information. However, LFIs may be requested to file a corresponding AIF, AIFT, RFI, or RFIT, and mention in the “Description of the Report” field the reason of filing. LFIs should ensure that the filer uses the correct web reference number of the initial report. In order to avoid such incident(s) and in order to safeguard the system data integrity, LFIs should adopt a maker and checker process/concept to verify the quality and accuracy of uploaded information.
4. Timing of Alert Reviews and STR or SAR Filings
4.1. Alert Review, Case Investigation, and STR or SAR Decision Making
An efficient alert management and dispositioning process is essential to safeguarding the financial integrity of LFIs, assisting law enforcement in the identification and investigation of criminal activity, and satisfying regulatory expectations concerning timely suspicious activity reporting. The alert management and dispositioning process should be adequately staffed and free of bottlenecks and should include a process for the expedited filing of urgent reports in appropriate cases. For purposes of this guidance, “alerts” shall be understood to include automated transaction monitoring alerts, employee referrals, and law enforcement requests. The LFI should apply a risk-based approach to the alert review process by prioritizing alerts based on their risk category. For instance, alerts generated on suspicious transactions of higher-risk customers should be risk-scored higher and prioritized for review.
Alert Review: An LFI’s employees should review an alert and determine whether further investigation is warranted. The underlying basis for the determination should be documented in accordance with an LFI’s investigations procedures. An LFI may choose to have alert review decisions subject to Quality Control (“QC”) review, prior to final dispositioning.
Where the facts available at the alert review stage are or may be sufficient to warrant an STR or SAR filing without further investigation, or where the transaction may otherwise require immediate attention (per criteria set forth below in 4.4 Activity Requiring Immediate Attention), employees should immediately escalate the alerted activity to the designated STR or SAR decision authority for expedited review.
Case Investigation: For any alerted activity determined to require further investigation, employees should conduct and complete (at least preliminarily) an investigation of the alerted activity, document the results of any research or analysis performed, and make a recommendation as to whether an STR or SAR should be filed.
Where a case investigator becomes aware of activity that requires immediate attention (per criteria set forth below in 4.4 Activity Requiring Immediate Attention), employees should immediately escalate the activity to the designated STR or SAR decision authority for expedited review.
If, in the case investigator’s judgment, the facts available at the filing recommendation deadline meet one or more of the UAE regulatory definitions of suspicious activity, the case investigator should submit a recommendation to file an STR or SAR, even if certain aspects of the activity remain unexplained. Unanswered requests for information (RFIs) made in the course of a case investigation should not delay the timely submission of recommendations with respect to an STR or SAR filing. LFIs should define the reasonable RFI timeframe to allow the customer to respond to quires raised during a case investigation as part of the RFI process.
In the event of escalation for expedited review, the Compliance Officer or MLRO should review the activity and make a determination as to whether it is suspicious within 24 hours of the date of escalation. Where appropriate, the Compliance Officer or MLRO also should escalate the activity for potential exit and account closure.
4.2. STR/SAR Decision Making and Filing
In the absence of escalation for expedited review, LFIs are expected to file an STR/SAR within a maximum of 35 business days from the date of automated alert generation. The establishment of adequate grounds of suspicion may involve the investigation procedures as per the LFIs' AML and/or Financial Crime Compliance policies and procedures. LFIs are expected to complete the required investigative procedures as expeditiously as possible. LFIs must maintain adequately detailed records of investigative procedures performed against alerts and when filing an STR/SAR, must include a summary justifying the time taken to establish grounds of suspicion.
In the event of escalation for expedited review, the Compliance Officer or MLRO should file an STR or SAR to the FIU within 24 hours of the determination. All prospective STRs or SARs should be reviewed for accuracy and completeness prior to filing, in accordance with applicable procedures.
LFIs are ultimately responsible under UAE’s AML-CFT Law to report suspicious activity without delay and should seek to file STRs and SARs ahead of the prescribed timeline.
4.3. Monitoring and Reporting of Continuing Suspicious Activity
Upon filing an STR/SAR pertaining to an account holder, LFIs are expected to implement enhanced monitoring on such account holders. In the case of continued suspicious activity detected against said account holder, LFIs are expected to expeditiously file an STR/SAR with the FIU.
4.4. Activity Requiring Immediate Attention
Situations requiring immediate attention include reportable violations that are ongoing (e.g., part of an ongoing money laundering scheme as indicated by an appropriate law enforcement authority) and transactions that the LFI suspects are related to the financing of terrorism and illegal organisations.
4.5. Exceptions for Complex Investigations
There may be instances when the LFI encounters potentially unusual or suspicious activity that is of a “complex” nature. The following is a non-exhaustive list of factors that should be considered to determine whether investigated activity qualifies as a complex investigation: employee-related investigations; significant investigations involving multiple customers, multiple jurisdictions, multiple accounts, multiple transactions, and/or multiple subpoena requests; and legal referred investigations.
If the LFI designates an investigation as “complex”, the LFI should submit an initial STR or SAR to the FIU within 15 business days of the alert generation. The initial STR/SAR should be labelled as a “Complex investigation” to the FIU. Following the initial STR or SAR filing, the LFI has an additional 30 business days to obtain all necessary information related to the complex investigation and submit a follow-up STR or SAR to the FIU.
4.6. Summary of Review, Investigation, and Reporting Timelines
The following table summarizes the recommended suspicious activity review, investigation, and reporting timelines in the absence of escalation for expedited review. Please note – the following table captures the maximum timeline by which LFIs should identify and report suspicious activity and transactions. LFIs are ultimately responsible under UAE’s AML-CFT Law to report suspicious activity without delay and should seek to file STRs and SARs ahead of the below timelines.
Action Maximum Timeline in Calendar Days Dispositioning of alert; recommendation on whether to file an STR or SAR; and decision on whether to file an STR or SAR LFIs are expected to file an STR/SAR within a maximum of 35 business days from the date of automated alert generation. Filing of a follow-up STR or SAR for a “complex investigation” If an LFI designates an investigation as “complex”, the LFI should submit an initial STR within 15 business days of alert generation – SAR/STR to be labelled “Complex investigation”. Follow-up SAR/STR to be submitted within 30 business days of filing the initial STR. Filing of STR or SAR on continuing activity Upon filing an STR/SAR pertaining to an account holder, LFIs are expected to implement enhanced monitoring on such account holders. In the case of continued suspicious activity detected against said account holder, LFIs are expected to expeditiously file an STR/SAR continuing activity with the FIU. 4.7. Escalation for Expedited Review
In certain cases, an alert or case may need to be dispositioned and an STR or SAR filed more rapidly than usual processes allow. In such cases, the alert will be dispositioned and the STR or SAR filed according to the expedited review timeline as laid out below.
Circumstances where expedited review is expected include:
• The activity requires immediate attention (as defined above); and • The facts available at the alert review stage are or may be sufficient to warrant an STR or SAR filing without further investigation.
The following table summarizes the recommended suspicious activity review, investigation, and reporting timelines in the event of escalation for expedited review.
Action Maximum Timeline in Calendar Days Decision on whether to file an STR or SAR and filing of first STR or SAR 24 hours from decision to file Filing of STR or SAR on continuing activity Upon filing an STR/SAR pertaining to an account holder, LFIs are expected to implement enhanced monitoring on such account holders. In the case of continued suspicious activity detected against said account holder, LFIs are expected to expeditiously file an STR/SAR with the FIU. 5. Confidentiality and Prohibition against “Tipping Off”
According to Article 18 of the AML-CFT Decision, when reporting suspicious activity or transactions to the FIU, LFIs are obliged to maintain confidentiality with regard to both the information being reported and to the act of reporting itself, and to make reasonable efforts to ensure that the information and data reported are protected from access by any unauthorized person.
As part of their risk-based AML/CFT framework, and in keeping with the nature and size of their businesses, LFIs and their foreign branches or group affiliates where applicable, should establish adequate policies, procedures and controls to ensure the confidentiality and protection of information and data related to STRs, SARs, and other report types. These policies, procedures and controls should be documented, approved by senior management, and communicated to the appropriate levels of the organization.
LFIs must ensure that all relevant information relating to STRs, SARs, and other report types is kept confidential, with due regard to the conditions and exceptions provided for in the law, and the guiding principles for this must be established in policies and procedures. LFIs should ensure that policy and procedures are reflected in for example, appropriate access rights with regard to core systems used for case management and notifications, secure information flows and guidance/training to all employees involved. This guidance and training are particularly important for the first line of defense employees who have contact with customers. It is essential that these employees know when there may be cases of suspicious transactions, what questions they have to ask the customer and which information they must not under any circumstances disclose to the customer.
It should be noted that the confidentiality requirement does not pertain to communication within the LFIs or its affiliated group members (foreign branches, subsidiaries, or parent company) for the purpose of sharing information relevant to the identification, prevention or reporting of suspicious transactions and/or crimes related to money laundering and the financing of terrorism and illegal organisations, according to the Article 39.1 of the AML-CFT Decision.
It is a federal crime for LFIs or their managers, employees, or representatives, to inform a customer or any other person, whether directly or indirectly, that a report has been filed or will be filed, or of any information or data contained in the report, or that an investigation is under way concerning the transaction, otherwise known as “tipping off.” Any person violating this prohibition is liable to a penalty of no less than AED100,000 and no more than AED500,000 and imprisonment for a term of not less one year, according to the Article 25 of the AML-CFT Law.
6. Handling of Transactions and Business Relationships after Filing STRs or SARs
6.1. Requirements for Corresponding with the FIU
As a standard practice and as specified in Article 9.1 of the AML-CFT Law, the FIU can reach out to LFIs to provide additional requested information pertaining to an STR or SAR. Therefore, when responding to the FIU’s inquiries, details should be provided in a way that is precise and outlined as per the request. LFIs should maintain clarity on the presented information and provide it in the required format (e.g., tabular format, pdf, etc.). Moreover, LFIs should avoid adding unnecessary codes and abbreviations or any raw information extracted directly from the core databases, which are unknown to the FIU. It is important to understand that the details pertaining to the source and destination of funds are essential for investigating the reported activity. Therefore, names; account numbers; country of origin and destination; currencies; dates; source and purpose of transactions; and other related information should be detailed in LFI’s response. Once the report is filed, LFI should send the report web reference number and inform the FIU via the goAML Message Board.
6.2. Post STR and SAR Process
Following an STR or SAR filing, the FIU may or may not revert to the LFI with specific instructions, requests for additional information, feedback or further guidance related to the STR or SAR, or to the business relationship in general. In such cases, these communications will generally be directed to the Compliance Officer or MLRO of the LFI. However, LFIs may not receive instructions, additional information requests, or other feedback from the FIU regarding STRs or SARs that have been filed; or the receipt of such communications may be delayed beyond what they consider to be a reasonable time period. In such instances, LFIs must follow their internal policies in relation to such customers and should determine the appropriate handling of the STR or SAR and of the business relationship in general, taking into consideration all of the risk factors involved.
Specifically, once a suspicious transaction or other suspicious information related to a customer or business relationship has been reported to the FIU, the LFI should take the following immediate responses:
• LFIs should follow the instructions, if any, of the FIU in relation to both the specific transaction and to the business relationship in general. • LFIs should identify all related/associated accounts or relationship of STR or SAR customers and conduct a review on those accounts/relationship to check whether any suspicious transaction(s) has taken place. If yes, appropriate risk-based Enhanced Due Diligence (“EDD”) and ongoing monitoring procedures should be implemented. • The customer or business relationship, including the related/associated accounts and relationship to the STR or SAR customers, should immediately be classified as a high-risk customer and appropriate risk-based EDD and ongoing monitoring procedures should be implemented in order to mitigate the associated money laundering and the financing of terrorism and illegal organisations risks.
Unless specifically instructed by the FIU to do so, LFIs are under no obligation to carry out transactions they suspect, or have reasonable grounds to suspect, of being related to a crime. Furthermore, unless specifically instructed by the FIU to maintain the business relationship (for example, so that the competent authorities may monitor the customer’s activity), it should be the LFI’s responsibility to take appropriate steps in order to decide whether or not to maintain the business relationship based on their risk appetite. However, LFIs should consider the risk of tipping off a customer when taking these restrictive measures on the account. These steps may include, but are not limited to:
• Reassessing the business relationship risk and re-evaluating the customer’s risk profile, where necessary. • Initiating an enhanced customer due diligence review. • Considering the performance of an enhanced background investigation (including, if appropriate, the use of a third-party investigation service). • Any other reasonable steps, commensurate with the nature and size of their businesses, and bearing in mind the obligation to avoid “tipping off” the customer.
LFIs that determine to maintain the business relationship should, commensurate with the nature and size of their businesses:
• Document the process by which the decision was made to maintain the business relationship, along with the rationale for, and any conditions related to, the decision; and • Implement adequate EDD measures to manage and mitigate the money laundering/the financing of terrorism and illegal organisations risks associated with the business relationship.
In such cases, beyond EDD measures, LFIs should also implement additional control measures such as, but not limited to:
• Requiring additional data, information or documents from the customer in order to carry out transactions (for example, evidence of relevant licenses or authorizations, customs documents, additional identification documents, bank or other references). • Restricting the customer’s use of certain products or services. Placing restrictions and/or additional approval requirements on the processing of the customer’s transactions (for example, transaction size and/or volume limits, or limits to the number of transactions of certain types that can be executed during a given time period).
LFIs should also document the specific EDD, ongoing monitoring, and additional control measures to be taken. In this regard, LFIs should obtain senior management approval for the plan, including its specific conditions, duration and any requirements for its removal, as well as the roles and responsibilities for its implementation, monitoring and reporting, commensurate with the nature and degree of the money laundering and the financing of terrorism and illegal organisations risks associated with the business relationship.
Thus, retaining a customer relationship, exiting the relationship, restricting an account, or any other actions taken by an LFI following the filing of an STR, SAR, or other report is a decision based on the LFI’s internal policies and procedures, including its risk appetite, to safeguard the LFI from relevant risks. This is unless the entity receives instructions from the FIU or any other competent authority that should be immediately implemented without delay. In cases where the LFI decides to reject a new customer or to exit an existing relationship due to an STR or SAR filing (or other report), the LFI should ensure that the subject of the filing is added to internal watch lists, (e.g., a list of individuals and entities that have been exited for financial crime-related reasons and that should be screened by the LFI to avoid future on-boarding).
While individual STRs, SARs, or other reports that pose particular risk may require escalation and review for potential exit, repeated filings on a single account or group of related accounts should trigger consideration of customer exit. Repeat filings should also prompt a review of risks associated with accounts of a similar type and of whether internal controls are effectively mitigating risk. An LFI should determine a threshold for which an account that has been subject to a certain amount of STR or SAR filings (or other report) will be escalated to senior management for consideration of account closure, possible restrictions on the account, and/or enhanced monitoring.
LFIs should also maintain a customer exit policy that outlines the process for reviewing the overall customer relationship and deciding on next steps, including ending the relationship and notifying law enforcement and/or other group affiliates, as appropriate. Customer exit policies should include criteria for when these actions are appropriate and outline how the LFI should monitor the activity of a customer it decides to retain. The LFI should contact law enforcement before closing an account if the entity has knowledge of an ongoing law enforcement investigation involving that account or customer, or the LFI has filed an STR(s), SAR(s), or other report types on the customer or account due to continuing suspicious activity. LFIs should be aware that law enforcement may have an interest in ensuring that certain accounts remain open notwithstanding suspicious or potential criminal activity in connection with those accounts. If a law enforcement agency requests that an LFI keep a particular account open, the LFI should ask for a written request. The written request should indicate that the agency has requested that the LFI maintain the account along with the purpose and duration of the request. Ultimately, the decision to maintain or close an account should be made by an LFI in accordance with its own standards and guidelines.
6.3. Governance and Reporting to Senior Management
LFIs should have mechanisms to inform the Board of Directors (or a committee of the Board) and senior management of compliance initiatives, compliance deficiencies, STRs, SARs, or other regulatory reports filed, and corrective actions taken. LFIs should also develop and maintain a system of reporting that provides accurate and timely information on the status of the AML/CFT program, including statistics on key elements of the program, such as the number of transactions monitored, alerts generated, cases created, and STRs, SARs, or other report types filed.
Employees should report the number and types of STRs, SARs, or other regulatory reports filed to the Board of Directors or a Board-designated committee. While employees are not required to provide actual copies of STRs, SARs, or other regulatory reports to the Board (or a committee of the Board), such notifications should contain sufficient information to enable the Board or its committee to provide appropriate oversight over the LFI’s AML/CFT program. Where an individual filing documents activity that poses a particular risk, management may provide a copy of the report to the Board or Board-designated committee. Where appropriate, the suspicious activity or transaction underlying the filing of an STR, SAR, or other regulatory reports should be communicated to those individuals responsible for managing the risk associated with the customer and/or activity that is the subject of the STR, SAR, or other regulatory reports in order to permit such employees to respond appropriately to the AML/CFT risks identified. Although all such communications are subject to the confidentiality restrictions, it should be noted that the confidentiality requirement does not pertain to communication within the LFIs or its affiliated group members (foreign branches, subsidiaries, or parent company) for the purpose of sharing information relevant to the identification, prevention, or reporting of suspicious transactions and/or crimes related to money laundering and the financing of terrorism and illegal organisations, according to Article 39.1 of the AML-CFT Decision (also referenced in Section 5. Confidentiality and Prohibition against “Tipping Off”).
6.4. Record Retention
According to Article 24 of the AML-CFT Decision, LFIs are required to retain all records and documents pertaining to STRs and the results of all analysis or investigations performed for at least five (5) years from the date of completion of the transaction or termination of the business relationship. Such records relate to both internal STRs and those filed with the FIU, and should include but are not limited to:
• Suspicious transaction indicator alert records, logs, investigations, recommendations and decision records, and all related correspondence; • Competent authority request for information, correspondent bank requests for assistance, and their related investigation files and correspondence; • CDD and Business Relationship monitoring records, documents, and information obtained in the course of analyzing or investigating potentially suspicious transactions, requests for assistance by LFIs, and all internal or external correspondence or communication records associated with them; • STRs, SARs, and other report types (internal and external), logs, and statistics, together with their related analysis, recommendations and decision records, and all related correspondence; and • Notes concerning feedback provided by the FIU with respect to reported STRs, SARs, and other report types, as well as notes or records pertaining to any other actions taken by, or requested by, the FIU.
Annex 1. Indicative Examples of Insufficient STR and SAR Narratives
Example 1:
• Reason for reporting: Statements show large payments to luxury car companies. High amounts of funds transfers continue over several months.
Comments: The narrative lacks identifying information on the STR subject (name, occupation, address, account number, etc.), and no explanation is given as to why the LFI considers this activity suspicious. The narrative lacks specific transaction data that identifies the dates and amounts of the large payments and specific details on the destination of the funds (the name, location, bank, and account number of the beneficiary car companies, if identifiable).
Example 2:
• Money orders were purchased on 03-28-21 to ABC Corporation in the amount of AED30,000.
Comments: No explanation is given as to why the MVTS considers this activity suspicious. The LFI does not indicate if money orders were purchased with cash. The LFI does not provide any information about the purchaser or nature of the business (ABC Corporation) and if this activity was normal or unusual for the purchaser or the business.
Example 3:
• Mr. X was the originator of 12 wires totaling AED400,000. All of the wires were remitted to a Hong Kong based company. During the same period of time, Mr. X deposited cash into his account.
Comments: The narrative lacks specific details on the destination of the funds (the name of the Hong Kong based company, bank, and account number of the beneficiary, if identifiable). The depository LFI fails to include any information concerning the relationship, if any, between the LFI and the customer. Also, no specific transaction data is provided that identifies the dates and amounts of each wire transfer and the cash deposit.
Example 4:
• The reason for the suspicion is due to multiple third-party transfers being paid into Mr. Y account that were soon followed by multiple cash withdrawals. Funds sent from the account to multiple third parties.
Comments: The narrative lacks specific details on the source of the funds (the individual/entity sending the multiple third-party transfers). The STR does not provide a timeframe of when the transfers were made, the number and value of the third-party transfers, the number and value of the cash withdrawals, and the timeframe (how soon) the cash withdrawals were made following the third-party transfers. The depository LFI fails to include any information concerning the relationship, if any, between the individual/entity sending the multiple third-party transfers and the customer.
Example 5:
• Information has come to our attention that the Mrs. Y has been convicted of a drug trafficking offense.
Comments: The narrative fails to describe the depository LFI’s relationship with the subject and include additional identifying details about the subject (name, occupation, address, account number, etc.). The narrative does not describe any suspicious activity aside from the conviction and fails to state if the suspicion is related to money laundering or if there are possible links to the financing of terrorism and illegal organisations.
Example 6:
• Mrs. Y came into the bank and asked questions during the account opening process that were suspicious.
Comments: The narrative does not describe the suspicious activity in detail as a basis for filing the SAR (e.g., the customer refusing to answer account opening questions; providing falsified or counterfeit documentation; exhibiting reluctance to provide detailed information about the customer’s business). The narrative template also fails to describe information that the LFI was able to gather on the prospective customer during account opening (occupation, address, etc.).
Example 7:
• Mr. LMN was the subject of adverse media involving his association with a terrorist group.
Comments: The narrative fails to describe the depository LFI’s relationship with the subject and include additional identifying details about the subject (name, occupation, address, account number, etc.). The narrative template also does not identify the terrorist group, describe the customer’s relationship with the terrorist group, the timeframe for the customer’s involvement with the terrorist group, and how the LFI became aware of this association, such as a hyperlink to the adverse media report.
Example 8:
• Mrs. ABC purchased an insurance product using unusual payment methods. Mrs. ABC is a teacher at Happy Day Elementary School in Dubai and resides at 11111 Street Name, Dubai, UAE. Mrs. ABC also has two motor vehicles insured with the LFI since April 2019.
Comments: The narrative fails to describe the type of insurance product purchased, on what date, with what payment method, and why the institution considers this payment method unusual. The institution also does not indicate the customer’s stated purpose for purchasing the insurance product and if this is line with what the LFI knows about the customer.
Example 9:
• Mr. XYZ requests to increase payments on his life insurance policy during the period from 02-01- 21 to 05-01-21, and the payments appear to be excessive, given Mr. XYZ’s prior history.
Comments: The narrative fails to include additional identifying details about the subject (name, occupation, address, etc.). The narrative lacks specific transaction data that identifies the dates, amounts, and method of payment on the life insurance policy. The narrative also does not describe why the institution considers these payments to be excessive based on the customer’s prior history of payments. The narrative does not indicate how long the subject has been in possession of the life insurance policy.
Annex 2. Red Flag Indicators in the Context of the UAE
The FIU published the following typologies and indicators in their Biannual Financial Crime Trends and Typologies Report (January - June 2020). These typologies and indicators, as well as any future ones the FIU may determine, should be incorporated into an LFI’s AML/CFT program with a view to update policies, procedures, detection scenarios, and red flag indicators for identifying potentially suspicious activity.
B.1 General indicators
According to the FIU, the following indicators are present in many of the typologies used in money laundering and the financing of terrorism and illegal organisations.
• Transactions involving locations with poor AML/CFT regimes or high exposure to corruption. • Significant and/or frequent transactions in contrast to known or expected business activity. • Significant and/or frequent transactions in contrast to known employment status. • Ambiguous or inconsistent explanations as to the source and/or purpose of funds. • Where relevant, nervous or uncooperative behavior exhibited by the LFI’s employees and/or customers.
B.2 Wire transfers to and from bank accounts
• How it works: Transferring proceeds of crime from one person to another via money remittance services. • Possible indicators o Significant and/or frequent cash payments for transfers. o Transfers to or from locations that have poor AML/CFT regimes or high exposure to corruption. o Transfers to high-risk countries or known tax havens. o Transfers to numerous offshore jurisdictions with no business rationale. o Same home address provided by multiple remitters. o Reluctant to provide the LFI with identification details.
B.3 Purchase of valuable commodities
• How it works: Laundering proceeds of crime by purchasing valuable commodities, for example, precious metals or gems. • Possible indicators o Significant and/or frequent cash purchases of valuable commodities. o Regularly buying and selling of valuable commodities that is not supported with a business purpose and/or does not make economic sense.
B.4 Purchase of valuable assets
• How it works: Laundering proceeds of crime by purchasing valuable assets, for example, property or vehicles. • Possible indicators o Purchase/sale of real estate above/below market value irrespective of economic disadvantage. o Cash purchases of valuable assets with cash and/or cash deposits for valuable assets. o Low value property purchased with improvements paid for in cash before reselling. o Rapid repayment of loans/mortgages with cash or funds from an unlikely source.
B.5 Offshore companies
• How it works: The process of registering companies in the UAE, especially in the free zones, with foreign directors and/or shareholders in order to open bank accounts to facilitate money laundering and/or the financing of terrorism and illegal organisations by unverified beneficiaries. • Possible indicators o Large numbers of companies registered with the same office address. o Address on file is for a ‘Virtual office’. o Accounts/facilities are opened/operated by company formation agents. o Lack of information regarding overseas directors/beneficiaries. o Complex ownership structures. o Companies where there is no apparent business purpose. • Additional indicators: o The same natural person is the director for a large number of single director companies. o The same person (natural or corporate) is the shareholder of a large number of single-shareholder companies. o Use of a small number of local 'agents' who undertake transactions with the companies’ register.
B.6 Nominees, trustees, family members or third parties
• How it works: Utilizing other people to carry out transactions in order to conceal the true identity of the individual ultimately controlling the proceeds of crime. • Possible indicators o Customers using family members or third parties, including the use of children’s accounts. o Transactions where third parties seem to be retaining a portion of funds, which would indicate the use of mules. o Accounts operated by someone other than the account holder. o Many transactions conducted at various LFIs and/or branches, in one day. o Significant and/or frequent transactions made over a short period of time.
B.7 Trade-based money laundering
• How it works: Manipulating invoices, often in connection with international trade, by overstating the value of a shipment providing criminal entities with a paper justification to either launder proceeds of crime and/or send funds overseas to finance terrorism. • Possible indicators o Invoice value greater than value of goods. o Discrepancies in domestic and foreign import/export data. o Suspicious cargo movements. o Suspicious domestic import data. o Discrepancies in information regarding the origin, description, and value of the goods. o Discrepancies with tax declarations on export declarations. o Sudden increase in online auction sales by particular vendors (online auction sites). o Frequent purchases between same buyers and vendors (online auction sites).
B.8 Cancellation of credits or overpayments
• How it works: Laundering proceeds of crime by overpaying then requesting refund cheques for the balance. • Possible indicators o Frequent cheque deposits issued by car dealers, dealers in jewelry, etc. o Significant and/or frequent payments to utility companies, for example, prepaid cards for fuel, telecom e-wallets etc. o Frequent cheque deposits issued by utility companies (i.e., electricity providers). o Significant and/or frequent payments for purchases from online auction sites. o Frequent personal cheque deposits issued by third parties.
B.9 Electronic transfers to and from bank accounts
• How it works: Transferring proceeds of crime from one bank account to another via LFIs. • Possible indicators o Transfers to or from locations that have poor AML/CFT regimes or high exposure to corruption. o Transfers involving accounts located in high-risk countries or known tax havens. o Transfers to offshore jurisdictions with no business rationale. o Multiple transfers sent to the same person overseas by different people. o Departure from the UAE shortly after transferring funds. o Transfers of funds between various accounts that show no economic purpose (i.e., multiple transfers incurring bank fees where one single transfer would have been sufficient).
B.10 Co-Mingling
• How it works: Combining proceeds of crime with legitimate business takings. • Possible indicators o Significant and/or frequent cash deposits when business has electronic funds transfer at point-of-sale facilities. o Large number of accounts held by a customer with the same LFI. o Accounts operated by someone other than the account holder. o Merging businesses to create layers. o Complex ownership structures. o Regular use of third-party accounts.
B.11 Gatekeepers/professional services
• How it works: Utilizing ‘Professionals’ to establish seemingly legitimate business activities, for example, Lawyers, Accountants, Brokers, Company Formation Agents. • Possible indicators o Accounts and/or facilities opened and/or operated by company formation agents. o Gatekeepers that appear to have full control. o Known or suspected corrupt professionals offering services to criminal entities. o Accounts operated by someone other than the account holder.
B.12 Cash deposits
• How it works: Placement of cash into the financial system. • Possible indicators o Large cash deposits followed immediately by withdrawals or electronic transfers.
B.13 Structuring
• How it works: Separating large transactions into small transactions to avoid scrutiny and detection from LFIs. • Possible indicators o Many transactions conducted at various LFIs and/or branches, in one day. o Small/frequent cash deposits, withdrawals, electronic transfers made over a short time period. o Multiple low value domestic or international transfer.
B.14 Smurfing
• How it works: Utilizing third parties or groups of people to carry out structuring. • Possible indicators o Third parties conducting numerous transactions on behalf of other individuals. o Many transactions conducted at various LFIs and/or branches, in one day. o Accounts operated by someone other than the account holder.
B.15 Credit Cards/Cheques/Promissory Notes
• How it works: Instruments used to access funds held in an LFI, often in another jurisdiction. • Possible indicators o Frequent cheque deposits in contrast to known or expected business activity. o Multiple cash advances on credit card facilities. o Credit cards with large credit balances.
B.16 Transactions inconsistent with intended purpose of the account
• How it works: Transactions that are out of the ordinary for the individual or conducted without a clear rationale. • Possible indicators o Transactions to or from unrelated parties. o Transaction amounts that are inconsistent with the account’s expected volumes or frequencies. o Transactions that are out of the ordinary for the customer’s profession or business activity.
B.17 Cash couriers
• How it works: Concealing the movement of currency from one jurisdiction to another using people, luggage, mail, or any other mode of shipment, without declaration. • Possible indicators o Transactions involving locations with poor AML/CFT regimes or high exposure to corruption. o Customers originating from locations with poor AML/CFT regimes/high exposure to corruption. o Significant and/or frequent cash deposits made over a short period of time. o Significant and/or frequent currency exchanges made over a short period of time.
B.18 Other payment technologies
• How it works: Utilizing emerging or new payment technologies such as virtual currencies/crypto- currencies, peer-to-peer (P2P) lending etc. to facilitate money laundering and/or the financing of terrorism and illegal organisations. • Possible indicators o Excessive use of stored value cards. o Significant and/or frequent transactions using mobile telephone services. o Unjustified transactions to and from Cryptocurrency platforms and digital assets exchanges.
B.19 Underground banking/alternative remittance services
• How it works: Transferring proceeds of crime from one person to another via informal banking mechanisms such as unregistered Hawaladars. • Possible indicators o Mostly prevalent under the auspices of a general trading company license. o Significant and/or frequent cash payments for transfers in which the cash deposits could be from many different individuals using the cash deposit machines. o Cash volumes and transfers in excess of average income of migrant account holders. o Transfers to or from locations that have poor AML/CFT regimes or high exposure to corruption. o Large transfers from accounts to potential cash pooling accounts. o Significant and/or frequent transfers recorded informally using unconventional bookkeeping. o Significant and/or frequent transfers requested by unknown or intermittent customers. o Numerous deposits to one account followed by numerous payments made to various people. o Vague invoices and documentation which may deliberately be made to appear complex.
B.20 Cash exchanges
• How it works: Exchanging low denomination notes for high denomination notes (also known as refining) as a means to launder proceeds of crime, as well as reduce large volumes of cash obtained from serious crime. • Possible indicators o Significant and/or frequent cash exchanges from small to large denominations.
B.21 Currency conversion
• How it works: Converting one currency into another as a means to launder proceeds of crime, as well as reduce large volumes of cash obtained from serious crime. • Possible indicators o Significant and/or frequent local or foreign currency exchanges. o Opening of foreign currency accounts with no apparent business or economic purpose.
Annex 3. Red Flag Indicators for the UAE Insurance Sector
The UAE Insurance Authority has issued the following list of red flag indicators when handling life and general insurance products. The indicators, as well as any future ones the UAE Insurance Authority may determine, should be incorporated into an LFI’s AML/CFT program with a view to update policies, procedures, detection scenarios, and red flag indicators for identifying potentially suspicious activity related to life and general insurance products.
1. The purchase of an insurance product does not reflect a customer’s known needs (e.g., purpose of the account). 2. The early surrender of an insurance product is taken at a cost to the customer. 3. The surrender of an insurance product is initiated with the refund directed to a third party. 4. The customer exhibits no concern for the investment performance of a purchased insurance product and instead exhibits significant concern for its early surrender terms. 5. The customer purchases insurance products using unusual payment methods, such as cash or cash equivalents, or with monetary instruments in structured amounts. 6. The customer demonstrates reluctance to provide identifying information when purchasing an insurance product. 7. The customer borrows the maximum amount available from their insurance product shortly after purchase. 8. The customer used to purchase low-premium insurance and pay premiums by making regular payments but suddenly purchases insurance that requires a large lump-sum premium payment, for which no reasonable explanations are provided. 9. The customer purchases an insurance product without concern for the coverage or benefits, or the customer only cares about the procedures for the policy loan, cancellation of insurance policy, or changing beneficiary when purchasing an insurance policy that has a high cash value or requires a high lump-sum premium payment. 10. The customer usually pays a premium by making regular payments but suddenly requests to purchase a large-sum policy by paying off premium all at once. 11. The customer purchases insurance products with high cash value successively over a short period of time, and the insurance products purchased do not appear to be commensurate with the customer’s status and income or are unrelated to the nature of the customer’s business. 12. The customer pays premiums in cash and in several payments marginally below the threshold for declaration but cannot reasonably explain the source of funds. In addition, the transactions do not appear to be commensurate with the customer’s status and income or are unrelated to the nature of the customer’s business. 13. The customer, after making a large premium payment for a policy purchased, applies for a large policy loan or cancels the policy in a short period of time, for which no reasonable explanations are provided. 14. The customer is a policyholder of several motor vehicles which is inconsistent with their profile. 15. The theft of a motor vehicle is not reported by the customer/policyholder. 16. The customer attempts to insure a motor vehicle that was reported as stolen or as a total loss.
Annex 4. Overarching Rules and Principles for the goAML System
The FIU published the goAML XML Submission Guide (please see Section 3.4) with additional detail on the rules that an LFI should consider when submitting an STR, SAR, or other report type in the goAML system:
• All LFIs transactions should be reported as bi-party transactions on the goAML system. • Reporting entities should submit only suspicious transactions in a report. Any additional transactions can be submitted via an AIFT (upon request only). • For AIFT submissions where the number of transactions exceed 10,000, reporting entities are advised to split them into more than one AIFT; however, the AIFT should use the same “Internal Reference Number”. • A deposit is composed of a bi-party transaction occurring from a person who may be a conductor to an account. • A withdrawal is composed of a bi-party transaction occurring from an account to a person. • A remittance is composed of a bi-party transaction occurring from one person/account/entity to another. • A wire transfer is composed of a bi-party transaction occurring from an account to another account. • In case a LFI is acting as a correspondent bank within a reported transaction, then the transaction is occurring from one account to another, in which both accounts should be classified as ‘Not My Client’ by the LFI/Compliance Officer/MLRO. • In the case of Exchange Houses, where a currency exchange transaction is being reported, it should be reported as a bi-party transaction, where the “from” and “to” parties are the same Person. • The conductor field is mandatory when the transaction is conducted from an entity. • If the date of birth for a subject (person) is unknown, then the user may enter the 1st of January 1900 in the ‘Birth Date’ field. • In case the expiration date of a registered ID is unknown, then the user may enter the 31st of December 2100 in the ‘Expiry Date’ field. • When reporting a transaction that involves an account, it is imperative that the LFI also provide details for the person or entity associated with the said account.
Annex 5. Synopsis of the Guidance
Introduction Purpose The purpose of the Guidance is to assist the understanding and effective performance by the United Arab Emirates Central Bank's (CBUAE) licensed financial institutions (LFIs) of their statutory obligations under the legal and regulatory framework in force in the UAE. Applicability This guidance applies to all natural and legal persons, which are licensed and/or supervised by CBUAE, in the following categories: •National banks, branches of foreign banks, exchange houses, finance companies, payment service providers, registered hawala providers and other LFIs; and •Insurance companies, agencies, and brokers. Legal Basis The legal basis of STR reporting is based on the (i) Federal Decree-Law No. (20) of 2018 on Anti-Money Laundering (AML) and Combatting the Financing of Terrorism (CFT) and Financing Illegal Organisations and Federal Decree law No. (26) of 2021 To amend certain provisions of Federal Decree-law No. (20) of 2018, on anti-money laundering and combating the financing of terrorism and financing of illegal organisations; (ii) Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation for Decree-Law No. (20) of 2018 on AML and CFT and Financing of Illegal Organisations; and (iii) Cabinet Decision No. (74) of 2020 Regarding Terrorism Lists Regulation and Implementation of UN Security Council Resolutions on the Suppression and Combating of Terrorism, Terrorist Financing, Countering the Proliferation of Weapons of Mass Destruction and its Financing and Relevant Resolution. The legal basis addresses (i) the consequences for failure to disclose suspicious activity, (ii) protection for individuals disclosing suspicious activity, and (iii) the meaning of suspicious transactions. Identification of Suspicious Transactions Role of the First Line of Defense The first line of defense plays a critical role in the management of customer and third-party risk and the timely escalation of potentially suspicious activity. The first line of defense is well-placed to identify suspicious transactions and assess that information once deemed reasonable—collected through interactions with a customer—now appears suspicious. Employees within the first line of defense include relationship managers, business executives, and back-office operations functions. Role of the Second Line of Defense The second line of defense (e.g., compliance employees) provides policy, advice, guidance, assurance, oversight, and challenge to the first line of defense. While employees in Financial Crime Operations Units (possibly in the first line of defense) can investigate suspicious transactions and document the resultant investigation, the ultimate filing of the STR or SAR should be made by the Compliance Officer or the money laundering reporting officer (MLRO) (in the second line of defense). The second line of defense is charged with overseeing the investigations programme. Role of the Third Line of Defense The third line of defense identifies gaps, deficiencies, and weaknesses in operational controls owned or overseen by an LFI’s business, operations, and compliance functions. Purpose of Transaction Monitoring The purpose of transaction monitoring is the ongoing, retrospective monitoring of customers’ and prospective customers’ transactions or activity to identify activity anomalous from normal behavior. This may, on further investigation, generate knowledge or reasonable suspicion of financial crime and thereby require reporting to the appropriate law enforcement and/or regulatory authority as an STR, SAR, or equivalent local report in line with AML/CFT regulatory and/or UAE FIU reporting requirements. Internal Organization An LFI’s internal organization is important to appropriately identify unusual or potentially suspicious activity. Internal organization comprises an LFI’s governance and management oversight; policies and procedures; clear lines of responsibility and reporting; and ongoing training to account for changes in the UAE’s legislative and regulatory frameworks. There are also specific considerations for institutions with foreign branches and subsidiaries. Transaction Monitoring Methods A transaction monitoring program should take into account the AML/CFT risks of the LFI’s customers, prospective customers, counterparties, businesses, products, services, delivery channels, and geographic markets in addition to helping prioritize high-risk alerts. Monitoring systems typically include employee identification or referrals, transaction-based (manual) systems, surveillance (automated) systems, or a combination of these, including an intelligence-led transaction monitoring approach. Procedures for the Reporting of Suspicious Transactions Importance of Filing an STR or SAR Information generated from an STR, SAR, and other report type is important for law enforcement and the FIU to effectively identify and combat financial crime. Specifically, the quality of STRs, SARs, and other report types is imperative for increasing the FIU’s analytical function to identify vulnerabilities and threats to the UAE financial system and develop an overall understanding of money laundering and the financing of terrorism and illegal organisations risks Basic Structure of an STR or SAR Different report types can be filed in the FIU’s “goAML” portal (i.e., STR, SAR, AIF, AIFT, RFI, RFIT, HRC, HRCA). In addition, an LFI should divide a narrative into three sections (introduction, body, and conclusion). Best Practices for Drafting an STR or SAR A narrative should identify and answer the five questions – who? what? when? where? and why? – of the suspicious activity being reported to the FIU in addition to the operation/modus operandi (or how?). The Guidance also addresses how defensive STR or SAR filings are generally discouraged. How to Submit an STR or SAR LFIs are required to submit suspicious transaction and activity reports directly to the FIU using the “goAML” portal. There are certain mandatory fields that an LFI should populate when submitting a report in the goAML portal in addition to providing certain supplemental documents. Amendments to Submitted Reports Once a report is submitted and accepted in the goAML system, changes cannot be applied, including amendments for missing or incorrect information. However, LFIs may file a corresponding AIF, AIFT, RFI, or RFIT. Timing of Alert Reviews and STR Filings Alert Review, Case Investigation, and STR/SAR Decision Making and Filing In the absence of escalation for expedited review, LFIs are expected to file an STR/SAR within a maximum of 35 business days from the date of automated alert generation. The establishment of adequate grounds of suspicion may involve the investigation procedures as per the LFIs' AML and/or Financial Crime Compliance policies and procedures. LFIs are expected to complete the required investigative procedures as expeditiously as possible. LFIs must maintain adequately detailed records of investigative procedures performed against alerts and when filing an STR/SAR, must include a summary justifying the time taken to establish grounds of suspicion. In the event of escalation for expedited review, the Compliance Officer or MLRO should file an STR or SAR to the FIU within 24 hours of the determination. All prospective STRs or SARs should be reviewed for accuracy and completeness prior to filing, in accordance with applicable procedures. Monitoring and Reporting of Continuing Suspicious Activity Upon filing an STR/SAR pertaining to an account holder, LFIs are expected to implement enhanced monitoring on such account holders. In the case of continued suspicious activity detected against said account holder, LFIs are expected to expeditiously file an STR/SAR with the FIU. Activity Requiring Immediate Attention Situations requiring immediate attention include reportable violations that are ongoing (e.g., part of an ongoing money laundering scheme as indicated by an appropriate law enforcement authority) and transactions that the LFI suspects are related to the financing of terrorism and illegal organisations. Exceptions for Complex Investigations If the LFI designates an investigation as “complex”, the LFI should submit an initial STR or SAR to the FIU within 15 business days of the alert generation. The initial STR/SAR should be labelled as a “Complex investigation” to the FIU. Following the initial STR or SAR filing, the LFI has an additional 30 business days to obtain all necessary information related to the complex investigation and submit a follow-up STR or SAR to the FIU. Summary of Review, Investigation, and Reporting Timelines There are recommended timelines for the review, investigation, and reporting of suspicious activity in the absence of an escalation for expedited review. Escalation for Expedited Review In certain cases, an alert or case may need to be dispositioned and an STR or SAR filed more rapidly than usual processes allow. In such cases, the alert will be dispositioned and the STR or SAR filed within 24 hours. Confidentiality and Prohibition against “Tipping Off” Confidentiality and Prohibition against “Tipping Off” When reporting suspicious activity or transactions to the FIU, LFIs are obliged to maintain confidentiality regarding both the information being reported and specific to the act of reporting itself, and to make reasonable efforts to ensure that the information and data reported are protected from access by any unauthorized person. Handling of Transactions and Business Relationships after Filing STRs Requirements for Corresponding with the FIU If the FIU reaches out to an LFI for additional information pertaining to an STR or SAR, details should be provided in a way that is precise and outlined as per the request. LFIs should maintain clarity on the presented information and provide it in the expected format. Post STR or SAR Process Following the filing of an STR or SAR filing, LFIs are obliged to follow the instructions, if any, of the FIU in relation to both the specific transaction and to the business relationship in general. LFIs may decide to retain a customer relationship, exit the relationship, or restrict an account, among others. Any actions taken by an LFI following the filing of an STR or SAR is a decision based on the LFI’s internal policies and procedures, including its risk appetite, although LFIs should consider the risk of tipping off a customer when implementing such restrictive measures. Governance and Reporting to Senior Management LFIs should have mechanisms to inform the Board of Directors (or a committee of the Board) and senior management on the status of its AML/CFT program, including reporting on the number and types of STRs or SARs. Record Retention LFIs are required to retain all records and documents pertaining to STRs or SARs and the results of all analysis or investigations performed for a period of no less than five (5) years from the date of completion of the transaction or termination of the business relationship. Annexes Annex 1: Indicative Examples of Insufficient STR or SAR Narratives Examples of insufficient STR or SAR narratives are provided with an explanation on why these STR or SAR narratives are not sufficient and comprehensive. Annex 2. Red Flag Indicators in the Context of the UAE The FIU published typologies and indicators of suspicious activity that an LFI should consider with a view to update policies, procedures, detection scenarios, and red flag indicators for identifying potentially suspicious activity. Annex 3. Red Flag Indicators for the UAE Insurance Sector The UAE Insurance Authority issued a list of red flag indicators that an LFI should consider with a view to update policies, procedures, detection scenarios, and red flag indicators for identifying potentially suspicious activity. Annex 4. Overarching Rules and Principles for the goAML System The goAML XML Submission Guide provides additional detail on the rules that an LFI should consider when submitting an STR, SAR, or other report type in the goAML system. Annex 5 Synopsis of the Guidance Guidance for Licensed Financial Institutions on the Implementation of Targeted Financial Sanctions
Effective from 4/7/20211. Introduction
1.1. Purpose
Article 44.11 of the Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations charges Supervisory Authorities with “providing Financial Institutions…with guidelines and feedback to enhance the effectiveness of implementation of the Crime-combatting measures.”
The purpose of this Guidance is to assist the understanding and effective performance by the United Arab Emirates Central Bank’s (“CBUAE”) licensed financial institutions (“LFIs”) of their statutory obligations under the legal and regulatory framework in force in the UAE. It should be read in conjunction with the CBUAE's Procedures for Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations1 (issued by Notice No. 74/2019 dated 19/06/2019) and the Executive Office of the Committee for Goods and Materials Subject to Import and Export Control‘s (“Executive Office”) Guidance on Targeted Financial Sanctions for Financial Institutions and Designated Non-financial Business and Professions2 (circulated by CBUAE Notice No. 2893 dated 02/06/2021) and any amendments or updates thereof. As such, while this Guidance neither constitutes additional legislation or regulation nor replaces or supersedes any legal or regulatory requirements or statutory obligations, it sets out the expectations of the CBUAE for LFIs to be able to demonstrate compliance with these requirements. In the event of a discrepancy between this Guidance and the legal or regulatory frameworks currently in force, the latter will prevail. This Guidance may be supplemented with additional separate guidance materials, such as outreach sessions and thematic reviews conducted by the Central Bank.
Furthermore, this Guidance takes into account standards and guidance issued by the Financial Action Task Force (“FATF”), industry best practices and red flag indicators. These are not exhaustive and do not set limitations on the measures to be taken by LFIs in order to meet their statutory obligations under the legal and regulatory framework currently in force. As such, LFIs should perform their own assessments of the manner in which they should meet their statutory obligations.
This Guidance comes into effect immediately upon its issuance by the CBUAE with LFIs expected to demonstrate compliance with its requirements within one month from its coming into effect.
1 Available at https://www.centralbank.ae/en/cbuae-amlcft.
2 Available at: https://www.uaeiec.gov.ae/en-us/un-page#1.2. Applicability
Unless otherwise noted, this Guidance applies to all natural and legal persons, which are licensed and/or supervised by CBUAE, in the following categories:
• National banks, branches of foreign banks, exchange houses, finance companies, payment service providers, registered hawala providers and other LFIs; and
• Insurance companies, agencies, and brokers.
1.3. Legal Basis
This Guidance builds upon the provisions of the following laws and regulations:
• Decree Federal Law No. 20 of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations (“AML-CFT Law”).
• Cabinet Decision No. (10) of 2019 concerning the Implementation Regulation of Decree Federal Law No. 20 of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations (“AML-CFT Decision”).
• Cabinet Decision No. (74) of 2020 Regarding Terrorism Lists Regulation and Implementation of UN Security Council Resolutions on the Suppression and Combating of Terrorism, Terrorists Financing & Proliferation of Weapons of Mass Destruction, and Related Resolutions (“Cabinet Decision 74”).
The AML-CFT Law and the AML-CFT Decision require LFIs to promptly apply directives issued by the competent authorities of the UAE for implementing the decisions issued by the United Nations Security Council (“UNSC”) under Chapter VII of the Charter of the United Nations (“UN”). In furtherance of this requirement, the Cabinet Decision 74 sets out the legislative and regulatory framework regarding the Targeted Financial Sanctions (“TFS”), including the Local Terrorist List and the UN Consolidated List.
The Executive Office3 acts as a national lead to coordinate and liaison implementation of TFS with all the federal and local government stakeholders including financial institutions (FIs) and designated non-financial business and professions (DNFBPs) and has issued the Guidance on Targeted Financial Sanctions for FIs and DNFBPs”. The Executive office is mainly responsible for:
• Receiving and processing grievances against Listing in UN and Local Lists decisions;
• Receiving and processing applications to use frozen funds as per sanctions lists;
• Working closely with the Supreme Council with regards to the local Listing;
• Circulating updates to the local and UN lists to the government and private sector; and
• Coordinating and exchanging information between Government Agencies.
This Guidance issued by the CBUAE is supplementary to the above mentioned “Guidance on Targeted Financial Sanctions for Financial Institutions and Designated Non-financial Business and Professions” issued by the Executive Office.
3 Website: Home | Committee for goods & material subjected to import & export (uaeiec.gov.ae)
1.4. Definitions
Controlling Shareholder: A shareholder who has the ability to directly or indirectly influence or control the appointment of the majority of the board of directors, or the decisions made by the board or by the general assembly of the entity, through the ownership of a percentage of the shares or stocks or under an agreement or other arrangement providing for such influence.
Direct Relationship: A relationship between two parties that knowingly provide the other material, technological, logistical, or financial support and both parties are directly impacted by the other party.
Funds: Assets of all types, in whatever form and however acquired, whether corporeal or incorporeal, tangible or intangible, movable or immovable, electronic, digital or encrypted, including national currency, foreign currencies, documents and legal instruments establishing ownership of such assets or any associated rights, in whatever form, including electronic or digital forms, as well as economic resources considered as assets of any kind, including oil and natural resources, and bank credits, cheques, money orders, shares, securities, bonds, drafts, and letters of credit and any interest, dividends, or other income accruing from or generated by such assets, and that may be used to obtain any other funds, goods or services including internet posting services or related services.
Indirect Relationship: A relationship between two parties that affect each other through a third-party source or one or more intermediaries.
Listed Person: Individuals, legal entities and groups listed by the UN Security Council on the UN Consolidated List, or listed by the UAE Cabinet on the Local Terrorist List, as the case may be.
Listing: Identifying the individuals, legal entities and groups subject to sanctions imposed pursuant to relevant UNSC Resolutions (“UNSCRs”), decisions of the Sanctions Committee, or relevant decisions of the UAE Cabinet, as the case may be, and implementing relevant sanctions against such individuals, legal entities and groups, with a statement of the reasons for Listing.
Local Terrorist List: Terrorism lists issued by the UAE Cabinet pursuant to the provisions of Article (63) paragraph (1) of Federal Law No. (7) of 2014 on Combating Terrorism Offences.
Other Measures: Sanction measures other than freezing that must be enforced, and which may be included in Relevant UNSCRs or UAE Cabinet decisions regarding the issuance of Local Terrorist List, such as prohibitions relating to travel, weapons, imports, or provision of fuel supplies and other.
Previous Customer: A customer with whom the relationship was terminated and the LFI maintains relevant records according to record keeping and other requirements.
Relevant UNSCRs: All current and future UNSCRs relating to the suppression and combating of terrorism, terrorist financing and proliferation of weapons of mass destruction and its financing, including but not limited to Resolutions 1267 (1999), 1373 (2001), 1988 (2011), 1989 (2011), 1718 (2006), 2231 (2015) and any successor resolutions.
Sanctions Committee: Any of the UN Security Council Committees established as per its resolutions, including UNSCRs 1267 (1999) and 1989 (2011) relating to ISIL and Al-Qaida, 1988 (2011) relating to the Security and Stability of Afghanistan, and 1718 (2006) relating to the suppression and combating of proliferation of weapons of mass destruction for the DPRK.
Subsidiary: An entity owned by another entity by more than 50% of its capital or under full control of that entity regarding appointment of the Board of Directors.
Targeted Financial Sanctions (TFS): The term Targeted Financial Sanctions means that such sanctions are against certain individuals, entities, groups, or undertakings. The term Targeted Financial Sanctions includes both asset freezing and prohibitions to prevent funds or other assets from being made available, directly, or indirectly, for the benefit of individuals, entities, groups, or organization who are sanctioned.
The Executive Office: The Executive Office of the Committee for Goods and Materials Subject to Import and Export Control.
UN Consolidated List: A list containing the names of individuals and organizations linked to terrorism, financing of terrorism or proliferation of weapons of mass destruction and its financing, and that are subject to sanctions imposed as per UNSCRs and decisions of the Sanctions Committee, along with information related to such persons and reasons for their Listing.
Without Delay: Within 24 hours of the Listing decision being issued by the UNSC, the Sanctions Committee or the UAE Cabinet, as the case may be.
2. Sanctions Compliance Program
LFIs should take appropriate steps to develop, implement and regularly update an appropriate Sanctions Compliance Program (SCP) in order to fulfil their obligation to comply with the provisions of the Cabinet Decision 74 as well as with the directives of the relevant competent authorities and supervisory authorities in regard to sanctions issued by the UNSC. An appropriate SCP also assists LFIs to manage their exposure to the risks associated with international financial sanctions programs and restrictive measures implemented by other countries.
LFIs should design and update their SCP so that its scope is proportionate to the level of their risk profile, tailored to their nature, scale, and complexity, appropriate for the products and services they offer, the customers, clients, and partner relationships they maintain, and the geographic regions in which they operate. LFIs should ensure the SCP includes the eight (8) essential components: senior management commitment, risk assessment, sanctions risk appetite, internal controls, policies and procedures, training, independent audit and testing of processes and systems, and record keeping.
2.1. Senior Management Commitment
Senior management is defined broadly to include senior leadership, executives, and the board of directors. Senior management’s commitment to, and support of, the LFI’s SCP is one of the most important factors in determining its success. In order to facilitate effective senior management commitment, an LFI should:
• Ensure that senior management has reviewed and approved the organization’s SCP. • Ensure that senior management has reviewed and approved the methodology used for undertaking the risk assessment and reviewed and approved the LFI’s risk assessments at least on an annual basis. • Clearly designate the personnel responsible for ensuring proper implementation of the SCP, including day-to-day operations, and compliance with statutory obligations. This personnel should have the appropriate competencies and experience, or be appropriately trained, to perform the duties and responsibilities associated with this role, has sufficient seniority, and is delegated sufficient authority and autonomy in order to discharge the LFI’s responsibilities. The personnel may have other responsibilities in the LFI, provided that these responsibilities do not conflict with their role in implementing the SCP. For example, large LFIs may choose to hire a dedicated sanctions compliance officer, while smaller LFIs may choose a specific officer or manager currently working at the LFI to be responsible for the SCP in addition to their other duties. • Ensure the existence of direct reporting lines between the personnel responsible for the SCP and senior management to facilitate the escalation of financial sanctions issues, including regular and periodic meetings. • Ensure that the SCP is fully integrated into the organization’s daily operations and allocated adequate resources in the form of human capital, expertise, information technology, and other resources as appropriate. • Recognize compliance failings and implement necessary measures to reduce future incidents, including through addressing root causes and implementing systemic solutions.
2.2. Risk Assessment
LFIs should take appropriate steps to conduct a regular and updated risk assessment to identify, understand, assess, monitor, and manage their risks in line with their business nature and size. While there is no “one-size-fits all” risk assessment, the assessment exercise should generally consist of a holistic review of the LFI from top-to-bottom and assess its touchpoints to the outside world where the LFI may potentially, directly or indirectly, be exposed to sanctioned parties or transactions. In most cases, LFIs should consider performing such risk assessments annually; however, assessments that are more frequent or less frequent may be justified, depending on the particular circumstances. These may include a change to the LFI risk profile, regulatory or law enforcement advisories, or global trends in terrorism financing (“TF”) and the financing of proliferation of weapons of mass of mass destruction (“PF”).
• In determining potential risks, LFIs should take into account, to the extent relevant, any vulnerabilities relating to: o its customers, supply chain, intermediaries, and counterparties; o its products and services, including how and where such items fit into other financial or commercial products, services, networks, or systems; o the geographic locations of the organization, as well as its customers, supply chain, intermediaries, and counterparties; o its distribution channels and business partners; o the complexity and volume of its transactions; o the development of new products and business practices including new delivery mechanisms, channels, and partners; and o the use of new or developing technologies for both new and pre-existing products and services. • LFIs should document risk assessment operations, maintain them up-to-date on an on-going basis, and make them available upon request. • The results of a risk assessment are integral to informing the SCP’s policies, procedures, internal controls, and training in order to effectively mitigate risks. • LFIs should develop and thoroughly document their risk assessment methodologies to identify, analyze, and address relevant risks. The methodologies should reflect the conduct and root cause of any violations or systemic deficiencies identified.
2.3. Sanctions Risk Appetite
LFIs should develop and maintain a comprehensive written sanctions risk appetite approved by the LFI’s senior management and embedded through policies, procedures, and screening systems parameterization.
• The sanctions risk appetite should specify which sanctions regimes are applicable to the LFI (for example UNSCR, OFAC, EU, UK etc.). • LFIs should specify their policy on treating of interests, properties, assets, or entities that are owned or controlled 50% or more by a Listed Person. • LFIs should specify their approach on mitigating the risk of breaching of unilateral sanctions, especially in the context of sanctions that may have extra-territorial implications or the Listed Persons may or may not have a presence in UAE (for example secondary sanctions by OFAC). • LFIs should specify their approach on screening of alias names such as one word synonyms, vessel names or paper based instruments. • LFIs should identify and document any exceptions to sanctions risk appetite or deviations from their policies and procedures; these should be approved by senior management.
For more details and information, please refer to Annex 2 for related Lessons learned from CBUAE Supervision.
2.4. Internal Controls
Internal controls are the mechanisms, rules, and procedures implemented to help ensure the integrity and effectiveness of an LFI’s SCP. As required by Cabinet Decision 74, LFIs must have appropriate internal controls in place, including the most recent publication of Targeted Financial Sanctions of the UN Consolidated List and the Local Terrorist List. Accordingly, LFIs must maintain strong and clear internal controls that ensure the effective implementation of their SCP, including policies, procedures, processes, and systems.
• LFIs should document how their processes and systems are configured in order to demonstrate that their configuration is reasonably expected to detect and manage the specific sanctions risks to which the LFI is exposed to and ensure transparency of any system limitations or risk-based decisions that the screening controls are not designed to detect.4 • LFIs should establish a mechanism to ensure that, upon learning of a weakness pertaining to its SPC compliance, immediate and effective action is taken to identify compliance gaps and their root causes, including all program-related software, systems, and other technology, and remediate them by implementing systemic solutions to reduce the chances of future failures.
2.5. Policies and Procedures
LFIs should develop and maintain clear and comprehensive written policies and procedures to enable them to manage and mitigate the sanctions risks they have identified, commensurate with the nature and size of their business.
• LFIs should ensure that policies and procedures are approved by senior management and that they: o Enable the LFI to clearly and effectively identify, prevent, escalate, and report suspicious transactions and activities; o Are tailored to the organization and capture the organization’s day-to-day operations and processes; o Are easy to follow and designed to prevent employees from engaging in misconduct; o Prohibit employees from, directly or indirectly, informing the customer or any third party that freezing or any Other Measures shall be implemented; o Require enhanced due diligence to be conducted on all customers and transactions that are assessed to be high-risk for TF and PF; and o Contain sufficient detail of their record keeping obligations. • LFIs should ensure the effective and consistent implementation of the policies and procedures related to the SCP across their organizations, including branches, Subsidiaries, and other entities in which LFIs hold a majority interest. • LFIs should clearly communicate the SCP’s policies and procedures, including for record keeping, to all relevant employees and external or outsourced service providers. • LFIs should review and update policies and procedures in a timely manner in response to events or emerging risks and ensure that such updates are communicated to employees on a timely basis. • LFIs should implement a formal review process at least annually of the policies and procedures at appropriate levels subject to approval where changes are material. • LFIs should identify and document any exceptions or deviations from the policies and procedures related to the SCP; these should be approved by senior management.
2.6. Training
The maintenance and implementation of an effective SCP requires that all relevant employees and management understand requirements and obligations, policies and procedures, internal control mechanisms, and threats, risks, and vulnerabilities. A robust training program is an integral component of an effective SCP. A training program should:
• Be of a scope and nature proportionate to the LFI’s overall risk profile; • Be specific to the role carried out by the employee, with tailored training for employees engaged in sensitive roles; • Provide training to all appropriate employees and personnel upon onboarding in a timely manner and at least annually thereafter; • Hold employees accountable for training through assessments; • Include measures to take immediate and effective action to provide corrective training or other corrective actions to relevant personnel upon learning of a confirmed negative risk assessment result or audit finding, or other deficiency pertaining to the SPC.
2.7. Independent Audit and Testing of Processes and Systems
Independent audit helps the LFI assess the effectiveness of current processes, including by assessing the sufficiency of the program and by checking for any inconsistencies between the policy and procedures and day-to-day operations in order to identify SCP weaknesses and deficiencies. Independent audits should:
• Be undertaken regularly to review and assess the effectiveness of the financial sanctions policies, procedures, systems and controls, and their compliance with the LFI’s obligations; • Be undertaken by the internal audit function, or by a competent independent external auditor, or both, and resourced with skilled and competent staff that understand the SCP of the LFI; and • Be commensurate to the level and sophistication of the SCP and updated to account for changing risk assessments or sanctions environments.
LFIs should ensure that the audit function is independent of the audited activities and functions, and has sufficient authority, skills, expertise, and resources within the organization. LFIs should immediately address negative audit findings and take the necessary steps to identify and implement compensating controls until the root cause is remediated.
In addition, LFIs should deploy an independent risk-based testing regime to regularly test their processes’ and systems’ adequacy and expected outcomes, as well as to assess their effectiveness in managing the specific risks articulated in the risk assessment. Regular testing of processes and systems ensures that the screening application generates expected alerts, threshold settings and/or screening rules to forego or suppress undesirable alerts in accordance with the LFI’s risk appetite. Regular testing should be supported by metrics, analysis, and reporting, and be reviewed by the personnel responsible for the SPC to determine whether risk acceptance or remediation is appropriate with respect to any relevant findings. Regular testing could be undertaken by the internal audit function, or by a competent external provider, or both.
2.8. Record Keeping
According to the AML-CFT Law and the AML-CFT Decision, LFIs must maintain detailed records associated with their ML/FT risk assessment and mitigation measures as well as all records, documents, data and statistics for all financial transactions, all records obtained through CDD measures for both the originators and the beneficiaries, account files and business correspondence, and copies of personal identification documents, including STRs and results of any analysis performed. LFIs must maintain the records in an organized manner so as to permit data analysis and the tracking of financial transactions. Records should be sufficient to permit reconstruction of individual transactions so as to provide, if necessary, evidence for prosecution of criminal activity. LFIs must make the records available to the competent authorities immediately upon request.
The statutory retention period for all records is at least five (5) years, from the date of completion of the transaction or termination of the business relationship, or from the date of completion of the inspection by the CBUAE, or from the date of issuance of a final judgment of the competent judicial authorities, all depending on the circumstances.
3. Screening Operations
Under Article 21.2 of Cabinet Decision 74, LFIs must regularly screen their databases and transactions against names on the UN Consolidated List and the Local Terrorist List, and also immediately when notified of any changes to any of such lists, provided that such screening includes the following:
- Searching their customer databases - Search for the names of parties to any transactions. - Search for the names of potential customers. - Search for the names of beneficial owners. - Search for names of persons and organizations with which they have a direct or indirect relationship. - Continuously search their customer database before conducting any transaction, or entering into a serious business relationship with any person, to ensure that their name is not listed on the UN Consolidated List or the Local Terrorist List.
3.1. Sanctions Evasion
Illicit actors targeted by sanctions are likely to utilize a range of tactics to evade the prohibitions, which can be difficult to identify. LFIs should remain vigilant in order to identify attempts to evade, avoid, or circumvent sanctioned activities. Frequent tactics employed for sanctions evasion include renaming, using intermediaries, creating front companies, and using alternative financial networks. LFIs should monitor not only for sanctions violations but also for red flags of potential evasion risks. LFIs also a need to remain vigilant for new methods of evading sanctions. Customer Due Diligence (“CDD”) and Enhanced Due Diligence (“EDD”) play a critical role, in combination with sanctions screening, to identify and prevent more complicated forms of sanctions evasion.
LFIs should also prohibit activity that aims to evade or circumvent sanctions prohibitions. Accordingly, LFIs must not engage in activities that could be part of a sanctions evasion scheme, including but not limited to:
• Tipping off customers or counterparties; • Omitting, withholding, altering, misstating, or removing any information about customers or transactions; • Accepting incomplete (when the customer deliberately does not provide an identifier to obscure being matched with the sanctions lists, such as a date of birth or address) or false information (when the customer provides a false identifier that would not match with the sanctions lists listed details, such as a wrong date of birth); • Providing false or incomplete information to counterparties or sanctions-imposing authorities; or • Any other activities that would cause a conflict with or failure to comply with this Guidance.
For more details and information, please refer to the Executive Office’s “Typologies on the circumvention of Targeted Sanctions against Terrorism and the Proliferation of Weapons of Mass Destruction” (circulated by CBUAE Notice No. 2893 dated 02/06/2021).
3.2. Maintenance of UN Consolidated List and Local Terrorist List
LFIs should rely on the official website of the UNSC for the most updated UN Consolidated List:
https://www.un.org/securitycouncil/content/un-sc-consolidated-list
LFIs should rely on the official website of the Executive Office to obtain the most recent publication of the Local Terrorist List issued by the UAE Cabinet:
https://www.uaeiec.gov.ae/en-us/ https://www.uaeiec.gov.ae/ar-ae/
In addition, under Article 21 of Cabinet Decision 74, LFIs must register on the Executive Office’s website in order to receive automated email notifications with updated and timely information about the Listing and de-Listing of individuals or entities in the Local Terrorist List and in the UN Consolidated List.
When LFIs utilize external vendors’ lists for their Sanctions List and Local Lists, it is the LFI’s responsibility to undertake due diligence on these vendors and ensure that the vendors’ lists contain all names listed by the UN Consolidated List and UAE Local Terrorist List.
3.3. Customer Screening
Screening processes should be conducted at various stages of the customer lifecycle to include:
• Periodic name screening: A change to either the customer identifying information or UN Consolidated List /Local Terrorist List should trigger an automatic rescreening. • Ad hoc name screening: Such screening is triggered by a specific business need or in order to comply with a request by a competent authority, or in the case of feedback from a downstream financial institution. • Re-screening: A specific scenario in the transaction monitoring system identifies a high-risk jurisdiction in updated customer information.
3.4. Name Screening
In addition to the regular screening utilizing the UN Consolidated List and Local Terrorist List indicated above, LFIs should maintain the following sanctions compliance procedures to prevent and detect sanctions breaches:
1. Ownership/Control Rule: Individuals or legal entities that are directly or indirectly owned or controlled mainly or fully by one or more Listed Person are subject to the same prohibitions as the Listed Person, even if such individuals or legal entities are not specifically named by the competent authority on the respective UN Consolidated List or Local Terrorist List.
The criterion to be taken into account when assessing whether an individual or legal entity is mainly owned by a Listed Person is the possession of more than 50% of the proprietary rights of an entity or having majority interest in it. If this criterion is satisfied, it is considered that the individual or legal entity is owned by a Listed Person.
The criteria to be taken into account when assessing whether an individual or legal entity or arrangement is mainly controlled by a Listed Person, alone or pursuant to an agreement with another shareholder or other third party, include the following:
• Having the right to appoint or remove a majority of the members of the administrative or management body of such a legal person, entity, group or arrangement;
• Having appointed solely as a result of the exercise of one's voting rights a majority of the members of the administrative or management body of a legal person, entity, group or arrangement who have held office during the present and previous financial year;
• Controlling alone, pursuant to an agreement with other shareholders in or members of a legal person, group or entity, a majority of shareholders' or members' voting rights in that legal person, entity, group or arrangement;
• Having the right to exercise a dominant influence over a legal person, group or entity, pursuant to an agreement entered into with that legal person, entity, group or arrangement, or to a provision in its Memorandum or Articles of Association, where the law governing that legal person, entity, group or arrangement permits its being subject to such agreement or provision;
• Having the power to exercise the right to exercise a dominant influence referred to in the previous point, without being the holder of that right;
• Having the right to use all or part of the assets of that legal person, entity, group or arrangement;
• Managing the business of that legal person, entity, group or arrangement on a unified basis, while publishing consolidated accounts; or
• Sharing jointly and severally the financial liabilities of legal person, entity, group or arrangement, or guaranteeing them.
2. Fuzzy Matching: An algorithm-based technique to match one data point, where the contents of the information being screened is not identical, but its spelling, pattern or sound is a close match to the contents contained on a list used for screening.
3. Weak or Low-quality Aliases: Relatively broad or generic alias may generate a large volume of false hits when such names are run through a computer-based screening system. LFIs should perform their own assessments on whether to screen for weak aliases based on their understanding of their own risk profile.
3.5. Verification of False Positives
Because many names may be common, various potential matches may be found. A potential match is when there is any match between data in the sanctions lists with any information in the LFI’s databases. However, it does not necessarily mean that the individual or entity the LFI is dealing with is subject to sanctions. When identifying the potential match, LFIs should suspend any transaction until they are satisfied it is not a Listed Person.
LFIs should compare potential matches with the UN Consolidated List and the Local Terrorist List in order to confirm whether they are true matches and to eliminate “false positives.” LFIs should compare information that is known about the party in question, such as date of birth and address, with other information provided in the designation order. Furthermore, LFIs should undertake efforts to obtain additional information and identification documents, which may have previously not been obtained from the customer or a counterparty to ascertain whether the customer is the actual designated person in the case of similar or common names. If the LFI establishes that the match is a false positive, then the LFI does not need to freezing or apply Other Measures related to sanctions. Therefore, the LFI may allow the transaction or relationship to continue its normal course, provided that the transaction or relationship is not suspicious and does not trigger any other concerns. LFIs are required to maintain evidence of the false positive verification process in their records and make them available to the competent authorities immediately upon request.
LFIs may create a “white list” (or a “good customer list”) of names of customers that have been flagged as potential matches to the UN Consolidated List and the Local Terrorist List but subsequently cleared through thorough due diligence by the LFI. Those “white lists” may be used to improve the process related to screening by leveraging the results of past due diligences and reducing the number of false positives. While an LFI should not overly rely on such a list and must diligently and continuously screen customers and transactions in case they are implicated in updated UN Consolidated List and Local Terrorist List, the use of such a “white list” may assist the LFI in expediting the dispositioning in case of repeated false positive matches. LFIs should have documented procedures to managing and periodically reviewing and updating those “white lists”.
For more details and information, please refer to Annex 2 for related Lessons learned from CBUAE Supervision.
3.6. Payments Screening
LFIs should also screen information regarding counterparties of all incoming and outgoing transfers in order to identify any potential match to Listed Persons. The information to be screened includes:
• The parties involved in a transaction, including the sender and the receiver; • Third parties and intermediaries; • Bank Names, Bank Identifier Code ("BIC”) and other routing codes; • Free text fields; • International Securities Identification Number (“ISINs”) or other risk relevant product identifiers (there are multiple fields in the identifier information section for sanctions lists. An ISIN number can be screened as an identifier number similar to a date of birth/passport number, and towns/regions can be screened as jurisdictions operating in); • Geography, including addresses, countries, cities, towns, regions.
3.7. Confirmed match
Under Articles 15 and 21 of Cabinet Decision 74, when a match is found through the screening process, LFIs must immediately, without delay and without prior notice, freeze all Funds. Without delay, as defined by Article 1 of Cabinet Decision 74, means within 24 hours of the Listing decision being issued by the UNSC, the Sanctions Committee or the UAE Cabinet, as the case may be.
For more details and information, please refer to the Executive Office’s Guidance on Targeted Financial Sanctions for FIs and DNFBPs.
4. Notification to Cbuae and Executive Office
Under Article 21(5) of Cabinet Decision 74, LFIs must immediately notify the CBUAE in the following cases:
• Identification of funds and actions that have been taken as per requirements of Relevant UNSCRs or decisions of the Cabinet regarding the issuance of Local Terrorist List (including but not limited to freezing), including attempted transactions. • Detection of any match with Listed Persons or entities, details of the matched data, and actions that have been taken as per the requirements of Relevant UNSCRs and Local Terrorist Lists, including attempted transactions. • Identification of a previous customer or an occasional customer listed on the UN Consolidated List or Local Terrorist List. • Suspicion that a current or previous customer, or a person with whom they have a business relationship, is a Listed Person or has a direct or indirect relationship with a Listed Person. • No action has been taken due to a false positive and the inability to dismiss a false positive through available or accessible information (i.e. given insufficient information, such as matching identifier information, address, DOB, or nationality). Please see also section 3.5 above. • Unfreezing of Funds, identifying the information relating to funds that have been unfrozen, including their status, nature, value and measures that were taken in respect thereof, and any other information relevant to such decisions.
Under Article 15(2) of Cabinet Decision, LFIs must also notify the Executive Office of any freezing measures and/or attempted transactions.
According to the Executive Office’s Guidance on Targeted Financial Sanctions for FIs and DNFBPs, LFIs should notify the CBUAE and the Executive Office within two (2) business days from taking any freezing measure and/or attempted transactions. For the reporting mechanism and form(s), please consult the CBUAE’s and the Executive Office’s websites as updated from time to time.
Annex 1. Red Flag Indicators for TF and PF
Accurately identifying and assessing the TF and PF risks of a customer or business relationship is critical for appropriately managing these risks. A single indicator on its own may seem insignificant, but when combined with others it could provide reasonable grounds to suspect that the transaction is related to TF or PF activity.
1. Red Flag Indicators for TF7
Potentially Suspicious Activity That May Indicate Terrorist Financing Published in the FFIEC BSA/AML Examination Manual5
Activity Inconsistent with the Customer’s Business:
• Funds are generated by a business owned by persons of the same origin or by a business that involves persons of the same origin from higher-risk countries (e.g., countries designated by national authorities and FATF as non-cooperative countries and territories). • The stated occupation of the customer is not commensurate with the type or level of activity. • Persons involved in currency transactions share an address or phone number, particularly when the address is also a business location or does not seem to correspond to the stated occupation (e.g., student, unemployed, or self-employed). • Regarding nonprofit or charitable organizations, financial transactions occur for which there appears to be no logical economic purpose or in which there appears to be no link between the stated activity of the organization and the other parties in the transaction. • A safe deposit box opened on behalf of a commercial entity when the business activity of the customer is unknown or such activity does not appear to justify the use of a safe deposit box.
Funds Transfers:
• A large number of incoming or outgoing funds transfers take place through a business account, and there appears to be no logical business or other economic purpose for the transfers, particularly when this activity involves higher-risk locations. • Funds transfers are ordered in small amounts in an apparent effort to avoid triggering identification or reporting requirements. • Funds transfers do not include information on the originator, or the person on whose behalf the transaction is conducted, when the inclusion of such information would be expected. • Multiple personal and business accounts or the accounts of nonprofit organizations or charities are used to collect and funnel funds to a small number of foreign beneficiaries. • Foreign exchange transactions are performed on behalf of a customer by a third party, followed by funds transfers to locations having no apparent business connection with the customer or to higher-risk countries.
Other Transactions That Appear Unusual or Suspicious:
• Transactions involving foreign currency exchanges are followed within a short time by funds transfers to higher-risk locations. • Multiple accounts are used to collect and funnel funds to a small number of foreign beneficiaries, both persons and businesses, particularly in higher-risk locations. • A customer obtains a credit instrument or engages in commercial financial transactions involving the movement of funds to or from higher-risk locations when there appear to be no logical business reasons for dealing with those locations. • Banks from higher-risk locations open accounts. • Funds are sent or received via international transfers from or to higher-risk locations. • Insurance policy loans or policy surrender values that are subject to a substantial surrender charge.
Terrorist Financing Indicators Published by FINTRAC (Canada’s Financial Intelligence Unit)6
• Transactions involving certain high-risk jurisdictions such as locations in the midst of or in proximity to, armed conflict where terrorist groups operate or locations which are subject to weaker ML/TF controls. • An account opened in the name of an entity, a foundation or association, which may be linked or involved with a suspected terrorist organization. • The use of funds by a non-profit organization is not consistent with the purpose for which it was established. • Raising donations in an unofficial or unregistered manner. • Client identified by media or law enforcement as having travelled, attempted or intended to travel to high-risk jurisdictions (including cities or districts of concern), specifically countries (and adjacent countries) under conflict and/or political instability or known to support terrorist activities and organizations. • Transactions involve individual(s) or entity(ies) identified by media and/or Sanctions List as being linked to a terrorist organization or terrorist activities. • Law enforcement information provided which indicates individual(s) or entity(ies) may be linked to a terrorist organization or terrorist activities. • Client conducted travel-related purchases (e.g. purchase of airline tickets, travel visa, passport, etc.) linked to high-risk jurisdictions (including cities or districts of concern), specifically countries (and adjacent countries) under conflict and/or political instability or known to support terrorist activities and organizations. • Individual or entity's online presence supports violent extremism or radicalization. • Client donates to a cause that is subject to derogatory information that is publicly available (e.g. crowdfunding initiative, charity, non-profit organization, non-government organization, etc.).
5 Available at: https://bsaaml.ffiec.gov/manual/Appendices/07
6 Available at: https://www.fintrac-canafe.gc.ca/guidance-directives/transaction-operation/indicators-indicateurs/fin_mltf-eng2. Red Flag Indicators for PF
(i) Transaction involves person or entity in foreign country of proliferation concern. (ii) Transaction involves person or entity in foreign country of diversion concern. (iii) The customer or counterparty or its address is similar to one of the parties found on publicly available lists of “denied persons” or has a history of export control contraventions. (iv) Customer activity does not match business profile, or end-user information does not match end-user’s business profile. (v) A freight forwarding firm is listed as the product’s final destination. (vi) Order for goods is placed by firms or persons from foreign countries other than the country of the stated end-user. (vii) Transaction involves shipment of goods incompatible with the technical level of the country to which it is being shipped, (e.g. semiconductor manufacturing equipment being shipped to a country that has no electronics industry). (viii) Transaction involves possible shell companies (e.g. companies do not have a high level of capitalisation or displays other shell company indicators). (ix) Transaction demonstrates links between representatives of companies exchanging goods i.e. same owners or management. (x) Circuitous route of shipment (if available) and/or circuitous route of financial transaction. (xi) Trade finance transaction involves shipment route (if available) through country with weak export control laws or weak enforcement of export control laws. (xii) Transaction involves persons or companies (particularly trading companies) located in countries with weak export control laws or weak enforcement of export control laws. (xiii) Transaction involves shipment of goods inconsistent with normal geographic trade patterns (e.g. does the country involved normally export/import good involved?). (xiv) Transaction involves financial institutions with known deficiencies in AML/CFT controls and/or domiciled in countries with weak export control laws or weak enforcement of export control laws. (xv) Based on the documentation obtained in the transaction, the declared value of the shipment was obviously under-valued vis-à-vis the shipping cost. (xvi) Inconsistencies in information contained in trade documents and financial flows, such as names, companies, addresses, final destination etc. (xvii) Pattern of wire transfer activity that shows unusual patterns or has no apparent purpose. (xviii) Customer vague/incomplete on information it provides, resistant to providing additional information when queried. (xix) New customer requests letter of credit transaction awaiting approval of new account. (xx) Wire instructions or payment from or due to parties not identified on the original letter of credit or other documentation. (xxi) Involvement of items controlled under WMD export control regimes or national control regimes. (xxii) Involvement of a person connected with a country of proliferation concern (e.g. a dual-national), and/or dealing with complex equipment for which he/she lacks technical background. (xxiii) Use of cash or precious metals (e.g. gold) in transactions for industrial items. (xxiv) Involvement of a small trading, brokering or intermediary company, often carrying out business inconsistent with their normal business. (xxv) Involvement of a customer or counterparty, declared to be a commercial business, whose transactions suggest they are acting as a money-remittance business. (xxvi) Transactions between companies on the basis of “ledger” arrangements that obviate the need for international financial transactions. (xxvii) Customers or counterparties to transactions are linked (e.g. they share a common physical address, IP address or telephone number, or their activities may be coordinated). (xxviii) Involvement of a university in a country of proliferation concern. (xxix) Description of goods on trade or financial documentation is nonspecific, innocuous or misleading. (xxx) Evidence that documents or other representations (e.g. relating to shipping, customs, or payment) are fake or fraudulent. (xxxi) Use of personal account to purchase industrial items.
7 Available at: fatf guidance on proliferation financing (fatf-gafi.org)
3. Red Flag Indicators for Potential Sanctions Circumventions
Some Red Flags or Situations to Identify Potential Sanctions Circumventions Published in the Executive Office’s “Typologies on the circumvention of Targeted Sanctions against Terrorism and the Proliferation of Weapons of Mass Destruction” 8
The following are some red flags or situations that could be looked at more closely or monitored by financial institutions and designated non-financial businesses or professions to identify potential sanctions circumventions of your clients, their business, or their transactions.
• Dealings in sectors vulnerable for terrorist financing and/or proliferation of weapons of mass destructions, for example o Financial sector o Hawalas or other money transfer services providers o Oil and gas sector o Non-profit organizations o International trade • Dealings, directly or through a client of your client, with high-risk countries for terrorism financing. • Dealings, directly or through a client of your client, with sanctioned countries or territories where sanctioned persons are known to operate. • The use of shell companies through which funds can be moved locally and internationally by misappropriating the commercial sector in the UAE. • Dealings with sanctioned goods or under embargo. For example: o Weapons o Oil or other commodities o Luxury goods (for DPRK sanctions) • Dealings with dual-used goods. • Dealings with controlled substances. • Identifying documents that seemed to be forged or counterfeited. • Identifying tampered or modified documents with no apparent explanation, especially those related to international trade. • Use of intermediaries. • When the flows of funds exceed those of normal business (revenues or turnover). • The activity developed or financed does not relate to the original or intended purpose of the company o entity. For example: • For companies, they are importing high-end technology devices, but they are registered as a company that commercializes nuts. • For a non-profit organization, they are exporting communication devices, but they are an entity aimed to provide health services. • Very complex commercial or business deals that seem to be aiming to hide the final destiny of the transaction or the good. • Complex legal entities or arrangements that seem to be aiming to hide the beneficial owner. • Carrying out of multiple ATM cash withdrawals in short succession (potentially below the daily cash reporting threshold) across various locations in territories where sanctioned people have influence or in the border of sanctioned countries. • Irregularities during the CDD process which could include, but is not limited to: o Inaccurate information about the source of funds and/or the relationship with the counterparty. o Refusal to honor requests to provide additional KYC documentation or to provide clarity on the final beneficiary of the funds or goods. o Suspicion of forged identity documents
8 Available at https://www.uaeiec.gov.ae/en-us/un-page#
Annex 2. Lessons learned from CBUAE Supervision
In 2020 the CBUAE’s AML/CFT Supervision Department conducted a thematic review of 30 LFIs’ sanctions screening systems. The aim of the review was to assess the LFIs’ compliance with these provisions and their sanctions screening systems’ effectiveness and efficiency levels.
For more details and information, please refer to the CBUAE’s “Sanctions Screening Testing Thematic Review – Lessons Learned and Expectations”.9
9 Available at https://www.centralbank.ae/en/cbuae-amlcft.
Annex 3. Synopsis of the Guidance
Purpose of this Guidance Purpose The purpose of this Guidance is to assist the understanding and effective performance by the CBUAE licensed financial institutions (LFIs) of their statutory obligations under the legal and regulatory framework in force in the UAE related to targeted financial sanctions, screening and reporting requirements as well as the development of an appropriate sanctions compliance program. Applicability This Guidance applies to all natural and legal persons, which are licensed and/or supervised by the CBUAE, in the following categories:
- national banks, branches of foreign banks, exchange houses, finance companies, payment service providers, registered hawala providers and other LFIs; and
- insurance companies, agencies, and brokers.
Sanctions Compliance Program Senior Management Commitment LFI senior management's commitment to, and support of, the Sanctions Compliance Program (SCP) is one of the most important factors in determining its success. In order to facilitate effective senior management commitment, an LFI should, among other things:
- Ensure that senior management has reviewed and approved the organization's SCP;
- Clearly designate the personnel responsible for ensuring proper implementation of the SCP; and
- Ensure that the SCP is fully integrated into the organization's daily operations and allocating adequate resources to it.
Risk Assessment LFIs should take appropriate steps to conduct a regular and updated sanctions risk assessment to identify, understand, assess, monitor and manage their risks in line with their business nature and size. Sanctions Risk appetite LFIs should develop and maintain a comprehensive written sanctions risk appetite approved by the LFI's senior management and embedded through policies, procedures, and screening systems parameterization. Internal Controls Internal controls are the mechanisms, rules, and procedures implemented to help ensure the integrity and effectiveness of an LFI's SCP. LFIs must have and maintain strong and clear internal controls to ensure compliance with their statutory sanctions obligations and ensure the effective implementation of their SCP. Policies and Procedures LFIs should develop and maintain clear and comprehensive written policies and procedures that should, among other things:
- Be approved by senior management; and
- Enable the LFI to clearly and effectively identify, prevent, escalate, and report potentially prohibited transactions and activities.
LFIs should ensure the effective and consistent implementation of the policies and procedures related to the SCP across their organizations, including branches, subsidiaries, and other entities in which LFIs hold a majority interest. LFIs should implement a formal review process, at least annually, of the policies and procedures at appropriate levels subject to approval where changes are material.
Training A robust training program is an integral component of an effective SCP and should, among other things:
- Be of a scope and nature proportionate to the LFI's overall risk profile;
- Be specific to the role carried out by the employee, with tailored training for employees engaged in sensitive roles; and
- Provide training to all appropriate employees and personnel upon onboarding in a timely manner and at least annually thereafter.
Independent Audit and Testing of Processes and Systems Independent audit helps the LFI assess the effectiveness of current processes, including by assessing the sufficiency of the program and by checking for any inconsistencies between the policy and procedures and day-to-day operations in order to identify SCP weaknesses and deficiencies. In addition, LFIs should deploy an independent risk-based testing regime to regularly test their processes’ and systems’ adequacy and expected outcomes, as well as to assess their effectiveness in managing the specific risks articulated in the risk assessment. Record keeping LFIs must maintain, at least for five years, detailed records associated with their ML/FT risk assessment and mitigation measures as well as all records, documents, data and statistics for all financial transactions, all records obtained through CDD measures for both the originators and the beneficiaries, account files and business correspondence, and copies of personal identification documents, including STRs and results of any analysis performed; and make them available to authorities on request. Screening Operations Sanctions Evasion LFIs should remain vigilant in order to identify attempts to evade, avoid, or circumvent sanctioned activities. LFIs should monitor not only for sanctions violations but also for red flags of potential evasion risks. LFI's should also prohibit activity that aims to evade or circumvent sanctions prohibitions. Maintenance of Sanctions List and Local Lists LFIs should rely on the official websites of the UNSC and the Executive Office of the Committee for Goods & Materials Subject to Import & Export Control (Executive Office) respectively for the most updated UN Consolidated List and Local Terrorist List. LFIs must register on the Executive Office's website in order to receive automated email notifications with updated and timely information about the listing and de-listing of individuals or entities in the Local Terrorist List and in the UN Consolidated List. Customer Screening Screening should be conduct at various stages of the customer lifecycle, to include periodic name screening, ad hoc name screening, and re- screening. Name Screening In addition to the regular screening utilizing the lists indicated above, LFIs should maintain additional sanctions compliance procedures relating to name screening to prevent and detect sanctions breaches. These procedures should address the ownership/control rule, fuzzy matching, and weak or low-quality aliases. Verification of False Positives LFIs should compare potential matches with the sanctions lists indicated above in order to confirm whether they are true matches and to eliminate “false positives.” If the LFI establishes that the match is a false positive, then the LFI does not need to freezing or apply other measures related to sanctions. The LFI may allow the transaction or relationship to continue its normal course, provided that the transaction or relationship is not suspicious and does not trigger any other concerns. LFIs are required to maintain evidence of the false positive verification process in their records and make them available to the competent authorities immediately upon request. Payments Screening LFIs should also screen information regarding counterparties of all incoming and outgoing transfers in order to identify any potential match to Listed Persons. Confirmed Match When a match is found through the screening process, LFIs must immediately, without delay and without prior notice, freeze all Funds. Without delay, as defined by Cabinet Decision 74, means within 24 hours of the listing decision being issued by the UNSC, the Sanctions Committee or the UAE Cabinet, as the case may be. Notifications Notifications to the CBUAE and Executive Office LFIs must immediately notify the CBUAE, as well as the Executive Office, of any freezing measures and/or attempted transactions. LFIs should notify the CBUAE and the Executive Office within two (2) business days from taking any freezing measures and/or attempted transactions. For the reporting mechanism and form(s), please consult the CBUAE's and the Executive Office's websites as updated from time to time. Annexes Annex 1 Red flag indicators for TF and PF Annex 2 Lessons learned from CBUAE Supervision Annex 3 Synopsis of the Guidance Guidance for Licensed Financial Institutions on Transaction Monitoring and Sanctions Screening
Effective from 8/9/20211. Introduction
1.1. Purpose
Article 44.11 of the Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations charges Supervisory Authorities with “providing Financial Institutions…with guidelines and feedback to enhance the effectiveness of implementation of the Crime-combatting measures.”
The purpose of this Guidance is to assist the understanding and effective performance by the United Arab Emirates Central Bank’s (“CBUAE”) licensed financial institutions (“LFIs”) of their statutory obligations under the legal and regulatory framework in force in the UAE. It should be read in conjunction with the CBUAE’s Procedures for Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations (issued by Notice No. 74/2019 dated 19/06/2019) and Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations for Financial Institutions (issued by Notice 79/2019 dated 27/06/2019) and any amendments or updates thereof.1 As such, while this Guidance neither constitutes additional legislation or regulation nor replaces or supersedes any legal or regulatory requirements or statutory obligations, it sets out the expectations of the CBUAE for LFIs to be able to demonstrate compliance with these requirements. In the event of a discrepancy between this Guidance and the legal or regulatory frameworks currently in force, the latter will prevail. This Guidance may be supplemented with additional separate guidance materials, such as outreach sessions and thematic reviews conducted by the Central Bank.
Furthermore, this Guidance takes into account standards and guidance issued by the Financial Action Task Force (“FATF”), industry best practices and red flag indicators. These are not exhaustive and do not set limitations on the measures to be taken by LFIs in order to meet their statutory obligations under the legal and regulatory framework currently in force. As such, LFIs should perform their own assessments of the manner in which they should meet their statutory obligations.
This Guidance comes into effect immediately upon its issuance by the CBUAE with LFIs expected to demonstrate compliance with its requirements within one month from its coming into effect.
1 Available at https://www.centralbank.ae/en/cbuae-amlcft.
1.2. Applicability
Unless otherwise noted, this guidance applies to all natural and legal persons, which are licensed and/or supervised by CBUAE, in the following categories:
• National banks, branches of foreign banks, exchange houses, finance companies and other LFIs; and • Insurance companies.
1.3. Legal Basis
This Guidance builds upon the provisions of the following laws and regulations:
(i) Federal Decree-Law No. (20) of 2018 on Anti-Money Laundering (“AML”) and Combatting the Financing of Terrorism (“CFT”) and Financing Illegal Organisations (‘AML-CFT Law”);
(ii) Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation for Decree-Law No. (20) of 2018 on AML and CFT and Financing of Illegal Organisations (“AML-CFT Decision”); and
(iii) Cabinet Decision No. (74) of 2020 Regarding Terrorism Lists Regulation and Implementation of United Nations Security Council (UNSC) Resolutions on the Suppression and Combating of Terrorism, Terrorist Financing, Countering the Proliferation of Weapons of Mass Destruction and its Financing and Relevant Resolution (“Cabinet Decision 74”).
With respect to transaction monitoring (“TM”), and as per Articles 4.2 (a) and 20 of AML-CFT Decision, LFIs are obliged to develop internal policies, controls, and procedures that are commensurate with the nature and size of their business and are approved by senior management to enable them to manage the crime risks that have been identified. They must also continuously update them. Furthermore, under Article 16 of AML-CFT Decision, LFIs must put in place indicators that can be used to identify suspicious transactions and other activity in order to file suspicious transaction reports (“STR”), suspicious activity reports (“SAR”) or other report types to the UAE’s Financial Intelligence Unit (“FIU). LFIs must update these indicators on an ongoing basis, in line with all applicable instructions from the UAE’s supervisory authorities and FIU.
With respect to sanctions screening, and as per Article 21.2 of Cabinet Decision 74, LFIs are obliged to regularly screen their databases and transactions against names on lists issued by the UNSC and its relevant Committees (UN Consolidated List) or by the UAE Cabinet (Local Terrorist List), and also immediately when notified of any changes to any of such lists. Such screening must include regular searches of their customer databases, parties to any transactions, potential customers, beneficial owners, and persons and organizations with which the LFI has a direct or indirect relationship. LFIs must also screen their customer database before conducting any transaction, or entering into a business relationship with any person, to ensure that their name is not listed on the UN Consolidated List or the Local Terrorist List.
For more details and information, please refer to the Executive Office of the Committee for Goods and Materials Subject to Import and Export Control’s (“Executive Office”) Guidance on TFS for Financial Institutions and Designated Non-financial Business and Professions2, the CBUAE’s Guidance for Licensed Financial Institutions on the Implementation of TFS, and the CBUAE’s Guidance for Licensed Financial Institutions on STR3. LFIs should consult the CBUAE’s and the Executive Office’s websites as updated from time to time.
2 Available at: https://www.uaeiec.gov.ae/en-us/un-page.
3 Available at: https://www.centralbank.ae/en/cbuae-amlcft.1.4. Acronyms
Terms Description AML Anti-money laundering CBUAE Central Bank of the United Arab Emirates CDD Customer due diligence CFT Combating the financing of terrorism FATF Financial Action Task Force FIU Financial intelligence unit ISIN International Securities Identification Numbers KYC Know your customer LFI Licensed financial institution MIS Management information systems ML Money laundering OCR Optical character recognition PF Proliferation financing SAR Suspicious activity report STR Suspicious transaction report SWIFT Society for Worldwide Interbank Financial Telecommunications TF Terrorist financing TM Transaction monitoring TFS Targeted financial sanctions 2. Transaction Monitoring
An effective TM program enables LFIs to detect, investigate, and report suspicious transactions, in compliance with the UAE’s legal and regulatory framework, and to ensure that the institutions’ customers and transactions remain within their risk appetite. Effective TM therefore depends critically on information obtained through the application of customer due diligence (“CDD”)/know your customer (“KYC”) measures, including but not limited to information regarding the types of transactions in which the customer would normally be expected to engage.
Obtaining a sufficient understanding of its customers and the nature and purpose of the customer relationship, together with the ongoing analysis of actual customer behavior and the behavior of relevant peer groups, allows the LFI to develop a baseline of normal or expected activity for the customer, against which unusual or potentially suspicious transactions can be identified. TM compliance personnel should escalate for priority remediation any identified omissions or inaccuracies in relevant customer or beneficial ownership information or gaps or data quality issues in required transaction or payment message fields.
An effective TM program consists of the following core elements:
• A well-calibrated risk-based framework: The risks LFIs face are dynamic and the transactions they carry out may be varied and high in volume. LFIs should therefore review and enhance their TM frameworks regularly and upon the occurrence of specified “trigger events,” such as material changes in the LFI’s business or risk profile or its legal and regulatory environment, to ensure that they remain tailored to the institution’s financial crime risks. Incorporating feedback from the personnel handling the alerts to the TM system also helps in better calibration and tuning.
• Robust training and risk awareness: To ensure proper functioning and implementation of their TM programs, LFIs should ensure that personnel with TM responsibilities have adequate experience and expertise and receive role-specific training on the institution’s TM policies, procedures, and risks.
• Meaningful integration into the AML/CFT program: LFIs should ensure that their TM systems and frameworks reinforce, and are reinforced by, the wider AML/CFT control environment of which they are a part. An effective TM program depends on the quality and completeness of data drawn from the LFI’s customer and transactional systems and databases. In tandem, the outcomes of TM should inform the LFI’s understanding and management of its financial crime risks, including by prompting off-cycle customer reviews and the application of enhanced scrutiny or additional controls to higher-risk customers or transactions.
• Active oversight: The LFIs’ board and senior management should take an active role in overseeing the performance of their TM programs and the ongoing enhancement of TM systems on the basis of the institution’s risks. Where the outcomes of TM are compromised by factors such as inappropriate calibration, process inefficiencies, staff issues, or system failures, it is necessary that the board (or a board-designated committee) and senior management be made aware of these issues in a timely manner so as to ensure that they are promptly and adequately remediated. The board and senior management should also communicate clear risk appetites within their institutions and set a strong tone from the top that the prevention, detection, and reporting of illegal or suspicious transactions are a priority. A quality assurance process should also play a crucial part in the TM program, by validating the review from accuracy and detail perspective. Any changes in the transaction codes or changes in the core banking system should be approved by senior management.
2.1. Risk Assessment
The design of an LFI’s TM program should be informed by the LFI’s risk assessment, so that TM controls are applied across the full range of risks to which the institution is exposed and enhanced scrutiny is applied to the areas of highest risk. An LFI’s risk assessment should include, at a minimum, an assessment of the customers, products and services, delivery channels, and geographic exposure presenting the greatest money laundering (“ML”), terrorist financing (“TF”), and proliferation financing (“PF”) risks, as well as the strength of the controls currently in place to mitigate these risks. The risk assessment serves a range of critical purposes, including but not limited to enabling an LFI to:
- understand the type of level of risk associated with its business relationships and transactions;
- develop risk-based policies, procedures and controls;
- make informed decisions with respect to resourcing and staffing;
- apply additional controls to areas of heightened risk; and
- ensure that the LFI’s residual risks are within its risk appetite.
With respect to transaction monitoring specifically, the risk assessment can be used to ensure that each mode of transacting with or through the institution—domestically or internationally—is subject to a form of TM that is commensurate with its risks and is operating effectively to mitigate those risks. The risk assessment should be updated at periodic intervals (at least annually or otherwise as appropriate and justified by the required circumstances) and also upon the occurrence of “trigger events,” such as material changes in the LFI’s business or risk profile or the legal and regulatory environment.
2.2. Risk-Based Deployment of Transaction Monitoring Controls
TM can include manual monitoring processes and the use of automated and intelligence-led monitoring systems. In all cases, the appropriate type and degree of monitoring should appropriately match the ML/TF/PF risks of the institution’s customers, products and services, delivery channels, and geographic exposure, and may therefore vary across an LFI’s business lines or units, where applicable. TM programs should also be calibrated to the size, nature, and complexity of each institution. LFIs with a larger scale of operations are expected to have in place automated systems capable of handling the risks from an increased volume and variance of transactions. LFIs utilizing automated systems should perform a typology assessment to design appropriate rule- or scenario-based automated monitoring capabilities and processes. While smaller LFIs may rely on TM systems that are less automated, they should still ensure that these are appropriately executed to address the risks from their day-to-day transactional activity.
Examples of automated tools include rule- or scenario-based automated suspicious activity monitoring systems (which typically perform post-execution batch screening of transactions on a daily, weekly, monthly, and/or ad hoc schedule), automated fraud detection systems, trade surveillance systems, and automated negative news screening tools. Examples of manual tools include unusual activity or unusual transaction reporting by business-line employees (including especially, but not limited to, customer relationship managers or those otherwise in customer-facing roles), reporting of potentially suspicious activity by LFI employees (including internal whistleblower reporting), manual reviews of document-based transactions (such as documentary trade finance transactions or loans), manual negative news screening, and periodic or event-based CDD reviews.
Particularly where purely manual processes are employed, LFIs should implement appropriate training on TM policies and procedures to ensure that personnel adhere to the internal processes for identification and referral of potentially suspicious activity. LFIs should be aware of all methods of identification and should ensure that their suspicious activity monitoring program includes processes to facilitate the transfer of internal referrals to appropriate personnel for further research. Regardless of whether automated or manual processes (or a combination of the two) are used to perform TM, it is the LFI’s responsibility to demonstrate that the monitoring program is effective and appropriately risk based.
Where practicable and on a risk basis, LFIs should monitor transactions at the customer or relationship level, including across financial groups, and not only on an individual account basis, so as to obtain a complete view of a customer’s transaction profile at the institution. Holistic monitoring of customers with multiple accounts is especially important for customers assessed to be politically exposed persons or as belonging to other high-risk categories.
2.3. Data Identification and Management
LFIs should have in place adequate processes to ensure that customer and transactional data feeding into their TM program (whether using manual or automated processes, or both) meets established data quality standards, that data is subject to testing and validation at risk-based intervals, and that identified data quality and completeness issues are remediated in a timely manner.
As an initial matter, LFIs should identify and document all data sources that serve as inputs into their TM program. TM data sources may include both internal customer databases, core banking or other transaction processing systems, and applicable “flat-file” databases, as well as external sources such as Society for Worldwide Interbank Financial Telecommunication (“SWIFT”) message data. Source system documentation should include the identification of a system owner or primary party responsible for overseeing the quality of source data and addressing identified data issues. Where automated TM systems are used, LFIs should institute data extraction and loading processes to ensure a complete, accurate, and fully traceable transfer of data from its source to TM systems. LFIs should also ensure that staff’s access rights to both source systems and TM systems are commensurate with their roles and responsibilities, so as to ensure that relevant staff can perform their duties effectively and that access is not extended to unauthorized persons or those no longer requiring system access.
Both prior to the initial deployment of a TM system or process and at risk-based intervals thereafter, LFIs should test and validate the integrity, accuracy, and quality of data to ensure that accurate and complete data is flowing into their TM program. Data testing and validation should typically occur at minimum every 12 to 18 months, as appropriate based on the LFI’s risk profile, and the frequency of such activities should be clearly mandated and documented in the LFI’s policies and procedures. Such testing can include data integrity checks to ensure that data is being completely and accurately captured in source systems and transmitted to TM systems, as well as the reconciliation of transaction codes across core banking and TM systems. Testing may also utilize quantitative data quality standards or benchmarks to track data quality over time and specify a threshold or range beyond which data irregularities or other data quality issues shall require corrective action.
In addition, LFIs should put in place appropriate detection controls, such as the analysis of trends observable through management information system (“MIS”) data and the generation of exception reports, to identify abnormally functioning TM rules or scenarios and ensure that any such irregularities caused by data integrity or other data quality issues are appropriately diagnosed and remediated. Where appropriate, a root cause analysis should be performed, and any findings and recommended remedial actions should be escalated to senior management to address the underlying issue in a timely manner.
2.4. Rule Definition and Pre-Implementation Testing
LFIs should employ TM detection scenarios (or “rules”) that are designed to identify potentially suspicious or illegal transactions and elevate them for further review and investigation, as warranted. LFIs utilizing automated systems should perform a typology assessment to design appropriate rule- or scenario-based automated monitoring capabilities and processes. Transactions may be suspicious simply in virtue of their individual characteristics (such as their value, source, destination, or use of intermediaries) or because, together with other transactions, they form a pattern that diverges from expected or historical transactional activity or may otherwise be indicative of illicit activity, including the evasion of reporting or recordkeeping requirements.
TM rules may be automated or manual and should employ value and other thresholds and parameters that take into account the specific risks and contexts of the institution, as identified in the financial crimes risk assessment, and the specific product or service and customer type involved in the transaction. To this end, LFIs should perform risk-based customer and product segmentation, so that rule parameters and thresholds are appropriately calibrated to the type of activity subject to TM. LFIs with larger transaction volumes should consider employing the use of statistical tools or methods such as above-the-line and below-the-line testing, which involves increasing and decreasing the predetermined thresholds of TM rules in a testing environment and measuring the resulting output, to better fine-tune their calibrations and reduce the volume of false-positive alerts.
In order to identify patterns of potentially suspicious or illegal activity spanning multiple transactions, LFIs should group individual TM parameters and thresholds into multi-factor risk scenarios in order to more precisely target transaction patterns and behaviors consistent with known illicit financing typologies. Key typologies and associated indicators of relevance in the context of the UAE published by the FIU are included in the CBUAE’s Guidance for LFIs on Suspicious Transaction Reporting.4 The use of scenarios should not be limited to LFIs with automated transaction monitoring systems, as smaller institutions with less-automated systems can and should apply the same logic in training and guiding their staff to detect these more complex risks. However, LFIs with a larger scale of operations are expected to have in place automated systems capable of handling the risks from an increased volume and variance of transactions. In all cases, LFIs should maintain documentation that articulates the institution’s current detection scenarios and their underlying assumptions, parameters, and thresholds.
Where automated systems are employed, LFIs should perform pre-implementation testing of TM rules and systems, using historical transaction data as appropriate. Such testing should include system integration testing to ensure compatibility of the TM system with source systems and other AML/CFT compliance infrastructure and user acceptance testing to ensure that the system performs as anticipated in the operating environment. Material data mapping, transaction coding, and other data quality issues, as well as irregularities in TM model performance and outputs, identified through pre-implementation testing should be prioritized for remediation and subject to re-testing prior to the deployment of a TM system.
4 Available at https://www.centralbank.ae/en/cbuae-amlcft.
2.5. Alert Scoring and Prioritization
Consistent with a risk-based approach, LFIs may consider assigning risk-weighted scores to TM alerts in order to prioritize higher-risk alerts for expedited review. LFIs may opt to assign a higher risk score, and thus to prioritize for review and investigations, transactions that violate individual TM rules corresponding with especially heightened risks (based on the risk profile and risk appetite of the institution) as well as transactions identified as violating multiple TM rules. LFIs with larger TM alert review and investigation teams may likewise opt to allocate higher-scoring alerts to more senior investigators or those with specialized expertise in certain risk areas. In such a scenario, non-high scoring alerts could then be allocated to the staff using a “round robin” or any other technique in order to ensure a balanced and efficient distribution of alerts among staff. Although alert scoring may be used to achieve a risk-based prioritization and allocation of manually generated TM alerts, such processes may be especially useful for LFIs faced with a high volume of alerts produced by automated TM systems.
2.6. Outcomes Analysis and Management Information Systems Reporting
LFIs should document and track TM outputs in order to identify and address any technical or operational issues and understand key risks or trends over time. Irregularities in TM system performance, including significant changes in the productivity of TM rules over time, may be indicative of underlying data quality or data integrity issues or of the need to recalibrate rule thresholds or parameters. Identified data quality or integrity issues should be reported back to designated data or owners, and apparent rule calibration issues (such as unproductive rules or those producing excessive volumes of false positive alerts) should be reported back to model owners for tuning and optimization. Where TM outcomes analysis reveals that certain transaction types or patterns are repeatedly flagged by the TM system and then consistently cleared as false positives by TM investigators, the LFI may consider employing a risk-based suppression logic or other “whitelisting” process to prevent the generation of alerts on activity repeatedly deemed not to be suspicious. Such methods, however, should not be applied to higher-risk customer or transaction types and should be carefully monitored and subject to periodic and event-driven testing, tuning, and validation, as described below.
In addition, LFIs should ensure that senior management is regularly updated on the performance and output of their TM program, including through the provision of metrics, trends, and other MIS reporting generated by TM systems or produced by TM alert review and investigation teams. Such reporting may include an analysis of the number of alerts produced by each TM rule and the proportion of such alerts that are cleared as false positives, that require further investigation, and that ultimately result in the filing of an STR/SAR. TM-related reporting and analysis should feed back into an LFI’s financial crimes risk assessment, and LFI management should use this information to ensure that the institution’s customers and transaction remain within the LFI’s risk appetite and that activity exceeding its risk appetite is addressed through appropriate risk mitigation measures, including but not limited to the use of account- or customer-based risk markers and/or activity, product, or service restrictions.
2.7. Post-Implementation Testing, Tuning, and Validation
On a periodic basis and in the event of material system output or operational irregularities, LFIs should reassess the functionality of TM systems and processes, including the continued relevancy of detection scenarios and assumptions and the calibration of rule threshold values and parameters. As with pre-implementation testing, post-implementation testing should include checks for system integration, data quality, and operational functionality, and should additionally include back-testing of TM rules to ensure that they remain current and effective in targeting riskier transactions and activity. Any proposed tuning or adjustment to TM rules, particularly material adjustments, should be subject to pre-implementation testing using sample or historical data to ensure the proper functioning of the new or revised rules, and should be reflected in updated TM documentation.
TM model testing and validation should be performed by individuals with sufficient expertise and appropriate level of independence from the model’s development and implementation. Generally, validation should be done by people who are not responsible for the development or use of the TM model and do not have a stake in whether a model is determined to be valid. Independence may be supported by the separation of reporting lines (as where model validation is performed by an internal audit department as part of independent testing of the AML/CFT program) or by the engagement of an external party not responsible for model development or use. As a practical matter, some validation work may be most effectively done by model developers and users; it is essential, however, that such validation work be subject to critical review by an independent party, who should conduct additional activities to ensure proper validation. All model validation activities and identified issues should be clearly documented, and management should take prompt action to address model issues.
3. Sanctions Screening
As per Article 21.2 of Cabinet Decision 74, LFIs are required to perform regular searches against applicable sanctions lists of their customer databases, parties to any transactions, potential customers, beneficial owners, and persons and organizations with which the LFI has a direct or indirect relationship, as well as continuous searches of their customer database before conducting any transaction or entering into a business relationship with any person. Sanctions screening systems and processes are essential, but are also only as effective as the customer and transactional information used when comparing against applicable sanctions lists. Therefore, effectiveness depends critically on the completeness and accuracy of information obtained through the application of CDD/KYC measures and contained in payment instructions and other transactional data fields.
Sanctions compliance personnel should escalate for priority remediation identified omissions or inaccuracies in relevant customer or beneficial ownership information, as well as gaps or data quality issues in required transaction or payment message fields. On a risk basis, LFIs should perform sample testing of payment messages to ensure proper usage of message types and compliance with payment transparency requirements.
An effective sanctions screening program consists of the following core elements:
• A well-calibrated risk-based framework: The risks LFIs face are dynamic and the transactions they carry out may be varied and high in volume. LFIs should therefore review and enhance their sanctions screening frameworks regularly and upon the occurrence of specified “trigger events,” such as material changes in the LFI’s business or risk profile or its legal and regulatory environment, to ensure that they remain tailored to the institution’s financial crime risks.
• Robust training and risk awareness: To ensure proper functioning and implementation of their sanctions screening programs, LFIs should ensure that personnel with sanctions screening responsibilities have adequate experience and expertise and receive role-specific training on the institution’s sanctions screening policies, procedures, and risks.
• Meaningful integration into the sanctions program: LFIs should ensure that their sanctions screening systems and frameworks reinforce, and are reinforced by, the wider sanctions control environment of which they are a part. An effective sanctions screening program depends on the quality and completeness of data drawn from the LFI’s customer and transactional systems and databases. In tandem, the outcomes of sanctions screening should inform the LFI’s understanding and management of its financial crime risks, including by prompting off-cycle customer reviews and the application of enhanced scrutiny or additional controls to higher-risk customers or transactions, as warranted.
• Active oversight: The LFIs’ board and senior management should take an active role in overseeing the performance of their sanctions screening programs and driving the ongoing enhancement of sanctions screening systems on the basis of the institution’s risks. Where the outcomes of sanctions screening are compromised by factors such as inappropriate calibration, process inefficiencies, staff issues, or system failures, it is necessary that the board (or a board-designated committee) and senior management be made aware of these issues in a timely manner so as to ensure that they are promptly and adequately remediated. The board and senior management should also communicate clear risk appetites within their institutions and set a strong tone from the top that the implementation of targeted financial sanctions is a priority. A quality assurance process should also play a crucial part in the sanctions screening program, by validating the review from accuracy and detail perspective.
3.1. Risk Assessment
An LFI’s risk assessment is a critical tool for ensuring that the institution has a complete, accurate, and up-to-date understanding of the sanctions risks to which their institution may be exposed, and for facilitating a risk-based approach to sanctions compliance. In the context of targeted financial sanctions, the risk-based approach cannot provide a justification for failing to apply sanctions-related controls, including sanctions screening, to all customer relationships and transactions, as defined below, which is a minimum legal requirement for all LFIs. Rather, the risk-based approach should be utilized by LFIs to apply additional or more rigorous controls—above the minimum legal requirement—to areas of heightened sanctions risk.
The LFI’s risk assessment should include, at a minimum, an assessment of the customers, products and services, delivery channels, and geographies through which the LFI is most likely to engage, directly or indirectly, with sanctioned persons, parties, countries, or regions, as well as the strength of the controls currently in place to mitigate sanctions risks. The risk assessment should be updated at periodic intervals (at least annually or otherwise as appropriate and justified by the required circumstances) and also upon the occurrence of “trigger events,” such as material changes in the LFI’s business or risk profile or its legal and regulatory environment.
3.2. Risk-Based Deployment of Sanctions Screening Controls
Sanctions screening can include the manual review of customers and transactions against applicable sanctions lists, as well as the use of automated screening and interdiction software and systems. In all cases, the appropriate method of sanctions screening and the screening criteria employed should be appropriately calibrated to the sanctions risks presented by the institution’s customers, products and services, delivery channels, and geographic exposure, and may therefore vary across an LFI’s business lines or units, where applicable. Areas of heightened risk may require additional sanctions-related due diligence, more frequent or more intensive manual reviews of customers, counterparties, and their transactions, enhanced monitoring for transactions or behavior designed to evade sanctions controls, or the specialized training for sanctions compliance personnel in high-risk roles.
Sanctions screening controls should also be calibrated to the size, nature, and complexity of each institution. LFIs with a larger scale of operations are expected to have in place automated systems capable of handling the risks from an increased volume and variance of transactions. While smaller LFIs may rely on sanctions screening systems that are less automated, they should also still ensure that these are appropriately executed to address the risks from their day-to-day transactional activity, as well as fully automated for the update of any changes to the UN Consolidated List and the Local Terrorist List.
Examples of automated tools include automated name screening tools that compare customer databases against applicable sanctions lists, live payment and other transaction filtering tools that screen payment message and transaction data against applicable sanctions lists prior to execution, and text analytics tools that automatically convert paper documentation into electronic data that can then be screened against applicable sanctions lists.
Examples of manual tools include manual reporting and escalations of potentially sanctions-related activity by LFI employees (including especially customer relationship managers and other business-line personnel), manual reviews of document-based transactions (such as documentary trade finance transactions or loans), and periodic or event-based CDD reviews.
Particularly where purely manual processes are employed, LFIs should implement appropriate training on sanctions screening policies and procedures to ensure that personnel adhere to the internal processes for identification and referral of potentially sanctions-related activity. LFIs should be aware of all methods of identification and should ensure that their sanctions screening program includes processes to facilitate the transfer of internal referrals to appropriate personnel for searches against applicable lists. Regardless of whether automated or manual processes (or a combination of the two) are used to perform sanctions screening, the onus is on the LFI to demonstrate that the screening program is effective and appropriately risk based.
3.3. Data Identification and Management
LFIs should have in place adequate processes to ensure that customer and transactional data feeding into their sanctions screening program (whether using manual or automated processes, or both) meets established data quality standards, that data is subject to testing and validation at risk-based intervals, and that identified data quality issues are remediated in a timely manner.
As an initial matter, LFIs should identify and document all data sources that serve as inputs into their sanctions screening program, including applicable customer databases and core banking or other transaction processing systems. Source system documentation should include the identification of a system owner or primary party responsible for overseeing the quality of source data and addressing identified data issues. Where automated sanctions screening systems are used, LFIs should institute data extraction and loading processes to ensure a complete and accurate transfer of data from its source to sanctions screening systems. LFIs should also ensure that staff’s access rights to both source systems and sanctions screening systems are commensurate with their roles and responsibilities, so as to ensure that relevant staff can perform their duties effectively and that access is not extended to unauthorized persons or those no longer requiring system access.
Both prior to the initial deployment of a sanctions screening system or process and at risk-based intervals thereafter, LFIs should test and validate the integrity, accuracy, and quality of data to ensure that accurate and complete data is flowing into their sanctions screening program. Data testing and validation should typically occur at minimum every 12 to 18 months, as appropriate based on the LFI’s risk profile, and the frequency of such activities should be clearly mandated and documented in the LFI’s policies and procedures. Such testing can include data integrity checks to ensure that data is being completely and accurately captured in source systems and transmitted to sanctions screening systems, as well as the reconciliation of transaction codes across core banking and sanctions screening systems. Testing may also utilize quantitative data quality standards or benchmarks to track data quality over time and specify a threshold or range beyond which data irregularities or other data quality issues shall require corrective action.
In addition, LFIs should put in place appropriate detection controls, such as the analysis of trends observable through MIS data and the generation of exception reports, to identify abnormally functioning sanctions screening logic and ensure that any such irregularities caused by data integrity or other data quality issues are appropriately diagnosed and remediated. Where appropriate, a root cause analysis should be performed, and any findings and recommended remedial actions should be escalated to appropriate senior management to address the underlying issue in a timely manner.
3.4. Screening Program Design and Pre-Implementation Testing
The process of screening information collected and maintained by an LFI on the parties it does business with and their related parties is referred to as “name screening”. The concept encompasses any data set within the LFI’s operations, separate from its transaction records, that may present a relevant sanctions risk indicator or be conducive to detection through screening on a periodic basis and prior to entering into a customer relationship. The process of screening a movement of value—including funds, goods, or assets— out of, into, or through the LFI between parties or accounts is referred to as “transaction screening”.
Where automated systems are employed, LFIs should perform pre-implementation testing of sanctions screening systems, using historical transaction data as appropriate. Such testing should include system integration testing to ensure compatibility of the sanctions screening system with source systems and other sanctions compliance infrastructure and user acceptance testing to ensure that the system performs as anticipated in the operating environment. Material data mapping, transaction coding, and other data quality issues, as well as irregularities in sanctions screening model performance and outputs, identified through pre-implementation testing should be prioritized for remediation and subject to re-testing prior to the deployment of a sanctions screening system.
The following sections provide additional detail about system design and pre-implementation testing as these relate specifically to name screening and transaction screening processes respectively.
3.4.1. Name Screening
As per the Executive Office’s Guidance on TFS for Financial Institutions and Designated Non-financial Business and Professions,5 name screening (whether automated or manual) must be performed prior to the onboarding of a customer and/or the facilitation of an occasional transaction and on an ongoing basis (at least daily) thereafter. As indicated above, name screening encompasses any data set within the LFI’s operations, separate from its transaction records, that may present a relevant sanctions risk indicator or be conducive to detection through screening on a periodic basis and prior to entering into a customer relationship.
Data relevant for name screening may include:
• Customer data, including the names and addresses of existing or prospective customers, their beneficial owners, and other related or connected parties whose information is collected pursuant to risk-based due diligence procedures;
• Employee data, including employee names and addresses;
• Third-party service provider data, including the names, addresses, and beneficial owners of an LFI’s vendors, landlords, and tenants, as applicable;
• International Securities Identification Numbers (“ISINs”) and other sanctions-relevant identifying features of assets held in custody by the LFI; and
• Recipients of the LFI’s corporate donations or sponsorship.
Not all data elements within an LFI’s records are relevant for sanctions screening. When determining what reference data should be screened, an LFI should identify the data within its operations and records that is relevant to sanctions risk, determine how it is relevant, ensure it is conducive to effective screening, and differentiate it from data that is not relevant or suitable to screening. For example, the names of individuals and entities with whom the LFI has a relationship are relevant for screening against name-based sanctions lists but not for geographic (region- or country-based) sanctions programs. Likewise, while the data contained in the addresses of such individuals and entities may not be directly relevant for screening against name-based sanctions lists, this data may assist in differentiating a true name match from a false name match when reviewing apparent name screening hits.
An LFI should also define other data elements (such as date of birth, nationality, and place of birth) that may be relevant for sanctions screening in some situations but not others. Date of birth, for example, is relevant as a distinguishing factor to assess a potential or a true match from a false match on an individual and might be used for screening in combination with another attribute, such as a name. In each case, LFIs should weigh up the relative incremental value of screening the data element against the reliability of the data and whether an alert against the data will meaningfully assist in detecting or preventing a sanctions risk that would not be reasonably detected through other controls, or by screening different data attributes. The screening criteria used by LFIs to identify name variations and misspellings should be based on the level of sanctions risk associated with the particular product or type of transaction. For example, in a higher-risk area with a high volume of transactions, the LFI’s interdiction software should be able to identify close name derivations for review.
An LFI’s reference data is typically maintained in electronic files and is most effective when screened through an automated process and repeated at defined intervals. The use of manual screening can be considered when the risk is sufficiently low and where the reference data cannot be sourced reliably, either electronically or in a format necessary for automated screening. For example, if an LFI has identified only a small population of names requiring screening, it may choose to forego investing in an automated screening system and instead manually input these names into an online screening filter.
5 Available at: https://www.uaeiec.gov.ae/en-us/un-page#.
3.4.2. Transaction Screening
LFIs should screen all payments prior to completing the transaction (also referred to as “real-time” screening), utilizing all transaction records necessary to the movement of value between parties and at a point in the transaction where detection of a sanctions risk is actionable to prevent a violation. The LFI should then identify which attributes within those records are relevant for sanctions screening and the context in which they become relevant. As with name screening, names of parties involved in a transaction are relevant for list-based sanctions programs, whereas addresses are more relevant to screening against geographic sanctions programs but can be used as identifying information to help distinguish a potential or true match from a false match under a list-based program. Other data elements, such as bank identification codes, may be relevant for both list-based and geographic sanctions programs.
Some data elements are more relevant for sanctions screening purposes when found in combination with other attributes or references. For example, detection of sectoral sanctions risk typically requires detection of multiple factors, such as those where both the targeted parties and the prohibited activities are involved. Where automated controls alone may not be capable of detecting both factors simultaneously, manual review of the associated activity may be required alongside review to confirm a true match to applicable sanctions lists. In addition, certain data elements offer little or no risk mitigation through screening, for example, amounts, dates, and transaction reference numbers have no relevance from a screening perspective, although they may be relevant for TM or other risk management purposes.
Data relevant for transaction screening may include:
• The parties involved in a transaction, including the originator and beneficiary;
• Agents, intermediaries, and financial institutions involved in a transaction;
• Bank names, Bank Identifier Codes (“BICs”), and other routing codes;
• Free text fields, such as payment reference information or the stated purpose of the payment in Field 70 of a SWIFT message;
• ISINs or other risk-relevant product identifiers, including those that relate to sectoral sanctions identifications within securities-related transactions, as applicable;
• Trade finance documentation, including any:
o Importers and exporters, manufacturers, drawees, drawers, notify parties, and signatories;
o Shipping companies, vessel names and International Maritime Organization (IMO) numbers, names of parties associated with the vessel (including ship owners, charterers, and captains), and freight forwarders;
o Facilitators, such as insurance companies, agents, and brokers; and
o Financial institutions, including issuing, advising, confirming, negotiating, claiming, collecting, reimbursing, and guarantor banks.
• Geographic details, including:
o Addresses, countries, cities, towns, regions, ports, and airports (e.g., as contained within SWIFT Fields 50 and 59 or acquired through vessel tracking inquiries);
o Phone or fax numbers and web addresses, insofar as these contain geographic or other relevant details;
o Place of taking in charge, receipt, dispatch, delivery, or final destination;
o Country of origin, destination, and transshipment of goods or services; and
o Airport of departure or destination.
Transaction screening should be performed at a point in time where a transaction can be stopped and before a potential violation occurs. This typically occurs at a number of points in the lifecycle of a transaction, but certainly prior to executing any commitment to move funds. Particular attention should be directed to any points within the transactional process where relevant information could be changed, modified, or removed in order to undermine screening controls.
Transactional records are typically found in large volumes and within business processes predicated on speed of execution. These transaction types are generally in electronic form and conducive to systemic, automated screening. Some transaction types, however, still rely on documentation in various formats and varying methods of presentation. LFIs may employ text analytics tools such as optical character recognition (“OCR”) that automatically convert paper documentation into electronic data that can then be screened against applicable sanctions lists, but some paper-based transactions, such as documentary trade finance transactions, may require manual screening processes, where relevant information is physically added into a system for screening. OCR requires quality assurance validation to ensure the information has been captured fully and accurately. Certain paper-based transactions, such as paper cheque clearing, where the volumes can be high and the manual screening process creates high rates of errors, may rely on controls other than screening, such as CDD/KYC processes, where the sanctions risks for the product are assessed as being low.
3.5. List Management
Under Article 21.2 of Cabinet Decision 74, LFIs’ sanctions screening lists must include all names on lists issued by the UNSC and its relevant Committees (UN Consolidated List) or by the UAE Cabinet (Local Terrorist List). LFIs’ sanctions screening processes should also include searches for entities that are not themselves listed but that are owned or controlled mainly or fully by a listed person (also referred to as “shadow listed persons”). LFIs cannot conduct transactions with shadow listed persons and must freeze any funds or assets of a shadow listed person that they may hold as per Article 15 of Cabinet Decision 74. Although shadow designated persons, by their very nature, are not listed by government authorities, LFIs should develop internal lists of such persons based on their own due diligence and consideration of external sources, such as adverse media reporting. LFIs should include such a list, together with any other internal lists (such as lists of customers exited for financial crime concerns) in its sanctions screening systems and processes.
Given the dynamic nature of targeted financial sanctions, LFIs should establish and implement sanctions list management procedures that enable the institution’s sanctions screening program to adjust rapidly to changes published by sanctions authorities. The following considerations are relevant to effective list management, and each should be documented and reviewed on a regular basis, to ensure that the LFI’s chosen approach remains in line with its risk appetite and in compliance with applicable legal requirements:
• List selection: The LFI should determine which sanctions lists are relevant for screening. Lists must include, at a minimum, all names on the UN Consolidated List and the Local Terrorist List, but may also include other jurisdictional lists as well as internal lists of persons known to have a sanctions nexus, lists of geographic terms (such as cities, regions, and ports), banking terms (such as BICs), and lists of prohibited goods or prohibited securities, where applicable. Although lists issues by the UNSC or by the UAE Cabinet must be employed in the screening of all customers and transactions, as outlined above, other lists may be employed on a risk basis. For example, screening against lists of prohibited goods may be limited to the context of trade finance transactions, whereas such transactions likely would not need to be screened against sanctioned securities.
• Sourcing of lists: The LFI should determine which lists are to be generated internally and which lists are best sourced from external vendors, and the processes for generating and implementing such lists.
• List maintenance: The LFI should determine the processes for adding and removing lists or entries on internal lists, where screening is no longer required or where the result is within the institution’s risk appetite. The LFI should identify and implement appropriate controls to ensure that lists remain up to date and that only appropriate individuals can add or remove lists or list entries.
• Data enhancement: The LFI should determine whether certain list entries should be modified or enhanced based on additional information.
• Whitelisting: The LFI may consider establishing and maintaining a “white list” of customer names or other data elements that have already been flagged and cleared through thorough due diligence by the LFI as false positives. These “white lists” may be used to improve the process related to screening by leveraging the results of past due diligence and reducing the number of false positives. While the LFI should not overly rely on such a list, and must diligently and continuously screen customers and transactions in case they are implicated in the updated UN Consolidated List and Local Terrorist List, the use of such a “white list” may assist the LFI in expediting the dispositioning in case of repeated false positive matches. LFIs should have documented procedures to managing and periodically reviewing and updating those “white lists” to account for the possibility that persons on a whitelist may later become sanctioned persons. Where automated screening tools are employed, the LFI should determine the management of rules for automatically eliminating potential hits caused by the interaction of certain list terms and frequently encountered data. Where manual screening processes are employed, the LFI should establish a process for manually reviewing potential hits against the whitelist.
• Geographic scope of application: Where the LFI has operations in multiple jurisdictions, the LFI should determine which lists should be screened in all jurisdictions of an LFI’s operations and which, if any, could be screened only within a certain jurisdiction or several jurisdictions.
• Exact matching versus “fuzzy logic”: The LFI should determine which lists should be deployed within the screening filter on an exact match basis, and which should use fuzzy matching (i.e., an algorithm-based technique to match one name or other string of words where the content of the information being screened is not identical—but its spelling, pattern, or sound is a close match—to the contents on a list used for screening).
• Frequency of screening: The LFI should determine the frequency or the triggers for static data screening, so as to account for additions to lists and changes in customer data.
List management procedures should be documented and subject to periodic review to ensure that list management practices remain aligned to the LFI’s risk profile and risk appetite.
3.6. Outcomes Analysis and Management Information Systems Reporting
LFIs should document and track sanctions screening outputs in order to identify and address any technical or operational issues and understand key risks or trends over time. Irregularities in sanctions screening system performance, including significant changes in the volume of apparent matches to sanctions lists over time, may be indicative of underlying data quality or data integrity issues or of the need to recalibrate sanctions screening search logic. Identified data quality or integrity issues should be reported back to designated data owners, and apparent screening logic issues should be reported back to model owners for tuning and optimization.
In addition, LFIs should ensure that senior management is regularly updated on the performance and output of their sanctions screening program, including through the provision of metrics, trends, and other MIS reporting generated by sanctions screening systems or produced by sanctions screening alert review and investigation teams. Such reporting may include an analysis of the number and type of screening hits and the proportion of apparent matches that are cleared as false positives compared to those that are confirmed as potential or true matches. Sanctions screening-related reporting and analysis should feed back into an LFI’s financial crimes risk assessment, and LFI management should use this information to ensure that the institution’s customers and transaction remain within the LFI’s risk appetite and that activity exceeding its risk appetite is addressed through appropriate risk mitigation measures, up to and including account activity restrictions and customer exit.
3.7. Post-Implementation Testing, Tuning, and Validation
On a periodic basis and in the event of material system output or operational irregularities, LFIs should reassess the functionality of sanctions screening systems and processes, including threshold settings, screening rules, and the accuracy and completeness of data used in the screening process. Any proposed material adjustments to sanctions screening search logic should be subject to pre-implementation testing using sample or historical data to ensure the proper functioning of the new or revised logic, and reflected in updated sanctions screening documentation.
Sanctions screening model testing and validation should be performed by individuals with sufficient expertise and appropriate level of independence from the model’s development and implementation. Generally, validation should be done by people who are not responsible for the development or use of the sanctions screening model and do not have a stake in whether a model is determined to be valid. Independence may be supported by the separation of reporting lines (as where model validation is performed by an internal audit department as part of independent testing of the sanctions compliance program) or by the engagement of an external party not responsible for model development or use. As a practical matter, some validation work may be most effectively done by model developers and users; it is essential, however, that such validation work be subject to critical review by an independent party, who should conduct additional activities to ensure proper validation. All model validation activities and identified issues should be clearly documented, and management should take prompt action to address model issues.
4. Program Governance and Oversight
The following sections outline program governance expectations relating to TM and sanctions screening systems and processes.
4.1. Oversight, Management Reporting, and Auditing
The LFI’s board of directors and senior management should exercise active oversight of the institution’s key financial crimes risks and the controls in place to mitigate those risks. The board (or a board-designated committee) and senior management should receive regular reports on the institution’s key risks and trends and the overall performance of AML/CFT and sanctions controls, and should review the institution’s financial crimes risk assessment, any AML/CFT and sanctions audit and regulatory reports, and the institution’s written AML/CFT and sanctions program. The AML/CFT and sanctions program should be subject to senior management approval, and the board and senior management should ensure that clear, current, and appropriate policies and procedures are put in place and that there are effective TM and sanctions screening systems supported by adequate internal expertise and resources.
TM and sanctions screening functions should be given clear and distinct responsibilities for their respective tasks in the TM and sanctions screening process chain (e.g., for alert handling and the filing of STRs/SARs). Additionally, as detailed above, LFIs are expected to implement effective reporting systems, to include quantitative MIS report as well as qualitative analysis of key risks and trends as appropriate, to ensure that their board and senior management are updated on key financial crimes risks in a timely manner. Any data quality or system functionality or output issues should be documented and tracked, and the status of remedial actions should be reported regularly to senior management.
TM and sanctions screening programs should be subject to independent testing by internal or external auditors with sufficient technological expertise and understanding of ML/TF/PF and sanctions risks and requirements. The LFI’s independent testing function (whether internal or external) should ensure adequate TM and sanctions screening coverage of the LFI’s customers, products, services, delivery channels, and geographies and may perform model testing and validation, as detailed above, as part of its AML/CFT and sanctions independent testing plan and methodology; otherwise, model testing and validation should be performed at periodic, risk-based intervals by a qualified and independent third party.
4.2. Use of Vendors and Other Third Parties
LFIs may use externally provided TM or sanctions screening services and other third-party providers to fulfil their legal and regulatory obligations to monitor and screen their customers and transactions. However, LFIs are ultimately responsible for complying with AML/CFT and sanctions requirements, even if they choose to use third-party models to assist with their compliance obligations.
The selection of third-party system or service should be guided by the LFI’s size, geographic footprint, business and technology environments, and financial crimes risks, as well as functional requirements, such as the volume of data to be screened, the degree to which TM and sanctions screening processes will be centralized across business lines within the LFI, the nature of existing data integrity processes, and the ability of the application to integrate effectively within an LFI’s technological infrastructure. When selecting a vendor, LFIs should require the vendor to provide developmental evidence explaining the product components, design, and intended use, so as to determine whether the model is appropriate for the LFI’s products, exposures, and risks. Vendors should provide appropriate testing results that show their product works as expected. They should also clearly indicate the model’s limitations and assumptions and where the product’s use may be problematic. LFIs should expect vendors to conduct ongoing performance monitoring and outcomes analysis, with disclosure to their clients, and to make appropriate modifications and updates over time.
LFIs are expected to validate their own use of vendor products. External models may not allow full access to computer coding and implementation details, so the LFI may have to rely more on sensitivity analysis and benchmarking. Vendor models are often designed to provide a range of capabilities and so may need to be customized by an LFI for its particular circumstances. An LFI’s customization choices should be documented and justified as part of validation. If vendors provide input data or assumptions, or use them to build models, their relevance for the LFI’s situation should be assessed. LFIs should obtain information regarding the data used to develop the model and assess the extent to which that data is representative of the LFI’s situation. The LFI also should conduct ongoing monitoring and outcomes analysis of vendor model performance using the LFI’s own outcomes. Systematic procedures for validation help the LFI to understand the vendor product and its capabilities, applicability, and limitations. Such detailed knowledge is necessary for basic controls of an LFI’s operations. It is also very important for the LFI to have as much knowledge in-house as possible, in case the vendor or the LFI terminates the contract for any reason, or if the vendor is no longer in business. LFIs should have contingency plans for instances when the vendor model is no longer available or cannot be supported by the vendor.
4.3. Role-Specific Training
LFIs should ensure that personnel responsible for performing TM and sanctions screening roles receive training that covers key financial crimes risks faced by the institution (such as common ML/TF/PF or sanctions evasion typologies), complex and higher-risk customer and transaction types relevant to TM and sanctions screening processes, applicable legal and regulatory requirements, and internal policies, procedures, and processes. Training should be tailored to each individual’s specific responsibilities and include desktop procedures or instructions for the use of any TM or sanctions screening systems or other technology relevant to the individual’s role.
An LFI’s TM and sanctions screening training should be based on an assessment of the institution’s training needs, incorporated into wider AML/CFT and sanctions training plans and programs, and subject to completion tracking and escalation procedures to ensure timely completion of mandatory training by all relevant personnel. Mandatory training should also be extended to any staff located abroad whose responsibilities cover accounts booked in or activity flowing into, out of, or through the UAE.
4.4. Record Keeping
According to Article 16 of the AML-CFT Law and Article 24 of the AML-CFT Decision, LFIs must maintain detailed records associated with their ML/FT risk assessment and mitigation measures as well as records, documents, data and statistics for all financial transactions, all records obtained through CDD measures for both the originators and the beneficiaries, account files and business correspondence, copies of personal identification documents, including STRs/SARs and results of any analysis performed. LFIs must maintain the records in an organized manner so as to permit data analysis and the tracking of financial transactions.
Records should be sufficient to permit reconstruction of individual transactions so as to provide, if necessary, evidence for prosecution of criminal activity. LFIs must make the records available to the competent authorities immediately upon request.
The statutory retention period for all records is at least five (5) years, from the date of completion of the transaction or termination of the business relationship with the customer, or from the date of completion of the inspection by the CBUAE, or from the date of issuance of a final judgment of the competent judicial authorities, or liquidation, dissolution, or other form of termination of a legal person or arrangement, all depending on the circumstances.
Annex 1. Synopsis of the Guidance
Purpose of this Guidance Purpose The purpose of this Guide is to assist the understanding and effective performance by CBUAE licensed financial institutions (LFIs) of their statutory obligations under the legal and regulatory framework in force in the UAE relating to the design, implementation, and maintenance of effective transaction monitoring and sanctions screening programs. Applicability This Guidance applies to all natural and legal persons, which are licensed and/or supervised by the CBUAE, in the following categories: national banks, branches of foreign banks, exchange houses, finance companies and other LFIs as well as insurance companies. Transaction Monitoring Risk Assessment An LFI's risk assessment should include, at a minimum, an assessment of the customers, products and services, delivery channels, and geographic exposure presenting the greatest money laundering ("ML"), terrorist financing ("TF"), and proliferation financing ("PF") risks, as well as the strength of the controls currently in place to mitigate these risks. The risk assessment should be updated at periodic intervals (at least annually or otherwise as appropriate and justified by the required circumstances) and also upon the occurrence of "trigger events" such as material changes in the LFI's business or risk profile or the legal and regulatory environment. Risk-Based Deployment of TM Controls In all cases, the type and degree of monitoring should appropriately match the ML/TF/PF risks of the institution's customers, products and services, delivery channels, and geographic exposure, and may therefore vary across an LFI's business lines or units, where applicable. TM programs should also be calibrated to the size, nature, and complexity of each institution. Where practicable and on a risk basis, LFIs should monitor transactions at the customer or relationship level, including across financial groups, and not only on an individual account basis, so as to obtain a complete view of a customer's transaction profile. Data Identification and Management LFIs should identify and document all data sources that serve as inputs into their TM program. LFIs should test and validate the integrity, accuracy, and quality of data to ensure that accurate and complete data is flowing into their TM program. In addition, LFIs should put in place appropriate detection controls, such as the analysis of trends through management information systems (MIS) data and the generation of exception reports, to identify abnormally functioning TM rules or scenarios and ensure they are appropriately diagnosed and remediated. Rule Definition and Pre-lmplementation Testing LFIs should employ TM detection rules or scenarios that are designed to identify potentially suspicious or illegal transactions and elevate them for further review and investigation, as warranted. To this end, LFIs should: - Perform a typology assessment to design appropriate rule- or scenario-based automated monitoring capabilities and processes;
- Perform risk-based customer and product segmentation, so that rule parameters and thresholds are appropriately calibrated;
- Consider employ statistical tools or methods such as above-the-line and below-the-line testing, to better fine-tune their calibrations and reduce the volume of false-positive alerts; and
- Perform pre-implementation testing of TM rules and systems to ensure compatibility of the TM system with source systems and other AML/CFT compliance infrastructure to ensure that it performs as anticipated in the operating environment.
Alert Scoring and Prioritization LFIs may consider assigning risk-weighted scores to TM alerts in order to prioritize higher-risk alerts for expedited review. LFIs with larger TM alert review and investigation teams may likewise opt to allocate higher-scoring alerts to more senior investigators or those with specialized expertise in certain risk areas. Outcomes Analysis and MIS Reporting LFIs should document and track TM outputs in order to identify and address any technical or operational issues and understand key risks or trends over time. In addition, LFIs should ensure that senior management is regularly updated on the performance and output of their TM program, including through the provision of metrics, trends, and other MIS reporting. Post-Implementation Testing, Tuning, and Validation On a periodic and event-driven basis, LFIs should reassess the functionality of TM systems and processes, including the continued relevancy of detection scenarios and assumptions and the calibration of rule threshold values and parameters. TM model testing and validation should be performed by individuals with sufficient expertise and appropriate level of independence from the model's development and implementation. All model validation activities and identified issues should be clearly documented, and management should take prompt action to address model issues. Sanctions Screening Risk Assessment The LFI's risk assessment should include, at a minimum, an assessment of the customers, products and services, delivery channels, and geographies presenting the greatest sanctions risks, as well as the strength of the controls in place to mitigate these risks. The risk assessment should be updated at periodic intervals (at least annually or otherwise as appropriate and justified by the required circumstances) and also upon the occurrence of "trigger events," such as material changes in the LFI's business or risk profile or its legal and regulatory environment. Risk-Based Deployment of Sanctions Screening Controls Sanctions screening programs should be appropriately calibrated to the sanctions risks presented by the institution's customers, products and services, delivery channels, and geographic exposure and may vary across an LFI's business lines or units, where applicable. Sanctions screening controls should also be calibrated to the size, nature, and complexity of each institution. LFIs should apply additional or more rigorous sanctions controls—such as enhanced customer or transactional due diligence, increased monitoring for sanctions evasion, and specialized training for personnel in high-risk roles—to areas of heightened sanctions risk. Data Identification and Management LFIs should identify and document all data sources that serve as inputs into their sanctions screening program and test and validate the integrity, accuracy, and quality of data flowing into their sanctions screening program. In addition, LFIs should put in place appropriate detection controls, such as MIS trends analysis and exception reports, to identify abnormally functioning screening logic to ensure such irregularities are appropriately diagnosed and remediated. Screening Program Design and Pre-Implementation Testing LFIs should perform pre-implementation testing of screening systems to ensure compatibility with source systems and other sanctions compliance infrastructure to ensure it performs as anticipated in the operating environment. Name screening (whether automated or manual) must be performed prior to the onboarding of a customer and/or the facilitation of an occasional transaction and on an ongoing basis (at least daily) thereafter. LFIs should screen all payments prior to completing the transaction (also referred to as "real-time" screening), utilizing all transaction records necessary to the movement of value between parties. Transaction screening should be performed at a point in time where a transaction can be stopped and before a potential violation occurs. List Management LFIs should establish and implement sanctions list management procedures that enable the institution's sanctions screening program to adjust rapidly to changes published by sanctions authorities. List management procedures should be documented and subject to periodic review to ensure that list management practices remain aligned to the LFI's risk profile and risk appetite. Outcomes Analysis and MIS Reporting LFIs should document and track screening outputs in order to identify and address any technical or operational issues and understand key risks or trends over time. In addition, LFIs should ensure that senior management is regularly updated on the performance and output of their screening program, including through the provision of metrics, trends, and other MIS reporting. Post-Implementation Testing, Tuning, and Validation On a periodic and event-driven basis, LFIs should reassess the functionality of sanctions screening systems and processes, including threshold settings, screening rules, and the accuracy and completeness of data used in the screening process. Sanctions screening model testing and validation should be performed by individuals with sufficient expertise and level of independence. All model validation activities and identified issues should be clearly documented, and management should take prompt action to address model issues. Program Governance and Oversight Oversight, Management Reporting, and Auditing LFIs'board (or board-designated committee) and senior management should receive regular reports on the key risks and trends and overall performance of the AML/CFT and sanctions controls. TM and sanctions screening functions should be given clear and distinct responsibilities for their tasks. TM and sanctions screening programs should be subject to independent testing by internal or external auditors. Use of Vendors and Other Third Parties LFIs may use externally provided TM or sanctions screening services. However, LFIs are ultimately responsible for complying with AML/CFT and sanctions requirements. Systematic procedures for validation help the LFI to understand the vendor product and its capabilities, applicability, and limitations. Role-Specific Training LFIs should ensure that TM and sanctions screening personnel receive role-specific training that covers key financial crimes risks, complex and higher-risk customer and transaction types, applicable legal and regulatory requirements, internal policies, procedures, and processes. Guidance for Licensed Financial Institutions Providing Services to Cash-intensive Businesses
Effective from 27/9/20211. Introduction
1.1 Purpose
Article 44.11 of the Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations charges Supervisory Authorities with “providing Financial Institutions…with guidelines and feedback to enhance the effectiveness of implementation of the Crime-combatting measures.”
The purpose of this Guidance is to assist the understanding and effective performance by the United Arab Emirates Central Bank’s (“CBUAE”) licensed financial institutions (“LFIs”) of their statutory obligations under the legal and regulatory framework in force in the UAE. It should be read in conjunction with the CBUAE's Procedures for Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations (issued by Notice No. 74/2019 dated 19/06/2019) and Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations for Financial Institutions (issued by Notice 79/2019 dated 27/06/2019) and any amendments or updates thereof.1 As such, while this Guidance neither constitutes additional legislation or regulation nor replaces or supersedes any legal or regulatory requirements or statutory obligations, it sets out the expectations of the CBUAE for LFIs to be able to demonstrate compliance with these requirements. In the event of a discrepancy between this Guidance and the legal or regulatory frameworks currently in force, the latter will prevail. This Guidance may be supplemented with additional separate guidance materials, such as outreach sessions and thematic reviews conducted by the Central Bank.
Furthermore, this Guidance takes into account standards and guidance issued by the Financial Action Task Force (“FATF”), industry best practices, and red flag indicators. These are not exhaustive and do not set limitations on the measures to be taken by LFIs in order to meet their statutory obligations under the legal and regulatory framework currently in force. As such, LFIs should perform their own assessments of the manner in which they should meet their statutory obligations.
This Guidance comes into effect immediately upon its issuance by the CBUAE with LFIs expected to demonstrate compliance with its requirements within one month from its coming into effect.
1 Available at https://www.centralbank.ae/en/cbuae-amlcft.
1.2 Applicability
Unless otherwise noted, this Guidance applies to all natural and legal persons, which are licensed and/or supervised by the CBUAE, in the following categories:
• National banks, branches of foreign banks, exchange houses, finance companies, payment service providers, registered hawala providers and other LFIs; and • Insurance companies, agencies, and brokers.
1.3 Legal Basis
This Guidance builds upon the provisions of the following laws and regulations:
1.4 Definitions
Bearer Negotiable Instruments: Financial instruments of whatever form, whether in the form of a bearer document, such as: traveler’s cheques; promissory notes and cheques, payment orders, or others. These instruments may either be in bearer form, endorsed without restriction, made out to a fictitious payee, or otherwise in such form that title thereto passes upon delivery; or may be incomplete instruments (including cheques, promissory notes and money orders) signed, but with the payee’s name omitted.
CBUAE Regulations: Any resolution, regulation, circular, rule, instruction, standard or notice issued by the Central Bank.
Cash Couriers: Natural persons who physically transport currency and bearer negotiable instruments on their person or accompanying luggage from one jurisdiction to another.
Cash or Currency: Banknotes and coins that are legal tender in circulation as a medium of exchange.
Cross-Border Transportation of Currency or Bearer Negotiable Instruments: Any in-bound or outbound physical transportation of currency or bearer negotiable instruments from one country to another country. The term includes the following modes of transportation: (1) physical transportation by a natural person, or in that person’s accompanying luggage or vehicle; (2) shipment of currency through containerized cargo; or (3) the mailing of currency or bearer negotiable instruments by a natural or legal person.
Predicate Offense: Any act constituting a felony or misdemeanor under the applicable laws of the UAE whether this act is committed inside or outside the UAE when such act is punishable in both countries.
2. Understanding Risks
2.1 Vulnerabilities of Cash
The FATF’s Mutual Evaluation Report of the UAE issued in April 2020 stated that, as the UAE is a cash-intensive economy and plays an important part in global trade, there are significant risks associated with the cross-border movement of cash and bearer negotiable instruments, including bulk-cash smuggling that is associated with third-party money laundering risks.
As a major medium of exchange in the UAE, cash is particularly vulnerable to abuse by illicit actors to conduct money laundering activities and finance criminal activities. The specific characteristics of cash-anonymity, interchangeability, and transportability—make it an attractive method by illicit actors seeking to conceal the proceeds of crime. Unlike other monetary instruments, such as credit cards or wire transfers, cash holds no record of its source or owner, and can be easily concealed in large quantities upon which it is difficult to trace once spent. Cash transactions are also instantaneous and widely accepted across jurisdictions.
Criminal activity—or a predicate offense—is often cash based. A predicate offense for money laundering is the underlying criminal activity that generates proceeds. Criminals then seek to “launder” these illicit proceeds, which leads to the offense of money laundering. The FATF Recommendations identify “designated categories of offenses”2 as the following:
• Participation in an organized criminal group and racketeering; • Terrorism, including financing of terrorism and illegal organisations; • Trafficking in human beings and migrant smuggling; • Sexual exploitation, including sexual exploitation of children; • Illicit trafficking in narcotic drugs and psychotropic substances; • Illicit arms trafficking; • Illicit trafficking in stolen and other goods; • Corruption and bribery; • Fraud; • Counterfeiting currency; • Counterfeiting and piracy of products; • Environmental crime; • Murder, grievous bodily injury; • Kidnapping, illegal restraint, and hostage-taking; • Robbery or theft; • Smuggling; • Tax crimes; • Extortion, Forgery; • Piracy and • Insider trading and market manipulation. However, as the FATF expects countries to include the above-mentioned list at the minimum, the UAE’s definition of Predicate Offense is broader to include any act constituting a felony or misdemeanor under the applicable laws of the UAE, whether this act is committed inside or outside the UAE when such act is punishable in both countries.
2 Available at https://www.fatf-gafi.org/glossary/d-i/
2.2 Vulnerabilities of Alternatives to Cash
Illicit actors also use various monetary instruments in conjunction with, or as a replacement to, cash. Both bearer negotiable instruments and prepaid cards for instance offer similar benefits to cash, including anonymity and accessibility. They can store large amounts of value in a compact physical size that makes them potentially vulnerable to abuse by illicit actors who use them instead of cash to make physical cross-border transportations of value. Illicit actors seeking to avoid an LFI’s identification and verification requirements can exploit the ease of payment offered by bearer negotiable instruments and prepaid cards for the purpose of moving their proceeds—thus obscuring the origin of the funds—and converting them to payments for other goods or services. This may also include obtaining funds in one jurisdiction and having access to cash withdrawals in another jurisdiction. Additional characteristics and associated vulnerabilities of bearer negotiable instruments and prepaid cards are discussed below.
2.2.1 Bearer Negotiable Instruments
Bearer negotiable instruments are financial instruments of whatever form, whether in the form of a bearer document, such as traveler’s cheques, promissory notes and cheques, payment orders, or other forms that can be attractive to illicit actors as alternatives to cash. Bearer negotiable instruments provide the opportunity to move large amounts of funds in bearer form without the bulkiness of cash. They are transferable documents that provide unconditional guarantees of cash payments either on demand or at a future date. The individual who issues a negotiable instrument is known as the ‘payer’ or ‘issuer,’ and the person who receives a negotiable instrument is known as the ‘bearer’ or ‘payee’.
Bearer negotiable instruments often include the instruction 'pay to the bearer', meaning the bearer would be the person in physical possession of the instrument. The risk, in this scenario, is that the holder is a criminal and/or not the intended payee of the negotiable instrument. Bearer negotiable instruments are also unique in that they can also be easily transferred from one party to another, which effectively obscures the paper trail on the ‘payer’ or ‘issuer’, and enables illicit actors to distance the proceeds of crime from the illegitimate source. LFIs should seek to mitigate these risks by continuing accepting cash and third party cheques as long as the due diligence measures regarding the person presenting the cheque have been duly conducted by the LFI.
2.2.2 Prepaid Cards
Prepaid cards can be used as an alternative to cash in that they provide access to funds that have been paid in advance. Funds can be claimed or transferred through an electronic device, such as through a card, code, electronic serial number, mobile identification number, or personal identification number within either an "open" or "closed" loop system:
• “Open loop” prepaid cards can be used for purchases at any merchant where that brand of the card is accepted and offers access to cash at any automated teller machine (“ATM”) that connects to the affiliated ATM network. Some prepaid cards may be reloaded, allowing the cardholder or third-party (such as an employer) to add value to the card. For example, a travel card can allow cardholders to top up at various locations, including online and at kiosks, and then allows cardholders to utilize the card to purchase local travel as well as goods or services at various participating stores.
• “Closed loop” prepaid cards generally can only be used to buy goods or services from the issuing merchant of the card or a select group of merchants that participate in that specific network. These cards generally do not allow for cash access, although they can often be re-sold through third-party websites in exchange for other closed loop cards or payments. For example, a chain of coffee shops may offer reloadable cards that can only be used to purchase goods at the coffee shop.
Prepaid cards can be abused by illicit actors seeking to launder money and finance terrorist activities. For instance, both open and closed loop prepaid cards can be utilized in conjunction with, or as a replacement to, bulk cash smuggling. Specifically, drug traffickers have been known to convert cash derived from narcotic sales to prepaid debit cards, which they then use to purchase goods and services or send to narcotic suppliers, who in turn use the cards to withdraw cash from an ATM. In addition, funds can be loaded onto prepaid cards in support of terrorist activities, such as purchasing various products and services whether buying a terrorist a plane ticket or providing other resources (e.g. car rental or hotel) to support a terrorist group.
When assessing the risks associated with prepaid cards, LFIs should consider the specific risks posed by the features and functionalities of the monetary instrument. If the cardholder is anonymous, or if the holder or purchaser provides false information on their identity for instance, the money laundering and financing of terrorism and illegal organisations risks are higher. In addition, LFIs should evaluate the risks associated with cash access, and the volume and velocity of funds that can be loaded and retrieved on prepaid cards. Further risk factors include type and frequency of loads and transactions, geographic location where the transaction activity occurs, value limits, distribution channels, and the nature of funding sources.
2.3 Vulnerabilities of Cash-Intensive Businesses
2.3.1 Types of Cash-Intensive Businesses
Cash-intensive businesses are businesses that experience a high volume of cash flows. However, because cash-based transactions are inherently difficult to trace, as discussed above, cash-intensive businesses may potentially be used as vehicles for money laundering and the financing of terrorism and illegal organisations. Businesses that generate a large volume of cash revenue may be susceptible to abuse by illicit actors that integrate the proceeds of crime into the banking system under the guise of legitimate business. In particular, they may exploit cash-intensive businesses for money laundering and the financing of terrorism and illegal organisations by using cash-intensive business to:
• Provide a front to launder large amounts of cash and reinvest cash proceeds of crime in the economy;
• Co-mingle illicit and legitimate income; and
• Finance, though often through small amounts of cash, terrorist activities without traceability.
Cash-intensive businesses span across various industry sectors. Most of these businesses are operating a legitimate business; however, some aspects of these businesses may be vulnerable to money laundering or the financing of terrorism and illegal organisations. Examples of cash-intensive businesses include but are not limited to the following:
• Convenience stores;
• Retail stores;
• Restaurants;
• Wholesale or general trading businesses;
• Travel agencies and tour operators; and
• Car dealers.
In addition, please consult the CBUAE’s Guidance for Licensed Financial Institutions providing services to the Real Estate and the Precious Metals and Stones sector3 for further information.
LFIs may expand on the above by considering additional factors when identifying cash-intensive businesses in their customer base. For example LFIs can define cash-intensive businesses based on specific criteria, such as a proportion or more of the business’ revenue is in cash or the business has a monthly revenue in cash above a certain threshold. In either scenario, the definition of cash-intensive business should be determined by the LFI, justified by a sound methodology that considers various factors including risk and characteristics, documented in the LFI’s policies and procedures, and approved by the LFI’s senior management.
The LFI should monitor whether the cash-intensive business appears to generate unusual transactions compared to the business’ expected activity and profile, and with other similar cash-intensive businesses. For example, a small business making significantly larger amounts of cash deposits than other businesses of a similar size in the same industry should be reviewed for potential money laundering activity. The extent of the vulnerability presented by cash-intensive businesses may be particularly severe due to large volumes of cash transactions, limited record keeping, and high customer turnover. LFIs should therefore understand the nature and purpose of the business relationship and expected activity of the customer in order to identify types of transactions that appear to be unusual, potentially suspicious, and/or inconsistent with the customer’s profile and stated purpose of the account.
The following sections examine common features of cash-intensive businesses that impact risk. LFIs should consider the specific risks posed by these features to determine whether the customer is considered as high-risk and should be subject to enhanced due diligence (“EDD”) measures. LFIs should incorporate this assessment into their AML/CFT program and update their policies, procedures, and processes with the aim to detect illicit activity and manage illicit financing risks.
3 Available at https://www.centralbank.ae/en/cbuae-amlcft
2.3.1.1 Cross-Border Movement of Cash and Cash Couriers
Cash-intensive businesses may move cash across borders as part of their business model. Cross-border movement of licit cash can be legal, subject to compliance with reporting and other relevant legal and regulatory requirements. However, criminals may also seek to move cash across borders; according to FATF, the physical transportation of cash across an international border is “one of the oldest and most basic forms of money laundering” and is still widely used today.4 The criminal economy tends to be cash-based with illicit proceeds of crime moving quickly and anonymously, including across borders. Illicit actors often choose to remove their illicit assets from a bank account in order to obscure the audit trail by transporting it to another country where they can spend the cash on goods or services or reintroduce the cash into the financial system. Illicit actors who generate cash proceeds also seek to move their profits to jurisdictions that will allow the placement of cash into the legal economy without detection. Their selection of a jurisdiction can be driven by the predominant use of cash in that jurisdiction, the weaker AML/CFT controls of a jurisdiction’s financial system including few or no restrictions on cash payments, or a jurisdiction’s reputation as a banking secrecy haven. Illicit actors can exploit the high volume of passenger, cargo, and mail movements into and out of jurisdictions to move cash without attracting the attention of authorities.
Cash-intensive businesses may utilize cash couriers to move cash across borders. Cash couriers are natural persons who physically transport currency and bearer negotiable instruments on their person or accompanying luggage from one jurisdiction to another. Couriers may be directly involved in the underlying crime or may be third parties recruited specifically to move money to another jurisdiction. Mechanisms to conceal the cash include within pieces of clothing on the physical persons (such as a money belt), hidden within luggage, or even concealed internally. Cash couriers may use air, sea, or rail transport to cross an international border and typically use high denomination banknotes as part of their transportation, which decreases the size and bulk of low denomination banknotes.
Specifically, cross-border movements of cash across an international border are used to:
• Launder proceeds of crime by placing them in another jurisdiction, typically with weaker AML/CFT controls. • Move illicit value to purchase assets that can hold considerable value, such as luxury goods, or transfer the value of the funds for them to be stored. • Hide proceeds from authorities and complicate asset recovery.
It is not illegal to move cash into or out of the UAE. However, natural or legal persons must declare upon entering or leaving the UAE any currencies, bearer negotiable instruments, precious metals and stones above the threshold of AED 60,000. The relevant extract of the Regulation on the Declaration of Currencies, Bearer Negotiable Instruments, and Precious Metals and Stones in Possession of Travelers Entering or Leaving the UAE (issued in the Official Gazette No 703 dated 31/05/2021) is in the box below.
Article (8) of Federal Decree-Law No. (20) of 2018 on Anti Money Laundering and Combating the Financing of Terrorism and the financing of Illegal Organizations stipulates that (when entering or leaving the country, any person must declare the currencies or bearer negotiable financial instruments, precious metals or stones of value, in accordance with the declaration regulation issued by the Central Bank).
Accordingly, the Board of Directors of the Central Bank has decided that the maximum threshold for currencies, bearer negotiable instruments, and precious metals and stones, shall be in accordance with the table below, and shall apply to all forms of physical cross-border transportation, whether by travelers or through mail and cargo. Bearer negotiable instruments mean financial instruments of whatever form, whether in the form of a bearer document, such as travelers checks, promissory checks, payment orders, or others. Based on the above, any natural or legal person shall declare upon entering or leaving the UAE any currencies, bearer negotiable instruments, precious metals and stones above the threshold specified in the table and shall provide an honest and clear answer and adequate information to the Customs authority and its staff upon request. Declarations shall also be made for currencies, bearer negotiable instruments, precious metals or stones of a value exceeding the specified threshold crossing the border through cargo, mail or shipments transported using transport service companies using the official customs systems of the UAE.
Maximum threshold for currencies, bearer negotiable instruments, and precious metals and stones
Currencies/Instruments/Metals/ Precious stones Threshold above which declaration is required 1. Currencies (UAE Dhrs or equivalent in other currencies) UAE Dhrs 60,000
or equivalent in any other
currencies2. Any type of bearer negotiable instruments UAE Dhrs 60,000
or equivalent in any other
currencies3. Precious metals with high economic value in any form, type or classification, provided they are not intended for commercial purposes or transported by a traveler that engages in the same trade or a traveler that transports such materials as a profession and frequently visits the department or the customs port. UAE Dhrs 60,000
or equivalent in any other currencies4. Precious stones with high economic value in any form, type or classification, provided they are not intended for commercial purposes or transported by a traveler that engages in the same trade or a traveler that transports such materials as a profession and frequently visits the department or the customs port. UAE Dhrs 60,000
or equivalent in any other
currenciesUnderstanding whether customers have made any such declarations, in accordance with the Regulation should form part of any due diligence by the LFIs where required. As part of due diligence, LFIs may require additional information on the customer or the transaction, including the source of funds and relevant documentation.
Potential Risk Indicators:
o Transactions involving locations or customers originating from locations with poor AML/CFT regimes or high exposure to corruption. o Significant and/or frequent cash deposits or currency exchanges made over a short period of time. o Customer is in possession of money supposedly for business reasons while travelling to countries where cash payments are restricted. o Customer requests to purchase, or has possession of, large volumes of high denomination banknotes. o Customer requests to purchase, or has possession of, large amounts of foreign currency without a plausible explanation. o Customers who use false identification or offer different identifications on separate occasions
4 FATF “Money Laundering through the Physical Transportation of Cash” (October 2015), available at: https://www.fatf- gafi.org/media/fatf/documents/reports/money-laundering-through-transportation-cash.pdf
2.3.1.2 Cash Deposits
Cash-intensive businesses can be expected to make cash deposits, which is legal and a natural fit with their business model. Illicit actors, however, will seek ways to place their illicit cash into the financial system. Illicit actors involved in cash generating crimes frequently need to use a significant portion of the cash they have acquired to pay for the illicit goods they have sold, to purchase additional goods, and to pay the various expenses incurred in acquiring or transporting the goods. As part of the money laundering process, individuals seek to use the proceeds of crimes by disguising the origin of the funds as legitimate economic activities. Terrorists also seek to finance, often through small amounts of cash, terrorist activities without traceability. LFIs should therefore be aware of cash deposits placed into the banking system that involve high-risk customers and/or geographical areas, third parties without a relationship to the customer, and transactions that lack an apparent business purpose. LFIs should, as the case may be, undertake CDD measures on the third party cash depositors transacting in any accounts above the threshold specified in Article 6 of the AML-CFT Decision. LFIs should also obtain appropriate information regarding the source of cash deposited in a customer’s account as well as mandate the use of Emirates ID for cash deposits in ATMs.
• Potential Risk Indicators: o Large cash deposits followed immediately by withdrawals or electronic transfers. o Large cash deposit followed by an immediate request that the money be wired out or transferred to a third party, without any apparent business purpose. o Frequent cash deposits by multiple individuals into a single bank account, followed by international wire transfers and /or international withdrawals through ATMs. o Large cash deposit is followed within a short time by wire transfers to high-risk jurisdictions. o Numerous cash deposits made in different bank branches over a short period of time. o Frequent cash deposits in small amounts, without any apparent business purpose or reasonable grounds. o Customers who use false identification or offer different identifications on separate ccasions
2.3.1.3 Currency Exchanges
Cash-intensive businesses may include currency exchanges as legitimate providers of services. Currency exchanges, however, can also be an attractive vehicle that illicit actors seek to exploit to enter the financial system and transfer their funds. According to the FATF, the simplicity and certainty of currency exchanges transactions and the anonymity and portability of cash make them attractive to money laundering and the financing of terrorism and illegal organisations.5 Once the money has been exchanged, it is difficult to trace its origin. There are two different ways to perform a currency exchange: (1) the use of cash to exchange and transfer the funds; or (2) the use of the internet to perform the currency exchange and transfer the funds to a bank account.
• Potential Risk Indicators: o Significant and/or frequent local or foreign currency exchanges. o Opening of foreign currency accounts with no apparent business or economic purpose. o Customers who know little about or are reluctant to disclose details about the payee, or customers or parties with no apparent ties to the destination country. o Suspicion that the customer is acting on behalf of a third party but not disclosing it. o Transactions involving charities and other non-profit organizations, which are not properly licensed or registered. It is reminded that when opening any accounts for non-profit organisations, LFIs must obtain an original signed letter from the Ministry of Community Development for opening accounts to collect donations and an authorization from the UAE Red Crescent for conducting financial transfers out of the UAE through some of these accounts. o Customers who use false identification or offer different identifications on separate ccasions. o Customers who receive transfers in seasonal patterns or transactions in a pattern consistent with criminal proceeds.
5 FATF “Money Laundering through Money Remittance and Currency Exchange Providers” (June 2010), available at: https://www.fatf-gafi.org/media/fatf/ML%20through%20Remittance%20and%20Currency%20Exchange%20Providers.pdf
3. Mitigating Risks
Effective risk mitigation is critical to protecting the LFI, complying with its legal obligations, and meeting supervisory expectations. When establishing and maintaining relationships with cash-intensive businesses, LFIs should establish policies, procedures, and processes to identify higher-risk relationships, assess AML/CFT risks of the cash-intensive business, conduct due diligence at account opening and throughout the relationship, and monitor these relationships for unusual or potentially suspicious activity. When performing a risk assessment of cash-intensive businesses, LFIs should allocate resources to those accounts that pose the greatest risk of money laundering or financing of terrorism and illegal organisations. To that end, LFIs should understand their risk and take effective, risk-based steps to protect themselves from abuse and from illicit actors and transactions.
The sections below discuss how LFIs can apply specific preventive measures to identify, manage, and mitigate the risks associated with cash-intensive businesses. LFIs should consult the legal and regulatory framework currently in force, the Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations for Financial Institutions, and the CBUAE issued Guidances for further information.6 The controls discussed below should be integrated into the LFI’s larger AML/CFT compliance program and supported with appropriate governance and training.
6 Available at https://www.centralbank.ae/en/cbuae-amlcft.
3.1 Risk-Based Approach
LFIs must take a risk-based approach to the preventive measures they put in place for all customers, including cash-intensive businesses. A risk-based approach means that LFIs should dedicate compliance resources and effort to customers, business lines, branches, and products and services in keeping with the risk presented by those customers, business lines, branches, and products and services, as assessed in accordance with Article 4 of AML-CFT Decision. The risk-based approach has three principal components:
3.1.1 Conducting an Enterprise Risk Assessment
As required by Article 4.1 of AML-CFT Decision, the enterprise risk assessment must reflect the presence of higher-risk customers, including cash-intensive business customers, in an LFI’s customer base. These assessments should in turn be reflected in the LFI’s inherent risk rating. In addition, the LFI’s controls risk assessment should take into consideration the strength of the controls that the LFI has in place to mitigate the risks posed by its cash-intensive business customers, including the preventive measures discussed below.
3.1.2 Identifying and Assessing the Risks Associated with Specific Customers
The LFI is expected to assess the risk of each customer to identify those that require EDD and to support its entity risk assessment. In assessing the risks of a cash-intensive business, LFIs should consider:
i. Geographic Risk: LFIs should assess the risks associated with the jurisdictions in which the business is registered/headquartered and where it operates, including the jurisdictions where it has subsidiaries, where it sources its products (where relevant), and where its main counterparties are based. These may include the overall risk of money laundering, financing of terrorism and illegal organisations, and financing of proliferation, as well as what is known regarding the prevalence of abuse of entities in these sectors. There are a number of sources that LFIs can use to develop a list of high-risk countries, jurisdictions, or regions. LFIs should consult any publications issued by the National Anti-Money Laundering and Combating the Financing of Terrorism and financing of Illegal Organizations Committee (NAMLCFTC)7, the UAE Financial Intelligence Unit (UAE FIU), and the FATF, including the FATF’s list of jurisdictions subject to countermeasures and to increased monitoring. LFIs may also use public free databases such as, for example, the Basel AML Index8 or the Transparency International Corruption Perceptions Index.9 LFIs should not solely rely on public lists, however, and should consider their own experiences and the nature of their exposure to each jurisdiction when assessing the risk of that jurisdiction.
ii. Customer Risks: LFIs should assess the type of cash-intensive business, the maturity of that relationship (if the relationship is a long-term business relationship of the LFI), and other characteristics of the business relationship, such as the customer’s ownership structure. Cash-intensive businesses that have a complex legal ownership structure, for example, may be higher risk than those with simpler ownership structures.
iii. Product, Service, and Delivery Channel Risk: LFIs should assess risk in this category based on the products and services that the customer intends to use, and the delivery channels through which the LFI will provide these services. LFIs should draw on their entity risk assessment to assess the risk of the products and services each customer uses or intends to use. (See also Section 3.2.3 below in relation to understanding the nature of the customer’s business and purpose of the business relationship.)
Questions that an LFI may ask to determine the risk profile of a cash-intensive business include, but are not limited to:
• Where is the business incorporated? Where does it operate? Are these high-risk jurisdictions? • What type of industry does the cash-intensive business operate in? • What types of products and services is the business requesting? • What is the intended volume, frequency, and nature of cash transactions that the cash-intensive business intends to conduct through its account? • What is the regulatory environment in the jurisdiction(s) where the cash-intensive business is incorporated/has operations? • What is the ownership structure of the customer? Do the customer’s beneficial owners, shareholders, directors, and senior managers reside in a high-risk jurisdiction? • What is the availability of information on the customer? Is the customer cooperating with the LFI to provide all the necessary customer due diligence (“CDD”)/EDD information to the LFI? • If the customer is an existing customer, does the customer have a history of Suspicious Transaction Report (“STR”) filings?
7 Available at: https://www.namlcftc.gov.ae/en/high-risk-countries.php
8 Available at: https://baselgovernance.org/basel-aml-index
9 Available at: https://www.transparency.org/en/cpi/2020/index/nzl3.1.3 Applying EDD and other Preventive Measures
Where the LFI determines a customer to be higher-risk, Article 4.2(b) of AML-CFT Decision requires that the LFI apply EDD. EDD is also required for specified higher-risk customer types, no matter their risk rating:
• Customers who are Politically Exposed Persons (“PEPs”) or that are owned or controlled by PEPs;
• Customers from higher-risk jurisdictions; and
• Customers with whom the LFI is establishing a correspondent relationship.
EDD measures should be designed to mitigate the specific risks identified with particular customers. Examples of EDD measures are described below in Section 3.2.
3.2 Customer Due Diligence and Enhanced Due Diligence
CDD, and where necessary EDD, are the core preventive measures that help LFIs manage the risks of all customers, particularly higher-risk customers. As discussed below, each stage of the CDD process gives LFIs an opportunity to collect the information they need to identify and manage the specific risks of higher-risk customers.
The goal of the CDD process is to ensure that LFIs understand who their customer is and the purpose for which the customer will use the LFIs services. Where an LFI cannot satisfy itself that it understands a customer, then it should not accept it as a customer. If there is an existing business relationship, the LFI should not continue it. LFIs should also consider filing a STR, as discussed in Section 3.3.2.
Under Article 5 of AML-CFT Decision, LFIs should conduct CDD before or during the establishment of the business relationship or account, or before executing a transaction for a customer with whom there is no business relationship. Although Article 5 permits CDD to be delayed in circumstances of lower risk, the potential higher risk of cash-intensive businesses makes it unlikely that delayed CDD will be appropriate in the context of onboarding such customers. To this end, at the time of account opening, the LFI should seek to understand the cash-intensive business’ operations and business structure, the intended use of the account (including anticipated transaction volume, products, and services used), the geographic location(s) involved in the relationship, and jurisdiction(s) of operations. As part of collecting this information, the LFI should also assess the availability of information on the cash-intensive business and cooperation of the business in providing information to the LFI.
The following elements of CDD should be carried out for all customers, no matter the customer type.
3.2.1 Customer Identification and Verification
Under Article 8 of AML-CFT Decision, LFIs are required to identify and verify the identity of all customers. As stipulated in the Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations for Financial Institutions, the identification and verification of the identity of customers is a fundamental component of an effective ML/FT risk management and mitigation program. Please see Section 6.3.1 of the above-mentioned Guidelines for further information on customer identification.
3.2.2 Beneficial Owner Identification
The majority of cash-intensive businesses will be legal persons. Article 9 of AML-CFT Decision requires all financial institutions to identify the beneficial owners of a legal person customer by obtaining and verifying the identity of all individuals who, individually or jointly, have a controlling ownership interest in the legal person of 25% or more. Where no such individual meets this description, the LFI should identify and verify the identity of the individual(s) holding the senior management position in the entity.
The beneficial owner of a legal person must be an individual. Another legal person cannot be classified as the beneficial owner of a customer, no matter what percentage it owns. LFIs should continue tracing ownership all the way up the ownership chain until it discovers all individuals who own or control at least 25% of the LFI’s customer. When the LFI has identified qualifying beneficial owners, it should perform CDD on each individual beneficial owner, in accordance with the requirements of Article 8.1(a) of AML-CFT Decision (10). If no individual qualifies as a beneficial owner, LFIs should identify the individual(s) holding the position of senior management officer(s) within the customer. This option should be used only as a last resort, however, and when the LFI is confident that no one individual, or small group of individuals, exercises control over the customer. Please see the CBUAE's Guidance for LFIs providing services to Legal Persons and Arrangements10 for more information on identification of beneficial owners.
10 Available at https://www.centralbank.ae/en/cbuae-amlcft.
3.2.2.1 EDD: Beneficial Ownership
If the LFI has followed the steps described above and is still not confident that it has identified the individuals who truly own or control the customer, or when other high-risk factors are present, the LFI should consider intensifying its efforts to identify the beneficial owners. The most common method of doing so is to identify additional beneficial owners below the 25% ownership threshold mandated by UAE law. This may involve identifying and verifying the identity of beneficial owners at the 10% or even the 5% level, as risk warrants. It should also involve requiring the customer to provide the names of all individuals who own or control any share in the customer—without requiring them to undergo CDD—in order to conduct sanctions screening or negative news checks.
3.2.3 Nature of the Customer’s Business and Purpose of the Business Relationship
Under article 8 of AML-CFT Decision, for all customer types, LFIs are required to understand the purpose for which the account or other financial services will be used, and the nature of the customer’s business. This step requires the LFI to collect information that allows it to create a profile of the customer and of the expected uses to which the customer will put the LFI’s products and services. This element of CDD will have important implications for the customer risk rating.
It is critical that LFIs have processes and controls in place to ensure that they are able to identify cash-intensive business customers. In line with a risk-based approach, LFIs should interview the customer, review the customer’s business license, request recent financial statements (audited if available), tax returns or additional information, search company databases and assess the primary business activity, products, and services offered by the customer to understand the full scope of the customer’s business.
If an LFI determines that a customer or prospective customer has materially misrepresented itself or its business, it should not onboard the customer and should exit the relationship if one has been established. In addition, the LFI should consider filing a Suspicious Transaction Report (STR), Suspicious Activity Report (SAR) or other report types to the UAE FIU as discussed in section 3.3.2 below. The LFI may also consider adding the customer, its beneficial owners, directors, and its managers to internal watchlists.
High-risk customers should be treated as high risk no matter the financial services they use. Even so, the risk to which the LFI may be exposed can vary based on the purpose of the account and the types of financial products and services the customer wishes to use. LFIs should fully understand the uses to which the cash-intensive business intends to put the account and the expected activity on the account, to the extent that it can generally predict activity on the account and identify activity that does not fit the profile. To that end, the LFI should seek to assess the expected volume, frequency, and nature of cash transactions that the customer intends to conduct through its account, as this will be an important risk factor for identifying money laundering and financing of terrorism and illegal organisations risks associated with the cash-intensive business. In addition, the LFI may wish to consider whether the expected volume of cash coming through the account is consistent with the declared sales income and whether the expected volume of cash appears reasonable compared to other similar cash-intensive customers of the LFI (i.e., operating as similar business types in similar markets).
3.2.4 Ongoing Monitoring
Under Article 7 of AML-CFT Decision, all customers must be subject to ongoing monitoring throughout the business relationship. Ongoing monitoring ensures that the account or other financial service is being used in accordance with the customer profile developed through CDD during onboarding, and that transactions are normal, reasonable, and legitimate.
3.2.4.1 CDD Updating
LFIs are expected to ensure that the CDD information they hold on all customers is accurate, complete, and up-to-date. This is particularly crucial in the context of customers that are companies or that engage in cash-intensive business. The risk associated with a cash-intensive business can change overnight if the customer changes its business activities. LFIs should update CDD for all customers on a risk-based schedule, with CDD on higher-risk customers being updated more frequently. EDD on all customers should involve more frequent CDD updates.
CDD updates should include a refresh of all elements of initial CDD, and in particular should ascertain that:
• The customer’s beneficial owners remain the same; • The customer continues to have an active status with a company registrar; • The customer has the same legal form and is domiciled in the same jurisdiction; and • The customer is engaged in the same type of business, and in the same geographies.
In addition to a review of the customer’s CDD file, the LFI should also review the customer’s transactions to determine whether they continue to fit the customer’s profile and business and are consistent with the business the customer expected to engage in when the business relationship was established. In this capacity, the LFI should pay particular attention whether the volume of cash coming through the account is consistent with the declared sales income of the cash-intensive business customer. This type of transaction review is distinct from the ongoing transaction monitoring discussed below. The purpose of the review is to complement ongoing transaction monitoring by identifying behaviours, trends, or patterns that are not necessarily subject to transaction monitoring rules.
The techniques used for transaction review will vary depending on the customer. For lower-risk customers, a review of alerts, if any, is likely to be sufficient. For higher risk customers, such as cash-intensive businesses rated as high-risk, a more intensive review may be necessary. For customers with a large volume of transactions, LFIs may use data analysis techniques to identify unusual behaviour. If the review finds that the customer’s behaviour or information has materially changed, the LFI should risk-rate the customer again. New information gained during this process may cause the LFI to believe that EDD is necessary or may bring the customer into the category of customers for which EDD is mandatory (i.e., customers that are PEPs; customers that are based in high-risk jurisdictions; etc.).
LFIs may consider requiring that the customer update them as to any changes in its beneficial ownership or business activities. Even if this requirement is in place, however, LFIs should not rely on the customer to notify it of a change but should still update CDD on a schedule appropriate to the customer’s risk rating.
3.2.4.2 EDD: Ongoing Monitoring
When customers are higher risk, such as for cash-intensive businesses rated as high-risk following the completion of the CDD process, monitoring should be more frequent, intensive, and intrusive. LFIs should review the CDD files of higher risk customers on a frequent basis, such as every six or nine months for very high-risk customers. The methods LFIs use to review the account should also be more intense and should not rely solely on information supplied for the customer. For example, LFIs should consider:
• Reviewing more or all transactions on the account, rather than a sample of transactions;
• Conducting site visits at the customer’s premises, whenever the LFI is not satisfied with the documentation provided by the customer, and requesting a meeting between an appropriate LFI representative and the customer’s managing director or Chief Financial Officer. Site visits can be particularly important for certain cash-intensive businesses, including those that use an LFI’s cash management services on a large scale, as they allow the LFI’s compliance personnel to inspect the institution’s cash management program and the controls it has in place to prevent illicit cash being commingled with legitimate funds; and
• Conducting searches of public databases, including news and government databases, to independently identify material changes in a customer’s ownership or business activities or to identify adverse media reports. Such searches should include adverse media searches of public records and databases, using relevant key words, including but not limited to, allegation, fraud, corruption, laundering.
3.3 Transaction Monitoring and STR Reporting
3.3.1 Transaction Monitoring
Under Article 16 of AML-CFT Decision, LFIs must monitor activity by all customers to identify behaviour that is potentially suspicious and that may need to be the subject of a suspicious transaction report (“STR”) or suspicious activity report ("SAR") or other report types. As with all customer types, LFIs that use automated monitoring systems should apply rules with appropriate thresholds and parameters that are designed to detect common typologies for illicit behaviour. When monitoring and evaluating transactions, the LFI should take into account all information that it has collected as part of CDD, including the identities of beneficial owners. For example, a series of transactions between two unconnected companies may not be cause for an alert. But if the companies are all owned or controlled by the same individual(s), the LFI should investigate to make sure that the transactions have a legitimate economic purpose. In addition, higher-risk customers should be subject to more stringent transaction monitoring, with lower thresholds for alerts and more intensive investigation.
Monitoring systems can include manual monitoring processes and the use of automated and intelligence-led monitoring systems. In all cases, the appropriate type and degree of monitoring should appropriately match the ML/TF risks of the institution’s customers, products and services, delivery channels, and geographic exposure, and may therefore vary across an LFI’s business lines or units, where applicable. TM programs should also be calibrated to the size, nature, and complexity of each institution. Please consult the CBUAE’s Guidance for Licensed Financial Institutions on Transaction Monitoring and Sanctions Screening for further information.11
The transaction monitoring system used by LFIs should be equipped to identify patterns of activity that appear unusual and potentially suspicious for cash-intensive business customers as well as unusual behaviour that may indicate that a customer’s business has changed in such a way as to require a high-risk rating. Some red flags for cash-intensive business customers are described below. If an LFI’s automated transaction monitoring system is not capable of alerting on these red flags, LFIs should have in place manual monitoring, such as management information systems.
• The business engages in significantly greater volumes of cash transactions in comparison to other similar business types operating in similar jurisdictions and markets. • The business engages in unusually frequent domestic and international ATM activity. • The customer makes a cash deposit followed by an immediate request that the money be wired out or transferred to a third party, without any apparent business purpose. • There are frequent cash deposits by multiple individuals into a single bank account, followed by international wire transfers and /or international withdrawals through ATMs. • The parties to the transaction (e.g. originator or beneficiary) are from countries that are known to support terrorist activities and organizations. • The customer uses a personal/individual account for business purposes or vice versa. • Upon request, a customer is unable or unwilling to produce appropriate documentation (e.g. invoices) to support a transaction, or documentation appears doctored or fake (e.g. documents contain significant discrepancies between the descriptions on the invoice, or other documents such as the certificate of origin or packing list). • The customer engages in transactions involving foreign currency exchanges that are followed within a short time by wire transfers to high-risk jurisdictions. • Funds are transferred into an account and are subsequently transferred out of the account in the same or nearly the same amounts, especially when the origin and destination locations are high-risk jurisdictions.
11 Available at https://www.centralbank.ae/en/cbuae-amlcft.
3.3.2 STR Reporting
As required by Article 15 of the AML-CFT Law and Article 17 of AML-CFT Decision, LFIs must file a suspicious transaction report (“STR”) or suspicious activity report ("SAR") or other report types with the UAE Financial Intelligence Unit (“UAE FIU”) when they have reasonable grounds to suspect that a transaction, attempted transaction, or funds constitute, in whole or in part, regardless of the amount, the proceeds of crime, are related to a crime, or are intended to be used in a crime. STR filing is not simply a legal obligation; it is a critical element of the UAE’s effort to combat financial crime and protect the integrity of its financial system. STR filings assist law enforcement in detecting criminal actors and preventing the flow of illicit funds through the UAE financial system.
In addition to the requirement to file an STR when an LFI suspects that a transaction or funds are linked to a crime, LFIs should consider filing an STR in the following situations involving higher-risk customers:
• A potential customer decides against opening an account or purchasing other financial services after learning about the LFI’s CDD requirements; • A current customer cannot provide required information about its business or its beneficial owners; • A customer cannot adequately explain transactions, provide supporting documents such as invoices, or provide satisfactory information about its counterparty; or • The LFI is not confident, after completing CDD procedures, that it has in fact identified the individuals owning or controlling the customer. In such cases, the LFI should not establish the business relationship, or continue an existing business relationship.
Please consult the CBUAE’s Guidance for Licensed Financial Institutions on Suspicious Transaction Reporting12 for further information.
12 Available at https://www.centralbank.ae/en/cbuae-amlcft.
3.4 Governance and Training
The specific preventive measures discussed above should take place within, and be supported by, a comprehensive institutional AML/CFT program that is appropriate to the risks the LFI faces. The core of an effective risk-based program is an appropriately experienced AML/CFT Compliance Officer who understands the LFI’s risks and obligations and who has the resources and autonomy necessary to ensure that the LFI’s program is effective. Additionally, the LFI’s senior management must clearly endorse and support the AML/CFT program.
As with all risks to which the LFI is exposed, the AML/CFT training program should ensure that employees are aware of the risks of cash-intensive business customers, familiar with the obligations of the LFI, and equipped to apply appropriate risk-based controls. Training should be tailored and customized to the LFI’s risk and the nature of its operations. For example, an LFI that has a large number of cash-intensive business customers should offer training that includes an in-depth discussion of risk factors and red flags related to such customers.
Annex 1. Synopsis of the Guidance
Purpose of this Guidance Purpose The purpose of this guidance is to assist Licensed Financial Institutions (LFIs) understand and mitigate the risks when providing services to customers who are cash-intensive businesses (CIBs), and to guide them in fulfilling their AML/CFT obligations. The FATF's Mutual Evaluation Report of the UAE issued in April 2020 stated that, as the UAE is a cash-intensive economy and plays an important part in global trade, there are significant risks associated with the cross-border movement of cash and bearer negotiable instruments. Applicability This guidance applies to natural and legal persons, which are licensed and/or supervised by CBUAE, in the following categories: - all national banks, branches of foreign banks, exchange houses, finance companies, payment service providers, registered hawala providers and other LFIs; and
- insurance companies, agencies, and brokers.
Understanding Risks Vulnerabilities of Cash The specific characteristics of cash—its anonymity, interchangeability, and transportability—make it an attractive option for illicit actors seeking to conceal the proceeds of crime. Cash holds no record of its source or owner and can be easily concealed in large quantities Cash transactions are also instantaneous and widely accepted across jurisdictions. Vulnerabilities of Alternatives to Cash Illicit actors also use various monetary instruments in conjunction with, or as a replacementto, cash. Both bearer negotiable instruments and prepaid cards, for instance, offer similar benefits to cash, including anonymity and accessibility. They can store large amounts of value in a compact physical size that is easily transportable and obscures the origin of the funds. - Bearer negotiable instruments are financial instruments of whatever form, whether in the form of a bearer document, such as traveler's cheques, promissory notes and cheques, payment orders, or others.
- Prepaid cards can be used as an alternative to cash in that they provide access to funds that have been paid in advance Funds can be claimed or transferred through an electronic device, such as through a card, code, electronic serial number, mobile identification number, or personal identification number within either an open or closed loop system.
Vulnerabilities of Cash- intensive Businesses Types of CIBs: CIBs are businesses that experience a high volume of cash flows. CIBs span across various industry sectors and most are operating a legitimate business. However, some aspects of these businesses may be vulnerable to money laundering or the financing of terrorism and illegal organisations. Examples of cash-intensive businesses that can pose a higher risk include but are not limited to: convenience and retail stores; restaurants; wholesale and general trading businesses; travel agencies and tour operators and car dealers. LFIs may expand on the above by considering additional factors when identifying cash-intensive businesses in their customer base and should consider the specific risks posed by the below features to determine whether the customer is considered as high-risk and should be subject to enhanced due diligence ("EDD") measures. Cross-Border Movement of Cash and Cash Couriers: CIBs may move cash across borders as part of their business model including by utilizing cash couriers. Cross-border movement of licit cash can be legal, subject to compliance with reporting and other relevant legal and regulatory requirements. However, criminals may also seek to move cash across borders to launder proceeds of crime by placing them in another jurisdiction. Natural of legal persons must declare upon entering or leaving the UAE any currencies, bearer negotiable instruments, precious metals and stones above the threshold of AED 60000. Understanding whether customers have made any such declarations, in accordance with the Regulation should form part of any due diligence by the LFIs where required. Cash Deposits: CIBscan be expected to make cash deposits, which is legal and a natural fit with their business model. Illicit actors, however, will also seek ways to place their illicit cash into the financial system Terrorists also seek to finance, often through small amounts of cash, activities without traceability. LFIs should, as the case may be, undertake CDD measures on the third party cash depositors transacting in any accounts above the threshold specified in Article 5 of the AML-CFT Decision. LFIs should also obtain appropriate information regarding the source of cash deposited in a customer's account as well as mandate the use of Emirates ID for cash deposits in ATMs. Currency Exchanges: CIBs may include currency exchanges as legitimate providers of services Currency exchanges, however, can also be an attractive vehicle for illicit actors seeking to enter the financial system and transfer their funds. Once the money has been exchanged, it is difficult to trace its origin. Mitigating Risks Risk-Based Approach LFIs must take a risk-based approach in their AML programs. This means that they should assess all customers, including CIB customers, to determine their degree of risk. The LFlis expected to assess the risk of each customer to identify those that require EDD and to support its entity risk assessment. In assessing the risks of a cash-intensive business, LFIs should consider: - Geographic Risk related to the jurisdiction(s) in which the customer is based and where it operates;
- Customer Risks related to the customer's customer base, incl, its type and the characteristics of the business relationship; and
- Product, Service, and Delivery Channel Risk related to the products and services the customer intends to use and the delivery channels through which the LFI will provide these services.
Customer Due Diligence and Enhanced Due Diligence For all customers, including CIB customers, LFIs must perform Customer Due Diligence ("CDD") with the following components: Customer Identification: LFIsare required to identify and verify the identity of all customers. Please seethe Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and illegal Organisations for Financial Institutions for further information on customer identification. Beneficial Owners identification: The majority of cash-intensive businesses will be legal persons. For all legal person customers, LFIs must identify all individuals who, individually or jointly, have a controlling ownership interest in the legal person of 25% or more. If no such individual can be identified, the LFI must identify the individual(s) holding the senior management position(s) within the legal person customer. Nature of the Customer's Business and Purpose of the Business relationship: The purpose of the account and the nature of the customer's business are critical drivers of risk for CIB customers. LFIs should fully understand the uses to which the CIB intends to put the account and the expected activity on the account, to the extent that it can generally predict activity on the account and identify activity that does not fit the profile. As they seek to understand the customer's business, LFIs should collect all information necessary to assess customer risk. Perform Ongoing Monitoring: For all customers, LFIs should ensure that the customer information is accurate, complete and up-to-date, and that the customer's profile and business are consistent with the expectations set at onboarding. If not, the customer risk rating may need to be changed. When customers are higher risk, such as for cash-intensive businesses rated as high-risk following the completion of the CDD process, monitoring should be more frequent, intensive, and intrusive. Transaction Monitoring and Suspicious Transaction Reporting The transaction monitoring system used by LFIs should be equipped to identify patterns of activity that appear unusual and potentially suspicious for CIB customers as well as unusual behaviour that may indicate that a customer's business has changed in such a way as to require a high-risk rating. Please consult the CBUAE's Guidance for Licensed Financial Institutions on Transaction Monitoring and Sanctions Screening for further information. LFIs must file a suspicious transaction report ("STR") or suspicious activity report ("SAR") or other report types with the UAE Financial Intelligence Unit ("UAE FIU")when they have reasonable grounds to suspect that a transaction, attempted transaction, or funds constitute, in whole or in part, regardless of the amount, the proceeds of crime, are related to a crime, or are intended to be used in a crime. Please consult the CBUAE's Guidance for LFIs on Suspicious Transaction Reporting for further information. Governance and Training The preventive measures discussed above should take place within, and be supported by, a comprehensive institutional AML/CFT program that is appropriate to the risks the LFI faces. As with all risks to which the LFI is exposed, the AML/CFT training program should ensure that employees are aware of the risks of cash-intensive business customers, familiar with the obligations of the LFI, and equipped to apply appropriate risk-based controls. Guidance for Licensed Exchange Houses
Effective from 11/11/20211. Introduction
1.1. Purpose
Article 44.11 of the Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations charges Supervisory Authorities with “providing Financial Institutions…with guidelines and feedback to enhance the effectiveness of implementation of the Crime-combatting measures.”
The purpose of this Guidance is to assist the understanding and effective performance by the United Arab Emirates Central Bank’s (“CBUAE”) Licensed Exchange Houses (“LEH”) of their statutory obligations under the legal and regulatory framework in force in the UAE. It should be read in conjunction with the Chapter 16 of the Standards for the Regulations Regarding Licensing and Monitoring for Exchange Business, Version 1.20 of November 2021 amending Version 1.10 of February 2018 (issued by Notice No. xx/2021 dated xx/xx/2021), the CBUAE's Procedures for Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations (issued by Notice No. 74/2019 dated 19/06/2019) and Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations for Financial Institutions (issued by Notice 79/2019 dated 27/06/2019) and any amendments or updates thereof.1 As such, while this Guidance neither constitutes additional legislation or regulation nor replaces or supersedes any legal or regulatory requirements or statutory obligations, it sets out the expectations of the CBUAE for LEH to be able to demonstrate compliance with these requirements. In the event of a discrepancy between this Guidance and the legal or regulatory frameworks currently in force, the latter will prevail. This Guidance may be supplemented with additional separate guidance materials, such as outreach sessions and thematic reviews conducted by the Central Bank.
Furthermore, this Guidance takes into account standards and guidance issued by the Financial Action Task Force (“FATF”), industry best practices and red flag indicators. These are not exhaustive and do not set limitations on the measures to be taken by LEH in order to meet their statutory obligations under the legal and regulatory framework currently in force. As such, LEH should perform their own assessments of the manner in which they should meet their statutory obligations.
This Guidance comes into effect immediately upon its issuance by the CBUAE with LEH expected to demonstrate compliance with its requirements within one month from its coming into effect.
1Available at https://www.centralbank.ae/en/cbuae-amlcft.
1.2. Applicability
Unless otherwise noted, this Guidance applies to all Exchange Houses that are licensed and supervised by the CBUAE.
1.3. Legal Basis
This Guidance builds upon the provisions of the following laws and regulations:
Furthermore, LEH may be guided by the FATF standards on AML/CFT, Guidance for a Risk Based Approach for Money or Value Transfer Services, and Report on Money Laundering through Money Remittance and Currency Exchange Providers2.
2 FATF: Guidance-RBA-money-value-transfer-services.pdf (fatf-gafi.org); and Money laundering through money remittance and currency exchange providers (fatf-gafi.org)
1.4. Definitions
Beneficial Owner: The ‘Natural Person’ who ultimately owns or exercises effective control, directly or indirectly, over a customer or the natural person on whose behalf a transaction is being conducted, or the natural person who exercises effective ultimate control over a legal person or legal arrangement.
Exchange Business: Shall mean: (1) Dealing in sale and purchase of foreign currencies and travelers cheques; (2) Executing remittance operations in local and foreign currencies; (3) Payment of wages through establishing a link to the operating system of “wages protection system” (WPS); and (4) Other business licensed by the CBUAE.
Exchange House: A juridical person licensed in accordance with the provisions of Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities to carry on money exchange activity, and conduct funds transfers within and outside the UAE, and any other businesses determined by the CBUAE.
Politically Exposed Person (PEP): natural persons who are or have been entrusted with a prominent public function in the UAE or any other foreign country such as heads of states or governments, senior politicians, senior government officials, judicial or military officials, senior executive managers of state-owned corporations, and senior officials of political parties, and persons who are, or have previously been, entrusted with the management of an international organization or any prominent function within such an organization; and the definition also includes the following:
1. Direct family members (of the PEP who are spouses, children, spouses of children, parents) 2. Associates known to be close to the PEP, which include: (a) Individuals having joint ownership rights in a legal person or arrangement or any other close business relationship with the PEP; (b) Individuals having individual ownership rights in a legal person or arrangement established in favor of the PEP.
Instant Money Transfer Service Provider: A money remitting institution licensed and regulated by an appropriate Regulator in its home country who will have the necessary proprietary software applications and infrastructure to transfer funds instantly from an agent in one country to an agent in another country and/or domestically.
Legal person: Any entities other than natural persons that can establish in their own right a permanent customer relationship with a financial institution or otherwise own property. This can include companies, bodies corporate, foundations, partnerships, or associations, along with similar entities.
Legal arrangement: A relationship established by means of a contract between two or more parties which does not result in the creation of a legal personality. Examples include trusts or other similar arrangements. Many legal arrangements allow for ownership, control, and enjoyment of funds to be divided between at least two different persons.
Licensed Exchange House (LEH): An Exchange House licensed by the CBUAE.
Source of funds: How the money, involved in the transaction, was originally derived or earned. Examples of source of funds are: salary, wages, inheritance, gratuity, end of service benefits, bank loan, income from businesses, sale of property, sale of land, sale of investments, etc. For verification of the source of funds, documents include but are not limited to salary slip, labor contract, court order, bank statements, etc.
2. Risks related to the Exchange Houses Sector
The FATF’s Mutual Evaluation Report of the UAE issued in April 2020 stated that the Money or Value Transfer Services’ sector (MVTS), including the Exchange Houses’ sector, is weighted as highly important in terms of risk and materiality in the UAE. The inherent risk and materiality of these sectors has been notably increased by their exposure to cash transactions.
The Exchange Houses sector provides widely used financial services to diverse customer sectors. While the majority of its Exchange Business is legitimate in purpose, it can be abused to facilitate illegal activity, including terrorist financing, money laundering, and other type of criminal activity. The Exchange Houses sector may provide significant opportunities for criminals to move, conceal and eventually use the funds generated by their illegal activities, unless appropriate safeguards are in place. This is due to the simplicity and speed of transactions, worldwide reach and often cash-based nature of transactions. Importantly, money laundering and financing of terrorism (ML/FT) vulnerabilities also stem from the fact that Exchange Houses often carry out occasional transactions rather than establishing an ongoing formal relationship with their customers, which means that their understanding of the ML/FT risk associated with the customer may be limited.
Risks to the Exchange Houses sector also stem from generally uneven regulatory disparity, supervision and enforcement of the sector globally because Exchange Business often involves different jurisdictions. Criminals may seek to exploit differences in regulatory requirements in different jurisdictions or deficiencies in certain jurisdictions to move, structure and conceal their funds.
Exchange Houses may also potentially be abused by criminal groups and corrupt employees or agents cooperating with criminals, who may seek to own an Exchange House outright, or indirectly through an associate, or could seek to coerce employees through financial incentives in order to use the Exchange House to circumvent AML/CFT obligations and advance criminal schemes.
3. Regulation and Supervision of Exchange Houses
The Exchange Houses sector is regulated by the Regulations and the Standards issued by the CBUAE. For more details and information on AML/CFT compliance, please refer to Chapter 16 of the Standards for the Regulations Regarding Licensing and Monitoring for Exchange Business, version 1.20 of November 2021 amending Version 1.10 of February 2018. LEH are supervised by the CBUAE, who may examine the activities of the LEH at any time it deems appropriate to ensure proper compliance with their statutory obligations under the legal and regulatory framework in the UAE, or impose supervisory action or administrative and financial sanctions for violations. Similar to its all LFIs, the CBUAE applies the principle of proportionality in its supervision and enforcement process, whereby small LEH may demonstrate to the CBUAE that the objectives of the regulatory requirements are met without necessarily addressing all the specifics cited in the legal and regulatory framework in the UAE.
4. AML/CFT Program for Licensed Exchange Houses
LEH must carefully design, document and effectively implement an AML/CFT Program in line with the provisions of the Standards, AML-CFT Law, and AML-CFT Decision. As per Paragraph 16.1 of the Standards, LEH must establish, maintain and regularly update effective, written, and risk-based AML/CFT programs designed to prevent LEH from being abused to facilitate ML/FT. When designing or updating their AML/CFT programs, the scope of the AML/CFT Program should be proportionate to the level of the risk posed by the LEH’s size, scale, complexity, the nature and volume of its Exchange Business, the nature of its customer base, the business relationships it maintains, and the geographic areas in which it operates. For example, a large LEH with a high volume of Exchange Business with high-risk countries is expected to have an AML/CFT Program commensurate with its higher risk of possibly being abused to facilitate ML/FT. However, as all LEH are exposed to some degree of risk, they must perform their own assessments and design their AML/CFT programs in accordance with their overall risk profile in order to meet their statutory obligations.
LEH should ensure the AML/CFT Program includes the following ten (10) essential components, which are described in detail in the following sections:
• Risk assessment, • Policies and procedures, • Governance and the Compliance Officer, • Customer due diligence, • Transaction monitoring, • Sanctions obligations and freezing without delay, • Training, • Independent audit, • Record keeping requirements, and • Managing employee risk. 4.1. Risk Assessment
As required by Article 4 of the AML-CFT Decision and Paragraph 16.2 of the Standards, LEH must identify, assess and understand the ML/FT risks associated with their businesses and perform an enterprise wide ML/FT risk assessment on a regular basis. It must develop a risk assessment in order to understand how and to what extent it is vulnerable to ML/FT, and help determine the nature and extent of AML/CFT resources necessary to mitigate and manage that risk.
The risk assessment creates the basis for the LEH’s risk-based approach. LEH may utilize a variety of models or methodologies to analyze their risks. In general, the risk assessment process would entail the following six (6) steps:
Step 1 Step 2 Step 3 Step 4 Step 5 Step 6 Scope Determination Risk Identification Inherent Risk Assessment Controls Evaluation Residual Risk Assessment Risk Mitigation Define in-scope processes Assess the exposure to threats and vulnerabilities in order to identify risks Assess the impact and likelihood of risks and assign inherent risk ratings Identify and evaluate effectiveness of controls and identify weaknesses Calculate Residual Risk (Inherent Risk Rating minus Controls Evaluation = Residual Risk Rating) Develop and implement mitigation plans against risks that are above an acceptable level The nature and extent of any assessment of ML/FT risks must be appropriate to the nature, size, and complexity of the LEHS business. The risk assessment should cover all relevant factors including but not limited to:
• Customer risk; • Products and services risk; • Delivery channel risk; • New technologies risk; • Jurisdiction or geographic risk; • Counterparty risk; and • Other areas of risk.
As per Article 4.2 of the AML-CFT Decision as well as Paragraphs 16.2 and 16.3 of the Standards, the senior management of the LEH must be closely engaged in the risk assessment process and take responsibility for conducting an appropriate assessment. It must review and approve at least on an annual basis the LEH’s risk appetite statement, risk assessment methodology, and risk assessment findings. If an initial risk assessment assesses the LEH as higher risk, it may be necessary to conduct a more intensive assessment of certain areas of the LEH’s operations. In assessing ML/FT risks, the LEH must have the following elements in place:
• Documented risk assessment methodology, procedures, and processes. • Documented risk assessment findings, including determination of overall risk and specific risks, and mitigating measures to be applied to minimize the impact of risks. • Written risk appetite statement that clearly identifies the acceptable level of risk. • Appropriate mechanisms to provide information on risk assessments to the CBUAE when required.
The risk assessment must be regularly updated annually at a minimum as well as in response to major changes in the LEH’s operations. The risk assessment process must also be fully aligned with the LEH’s products, services, customers, and geographic locations, changes in the LEH’s operations, appetite statement, the legal and regulatory framework in force in the UAE, and the guidance issued by the CBUAE. In addition, LEH may consult the FATF Guidance on the Risk-Based Approach for Money Services Businesses and the Wolfsberg Frequently Asked Questions on Risk Assessments for Money Laundering, Sanctions and Bribery & Corruption for more information on how to plan and perform comprehensive and appropriate risk assessments.3 In tandem, the risk assessment findings should be used to inform the AML/CFT Program policies, procedures, internal controls, and training in order to effectively mitigate risks. The risk assessment should also inform the LEH’s risk-based approach by directing an efficient allocation of AML/CFT risk management resources to the areas of greatest concern. The risk assessment findings should be provided to all business lines across the LEH, its senior management, and relevant employees.
3 Available at: https://www.fatf-gafi.org/media/fatf/documents/reports/Guidance-RBA-money-value-transfer-services.pdf; and https://www.wolfsberg-principles.com/sites/default/files/wb/pdfs/faqs/17.%20Wolfsberg-Risk-Assessment-FAQs-2015.pdf.
4.1.1. Customer Risk
Under Article 4.1 of the AML-CFT Decision and Paragraph 16.2.3 of the Standards, LEH must identify, assess, understand, and mitigate the risk posed by their customers. Customer risk is a critical component of an institutional-level risk assessment because customers engaged in illicit activity can seek to exploit the LEH to facilitate ML/FT and other types of financial crimes. The customer risk assessment process is composed of the customer risk rating, and the assessment of the inherent risk of the customer base. It should be noted that these are closely related concepts, and that risk in the customer base depends in part on the customer risk rating.
4.1.1.1. Customer Risk Rating
LEH should be able to determine whether a particular customer poses higher risk and the potential impact of any mitigating factors on that assessment. Such categorization may be due to the occupation, behavior, or activity of customers. Accordingly, the LEH should assess the risk of key customer elements in order to generate an overall customer rating. Generally, the list of elements includes but is not limited to the following:
• Customer’s address and country. • Type of customer (Domestic, foreign, company/corporate, cash-intensive business, etc.). • Industry in which the customer does business. • Anticipated transactional activities. • Customer’s source of wealth. • ML/FT risk of the customer’s industry • The beneficial owners. • Purpose of the relationship or transactional activities.
Below are some examples of risk factors that could be considered by the LEH:
• Customers conducting their business or transactions in an unusual manner. • Customers who travel unexplained distances to locations to conduct transactions. • Customers who are Politically Exposed Persons (PEPs) or their direct family members or known close associates and customers whose beneficial owner is a PEP. • Customers involved in transactions that have no apparent ties to the destination country and with no reasonable explanations. • Customers who have been the subject of legal proceedings in relation to proceeds-generating crimes known to the LEH. 4.1.1.2. Assessment of the Inherent Risk of the Customer Base
In addition to assessing individual customers, LEH should assess the inherent ML/FT risk of the customer base overall.
1. IDENTIFY: LEH should identify categories or types of customers that pose elevated risks. Under Chapter 16 of the Standards, the categories identified will depend on the specific customer base of the LEH and may include but are not limited to: customer types like dealers in precious metals and stones (DPMS), customers that qualify as Designated Non-Financial Businesses and Professions (DNFBPs), cash-intensive businesses which are rated as high-risk4, PEPs, and customers with ties to high risk jurisdictions. LEH should also include as a customer segment those customers who have been off-boarded or refused service due to ML/FT suspicions.
2. ASSESS: LEH should assign a risk rating (for example, low risk, medium risk, etc.) to each customer category or type identified above. In assessing the risk of each category or type, LEH should consider:
• Guidance published by the FATF; • The potential exposure of customers in each category to illicit funds; and • The features of each customer type that make them useful to illicit actors.
3. CALCULATE EXPOSURE: The LEH should then determine its exposure to the customer categories or types identified and rated above. LEH should consider the proportion of their entire customer base that is made up of each category of customer, the proportion of all transactions carried out by each category of customer, and the total value of all transactions carried out by each customer as a proportion of the LEH’s total transaction volume. The institutional risk assessment should also take into account the individual customer risk-ratings and the proportion of higher or lower risk customers within that group. Where a LEH has large exposure to higher-risk customer types and to higher-risk customers as assessed by individual risk ratings, its overall inherent risk will generally be higher.
4. DOCUMENT: A LEH’s approach to categorizing risk should be clearly documented. The LEH should keep detailed records of its assumptions, statistics used to complete this process, and the resulting analysis and outcomes. 4 For more details and information, please refer to the CBUAE’s Guidance for Licensed Financial Institutions providing services to Cash-Intensive Businesses available at https://www.centralbank.ae/en/cbuae-amlcft
4.1.2. Products and Services Risk
Under Article 4.1 of the AML-CFT Decision and Paragraph 16.2.3 of the Standards, LEH must identify, assess, understand, and mitigate the risk posed by the products and services they offer. The products and services risk is a critical component of an institutional-level risk assessment because customers engaged in illicit activity can seek to exploit the LEH to facilitate ML/FT and other types of financial crimes.
1. IDENTIFY: LEH should identify the full list of products and services they offer.
2. ASSESS: LEH should assign a risk rating to each product type identified above. Determining the risk of products and services should include a consideration of their characteristics and attributes and could include factors such as:
• Products or services that may inherently favor anonymity, or products that can readily cross international borders, such as cash, online money transfers, stored value cards, money orders and international money transfers by mobile phone. • Products or services that have a very high or no transaction limit. • The global reach of the product or service offered. • The complexity of the product or service offered. • Products or services that permit the exchange of cash for a negotiable instrument, such as a stored value card or a money order.
3. CALCULATE EXPOSURE: The LEH should consider what proportion of its total products and services, and of total transactional activity, is associated with higher and lower-risk products and services. Where a LEH has large exposure to higher-risk products and services, its overall inherent risk will generally be higher.
4. DOCUMENT: A LEH’s approach to categorizing risk should be clearly documented. The LEH should keep detailed records of its assumptions, statistics used to complete this process, and the resulting analysis and outcomes. 4.1.3. Delivery Channel Risk
Under Article 4.1 of the AML-CFT Decision and Paragraph 16.2.3 of the Standards, LEH must identify, assess, understand, and mitigate the risk presented by the delivery channels they use. Some delivery channels can increase ML/FT risk because they increase the risk that the LEH does not truly know or understand the identity and activities of the customer.
1. IDENTIFY: The LEH should identify the delivery channels that they use to provide their products and services to customers. These may include, for example: face-to-face; via a website; via an introducer or other third party; and other methods.
2. ASSESS: The LEH should assign an inherent risk rating to the delivery channels identified. The rating should take into consideration the characteristics and attributes of these delivery channels that make them more susceptible to abuse by illicit actors, and could include factors such as whether the delivery channel makes it more difficult to observe the customer’s behavior or to be certain that the person transacting is in fact the identified customer, allows for faster transactions, or involves reliance on a third party.
3. CALCULATE EXPOSURE: The LEH should then determine what proportion of its transactional activity involves each delivery channel, both by volume and value. Where a LEH delivers a large proportion of its products or services via higher-risk delivery channels, its overall risk is likely to be higher as well.
4. DOCUMENT: A LEH’s approach to categorizing risk should be clearly documented. The LEH should keep detailed records of its assumptions, statistics used to complete this process, and the resulting analysis and outcomes. 4.1.4. New Technologies Risk
Under Article 23 of the AML-CFT Decision and Paragraphs 16.2.3 and 16.2.7 of the Standards, LEH must identify, assess, understand, and mitigate the ML/FT risk to which they may be exposed by new technologies, including new delivery mechanisms and the use of new or developing technologies for both new and existing products. LEH must undertake the risk assessment prior to obtaining approval from the CBUAE to launch or use such products, services, and technologies if applicable.
1. IDENTIFY: LEH should identify the new technologies they plan to introduce. New technologies can involve new or modified products and services and also new or modified delivery channels.
2. ASSESS: The LEH should assign an inherent risk to each proposed new technology. Determining the risk of new technologies should include a consideration of their characteristics and attributes. In addition to the factors listed above under sections 4.1.2 and 4.1.3, this could include factors such as features of the technology that promote anonymity or obstruct access to transaction or customer information, a history of ML/FT abuse of the technology, the inherent risk of the target customer and market segments that are projected to use the new technology, and expected growth in use of the technology.
3. CALCULATE EXPOSURE: The LEH should consider the projected or expected volume of transactional activity associated with the new technology and follow the procedure described in sections 4.1.2 and 4.1.3 above.
4. DOCUMENT: A LEH’s approach to categorizing risk should be clearly documented. The LEH should keep detailed records of its assumptions, statistics used to complete this process, and the resulting analysis and outcomes.
4.1.5. Jurisdiction or Geographic Risk
Under Article 4.1 of the AML-CFT Decision and Paragraph 16.2.3 of the Standards, LEH must identify, assess, understand, and mitigate their jurisdiction or geographic ML/FT risk.
1. IDENTIFY: LEH should identify the geographic footprint of their operations, which should include:
• The jurisdictions in which they have locations, including domestic locations; • The jurisdictions in which their customers are resident or of which they are nationals (for Non-Resident Customers only); • The jurisdictions to which they send remittances to or receive remittances from; and • The jurisdictions to or from which they import or export foreign currency.
LEH need not include every single jurisdiction to or from which they send or receive remittances or with which their customers have ties in the risk assessment, but should at least include the jurisdictions to which they have regular or routine exposure.
2. ASSESS: The LEH should assign each jurisdiction identified above an inherent risk-rating, based on the degree of ML/FT risk present in that jurisdiction. The LEH is strongly encouraged to develop its own country risk model that takes into consideration any publications issued by the National Anti-Money Laundering and Combating the Financing of Terrorism and financing of Illegal Organizations Committee (NAMLCFTC)5, the UAE Financial Intelligence Unit (FIU), the FATF lists of High-Risk Jurisdictions subject to a Call for Action and Jurisdictions under Increased Monitoring,6 as well as the Organization for Economic Cooperation and Development (OECD) list of jurisdictions classified as uncooperative tax havens.7 The LEH should also consider whether a jurisdiction:
• Has been identified by credible sources as providing an environment conducive to funding or supporting terrorist activities or that have designated terrorist organizations operating within them. • Has been identified by credible sources as having significant levels of organized crime, corruption, or other criminal activity, including source or transit countries for illegal drugs, human trafficking and smuggling and illegal gambling. • Is subject to sanctions, embargoes or similar measures issued by international organizations such as the United Nations. • Has been identified by credible sources as having weak governance/law enforcement/regulatory regimes, including countries identified by the FATF as having weak AML/CFT regimes 8, for which financial institutions should give special attention to business relationships and transactions.
Finally, the LEH should take into consideration its own knowledge and experiences, such as the number of Suspicious Transaction Reports (STR) or Suspicious Activity reports (SAR) filed that involve each jurisdiction.
3. CALCULATE EXPOSURE: The LEH should consider what proportion of its total customer base and transactional activity, by volume and value, is associated with or linked to higher or lower-risk jurisdictions. Based on its documented understanding of the risks, the LEH may decide to weigh its exposure so that a cross-border transaction to a beneficiary in a high-risk jurisdiction has a greater impact than, for example, a domestic transaction between two UAE residents where one party is a citizen of a high-risk jurisdiction. Where a LEH has large exposure to higher-risk jurisdictions, its overall inherent risk will generally be higher.
4. DOCUMENT: A LEH’s approach to categorizing risk should be clearly documented. The LEH should keep detailed records of its assumptions, statistics used to complete this process, and the resulting analysis and outcomes. 5 Available at: https://www.namlcftc.gov.ae/en/high-risk-countries.php
6 Available at: https://www.fatf-gafi.org/publications/high-risk-and-other-monitored-jurisdictions/?hf=10&b=0&s=desc(fatf_releasedate)
7 Available at: http://www.oecd.org/ctp/harmful/theoecdissuesthelistofunco-operativetaxhavens.htm.
8 See footnote 124.1.6. Counterparty Risk
As required by Article 25 of the AML-CFT Decision and Paragraph 16.2.3 of the Standards LEH must identify, assess, understand, and mitigate counterparty risk prior to establishing business relationships with counterparties, and on an ongoing basis once the relationship is established. Counterparty relationships include the following types:
• Domestic and Foreign correspondent banking arrangements, such as those with banks, exchange houses, or any other financial institutions for the purpose of money transfer services. • Money transfer arrangements with instant money transfer service providers. • Hedging arrangements with local or foreign institutions. • Arrangements to import or export banknotes from/to foreign institutions, such as Banks, exchange houses, or other financial institutions outside the UAE. • Arrangements with local or foreign entities to offer special products/services.
1. IDENTIFY: LEH should identify all counterparties that fit the description above, including with affiliates and other members of the same group.
2. ASSESS: The LEH should assign an inherent risk rating to each counterparty. The determination of the counterparty’s risk should include a consideration of all characteristics and attributes that make the counterparty more or less susceptible to abuse by illicit actors, as well as characteristics and features of the counterparty relationship that could increase or decrease risk. This could include for example:
• The risk of the country in which a counterparty is registered; • The products and services it offers and the risks of the counterparty’s customer base overall; • Its reputation in the sector and any adverse media; • Its ownership (including links to PEPs or persons associated with adverse media); • The counterparty’s experience in this sector and its overall sophistication; • The quality and intensiveness of the counterparty’s AML/CFT program, including whether the program’s requirements are consistent with minimum requirements imposed in LEH by the legal and regulatory framework in force in the UAE; • The quality and rigor of supervision applied to the counterparty; • Any regulatory or criminal enforcement actions taken against the counterparty; and • The nature and purpose of the counterparty relationship, including the risk of the products and services involved and the types of customers who use the relationship.
3. CALCULATE EXPOSURE: LEH should determine the proportion of counterparties that are rated higher risk, both in terms of actual numbers and in terms of the volume and value of the transactions involving that counterparty. Because counterparty relationships may involve rapid, large changes in the volume of transactions, LEH should continuously monitor their exposure to counterparties and update their risk assessment whenever exposure changes substantially.
4. DOCUMENT: A LEH’s approach to categorizing risk should be clearly documented. The LEH should keep detailed records of its assumptions, statistics used to complete this process, and the resulting analysis and outcomes. 4.1.7. Other Areas of Risk
In addition to the ML/FT risks discussed in this section, LEH may be exposed to other areas of illicit finance risk, including sanctions and proliferation financing. The LEH may choose to include these risk domains in its AML/CFT assessment as long as the resulting assessment gives appropriate space and attention to ML/FT risk. Given the evolving nature of ML/FT risks, LEH may also choose to assess their ML/FT risk in additional categories to those discussed above (although they must always address at least the categories covered in this section).
Under Article 4.1 (b) of the AML-CFT Decision and Paragraph 16.2.5 of the Standards, LEH must thoroughly document their risk assessment process so that they can fully explain and justify their assessment methodology.
4.2. Policies and Procedures
As required by Article 4.2.a) of the AML-CFT Decision and Paragraph 16.3 of the Standards, LEH must establish and implement comprehensive and documented AML/CFT policies and procedures to enable them to effectively manage and mitigate the risks they have identified. Under Paragraph 16.3.6 of The Standards, these must be approved by the Manager in Charge, the Compliance Officer, and the Board of Directors (or Owner/Partners where there is no Board of Directors). They must be reviewed and updated annually at a minimum to ensure that they are consistent with statutory obligations and other international best practices, and effective in mitigating existing as well as emerging ML/FT risks as per Paragraph 16.3.7 of the Standards. Policies and procedures should at a minimum:
• Be commensurate with the nature, size, and complexity of the LEH’s operations. • Outline the AML/CFT Program. • Be consistently implemented across all branches, subsidiaries and affiliated entities in which the LEH holds a majority interest. • Capture the LEH’s day-to-day operations and processes. • Clearly define the roles and the day-to-day responsibilities of the Manager in Charge, Compliance Officer, Compliance Committee and employees in relation to AML/CFT compliance as well as the ones of the Board of Directors (or Owner/Partners where there is no Board of Directors) in relation to implementing a robust compliance program across the business of the LEH. • Enable the LEH to clearly and effectively identify, escalate, and report suspicious transactions and activities. • Require enhanced due diligence to be conducted on all customers and transactions that are assessed to be high-risk. • Prohibit employees from, directly or indirectly, informing the customer or any third party that their transactions are subject to monitoring or under investigation or have been reported to the FIU as suspicious transactions. • Contain sufficient detail of their record keeping obligations.
Policies and procedures should be clearly communicated to all relevant employees. They should be easy to follow and be designed to support the compliant and effective functioning of the AML/CFT program and prevent employees from engaging in misconduct.
4.3. Governance and Compliance Officer
The core of an effective risk-based program is an appropriately experienced AML/CFT Compliance Officer who understands the LEH’s risks and obligations and who has the resources and autonomy necessary to ensure that the LEH’s program is effective. As per Article 21 of the AML-CFT Decision and Paragraph 16.4 of the Standards, the LEH must appoint a Compliance Officer who is responsible for day-to-day compliance with the legal and regulatory framework in the UAE and the management of the AML/CFT Program. The role of Compliance Officer must be limited to tasks related to AML/CFT compliance and not be combined with any other functions of the LEH to avoid conflict of interest from multiple roles. Furthermore, as per Paragraphs 16.5 and 6.9.3 of the Standards, the LEH must further appoint an Alternate Compliance Officer to strengthen the AML/CFT Program as well as establish and maintain a Compliance Committee to provide additional oversight of the AML/CFT program. Chapter 6 of the Standards refers to Corporate Governance as the mechanisms and processes by which the LEH is managed, controlled and directed. For more details and information please refer to the relevant section in the Standards.
4.4. Customer Due Diligence
The goal of the CDD process is to ensure that LEH understand who their customer is and the purpose for which the customer will use the LEH’s services. Where a LEH cannot satisfy itself that it understands a customer, then it must not accept the customer. If there is an existing business relationship, the LEH should not continue it. LEH should also consider filing an STR, SAR or other report types to the FIU as discussed in section 5 below. This guidance is not an exhaustive list of CDD obligations and LEH should consult the legal and regulatory framework in force in the UAE for the measures to be taken.
Under Article 8 of AML-CFT Decision, LEHs are required to identify and verify the identity of all customers. In particular, when verifying the Emirates ID card (either physically or by way of digital or e-KYC solutions) the LEH must use the online validation gateway of the Federal Authority for Identity & Citizenship, the UAE-Pass Application, or other UAE Government supported solutions, and keep a copy of the Emirates ID and its digital verification record. Where acceptable IDs other than the Emirates ID are used in the KYC process, a copy must be physically obtained from the original ID and certified as “Original Sighted and Verified” by the employee who carries out the CDD process.
As required by Paragraph 16.7 of the Standards, LEH must implement a strong Know Your Customer (“KYC”) process that is based on clear and comprehensive written policies and procedures. Implementation of an effective KYC process is an essential cornerstone of a LEH’s AML/CFT Program and is necessary in order to:
• Understand who LEH’s customers and counterparties are. • Detect suspicious activity or transactions in a timely manner. • Promote safe and sound business practices. • Minimize the risk that the LEH is abused by illicit actors. • Reduce the risk of processing transactions when the customer is involved in criminal activity. • Protect the reputation of the LEH. • Comply with statutory obligations.
The KYC process must be risk-based and, as such, the KYC measures applied must be commensurate with the ML/FT risks associated with their customers or transactions. Accordingly, Paragraph 16.7.3 of the Standards requires three types of KYC processes that must be applied depending on the customer’s risk and the nature of the transaction and customer. These are:
• Customer Identification (CID); • Customer Due Diligence (CDD); and • Enhanced Due Diligence (EDD).
Please refer to the table below on when to use each KYC measure and to refer to the respective paragraphs in the Standards for the detailed requirements:
Customer Type Customer Activity Value of Transaction Preventive Measure Required Paragraph in the Standards, Version 1.20 Natural Persons Currency Exchange Equal to or greater than AED 3,500 and less than AED 35,000 CID 16.8 Equal to or greater than AED 35,000 and less than AED 55,000 within a 90-day period CID and
CDD16.8
16.9Equal to or greater than AED 55,000 within a 90-day period CID,
CDD, and
EDD16.8
16.9
16.10Money Transfer Any value less than AED 55,000 CID and
CDD16.8
16.9Equal to or greater than AED 55,000 within a 45-day period CID,
CDD, and
EDD16.8
16.9
16.10All Legal Persons or Arrangements Any Activity Any Value CDD and
EDD16.11 Counterparty Relationships Any Activity Any Value CDD and
EDD16.11.8 to
16.11.12
16.11.2PEPs Any Activity Any Value CID,
CDD, and
EDD16.13 DNFBPs/DPMS Any Activity Any Value CID (if the customer is a natural person), CDD, and
EDD16.14/16.15 High-Risk Natural Persons Any Activity Any Value CID,
CDD, and
EDD16.16
16.8,
16.9
16.10High-Risk circumstances Any Activity Any Value CID (if the customer is a natural person), CDD, and
EDD16.16
16.8,
16.9
16.10/11Third Party Transactions Any Activity Any Value CID (if the customer is a natural person), CDD, and
EDD16.20
16.8,
16.9
16.10/114.4.1. Ongoing Monitoring
Under Article 7 of the AML-CFT Decision, LEH are required to ensure that the documents, data or information obtained under CDD measures are up-to-date and appropriate by reviewing the records, particularly those of high-risk customer categories. Ongoing monitoring allows the LEH to ensure that the Exchange Business is being used in accordance with the customer or relationship profile developed through KYC during onboarding, and that transactions are normal, reasonable, and legitimate.
As per Paragraphs 16.9.11 and 16.11.7 of the Standards, where the customer is a natural person (when CDD must be applied) or a legal person or arrangement, the customer profile must be reviewed and updated either annually, or at least upon the expiry of the ID, the trade license or the ID of any person authorized to make transactions on behalf of the customer, whichever comes first. At this time, the LEH must conduct ongoing monitoring on the customer which must consist of the following:
• The original ID must be verified (in accordance with Paragraphs 16.8.3, 16.9.6 and 16.9.7) and its copy must be held in the records during the review of a customer profile; • CDD (and, where appropriate, EDD) must be repeated and the customer profile updated, including the information required under Paragraph 16.9.4 or 16.11.2 of this Chapter. • CDD and EDD must also be repeated whenever there is a change in the profile of the customer; • LEH must scrutinize the transactions concluded by a customer to ensure that transactions are consistent with its knowledge of the customer, the customer’s business, risk profile, the source of funds and where necessary, source of the customer’s wealth; and • LEH must review transaction monitoring results for the customer to determine whether any STR/SARs or other reports have been filed or whether the customer’s behavior has generated alerts.
Unless otherwise required, such as in the cases above mentioned, LEH should update the KYC information on customers and counterparties on a risk-based schedule, with KYC on higher-risk customers being updated more frequently. KYC updates should include a refresh of all elements of initial KYC, and in particular must ascertain whether:
• The customer/counterparty’s beneficial owners remain the same. • The customer continues to have an active status with the LEH Point of Sale system. • The customer/counterparty is domiciled in the same jurisdiction. • The customer/counterparty is engaged in the same type of business, and in the same geographies. • The customer/counterparty’s transactions continue to fit its profile and business, and are consistent with the business the customer expected to engage in when the business relationship was established, or the business that the LEH expected to engage in when it established the counterparty relationship.
If any of the above characteristics have changed, the LEH should risk-rate the customer/counterparty again.
Furthermore, LEH should conduct EDD when the revised risk rating demands it or if the customer/counterparty’s history of transactions is not consistent with its profile and the expectations established at account opening. In particular, if the customer/counterparty’s transactions/behavior have resulted in the filing of an STR/SAR with the FIU, the LEH should review the customer/counterparty profile and the activity that led to the report and make a determination as to whether the risk rating should be raised or the relationship should be terminated. LEH may consider requiring that the customer/counterparty update them as to any changes in its beneficial ownership. Even if this requirement is in place, however, LEH must not rely on the customer/counterparty to notify it of a change, but must still update KYC on a schedule appropriate to the customer’s risk rating.
4.5. Transaction Monitoring
As required by Article 7 of the AML-CFT Decision and Paragraph 16.24 of the Standards, LEH must continuously monitor all their transactions to ensure that the transactions conducted are consistent with the information they have about the customer, their type of activity and the risks they pose, including, when necessary, the source of funds. Transaction monitoring systems allow the LEH to monitor the transactions made by their customers in real-time and/or on a daily basis. All LEH should have a form of transaction monitoring system in place in order to monitor for any suspicious transactions to and from customers. Failure to have such a system in place may not only cost a LEH its reputation, but also lead to large fines and other penalties.
Transaction monitoring is distinct from the ongoing monitoring discussed in section 4.4.1. Both are required, but the purpose of transaction monitoring is not primarily to update the customer risk profile but to detect and investigate transactions that may need to be reported to the FIU because they are potentially related to illicit activity. While CDD review (as discussed in section 4.4.1) may take place once a year, transaction monitoring occurs in real time and is thus able to support prompt reporting to the FIU after the transaction takes place.
Under Article 4.2 (a) of the AML-CFT Decision and Paragraph 16.24.1 of the Standards, Transaction monitoring must be commensurate with the risk posed by the LEH’s size, scale, complexity, the nature and volume of its Exchange Business, the nature of its customer base, and the geographic areas in which it operates. The transaction monitoring system used by a LEH, whether automated or manual, must be able to flag unusual movements of funds or transactions for further analysis. Rules and parameters must take account of ML/FT typologies in the Exchange Houses sector.
When the monitoring system generates an alert, it must be investigated and either escalated or otherwise dispositioned in a timely fashion in order to support prompt reporting to the FIU. Transaction monitoring systems should create an audit trail of all activity related to alert generation, investigation, and disposition to have a clear understanding of the activity, and potentially report it to the relevant authorities.
For more details and information, please refer to the CBUAE Guidance for Licensed Financial Institutions on Transaction Monitoring Screening and Sanction screening9.
9 Available at https://www.centralbank.ae/en/cbuae-amlcft.
4.5.1. Indicative Risk Factors Associated with Transactions
The following is an indicative and non-exhaustive list of risk factors associated with transactions10.
• Customer’s behavior at point of origination: o Customer structures transaction in an apparent attempt to break up amounts to stay under any applicable CDD threshold to avoid reporting or other requirements. o Customer attempts a transaction, but given he or she would likely be subject to the CDD monitoring, cancels transaction to avoid reporting or other requirements. o Transaction is unnecessarily complex with no apparent business or lawful purpose o Number or value of transactions is inconsistent with financial standing or occupation, or outside the normal course of business of the customer in light of the information provided by the customer when conducting the transaction or during subsequent contact. o Customer offers a bribe or a tip, or is willing to pay unusual fees to have transactions conducted. o Customer has vague knowledge about amount of money involved in the transaction. o Customer makes unusual enquiries, threatens or tries to convince employees to avoid reporting. o Customer sends money internationally and then expects to receive an equal incoming transfer or vice versa. o Customer transfers money to illegal online gambling sites. Email addresses containing gambling references or transfers to countries with large numbers of internet gambling sites. o Customer wires money to higher-risk jurisdiction/country/corridor. o Customer transfers money to claim lottery or prize winnings o Customer transfers money to someone met only online or appears to have no familial relationship with the receiver and no explanation forthcoming for the transfer.
• Activity detected during monitoring (in many of these scenarios the customer’s activity may be apparent both during point-of-sale interaction and back-end transaction monitoring): o Transfers to the same person from different individuals or to different persons from the same individual with no reasonable explanation. o Unusually large aggregate wire transfers or high volume or frequency of transactions with no logical or apparent reason. o Customer uses aliases, nominees or a variety of different addresses. o Customers whose concentration ratio of transfers made to a jurisdiction is notably higher than what is to be expected considering overall customer base. o Customer transfers/receives funds from persons involved in criminal activities as per the information available. o A network of customers using shared contact information (such as address, telephone or e-mail) where such sharing is not normal or reasonably justifiable.
• Transactions received: o Transactions that are not accompanied by the required originator or beneficiary information. o Additional customer or transactional information was requested from an ordering counterparty but not received. o Large number of transactions received at once or over a certain period of time which do not seem to match the recipient’s usual past pattern. 10 FATF: Guidance-RBA-money-value-transfer-services.pdf (fatf-gafi.org)
4.6. Sanctions Obligations and Freezing Without Delay
Article 16.1 of the AML-CFT Law and Article 60 of the AML-CFT Decision require LEH to promptly apply directives issued by the Competent Authorities of the UAE for implementing the decisions issued by the United Nations Security Council under Chapter VII of the Charter of the United Nations (“UN”). In furtherance of this requirement, the Cabinet Decision 74 sets out the legal and regulatory framework in the UAE regarding Targeted Financial Sanctions (“TFS”).
For more information and details on their obligations in relation to their sanctions obligations LEH should consult Paragraph 16.25 of the Standards; the Executive Office of the Committee for Goods and Materials Subjected to Import and Export Control‘s “Guidance on Targeted Financial Sanctions for Financial Institutions and designated non-financial business and professions”; the “CBUAE Guidance for Licensed Financial Institutions on the Implementation of Targeted Financial Sanctions” as well as the “CBUAE Guidance for Licensed Financial institutions on Transaction Monitoring Screening and Sanctions screening”11.
Furthermore, LEH must sign up for the Integrated Enquiries Management System (IEMS) introduced by the FIU to automate and facilitate the execution process of requests for information, implementing decisions of public prosecutions and any other type of ML/FT requests. Via this system, the FIU can make requests to all LFIs simultaneously with the goal of processing requests and providing results to Law Enforcement Agencies more efficiently. For more information, LEH should consult the IEMS User Guide published by FIU12.
11 Available at: https://www.centralbank.ae/en/cbuae-amlcft
12 Available at: https://www.uaefiu.gov.ae/media/jtdnttby/integrated-enquiry-management-system.pdf4.7. Training
As per Paragraph 16.23 of the Standards LEH must provide comprehensive AML/CFT compliance training to all employees. The effective application of AML/CFT policies and procedures depends on the employees understanding not only of the processes they are required to follow, but also the risks these processes are designed to mitigate, and the possible consequences of those risks. Employees should remain abreast on an ongoing basis of emerging ML/FT typologies and new internal and external risks. The AML/CFT compliance training should be relevant to the LEH’s ML/FT risks, business activities and up to date with the latest legal and regulatory obligations and internal controls. It should be tailored to particular lines of business within the LEH, equipping employees with a sound understanding of specialized ML/FT risks they are likely to face, and their obligations in relation to those risks and must be provided to all new employees within thirty (30) calendar days from the date of joining. Thereafter, refresher training must be provided to all employees at regular intervals depending on the ML/FT risk exposure of each employee; for example, employees who deal directly with customers, products or services must be trained annually at a minimum. Refresher training must also be provided whenever there are changes in the legal and regulatory framework in force in the UAE or the LEH’s AML policy/procedures. Furthermore, the AML/CFT compliance training should be provided to relevant employees upon learning of a confirmed negative risk assessment result or audit finding, or other deficiency pertaining to the AML/CFT Program. Evidence for all trainings conducted must be retained for inspection by the CBUAE.
4.8. Independent Audit
The independent audit process helps the LEH assess the effectiveness and adequacy of its current processes, including by assessing the adequacy of the AML/CFT Program and checking for any inconsistencies between the policy and procedures and day-to-day operations in order to identify any weaknesses and deficiencies. Independent auditing must be undertaken regularly to review and assess the effectiveness of the AML/CFT compliance policies, procedures, systems and controls, and their compliance with the LEH’s obligations. As per Paragraph 16.31.1 of the Standards, the Compliance Officer’s function must undergo regular audit by the LEH’s internal audit department. In addition, under Paragraph 16.31.2 of the Standards, “agreed-upon procedures” for the review of the AML/CFT Compliance function must be performed by external auditors annually.
The independent audits, whether internal or external, should be undertaken by skilled and competent auditors. The internal audit department should be resourced with skilled and competent employees that understand the AML/CFT Program of the LEH. The audit should be commensurate to the level and sophistication of the LEH, and be updated to account for changes in risk assessments and the legal and regulatory framework in force in the UAE. The internal audit function should be accountable to the Board of Directors (or the Owner/Partners if there is no Board of Directors), independent of the audited activities and functions, and have sufficient authority, skills, expertise, and resources within the organization.
4.9. Record Keeping Requirements
Under Article 24 of the AML-CFT Decision, LEH must retain all records, documents, data and statistics for all transactions for a minimum period of five (5) years from the date of completion of the transaction or termination of the business relationship or from the closing date of the account. Records must be maintained in an organized manner so as to permit data analysis and, where relevant, the tracking of financial transactions. Records should be sufficient to permit reconstruction of individual transactions so as to provide, if necessary, evidence for prosecution of criminal activity. For more details and information please refer to paragraph 16.29 of the Standards.
4.10. Managing Employee Risk
As per Paragraphs 8.2 and 16.22 of the Standards, the LEH must implement an appropriate recruitment and Know Your Employee (“KYE”) process for hiring employees and confirm the background of applicants prior to placing them in employment. The level of vetting procedures applied should reflect the ML/FT risks to which individual employees are exposed in their assigned roles. The LEH should be aware of potential conflicts of interest for employees with AML/CFT responsibilities and should act to reduce or manage such conflicts of interest.
Furthermore, under Paragraph 16.28 of the Standards, the LEH must watch out for its employee’s behavior and be aware of possible indicators of illicit behavior displayed by employees, such as:
• An employee whose lifestyle cannot be supported by his/her salary, which may indicate receipt of tips or bribes. • An employee who is reluctant to take a vacation, which may indicate they have consented or are being forced to provide services to customers in violation of the law or company policy. • An employee who is associated with an unusually large number of transactions or a transaction in an unusually large amount, which may indicate they have consented or are being forced to provide services to customers in violation of the law or company policy.
5. Reporting Obligations
5.1. Reporting to the CBUAE
As per Paragraph 4.21 of the Standards, LEH must submit reports to the CBUAE, which may be updated from time to time in terms of the frequency and form of submission and their deadline. For the submission of periodical returns/reports via the online system, the LEH must obtain access to the CBUAE reporting portals, such as its Integrated Regulatory Reporting System, Remittance Reporting System and/or other applicable system.
5.2. Reporting to the FIU
All LEH should have procedures and systems in place to ensure that suspicious activity is reported to authorities in an appropriate and timely manner. LEH must take into account all information from both the ordering and beneficiary sides in order to determine whether an STR or SAR is to be filed.
As required by Article 15 of AML-CFT Law and Article 17 of AML-CFT Decision, LEH must file without any delay an STR or SAR or other report types with the FIU using the “goAML” portal when they have reasonable grounds to suspect that a transaction, attempted transaction, or funds constitute, in whole or in part, regardless of the amount, the proceeds of crime, are related to a crime, or are intended to be used in a crime. Under Article 24 of the AML-CFT Law, any person, including a LEH or their managers and employees, who violates on purpose or by gross negligence their statutory obligation to report a suspicion of money laundering and related predicate offences, financing of terrorism or illegal organisations is liable of the following sanctions:
• Imprisonment and fine of no less than AED100,000 and no more than AED1,000,000; or • Any of these two sanctions (i.e. imprisonment or fine of no less than AED100,000 and no more than AED1,000,000). • For more details and information, please refer to Paragraph 16.27 of the Standards as well as the “CBUAE Guidance for Licensed Financial Institutions on Suspicious Transaction Reporting”13. 13 Available at: https://www.centralbank.ae/en/cbuae-amlcft
6. Prohibition of Tipping Off
Under Article 25 of AML-CFT Law, anyone who notifies or warns a person or reveals any transaction under review in relation to suspicious transactions or being investigated by the competent authorities is punishable by a penalty of imprisonment for no less than six months and/or a fine of no less than AED 100,000 and no more than AED 500,000. Any such action is known as “tipping off.” As per Paragraph 16.27 of the Standards, the prohibition on tipping off means that the LEH or its employees must not inform customers or any persons or third parties, either directly or indirectly, that their transactions are subject to monitoring, under investigation or have been reported to the FIU as suspicious transactions. The Compliance Officer should ensure that all employees of the LEH are aware of the consequences of tipping off. Sufficient AML/CFT training should be provided to all employees to ensure that they understand what constitutes tipping off and how to avoid it.
Annex1 - Synopsis of the Guidance
Purpose of this Guidance Purpose The purpose of this Guidance is to assist the understanding of risks and effective performance by the Licensed Exchange Houses ("LEH") of their AML/CFT statutory obligations. The FATF's Mutual Evaluation Report of the UAE issued in April 2020 stated that the Money or Value Transfer Services' sector, including the Exchange Houses' sector, is weighted as highly important in terms of risk and materiality in the UAE. The inherent risk and materiality of these sectors has been notably increased by their exposure to cash transactions. Applicability This Guidance applies to all Exchange Houses that are licensed and supervised by the CBUAE. Risks Related to the Exchange House Sector The Exchange House sector provides widely used financial services to diverse customer sectors. While the majority of its Exchange Business is legitimate in purpose, it can be abused to facilitate illegal activity, including terrorist financing, money laundering, and other type of criminal activity. This is due to the simplicity and speed of transactions, worldwide reach, global regulatory disparity and often cash-based nature of transactions. Exchange Houses may also potentially be abused by criminal groups and corrupt employees or agents co-operating with criminals, who may seek to own an Exchange House outright, or indirectly through an associate or could seek to coerce employees through financial incentives. Regulation and Supervision of Exchange Houses The Exchange Houses sector is regulated by the Regulations and the Standards issued by the CBUAE. For more detail and information, please refer to Chapter 16 on AML/CFT Compliance of the Standards for the Regulations Regarding Licensing and Monitoring of Exchange Business (Version 1.20 of November 2021 amending Version 1.10 of February 2018 ("The Standards")). LEH are supervised by the CBUAE, which may examine the activities of the LEH at any time it deems appropriate to ensure proper compliance with their statutory obligations under the legal and regulatory framework in the UAE, or impose supervisory action or administrative and financial sanctions for violations. AML/CFT Compliance Program for LEH AML/CFT Program LEH must carefully design, document and effectively implement an AML/CFT Program in line with the provisions of the Standards, AML-CFT Law, and AML-CFT Decision. When designing or updating their AML/CFT programs, the scope of the AML/CFT Program should be proportionate to the level of the risk posed by the LEH's size, scale, complexity, the nature and volume of its Exchange Business, the nature of its customer base, the business relationships it maintains, and the geographic areas in which it operates. Risk Assessment LEH must develop a risk assessment in order to understand how and to what extent it is vulnerable to ML/TF, and help determine the nature and extent of AML/CFT resources necessary to mitigate and manage that risk, which should cover all relevant factors including but not limited to:
• Customer risk;
• Products and services risk;
• Delivery channel risk;
• New technologies risk;
• Jurisdiction or geographic risk;
• Counterparty risk; and
• Other areas of risk.Policies and Procedures LEH must establish and implement comprehensive and documented AML/CFT policies and procedures to enable them to effectively manage and mitigate the risks identified. They must be approved, reviewed and updated, annually at a minimum, to ensure that they are consistent with the legal and regulatory framework in the UAE and other international best practices, and effective in mitigating existing as well as emerging ML/FT risks. Governance and the Compliance Officer The core of an effective risk-based program is an appropriately experienced AML/CFT Compliance Officer who understands the LEH's risks and obligations and who has the resources and autonomy necessary to ensure that the LEH's program is effective. The role of Compliance Officer must be limited to tasks related to AML/CFT compliance and not be combined with any other functions of the LEH to avoid conflict of interest from multiple roles. The LEH must also appoint an Alternate Compliance Officer. Customer Due Diligence and Ongoing Monitoring The goal of the CDD process is to ensure that LEH understand who their customer is and the purpose for which the customer will use the LEH's services. Where an LEH cannot satisfy itself that it understands a customer, then it must not accept the customer. If there is an existing business relationship, the LEH should not continue it. LEH should also consider filing an suspicious transaction report ("STR") or suspicious activity report ("SAR") or other report types to the FIU as discussed in section 5 of the Guidance.
The Standards require three types of KYC processes that must be applied depending on the customer's risk and the nature of the transaction and customer. These are Customer Identification (CID); Customer Due Diligence (CDD); and Enhanced Due Diligence (EDD). Please refer to the table in Section 4.4 on when to use each KYC measure and to the respective paragraphs in the Standards for the detailed requirements.
LEH are required to ensure that the documents, data or information obtained under CDD measures are up-to-date and appropriate by reviewing the records, particularly those of high-risk customer categories. Unless otherwise required, LEH should update the KYC information on customers and counterparties on a risk-based schedule, with KYC on higher-risk customers being updated more frequently. When customer's characteristics has changed, LEH should risk-rate the customer again, and, where necessary, conduct EDD.Transaction Monitoring LEH must continuously monitor all their transactions to ensure that the transactions conducted are consistent with the information they have about the customer, their type of activity and the risks they pose, including, when necessary, the source of funds. All LEH should have a form of transaction monitoring system in place in order to monitor for any suspicious transactions to and from customers; failure to have such a system in place may not only cost an LEH its reputation, but also lead to large fines and other penalties. For more information and details, please consult the CBUAE's Guidance for Licensed Financial Institutions on Transaction Monitoring Screening and Sanction screening. Sanctions Obligations and Freezing Without Delay LEH are required to promptly apply directives issued by the Competent Authorities of the UAE for implementing the decisions issued by the United Nations Security Council under Chapter VII of the Charter of the United Nations and the requirements set by Cabinet Decision 74 of 2020 regarding Targeted Financial Sanctions. For more information and details, please consult the Standards, the Executive Office of the Committee for Goods and Materials Subjected to Import and Export Control's Guidance on Targeted Financial Sanctions for Financial Institutions and designated non-financial business and professions, the CBUAE's Guidance for Licensed Financial Institutions on the Implementation of Targeted Financial Sanctions as well as the CBUAE's Guidance for Licensed Financial institutions on Transaction Monitoring Screening and Sanctions screening.
Furthermore, LEH must sign up for the Integrated Enquiries Management System (IEMS) introduced by the FIU to automate and facilitate the execution process of requests for information, implementing decisions of public prosecutions and any other type of ML/FT requests.Training LEH must provide comprehensive AML/CFT compliance training to all employees, which should be relevant to the LEH's ML/FT risks, business activities and up to date with the latest legal and regulatory obligations and internal controls. It should be tailored to particular lines of business within the LEH, equipping employees with a sound understanding of specialized ML/FT risks they are likely to face and their obligations in relation to those risks, and provided to all new employees within thirty calendar days from the date of joining and regularly thereafter proportionate to their ML/FT risk exposure. Independent Audit Independent auditing must be undertaken regularly to review and assess the effectiveness of the AML/CFT compliance policies, procedures, systems and controls, and their compliance with the LEH's obligations by the LEH's Internal Audit Department. In addition, "agreed-upon procedures" for the review of the AML/CFT Compliance function must be performed by external auditors annually. Record-Keeping LEH must retain all records, documents, data and statistics for all transactions for a minimum period of five (5) years from the date of completion of the transaction or termination of the business relationship or from the closing date of the account. Records must be maintained in an organized manner so as to permit data analysis and, where relevant, the tracking of financial transactions. Managing Employee Risk The LEH must implement an appropriate recruitment and Know Your Employee ("KYE") process for hiring employees and confirm the background of applicants prior to placing them in employment. The level of vetting procedures applied should reflect the ML/FT risks to which individual employees are exposed in their assigned roles. Reporting Obligations Reporting to the CBUAE LEH must submit reports to the CBUAE, which may be updated from time to time in terms of the frequency and form of submission and their deadline. For the submission of periodical returns/reports via the online system, the LEH must obtain access to the CBUAE reporting portals, such as its Integrated Regulatory Reporting System ("IRR"), Remittance Reporting System ("RRS") and/or other applicable system. Reporting to the FIU LEH must file without any delay a STR, SAR or other report types with the FIU using the "goAML" portal when they have reasonable grounds to suspect that a transaction, attempted transaction, or funds constitute, in whole or in part, regardless of the amount, the proceeds of crime, are related to a crime, or are intended to be used in a crime. Please consult the CBUAE's Guidance for Licensed Financial institutions on Suspicious Transaction Reporting for further information. Prohibition of Tipping Off The prohibition on tipping off means that the LEH or its employees must not inform customers or any persons or third parties, either directly or indirectly, that their transactions are subject to monitoring, under investigation or have been reported to the FIU as suspicious transactions. Guidance for Licensed Financial Institutions Providing Services to Legal Persons and Arrangements
Effective from 7/6/20211. Introduction
1.1. Purpose of this Guidance
Article 44.11 of the Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations charges Supervisory Authorities with “providing Financial Institutions…with guidelines and feedback to enhance the effectiveness of implementation of the Crime-combatting measures.”
The purpose of this Guidance is to assist the understanding and effective performance by the United Arab Emirates Central Bank’s (“CBUAE”) licensed financial institutions (“LFIs”) of their statutory obligations under the legal and regulatory framework in force in the UAE. It should be read in conjunction with the CBUAE’s Procedures for Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations (issued by Notice No. 74/2019 dated 19/06/2019) and Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations for Financial Institutions (issued by Notice 79/2019 dated 27/06/2019) and any amendments or updates thereof.1 As such, while this Guidance neither constitutes additional legislation or regulation nor replaces or supersedes any legal or regulatory requirements or statutory obligations, it sets out the expectations of the CBUAE for LFIs to be able to demonstrate compliance with these requirements. In the event of a discrepancy between this Guidance and the legal or regulatory frameworks currently in force, the latter will prevail. This Guidance may be supplemented with additional separate guidance materials, such as outreach sessions and thematic reviews conducted by the Central Bank.
Furthermore, this Guidance takes into account standards and guidance issued by the Financial Action Task Force (“FATF”), industry best practices and red flag indicators. These are not exhaustive and do not set limitations on the measures to be taken by LFIs in order to meet their statutory obligations under the legal and regulatory framework currently in force. As such, LFIs should perform their own assessments of the manner in which they should meet their statutory obligations.
This Guidance comes into effect immediately upon its issuance by the CBUAE with LFIs expected to demonstrate compliance with its requirements within one month from its coming into effect.
1 Available at https://www.centralbank.ae/en/cbuae-amlcft
1.2. Applicability
Unless otherwise noted, this guidance applies to all natural and legal persons, which are licensed and/or supervised by CBUAE, in the following categories:
• National banks, branches of foreign banks, exchange houses, finance companies, payment service providers, registered hawala providers and other LFIs; and
• Insurance companies, agencies, and brokers.
1.3. Legal Basis
This Guidance builds upon the provisions of the following laws and regulations:
1.4. Definitions
Key TermsBeneficial owner: The natural person who owns or exercises effective ultimate control, directly or indirectly, over a client; or the natural person on whose behalf a transaction is being conducted; or the natural person who exercises effective ultimate control over a legal person or legal arrangement.
Legal person: Any entities other than natural persons that can establish in their own right a permanent customer relationship with a financial institution or otherwise own property. This can include companies, bodies corporate, foundations, partnerships, or associations, along with similar entities.
Legal arrangement: A relationship established by means of a contract between two or more parties which does not result in the creation of a legal personality. Examples include trusts or other similar arrangements. Many legal arrangements allow for ownership, control, and enjoyment of funds to be divided between at least two different persons.
Settlor: A natural or legal person who transfers the control of his funds to a trustee under a trust document.
Trust: A legal relationship in which a settlor places funds under the control of a trustee for the interest of a beneficiary or for a specified purpose. These assets constitute funds that are independent of the trustee's own estate, and the rights to the trust assets remain in the name of the settlor or in the name of another person on behalf of the settlor.
Trustee: A natural or legal person who has the rights and powers conferred to him by the settlor or the trust, under which he administers, uses, and acts with the funds of the settlor in accordance with the conditions imposed on him by either the settlor or the trust.
2. Understanding and Assessing the Risks of Legal Persons and Arrangements
Legal persons and arrangements are critical to the conduct of business, charitable activity, estate planning, and many other activities. They have a wide variety of acceptable and desirable purposes, and the vast majority of legal persons and arrangements are engaged solely in licit behaviour.
Nevertheless, certain aspects of legal persons and arrangements are acknowledged to pose risk for LFIs that accept such entities as customers. Most importantly, the use of legal persons and arrangements to manage funds or do business can obscure or conceal the identity of the individuals who are truly controlling, directing, or benefiting from the services the LFI offers its legal person or legal arrangement customer. This concealment can allow illicit actors to abuse services offered by LFIs in order to launder the proceeds of crime, engage in terrorist financing, evade United Nations or UAE sanctions, and threaten the integrity of the UAE financial system and the security of the State.
Legal persons and arrangements are attractive to participants in illicit finance—including money laundering (ML), the financing of terrorism (TF), and the financing of proliferation (PF)—because these entities offer the opportunity to transact anonymously, or nearly anonymously, through complex and/or opaque corporate structures. Section 2.1 discusses the ways that legal persons and arrangement can be abused to conceal illicit transactions from financial institutions.
It is important to be aware, however, that not all legal persons and arrangements pose equal risk of abuse. The vulnerabilities arising from the basic characteristics of legal persons and arrangements can be enhanced or mitigated through the formation process and other controls jurisdictions apply to legal persons and arrangements. Thus, it is critical for LFIs seeking to understand the risks of their customer base to be aware of the presence or absence of these features and controls in the jurisdiction of formation. Section 2.2 below discusses specific aspects of a control regime and how these can impact vulnerability.
2.1. ML/TF Risks Legal Persons and Arrangements Pose to LFIs
Legal persons and arrangements offer many advantages to illicit actors. Most importantly, however, they could be abused to hide the identity of natural persons and allow bad actors to seek to open an account or carry out a transaction with an LFI under a name other than their own. Weak laws governing the formation of legal persons and arrangements, could allow for bad actors to abuse legal persons and arrangements and enable them to conduct a transaction or transactions almost without the LFI understating the real risks and the involvement of the bad actors—an action that would otherwise be prohibited under the laws of most jurisdictions. This ability to conceal identity has a number of ramifications for financial institutions.
2.1.1. Obscuring Identity/Beneficial Ownership
Individuals can use legal persons and arrangements to obscure or conceal their involvement in a transaction. In many jurisdictions, the individuals who truly own, control, direct, or benefit from a transaction—known as the beneficial owners—are not required to reveal their identities to the authorities. Individuals who are wanted criminals, known terrorist financiers, or connected to heavily sanctioned jurisdictions can form opaque companies in lower-risk jurisdictions and seek financial services under the name of a legal person or arrangement they control.
Even in jurisdictions where legal persons and arrangements are required to report their beneficial ownership, illicit actors can seek to conceal their ownership interest through the use of complex corporate structures, intermediaries, and nominees, as discussed below.
2.1.2. Obscuring the Purpose of an Account or Transaction
Legal persons, particularly businesses, engage in a wide variety of transactions with a wide range of counterparts. Depending on its size and the nature of its business, a legal person customer might be likely to send and receive far larger and more irregular transfers than would an individual—many of them with counterparties that are also legal persons. For example, a company that manufactures for export may send payments to suppliers in a number of foreign jurisdictions, and receive payments from purchasers in different jurisdictions.
The variety and unpredictability of transactions carried out by legal persons can make it more difficult to identify behaviour that is unusual or has no obvious economic purpose. This is especially true when the counterparts are also opaque legal persons or arrangements. For example, a company may seek to reduce its tax burden by claiming that certain transfers are tax-deductible expenses, when in reality they are payments to a legal person with the same beneficial owners as the originating company.
2.1.3. Obscuring Source of Funds or of Wealth
Legal persons can also be abused by individuals seeking to hide the source of an incoming transfer. For example, a politically exposed person (PEP) might receive a transfer that supposedly represents investment returns from a company located in another jurisdiction. Without knowing the beneficial owners of the originating company, it is difficult to say whether the transfer does in fact represent a return on investments, or whether it is in fact a bribe or somehow related to corruption.
The involvement of legal persons and arrangements can also make it more difficult for LFIs to identify a customer’s true source of wealth. A legal person that is represented as a profitable business, for example, may in fact be a shell company that merely passes on income from illicit sources.
2.1.4. Common Typologies of Abuse of Legal Persons and Arrangements
The use of shell companies: Shell companies, commonly defined as companies that have no significant operations or related assets, may have legitimate business purposes. A shell company’s lack of employees and physical presence, however, makes it possible to abuse it as a vehicle for illicit transactions. These features also make it very difficult for law enforcement agencies in jurisdictions where the company operates to investigate its owners and activities.
Case Study: Shell CompaniesA group of individuals conducted an investment fraud scheme which promised victims high returns on an initial investment of USD 35,000. As part of the scheme, the group established a complex web of bank and brokerage accounts and shell companies in the United States and several foreign jurisdictions. The group also opened cash management accounts at brokerages utilizing the shell corporations. Investors were told to send their investment funds to the accounts established utilizing the shell corporation names. Once in this account, the funds were transferred to secondary accounts. From these accounts, the funds were then disbursed to various foreign and domestic accounts and liquidated through the use of checks, debit cards, and ATM cards.
Complex ownership and control structures: Individuals who seek to hide their interest in a company may create multiple layers of ownership and control that make it difficult to identify who really owns and controls the company. For example, a company may be owned by a second legal person, that is in turn owned by three legal persons, that are controlled via a debt financing arrangement. Where directors are required to be reported to the registering authority, a company may name legal persons as directors, further complicating the control structure.
Case Study: Complex OwnershipCompany G was 95% owned by Mr. A and 5% by Mr. B. Company G purchased a power generator from Company K, owned by Company R in the Cayman Islands. Company R was linked to Panamanian Foundation P, which had Mr. A and his spouse as beneficiaries. Company G leased the generator to Company E, receiving amounts cleared by Company L The funds were drawn against Company K’s bank account, and Company G made payments to Company K to settle a debt. The funds were credited to the accounts of Companies S, T and R.
Use of nominee shareholders and directors: Nominee arrangements involve an individual (the nominator) assigning his or her shares or voting rights to a second individual (the nominee) who agrees to act in accordance with the wishes of the nominator. The nominee is listed as the shareholder or director of record, but in fact has no power to direct the company and does not have a legal ownership right over the benefits accruing to the ownership interest, such as dividends. Nominee relationships may be contractual or based on a handshake agreement. Such informal arrangements often involve a nominator and nominee who are close associates or family members.
Case Study: Informal Nominee Shareholders and DirectorsA Russian state agency contracted with Company 1 and Company 2 to perform software development. Neither company had the relevant expertise; they each hired subcontractors to do the work. The majority of funds received by both companies were funnelled into foreign shell companies, invested in real estate, or used to purchase luxury goods. Company 2 had previously been owned by Mr. X, who transferred the ownership to complicit associates. The real estate company that received the investment funds was owned by Mr. X’s daughter. Mr. X also controlled the nominal owners of Company 1, who received a salary from the company. Mr. X was the brother of the director of the state agency’s research department.
Use of intermediaries: Individuals seeking to create complex, opaque corporate structures will often seek out professional intermediaries (lawyers, accountants, and trust and company service providers (TCSPs)) who are experienced in bending and manipulating the rules in the jurisdiction where the legal person or arrangement is formed. Intermediaries may create new legal persons or arrangements, or sell the rights to existing legal persons that appear to have been in operation for some time. These intermediaries may also serve as directors, nominees, or trustees of the resulting legal persons and arrangements.
Case Study: Use of IntermediariesCompanies registered in New Zealand by a Vanuatu-based TCSP operated by New Zealand citizens were suspected of acting as shell companies that facilitated crime in foreign jurisdictions. The TCSP acted as nominee shareholders and provided nominee directors who resided in jurisdictions such as Vanuatu, Panama and the Seychelles. The TCSP also provided a New Zealand-based nominee director to satisfy the legal requirement to have a New Zealand resident director and address. By 2010, the TCSP had registered approximately 2,000 companies in New Zealand on behalf of clients in foreign jurisdictions. Its address, in Auckland, was used as the registered office for most of the companies. Authorities suspect that at least 73 of these companies facilitated crimes in foreign jurisdictions.
2.2. Features and Controls that Mitigate the Risk of a Legal Person or Arrangement
At a high level, features and controls that affect the vulnerabilities of legal persons and arrangements can be divided into four categories:
• The formation process and requirements to establish the legal person or arrangement; • The identification of the individuals actually owning and controlling legal persons and arrangements; • The reporting and recordkeeping requirements imposed on companies throughout their lifetime; and • The formation authority’s supervisory regime and enforcement tools.
The subsections that follow briefly discuss the various measures that—if effectively implemented—can help mitigate the vulnerabilities of legal persons and arrangements.
LFIs should be aware of the risks associated with all customer types, including legal persons and arrangements established outside the UAE. Appropriately assessing these risks will often involve developing an understanding of the controls in place to ensure transparency.
CBUAE recognizes that LFIs do not control the legal frameworks governing their customers. Nevertheless, CBUAE recommends that LFIs familiarize themselves with the features of the company forms most commonly found within their customer base, and the controls in place in the jurisdictions where their legal person customers are most commonly registered. LFIs should also consider seeking some or all of the following information in order to understand legal person and legal arrangement risks, particularly when conducting enhanced due diligence on legal person and legal arrangement customers that pose higher risks.
2.2.1. Formation Requirements and Process
Abuse of legal persons and arrangements for ML/TF/PF often includes the creation of complex ownership structures with many such entities—including entities of different types and in different jurisdictions; the use of one-time ‘disposable’ entities that are abandoned after they have served their purpose; or the use of previously inactive ‘shelf companies. In addition, illicit actors will be able to more easily transact anonymously if they are required to reveal only minimal information during the formation process, can rely on nominees, or can complete processes without face-to-face interaction. For these reasons, legal persons and arrangements in jurisdictions whose formations processes allow for rapid, remote, and inexpensive formation and registration may be more attractive to illicit actors.
2.2.2. Identification and Reporting of Beneficial Owners
Because anonymity is one of the greatest attractions for illicit actors who seek to abuse legal persons and arrangements, they are likely to gravitate towards jurisdictions and company forms that require them to provide minimal information about the entities and themselves and that make it difficult for third parties to identify who in fact owns and controls the entity. The following controls that may be applied by the jurisdiction registering the entity in question can, to a certain extent, reduce the vulnerabilities created by corporate opacity.
• The registering authority collects key information about the company (such as name, address, and the names of directors) at formation and makes it available to the public; • The registering authority collects the identities of all beneficial owners, or all beneficial owners owning at least a given percentage of the company, at the time of establishment, and makes this information available to domestic and foreign law enforcement, as well as AML/CFT regulated entities. o The threshold for identifying ownership should be in line with international and UAE standards. o Where the registering authority applies a threshold that exceeds 25% of the ownership interests in a legal person, LFIs should be aware that the customer is not required to report all individuals qualifying as beneficial owners in the UAE; • The legal person or arrangement is prohibited from being owned by another legal person or arrangement; • Nominee shareholders and directors are prohibited, or are appropriately regulated.
2.2.3. Reporting and Recordkeeping
Unlike individuals, legal persons and arrangements can swiftly change fundamental elements of their identity, rendering information provided during the formation process obsolete. Legal persons and arrangements can also compartmentalize information about themselves so that no single individual possesses full information about the entity. Because legal persons and arrangements abused for ML/TF/PF may not engage in licit commercial activity and may be controlled by only a small number of closely connected individuals, there is little commercial rationale for such entities to maintain adequate books and records. Illicit actors take advantage of these features by purchasing already-established companies “off the shelf;” selling companies to new owners; changing the company name; or failing to maintain records of their ownership. These vulnerabilities can, to a certain extent, be mitigated through effective controls, such as:
• Legal persons and arrangements are required to promptly update the registering authority if their key information (including beneficial ownership) changes; • Legal persons and arrangements are required to appoint a resident agent in the jurisdiction where they are established to respond to inquiries; • Legal persons and arrangements are required to make annual financial reports to their registering authority and/or to undergo a regular audit and provide the audit report to their registering authority.
2.2.4. Supervision
The effectiveness of any regime of controls over legal persons and arrangements depends on the consistency with which such controls are enforced and on the sanctions available to the supervisor and law enforcement.
• Legal persons and arrangements are monitored by their supervisor for their compliance with requirements; • The supervisor can and does levy substantial penalties, whether civil or criminal, for violations of these requirements.
3. Legal Persons and Arrangements in the UAE
The UAE has a complex regime for formation of legal persons and arrangements, with 39 corporate registrars across the Emirates, the Commercial Free Zones (CFZs), and the Financial Free Zones (FFZs). Historically, each registrar has its own processes, but following the passage of AML-CFT Decision, which institutes common basic standards for all registrars, these processes are being harmonized across the UAE.
Certain information on legal persons doing business in the UAE is publicly available through the National Economic Register. For entities with a UAE business license, the National Economic Register contains the entity’s license number, address, business activities, and the name of a manager. LFIs are encouraged to consult the Register when conducting CDD on legal persons, but should not rely on information contained in the Register without independently verifying it with the customer.
3.1. Identification of Beneficial Owners
Under AML-CFT Decision, all registrars of legal persons in the UAE must comply with the following requirements:
• Registrars must provide the public with information on the types and features of companies they establish, the process for creating those companies, and the process by which members of the public can obtain information on those companies, including on the beneficial owner(s). • Registrars must obtain and maintain certain basic information on each company they register, including its name, address, a list of directors, its legal form, and its founding statutes. • Registrars must identify the beneficial owners of each company they register, defined as any individual owning or controlling at least 25 percent of the company.
In addition, all legal persons in the UAE are required to:
• Maintain accurate and up to date information on their shareholders and beneficial owners; • Identify nominee shareholders and directors to their Registrar; and • Appoint an individual resident in the UAE to be responsible for providing this information to the Registrar.
Cabinet Decision No. (58) of 2020 Regulating the Beneficial Owner Procedures further defined these requirements. All legal persons in the UAE must be licensed or registered, must identify their beneficial owners, and must hold accurate, up-to-date information on their beneficial owners in a Register of Beneficial Owners. They must also report the same information to the relevant registrar. The Resolution also requires that nominee directors identify themselves to the legal person for which they serve as director, and this information must also be included in the legal person’s Register.
There are certain limited exemptions to this requirement. For example, legal persons that are publicly traded on a stock exchange, or that are owned by such a company, do not have to identify or report their beneficial owners because of other transparency-related measures and obligations associated. In addition, if no individual meets the threshold by owning at least 25% of a legal person, that entity can report an individual who controls the entity (such as its managing director) instead of a true beneficial owner.
Together, these requirements aim to ensure that customers that are legal persons established and registered under the laws of the UAE must identify their beneficial owners and must always have up-to-date information on these individuals available. LFIs cannot rely solely on customers’ statements and must verify the identity of beneficial owners independently. But a UAE-based legal person customer that claims to be unfamiliar with the requirements, or represents that it has never been required to identify its beneficial owners, may not be in compliance with the law and should be treated as at least high risk.
3.2. Legal Arrangements Under UAE Law
Two types of legal arrangements can be formed under UAE law:
• Trusts can be formed in the Mainland as well as in the Dubai International Financial Centre (DIFC) and the Abu Dhabi Global Market (ADGM). In a trust arrangement, the owner of certain funds, known as the settlor, places these funds under the control of a trustee for the interest of a beneficiary or for a specified purpose. These assets constitute funds that are independent of the trustee's own estate, and the rights to the trust assets remain in the name of the settlor or in the name of another person on behalf of the settlor. • Awqaf (singular waqf), also known as endowments, can be created on the Mainland. Awqaf are a form of legal arrangement created according to shari’a law. A waqf allows a property owner to endow certain assets (often real property, but also shares or other income-producing assets) for the benefit of family members or a charitable cause. The endower loses control and ownership of the assets, which are registered as endowed and managed by a supervisor or trustee. Many awqaf are directly managed by the General Authority for Islamic Affairs and Endowments, but others are privately superintended.
Under AML-CFT Decision, Articles 9 and 37, trustees of legal arrangements, or persons holding analogous positions in other legal arrangements, are required to hold accurate and up-to-date information on the beneficial owners of the trust or other legal arrangement. For legal arrangements, the beneficial owners are defined as the settlor, the trustee, and the beneficiaries or identifiable class of beneficiaries, along with any other individual exercising ultimate effective control over the legal arrangement. Under Article 9 of AML-CFT Decision, LFIs must identify these individuals as the beneficial owners of their legal arrangement customers.
In both cases, it is important for financial institutions to be aware that these legal arrangements allow for an individual to legally hold and control funds that he or she does not own and does not have the right to benefit from. A trustee of a trust or waqf may open an account for trust funds under his or her own name, so that the account appears to belong to an individual rather than a legal arrangement. Although trustees are required to disclose their status, LFIs, as part of Customer Due Diligence (CDD), should take a proactive approach to identifying whether a customer is a trustee. This may include directly asking customers whether they are acting as trustees.
3.3. Economic Substance Requirements
Under Cabinet Resolutions (31) of 2019, (7) of 2020, and (57) of 2020, UAE legal persons operating in certain sectors with relevant income must meet requirements related to the level of core business activities that they carry out in the UAE (the Economic Substance Test). All firms conducting any of the following activities must pass the annual Economic Substance Test:
• Banking; • Insurance; • Investment Funds Management; • Lease-Finance; • Headquarters operations; • Shipping; • Holding Company activities; • Intellectual Property; • Distribution and service centres.
In order to pass the test, these firms are required to make an annual report, the Economic Substance Report, to their registrar showing that they in fact carry out core income-generating activities within the UAE, that these activities are directed and managed from the UAE, that the firms maintain an appropriate number of employees, and that the firms have appropriate physical premises. The report is then reviewed by the Federal Tax Authority, which makes a determination as to whether the criteria for economic substance have been satisfied. The Economic Substance Report is not currently available to financial institutions directly, but LFIs may request an attested copy of the Report from their customer or prospective customer.
The Economic Substance Test could help reduce the likelihood that UAE companies in these sectors are shell companies. The Economic Substance Test is retroactive, however, with companies required to submit Reports at the end of the twelve-month period in which the qualifying activity took place. In addition, Reports may not be promptly reviewed. LFIs should not rely on a customer’s assertion that it has passed the Economic Substance Test and must conduct appropriate customer due diligence, as discussed in section 4.3 below. This may include requesting the customer’s Economic Substance Report from the customer itself.
4. Mitigating Risk
Legal persons and arrangements are an important part of LFIs’ customer base and of economic activity in the UAE. However, legal persons and arrangements create real, and diverse, risks for financial institutions. LFIs are not expected to prohibit legal person and arrangement customers. Instead, they must understand, manage, and mitigate the risk through the appropriate application of preventive measures required under AML-CFT Decision and CBUAE directives and guidance documents.
This section describes LFIs’ obligations under UAE Law with specific reference to legal persons and arrangements. It is not a comprehensive discussion of all requirements imposed on LFIs. LFIs should consult the Laws and regulations including AML-CFT Decision and the CBUAE’s Anti-Money Laundering the Combating the Financing of Terrorism and Illegal Organizations Guidelines. The controls discussed below must be integrated into the LFI’s larger AML/CFT compliance program, and supported with appropriate governance and training.
4.1. Requirements for Legal Person and Arrangement Customers Under AML-CFT Decision
Under Article 8(b) of AML-CFT Decision, when conducting CDD on legal persons and arrangements, LFIs must collect the following information and verify it based on documents from a reliable and independent source:
• The name [this may not apply for legal arrangements], Legal Form and Memorandum of Association; • Headquarters’ office address or the principal place of business; in addition, if the legal person or arrangement is a foreign entity, the name and address of its legal representative in the State; • Articles of Association or any similar documents, approved by the relevant authority within the State; • Names of relevant persons holding senior management positions in the legal person or legal arrangement.
Legal persons and arrangements, by definition, cannot take action on their own and must be represented by a natural person. Therefore, for all legal persons and arrangements the LFI must verify that the individual acting on behalf of the customer is authorized to do so, and conduct CDD on that person as required by Article 8(a) of AML-CFT Decision.
In addition to the information described above, under Article 9 of AML-CFT Decision, the LFI must take reasonable measures to identify the beneficial owner(s) of all legal person and legal arrangement customers.
• For legal persons, LFIs must at least obtain and verify the identity of all individuals who, individually or jointly, have a controlling ownership interest in the legal person of 25% or more. If no individual can be identified, the LFI must identify the individual(s) holding the senior management position(s) within the legal person customer. • For legal arrangements, LFIs must verify the identity of the settlor and the trustee (or anyone holding equivalent positions for non-trust legal arrangements), the beneficiaries or class of beneficiaries, and any other individuals in control of the legal arrangement. LFIs must also obtain sufficient information on the beneficial owners of a legal arrangement to enable verification of the beneficial owner when paying trust funds to the beneficial owner, or when the beneficial owner begins to exercise his or her legally acquired rights. (This may take place, for example, when a beneficiary of a trust reaches his or her majority and takes full control and ownership of the trust funds.)
As stipulated by Article 10 of AML-CFT Decision, LFIs may omit collecting information from the customer to identify the beneficial owner of a legal person or arrangement customer only in two narrowly defined circumstances, which both apply to legal persons only:
a) The customer is a company listed on a regulated stock exchange and subject to disclosure requirements that ensure adequate transparency with regards to the customer’s beneficial owner(s); b) A subsidiary whose majority shares or stocks are held by the shareholders of the holding company.
In both cases, LFIs must still identify the beneficial owner(s) using reliable public sources. LFIs must also verify that the customer does in fact qualify for the exemption. LFIs remain responsible for using a risk-based approach and for ensuring that they understand their customer. LFIs should not seek to take advantage of this exemption if they cannot identify the beneficial owner(s) using reliable public sources. LFIs are unlikely to find reliable public information on the beneficial owners of privately-held holding companies.
In all cases, LFIs are also required by Article 8.4 of AML-CFT Decision to understand the customer’s ownership and control structure.
4.2. The Risk-Based Approach, Customer Risk Rating, and the Institutional Risk Assessment
LFIs should take a risk-based approach to the preventive measures they put in place for all customers, including legal persons and arrangements. A risk-based approach means that LFIs should dedicate compliance resources and effort to customers, business lines, branches, and products and services in keeping with the risk presented by those customers, business lines, branches, and products and services, as assessed in accordance with Article 4 of AML-CFT Decision.
The risk-based approach has three principal components:
1. Conducting an enterprise risk assessment, as required by Article 4.1 of AML-CFT Decision.
The enterprise risk assessment should reflect the presence of legal persons and arrangements in an LFI’s customer base. The risk assessment should consider the most common forms of legal persons and arrangements in the LFI’s customer base and should assess the risks of each form. This assessment should carefully consider and incorporate the ML/TF risks legal persons and arrangements pose to LFIs discussed above (section 2.1), although LFIs may have legal person and arrangement customers from outside the UAE whose risks will also need to be assessed. These assessments should in turn be reflected in the LFI’s inherent risk rating.
In addition, the LFI’s risk assessment should take into consideration the strength of the controls that the LFI has in place to mitigate the risks posed by its legal person and arrangement customers, including the preventive measures discussed below.
2. Identifying and assessing the risks associated with specific customers.
The LFI should assess the risk of each customer to identify those that require enhanced due diligence (EDD). Customer risk assessment for legal person and arrangements should incorporate at least all elements of the customer risk assessment for individuals, but should apply them both to the legal person or arrangement customer itself and to the individuals prominently associated with it. For example, the assessment of the legal person or arrangement’s jurisdictional risk should take into consideration not just the customer’s jurisdiction of establishment, but also the residence and nationality of the beneficial owners, senior manager, and directors.
Other risk assessment considerations that are unique to legal person and arrangement customers include:
• The legal form of the customer, and the controls in place to ensure transparency; • The status of the beneficial owners and senior management. For example, if a beneficial owner or senior manager of a customer is a PEP, as defined in Article 15 of AML-CFT Decision, the customer may also need to be treated as PEP, depending on the extent of the PEP’s ownership and control and his or her relationship to the other beneficial owners or managers.
3. Applying EDD and other preventive measures to customers the LFI determines to be higher-risk, as required by Article 4.2(b) of AML-CFT Decision, or to specific customer types, no matter their risk rating, as required by AML-CFT Decision.
Many EDD measures for legal persons and arrangements are the same as those applied to individual customers. EDD measures that are specific to legal person and arrangement customers are discussed in section 4.3 below.
Under AML-CFT Decision, the legal person customer types for which enhanced or special due diligence is required are:
• Legal persons based in high-risk countries (Article 22);
• Financial institutions with which the LFI proposes to enter into a correspondent relationship (Article 25);
• Legal person customers that are fully owned or controlled by PEPs, their direct family members, or their close associates (Article 15). If a PEP, a direct family member, or an associate is a partial owner of a customer, LFIs may take a risk-based approach to applying EDD to the customer.
• Non-Profit Organisations (Article 33).
4.3. Customer Due Diligence and Enhanced Due Diligence
CDD, and, where necessary, EDD are the core preventive measures that help LFIs manage the risks of legal person and legal arrangement customers. Because of this, LFIs are prohibited from maintaining anonymous accounts, and from onboarding any account or customer with fictitious names or characteristics. LFIs must perform CDD on every customer.
The goal of the CDD process is to ensure that LFIs understand who their customer is and the purpose for which the customer will use the LFI’s services. Therefore, the LFI must identify customers that are legal persons and legal arrangements. When the customer is a legal person or arrangement, the process of understanding the customer (“knowing your customer”) is more complex and requires additional steps.
Where an LFI cannot satisfy itself that it understands a legal person or legal arrangement-including when it has doubts that it has identified the individuals who truly own and control the legal person or legal arrangement—then it must not accept that legal person or legal arrangement as a customer. If there is an existing business relationship, the LFI should not continue it. LFIs should also consider filing a Suspicious Transaction Report, as discussed 4.4 below.
4.3.1. Core Elements of Customer Due Diligence
LFIs are reminded that all elements of CDD (and EDD) apply to customers that are legal persons and legal arrangements. LFIs should refer to the Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations for Financial Institutions for a full discussion of CDD obligations. CDD obligations include, but are not limited to, the requirement that LFIs, using a risk-based approach:
• Identify the customer and verify if the customer’s identity is reliable by using independent sources (discussed in this section); • Identify beneficial owners of the customer (discussed in section 4.3.2 below); • Assess and understand customer risk (discussed in section 4.2 above); • Obtain information on the purpose and intended nature of the account (discussed in section 4.3.3 below); and • Ensure ongoing due diligence is conducted and that the business relationship and transactions are scrutinized in the course of the relationship (discussed in section 4.3.4 below).
LFIs must maintain records of the customer information obtained through CDD to enable the LFI to demonstrate compliance to CBUAE and to comply with requests for information from competent authorities.
As discussed above in section 4.1, LFIs must identify legal person customers by collecting the following information and verifying it using independent, reliable sources:
• The name [this may not apply for legal arrangements], Legal Form and Memorandum of Association; • Headquarters’ office address or the principal place of business; in addition, if the legal person or arrangement is a foreign entity, the name and address of its legal representative in the State; • Articles of Association or any similar documents, approved by the relevant authority within the State; • Names of relevant persons holding senior management positions in the legal person or legal arrangement.
Verification of information collected to identify the customer should be risk-based. In standard cases, verification should rely on government-issued or certified documents, such as business licenses and notarized copies of the legal person’s memorandum of association. Where risks are lower, LFIs may consider using non-documentary sources, such as public registries, including the registries maintained by company registrars in the UAE. Consulting a registry, however, is not a replacement for collecting the documents specifically required by the AML-CFT Decision, even if the customer was required to submit the same documents to the registry.
4.3.2. Identification of Beneficial Owners and of Ownership and Control Structure
4.3.2.1. UAE Requirements
As discussed in section 4.1 above, the UAE requires all financial institutions to identify the beneficial owners of a legal person customer by obtaining and verifying the identity of all individuals who, individually or jointly, have a controlling ownership interest in the legal person of 25% or more. Where no such individual meets this description, the LFI must identify and verify the identity of the individual holding the senior management position in the entity.
The AML-CFT Decision does not define “senior management position,” and LFIs should make a judgment, based on the specific facts and circumstances, as to the individual who meets this description. The senior management official should be a single individual with significant responsibility to control, manage, or direct a legal person customer. This may include the entity’s Chief Executive Officer, Chief Financial Officer, Chief Operating Officer, Managing Director, General Partner, or President.
LFIs should consider whether the individual’s background, experience, and expertise make it plausible that they would indeed hold a position of responsibility at a legal person of the customer’s size. Where a customer identifies a relatively young or inexperienced individual as its senior manager, that may be a sign that the individual does not in fact control the customer and instead takes orders from another individual who wishes to obscure his or her identity.
For legal arrangement customers, LFIs must verify the identity of the settlor and the trustee (or anyone holding equivalent positions for non-trust legal arrangements), the beneficiaries or class of beneficiaries, and any other individuals in control of the legal arrangement.
The beneficial owner of a legal person or arrangement must be an individual. Another legal person or arrangement cannot be the beneficial owner of a customer, no matter what percentage it owns. LFIs must continue tracing ownership all the way up the ownership chain until it discovers all individuals who own or control at least 25% of the LFI’s customer.
When the LFI has identified qualifying beneficial owners, it should perform CDD on each individual beneficial owner, in accordance with the requirements of Article 8.1(a) of AML-CFT Decision. Where the customer is a UAE legal person, LFIs may require the customer provide the beneficial ownership report it has submitted to its company registrar as per Cabinet Decision (58). This should not be a substitute, however, for independent identification of beneficial owners by the LFI.
LFIs are also required to understand the customer’s ownership and control structure. This means that LFIs must be aware of who owns the customer, even if they have not verified the identity of the individuals owning every company in the customer’s ownership chain. LFIs should have confidence that they fully understand who has the power to direct and control their customer’s actions.
4.3.2.2. Applying a Risk Based Approach
It is important to note that the legal requirements mentioned above (section 4.3.2.1) are baseline obligations rather than definitions of beneficial ownership. A beneficial owner, as defined in AML-CFT Decision, is any individual who owns or controls all or part of a legal person. This means that a legal person can have several beneficial owners, not all of whom are required to be identified under the law. LFIs should always identify and verify the identity of all individuals owning or controlling at least 25% of a legal person, but they should also make a risk-based decision as to whether to identify and verify the identity of additional beneficial owners. For legal person customers that require EDD, whether as a function of law or because they are higher risk, LFIs should always consider lowering the ownership threshold below 25%.
LFIs should be aware that even minority owners of a legal person customer can exercise control over the legal person through information arrangements, family relationships, and specific governance arrangements (e.g. preferred stock), among other methods. Customers whose minority owners include individuals that are subject to United Nations or UAE sanctions may also create serious risks for LFIs, even if the individual only owns a small share of the customer (see section 4.5 below). Thus, particularly in higher risk scenarios, LFIs should consider completing an ownership and control chart that includes at least the names of all beneficial owners of every legal customer, or all individuals owning at least 5% of the customer. Collecting the names of beneficial owners is distinct from identifying them and verifying their identity and does not require the LFI to collect identifying information. LFIs must still identify and verify the identity of all individuals owning at least 25% of legal person customers.
Beyond lowering the ownership threshold, EDD methods related to identification of ownership and control can include requiring the beneficial owners of customers to verify their ownership by presenting share certificates or contracts.
Example 1: Company A is a UAE-based company that leases office space. Company A applies to open an account with Bank Lion, a CBUAE-supervised LFI. Bank Lion verifies that Company A is 50% owned by Mr. Y and 40% owned by Ms. W. Bank Lion is aware that Company A has additional owners, but knows they own less than 10% of Company A.
Because Company A is a low-risk domestic firm, Bank Lion is not required to identify the additional owners of Company A.
Example 2: Company B is a Cayman Islands-based company with no business operations and a letterbox address on the premises of a known Cayman Islands TCSP. Company B applies to open an account with Bank Lion, a CBUAE-supervised LFI. Bank Lion verifies that Company B is 50% owned by Mr. Y, a citizen of Russia and 40% owned by Ms. W, a citizen of Malta.
Company B is likely a shell company, and its known beneficial owners are from high-risk jurisdictions. Therefore, Bank Lion decides to take the step of identifying and verifying the identity of the individuals who owns the remaining 10% of the company before accepting Company B as a customer. It discovers that the remaining 10% of shares are owned by Mr. Y’s father, a well-known Russian businessman. Because Mr. Y is only 22 and a recent university graduate, Bank Lion suspects that Mr. Y is a nominee and that his father may be the true controlling owner of Company B.
4.3.2.3. Legal Persons – Common Situations
In many cases, identifying the beneficial owners of a legal person customer will be a straightforward process. A customer may be directly owned by one or two individuals:
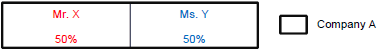
In such cases, an LFI is obliged to identify and to verify the identity of both individuals, Mr. X and Ms. Y.
Legal persons may have more complex ownership structures, however, in which other legal persons are involved in the ownership chain. In such cases, LFIs must continue up the chain until they identify an individual:
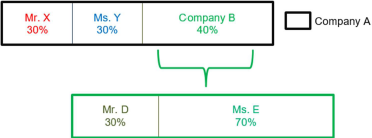
In this situation, the owners of Company A are as follows:
Owner Share Ownership Type Mr. X 30% Direct Ms. Y 30% Direct Ms. E 28% Indirect - Ms E owns 70% of Company B, which in turn owns 40% of Company A Mr. D 12% Indirect - Mr. D owns 30% of Company B, which in turn owns 40% of Company A Mr. X, Ms. Y, and Ms. E must all be identified under UAE law, as they own at least 25% of Company A. Mr. D owns 12%, so he is not required to be identified. But the LFI should make a risk-based decision as to whether to identify him.
Illicit actors may seek to use complex ownership structures to hide the fact that they own 25% or more of the customer. This is why it is important for LFIs to use a risk-based approach and to be confident that, at the end of the process, they fully understand who controls their customer.
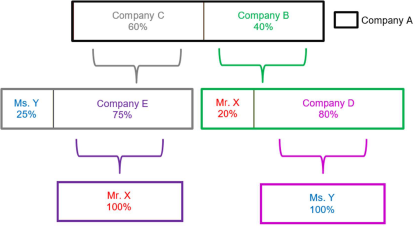
In this situation, although it at first appears that Ms. Y and Mr. X each own less than 25% of Company A, in fact between them they own 100% of the company. Their ownership interests can be calculated as follows:
Mr. X:
• 20% of Company B, which owns 40% of Company A: 20% of 40% is 8%; plus • 100% of Company E, which owns 75% of Company C, which owns 60% of Company A: 100% of 75% of 60% is 45%. • Mr. X owns 53% of Company A.
Ms. Y:
• 25% of Company C, which owns 60% of Company A: 25% of 60% is 15%; plus • 100% of Company D, which owns 80% of Company B, which owns 40% of Company A: 100% of 80% of 40% is 32%. • Ms. Y owns 47% of Company A.
Both Mr. X and Ms. Y must be identified under UAE law. In addition, LFIs should be aware that Mr. X and Ms. Y are likely associated parties and should question whether there is a legitimate economic purpose for the ownership structure of Company A.
4.3.2.4. Legal Arrangements - Common Situations
Legal arrangements may not present the layered ownership structures seen in legal persons. This does not mean, however, that identifying the beneficial owners of legal arrangements is always straightforward. In particular, the very different forms of legal arrangements that may be formed in different jurisdictions can make it difficult to identify the individuals who hold roles analogous to settlor, trustee, and beneficiary. LFIs should always identify the following individuals:
• The legal entities or individuals who have the power to control the property of the legal arrangements. These legal entities or individuals are analogous to trustees. If a legal entity (such as a financial institution) acts as trustee, LFIs must identify the beneficial owners of that legal entity. • The legal entities or individuals for whose present or future benefit the trustees are safeguarding the legal arrangement property. These legal entities or individuals are analogous to the beneficiaries. o Beneficiaries may be defined as a class which can change over time (e.g., “all the underage grandchildren of the settlor”). o LFIs should identify the class of beneficiaries, and all beneficiaries currently in existence, at the time of onboarding the customer. During periodic CDD refresh, they should ascertain whether additional identifiable individuals have joined or left the beneficiary class (e.g. a new child has been born, a beneficiary has come of legal age). o If a legal entity is the named beneficiary, LFIs must identify the beneficial owners of that legal entity. • The legal entities or individuals who assigned control of the legal arrangement property to the trustees (or individuals holding a similar position). This individual or legal entity is analogous to the settlor. A settlor may or may not retain underlying legal ownership of the legal arrangement property. If a legal entity acts as settlor, LFIs must identify the beneficial owners of that legal entity.
In addition, where trustees are financial institutions, lawyers or any other professional with secrecy rules in a foreign jurisdiction, it may be difficult to obtain the information LFIs need. LFIs should be aware that if they cannot obtain this information, they should not establish the business relationship or continue an existing relationship.
Legal arrangements may also be part of the ownership structures of other legal persons or arrangements. Because trusts do not have shares or equity, LFIs should treat all participants in a trust or similar legal arrangement as if they own 100% of the legal arrangement.
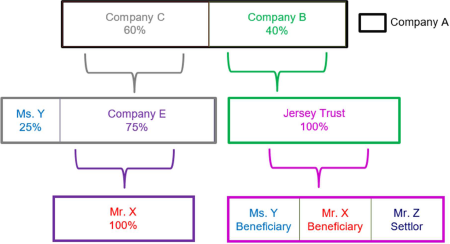
In the example above, Company A is 40% owned by Company B, which is in turn wholly owned by a trust established in the Isle of Jersey. Ms. Y and Mr. X are beneficiaries of the trust and also indirectly own shares of the Company A through Company C. Mr. X has to be identified and verified based solely on his indirect 45% ownership of Company A through Company E. Ms. Y and Mr. Z, must also be identified and verified because they are beneficial owners of a legal arrangement that owns 40% of Company A.
4.3.3. Understanding the Purpose of the Account and Nature of the Customer’s Business
For all customer types, LFIs are required to understand the purpose for which the account or other financial services will be used, and the nature of the customer’s business. This step requires the LFI to collect information that allows it to create a profile of the customer and of the expected uses to which the customer will put the LFI’s services. Because almost all legal persons and arrangements are created to make it easier to do business, invest assets, or engage in some form of organized activity, this element of CDD is critical to understanding customers who are legal persons and arrangements.
Legal persons and arrangements engage in an extremely wide variety of financial activity, potentially a wider variety than individual customers are likely to display. The activity profile of a cash-intensive business such as a taxi firm will be completely different from that of an investment vehicle or of a waqf that collects revenues from real property and distributes them to charitable causes. But specific legal person and arrangements customers are also likely to engage in patterns of activity that remain constant from month to month and year to year. Understanding the purpose of the account allows LFIs to develop expected patterns and compare them to actual behaviour. For example:
• A taxi company is likely to see substantial cash inflows and make regular, predictable transfers to cover payroll and to a limited set of suppliers (e.g. mechanics, gas stations). If a taxi company starts making transfers to a foreign jurisdiction, even a low-risk one, that behaviour may not fit the expected pattern and if so would require investigation. • A waqf managing an apartment building should receive very regular monthly rent payments from residents, whether by cash, check or Automated Clearing House. The waqf should have regular expenses for maintenance and property taxes, as well as predictable payments to the beneficiaries of the waqf. If the waqf suddenly doubles its cash deposits, the LFI will need to investigate to understand why the customer’s behaviour has changed.
Understanding the nature of the customer’s business can be a straightforward process. Most legal person customers will be engaged in familiar, easily identifiable activities in recognized sectors: manufacturing, retail, agricultural production, etc. In other cases, it may not be so simple. A legal person customer may be formed solely to facilitate a complex financial transaction. In other cases, the legal person may not have fully determined their business model or may plan to engage in a business activity that is out of keeping with the owners’ and managers’ resources and expertise, or that don’t seem to make economic sense. Finally, a customer may try to conceal its actual business; for instance, a company that is engaged in computer hacking and fraud may describe itself as a software engineering firm or a call centre.
As LFIs advance efforts to understand their customer’s business and financial activities, they should consider whether aspects of the customer profile require EDD. The following are some situations in which EDD may be appropriate:
• The customer has business or other ties to high-risk jurisdictions (if the customer or its beneficial owners are based in a high-risk jurisdiction, EDD is mandatory). • The customer is engaged in a high-risk sector. High-risk sectors can include, but are not limited to: o Sectors with high flows of cash; o Other financial sectors (e.g. customers who are MSBs or payment processors); o Sectors that involve the import or export of dual-use technology (technology that may be used for proliferation); o Sectors that are at high risk for human trafficking (bars and dance venues; construction; cleaning); o Charitable activities, especially those involving high-risk jurisdictions. • The customer is a state-owned-enterprise (SOE). SOEs engage in a wide variety of business activities; their close relationship to government and government officials means that they may be at higher risk for corruption-related transactions. • The customer intends to use high-risk financial products and services, such as bulk cash services or purchase and exchange of virtual assets. • The LFI does not fully understand the customer’s business model or activities. Customers that generate revenue, but that have no apparent business activities, are perhaps the highest risk.
When conducting EDD on the business activities and account use of legal persons and arrangements, LFIs should use techniques designed to manage the specific risks of the customer. These may include, but are not limited to:
• Requiring the customer to provide invoices documenting incoming and outgoing transfers; • Requiring the customer to provide its Economic Substance Report; • For customers operating in licensed sectors, requiring the customer to provide proof that it has a valid business license; • Inspecting payroll documents and other business records; • Visiting the customer’s business premises and interviewing its personnel; • Requesting a reference from a current customer or other well-known firm with which the new customer claims to do business, or which operates in the same sector as the new customer.
4.3.4. Ongoing Monitoring
Like all customers, legal persons and arrangements must be subject to ongoing monitoring throughout the business relationship. Ongoing monitoring ensures that the account or other financial service is being used in accordance with the customer profile developed through CDD during onboarding, and that transactions are normal, reasonable, and legitimate.
4.3.4.1 CDD Updating
LFIs are required to ensure that the CDD information they hold on all customers is accurate, complete, and up-to-date. This is particularly crucial in the context of legal person and arrangement customers, which, by their very nature, can change their fundamental identity overnight. With the stroke of a pen, a company engaged in a low-risk business and owned by reputable UAE residents can move its activities to a high-risk sector and can transfer ownership to nationals of a high-risk foreign jurisdiction.
LFIs should update CDD on legal person and arrangement customers on a risk-based schedule, with CDD on higher-risk customers being updated more frequently. EDD on all customers, including legal persons and arrangements, should involve more frequent CDD updates.
CDD updates should include a refresh of all elements of initial CDD, and in particular must ascertain that:
• The customer’s beneficial owners remain the same; • The customer continues to have an active status with a company registrar (this may not apply to legal arrangement customers); • The customer has the same legal form and is domiciled in the same jurisdiction; • The customer is engaged in the same type of business, and in the same geographies; • The customer’s transactions continue to fit its profile and business, and are consistent with the business the customer expected to engage in when the business relationship was established.
If any of the above characteristics have changed, the LFI should risk-rate the customer again.
The LFI should conduct EDD when the revised risk rating demands it or if the customer’s history of transactions is not consistent with its profile and with the expectations established at account opening. LFIs must always conduct EDD when this is required by law (a beneficial owner of the customer is a PEP, as defined in Article 15 of AML-CFT Decision, or the customer or its beneficial owner is domiciled in a high-risk jurisdiction).
LFIs may consider requiring that the customer update them as to any changes in its beneficial ownership. Even if this requirement is in place, however, LFIs should not rely on the customer to notify it of a change, but must still update CDD on a schedule appropriate to the customer’s risk rating.
4.3.4.2. Transaction Monitoring
As with all customers, LFIs must monitor activity by legal person and arrangement customers to identify behaviour that is potentially suspicious and that may need to be the subject of a Suspicious Transaction Report (see section 4.4 below). Legal persons, especially those that engage in commerce, are likely to engage a wider range of financial activity than are individual and most legal arrangement customers. This can make identifying suspicious behaviour by legal persons difficult.
As with other customer types, LFIs that use automated monitoring systems should apply rules that are designed to detect common typologies for illicit behaviour. When monitoring and evaluating transactions, the LFI should take into account all information that it has collected as part of CDD, including the identities of beneficial owners. For example, a series of transactions between two unconnected companies may not be cause for an alert. But if the companies are all owned or controlled by the same individual(s), the LFI should investigate to make sure that the transactions have a legitimate economic purpose.
Where possible, monitoring systems should also flag unusual behaviour that may indicate that a legal person customer’s business has changed—for example, a first transfer to or from a high-risk jurisdiction, or a large transaction involving a new counterparty. LFIs should follow up on such transactions with the customer to discover whether the customer has changed its business model in such a way as to require a higher risk rating.
A list of red flags for illicit behaviour involving legal persons and arrangements is provided in the Annex to this Guidance.
4.4. Suspicious Transaction Report Filing
As required by Article 15 of AML-CFT Law and Article 17 of AML-CFT Decision, LFIs must file a Suspicious Transaction Report (STR) with the UAE Financial Intelligence Unit (UAE FIU) when they have reasonable grounds to suspect that a transaction, attempted transaction, or certain funds constitute, in whole or in part, the proceeds of crime, is related to a crime, or is intended to be used in a crime. STR filing is not simply a legal obligation; it is a critical element of the UAE’s effort to combat financial crime and protect the integrity of its financial system. By filing STRs with the UAE FIU, LFIs alert law enforcement about suspicious behaviour and allow investigators to piece together transactions occurring across multiple LFIs.
In addition to the requirement to file an STR when an LFI suspects that a transaction or funds are linked to a crime, LFIs should consider filing an STR in the following situations involving legal persons or arrangements:
• A potential legal person or arrangement customer decides against opening an account or purchasing other financial services after learning about the LFI’s CDD requirements; • A current legal person or customer cannot provide required information about its business or its beneficial owners; • A legal person or arrangement customer cannot adequately explain transactions, provide supporting documents such as invoices, or provide satisfactory information about its counterparty; • The LFI is not confident, after completing CDD procedures, that it has in fact identified the individuals owning or controlling the legal person or arrangement. In such cases, the LFI should not establish the business relationship, or continue an existing business relationship, and should also consider filing an STR.
Please consult the CBUAE’s Guidance on Suspicious Transaction Reporting for further information.
4.5. Implementation of Targeted Financial Sanctions - Special Considerations for Legal Persons and Arrangements
Key Terms for Targeted Financial SanctionsAffiliate is an entity owned by another entity by more than 25% and less than 50% of its capital.
Controlling shareholder is a shareholder who has the ability to directly or indirectly influence or control the appointment of the majority of the Board of directors, or the decisions made by the board.
Listed Person is a person or organization listed by the UN Security Council on the Sanctions List, or listed by the Cabinet on Local Lists, as the case may be.
Subsidiary is an entity owned by another entity by more than 50% of its capital or under full control of that entity regarding appointment of the Board of Directors.
Legal persons can be included on international sanctions lists. In addition, the obligation to freeze the funds of a listed person, imposed by AML-CFT Decision and by articles 15 and 21 of Cabinet Decision (74) of 2020, extends to funds that a Listed Person owns or controls through ownership or control of a legal person or through a legal arrangement.
Listed individuals and legal persons are known to seek to evade sanctions by hiding their interest in a transaction via complex layers of control and ownership, through informal nominee arrangements, and through the assistance of complicit professionals. Listed Persons may also use front companies-companies mixing legitimate and illicit economic activity—to conceal their activities. For this reason, identification of beneficial ownership through the entire corporate ownership structure is critical for effective sanctions implementation, as is fully understanding the nature of the customer’s business.
LFIs that employ automated screening technologies to identify matches to sanctions lists must ensure that their screening tools include all individuals associated with a legal person customer, including beneficial owners, authorized signatories, directors, and senior management.
Legal persons and arrangements that are directly or indirectly (i) owned 50% or more in the aggregate, or (ii) controlled, by one or more Listed Person, including subsidiaries of a Listed Person, and entities where a listed person is a controlling shareholder, are subject to the same prohibitions as the Listed Person, even if such entities are not specifically listed by the UAE or the United Nations.
Financial institutions should observe caution when considering a transaction with an entity that is not a Listed Person in which one or more Listed Persons have a significant ownership interest that is less than 50 percent or which one or more Listed Persons may control by means other than a majority ownership interest. Such non-listed entities, to include affiliates, may become the subject of future designations or enforcement actions. As discussed above, LFIs should make a risk-based decision as to whether to identify beneficial owners who own or control less than 25% of the legal persona or arrangement. LFIs are not required to identify every beneficial owner in order to conduct sanctions screening. But should an LFI, in the course of enhanced due diligence, discover that a Listed Person owns a minority interest in a legal person, this information must be taken into consideration in risk-rating that customer.
Please see the Guidance on Targeted Financial Sanctions for more information on this issue.
LFIs should consult the CBUAE and the Supreme Council for National Security if they have any questions regarding implementation of UN or UAE sanctions. LFI employees must be trained on these issues as part of comprehensive ongoing training.
Example: Listed individual Ms. Y owns 25% of foreign Company A. Foreign Company A owns 30% of UAE Company B. Company B is a customer of UAE LFI Lion Bank. Ms. Y has no other ownership interests in Company B. Ms. Y therefore ultimately owns 7.5% of Company B.
Ms. Y’s minority interest may not in itself give her ownership or control Company B. But Lion Bank should also consider the following factors when determining whether Ms. Y exercises control over Company B:
• The other beneficial owners of Company B are known close associates of Ms. Y’s; and • Ms. Y has loaned Company B a sum equal to 100% of its operating revenue in the previous financial year, and under the terms of the loan agreement, if Company B does not repay the loan Ms. Y will acquire an additional 35% of Company B.
When these factors are considered, it becomes likely that Ms. Y does in fact exercise control over Company B, despite her relatively small ownership stake, and transactions with Company B may therefore be prohibited under Cabinet Decision (20) of 2019. Alternatively, if Company B operates in the high-tech manufacturing sector, and Ms. Y has been listed for proliferation activities, the LFI may conclude that the sanctions evasion risk posed by Company B is too great to permit accepting it as a customer, even if Ms. Y does not exercise control of the company. 4.6. Training
As will all risks to which the LFI is exposed, the AML/CFT training program must ensure that employees are aware of the risks of legal persons and arrangements, are familiar with the obligations of the LFI, and are equipped to apply appropriate risk-based controls.
5. Lessons Learned and Examples from Amld Supervision
The CBUAE’s examinations of LFIs have found that some LFIs struggle with key aspects of the preventive measures regime for legal persons. LFIs should take care to implement effective compliance programs, including by avoiding common deficiencies such as:
• Incomplete and out of date CDD: CBUAE has identified instances where CDD files are missing key information, such as the country of operation, the nature of the business, and the nationality of beneficial owners, shareholders, and directors. Equally important, CDD files are often out of date, with expired customer information.
• Inadequate systems: LFIs’ systems for supporting CDD do not always mandate the collection of all required information or guide the compiler to supply complete information, such as the full name of a beneficial owner. LFIs’ core banking systems may not be capable of linking or tracking related parties, which inhibits identification of suspicious behavior. In some cases, risk-rating and identification of UBOs is done manually, which increases the likelihood of user error or manipulation.
• Incomplete risk-rating: LFIs’ risk rating tools for legal persons and arrangements did not always take into account critical information, such as the type of entity and the risk rating of beneficial owners.
Annex 1. Red Flags for Concealment of Beneficial Ownership
The following are indicators that Financial Action Task Force (FATF) member states have observed in connection to abuse of legal persons and arrangements. This is not an exhaustive list of every potential indicator of illicit activity involving legal persons and arrangements, but it represents a wide range of behaviours and activities that should prompt LFIs to investigate further, to consider closing or not opening an account, and to consider filing an STR.
Indicators Related to the Customer
• The customer is reluctant to provide personal information. • The customer is reluctant or unable to explain:
o their business activities and corporate history o the identity of the beneficial owner o their source of wealth/funds o why they are conducting their activities in a certain manner o who they are transacting with o the nature of their business dealings with third parties (particularly third parties located in foreign jurisdictions).
• Individuals or connected persons:
o insist on the use of an intermediary (either professional or informal) in all interactions without sufficient justification; o are actively avoiding personal contact without sufficient justification; o are foreign nationals with no significant dealings in the country in which they are procuring professional or financial services; o refuse to co-operate or provide information, data, and documents usually required to facilitate a transaction o are politically exposed persons, or have familial or professional associations with a person who is politically exposed; o are conducting transactions which appear strange given an individual’s age (this is particularly relevant for underage customers); o have previously been convicted for fraud, tax evasion, or serious crimes; o are under investigation or have known connections with criminals; o have previously been prohibited from holding a directorship role in a company or operating a trust and company service provider (TCSP); o are the signatory to company accounts without sufficient explanation; o conduct financial activities and transactions inconsistent with their customer profile; o have declared income which is inconsistent with their assets, transactions, or lifestyle.
• Legal persons or legal arrangements:
o have demonstrated a long period of inactivity following incorporation, followed by a sudden and unexplained increase in financial activities; o describe themselves as a commercial business but cannot be found on the internet or social business network platforms (such as LinkedIn, XING, etc.); o are registered under a name that does not indicate the activity of the company; o are registered under a name that indicates that the company performs activities or services that it does not provide; o are registered under a name that appears to mimic the name of other companies, particularly high-profile multinational corporations; o use an email address with an unusual domain (such as Hotmail, Gmail, Yahoo, etc.); o are registered at an address that does not match the profile of the company; o are registered at an address that cannot be located on internet mapping services (such as Google Maps); o are registered at an address that is also listed against numerous other companies or legal arrangements, indicating the use of a mailbox service; o where the director or controlling shareholder(s) cannot be located or contacted; o where the director or controlling shareholder(s) do not appear to have an active role in the company; o where the director, controlling shareholder(s) and/or beneficial owner(s) are listed against the accounts of other legal persons or arrangements, indicating the use of professional nominees; o have declared an unusually large number of beneficiaries and other controlling interests; o have authorised numerous signatories without sufficient explanation or business justification; o are incorporated/formed in a jurisdiction that is considered to pose a high money laundering or terrorism financing risk; o are incorporated/formed in a low-tax jurisdiction or international trade or finance centre; o regularly send money to low-tax jurisdictions or international trade or finance centre; o conduct a large number of transactions with a small number of recipients’ o conduct a small number of high-value transactions with a small number of recipients; o regularly conduct transactions with international companies without sufficient corporate or trade justification; o maintain relationships with foreign professional intermediaries in the absence of genuine business transactions in the professional’s country of operation; o receive large sums of capital funding quickly following incorporation/formation, which is spent or transferred elsewhere in a short period of time without commercial justification; o maintain a bank balance of close to zero, despite frequent incoming and outgoing transactions; o conduct financial activities and transactions inconsistent with the corporate profile; o are incorporated/formed in a jurisdiction that does not require companies to report beneficial owners to a central registry; o operate using accounts opened in countries other than the country in which the company is registered; o involve multiple shareholders who each hold an ownership interest just below the threshold required to trigger enhanced due diligence measures.
• There is a discrepancy between the supposed wealth of the settlor and the object of the settlement. • Individuals, legal persons and/or legal arrangements:
o make frequent payments to foreign professional intermediaries; o are using multiple bank accounts without good reason; o are using bank accounts in multiple international jurisdictions without good reason; o appear focused on aggressive tax minimisation strategies; o demonstrate limited business acumen despite substantial interests in legal persons; o provide falsified records or counterfeit documentation; o appear to engage multiple professionals in the same country to facilitate the same (or closely related) aspects of a transaction without a clear reason for doing so.
• Examination of business records indicate:
o a discrepancy between purchase and sales invoices; o double invoicing between jurisdictions; o fabricated corporate ownership records; o false invoices created for services not carried out; o falsified paper trail; o inflated asset sales between entities controlled by the same beneficial owner; o agreements for nominee directors and shareholders; o family members with no role or involvement in the running of the business are listed as beneficial owners of legal persons or arrangements; o employees of professional intermediary firms acting as nominee directors and shareholders; o the resignation and replacement of directors or key shareholders shortly after incorporation; o the location of the business changes frequently without an apparent business justification; o officials or board members change frequently without an appropriate rationale.
• Complex corporate structures that do not appear to legitimately require that level of complexity or which do not make commercial sense. • Simple banking relationships are established using professional intermediaries.
Indicators of shell companies
• Nominee owners and directors:
o formal nominees (formal nominees may be “mass” nominees who are nominated agents for a large number of shell companies); o informal nominees, such as children, spouses, relatives or associates who do not appear to be involved in the running of the corporate enterprise.
• Address of mass registration (usually the address of a TCSP that manages a number of shell companies on behalf of its customers). • Only a post-box address (often used in the absence of professional TCSP services and in conjunction with informal nominees). • No real business activities undertaken. • Exclusively facilitates transit transactions and does not appear to generate wealth or income (transactions appear to flow through the company in a short period of time with little other perceived purpose). • No employees (or only a single employee). Pays no taxes, superannuation, retirement fund contributions or social benefits. • Does not have a physical presence.
Indicators about the transaction
• The customer is both the ordering and beneficiary customer for multiple outgoing international funds transfers. • The connections between the parties are questionable, or generate doubts that cannot be sufficiently explained by the client. • Finance is provided by a lender, whether a natural or a legal person, other than a known credit institution, with no logical explanation or commercial justification. • Loans are received from private third parties without any supporting loan agreements, collateral, or regular interest repayments. • The transaction:
o is occurring between two or more parties that are connected without an apparent business or trade rationale; o is a business transaction that involves family members of one or more of the parties without a legitimate business rationale; o is a repeat transaction between parties over a contracted period of time; o is a large or repeat transaction, and the executing customer is a signatory to the account, but is not listed as having a controlling interest in the company or assets; o is executed from a business account but appears to fund personal purchases, including the purchase of assets or recreational activities that are inconsistent with the company’s profile; o is executed from a business account and involves a large sum of cash, either as a deposit or withdrawal, which is anomalous, or inconsistent with the company’s profile; o appears cyclical (outgoing and incoming transactions are similar in size and are sent to, and received from, the same accounts, indicating that outgoing funds are being returned with little loss) (aka “round-robin” transactions); o involves the two-way transfer of funds between a client and a professional intermediary for similar sums of money; o involves two legal persons with similar or identical directors, shareholders, or beneficial owners; o involves a professional intermediary without due cause or apparent justification; o involves complicated transaction routings without sufficient explanation or trade records; o involves the transfer of real property from a natural to a legal person in an off-market sale; o involves the use of multiple large cash payments to pay down a loan or mortgage; o involves a numbered account; o involves licensing contracts between corporations owned by the same individual; o involves the purchase of high-value goods in cash; o involves the transfer of (bearer) shares in an off-market sale; o a loan or mortgage is paid off ahead of schedule, incurring a loss; o includes contractual agreements with terms that do not make business sense for the parties involved; o includes contractual agreements with unusual clauses allowing for parties to be shielded from liability but make the majority of profits at the beginning of the deal; o is transacted via a digital wallet.
• The funds involved in the transaction:
o are unusual in the context of the client or customer’s profile; o are anomalous in comparison to previous transactions; o are sent to, or received from, a foreign country when there is no apparent connection between the country and the client; and/or are sent to, or received from, a low-tax jurisdiction or international trade or finance centre; o are sent to, or received from, a jurisdiction that is considered to pose a high money laundering or terrorism financing risk.
• Unexplained use of powers of attorney or other delegation processes (for example, the use of representative offices). • Unexplained use of express trusts, and/or incongruous or unexplained relationships between beneficiaries and the settlor. • Unexplained or incongruous classes of beneficiaries in a trust.
Annex 2. Synopsis of the Guidance
introduction Purpose The purpose of this guidance is to assist Licensed Financial Institutions (LFIs) understand and mitigate the risks when providing services to legal persons and arrangements, and to guide them in fulfilling their AML/CFT obligations. Applicability This guidance applies to all natural and legal persons, which are licensed and/or supervised by CBUAE, in the following categories: - national banks, branches of foreign banks, exchange houses, finance companies, payment service providers, registered hawala providers and other LFIs; and
- insurance companies, agencies, and brokers.
Understanding and Assessing the Risks of Legal Persons and Arrangements ML/TF Risks of Legal Persons and Arrangements Legal persons and arrangements are attractive to illicit actors because they can assist criminals and their associates to: - Hide the identify of the individuals directing a transaction or controlling an account;
- Obscure the true nature and purpose of an account or transaction; and
- Conceal the source of funds involved in a transaction or account.
Features and Controls that Mitigate Risks Certain rules governing the formation and operation of legal persons and arrangements can, if enforced, reduce the risk that they will be abused by illicit actors: - Formation processes that deter creation of shell companies;
- Collection of beneficial ownership information for all legal persons and arrangements;
- Requiring legal persons and arrangements to keep certain records and make regular reports;
- Supervision and monitoring by appropriate government authorities.
Legal persons and arrangements in the UAE
Identification of Beneficial Owners All legal persons and arrangements in the UAE (except those traded on a stock exchange, or owned by a company traded on a stock exchange) are required to identify all individuals who own or control at least 25% of the legal person or arrangements. Legal persons and arrangements must hold this information, and legal persons must also report it to their registrar. They must maintain and update this information when their beneficial owners change. Legal Arrangements Under UAE Law UAE law allows for the creation of two types of legal arrangements: trusts and awqaf. Trustees and waqf supervisors must comply with certain requirements related to identifying the individuals party to the legal arrangement. Economic Substance Requirements All companies operating in certain sectors must prove on an annual basis that they actually conduct substantive activities in the UAE by submitting certain required information to their registrar. Although this information is not directly available to LFIs, they should be aware of these requirements and can request the information from legal person customers. Mitigating Risk: Requirements for LFls Risk-Based Approach LFIs must take a risk-based approach in their AML programs and to individual customers. This means that they should assess all customers, including legal person/legal arrangement customers, to determine their degree of risk. In assessing the risk of a legal person or arrangement customer, LFIs should consider at least the following factors:
- The legal form of the customer;
- The controls governing the formation of that type of customer;
- The controls in place to ensure that the customer identifies and reports its beneficial owners;
- Whether the customer is subject to recordkeeping and reporting requirements;
- Whether the customer is appropriately supervised for its compliance with these requirements.
Customer Due Diligence For all customers, LFIs must perform Customer Due Diligence with the following components: Customer Identification: For all legal person and legal arrangement customers, LFIs must collect the following information - The name [this may not apply for legal arrangements], Legal Form and Memorandum of Association;
- Headquarters’ office address or the principal place of business; in addition, if the legal person or arrangement is a foreign entity, the name and address of its legal representative in the State;
- Articles of Association or any similar documents, approved by the relevant authority within the State;
- Names of relevant persons holding senior management positions in the legal person or legal arrangement.
Identification of Beneficial Owners: For all legal person and legal arrangement customers, LFIs must identify the following individuals: - For legal persons, all individuals who, individually or jointly, have a controlling ownership interest in the legal person of 25% or more. If no individual can be identified, the LFI must identify the individual(s) holding the senior management position(s) within the legal person customer.
- For legal arrangements, the individuals acting as the settlor and the trustee (or anyone holding equivalent positions for non-trust legal arrangements), the beneficiaries or class of beneficiaries, and any other individuals in control of the legal arrangement.
Understand the Purpose of the Account and the Nature of the Customer's Business: LFIs must understand the business in which their customer engages as well as the reason for creating the account. The answers to these questions can have a significant impact on the risk the customer poses for the financial institution and therefore should be reflected in the customer risk rating. Perform Ongoing Monitoring: For all customers, LFIs must ensure that the customer information on file is up to date and accurate, and that the customer's activities are in line with the expectations set at onboarding. If not, the customer risk rating may need to be changed. Suspicious Transaction Reporting For customers of all types, LFIs must report any behavior that they reasonably suspect may be linked to money laundering, the financing of terrorism, or a criminal offence. Please consult the CBUAE's Guidance on Suspicious Transaction Reporting for further information. Implementation of TFS A legal person or arrangement that is not itself designated on a sanctions list may be owned by someone who is designated. LFIs should screen the beneficial owners of all legal person and legal arrangement customers against sanctions lists, and should freeze any accounts or transactions related to a legal person or legal arrangement that is more than 50% owned or controlled by a designated person. Guidance for Licensed Financial Institutions Providing Services to the Real Estate and the Precious Metals and Stones Sectors
Effective from 16/6/2021Introduction
1.1 Purpose
Article 44.11 of the Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations charges Supervisory Authorities with “providing Financial Institutions...with guidelines and feedback to enhance the effectiveness of implementation of the Crime-combatting measures.”
The purpose of this Guidance is to assist the understanding and effective performance by the United Arab Emirates Central Bank's (“CBUAE”) licensed financial institutions (“LFIs”) of their statutory obligations under the legal and regulatory framework in force in the UAE. It should be read in conjunction with the CBUAE's Procedures for Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations (issued by Notice No. 74/2019 dated 19/06/2019) and Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations for Financial Institutions (issued by Notice 79/2019 dated 27/06/2019) and any amendments or updates thereof.
1 As such, while this Guidance neither constitutes additional legislation or regulation nor replaces or supersedes any legal or regulatory requirements or statutory obligations, it sets out the expectations of the CBUAE for LFIs to be able to demonstrate compliance with these requirements. In the event of a discrepancy between this Guidance and the legal or regulatory frameworks currently in force, the latter will prevail. This Guidance may be supplemented with additional separate guidance materials, such as outreach sessions and thematic reviews conducted by the Central Bank.Furthermore, this Guidance takes into account standards and guidance issued by the Financial Action Task Force (“FATF”), industry best practices and red flag indicators. These are not exhaustive and do not set limitations on the measures to be taken by LFIs in order to meet their statutory obligations under the legal and regulatory framework currently in force. As such, LFIs should perform their own assessments of the manner in which they should meet their statutory obligations.
This Guidance comes into effect immediately upon its issuance by the CBUAE with LFIs expected to demonstrate compliance with its requirements within one month from its coming into effect.
1 Available at centralbank.ae/en/cbuae-amlcft.
1.2 Applicability
Unless otherwise noted, this Guidance applies to all natural and legal persons, which are licensed and/or supervised by the CBUAE, in the following categories:
• National banks, branches of foreign banks, exchange houses, finance companies, payment service providers, registered hawala providers and other LFIs; and
• Insurance companies, agencies, and brokers.
1.3 Legal Basis
This Guidance builds upon the provisions of the following laws and regulations:
2. Understanding Risks
The FATF's Mutual Evaluation Report of the UAE issued in April 2020 stated that the two sectors of real estate and precious metals and stones are weighted as highly important in terms of risk and materiality in the UAE. While the nature and extent of the risk posed by the two sectors to the LFIs providing them with accounts and other financial services is different, they do share common characteristics that LFIs should recognize and take into account:
• Attractiveness to illicit finance. The real estate and precious metals and stones sectors are important parts of the UAE's economy, and each provides important, legitimate goods and services to the UAE population and global trading partners. Nevertheless, experience shows that these sectors offer services that are particularly attractive to illicit actors.
• Facilitation of the international movement of value. Despite their different natures, both sectors allow individuals to move large values across international borders, sometimes with only minimal involvement from the formal financial system. For example, a courier carrying a valuable diamond can move millions of AED of value simply by taking a short international flight. In addition, the real estate and precious metals and stones sectors allow individuals to hold value in a form that retains value over time (such as gold or real property) without having to maintain an account in the formal financial system. These facilities are useful to many legitimate businesses, but are also highly sought-after by illicit actors.
• Varying regulatory regimes. The extent and nature of regulation on these sectors varies widely between jurisdictions. In some jurisdictions, participants such as dealers in precious metals and stones (DPMS) and real estate agents and brokers are required to be licensed or registered, and to comply with AML/CFT requirements that are similar to those imposed on LFIs. These include, at a minimum, the requirement to perform CDD on customers and to report suspicious transactions. Despite the existence of these requirements, however, sector participants are in many cases not closely supervised or monitored for compliance. Their understanding of their risk and of their compliance obligations may not be well-developed or accurate. In other jurisdictions, there are limited or no obligations placed on these actors, and they may not have any understanding of how they can be abused by illicit actors, or the steps they should take to protect themselves.
2.1 Understanding and Assessing Risks Related to DPMS
Dealers in precious metals and stones (DPMS) play a significant role in the economy of the UAE. DPMS engage in a wide range of activities related to precious metals and stones, from production to trading, establishing the UAE as an important regional hub for this sector. The Dubai Multi Commodities Centre specializes in providing services to precious metal dealers and exchanges, and a significant volume of transactions also goes through the Jebel Ali Free Zone. A significant amount of activity also occurs in the Dubai Gold Souk.
Nonetheless, the precious metals and stones sector offers opportunities for criminals seeking to conceal, transfer, and/or invest their illicit proceeds. Like cash, precious metals and stones offer high value by weight, are difficult to trace and identify, and retain their value over time. DPMS, if they do not apply effective preventive measures, could be vulnerable to abuse by illicit actors engaged in laundering the proceeds of crime, financing of terrorism, arms trafficking, sanctions evasion, and other illicit activities.
2.1.1 Risks of Precious Metals and Stones
The characteristics of precious metals and stones make them uniquely appropriate as media to store, transfer, and exchange value:
i. Precious metals and stones are generally compact, durable, odourless, and of high value.
ii. Certain metals and stones (e.g., gold or diamond) are widely accepted as a method of exchange or currency.
iii. Precious metals and stones retain their value over time, and have roughly the same value all over the world.
In addition to these properties, precious metals and stones have characteristics that make them particularly attractive to criminals seeking to launder funds and others engaged in illicit behaviour:
i. Differentiating precious metals and stones often requires laboratory techniques, so it can be difficult or impossible to track their movement;
ii. Precious metals and stones can be transformed (through re-cutting or recycling) into different objects while retaining their value, interrupting known custody and transfer chains;
iii. Purchase, sale, and exchange of precious metals and stones often takes place outside the formal financial system.
For these reasons, DPMS may be targeted by illicit actors seeking to abuse their services and exploit the advantages of precious metals and stones. Although the majority of transactions involving DPMS are legal, these businesses may trade in items that could be the proceeds of crime, purchased with the proceeds of crime, and/or used to launder the proceeds of crime, unknowingly or complicitly.
Because they are themselves at high risk of abuse, DPMS pose a risk to LFIs. Complicit DPMS may knowingly partake in illicit activities and may in turn use their business relationships with LFIs to launder the proceeds of crime or carry out other illicit activity. Even DPMS that are not knowingly involved in illicit activities may use their accounts with an LFI to deal in the proceeds of crime. For example, a DPMS may wire payment for illegally mined gold to the entity responsible for mining and processing the gold.
Gold as a High-Risk Medium of ExchangeGold is easy to exchange and transfer, and may provide anonymity when processing transactions, as it is difficult to trace. It also has a universal price standard, a relatively stable market for investment, and may be used as a currency. Gold dealers may provide specific services to their clients, such as metal accounts, for storage or for investment properties. This may enable criminals to move gold under the guise of legitimate business.
2.1.2 Features of DPMS that Increase Risk
Not all DPMS pose equal risk. A DPMS is likely to be considered higher risk when it provides products or services that are attractive to illicit actors, has operations in high-risk jurisdictions, or does not apply appropriate anti-money laundering/combatting the financing of terrorism (AML/CFT) controls.
2.1.2.1 Regulatory Environment
In many jurisdictions, DPMS are not required to comply with requirements related to identification of customers and reporting suspicious activities. In other jurisdictions, these requirements are nominally in place, but DPMS are not subject to effective supervision and enforcement. Even in a jurisdiction that imposes and enforces such requirements, they frequently apply only to DPMS that engage in cash transactions above a certain value threshold. Where DPMS are unregulated or under-regulated, they are unlikely to be taking effective measures to protect themselves from abuse.
In contrast, an effective AML/CFT framework and supervisory regime for DPMS can protect DPMS and LFIs that serve them by effectively imposing AML/CFT requirements and by detecting, deterring, and prosecuting ML/TF crimes. It is important to note that, like LFIs, certain DPMS in the UAE are required to comply with all requirements of AML-CFT Decision, including the requirement to perform Customer Due Diligence (CDD) and report suspicious transactions (see section 2.1.4).
2.1.2.2 Products, Services, and Delivery Channels
Products, services, and delivery channels that facilitate the rapid, efficient, anonymous movement of value on a large scale will be more attractive to illicit actors and may put a DPMS at a higher risk of abuse. Such products, services, and delivery channels may include:
• Products (such as bullion and uncut stones) that are particularly hard to trace, retain or even increase in value despite being transformed into new forms (melted down, re-cut, etc.), and offer high value by weight. • Services, such as metal accounts, that allow customers to rapidly purchase and sell precious metals or stones. • Delivery channels that allow transactions to be carried out quickly and anonymously, such as accepting cash or virtual assets and conducting transactions online or through intermediaries.
2.1.2.3 Customer Base
The types of customers that a DPMS serves can also impact risk. For example, a DPMS that primarily deals with PEPs may be higher risk than one that serves a lower-profile clientele.
2.1.2.4 Geography
DPMS may be based, or may trade internationally, in jurisdictions that are higher risk for money laundering, the financing of terrorism, and the financing of proliferation. Such DPMS may pose heightened risk to LFIs. Higher-risk jurisdictions may be characterized by:
• A low level of government oversight and regulation of the precious metal and stone value chain;
• Low economic and political stability;
• High use of the informal banking system;
• High levels of corruption;
• The presence of terrorist and other non-state armed groups;
• Weak border control measures; and/or
• Sanctions and embargoes
Where a DPMS is based in a high-risk jurisdiction, LFIs are required by AML-CFT Decision to perform Enhanced Due Diligence.
2.1.3 Typologies
Precious metals and stones may be involved in a wide variety of illicit finance schemes. The following are some of the most common.
• Illegal mining or mining supported by the proceeds of crime. In jurisdictions where precious metals or stones are mined, illicit actors may operate small-scale ‘artisanal' mines without receiving a license or paying taxes to the state. The products of these mines are then exported to a refining or cutting hub for processing into saleable goods, like gold bullion and cut stones.
In many cases, criminal organizations control a mine or a network of small-scale miners. They may invest the proceeds of other illegal activities, such as drug trafficking, into the illegal mines and take the majority share of the resulting production as a return on investment. When the resulting precious metals or stones are processed, the criminal organization can sell them on world markets. The proceeds fund further illicit activities and may also support terrorism.
Example: Trading in gold to legitimise the proceeds of drug traffickingA criminal organisation in Country X was buying gold from various precious metals retailers using illicit proceeds from narcotics sales. The gold was then sold to a precious metals broker who then sold it to other businesses. The proceeds of the sale were then wired to a third party outside of Country X with links to the drug trafficking organization, thus completing the money laundering cycle.
• Use of precious metals and stones in sanctions evasion. The tradable nature, liquidity, wide availability, and anonymity of precious metals and stones has made them popular with individuals, organizations, and governments seeking to evade sanctions imposed by the United Nations or other jurisdictions. This activity may involve mining precious metals or stones under the control of the sanctioned person; the resulting products are then injected into legal trade using front companies and complicit DPMS, earning money for the sanctioned group. Or sanctioned actors may use precious metals and stones to disrupt a transaction chain involving the formal financial system and thus hide their interest in a transaction.
Example: Large-scale sanctions evasion using precious metalsAccording to Country A's federal indictments, a government sanctioned by Country A used front companies and complicit financial institutions to buy large quantities of gold in Country B. The gold was supposedly exported to the purchasing country, but was in fact moved by courier to the UAE, where it was sold in exchange for cash (U.S. dollars and euros). The cash was deposited with LFIs in the UAE under the names of front companies, and was made available to the sanctioned government to use in proliferation activities.
• Evasion of duties on precious metals and stones. Precious metals and stones are often the subject of heavy customs duties and other taxes. As a result, illicit actors will frequently seek to smuggle these goods from high-tax to low-tax jurisdictions, or may declare artificially low values for the goods by misrepresenting their quality or purity.
• Trade-based money laundering (TBML). The value of precious metals and stones varies highly based on their quality and purity, features which may not be apparent to the naked eye. In addition, the value of certain precious stones, particularly diamonds, can differ for different non-industry customers based on their personal preferences. This makes precious metals and stones particularly vulnerable to TBML, in which illicit actors use supposedly or actually licit trade to hide illicit finance. This can take a variety of forms:
o Trading the same goods—often precious stones—repeatedly between co-conspirators to justify funds transfers between members of a criminal network, or between companies owned by the same individual(s). In these schemes, a single precious stone may be repeatedly sold between members of the network, or a single stone may be sold to multiple “purchasers” at the same time, each time with a different description.
o Inflation or deflation of the value of traded stones to provide justification for cross-border transfers. A merchant may sell low-value precious metals or stones to a purchaser, but invoice for higher-quality goods and thus a higher sum. The purchaser pays the full invoice price, justifying the transaction to financial institutions, and also receives illicit goods such as drugs or smuggled items.
• Use of precious metals and stones as security for fraudulent loans. In a typology that is often related to TBML, precious metals or stones may be repeatedly sold or falsely valued between members of a network in order to justify loans and other forms of financing.
Example: Over-Valuation to Justify Illicit TransfersMr. A, a licensed DPMS, entered Country X numerous times, each time declaring that he was carrying valuable precious stones. He was in fact carrying gems that were lower value than the ones he declared. He then substituted the lower value gems for higher value gems that were already in Country X and presented them for inspection and clearance at an official diamond exchange. Through these methods, Mr. A obtained validated official importation statements for multiple importations of high-value stones which did not actually take place. He used these statements, together with fake invoices, to facilitate international foreign currency transfers to entities abroad in the guise of payment for the imported goods. He ordered these transactions both for himself and on behalf of other DPMS wanting to receive funds abroad without having to face scrutiny by financial institutions and public authorities.
2.1.4 Regulation and Supervision of DPMS in the UAE
DPMS that qualify as Designated Nonfinancial Businesses and Professions (DNFBPs) are subject to AML/CFT requirements that are substantially the same as those imposed on LFIs, including the requirement to identify customers, to report suspicious transactions, and to perform a risk assessment. Under Article 3 of AML-CFT Decision, DPMS qualify as DNFBPs only if they are “carrying out any single monetary transaction or several transactions that appear to be interrelated or equal to more than AED 55,000". A DPMS that does not engage in such transactions is not required to take any preventive measures. Although cash transactions are certainly high risk, LFIs should be aware that the fact that a DPMS does not qualify as a DNFBP does not mean that it is low-risk. All DPMS, regardless of whether they qualify as DNFBPs, must have a commercial license to operate legally in the UAE. The Ministry of Economy is also responsible for identifying and classifying DPMS as DNFBPs; LFIs are not required to make this determination. But LFIs should discover, through the CDD process, whether their customer has been classified as a DNFBP by the Ministry of Economy.
Obliged DPMS are supervised for compliance by the Ministry of Economy, which has issued guidelines for supervised entities describing their AML/CFT compliance obligations.2
2 Available at economy.gov.ae/english/Pages/AML.aspx.
2.2 Understanding and Assessing Risks Related to the Real Estate Sector
The real estate sector is an important part of the UAE's economy, responsible for as much as 20 percent of Gross Domestic Product (GDP). The UAE real estate sector is diverse, encompassing construction and development, commercial real estate sales, and a wide variety of residential real estate, from apartments to luxury villas. A large number of professional real estate agents and brokers—over 11,500—support this sector.
Most transactions within the sector are legitimate. Nevertheless, LFIs should be aware that the real estate sector offers opportunities for criminals seeking to conceal, transfer, and/or invest their illicit proceeds. The real estate market is a fairly liquid market in which assets generally retain stable values over time. Real estate transactions are generally large and offer criminals the opportunity to launder large values in a single transaction. And unlike other stores of value, such as cash or precious metals and stones, real estate can be enjoyed or can earn income while it is in the owner's possession.
2.2.1 Risks of the Real Estate Sector
The real estate sector is attractive to criminals and other illicit actors for many of the same reasons that it is popular with legitimate investors: real estate is a fairly liquid market, with assets that generally maintain or appreciate in value over time. Like certain forms of gold and precious metals, and unlike stores of value such as currency and stocks, real estate can be enjoyed by the owner. Indeed, the purchase of luxury real estate may in fact be the ultimate goal of the money laundering process.
In addition, certain characteristics of the sector, while not in themselves illicit or undesirable, offer advantages for those seeking to launder funds and to move large values between individuals and across borders in a relatively short time:
• The sale or purchase of real estate is a normal, everyday transaction, and offers a simple, convenient explanation for the source of funds in a large transaction.
• Real estate transactions are typically high-value, allowing illicit actors to launder large sums in a single transaction.
• Real estate transactions of all kinds often take place between shell companies created for the sole purpose of owning real property. This practice makes it difficult to identity the true owner of the property. In addition, the ubiquity of this practice makes it difficult to distinguish licit from illicit transactions.
• The price of real estate is not fixed and is somewhat subjective, allowing illicit actors to inflate or deflate sales or purchase prices to better suit to their schemes.
• Real estate is frequently sold and re-sold in fairly quick succession, making it less suspicious when a criminal engages in similar behaviors in order to layer laundered funds.
• In some jurisdictions, the ownership of real estate gives the owners access to residency rights. Illicit actors may take advantage of these rights to expand their criminal networks to new jurisdictions, to escape criminal investigation in their home countries, and to hold assets offshore without alerting their home authorities.
The real estate sector may be abused at any stage of the laundering process
• Placement: A criminal may invest illicit funds into the sector through an initial purchase in cash. • Layering: A criminal may conceal the true origin of illicit funds by selling and purchasing a number of properties, extending the distance between current assets and the original placement of the funds. • Integration: A criminal may sell a property and invest the funds in stocks, using the paperwork from the sale to demonstrate an apparently acceptable source of funds.
2.2.2 Features of the Real Estate Sector that Increase Risk
Certain features of the real estate sector in different jurisdictions can increase the attractiveness of the sector to illicit actors. Although these features are not in themselves negative or undesirable, they have the effect of increasing the ease with which illicit actors can use the sector to launder funds.
• Varying regulation and supervision of real estate professionals. Real estate agents and brokers are well placed both to detect and to collude in suspicious transactions. Agents and brokers are able to observe suspicious client behaviour, as well as aspects of a transaction that do not have a reasonable explanation. Conversely, complicit real estate professionals may advise a client on how to avoid scrutiny from LFIs and government authorities. This risk is increased in jurisdictions where agents handle client funds, such as in escrow or trust accounts.
Because of the special role played by real estate professionals, the FATF Recommendations require that many such professionals be regulated and supervised, with AML/CFT obligations like those imposed on financial institutions. Where these obligations are not imposed and enforced, and where real estate professionals are not monitored for their compliance, the sector may be higher risk.
• Widespread use of cash. In certain jurisdictions, real estate transactions are frequently executed entirely or partially in cash. This allows a transaction to take place without involving the formal financial system. In addition, criminal activities often produce high volumes of cash, and placement of cash derived through illegal activities is often the first step in the money laundering process. Even if a particular transaction is executed through bank cheque or other similar means, if the property was purchased for cash in the recent past it can be difficult or impossible to fully understand the chain of ownership and thus to identify whether a transaction is part of the money laundering process (e.g., the property was purchased in cash by A, sold to B to launder the original purchase funds, and is now being re-sold to A).
• Lack of transparency on beneficial owners. As discussed above, illicit actors, like many purchasers of real estate, often engage in transactions using shell companies, and engage intermediaries such as law firms to represent them and obscure their interest in a property transaction. Where a jurisdiction does not collect beneficial ownership information for such companies or for real property in general, and permits foreign companies to own real estate, it increases the likelihood that law enforcement and LFIs will not be able to identify the individuals behind a purchase or sale.
• Openness to foreign purchasers. A real estate sector that is entirely open to non-residents and non-citizens is likely to be more liquid than a closed sector. In addition, an open sector is exposed to illicit funds generated all over the world. Jurisdictions that offer residency or citizenship rights to foreign purchasers of domestic real estate may be particularly attractive to foreign illicit actors.
• High liquidity and rising prices. Illicit actors, like licit investors, want assurance that they will be able to sell an investment property for an amount that recoups their investment or offers a profit. Although they may be willing to tolerate a modest loss on the investment as the cost of money laundering, they may be more likely than most purchasers to seek to ‘flip' properties, buying and selling them in quick succession. A highly liquid market facilitates flipping and increases the likelihood that the sale price will meet or exceed the purchase price. In addition, rising prices and a ‘hot' market make it easier to disguise certain typologies, such as making small renovations to a property and then reselling it to an associate for a steeply increased price. The difference between the purchase price and the market value is then secretly refunded to the buyer in cash.
2.2.3 Typologies
Illicit actors may use a wide variety of strategies to launder the proceeds of crime through the real estate sector. Many of these strategies are not specific to the real estate sector and appear in a variety of contexts.
The following are some of the most common.
• Placement of cash. There are a variety of ways that the real estate sector can be used to place the cash proceeds of crime.
o Perhaps the simplest is purchasing a property in cash and then selling it, with the purchase price paid via wire or bank cheque. The criminal can identify a clear source of funds for the funds received, and can proceed to layer them using other techniques.
o This basic typology is subject to a number of variations. A property owner may pay for renovations in cash that represents the proceeds of crime, thus increasing the property's value. When the property is sold, the purchase price will include the value of illicit funds spent on renovations.
o An illicit actor may receive a bank loan to purchase the property, and then pay the loan back early in cash, or make payments in cash.
o Real estate investments, such as rental properties, may also be cash-intensive businesses. In jurisdictions where it is common to pay rent in cash, these properties can be used to commingle licit with illicit funds.
• Use of shell companies or other legal entities to obscure ownership. As discussed above, the use of shell companies—legal persons with no operations or employees—to hold real property is a common feature of real estate sectors all over the world. This practice facilitates investment and business (e.g. owning a shopping mall and collecting rent from tenants) and also preserves privacy (e.g. a prominent individual purchasing a home using a shell company to avoid her address becoming public knowledge).
Despite the legitimate uses of this technique, however, it can also be used to hide ownership when the true owner is an individual who does not want to be linked to the purchase. This may include Politically Exposed Persons (PEPs) who are purchasing properties that are inconsistent with their known sources of wealth; individuals who have past convictions for proceeds-generating offenses or are associated with negative news; and sanctioned individuals.
In place of or in addition to shell companies, illicit actors may use complex ownership structures, legal arrangements, and nominee arrangements to conceal their ownership interest in a real estate transaction. Please see the CBUAE's Guidance for Licensed Financial Institutions providing services to Legal Persons and Arrangements3 for more information on the risks of legal persons and arrangements.
• Use of intermediaries to obscure ownership. Similarly, individuals who wish to hide their connection to a real estate purchase or sale may rely on professional intermediaries—such as real estate brokers, lawyers, and accountants—to engage directly with financial institutions. Such intermediaries may be directly complicit in the concealment and aware that the true identity of their customer would raise questions about the transaction. Or they may simply be following professional rules that mandate professional secrecy regarding their clients.
• Manipulation of property values. Although real estate pricing is somewhat predictable, prices are sufficiently subjective to justify inflated or deflated pricing in service of laundering schemes.
o Two co-conspirators may arrange a sale of a property for a sum that does not represent its market value, with the difference being paid in cash: for example, the sale price is 20% higher than the market value, and the seller repays the buyer in cash. A purchase price higher than market value may be justified to authorities on the grounds that the property was perfect for the buyer's needs, or the buyer was anxious to complete the sale quickly. Similarly, a purchase price below market value may be justified on the grounds that the seller wanted a quick sale, or the property had structural issues.
o Illicit actors may conspire with corrupt officials or bank employees to inflate the assessed value of a property, facilitating these schemes.
o A criminal may also disguise illicit transfers as loans raised using the property as security. The higher the value of the property, the more money that can be laundered using this technique.
• Sequential selling. The repeated selling of real estate by a group of conspirators, or by a single individual using multiple shell companies, in an attempt to separate the ultimate owner from the criminal proceeds originally used to purchase the property. In many cases, the same individual(s) will buy the property or sell the property multiple times.
3 Available at centralbank.ae/en/cbuae-amlcft.
2.2.4 Regulation and Supervision of the Real Estate Sector in the UAE
2.2.4.1 Regulation of the Real Estate Sector
Regulation of the real estate sector as a whole—as opposed to regulation of real estate professionals—is the responsibility of each of the emirates and as a result varies across the UAE. This section discusses key aspects of regulation of the sector in Dubai and Abu Dhabi, the two largest property markets. Section 2.2.4.2 discusses regulation of real estate agents and brokers.
2.2.4.1.1 Openness to Foreign Purchasers
• Dubai: With the exception of nationals of the Gulf Cooperation Council (GCC), non-residents and non-citizens of the UAE are permitted to own real estate in Dubai only in one of the designated real estate investment areas. In general, foreign purchasers must be individuals; legal persons are not able to purchase real estate in the investment areas unless they make the purchase through a subsidiary incorporated in a Free Zone. Foreign trusts and other legal arrangements, including trusts or legal arrangements established in the Free Zones, are also not permitted to purchase real estate anywhere in the Emirate.
• Abu Dhabi: As in Dubai, foreigners are permitted to purchase real estate in Abu Dhabi only in one of nine designated real estate investment areas. Within these areas, there are no restrictions on the type of property they can own or the period of time for which they can own it. Outside of these areas, foreigners cannot exercise freehold ownership of property, although they can exercise other forms of long-term ownership, such as leaseholds and usufruct rights.
2.2.4.1.2 Residency Rights
Owners of freehold properties above a certain value may obtain an investor visa that grants them limited residency rights in the UAE. The larger the value of the property, the longer the length of the visa. Visa rules are set by the UAE federal government through Cabinet Resolution (56) of 2018 on Regulating the Residence Permits for Investors, Entrepreneurs and Specialised Talents, and thus apply to all emirates:
• Ownership of a property worth at least AED 1 million comes with a six-month multi-entry visa. Dubai will grant a three-year renewable residency visa in such circumstances.
• An individual who purchases a property of at least AED 5 million and retains it for three years is entitled to a five year residency visa.
• An individual who purchases a property of at least AED 10 million without a mortgage or other loan and retains it for three years is entitled to a ten year residency visa.
2.2.4.1.3 Use of cash
There are no legal restrictions on use of cash to purchase real estate or property in Dubai or Abu Dhabi.
2.2.4.2 Regulation and Supervision of Real Estate Professionals
Real estate agents and brokers in the UAE are required to be licensed. The Land Departments or municipality of each emirate and CFZ are responsible for granting licenses in the Mainland and CFZs; the Financial Services Regulatory Authority (FSRA) and Dubai Financial Services Authority (DFSA) license real estate agents in the FFZs.
Under Article 3 of AML-CFT Decision, real estate agents and brokers qualify as DNFBPs when they “conclude operations for the benefit of their Customers with respect to the purchase and sale of real estate." When they qualify as DNFBPs, real estate agents and brokers must comply with the same AML/CFT preventive measures as LFIs, including the requirements to conduct a risk assessment, perform CDD, and report suspicious transactions.
The Ministry of Economy supervises real estate professionals in the mainland and CFZs for compliance with AML/CFT obligations, and the FSRA and DFSA supervises them in the FFZs. The Ministry of Economy has issued guidelines for supervised entities describing their AML/CFT compliance obligations.4
4 These guidelines may be found at economy.gov.ae/english/Pages/AML.aspx.
3 Mitigating Risks
Although LFIs should judge their own risk tolerance and risk management capabilities, the CBUAE does not expect or encourage LFIs to broadly prohibit or exit customer relationships with the real estate and precious metals and stones sectors. These sectors are important parts of the UAE economy, and they need access to financial services to conduct their legitimate business. The CBUAE does expect, however, that LFIs understand their risk and take effective, risk-based steps to protect themselves from abuse and from illicit actors and transactions. Effective risk mitigation is therefore critical to protecting the LFI, complying with its legal obligations, and meeting supervisory expectations.
The sections below discuss how LFIs can apply specific preventive measures to identify, manage, and mitigate the risks associated with the real estate and precious metals and stones sectors. It is not a comprehensive discussion of all AML/CFT requirements imposed on LFIs. LFIs should consult the UAE legal and regulatory framework currently in force. The controls discussed below should be integrated into the LFI's larger AML/CFT compliance program, and supported with appropriate governance and training.
3.1 Risk-Based Approach
3.1.1 Overarching common requirements
LFIs must take a risk-based approach to the preventive measures they put in place for all customers, including customers in the real estate and precious metals and stones sectors. A risk-based approach means that LFIs should dedicate compliance resources and effort to customers, business lines, branches, and products and services in keeping with the risk presented by those customers, business lines, branches, and products and services, as assessed in accordance with Article 4 of AML-CFT Decision.
The risk-based approach has three principal components:
3.1.1.1 Conducting an enterprise risk assessment, as required by Article 4.1 of AML-CFT Decision.
The enterprise risk assessment should reflect the presence of higher-risk customers, including DPMS and real estate sector participants in an LFI's customer base. This assessment should include higher-risk customers from outside the UAE whose risks will also need to be assessed. These assessments should in turn be reflected in the LFI's inherent risk rating. In addition, the controls risk element of the LFI's enterprise risk assessment, as required by section 4.2.1 of the Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations Guidelines for Financial Institutions, should take into consideration the strength of the controls that the LFI has in place to mitigate the risks posed by its higher-risk customers, including the preventive measures discussed below.
3.1.1.2 Identifying and assessing the risks associated with specific customers.
The LFI should assess the risk of each customer to identify those that require enhanced due diligence (EDD) and to support its entity risk assessment. In assessing the risks of a DPMS or real estate sector participant, LFIs should consider:
i. Geographic Risk: The risks associated with the jurisdictions in which the customer lives (for individuals) or is registered/headquartered (for legal persons) and where it operates, including the jurisdictions where it has subsidiaries, where it sources its products (where relevant), and where its main counterparties are based. These may include the overall risk of money laundering, terrorist financing, and financing of proliferation, as well as what is known regarding the prevalence of abuse of entities in these sectors.
There are a number of sources that LFIs can use to develop a list of high-risk countries, jurisdictions, or regions. LFIs should consult any publications issued by the National Anti-Money Laundering and Combating the Financing of Terrorism and financing of Illegal Organizations Committee (NAMLCFTC)5, UAE FIU and by the FATF, including the FATF's list of jurisdictions subject to countermeasures and to increased monitoring. LFIs may also use public free databases such as, for example, the Basel AML Index6 or the Transparency International Corruption Perceptions Index.7 LFIs should not rely solely on public lists, however, and should consider their own experiences and the nature of their exposure to each jurisdiction when assessing the risk of that jurisdiction.
ii. Customer Risks: For real estate agents and brokers and DPMS, customer risk can be assessed as the proportion of higher-risk customer types (e.g. PEPs, legal persons, and customers from high- risk jurisdictions) within a customer's customer base.
iii. Product, Service, and Delivery Channel Risk: LFIs should assess risk in this category on two dimensions:
a. The products and services that the customer offers to its customers, and the delivery channels through which it offers these products and services. Products, services, and delivery channels that promote the rapid, anonymous transfer of high values are particularly attractive to illicit actors. These may include, but are not limited to:
i. Online/non-contact sales: Non-face to face transactions make it easier for criminals to hide their identifies.
ii. Accepting cash for high-value purchases. Cash is very difficult to trace and can be exchanged without involving the formal banking system, and thus is particularly attractive to criminals.
iii. Accepting virtual assets: Virtual assets, like cash, are anonymous and difficult to trace to their users. Unlike cash, virtual assets allow parties to carry out transactions even when they are at a distance from one another. These qualities, combined with the lack of consistent regulation of entities that deal in virtual assets, make virtual assets high risk for abuse by illicit actors.
Specific high-risk products and services offered by each customer type are discussed below in sections 3.1.2 and 3.1.3.
b. The LFI products and services that the customer intends to use, and the delivery channels through which the LFI will provide these services. LFIs should draw on their entity risk assessment to assess the risk of the products and services each customer uses or intends to use. (This subject is also discussed in section 3.2.1.3.2 below in relation to understanding the nature and purpose of the business relationship.)
iv. Controls Risk: LFIs should seek to understand the regulatory requirements in place for the customer, as well as how well they are enforced. This assessment is particularly important for those DPMS and real estate brokers that qualify as DNFBPs and therefore are also subject to such requirements. Other participants in the real estate sector, such as developers, are not required to comply with AML/CFT preventive measures. In addition, participants in the precious metals and stones sector may also be required to comply with UAE requirements or global standards related to sourcing precious metals and stones and transparency of supply chains. Where relevant to a customer's business, LFIs should consider whether its customer conducts appropriate supply chain due diligence.
Questions that an LFI may ask to determine customer risk profile include, but are not limited to:
• Where is the customer incorporated? Where does it operate? Are these high-risk jurisdictions? • What products and services does the customer provide? • What is the trading volume of the business? • What customer base does the customer serve? • What is the regulatory environment in the jurisdiction(s) where the customer is incorporated/has operations? • Is there an authority that actively enforces the requirements? • Is the customer required to perform CDD on cash customers above a certain threshold in all jurisdictions where it operates? In such scenarios, is it required to identify the beneficial owners of legal person customers? • Is the customer required (as are DNFBPs in the UAE) to conduct a regular independent audit? Did the most recent audit have any material findings? • Does the customer perform sanctions screening? • What is the main channel (in-person vs. online) and methods (cash, wire transfers, checks, etc.) of conducting transactions and in which currency (or multiple currencies)?
In addition to risk rating customers, LFIs should also consider the risks of specific transactions, especially high-value transactions, those involving high-risk jurisdictions, and those that represent departures from a customer's standard or expected behavior. LFIs should be aware of sectoral risks when reviewing large transactions associated with the DPMS or real estate sectors, or transactions of any size that do not have a clear licit economic purpose.
5 Available at: namlcftc.gov.ae/en/high-risk-countries.php
6 Available at: baselgovernance.org/basel-aml-index
7 Available at: transparency.org/en/cpi/2020/index/nzl3.1.1.3 Applying EDD and other preventive measures
LFIs must apply EDD and other preventive measures to customers determined to be higher-risk, as required by Article 4.2(b) of AML-CFT Decision, or to specified higher-risk customer types, no matter their risk rating, as required by AML-CFT Decision. EDD measures should be designed to mitigate the specific risks identified with particular customers. Examples of EDD measures are offered below in section 3.2.
3.1.2 Key Considerations for DPMS
Beyond the general considerations discussed above, in assessing the risk of a DPMS customer LFIs should consider:
• Geographic Risk: Whether the jurisdiction(s) in which the customer is based or operates are known centres for illegal or unregulated mining of precious metals and stones.
• Product, Service, and Delivery Channel Risk: The following products and services are particularly high risk:
o Trade in gold bullion and diamonds: The high inherent value of these substances, their ability to retain value for a long period of time, the size and stability of the market, relative ease of exchange, high value by weight, and the difficulty of tracing them makes gold and diamonds particularly attractive to criminals.
o Metal accounts: Metal accounts are accounts held by a custodian institution and denominated in precious metals (such as gold, silver, or platinum) rather than in fiat currencies. They allow the account holder to quickly buy and sell precious metals without needing to have a face-to-face interaction with a DPMS.
3.1.3 Key Considerations for the Real Estate Sector
Beyond the general considerations discussed above, in assessing the risk of a customer who is a participant in the real estate sector, LFIs should consider:
• Controls Risk: In the case of transactions or customers related to the real estate sector, an assessment of controls risk should also include the regulations governing the real estate sector as a whole, and not just regulations governing the sector participants (real estate agents and brokers). LFIs should assess whether regulations governing property transactions are likely to make the sector more or less attractive to illicit actors. As discussed above in section 2.2.2, these may include the openness to foreigners, the widespread use of cash and shell companies, and the intensity of scrutiny of real estate transactions.
In many cases neither party to a real-estate related-transaction will be a business or individual whose primary activity is related to the real estate sector (e.g., the sale of a private home). In such cases, in addition to the risk of the specific customer involved, LFIs should consider aspects of the transaction itself, including:
• The jurisdiction in which the real property that is the subject of the transaction is located; • The jurisdiction in which the customer's counterparty is located; • If the LFI's customer is the purchaser, whether the purchase price is consistent with the purchaser's known means and income; • Whether the purchase price is generally consistent with the market price for roughly similar properties; • Whether all parties to the transaction are resident in jurisdictions other than the jurisdiction in which the property is located; • Whether the seller of the property has owned it only for a short period of time; • Whether shell companies or other legal structures are involved in the purchase in such a way as to obscure the true owner of the property; and • Whether the parties to the transaction appear to be related (e.g. are represented by the same law firm or real estate broker, share corporate directors, or share an address), but the relationship between them is unclear.
3.2 Customer Due Diligence and Enhanced Due Diligence
CDD, and where necessary EDD, are the core preventive measures that help LFIs manage the risks of all customers, particularly higher-risk customers. As discussed below, each stage of the CDD process gives LFIs an opportunity to collect the information they need to identify and manage the specific risks of higher- risk customers.
The goal of the CDD process is to ensure that LFIs understand who their customer is and the purpose for which the customer will use the LFI’s services. Where an LFI cannot satisfy itself that it understands a customer, then it should not accept that legal person or legal arrangement as a customer. If there is an existing business relationship, the LFI should not continue it. LFIs should also consider filing a Suspicious Transaction Report (STR), as discussed in section 3.3 below.
Under Article (5) of AML-CFT Decision, LFIs must conduct CDD before or during the establishment of the business relationship or account, or before executing a transaction for a Customer with whom there is no business relationship. Although Article 5 permits CDD to be delayed in circumstances of lower risk, the higher risk of the DPMS and real estate sectors makes it very unlikely that delayed CDD will be appropriate in the context of onboarding such customers.
LFIs should consult the UAE legal and regulatory framework currently in force for a full discussion of their CDD obligations and of the CBUAE's expectations for CDD procedures.
3.2.1 Overarching common requirements
The following elements of CDD should be carried out for all customers, no matter the customer type.
3.2.1.1 Customer Identification and verification
Under Article 8 of AML-CFT Decision, LFIs are required to identify and verify the identity of all customers.
In most countries, including the UAE, anyone operating a business, whether as an individual or a legal person, must have a business license. Such persons may also need to be registered with their country's ministry of commerce or economy. Among other documents required for customer identification and verification, LFIs should ensure that they collect proof of an active license and/or registration from all business customers. Where a license is required, lack of one may indicate that a customer is attempting to avoid regulation and supervision by the authorities in the UAE or in its home jurisdiction.
3.2.1.2 Beneficial Owner Identification
The majority of DPMS and real estate sector customers will be legal persons. The UAE requires all financial institutions to identify the beneficial owners of a legal person customer by obtaining and verifying the identity of all individuals who, individually or jointly, have a controlling ownership interest in the legal person of 25% or more. Where no such individual meets this description, the LFI must identify and verify the identity of the individual(s) holding the senior management position in the entity.
Legal arrangements may be involved in transactions related to real estate. For legal arrangement customers, LFIs must verify the identity of the settlor, the trustee(s), or anyone holding a similar position, the identity of the beneficiaries or class of beneficiaries, the identity of any other natural person exercising ultimate effective control over the legal arrangement and obtain sufficient information regarding the beneficial owner to enable verification of his/her identity at the time of payment, or at the time he/she intends to exercise his/her legally acquired rights.
The beneficial owner of a legal person or arrangement must be an individual. Another legal person or arrangement cannot be the beneficial owner of a customer, no matter what percentage it owns. LFIs must continue tracing ownership all the way up the ownership chain until they discover all individuals who own or control at least 25% of the LFI's customer.
When the LFI has identified qualifying beneficial owners, it should perform CDD on each individual beneficial owner, in accordance with the requirements of Article 8.1(a) of AML-CFT Decision.
Please see the CBUAE's Guidance for Licensed Financial Institutions providing services to Legal Persons and Arrangements8 for more information on identification of beneficial owners.
8 Available at centralbank.ae/en/cbuae-amlcft
3.2.1.2.1 EDD: Beneficial Ownership
If the LFI is not confident that it has identified the individuals who truly own or control the customer, or when other high-risk factors are present, the LFI should consider intensifying its efforts to identify the beneficial owners. The most common method of doing so is to identify additional beneficial owners below the 25% ownership threshold mandated by UAE law. This may involve identifying and verifying the identity of beneficial owners at the 10% or even the 5% level. It may also involve requiring the customer to provide the names of all persons who own or control any share in the customer—without requiring them to undergo CDD—in order to conduct sanctions screening or negative news checks.
3.2.1.3 Nature of the Customer’s Business and Nature and Purpose of the Business Relationship
For all customer types, LFIs are required to understand the purpose for which the account or other financial services will be used, and the nature of the customer's business. This step requires the LFI to collect information that allows it to create a profile of the customer and of the expected uses to which the customer will put the LFI's services. This element of CDD will have important implications for the customer risk rating. This is particularly true of the nature of the customer's business, which will likely be the critical determinant of risk for customers of the types addressed in this Guidance.
3.2.1.3.1 Nature of the Customer’s Business
Understanding the nature of the customer's business involves first i) identifying that the customer is a participant in a higher-risk sector; and ii) collecting all the information necessary to assess the risk factors for that specific customer type, as described in section 3.1 above. Customers may not identify themselves explicitly as DPMS or real estate sector participants. In some cases, the nature of the customer's business will be clear based on the customer's own statements; in others, the LFI may need to ask additional questions to ascertain whether or not the customer carries out any of the qualifying activities. For example, an importer/exporter may qualify as a DPMS if it trades in precious metals and stones among other products, or a department store may qualify if it sells fine jewelry.
Following the determination of the customer's sector, the LFI should collect the information necessary to understand the products and services the customer offers, where it operates, and who its customers are. The exact information collected will depend on both the nature of initial findings and on the risk level of the entity. For example:
• Company A is a large commercial real estate broker licensed in Sharjah and supervised as a DNFBP by the Ministry of Economy. Company A applies for a general purpose business account with Bank C, an LFI. Bank C interviews Company A regarding its business activities and customer base, and asks Company A to supply a copy of its institutional risk assessment and its CDD and STR policies.
• Company B, a small business based in Dubai, seeks to establish a checking account with Bank C, an LFI. Company B represents that it primarily sells furniture and curios, but in response to questions from Bank C during the CDD process discloses that it sells gold and silver coins and also that it accepts cash payments. Company B is not licensed as a DPMS and is not registered by the Ministry of Economy. Bank C decides to make an unannounced site visit to Company Band discovers that gold objects make a up a large part of its inventory. Bank C declines to consider opening the account until Company B is licensed and registered as a DPMS.
3.2.1.3.2 Nature and Purpose of the Business Relationship
The risk to which the LFI may be exposed can vary based on the purpose of the account and the types of financial products and services the customer wishes to use. Nevertheless, if other risk factors are present a customer may still qualify as high risk even if they use only low-risk products and services.
• Certain aspects of a customer's business may be higher risk than others. For example, an account used for payroll may be lower risk than an account used to pay suppliers or that receives payments directly from customers.
• Certain LFI products and services may expose the LFI to higher risk. These include cash management services or large-scale cash deposits, and international wires, especially wires to or from high-risk or secrecy jurisdictions. These services are higher risk because they facilitate rapid movements of value across borders, or (in the case of cash) because they are conducive to anonymity. The LFI's entity risk assessment should identify its higher-risk products and services, and a customer that intends to use such services should be risk-rated accordingly.
For example:
• Company X is a small DPMS operating in the Dubai Gold Souk that applies for a general purpose checking account with Bank C, an LFI. Company X tells Bank C that it sells gold jewelry. It claims that it does not accept cash and has not registered as a DNFBP, but tells Bank C to expect weekly cash deposits. The relationship manager visits the store and observes a sign by the cash register saying “Payment by Cheque or Credit Only.” Bank C decides to prohibit cash deposits into the account with prior authorization, and to restrict such deposits to a low monthly total.
3.2.1.3.3 Developing a Customer Profile
Businesses, including those in the DPMS and real estate sectors engage in an extremely wide variety of financial activity, potentially a wider variety than individual customers are likely to display. The activity profile of a cash-intensive business such as a small DPMS is likely to be completely different from that of a large- scale commercial developer. At the same time, specific businesses are also likely to engage in patterns of activity that remain constant from month to month and year to year. Understanding the purpose of the account allows LFIs to develop expected patterns and compare them to actual behaviour.
3.2.1.3.4 EDD: Customer’s Business and the Business Relationship
As LFIs advance efforts to understand their customer's business and financial activities, they should consider whether aspects of the customer profile require EDD. The following are some situations in which EDD may be appropriate:
• The customer has business or other ties to high-risk jurisdictions (if the customer or its beneficial owners are based in a high-risk jurisdiction, EDD is mandatory). • The customer intends to use high-risk financial products and services, such as bulk cash services or purchase and exchange of virtual assets. • The LFI does not fully understand the customer's business model, or the customer has no clear business activities that would justify its expected to use of the account.
EDD on the business activities and account use of business like DPMS and real estate sector participants can involve the following:
• Requiring the customer to provide invoices documenting incoming and outgoing transfers; • Inspecting payroll documents and other business records; • Visiting the customer's business premises and interviewing its personnel; • Requesting a reference from a current customer or other well-known firm with which the new customer claims to do business, or which operates in the same sector as the new customer.
3.2.1.4 Ongoing Monitoring
All customers must be subject to ongoing monitoring throughout the business relationship. Ongoing monitoring ensures that the account or other financial service is being used in accordance with the customer profile developed through CDD during onboarding, and that transactions are normal, reasonable, and legitimate.
3.2.1.4.1 CDD Updating
LFIs are required to ensure that the CDD information they hold on all customers is accurate, complete, and up-to-date. This is particularly crucial in the context of customers that are companies, which, by their very nature, can change their fundamental identity overnight. With the stroke of a pen, a company engaged in a low-risk business and owned by reputable UAE residents can move its activities to a high-risk sector and can transfer ownership to nationals of a high-risk foreign jurisdiction. For example:
• Mr. Y and Sons is a highly-reputable dealer in uncut diamonds that has been banking with Bank C for more than 40 years. Bank C's account manager reads in the newspaper that Mr. Y has recently passed away and calls on Mr. Y's sons to express his condolences. During the course of the conversation, the account manager asks which son will be in charge of the business going forward. They inform him that they have just sold the business to a consortium of investors who wished to remain anonymous but who were represented by a global law firm with offices in the Free Zone. Once it has become aware of this fact, Bank C should rapidly identify the new beneficial owners of the customer. If it cannot do so promptly, it should suspend activity on the account.
LFIs should update CDD for all customers on a risk-based schedule, with CDD on higher-risk customers being updated more frequently. EDD on all customers should involve more frequent CDD updates.
CDD updates should include a refresh of all elements of initial CDD, and in particular should ascertain that:
• The customer's beneficial owners remain the same; • The customer continues to have an active status with a company registrar; • The customer has the same legal form and is domiciled in the same jurisdiction; • The customer is engaged in the same type of business, and in the same geographies;
In addition to a review of the customer's CDD file, the LFI should also review the customer's transactions to determine whether they continue to fit the customer's profile and business, and are consistent with the business the customer expected to engage in when the business relationship was established. This type of transaction review is distinct from the ongoing transaction monitoring discussed in section 3.2.1.4.2 below. The purpose of the review is to complement transaction monitoring by identifying behaviours, trends, or patterns that are not necessarily subject to transaction monitoring rules. For example:
• Bank C is conducting its scheduled CDD review for Company A, a commercial real estate brokerage firm. When reviewing the customer's transactions over the past year, Bank C notices that Company A has begun making fairly regular payments to a counterparty in Country 1. Previously, Company A had engaged in extremely limited cross-border activity. The payments do not exhibit any red flags and therefore were not flagged by Bank C's automated transaction monitoring system. Bank C contacts Company A and learns that it is has recently entered into a referral agreement with a private bank in Country 1. The bank refers customers looking to invest in the real estate sector, in Country 2, to Company A and in return receives a percentage of any commission Company A makes on a resulting sale. Bank C decides to conduct additional due diligence to learn more about the customer base referred to Company A by the bank in Country 1.
The techniques used for transaction review will vary depending on the client. For lower-risk clients, a review of alerts, if any, is likely to be sufficient. For higher risk clients, a more intensive review may be necessary. For clients with a large volume of transactions, LFIs may use data analysis techniques to identify unusual behaviour.
If the review finds that the customer's behaviour or information has materially changed, the LFI should risk- rate the customer again. New information gained during this process may cause the LFI to believe that EDD is necessary, or may bring the customer into the category of customers for which EDD is mandatory (i.e. customers that are PEPs, or owned or controlled by PEPs, or their family members or associates; and customers that are based in high-risk jurisdictions).
LFIs may consider requiring that the customer update them as to any changes in its beneficial ownership or business activities. Even if this requirement is in place, however, LFIs should not rely on the customer to notify it of a change, but should still update CDD on a schedule appropriate to the customer's risk rating.
3.2.1.4.2 Transaction Monitoring
LFIs must monitor activity by all customers to identify behaviour that is potentially suspicious and that may need to be the subject of an STR (see section 3.3 below). As with all customer types, LFIs that use automated monitoring systems should apply rules with appropriate thresholds and parameters that are designed to detect common typologies for illicit behaviour. When monitoring and evaluating transactions, the LFI should take into account all information that it has collected as part of CDD, including the identities of beneficial owners. For example, a series of transactions between two unconnected companies may not be cause for an alert. But if the companies are all owned or controlled by the same individual(s), the LFI should investigate to make sure that the transactions have a legitimate economic purpose.
Where possible, monitoring systems should also flag unusual behaviour that may indicate that a customer's business has changed—for example, a first transfer to or from a high-risk jurisdiction, or a large transaction involving a new counterparty. LFIs should follow up on such transactions with the customer to discover whether the customer has changed its business activities in such a way as to require a higher risk rating.
Sample red flags for illicit behaviour involving DPMS and the real estate sector are provided in the Annex to this Guidance.
3.2.1.4.3 EDD: Ongoing Monitoring
When customers are higher risk, monitoring should be more frequent, intensive, and intrusive. LFIs should review the CDD files of higher risk customers on a frequent basis, , such as every six or nine months for very high-risk customers. The methods LFIs use to review the account should also be more intense and should not rely solely on information supplied for the customer. For example, LFIs should consider:
• Manually reviewing all transactions on the account on a quarterly basis, rather than a sample of transactions (as discussed above, such manual review should be in addition to automated transaction monitoring). Manual review can take the form of reviewing individual transactions, or of using data analysis to determine information about the customer's activity (e.g., overall percentage of counterparties in high-risk jurisdictions; new jurisdictions of activity compared to last quarter; overall percentage of transactions that are round numbers, etc.) that would not be apparent to automated transaction monitoring systems;
• Conducting site visits at the customer's premises and requesting a meeting with the customer's managing director or Chief Financial Officer;
• Conducting searches of public databases, including news and government databases, to independently identify material changes in a customer's ownership or business activities or to identify adverse media reports. Searches for adverse media should include relevant key words, including, but not limited to, allegation, fraud, corruption, and laundering.
In addition, higher-risk customers should be subject to more stringent transaction monitoring, such as lower thresholds for alerts and more intensive investigation.
3.2.2 Key Considerations for DPMS
All of the requirements above apply fully to DPMS customers. This section describes specific or additional considerations that LFIs should have in mind when carrying out CDD on such customers.
• Nature of the Customer’s Business: Understanding the nature of the customer's business is particularly important in the context of DPMS, as risk is largely driven by the nature of the entity's business activities. LFIs should consider factors such as:
o Whether the customer qualifies as a DNFBP, and, if so, whether it is registered as such with the appropriate authority in its home jurisdiction (in the UAE, this is the Ministry of Economy, see section 2.2.4);
o The DPMS-specific risks of the countries where the customer does business (see section 3.1.1.2 (i)). Certain countries that may not be considered extremely high risk in other contexts may be very high risk in the DPMS sector, such as countries where illegal mining takes place on a significant scale, or countries were smuggling of gold and precious stones is particularly common;
o The products and services the customer provides, and their attractiveness to illicit actors.
o Example: Customer, a large Abu Dhabi luxury goods store, seeks to establish a general purpose business account with Bank B, an LFI. Customer sells fine jewelry to a clientele that includes a number of PEPs. Bank B collects additional information about sales and policies from Customer, and determines that all purchases of fine jewelry must be made using a credit card, and that fine jewelry accounts for less than 10% of Customer's annual turnover. Bank B decides that EDD is not necessary at this point, but decides to review activity on the account after six months to determine whether it presents any red flags.
• Ongoing Monitoring: Because DPMS risk varies with their business activities, it is particularly important that LFIs monitor DPMS accounts for any unexpected changes in activity. A change in activity is not necessarily a sign of illicit behaviour, but it may indicate that a DPMS has changed its activity profile in ways that affect its risk rating.
o Example: When conducting its scheduled review of activity on the account of Customer, a large Abu Dhabi luxury goods store, Bank B notices that Customer has recently begun to receive large transfers from Iraq. When Bank B contacts Customer, the store explains that they've just begun conducting ‘trunk shows' of fashion and fine jewelry for customers in Iraq and as a result have substantially increased the business they do with customers there. Based on this information, Bank B increases Customer's risk rating and considers placing other controls on the relationship.
3.2.3 Key Considerations for the Real Estate Sector
Customers that are overall low-risk, and whose business is unrelated to the real estate sector, can nonetheless engage in high-risk transactions related to the sector. For example, a retired businesswoman who has been a customer of an LFI for twenty years may sell her luxury villa to a foreign PEP. In such cases, the CDD that has been performed on the customer may not be sufficient to manage the risk of this particular transaction, and LFIs may need to perform additional transactional due diligence. Transactional due diligence may also be necessary to comply with the requirements of Article 7.1 of AML-CFT Decision, which requires LFIs to audit transactions carried out throughout the business relationship to ensure that the transactions are consistent with the customer's risk profile.
Transactional due diligence should at least involve collecting additional information about the underlying activity and the customer's counterparty. Information that an LFI may request in the context of transactional due diligence on real estate transactions includes:
• Sufficient information about the property to support an assessment that the purchase/sale price is reasonable and generally consistent with values for similar properties. This may include its official valuation for property tax purposes (where one exists); cadastral maps for the area where the property is located; floor plans; photographs; and recent sales information for similar properties. Where the LFI is financing a purchase, or has previously financed the purchase of the same property, it likely has this information on hand already.
• Information about the customer's counterparty. Where the counterparty is an individual, this should include sufficient information to perform adverse media, sanctions and PEP screening. Adverse media searches should include searches of public records and databases using relevant key words, including but not limited to, allegation, fraud, corruption, laundering.
• Where the counterparty is a legal person, it should include the jurisdiction in which the counterparty is registered/headquartered; identifying information on the counterparty's beneficial owners and line of business.
• Information on source of funds and source of wealth. LFIs should be able to identify the source of funds for every large transaction related to the real estate sector. Where a transaction is financed, the source of funds will often be a bank loan, but for unfinanced transactions the determination may be more difficult. For high-risk customers or counterparties, such as PEPs, LFIs should also understand the source of overall wealth, in addition to the source of the specific funds used to purchase the property.
3.3 STR Reporting
As required by Article 15 of AML-CFT Law and Article 17 of AML-CFT Decision, LFIs must file a STR with the UAE Financial Intelligence Unit (UAE FIU) when they have reasonable grounds to suspect that a transaction, attempted transaction, or certain funds constitute, in whole or in part, the proceeds of crime, is related to a crime, or is intended to be used in a crime. STR filing is a legal obligation and a critical element of the UAE’s effort to combat financial crime and protect the integrity of its financial system. By filing STRs with the UAE FIU, LFIs help to alert law enforcement about suspicious behaviour and allow investigators to piece together transactions occurring across multiple LFIs.
In addition to the requirement to file an STR when an LFI suspects that a transaction or funds are linked to a crime, LFIs should consider filing an STR in the following situations:
• A potential customer decides against opening an account or purchasing other financial services after learning about the LFI's CDD requirements; • A current customer cannot provide required information about its business or its beneficial owners; • A customer cannot adequately explain transactions, provide supporting documents such as invoices, or provide satisfactory information about its counterparty; or • The LFI is not confident, after completing CDD procedures, that it has in fact identified the individuals owning or controlling the customer. In such cases, the LFI should not establish the business relationship, or continue an existing business relationship.
Please consult the CBUAE's Guidance for Licensed Financial Institutions on Suspicious Transaction Reporting9 for further information.
9 Available at centralbank.ae/en/cbuae-amlcft
3.4 Governance and Training
The specific preventive measures discussed above should take place within, and be supported by, a comprehensive institutional AML/CFT program that is appropriate to the risks the LFI faces. The core of an effective risk-based program is an appropriately experienced AML/CFT compliance officer who understands the LFI’s risks and obligations and who has the resources and autonomy necessary to ensure that the LFI’s program is effective.
As with all risks to which the LFI is exposed, the AML/CFT training program should ensure that employees are aware of the risks of DPMS and real estate sector customers, are familiar with the obligations of the LFI, and are equipped to apply appropriate risk-based controls. Training should be tailored and customized to the LFI's risk and the nature of its operations. For example, an LFI that has a large number of DPMS customers should offer training that includes an in-depth discussion of risk factors and red flags related to such customers.
Annex 1. Red Flags
Red Flags for DPMS
Trade practices
• Precious metals and stones originate from a country where there is limited production or no mines at all.
• Trade in large volumes conducted with countries which are not part of a specific precious metals and stones pipeline.
• An increase of the volume of the activity in a DPMS account despite a significant decrease in the industry-wide volume.
• Selling or buying precious metals and stones between two local companies through an intermediary located abroad (lack of business justification. uncertainty as to actual passage of goods between the companies).
• Volume of purchases and/or imports that grossly exceed the expected sales amount.
• Sale of gold bars, coins, and loose diamonds from a jewelry store (retail).
• Payments related to the appearance of rare or unique precious stones in the international market outside of known trading procedures (e.g., Argyle's rare pink diamond appearing in the international marketplace outside of the annual tender process). This to the best knowledge of the financial institution.
• A single bank account is used by multiple businesses.
Transactions/financing of precious metals and stones trade
• Unusual forms of payment in the trade, for example, use of travelers cheques (all stages according to the accepted forms of payments).
• Date of payment not customary in the trade, (e.g. receiving/sending funds for a precious metal and stone deal conducted a very long time ago (outside accepted payment terms). Or, a customer paying upfront where the customary payment date is within a 120 days term.
• Financial activity is inconsistent with practices in the precious metal and stone trade. For example,
o Foreign currency deposits followed by currency conversion and cash withdrawal in local currency.
o Cheque deposits followed by immediate cash withdrawals in slightly lower amounts (possible use of the DPMS account for cheques discounting).
o Transfers of foreign currency and/or foreign currency cheques deposits, followed by currency conversion and immediate withdrawal from the account (possible use of the DPMS account for exchange services)
• No economic rationale for transactions involving an individual or company in the precious metal and stone industry.
• Deposits immediately followed by withdrawals, atypical of practices in the precious metal and stone trade, including but not limited to:|
o Circular transaction related to import/export of precious metals and stones.
o Circular transactions related to local trade (between local bank accounts).
o Circular financial transactions between a precious metal and stone company's account and the private account of the company's shareholder/director, without business or economic reason.
o High turnover of funds through an account with a low end of day balance.
• Deposits or transfers to a precious metal and stone dealer's account from foreign companies followed by immediate transfer of similar amounts to another jurisdiction.
• Immediately after a precious metal and stone dealer's related account is opened, high-volume and high-value account activity is observed.
• Transactions between accounts of different companies which are affiliated with the same customer, particularly to or from Free Trade Zones or countries with tax leniencies 119 (may be an indication of transfer pricing or trade mispricing).
• Open export is settled by offsetting to, and receiving payment from, a third party.
• Open export is settled abroad by offset in front of the importer.
• Settling an open export invoice with unrelated companies that engage in a specific precious metal and stone and not through value/return from abroad or return of goods to the precious metal and stone merchant.
• Details of the transaction are different from the details of the commercial invoice presented by the DPMS to the bank (name of importer/exporter, sum, place etc.)
• High-value funds deposited or transferred to an account described as short-term loans with no transactions showing repayment of loans.
• Early repayment of DPMS loan (a loan for 25 years is repaid after five month) with no reasonable explanation.
• Sale of diamonds and jewelry at small incremental amounts (retail).
• Multiple cheques drawn on the same DPMS' account on the same day.
• Origin/destination of funds is different from the destination/origin of the specific precious metal and/or stone.
• DPMS is credited by transactions with no evidence of sales.
• Numerous returns of advanced payments.
Customers
• Activity does not match KYC, for example:
o Actual trade volumes are significantly larger than the expected volume.
o Customers and/or suppliers of the customer do not correspond to the stage of the trade initially declared.
• DPMS is not familiar with trade practices.
• DPMS maintains high level of secrecy.
• DPMS conducting activity in a branch not specializing in precious metals and stones (where such branches exist).
• Use of a bank account in the name of a charity to transfer funds to/from DPMS.
• Frequent changes in company name and contact person for a business in the industry (mainly wholesale)
Use of third parties
• Customer consults a third party while conducting transactions.
• Receiving/transferring funds for import/export activity to/from entities that are not known to be involved in the precious metals and stones trade (either an individual or a legal entity).
• Return of an advanced payment from a third party.
• Receiving/transferring funds for import/export where the ordering customer/beneficiary is an MSB.
• Use of third parties to deposit funds into single or multiple DPMS' accounts.
• Return of an advanced payment from a third party.
• Name of sender in the payment transfer to the DPMS is not the importer/buyer (mainly rough and polished trade).
• Name of receiver in the payment from the DPMS is not the exporter/supplier.
• A single bank account with multiple deposit handlers (retail and wholesale).
Use of missing/suspicious/falsified documents
• For diamond dealers, Kimberly Process (KP) certificate is or seems to be forged.
• Long validity of a KP certificate
• Transfers of funds or an attempt to transfer funds through a DPMS company's account without producing appropriate documentation.
• DPMS claims funds received/transferred are an advanced payment without producing any appropriate export/import invoice to support it.
• Transfers between a DPMS and a private account that are reported to the bank as precious metal and/or stone transactions, without presenting appropriate documentation.
• Invoice presented by the DPMS appears to the bank as unreliable/fake.
• Failing to provide a customs declaration in relation to a foreign currency cash deposit resulting from selling precious stones abroad.
Red Flags for the Real Estate Sector
Natural persons
• Transactions involving individuals residing in tax havens or risk territories, when the characteristics of the transactions match any of those included in the list of indicators. • Transactions carried out on behalf of minors, incapacitated persons or other persons who, although not included in these categories, appear to lack the economic capacity to make such purchases. • Transactions involving persons who are being tried or have been sentenced for crimes or who are publicly known to be linked to criminal activities involving illegal enrichment, or there are suspicions of involvement in such activities and that these activities may be considered to underlie money laundering • Transactions involving persons who are in some way associated with the foregoing (for example, through family or business ties, common origins, where they share an address or have the same representatives or attorneys, etc.). • Transactions involving an individual whose address is unknown or is merely a correspondence address (for example, a PO Box, shared office or shared business address, etc.), or where the details are believed or likely to be false. • Several transactions involving the same party or those undertaken by groups of persons who may have links to one another (for example, family ties, business ties, persons of the same nationality, persons sharing an address or having the same representatives or attorneys, etc.). • Individuals who unexpectedly repay problematic loans or mortgages or who repeatedly pay off large loans or mortgages early, particularly if they do so in cash.
Legal persons
• Transactions involving legal persons or legal arrangements domiciled in tax havens or risk territories, when the characteristics of the transaction match any of those included in the list of indicators. • Transactions involving recently created legal persons, when the amount is large compared to their assets. • Transactions involving legal persons or legal arrangements, when there does not seem to be any relationship between the transaction and the activity carried out by the buying company, or when the company has no business activity. • Transactions involving foundations, cultural or leisure associations, or non-profit-making entities in general, when the characteristics of the transaction do not match the goals of the entity. • Transactions involving legal persons which, although incorporated in the country, are mainly owned by foreign nationals, who may or may not be resident for tax purposes. • Transactions involving legal persons whose addresses are unknown or are merely correspondence addresses (for example, a PO Box number, shared office or shared business address, etc.), or where the details are believed false or likely to be false. • Various transactions involving the same party. Similarly, transactions carried out by groups of legal persons that may be related (for example, through family ties between owners or representatives, business links, sharing the same nationality as the legal person or its owners or representatives, sharing an address, in the case of legal persons or their owners or representatives, having a common owner, representative or attorney, entities with similar names, etc.). • Formation of a legal person or increases to its capital in the form of non-monetary contributions of real estate, the value of which does not take into account the increase in market value of the properties used. • Formation of legal persons to hold properties with the sole purpose of placing a front man or straw man between the property and the true owner. • Contribution of real estate to the share capital of a company which has no registered address or permanent establishment which is open to the public in the country. • Transactions in which unusual or unnecessarily complex legal structures are used without any economic logic. Natural and legal persons • Transactions in which there are signs, or it is certain, that the parties are not acting on their own behalf and are trying to hide the identity of the real customer. • Transactions which are begun in one individual's name and finally completed in another's without a logical explanation for the name change. (For example, the sale or change of ownership of the purchase or option to purchase a property which has not yet been handed over to the owner, reservation of properties under construction with a subsequent transfer of the rights to a third party, etc.). • Transactions in which the parties: o Do not show particular interest in the characteristics of the property (e.g. quality of construction, location, date on which it will be handed over, etc.) which is the object of the transaction. o Do not seem particularly interested in obtaining a better price for the transaction or in improving the payment terms. o Show a strong interest in completing the transaction quickly, without there being good cause. o Show considerable interest in transactions relating to buildings in particular areas, without caring about the price they have to pay. o Transactions in which the parties are foreign or non-resident for tax purposes and: o Their only purpose is a capital investment (that is, they do not show any interest in living at the property they are buying, even temporarily, etc.). o o They are interested in large-scale operations (for example, to buy large plots on which to build homes, buying complete buildings or setting up businesses relating to leisure activities, etc.).
• Transactions in which any of the payments are made by a third party, other than the parties involved. Cases where the payment is made by a credit institution registered in the country at the time of signing the property transfer, due to the granting of a mortgage loan, may be excluded. Intermediaries • Transactions performed through intermediaries, when they act on behalf of groups of potentially associated individuals (for example, through family or business ties, shared nationality, persons living at the same address, etc.). • Transactions carried out through intermediaries acting on behalf of groups of potentially affiliated legal persons (for example, through family ties between their owners or representatives, business links, the fact that the legal entity or its owners or representatives are of the same nationality, that the legal entities or their owners or representatives use the same address, that the entities have a common owner, representative or attorney, or in the case of entities with similar names, etc.). • Transactions taking place through intermediaries who are foreign nationals or individuals who are non-resident for tax purposes.
Means of Payment
• Transactions involving payments in cash or in negotiable instruments which do not state the true payer (for example, bank drafts), where the accumulated amount is considered to be significant in relation to the total amount of the transaction. • Transactions in which the party asks for the payment to be divided in to smaller parts with a short interval between them. • Transactions where there are doubts as to the validity of the documents submitted with loan applications. • Transactions in which a loan granted, or an attempt was made to obtain a loan, using cash collateral or where this collateral is deposited abroad. • Transactions in which payment is made in cash, bank notes, bearer cheques or other anonymous instruments, or where payment is made by endorsing a third-party's cheque. • Transactions with funds from countries considered to be tax havens or risk territories, according to anti-money laundering legislation, regardless of whether the customer is resident in the country or territory concerned or not. • Transactions in which the buyer takes on debt which is considered significant in relation to the value of the property. Transactions involving the subrogation of mortgages granted through institutions registered in the country may be excluded. Nature of the Transaction • Transactions in the form of a private contract, where there is no intention to notarise the contract, or where this intention is expressed, it does not finally take place. • Transactions which are not completed in seeming disregard of a contract clause penalising the buyer with loss of the deposit if the sale does not go ahead. • Transactions relating to the same property or rights that follow in rapid succession (for example, purchase and immediate sale of property) and which entail a significant increase or decrease in the price compared with the purchase price. Transactions entered into at a value significantly different (much higher or much lower) from the real value of the property or differing markedly from market values. • Transactions relating to property development in high-risk urban areas, in the judgement of the company (for example, because there is a high percentage of residents of foreign origin, a new urban development plan has been approved, the number of buildings under construction is high relative to the number of inhabitants, etc.). • Recording of the sale of a building plot followed by the recording of the declaration of a completely finished new building at the location at an interval less than the minimum time needed to complete the construction, bearing in mind its characteristics. • Recording of the declaration of a completed new building by a non-resident legal person having no permanent domicile indicating that the construction work was completed at its own expense without any subcontracting or supply of materials. • Transactions relating to property development in high-risk urban areas based on other variables determined by the institution (for example, because there is a high percentage of residents of foreign origin, a new urban development plan has been approved, the number of buildings under construction is high relative to the number of inhabitants, etc.).
Annex 2. Synopsis of the Guidance
Purpose of this Guidance (1) Purpose The purpose of this Guidance is to help Licensed Financial Institutions (LFIs) understand and mitigate risks when providing services to the dealers in precious metals and stones (DPMS) and real estate (RE) sectors, and to guide them in fulfilling their AML/CFT obligations. The FATF's Mutual Evaluation Report of the UAE issued in April 2020 stated that the two sectors are weighted as highly important in terms of risk and materiality in the UAE. Applicability This Guidance applies to all natural and legal persons, which are licensed and/or supervised by the CBUAE, in the following categories: - national banks, branches of foreign banks, exchange houses, finance companies, payment service providers, registered hawala providers and other LFIs; and
- insurance companies, agencies, and brokers.
Understanding and Assessing the Risks of DPMS(2.1) ML/TF Risks of DPMS DPMS present higher risks to LFIs because their services and products are attractive to illicit actors as the trade in precious metals and stones permits illicit actors to move large quantities of value in a liquid, fungible format across borders outside of the traditional financial system. Features of DPMS that Increase Risk Not all DPMS pose equal risk to LFIs. DPMS with the following characteristics may be higher risk: - Operating in jurisdictions with lax or non-existent regulation or that are high risk for crime and terrorism;
- Offer products and services—such as the sale of gold bullion or of uncut stones—that allow customers to access a widely traded, fungible, anonymous form of value; or
- Serve a high-risk customer base, such as a high proportion of PEPs.
Supervision of DPMS in the UAE DPMS in the UAE may qualify as DNFBPs when they carry out any single monetary transaction or several transactions that appear to be interrelated or equal to more than AED 55,000. If so, they are required to apply AML/CFT controls like those used by LFIs. They are supervised by the Ministry of Economy, which has issued guidelines for supervised entities describing their AML/CFT compliance obligations. Understanding and Assessing the Risks of the RE sector (2.2) ML/TF Risks of the RE Sector The RE sector presents a higher risk to LFIs because the sector offers an attractive way for illicit actors, criminals, and corrupt officials to move and store value while hiding their identity. Features of RE Sectors that Increase Risk Not all customers and transactions related to the RE sector (in the UAE or elsewhere) pose equal risk to LFIs. Sectors with the following characteristics may be higher risk: - Weak regulation and/or supervision of real estate brokers and agents;
- Widespread use of cash to purchase real property;
- Lack of transparency on beneficial owners of real estate;
- Openness to foreign purchasers, including 'golden visa' programs; and
- High liquidity and rising prices.
Supervision of the RE Sector in the UAE Real estate agents and brokers qualify as DNFBPs when they conclude operations for the benefit of their customers with respect to the purchase and sale of real estate. When they qualify, they are required to apply AML/CFT controls like those used by LFIs. They are supervised by the Ministry of Economy, which has issued guidelines for supervised entities describing their AML/CFT compliance obligations. Mitigating Risk: Requirements for LFIs (3) Risk-Based Approach LFIs must take a risk-based approach in their AML programs and to individual customers. This means that they should assess all customers, including DPMS and RE sector customers, to determine their degree of risk.
In assessing the risk of a DPMS and RE sector customers, LFIs should consider at least the following factors:
- The jurisdiction(s) in which the customer is based or does business, including both the jurisdictional risk of crime and terrorism but also the regulation in place on the DPMS and real estate sectors;
- The products and services the customer supplies to its customers;
- The customer's customer base;
- The quality of the customer's AML/CFT controls, where they exist.
Customer Due Diligence For all customers, including DPMS and RE Sector customers, LFIs must perform Customer Due Diligence with the following components: Customer Identification: DPMs and RE sector customers will often be businesses, and LFIs should ensure that their customer has the required licenses. Identification of Beneficial Owners: DPMs and RE sector customers will often be legal persons. For all legal person customers, LFIs must identify all individuals who, individually or jointly, have a controlling ownership interest in the legal person of 25% or more. If no individual can be identified, the LFI must identify the individual(s) holding the senior management position(s) within the legal person customer. Understand the Purpose of the Account and the Nature of the Customer's Business: The purpose of the account and the nature of the customer's business are critical drivers of risk for DPMS and RE sector customers. LFIs should fully understand how their customer makes money and what types of transactions it expect to carry out through the LFI's account. As they seek to understand the customer's business, LFIs should collect all information necessary to assess customer risk. Perform Ongoing Monitoring: For all customers, LFIs must ensure that the customer information on file is up to date and accurate, and that the customer's activities are in line with the expectations set at onboarding. If not, the customer risk rating may need to be changed. Special Considerations for RE transactions: Many transactions related to the RE sector will be between persons who are not themselves members of the sector. LFIs should perform due diligence on all transactions that are outside of a customer's normal behavioral profile. If LFIs discover that a transaction is related to the purchase or sale of real estate, it may be necessary to perform additional due diligence. Suspicious Transaction Reporting For customers of all types, LFIs must report any behavior that they reasonably suspect may be linked to money laundering, the financing of terrorism, or a criminal offence. Please consult the CBUAE's Guidance on Suspicious Transaction Reporting for further information. Governance and Training The measures discussed above should be supported by a larger AML/CFT program with effective governance arrangements, including a sufficiently empowered Compliance Officer, and training that educates LFI staff on the risks of these sectors. Guidance for Registered Hawala Providers and Licensed Financial Institutions Providing Services to Registered Hawala Providers
Effective from 15/8/2021Part I: Registered Hawala Providers and Licensed Financial Institutions
1 Introduction
1.1 Purpose
Article 44.11 of the Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations charges Supervisory Authorities with "providing Financial Institutions...with guidelines and feedback to enhance the effectiveness of implementation of the Crime-combatting measures.''
The purpose of this Guidance is to assist the understanding and effective performance by the United Arab Emirates Central Bank's ("CBUAE'') licensed financial institutions ("LFIs'') of their statutory obligations under the legal and regulatory framework in force in the UAE. It should be read in conjunction with the CBUAE's Procedures for Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations (issued by Notice No. 74/2019 dated 19/06/2019) and Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations for Financial Institutions (issued by Notice 79/2019 dated 27/06/2019) and any amendments or updates thereof.1 As such, while this Guidance neither constitutes additional legislation or regulation nor replaces or supersedes any legal or regulatory requirements or statutory obligations, it sets out the expectations of the CBUAE for LFIs to be able to demonstrate compliance with these requirements. In the event of a discrepancy between this Guidance and the legal or regulatory frameworks currently in force, the latter will prevail. This Guidance may be supplemented with additional separate guidance materials, such as outreach sessions and thematic reviews conducted by the CBUAE.
Furthermore, this Guidance takes into account standards and guidance issued by the Financial Action Task Force ("FATF''), industry best practices and red flag indicators. These are not exhaustive and do not set limitations on the measures to be taken by LFIs in order to meet their statutory obligations under the legal and regulatory framework currently in force. As such, LFIs should perform their own assessments of the manner in which they should meet their statutory obligations.
This Guidance comes into effect immediately upon its issuance by the CBUAE with LFIs expected to demonstrate compliance with its requirements within one month from its coming into effect.
1 Available at centralbank.ae/en/cbuae-amlcft.
1.2 Applicability
Unless otherwise noted, this Guidance applies to all natural and legal persons which are licensed and/or supervised by the CBUAE in the following categories:
• Registered Hawala Providers ("RHP''); • National banks, branches of foreign banks; and • Exchange houses.
Key Definitions and AcronymsAML/CFT: Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations.
Beneficial owner: The natural person who owns or exercises effective ultimate control, directly or indirectly, over a client; or the natural person on whose behalf a transaction is being conducted; or the natural person who exercises effective ultimate control over a legal person or legal arrangement.
Beneficiary Hawala Provider: The beneficiary's Hawala Provider, or receiving Hawala Provider, that receives the funds or equivalent value from the Originating Hawala Provider.
CBUAE Regulations: Any resolution, regulation, circular, rule, instruction, standard or notice issued by the CBUAE.
Hawala Activity: The arrangements for transfer and receipt of funds or equivalent value and settlement through trade and cash.
Hawala Provider Certificate: The Certificate issued by the CBUAE for carrying on Hawala activity in the UAE.
Legal person: Any entities other than natural persons that can establish in their own right a permanent customer relationship with a financial institution or otherwise own property. This can include companies, bodies corporate, foundations, partnerships, or associations, along with similar entities.
Money or Value Transfer Service (MVTS): financial services that involve the acceptance of cash, cheques, other monetary instruments or other stores of value and the payment of a corresponding sum in cash or other form to a beneficiary by means of a communication, message, transfer, or through a clearing network to which the MVTS provider belongs.
Originating Hawala Provider: The originator's Hawala Provider, or sending Hawala Provider, that initiates and carries out the transfer of funds or equivalent value to the Beneficiary Hawala Provider.
Registered Hawala Provider: Any natural person holding a valid residency visa or Legal Person, who is registered in the CBUAE's Hawala Providers Register in accordance with the provisions of its Circular No. 24/2019, including its agents or a network of agents.
Registered Hawala Provider Agent: Any natural or legal person carrying out activity outside the UAE on behalf of a Registered Hawala Provider.
1.3 Legal Basis
This Guidance builds upon the provisions of the following laws and regulations:
• Decree Federal Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations (''AML-CFT Law''). • Cabinet Decision No. (10) of 2019 concerning the Implementing Regulation of Decree Federal Law No. 20 of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations ("AML-CFT Decision"). • Cabinet Decision No. (74) of 2020 Regarding Terrorism Lists Regulation and Implementation of United Nations Security Council (UNSC) Resolutions on the Suppression and Combating of Terrorism, Terrorists Financing & Proliferation of Weapons of Mass Destruction, and Related Resolutions ("Cabinet Decision 74"). • Registered Hawala Providers Regulation issued by the CBUAE ("Circular No. 24/2019").
Under Articles 4 and 5 of Circular No. 24/2019, RHP and their customers and agents must strictly abide by all UAE laws, including civil laws, Commercial Companies' Law, federal laws on AML/CFT, and any Regulations and directions issued by the CBUAE ("the legal and regulatory framework in the UAE"). RHP may be guided by the FATF standards on AML/CFT and Proliferation and must abide by guidance issued by the CBUAE in this regard.
1.4 Organization of this Guidance
The FATF's Mutual Evaluation Report of the UAE issued in April 2020 stated that the MVTS sector, including the Hawala service providers, is weighted as highly important in terms of risk and materiality in the UAE. This Guidance is addressed to the i) RHP and ii) LFIs that provide accounts or financial services to RHP. Part I of this Guidance applies to both RHP and LFIs, whereas Part II applies specifically to RHP and Part III specifically to LFIs.
2 Overview of Hawala activity
The FATF defines hawala providers (and other similar service providers) as money transmitters, particularly with ties to specific geographic regions or ethnic communities, that arrange for transfer and receipt of funds or equivalent value and settle through trade, cash, and net settlement over a long period of time. While hawala providers-also known as hawaladars-often use banking channels to settle between them, what makes them distinct from other money transmitters is their use of other settlement methods, including trade, cash, and long-term net settlement.2 Hawala is an activity based on trust and was established to avoid high charges by people who cannot afford them, the ability to reach beneficiaries in remote places quickly where banks do not operate, and the existence of strict currency controls in some countries. Because communication is often by text message and there is no need for funds to clear, hawala transfers may also be available faster than the ones made using the formal financial system. Although hawala providers generally specialize in transferring money between certain jurisdictions, they are also part of larger networks that can arrange transfers to almost any part of the world. Such transfers are likely to be slower and more expensive than transfers within the corridors in which the provider specializes. Although the hawala system minimizes use of the formal financial system, including use of international wires, it is important to note that almost all hawaladars will ultimately seek to conduct transfers, particularly international transfers through LFIs, and possibly to use other financial services. In doing so, they could expose the LFI with which they do business with to the risks of their own business activities and customers.
Common Attributes of Hawala Providers• Fees for funds transfers are less than other channels and funds are available faster. • Operates in communities in which the Hawala Provider is known, visible and accessible to the customers. • Operates in areas with high numbers of expatriates/migrant workers of a specific ethnic group by providing cultural convenience with absence of language barriers, trust among community members, and solidarity among migrants with limited education levels and literacy. • Operates with jurisdictions and regions underserved by other types of financial service providers, such as high-risk areas experiencing wars, civil unrest, conflicts, economic crisis, or weak or non-existent banking systems. • Operates as a hawala provider to facilitate remittance services as a side business to other business activities. • Provides one-off remittance services and communicates with the customer only as much as needed to conduct the transaction. Sample Hawala Transaction:3
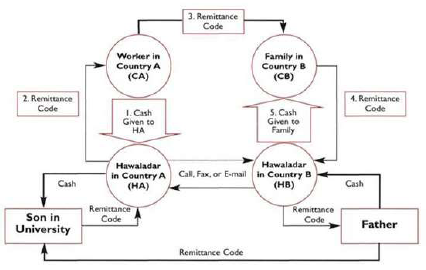
2 See also the FATF report The Role of Hawala and Other Similar Service Providers in ML/TF (fatf-gafi.org)
3 Source: IMF III Features of the Informal Hawala System : Informal Funds Transfer Systems : An Analysis of the Informal Hawala System: (imf.org)3 Global risks of Hawala activity
Hawaladars' business model is built around satisfying customers' needs to move money rapidly across borders, a service that may also be misused by criminals as is to individuals seeking to conduct legitimate personal remittances. In recent years hawala providers have been repeatedly abused to transfer illicit funds, including funds involved in terrorist financing. Certain providers have been found to be fully complicit in these schemes, and even to operate as professional money launderers. In addition, hawala providers generally have the greatest competitive advantage in areas where more formal MVTS providers do not operate or have limited infrastructure, often because these jurisdictions are remote or classified as very high risk. Although this certainly does not mean that every transaction to those areas is illicit, it does suggest that the institutional risk profile of the average hawala provider is likely to be higher than that of other MVTS providers. In many jurisdictions, hawala providers operate underground, because they are providing an illegal service or because they and their customers don't want to be required to comply with rules related to taxes, currency controls, and AML/CFT compliance. This is especially common among hawala providers operating in jurisdictions where hawala is prohibited, unregulated, or illegal.
The inherent risk of hawala providers is influenced primarily by the regulatory environment and illicit finance risks in the jurisdictions in which they do business, the products and services they provide, and their customer base:
1. Regulatory Environment
The regulatory environment for hawala providers clearly varies across jurisdictions. In some jurisdictions, they are not able to maintain a license or registration and therefore operate entirely underground. While operating underground is generally prohibited under the laws of the country where the hawala provider operates, it does not necessarily mean that a provider is a money launderer. Still, underground providers will seek to conceal their activities from financial institutions, and are extremely unlikely to comply with any AML/CFT obligations. Such entities may present themselves to LFIs as "general trading companies'' or describe other business types that can justify regular international transfers, including dealing in precious metals or stones, trading in used cars, or in high value carpets.
Even in jurisdictions where hawala is legal and regulated such as the UAE, hawala providers may have only a basic understanding of their financial crime risks and obligations, and may not use systems and technologies that support compliance with those obligations. Furthermore, because hawaladars may lack strong AML/CFT preventive measures, they may be sought out by customers specifically hoping to take advantage of this possible weakness. As a result, hawala providers are almost always found to be classified as very high-risk customers by banks. A hawala provider can strive to manage this risk by applying strong, targeted controls and maintaining an effective AML/CFT program that meets or exceeds UAE requirements and global standards (see Part II section 3 below).
2. Geography
Hawala providers, like all financial institutions, are heavily exposed to the risks prevalent in the geographies where they operate. The risk of a hawala provider, therefore, will depend in part on the illicit finance risks--including ML/TF and sanctions evasion--in the jurisdictions where it is established or has subsidiaries. In addition, a provider's risk will also be impacted by the jurisdictions with which it most frequently does business. For example, the risk of a hawaladar operating in the UAE and primarily executing transfers to and from Country X should be assessed based on the illicit finance risk in both the UAE and Country X.
3. Products, Services, and Delivery Channels
Hawala providers, by definition, all provide money or value transfer services using hawala networks, which is subject to higher risks. The risk of hawala transactions may be increased or decreased by the size and purpose of the transaction. Some hawaladars only carry out low-value personal remittances, while others service businesses by supporting commercial operations, which may involve relatively high-value transactions. Low-value personal remittances may be considered lower-risk, although low-value remittances to jurisdictions at high-risk for terrorist financing should be treated as equally high risk. RHP in the UAE may perform only limited services (listed in section 4.1 below), but hawala providers established elsewhere may not have such restrictions on their activity.
The risk involved in providing the hawala service is further impacted by the delivery channels through which it is offered. Channels that promote anonymity (accepting transaction orders by text or telephone; accepting cash; allowing agents or third parties to order transactions on behalf of the originator) increase the risk of the service. Some international law enforcement agencies have reported cases of hawala providers operating in virtual currencies; although still rare, such a delivery channel would be extremely high risk, as it would combine the general risks of hawala providers with those of virtual currencies, which offer illicit actors anonymity and access to a practically unregulated financial sector.
In addition, hawala services may not be the only financial product hawala providers offer. In many jurisdictions providers also offer small loans (often with pawned items as security) and sell stored value cards, or provide safekeeping services for cash. They may also engage in non-financial lines of business such as selling calling cards, mobile phones and SIM cards. All of these lines of business are cash intensive4 and high-risk, and are generally not subject to AML/CFT controls. Even in a jurisdiction where hawala providers are regulated, they may commingle cash proceeds of these other services with hawala funds. This means that a hawala provider with an account at an LFI could use that account to support all aspects of its business, not simply provision of hawala services.
4. Customer Base
Most hawala providers are likely to serve a customer base made up of lower-income individuals seeking to conduct or receive fairly low-value transfers. Such a customer base is not necessarily low-risk, especially when customers have ties to jurisdictions that are at high risk for terrorist financing. The risk of the provider's customer base, however, will be further increased if the provider conducts larger transfers on behalf of business entities (e.g. trade-based transactions), if it has a high proportion of legal person customers, or if its customers include politically exposed persons.
4 The CBUAE will issue Guidance for LFIs providing services to Cash Intensive Businesses.
4 Regulation and Supervision of RHP in the UAE
The CBUAE permits legitimate Hawala Activity as an important element of its continuous efforts to support financial inclusion and bring the unbanked population into the regulated financial system. To this end, Hawala is regulated by the Registered Hawala Providers Regulation issued by the CBUAE (``Circular No. 24/2019''). As per its articles 2.1 and 7.1 and Article 26 of the AML-CFT Decision, all providers carrying on Hawala Activity in the UAE must hold a Hawala Provider Certificate issued by the CBUAE; it is not permitted to carry on Hawala Activity without being registered with the CBUAE. RHP are supervised by the CBUAE, who has the right to examine the business of RHP and their agents and customers whenever it deems appropriate to ensure proper compliance with their statutory obligations under the legal and regulatory framework in the UAE, or impose supervisory action or administrative and financial sanctions for violations. Similar to its all LFIs, the CBUAE applies the principle of proportionality in its supervision and enforcement process, whereby small RHP may demonstrate to the CBUAE that the objectives are met without necessarily addressing all of the specifics cited in the legal and regulatory framework in the UAE.
4.1 Permitted and non-permitted services by RHP
RHP are only permitted to provide well-defined services, which include non-commercial personal remittances and money transfer services to support commercial operations (such as trade transactions with jurisdictional corridors serviced by the hawala community).
RHP are not permitted to engage in any of the following transactions:
• Take deposits, exchange currencies or sell and purchase travellers' cheques; • Provide any financial services other than money transfers (e.g. exchange of virtual assets/cryptocurrencies, loans, purchase of debts); or • Execute transactions involving or on behalf of any other hawala provider in the UAE (as they are required by Circular No. 24/2019 to manage their business personally and never assign such task to another person, also known as "nesting''). This excludes the agents of the RHP in a foreign country (see also Part II section 3.3.5 below).
Part II: Guidance for RHP
1 Sanctions Obligations and Freezing Without Delay
Targeted Financial Sanctions (TFS) are legal restrictions on financial activity imposed by the United Nations Security Council (UNSC) or the UAE. An individual or legal person subject to TFS cannot send or receive money, or engage in any other kind of financial activity, without specific permission from the government of the UAE. The names of individuals or legal persons that are subject to TFS are included in lists published by the UN and the UAE (also known as "listed persons'' or "sanctioned persons.'')
RHP are required to fully comply with the obligation to implement all necessary measures without delay as described in the Cabinet Decision No. (74) of 2020, the ''Guidance on TFS for FIs and Designated Non-Financial Business and Professions (DNFBPs)'' issued by the Executive Office of the Committee for Goods & Material Subject to Import and Export Control (''Executive Office''), the ''Guidance for LFIs on the implementation of TFS'' issued by the CBUAE, the CBUAE Notice No. 3895/2021, and any of their amendments or updates thereof.5 RHP should be aware that it is a crime in the UAE to provide funds or financial services, including money transmissions services, to a person subject to TFS. This means that if a person is subject to TFS, the RHP cannot do any of the following:
• Send that person money on behalf of a customer, no matter where in the world they are; • Provide that person with money that another person has sent them; or • Carry out a transaction of any kind for that person.
Appropriate implementation of TFS has four key steps, which RHP must follow to ensure they are compliant:
1. Maintain awareness of UNSC and UAE sanctions lists, and rapidly become informed of changes to these lists.
RHP should rely on the official website of the UNSC for the most updated UN Consolidated List:
• un.org/securitycouncil/content/un-sc-consolidated-list
RHP should rely on the official website of the Executive Office to obtain the most recent publication of the UAE sanctions List (Local Terrorist List) List issued by the UAE Cabinet:
• uaeiec.gov.ae/en-us/un-page • uaeiec.gov.ae/ar-ae/un-page
In addition, under Article 21 of Cabinet Decision 74, RHP must register on the Executive Office's website in order to receive automated email notifications with updated and timely information about the listing and de-listing of individuals or entities in the Local Terrorist List and in the UN Consolidated List.
2. Check the names of customers against the lists of sanctioned persons.
Every time an RHP carries out a transaction, it must check before it sends or receives any money to make sure its customer, counterparty, or anyone else involved in the transaction is not listed on the UN or UAE sanctions lists. This process is known as 'screening process.' The RHP must screen the customer and the person to or from whom the customer is sending or receiving money. Where the customer is a legal person, it must screen the customer's beneficial owners (see section 3.3.3 below) and senior managing official. The RHP must also screen its counterparty who is executing the transaction at the other end. The result of the screening process can have the following results:
• A ''confirmed match''; i.e. a customer or a customer's counterparty has the same full name as a sanctioned person; or • A ''potential match''; i.e. a customer or a customer's counterparty has a similar or partially matching name as a sanctioned person; in those cases, the RHP should use additional information, such as the person's date of birth, address, and nationality, to distinguish the two persons.
In addition, every time there is a change to the sanctions lists, the RHP must compare the newly listed persons against its list of past customers. If an RHP finds that it previously carried out a transaction involving a person who was not listed at the time but is now listed, it has not done anything wrong. But it must report the transaction so that the authorities are aware (see step 4 below).
3. Immediately freeze any funds in the possession or under the control of the RHP that may belong to a listed person and cancel (where possible) any transactions involving a listed person.
When a ''confirmed match'' is found through the screening process, RHP must immediately, without delay and without prior notice, freeze all funds.
i. ''Freeze all funds'' means that you must hold the funds. You cannot send them or give them to anyone except to a UAE authority. You cannot return them to the person who gave them to you. If the funds are cash, you should place the funds in a safe place, separate from other funds, until the authorities can collect them. If the funds are held in a financial institution, such as a bank, you should notify the financial institution, who will place them in a special account. If an RHP has recently completed a transaction that involves a listed person, the RHP should notify its counterparty so that they can freeze the funds at the other end if possible. It must keep records of the information that it used to confirm this. ii. ''Without delay'' means within 24 hours of the listing decision being issued by the UNSC, the Sanctions Committee or the UAE Cabinet, as the case may be. This means that you must take active efforts to become aware of changes to the sanctions lists by registering on the Executive Office's website in order to receive automated email notifications, and that once a change has been made, you must immediately put it into effect by refusing to carry out any transactions for or with a listed person. iii. ''Without prior notice'' means that you must not tell the customer, or the person whose funds are being frozen, what the RHP is going to do.
When a ''potential match'' is found through the screening process, the RHP must suspend without delay any transaction and refrain from offering any funds or services. It must keep records of the information that it used to confirm this.
4. Report any listed persons and the actions the RHP has taken to the appropriate authorities
With regards to LFIs obligation for TFS reporting, the CBUAE in coordination with the Executive Office, has established a unified mechanism to report TFS obligations utilizing the UAE Financial Intelligence Unit's (FIU) online reporting platform (goAML).
In case of any ''confirmed match'' to a listing of names of individuals or legal persons to the Local Terrorist List and the UN Consolidated List, the RHP are required to report any freezing measures, prohibition to provide funds or services or any attempted transactions via the goAML platform within two business days by selecting the Fund Freeze Report (FFR). The RHP must also ensure all the necessary information and documents are submitted.
In case of any ''potential match'' to a listing of names of individuals or legal persons to the Local Terrorist List or UN Consolidated List, the RHP are required to report the potential match via the goAML Platform by selecting the Partial Name Match Report (PMNR). The RHP must also ensure all the necessary information and documents are submitted. In addition, the RHP must uphold suspension measures related to the ''potential match'' until further instructions are received via the goAML Platform on whether to cancel the suspension or implement freezing measures.
The TFS related reports (FFR or PMNR) submitted via the goAML Platform will be received simultaneously by the CBUAE and the Executive Office. RHP should also consult the CBUAE's6 and the Executive Office's7 websites respectively as updated from time to time.
5 Available at centralbank.ae/en/cbuae-amlcft.
6 Available at: centralbank.ae/en/cbuae-amlcft
7 Available at: uaeiec.gov.ae/en-us/un-page2 Registration and other Requirements
2.1 Registration
Under Article 2 of Circular No. 24/2019, a resident natural person or legal person may not carry on Hawala Activity in the UAE unless the applicant holds a Hawala Provider Certificate issued by the CBUAE and registered in the CBUAE Hawala Providers Register. Any resident natural person or legal person may apply for registration and obtain a Hawala Provider Certificate from the CBUAE. The applicant should not be of UAE nationality, should be legally competent, and officially residing in the UAE. The said application shall be made on the CBUAE's prescribed forms on the CBUAE's website.8
8 Available at centralbank.ae/en/cbuae-amlcft.
2.2 CBUAE Notification of Approval/Rejection
Under Article 3 of Circular No. 24/2019, the CBUAE may agree or decline an application for a Hawala Provider Certificate. In case of approval, the CBUAE shall issue a Hawala Provider Certificate valid for one year, renewable for similar periods. The CBUAE shall notify the applicant in writing, and may include in the Hawala Provider Certificate whatever terms and conditions it deems appropriate. In case of rejection, the CBUAE shall notify the applicant in writing indicating reasons for rejection.
2.3 Re-Registration
Under Articles 2 and 4 of Circular No. 24/2019, RHP should submit to the CBUAE an application for renewal of the Hawala Provider Certificate within a period of not less than two months from the date of expiry of the original certificate or any renewals thereof. The said application should be made on the CBUAE's prescribed form titled ''Application to Re-register Hawala Providers'' on the CBUAE's website.
2.4 Requirements for Trade License, Security and Reporting Systems
As per Article 2 of Circular No. 24/2019 and the respective application requirements, RHP must complete the following requirements within 90 days from the date mentioned in the final registration certificate as well as submit proof of completion to the Licensing Division of the CBUAE:
• Add Hawala Activity to the commercial trade license. • Install security systems; i.e. CCTV and police connections. • Register in the relevant Services Access Control Manager (SACM) and subsequently to the UAE FIU's goAML portal by following the steps in the registration guides issued by the FIU previously sent to RHP. Registration on SACM is a prerequisite for goAML registration; • Register in the relevant SACM and subsequently to the CBUAE's Remittance Reporting System (RRS) for the daily reporting and Integrated Regulatory Reporting System (IRR) for the quarterly reporting (see Part II section 4 below). Registration in SACM is a prerequisite for RRS & IRR registration. In order to register in SACM, RHP will be required to provide the following information to the CBUAE via e-mail on hawala@cbuae.gov.ae: • Trade name of the RHP; • First and last name of the user; • Emirates ID number and copy of Emirates ID; • Email address; and • Mobile phone number. • RHP should register for the Integrated Enquiries Management System (IEMS) by referring to the IEMS User Guide available at the relevant link in FIU's website.9
Failure to submit the above within the specified period may result in a registration certificate withdrawal.
9 Available at: uaefiu.gov.ae.
2.5 Requirement for a Bank Account
As per Article 2 of Circular No. 24/2019 the RHP must maintain an account with a bank operating in the UAE to be used for settlement and provide the CBUAE with details of such account. In addition, they should inform their account manager at the bank of their intention to use the account to carry out Hawala Activity.
3 AML/CFT Program
As per Articles 4, 20, 21 and 26 of the AML-CFT Decision, RHP are required to establish and maintain effective AML/CFT compliance programs designed to prevent them from being misused to facilitate money laundering or terrorist financing (ML/TF). The program must be risk-based and appropriate to the risk of the RHP, taking into consideration its:
• Size; • Volume of transactions; • Types of remittances offered (personal only or personal and commercial); • Complexity; • The nature and volume of its Hawala Activity; • The nature of its customer base; and • The geographic areas in which it operates.
This means that where an RHP engages in higher-risk activities (as discussed below in section 3.2), or does a higher volume of business, it must have a more sophisticated AML/CFT program and employ more intensive measures to manage this risk. The section that follows discusses the mandatory minimum elements of an AML/CFT program under the legal and regulatory framework in the UAE as well as ways that RHP can make adjustments to respond to their risk. It is divided into four parts, as follows:
1. The AML/CFT Program and the Compliance Officer. This part discusses the content of the AML/CFT program and how it should be implemented by the RHP. 2. Understanding Risks. This section discusses how to identify the RHP's ML/TF risks so that the RHP can build an appropriate AML/CFT program. 3. Customer Due Diligence. This section discusses the mandatory procedures for identifying and understanding the RHP's customers and counterparties. 4. Record Keeping. This section discusses the records of activity that the RHP must maintain and provide to law enforcement authorities and counterparties.
3.1 The AML/CFT Program and the Compliance Officer
As per Article 21 of the AML-CFT Decision, each RHP must have a specific person, the Compliance Officer, who is responsible for day-to-day compliance with the legal and regulatory framework in the UAE and the management of the AML/CFT program. This person must be an employee, manager, or owner of the RHP. In large RHP, with multiple employees and substantial revenues from Hawala Activity, the CBUAE expects that the Compliance Officer will be a full-time position without any other responsibilities for managing the business. In small RHP, however, the CBUAE recognizes that the Compliance Officer is likely to have other responsibilities beyond management of the compliance program. If the RHP is owned and operated by a single person, that person will be the Compliance Officer.
The Compliance Officer is responsible for the following:
• Ensure full compliance with the legal and regulatory framework in the UAE and this Guidance. • Making sure that other employees of the RHP (where relevant) comply with the legal and regulatory framework in the UAE and this Guidance, and abide by the RHP's own policies and procedures; and • Implementing the compliance program elements described in this Guidance, including conducting the risk assessment.
The RHP's AML/CFT compliance program must include all the measures discussed in the following sections as well as the following components:
• Provide education and training to appropriate personnel. RHP employees who participate in Hawala Activity must be trained to understand how to comply with the legal and regulatory framework in the UAE and this Guidance, and abide by the RHP's policies and procedures. It is not acceptable for an untrained employee to have responsibility for collecting or disbursing customer funds and initiating transactions. • Conduct a periodic audit of the AML/CFT program. RHP are required to arrange for a regular independent audit of their program by hiring an external qualified independent auditor approved by the CBUAE. Small RHP should be audited once every two or three years, while large RHP once every year. It is important to note that the audit must be independent; i.e. an RHP may not audit itself.
3.2 Understanding Risks
According to Article 16 of the AML-CFT Law and Article 4 of the AML-CFT Decision, RHP must identify, assess and understand the ML/TF risks to which they are exposed, and how they may be affected by those risks, in order to determine the nature and extent of AML/CFT resources necessary to mitigate and manage those risks. The sophistication of an RHP's risk assessment process depends on the RHP's size and operations. A large RHP is expected to produce an extensive risk assessment that complies fully with the standards outlined in the Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations for Financial Institutions (issued by Notice 79/2019 dated 27/06/2019) and any amendments or updates thereof. This assessment may be done by an external consultant, but the RHP retains ultimate responsibility for its content and its compliance with the standard set in the Guidelines. The CBUAE recognizes, however, that a small RHP has limited services and resources. RHP of this type can follow the risk assessment process discussed below. All RHP must document their risk assessment, even if it is in the form of notes, to demonstrate that they have thoughtfully completed this process. They must be able to understand their findings and explain them if called upon to the CBUAE.
The Compliance Officer should begin the risk assessment process by carefully reading and understanding Parts I and II of this Guidance, which contain essential information about the risks faced by an RHP. The Compliance Officer should then consider the RHP's risk in the following risk categories. The discussion below does not cover every factor that increases or decreases risk and RHP should consider any other factors based on their knowledge and experience.
1. Customer Risk. This is the risk that your customers may be involved in ML/TF. By receiving money from a customer who is involved in illegal activities, the RHP itself can unwittingly become involved in those activities. Some examples of questions that RHP can use to assess customer risk include:
a. Are my customers mostly individuals, or do I have many customers that are legal persons? When you provide services to a company, you don't always know who you're really dealing with. So having many legal person customers may increase your risk.
b. Are my customers only sending remittances to family, or are they engaging in business? Business activities are generally considered to be higher risk for ML/TF because amounts are higher and it's harder for the RHP to understand the true purpose of the transaction.
2. Geographic Risk. Some countries are high risk for illicit activity, whether because they have a high volume of crime and terrorism, or because their financial sector doesn't have controls to prevent the movement of illicit funds. If an RHP operates in those countries, either because it has agents there or because it frequently sends or receives money there, then it is exposed to that risk. Questions an RHP can ask to assess its geographic risk include:
a. Do I regularly do business in or with countries that have an ongoing insurgency? Where terrorist attacks are frequent? These countries will be very high risk.
b. Do I regularly do business in or with countries listed on the FATF list of monitored jurisdictions?10
3. Products and Services Risk. RHP are permitted to offer only limited products and services (see Part I section 4.1 above). Within the group of permitted products, transfers connected to commercial activity are generally considered to be higher risk than those connected to personal remittances.
4. Delivery Channel Risk. The way an RHP delivers its products and services will also impact its risk, because some delivery channels make it difficult to understand and observe the customer. For example, if an RHP accepts orders for remittances via text message or phone call, or allows customers to initiate a transaction by giving money to an associate, who then delivers it to the RHP, this will make their activities higher risk.
Based on the considerations above, RHP should give themselves an overall score of Low, Medium, or High risk. RHP should complete the risk assessment process at least once a year. RHP should understand their risk assessment, its findings, and what it means for their business. They should consider their risk assessment when designing and implementing their AML/CFT program. Where they assess themselves as higher risk, they should take additional precautions.
10 The FATF list can be found at fatf-gafi.org/publications/high-risk-and-other-monitored-jurisdictions/?hf=10&b=0&s=desc(fatf_releasedate).
3.3 Customer Due Diligence
Customer due diligence (''CDD'') is the process by which an RHP identifies and understands its customer. CDD is required by Article 5 of the AML-CFT Decision and is essential to protecting the RHP from abuse, and to deterring and detecting ML/TF schemes. In specific cases outlined below, and whenever the RHP believes that higher risks are present, the RHP must perform Enhanced Due Diligence (''EDD''). EDD involves more intensive measures to discover information about the customer.
The RHP must perform Customer Identification Diligence (''CID''), CDD or EDD prior to conducting each and every transaction, even if the customer is a repeat customer (see sections 3.3.1 to 3.3.4 below for their details). An RHP must not conduct a transaction if the appropriate diligence has not been performed or completed.
When to Use CID, CDD and EDD Transaction What is Required A natural person sends or receives a transfer between AED 1 and AED 3,499 CID, unless higher risks are present, in which case CDD & EDD as well. A natural person sends or receives a transfer of between AED 3,500 to AED.54,999 CDD, unless higher risks are present, in which case EDD as well. A natural person sends or receives a transfer of AED 55,000 or greater. CDD and EDD A natural person from a high-risk jurisdiction sends or receives a transfer of any value. CDD and EDD A natural person who is a politically exposed person sends or receives a transfer of any value. CDD and EDD A legal person sends or receives a transfer of any value. CDD and EDD 3.3.1 Customer Identification Diligence
The CID process must be applied for a natural person who sends or receives a transfer between AED 1 and AED 3,499. The CID process is the verification of the original identification documents of the customer who is a natural person and the systematic recording of basic customer information in the point of sale system without the need to retain copies of the identification documents. The customer's full name, address, mobile number, nationality, date of birth, ID type (Emirates ID, or passport number when Emirates ID is not available) and ID number must be recorded in the point of sale system and printed on receipts.
3.3.2 Customer Due Diligence for Natural Persons
Article 4 of Circular No. 24/2019 requires RHP to identify and verify the identity of their customers, including remitters and beneficiaries, by using Emirates ID, or passport when Emirates ID is not available. RHP must collect at least the following information for each customer:
• Name, • Emirates ID number or passport number when Emirates ID is not available; • Date of birth and nationality; • Address; • Mobile number; • Occupation; and • The name of the person from whom the customer is receiving money, or the person to whom the customer is sending money and their country.
This information must be printed on customer receipts. RHP must record this information and store it in their files for five years. RHP must also take a clear photo or photocopy of the customer's identification document and retain it for five years.
The CDD process should also be applied when it appears that a natural person may be deliberately splitting up a larger transfer to evade the CDD requirement (for example by repeatedly once in a week transfer value below AED 3,500 per transaction).
Using this information, as discussed in Part II section 1 above on sanctions obligations, RHP should screen their customers, including the sender/beneficiary as appropriate, and the transaction against the UN Consolidated List and the Local UAE Terrorist List. Screening must be performed before carrying out any transaction for the customer. If there is a match, the RHP should carefully consider whether the other data collected (date of birth, country of birth) match the information available for the listed person in question. The RHP may continue with the transaction only if it is confident that its customer or the person on the other end of the transaction is not a listed person. In addition, if the RHP discovers that any party to the transaction is listed on the UN Consolidated List and the Local Terrorist List, it must not return the customer's funds or provide the customer with funds that have been sent to him, but must instead freeze the funds.
Furthemore, RHP should obtain a clear understanding of the intended purpose and nature of the transaction and ensure that it does not breach the permitted services by RHP listed in Part I section 4 above. RHP should consider whether it is consistent with what they know about the customer. Some examples of transactions that may require further investigation include:
• A customer who says he works as a labourer wishes to transfer a sum that is greater than the average yearly income for someone in his position.
• A customer visits the RHP on a regular basis and makes small or moderate-sized transfers, but the sum of the amounts he transfers over the course of the year is greater than the yearly income for someone in his position.
• A customer says that he has no occupation, but continues to make transfers or transfers a large sum.
• A customer who is from country A states that he is sending funds to a family member, but the beneficiary is located in country B.
• A customer from country A makes regular transfers to people he says are family members in that country, but they appear to live in different regions of country A and their relationship to the customer is not clear.
These transactions are not necessarily illicit, but they suggest that the RHP needs to collect additional information. For example, a customer may actually be acting on behalf of a business. In that case, the RHP's customer is actually the business, and it must perform CDD on the business as described in section 3.3.3 below. If the RHP has any additional concerns, it should follow the EDD procedures discussed in section 3.3.4 below.
RHP must cease and reject any transaction if they cannot collect any of the information required above, or if they cannot comply with any of the above requirements.
3.3.3 Customer Due Diligence for Legal Persons
When a legal person like a company uses an RHP to conduct a transaction, the RHP's customer is the company itself, not the individual representing the company. A legal person conducts a transaction when the funds involved belong to the legal person, and when the transaction is made as part of carrying out the legal person's business. If the customer is a legal person, it must be registered and based in the UAE to carry out transactions through a RHP. Legal persons such as companies, bodies corporate, foundations, partnerships, or associations, along with similar entities do not have bio-data like individuals and can transact under their own names while being controlled by other individuals. This means that they require specific CDD procedures. As per Articles 8 and 9 of the AML-CFT Decision RHP must perform the following actions for a legal person customer:
1. Collecting and recording the following information about the legal person customer: a. The legal person's name; b. The legal person's legal form (e.g., limited liability company); c. The address of the legal person's main office or headquarters; d. The legal person's trade license; and e. The name of the legal person's senior managing official. 2. Conducting CDD as described in section 3.3.2 above on the individual representing the customer (the individual who is directly ordering the transaction). 3. Determining that the representative is authorized to conduct the transaction via a valid authorization, such as the trade license and/or a letter from the legal person customer's management on its letterhead. 4. Identifying and verifying the identity of the customer's beneficial owners. a. Beneficial owners are the individuals who own and control the legal person. In many cases, the managing director or other similar top official will also be the beneficial owner, but not always. b. RHP must identify every individual who owns 25% or more of the legal person customer. They must collect their names, and then perform CDD on them as required by section 3.3.2 above. c. RHP can collect the names of beneficial owners, and thus determine who to perform CDD on, by asking the customer's representative. If they are concerned about the information provided by the representative, they should ask for documentation to prove ownership. d. If no individual owns 25% of the legal person customer, RHP must identify, and conduct CDD on the individual who is the customer's senior managing official. e. Beneficial owners cannot be other legal persons. If a legal person customer is owned by other legal persons, the RHP must understand their ownership as well until it identifies all individuals owning at least 25% of its customer. 5. Understanding the customer's ownership and control structure. The RHP must understand who owns the customer, who exercises control over it and how. 6. Understanding the nature of the customer business. The RHP must understand what sort of business the customer engages in and how the customer makes its money. If the customer's business doesn't make sense, or if the customer has no apparent business activities, that calls into question whether the funds involved in the transaction actually came from legitimate business activities. • Conducting sanctions screening on all related parties. The RHP must at least screen the following names against sanctions lists: a. The name of the legal person customer; b. The name of the customer's representative; c. The name of the beneficial owner(s); d. The name of the customer's senior managing official; and e. The customer's address.
As with CDD for natural persons, RHP must take a clear, readable photo or photocopy of documents obtained from the customer during CDD, and must retain those documents for five years after the transaction.
3.3.4 Enhanced Due Diligence
Sometimes CDD alone as described above is not sufficient to fully understand a customer. In addition, for certain customers, an extra level of due diligence is required. In those cases, the RHP must perform EDD in the following circumstances:
1. The customer is a legal person. In these cases, the RHP must perform all the steps listed in section 3.3.3 above, plus additional due diligence as described here.
2. The customer is a natural person carrying out a transfer worth AED 55,000 or above. In those cases, the RHP must perform all the steps listed in section 3.3.2 above, plus additional due diligence as described in this section below.
3. The customer is a politically exposed person. During CDD, the RHP must collect information regarding the occupation of a natural person customer, and the beneficial owners of a legal person customer. If the customer, or the beneficial owners of a legal person customer, indicates that he or she is a government official with any government, the RHP must ask additional questions to understand that individual's rank and status. If the individual holds a high-ranking position in any government, then EDD is required for the customer. This is to make sure that the funds involved are not related to corruption or abuse of the customer's position.
4. The customer is from, or is sending a remittance to, a high-risk jurisdiction. As discussed in section 3.2 above, high-risk jurisdictions are those with a higher risk of ML/TF.
RHP should consider performing EDD when there are other high risks associated with the transaction, such as concerns about the customer's behaviour or about the source of the funds involved in the transaction.
When performing EDD, RHP must follow the following mandatory steps:
• Seek approval from the manager of the RHP to carry out the transaction. If the RHP is owned and operated by a single person, this step is not necessary. • Collect additional information to understand the source of funds involved in the transaction and the customer's overall source of funds (i.e. source of wealth). For instance, the RHP may ask for a pay slip to verify the customer's income. • Collect additional information about the customer's business. For example, if a transaction is linked to the sale of goods, the RHP may request to see the invoice.
3.3.5 Agent Due Diligence
RHP may use agents in a foreign country to carry out activity on their behalf in that foreign country. This generally entails the corresponding agent in the foreign country executing payments on instructions from the RHP, or the agent sending instructions to the RHP to execute payments domestically. It should be noted that RHP are not permitted to use agents to carry out activity on their behalf in the UAE (as they are required by Circular No. 24/2019 to manage their business personally and never assign such task to another person, also known as ''nesting''.)
RHP are exposed to risks when their agents engage in transactions that create risks for ML or TF. RHP must identify and assess the ML/TF risks they may be exposed to from the use of agents to provide activity on their behalf in a foreign country. RHP should ensure that they understand who their agents are, and that they are not breaching any applicable AML/CFT laws and regulations. In order to reduce their exposure to ML/TF risks, RHP are required to perform appropriate due diligence on their agents, to ensure they thoroughly know their agents and monitor their transactions to ensure that they are legitimate. The required elements of due diligence on agents are as follows:
• When entering into a business relationship with an agent, as a first step, the RHP should identify and verify the identity of the agent, using reliable, independent source documents, data or information. • RHP should also identify and take reasonable measures to verify the identity of the beneficial owner(s) and understand the ownership and control structure of the agent, such that the RHP is satisfied that it knows the beneficial owner(s) and that the agent is not a shell bank. • RHP should gather sufficient information to understand the purpose and intended nature of the business relationship, which includes understanding what types of customers the agent intends to service through the business relationship, how it will offer services, the transaction volume and value, and the extent to which any of these are assessed as high risk. • RHP should also gather sufficient information and determine from publicly available information the reputation of the agent, including whether it has been subject to a ML/TF investigation or regulatory action. In addition, RHP should ensure that the agent has proper AML/CFT controls. • RHP should conduct ongoing due diligence of the business relationship, including periodical reviews of the CDD information on the agent, and ongoing monitoring to detect any changes in the agents' activity pattern that may indicate unusual activity.
RHP should keep up-to-date agent lists and retain them for a period of five years. RHP must provide the CBUAE current lists of their agents and the countries in which they operate. In addition, RHP should make current lists of their agents available to the relevant authorities within the country in which they operate. RHP should ensure that their agents fully adhere to the procedures of record keeping as described in this Guidance and that they make those records available to the RHP immediately upon request.
3.4 Record Keeping
Under Article 16 of AML-CFT Law and Article 24 of the AML-CFT Decision, RHP, as remittance providers, have very important obligations relating to the records they maintain about the remittances they execute.
3.4.1 Record Keeping Related to Remittances
1. Sending a Remittance
When the RHP's customer is the person originating a transaction, the RHP must collect the following information through the CID and CDD process:
• The sending customer's name; • His or her Emirates ID, or passport number when Emirates ID is not available; • His or her date and nationality; • His or her address; • Mobile number; • Occupation; and • The name of the beneficiary of the transaction and the country it is sent to.
The RHP must assign the transaction a unique ID number that allows the RHP to quickly identify and track the transaction. The RHP must provide all of this information to the hawala provider at the other end of the transaction and keep the relevant record. The RHP must not carry out the transaction if it has not supplied this information.
2. Receiving a Remittance
When the RHP's customer is the person receiving the remittance, the RHP must conduct CDD on the beneficiary and make sure that its customer's information matches that of the beneficiary identified in the information provided by the Originating Hawala Provider and keep the relevant record. The information must include:
• The receiving customer's name; • His or her Emirates ID, or passport number when Emirates ID is not available; • His or her date and nationality; • His or her address; • Mobile number; • Occupation; and • The name of the sender of the transaction and the country it is sent from.
The RHP's partners and agents outside the UAE should comply with the requirements under ``Sending a Remittance'' above even though they are not subject to UAE laws. If a RHP receives a transaction order from a hawala provider outside the UAE that does not contain the information required under ``Sending a Remittance'' above, it cannot perform required sanctions screening or identify whether the transaction is suspicious and needs to be reported to the FIU. Therefore, the RHP should require its agent or counterpart to provide the information listed before it releases the funds to the beneficiary.
3.4.2 Other Types of Record Keeping
According to the AML-CFT Law and the AML-CFT Decision, RHP must keep all records obtained through the CDD process; copies of personal identification documents provided during CDD; and copies of Suspicious Transaction Reports (STR) filed with the FIU. Under Article 4 of Circular No. 24/2019, RHP are required to have forms in which the customers fills in the necessary information to originate the transaction; RHP must retain these forms as well.
RHP must also maintain records of transactions. These records must be sufficiently detailed to allow authorities to reconstruct and understand the transaction. They must at least include the names of the sender and beneficiary, the date of the transaction, and the amount of the transaction, and be organized in such a way so that the RHP and authorities can easily find the records they need for a specific transaction.
RHP must make the records described here, or any other records, available to the competent authorities immediately upon request. All the records described in this section must be kept for at least five (5) years, from the date of completion of the transaction, or for longer if directed by the CBUAE or other authority.
4 Reporting Obligations
4.1 Daily Reporting
Under Article 4 of Circular No. 24/2019, RHP are required on a daily basis to upload electronically to the CBUAE, via its Remittance Reporting System ("RRS") and/or other applicable system, the data and details of all transfers, remitters and beneficiaries as per the forms prepared by the CBUAE for this purpose.
4.2 Quarterly Settlement Statements
Under Article 4 of Circular No. 24/2019, RHP should submit to the CBUAE statements of their settlement accounts on a quarterly basis along with other required forms, as well as provide the CBUAE with any data, information, or statistics it may require at any time and for any specific period.
4.3 Reporting Suspicious Transactions and Registration to GoAML
RHP must monitor transactions that they carry out to identify those that may be suspicious and where a Suspicious Transaction Report (``STR''), or suspicious activity report ("SAR") or other report types may need to be filed with the FIU. Monitoring begins at the CDD stage, but does not end there. RHP must keep records of customer activity so that they can examine it to identify patterns over time that may be cause concern. RHP must take into account all information available, including regarding the originator and beneficiary(ies) of a transaction, in order to determine whether an STR is to be filed.
Situations in which it may be necessary to file an STR/ SAR include:
• A customer begins the CDD process, but cancels the transaction and leaves when he discovers the information that the RHP is required to collect.
• The RHP completes CDD on a customer, but still has doubts as to whether the transaction was legitimate or whether the customer's stated reason for the transaction was the true one.
• A customer carries out transactions larger than his stated income without providing a valid justification.
• A natural person customer regularly orders transactions just below the AED 55,000 threshold for when EDD is required (i.e. either tied to the threshold or if there are other risk factors that may trigger EDD).
• Multiple customers send money to, or receive money from, the same person, and there is no clear connection between the customers.
• The RHP suspects that a customer is carrying out transactions that are disallowed under Part I, section 4.1 of this guidance.
Under Article 15 of the AML-CFT Law and Article 17 of the AML-CFT Decision, if the RHP suspects that a transaction, attempted transaction, activity, or funds (including agents' transactions), constitute, in whole or in part, regardless of the amount, the proceeds of crime, are related to a crime, or are intended to be used in a crime, they must submit an STR, SAR or other report types to the FIU using the ``goAML'' portal. RHP must submit this report without delay, meaning as soon as reasonably possible after the transaction takes place or their suspicions develop. All RHP must register with the goAML portal so that they can easily file these reports.
Reporting a suspicious transaction is not an admission of guilt or wrongdoing. STRs filed by RHP help law enforcement authorities identify and track potential criminal behaviour. As long as the RHP complies with the procedures in this guidance document, it will not generally be held responsible for a transaction that turns out to have been involved in a crime. But a failure to report a transaction that an RHP should know to be suspicious can result in penalties.
For more detail and information, please refer to the "CBUAE Guidance for Licensed Financial Institutions on Suspicious Transaction Reporting.''
5 Penalties
Under Article 7 of Circular No. 24/2019, violation of any provision may be subject to supervisory action as deemed appropriate by the CBUAE. In addition, without prejudice to other sanctions stated in other laws in the UAE, the CBUAE may impose administrative and financial sanctions and penalties in accordance with the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities and the CBUAE Regulations issued in implementation thereof.
Part III: Guidance for LFIs
1 Understanding Risks
Please refer to Part I, Section 3 for a description of the risks of Hawala Activity.
The Circular No. 24/2019 requires that RHP must maintain an account with a bank operating in the UAE to be used for settlement and provide the CBUAE with details of such account. The CBUAE expects LFIs to accept RHP customers, but LFIs must manage the risk that these transactions create through the use of appropriate controls (see Part III, section 2 below). LFIs must not accept as customers unregistered hawala providers based in the UAE, and must immediately report an STR to the FIU, inform CBUAE when they are detected, and closely monitor the relationship. Please see Part III, sections 2.2 and 2.3 below for guidance on detecting unregistered MVTS. 2 Mitigating Risks
The sections below elaborate on how LFIs can apply specific preventive measures to identify, manage, and mitigate the risks associated with hawala providers customers. These are not exhaustive and LFIs should consult the legal and regulatory framework in force in the UAE for the measures to be taken. The controls mentioned below should be at the minimum integrated into the LFI's larger AML/CFT compliance program, and supported with appropriate governance and training.
2.1 Risk-Based Approach
LFIs should take a risk-based approach to the preventive measures they put in place for all customers, including hawala providers. The risk-based approach has three principal components:
2.1.1 Conducting an Enterprise Risk Assessment
As required by Article 4.1 of the AML-CFT Decision, the enterprise risk assessment should reflect the presence of higher-risk customers, including hawala providers, in an LFI's customer base. These assessments should in turn be reflected in the LFI's inherent risk rating. In addition, the LFI's controls risk assessment should take into consideration the strength of the controls that the LFI has in place to mitigate the risks posed by its hawala providers customers, including the preventive measures discussed below.
2.1.2 Identifying and Assessing the Risks Associated with Specific Customers
The LFI should assess the risk of each customer to identify those that require EDD and to support its entity risk assessment. As discussed in Part I section 3 above, the regulatory environment and illicit finance risks in the jurisdictions in which they do business, the products and services they provide and its customer base, are critical determinants of a hawala provider's inherent risk. In assessing the risks of a hawala provider customer, LFIs should consider:
i. Controls Risk: LFIs should seek to understand the regulatory requirements in place for the customer, as well as how well they are enforced. The regulatory requirements placed on hawala providers vary markedly across jurisdictions.
ii. Geographic Risk: The risks associated with the jurisdictions in which the provider lives (for individuals) or is registered/established (for legal persons) and where it operates, including the jurisdictions where its main counterparties are based and where it has subsidiaries.
iii. Product, Service, and Delivery Channel Risk: LFIs should assess risk in this category on two dimensions:
a. The products and services that the hawala provider offers to its customers, and
b. The delivery channels through which it offers these products and services.
Products, services, and delivery channels that promote the rapid, anonymous transfer of high values are particularly attractive to illicit actors.
iv. Customer Risks: For hawala provider customers, customer risk can be assessed as the proportion of higher-risk customer types (e.g. politically exposed persons, legal persons, and customers from high-risk jurisdictions) within the provider's customer base.
Questions that an LFI may ask to determine the risk profile of a hawala provider customer include, but are not limited to:
• Where is the provider incorporated? Where does it operate? Are these high-risk jurisdictions? • What products and services does the provider offer its customers? • What volume of transactions does the provider carry out? • What customer base does the provider serve? • What is the regulatory environment in the jurisdiction(s) where the provider is incorporated/has operations? • Is there an authority that actively enforces the requirements? • Does the provider perform appropriate CDD, transaction monitoring, record keeping, and sanctions screening? • Does the provider intend to use its account to execute transactions on behalf of its customers?
In addition to risk rating hawala providers, LFIs should also consider the risks of specific transactions, especially high-value transactions, those involving high-risk jurisdictions, and those that represent departures from a customer's standard or expected behaviour.
2.1.3 Applying EDD and Other Preventive Measures
Where the LFI determines a customer to be higher-risk, Article 4.2(b) of the AML-CFT Decision requires that the LFI apply EDD. Specific EDD steps are also required for hawala providers customers that are politically exposed persons, or are owned or controlled by a politically exposed person, or are based in a higher-risk jurisdiction.
2.2 Customer Due Diligence and Enhanced Due Diligence
The goal of the CDD process is to ensure that LFIs understand who their customer is and the purpose for which the customer will use the LFI's services. Where an LFI cannot satisfy itself that it understands a customer, then it must not accept the customer. If there is an existing business relationship, the LFI should not continue it. LFIs should also consider filing an STR, SAR or other report types to the FIU as discussed in section 2.3.2 below. This guidance is not an exhaustive list of LFIs' CDD obligations and LFIs should consult the legal and regulatory framework in force in the UAE for the measures to be taken.
2.2.1 Customer Identification and Verification
Under Article 8 of AML-CFT Decision, LFIs are required to identify and verify the identity of all customers. Please see also the AML/CFT Guidelines for Financial Institutions for full information on customer identification. In particular, when verifying the Emirates ID card, LFIs must use the online validation gateway of the Federal Authority for Identity & Citizenship and keep a copy of the Emirates ID and its digital verification.
Hawala providers based in the UAE are required to have an active registration certificate issued by the CBUAE and a commercial trade license that includes Hawala Activity. In particular, when opening any accounts for hawala providers, LFIs must physically check the original hawala provider registration certificate issued by the CBUAE and keep a copy thereof. LFIs should not form business relationships or conduct transactions with hawala providers without an active registration certificate issued by the CBUAE (unregistered hawala providers). In addition, if an LFI determines that a customer or prospective customer has materially misrepresented itself or its business, it must not accept the customer, must exit the relationship if one has been established, should add the customer, its beneficial owners, directors and managers to its internal watchlists, and should file an STR with the FIU.
2.2.2 Beneficial Owner Identification
Where the hawala provider customers is a legal person, please consult the CBUAE's Guidance for LFIs providing services to Legal Persons and Arrangements for details on the identification of beneficial owners.11
11 Available at centralbank.ae/en/cbuae-amlcft.
2.2.3 Customer's Business and Business Relationship
For all customer types, LFIs are required to understand the purpose for which the account or other financial services will be used, and the nature of the customer's business. This element of CDD will have important implications for the customer risk rating. This is particularly true of the purpose of the account, which will likely be an essential determinant of risk for hawala provider customers. It is critical that LFIs have processes and controls in place to ensure that they are able to identify hawala customers. LFIs must ensure that they fully understand their customers' source of funds and the business in which they are engaged. In addition to interviewing the customer, requesting financial records, and reviewing invoices, LFIs should also search company databases and consider visiting the customer's business premises.
Underground hawala providers often try to evade detection by creating new companies and/or frequently switching to new financial institutions. In addition, even those that operate legally, may seek to misrepresent the purpose of the relationship in order to evade scrutiny and controls imposed by the LFI. It can be particularly difficult for an LFI to establish the bona fides and business activities of a newly established company, which is likely to not have any customers or inventory, especially when that company's line of business (e.g. import/export) is vague. LFIs should screen the names of new customer's beneficial owners, directors, and managers against its internal watchlists of customers previously exited by the LFI.
When a customer provides information indicating it is a hawala provider, LFIs must collect sufficient information during the CDD process to understand the full scope of the customer's business, including not only its provision of hawala services but also any other business activities in which the customer engages. LFIs should pay particular attention to the jurisdictions with which their hawala provider customers does business, and must understand whether their customer offers financial services to other hawala providers (e.g. participates in clearing networks or makes transfers on behalf of the customers of another provider who lacks a network in certain jurisdictions). Furthermore, LFIs must fully understand the intended use of the account and the expected activity on the account, to the extent that it can generally predict activity on the account and identify activity that does not fit the profile. This may be many small cash deposits followed by large cross-border transfers or volume of activity that does not fit the customer's business. They must also understand whether the hawala provider may be using the LFI's accounts to conduct business and to move funds on behalf of customers while attempting to conceal this activity from the LFI. Section 2.3.1 contains red flags for concealed activity.
2.2.4 Ongoing Monitoring
All customers must be subject to ongoing monitoring throughout the business relationship to ensure that transactions are reasonable, and legitimate. Ongoing monitoring is particularly important in the context of business relationships with hawala providers, where the risks these relationships create for the LFI can change significantly based on the hawala provider's business activities. LFIs are required to ensure that the CDD information they hold on all customers is accurate, complete, and up-to-date. LFIs should update CDD for all customers on a risk-based schedule, with CDD on higher-risk customers being updated more frequently. EDD on all customers should involve more frequent CDD updates.
In addition to a review of the customer's CDD file, the LFI should also review the customer's transactions to determine whether they continue to fit the customer's profile and business, and are consistent with the business the customer expected to engage in when the business relationship was established. This type of transaction review is distinct from the ongoing transaction monitoring discussed in 2.3.1 below. The purpose of the review is to complement ongoing transaction monitoring by identifying behaviours, trends, or patterns that are not necessarily subject to transaction monitoring rules. For example:
• Company M, a hawala provider, opens an account with Bank B, an LFI. At onboarding, Company M tells Bank B that it operates as a money transfer service to Country X. A year after the account is opened, Bank B conducts a scheduled CDD review and discovers that, six months after onboarding, Company M began to make and receive periodic transfers to and from Country Y. Bank B makes inquiries and discovers that Company M is now providing money transfer services to Country Y as well. Bank B decides to put a restriction on the account requiring prior authorization to make transfers beyond Country X and Country Y, requires Company M to sign a warrant that it will inform Bank B in advance of any future changes to its business model, and raises the customer risk-rating.
When customers are higher risk, including hawala provider customers, monitoring should be more frequent, intensive, and intrusive. LFIs should review the CDD files of higher risk customers on a frequent basis, such as twice a year. The methods LFIs use to review the account should also be more intense and should not rely solely on information supplied for the customer. For example, LFIs should consider:
• Reviewing all transactions on the account, rather than a sample of transactions;
• Conducting site visits at the customer's premises and requesting a meeting with the customer;
• Conducting searches of public databases, including news and government databases in order to independently identify material changes in a customer's ownership or business activities. Such searches should include adverse media searches of public records and databases, using relevant key words, including but not limited to, allegation, fraud, corruption, laundering.
2.3 Transaction Monitoring and STR Reporting
2.3.1 Transaction Monitoring
Where possible, transaction monitoring systems used to monitor activity in the accounts of the RHP should also be equipped to identify breaches of the permitted services by RHP listed in Part I section 4.1. The transaction monitoring system used by LFIs should also be equipped to identify RHP that are using the LFI's accounts to conduct their business and to move funds on behalf of customers while attempting to conceal this activity from the LFI. Red flags for concealed activity appear below. If an LFI's automated transaction monitoring system is not capable of alerting on these red flags, LFIs should have in place manual monitoring, such as management information systems that are capable of doing so. Frequent deposits by multiple individuals into a single bank account, followed by international wire transfers and /or international withdrawals through ATMs.
• Money being transferred at regular intervals to international locations known to be clearing houses for remittances. • An account being used as a temporary repository with the funds quickly transferred. • Usage of third-party accounts to disguise and to avoid detection by authorities. • Wire transfers frequently sent by traders to foreign countries that do not seem to have any business connection to the destination countries. • Business accounts used to receive or disburse large sums of money but show virtually no reasonable business-related activities such as payment of payrolls, invoices etc. • Frequent deposits of third-party checks and money orders into business or personal accounts. • Frequent international wire transfers from bank accounts that appear inconsistent with stated business activities. • Sudden change in pattern of financial transactions from low value international fund transfers to large value transfers.
2.3.2 STR Reporting
As required by Article 15 of AML-CFT Law and Article 17 of AML-CFT Decision, LFIs must file an STR, or SAR or other report types with the FIU when they have reasonable grounds to suspect that a transaction, attempted transaction, or funds constitute, in whole or in part, regardless of the amount, the proceeds of crime, are related to a crime, or are intended to be used in a crime. STR filing is not simply a legal obligation; it is a critical element of the UAE's effort to combat financial crime and protect the integrity of its financial system. STR filings are essential to assist concerned UAE authorities, such as law enforcement, in detecting criminal actors and preventing the flow of illicit funds through the UAE financial system.
In addition to the requirement to file an STR when an LFI suspects that a transaction or funds are linked to a crime, LFIs should consider filing an STR in the following situations:
• A potential customer decides against opening an account or purchasing other financial services after learning about the LFI's CDD requirements; • A current customer cannot provide required information about its business or its beneficial owners; • A customer cannot adequately explain transactions, provide supporting documents such as invoices, or provide satisfactory information about its counterparty; • The LFI is not confident, after completing CDD procedures, that it has in fact identified the individuals owning or controlling the customer. In such cases, the LFI should not establish the business relationship, or continue an existing business relationship; or • If the LFI believes that a customer may be acting as an unregistered hawaladar.
Please see also the CBUAE's Guidance for LFIs on Suspicious Transaction Reporting for further information.
2.4 Governance and Training
The specific preventive measures mentioned above must take place within, and be supported by, a comprehensive institutional AML/CFT program that is appropriate to the risks the LFI faces. The core of an effective risk-based program is an appropriately experienced AML/CFT compliance officer who understands the LFI's risks and obligations and who has the resources and autonomy necessary to ensure that the LFI's program is effective. As with all risks to which the LFI is exposed, the AML/CFT training program must ensure that employees are aware of the risks of hawala provider customers, familiar with the obligations of the LFI, and equipped to apply appropriate risk-based controls. Training should be tailored and customized to the LFI's risk and the nature of its operations. For example, an LFI that has a large number of hawala provider customers should offer training that includes an in-depth discussion of risk factors and red flags related to such customers.
Annex 1. Synopsis of the Guidance
PART I: REGISTERED HAWALA PROVIDERS AND LICENSED FINANCIAL INSTITUTIONS Introduction Purpose The purpose of this Guidance is to assist the understanding and effective performance by the Registered Hawala Providers and other Licensed Financial Institutions (LFIs) of their statutory obligations under the legal and regulatory framework in force in the UAE. Applicability This Guidance applies to all natural and legal persons which are licensed and/or supervised by the CBUAE in the following categories: Registered Hawala Providers ("RHP"), National banks, branches of foreign banks, and Exchange houses. Legal Basis This Guidance builds upon the provisions of UAE laws and regulations, including the AML-CFT Law, the AML-CFT Decision, the Cabinet Decision 74 of 2020 and the Registered Hawala Providers Regulation issued by the CBUAE ("Circular No. 24/2019"). Overview of Hawala
activity
Hawala is an activity based on trust and was established to avoid high charges by people who cannot afford them, the ability to reach beneficiaries in remote places quickly where banks do not operate, and the existence of strict currency controls in some countries. While hawala providers, also known as hawaladars, often use banking channels to settle between them, what makes them distinct from other money transmitters is their use of other settlement methods, including trade, cash, and long-term net settlement. Global risks of Hawala Activity Hawaladars' business model is built around satisfying customers' needs to move money rapidly across borders, a service that may also be misused by criminals as it is to individuals seeking to conduct legitimate personal remittances. The risk of a hawala provider is influenced by the regulatory environment and illicit finance risks in the jurisdictions in which they do business, the products and services they provide, and their customer base. Regulation in the UAE The CBUAE permits legitimate Hawala Activity as an important element of its continuous efforts to support financial inclusion and bring the unbanked population into the regulated financial system. To this end, Hawala is regulated by the Registered Hawala Providers Regulation issued by the CBUAE. All providers carrying on Hawala Activity in the UAE must hold a Hawala Provider Certificate issued by the CBUAE; it is not permitted to carry on Hawala Activity without being registered with the CBUAE. Registered Hawala Providers (RHP) are only permitted to provide well-defined services that include non- commercial personal remittances and money transfer services to support commercial operations. RHP are not permitted to engage in any of the following transactions: Take deposits, exchange currencies or sell and purchase travellers' cheques; Provide any financial services other than money transfers (e.g. exchange of virtual assets/cryptocurrencies, loans, purchase of debts); or Execute transactions involving or on behalf of any other hawala provider in the UAE. This excludes the agents of the RHP in a foreign country. PART II: GUIDANCE FOR REGISTERED HAWALA PROVIDERS Sanctions Obligations Targeted Financial Sanctions (TFS)are legal restrictions on financial activity imposed by the United Nations Security Council (UNSC) or the UAE. RHP are required to fully comply with the obligation to implement all necessary measures without delay as described in the Cabinet Decision 74 of 2020, the "Guidance on TFS for FIs and Designated Non-Financial Business and Professions (DNFBPs)' issued by the Executive Office of the Committee for Goods & Material Subject to Import and Export Control, the CBUAE's Guidance for LFIs on the implementation of TFS, the CBUAE Notice No. 3895/2021, and any of their amendments or updates thereof. RHP should be aware that it is a crime in the UAE to provide funds or financial services, including money transmissions services, to a person subject to TFS.
Appropriate implementation of TFS has four key steps, which RHP must follow to ensure they are compliant:
- Maintain awareness of UNSC and UAE sanctions lists, and rapidly becoming informed of changes to these lists.
- Check the names of customers against the lists of sanctioned persons.
- Immediately freeze any funds in the possession or under the control of the RHP that may belong to a listed person, and cancelling (where possible) any transactions involving a listed person.
- Report any listed persons and the actions the RHP has taken to the appropriate authorities (via the goAML Portal).
Registration and other Requirements Registration A resident natural person or legal person may not carry on Hawala Activity in the UAE unless the applicant holds a Hawala Provider Certificate issued by the CBUAE and is registered in the CBUAE Hawala Providers Register. CBUAE Notification of Approval/Rejection The CBUAE may agree or decline an application for a Hawala Provider Certificate and will notify the applicant in writing of its decision. Re-Registration RHP should submit to the CBUAE an application for renewal of the Hawala Provider Certificate within a period not less than two months from the date of expiry of the original certificate or any renewals thereof. Requirements for Trade License, Security and Reporting Systems RHP are required to complete the following requirements within 90 days from the date mentioned in the final registration certificate as well as submit proof of completion to the Licensing Division of the CBUAE:
- Add Hawala Activity to the commercial trade license.
- Install security systems i.e. CCTV and police connections.
- Register o the UAE Financial Intelligence Unit's (FIU)goAML portal.
- Register to the CBUAE's Systems for the daily and quarterly reporting.
- RHP should register for the FlU's Integrated Enquiries Management System.
Requirement for a Bank Account RHP must maintain an account with a bank operating in the UAE to be used for settlement and provide the CBUAE with its details. In addition, they should inform their account manager at the bank of their intention to use the account to carry out Hawala Activity. AML/CFT program AML/CFT Program and Compliance Officer RHP are required to establish and maintain effective AML/CFT compliance programs designed to prevent them from being misused to facilitate money laundering or terrorist financing. The program must be risk-based and appropriate to the risk of the RHP, taking into consideration its size, volume of transactions, types of remittances offered (personal only or personal and commercial), complexity, the nature and volume of its Hawala Activity, the nature of its customer base and the geographic areas in which it operates. Each RHP must have a specific person, the Compliance Officer, who is responsible for day-to-day compliance with the legal and regulatory framework in the UAE and the management of the AML/CFT program. This person must bean employee, manager, or owner of the RHP depending on the size of the RHP. They should also provide education and training to appropriate personnel and conduct a periodic audit of the AML/CFT program. Understanding Risks The Compliance Officer should begin the risk assessment process by carefully reading and understanding Parts 1 and II of this Guidance, which contain essential information about the risks faced by an RHP and consider the customer, geographic, products and services, and delivery channel risks. RHP should complete this risk assessment process at least once a year. Where they assess themselves as higher risk, they should take additional precautions. AML/CFT Program Customer and Agent Due Diligence Customer due diligence ("CDD") is the process by which an RHP identifies and understands its customer; it is required by law. The RHP must perform Customer Identification Diligence ("CID"), CDD or Enhanced Due Diligence ("EDD") prior to conducting each and every transaction, even if the customer is a repeat customer. An RHP must not conduct a transaction if the appropriate diligence has not been performed or completed depending on their nature as follows:
- CID: When natural persons sends or receives a transfer between AED 1-3, 499 and no higher risks are present.
- CDD: In all other cases between AED 3,500-54,999.
- EDD: When the customer is a natural person carrying out a transfer above ED 55,000, or when the customer is from/sending a remittance to a high-risk jurisdiction, or when the customer is a politically exposed person or a legal person, or when other higher risks are present.
RHP may use agents in a foreign country to carry out activity on their behalf in that foreign country. RHP are not permitted to use agents to carry out activity on their behalf in the UAE (also known as "nesting"). RHP are required to perform appropriate due diligence on their agents and monitor their transactions to ensure that they are legitimate, keep up-to-date agent lists for a period of five years and provide them upon request to the CBUAE and/or to relevant authorities within the country in which they operate.
Transaction Monitoring and Record Keeping When an RHP's customer is originating a transaction, the RHP must collect and keep certain information for every transaction. When RHP's customer is receiving the remittance, they must in addition conduct CDD on the beneficiary and make sure that its customer's information matches that of the beneficiary identified in the information provided by the originating hawala provider. RHP must keep all records obtained through the CDD process and maintain records of all transactions for at least five years from the date of completion of the transaction or longer if directed by the CBUAE or any other authority. Reporting Obligations Daily Reporting RHP must upload electronically to the CBUAE's reporting systems on a daily basis the data and details of all transfers, remitters and beneficiaries as per the forms prepared by the CBUAE for this purpose. Quarterly Settlement Statements RHP must further submit to the CBUAE statements of their settlement accounts on a quarterly basis along with other required forms, as well as provide the CBUAE with any data, information, or statistics it may require. Reporting Suspicious Transactions to the FIU If the RHP suspects that a transaction, attempted transaction, activity, or funds (including agents' transactions), constitute, in whole or in part, regardless of the amount, the proceeds of crime, are related to a crime, or are intended to be used in a crime, they must submit a Suspicious Transaction Report (STR), Suspicious Activity Report (SAR) or other report types to the FIU using the goAML portal. RHP must submit this report without delay, meaning as soon as reasonably possible after the transaction takes place or their suspicions develop. Please see also the CBUAE's Guidance for LFIs on Suspicious Transaction Reporting fox further information. Penalties Violation of any statutory obligations may be subject to supervisory action, administrative and financial sanctions and penalties as deemed appropriate by the CBUAE. PART III: GUIDANCE FOR LFIs Understanding Risks Circular 24/2019 requires that RHP must maintain an account with a bank operating in the UAE to be used for settlement and provide the CBUAE with its details. The CBUAE expects LFIs to accept RHP customers, but LFIs must manage the risk that these transactions create through the use of appropriate controls. LFIs must not accept as customers unregistered hawala providers based in the UAE, and must immediately report an STR to the FIU, inform CBUAE when they are detected, and closely monitor the relationship. Mitigating Risks Risk-Based Approach LFIs should take a risk-based approach to the preventive measures they put in place for all customers, including hawala providers. The approach should include at the minimum the conduct of an enterprise risk assessment, identification and assessment of the risks associated with specific customers, and the application of EDD and other preventive measures. CDD and EDD Customer Identification and verification: LFIs are required to identify and verify the identity of all customers. Among other requirements, LFIs must physically check the original hawala provider registration certificate issued by the CBUAE and keep a copy thereof. LFIs should not form business relationships or conduct transactions with hawala providers without a valid registration certificate issued by the CBUAE (unregistered hawala providers). Beneficial Owner Identification: Where the hawala provider customers is a legal person, please consult the CBUAE's Guidance for LFIs providing services to Legal Persons and Arrangements for details on the identification of beneficial owners. Customer's Business and Business Relationship: It is critical that LFIs have processes and controls in place to ensure that they are able to identify hawaladar customers. LFIs must ensure that they fully understand their customers' source of funds and the business in which they are engaged, the intended use and expected activity on the account, to the extent that they can generally predict and identify activity that does not fit the profile. Ongoing Monitoring: All customers must be subjectto ongoing monitoring throughout the business relationship to ensure that transactions are reasonable and legitimate. LFIs are required to ensure that the CDD information they hold on all customers is accurate, complete, and up-to- date. When customers are higher risk, including hawala provider customers, monitoring should be more frequent, intensive, and intrusive. Transaction Monitoring and Suspicious Transaction Reporting Where possible, transaction monitoring systems used to monitor activity of the RHP should also be equipped to identify breaches of the permitted services by RHP. The transaction monitoring system used by LFIs should also be equipped to identify RHP that attempt to conceal activity from the LFI. LFIs must file a Suspicious Transaction Report, Suspicious Activity Report or other report types with the FIU when they have reasonable grounds to suspect that a transaction, attempted transaction, or funds constitute, in whole or in part, regardless of the amount, the proceeds of crime, are related to a crime, or are intended to be used in a crime. Please see also the CBUAE's Guidance for LFIs on Suspicious Transaction Reporting for further information. Governance and Training The specific preventive measures mentioned in this Guidance must take place within, and be supported by, a comprehensive institutional AML/CFT program that is appropriate to the risks the LFI faces. As with all risks to which the LFI is exposed, a training program must ensure that employees are aware of the risks of hawala provider customers, familiar with the obligations of the LFI, and equipped to apply appropriate risk-based controls. Guidance for Licensed Financial Institutions on the Risks Relating to Payments
Effective from 1/8/20221. Introduction
1.1. Purpose of the Guidance
Article 44.11 of the Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations charges Supervisory Authorities with “providing Financial Institutions…with guidelines and feedback to enhance the effectiveness of implementation of the Crime-combatting measures.”
The purpose of this Guidance is to assist the understanding and effective performance by the United Arab Emirates Central Bank’s (“CBUAE”) licensed financial institutions (“LFIs”) of their statutory obligations under the legal and regulatory framework in force in the UAE. It should be read in conjunction with the CBUAE’s Procedures for Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations (issued by Notice No. 74/2019 dated 19/06/2019) and Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations for Financial Institutions (issued by Notice 79/2019 dated 27/06/2019) and any amendments or updates thereof.1 As such, while this Guidance neither constitutes additional legislation or regulation nor replaces or supersedes any legal or regulatory requirements or statutory obligations, it sets out the expectations of the CBUAE for LFIs to be able to demonstrate compliance with these requirements. In the event of a discrepancy between this Guidance and the legal or regulatory frameworks currently in force, the latter will prevail. This Guidance may be supplemented with additional separate guidance materials, such as outreach sessions and thematic reviews conducted by the Central Bank.
Furthermore, this Guidance takes into account standards and guidance 2 issued by the Financial Action Task Force (“FATF”), industry best practices and red flag indicators. These are not exhaustive and do not set limitations on the measures to be taken by LFIs in order to meet their statutory obligations under the legal and regulatory framework currently in force. As such, LFIs should perform their own assessments of the manner in which they should meet their statutory obligations.
This Guidance comes into effect immediately upon its issuance by the CBUAE with LFIs expected to demonstrate compliance with its requirements within one month from its coming into effect.
1 Available at centralbank.ae/en/cbuae-amlcft.
2 FATF: Guidance for a Risk-Based Approach: Prepaid Cards, Mobile Payments and Internet-Based Payment Services, 2013, fatf-gafi.org/media/fatf/documents/recommendations/Guidance-RBA-NPPS.pdf, and Correspondent Banking Services, 2016, fatf-gafi.org/media/fatf/documents/reports/Guidance-Correspondent-Banking-Services.pdf
1.2. Applicability
Unless otherwise noted, this guidance applies to all natural and legal persons, which are licensed and/or supervised by the CBUAE, in the following categories:• National banks, branches of foreign banks, exchange houses, finance companies; and • Stored value facilities, retail payment service providers, and card schemes.
1.3. Legal Basis
This Guidance builds upon the provisions of the following laws:• Decree Federal Law No. 20 of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations as amended by Decree Federal Law No. (26) of 2021 (“AML-CFT Law”). • Cabinet Decision No. (10) of 2019 concerning the Implementing Regulation of Decree Federal Law No. 20 of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations as amended by Cabinet Decision No. (24) of 2022 (“AML-CFT Decision”). • Cabinet Decision No. (74) of 2020 Regarding Terrorism Lists Regulation and Implementation of United Nations Security Council (UNSC) Resolutions on the Suppression and Combating of Terrorism, Terrorist Financing, Countering the Proliferation of Weapons of Mass Destruction and its Financing and Relevant Resolution (“Cabinet Decision 74”).
1.4. Acronyms and Definitions
Card Scheme: a single set of rules, practices and standards that enable a holder of a payment instrument to effect the execution of card-based payment transactions within the UAE which is separated from any infrastructure of payment system that supports its operation, and includes the card scheme governing body. For the avoidance of doubt, a card scheme may be operated by a private or public sector entity.
Correspondent Banking Relationship: the relationship between a correspondent financial institution and a respondent one through a current account or any other type of account(s) or through a service related to such an account and includes a corresponding relationship established for the purpose of securities transactions or transfer of funds.
Nesting: defined by the FATF as the use of a bank’s correspondent relationship by a number of respondent banks through their relationships with the bank’s direct respondent bank to conduct transactions and obtain access to other financial services.
New Payment Products and Services (NPPS): defined by the FATF as new and innovative payment products and services that offer an alternative to traditional financial services.
Payment Sector: refers to different forms of payment that are transmitted and exchanged across various delivery channels, frequently utilizing digital platforms, systems, services and products.
PPS: Payment Products and Services.
Retail Payment Services: any of the following services: payment account issuance; payment instrument issuance; merchant acquiring; payment aggregation; domestic fund transfer; cross-border fund transfer; payment token; payment initiation; and payment account information.
Stored Value Facility (SVF): a facility (other than cash) for or in relation to which a customer, or another person on the customer’s behalf, pays a sum of money (including money’s worth such as values, reward points, crypto-assets or virtual assets) to the issuer, whether directly or indirectly, in exchange for: (a) the storage of the value of that money (including money’s worth such as values, reward points, crypto-assets or virtual assets) whether in whole or in part, on the facility; and (b) the relevant undertaking. SVF includes device based SVF and non-device based SVF.
2. Understanding Risks
There is no uniform global approach to regulation of the Payment Sector and participants may be classified as different types of entities in different regulatory regimes. Some types of participants may be regulated as financial institutions in some jurisdictions but not in others. Operating within a global financial center, LFIs in the UAE may be exposed not just to participants licensed by the CBUAE, but also to those operating globally. This exposure can be direct (i.e., providing financial services directly to a participant), or indirect (e.g., when a customer initiates a withdrawal from his checking account using a foreign smartphone-based app that he has linked to that account).
The Payment Sector is becoming increasingly diverse, and payment processes more complex. The Payment Sector is no longer solely dominated by traditional financial institutions like banks and exchange houses, which also offer new and innovative methods using the internet or mobile phone technology. A variety of new types of Payment Sector participants, such as companies that offer internet-or smartphone-based payment applications and providers of prepaid cards and devices, are involved in a growing percentage of all payment transactions. These entities allow almost anyone to accept and originate payments using a wide variety of techniques and payment routes. Whenever a customer makes a purchase or pays a bill online, these new participants are likely to be involved. These entities may also be used outside commercial contexts, such as by crowdfunding platforms or charitable organizations.
Furthermore, as innovative technologies emerge and commerce and economic activity increasingly grows online, merchants and consumers are relying on a diverse array of New Payment Products and Services (NPPS). The FATF defines NPPS as “new and innovative payment products and services that offer an alternative to traditional financial services.” Examples of NPPS include prepaid cards, mobile payments, and internet-based payment services; these are neither exhaustive, nor exclusive as a provider of mobile money, for instance, may utilize prepaid cards or provide internet-based payment services. In contrast, payment methods such as credit cards and cheques, and bulk funds transfer systems such as national payment systems, would generally not qualify as NPPS. Because NPPS are so diverse, they do not share a single risk profile and pose money laundering and financing of terrorism (ML/FT) risks for financial institutions when they do not understand the operation or the vulnerabilities in the NPSS operational models. The provision of these NPPS is frequently implemented or facilitated by a group or network of different companies, some of them invisible to the consumer or even all the participants in the network, given the presence of multiple participants in the chain with whom not all participants will have a contractual relationship.
The vast majority of payment transactions carried out each year across the globe are legitimate. But the Payment Sector—and NPPS in particular—has characteristics that make it both attractive and vulnerable to illicit actors. As LFIs are increasingly exposed to new participants in this sector, they must remain alert to and understand the risks this exposure creates.
Section 2.1 below discusses the ML/FT risks of the Payment Sector with a focus on risks related to NPPS. It applies to financial institutions that are directly involved in the provision of such products and services, which includes both traditional LFIs and those that are solely engaged in providing payments. Section 2.2 discusses risks specific to LFIs that provide services to other Payment Sector participants.
2.1. ML/FT Risks of the Payment Sector
2.1.1. Characteristics of the Movement of Funds
PPS, and NPPS in particular, are extremely attractive to illicit actors because of the rapid movement of funds between Payment Sector participants and across borders. The risks of a specific payment network or application however can vary based on the features that make it more or less attractive to illicit actors, such as:• Transaction speed. Are transactions instantaneous, or do they take hours or days? The quicker the transaction, the easier it is for illicit actors to conduct multiple transfers, further obscuring the origin of the funds, before coming to the attention of the authorities.
• Transaction limits. Does the PPS have transaction caps or limits? Smaller-value payments are not without risk, especially in the terrorist financing context, but they do make it more difficult to move illicit funds on a large scale.
• Closed vs open loop system. PPS, primarily SVF, can be “closed” or “open” loop. In a closed loop system, the payment method can only be used for payments to a specific payee. Examples include transit passes and store gift cards. In an open loop system, the payment method can be used to pay a wide variety of payees, and can be linked to other payment methods that further expand its reach. Although it is certainly possible to use closed loop systems for ML/FT (for instance, if a terrorist group collects store gift cards and uses them to purchase equipment), the restrictions on their use makes them less attractive to illicit actors.
• Methods of funding and access to cash.3 The methods by which a PPS can be funded (such as by cash, through another payment service, a prepaid model, or by third-party funding from anonymous sources) may increase risk. The inputs and outputs of a given PPS are therefore an important consideration when assessing risk, including whether the funding source is located internationally such as a high-risk country. For example, illicit actors may seek to place cash in the financial system or to obscure transaction trails by converting funds in and out of cash. PPS that permit users to fund their accounts with cash, or that allow users to withdraw cash, may be higher risk. In addition, as discussed above in the context of open loop systems, the more open and porous the PPS, the higher the risk it may present. PPS that allow users to fund accounts from multiple sources, and to withdraw funds using multiple methods, are likely to be more attractive to illicit actors, and will be harder to effectively monitor.
• Payment transparency. NPPS often have aggregated payments and settlement accounts involving multiple parties and long payment chains thereby potentially causing LFIs to have reduced visibility into payment activity taking place through the PPS as well as obscuring an LFI’s ability to identify the ultimate payer and payee for all transactions.
• Ability for one person to create multiple accounts. Some PPS allow customers to create multiple accounts using the same ID. These may be individual accounts or created on behalf of minors or other family members. Illicit actors may seek to rapidly cycle funds through accounts (whether or not these take the form of virtual ‘wallets’ or other SVF) in order to obscure payment trails. They may also seek to open multiple accounts to facilitate fraud and other criminal activity. Restricting a customer to one account does not eliminate risk, since illicit actors often work in groups, but it makes it more difficult for a single person to launder funds by conducting a self-transfer.
• Non-face-to-face relationships. Does the payment method allow for a non-face-to-face business relationship? What are the payment method’s characteristics? Can the relationship be established through agents, online or through a mobile payment system? The absence of contact and/or anonymity may increase the risk of identity fraud or customers providing inaccurate information.
• Use of virtual assets.4 As interest in virtual assets grows, more and more payment methods and schemes are integrating with virtual assets. For example, a global payments firm allow users in some countries to purchase virtual assets using the funds in their account, although not to use them directly for payments. Payment methods and schemes that integrate virtual assets could expose financial institutions to the specific risks of this sector.
3 For details on the vulnerabilities of cash and alternatives to cash, please consult the CBUAE’s Guidance for Licensed Financial Institutions providing services to Cash-Intensive Businesses
4 Please note that the risks relating to Virtual Assets/Virtual Assets Service Providers are out of the scope of this guidance and addressed in a separate guidance to be issued by the CBUAE.
2.1.2. Peer-to-Peer Payments
NPPS have revolutionized the ability to make payments or transfer funds. Where cash transactions previously required face-to-face interaction and bank transfers involved transactions’ fees and an execution time in the past, NPPS allow participants to send money that will be instantly available to the beneficiary, reducing the need for trust in the relationship. As a result, the availability of convenient, inexpensive PPS has led to a decreasing use of cash, particularly in highly developed countries. Bringing transactions into the formal financial system has many advantages from the perspective of combating illicit finance. These transactions can flow through third parties that are in many cases subject to AML/CFT requirements. In most cases, the payments that involve such third parties include information on the payer and the payee and are permanently recorded by a financial institution, making it easier for law enforcement to track transactions. But the use of PPS for peer-to-peer payments also creates risk for financial institutions because it means that many smaller illicit transactions that once took place in cash are now being conducted via PPS, particularly NPPS.
2.1.3. Cross-Border Movement
One of the principal features of many NPPS is that they can be used globally for making payments or transferring funds. While the usefulness of cash and cheques is limited outside the jurisdiction where they were issued, many PPS are internet-based services and specialize in conducting transfers between countries and currencies. For example, a UAE bank that offers checking accounts to UAE residents may have no ATMs or branches outside the UAE. But, if users link their accounts to global or regional payment apps, they can conduct transactions with persons over the world and can use their smartphone as a payment instrument in countries where the bank has no presence, thus introducing new geographical exposure potentially to high-risk countries. And unlike cross-border wires, which carry full identifying information, the bank will frequently only see the customer’s transactions with the payment network itself, rather than their location or ultimate destination. Many illicit finance schemes involve the cross-border movement of funds. Criminals may seek to finance terrorism in other countries, move funds out of sanctioned jurisdictions, or evade the attention of law enforcement in the jurisdiction where a proceeds-generating offense was committed. PPS that allow or facilitate cross-border movement of funds may therefore be particularly attractive to illicit actors.
2.1.4. Global Regulatory Gaps
Countries take a variety of approaches to regulating the Payment Sector and there is no one widely accepted classification of participants. As a result, two regulators in two different jurisdictions may subject a single company to very different requirements based on each jurisdiction’s regulatory framework. The company may be regulated as a financial institution in one jurisdiction, and thus subject to AML/CFT requirements, but treated as a tech company in another with no requirement to apply preventive measures. Companies may provide services to customers in a given country without being regulated in that country at all. Even where Payment Sector participants are fully regulated and subject to stringent AML/CFT requirements, supervisors’ expectations for this sector may be lower than for traditional financial institutions such as banks. And participants, as relatively new market entrants, may lack the experience, expertise, or commitment to apply fully effective preventive measures. These entities may be less able to protect themselves and their partners, and thus vulnerable to abuse by illicit actors.
2.1.5. Intermediation
The Payment Sector may be complex with a number of participants potentially involved in a single transaction. As a result, many payment transactions will be highly intermediated, with multiple financial institutions involved in a funds transfer. Additional entities (some of which may not be financial institutions) can potentially facilitate the transaction through the exchange of information. Intermediated transactions create risk because no regulated entity participating in the transaction has the visibility necessary to fully understand the transaction and the participants. Illicit transactions may have red flags when viewed as a whole, but may appear legitimate when seen from the perspective of each of the financial institutions involved. This creates a vulnerability that illicit actors can exploit.
For example, consider the hypothetical transaction below, a purchase on an online marketplace that allows individual sellers to sell items directly to customers: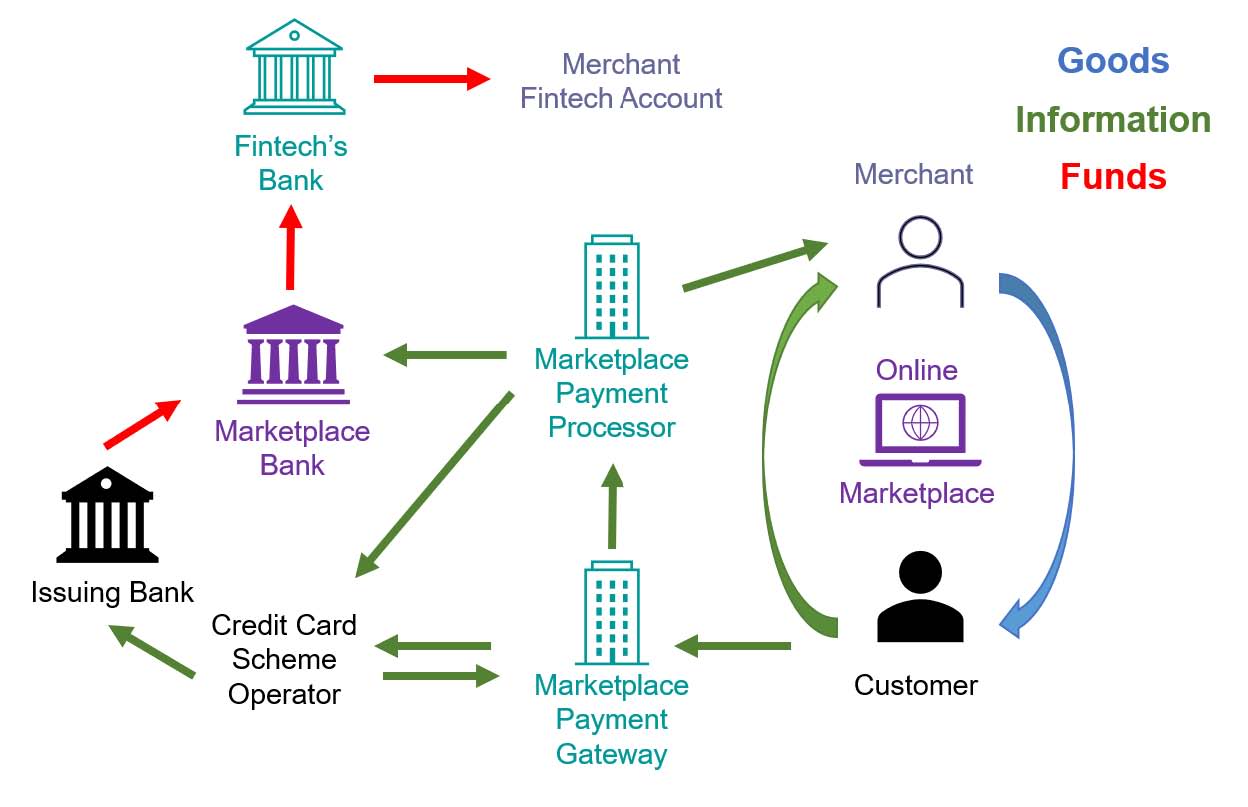 In this transaction, the customer is using a credit card to purchase goods from the merchant, but the merchant is not a participant in the credit card scheme. A number of Payment Sector participants help to bridge this gap and facilitate the transaction:
In this transaction, the customer is using a credit card to purchase goods from the merchant, but the merchant is not a participant in the credit card scheme. A number of Payment Sector participants help to bridge this gap and facilitate the transaction:• The marketplace uses a payment gateway that accepts the customer’s credit card credentials, encrypts them, and validates them against data held by the credit card scheme operator. The marketplace may also integrate with providers that provide ‘one-click’ payment information to the payment gateway without requiring the customer to enter his or her credit card details. In the UAE, these providers would be classified as conducting payment account information services, but in many other jurisdictions they are not regulated as financial institutions.
• The credit card scheme operator validates the customer information provided by the payment gateway, conducts initial fraud checks, and informs the payment gateway that the credit account is in good standing and the credit limit has not been exceeded.
• The payment gateway informs the marketplace’s payment processor that a transaction of an identified value can proceed using the customer’s credit card details.
• The marketplace payment processor informs the merchant that the transaction has been confirmed and instructs the credit card scheme operator to debit the customer’s account for the purchase price, in favor of the marketplace.
• The credit card scheme operator passes this payment instruction on to the bank that issued the customer’s credit card (the issuing bank). Meanwhile, the merchant ships the customer the merchandise purchased.
• The issuing bank transfers funds in the purchase value to the marketplace’s bank (this transfer may in fact go through the marketplace payment processor’s account at the same bank).
• The marketplace bank transfers the purchase funds to the merchant’s fintech (likely a provider of SVF), which in turn transfers the funds to the merchant’s account. The marketplace’s payment processor likely facilitates this transaction by instructing the bank where to send the funds.
It is unlikely that any of the Payment Sector participants in this transaction have full visibility into the funds transfer chain. The banks are unlikely to have information on anyone other than their immediate customers or correspondents. The payment gateway likely does not identify the merchant. The fintech likely does not identify the customer. The marketplace payment processor is likely aware that the customer and merchant are engaging in a transaction, but may not know where the customer’s funds are coming from or where the merchant’s funds are going. And because the marketplace payment processor does not hold funds at any point in the transaction, it may not be regulated as a financial institution in all jurisdictions. In this instance, a marketplace payment processor may apply certain conditions on what types of customers and merchants it engages. For more information on how LFIs can mitigate and manage ML/FT risks related to this sector, including the risks arising from the use of NPPS, please see section 3 “Mitigating Risks.”2.1.6. Nesting
Nesting is a form of intermediation that presents specific risks. In most Correspondent Banking Relationships that involve nesting, the respondent financial institution is not aware of individual transactions ordered by the ultimate customer; instead, the respondent sees bulk activity in the correspondent’s account that represents aggregate customer orders and perhaps also proprietary transactions by the correspondent. As a result, the transaction is intermediated because the respondent cannot see—nor assess the risk of— the original customer.
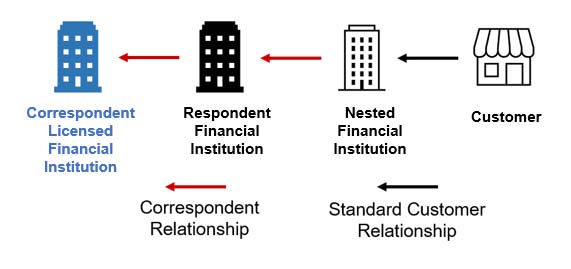
Although nesting can occur in the context of any financial service, some features of the Payment Sector— the long payment chains and the involvement of multiple parties—can increase the likelihood that nesting will take place. In particular, some Payment Sector participants specialize in providing financial services to dubious merchants or customers who would be rejected by larger financial institutions. A participant servicing these customers, frequently offering merchant acquiring or payment aggregation services, will establish a nested relationship with a third participant that in turn has a Correspondent Banking Relationship with a bank. Although all the parties involved must and may claim to perform appropriate merchant due diligence, in practice, the risk may be that the bank is relying on its correspondent, which is in turn relying on the nested financial institution, with the first two parties not having full visibility into the nested financial institution’s customer base or due diligence practices.
2.1.7. Use of Agents and Affiliates
Payment Sector participants often interact in a dense web of agency and affiliate relationships, with each participant playing a defined role. A large number of entities involved in the NPPS, in particular when involving several countries, may increase the ML/FT risk.For example, entities involved in the provision of SVF through a prepaid card scheme could include:5• The issuer of the SVF, such as the issuer of prepaid cards, who is accountable to the customer for holding the funds they have loaded into the SVF (issuers are often banks that maintain program funds in a single program account); • The merchant acquirer (or acquirers), who establishes a direct relationship with merchants, distributes and maintains the payment gateway, collect funds on their behalf, and distributes them to merchants; • The program manager, who operates the network and provides services to the issuer (because all program funds are generally maintained in a single account, program managers often maintain the electronic records that track the “movement” of funds into and out of customer’s individual wallets); • The retailer, who sells SVF devices like prepaid cards to customers; • The network operator, who maintains the link between merchants’ point of sale devices, or other payment gateways, and the program manager; and • Persons, who act as agents for the scheme, such as by accepting cash in exchange for topping up wallet balance.
Another example includes the provision of mobile payment services. The roles of Payment Sector participants depend largely on the business model of the mobile payment service. Furthermore, various roles may be carried out by a single entity or through agents. Entities involved in the provision of mobile payments may include the following:• The network operator, who provides the platform to allow access to the funds through a mobile phone. • The distributor (including retailer), who sells or arranges for the issuance of funds on behalf of the issuer to customers. • The issuer of the SVF, or the electronic money issuer, who issues electronic money, which is defined here as a record of funds or value available to a customer stored on a payment device, such as a prepaid card or mobile phone.
This interplay between different entities can lead to risks resulting from intermediation as discussed above. But it can also give rise to risks when the participating entities have not assigned clear responsibility for compliance with AML/CFT requirements. The PPS risk’s exposure may then be dependent on multiple actors who may have a deficient understanding of AML/CFT obligations. For example, in the prepaid card scheme described above agents could facilitate money laundering by accepting large volumes of cash and breaking the value of the deposit up across several wallets, thus avoiding scrutiny related to large cash deposits. The entities acting as merchant acquirers could be aware that the merchants are providing illegal goods or services or are fraudulent, but conceal this knowledge in order to continue to receive fees related to transactions involving the merchants in its network.The risks created by the use of agents and affiliates increase when agents and affiliates are responsible for sensitive steps in the system (customer or merchant onboarding, or cash acceptance) and when there are multiple agents or affiliates between the customer and the ultimate provider of payment services. For example in card schemes, merchant acquirers will frequently work with contractors who identify merchants and bring them to the acquirer in return for a fee. Depending on the relationships involved, the financial institution that maintains the merchant accounts may not have any actual direct contact with and have a limited visibility of the merchant, as the relationship is intermediated through the merchant acquirer and also the merchant acquirer’s contractor. Since contractors do not get paid unless the financial institution accepts the merchant as a customer, they may be incentivized to help the merchant conceal the true nature of its business.5 Please note that one entity can hold various roles related to the provision of SVF (e.g., an issuer of the SVF can also be a program manager). The risk is extended where different agents are involved in the provisioning of a prepaid card.
2.1.8. Merchant Risks
All merchants accept payments in one form or another, and most merchants today are at least considering integrating NPPS into their financial arrangements. On the other end of the spectrum, NPPS lower the barriers for merchants to access financial services, making it easier to start and operate a small business, particularly in the e-commerce sector. These lower barriers to entry however can also create risks when merchants are not properly vetted. Globally, Payment Sector participants including providers of NPPS have been abused by or directly complicit with merchants who offer fraudulent or illegal goods or services, or whose business models pose reputational risks to financial institutions. These can for example include traffickers in narcotics who disguise their transactions as financial activity related to a supposedly legitimate small business. They can also include businesses that are legal in some jurisdictions but not others (such as gambling websites) and seek to accept payments from customers resident in jurisdictions where the business is illegal. Finally, they may include sites that are legal in many jurisdictions but that pose reputational risk, and that are therefore outside a financial institution’s risk appetite, or online marketplaces that do not thoroughly police their merchants and thus could themselves be abused by illicit actors.
Any factors—particularly intermediation, nesting, and the use of agents and affiliates—that prevent a financial institution from understanding exactly what merchants or what types of merchants it is serving when it provides a PPS, increase the risks. Risks may be higher in cross-border networks, as businesses may be legal in some jurisdictions and illegal in others, while customers can use the PPS to purchase services that would be illegal in their jurisdiction. Relying on third parties to conduct customer due diligence (CDD) on merchants can also increase risk if the relationship is not well-governed.
2.2. ML/FT Risks for LFIs Providing Services to Payment Sector Participants
Many traditional LFIs, including banks, are full participants in the Payment Sector. Banks serve for example as issuers and acquirers in credit, debit, and prepaid card schemes, and are actively involved in developing new payment methods to better serve their customers. When banks play such roles, they are directly exposed to the determinants of risk discussed in section 2.1 above, and should thus conduct appropriate CDD on all Payment Sector participants. Banks and any other LFIs that offer services to other Payment Sector participants, or have customers who use these services, are exposed to specific forms of risk that include:
2.2.1. Correspondent and Correspondent-Type Risk
Because large-scale national clearing and settlement systems are often opened only to banks and other depository institutions, the majority of retail payments will ultimately pass through a bank generally as part of batch settlement. In order to facilitate this activity, non-bank financial institutions involved in payments, as well as unregulated Payment Sector participants, generally maintain deposit accounts with banks. These accounts can be used to safeguard customer funds (for example funds that have been deposited with a prepaid scheme) or to aggregate customer funds before disbursing them directly to customer’s account (for example when a merchant acquirer aggregates multiple payments to a merchant partner before disbursing them in a single transfer). Correspondent Banking Relationships in which the correspondent’s customers’ funds flow through an account held at the respondent financial institution are particularly high risk, because they expose the respondent institution directly to any potentially illicit activity in which the correspondent’s customers are engaged. Because banks that offer services to correspondents have limited information on these transactions, they are reliant on the correspondent to implement an effective AML/CFT program. Please see section 3.4.2 for the respective preventive measures.
2.2.2. Other Risks Related to Intermediation
Even banks that view themselves as having limited to no exposure to NPPS may in fact have indirect exposure through customers who link their bank accounts to payment apps, or use their bank accounts to fund SVF accounts or wallets (or withdraw funds received in such wallets to their accounts), or withdraw funds as cash and use it to purchase other prepaid instruments. Account activity of this type poses unique challenges for account and customer surveillance, because frequently the bank will be aware only of the immediate source or destination for the transaction, rather than the entire transaction chain. This can allow customers to deliberately thwart transaction monitoring programs and prevent the bank from understanding and assessing the activity on the customer’s account to determine whether it is in fact in line with the customer profile. Examples of how intermediation can limit a bank’s ability to identify suspicious or unusual behavior include:• Many banks have automated transaction rules designed to identify possible unlicensed money transfer activity by alerting on accounts that receive multiple small deposits from different sources, followed by a single large cross-border transaction. A customer could thwart this surveillance by having associates deposit the funds to be transferred in an SVF wallet, and then moving those funds to a linked bank account in order to execute the cross-border transfer. From the bank’s perspective, it would appear that the customer received only one deposit. Relatedly, the provider of SVF could not know that the funds were ultimately transferred across borders. • Many banks use watchlists to identify transactions that may be illegal or in violation of bank policy, such as the use of gambling websites. A customer seeking to evade these restrictions could use a foreign payment app linked to their account to purchase the assets; this transfer would likely appear on the bank’s records as a debit in favor of the operator of the payment app. The operator, in turn, may not be responsible for enforcing the laws of the jurisdictions where its foreign customers are based. It is therefore important for banks to identify foreign payment apps in order to appropriately assess the risks of the transactional activity. • A customer that generates a high quantity of illicit proceeds in cash can evade surveillance the bank applies to cash deposits by depositing the cash with a provider of NPPS (including both SVF and any other payment app that accepts cash inputs) and then withdrawing the funds from the payment service to his/her linked bank account.
2.2.3. Risks Related to Outsourcing
Banks often serve as the backbones of PPS such as credit, debit, and prepaid schemes without serving as the administrator or governing body of the scheme. In these situations, banks provide their reputation, stability, ability to hold deposits, and access to national payment systems while program administrators actually manage the movement of funds throughout the scheme. Because program operators have more direct contact with customers and more insights into the movement of funds, banks involved in these schemes often outsource CDD and other elements of the AML/CFT program to the program operators. But as banks continue to be exposed to funds involved in the program, they remain responsible for implementing an effective and compliant AML/CFT program, even if transactions flow through third parties that may or may not be subject to AML/CFT requirements. LFIs should therefore adopt policies to mitigate risks arising from reliance on outside service providers, including ones that operate in high-risk countries. Where roles and responsibilities are not clearly assigned, or where the program administrator does not implement an effective program, illicit actors can exploit the cracks in the program, and the bank and the program operator together will likely be less effective than if either party were operating alone. In such cases, LFIs should maintain a contingency arrangement as necessary.
3. Mitigating Risks
LFIs, whether they are primarily Payment Sector participants or have more limited exposure, are expected to take a risk-based approach to mitigating and managing ML/FT risks related to this sector, including the risks arising from the use of NPPS. A risk-based approach means that risk mitigation should begin with, and be based on, an appropriate assessment of the LFI’s payments-related risks. This assessment should in turn be reflected in the design and operation of the LFI’s AML/CFT program, including but not limited to the particular program elements discussed below, so that the LFI devotes greater resources and attention where risks are higher.
The sections below discuss how LFIs can apply specific preventive measures to mitigate and manage their payments-related risk. Sections 3.1-2 and 3.5-7 apply to all LFIs. Section 3.3 describes preventive measures recommended for LFIs that provide PPS directly to customers (including both consumers and merchants, or payers and payees), and section 3.4 for LFIs that provide services to other Payment Sector participants. The controls discussed should be integrated into the LFI’s larger AML/CFT compliance program and supported with appropriate governance and training. It is not an exhaustive discussion of all AML/CFT requirements and LFIs should continuously consult the UAE legal and regulatory framework currently in force.
3.1. AML/CFT Obligations under CBUAE Regulations
The CBUAE regulatory framework clearly state expectations for compliance with AML/CFT obligations. In addition to this guidance, LFIs including non-bank payment service providers should carefully review all the relevant regulations issued by the CBUAE, which provide a comprehensive coverage of all payment products, services, and systems that are issued, provided and/or operated in the UAE, to ensure they fully understand and comply with their obligations.
3.1.1. Providers of Stored Value Facilities
In November 2020 the CBUAE issued the Stored Value Facilities (SVF) Regulation (Circular No. 6/2020 issued by Notice 4834/2020). Under its Article 14, all licensees must comply with the existing legal obligations and regulatory requirements for AML/CFT of the CBUAE and address ML/FT risks through appropriate preventive measures to deter abuse of the sector as a conduit for illicit funds, detect ML/FT activities, and report any suspicious transactions to the UAE Financial intelligence Unit (UAE FIU). Among their detailed regulatory obligations, the licensees must assess the risk level of business relationships and undertake periodic risk profiling and assessment of products based on the AML/CFT requirements.
3.1.2. Retail Payment Services and Card Schemes Regulation
In July 2021 the CBUAE issued the Retail Payment Services and Card Schemes Regulation (Circular No. 15/2021 issued by Notice 3603/2021). Under its Article 12, payment service providers must comply with the relevant UAE AML/CFT laws and regulations and address ML/FT risks through appropriate preventive measures to deter abuse of the sector as a conduit for illicit funds, detect ML/FT activities, and report any suspicious transactions to the UAE FIU. Among their detailed regulatory obligations, the licensees must conduct business relationship-specific risk assessments and undertake periodic risk profiling and assessment of retail payment service users based on AML/CFT requirements. In addition, under Article 18.14, card schemes must report transactions to the UAE FIU when there are suspicions, or reasonable grounds to suspect, that the proceeds are related to a crime, or to the attempt or intention to use funds or proceeds for the purpose of committing, concealing or benefitting from a crime.
3.1.3. Large Value and Retail Payment Systems Regulations
In March 2021 the CBUAE issued the Large Value Payment Systems Regulation (Circular No 9/2020 issued by Notice 1410/2021) which covers clearing and settlement systems designated primarily to process large-value and/or wholesale payments typically among financial market participants or involving money market, foreign exchange or many commercial transactions. In tandem, the CBUAE issued the Retail Payment Systems Regulation (Circular No. 10/2020 issued by Notice 1408/2021) which covers fund transfer systems and related instruments, mechanisms, and arrangements that typically handle a large volume of relatively low-value payments in such forms as cheques, credit transfers, direct debit, card payment transactions or a regulated medium of exchange. Among their detailed regulatory obligations, all licensees are required to comply with any instructions issued by the CBUAE and any relevant international standards.
3.2. Risk Assessment
Under Article 4 of the AML-CFT Decision, LFIs are required to identify, assess, and understand the ML/FT risks to which they are exposed and how they may be affected by those risks, in order to determine the nature and extent of AML/CFT resources necessary to mitigate and manage those risks. In addition, under Article 23 of the Decision, LFIs are required to identify and assess the ML/FT risks of that may arise when developing new products and new professional practices, including means of providing new services and using new or under-development techniques for both new and existing products. An appropriate risk assessment should consider all the PPS that an LFI provides, and the LFI’s direct relationships to Payment Sector participants, both domestic and foreign.When assessing its direct exposure to the Payment Sector, whether in the form of PPS it offers, or relationships it maintains with other participants, the LFI should consider the risk factors discussed in section 2 above. The risk assessment should take into consideration:• Movement of Funds. What are the financial flows through the PPS and through the LFI’s accounts? What is the speed of transactions? Is there a cap on transaction value? Is there a daily, weekly, or monthly cap on the volume of transactions? Is the payment service in question closed loop or open loop? Can single users open multiple accounts?
• Mode of Funding: How do users fund their accounts and make withdrawals, and is funding permitted prior to customer verification?
• Peer-to-Peer Payments. Does the PPS allow users to conduct peer-to-peer transfers, or can they only send transfers to merchants/from customers? How is this restriction implemented and enforced?
• Cross-Border Movement. Does the PPS permit funds to move across borders and to high-risk countries through relationships with foreign financial institutions? Can users access the PPS when they are outside the UAE? Does the service support multiple currencies?
• Regulatory Status. Is the PPS that the LFI provides a regulated activity in the UAE and in all jurisdictions where it is provided?
• Use of Agents and Affiliates. How many entities are involved in delivering the PPS? How open is the network supporting the PPS? Does it include entities that are not regulated as LFIs—for example convenience stores that accept cash in return for topping up account balance? What is the role of each player in the system, and are responsibilities clearly defined in governance documents?
• Intermediation. How much visibility does the LFI have into payment activity taking place through the PPS? Can the LFI identify the ultimate payer and payee for all transactions? How many entities are in the payment chain?
• Controls. Does the PPS integrate appropriate features that contribute to managing the risk created by the factors listed above, such as by performing a robust customer verification process? These can include both the AML/CFT-specific features discussed in section 3.3 below and measures related to cybersecurity and counter-fraud.
Where LFIs, particularly banks, provide services such as deposit accounts to Payment Sector participants, they should also consider the following in assessing the risk of the relationship:• Nature of the Relationship: What products or services does the LFI provide to the participant? Does the relationship involve direct exposure to the funds of the participant’s customers? Is the sector participant using the relationship to facilitate activity by other Payment Sector participants?
• Regulatory Status: Is the participant required to be licensed in the UAE, its home jurisdiction, and all jurisdictions where it operates? Is it subject to AML/CFT requirements in all jurisdictions that are at least as stringent as those imposed in the UAE?
• Relationship Governance: Are AML/CFT responsibilities within the relationship clearly defined? Does the LFI outsource some aspects of AML/CFT program implementation to the Payment Sector participant?
The risk assessment should also consider the LFI’s indirect exposure to the Payment Sector through its customers, who may connect their account with an LFI to a variety of PPS, or may fund their account by using such PPS. Because many payment service providers use existing domestic or international payment systems to execute transfers on behalf of their customers, an LFI may not be aware that its customers are using such services nor able to prohibit their use or detect payments activity in customer’s accounts. LFIs should therefore consider a variety of tools to assess their indirect exposure to this sector. These may include:• applying appropriate level of due diligence and asking questions during the CDD process to obtain all relevant information;
• administering customer surveys to better understand customer’s interest in and use of payment services; and
• utilizing watchlist-based screening over a sample period.
When LFIs have a sense of the most common PPS their customers use, they should assess the risk these services and products pose, considering the factors discussed above, including the involvement of high-risk countries and the extent of exposure. These assessments should in turn be reflected in the LFI’s inherent risk rating. In addition, the LFI’s controls risk assessment should take into consideration the strength of the controls that the LFI has in place to mitigate the risks posed.3.3. Preventive Measures for LFIs Providing Products and Services Directly to Customers
Under Article 4(2) of the AML-CFT Decision, all LFIs must implement an AML/CFT program designed to manage the risks identified in their risk assessment that should include:
3.3.1. Customer Due Diligence, Enhanced Due Diligence and Ongoing Monitoring
Under Article 5 of the AML-CFT Decision, LFIs should conduct CDD before or during the establishment of the business relationship or account, or before executing a transaction for a customer with whom there is no business relationship. Payment Sector participants, including providers of SVF, retail payment services, and card schemes, generally establish relationships with their customers rather than treat all customers as occasional or walk-in customers. In these scenarios, LFIs must perform, no matter the customer type, all the elements of CDD required under sections 2 and 3 of the AML-CFT Decision, which include customer identification and verification, beneficial owner identification, understanding of the nature of the customer’s business and purpose of the business relationship, and ongoing monitoring. CDD, and where necessary enhanced due diligence (EDD), are the core preventive measures that help LFIs manage the risks of all customers, particularly higher-risk customers.In addition to these mandatory elements, LFIs should consider the following additional elements of CDD that are particularly important in the context of NPPS:• User identification and verification. Many, if not most, NPPS involve the use of digital as opposed to face-to-face methods of onboarding and identifying customers (a.k.a. “electronic Know Your Customer,” or “e-KYC”). Digital delivery of services is increasingly common, but can present higher risks when LFIs do not take appropriate steps to ensure that they fully understand the customer and that the person using the services is in fact the identified customer. In particular, when verifying the Emirates ID card (either physically or by way of digital or e-KYC solutions) LFIs must use the online validation gateway of the Federal Authority for Identity, Citizenship, Customs & Port Security, the UAE-Pass Application, or other UAE Government supported solutions, and keep a copy of the Emirates ID and its digital verification record. Where passports, other than the Emirates ID are used in the KYC process, a copy must be physically obtained from the original passport which must be certified (i.e. certified copy) as “Original Sighted and Verified” under the signature of the employee who carries out the CDD process and retained.
• Use of IP addresses and geographical (spatial and temporal) locators. As discussed above, payment services that are internet-based or accessible through smartphones can allow customers to access financial services no matter where they are in the world. LFIs are of course free to allow their customers to access their services while outside the UAE, but should take advantage of geographical location tools at both the onboarding and the ongoing monitoring stages to ensure that they understand the geographic risk they might be exposed to by their customers. This can include:
o Requiring additional authentication or verification when a customer accesses the service from an IP address or device different from the one used at onboarding, or from a different country and/or time zone than the customer’s stated country of residence.
o Reviewing the customer’s log-in locations during CDD refresh to identify any suspicious log-in or movement patterns (for example, high numbers of transactions taking place when the customer is near a border with a high-risk country where the PPS is blocked).
• SVF due diligence: Risk mitigating measures should include as per Article 14.4 of the SVF Regulation: (a) the application of limits on the maximum storage values, cumulative turnover or transaction amounts; (b) disallowing higher risk funding sources; (c) restricting the SVF product being used for higher risk activities; (d) restricting higher risk functions such as cash access; and (e) implementing measures to detect multiple SVF accounts/cards held by the same Customer or group of Customers.
• Merchant due diligence. Payment Sector participants that deal directly with merchants (whether as providers of SVF or card schemes, or conducting merchant acquisition or payment aggregation) may have two main classes of customers: consumers and merchants. It is important to remember that merchants who use the service are customers of the LFI and that merchants that may engage in deceptive or fraudulent business practices or use their legitimate business as a cover for criminal activities, can expose the LFI to extremely high ML/FT risk. Merchants should therefore be subject to CDD designed to understand the nature of their business and the expected transaction volumes. LFIs should understand the merchant’s current financial and payments operations and in particular ascertain why the merchant is seeking a new provider of financial services, as fraudulent merchants may move from LFI to LFI seeking to conceal their activities. Merchants operating in higher-risk sectors, and those that are cash-intensive businesses, are likely to require EDD that could involve performing a periodic site visit of the merchant’s place of business. For more information, please consult the CBUAE’s Guidance for LFIs providing services to the Real Estate and Precious Metals and Stones sectors, and Guidance for LFIs providing services to Cash-Intensive Businesses.
As per Article 7 of the AML-CFT Decision, all customers must be subject to ongoing monitoring to make sure that CDD information on file is accurate, complete and up-to-date and to ensure that transactions conducted are consistent with the expected customer profile. To support this process, LFIs should apply solutions that ensure the accuracy and completeness of their data. It also may be appropriate to include non-standard elements of monitoring to reflect the risks of payments customers, such as geographic and IP-address monitoring discussed above, and the monitoring of the balance between peer-to-peer and merchant payments in a customer’s account. For merchant relationships, ongoing monitoring should include an examination of the number of ‘chargebacks’ or refunds the LFI has had to award to customers of the merchant, as well as any customer complaints the LFI has received. Where a merchant generates a large number of customer complaints or refund requests, or none at all, it may be a sign that it is operating a fraudulent business.3.3.2. Controls
In line with their risk appetite and AML/CFT program, LFIs should develop controls that are commensurate with the nature and size of their business to enable them to manage the risks identified. Effective controls are those designed to minimize or eliminate those aspects of the PPS and NPPS that make them most attractive to illicit actors as discussed in section 2 above. LFIs should in particular consider:• Geographical limits. LFIs should strongly consider using IP addresses and smartphone geolocation capabilities to prevent customers accessing PPS from high-risk countries. There are a number of sources that LFIs can use to develop a list of high-risk countries, jurisdictions, or regions. LFIs should consult any publications issued by the National Anti-Money Laundering and Combating the Financing of Terrorism and financing of Illegal Organizations Committee (NAMLCFTC)6, the UAE Financial Intelligence Unit (UAE FIU), and the FATF. LFIs may also use public free databases such as, for example, the Basel AML Index7 or the Transparency International Corruption Perceptions Index.8 LFIs should not solely rely on public lists, however, and should consider their own experiences and the nature of their exposure to each jurisdiction when assessing the risk of that jurisdiction. LFIs should be aware, however, that given the widespread availability of Virtual Private Network (VPN) services, simply using IP address-based screening is not likely to be effective in preventing access to their service from specified areas. LFIs that use this control should make sure their systems are designed to detect VPN usage.
• Transaction limits. Smaller transactions are not without illicit finance risk, but from the perspective of materiality, transaction and volume limits (daily, weekly, monthly, etc.) can decrease an LFI’s exposure to illicit payments and also make the PPS overall less attractive to illicit actors.
• Funding constraints. Requiring customers to fund their accounts and to withdraw funds using only transfers from regulated domestic financial institutions can help protect PPS from the risks related to cash and ensure that the customer will be subject to CDD and monitoring.
• Multi-factor authentication. Requiring customers to provide a One-Time Password (OTP), or answer a phone call, or prompt on their smartphone when logging into an internet-based PPS can help prevent the misappropriation of customer funds by hackers. With regard to the OTP, all banks are required to include specific information in the messages that contain an OTP (full transaction amount, detailed beneficiary merchant name and website and a dedicated telephone number for customers to report suspected fraudulent activity). Banks are also required to ensure that card acquirers and issuers assist them to provide the additional OTP information as needed.9
6 Available at: namlcftc.gov.ae/en/more/jurisdictions/
7 Available at: baselgovernance.org/basel-aml-index
8 Available at: transparency.org/en/cpi/2020/index/nzl
9 Notice 4892/2021 issued by the CBUAE to all Banks in October 2021 regarding “One-Time Password (OTP) for card transactions”.3.3.3. Wire Transfers Requirements
Articles 27-29 of the AML-CFT Decision contain specific requirements with regard to information that LFIs must collect, and transmit with the wire transfer, when conducting an international wire transfers as well as specific obligations related to domestic wire transfers. In addition, Guidance on CDD measures concerning wire transfers is laid down in section 6.3.2 of the Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations for Financial Institutions. It is important to note that since many Payment Sector participants qualify as financial institutions, the applicability of these requirements is wide-ranging.
3.4. Preventive Measures for LFIs Providing Services to other Payment Sector Participants
3.4.1. Customer Due Diligence, Enhanced Due Diligence and Ongoing Monitoring
As mentioned above, LFIs must conduct appropriate CDD on all customers, regardless of their type or sector. The majority, if not all, of Payment Sector participant customers will be legal persons for which LFIs should conduct CDD as required by Articles 8 and 9 of the AML-CFT Decision. In particular, under Article 9 of the AML-CFT Decision, LFIs are required to identify the beneficial owners of a legal person customer by obtaining and verifying the identity of all individuals who, individually or jointly, have a controlling ownership interest in the legal person of 25% or more, and where no such individual meets this description, the LFI must identify and verify the identity of the relevant individual(s) holding the senior management position in the entity. For more information, please consult the CBUAE’s Guidance for Licensed Financial Institutions providing services to Legal Persons and Arrangements. LFIs should ensure that their contractual agreements with Payment Sector participant customers ensure that the LFI can access necessary information in a timely fashion. If LFIs cannot access this information in accordance with timelines laid out in its policies, they should consider restricting and ultimately terminating the relationship.Furthermore, as per Articles 8.3 and 4 of AML-CFT Decision, for all customer types, LFIs are required to understand the purpose for which the account or other financial services will be used, and the nature of the customer’s business. This step requires the LFI to collect information that allows it to create a profile of the customer and of the expected uses to which the customer will put the LFI’s products and services. In the context of payments, the LFI must understand whether and how its services are being used by its Payment Sector participant customer to facilitate provision of the PPS to its customer (Payment Sector participant customers may also be transacting on a proprietary basis). This should include a determination of whether nesting will take place. If the LFI prohibits nesting, it should make that prohibition clear to the customer.In addition to the standard required CDD elements of Sections 2 and 3 of the AML-CFT Decision, LFIs should collect all the information necessary to risk-rate the Payment Sector participant customer considering the risk factors described in section 3.2 above and whether aspects of the customer profile require EDD. LFIs should also consider the following steps to gain a more detailed understanding of the customer’s business in order to be sure that they fully understand it:• Review the customer’s promotional materials, including its website, to understand its target customers and the services it purports to offer.
• Understand how the customer provides payment services, the other participants it works with to do so, and whether it uses agents or affiliates.
• Requiring the customer to identify its major merchant customers by providing information such as the merchant’s name, principal business activity, geographic location, and transaction volume, and use public records searches or information provided by the customer to determine whether these merchants are operating a legitimate business.
• Visiting the customer’s headquarters and business operations center and evaluating the customer’s AML/CFT controls.
• Reviewing public databases to ensure that the customer, its beneficial owners, and its senior management have not been subject to law enforcement actions.
Under Article 7 of the AML-CFT Decision, all customers must also be subject to ongoing monitoring throughout the business relationship. Changes in the design or structure of a PPS, as well as changes in a Payment Sector participant’s customer base (including both the consumer and merchant customer base), can have a major impact on the overall risk associated with the Payment Sector participant. Ongoing monitoring of the customer relationship should be sufficiently rigorous to identify when such changes have taken place, as well as any other changes that impact the customer’s risk rating, and should be conducted at a frequency appropriate to the customer’s risk and the materiality of its transactions. Ongoing monitoring should also include a review of the customer’s transactional activity to determine whether it is in line with expectations established at onboarding and with activity during the previous review period. Sharp or substantial changes in activity may have a fully legitimate cause, such as growth in the customer’s user base, but LFIs should still ensure they understand the reasons for these changes.3.4.2. Correspondent Due Diligence
Article 25 of the AML-CFT Decision sets out specific mandatory requirements for LFIs entering into a Correspondent Banking Relationship or any similar relationship, no matter the nature of their customer, which include the following:• Refrain from entering into or maintaining a Correspondent Banking Relationship with shell banks or an institution that allows their accounts to be used by shell banks;
• Collect sufficient information about any receiving correspondent banking institution for the purpose of identifying and achieving a full understanding of the nature of its business and to make available, trough publicly available information, its reputation and level of control, including whether it has been investigated;
• Evaluate the AML/CFT controls applied by the receiving institution;
• Obtain approval from senior management before establishing new Correspondent Banking Relationship; and
• Understand each institution’s AML/CFT responsibilities.
In the context of Correspondent Banking Relationships with Payment Sector participants, LFIs should conduct correspondent due diligence that reflects the unique risks and features of those relationships. As discussed above, in the case of extended, intermediated transaction chains such as those frequently seen in the Payment Sector, each LFI involved is ultimately responsible for monitoring all transactions processed or conducted through the LFI, using the information available to it. Thus, LFIs should be aware of intermediated risk posed by Payment Sector participants—including providers of SVF, retail payment services, and card schemes—that access banking services through their accounts with an LFI. As a result, LFIs should in particular consider:• Regulatory status. As discussed above in section 2.1.4, jurisdictions take different approaches to regulating the Payment Sector, and not all Payment Sector participants that would qualify as financial institutions under the UAE’s legal and regulatory framework are required to be licensed and regulated in their home jurisdiction. When offering services to a foreign entity, LFIs should consider not just its licensing status under its home jurisdiction’s laws, but its licensing status should it carry out those same activities in the UAE. Where a foreign entity would require a license in the UAE, LFIs should treat it as a financial institution and subject it to correspondent due diligence. In these cases, LFIs should be particularly cautious to ensure that their correspondent implements an AML/CFT program that at least meets the requirements of the AML-CFT Law and Decision, and be aware that the correspondent is likely not supervised to ensure effective implementation of this program, increasing its risk.
• Merchant Due Diligence. LFIs should ensure that their Payment Sector participant customers conduct appropriate due diligence not just on customers but on merchants as well. LFIs should request and review the correspondent’s due diligence policies, procedures, and processes to determine the adequacy of its due diligence standards for merchant and consumer customers.
• Controls related to nesting. When an LFI offers services to a correspondent without knowing that nesting is taking place, it is unable to take appropriate measures to manage the risk of the nested relationship and, thus, likely to be exposed to higher risks. LFIs should therefore always understand all purposes for which the correspondent account will be used and ensure that the CDD and monitoring applied to the relationship will assess whether nesting is taking place.
• Testing and auditing. On a risk-basis, LFIs should consider taking active measures to test the correspondent’s AML/CFT program. This can include, at a minimum, reviewing the correspondent’s internal audit reports and can extend to requiring the correspondent to hire an external auditor, conducting on-site reviews and discussions at the correspondent’s premises.
3.5. Targeted Financial Sanctions
Article 16.1 of the AML-CFT Law and Article 60 of the AML-CFT Decision require LFIs to promptly apply directives issued by the Competent Authorities of the UAE for implementing the decisions issued by the United Nations Security Council under Chapter VII of the Charter of the United Nations. In furtherance of this requirement, the Cabinet Decision 74 of 2020 sets out the legal and regulatory framework in the UAE regarding Targeted Financial Sanctions (“TFS”), including the Local Terrorist List and the UN Consolidated List. For more information, please consult the Executive Office of the Committee for Goods and Material Subjected to Import and Export Control’s Guidance on TFS for Financial Institutions and Designated Non-financial Business and Professions and Virtual Assets Service Providers10, the CBUAE’s Guidance for LFIs on the Implementation of TFS, and Guidance for LFIs on Transaction monitoring and Sanctions screening11.
LFIs should take appropriate steps to develop, implement and regularly update an appropriate Sanctions Compliance Program in order to fulfil their obligation to comply with the related requirements that includes screening of customers and transactions. LFIs should be aware that, for all PPS they offer, they should have in place operational systems that ensure they can appropriately screen transactions related to those products or services. If they cannot conduct appropriate screening, they should not offer that product or service. LFIs should also ensure that the required information fields are created and duly transmitted throughout the payment cycle across the different PPS. LFIs should screen all information they have about a transaction, including any messages between users engaging in a peer-to-peer transfer that may have a non-uniform number of characters, use special characters, or present other challenges to screening systems.
An LFI that does not wish to have any exposure to high-risk countries will need to take additional measures to control where its customers use its products or services. Furthermore, sanctions risk assessments can change from time to time depending on where a customer is currently located. In intermediated correspondent relationships, LFIs should ensure that they fully understand their correspondents’ sanctions screening approaches, and should not process any payments for a correspondent unless they are entirely confident that the correspondent conducts appropriate screening. LFIs cannot rely on another LFI to fulfill screening obligations related to transactions on their own accounts or systems.
Furthermore, LFIs must sign up for the Integrated Enquiries Management System (“IEMS”) introduced by the UAE FIU to automate and facilitate the execution process of requests for information, implementing decisions of public prosecutions and any other type of ML/FT requests. Via this system, the FIU can make requests to all LFIs simultaneously with the goal of processing requests and providing results to law enforcement authorities more efficiently. For more information, please consult the IEMS User Guide published by the UAE FIU.12
10 Available at uaeiec.gov.ae/en-us/un-page#
11 Available at centralbank.ae/en/cbuae-amlcft
12 Available at uaefiu.gov.ae/media/jtdnttby/integrated-enquiry-management-system.pdf3.6. Transaction Monitoring and Suspicious Transaction Reporting
Under Article 16 of the AML-CFT Decision, LFIs must monitor activity by all customers to identify behaviour that is potentially suspicious and that may need to be the subject of a Suspicious Transaction Report (STR), a Suspicious Activity report (SAR) or other report types. When monitoring and evaluating transactions, the LFI should take into account all information that it has collected as part of CDD. In all cases, the appropriate type and degree of monitoring should appropriately match the ML/FT risks of the institution’s customers, products and services, delivery channels, and geographic exposure. For more information, please consult the CBUAE’s Guidance for Licensed Financial Institutions on Transaction Monitoring and Sanctions Screening.
As required by Article 15 of the AML-CFT Law and Article 17 of the AML-CFT Decision, LFIs must file a STR, a SAR or other report types with the UAE FIU when they have reasonable grounds to suspect that a transaction, attempted transaction, or certain funds constitute, in whole or in part, regardless of the amount, the proceeds of crime, is related to a crime, or is intended to be used in a crime. STR filing is not sim ply a legal obligation; it is a critical element of the UAE’s effort to combat financial crime and protect the integrity of its financial system. By filing STRs with the UAE FIU, LFIs alert law enforcement authorities about suspicious behaviour and allow investigators to piece together transactions occurring across multiple LFIs.
As discussed above, in the case of extended, intermediated transaction chains such as those frequently seen in the Payment Sector, each LFI involved is ultimately responsible for monitoring all transactions processed or conducted through the LFI, using the information available to it. Although LFIs cannot outsource their responsibility to report suspicious activity, they can outsource certain aspects of transaction monitoring. In the prepaid card scheme described in section 2.1.7, for example, the bank that offers the prepaid cards may outsource automated transaction monitoring to the program manager, which has more direct insight into individual transactions. The bank in this situation, and any LFI that outsources any elements of transaction monitoring, nevertheless retains ultimate responsibility for identifying and reporting suspicious transactions.
3.7. Governance and Training
The specific preventive measures discussed above should take place within, and be supported by, a comprehensive institutional AML/CFT program that is appropriate to the risks the LFI faces. Therefore, in addition to the mandatory governance and training requirements set forth in the AML-CFT Law and Decision, Payment Sector participants and LFIs providing them services should endeavor to incorporate the following considerations into the design of their governance frameworks and their training programs.• Clear allocation of AML/CFT responsibilities among LFIs. When a network of Payment Sector participants combine to deliver a payment service and execute transactions, risks arise when they do not have a clear understanding of each participant’s AML/CFT responsibilities. Allocating responsibilities is particularly important when some LFIs involved in a payment will not form a relationship with the ultimate customer or beneficiary. Card schemes should have a governing body, but this may not be a requirement for other Payment Sector participants depending on their role in processing payments. LFIs should understand the parties and their roles and responsibilities in the scheme and manage risks accordingly. Any LFI that provides payment services as part of a network should assume full responsibility for CDD. Furthermore, LFIs cannot rely on any other entities to implement elements of the AML/CFT program, such as the appointment of a compliance officer and the reporting suspicious transactions. Similarly, when a LFI provides services to a Payment Sector participant as part of a Correspondent Banking Relationship, they should also understand each party’s AML/CFT responsibilities and document them in the contract or other program documents. Understanding the parties’ respective AML/CFT responsibilities is a mandatory element of correspondent CDD under Article 25 of the AML-CFT Decision.
• Agent Governance and Training. Where a payment service or product relies on the use of agents for delivery, it is critical that they are appropriately trained to recognize red flags for illicit activity, and to carry out the elements of the AML/CFT program for which they are responsible. LFIs that use agents should have appropriate programs in place to manage them through effective governance arrangements that, among other measures, set clear requirements for terminating relationships if agents do not comply with the LFI’s policy. LFIs should provide training directly to agents and test their compliance on a regular basis. Where agents participate in sensitive activities, such as cash acceptance or onboarding, they should receive increased training and be subject to additional controls and testing.
• Employee Training. As with all risks to which the LFI is exposed, the AML/CFT training program should ensure that employees are aware of the risks of PPS, familiar with the obligations of the LFI, and equipped to apply appropriate risk-based controls. Training should be tailored and customized to the LFI’s risk and the nature of its operations. For Payment Sector participants that offer PPS as their primary business, employee training should be focused on payments-related risks. For LFIs that offer services to Payment Sector participants, employee training should cover payment risks as appropriate to the employee’s role and responsibilities as well as the LFI’s overall exposure to the sector.
Annex 1. Synopsis of the Guidance
Purpose of this Guidance Purpose The purpose of this Guidance is to assist the understanding and effective performance by Licensed Financial Institutions (LFIs) of their statutory obligations under the legal and regulatory framework in force in the UAE. Applicability This Guidance applies to all natural and legal persons, which are licensed and/or supervised by the CBUAE, in the following categories: national banks, branches of foreign banks, exchange houses, finance companies, stored value facilities, retail payment service providers, and card schemes. Understanding Risks ML/FT Risks of the Payment Sector Characteristics of the Movement of Funds: Products and Services (PPS) and New Payment Products and Services (NPPS)in particular are extremely attractive to illicit actors because of the rapid movement of funds between Payment Sector participants and across borders. The risks vary based on transaction speed, transaction limits, closed vs. open loop system, methods of funding and access to cash, payment transparency, ability for one person to create multiple accounts, non-face-to-face relationships, and use of virtual assets (the latter is addressed in a separate guidance to be issued by CBUAE). Peer-to-Peer Payments: NPPS allow participants to send money that will be instantly available to the beneficiary, reducing the need for trust in the relationship. The use of PPS for peer-to-peer payments creates risk for financial institutions because transactions can flow through third parties that may not be subject to AML/CFT requirements. Cross-Border Movement: Many NPPS can be used globally for making payments or transferring funds, thus introducing banks to new geographical exposure. Unlike cross-border wires, which carry full identifying information, banks will frequently only see the customer's transactions with the payment network itself, rather than their location or ultimate destination. Global Regulatory Gaps: Countries take a variety of approaches to regulating the Payment Sector and there is no one widely accepted classification of participants. And participants, as relatively new market entrants, may lack the experience, expertise, or commitment to apply fully effective preventive measures. Intermediation: A number of participants potentially involved in a single transaction. Intermediated transactions create risk because no regulated entity participating in the transaction has the visibility necessary to fully understand the transaction and the participants. Nesting: Nesting is a form of intermediation that presents specific risks. In most Correspondent Banking Relationships that involve nesting, the respondent financial institution is not aware of individual transactions ordered by the ultimate customer. Use of Agents and Affiliates: Payment Sector participants often interact in a dense web of agency and affiliate relationships. A large number of entities involved in the NPPS, in particular when involving several countries, may increase the ML/FT risk. The interplay between different entities can lead to risks from intermediation and also when the participating entities have not assigned clear responsibility for compliance with AML/CFT requirements. Merchant Risks: Globally, Payment Sector participants including providers of NPPS have been abused by or directly complicit with merchants who offer fraudulent or illegal goods or services, or whose business models pose reputational risks to financial institutions. Relying on third parties to conduct customer due diligence (CDD) on merchants can also increase risk if the relationship is not well-governed. ML/FT Risks for LFIs Providing Services to Payment Sector Participants Correspondent and Correspondent-Type Risk: Correspondent Banking Relationships in which the correspondenfs customers' funds flow through an account held at the respondent financial institution are particularly high risk, because they expose the respondent institution directly to any potentially illicit activity in which the correspondent's customers are engaged. Because banks that offer services to correspondents have limited information on these transactions, they are reliant on the correspondent to implement an effective AML/CFT program. Other Risks Related to Intermediation: Even banks that view themselves as having limited to no exposure to NPPS may have indirect exposure through customers who link their bank accounts to payment apps, or use their bank accounts to fund stored value facilities (SVF) accounts or wallets, or withdraw funds as cash and use it to purchase other prepaid instruments. Risks Related to Outsourcing: Banks often serve as the backbones of PPS such as credit, debit, and prepaid schemes without serving as the administrator or governing body of the scheme. Banks involved in these schemes often outsource CDD and other elements of the AML/CFT program to the program operators who have more direct contact with customers and insight to movement of funds. But Banks remain responsible for implementing an effective and compliant AML/CFT program. Mitigating Risks AML/CFT obligations under CBUAE Regulations In addition to this guidance, LFIs including non-bank payment service providers should carefully review all the relevant regulations issued by the CBUAE, which provide a comprehensive coverage of all payment products, services, and systems that are issued, provided and/or operated in the UAE, to ensure they fully understand and comply with their AML/CFT obligations. In 2020-2021 the CBUAE issued the SVF Regulation, the Retail Payment Services and Card Schemes Regulation, the Large Value Payment Systems Regulation, and the Retail Payment Systems Regulation. Risk Assessment An appropriate risk assessment should consider all the PPS that an LFI provides, and the LFI's direct relationships to Payment Sector participants, both domestic and foreign. When assessing an LFI's direct exposure to the Payment Sector, the LFI should consider the risk factors discussed in section 2 of the Guidance, such as the movement of funds, mode offunding, and peer-to-peer payments among others. Where LFIs provide services to Payment Sector participants, they should also assess the risk of the relationship as well as their indirect exposure to the Payment Sector through their customers. Preventive Measures for LFIs Providing Products and Services directly to Customers Customer Due Diligence, Enhanced Due Diligence and Ongoing Monitoring: LFIs must perform all the elements of CDD, which include customer identification and verification, beneficial owner identification, understanding of the nature of the customer's business and purpose of the relationship, and ongoing monitoring. In addition to these mandatory elements, LFIs should consider the following elements that are particularly important in the context of NPPS: user identification and verification, use of IP addresses and geographical (spatial and temporal) locators, and SVF and merchant due diligence. Controls: LFIs should develop controls that are commensurate with the nature and size of their business to manage the risks identified. LFIs should in particular consider geographical limits, transaction limits, funding constraints, and multi-factor authentication to minimize or eliminate those aspects of the PPS and NPPS that make them most attractive to illicit actors. Wire Transfers Requirements: The AML-CFT Decision contain specific requirements with regard to information that LFIs must collect, and transmit with the wire transfer, when conducting an international wire transfers as well as specific obligations related to domestic wire transfers (the Guidelines further contain CDD measures). Since many Payment Sector participants qualify as financial institutions, the applicability of these requirements is wide-ranging. Preventive Measures for LFIs Providing Services to other Payment Sector Participants Customer Due Diligence, Enhanced Due Diligence and Ongoing Monitoring: LFIs must conduct appropriate ODD on all customers, regardless of their type or sector (the majority, if not all, of Payment Sector participant customers will be legal persons). In this context, the LFIs should also consider a determination of whether nesting will take place. In addition to the standard required ODD elements, LFIs should collect all the information necessary to risk-rate the Payment Sector participant customer and evaluate whether aspects of the customer profile require EDD. All customers must also be subject to ongoing monitoring throughout the business relationship. Correspondent Due Diligence: In the context of Correspondent Banking Relationships with Payment Sector participants, LFIs should conduct correspondent due diligence that reflects the unique risks and features of those relationships. In the case of extended, intermediated transaction chains such as those frequently seen in the Payment Sector, each LFI involved is ultimately responsible for monitoring all transactions processed or conducted through the LFI, using the information available to it. LFIs should in particular consider regulatory status, merchant due diligence, controls relating to nesting, and testing and auditing of the correspondents AML/CFT program. Targeted Financial Sanctions LFIs are required to promptly apply directives issued by the Competent Authorities of the UAE for implementing the decisions issued by the United Nations Security Council under Chapter VII of the Charter of the United Nations and the requirements set by Cabinet Decision 74 of 2020 regarding Targeted Financial Sanctions. LFIs should be aware that, for all PPS they offer, they should have in place operational systems that ensure they can appropriately screen transactions related to those products or services. In intermediated correspondent relationships, LFIs should ensure that they fully understand their correspondents' sanctions screening approaches, and should not process any payments for a correspondent unless they are entirely confident that the correspondent conducts appropriate screening. Transaction Monitoring and Suspicious Transaction Reporting LFIs must monitor activity by all customers to identify behaviour that is potentially suspicious and that may need to be the subject of a Suspicious Transaction Report (STR), a Suspicious Activity report (SAR), or other report types. When monitoring and evaluating transactions, the LFI should take into account all information that it has collected as part of ODD. As discussed above, in the case of extended, intermediated transaction chains such as those frequently seen in the Payment Sector, each LFI involved is ultimately responsible for monitoring all transactions processed or conducted through the LFI, using the information available to it. Any LFI that outsources any elements of transaction monitoring retains ultimate responsibility for identifying and reporting suspicious transactions. Governance and Training Payment Sector participants and LFIs providing them services should endeavor to incorporate the following considerations into the design of their governance frameworks and their training programs: clear allocation of AML/CFT responsibilities among LFIs, agent governance and training, and employee training. When a network of Payment Sector participants combine to deliver a payment service and execute transactions, risks arise when they do not have a clear understanding of each participant's AML/CFT responsibilities. Any LFI that provides payment services as part of a network should assume full responsibility for CDD. When a LFI provides services to a Payment Sector participant as part of a Correspondent Banking Relationship, they should also understand each party's AML/CFT responsibilities and document them in the contract or other program documents. Guidance for Licensed Financial Institutions on the Risks Relating to Politically Exposed Persons
Effective from 1/8/20221. Introduction
1.1. Purpose of the Guidance
Article 44.11 of the Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations charges Supervisory Authorities with “providing Financial Institutions…with guidelines and feedback to enhance the effectiveness of implementation of the Crime-combatting measures.”
The purpose of this Guidance is to assist the understanding and effective performance by the United Arab Emirates Central Bank’s (“CBUAE”) licensed financial institutions (“LFIs”) of their statutory obligations under the legal and regulatory framework in force in the UAE. It should be read in conjunction with the CBUAE’s Procedures for Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations (issued by Notice No. 74/2019 dated 19/06/2019) and Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations for Financial Institutions (issued by Notice 79/2019 dated 27/06/2019) and any amendments or updates thereof.1 As such, while this Guidance neither constitutes additional legislation or regulation nor replaces or supersedes any legal or regulatory requirements or statutory obligations, it sets out the expectations of the CBUAE for LFIs to be able to demonstrate compliance with these requirements. In the event of a discrepancy between this Guidance and the legal or regulatory frameworks currently in force, the latter will prevail. This Guidance may be supplemented with additional separate guidance materials, such as outreach sessions and thematic reviews conducted by the CBUAE.
Furthermore, this Guidance takes into account standards and guidance issued by the Financial Action Task Force (“FATF”), industry best practices and red flag indicators identified by the FATF. These are not exhaustive and do not set limitations on the measures to be taken by LFIs in order to meet their statutory obligations under the legal and regulatory framework currently in force. As such, LFIs should perform their own assessments of the manner in which they should meet their statutory obligations.
This Guidance comes into effect immediately upon its issuance by the CBUAE with LFIs expected to demonstrate compliance with its requirements within one month from its coming into effect.
1 Available at centralbank.ae/en/cbuae-amlcft.
1.2. Applicability
Unless otherwise noted, this guidance applies to all natural and legal persons, which are licensed and/or supervised by CBUAE, in the following categories:
• National banks, branches of foreign banks, exchange houses, finance companies, stored value facilities, retail payment service providers, card schemes, registered hawala providers and other LFIs; and • Insurance and re-insurance companies, agencies, and brokers. 1.3. Legal Basis
This Guidance builds upon the provisions of the following laws:
1.4. Acronyms and Definitions
Heads of International Organizations (HIO): Natural persons who are or have been entrusted with the management or any prominent function within an international organization.
International Organizations: Entities established by formal political agreements between their Member States that have the status of international treaties; their existence is recognised by law in their member countries; and they are not treated as resident institutional units of the countries in which they are located. Examples of international organisations include the United Nations and affiliated international organisations; regional international organisations; military international organisations, and economic organisations.
Politically Exposed Persons (PEP): Natural persons who are or have been entrusted with a prominent public function in the UAE or any other foreign country such as heads of states or governments, senior politicians, senior government officials, judicial or military officials, senior executive managers of state owned corporations, and senior officials of political parties, and persons who are, or have previously been, entrusted with the management of an international organisation or any prominent function within such an organisation; and the definition also includes the following:
• Direct family members (of the PEP who are spouses, children, spouses of children, parents) • Associates known to be close to the PEP, which include: o Individuals having joint ownership rights in a legal person or arrangement or any other close business relationship with the PEP; o Individuals having individual ownership rights in a legal person or arrangement established in favor of the PEP.
Related Customers: Customers that are the direct family members of a PEP or the associates known to be close to a PEP.
2. Understanding Risks
Article 15 of the AML-CFT Decision and the FATF standards impose specific Customer Due Diligence (CDD) obligations on LFIs with respect to Customers that are Politically Exposed Persons (PEPs) which include the Direct Family Members or Associates Known to be Close to the PEPs. The AML-CFT Law and Decision give special attention to these customers because they are likely to expose LFIs to a heightened risk of money laundering, terrorism financing, and other illicit finance. The special requirements related to PEPs are not an indication that LFIs should avoid dealing with such customers. Instead, these requirements are meant to ensure that LFIs have done the due diligence necessary to fully identify, understand their customers and have made fully-informed decisions regarding whether or not to accept the customer or to continue the relationship. There are three sub-groups of PEPs:
• PEPs who are or have been entrusted with their prominent public position in the UAE are known as “domestic PEPs”; • PEPs who are or have been entrusted with their prominent public position in any other foreign country are known as “foreign PEPs”; and • PEPs who are or have been entrusted with the management or any prominent function within an international organization are known as “Heads of International Organizations (HIOs)”.
Customers that are PEPs, and transactions involving PEPs, receive special attention under the UAE legal and regulatory framework and the FATF standards because they bear a higher risk of involvement in certain proceeds-generating offenses: corruption, misuse or theft of public funds, and bribery. It is important to note that the majority of PEPs are law-abiding public servants and that no more than a small percentage of PEPs are involved in these offenses. Nevertheless, the risk is still higher than in the general population.
PEPs are at higher risk of involvement in these crimes because of the powers that come with their position or status. Most importantly, a PEP has power or influence over how government funds are spent, or over state action. PEPs may use their power or influence to directly enrich themselves, their family members, and their associates, by stealing or misdirecting government funds. Or they may sell their power or influence to illicit actors who are seeking to obtain a specific outcome, whether it is a lucrative contract, the passage of a regulation, or the transfer of government secrets.
The AML-CFT Decision also requires LFIs to perform the same specific due diligence on the direct family members and known close associates of a PEP. These individuals may not themselves have any direct power or influence over government actions, but they nevertheless present higher risks to LFIs as a result of their relationship with a PEP.
• PEPs, knowing that their financial transactions will be subject to scrutiny, may use family members or associates to carry out illicit transactions or collect illicit funds, in an attempt to hide their involvement in a transaction and their illicit gains. In many countries where corruption is an issue, PEPs themselves may nominally possess few assets, while their family members and associates openly display their wealth. • Illicit actors seeking to persuade a PEP to take certain actions may seek to achieve this goal by paying off the people close to the PEP, the PEP’s family members and close associates. For instance, a person seeking a government contract may pay a PEP’s spouse to “put in a good word for him or her” with the PEP, or to gain access to the PEP by inviting the contractor to the PEP’s home. These payments may be made with or without the knowledge or consent of the PEP.
Article 15 of the AML-CFT Decision also requires LFIs to identify those legal person and legal arrangement customers that have at least one beneficial owner who is a PEP (see sections 3.2.1 and 3.2.2 below). In this Guidance, customers that are the direct family members of a PEP, the known close associates of a PEP, or that are legal persons or legal arrangements with at least one beneficial owner who is a PEP will be referred to as “Related Customers.”
Although LFIs are required to apply special procedures for all PEPs and Related Customers, not all PEPs and Related Customers are equally high-risk. The sources of risk for a PEP are closely related to the risk that a PEP could have abused his or her position for financial gain. Some factors that can influence the risks of a particular PEP are:
• The PEP’s ability to control highly consequential outcomes. Certain roles are more likely to attract large-scale corruption. For example, a judge in a traffic court may be offered bribes, but these are likely to be lower in value than the bribes potentially offered to a judge who presides over the trials of organized criminal groups. • The authority and independence inherent in the PEP’s role or function. Where a PEP has greater authority or independent decision-making authority, he or she is more likely to be able to achieve outcomes that are beneficial to him/herself or his/her family or associates. • The access to funds inherent in the PEP’s role. A PEP that can control the disbursement of funds is likely to have more opportunities for engaging in embezzlement and self-dealing. • The nature of governance in the state or organization that has entrusted the PEP with a prominent function. Poor governance undermines transparency and accountability. Strong governance can help ensure that public officials are unable to use their office for gain, or are quickly caught if they do so. Governance is a broad category that includes the strength of anti-corruption laws, the vigor with which corruption is investigated and prosecuted, and the authority of independent public auditors. • The overall level of corruption in the state or organization that has entrusted the PEP with a prominent function. Where corruption is rife, public officials are unlikely to be entirely immune.
The sources of risk for a Related Customer can be divided into two broad categories:
• The risk of the PEP to which the Related Customer is connected (i.e. understanding the risk of the PEP and its characteristics). • The relationship between the Related Customer and the PEP (i.e. the type and strength of the relationship (e.g. the closer the relationship, the more likely the Related Customer is to share the PEP’s risk)). 3. Mitigating Risks
The AML-CFT Decision contains specific, mandatory requirements for managing risks related to PEPs. It is important for LFIs to be aware that the Decision imposes baseline requirements that are higher than for other types of customers. LFIs cannot choose to omit these requirements even when they consider that risks associated with a specific customer or transaction are low. This does not mean, however, that LFIs are not expected to take a risk-based approach to these customers. LFIs should implement the baseline controls described below as well as consider whether additional controls are necessary when even higher risks are present.
Furthermore, the sections below discuss how LFIs can apply the required specific preventive measures to identify, manage, and mitigate the risks associated with PEPs. It is not a comprehensive discussion of all AML/CFT requirements imposed on LFIs. LFIs should consult the legal and regulatory framework currently in force, the Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations for Financial Institutions, and the CBUAE issued Guidances for further information2. The controls discussed below should at the minimum be integrated into the LFI’s larger AML/CFT compliance program and supported with appropriate governance and training.
2 Available at centralbank.ae/en/cbuae-amlcft
3.1. Legal Requirements
Article 15 of the AML-CFT Decision requires LFIs to carry out specific mandatory due diligence measures on PEPs and Related Customers, in addition to the standard CDD required for all customers under its Section 3 (described in Articles 5-14). In line with FATF standards (Recommendation 12), Article 15 imposes on LFIs different requirements for foreign PEPs as opposed to domestic PEPs and HIOs. For foreign PEPs and Related Customers, LFIs must:
(a) Put in place suitable risk management systems to determine whether a Customer or the Beneficial Owner is considered a PEP (i.e. a foreign PEP, or the direct family member or known close associate of a PEP). (b) Obtain senior management approval before establishing a business relationship, or continuing an existing one, with a PEP (i.e. foreign PEP and Related Customers). (c) Take reasonable measures to establish the source of funds and wealth of Customers and Beneficial Owners identified as PEPs (i.e. foreign PEPs and Related Customers). (d) Conduct enhanced ongoing monitoring over such relationship (i.e. the relationship with a foreign PEP or Related Customers).
For domestic PEPs and HIOs and their Related Customers, LFIs must:
(a) Take sufficient measures to identify whether the Customer or the Beneficial Owner is considered one of those persons (see section 3.2.4). (b) Take the measures identified in (b), (c), and (d) when there is a high-risk business relationship accompanying such persons.
Like the FATF standards, article 15.2 of the AML-CFT Decision imposes special PEP-related requirements for certain insurance policies, although its requirements apply to a slightly broader range of policies. LFIs must take reasonable measures to determine whether the beneficiary, or the beneficial owner of a beneficiary, of a life insurance policy or of family takaful insurance is a PEP or a Related Customer. If identified as a PEP or Related Customer, LFIs must inform senior management before pay-out of those policies, or prior to the exercise of any rights related to them. LFIs must also thoroughly examine the overall business relationship, and consider filing a suspicious transaction report (STR), a suspicious activity report (SAR) or any other report types with the FIU where applicable (please see section 3.3.2 below).
3.2. Applying Legal Requirements
3.2.1. Classifying Customers as PEPs
The definition of PEP in the AML-CFT Decision specifically lists the following roles as persons who always qualify as PEPs:
• Heads of States or Governments; • Senior politicians; • Senior government officials; • Judicial officials; • Military officials; • Senior executive managers of state-owned corporations; • Senior officials of political parties; and • Persons who are, or have previously been, entrusted with the management of an international organisation or any prominent function within such an organisation.
However, as there is no exhaustive list of the positions that qualify an individual as a PEP globally, the above list is not exhaustive and LFIs should use their discretion in identifying PEPs, and develop risk-based policies and procedures to ensure they appropriately identify customers who are PEPs, or the family members or close associates of PEPs.
For example, LFIs should use discretion in determining whether a customer who is government official or manager of a state-owned corporation is sufficiently “senior” to qualify as a PEP under the definition of the AML-CFT Decision. Not all public sector employees are PEPs. For example, a civil servant who sorts mail at the post office is unlikely to be a PEP, and although any public employee can carry some level of corruption risk, in such cases the risk is not sufficiently high to warrant special procedures. This distinction is captured in the AML-CFT Decision’s definition of a PEP as a natural person who has been awarded a “prominent public function.” At the same time, the decision whether or not to treat a customer as a PEP cannot be based solely on the customer’s title, rank, civil service grade, or other similar factors. It is also important to be aware that “prominent” is not simply equivalent to ‘famous’ or ‘well-known,’ and that individuals may be “entrusted” with a public function in a wide variety of ways, including by appointment, election, and promotion through the civil service.
Furthermore, LFIs should also be aware that high risks of corruption can exist even when a customer is not immediately qualifying as a PEP per definition. For example, the heads of large trade unions and professional associations are likely to wield political power without having been appointed to those roles by a government or international organization. LFIs may decide, in terms of their own risk appetite, to treat such individuals as PEPs.
The determination of whether a customer is a PEP should therefore consider a number of factors, including, most importantly, whether the natural person currently holds, or has recently held, a role that gives him or her power or influence over decisions, policy or the disbursal of funds belonging to a government or an international organization. Factors to consider when making this determination include the nature of the political and governance system in the country or international organization where the customer holds his or her position; roles and responsibilities within that system; authority over government decisions and activities, and access to government funds and assets (whether directly or indirectly such as through the awarding of government contracts).
PEPs are always natural persons. However, LFIs should perform a PEP analysis on customers who are the beneficial owners of legal persons or legal arrangements. Depending on the customer’s ownership and control structure, it may also be appropriate to perform a PEP analysis on the customer’s senior managing officer or senior management. Where risks are higher, for example, in the case of companies with complex structure and complex trust arrangements, LFIs should consider identifying beneficial owners below the 25% threshold mandated by the AML-CFT Decision. For example, a PEP and his spouse and three children may each own 15% of a company. No single family member would have to be identified as a beneficial owner under UAE law, but when their ownership shares are added together the family clearly exercises control over the company. Such a company would likely need to be subjected to the EDD requirements discussed in section 3.2.6.
3.2.2. Classifying Customers as Related Customers
The AML-CFT Decision requires LFIs to treat the direct family members and close associates of PEPs as if they were PEPs themselves.
• Article 1 of the AML-CFT Decision defines direct family members of a PEP as the PEP’s spouses, children, spouses of children, and parents. • Article 1 of the AML-CFT Decision defines close associates of a PEP as:
o Natural persons having joint ownership rights in a legal person or arrangement or any other close business relationship with the PEP; and o Natural persons having individual ownership rights in a legal person or arrangement established in favour of the PEP.
The above-mentioned relationships should be viewed as a mandatory minimum, not as an exhaustive list of all relationships that may justify to treat a customer as a PEP. The link between the family member or the close associate with the PEP determine the level of risk. LFIs should take a risk-based approach and consider whether a relationship exists between their customer and the PEP that could be exploited or abused to obscure the PEP’s connection to illicit funds.
For example, an LFI may choose to also define as a direct family members any person in a relationship with a PEP, and, as close associates, partners, prominent members of the same political party or civil organization as the PEP; close friends or advisors; business partners or associates, especially those that share (beneficial) ownership of legal entities with the PEP, or who are otherwise connected (e.g. through joint membership of a company board) in accordance with FATF Guidance and the above mentioned definition.
Once an LFI has established that a qualifying relationship exists between a customer (or the beneficial owner of a customer) and a PEP, the LFI must treat the customer as a PEP (or as owned by a PEP). There is one important distinction, however, between a PEP and the direct family member or close associate of a PEP: the latter cannot transfer their status to their own family members and close associates. For example:
• General A is the head of the Air Force of a country. Mr. B, her son, is married to Mrs. B, a private citizen who owns a grocery store. General A is a PEP, and Mr. B and Mrs. B must be treated as PEPs because they are direct family members of General A.
• Mrs. B is the daughter-in-law of General A. Her brother, Mr. C, a lawyer in private practice, is not required to be treated as a PEP. Mr. C’s connection to the true PEP (General A) is too distant. Even though Mrs. B is treated as a PEP, Mr. C does not need to also be treated as a PEP merely because he is a sibling of Mrs. B.
LFIs should, however, apply EDD requirements and/or enhanced monitoring of the relationship if they have identified any high risks, such as concerns that the more distant family members or business associates of a PEP may be involved in corruption or any other sort of illicit activity, whether or not it involves the PEP.
Similarly:
• Mr. X is a prominent politician in a country who recently left office, but who may run for office in the future. Following his departure from office, Mr. X and Mrs. Y became cofounders of a real estate development company, with each owning 50% of the company. Due to Mr. X’s prominent function, the partnership has been extensively covered in the media. Mr. X is a PEP because of his recent past position. Mrs. Y must be treated as a PEP because she is a known close associate of Mr. X.
• Mrs. Y is also a 50% owner of an entirely separate business that manufactures cell phones. Mrs. Y’s co-owner of that business, Mr. Z, does not need to be treated as a PEP. As the business partner of a business partner of a PEP, his connection to Mr. X is too distant. LFIs should, however, apply EDD requirements and/or enhanced monitoring of the relationship if they have any concerns that the more distant family members or business associates of a PEP are involved in corruption or any other sort of illicit activity, whether or not it involves the PEP. 3.2.3. Time Limits of PEP Status
The definition of PEP in the AML-CFT Decision makes clear that a PEP does not cease to qualify as a PEP simply because they no longer hold a prominent public function (i.e. “Natural persons who are or have been entrusted with prominent public functions”). Nor does a Related Customer cease to require PEP treatment simply because the PEP to whom they are related no longer holds that position. A PEP’s risk (and, indirectly, the risk of a Related Customer) derives from the PEP’s power or influence over decisions, funds, or policy. Therefore, it may not be appropriate to continue to treat a customer as a PEP long after they have lost such power or influence. On the other hand, if PEP has amassed funds through corruption during his or her period in office, the PEP is likely to wait until being out of office to access or enjoy those funds. This means that the corruption risk remains even if a PEP has been out of office for a certain time.
Because each case is different it would not be appropriate for LFIs to apply a universal rule for determining whether a customer is no longer a PEP (e.g. one year after relinquishing the public position). Therefore, while LFIs may set a schedule to review PEP status, they should make a risk-based decision as to when sufficient time has passed for a customer to no longer be classified as a PEP. Factors to consider when making such a determination include:
• The seniority, prominence, and power inherent in the customer’s (or the customer’s beneficial owner’s) previous role.
• The corruption potential of the customer’s previous role. Where there was greater opportunity for illicit gain, it is more likely that the customer’s source of funds will continue to be corrupt proceeds for some time after the customer leaves office.
• Whether the customer still exercises informal influence over government decision-making through his or her current formal role (e.g. head of a prominent lobbying organization) or through informal relationships (e.g. the customer is an informal but widely accepted leader of a political party but has no official title).
• Whether the previous and current role of the customer are linked in any way;
• The customer’s relationships to other PEPs (e.g., if the customer is a retired politician whose children are involved in politics. In such cases the customer would also likely qualify as the family member of a PEP).
• The nature and purpose of the business relationship, and the overall risks of the products and services the customer avails or intends to avail.
• The customer’s relationship to the PEP. Family relationships tend to endure through time, but business relationships do not always persist. A customer who was formerly the close associate of a PEP, but who severed the business relationship some time ago, may present reduced corruption risk. 3.2.4. PEP Screening
Classification of a customer as a PEP or a Related Customer should take place during the CDD stage, prior to the commencement of the business relationship. Under Article 15 of the AML-CFT Decision, LFIs are required to have suitable risk management systems in place to determine whether a customer, or the beneficial owner of a customer, is a foreign PEP, or Related Customer and are required to take sufficient measures to identify whether a customer, or the beneficial owner of a customer, is a domestic PEP or an HIO, or Related Customer. In practice, however, it will generally be appropriate to conduct onboarding screening and ongoing screening on all customers. Even citizens of the UAE may qualify as foreign PEPs if they have been entrusted with prominent functions by foreign governments, for example, if they are dual citizens, or held office in a country that does not restrict prominent functions to citizens.
Screening may begin by including a question in onboarding forms or interviews that inquires whether the customer or any beneficial owner is a PEP or Related Customer. LFIs should not however rely solely on a customer’s assertion, but supplement this basic screening question with additional due diligence such as additional questions regarding the customer’s employment and job title, questions regarding the customer’s sources of funds and wealth, and conducting searches of public records (e.g. internet searches or searches of UAE databases) or proprietary databases. Should searches of public records or proprietary databases reveal adverse media on the potential PEP customer, the LFI should review the adverse media and determine whether it is within the LFI's risk appetite to onboard the potential PEP customer and/or subject the PEP to enhanced monitoring.
Where customers are public servants, LFIs should be sure to conduct these searches using not only the customer’s name but also the customer’s title, as some useful information (such as lists of high-level government positions) may be available by title only.
Some PEPs and Related Customers may be determined to conceal their status from financial institutions and the public at large in order to avoid enhanced scrutiny. In these cases, searches of public records or private databases may not reveal their status or the connection between the customer and a PEP. As always, LFIs should be alert to any aspects of a customer profile that are inconsistent or do not have a clear explanation. These ‘red flags’ may be connected to a variety of illicit or questionable activity, including concealed PEP status. Some potential indicators include:
• The customer purports to own and operate a business (particularly a business that relies on political connections) without having the experience or expertise that would likely be considered necessary to successfully operate such a business (e.g., a young person, or a person with no work history, owns a company in an industry that is closely connected to the public sector; or a small firm receives a large government contract that appears far beyond its work experience and capabilities);
• The customer engages in financial transactions that are inconsistent with his or her declared income;
• A minor, or a person with few assets, owns a shell company;
• The customer is a legal arrangement (particularly a complex legal arrangement) where the ultimate settlor and the ultimate beneficiary is the same person;
• The customer wishes to engage in complex transactions, or uses complex corporate structures, with no clear economic purpose.
Because a customer transforms from a non-PEP to a PEP immediately on being entrusted with a prominent public function, LFIs should use the ongoing monitoring process to determine whether a customer’s status has changed. Where a PEP customer, or a PEP who is connected to a Related Customer, has lost the prominent public function that qualified him or her for PEP status, ongoing monitoring can also determine whether it is appropriate to no longer classify the customer as a PEP or as a Related Customers, and to cease enhanced measures.
3.2.5. PEP Risk Rating
Under article 15.1.First.d) of the AML-CFT Decision, LFIs must conduct enhanced ongoing monitoring over relationship with foreign PEPs and Related Customers. This does not mean however that such customers should all be automatically assigned the same risk rating. In addition, as per article 15.1.Second.b), for domestic PEPs and HIOs, and their Related Customers, the EDD requirements in section 3.2.6 below are mandatory when there is a high-risk business relationship accompanying such persons. Therefore, it is important to appropriately risk-rate all PEP customers, customers whose beneficial owners are PEPs, and customers that are direct family members and close associates of a PEP. PEP-specific factors to consider in risk rating include:
• The nature of the PEP’s position. As discussed in section 2 above, where a PEP has greater ability to control or influence consequential government decisions, the corruption risk is greater. LFIs should consider, among other factors:
o The nature of the issues or decisions over which the PEP has or had control; o The extent to which the PEP had control over the disbursement of funds; o The degree of autonomy or independence the PEP has or had in decision-making; o The PEP’s rank or status within the government or international organization.
• The controls in place in the PEP’s own country jurisdiction to prevent corruption, including:
o The country’s position on widely adopted global corruption or transparency ratings; o The extent to which the country investigates and prosecutes high-level corruption; o Whether the country has a free and empowered political opposition and a free press; o Whether the agency, body, or organization in which the PEP holds his or her function has an internal audit/inspector/comptroller function; o Whether asset disclosure requirements or similar requirements apply to PEPs in that country or jurisdiction.
For Related Customers, LFIs should consider the risk of the PEP to which the customer is connected, and also the nature and extent of the connection, in determining the risk rating.
The risk-rating process should also take into consideration not just features specific to PEPs but also all the standard elements of customer risk rating, such as the nature of the customer’s business and the products and services the customer intends to use. For example, a PEP who owns a cash-intensive business and seeks to make bulk cash deposits would likely be considered higher risk than a PEP whose only income is his salary, even if the two customers hold similar positions within a similarly high-risk jurisdiction.
In those cases where a natural person customer has PEP status from two sources, or where more than one PEP is involved in a legal person customer, LFIs should always use the higher risk rating. For example, if a single natural person customer has been appointed to prominent public functions by both the government of the UAE and a foreign government, that customer should be treated as a foreign PEP. Similarly, if a legal person customer has two domestic PEP owners, one high risk and the other medium risk, the legal person customer should be subject to EDD requirements.
3.2.6. Enhanced Due Diligence Requirements
Under Article 15 of AML-CFT Decision, when a customer (or the beneficial owner of a customer) is determined to be a foreign PEP or Related Customer, or where a customer (or the beneficial owner of a customer) is determined to be a domestic PEP or HIO or Related Customer, and when there is a high-risk business relationship accompanying such persons, LFIs must take the following mandatory steps:
• Obtain senior management approval before establishing a business relationship, or continuing an existing one, with a PEP or Related Customer. The specific senior management member within the LFI who are responsible for approving these relationships will vary based on the LFI’s own unique governance arrangements. The CBUAE expects that, if the approving member represents the business (e.g. the Chief Executive Officer or Chief Operating Officer) as opposed to the compliance function (e.g. the Compliance Officer), the LFI’s policies and procedures will clearly require that the head of the LFI’s compliance function give an opinion as to whether the risk associated with the customer is acceptable. When approving an existing relationship with a PEP or Related Customer, senior management should be notified and their approval obtained for the continuance of the relationship. • Take reasonable measures to establish the source of funds, including the source of wealth, of PEPs and Related Customers. This requirement encompasses two distinct concepts:
o Source of funds: The direct source of the funds that are used to initially fund the account, and of any funds that are transacted through the account during the course of the business relationship. o Source of wealth: The source of the customer’s overall wealth, whether or not the LFI is exposed to it.
In the case of foreign PEPs, higher risk domestic PEPs or HIOs, and Related Customers, LFIs should understand, at least at a high level, how the customer acquired his or her wealth. The goal of the process is to provide the LFI with a reasonable degree of confidence that the customer has not generated his or her wealth through illicit activities. Determining source of wealth does not require that the LFI identify and account for every one of the customer’s assets. But the LFI should require the customer to provide information on the customer’s total net worth, and the customer’s principal sources of income (e.g., salary, inheritance, business income, spousal support, etc.). The LFI should supplement information provided by the customer with publicly or privately available information, including, for example media reports, public employee asset declarations (where required by the PEP’s national laws), or published salaries for civil service positions.
The LFI should then make two determinations:
o Whether the customer’s stated net worth is consistent with his or her declared sources of income. For example, if a customer who has spent his career in public service claims not to have inherited any funds yet has a net worth of several million of a currency, this would require further investigation. Alternatively, if a customer was a successful business person for most of his career and only recently entered public service, a high net worth may not be a “red flag”. o Whether the customer’s stated net worth is consistent with the customer’s financial behavior. PEPs who have engaged in illicit activities may lie about their net worth to hide discrepancies with their disclosed sources of income. This is likely to be exposed however when the PEP attempts to engage in financial behavior inconsistent with his or her declared income or net worth. For example, if a PEP declares a total net worth of one million of a currency, this may be consistent with his or her declared licit income; but if he or she chooses to invest a sum equivalent to the entire declared net worth in a speculative investment, this is a sign that his or her wealth requires further investigation.
Where risks are higher, LFIs should perform more intense due diligence on the customer’s source of wealth. For example, if a PEP declares that a substantial portion of his net worth is derived from ownership of a business, the LFI should collect information to satisfy itself that the business exists, is operational, and can reasonably be expected to generate such funds for the PEP.
• Conduct enhanced ongoing monitoring of the relationship. LFIs must perform risk-based ongoing monitoring of the business relationship for all customers. In the above mentioned cases, the required enhanced ongoing monitoring could include a number of actions designed to manage the enhanced risk of these customers:
o Subjecting the customer file to more frequent review and updating, including a manual review of transactions. All customer files should be reviewed on a risk-based schedule. For the highest-risk PEPs and Related Customers, reviewing the file as frequently as every six or nine months may be appropriate. This review should also include a review of substantial transactions on the account to ensure that they are consistent with information provided by the customer regarding source of funds and source of wealth. o Applying specific risk-based transaction monitoring rules. Where automated transaction monitoring systems allow it, LFIs should apply specific monitoring rules to all PEPs and Related Customers. These rules should have more sensitive thresholds for alerts, and should also be able to flag transactions between PEPs and Related Customers where both customers maintain accounts with the LFI. o Requiring pre-approval for large transactions. It may be appropriate for LFIs to require pre-approval from the compliance function for any transactions representing a substantial portion of the PEP’s declared net worth, taking into consideration the size of the LFI and defined risk appetite. 3.3. Transaction Monitoring and Suspicious Transaction Reporting
3.3.1. Transaction Monitoring
As required by Article 7 of the AML-CFT Decision, LFIs must continuously monitor all their transactions to ensure that the transactions conducted are consistent with the information they have about the customer, their type of activity and the risks they pose, including, when necessary, the source of funds. As with all customer types, LFIs that use automated monitoring systems should apply rules with appropriate thresholds and parameters that are designed to detect common typologies for illicit behaviour. When monitoring and evaluating transactions, the LFI should take into account all information that it has collected as part of CDD.
Monitoring systems can include manual monitoring processes and the use of automated and intelligence led monitoring systems. In all cases, the appropriate type and degree of monitoring should appropriately match the money laundering and financing of terrorism (ML/FT) risks of the institution’s customers, products and services, delivery channels, and geographic exposure, and may therefore vary across an LFI’s business lines or units, where applicable. TM programs should also be calibrated to the size, nature, and complexity of each institution. The transaction monitoring system used by LFIs should be equipped to identify patterns of activity that appear unusual and potentially suspicious for PEPs customers as well as unusual behaviour that may indicate that a customer’s business has changed in such a way as to require a high risk rating. Please consult also the CBUAE’s Guidance for Licensed Financial Institutions on Transaction Monitoring and Sanctions Screening3 for further information.
3 Available at: centralbank.ae/en/cbuae-amlcft
3.3.2. Suspicious Transaction Reporting
As required by Article 15 of the AML-CFT Law and Article 17 of AML-CFT Decision, LFIs must file an STR, SAR or other report types with the UAE Financial Intelligence Unit (UAE FIU) when they have reasonable grounds to suspect that a transaction, attempted transaction, or funds constitute, in whole or in part, regardless of the amount, the proceeds of crime, are related to a crime, or are intended to be used in a crime. As per Article 18 of the AML-CFT Decision, In reporting their suspicions, employees must maintain confidentiality with regard to both the information being reported and the act of reporting itself, and make reasonable efforts to ensure the information and data reported are protected from access by any unauthorised person (Please consult also section 7.8 of the CBUAE’s Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations for Financial Institutions). STR filing is not simply a legal obligation; it is a critical element of the UAE’s effort to combat financial crime and protect the integrity of its financial system. STR filings assist law enforcement in detecting criminal actors and preventing the flow of illicit funds through the UAE financial system. Please consult also the CBUAE’s Guidance for Licensed Financial Institutions on Suspicious Transaction Reporting4 for further information.
4 Available at: centralbank.ae/en/cbuae-amlcft
3.4. Governance and Training
The specific preventive measures discussed above should take place within, and be supported by, a comprehensive institutional AML/CFT program that is appropriate to the risks the LFI faces. The core of an effective risk-based program is an appropriately experienced AML/CFT Compliance Officer who understands the LFI’s risks and obligations and who has the resources and autonomy necessary to ensure that the LFI’s program is effective. Additionally, the LFI’s senior management must clearly endorse and support the AML/CFT program. As with all risks to which the LFI is exposed, the AML/CFT training program should ensure that employees are aware of the risks of PEPs customers, familiar with the obligations of the LFI, and equipped to apply appropriate risk-based controls. Training should be tailored and customized to the LFI’s risk and the nature of its operations. As such, an LFI that has a significant number of PEPs customers should offer training that includes an in-depth discussion of risk factors and “red flags” related to such customers (see Annex 1 below).
Annex 1. Red flags
The following is a list of red flags and indicators for suspicion associated with PEPs.5 PEPS ATTEMPTING TO SHIELD THEIR IDENTITY:
• Use of corporate vehicles (legal entities and legal arrangements) to obscure the beneficial owner. • Use of corporate vehicles without valid business reason. • Use of intermediaries when this does not match with normal business practices or when this seems to be used to shield identity of PEP. • Use of family members or close associates as legal owner.
RED FLAGS AND INDICATORS RELATING TO THE PEP AND HIS BEHAVIOUR:
• Use of corporate vehicles (legal entities and legal arrangements) to obscure i) ownership, ii) involved industries or iii) countries. • The PEP makes inquiries about the institution’s AML policy or PEP policy. • The PEP seems generally uncomfortable to provide information about source of wealth or source of funds. • The information that is provided by the PEP is inconsistent with other (publicly available) information, such as asset declarations and published official salaries. • The PEP is unable or reluctant to explain the reason for doing business in the country of the financial institution or Designated Nonfinancial Business and Profession (DNFBP). • The PEP provides inaccurate or incomplete information. • The PEPs seeks to make use of the services of a financial institution or DNFBP that would normally not cater to foreign or high value clients. • Funds are repeatedly moved to and from countries to which the PEPs does not seem to have ties with. • The PEP is or has been denied entry to the country (visa denial). • The PEP is from a country that prohibits or restricts its/certain citizens to hold accounts or own certain property in a foreign country.
THE PEP’S POSITION OR INVOLVEMENT IN BUSINESSES:
• The PEP has a substantial authority over or access to state assets and funds, policies and operations. • The PEP has control over regulatory approvals, including awarding licences and concessions. • The PEP has the formal or informal ability to control mechanisms established to prevent and detected ML/FT. • The PEP (actively) downplays importance of his/her public function, or the public function s/he is relates to associated with. • The PEP does not reveal all positions (including those that are ex officio). • The PEP has access to, control or influence over, government or corporate accounts. • The PEP (partially) owns or controls financial institutions or DNFBPs, either privately, or ex officio. • The PEP (partially) owns or controls the financial institution or DNFBP (either privately or ex officio) that is a counter part or a correspondent in a transaction. • The PEP is a director or beneficial owner of a legal entity that is a client of a financial institution or a DNFBP.
RED FLAGS AND INDICATORS RELATING TO THE INDUSTRY/SECTOR WITH WHICH THE PEP IS INVOLVED:
• Arms trade and defence industry. • Banking and finance. • Businesses active in government procurement, i.e., those whose business is selling to government or state agencies. • Construction and (large) infrastructure. • Development and other types of assistance. • Human health activities. • Mining and extraction. • Privatisation. • Provision of public goods, utilities.
BUSINESS RELATIONSHIP / TRANSACTION, PURPOSE OF BUSINESS RELATIONSHIP:
• Multiple STRs or other reports have been submitted on a PEP. • (Consistent) use of rounded amounts, where this cannot be explained by the expected business. • Deposit or withdrawal of large amounts of cash from an account, use of bank cheques or other bearer instruments to make large payments. Use of large amounts of cash in the business relationship. • Other financial institutions and DNFBPs have terminated the business relationship with the PEP. • Other financial institutions and DNFBPs have been subject to regulatory actions over doing business with the PEP. • Personal and business related money flows are difficult to distinguish from each other. • Financial activity is inconsistent with legitimate or expected activity, funds are moved to or from an account or between financial institutions without a business rationale. • The account shows substantial activity after a dormant period; or over a relatively short time; or shortly after commencing the business relationship. • The account shows substantial flow of cash or wire transfers into or out of the account. • Transactions between non-client corporate vehicles and the PEP’s accounts. • A PEP is unable or reluctant to provide details or credible explanations for establishing a business relationship, opening an account or conducting transactions. • A PEP receives large international funds transfers to a gaming account. The PEP withdraws a small amount for gaming purposes and withdraws the balance by way of cheque. • A PEP uses third parties to exchange gaming chips for cash and vice versa with little or minimal gaming activity. • A PEP uses multiple bank accounts for no apparent commercial or other reason.
PRODUCTS, SERVICE, TRANSACTION OR DELIVERY CHANNELS:
• Businesses that cater mainly to (high value) foreign clients. • Trust and company service providers. • Wire transfers, to and from a PEP account that cannot be economically explained, or that lack relevant originator or beneficiary information. • Correspondent and concentration accounts. • Dealers in precious metals and precious stones, or other luxurious goods. • Dealers in luxurious transport vehicles (such as cars, sports cars, ships, helicopters and planes). • High-end real estate dealers.
COUNTRY SPECIFIC RED FLAGS AND INDICATORS
• The foreign or domestic PEP is from a higher risk country. • Additional risks occur if a foreign or domestic PEP from a higher risk country would in his/her position have control or influence over decisions that would effectively address identified shortcomings in the AML/CFT system. • Foreign or domestic PEPs from countries identified by credible sources as having a high risk of corruption. • Foreign or domestic PEPs from countries that have not signed or ratified or have not or insufficiently implemented relevant anti-corruption conventions, such as the UNCAC, and the OECD Anti-Bribery Convention. • Foreign or domestic PEPs from countries with a mono economies (economic dependency on one or a few export products), especially if export control or licensing measures have been put in place. • Foreign or domestic PEPs from countries that are dependent on the export of illicit goods, such as drugs. • Foreign or domestic PEPs from countries (including political subdivisions) with political systems that are based on personal rule, autocratic regimes, or countries where a major objective is to enrich those in power, and countries with high level of patronage appointments. • Foreign or domestic PEPs from countries with poor and/or opaque governance and accountability. • Foreign or domestic PEPs from countries identified by credible sources as having high levels of (organised) crime. 5 FATF: fatf-gafi.org/media/fatf/documents/recommendations/Guidance-PEP-Rec12-22.pdf
Annex 2. Synopsis
Purpose of this Guidance Purpose The purpose of this Guidance is to assist the understanding and effective performance by licensed financial institutions (LFIs) of their statutory obligations under the legal and regulatory framework in force in the UAE relating to PEPs. Applicability This Guidance applies to all natural and legal persons, which are licensed and/or supervised by the CBUAE, in the following categories: national banks, branches of foreign banks, exchange houses, finance companies, stored value facilities, retail payment service providers, card schemes, registered Hawala providers, and other LFIs; and insurance and re-insurance companies, agencies, and brokers. Understanding Risks Article 15 of the AML-CFT Decision and the FATF standards impose specific Customer Due Diligence (CDD) obligations on LFIs with respect to Customers that are Politically Exposed Persons (PEPs) which include the Direct Family Members or Associates Known to be Close to the PEPs. The special requirements related to PEPs are not an indication that LFIs should avoid dealing with such customers. Instead, these requirements are meant to ensure that LFIs have done the due diligence necessary to fully identify, understand their customers and have made fully-informed decisions regarding whether or not to accept the customer or to continue the relationship.
There are three sub-groups of PEPs: (1) Domestic PEPs; (2) Foreign PEPs; and (3) Heads of International Organizations (HIOs). PEPs are at higher risk of involvement in crimes because of the powers that come with their position or status. PEPs may use their power or influence to directly enrich themselves, their family members, and their associates, by stealing or misdirecting government funds. Customers that are the direct family members of a PEP, the known close associates of a PEP, or that are legal persons or legal arrangements with at least one beneficial owner who is a PEP are referred to as "Related Customers.''
Although LFIs are required to apply special procedures for all PEPs and Related Customers, not all PEPs and Related Customers are equally high-risk. Some factors that can influence the risks of a particular PEP are:
• The PEP's ability to control highly consequential outcomes. • The authority and independence inherent in the PEP's role or function. • The access to funds inherent in the PEP's role. • The nature of governance in the state or organization that has entrusted the PEP with a prominent function. • The overall level of corruption in the state or organization that has entrusted the PEP with a prominent function. The sources of risk for a Related Customer can be divided into two broad categories:
• The risk of the PEP to which the Related Customer is connected • The relationship between the Related Customer and the PEP. Mitigating Risks Legal requirements The AML-CFT Decision requires LFIs to carry out specific mandatory due diligence measures on PEPs and Related Customers, in addition to the standard CDD required for all customers. In line with FATF standards, the AML-CFT Decision imposes different requirements on LFIs for foreign PEPs as opposed to domestic PEPs and HIOs.
• For foreign PEPs and Related Customers, LFIs must: (1) Put in place suitable risk management systems to determine whether a Customer or the Beneficial Owner is considered a PEP: (2) obtain senior management approval before establishing a business relationship, or continuing an existing one, with a PEP; (3) take reasonable measures to establish the source of funds and the sources of wealth of Customers and Beneficial Owners identified as PEPs; and (4) conduct enhanced ongoing monitoring over such relationship. • For domestic PEPs and HIOs and Related Customers, LFIs must (1) Take sufficient measures to identify if their customer or the Beneficial Owner is considered one of those persons and (2) Take the measures identified in (b), (c), and (d) when there is a high-risk business relationship accompanying such persons. LFIs must take reasonable measures to determine whether the beneficiary, or the beneficial owner of a beneficiary, of a life insurance policy or of family takaful insurance is a PEP or a Related Customer. LFIs must inform senior management before pay-out of those policies, or prior to the exercise of any rights related to them. LFIs must also thoroughly examine the overall business relationship.
Applying Legal Requirements Classifying Customers as PEPs:
• The legal definition of PEP specifically lists the roles of persons who always qualify as PEPs, such as Heads of States or Governments, senior politicians, senior government officials, and judicial officials, among others. • However, as there is no exhaustive list of the positions that qualify an individual as a PEP globally and LFIs should use their discretion in identifying PEPs and develop risk-based policies and procedures to ensure they appropriately identify customers who are PEPs, or the family members or close associates of PEPs. • The determination of whether a customer is a PEP should therefore consider a number of factors, including, most importantly, whether the natural person currently holds, or has recently held, a role that gives him or her power or influence over decisions, policy or the disbursal of funds belonging to a government or an international organization. • PEPs are always natural persons, and LFIs should perform a PEP analysis on customers who are the beneficial owners of legal persons or legal arrangements. Classifying Customers as Related Customers:
• LFIs are required to treat the direct family members (spouses, children, spouses of children, and parents) and close associates of PEPs (Natural persons having joint ownership rights in a legal person or arrangement or any other close business relationship with the PEP or having individual ownership rights in a legal person or arrangement established in favour of the PEP) as if they were PEPs themselves. • The above-mentioned relationships should be viewed as a mandatory minimum, not as an exhaustive list of all relationships that may justify to treat a customer as a PEP. LFIs should take a risk-based approach and consider whether a relationship exists between their customer and the PEP that could be exploited or abused to obscure the PEP's connection to illicit funds. • Once an LFI has established that a qualifying relationship exists between a customer (or the beneficial owner of a customer) and a PEP, the LFI must treat the customer as a PEP (or as owned by a PEP). However, between a PEP and the direct family member or close associate of a PEP: the latter cannot transfer their status to their own family members and close associates. Time Limits of PEP Status:
• A PEP's risk derives from the PEP's power or influence over decisions, funds, or policy. Therefore, it may not be appropriate to continue to treat a customer as a PEP long after they have lost such power or influence. While LFIs may set a schedule to review PEP status, they should make a risk-based decision as to when sufficient time has passed for a customer to no longer be classified as a PEP. • Factors to consider when making such a determination include: the seniority and power inherent in the customer's previous role; the corruption potential of the customer's previous role; whether the customer still exercises informal influence over government decisionmaking through his or her current formal role; whether the previous and current role of the customer are linked in any way; the customer's relationships to other PEPs and the nature and purpose of the business relationship, and the overall risks of the products and services the customer avails or intends to avail. PEP Screening:
• Classification of a customer as a PEP or a Related Customer should take place during the CDD stage, prior to the commencement of the business relationship. LFIs are required to have suitable risk management systems in place to determine whether a customer, or the beneficial owner of a customer, is a foreign PEP, or Related Customer and are required to take sufficient measures to identify whether a customer, or the beneficial owner of a customer, is a domestic PEP or an HIO, or Related Customer. In practice, however, it will generally be appropriate to conduct onboarding screening and ongoing screening on all customers. • Preliminary screening may begin by including a question in onboarding forms or interviews that inquires whether the customer or any beneficial owner is a PEP or Related Customer. LFIs should not however rely solely on a customer's assertion, but supplement this basic screening question with additional due diligence. • LFIs should be alert to any aspects of a customer profile that are inconsistent or do not have a clear explanation. LFIs should use the ongoing monitoring process to determine whether a customer's status has changed. PEP Risk Rating: Under the AML-CFT Decision, LFIs must conduct enhanced ongoing monitoring over relationships with foreign PEPs and Related Customers. Therefore, it is important to appropriately risk-rate all PEP customers, customers whose beneficial owners are PEPs, and customers that are direct family members and close associates of a PEP. PEP-specific factors to consider in risk rating include: the nature of the PEP's position, and the controls in place in the PEP's own country jurisdiction to prevent corruption. For Related Customers, LFIs should consider the risk of the PEP to which the customer is connected, and also the nature and extent of the connection, in determining the risk rating. In cases where a natural person customer has PEP status from two sources, or where more than one PEP is involved in a legal person customer, LFIs should always use the higher risk rating. Enhanced Due Diligence Requirements: Under the AML-CFT Decision, when a customer (or the beneficial owner of a customer) is determined to be a foreign PEP or Related Customer, or where a customer is determined to be a domestic PEP or HIO or Related Customer, and when there is a high-risk business relationship accompanying such persons, LFIs must take the following mandatory steps: (1) Obtain senior management approval before establishing a business relationship, or continuing an existing one, with a PEP or Related Customer; (2) take reasonable measures to establish the source of funds, including the source of wealth, of PEPs and Related Customers; and (3) conduct enhanced ongoing monitoring of the relationship. Transaction Monitoring and Suspicious Transaction Reporting Transaction Monitoring: As required by the AML-CFT Decision, LFIs must continuously monitor all their transactions to ensure that transactions are consistent with the information they have about the customer, their type of activity and the risks they pose, including, when necessary, the source of funds. Monitoring systems can include manual monitoring processes and the use of automated and intelligence led monitoring systems. The transaction monitoring system used by LFIs should be equipped to identify patterns of activity that appear unusual and potentially suspicious for PEP customers as well as unusual behaviour that may indicate that a customer's business has changed in such a way as to require a high-risk rating. Suspicious Transaction Reporting: As required by the AML-CFT Law and the AML-CFT Decision, LFIs must file a suspicious transaction report (STR) or suspicious activity report (SAR) or other report types with the UAE Financial Intelligence Unit (UAE Fill) when they have reasonable grounds to suspect that a transaction, attempted transaction, or funds constitute, in whole or in part, regardless of the amount, the proceeds of crime, are related to a crime, or are intended to be used in a crime. Governance and Training The specific preventive measures discussed above should take place within, and be supported by, a comprehensive institutional AML/CFT program that is appropriate to the risks the LFI faces. As with all risks to which the LFI is exposed, the AML/CFT training program should ensure that employees are aware of the risks of PEPs customers, familiar with the obligations of the LFI, and equipped to apply appropriate risk-based controls. Guidance for the Insurance Sector
Effective from 31/10/20221. Introduction
1.1. Purpose
Article 44.11 of the Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations, as amended, charges Supervisory Authorities with “providing Financial Institutions…with guidelines and feedback to enhance the effectiveness of implementation of the Crime-combatting measures.”
The purpose of this Guidance is to assist the understanding, and effective performance by the United Arab Emirates Central Bank’s (“CBUAE”) licensed insurers, agents, and brokers of their statutory obligations under the legal and regulatory framework in force in the UAE. It should be read in conjunction with the CBUAE’s Procedures for Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations (issued by Notice No. 74/2019 dated 19/06/2019) and Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations for Financial Institutions (issued by Notice 79/2019 dated 27/06/2019) and any amendments or updates thereof.1 As such, while this Guidance neither constitutes additional legislation or regulation nor replaces or supersedes any legal or regulatory requirements or statutory obligations, it sets out the expectations of the CBUAE for licensed insurers, agents, and brokers to be able to demonstrate compliance with these requirements. In the event of a discrepancy between this Guidance and the legal or regulatory frameworks currently in force, the latter will prevail. This Guidance may be supplemented with additional separate guidance materials, such as outreach sessions and thematic reviews conducted by the Central Bank.
Furthermore, this Guidance takes into account standards and guidance issued by the Financial Action Task Force (“FATF”), industry best practices, and red flag indicators identified by the FATF and leading jurisdictional authorities. These are not exhaustive and do not set limitations on the measures to be taken by licensed insurers, agents, and brokers in order to meet their statutory obligations under the legal and regulatory framework currently in force. As such, licensed insurers, agents, and brokers should perform their own assessments of the manner in which they should meet their statutory obligations.
This Guidance comes into effect immediately upon its issuance by the CBUAE with licensed insurers, agents, and brokers expected to demonstrate compliance with its requirements within one month from its coming into effect.
1 Available at: centralbank.ae/en/cbuae-amlcft.
1.2. Applicability
Unless otherwise noted, this Guidance applies to all insurance and re-insurance companies, agents, and brokers that are licensed and supervised by the CBUAE.
1.3. Legal Basis
This Guidance builds upon the provisions of the following AML/CFT related laws and regulations:
1.4. Acronyms
Terms Description AML Anti-money laundering CBUAE Central Bank of the United Arab Emirates CDD Customer due diligence CFT Combating the financing of terrorism DNFBP Designated non-financial business or profession EDD Enhanced due diligence FATF Financial Action Task Force FFR Fund Freeze Report FIU Financial intelligence unit LFI Licensed financial institution ML Money laundering PEP Politically exposed person PNMR Partial Name Match Report SAR Suspicious activity report SDD Simplified due diligence STR Suspicious transaction report TF Terrorist financing UN United Nations UNSC United Nations Security Council UNSCR UN Security Council Resolution 2. Understanding and Assessing the ML/FT Risks
2.1. Overview of Insurance Sector Activities and Participants
The insurance sector offers a range of products and services to individuals and companies designed to provide a guarantee of compensation for specified loss, damage, illness, or death and facilitate financial planning and risk management in the face of uncertain future events. At the most general level, insurance products can be divided into two categories:
• Insurance of persons and funds accumulation (hereafter referred to as “life and other investment-related insurance”), which provides long-term coverage against the risk of a future loss, such as death, and may serve as an alternative long-term savings or investment vehicle (e.g., to be paid out upon retirement); and
• Property and liability insurance (hereafter referred to as “general insurance”), which provides shorter-term coverage against the risk of specific losses, such as damage to property, illness and associated medical expenses, or personal or corporate liability.
Both types of insurance may be offered in the UAE by conventional and Takaful insurance companies. The classes and types of the above-mentioned insurance categories are defined by Articles 3 and 4 of the Executive Regulation2 of the Federal Law No. (6) of 2007 on the Establishment of the Insurance Authority & Organization of Its Operations as amended by Federal Law No. 3 of 2018 (“Insurance Law”)).
Under Article 2.16 of the AML-CFT Decision as amended, only life insurance and other investment-related insurance products are subject to the UAE’s AML/CFT legal and regulatory framework. It is therefore critical that each licensed insurer, re-insurer, agent, and broker undertakes a comprehensive assessment of its ML/FT risks, including especially the risks associated with its life insurance and other investment-related insurance product offerings, and that it designs and implements an AML/CFT compliance program that is commensurate with those risks.
Insurance sector participants include operators in the insurance sector, which sell or facilitate the sale of insurance products and must be licensed by the CBUAE, and customers who own, pay for, and/or are covered by or the beneficiaries of insurance products.
Principal insurance sector operators, as defined by the Insurance Law, include:
• Insurers, defined as any insurance company incorporated in the UAE or foreign company licensed to carry out insurance operations in the UAE according to the provisions of the Insurance Law, including Takaful insurance companies.
○ Note: An insurer can issue insurance policies to consumers, or to other insurers or re-insurers, in exchange for payment of a premium.
• Re-insurers, defined as any re-insurance company incorporated in the UAE of foreign re-insurance company licensed to carry out insurance operations inside the UAE or a foreign re-insurance company outside the UAE.
○ Note: Reinsurers are insurers that issue insurance policies to customers that are themselves insurers or reinsurers. Reinsurance includes both “treaty” agreements, which cover broad groups of policies issued by the primary insurer, as well as “facultative” agreements, which cover specific policies or risks, negotiated on an ad hoc basis.
• Insurance agents, defined as any natural or legal person approved and authorized by the insurance company to carry out insurance operations on its behalf or on behalf of any branch thereof.
○ Note: All insurance agents are “tied” agents, meaning they have a contractual agreement to underwriting and sell insurance products exclusively on behalf of a single insurer. Persons who are contractually free to sell insurance on behalf of multiple insurers or as a freestanding intermediary between insurers and consumers are referred to as insurance brokers, as defined below.
• Insurance brokers, defined as any legal person who independently intermediates in insurance and re-insurance operations between the insurance or re-insurance seeker on one side and any insurance or re-insurance company on the other side and receives for his efforts commission from the insurance company or the re-insurance company with which the insurance or re-insurance has been accomplished.
○ Note: Insurance brokers can be authorized by multiple insurers to sell insurance products to consumers (or other insurers or reinsurers) on their behalf or to execute insurance sales as freestanding intermediaries between insurers and consumers, in either case in exchange for payment of a commission from the insurer.
Under the Insurance Law and supporting Insurance Authority Board Resolutions3, insurance operators also include:
- Health insurance third-party administrators, defined as legal persons licensed by the CBUAE to perform health insurance third party administration in accordance with the provisions of the related instructions (e.g. manage health insurance programs and pay health insurance claims on behalf of an insurer); - Insurance producers, defined as natural or legal persons licensed by the CBUAE to practice the profession of marketing insurance policies through ordinary means or electronic means; - Price comparison websites (also referred to as “insurance aggregators”), defined as legal persons registered by the CBUAE to provide insurance premium price comparison services using the Internet; - Consultants, defined as natural or legal persons who study the insurance requirements for his customers, give advice in respect of the suitable insurance coverage, assist in preparing the insurance claims along with conducting the other duties specified in the regulation and receive their fees from his customers;4 - Actuaries, defined as persons who estimate values of the insurance contracts, documents and the related accounts; and - Loss and damage adjusters, defined as persons who examine the damages occurred to the subject matter of the insurance, and assess them.
However, as these participants are not involved or play a very limited role in selling or facilitating the sale of insurance products, and as per Article 2 of the AML-CFT Decision, they are not included under Section 1.2. Applicability of this Guidance.
Principal insurance sector customers include:
• Policyholders or policy owners, defined as natural persons, legal persons, or legal arrangements who own and maintain the contractual rights of an insurance policy, including powers to inject funds, establish the beneficiary, and exercise early surrender rights. In the case of a group policy, the policyholder is the owner of the master policy.
• Policy payers, defined as natural persons, legal persons, or legal arrangements who pay the necessary premium to keep the policy in force.
• Insured, defined by the Insurance Law as natural persons, legal persons, or legal arrangements who concluded an insurance contract with the Insurer.
○ Note: In many cases, the policyholder, policy payer, and insured will be the same person. The insured will also be the person covered by the insurance policy.
• Beneficiaries, defined by the Insurance Law as natural persons, legal persons, or legal arrangements who acquired the rights of the insurance contract at the start or these rights has been legally transferred thereto.
○ Note: Beneficiaries and other payees are entitled to receive claim payments, distributions, or other payouts under an insurance policy. The payee of a general insurance policy is typically the insured, although certain property insurance policies may specify a third party, such as a lender or lessor with an interest in the covered property, as entitled to all or part of the claim payments on the policy.5 2 Insurance Authority – The Board of Directors’ Resolution No.2 of 2009 on Issuance of the Executive Regulation of the Federal Law No.6 of 2007 on Establishment of the Insurance Authority and Organization of the Insurance Operations (Published in the Official Gazette No.504 on 31/01/2010).
3 Including Insurance Authority Board Resolution No. 9 of 2011 Concerning the Instructions for Licensing Health Insurance Third Party Administrators and Regulation and Control of their Business, Insurance Authority Board of Directors’ Decision No. 12 of 2018 Concerning the Regulation on Licensing and Registration of Insurance Consultants and Organization of their Operations, Insurance Authority Board of Directors’ Resolution No. 27 of 2020 Concerning the Instructions for Licensing Insurance Producers, and Insurance Authority Board of Directors’ Resolution No. 18 of 2020 Concerning the Electronic Insurance Regulations.
4 Unlike agents and brokers, consultants are not authorized to complete insurance sales (or to “bind coverage”) on behalf of an insurer.
5 A policyholder’s insurable interest is an interest in the value of the subject of insurance, including any item, event, action, or legal or financial relationship whose loss would cause a financial or other hardship. An insurable interest may result from property rights, contractual rights, or potential legal liability.2.2. ML/FT Risks Relevant to Life Insurance and other Investment-Related Insurance Products
Criminal actors may use life insurance and other investment-related insurance products to place illicit proceeds into the financial system, especially (though not exclusively) where the insurer or intermediary accepts premium payments in cash. Such products may be purchased with the intention of either holding the insurance policy over its standard duration or canceling coverage before maturity and, where permitted, withdrawing premiums paid less a penalty (a practice known as “early surrender”) so as to free up funds for alternative uses. Illicit actors may also deliberately overpay premiums and request a refund for the amount overpaid to the insurance carrier in order to trigger payout under a policy. Reimbursed premiums, withdrawn contributions, and payout proceeds (whether legitimate or fraudulent) can then be deposited into a bank account or used to purchase other financial instruments without necessarily revealing the ultimate origin of the funds.
As noted above, life and other investment-related products are generally considered to present higher ML/FT risk, particularly where they have high cash values upon surrender. The following methods may be employed to launder funds through life insurance and other investment-related insurance products or relationships:
• Assigning policies and payments to third parties, especially through policies (such as secondhand endowment and bearer insurance policies) that allow the policyholder to change the beneficiary before maturity or surrender without the knowledge or consent of the insurer;
• Borrowing against the cash surrender value of permanent life insurance policies or using a policy as collateral to purchase other financial instruments;
• Selling units in investment-linked products, such as annuities;
• Buying products with insurance termination features without concern for the product’s investment performance; and
• Establishing fictitious insurance or reinsurance companies or intermediaries in order to place or move illicit proceeds without revealing the true source of funds.
In addition to these vulnerabilities, the insurance sector is also vulnerable to abuse from other types of economic crime, particularly orchestrated fraud. Moreover, even where insurance products or relationships are not directly abused to launder money or perform other illicit transactions, insurance may be purchased by illicit actors to provide an appearance of legitimacy to the underlying, insured activities. As per Article 11.2 of the AML-CFT Decision, LFIs must consider the customer and the beneficiary of life insurance and family Takaful policies as risk factors when determining the applicability of enhanced due diligence procedures (EDD).
The remainder of this section presents additional examples of key ML/FT risk factors relevant to the insurance sector for life insurance and other investment-related insurance products, organized by risks related to insurance products, services and transactions, distribution channels and intermediaries, customers, and geographies. These should be considered by insurance sector operators when performing their financial crimes risk assessments (see section 3.1) and determining the risks presented by specific customers or business activities. Individual risks may be heightened in view of the UAE’s national and regional circumstances and the composition of the local insurance sector. Where a risk factor is coupled with one or more of the red flag indicators provided in Annex 1 of this Guidance, insurance sector operators should consider assigning additional resources or controls to the area of heightened risk, such as by applying enhanced due diligence (“EDD”) or heightened ongoing monitoring.
Insurance operators are expected to perform and document an enterprise ML/FT risk assessment and keep the risk assessment up to date given material changes to their risk profile or legal, regulatory, or supervisory environment. Additional details on the enterprise risk assessment process and the use of risk assessment findings to support a risk-based approach are provided in section 3.1.
2.2.1. Product Risk Factors
Product risk is assessed by identifying how vulnerable a product is to money laundering and terrorist financing based on the product’s design. Product risk should be assessed periodically and when significant changes are made to product offerings, including the development of new products, services, or technologies. Product risk is a significant factor in identifying unusual activity.
The following table describes attributes used to assess the vulnerability of product offerings and provides lower-and higher-risk examples of each.
Attribute Lower-risk example Higher-risk example Ability to hold funds or transact large sums Product design that does not hold a balance or cannot be withdrawn against, such as group benefits Product design that allows funds to be held on behalf of the customer; high-value or unlimited-value premium payments, overpayments, or large volumes of lower-value payments Customer anonymity or third-party transactions Product design that only allows transactions from customers with identification, or where all funds flow back to the customer Product design that allows deposits and payments by third parties or that provides for non-face-to-face transactions (e.g., mobile apps where payment source is unknown) Liquidity Product design that does not permit withdrawals or includes significant fees or other penalties for early withdrawals Product design that has no (or no significant) fees or other penalties for early withdrawal Time horizon Products that are typically held for a long period of time, such as years, until retirement or death Products that are typically held for a shorter time period Purpose or intended use of the product Product design makes it easy to identify if products are not being used as intended Product design makes it difficult to identify if products are not being used as intended 2.2.2. Service and Transaction Risk Factors
Service and transaction risk can be assessed by identifying how vulnerable a product is to use by a third party or unintended use based on the methods of transaction available. Service and transaction risk is influenced by product design. Understanding potential service and transaction risks in the business is a significant factor in recognizing unusual activity at a customer level.
The following table describes attributes used to assess service and transaction risk and provides lower-and higher-risk examples of each.
Attribute Lower-risk example Higher-risk example Difficulty in tracing ownership of funds Preprinted checks, bill payments, and electronic funds transfer (EFT) payments with verified banking records Cash, bank drafts in bearer form, travelers checks, counter checks (where ownership information is handwritten or typed in a different font than the rest of the check), and potentially some digital currencies The customer is not the payer or recipient of the funds The funds are moved from or to another financial institution The third-party paying or receiving funds has not previously been disclosed Payment source or recipient is based outside of the country The recipient or payer is the policyholder and is in a low-risk country The recipient or payer is the policyholder and is in a higher-risk country or is a third party outside the country (making it more difficult to trade or confirm the source of funds) Number of transactions The low number of transactions or transaction frequency that is typical for the product A large number of transactions back and forth with the customer or third parties, especially where it exceeds typical usage for the product Transactional patterns Regular and expected customer account activity Significant, unexpected, and unexplained change in the customer’s typical activity, such as early surrenders or withdrawals where such service is offered 2.2.3. Distribution Channel and Intermediary Risk Factors
The distribution channel is the method a customer uses to open a new policy or account. The distribution channel risk is identified by assessing how vulnerable the channel is to money laundering or terrorist financing activities based on attributes that may make it easier to obscure customer identity.
The risk of failing to identify a customer correctly may be higher for distribution channels that use an intermediary or do not require face-to-face contact. Depending on the product, distribution channel risk may be mitigated by using distributors who are also subject to AML/CFT obligations or a pension scheme subscribed through the customer’s employer.
The following table describes attributes used to assess the vulnerability of distribution channels and provides lower- and higher-risk examples of each.
Attribute Lower-risk example Higher-risk example The distributor has AML/CFT obligations The distributor is overseen by a regulatory authority and subject to AML/CFT laws equivalent to or stronger than the insurer Distributor is not subject to AML/CFT requirements Payment to an insurer Customer pays the insurer directly from their account at a bank or securities dealer The customer pays the distributor, who then pays the insurer The direct relationship of customer to insurer Tied agents, brokers, and banking consultants; products distributed directly by insurers Non-face-to-face relationships6 with insurers or agents (e.g., trusts or insurance sold by telephone or online without adequate safeguards for confirmation of identity) 6 As discussed in section 3.3.1.5 below, relationships in which personal contact between an insurer or agent and the customer is achieved via video teleconference are not considered to be non-face-to-face relationships.
2.2.4. Customer Risk Factors
Customer-based risk factors are assessed to evaluate the level of vulnerability to ML/FT threats posed by customers based on their characteristics. Understanding the inherent risks enables an insurer, agent, or broker to identify appropriate mitigating controls and manage residual risks. Customer risk factors combined with business risk factors can be used as criteria for risk scoring to identify high-risk customers. Such risk factors include:
• Customer identity; • Third-party involvement; • Customer’s source of wealth or funds; • Customers who are politically exposed persons (“PEPs”), including the direct family members and close known associates of a PEP, and legal entities where at least one beneficial owner is a PEP; and • Known criminals, terrorists, or persons on sanctions lists.7
The following table describes attributes used to assess customer risks and provides lower- and higher-risk examples of each.
Attribute Lower-risk example Higher-risk example Identification Customer provides identification or can be identified using third-party sources. Customer has difficulty producing identification, or the authenticity of the identification provided is questionable Third-party relationships No third-party involvement Customer is controlled by a third party, or there are multiple indicators of third-party deposits or payments; customer is controlled by a gatekeeper (such as an accountant, lawyer, or other professional holding accounts or contracts at the insurer) without any interaction with the beneficial owner Customer’s legal form Customer is a living person or is a large, publicly-traded legal entity with clear ownership and control Customer is a legal entity with a complex structure where it is difficult to ascertain those who own or control the entity; policyholder and/or beneficiary are companies with nominee shareholders and/or shares in bearer form Occupation, business type, or another source of wealth or funds Customer’s business type or occupation is in a lower-risk industry Customer’s business or occupation is in a higher-risk industry (such as a cash-intensive business or an industry that has extensive international exposure or is associated with crime typologies) or is associated with a lower income for a high-value deposit without a confirmed source of funds or wealth (such as inheritance or real estate) Depth and duration of relationship with customer Customer has a long history with the insurer or its agents and additional information is on file (such as credit underwriting, insurance underwriting, customer due diligence, etc.) Customer is new to the insurer or insurer has little or no experience with the customer Customer only holds accounts with lower risk products and services Customer holds policies or accounts that are registered with the government, such as a registered retirement savings plan Customer only holds non-registered policies or accounts (e.g., investment or bank accounts with an affiliate) Political exposure Customer does not have any ties to politically exposed persons Customer is considered a politically exposed person, particularly from a foreign jurisdiction Other screening results Customer does not have negative news media or media confirms what is known about the customer (such as career confirmation or community engagement) Customer has ties to or is on a designated sanctions list; has a history of predicate offenses; or is associated with negative news 7 Please see section 3.5 below and also refer to the Executive Office’s “Typologies on the circumvention of Targeted Sanctions against Terrorism and the Proliferation of Weapons of Mass Destruction”: available at uaeiec.gov.ae/en-us/un-page?p=2#
2.2.5. Geographic Risk Factors
A customer’s geographic location or connections may indicate a higher risk for ML/FT activities. To mitigate risk, controls are recommended based on domestic and international geographic risk factors. Where available, data from internal insurer historical case experiences or government data based on crimes applicable to ML or predicate offenses can be used to inform the assessment of domestic geographical risk. Customer risk is higher among customers with connections outside the country, especially connections to higher-risk countries. According to the National Assessment of Inherent Money Laundering and Terrorist Financing Risks in the United Arab Emirates, the regions and jurisdictions most often involved in criminal activity in relation to the UAE were Pakistan, India, Iran, Bangladesh, China, Russia, South Africa, Nigeria, Somalia, Lebanon, Yemen, Syria, Iraq, Afghanistan, and North Africa. The following table describes attributes used to assess geographic risks and provides each's lower- and higher-risk examples.
Attribute Lower-risk example Higher-risk example Higher-crime regions Customer does not reside in a region with higher frequency and severity of crimes with ML risk, based on the insurer’s own risk assessment (utilizing historical case experiences or government data where appropriate) Customer resides in a region with high frequency and severity of crimes with ML risk, based on the insurer’s own risk assessment (utilizing historical case experiences or government data where appropriate) History high-risk activity or fraud Customer does not reside in a region that experiences a higher incidence of high-risk activity or fraud Customer resides in a region that experiences a higher incidence of high-risk activity or fraud Foreign tax or physical residency of customer Countries risk rated as low by the insurer Countries risk rated as high by the insurer Foreign ties or transactions Customer does not have any indicators of foreign residency or transactions outside of country Customer has requested or performed transactions with ties to high-risk countries, including especially those on the NAMLCFTC’s and FATF’s lists of high-risk jurisdictions subject to a call for action and jurisdictions under increased monitoring. 3. Mitigating Risks
The sections below discuss how insurance operators can apply preventive measures to identify, assess, manage, and mitigate the risks associated with the insurance sector for life insurance and other investment-related insurance products. This is not a comprehensive discussion of all AML/CFT requirements imposed on insurance sector participants; insurers, agents, and brokers should therefore consult the UAE legal and regulatory framework currently in force.
The controls discussed below should be integrated into each institution’s larger AML/CFT compliance program and supported by appropriate governance, training, and independent audit. As discussed in section 3.6 below, insurers are permitted to delegate the performance of specified controls to insurance agents, brokers, banks, or other intermediaries, using either a third-party reliance or an outsourcing model.
• Under a third-party reliance model, insurers may rely on any third-party LFI, such as a bank, insurance agent, or insurance broker, to perform the elements of general CDD described in sections 3.3.1.1 through 3.3.1.3, following the third party’s AML/CFT policies and procedures. In such circumstances, the third party will usually have an existing business relationship with the customer, which is independent of the relationship to be formed by the customer with the relying institution. The third-party reliance model is most commonly employed in the case of insurance brokers, who sell insurance products to consumers on behalf of multiple insurers and therefore typically maintain and apply their own AML/CFT policies and procedures. • Under an outsourcing model, by contrast, insurers may engage a third-party service provider, such as an insurance agent, broker, or other intermediaries, to apply some or all of the AML/CFT preventive measures described in this section on behalf of the delegating institution, following the insurer’s AML/CFT policies and procedures. In an outsourcing scenario, the third party is subject to the delegating insurer’s control regarding the effective implementation of those policies and procedures by the outsourcing entity. The outsourcing model is most commonly employed in the case of tied agents, who sell insurance products to consumers exclusively on behalf of a single insurer and therefore typically follow the insurer’s AML/CFT policies and procedures.
Under either model, the insurer retains ultimate responsibility for the implementation of applicable AML/CFT preventive measures (including maintaining the availability of all relevant data and records), and the arrangement must satisfy the conditions set forth in section 3.6 below.
3.1. Risk-Based Approach and Enterprise Risk Assessment
Under article 4 of the AML-CFT Decision, the insurance operator is required to perform, document, and keep up to date an enterprise risk assessment for the purposes of identifying, assessing, and understanding its ML/FT risks for life insurance and other investment-related insurance products, including those arising in relation to its:
• Products; • Services and transactions; • Distribution channels and intermediaries; • Customers; and • Geographies, in terms of both the jurisdictions or regions in which has operations and the jurisdictions or regions in which its customers are located or do business.
The insurance operator is expected to document the methodology and findings of the risk assessment, considering all relevant risk factors before determining the level of overall risk and the appropriate type and extent of mitigation to be applied. Insurance operators must keep their risks assessments up to date and ensure that identified risks are within the institution’s risk appetite and that identified deficiencies are appropriately tracked and remediated. Risk assessments should provide a consolidated assessment of the insurance operator’s ML/FT risks across all business units, product lines, and delivery channels, including those of branches, subsidiaries, parent entities, or other affiliates located outside the UAE.
ML/FT risk factors relevant to the insurance sector for life insurance and other investment-related insurance products can be found in section 2.2 above, and red flag indicators for the UAE insurance sector are provided in Annex 1. Please consult also the CBUAE’s AML/CFT Guidelines for Financial Institutions, section 48 for further information.
8 Available at: centralbank.ae/en/cbuae-amlcft.
3.2. New Products, Practices, and Technologies
Under Article 23 of the AML-CFT Decision, an insurance operator is required to identify and assess the ML/FT risks for life insurance and other investment-related insurance products that may arise in relation to:
• The development of new products and new business practices, including new delivery mechanisms (such as mobile insurance applications, insurance portals, transaction terminals, and insurance booths); and • The use of new or developing technologies for both new and preexisting products.
An operator must undertake such risk assessments prior to the launch or use of new products, practices, and technologies and must take appropriate measures to manage and mitigate the identified risks. Operators should pay special attention to new products, practices, or technologies that favor anonymity.
3.3. Customer Due Diligence
3.3.1. General CDD Measures
For life insurance and other investment-related insurance products, insurance operators must perform customer due diligence (“CDD”) on their customers, defined as natural persons, legal persons, or legal arrangements with whom an insurer, agent, or broker establishes or intends to establish a business relationship to carry out insurance operations, as defined in Articles 4 and 5 of the Insurance Law.
Unless otherwise specified below, the customer of an insurance operator is the existing or prospective policyholder, defined as the natural person, legal person, or legal arrangement who owns and maintains the contractual rights of the insurance policy. Where the insurer is acting as a reinsurer, the customer will be the insurer (or reinsurer) in whose name the reinsurance policy is issued. Additionally, in the case of group life insurance or other policies, when the insured persons have active powers on the contract (e.g., to inject sums into the contract, establish the beneficiary, or exercise early surrender of the amounts), those persons should be considered equal to customers, and life insurers and relevant intermediaries should therefore conduct CDD on these persons, as well as on their related third parties. In cases where the insured persons have no active powers, their names should be screened against sanctions lists, but they are not considered customers for AML/CFT purposes, and insurers and intermediaries are not required to conduct full CDD checks on them.
Finally, although in most cases the policyholder will also be the party who pays the necessary premium to keep the policy in force, there may be exceptional cases in which the policy payer is an unrelated third party (referred to as a third-party payer). In such cases, the insurer—or its agent, under a third-party reliance or outsourcing arrangement, if applicable—should perform the following general CDD measures on both the policyholder and the third-party payer.
3.3.1.1. Customer Identification and Verification
Under Article 8 of the AML-CFT Decision, insurance operators are required to identify and verify the identities of all customers. Customers should generally be identified and verified prior to establishing a business relationship. However, in exceptional circumstances, as per Article 4.3 of the AML-CFT Decision, where there is no ML/FT suspicion and ML/FT risks are assessed to be low, an operator may complete the verification of the customer’s identity after establishing a business relationship, as set forth in section 3.3.3 below.
When verifying the Emirates ID card either physically, by way of digital or electronic Know Your Customer (e-KYC) solutions, the insurance operator must use the online validation gateway of the Federal Authority for Identity & Citizenship, Customs & Port Security, the UAE-Pass Application or other UAE Government supported solutions, and keep a copy of the Emirates ID and its digital verification record. Where passports, other than the Emirates ID are used in the KYC process, a copy must be physically obtained from the original passport which must be certified (i.e. certified copy) as “Original Sighted and Verified” under the signature of the employee who carries out the CDD process and retained.
Please consult also the CBUAE’s AML/CFT Guidelines for Financial Institutions, section 6.3.1, for further information.
3.3.1.2. Beneficial Owner Identification and Verification
Under Article 9.1 of the AML-CFT Decision, insurance operators are required to identify and verify the identities of all beneficial owners of any legal person customer, defined as all individuals who, individually or jointly, have a controlling ownership interest in the legal person of 25 percent or more. Where no individual meets this description, the operator is required to identify and verify the identity of the individual(s) holding the senior management position in the entity. This option should be used only as a last resort, however, and when the operator is confident that no one individual, or small group of individuals, exercises control over the customer.
Under Article 9.2 of the AML-CFT Decision, for legal arrangements, insurance operators must verify the identity of the settlor, the trustee(s), or anyone holding a similar position, the identity of the beneficiaries or class of beneficiaries, the identity of any other natural person exercising ultimate effective control over the legal arrangement and obtain sufficient information regarding the beneficial owner to enable verification of his/her identity at the time of payment, or at the time he/she intends to exercise his/her legally acquired rights. The beneficial owner of a legal person or arrangement must be an individual. Another legal person cannot be classified as the beneficial owner of a customer, no matter what percentage it owns. Insurance operators should continue tracing ownership all the way up the ownership chain until it identifies all individuals who own or control at least 25 percent of the operator’s customer. If the insurance operator has followed the steps described above and is still not confident that it has identified the individuals who truly own or control the customer, or when other high-risk factors are present, the operator should consider intensifying its efforts to identify the beneficial owners. The most common method of doing so for legal person is to identify additional beneficial owners below the 25 percent ownership threshold mandated by UAE law. This may involve identifying and verifying the identity of beneficial owners at the 10 percent or even the 5 percent level, as risk warrants. It may also involve requiring the customer to provide the names of all individuals who own or control any share in the customer—without requiring them to undergo CDD— in order to conduct sanctions screening or negative news checks.
Beneficial owners should generally be identified and verified prior to establishing a business relationship. However, in exceptional circumstances, pursuant to Article 4.3 of the AML-CFT Decision, where there is no ML/FT suspicion and ML/FT risks are assessed to be low, an operator may complete verification after establishing a business relationship, as set forth in section 3.3.3 below.
Please consult also the CBUAE’s AML/CFT Guidelines for Financial Institutions, sections 6.3.1 and 6.3.3, respectively, as well as the CBUAE’s Guidance for LFIs providing services to Legal Persons and Arrangements9 for further information.
9 Available at: centralbank.ae/en/cbuae-amlcft.
3.3.1.3. Understanding the Nature of the Customer’s Business and the Nature and Purpose of the Business Relationship
Under Article 8 of the AML-CFT Decision, insurance operators are required to understand the nature of the customer’s business and the nature and purpose of the operator’s relationship with the customer, including the expected uses to which the customer will put the operator’s products or services. This step requires the operator to collect information that allows it to create a profile of the customer, including the types and volumes of transactions the customer is expected to engage in, and to assess the risks associated with the relationship. In certain instances, the expected type and volume of transactions are implicit in the specific insurance product being provided, in which case this aspect of the customer’s profile can be derived directly from the product choice.
Obtaining a sufficient understanding of its customers and the nature and purpose of the customer relationship—together with the ongoing analysis of actual customer behavior and the behavior of relevant peer groups—allows the insurance operator to develop a baseline of normal or expected activity for the customer, against which unusual or potentially suspicious transactions can be identified. This element of CDD can also serve to inform the operator’s risk rating or other risk assessment of the customer for the purposes of performing risk-based ongoing monitoring (see section 3.3.1.4) and determining whether simplified or enhanced due diligence measures may be warranted (see sections 3.3.3 and 3.3.4, respectively).
3.3.1.4. Ongoing Monitoring
Under Article 12 of the AML-CFT Decision, insurance operators are required to subject all customers to ongoing monitoring throughout the business relationship. Ongoing monitoring ensures that the operator’s products and services are being used in accordance with the customer profile developed through CDD during onboarding, and that transactions are normal, reasonable, and legitimate.
Insurance operators are required to ensure that the CDD information they hold on all customers is accurate, complete, and up to date. This is particularly crucial in the context of customers that are companies or that engage in business. Operators should update CDD for all customers on a risk-based schedule, with CDD on higher-risk customers being updated more frequently. EDD on all customers should involve more frequent CDD updates.
CDD updates should include a refresh of all elements of initial CDD, and in particular should ascertain that:
• The customer’s beneficial owners remain the same; • The customer continues to have active status with a company registrar; • The customer has the same legal form and is domiciled in the same jurisdiction; and • The customer is engaged in the same type of business and in the same geographies.
In addition to a review of the customer’s CDD file, under Article 7 of the AML-CFT Decision, the operator must also review the customer’s transactions to ensure that the transactions conducted are consistent with the information they have about the customer, their type of activity and the risks they pose, including, when necessary, the source of funds. It must determine whether they continue to fit the customer’s profile and business and are consistent with the business the customer is expected to engage in when the business relationship was established. This type of transaction review is distinct from the transaction monitoring discussed in section 3.4 below and its purpose is to complement it by identifying behaviors, trends, or patterns that are not necessarily subject to transaction monitoring rules. The techniques used for transaction review will vary depending on the customer. For lower-risk customers, a review of alerts, if any, is likely to be sufficient. For higher-risk customers, a more intensive review may be necessary. For customers with a large volume of transactions, operators may use data analysis techniques.
If the review finds that the customer’s behavior or information has materially changed, the operator should risk-rate the customer again. New information gained during this process may cause the operator to determine that EDD is necessary or may bring the customer into the category of customers for which EDD is mandatory (i.e., customers that are PEPs, or owned or controlled by PEPs, the direct family members or associates known to be close to the PEPs; customers that are based in high-risk jurisdictions; etc.).
Operators may consider requiring that the customer update them on any changes in its beneficial ownership or business activities. Even if this requirement is in place, however, operators should not rely on the customer to notify it of a change but should still update CDD on a schedule appropriate to the customer’s risk rating.
3.3.1.5. Non-Face-to-Face Relationships
Insurance operators should develop policies and procedures to address any specific risks associated with non-face-to-face customer relationships and transactions undertaken in the course of such relationships. Such policies and procedures should be applied when establishing a new customer relationship and when conducting ongoing monitoring, and should be at least as stringent as those that would be required to be performed if there was face-to-face contact.
○ Note: Relationships in which personal contact between an insurer or agent and the customer is achieved via video teleconference are not considered to be non-face-to-face relationships for the purpose of this Guidance.
Heightened ML/FT risks may arise from establishing business relationships or undertaking transactions according to instructions conveyed by customers over the internet (absent personal contact via video teleconference), post, fax, or telephone. An operator should note that online applications and transactions may pose greater risks than other non-face-to-face business due to the following factors, which taken together may compound the associated ML/FT risks:
• The ease of unauthorized access to the facility, across time zones and locations;
• The ease of making multiple fictitious applications without incurring additional cost or the risk of detection;
• The absence of physical documents; and
• The speed of electronic transactions.
The measures taken by an insurance operator for verifying the identity of customers and beneficial owners in the context of non-face-to-face relationships will depend on the nature and characteristics of the product or service provided and the customer’s risk profile. Where verification of identity is performed without face-to-face contact (e.g., electronically), an operator should apply additional checks to manage the risk of impersonation. The additional checks may consist of robust anti-fraud checks that the operator routinely undertakes as part of its existing procedures, which may include as appropriate and feasible:
• Telephone contact with the customer at a residential or business number that can be verified independently;
• Confirmation of the customer’s address through an exchange of correspondence or other appropriate method;
• Subject to the customer’s consent, telephone confirmation of the customer’s employment status with his or her employer’s human resource department at a listed business number of the employer;
• Confirmation of the customer’s salary details by requiring the presentation of recent bank statements where applicable;
• Provision of certified identification documents by lawyers or notaries public;
• Requiring the customer to make an initial premium payment using a check drawn on the customer’s personal account with a bank in the UAE; and
• Video call with the customer. 3.3.1.6. Name Screening
An insurance operator should screen the following parties against relevant ML/FT information sources (such as negative media databases) and internal watchlists (such as lists of customers previously exited for financial crime reasons) prior to a customer's onboarding:
• All customers, regardless of risk rating or risk profile;
• Beneficial owners of legal entity customers;
• Natural persons appointed to act on behalf of the customer (see section 3.3.2.1);
• Directors, partners, and managers of customers that are legal persons;
• Natural persons having executive authority over customers that are legal arrangements; and
• Insured with no active powers on the contract (if any).
With respect to sanctions lists, the parties listed above must be screened prior to a customer's onboarding and on an ongoing basis thereafter (please see section 3.5 below). In addition, at the time of payout, an insurer must screen against sanctions lists and should screen against the same other lists and information sources all beneficiaries or other payees and their beneficial owners (where applicable).
The results of screening and assessment by the insurance operator should be documented. Please consult the CBUAE’s Guidance for Licensed Financial Institutions on Transaction Monitoring and Sanctions Screening10 for further information.
10 Available at: centralbank.ae/en/cbuae-amlcft.
3.3.1.7. Customer Rejection and Exit
Insurance operators should not deal with any person on an anonymous basis or any person using a fictitious name. Prior to establishing an insurance relationship, if an insurance operator has any reasonable grounds to suspect that the assets or funds of a customer are the proceeds of crime or related to the financing of terrorism, the operator should reject the business relationship and, per Article 17 of the AML-CFT Decision, file a suspicious transaction report (“STR”) with the UAE Financial Intelligence Unit (“FIU”).
As per article 13 of the AML-CFT Decision, where an insurance operator is unable to undertake the CDD measures described above, or is a confirmed match to a party included on applicable sanctions lists, the insurance operator must:
• Not onboard the customer;
• Exit the relationship if one has been established;
• Not make any payment to a payee or beneficiary under the customer’s policy or other insurance relationship; and • Maintain the related records (Please see Section 3.10 below).
In addition, it should add the customer, its beneficial owners, directors, and managers to internal watchlists. The operator should also determine whether the circumstances warrant the filing of a suspicious transaction report (“STR”) or SAR.
3.3.2. Specific CDD Measures for Insurers
In addition to performing general CDD on their customers, insurers are also expected to collect and verify the identities of any natural persons appointed to act on the customer’s behalf and are required, under Article 11 of the AML-CFT Decision, to collect and verify the identities of the beneficiaries or other payees of an insurance policy and their beneficial owners (where applicable), as set forth below.
3.3.2.1. Identification and Verification of Natural Persons Appointed to Act on a Customer’s Behalf
As per Article 8.2 of the AML-CFT Decision, where a customer appoints one or more natural or legal persons (such as an insurance broker) to act on his, her, or its behalf in establishing a business relationship with an insurer, the insurer must identify and verify the identity of each such natural person in accordance with the same procedures used to identify and verify the identity of a natural person customer. The insurer should also verify the due authority of each natural person appointed to act on behalf of the customer by obtaining, at a minimum:
• The appropriate documentary evidence authorizing the appointment of such natural or legal person by the customer to act on his, her, or its behalf; and
• The signature of such a natural or legal person appointed.
As with customers, natural persons appointed to act on a customer’s behalf should generally be identified and verified prior to establishing a business relationship. However, in exceptional circumstances, where there is no ML/FT suspicion, and ML/FT risks are assessed to be low, and where the deferral of verification is essential in order not to interrupt the normal course of business operations, an operator may complete the verification of the appointed person’s identity after establishing a business relationship, as set forth in section 3.3.3 below.
3.3.2.2. Identification and Verification of Beneficiaries or Other Payees and Their Beneficial Owners
Under Article 11.1 of the AML-CFT Decision, insurers are required to conduct CDD measures, including ongoing monitoring, with respect to any beneficiary of life insurance and other investment insurance insurance products, including life insurance products relating to investments and family Takaful insurance, as soon as the beneficiary is identified or designated. In addition, as soon as a beneficiary or other payee is designated, an insurer must perform the following:
• For a beneficiary or payee who is identified as a specifically named natural person, legal person, or legal arrangement, obtain the full name, including any aliases, of such beneficiary or payee; or • For a beneficiary or payee who is designated by characteristics, class, or other means, obtain sufficient information concerning the beneficiary or payee to satisfy itself that it will be able to establish the identity of such beneficiary or payee at the time of payout. • At the time of payout, insurers must also verify the identities of all beneficiaries or payees and their beneficial owners in accordance with the same procedures used to identify and verify the identity of a natural person customer. 3.3.3. Simplified Due Diligence for Lower-Risk Scenarios
As per Article 4.3 of the AML-CFT Decision, an insurance operator may perform simplified due diligence (“SDD”) measures in relation to a customer, a beneficial owner of a customer, a natural person appointed to act on behalf of a customer, or a beneficiary or other payee if it is satisfied that the risks of ML/FT are low. The assessment of low risks should be supported by an adequate analysis of risks by the insurance operator, and the selection of simplified measures should be commensurate with the type and level of risk identified through such risk analysis. In all cases, the operator should document the details of its risk analysis and the nature of the SDD measures employed.
Examples of potentially lower-risk scenarios include, but are not limited to, those in which:
• The customer is a UAE government entity, including UAE state-owned enterprises; • The customer is an entity listed on a stock exchange and subject to regulatory disclosure requirements relating to adequate transparency with respect to beneficial owners; • The insurance product does not offer cash payouts except upon the occurrence of specified trigger events; • The insurance product does not have an early surrender option and cannot be used as collateral; or • The insurance product is a pension or other scheme where contributions are made via deduction from wages and scheme rules and do not permit the assignment of a member’s interest under the scheme.
Additional examples of lower-risk attributes for the insurance sector are provided in section 2.2 above.
Where an insurance operator is satisfied that the ML/FT risks are low, the operator may perform one or more of the following SDD measures, as warranted by the risk analysis:
• Verifying the identity of the customer and any beneficial owner(s) after establishing the business relationship, provided verification is nonetheless completed in a timely fashion (to be documented in the operator’s internal procedures) and appropriate controls are in place to manage the ML/FT risks associated with the customer and the relationship prior to verification;11 • Reducing the frequency of updates to CDD information; • Reducing the degree of ongoing monitoring and scrutiny of transactions, based on a reasonable monetary threshold; or • Developing an understanding of the intended nature and purpose of the customer relationship on the basis of the relationship type and the customer’s historical transaction activity, rather than by collecting information regarding the intended nature and purpose of the relationship during onboarding or CDD updating.
An insurance operator should not perform SDD measures where:
• A customer or any beneficial owner of the customer is from or in a country or jurisdiction against which the FATF has called for countermeasures; • A customer or any beneficial owner of the customer is from or in a country or jurisdiction known to have inadequate AML/CFT measures, as determined by the operator for itself or notified to operators generally by local regulatory or supervisory authorities; or • The operator suspects that ML or FT is involved. 11 Such measures may include holding funds in suspense or escrow until verification of identity has been completed or making completion of identity verification a precondition of closing any transaction with or on behalf of the customer.
3.3.4. Enhanced Due Diligence for Higher-Risk Scenarios
The AML-CFT Law and the AML-CFT Decision impose specific and enhanced due diligence obligations on insurance operators with respect to two classes of customers or transactions:
• Customers that are politically exposed persons (“PEPs”), which include the direct family members or associates known to be close to the PEPs; and
• Business relationships and transactions with natural persons, legal persons, or legal arrangements from high-risk countries.
The AML-CFT Law and Decision give special attention to customers in these groups because they are likely to expose operators to a heightened risk of money laundering, terrorism financing, and other illicit finance.
In addition to these classes of customers and transactions, for which EDD is mandatory, operators are expected to implement appropriate policies and procedures to determine whether relationships with or transactions undertaken for or on behalf of a customer present a higher risk for ML or FT. Examples of potentially higher-risk scenarios include, but are not limited to, those in which:
• The customer belongs to a higher-risk industry or sector identified in topical risk assessments, or to an industry or sector identified by the operator as higher-risk for ML or FT;
• The ownership structure of a legal entity customer appears unusual or excessively complex given the nature of the legal entity’s business;
• The legal entity customer is a personal asset-holding vehicle;
• The business relationship is conducted under unusual circumstances, such as significant unexplained geographic distance between the operator and the customer;
• The legal entity customer has nominee shareholders or shares in bearer form;
• The customer is a cash-intensive business;
• The customer operates in or does business with a jurisdiction that has relatively higher levels of corruption or organized crime, or inadequate AML/CFT measures, as identified by the FATF;
• The customer operates in or does business with a jurisdiction identified by credible bodies (e.g., reputable international bodies such as Transparency International) as having significant levels of corruption, terrorism financing, or other criminal activity;
• The relationship involves or could involve cash or anonymous transactions;
• The relationship involves or could involve frequent payments received from unknown or unassociated third parties.
Additional examples of higher-risk attributes and red flag indicators for the insurance sector are provided in section 2.2 and Annex 1 of this Guidance respectively.
As per Article 4.2 b) of the AML-CF Decision, where the operator identifies a customer or relationship as presenting higher ML/FT risks, it must apply EDD measures commensurate with those risks. Examples of EDD measures include but are not limited to:
• Obtaining approval from the operator’s senior management to establish or continue a business relationship with the customer, including making any payment to a beneficiary or payee;
• Establishing the source of wealth and source of funds of the customer and any beneficial owner of the customer;
• Conducting enhanced monitoring during the course of the business relationship with the customer, including by increasing the degree and nature of transaction monitoring and CDD updating;
• Requiring the first payment to be carried out through an account in the customer’s name with a bank subject to similar or equivalent CDD standards;
• Using public sources of information (e.g., websites) to gain a better understanding of the reputation of the customer or any beneficial owner of the customer;
• Commissioning external intelligence reports where it is not possible for the operator to easily obtain information through public sources or where there are doubts about the reliability of public information; and
• For high-net-worth individuals, particularly those utilizing higher-risk products or services or characterized by other markers of heightened ML/FT risk:
○ Independently corroborating information obtained on the source of wealth of customers and beneficial owners against documentary evidence or public information sources;
○ Screening operating companies and individual benefactors contributing to the customer’s and beneficial owner’s wealth or funds; and
○ Scrutinizing transactions relating to customers that have multiple policies with the operator or to customers having a common beneficial owner.
In addition, as noted in section 3.3.1.2 above, if the insurance operator has followed its standard beneficial ownership identification and verification procedures and is still not confident that it has identified the individuals who truly own or control the customer, or when other high-risk factors are present, the operator should consider intensifying its efforts to identify the beneficial owners. The most common method of doing so is to identify additional beneficial owners below the 25 percent ownership threshold mandated by UAE law. This may involve identifying and verifying the identity of beneficial owners at the 10 percent or even the 5 percent level, as risk warrants. It may also involve requiring the customer to provide the names of all individuals who own or control any share in the customer—without requiring them to undergo CDD—in order to conduct sanctions screening or negative news checks.
Additional examples of EDD measures are provided in the CBUAE’s AML/CFT Guidelines for Financial Institutions, section 6.4.
3.4. Transaction Monitoring and Suspicious Transaction Reporting
3.4.1. Transaction Monitoring
Under Article 16 of the AML-CFT Decision, insurance operators must monitor activity by all customers to identify behavior that is potentially suspicious and that may need to be the subject of an STR or SAR when conducting operations related to life insurance and other investment-related insurance products. Transactions may be suspicious simply in virtue of their individual characteristics (such as their value, source, destination, or use of intermediaries) or because, together with other transactions, they form a pattern that diverges from expected or historical transactional activity or may otherwise be indicative of illicit activity, including the evasion of reporting or recordkeeping requirements. When monitoring and evaluating transactions, the operator should take into account all information that it has collected as part of CDD, including the identities of beneficial owners. In addition, higher-risk customers should be subject to more stringent transaction monitoring, with lower thresholds for alerts and more intensive investigation.
Transaction monitoring can include manual monitoring processes and the use of automated and intelligence-led monitoring systems. In all cases, the appropriate type and degree of monitoring should appropriately match the ML/FT risks of the operator’s customers, products and services, delivery channels, and geographic exposure, and may therefore vary across an operator’s business lines or units, where applicable.
Transaction monitoring programs should also be calibrated to the size, nature, and complexity of each institution. Operators with a larger scale of operations are expected to have in place automated systems capable of handling the risks from an increased volume and variance of transactions. Operators utilizing automated systems should perform a typology assessment to design appropriate rule- or scenario-based automated monitoring capabilities and processes. While smaller operators may rely on transaction monitoring systems that are less automated, they should still ensure that these are appropriately executed to address the risks from their day-to-day transactional activity.
Please consult the CBUAE’s Guidance for Licensed Financial Institutions on Transaction Monitoring and Sanctions Screening for further information.
3.4.2. STR Reporting
As required by Article 15 of the AML-CFT Law and Article 17 of AML-CFT Decision, insurance operators must file without any delay an STR or SAR with the UAE FIU when they have reasonable grounds to suspect that a transaction, attempted transaction, or certain funds constitute, in whole or in part, regardless of the amount, the proceeds of crime, are related to a crime, or are intended to be used in a crime. STR/SAR filing is not simply a legal obligation; it is a critical element of the UAE’s effort to combat financial crime and protect the integrity of its financial system. STR/SAR filings are essential to assisting law enforcement authorities in detecting criminal actors and preventing the flow of illicit funds through the UAE financial system.
In addition to the requirement to file an STR when an operator suspects that a transaction or funds are linked to a crime, operators should consider filing an STR or SAR in the following situations involving higher-risk customers:
• A potential customer decides against purchasing financial services after learning about the operator’s CDD requirements; • A current customer cannot provide required information (including documentation) about its business or its beneficial owners; • A customer cannot adequately explain transactions, provide supporting documents such as invoices, or provide satisfactory information about its counterparty; • The operator is not confident, after completing CDD procedures, that it has in fact identified the individuals owning or controlling the customer. In such cases, the operator should not establish the business relationship, or continue an existing business relationship; or • Other situations that are suspicious or involve activity with no legitimate business or other lawful purpose.
Please consult the CBUAE’s Guidance for Licensed Financial Institutions on Suspicious Transaction Reporting12 for further information.
12 Available at: uaeiec.gov.ae/en-us/un-page.
3.5. Sanctions Obligations and Freezing Without Delay
The AML-CFT Law and AML-CFT Decision require insurance operators to promptly apply directives issued by the Competent Authorities of the UAE for implementing the decisions issued by the United Nations Security Council (“UNSC”) under Chapter VII of the Charter of the United Nations (“UN”). In furtherance of this requirement, the Cabinet Decision No. (74) of 2020 sets out the legislative and regulatory framework regarding the Targeted Financial Sanctions (“TFS”), including the Local Terrorist List and the UN Consolidated List. As per Cabinet Decision 74 and in particular its Article 15, all insurance operators without any exception, are obliged to apply policies, procedures and controls to implement TFS to those sanctioned and designated in the Local Terrorist List and the UN Consolidated List.
For more information and details on their obligations in relation to their sanctions obligations, insurance operators should consult the Executive Office for Control and Non-Proliferation (former Executive Office of the Committee for Goods and Materials Subjected to Import and Export Control‘s – referred to as the Executive Office) “Guidance on Targeted Financial Sanctions for Financial Institutions and designated non-financial business and professions”13; the CBUAE’s Guidance for Licensed Financial Institutions on the Implementation of Targeted Financial Sanctions as well as the CBUAE’s Guidance for Licensed Financial institutions on Transaction Monitoring Screening and Sanctions screening and any of their amendments or updates thereof. Insurance operators should also consult the CBUAE’s and the Executive Office’s websites as updated from time to time, and refer to the Executive Office’s list of Frequently Asked Questions (FAQ) for the insurance sector.
13 Available at: uaeiec.gov.ae/en-us/un-page.
3.6. Third-Party Reliance and Outsourcing
As noted above, insurers are permitted to delegate the performance of specified controls to insurance agents or other intermediaries, using either a third-party reliance or an outsourcing model.
• Under a third-party reliance model, insurers may rely on any third-party LFI, such as a bank or insurance agent or broker, to perform the elements of general CDD described in sections 3.3.1.1 through 3.3.1.3, following the third party’s AML/CFT policies and procedures. In such circumstances, the third party will usually have an existing business relationship with the customer, which is independent of the relationship to be formed by the customer with the relying institution. The third-party reliance model is most commonly employed in the case of insurance brokers, who sell insurance products to consumers on behalf of multiple insurers and therefore typically maintain and apply their own AML/CFT policies and procedures. • Under an outsourcing model, by contrast, insurers may engage a third-party service provider, such as an insurance agent or other intermediary, to apply some or all of the AML/CFT preventive measures described in this section on behalf of the delegating institution, following the insurer’s AML/CFT policies and procedures. In an outsourcing scenario, the third party is subject to the delegating insurer’s control regarding the effective implementation of those policies and procedures by the outsourcing entity. The outsourcing model is most commonly employed in the case of tied agents, who sell insurance products to consumers exclusively on behalf of a single insurer and therefore typically follow the insurer’s AML/CFT policies and procedures.
Under either model, the insurer retains ultimate responsibility for the implementation of applicable AML/CFT preventive measures.
3.6.1. Third-Party Reliance
Insurers are permitted to rely on third-party LFIs to perform the elements of general CDD described in sections 3.3.1.1 through 3.3.1.3, provided the insurer relying on a third party:
• Immediately obtains the necessary CDD information concerning the elements described in sections 3.3.1.1 through 3.3.1.3; • Takes adequate steps to satisfy itself that copies of identification data and other relevant documentation relating to the CDD requirements will be made available from the third party upon request without delay; • Satisfies itself that the third party is regulated, supervised, or monitored for, and has measures in place for compliance with, CDD and recordkeeping requirements in line with FATF standards and local law and regulation; and • Takes appropriate steps to identify, assess, and understand the ML/FT risks specific to the countries or jurisdictions in which the third party operates.
With respect to the second of these conditions, a best practice is for insurers to obtain a copy of the relevant CDD records or have direct access to the database where such information is held, in order to facilitate ongoing monitoring of the business relationship and, if applicable, the filing of STRs and for a complete assessment record in case of a change of intermediary servicing the policy.
Insurers are not permitted to rely on third parties to conduct ongoing monitoring of business relationships (described in section 3.3.1.4), although they may outsource such functions following the guidelines described immediately below.
3.6.2. Outsourcing
In an outsourcing or agency scenario, the outsourced entity applies CDD or other AML/CFT measures on behalf of the delegating insurer, in accordance with the insurer’s internal policies and procedures, and is subject to the insurer’s control of the effective implementation of those policies and procedure by the outsourced entity. When outsourcing a part of their AML/CFT function, including the distribution of products, an insurer should therefore include any outsourced entity in its own AML/CFT program and internal control processes, and should monitor such an entity for compliance with its internal AML/CFT policies and procedures. Outsourced entities should also be subject to the employee and agent screening and monitoring checks described immediately below.
3.7. Employee, Officer, Agent, and Broker Risk Management
Insurance operators should have in place screening procedures to ensure high standards when hiring employees, appointing officers, or engaging agents or brokers (including but not limited to outsourced entities, as described in section 3.6.2 above). Employee, officer, and agent or broker screening procedures should include:
• Background checks of employment history; and • Screening against sanctions lists, ML/FT information sources, and internal watchlists.
In addition, insurance operators should conduct credit history checks on a risk basis. The operator should be aware of potential conflicts of interest for staff with AML/CFT responsibilities and should act to reduce or manage such conflicts of interest, for example by reallocating responsibilities or by instituting quality controls and “four-eye” reviews of the conflicted employee’s work.
Operators should also monitor on an ongoing basis for possible indicators of suspicious or illicit behavior by employees, such as:
• An employee whose lifestyle cannot be supported by his/her salary, which may indicate receipt of tips or bribes. • An employee who is reluctant to take a vacation, which may indicate they have agreed or are being forced to provide services to customers in violation of the law or company policy. • An employee who is associated with an unusually large number of transactions or a transaction in an unusually large amount, which may indicate they have agreed or are being forced to provide services to customers in violation of the law or company policy. 3.8. Training
As with all risks to which the operator is exposed, the AML/CFT training program should ensure that employees are aware of the risks facing the insurance sector for life insurance and other investment-related insurance products, familiar with the obligations of the operator, and equipped to apply appropriate risk-based controls. Training should be tailored and customized to the operator’s risk and the nature of its operations, and should be clearly documented in the operator’s AML/CFT compliance program and associated training policies, procedures, plans, materials, and attendance records.
3.9. Governance and Independent Audit
The specific preventive measures discussed above should take place within, and be supported by, a comprehensive institutional AML/CFT program that is appropriate to the risks the operator faces and organized in accordance with the “three lines of defense” model. All three lines of defense must report up to and have the active support and oversight of the operator’s senior management, defined broadly to include executives, senior leadership, and the Board of Directors.
Under the model, an operator’s business units, sales or relationship managers, and other frontline personnel represent the units or functions that create risk and should therefore serve as the first line of defense against ML/TF, and other forms of illicit activity. They should scrutinize customers and their related parties at onboarding and performing periodic and risk-based reviews to update customer information and the operator’s understanding of the customer’s risks.
The operator’s AML/CFT compliance function, in turn, constitutes the second line of defense, supporting the frontline units’ risk management activities through its system of internal controls and related monitoring, reporting, and risk assessment responsibilities. The core of an effective risk-based program is an appropriately experienced AML/CFT compliance officer, located within the second line of defense, who understands the operator’s risks and obligations and who has the resources and autonomy necessary to ensure that the operator’s program is effective.
Finally, under article 20.6 of the AML-CFT decision, operators must be subject to independent testing by internal or external auditors, who represent the third line of defense by providing independent assurance to the Board and executive management on the effectiveness and adequacy of the operator’s governance, risk management, and internal controls. Auditors should have sufficient expertise and understanding of ML/FT risks and requirements and should be fully independent of the activities and reporting structure of the functions subject to independent testing.
Additionally, as per article 32 of the AML-CFT decision, operators with overseas branches, subsidiaries, or other affiliates or legal entities must ensure that all entities within the affiliate network are subject to the AML/CFT policies, procedures, and controls that are at least as stringent as those in place at the entity located in the UAE. Likewise, all entities within the affiliate network should be included in the operator’s enterprise risk assessment and subject to AML/CFT independent testing and consolidated governance and oversight.
3.10. Record Keeping
According to Article 16 of the AML-CFT Law and Article 24 of the AML-CFT Decision, insurance operators must maintain detailed records associated with their ML/FT risk assessment and mitigation measures as well as records, documents, data and statistics for all financial transactions, all records obtained through CDD measures for both the originators and the beneficiaries, account files and business correspondence, copies of personal identification documents, including STRs/SARs and results of any analysis performed. Operators should maintain the records in an organized manner so as to permit data analysis and the tracking of financial transactions. Records should be sufficient to permit reconstruction of individual transactions so as to provide, if necessary, evidence for prosecution of criminal activity. Operators must make the records available to the competent authorities immediately upon request.
The statutory retention period for all records is at least five (5) years, from the date of completion of the transaction or termination of the business relationship with the customer, or from the date of completion of the inspection by the CBUAE, or from the date of issuance of a final judgment of the competent judicial authorities, or liquidation, dissolution, or other form of termination of a legal person or arrangement, all depending on the circumstances.
Annex 1. Red Flag Indicators for the UAE Life Insurance Sector
The UAE Insurance Authority (now merged with the CBUAE) has issued the following list of red flag indicators when handling life insurance and other investment-related insurance products. 14 These indicators should be incorporated into an insurance operator’s AML/CFT policies, procedures, detection scenarios, and other processes for identifying potentially suspicious activity related to life and general insurance products.
1. The purchase of an insurance product does not reflect a customer’s known needs (e.g., purpose of the account). 2. The early surrender of an insurance product is taken at a cost to the customer. 3. The surrender of an insurance product is initiated with the refund directed to a third party. 4. The customer exhibits no concern for the investment performance of a purchased insurance product and instead exhibits significant concern for its early surrender terms. 5. The customer purchases insurance products using unusual payment methods, such as cash or cash equivalents, or with monetary instruments in structured amounts. 6. The customer demonstrates reluctance to provide identifying information when purchasing an insurance product. 7. The customer borrows the maximum amount available from their insurance product shortly after purchase. 8. The customer used to purchase low-premium insurance and pay premiums by making regular payments but suddenly purchases insurance that requires a large lump-sum premium payment, for which no reasonable explanations are provided. 9. The customer purchases an insurance product without concern for the coverage or benefits, or the customer only cares about the procedures for the policy loan, cancellation of insurance policy, or changing beneficiary when purchasing an insurance policy that has a high cash value or requires a high lump-sum premium payment. 10. The customer usually pays a premium by making regular payments but suddenly requests to purchase a large-sum policy by paying off premium all at once. 11. The customer purchases insurance products with high cash value successively over a short period of time, and the insurance products purchased do not appear to be commensurate with the customer’s status and income or are unrelated to the nature of the customer’s business. 12. The customer pays premiums in cash and in several payments marginally below the threshold for declaration but cannot reasonably explain the source of funds. In addition, the transactions do not appear to be commensurate with the customer’s status and income or are unrelated to the nature of the customer’s business. 13. The customer, after making a large premium payment for a policy purchased, applies for a large policy loan or cancels the policy in a short period of time, for which no reasonable explanations are provided. 14 Sources: FATF, Life Insurance Sector: Guidance for a Risk-Based Approach (October 2018), available at: fatf-gafi.org/media/fatf/documents/recommendations/pdfs/RBA-Life-Insurance.pdf; and U.S. Federal Financial Institutions Examination Council, Bank Secrecy Act/Anti-Money Laundering Examination Manual, “Insurance,” available at: bsaaml.ffiec.gov/manual/RisksAssociatedWithMoneyLaunderingAndTerroristFinancing/16.
Annex 2. Synopsis
Purpose of this Guidance Purpose The purpose of this Guidance is to assist the understanding of risks and effective performance by CBUAE licensed insurers, agents, and brokers of their AML/CFT obligations. Applicability This Guidance applies to all insurance and re-insurance companies, agents, and brokers that are licensed and supervised by the CBUAE. Understanding and Assessing ML/FTRisks Overview of Insurance Sector Activities and Participants Under Article 2.16 of the AML-CFT Decision, as amended, only direct insurance and re-insurance operations with respect to insuranee of persons and funds accumulation (referred to as life insurance and other investment-related insurance products' hereafter) are subject to the UAE's AML/CFT legal and regulatory framework, with the exception of the targeted financial sanctions' requirements applicable for all insurance operators. Insurance sector participants include operators in the insurance sector, which sell or facilitate the sale of insurance products and must be licensed by the CBUAE, and customers, who own, pay for, and/or are covered by or the beneficiaries of insurance products. • Operators principally include insurers, re-insurers, insurance agents, and insurance brokers. Operators also include consultants, actuaries, loss and damage adjusters, third-party administrators, insurance producers, and price comparison websites (or "insurance aggregators"), although due to their reduced risk exposure these operators are not subject to the Guidance with the exception of the requirements relating to targeted financial sanctions. • Customers principally include policy holders (or "policy owners), policy payers, insureds, and beneficiaries. ML/FT Risks relevant to life insurance and other investment-related insurance products • Criminal actors may use life insurance and other investment-related insurance products to place illicit proceeds into the financial system, especially (though not exclusively) where the insurer or intermediary accepts premium payments in cash. • Reimbursed premiums, withdrawn contributions, and payout proceeds (whether legitimate or fraudulent) can be deposited into a bank account or used to purchase other financial instruments without necessarily revealing the ultimate origin of the funds. • Life and other investment-related products are generally considered to present higher ML/FT risk, particularly where they have high cash values upon surrender (e.g. assigning policies and payments to third parties, borrowing against the cash surrender value of permanent life insurance policies, selling units in investment-linked products or buying products with insurance termination features without concern for the product's investment performance). Product Risk Factors Higher-risk productscan include those: whose design allows the insurance operator to hold funds or transact large sums on behalf of the customer; provides for customer anonymity or third-party transactions; has no (or very small) fees or penalties for early withdrawal; allows the product to be held for a shorter period of time; and makes it difficult to identify if products are not being used as intended. Service and Transaction Risk Factors Higher-risk services and transactions can include those: for which it is difficult to trace the ownership of funds; where the customer is not the payer or recipient of the funds; where the payment source or recipient is based outside the country; or involving a large number or transactions back and forth or significant, unexpected, and unexplained changes in the customer's typical activity. Distribution Channel and Intermediary Risk Factors Higher-risk distribution channels can include those: involving a distributor or other intermediary that is not subject to AML/CFT requirements; where the customer pays a distributor, who then pays the insurer; or where the customer has a purely non-face-to-face relationship with insurers or agents (e.g., insurance sold online without adequate safeguards to confirm identity). Customer Risk Factors Higher-risk customers can include those: with incomplete or questionable identification; who are controlled by third parties; that are legal entities with a complex structure: in high-risk industries; making high-value transactions without a confirmed source of funds or wealth; who are new to the insurer; who only hold non-registered policies or accounts; who are politically exposed persons; or who are sanctioned, have ties to sanctioned persons, or are associated with negative news. Geographic Risk Factors Higher-risk geographies can include: regions with high frequency and severity of crimes with ML risk; regions that experience a higher incidence of high-risk activity or fraud; countries risk-rated as high by the insurer; or countries on the NAMLCFTC's or FATF's lists of high-risk jurisdictions or FATF's list of jurisdictions under increased monitoring. Mitigating Risks Risk-Based Approach and Enterprise Risk Assessment Any insurance operator is required to perform, document, and keep up to date an enterprise risk assessment for the purposes of identifying, assessing, and understanding its ML/TF risks for life insurance and other investment-related insurance products and to ensure that identified risks are within the institution's risk appetite and that identified deficiencies are appropriately tracked and remediated. New Products, Practices, and Technologies An insurance operator is required to identify, assess, and take steps to mitigate the ML/TF risks for life insurance and other investment-related insurance products that may arise in relation to: (i) the development of new products and new business practices, including new delivery mechanisms; and (ii) the use of new or developing technologies for both new and preexisting products. The operator must undertake such risk assessments prior to the launch or use of the new products, practices, and technologies and must take appropriate measures to manage and mitigate the identified risks Customer Due Diligence ("CDD") For life insurance and other investment-related insurance products, all insurance operators must perform general CDD on their customers, including customer identification and verification, beneficial ownership identification and verification, understanding the nature of the customer's business and the nature and purpose of the relationship, ongoing monitoring, and name screening. • Additionally, insurance operators are expected to collect and verify the identities of: (i) any natural persons appointed to act on the customer's behalf and (ii) the beneficiaries or other payees of an insurance policy and their beneficial owners. • In low-risk scenarios, insurance operators may perform certain simplified due diligence ("SDD") measures, such as verifying the customer's or beneficial owner's identity after establishing the business relationship, unless there is a suspicious of ML/TF. • In higher-risk scenarios, insurance operators must perform enhanced due diligence ("EDD")measures, such as establishing the source of wealth or funds or conducting enhanced monitoring during the course of the business relationship. Transaction Monitoring and STR Reporting When conducting operations related to life insurance and other investment-related insurance products, Insurance operators must monitor activity by all customers to identify behavior that is potentially suspicious. Insurance operators must file without any delay an STR or SAR with the UAE FIU when they have reasonable grounds to suspect that a transaction, attempted transaction, or certain funds constitute, in whole or in part, regardless of the amount, the proceeds of crime, are related to a crime, or are intended to be used in a crime. Please consult CBUAE's Guidance for Licensed Financial Institutions (LFI) on Transaction Monitoring and Sanctions Screening as well as CBUAE's Guidance for LFIs on Suspicious Transaction Reporting. Sanctions Obligations and Freezing without delay All insurance operators without any exception, are obliged to apply policies, procedures and controls to implement TFS to those sanctioned and designated in the Local Terrorist List and the UN Consolidated List. Please consult the Executive Office for Control and Non-Proliferation (previously known as the Executive Office of the Committee for Goods and Materials Subjected to Import and Export Control's - referred to as the Executive Office) "Guidance on TFS for Financial Institutions and designated non-financial business and professions"; the CBUAE's Guidance for LFIs on the Implementation of Targeted Financial Sanctions as well as the CBUAE's Guidance for LFIs on Transaction Monitoring Screening and Sanctions screening. Insurance operators should also consult the CBUAE's and the Executive Office's websites as updated from time to time (in particular the Executive Office's list of FAQ for the insurance sector). Third-Party Reliance and Outsourcing Insurers are permitted to delegate the performance of specified controls to insurance agents or other intermediaries, using either a third-party reliance model (whereby a third-party licensed financial institution carries out CDD measures following its own AML/CFT policies and procedures) or an outsourcing model (whereby insurers engage a third-party service provider to apply all or some of the insurer's own AML/CFT policies and procedures). Under either model, the insurer retains ultimate responsibility for the implementation of applicable AML/CFT preventive measures. Employee, Officer, Agent, and Broker Risk Management Insurance operators should have in place screening procedures to ensure high standards when hiring employees, appointing officers, or engaging agents or brokers. Operators should also monitor on an ongoing basis for possible indicators of suspicious or illicit behavior. Training An operator's AM L/CFT training program should ensure that employees are aware of the risks facing the insurance sector for life insurance and other investment-related insurance products, are familiar with the obligations of the operator, and are equipped to apply appropriate riskbased controls. Governance and Independent Audit The preventive measures discussed above should take place within, and be supported by, a comprehensive institutional AML/CFT program that is appropriate to the risks the operator faces and organized in accordance with the "three lines of defense" model, comprising business unites, a compliance function, and an independent audit function. Guidance for Licensed Financial Institutions on Digital Identification for Customer Due Diligence
Effective from 31/10/20221. Introduction
1.1. Purpose
Article 44.11 of the Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organisations charges Supervisory Authorities with “providing Financial Institutions…with guidelines and feedback to enhance the effectiveness of implementation of the Crime-combatting measures.”
The purpose of this Guidance is to assist the understanding and effective performance by the United Arab Emirates Central Bank’s (“CBUAE”) licensed financial institutions (“LFIs”) of their statutory obligations under the legal and regulatory framework in force in the UAE. It should be read in conjunction with the CBUAE’s Procedures for Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations (issued by Notice No. 74/2019 dated 19/06/2019), Guidelines on Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations for Financial Institutions (issued by Notice 3090/2021 dated 29/06/2021), and the Guidelines for Financial Institutions adopting Enabling Technologies (dated 11/07/2021), and any amendments or updates thereof.1 As such, while this Guidance neither constitutes additional legislation or regulation nor replaces or supersedes any legal or regulatory requirements or statutory obligations, it sets out the expectations of the CBUAE for LFIs to be able to demonstrate compliance with these requirements. In the event of a discrepancy between this Guidance and the legal or regulatory frameworks currently in force, the latter will prevail. This Guidance may be supplemented with additional separate guidance materials, such as outreach sessions and thematic reviews conducted by the Central Bank.
Furthermore, this Guidance takes into account standards and guidance issued by the Financial Action Task Force (“FATF”), industry best practices and red flag indicators. These are not exhaustive and do not set limitations on the measures to be taken by LFIs in order to meet their statutory obligations under the legal and regulatory framework currently in force. As such, LFIs should perform their own assessments of the manner in which they should meet their statutory obligations.
This Guidance comes into effect immediately upon its issuance by the CBUAE with LFIs expected to demonstrate compliance with its requirements within one month from its coming into effect.
1 Available at centralbank.ae/en/cbuae-amlcft and centralbank.ae/en/fintech-office.
1.2. Applicability
Unless otherwise noted, this guidance applies to all natural and legal persons, which are licensed and/or supervised by CBUAE, in the following categories:
• National banks, branches of foreign banks, exchange houses, finance companies, issuers and providers of stored value facilities, licensed retail payment service providers, card schemes, registered hawala providers, and other LFIs; and • Insurance companies, agencies and brokers. 1.3. Legal Basis
This Guidance builds upon the provisions of the following laws and regulations:
This Guidance also builds on global standards and best practices issued by the Financial Action Task Force (“FATF”)2 and the Wolfsberg Group, as well as on industry standards and best practices.
2 Including FATF Guidance on Digital ID, available at: fatf-gafi.org/publications/fatfrecommendations/documents/digital-identity-guidance.html.
1.4. Acronyms
Terms Description AML Anti-money laundering API Application program interface CBUAE Central Bank of the United Arab Emirates CDD Customer due diligence CFT Combating the financing of terrorism CSP Credential service provider DNFBP Designated non-financial business or profession DPP Data protection and privacy FATF Financial Action Task Force FIDO Fast Identity Online ID Identity IDSP Identity service provider IP Internet Protocol LFI Licensed financial institution MAC Media Access Control MFA Multifactor authentication ML Money laundering NIST National Institute of Standards and Technology OTP One-time password PKI Public key infrastructure PII Personally identifiable information PIN Personal identification number SIM Subscriber identity module TF Terrorist financing 2. Overview of Digital ID Systems and Participants
2.1. Terminology and Definitions
For the purposes of this Guidance, in relation to identifying and verifying the identity of a customer as part of the customer due diligence (“CDD”) process, identity (“ID”) refers to the specification of a unique natural person that is:
• Based on characteristics (attributes or identifiers) of the person that establish a person’s uniqueness in the population or particular context(s); and • Recognized by the state for regulatory and other official purposes.
Proof of identity generally depends on some form of government-provided or issued registration, documentation, or certification (such as a birth certificate, identity card, or digital ID credential) that constitutes evidence of core attributes (such as name and date and place of birth) for establishing and verifying identity. Proof of identity may be provided through general-purpose ID systems (such as national ID and civil registration systems) or various limited-purpose ID systems (such as taxpayer identification numbers, driver’s licenses, passports, voter registration cards, social security numbers, and refugee identity documents).
Digital ID systems use electronic means to assert and prove a person’s identity online and/or in in-person environments, including through the use of:
• Electronic databases, including distributed databases and/or ledgers, to obtain, confirm, store, and/or manage identity evidence; • Digital credentials to authenticate identity for accessing mobile, online, and offline applications; • Biometrics to help identify and/or authenticate individuals; and • Digital application program interfaces (“APIs”), platforms, and protocols that facilitate online identification and the verification and authentication of identity.
Identification Systems in the UAELFIs should understand and utilize national-level identification systems and processes currently in place or under development in the UAE, including but not limited to:
• UAE Pass, the UAE’s first national digital identity and signature solution that enables users to identify themselves to government service providers in all emirates through a smartphone-based authentication protocol and to sign documents digitally with a high level of security. The UAE Pass app uses biometric facial recognition software to verify and register users without requiring an in-person visit to a government services center. The UAE Pass also includes a “digital vault” for storing users’ digital documents and sharing them with government departments, as well as a “digital signature” function to complete official transactions without the need for paper documents or physical signatures.
• Emirates ID, the mandatory, government-issued identity card for all UAE citizens and residents. While issued as a physical card, the Emirates ID card uses public key infrastructure to attach individual identities to digital certificates that can be used to sign and encrypt data, as well as fingerprint biometrics. When verifying an Emirates ID card, LFIs should use the online validation gateway of the Federal Authority for Identity and Citizenship and should keep a copy of the Emirates ID and its digital verification in their records.
• Emirates Facial Recognition, an initiative launched by the UAE Ministry of Interior and Federal Authority for Identity, Citizenship, Customs & Port Security, together with private sector partners. The facial recognition initiative includes a “face fingerprint” system for digital verification of digital transactions and remote identities.
Digital ID systems involve two basic components and an optional third component:
• Identity proofing and enrollment answers the question: Who are you? It involves collecting, validating, and verifying identity evidence and information about a person, establishing an identity account, and binding the individual’s unique identity to authenticators possessed and controlled by this person.
• Authentication and identity lifecycle management answers the question: Are you the person who has been identified and verified? It establishes, based on possession and control of authenticators, that the person asserting the identity is the same person who was identity proofed and enrolled, and ensures that adequate controls are in place to manage events that can occur over the identity lifecycle that affect the use, security, and trustworthiness of authenticators.
• Portability and interoperability mechanisms, where used, enable proof of identity to be portable, so that an individual’s digital ID credentials can be used to prove identity for new customer relationships at unrelated private-sector or governmental entities, without their having to obtain and verify personal data and conduct customer identification and verification each time. Portability and interoperability are optional components of any digital ID system.
Not all elements of a digital ID system are necessarily digital. Some elements of identity proofing and enrollment can be either digital or physical, or a combination; however, binding, credentialing, authentication, and portability/federation (where applicable) are always and necessarily digital. These concepts are explained further in the following sections.
Digital ID systems can enable remote customer identification and verification, support remote financial transactions, and otherwise facilitate non-face-to-face business relationships and transactions, defined as interactions in which the parties are not in the same physical location and conduct activities by digital or other non-physically present means, such as mail or telephone. Under international standards, non-face-to-face business relationships and transactions are included as an example of a potentially higher-risk situation in undertaking CDD.3 However, given the evolution of digital ID technology, architecture, and processes, and the emergence of consensus-based open-source digital ID technical standards, non-face-to-face interactions that rely on reliable, independent digital ID systems with appropriate risk mitigation measures in place may present a standard level of risk, and may even present a lower level of risk where higher assurance levels are implemented and/or appropriate control measures are present.4 See section 4 below for specific risk mitigation measures and strategies that can help ensure that a digital ID system is suitably “reliable” and “independent” in this sense.
3 See The FATF Recommendations, Interpretive Note to Recommendation 10, at 68, available at: fatf- gafi.org/media/fatf/documents/recommendations/pdfs/FATF%20Recommendations%202012.pdf.
4 FATF, Guidance on Digital Identity, at 30, available at: fatf-gafi.org/media/fatf/documents/recommendations/Guidance- on-Digital-Identity.pdf.
2.2. Identity Proofing and Enrollment
Identity proofing and enrollment (with initial binding/credentialing) constitute the first stage of a digital ID system. This component is directly and most immediately relevant to LFIs’ customer identification and verification obligations under Article 8 of the AML-CFT Decision. For illustrative purposes only, Figure 1 below presents a sample process flow for identity proofing and enrollment; the discussion that follows explains each step in greater detail.
Figure 1. Identity Proofing and Enrollment
 Source: The Financial Action Task Force5
Source: The Financial Action Task Force5Identity proofing comprises three actions: (1) collection and resolution, (2) validation, and (3) verification. Examples of each of these actions are included in the discussion below for illustrative purposes only; there is no expectation that LFIs employing a digital ID system for CDD use any particular method of identity proofing unless otherwise required.
1. Collection and resolution involves obtaining attributes, collecting attribute evidence, and resolving identity evidence and attributes to a single unique identity within a given population or context (a process known as “de-duplication”).6
○ Attribute evidence may be either physical (documentary) or purely digital, or a digital representation of physical attribute evidence (such as a digital representation of a paper or plastic driver’s license). Identity evidence has traditionally taken a physical form and been physically presented by the person seeking to prove his or her identity (known as a “claimant”) to an identity service provider (“IDSP”). However, with the development of digital technology, identity evidence may now be generated digitally (or converted from physical to digital form) and stored in electronic databases, allowing the identity evidence to be obtained remotely and/or identity evidence to be remotely verified and validated against a digital database. ○ Attributes may also be inherent, that is, based on an individual’s personal biometric characteristics, including:
• Biophysical biometrics, such as fingerprints, iris patterns, voiceprints, and facial recognition—all of which are static;
• Biomechanical biometrics, such as keystroke mechanics, which are the product of unique interactions of an individual’s muscles, skeletal system, and nervous system—all of which are dynamic; and
• Behavioral biometrics, such as email or text message patterns, mobile phone usage, geolocation patterns, and file access log, which are based on an individual’s patterns of movement and usage in what are known as “geospatial temporal data streams.”
○ Under Article 8.1 of the AML-CFT Decision and section 6.3.1 of the AML/CFT Guidelines for Financial Institutions, required identity attributes for CDD under UAE regulations and guidance include, for a natural person, the name (as in the passport or identity card, number, country of issuance, date of issuance and expiration date of the identity card or passport), the nationality, the address (i.e., the permanent residential address), the date and place of birth, and the name and address of employer (if applicable).
When verifying the Emirates ID card, either physically or by way of digital or electronic Know Your Customer (“e-KYC”) solutions, LFIs should use the online validation gateway of the Federal Authority for Identity, Citizenship, Customs & Port Security, the UAE Pass Application, or other UAE Government-supported solutions, and keep a copy of the Emirates ID and its digital verification record. Where passports, other than Emirates IDs, are used in the KYC process, a copy should be physically obtained from the original passport, which should be certified as “Original Sighted and Verified” under the signature of the employee who carries out the CDD process and retained.
2. Validation involves determining that the evidence is genuine (i.e., not counterfeit, forged, or misappropriated) and that the information the evidence contains is accurate. Validation is performed by checking the identity information and evidence against an authoritative and reliable source to establish that the information matched reliable, independent source data or records.
○ For instance, in order to assess whether an individual’s physical identity evidence (such as a driver’s license or passport), or the digital images thereof, is genuine, an IDSP may review the evidence to determine that there have been no alterations, that the identification numbers follow standard formats, and that the physical and digital security features are valid and intact.
• When utilizing a physical or digital copy of identity evidence such as an Emirates ID card for purposes of validation, LFIs are expected to review the evidence for physical or digital abnormalities or possible alterations and to make a determination as to whether the evidence has been altered or forged.
○ In order to assess whether such evidence is accurate, the IDSP may query the government issuing sources for the license or passport and confirm that the information matches.
• As noted above, LFIs should use the online validation gateway of the Federal Authority for Identity, Citizenship, Customs & Port Security, the UAE Pass Application, or other UAE Government-supported solutions, to ensure that the information presented for validation purposes matches the information included in reliable databases or other sources.
3. Verification involves confirming that the validated identity relates to the specific individual being identity-proofed, including (but not limited to) through the use of biometric solutions like facial recognition or liveliness detection.
○ For example, if performing verification remotely, an LFI or other IDSP could ask the applicant to take and send a mobile phone video or photo with other liveliness checks, compare the submitted photos to the photos on the applicant’s Emirates ID, passport, or other valid documents, and determine that they match to a given level of certainty.
○ To tie this identity evidence to the actual (real-person) applicant, the IDSP could then send an enrollment code to the applicant’s validated phone number, email address, or another address that is tied to the identity, require the applicant to provide the enrollment code to the IDSP, and confirm that the submitted code matches the code sent. Such measures would verify that the applicant is a real person, in possession and control of the validated phone number. At this point, the applicant will have been identity proofed.
The fourth and final action in the first stage of a digital ID system is enrollment and binding.
4. Enrollment is the process by which an IDSP registers (or “enrolls”) an identity-proofed applicant as a “subscriber” and establishes their identity account. This process authoritatively binds the subscriber’s unique verified identity (i.e., the subscriber’s attributes/identifiers) to one or more authenticators possessed and controlled by the subscriber, using an appropriate binding protocol. The process of binding the subscriber’s identity to authenticator(s) is also referred to as “credentialing.”
○ An authenticator is something the claimant possesses and controls—typically, a cryptographic module, one-time code generator, or password—that is used to confirm or “authenticate” that the claimant is the individual to whom a credential was issued and therefore is (to a given degree of likelihood) the actual subscriber and accountholder. The likelihood that the claimant to whom a credential was issued is in fact the actual subscriber is a function, in part, of the strength of the authentication component; stronger authenticators, such as longer and more complex passwords, can increase an IDSP’s confidence that the claimant is in fact the actual subscriber.
○ A credential is a physical object or digital structure, such as a physical or electronic ID card, that authoritatively binds a subscriber’s proofed identity (via one or more identifiers) to at least one authenticator possessed and controlled by the subscriber. When a digital IDSP issues an authenticator (such as a password or PIN) and authoritatively binds the authenticator to the subscriber’s identity, the physical object or digital structure that results (such as an ID card) is a credential.
Typically, an IDSP issues one or more authenticators (such as a password or auto-generated code) to the subscriber and registers the authenticators in a way that ties them to the subscriber’s proofed identity at enrollment. However, the IDSP can also bind the subscriber’s account to authenticators provided by the subscriber that are acceptable to the IDSP. For example, users of the UAE Pass app are prompted to create a signing password while completing the verification step at a UAE Pass kiosk or through the mobile app. The IDSP can also bind a subscriber’s credentials to additional or alternative authenticators at a later point in time, as part of identity lifecycle management (discussed immediately below). 5 Available at: fatf-gafi.org/media/fatf/documents/recommendations/Guidance-on-Digital-Identity.pdf.
6 Some government-provided ID solutions include a de-duplication process as part of identity proofing, which may involve checking the applicant’s specific biographical attributes (such as name, age, or gender), biometrics (such as fingerprints, iris scans, or facial recognition images), and/or government-assigned attributes (such as driver’s license, passport, or taxpayer identification numbers) against the identity system’s database of enrolled individuals and their associated attributes and identity evidence to prevent duplicate enrollment.
2.3. Authentication and Identity Lifecycle Management
Authentication and identity lifecycle management constitute the second stage of a digital ID system. Authentication answers the question: Are you the person who has been identified and verified? It establishes the individual seeking to access an account (or other services or resources) is the same person who has been identity proofed, enrolled, and credentialed and has possession and control of the binding credentials and other authenticators, if applicable. In other words, it establishes that the claimant is the onboarded customer. Authentication can rely on various types of authentication factors and processes, with the trustworthiness of the authentication depending on the type of authentication factors used and the security of the authentication processes:
• Authentication factors fall into three basic categories:
○ Knowledge factors, that is, something you know, such as a shared secret (e.g., username, password, or passphrase), a personal identification number (“PIN”), or a response to a pre-selected security question;
○ Ownership factors, that is, something you have, such as a cryptographic key stored in hardware (e.g., in a mobile phone, tablet, computer, or USB-dongle) or software that the subscriber controls; a one-time password (“OTP”) generated by a hardware device; or a software OTP generator installed on a digital device, such as a mobile phone; and
○ Inherence factors, i.e., something you are, including biophysical biometrics, biomechanical biometrics, and behavioral biometrics (as discussed in section 2.2 above).
• Authentication processes have historically been assessed by the number and type of authentication factors the process requires, on the assumption that the more factors an authentication process employs, the more robust and trustworthy the authentication system is likely to be. As authentication technology and processes have evolved, however, this assumption has been revised, and the strength of the authentication component is no longer assumed to depend on how many factors (or types of factors) it uses but rather on whether its authentication processes are secure: that is, resistant to compromise by commonly executed and evolving attacks, such as phishing and man-in-the-middle attack vectors. In this revised paradigm, multifactor authentication (“MFA”)—where an IDSP uses two or more independent authenticators from at least two different authentication factor categories (knowledge/possession/inherence) to authenticate the claimant’s identity—is typically assumed.
○ As detailed in the Guidance for Financial Institutions adopting Enabling Technologies, LFIs should implement MFA using a biometric factor where possible to authorize high-risk activities and protect the integrity of customer account data and transaction details. High-risk activities include changes to personal data (e.g., customer office or home address, email address, or telephone contact details), registration of third-party payee details, high-value funds transfers, and revisions to funds transfer limits.
• LFIs deploying MFA at login that includes a biometric factor should consider employing phishing-resistant authenticators where at least one factor relies on public key encryption to secure the customer authentication process.
○ Digital ID authentication has traditionally been conducted at a particular point in time: namely, when the claimant asserts the customer’s/subscriber’s identity and seeks authorization to begin a digital or in-person interaction to access his or her account or other financial services or resources. Today, however, many regulated entities augment traditional authentication at the beginning of an online interaction with continuous authentication solutions that leverage biomechanical biometrics, behavioral biometrics, and/or dynamic transaction risk analysis.
• Instead of relying on something the claimant has/knows/is to establish at the beginning of the interaction that the claimant is the onboarded customer and is in control of the authenticators issued to that customer, continuous authentication focuses on ensuring that certain data points collected throughout the course of an online interaction—such as geolocation, Media Access Control (“MAC”) and Internet Protocol (“IP”) addresses, typing cadence, and mobile device angle— match what should be expected during the entire session.
• However, ways of measuring the effectiveness of continuous authentication technology in mitigating authentication risks have not reached maturity, and the digital ID technical standards, such as the U.S. National Institute of Standards and Technology (“NIST”) Digital Identity Guidelines, do not currently address them.
• Finally, identity lifecycle management refers to the actions IDSPs should take in response to events that can occur over the lifecycle of a subscriber’s authenticator that affect the use, security, and trustworthiness of the authenticator. The attributes associated with an identity may change from year to year, and analytics systems may uncover risk signals suggesting an identity is being used in a manner consistent with fraud or account compromise. Key identity lifecycle events may include:
○ Issuing and recording credentials: At customer onboarding, the IDSP issues the credential and records and maintains the credential and associated enrollment data in the subscriber’s identity account throughout the credential’s lifecycle.
○ Binding: Throughout the digital ID lifecycle, the IDSP should also maintain a record of all authenticators that are, or have been, associated with the identity account of each of its subscribers, as well as the information required to control authentication attempts. When an IDSP binds a new authenticator to the subscriber’s account post-enrollment, it should require the subscriber to first authenticate at the assurance level (or higher) at which the new authenticator will be used.
○ Compromised authenticators: If a subscriber loses or otherwise experiences compromise of all authenticators of a factor required for MFA, the subscriber should repeat the identity proofing process, confirming the binding of the authentication claimant to previously proofed evidence, before the IDSP binds a replacement for the lost authenticator to the subscriber’s identity account. If the subscriber has MFA and loses one authenticator, the IDSP should require the claimant to authenticate, using the remaining authentication factors.
○ Expiration and renewal: Where an IDSP has issued an authenticator that expires, the IDSP should bind an updated authenticator prior to expiration, using a process that conforms to the initial authenticator binding process and protocol, and then revoke the expiring authenticator.
○ Revocation or termination: IDSPs should promptly revoke the binding of authenticators when an identity ceases to exist (e.g.., because the subscriber has died or is discovered to be fraudulent); when requested by the subscriber; or when the IDSP determines that the subscriber no longer meets its eligibility requirements. 2.4. Portability and Interoperability Mechanisms
Digital ID systems can—but need not—include a component that allows proof of identity to be portable. An individual’s identity is portable when his or her digital ID credentials can be used to prove identity for new customer relationships at unrelated private sector or government entities, without their having to obtain and verify personally identifiable information (“PII”) and conduct customer identification and verification each time. Portability requires developing interoperable digital identification products, systems, and processes, including through the use of federated digital architecture and assertion protocols to convey identity and authentication information across a set of networked systems or through APIs that do not use federated architecture and protocols.
Portability and interoperability can potentially save relying parties (e.g., financial institutions and government entities) time and resources in identifying, verifying, and managing customer identities, including for account opening and authorizing customer account access, and may reduce the risk of identity theft stemming from the repeated exposure of PII. However, as discussed below, portability and interoperability are optional components of a digital ID system and will not be a focus of this Guidance.
2.5. Focus of this Guidance
This Guidance focuses on the use of digital ID systems for CDD, specifically for customer identification and verification at onboarding or account opening and for ongoing CDD monitoring, thus enabling LFIs to fulfill their obligations under Articles 8 and 7, respectively, of the AML-CFT Decision. The Guidance emphasizes, however, that customer identification and verification and ongoing monitoring of the business relationship are only two components of LFIs’ wider CDD obligations, which include identifying and verifying the identities of a legal entity customer’s beneficial owners and understanding the nature of the customer’s business and the nature and purpose of the customer’s business relationship with the LFI. LFIs are also separately required under Article 24 of the AML-CFT Decision to maintain all records and documents obtained through CDD measures for a period of no less than five years from the date of termination of the business relationship with the customer; under FATF standards and UAE regulation, such recordkeeping requirements are technology neutral, meaning they apply equally to records kept in digital and physical (documentary) form.
The Guidance focuses primarily on identity proofing and enrollment and secondarily on authentication; it does not address portability and interoperability, as these components are regarded as optional under international AML/CFT standards and are less directly relevant to the application of CDD measures by LFIs. Particular emphasis will be placed on the use of third-party sources or providers to verify and authenticate customer identity through digital means.
Finally, the Guidance focuses on the use of digital ID systems to identify and verify the identity of customers that are individuals (natural persons). It does not examine the use of digital ID systems to help identify and verify the identity of a legal person’s representative(s) or beneficial owner(s) or to understand and obtain information on the nature and intended purpose of the business relationship—although reliable, independent digital ID systems are important for all of these CDD functions.
3. Use of Digital ID Systems for CDD
3.1. Customer Identification and Verification
Under Article 8 of the AML-CFT Decision, LFIs are required to identify each customer and verify the customer’s identity using documents, data, or any other identification information from a reliable and independent source. This requirement is technology neutral and expressly permits LFIs to use documentary as well as non-documentary sources (i.e., information or data) when performing identification and verification; it does not impose any restrictions on the form—physical or digital—that identity evidence must take, nor does it impose limitations as to the use of digital ID systems for the purpose of linking a customer’s verified identity to a unique, real-life individual, provided this is done using a “reliable” and “independent” source. As such, LFIs are permitted to utilize digital ID systems as well as physical forms to perform customer identification and verification, consistent with the expectations set forth in this Guidance.
In the digital ID context, the requirement that digital source documents, data, or information must be “reliable” and “independent” means that the digital ID system used to conduct CDD relies upon technology, adequate governance, processes, and procedures that provide an appropriate level of confidence that the system produces accurate results. Reliability and independence in this sense depends specifically on the effective application of mitigation measures to prevent and manage risks related to identity proofing and enrollment, such as the risks of an applicant using falsified identity evidence or another individual’s identity, as well as risks related to authentication and identity lifecycle management, including various risks that bad actors will illicitly obtain an individual’s legitimate identity credentials and assert them to open an account or obtain unauthorized access to products, services, and data. These risks and the corresponding mitigating measures that LFIs should consider implementing are discussed in greater detail in section 4 below.
3.2. Ongoing Due Diligence on the Business Relationship
Under Article 7 of the AML-CFT Decision, all customers must be subject to ongoing monitoring throughout the business relationship. Ongoing monitoring ensures that the account or other financial service is being used in accordance with the customer profile developed through CDD during onboarding, and that transactions are normal, reasonable, and legitimate.
As discussed in section 2 above, authentication using a digital ID system establishes confidence that the person asserting identity today is the same person who previously opened the account or other financial service and is in fact the same individual who underwent reliable, independent identification and verification at onboarding. In other words, ongoing digital authentication of the customer’s identity links that individual with their financial activity. LFIs that use digital ID systems to authenticate the identity of their existing customers as part of account authorization should leverage the data generated by authentication and related information (such as geolocation or IP addresses) to support ongoing due diligence and transaction monitoring, such as to assess whether a customer’s actual activity conforms to the LFI’s expectations of normal or typical activity and to identify cases in which a customer may be transacting from a sanctioned, otherwise prohibited, or high-risk jurisdiction.
3.3. Third-Party Reliance and Provision of Digital ID Services
Per Article 19 of the AML-CFT Decision, LFIs are permitted to rely on customer identification and verification undertaken by a third party at onboarding, provided the relying LFI:
1. Immediately obtains the necessary information concerning customer identification and verification from the third party, including the assurance levels, where applicable;
○ For example, the digital ID system could enable the prospective customer to assert identity to the relying LFI and the third party to authenticate the person’s identity and provide additional needed information, such as the person’s name, date of birth, government-provided unique identity number, or other attributes required to prove official identity.
2. Takes adequate steps to satisfy itself that the third party will make available copies of or other appropriate forms of access to identification data and other relevant CDD information and documentation without delay;
○ For example, the relying LFI could take appropriate steps to satisfy itself: (a) that, as part of identity proofing and enrollment, the third party established a digital ID account for the identified person that contains adequate attribute evidence and other identity data and information; and (b) that the third party’s authentication processes enable it to provide that information to the relying party upon request without delay.
3. Satisfies itself that the third party adheres to the CDD and recordkeeping requirements set forth in the AML-CFT Decision and is regulated and supervised for compliance with these requirements. In practice, this means that the third party should either be another LFI, a designated non-financial business and profession (“DNFBP”), or another regulated entity, as defined in UAE regulation and guidance; and
4. Considers country risk information when determining in which countries a third party meeting the above conditions can be based.
Unlike outsourcing relationships, in which an LFI engages a third-party provider to perform certain control functions on the LFI’s behalf and in conformity with the LFI’s AML/CFT policies and procedures,7 third-party reliance relationships typically involve an LFI relying the customer identification and verification measures already undertaken by another regulated entity on an existing customer of that entity in accordance with the entity’s own AML/CFT policies and procedures. In reliance relationships, that is, the third party will usually already have a business relationship with the customer that is independent of the relationship to be formed by the customer with the relying institution. The third party will therefore have onboarded the customer in accordance with its own AML/CFT policies and procedures. In a typical reliance scenario, a prospective customer will assert identity to the relying LFI using a digital ID system, at which point the third party will be prompted by the system to authenticate the person’s identity and (per condition 1 above) immediately provide relevant identification and verification information to the relying LFI. In all reliance relationships, the ultimate responsibility for CDD measures remains with the LFI that relies on the third party.
7 See also Guidance for Financial Institutions adopting Enabling Technologies, section 3.90 for additional detail related specifically to the outsourcing of biometric activities.
4. Risks and Challenges Presented by Digital ID Systems
Like any ID system, the reliability of digital ID systems depends on the strength of the documents, processes, technologies, and security measures used for identity proofing, credentialing, and authentication, as well as ongoing identity management. In both documentary and digital ID systems, reliability can be undermined by identity theft and source documents that can be easily forged or tampered with. Some types of fraud, such as “massive attack” frauds, may be less likely to occur in-person or in processes requiring human intervention. While digital ID systems provide security features that mitigate some issues with paper-based systems, they also increase some risks, such as data loss, data corruption, or misuse of data due to unauthorized access.
Digital ID systems also present a variety of technical challenges and risks due to their reliance on open communications networks (i.e., the Internet) for identity proofing and authentication, and the involvement of multiple parties (such as the IDSP, the customer, and the relying LFI), which together can present multiple opportunities for cyberattacks. Without careful consideration of relevant risk factors and the implementation of appropriate, technology-based safeguards and effective governance and accountability measures to address these risks, criminals, money launderers, terrorists, and other illicit actors may be able to abuse digital ID systems to create false identities or exploit (e.g., hack or spoof) authenticators linked to a legitimate identity.
The discussion below covers both identity proofing and enrollment risks and authentication risks. Risks at the identity proofing stage include the risk that proofing and enrollment processes result in digital IDs that are fake—that is, obtained under false pretenses through an intentionally malicious act—and can be used to facilitate illicit activities. These risks are mitigated by having an appropriate identity assurance level. Risks at the authentication stage include the risk that a legitimately issued digital ID has been compromised and that its credentials or authenticators are under the control of an unauthorized person. These risks are mitigated by having an appropriate authentication assurance level. This section concludes with a discussion of broader connectivity, cybersecurity, and privacy challenges in the digital space that may impact the integrity or availability of digital ID systems to conduct CDD.
4.1. Identity Proofing and Enrollment Risks
This section focuses on threats to the identity proofing and enrollment process presented by cyberattacks, security breaches, and the production and presentation of false identity evidence, either by stealing a real person’s identity or by combining real and fake information to create a new identity. The enrollment process may also be threatened through the compromise of, or misconduct by, an IDSP or through the compromise of the broader digital ID infrastructure. The latter type of threat is outside the scope of this Guidance and should be directly addressed by traditional computer security controls (such as intrusion protection, recordkeeping, and independent audits) and by broader governance and organizational requirements and digital ID assurance frameworks and standards.
In certain respects, the risks arising from the presentation of stolen or counterfeit identity evidence can be even greater in digital ID systems, as online counterfeiters and cybercriminals may be able to obtain or produce false identity evidence at far greater scale than illicit actors trading solely in physical documents. Impersonation involves a person pretending to have the identity of another genuine person, including by using a stolen document of someone with a similar appearance or by combining stolen identity evidence with counterfeit or forged evidence (as when an imposter places his or her photo onto a stolen passport or ID card). By contrast, a synthetic ID is created by criminals by combining real (usually stolen) and fake information to create a new, synthetic identity, which can be used to open fraudulent accounts and make fraudulent purchases. Unlike impersonation, the criminal using a synthetic ID is pretending to be someone who does not exist in the real world, rather than impersonating an existing identity.
For example, criminal groups have been known to produce synthetic digital IDs at large scale by stealing real individuals’ identity attributes and other data from online transactions or by hacking Internet databases, and combining these attributes with entirely fake information. The resulting synthetic IDs have been used to obtain credit cards or online loans and to withdraw funds, with the account abandoned shortly thereafter.
The table below sets out these risks and presents some strategies for mitigating threats to the identity proofing and enrollment process, based on the U.S. National Institute of Standards and Technology (“NIST”) Digital Identity Guidelines (also incorporated into the FATF’s Guidance on Digital Identity). FATF further advises regulated entities to utilize safeguards built into digital ID systems to prevent fraud, such as monitoring authentication events to detect systemic misuse of digital IDs to access accounts, including through lost, compromised, stolen, or sold digital ID credentials/authenticators, to feed into suspicious activity monitoring and reporting systems.
Type of Risk Description Potential Risk Mitigation Strategy Falsified identity proofing evidence An applicant claims an incorrect identity by using a forged driver’s license • IDSP validates physical security features of presented evidence • IDSP validates personal details in the evidence with the issuer or other authoritative source Fraudulent use of another’s identity An applicant uses a passport associated with a different individual • IDSP verified identity evidence and biometric of applicant against information obtained from issuer or other authoritative source 4.2. Authentication and Identity Lifecycle Management Risks
Risks at the authentication stage involve the possibility of bad actors asserting an individual’s legitimate identity to a relying party to open an account or obtain unauthorized access to products, services, and data. Key authentication vulnerabilities include:
• Credential stuffing (also referred to as breach replay or list cleaning): a type of cyberattack where stolen account credentials, often from a data breach, are tested for matches on other systems. This type of attack can be successful if the victim has used the same password that was stolen in the data breach for another account.
• Phishing: a fraudulent attempt to gather credentials from unknowing victims using social engineering attacks such as deceptive emails, phone calls, text messages, or websites. For example, a criminal may attempt to trick his or her victim into supplying names, passwords, government ID numbers, or credentials to a seemingly trustworthy source that is in fact controlled by the criminal.
• Man-in-the-middle (also known as credential interception): an attack that attempts to achieve the same goal as phishing and can be a tool to commit phishing, but does so by intercepting communications between the victim and the service provider.
• PIN code capture and replay: an attack in which a criminal uses a key logger to capture a PIN code entered on a computer keyboard or other device and, without the user noticing, uses the captured PIN to access services (e.g., when a smartcard is present in the reader).
Most authentication vulnerabilities are exploited without the identity owner’s knowledge, but abuse can also involve the witting participation of subscribers or IDSPs. For example, shared-secret authenticators, such as passwords, may be stolen and exploited by bad actors, but they can also be deliberately shared by the owner of the identity credentials for illicit purposes, as in the case study below.
Misuse of Digital ID by Straw MenCriminal organizations can purchase digital ID credentials from individuals that enable them to access the individuals’ accounts at LFIs or other regulated entities, in effect turning them into digital mules for the organization. The individuals may either already have an account or agree to open one in connection with selling the identity credentials.
In one case highlighted by the FATF, criminal groups opened bank accounts using straw men, who established the account, obtained a digital ID and a security code, and provided their credentials to the criminal group, in exchange for money. In many cases, multiple digital IDs were used on a single mobile phone or tablet. Access to these accounts afforded the criminal groups access to real-time transactions, making it possible for them to quickly transfer money between various accounts. As the FATF notes, the overwhelming majority of digital IDs that are misused by criminal groups are issued on the basis of legitimate identity evidence.
Some of the primary known risks at the authentication stage are associated with specific types of authenticators or authentication processes, including:
• Multifactor authentication vulnerabilities: Passwords or passcodes, which are supposed to be shared-secret knowledge authenticators, are vulnerable to brute-force login attacks, phishing attacks, and massive online data breaches, and are very easily defeated. Stolen, weak, or default passwords are believed to be behind the vast majority of data breaches. MFA solutions, such as SMS one-time codes texted to the subscriber’s phone, add another layer of security to passwords and passcodes, but they can also be vulnerable to phishing, subscriber identity module (“SIM”) card swapping, mobile device compromise, and other attacks.
○ Phishing-resistant authenticators, where at least one factor relies on public key encryption, can help combat these vulnerabilities. In public-key encryption, a pair of keys are generated for an entity (person, system, or device), and that entity holds the private key securely, while freely distributing the public key to other entities. Anyone with the public key can then use it to encrypt a message to send to the private-key holder, knowing that only they will be able to open it. Examples of phishing-resistant authenticators include authenticators built off public key infrastructure (“PKI”) certificates or the Fast Identity Online (“FIDO”) Alliance standards.
○ Per the Guidance for Financial Institutions adopting Enabling Technologies, LFIs should implement MFA using a biometric factor (discussed immediately below) where possible to authorize high-risk activities (including changes to personal, registration of third-party payee details, high-value funds transfers, and revisions to funds transfer limits) and to protect the integrity of customer account data and transaction details. Moreover, LFIs deploying MFA at login that includes a biometric factor should consider employing phishing-resistant authenticators where at least one factor relies on public key encryption to secure the customer authentication process.
• Biometric authenticators: Biophysical authenticators, such as fingerprints and iris scans, are more difficult to defeat than traditional authenticators and are increasingly ubiquitous. Most smart phones have built-in fingerprint scanners, some have built-in iris scanners, and facial recognition capabilities are built into many personal computer systems and advanced smart phones. Biometric characteristics can be stolen in bulk from central databases, obtained by taking high-resolution photos, lifted from objects the individual touches, or captured with high-resolution images and then spoofed. Currently, however, these types of attacks are difficult and/or highly resource intensive and therefore not scalable. For example, biometric authenticators that require on-device matching cannot be fraudulently used at scale because they require physical access to the device of the customer.
○ Biometrics have a variety of other weaknesses that give rise to reliability concerns when used for authentication purposes and have led some technical standards to restrict their use for authentication (although not for identity proofing). Fingerprints may not be read or may be read incorrectly; and facial recognition factors can be rendered unreliable by changes in facial expressions, facial hair, makeup, or lighting conditions. Due to incomplete data sets, facial recognition has been less reliable for persons with darker skin pigmentation and certain ethnic features, although this is improving. In contrast to knowledge- or possession-based authenticators, stolen biometric authenticators are difficult to revoke or replace.
• Identity life cycle risks: Poor identity life cycle and access management can, wittingly or unwittingly, compromise the integrity of authenticators and enable unauthorized persons to access and misuse customer accounts, undermining the purpose of customer identification and verification, ongoing due diligence, and transaction monitoring requirements in protecting the financial system from abuse.
• Compromised MFA workflow bypass: Attackers have also been known to identify loopholes in MFA protocols, for example by initiating a denial-of-service attack that causes the MFA workflow to break or its security to degrade.
• Unknown risks: Digital ID systems develop and evolve. In many cases, technical design changes introduce operational improvements but bring with them vulnerabilities that are not apparent until they are exploited by bad actors in ways that disclose how the digital ID system has been compromised. 4.3. Broader Issues Presented by Digital ID Systems
Beyond specific risks associated with identity proofing/enrollment and authentication, there are a number of broader issues in the digital space that may impact the integrity or availability of digital ID systems to conduct CDD. These include but are not limited to:
• Connectivity issues: The lack of a reliable network infrastructure can undermine digital ID systems at particular customer touchpoints or across larger geographic areas for meaningful periods of time. However, digital ID systems can be designed to support both offline and online transactions, allowing them to function with or without access to the Internet or a mobile network. LFIs should consider the resilience of available networks and systems, including the geographic locations from which customers may be utilizing a digital ID system for authentication, when deciding whether to use a digital ID system for CDD.
• UAE frameworks for official identity: The reliability and independence of purely documentary approaches can be undermined by identity theft and the widespread counterfeiting of official identity documents, including where official identity documents either lack advanced security features to prevent tampering or counterfeiting or are issued without adequate identity proofing. Such weaknesses in the reliability of documentary identity evidence can have a cascading effect on the risks posed by digital ID systems, and identity theft from online databases can generate similar risks for both digital ID systems and documentary approaches.
○ The Emirates ID utilizes ultraviolet ink, public key infrastructure, and fingerprint biometrics to prevent tampering or counterfeiting of the card.
○ To further mitigate the risks associated with tampering or counterfeiting of official identity documents, LFIs should use the online validation gateway of the Federal Authority for Identity and Citizenship when verifying the Emirates ID card, and should keep a copy of the Emirates ID and its digital verification in their records.8
• Data protection and privacy challenges: Digital ID involves the collection and processing of PII, potentially including biometrics. As such, digital ID systems are subject to local data protection and privacy (“DPP”) requirements, including Federal Decree-Law No .34 of 2021 Concerning the Fight Against Rumors and Cybercrime; Federal Decree-Law No. 46 of 2021 On Electronic Transactions and Trust Services; the Internet Access Management (IAM) policy; relevant Emirate-level requirements such as the Dubai Data Law; and Federal Decree-Law No. 45 of 2021 on the Protection of Personal Data, where relevant.
○ Under the UAE’s DPP framework, LFIs and DISPs are not permitted to transfer or store personal data, including digital or physical copies of Emirates IDs, outside of the UAE, except as permitted by Articles 22 and 23 of the Federal Decree-Law No. 45 of 2021.
○ LFIs should also consult the Principles on Identification for Sustainable Development, including Principle 8 regarding the protection of personal data and the maintenance of cyber security,9 as well as guidance from global standard-setting bodies in their respective sub-sectors.
• Financial exclusion considerations: Where digital ID systems do not cover all, or most, persons within a jurisdiction, or where they exclude certain populations, they may drive (or at least fail to mitigate) financial exclusion. The mandatory use of a specific digital ID that is not universally available for CDD presents challenges similar to the prescriptive use of a documentary ID that is not accessible to the entire population.
○ Lack of access to digital technology or low levels of technological literacy may compound exclusion risks. For example, lack of access to mobile phones, smartphones, or other digital access devices, or lack of coverage and/or unreliable connectivity, may exclude poor and rural populations or women as well as those living in fragile and conflict-affected areas, such as refugees and displaced people.
○ Digital ID systems may also contribute to financial exclusion if they use biometric authentication without providing alternative mechanisms for authentication, as certain biometric modalities have greater failure rates for some vulnerable groups. For example, manual laborers may have worn fingerprints, which cannot be read by biometric readers; the elderly may experience frequent match failure, due to altered facial characteristics, hair loss, or other signs of aging, illness, or other factors; and certain ethnic groups and individuals with certain physical characteristics related to darker pigmentation, eye shape, or facial hair experience disproportionate facial recognition failures.
○ Special considerations for LFIs related to financial inclusion are discussed in section 5.2 below. 8 See ica.gov.ae/en/ica-validation-gateway/.
9 See id4d.worldbank.org/principles. Although developed to support the creation of “good” government-recognized ID systems, FATF’s Guidance on Digital ID notes that they apply more broadly and can be adopted by both public- and privately-provided and used identity systems and services.5. Assessing the Reliability and Independence of Digital ID Systems for CDD
Unless otherwise specified,10 the UAE permits LFIs to adopt digital ID systems of their choosing, provided that they “rely upon technology, adequate governance, processes, and procedures that provide appropriate levels of confidence that the system produces accurate results.”11 This means that there is an appropriate level of confidence (or “assurance,” in the FATF’s terminology) that the digital ID system works as it is supposed to and produces accurate results. The digital ID system should also be adequately protected against internal or external manipulation or falsification designed to fabricate and credential false identities or authenticate unauthorized users, including by cyberattack or insider malfeasance.
To this end, LFIs should conduct:
• An assurance level assessment, through which the LFI can understand the assurance levels that the digital ID system provides based on its technology, architecture, and governance and determine its reliability and independence; and
• An appropriateness assessment, through which the LFI can make a risk-based determination— given the digital ID system’s assurance levels—of whether the digital ID system is appropriately reliable and independent for CDD in light of potential ML, TF, fraud, and other illicit financing risks.
As explained in greater detail below, these assessments should be performed sequentially. If an LFI cannot assess a digital ID system’s assurance level or determines that it is not sufficiently reliable and independent for its purposes, it should not proceed with using the system for CDD unless it can be adequately strengthened or supplemented; in such a case, it is therefore not necessary to perform an appropriateness assessment until assurance concerns have been resolved.
Both an LFI’s assurance assessment of a digital ID system and its determination of the system’s appropriateness for CDD given its business and risk profile should be documented—whether as part of the institution’s enterprise risk assessment or through a separate process—and updated on a periodic and event-driven basis. LFIs may determine which functional unit or team within the institution is best suited to carry out the assurance and appropriateness assessments; there is no requirement that these assessments be performed by a specific unit, such as an internal audit department.
10 For example, as noted above, when verifying the Emirates ID card, LFIs should use the online validation gateway of the Federal Authority for Identity and Citizenship and keep a copy of the Emirates ID and its digital verification in their records; see ica.gov.ae/en/ica-validation-gateway/.
11 Available at centralbank.ae/en/cbuae-amlcft; see p. 49.5.1. Understanding the System’s Assurance Levels
Where UAE law, regulation, or supervisory guidance has not mandated or prohibited the use of a specific digital ID system for CDD, LFIs should first determine, for any digital ID system it is considering adopting, the system’s assurance levels.12 In determining the reliability and independence of a given system, LFIs may either:
• Perform the assurance assessment themselves; or • Obtain audit or certification information on assurance levels from an expert body.
Where an LFI performs the assurance assessment itself, it should conduct appropriate due diligence on the digital ID system provider, including the governance systems in place, and exercise additional caution. An LFI should only use information from an expert body, including another member of the same financial group or an independent third party, if it has a reasonable basis for concluding that the entity accurately applies appropriate, publicly disclosed assurance frameworks and standards.
Digital ID assurance frameworks and technical standards are a set of open source, consensus-driven assurance guidelines and best practices for digital ID systems that have been developed in several jurisdictions and by international organizations and industry bodies, and provide a useful tool for informing an LFI’s or expert body’s assurance assessment.13 LFIs are encouraged to consider the reliability of each of the system’s main digital ID components separately, as the same degree of reliability may not be required for each component of the digital ID system (identity proofing/enrollment, authentication, or, if applicable, federation), depending on the relevant risk factors and mitigating measures in place.
Digital ID technology and architecture, and digital ID assurance frameworks and standards, are dynamic and evolving. The standards themselves are flexible and outcome-based in order to facilitate innovation. They permit different technologies and architectures to satisfy the requirements for different assurance levels and are framed in ways intended to help make them as future-proof as possible (e.g., by providing a floor, rather than a ceiling, for reliability).
Digital ID assurance frameworks and standards usually set out various, progressively more reliable assurance levels, with increasingly rigorous technical requirements, for each of the three main steps in a digital ID system. The technical standards provide ID reliability factors, in the form of assurance levels for the basic constituent processes of a digital ID system. Each assurance level reflects a specified level or certitude or confidence in the process at issue; a process with a higher assurance level is more reliable, while a process with a lower assurance level presents a greater risk of failure and is less reliable. This Guidance does not require or recommend any particular assurance level; rather, LFIs are expected to perform an assurance assessment and to determine what assurance levels for which processes are appropriate, given their ML, TF, fraud, and other illicit financing risks.
For illustrative purposes only, the following table summarizes and adapts some of the technical requirements from the NIST Digital ID Guidelines14 for the identity proofing and enrollment stage of a digital ID system, which LFIs might leverage in assessing the degree to which a digital ID system is reliable and independent.
Reliability Factor No Assurance High Assurance Very High Assurance Presence No requirements In-person or remote proofing is permitted Either in-person or supervised15 remote proofing is required Resolution No requirements Collection of as many identity attributes as necessary to achieve resolution into a single unique identity (i.e., to achieve de-duplication) is required; knowledge-based verification may be used for added confidence Same as “High” Evidence No identity evidence is collected Evidence of identity attributes is collected based on the quality of the evidence (classified as weak, fair, strong, or superior) and the number of documents or quantity of digital information relied upon Same as “High,” albeit with higher thresholds for evidence quality and quantity; use of biometrics is mandatory (noted below) Validation No validation Each piece of evidence is validated as genuine and accurate against independent and reliable sources Same as “High” Verification No verification The identity evidence is verified, confirming that the validated identity relates to the individual applicant16 Identity evidence is verified by an authorized and trained credential service provider (“CSP”) representative Address Confirmation No requirements for address confirmation Required Required Biometric Collection None Optional Mandatory Security Controls Not applicable Moderate Baseline (per NIST Digital ID Guidelines)17 or equivalent jurisdictional or industry standard High Baseline (per NIST Digital ID Guidelines)18 or equivalent jurisdictional or industry standard Likewise, the NIST Digital ID Guidelines set forth technical requirements for authentication protocols and processes (including credential and authenticator issuance and binding) and authenticator lifecycle management (including revocation in the event of loss or theft, and expiration/re-proofing and re-binding). For illustrative purposes only, the following table describes at a high level of generality some of the NIST requirements for authentication at various authentication assurance levels.19
Assurance Level General Requirements Some Assurance • This assurance level can be achieved through a wide range of authentication technologies and authenticator types, and information security controls at a low baseline
• Biometrics alone may be used as a single-factor authenticator at this level High Assurance • MFA is required (i.e., either a multi-factor authenticator or two single-factor authenticators), using secure authentication protocols that incorporate specified approved cryptographic techniques, and information security controls at a moderate baseline
• More stringent requirements are imposed on authenticator types at this level20
• Biometrics may be used as one authentication factor (something you are), with the device authenticated as a second factor (something you have), but cannot serve as the only authenticator type Very High Assurance • Requires MFA that uses both a hardware-based authenticator and an authenticator that provides verifier impersonation resistance, based on proof of possession of a key through an approved cryptographic protocol21
• Claimants prove possession and control of two distinct authentication factors through secure authentication protocols, using approved cryptographic techniques
• The authenticators are verifier impersonation resistant, replay resistant, and resist relevant side-channel attacks
• When a biometric factor is used, the identity service provider (verifier) makes its own determination that the biometric sensor and subsequent processing meet specified performance requirements
• The CSP employs appropriately tailored security controls at a high baseline 12 Where the government of the UAE has mandated a specific digital ID system for CDD, as in the case of verifying the Emirates ID card via the online validation gateway of the Federal Authority for Identity and Citizenship, LFIs may rely on the government’s assessment of such system’s assurance levels.
13 See, for example, FATF, Guidance on Digital Identity, Appendix D (Digital ID Assurance Framework and Technical Standard-Setting Bodies) and Appendix E (Overview of U.S. and EU Digital Assurance Frameworks and Technical Standards), available at: fatf-gafi.org/media/fatf/documents/recommendations/Guidance-on-Digital-Identity.pdf.
14 The NIST 800-63 Digital Identity Guidelines consists of a suite of documents: NIST SP 800-63-3 Digital Identity Guidelines (Overview); NIST SP 800-63A: Digital Identity Guidelines: Enrollment and Identity Proofing; NIST SP 800-63B Digital Identity Guidelines: Authentication and Life Cycle Management; and NIST SP 800-63C, Digital Identity Guidelines: Federation and Assertions. For additional context, see Appendix E of the FATF Guidance on Digital Identity.
15 Supervised remote proofing involves a remote interaction with the applicant that is supervised by an operator in accordance with specified requirements so as to achieve comparable levels of confidence and security to in-person identity proofing. NIST comparability requirements, are provided in Box 19 of Appendix E of the FATF Guidance on Digital Identity, at 96.
16 As noted above, an LFI need not verify the accuracy of every element of identifying information obtained at the collection and resolution stage but should do so for enough information to form a reasonable belief it knows the true identity of the customer.
17 See FATF, Guidance on Digital Identity, pp. 97-98.
18 See FATF, Guidance on Digital Identity, pp. 97-98.
19 Appendix E of the FATF Guidance on Digital Identity also presents summary of authentication assurance levels under EU Regulation No. 910/2014 on Electronic Identification and Trust Services for Electronic Transactions in the Internal Market.
20 Under NIST standards, a “High” assurance level permits the use of any of the following multi-factor authenticators: multi-factor OTP device; multi-factor cryptographic software; or multi-factor cryptographic device. When a combination of two single-factor authenticators is used, one authenticator must be a memorized secret authenticator and the other must be possession-based (i.e., “something you have”) and use any of the following: look-up secret; out-of-band device; single-factor OTP device; single-factor cryptographic software; or single-factor cryptographic device.
21 The claimant uses a private key stored on the authenticator to prove possession and control of the authenticator. An IDSP (verifier), knowing the claimant’s public key through some credential (typically, a public key certificate) uses an approved cryptographic authentication protocol to verify that the claimant has possession and control of the associated private key authenticator, and asserts the person’s verified identity to the RP.5.2. Determining Appropriate Usage in Context of Risk
Once the LFI is satisfied that it knows the assurance levels of the digital ID system, it should analyze whether the digital ID system is adequate for the purposes of performing CDD in the context of the relevant illicit financing risks associated with the LFI’s customers, products and services, geographic areas of operations, and other relevant factors. Depending on the availability of digital ID systems, LFIs may have the option to select from multiple digital ID systems that have different assurance levels for identity proofing and authentication. In such circumstances, LFIs should match the robustness of the system’s identity proofing and/or authentication processes to the type of potential illicit activities and level of ML/TF risks.
In choosing among digital ID systems providing the same assurance level, or selecting among varying levels of identity proofing and/or particular credentials and authenticators offered by a single system, LFIs should consider their specific ML/TF risks as they relate to identity proofing and authentication in selecting an option. LFIs may also have the option to choose appropriate digital ID systems for lower-risk scenarios.
Cabinet Decision 58 of 2020: Beneficial Owner Procedures
Cab Dec 58/2020 Effective from 25/8/2020Cabinet Decision No. (58) of 2020 Regulating the Beneficial Owner Procedures
The Cabinet:
Pursuant to the perusal of the Constitution,
- Federal Law No. (1) of 1972 Concerning the Competencies of the Ministries and Powers of the Ministers and its amendments;
- Federal Law No. (5) of 1975 on the Commercial Register;
- Federal Law No. (2) of 2015 on Commercial Companies and its amendments;
- Federal Law No. (14) of 2016 concerning the Violations and Administrative Sanctions in the Federal Government;
- Cabinet Decision No. (34) of 2020 concerning Regulating the Beneficial Owner Procedures; and
- Upon the proposal of the Minister of Economy and the approval therefore of the Cabinet,
Has resolved:
Article (1)
Definitions
In application of the provisions of this Decision, the following terms and expressions shall have the meanings assigned against each, unless the context otherwise requires:
State: The United Arab Emirates. Minister: The Minister of Economy. ministry: The Ministry of Economy. Decree-Law: The Federal Decree-Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Financing of Illegal Organizations. Executive Regulations: The Cabinet Decision No. (10) of 2019 concerning the Executive Regulations of the Federal Decree-Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Financing of Illegal Organizations. Licensing Authority: The Authority in charge of licensing or registration of the Legal Persons in the State. Registrar: The entity in charge of supervision of the commercial names register for different types of corporate entities registered in the State, which includes the Licensing Authority. Relevant Entities: The Governmental Entities in charge of implementation of any provisions of the Federal Decree-Law and the Executive Regulations. Beneficial Owner: The natural person who ultimately owns or controls the Legal Person, whether directly or through a chain of ownership or control or any-other indirect means, and also the natural person on whose behalf the transactions are being conducted or who exercises ultimate control over a legal person, as defined in Article (5) hereof. Nominee Board Member: Any natural person who acts in accordance with the directives, instructions or wills of another person. Higher Management: The decision-making authority in the Legal Person. Register of Beneficial Owner: A Specific Register of the Beneficial Owners in the Legal Person, which includes all of their data. Register of Partners or Shareholders: A Specific Register of the Partners or Shareholders in the Legal Person, which includes all of their data. Trustor: A natural or legal person who transfers the management of his funds to a trustee by virtue of a deed. Trustee: A natural or legal person who enjoys the rights and authorities granted by the Trustor or the Trust Fund, to manage, use and dispense of the Trustor's funds in accordance with the conditions imposed on him by either of them. Trust Fund: A legal relationship in which the Trustor places the funds under control of the Trustee for the interest of a beneficiary or for a specific purpose, which funds shall be independent of the Trustor's properties, and the right in the Trustor's funds shall remain under the name of the Trustor or under the name of another person on behalf of the Trustor. Article (2)
Objectives of the Decision
The Decision has for objective to:
- Contribute to the development of business environment, capacities of the State and its economic position in accordance with the international requirements, by regulating the minimum obligations of the Registrar and Legal Persons in the State, including the licensing or registration procedures, regulating the Register of Beneficial Owner and the Register of Partners or Shareholders.
- Develop effective and sustainable executive and regulatory mechanisms and procedures for the beneficial owner data.
- Contribute to the development of business environment, capacities of the State and its economic position in accordance with the international requirements, by regulating the minimum obligations of the Registrar and Legal Persons in the State, including the licensing or registration procedures, regulating the Register of Beneficial Owner and the Register of Partners or Shareholders.
Article (3)
Scope of Application
- The provisions of this Decision shall apply to the Registrar and the licensed or registered Legal Persons in the State, including the Commercial Free Zones.
- The provisions of this Decision shall not apply to the companies which are wholly owned by the Local or Federal Government, or any-other companies wholly-owned by such companies, and the Financial Free Zones.
- The provisions of this Decision shall apply to the Registrar and the licensed or registered Legal Persons in the State, including the Commercial Free Zones.
Article (4)
Licensing or Registration of Legal Persons
- The Legal Person shall be licensed or registered in the State and shall, while submitting its licensing or registration application, provide the Registrar with the following basic data:
- Name, legal form and memorandum of association.
- Head office address or the principal address of business and, in case of a foreign Legal Person, the name and address of its legal representative in the State, with a proof thereof.
- Articles of Association or any-other similar documents approved by the Relevant Entity in the State.
- Names of the relevant persons who are holding higher management positions in the Legal Person, providing their data from their passports or identity cards, including such documents' numbers, issuance and expiry dates and issuing entity.
- The Legal Person may not be licensed or registered under a trade name that is previously registered in the State or in similar name to the extent that it may lead to confusion.
- The Legal Person shall not use a name other than its registered name, and such name must be followed by the legal form of the Legal Person. The Legal Person may submit an application to the Registrar to change its trade name and in case of the approval, the legal person shall not use the cancelled name. All correspondence and documents of the Legal Person shall clearly state its trade name and address in the State.
- The Legal Person shall have a clear, detailed and registered address in the State and to notify the Registrar thereof. Such address shall be used in all correspondence and notices to be served on the Legal Person.
- The Legal Person shall be licensed or registered in the State and shall, while submitting its licensing or registration application, provide the Registrar with the following basic data:
Article (5)
Identification of the Beneficial Owner
- For the purposes of implementing the provisions of this Decision, the Beneficial Owner of the Legal Person shall be whoever person that ultimately owns or controls, whether directly through a chain of ownership or control or by other means of control such as the right to appoint or dismiss the majority of its Directors, 25% or more of the shares or 25% or more of the voting rights in the Legal Person.
- The Beneficial Owner may be traced through any number of Legal Persons or arrangements of whatsoever kind.
- If two or more natural persons jointly own or control a ratio of capital in the Legal Person, all of them shall be deemed as jointly owners or controllers of such ratio.
- If, after all reasonable means have been taken, no natural person is identified as an ultimate Beneficial Owner in accordance with Clause (1) of this Article, or there is reasonable doubt that any natural person identified as an ultimate Beneficial Owner is the true Beneficial Owner in the Legal Person; then the natural person who controls the Legal Person by other means of control shall be deemed as the Beneficial Owner.
- Where no natural person is identified in accordance with Clause (4) of this Article; then the natural person who holds the position of a higher management official shall be deemed as the Beneficial Owner.
- For the purposes of implementing the provisions of this Decision, the Beneficial Owner of the Legal Person shall be whoever person that ultimately owns or controls, whether directly through a chain of ownership or control or by other means of control such as the right to appoint or dismiss the majority of its Directors, 25% or more of the shares or 25% or more of the voting rights in the Legal Person.
Article (6)
Transparency and Beneficial Owner
- The Legal Person shall take reasonable procedures to obtain and maintain adequate, accurate and up-to-date data in respect of the Beneficial Owner.
- The provisions of Clause (1) of this Article shall not apply to the licensed or registered Legal Persons in the State that are owned by a company listed on a recognized stock exchange subject to disclosure requirements which ensure sufficient transparency on its beneficial owners or a company wholly-owned by such listed company.
- The Legal Person shall take reasonable procedures to obtain and maintain adequate, accurate and up-to-date data in respect of the Beneficial Owner.
Article (7)
Notices of Beneficial Owner
- If the Legal Person believes that a person could be a Beneficial Owner whose ultimate beneficial ownership data are not correctly recorded in the Register of Beneficial Owner, the Legal Person shall inquire as to the person's status as a Beneficial Owner. If (15) fifteen days have lapsed without any response to such inquiry being received, the Legal Person shall give such person a notice thereof.
- The notice referred to in Clause (1) of this Article shall:
- State that it is given by virtue of this Decision.
- Set-out the Beneficial Owner's relevant data that the Legal Person reasonably knows or believes to be correct, with a request to provide the data that are missed and required to complete data of the Beneficial Owner's Register.
- Request the addressee the following:
- State whether or not he is the Beneficial Owner of the Legal Person;
- Confirm or correct any data set-out in the notice;
- Supply any data that are missing.
- If the addressee fails to comply with the notice within (15) fifteen days of dispatching the notice, the Legal Person shall enter the notified data in the Register of Beneficial Owner.
- For the purpose of identifying the Beneficial Owner, the Legal Person may rely on the written response of the person to whom a notice was given, unless the Legal Person has reasonable reasons to suspect that the response is misleading or false, where he shall register the beneficial ownership data of such person as a Beneficial Owner and notify him of the same.
- If the Legal Person believes that a person could be a Beneficial Owner whose ultimate beneficial ownership data are not correctly recorded in the Register of Beneficial Owner, the Legal Person shall inquire as to the person's status as a Beneficial Owner. If (15) fifteen days have lapsed without any response to such inquiry being received, the Legal Person shall give such person a notice thereof.
Article (8)
Register of Beneficial Owner
- The Legal Person shall keep and maintain the data of each Beneficial Owner in a register of beneficial Owner to be established within (60) sixty days from the date of promulgation of this Decision or the date on which the Legal Person comes into existence. The Legal Person shall update and record any changes to the data contained in the Register of Beneficial Owner within (15) fifteen days of becoming aware of such change.
- The Register of Beneficial Owner shall include the following data in respect of each Beneficial Owner:
- Full name, nationality, date and place of birth.
- Residential address or the address which the notices shall be sent on it, by virtue of this Decision.
- Number of passport or identity card, the country of issuance, date of issuance and expiry.
- Basis and date on which the person became a Beneficial Owner of the Legal Person.
- Date on which the person ceased to be a Beneficial Owner of the Legal Person.
- If the Legal Person enters name of a natural person as a Beneficial Owner in its Register of the Beneficial Owner, information and data were not provided by such natural person or with his knowledge, the Legal Person shall, within (15) fifteen days of making such entry, notify the natural person of such inclusion.
- Any concerned or interested person may make an application to the competent court to rectify the Register of Beneficial Owner, in the following cases:
- Name of any person is, without sufficient cause, entered-into or omitted from the Register of Beneficial Owner.
- A person's name is not entered into the Register of Beneficial Owner.
- An undue delay takes place in entrance of the name of any person into the Register of Beneficial Owner, or omitting the name of any person who has ceased to be a beneficial owner from the Register of Beneficial Owner.
- The Legal Person may not register or give effect to any document relating to a change in its ownership, unless a statement is provided by or on behalf of the transferee, which states whether the transfer will result in a change in the Beneficial Owner for the Legal Person, and the nature of such change or no. The said statement shall include the data of the new Beneficial Owner and to be entered into the Register.
- The Legal Person shall keep and maintain the data of each Beneficial Owner in a register of beneficial Owner to be established within (60) sixty days from the date of promulgation of this Decision or the date on which the Legal Person comes into existence. The Legal Person shall update and record any changes to the data contained in the Register of Beneficial Owner within (15) fifteen days of becoming aware of such change.
Article (9)
Nominee Board Members
- A manager or board member who acts as a Nominee Board Member shall inform the Legal Person that he is a nominee board member and provide all the data referred to in Article (10) hereof within (15) fifteen days of becoming a nominee board member. A nominee board member who acquired such capacity prior to the promulgation of this Decision shall inform the Legal Person of this fact within (30) thirty days of the promulgation date of this Decision.
- A Nominee Board Member shall inform the Legal Person of any change to the data referred to in Article (10) hereof within (15) fifteen days of making such change.
- A Nominee Board Member shall inform the Legal Person that he ceased to be a nominee Board Member within (15) fifteen days of such cessation.
- A manager or board member who acts as a Nominee Board Member shall inform the Legal Person that he is a nominee board member and provide all the data referred to in Article (10) hereof within (15) fifteen days of becoming a nominee board member. A nominee board member who acquired such capacity prior to the promulgation of this Decision shall inform the Legal Person of this fact within (30) thirty days of the promulgation date of this Decision.
Article (10)
Register of Partners or Shareholders
- The Legal Person shall keep and maintain a Register of Partners or Shareholders, in which it includes the data in respect of each of its partners or shareholders. The Legal Person must update and record any change to the Register within (15) fifteen days of becoming aware of such change. The Register of Partners and Shareholders shall include:
- Number of shares held by each of them along with their categories and associated voting rights.
- Date on which such partner or shareholder acquire that capacity in the Legal Person.
- In case of natural partners or shareholders: the full name as it appears on the identity card or the passport, nationality, address, place of birth, name and address of employer and a true copy of the valid passport or ID.
- In case of corporate partners or shareholders: the data stated in Clause (1) of Article (4) hereof.
- The Legal Person shall enter into the Register of Partners or Shareholders the data of any partner(s) or shareholder(s) acting as Trustor or Nominee Board Member.
- The Register of Partners or Shareholders shall include the data of persons represented by any Trustee or Nominee Board Member, as specified in Clause (2) of Article (8) hereof.
- The Legal Person shall keep and maintain a Register of Partners or Shareholders, in which it includes the data in respect of each of its partners or shareholders. The Legal Person must update and record any change to the Register within (15) fifteen days of becoming aware of such change. The Register of Partners and Shareholders shall include:
Article (11)
Provision of Information to the Registrar
- The Legal Person shall, within (60) sixty days of the promulgation date of this Decision or date of licensing or registration of the Legal Person, furnish the Registrar with the data contained in the Register of Beneficial Owner and Register of Partners or Shareholders and shall carry-out the reasonable procedures to protect its registers from loss, damage or destruction.
- The Legal Person shall provide any additional information as may be required by the Registrar within the specified duration.
- Subject to the legislation in force, the Legal Person shall furnish the Registrar with all data referred to in Clause (1) of Article (4) hereof, upon submitting the application of incorporation, licensing, registration, renewal, amendment or any other procedures as the Registrar may deem proper to this effect.
- The Legal Person shall provide the Registrar with the name of a natural person residing in the State and authorized to disclose to the Registrar all data and information required by the mentioned Federal Decree-Law or the Executive Regulations or this Decision, along with his address, contact numbers and a copy of his valid passport or ID.
- The licensed or registered Legal Person in the State may not issue bearer share warrants.
- The Legal Person shall, on the issuance of shares in the name of persons or board members , disclose to the Registrar the data in respect of such shares and the identity of such persons or board members within (15) fifteen days of such issuance.
- If the Legal Person is in the process of dissolution or liquidation , the liquidator shall hand-over to the Registrar a copy of the Beneficial Owner Register and Register of Partners or Shareholders, if any, or a true copy thereof within (30) thirty days of his appointment.
- The Legal Person, its managerial body, the liquidator or other person responsible for the dissolution affairs of the Legal Person shall keep, maintain the records and all data referred to herein for at least (5) five years after the date of dissolution, liquidation or de-registration.
- The Legal Person shall, within (60) sixty days of the promulgation date of this Decision or date of licensing or registration of the Legal Person, furnish the Registrar with the data contained in the Register of Beneficial Owner and Register of Partners or Shareholders and shall carry-out the reasonable procedures to protect its registers from loss, damage or destruction.
Article (12)
Notices issued by the Registrar
- For the registrar to be able to carry out his tasks, the Legal Person, or any other person who has data or documents related to the Beneficial Owners or the Nominee Board Members, shall abide - without prejudice to any privilege he might have - by the Registrar's request to provide such data or documents, or disclose the same to his personnel or authorized agents. This is done by virtue of a written notice sent to either of them in the time and place specified in the notice.
- The granted powers to the Registrar by virtue of Clause (1) of this Article shall include:
- Take copies of the provided documents, according to circumstances as the Registrar deems fit.
- Where the data or documents are not provided , to require the person who was required to provide them to state where they are, attend at such time and place as may be required by the Registrar and answer any questions relating to any matters that require providing data.
- Lawyers and other independent legal professionals and chartered auditors shall be exempted from providing such information required in the notice where such provision relates to their assessment of the legal status of the Legal Person or its defense or representation in legal action, arbitration, mediation or conciliation or the provision of any legal opinion in a mater related to judicial proceedings, including an advice on initiating or avoiding such proceedings, whether such data have been obtained prior to, during or after the taking of judicial proceedings or in other circumstances under which they are subject to professional confidentiality.
Article (13)
Obligations of the Registrar
The Registrar shall abide by the following:
- Prepare and issue the templates, notices and manuals related to the licensing or registration procedures, in such manner as may be required to achieve efficiency.
- Provide adequate human resources that enable him to perform his functions in an effective manner.
- Automate the information obtained by him, and classify the same in a manner that facilitates the reference thereto and exchange thereof with the Relevant Entities, upon request.
- Furnish the required data concerning the National Economic Register within (6) six months of the date of promulgation of this Decision and any other information as may be required by the Ministry.
- Furnish information on the Legal Persons in the State and make them available to public as follows:
- Description of their types, forms and main characteristics.
- Their licensing or registration procedures.
- The procedures for obtaining the basic information stated in Clause (1) of Article (4) hereof.
- The procedures for obtaining the Beneficial Owner data.
- Keep and maintain the basic information stated in Clause (1) of Article (4) hereof, and ensure that they are accurate, up-to-date and available to public.
- Obtain the Beneficial Owner data upon licensing or registering the Legal Person or the update thereof, and verify their accuracy.
- Maintain all registers delivered to him under Clause (7) of Article (11) hereof for a period of (5) five years after the date of dissolution, liquidation or de-registration of the Legal Person.
- Update the basic information stated in Clause (1) of Article (4) of this Decision and the data contained in the Register of Beneficial Owner and Register of Partners or Shareholders on constant basis, based on information provided by the Legal Person, and furnish or disclose the same to the Ministry upon Relevant Entity's request.
- Prepare and issue the templates, notices and manuals related to the licensing or registration procedures, in such manner as may be required to achieve efficiency.
Article (14)
Change of Data
- The Legal Person shall keep and maintain all basic information required by virtue of Article (8) of this Decision, and the data contained in the Register of Partners or Shareholders and the Register of Beneficial Owner, and any-other data or information may be required to be kept by virtue of the legislation in force, to be accurate and updated.
- The Legal Person who makes an amendment or change in data or information required hereunder shall within (15) fifteen days of the date of making the amendment or change, notify the Registrar thereof.
- The Legal Person shall keep and maintain all basic information required by virtue of Article (8) of this Decision, and the data contained in the Register of Partners or Shareholders and the Register of Beneficial Owner, and any-other data or information may be required to be kept by virtue of the legislation in force, to be accurate and updated.
Article (15)
Data Confidentiality
- The Ministry and Registrar shall not disclose to any person the data contained in the Register of Beneficial Owner or the Register of Partners or Shareholders, without a written consent of the Beneficial Owner or the Nominee Board Member.
- The provisions of Clause (1) above shall not apply to:
- Disclosure obligations set forth herein.
- Anything provided for by the international laws and conventions in force in the State, particularly the provisions of Anti-Money Laundering and Combating the Financing of Terrorism and Financing of Illegal Organizations.
- The Ministry and Registrar shall not disclose to any person the data contained in the Register of Beneficial Owner or the Register of Partners or Shareholders, without a written consent of the Beneficial Owner or the Nominee Board Member.
Article (16)
Domestic and international cooperation
- The Ministry shall, upon a request from the Relevant Entities, provide to the Relevant Entities the basic information required under Clause (1) of Article (4) hereof and the data contained in the Register of Beneficial Owner and Register of Partners or Shareholders.
- The Ministry shall provide international cooperation in respect of the basic information on the Legal Person and the data contained in the Register of Beneficial Owner and Register of Partners or Shareholders. Such cooperation shall include:
- Facilitate the access of foreign authorities to the basic information contained in the registers of the Legal Person.
- Exchange data and information of the partners or shareholders of the Legal Person.
- Exercise its powers to obtain all the beneficial owner data on behalf of its counterpart foreign entities.
- The Ministry shall supervise the quality of implementation of international cooperation operations received by the other states in relation to the requests for basic information on the Legal Persons and the data in respect of the Beneficial Owner of the Legal Persons, and international cooperation requests on the whereabouts of the Beneficiary Owner abroad.
- The Ministry shall, upon a request from the Relevant Entities, provide to the Relevant Entities the basic information required under Clause (1) of Article (4) hereof and the data contained in the Register of Beneficial Owner and Register of Partners or Shareholders.
Article (17)
Administrative Sanctions
The Minister or any Licensing Authority delegated by him may, in case of contravention of the provisions hereof, impose one or more of the sanctions specified in the List of Administrative Sanctions issued by Cabinet Decision upon proposal of the Minister of Finance and after coordination with the Minister.
Article (18)
Grievance
Sanctions imposed under the provisions of Article (17) hereof may be appealed within (30) thirty days from the notification date, before a committee formed to this effect by decision of the Minister or the Head of the delegated Licensing Authority. The Committee shall decide on the appeal within (30) thirty days from its submission date.
Article (19)
Repeals
The Cabinet Decision No. (34) of 2020 concerning the Regulation of Beneficial Owner Procedures shall be repealed, and any provision that contradicts or is in conflict with this Decision shall be annulled.
Article (20)
Decision Promulgation and Entry into Force
This Decision shall be promulgated in the Official Gazette and shall come into force on the day following its Promulgation.
Cabinet Decision 74 of 2020: Terrorism Lists Regulation and Implementation of UN Security Council Resolutions
CAB DEC 74/2020 Effective from 27/10/2020The Cabinet:
- Having perused the Constitution,
- Federal Law No (1) of 1972 on the Mandates of Ministries and Powers of Ministers, and amendments thereto;
- Federal Law No. (17) of 2006 on the Establishment of the Supreme Council for National Security;
- Federal Law No. (13) of 2007 on Goods Subjected to Import and Export Control, and amendments thereto;
- Federal Law No. (7) of 2014 on Combating Terrorism Offences;
- Cabinet Decision No. (20) of 2019 on Terrorism Lists Regulation and Implementation of UN Security Council Resolutions on the Suppression and Combating of Terrorism, Terrorist Financing and Proliferation of Weapons of Mass Destruction, and Relevant Resolutions, and
- Based on the proposal of the Minister of Foreign Affairs and International Cooperation and the Cabinet’s approval;
Resolved as follows:
Article 1 - Definitions
In the implementation of the provisions of this Decision, and unless the context otherwise requires, the following terms and expressions shall have the meanings cited against each:
The State: The United Arab Emirates;
The Council: The Supreme Council for National Security;
The Ministry: The Ministry of Foreign Affairs & International Cooperation;
The Competent Court: The Court that has jurisdiction over State Security Offences;
The Office: The Executive Office of the Committee for Goods Subjected to Import and Export Control;
Supervisory Authorities: Federal and Local authorities entrusted as per Legislations, with the supervision of Financial Institutions and Designated Non-Financial Businesses and Professions.
Law Enforcement Authorities: Federal and Local authorities entrusted, as per Legislations with the tasks of combating crime, search, investigation, and collection of evidence in offences, including money laundering, financing of terrorism and the financing of illegal organizations.
Sanctions Committee: Any of the UN Security Council Committees established as per its resolutions, including UNSCRs 1267 (1999) and 1989 (2011) relating to ISIL and Al-Qaida, 1988 (2011) relating to the Security and Stability of Afghanistan, and 1718 (2006) relating to the suppression and combating of proliferation of weapons of mass destruction for the DPRK.
Listed Person: A person or organization listed by the UN Security Council on the Sanctions List, or listed by the Cabinet on Local Lists, as the case may be.
Person: A natural or legal person.
Ombudsperson: The person appointed by the UN Secretary General to assist the Sanctions Committee when examining requests submitted by individuals, groups, undertakings and entities for delisting from the ISIL and Al Qaeda Sanctions List.
Focal Point: The focal point established within the Secretariat pursuant to UNSCR 1730 (2006) to receive petitions from persons or entities in the State or holding the State’s nationality, listed on the relevant list, requesting to be de-listed or seeking exemptions for humanitarian reasons, from a travel ban, or from freezing measures or persons claiming to have been wrongfully sanctioned.
Relevant UNSCRs: All current and future UN Security Council resolutions relating to the suppression and combating of terrorism, terrorist financing and proliferation of weapons of mass destruction and its financing, including but not limited to Resolutions 1267 (1999), 1988 (2011), 1989 (2011), 1718 (2006), 2231 (2015) and any successor resolutions.
Listing: Identifying the individual or organization subject to sanctions imposed pursuant to relevant UNSCRs, decisions of the Sanctions Committee, or relevant decisions of the Cabinet, as the case may be, and implementing relevant sanctions against such individual or organization, with a statement of the reasons for listing.
Local Lists: Terrorism lists issued by the Cabinet pursuant to the provisions of Article (63) paragraph (1) of Federal Law No (7) of 2014.
Sanctions List: A list containing the names of individuals and organizations linked to terrorism, financing of terrorism or proliferation of weapons of mass destruction and its financing, and that are subject to sanctions imposed as per UNSCRs and decisions of the Sanctions Committee, along with information related to such persons and reasons for their listing.
Narrative Summary: The declared part of the reasons for Listing an individual or organization on the Sanctions List annexed to the Listing decision by the Sanctions Committee.
Funds: Assets of all types, in whatever form and however acquired, whether corporeal or incorporeal, tangible or intangible, movable or immovable, electronic, digital or encrypted, including national currency, foreign currencies, documents and legal instruments establishing ownership of such assets or any associated rights, in whatever form, including electronic or digital forms, as well as economic resources considered as assets of any kind, including oil and natural resources, and bank credits, checks, money orders, shares, securities, bonds, drafts, and letters of credit and any interest, dividends, or other income accruing from or generated by such assets, and that may be used to obtain any other funds, goods or services including internet posting services or related services.
Other Measures: Sanction measures other than freezing that must be enforced, and which may be included in relevant UNSCRs or Cabinet decisions regarding the issuance of local lists, such as prohibitions relating to travel, weapons, imports, or provision of fuel supplies and other.
Without Delay: Within 24 hours of the Listing decision being issued by the UN Security Council, the Sanctions Committee or the Cabinet, as the case may be.
Article 2 - Mandate of the Council
- For the purposes of implementing the provisions of this decision, the Council shall have the following mandate:
- Establish one Local List or more, where it proposes the listing, de-listing or re-listing of terrorist persons and organizations and the updating of such list, whether spontaneously or upon the request of another country, or in case the State has an international obligation to list such persons or organizations.
- Coordinate with other countries to list a terrorist person or organization in their local terrorist lists.
- Propose the listing of terrorist persons or organizations on the Local List to the Sanctions Committee.
- Submit requests for de-listing terrorist persons or organizations from the Sanctions List, when it believes that such terrorist persons or organizations do not or no longer meet the designation criteria, while taking into account procedures and criteria set out in relevant UNSCRs.
- Conduct a regular review of Local Lists in coordination with the Ministry of Justice. The Council is entitled to request any clarifications or document it deems suitable from Law Enforcement Authorities and concerned entities in the State to review such, provided that the period for review does not exceed one year.
- Establish one Local List or more, where it proposes the listing, de-listing or re-listing of terrorist persons and organizations and the updating of such list, whether spontaneously or upon the request of another country, or in case the State has an international obligation to list such persons or organizations.
- The Council shall exercise its powers set forth in sub-paragraphs a, b and c of paragraph 1 of this Article in accordance with the rules and procedures set forth in Relevant UNSCRs, whenever there are reasonable grounds for such, irrespective of the existence of criminal proceedings.
- For the purposes of implementing the provisions of this decision, the Council shall have the following mandate:
Article 3 - Proposing Listing and Re-listing on Local Lists and Updating Such
Subject to the provisions of Article (2) Paragraph (2) of the present Decision, the Council shall coordinate with any entity it deems suitable in the State and abroad to obtain information regarding the designation of terrorist persons and organizations that meet the designation criteria for the purpose of preparing a proposal for listing on Local Lists according to the following procedures:
- The Council shall, unilaterally and without prior notice to the Listed Person, establish one Local List or more where it proposes the Listing of terrorist persons and organizations, or propose Listing upon the request of another country, whenever the Council is satisfied with the presence of reasonable grounds or sound basis for suspicion or when it believes that such person or organization meets the designation criteria for Listing, or if the State is internationally committed to list such persons and organizations. The Council shall take such decision as swiftly as possible.
- In the Listing process, the Council shall take into account the designation criteria contained in UNSCR 1373 (2001), which include the following:
- Any person or organization that commits, attempts to commit, participates in or facilitates the commission of terrorist acts.
- Any organization directly or indirectly owned or controlled by a person or organization as set out in sub-paragraph (a) of paragraph (2) of the present Article.
- Any person or organization acting on behalf of or at the direction of any person or organization as set out in sub-paragraph (a) of paragraph (2) of the present Article.
- Any person or organization that commits, attempts to commit, participates in or facilitates the commission of terrorist acts.
- The Council shall coordinate with the Ministry of Justice with regard to proposed Listing on Local Lists, if the Council determines that a person or an organization meets the designation criteria referred to in paragraph (2) of the present Article. The Council then forwards the proposal to the Ministry of Presidential Affairs for consideration and issuing by the Cabinet.
- In case Local Lists were issued by the Cabinet, the Office shall be notified for publication, Without Delay, as per its established procedures.
- The procedures set forth in the present Article shall be implemented when Local Lists are updated, and when re-listing any previously de-listed person, in case there are reasons requiring their Listing in such lists, in accordance with the provisions of paragraph (2) of the present Article.
- The Council shall, unilaterally and without prior notice to the Listed Person, establish one Local List or more where it proposes the Listing of terrorist persons and organizations, or propose Listing upon the request of another country, whenever the Council is satisfied with the presence of reasonable grounds or sound basis for suspicion or when it believes that such person or organization meets the designation criteria for Listing, or if the State is internationally committed to list such persons and organizations. The Council shall take such decision as swiftly as possible.
Article 4 - De-listing From Local Lists
The Council may de-list a Listed Person from Local Lists according to the following procedures:
- The Council shall notify the Ministry of Presidential Affairs of reasons to de-list, if it considers that the information or evidence regarding a Listed Person on the Local List no longer require their listing, and once it has verified that the reasons for the Listing no longer exist.
- The Ministry of Presidential Affairs shall be in charge of submitting the proposal to de-list the Listed Person from the Local Lists to the Cabinet, in order for the Cabinet to decide whether to approve or reject the request.
- The Office shall be notified of the de-listing decision referred to under paragraph (2) of the present Article, immediately upon issuance thereof, to circulate the decision, lift freezing and any other measures taken, as per its established procedures.
- The Council shall notify the Ministry of Presidential Affairs of reasons to de-list, if it considers that the information or evidence regarding a Listed Person on the Local List no longer require their listing, and once it has verified that the reasons for the Listing no longer exist.
Article 5 - Enforcement and Publication of Local Lists
- Decisions to list, de-list and re-list on Local Lists, and to update such lists shall be effective from the date of their issuance, or from the date determined by the Cabinet, and shall be published in the Official Gazette.
- Decisions to list, de-list and re-list on Local Lists, and to update such lists shall be published in the media, in both Arabic and English, as per the regulations established by the Council.
- Decisions to list, de-list and re-list on Local Lists, and to update such lists shall be effective from the date of their issuance, or from the date determined by the Cabinet, and shall be published in the Official Gazette.
Article 6 - Grievances Against Decisions to List on Local Lists
Anyone whose name is listed on Local Lists may file a grievance against such decision according to the following procedure:
- The Listed Person may submit, in person or through a legal representative, a written grievance application to the Office, in accordance with the latter’s established mechanism, attaching thereto all documents supporting the grievance.
- The Office shall refer the grievance to the Council for review and examination. Both the Office and the Council shall have the right to request any clarifications or further documentation from the applicant, or from Law Enforcement Authorities or other relevant entities in the State, for the purposes of deciding on the application.
- The Council shall receive the grievance application, verify whether it is new or recurring, and may reject it, if it was recurring and did not include additional information other than the information contained in the previous grievance, or for any other reasons.
- If the Council, during its review of the grievance application, determines that the information or evidence regarding the Listed Person on Local List no longer require their listing, and once it has confirmed that the reasons that called for the Listing no longer exist, the Council shall notify the Ministry of Presidential Affairs.
- The Minister of Presidential Affairs shall be in charge of submitting the grievance application, along with the Council’s opinion to the Cabinet, as per its established submittal mechanisms, in order for the Cabinet to make a decision to either approve or reject the grievance.
- In case of approval of the grievance by the Cabinet, the name of the Listed Person shall be removed from Local Lists and freezing and other measures taken in accordance with the Listing decision shall be lifted. The Office shall be notified immediately upon issuance thereof to notify the applicant and publish the decision as per the Office’s established procedures.
- In case the grievance is rejected or if no response is received regarding the application within sixty days from the date of its submission, the applicant may appeal the Cabinet’s Listing decision before the Competent Court within sixty days from the date he/she was notified of the rejection, or from the expiry of the response period.
- The court’s decision regarding the grievance shall be not be subject to appeal. If a grievance is rejected, a new grievance may only be submitted after six months from the date of rejection of the previous grievance, unless a serious reason that is accepted by the president of the court arises before the expiry of such period.
- An appeal against a Listing or re-Listing decision shall not be accepted before a grievance against it is filed and rejected, or before the period given to respond expires, as set out in the present Article.
- The Listed Person may submit, in person or through a legal representative, a written grievance application to the Office, in accordance with the latter’s established mechanism, attaching thereto all documents supporting the grievance.
Article 7 - Lifting Freezing and Other Measures in the Case of False Positives on Local Lists
Any person or organization inadvertently affected by freezing or other measures due to a similarity between their name and the name of a Listed Person on Local Lists, and any person or organization that has been affected by such measures may cancel such procedures as follows:
- Submitting a written request to the Office, in person or through a legal representative, to lift freezing or any other measures taken against them, along with all supporting documents.
- The Office shall refer the request to the Council for examination. Both the Office and the Council may ask for any clarifications or additional documents from the applicant, Law Enforcement Authorities or relevant entities in the State, for the purpose of deciding on the request.
- After examining that the applicant or his/her funds are not related to the Listing, the Council shall issue its decision to accept or reject the request, and shall send such decision, within thirty days from date of receipt of the request to the Office, which would in turn notify the applicant of the outcome in writing.
- In case the request is accepted by the Council, the Office shall address the entity where the funds are frozen, Law Enforcement Authorities and the entities concerned with Other Measures, to lift the actions taken against the applicant. The addressed entity should immediately execute the decision.
- In case the request is rejected by the Council, or if no response to the request is received within thirty days from date of its submission, the applicant may file a grievance before the Competent Court within sixty days from the date of notification of the rejection, or from the expiry of the response period.
- The court’s decision on the grievance shall be not be subject to appeal, and if the court ruled to reject the grievance, a new grievance may only be filed after six months from the date of rejection of the grievance, unless a serious reason that is accepted by the president of the court arises before the expiry of such period.
- An appeal against a decision to apply freezing and Other Measures shall not be accepted before a grievance against such is filed and rejected, or before the period given to respond expires, as set out in the present Article.
- Submitting a written request to the Office, in person or through a legal representative, to lift freezing or any other measures taken against them, along with all supporting documents.
Article 8 - Permission to Use Funds Frozen pursuant to Listing on Local Lists
- Any Listed Person on Local Lists, or their legal representative, and any interested party may submit to the Office a written request to use the Listed Person’s frozen Funds. The Office shall refer the request to the Ministry of Justice, provided such request includes all supporting documents.
- The Ministry of Justice shall examine the request, its reasons and the amounts to which access is requested and may reduce such amounts or reject the request based on justified reasons.
- Following coordination with the Council, The Ministry of Justice may approve the request to use the frozen funds of a Listed Person on Local Lists, for any of the following purposes:
- To cover necessary or basic expenses, such as the amounts payable for foodstuff, rent, mortgage, medicine, medical treatment, taxes, insurance premium, educational or judicial fees, or public utility fees.
- To pay professional fees or costs relating to legal services rendered or other extraordinary expenses within reasonable limits; or fees for services relating to safekeeping or management of frozen Funds.
- To cover necessary or basic expenses, such as the amounts payable for foodstuff, rent, mortgage, medicine, medical treatment, taxes, insurance premium, educational or judicial fees, or public utility fees.
- The Ministry of Justice shall notify the Office of the approval or rejection of the request, and the Office shall in turn notify the applicant of the decision in writing.
- In case the request is rejected, or if no response to the request is received within thirty days from date of its submission, the applicant may file a grievance before the Competent Court within thirty days from the date when he/she was notified of the rejection, or from the expiry of the response period.
- An appeal against the rejection of the request shall not be accepted before a grievance against it is filed and rejected, before the period given to respond expires, as set out in the present Article.
- In all cases, the procedures set forth in UNSCR 1452 (2002) and any successor resolutions shall be taken into account.
- Any Listed Person on Local Lists, or their legal representative, and any interested party may submit to the Office a written request to use the Listed Person’s frozen Funds. The Office shall refer the request to the Ministry of Justice, provided such request includes all supporting documents.
Article 9 - Request to Listing on Another Country's List
Subject to paragraph (2) of Article (2) of the present Decision, the Council may, unilaterally, request a foreign country to list a person or organization that meets the designation criteria under UNSCR 1373 (2001) on the local list of such country, through the following procedures:
- Communicate through diplomatic or established security channels with the country of nationality or previous or current residence of the person or organization, to obtain, as much as possible, information supporting the Listing request.
- The Listing request should include as much details as possible on the grounds and justifications of such request and may include the following:
- Specific information supporting links to terrorist organizations, individuals or activities or otherwise establishing that the person or organization meets the designation criteria.
- Evidence or documents supporting the Listing request such as reports from Law Enforcement Authorities, security services, the Judiciary, the media and others.
- Specific information supporting links to terrorist organizations, individuals or activities or otherwise establishing that the person or organization meets the designation criteria.
- The Council shall attach to the Listing request all personal information to enable accurate and positive identification of the person requested for listing, along with all data and information supporting that the person requested for listing meets the designation criteria set forth in UNSCR 1373 (2001).
- The Council shall send the Listing request to the Ministry, which would in turn address the concerned country and notify the Council upon receipt of the response.
- Communicate through diplomatic or established security channels with the country of nationality or previous or current residence of the person or organization, to obtain, as much as possible, information supporting the Listing request.
Article 10 - Proposal for Listing to the Sanctions Committee
Subject to paragraph (2) of Article (2) of the present Decision, and if the Council is satisfied that there are reasonable grounds or a sound basis to suspect or believe that a person or organization meets the designation criteria for Listing on the Sanctions List, the Council may, unilaterally and without prior notice, propose Listing on the relevant Sanctions List of any person or organization, by submitting such proposal to the Security Council or the concerned Sanctions Committee such as those established pursuant to UNSCRs 1988 (2011), 1267 (1999), 1989 (2011), 2253 (2015), 1718 (2006) and 2231 (2015) for designation and successor resolutions, while taking into account the relevant designation criteria and using the standard forms approved by the relevant committee for Listing in accordance with the following procedures:
- The Council shall seek to collect information about the person or organization proposed for Listing using the assistance of Law Enforcement Authorities and relevant entities in the State, for the purposes of preparing the proposal for Listing on the Sanctions List.
- The Council shall communicate, through diplomatic or established security channels with the country of nationality or current or past residence of the proposed person in order to obtain information, if possible.
- The Listing proposal must include a detailed statement of the case to support the proposed Listing, and the specific criteria on the basis of which the name of the person or organization was proposed for Listing, including:
- Specific results and reasons showing fulfillment of the Listing criteria as set out in relevant UNSCRs or by the relevant Sanctions Committee.
- Evidence or documents supporting the Listing proposal such as reports of Law Enforcement Authorities, security services, the Judiciary, the media and others.
- Details on any relationship with a person currently listed on the Sanctions List.
- Specific results and reasons showing fulfillment of the Listing criteria as set out in relevant UNSCRs or by the relevant Sanctions Committee.
- The Council shall work on providing a statement of information to the extent possible as per the Consolidated Form for the purposes of Listing on the relevant Sanctions List.
- The Listing proposal must include a statement by the State as to whether the Sanctions Committee can disclose that the State is the entity requesting the listing or not.
- The Council shall send the Listing proposal to the relevant Sanctions Committee through the Office.
- The Council shall seek to collect information about the person or organization proposed for Listing using the assistance of Law Enforcement Authorities and relevant entities in the State, for the purposes of preparing the proposal for Listing on the Sanctions List.
Article 11 - Mandate of the Office
For the purposes of implementing the provisions of the present Decision, the Office - as a National Coordination Body - shall have the following mandate:
- Take necessary measures to implement UN Security Council resolutions, Without Delay and without prior notice to the Listed Person, in accordance with the requirements thereof, particularly resolutions related to Terrorism, Terrorist Financing and the Prevention, Suppression and Disruption of Proliferation of Weapons of Mass Destruction and its Financing.
- Publish the Sanctions List and the updated Local Lists on the Office’s website, Without Delay.
- Notify a Listed Person residing in the State of their Listing, after the completion of the Funds freezing procedures, and provide such Listed Person with the Narrative Summary directly, or with the necessary information on the reasons for their listing, and explain the implications of their Listing on the Sanctions List, the procedures that the Sanctions Committee follows in considering requests for de-listing from the Sanctions List, including the possibility of submitting such requests to the Ombudsperson or Focal Point, as the case may be, in addition to the possibility of using part of the Funds frozen in accordance with the provisions of the present Decision , by making this information available on the Office’s website.
- Receive and process notifications relating to measures taken in implementation of the relevant UNSCR or Local Lists.
- Receive grievances against Listing on Local Lists, requests for lifting freezing or Other Measures taken against persons with names similar to the names of Listed Persons, in addition to requests for using frozen Funds.
- Internal coordination and exchange of information between concerned entities regarding the implementation of the provisions of the present Decision, including coordination to develop typology reports on the evasion of freezing and Other Measures, and cooperation with the Financial Intelligence Unit (FIU) in developing red flags at financial institutions and DNFBPs related to evading freezing and Other Measures.
- Collect the results of supervision and enforcement measures from Supervisory Authorities related to implementing the provisions of the present Decision and coordinate efforts in this regard.
- Communicate and engage with FIs, DNFBPs and the public with regards to the implementation of the provisions of the present Decision, including by providing training, outreach and awareness raising in coordination with Supervisory Authorities, in order to enhance effectiveness at the level of receiving notifications from the Office related to the Sanctions List and Local Lists, Without Delay; and issue the necessary instructions on compliance and collect statistics related to the implementation of the present Decision.
- Take necessary measures to implement UN Security Council resolutions, Without Delay and without prior notice to the Listed Person, in accordance with the requirements thereof, particularly resolutions related to Terrorism, Terrorist Financing and the Prevention, Suppression and Disruption of Proliferation of Weapons of Mass Destruction and its Financing.
Article 12 - Publication of the Sanctions List, Local Lists, and Implementation of Related Decisions
- The Office shall publish Sanctions List and Local Lists by sending them using the means it deems appropriate to Supervisory Authorities, financial institutions and DNFBPs for the implementation of the freezing decision, and to Law Enforcement Authorities for the implementation of Other Measures, Without Delay and without prior notice to the Listed Person.
- Law Enforcement Authorities and Supervisory Authorities shall provide the Office with any information, if applicable, regarding the outcome of the implementation of the freezing or Other Measures, as the case may be, within five business days from the date of implementation.
- The Office shall send the data and information received from Supervisory Authorities and Law Enforcement Authorities to the UN Security Council and the Sanctions Committee, as the case may be, through the Ministry.
- The Office shall send information and data received from Supervisory Authorities and Law Enforcement Authorities regarding measures taken in relation to Local Lists, to the Council.
- The Office shall publish Sanctions List and Local Lists by sending them using the means it deems appropriate to Supervisory Authorities, financial institutions and DNFBPs for the implementation of the freezing decision, and to Law Enforcement Authorities for the implementation of Other Measures, Without Delay and without prior notice to the Listed Person.
Article 13 - Declared Procedures Relating to Sanctions List
The Office shall state, on its official website, procedures for submitting requests for de-listing from the Sanctions List, including the following procedures:
- Guiding Listed Person as per relevant UNSCRs to submit a de-listing request to the Ombudsperson or Focal Point directly, as the case may be, showing the applicable steps to submit a request as indicated below:
- Submit a request to the Focal Point or the Ombudsperson, as the case may be, to verify such, coordinate with the concerned states and present the request to the relevant Sanctions Committee.
- The Office shall receive, from the Ombudsperson or the Focal Point, the additional information request related to the Listed Person’s request for de-listing.
- The Office shall coordinate with the concerned authorities it deems appropriate to examine the request for additional information during the period specified by the Ombudsperson or Focal Point, and provide them with its observations and to what extent the Listed Person or organization is entitled to be de-listed. The Office may ask any questions or ask for more clarifications from the Listed Person submitting the request and shall respond to any other queries raised by the Ombudsperson or Focal Point.
- Submit a request to the Focal Point or the Ombudsperson, as the case may be, to verify such, coordinate with the concerned states and present the request to the relevant Sanctions Committee.
- Procedures to lift freezing measures imposed due a false positive.
- Cases where access to frozen Funds is permitted and cases of exemption from Other Measures.
- Mechanisms for notifying Supervisory Authorities, Law Enforcement Authorities, Financial Institutions and DNFBPs of cases of de-listing or lifting of freezing measures.
- Guiding Listed Person as per relevant UNSCRs to submit a de-listing request to the Ombudsperson or Focal Point directly, as the case may be, showing the applicable steps to submit a request as indicated below:
Article 14
- The Office shall submit a request for de-listing a deceased person or a defunct organization from the Sanctions List and Local Lists, to the Ombudsperson or Focal Point, as the case may be, along with a death certificate for natural persons and any information proving that the organization no longer exists or is no longer active.
- The Office shall take necessary actions to ensure, in coordination with concerned entities, that the funds that were in the possession of the Listed Person are not transferred or at any time distributed to other persons listed on the Sanctions List or Local Lists, including ensuring that none of the legal heirs or beneficiaries of the Funds is listed on the Sanctions List or Local Lists, and the Office should notify the Ombudsperson or Focal Point, as the case may be, to such effect.
- The Office shall take necessary actions to lift the freezing of Funds of Listed Person referred to in the present Article, after receiving the response of the Ombudsperson or Focal Point, as the case may be. If the State was the party that proposed the Listing on the Sanctions List, and a de-listing request was submitted to the Ombudsman or Focal Point, the Office shall examine the request in coordination with the Council and shall proceed with the actions mentioned the present Article.
- The Office shall submit a request for de-listing a deceased person or a defunct organization from the Sanctions List and Local Lists, to the Ombudsperson or Focal Point, as the case may be, along with a death certificate for natural persons and any information proving that the organization no longer exists or is no longer active.
Article 15 - Freezing Funds As per the Sanctions List & Local Lists
- Any person shall, Without Delay and without prior notice, freeze Funds as per the Sanctions List and Local Lists without limiting such measure to funds that may only be used to perpetrate a certain act, conspiracy, threat or agreement related to terrorism and its financing or WMD proliferation and its financing. The freezing measure shall include the following:
- Funds owned or controlled, wholly or jointly, directly or indirectly, by the Listed Person or funds owned or controlled, wholly or jointly, directly or indirectly, by a person or organization acting on behalf or at the direction of the Listed Person;
- Funds derived or generated from funds under sub-paragraph (a) of the present Article.
- Funds owned or controlled, wholly or jointly, directly or indirectly, by the Listed Person or funds owned or controlled, wholly or jointly, directly or indirectly, by a person or organization acting on behalf or at the direction of the Listed Person;
- Any person must notify the Office of any freezing measures taken pursuant to Paragraph (1), within five business day of the date of the freezing.
- No person shall make funds available or provide financial or other related services, whether in whole or in part, directly or indirectly, to any of the persons or entities mentioned in paragraph (1) of the present Article, except upon authorization from the Office in line with the provisions of the present Decision, and after coordination with the Council or the UN Security Council or the relevant Sanctions Committee, and in line with Cabinet decisions regarding the issuance of Local Lists, or relevant UNSCRs, as the case may be.
- In all cases, the rights of bona fide third parties shall be taken into account when implementing any freezing measure.
- Any person shall, Without Delay and without prior notice, freeze Funds as per the Sanctions List and Local Lists without limiting such measure to funds that may only be used to perpetrate a certain act, conspiracy, threat or agreement related to terrorism and its financing or WMD proliferation and its financing. The freezing measure shall include the following:
Article 16
- The implementation of freezing measures pursuant to UNSCRs 1718 (2006) and 2231 (2015) shall not prevent adding to the frozen account any interest, profits or other payments due under contracts, agreements or obligations that arose prior to the date on which the account was subject to provisions of the said resolutions, provided such additions are immediately frozen and reported to the Office.
- In all cases, procedures set forth in UNSCRs 1452 (2002), 2231 (2015), 1718 (2006) and 2270 (2016) and any successor resolutions must be observed.
- The implementation of freezing measures pursuant to UNSCRs 1718 (2006) and 2231 (2015) shall not prevent adding to the frozen account any interest, profits or other payments due under contracts, agreements or obligations that arose prior to the date on which the account was subject to provisions of the said resolutions, provided such additions are immediately frozen and reported to the Office.
Article 17
The implementation of a freezing order pursuant to UNSCR 1737 (2006), continued pursuant to UNSCR 2231 (2015) or taken pursuant to UNSCR 2231 (2015), shall not prevent a Listed Person or organization from making a payment due under a contract that was concluded prior to their listing, subject to the following conditions:
- The Office has determined that the contract is not related to any prohibited items, materials, equipment, goods, technologies, assistance, training, financial assistance, investments, brokerage or services referred to in UNSCR 2231 (2015) or any future successor resolution.
- The Office has determined that the payment is not received, directly or indirectly, by any person or organization listed pursuant to Paragraph (6) of Appendix B of UNSCR 2231 (2015).
- The Office has submitted a prior notification to the UN Security Council, including its request to make or receive such payments or to authorize, where appropriate, the unfreezing of funds for this purpose, within ten business days before the issuance of such authorization.
- The Office has determined that the contract is not related to any prohibited items, materials, equipment, goods, technologies, assistance, training, financial assistance, investments, brokerage or services referred to in UNSCR 2231 (2015) or any future successor resolution.
Article 18 - Lifting the Freezing of Funds & Other Measures Taken in Cases of False Positives on the Sanctions List
The mechanism for lifting freezing and any other measures taken against a person or organization bearing a name similar to that of a listed person, shall be as follows:
- The affected person shall submit a written request to the Office in person or through a legal representative, to lift freezing or any other measures taken against him, along with all documents supporting a false positive.
- The Office shall examine the request, and for the purposes of deciding on the request, may ask for any clarifications or additional documents, it deems suitable from the applicant, the UN Security Council, the relevant Sanctions Committee or any other party.
- The Office shall issue its decision to reject or approve the request to lift the freezing measures within thirty days from date of receipt of the request and shall notify the applicant accordingly.
- The Office shall communicate the decision to approve the request, to the entity where the funds are frozen, Law Enforcement Authorities and concerned agencies. The addressed organization shall immediately execute the decision to lift freezing and other measures taken against the applicant due to a false positive.
- In case the request to lift freezing and Other Measures is rejected, or remained without a response for thirty days from date of its submission, the applicant may file a grievance before the Competent Court within sixty days from the date on which he/she was notified of the rejection of the request, or from the expiry of the response period.
- The court’s decision regarding the grievance shall not be subject to appeal. If a grievance is rejected, a new grievance may only be submitted after six months from the date of rejection of the previous grievance, unless a serious reason that is accepted by the president of the Court arises before the expiry of such period.
- An appeal against a decision regarding freezing or Other Measures shall not be accepted before a grievance against such is filed and rejected, or the period for responding to such grievance has elapsed, as set out in the present Article.
- The affected person shall submit a written request to the Office in person or through a legal representative, to lift freezing or any other measures taken against him, along with all documents supporting a false positive.
Article 19 - Permission to Use Funds Frozen as Per the Sanctions List
- The Office may approve a person’s request to access funds frozen as per the Sanctions List, in the following cases:
- To cover necessary or basic expenses, such as the amounts payable for foodstuff, rent, mortgage, medicine, medical treatment, taxes, insurance premiums, educational or judicial fees, or public utility fees.
- To pay professional fees and costs relating to rendered legal services within reasonable limits; or services relating to the safekeeping or management of frozen Funds.
- To cover extraordinary expenses other than those mentioned in sub-paragraphs (a and b) of this paragraph.
- In the case of sanctions imposed pursuant to UNSCRs 1718 (2006) and 1737 (2006), and continued as per UNSCR 2231 (2015), and in addition to the measures mentioned above, if access was requested to use frozen funds which are subject to mortgage, or a judicial, administrative or arbitral lien or ruling, and if the funds will be used, exclusively, to satisfy the expenses of that lien or judgment, and provided that the mortgage or the ruling entered into effect at a time prior to the date of the listing in accordance with the referenced resolutions, and that the funds are not used for the benefit of any Listed Peron, and after the Office notifies the UN Security Council or the relevant Sanctions Committee, as the case may be.
- To cover necessary or basic expenses, such as the amounts payable for foodstuff, rent, mortgage, medicine, medical treatment, taxes, insurance premiums, educational or judicial fees, or public utility fees.
- Requests for the purpose of deciding on any of the items under paragraph (1) of this article, shall be submitted directly to the Office, by the Listed Person or their legal representative, along with all supporting documents.
- The Office shall examine the requests referred to in paragraph (2) of this article, their reasons, and the requested amounts, and may reduce or reject such amounts, based on justifiable grounds.
- In the event that the submitted request is related to the expenses mentioned in sub-paragraphs (a, b, and d) of paragraph (1) of the present Article, the Office must notify the UN Security Council or the Sanctions Committee of its intention to approve the submitted request following consideration thereof in accordance with the provisions of paragraph (3) of this article, and in case the sanctions committee does not object, or issue a decision of rejection within five business days from the date of its notification, the funds that the Office agreed to unfreeze shall be unfrozen and the entity holding the frozen funds shall be immediately notified in writing to such effect and asked to implement the decision immediately. Such entity shall notify the Office of the actions taken in this regard.
- In case the submitted request relates to the expenses mentioned in sub-paragraph (c) of Paragraph (1) of the present Article, the Office shall notify the Sanctions Committee of its intention to approve the submitted request following consideration thereof in accordance with the provisions of Paragraph (3) of this article, and obtain the Sanctions Committee’s written approval.
- For the purposes of paragraphs (4) and (5) of this article, the Office must notify the person requesting the use of funds frozen as per the Sanctions List, or their legal representative, in writing, of its approval of the request or its justified rejection of such, as soon as possible.
- The Office may revoke its decision to approve the request to use funds frozen under the Sanctions List, any time there are reasonable grounds for suspicion that the funds are used for financing terrorism or financing WMD proliferation.
- In case the request to use funds frozen under the Sanctions List is rejected, or remains without response for thirty days from date of its submission, the applicant may file a grievance before the Competent Court within sixty days from the date on which he/she was notified of the rejection of the request, or from the expiry of the response period.
- The Court’s decision on the grievance may not be appealed, and if the court ruled to reject the grievance, a new grievance may only be filed after six months from the date of rejection of the grievance, unless a serious reason that is accepted by the president of the Court arises before the expiry of such period.
- An appeal against a decision to refuse the use of frozen funds shall not be accepted before a grievance against such is filed and rejected, or the period for responding to such grievance has elapsed.
- In all cases, the procedures set forth in UNSCRs 1452 (2002), 1718 (2006) and 2231 (2015) and any successor resolutions, shall be observed.
- The Office may approve a person’s request to access funds frozen as per the Sanctions List, in the following cases:
Article 20
The Office may set any controls it deems appropriate for the exemptions and payments stipulated in this Decision, to prevent the use of the funds for financing terrorism or WMD proliferation.
Article 21 - Obligations of Financial Institutions and DNFBPs
For the purposes of implementing the present Decision, financial institutions and DNFBPs shall abide by the following:
- Register on the Office’s website in order to receive notifications related to new listing, re-listing, updating, or de-listing decisions issued by the UN Security Council, the Sanctions Committee or the Cabinet.
- Regularly screen their databases and transactions against names on lists issued by the UN Security Council, the Sanctions Committee or the Local Lists, and also immediately when notified of any changes to any of such lists, provided that such screening includes the following:
- Searching their customer databases.
- Search for the names of parties to any transactions.
- Search for the names of potential customers.
- Search for the names of beneficial owners.
- Search for names of persons and organizations with which they have a direct or indirect relationship.
- Continuously search their customer database before conducting any transaction, or entering into a serious business relationship with any person, to ensure that their name is not listed on the Sanctions List or Local Lists.
- Searching their customer databases.
- Implement freezing measures, without delay, and without prior notice to the Listed Person, immediately when a match is found through the screening process referred to in paragraph (2) of this article.
- Implement decisions to lift freezing measures without delay, pursuant to Relevant UNSCRs or decisions of the Cabinet regarding the issuance of Local Lists.
- Immediately notify the Supervisory Authority in the following cases:
- Identification of funds and actions that have been taken as per requirements of Relevant UNSCRs or decisions of the Cabinet regarding the issuance of Local Lists, including attempted transactions.
- Detection of any match with listed persons or entities, details of the match data and actions that have been taken as per the requirements of Relevant UNSCRs and Local Lists, including attempted transactions.
- If it was found that one of its previous customers or any occasional customer it dealt with, is listed on the Sanctions List or Local Lists.
- If it suspects that one of its current or former customers, or a person it has a business relationship with is listed or has a direct or indirect relationship with the Listed Person.
- No action has been taken due to a false positive, and the inability to dismiss such false positive through available or accessible information.
- Information relating to funds that have been unfrozen, including their status, nature, value and measures that were taken in respect thereof, and any other information relevant to such decisions.
- Identification of funds and actions that have been taken as per requirements of Relevant UNSCRs or decisions of the Cabinet regarding the issuance of Local Lists, including attempted transactions.
- Establish and effectively implement internal controls and procedures to ensure compliance with the obligations arising from this Decision.
- Establish and implement policies and procedures that prohibit staff from, directly or indirectly, informing the customer or any third party that freezing or any Other Measures shall be implemented in accordance with the provisions of this Decision.
- Cooperate with the Office and the Supervisory Authority in verifying the accuracy of submitted information.
- Register on the Office’s website in order to receive notifications related to new listing, re-listing, updating, or de-listing decisions issued by the UN Security Council, the Sanctions Committee or the Cabinet.
Article 22 - Obligations of Supervisory Authorities
Supervisory Authorities shall abide by the following:
- Receive all information from FIs and DNFBPs regarding frozen funds, or any measures taken in compliance with prohibition requirements pursuant to the present Decision, including attempted transactions and send such information to the Office within five working days from the date of its receipt.
- Supervise, monitor and follow-up to ensure compliance with the provisions of this Decision, through onsite and offsite inspection, and imposing appropriate administrative sanctions in case of violation or failure to implement such provisions.
- Establish a list of cases detected, as per the provisions of this Decision, by FIs and DNFBPs, where the customer or beneficial owner was a Listed Person or organization.
- Identify any funds related to a Listed Person that have been detected and frozen by FIs and DNFBPs, and whether or not relevant reports were submitted to the Office in line with the provisions of the present Decision.
- Submit reports to the Office at least semiannually on results of supervision, monitoring and follow-up on the implementation of FIs and DNFBPs of their obligations under the present Decision.
- Receive all information from FIs and DNFBPs regarding frozen funds, or any measures taken in compliance with prohibition requirements pursuant to the present Decision, including attempted transactions and send such information to the Office within five working days from the date of its receipt.
Article 23 - General Provisions
- Any person who, due to the nature of their work, has access to, or becomes aware of, any information provided or exchanged pursuant to the provisions of the present Decision, whether directly or indirectly, shall not disclose this information in any form, unless for the purposes of implementing the present Decision.
- A person who, in good faith, freezes Funds, denies disposal thereof, refuses to provide financial services relating thereto, or declines to perform any other obligation in compliance with the provisions of the present Decision, shall be exempt from any damages or claims resulting from such actions.
- Violating the provisions of the present Decision shall result in the implementation of penal and administrative sanctions stipulated in Federal Decree Law No. (20) of 2018.
- Any person who, due to the nature of their work, has access to, or becomes aware of, any information provided or exchanged pursuant to the provisions of the present Decision, whether directly or indirectly, shall not disclose this information in any form, unless for the purposes of implementing the present Decision.
Article 24 - Administrative Measures
- Both the Council and the Office may, within the limits of their respective mandates, issue procedures and instructions concerning the implementation of the present Decision.
- Procedures, criteria and templates adopted by the UN Security Council and its Committees are considered the main reference for implementing the provisions of the present Decision and any other related procedures.
- Subject to relevant UNSCRs, the Council or the Office, as the case may be, may ask the Ministry of Justice to appoint whoever it deems appropriate to manage frozen Funds, if necessary.
- Both the Council and the Office may, within the limits of their respective mandates, issue procedures and instructions concerning the implementation of the present Decision.
Article 25 - Repeal of Conflicting Provisions
Cabinet Decision No. (20) of 2019 referred to above is hereby repealed as any provisions conflicting with the provisions of the present Decision are repealed.
Article 26 - Publication and Entering into Effect
The present Decision shall be published in the Official Gazette, and shall come into effect on the day following the date of its publication.
Registered Hawala Providers Regulation
Res 20/2/2019 Effective from 14/6/2012The Chairman of the Board of Directors of the Central Bank,
Having perused provisions Federal Law No. (7) of 2014 regarding Combating Terrorism Crimes;
Decretal Federal Law No. (20) of 2018 on Anti-Money Laundering and Countering the Financing of Terrorism and Illegal Organizations and its Executive Regulations;
The Central Bank Board of Directors’ Resolution No 20/2/2019 regarding approving the Registered Hawala Providers Regulation; and
National Anti-Money Laundering Committee’s decision in its meeting of 14 June 2012.
Has decided the following:
Objective:
The objective of this Regulation is to provide a regulatory framework for Hawala Providers in the UAE in order to operate within the UAE financial sector in a robust and prudent manner. As such, the framework set out in this Regulation is aimed at protecting the customers of Registered Hawala Providers and the reputation of the financial system of the UAE.
This Regulation is issued by the Central Bank pursuant to the powers vested in the Central Bank Law.
Where this Regulation includes a requirement to provide information or to take certain measures, or to address certain items listed at a minimum, the Central Bank may impose requirements, which are additional to the list provided in the relevant article.
Application:
This Regulation applies to any person carrying out Hawala activity in the UAE.
Article 1: Definitions
The following terms and phrases shall have the definitions assigned to them for the purpose of this Regulation:
Central Bank: The Central Bank of the United Arab Emirates;
Central Bank Law: Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities;
Hawala Activity: The arrangements for transfer and receipt of funds or equivalent value and settlement through trade and cash;
Hawala Provider Certificate: The certificate issued by the Central Bank for carrying on Hawala activity in the U.A.E;
Juridical Person: A juridical person in accordance with Article 92 of Federal Law No. 5 of 1985 Concerning the Issuance of the Civil Transactions Law as amended. For the purpose of this Regulation, this definition only refers to Juridical Persons in the UAE;
Registered Hawala Provider: Any natural person holding a valid residency visa or Juridical Person, who is registered in the Central Bank’s Hawala Providers Register in accordance with the provisions of this Regulation, including its agents or a network of agents;
Registered Hawala Provider’s Agent: Any natural or Juridical Person carrying out activity on behalf of a Registered Hawala Provider, whether by contract with or under the direction of the Registered Hawala Provider; and
Regulations: Any resolution, regulation, circular, rule, instruction, Standard or notice issued by the Central Bank.
The terms mentioned in the Central Bank Law shall bear the same meanings ascribed thereto in the said Law when used in this Regulation, unless a definition otherwise is stated herein.
Article 2: Registration and Certificate Requirements
2-1 A resident natural person or a juridical person may not carry on Hawala activity in the UAE unless he holds a Hawala Provider Certificate issued by the Central Bank in accordance with the provisions of this Regulation.
2-2 Any natural person or juridical person may apply for registration and obtain a Hawala Provider Certificate. The said application shall be made on the Central Bank’s prescribed form for this purpose and be accompanied by the following documents:
- A statement showing the nature and scope of the Hawala activity carried out by the applicant, in addition to any plans he may have for future business expansion, and details of the applicant’s arrangements for management of his business;
- The applicant’s name, address, age and occupation, along with a true copy of his UAE ID card and/or passport, for natural persons, and a true copy of the commercial license for juridical persons;
- An undertaking by the applicant:
- to guarantee all transfers for its customers;
- that the Central Bank bears no responsibility whatsoever towards customer funds regardless of their value;
- to maintain an account with a bank operating in the UAE to be used for settlement and provide the Central Bank with details of such account;
- to abide, alike with its agents, by all UAE established laws, including civil laws, commercial companies’ law, federal laws on AML/CFT, and Central Bank Regulations;
- to notify the competent authorities of the violation of said laws and Regulation;
- to make his records and documents available for examination by the Central Bank's staff or any third party authorized to act on its behalf;
- to provide any information or documents the Central Bank may require for the purposes of deciding on the application for registration;
- to amend the license provided by the relevant economic department to reflect Hawala activity; and
- to install all security systems (alarm system/CCTV), in accordance with the relevant authority requirements and use authorized cash transit Service providers for bulk currency transfers.
- to guarantee all transfers for its customers;
3-2 A Hawala Provider Certificate shall only be granted if the following conditions are met:
- The applicant undertakes to provide the Central Bank, electronically via the Central Bank’s Remittance Reporting System and/or other applicable Central Bank system, with the data and information on remitters and beneficiaries required as per the forms prepared by the Central Bank for this purpose;
- The applicant is not of UAE nationality and is legally competent and officially residing in the UAF.;
- The applicant is of good conduct and behavior and has not been convicted of any crime of honor or honesty and has not failed to honor his liabilities towards financial institutions or any other creditors. Furthermore, the applicant should not have been declared bankrupt nor reached a settlement agreement with his creditors or have his property confiscated or put under court receivership;
- The applicant has a reasonable level of education, administrative, and professional experience.
- A statement showing the nature and scope of the Hawala activity carried out by the applicant, in addition to any plans he may have for future business expansion, and details of the applicant’s arrangements for management of his business;
Article 3: Notification of Approval/Rejection and Certificate Conditions
3-1 The Central Bank may agree or decline to issue a Hawala Provider Certificate.
3-2 In case of approval or rejection of the application for a Hawala Provider Certificate, the Central Bank shall notify the applicant in writing indicating reasons in case of rejection.
3-3 The Central Bank shall issue a Hawala Provider Certificate valid for one year, renewable for similar periods. The Central Bank may include in the Hawala Provider Certificate whatever terms and conditions it deems appropriate.
Article 4: On-Going Obligations of Registered Hawala Providers
4-1 A Registered Hawala Provider should strictly abide by the following:
- Its commercial name should not include any financial activity term, such as bank, exchange house or any other licensed activity by the Central Bank (for juridical persons);
- Manage his business personally and never assign such task to another person;
- Not to change his address, place of residence/business, sponsor or commercial activity without obtaining the Central Bank’s approval;
- Carry out his activity in suitable premises that enables the Central Bank's staff to visit and examine his records;
- Upload electronically to the Central Bank the details of all transfers, remitters and beneficiaries in the Central Bank's prescribed systems on a daily basis;
- Receive all applications for money value transfers as per official vouchers for each transaction. Such vouchers should be appropriately stored;
- Verify identities of remitters and beneficiaries using Emirates ID or passports;
- Deposit funds received from its customers in the account designated for settlement;
- Submit to the Central Bank statements of his settlement account on a quarterly basis along with other required forms;
- Provide the Central Bank with any data, information or statistics it may require at any time and for any specific period. Such data and information shall be regarded as confidential and shall be treated accordingly. A Registered Hawala Provider may not disclose such information except in accordance with the law;
- A Registered Hawala Provider must exercise due diligence when approving an agent and provide the Central Bank a current list of its agents and the countries in which they operate;
- Submit to the Central Bank an application for renewal of the Hawala Provider Certificate within a period not less than two months from the date of expiry of the original certificate or any renewals thereof; and
- Abide, alike with its customers and agents, by all UAE laws, including civil laws, Commercial Companies’ Law, federal laws on AML/CFT, and Central Bank Regulations particularly with regard to notifying the competent authorities of any violation thereof.
- Its commercial name should not include any financial activity term, such as bank, exchange house or any other licensed activity by the Central Bank (for juridical persons);
Article 5: Specific Obligations with Regard to ML/FT Risks
5-1 In addition, a Hawala Provider registered in the Central Bank's Hawala Providers Register must strictly comply with Decretal Federal Law No. (20) of 2018 on Anti-money Laundering and Countering the Financing of Terrorism and Illegal Organizations and its executive regulations, and any Regulations and directions issued by the Central Bank in this regard.
5-2 Hawala Providers may be guided by the Financial Action Task Force (FATF) Standards on anti-money laundering and countering the financing of terrorism and proliferation and to abide by guidance issued by the Central Bank in this regard.
Article 6: Supervision and Examination
6-1 The Central Bank shall have the right to examine the business of the Hawala Providers and their agents and customers whenever it deems appropriate to ensure proper implementation of the provisions of this Regulation.
Article 7: Enforcement and Sanctions
7-1 Violation of any provision of this Regulation may be subject to supervisory action as deemed appropriate by the Central Bank. In addition, without prejudice to other sanctions stated in any other laws in the UAE, the Central Bank may impose administrative and financial sanctions and penalties in accordance with the Central Bank Law and the Regulations issued in implementation thereof.
Article 8: Interpretation of the Provisions of the Regulation
8-1 The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
Article 9: Cancellation of Previous Resolutions
9-1 The Central Bank Board of Directors’ Resolution No 109/5/2002 regarding the preparation of a simple regulation for licensing and monitoring of Hawala intermediaries is cancelled.
9-2 This Regulation replaces “Hawala Intermediaries Regulation” issued on 2 July 2012.
Article 10: Publication and Application
10-1 This Regulation shall be published in the Official Gazette in both Arabic and English and shall come into effect one month from the date of publication
Market Conduct & Consumer Protection
Consumer Protection Regulation
C 8/2020 Effective from 25/12/2020Introduction
One of the Central Bank’s objectives, as mandated by the Decretal Federal Law No. 14 of 2018 Regarding the Central Bank & Organization of Licensed Financial Institutions and Activities, is to establish Regulations and Standards for protection of Consumers of Licensed Financial Institutions. This Regulation and the accompanying Standards are issued pursuant to the powers vested to the Central Bank according to Article (121) of the aforementioned Decretal Federal Law.
This Regulation is intended to ensure protection of Consumers’ interests in their use of any financial product and/or service or relationship with Licensed Financial Institutions. This Regulation is principles based and provides a broad scope of conduct expected from Licensed Financial Institutions. The Regulation will be supported by Standards whereby the Central Bank will define regulatory requirements to ensure consistent interpretation and implementation of this Regulation.
By introducing this Regulation & the accompanying Standards, the Central Bank will ensure that the Licensed Financial Institutions’ approach to Consumer Protection is in line with international standards. This Regulation and the accompanying Standards establish the overarching Regulatory framework for Licensed Financial Institutions in relation to Consumer protection in and of Licensed Financial Institutions in the State. These Regulations & the accompanying Standards must be interpreted in conjunction with other regulations, including but not limited Shari’ah compliance regulations.
Objectives:
The primary objectives of the Regulation is to protect Consumers and contribute to the overall stability of the Financial Services industry. The Regulation and supporting Standards promote a culture within Licensed Financial Institutions of respecting and acting in the best interest of Consumers and specifically aim to protect Consumers by defining the Institutional obligations for the protection of Consumers that include:
- Setting standards of Business and Market conduct by Licensed Financial Institutions.
- Strengthening the governance and oversight over the design, promotion and sale of Financial Products and/or Services;
- Promoting responsible financing practices to protect consumers from becoming over indebted;
- Ensuring the quality and timing of effective disclosure to consumers by Licensed Financial Institutions regarding matters and/or risks that may affect a Consumer’s decision to purchase a Financial Product and/or Service;
- Providing Consumers with the access to the right information at the right time to provide the Consumer the opportunity to make informed decisions;
- Addressing unreasonable barriers and limits to fair competition and Consumer choice;
- Implementing clear and reasonable mechanisms by Licensed Financial Institutions for redress of Consumer Complaints;
- Improving Consumers’ knowledge, awareness and ability to assess Financial Products and/or Services; and
- Promoting inclusions for all segments of society by eliminating unreasonable barriers or practices that limit access to Financial Products and/or Services.
- Setting standards of Business and Market conduct by Licensed Financial Institutions.
Scope of Application
This Regulation and accompanying Standards apply to all Licensed Financial Institutions licensed by the Central Bank in relation to their activities specified in Article 65 of the Decretal Law No. 14 of 2018 Regarding the Central Bank & Organization of Licensed Financial Institutions and Activities in provision of Financial Products and/or Services to Consumers that are Natural Persons and Sole Proprietorships.
This Regulation and the accompanying Standards are in addition to any requirement of any other regulatory authority as applicable to Licensed Financial Institutions. In case of any conflict with such requirement, the provisions of this Regulation and accompanying Standards will prevail.
Where this Regulation or its accompanying Standards include requirements to provide information or take certain measures or to address certain items listed as a minimum, the Central Bank may impose requirements that are additional to the listing provided in the relevant Articles.
The Central Bank’s Financial Consumer Protection Department may issue further guidance relating to the Regulation and Standards.
Article 1: Definitions
For the purposes of this Regulation, words and expressions shall have the usual meaning assigned to, unless the context requires otherwise, as mentioned below and/or defined in other Laws and Regulations:
- Advertising: The activity of marketing, designing, producing and/or packaging information about a Licensed Financial Institution and its Financial Products and/or Services for the purpose of public display, including financial promotion to recruit new Consumers and/or induce existing Consumers to try Financial Products and/or Services.
Advice: Specific Advice:
Specific Advice on Financial Products or Services includes any method of communication that:
- provides an opinion, evaluation, recommendation, and / or biased information / comparisons to a Consumer or when acting as a Consumer’s agent; and
- the Advice or actions could reasonably be regarded as having the intent to influence a Consumer’s choice or decision to select, buy, sell, hold, subscribe to a particular financial product/service, related options or an interest in a particular financial product/service.
Generic Advice:
Giving Generic Advice in any newspaper, journal, magazine, broadcast service, education initiatives or similar service in any medium if the principal purpose of the publication or service, taken as a whole, is neither:
- that of giving advice of the kind specified in the Specific Advice definition; nor
- that of leading or enabling Consumers to buy, sell, subscribe for a particular financial product/service of the kind in Specific Advice.
- provides an opinion, evaluation, recommendation, and / or biased information / comparisons to a Consumer or when acting as a Consumer’s agent; and
Annual Interest/Profit Rate: The annual amount to be paid by a Borrower / Financee as expressed as a percentage of the total amount of the credit facility.
The annual amount earned by a Consumer and expressed as a percentage of the total amount of a deposit, investment and other financial product.
- Annual Percentage Rate (APR): The percentage of the total amount that a Borrower owes to a Lender including cost of other Fees charged by the Lender annually for the Borrower to use the Lender's funds or asset, or charged by a Financier to a Financee as part of price/rental, due to the Financee’s purchase or renting of asset from the Financier.
- Applicable Laws: Applicable UAE Laws and amendments thereof.
- Arrears: The state of being behind in the discharge of obligations, an unfinished duty and or an unpaid and overdue debt in accordance with the loan/financing contract, by the scheduled due date.
- Authorized Agents: Authorized Agent is a commercial representation by a contract pursuant to which the authorized agent undertakes to enter into transaction in the name and for the account of the Licensed Financial Institution and the Licensed Financial Institution shall be liable for any transactions and contracts entered into by the authorized agent within the limits of the authority conferred to the authorized agent by the Licensed Financial Institution.
- Base Lending Rate: Interest rate that is set as a benchmark against which Credit Facilities are to be priced and re-priced.
- Board: A Licensed Financial Institution’s Board of Directors (Owner/Partners in the absence of a Board of Directors).
- Borrower / Financee: A Consumer to which a Licensed Financial Institution provides Credit as a Service and/or Product.
- Call-back: A follow-up call to a Consumer that a Licensed Financial Institution conducts to assess whether a Consumer has received and understood the disclosures of a Product and/or Service provided by the Licensed Financial Institution.
- Central Bank: The Central Bank of the United Arab Emirates.
- Complaint: An expression of dissatisfaction by a Consumer with a product, service, policy procedure or actions by the Licensed Financial Institution that is presented to an Employee of the Licensed Financial Institution in writing or verbally.
- Commitment to Donate: The practices related to the customer’s commitment to donate to a third party due to late payment of a due amount in a financing arrangement.
- Compliance of an IFI with Islamic Shari’ah: Compliance of an IFI with Islamic Shari’ah refers to compliance with Shari’ah in accordance with:
- resolutions, fatawa, regulations, and standards issued by the Higher Shari’ah Authority (HSA) in relation to licensed activities and businesses of IFIs (“HSA’s Resolutions”); and
- resolutions and fatawa issued by ISSC of respective IFI, in relation to licensed activities and businesses of such institution (“the Committee’s Resolutions”), provided they do not contradict HSA’s Resolutions.
- resolutions, fatawa, regulations, and standards issued by the Higher Shari’ah Authority (HSA) in relation to licensed activities and businesses of IFIs (“HSA’s Resolutions”); and
- Conflict of Interest: A Conflict of Interest occurs when the interests of a client are at odds with the interests of the firm, an employee or another client.
- Consumer: A Consumer is a customer for the purpose of this Regulation and the accompanying Standards. A Customer is any Natural Person or Sole Proprietor who obtains or may prospectively obtain Financial Services and/or Products – with or without charge – to satisfy his/her personal need or others’ needs.
- Cooling-off Period: A period of time after agreeing to the Product and/or Service that allows a Consumer to reconsider the purchase and to withdraw from the Contract without suffering any undue costs, obligations or inconvenience. The Cooling-off Period begins immediately after signing of the contract.
For Shari’ah compliant products and services, relevant Shari’ah standards for reconsideration by the Consumer may apply.
- Credit Information Agency: Al Etihad Credit Bureau and any credit information agency established for the purpose of credit reporting requirements.
- Credit Products: Products that provide funding including any advance, loan/financing or other facility in whatever form, including the giving of a guarantee or undertaking of any surety obligations for a Consumer.
- Data/Personal Data: A collection of organized information, facts, concepts, instructions, observations or measurements, in the form of numbers, alphabets, symbols, images or any other form, that are collected, produced, or processed by Licensed Financial Institutions.
Personal Data is any information relating to an identified natural person or identifiable natural person. "Identifiable natural person" is defined as a natural person who can be identified, directly or indirectly, in particular by reference to an identification number or to one or more factors specific to their biological, physical, biometric, physiological, mental, economic, cultural or social identity.
- Decretal Law: Decretal Federal Law No. (14) Of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities.
- Deposit Products: Deposit Products include savings accounts, current accounts, digital accounts, term deposits, cheques, banking and payment wallets and related stored value cards.
- Digital Channels: Internet, mobile phones, Automated Teller Machine (ATMs), Point of Sale (POS) terminals, mobile applications, or other similar digital channels.
- Disposable Income: A person’s Income after taking into account basic personal expenses, net interest/profit and dividends received and the payment of taxes and social contributions.
- Early Settlement Fee: A Fee charged by a Lender/Financier to a Borrower / Financee who terminates a Credit Facility by paying the outstanding amount before a date specified in the contract.
- Error: An outcome of an action that is contrary to an agreement, understanding or documented policy or operational and control procedures, which has a financial or other effect on one or more Consumers.
- Fee: Any fees, charges, penalties and commissions incurred on a Product and/or Service.
- Financial Crime Compliance: Financial Crime Compliance is the requirement to comply with, including and not limited to, all applicable fraud, anti-money laundering, counter-terrorism financing, sanctions, bribery and corruption laws, rules and regulations.
For the sake of clarity, this Regulation / accompanying Standards do not impose, reduce or modify any requirements pertaining to the compliance with all laws, rules and regulations relating to Financial Crime Compliance.
- Financial Products and/or Services: Products and/or Services (including stored value facilities) provided by Licensed Financial Institutions, with or without charge, through their Financial Activities. It will be referenced to as Products and/or Services in this Regulation.
- Higher Shari’ah Authority (HSA): An authority that determines rules, standards, and general principles applicable to Shari’ah compliant businesses and Licensed Financial Activities, and supervises and oversees the Internal Shari’ah Supervision Committees in accordance with the Decretal Federal Law No. (14) of 2018, Regarding the Central Bank & Organization of Financial Institutions and Activities.
- Financial Complaint Resolution Mechanism: A Complaint resolution system provided by Licensed Financial Institutions for the purpose of resolving Consumer Complaints.
- Internal Shari’ah Supervision Committees (ISSC): A body appointed by an IFI, comprised of scholars specialized in Islamic financial transactions, which independently supervises transactions, activities, and products of the IFI and ensures they are compliant with Islamic Shari’ah in all its objectives, activities, operations, and code of conduct.
- Islamic Financial Institution (IFI): The Licensed Financial Institutions that conduct all or part of their activities and businesses in accordance with the provisions of Islamic Shari’ah.
- Key Facts Statement: A concise and user-friendly summary, in plain language, of the key features and risks of a Product and/or Services for a Consumer.
- Lender/Financier: A Licensed Financial Institution that provides Credit as a Service and/or Product to its Consumers in any manner or method.
- Licensed Financial Activities: The financial activities subject to Central Bank licensing and supervision as specified in Article (65) of the Decretal Federal Law No. (14) of 2018.
- Licensed Financial Institutions: Banks and other financial institutions licensed in accordance with the provisions of the Decretal Federal Law No. (14) of 2018, to carry on a Licensed Financial Activity or more, including those which carry on the whole or a part of their business in compliance with the provisions of Islamic Shari’ah, and are either incorporated inside the State or in other jurisdictions, or have branches, subsidiaries or Representative Offices inside the State.
- Market: The financial Market where Licensed Financial Institutions promote and/or sell Financial Products and/or Services and compete for Consumers.
- Market Conduct: Market Conduct is the focus on Licensed Financial Institutions' Market place actions, behavior and practices that are applied in providing Financial Products and/or Services to the market.
- Minority Group: A category of people who experience relative disadvantage as compared to members of a dominant social group, Minority Group membership is typically based on differences in observable characteristics or practices, such as ethnicity, race, religion or determination.
- Mumatil: With respect to Shari’ah transactions, it is a debtor who refuses to pay a debt that is due, without any legitimate reason after receiving demand for payment.
- Outsourcing: An agreement with another party either within or outside the UAE, including a party related to the Licensed Financial Institution, to perform on a continuing basis an activity which currently is or could be undertaken by the Licensed Financial Institution itself.
- Partial Settlement Charge: A fee levied by the Licensed Financial Institution on the Consumer in the event that the amount of the loan/financing is repaid in part before a date or event.
- People of Determination: A person suffering from a temporary or permanent, full or partial deficiency or infirmity in his physical, sensory, mental, communicational, educational or psychological abilities to an extent that limits his possibility of performing the ordinary requirements.
- Permissible: Any action that is specifically permitted by regulation or standards, or any actions which the Consumer is allowed by laws, rules and regulations to agree to and is confirmed by expressed consent.
- Person: A natural or juridical Person, as the case may be.
- Reducing Balance Method: An interest/profit amount calculation method where the interest/profit to be paid by the Borrower / Financee is based on the outstanding loan/credit amount after periodic repayments/payments.
- Regulation: The term includes any resolution, legislation, circular, rule, instruction, standard or notice issued by the Central Bank.
- Regulatory Supervision: Supervision of Licensed Financial Institution by the Central Bank.
- Retail Operations: A Licensed Financial Institution’s operational practice in the design, production, promotion, sales and distribution of its Financial Products and/or Services to Consumers.
- Senior Management: The executive management of the Licensed Financial Institution responsible and accountable to the Board (or Owner/Partners where there is no Board of Directors) for the sound and prudent day-to-day management of the Licensed Financial Institution, generally including, but not limited to, the chief executive officer, chief financial officer, chief risk officer and heads of the compliance and internal audit functions.
- Sole Proprietorships: A legal entity for the undertaking of commercial or professional activities owned and operated by a natural person, who is in complete control of the business operations and profits and bears personal unlimited liability. For clarity, a Sole Proprietorship is not a limited liability company, LLC.
- Staff: One or more employee(s) of the Licensed Financial Institution or third parties acting in any capacity for or on behalf of the Licensed Financial Institution.
- State: The United Arab Emirates.
- Stored Value Facility (SVF): A facility (other than cash) for or in relation to which a Customer, or another person on the Customer’s behalf, pays a sum of money (including Money’s Worth such as values, reward points, Crypto-Assets or Virtual Assets) to the issuer, whether directly or indirectly, in exchange for:
- the storage of the value of that money (including Money’s Worth such as values, reward points, Crypto-Assets or Virtual Assets), whether in whole or in part, on the facility; and
- the “Relevant Undertaking”. SVF includes Device-based Stored Value Facility and Non-device based Stored Value Facility.
- the storage of the value of that money (including Money’s Worth such as values, reward points, Crypto-Assets or Virtual Assets), whether in whole or in part, on the facility; and
- Suspicious Transactions: Any transaction, attempted transaction, or funds which a Licensed Financial Institution has reasonable grounds to suspect as constituting in whole or in part, and regardless of the amount or the timing any of the following:
- The proceeds of crime (whether designated as a misdemeanor or felony, and whether committed within the State or in another country in which it is also a crime);
- Being related to the crimes of money laundering, the financing of terrorism, or the financing of illegal organizations;
- Being intended to be used in an activity related to such crimes.
- The proceeds of crime (whether designated as a misdemeanor or felony, and whether committed within the State or in another country in which it is also a crime);
- Systemic Error: Error that affects a group in a similar manner and to a similar magnitude.
- Third Party: Any person, group of persons or organization external to, and not a related party to, a Licensed Financial Institution.
- UAEPNG System: The Persona Non Grata System established by the Central Bank.
- Unauthorized Transaction: Unauthorized transaction includes the execution of payment instruction without explicit authentication or authorization from the consumer and incorrectly executed payment transactions.
- Undue Pressure: Any practice, communication or action that could be reasonably considered excessive or persistent in the circumstances.
- Writing: For any requirement of communications and signatories, declarations, consents, agreements or other instruments/requirements in writing, for the sake of clarity, these terms applies to electronic, digital and paper based insofar an Electronic Document or Record satisfies the requirement of the provision of Federal Law No. (1) of 2006 are complied with.
- Year: The Gregorian calendar year.
- Advertising: The activity of marketing, designing, producing and/or packaging information about a Licensed Financial Institution and its Financial Products and/or Services for the purpose of public display, including financial promotion to recruit new Consumers and/or induce existing Consumers to try Financial Products and/or Services.
Article 2: Disclosure and Transparency
2.1 Disclosure
2.1.1 Introduction
Quality, accuracy, completeness and effectiveness of the information provided to Consumers are fundamental to an open, transparent and competitive Market. Consumers must be proactively provided with all the information necessary to make an informed decision regarding Financial Products and/or Services.
2.1.2 Description
- 2.1.2.1 A Licensed Financial Institution’s Board and Senior Management are responsible for providing direction and oversight to ensure that good disclosure practices for Financial Products and/or Services are adopted throughout the institution.
- 2.1.2.2 Information must be provided in a proactive and transparent manner to allow a Consumer sufficient time to understand the information, including the terms and conditions.
- 2.1.2.3 Licensed Financial Institutions must use specific disclosure mechanisms, including warnings, to inform Consumers of the key characteristics of and limitations on the product and/or service including associated risks, costs, fees, interest/profit rates, tenor, locked terms, or other pertinent issues relating to the product and/or service.
- 2.1.2.4 Licensed Financial Institutions must provide effective disclosure at all stages of the relationship with the Consumer. Consumers must be made aware in advance of any permissible change in terms and conditions through all stages of the relationship.
- 2.1.2.5 Licensed Financial Institutions must not provide only partial or biased disclosure to entice a Consumer by limiting the initial disclosure material that only presents the positive aspects of the product and/or service and only then disclosing the full characteristics of the product at the point of sale or post-sale, a point at which the Consumer may feel obligated to complete the transaction(s) or do not have a recourse to exit the Product and/or Service post-sale.
- 2.1.2.6 Licensed Financial Institutions must continuously monitor and improve the effectiveness of its disclosures with techniques including and not limited to Complaint analysis and Consumer satisfaction surveys.
- 2.1.2.7 The information must be disclosed in plain language that is accessible and communicated in terms that are easily understandable.
- 2.1.2.8 Information must be available in both official languages English & Arabic.
- 2.1.2.9 The method or manner of disclosure must be adjusted to meet the capabilities and level of understanding of the Consumer.
- 2.1.2.10 Licensed Financial Institutions must ensure the accuracy of all disclosures made including the verification and correctness of statement and any related calculation, assumption or reference.
2.2 Transparency
2.2.1 Introduction
Transparency is positive conduct, which complements Disclosure. Transparency goes beyond the simple act of disclosure regarding a product and/or service provided to a Consumer. It means that Licensed Financial Institutions must proactively provide useful information and advice in the Market.
2.2.2 Description
- 2.2.2.1 Licensed Financial Institutions must provide practical and suitable options to help Consumers make informed decisions that are in Consumers’ best interest including assessment of affordability and suitability.
- 2.2.2.2 Licensed Financial Institutions must promote, sell, distribute and manage Financial Products and/or Services in a responsible manner. Licensed Financial Institutions must not knowingly benefit from Consumers’ ignorance or apathy as to, including and not limited to, possible choices, the impact of risks, affordability, suitability, Conflict of Interest with the Staff.
- 2.2.2.3 Licensed Financial Institutions must take necessary steps to ensure that Consumers are made aware of and understand the proposed terms & conditions prior to the final stage of the sales process or the time of signing of the agreement.
- 2.2.2.4 Licensed Financial Institutions must be transparent in their pricing and product structure.
2.3 Responsible Advertising and Marketing
2.3.1 Introduction
Advertising and marketing can utilize multiple channels to access the public for the promotion of a Licensed Financial Institution and its Products and/or Services. Advertising issued by Licensed Financial Institutions must not be deceptive, misleading, fraudulent or unfair and must be easily understandable by a Consumer. All text and numbers must be clearly visible and understandable.
2.3.2 Description
- 2.3.2.1 Advertising and marketing activities and promotional materials must be designed, delivered and clearly identified as a financial promotion.
- 2.3.2.2 Licensed Financial Institutions must not make any representation, omission, or engage in any Advertising and marketing activity that is likely to be deceptive, misleading, fraudulent or unfair.
- 2.3.2.3 Licensed Financial Institutions must not exaggerate the advantages of a product and/or service or present the information in a confusing manner. This includes general impressions conveyed through words, pictures, digital images, audio and/or video, and the use of disclaimers not clearly and prominently disclosed and displayed.
- 2.3.2.4 All Advertising and marketing material must be in plain and understandable language.
- 2.3.2.5 The Regulation and accompanying Standards apply to any Advertising and marketing activity through all channels, including and not limited to branches, television, radio, website, mobile applications, automated teller machines (ATMs), telephone banking, account statements, social media and public media comprised of any form of audio, visual and print content.
- 2.1.2.1 A Licensed Financial Institution’s Board and Senior Management are responsible for providing direction and oversight to ensure that good disclosure practices for Financial Products and/or Services are adopted throughout the institution.
Article 3: Institutional Oversight
3.1 Institutional Oversight
3.1.1 Introduction
The Central Bank expects Licensed Financial Institutions to be effectively managed by establishing an appropriate organizational structure, a supportive and constructive corporate culture; engaging well-qualified staff, defining clear policies and procedures, creating proper monitoring and controls supported by proper overall governance. The principle is to promote positive institutional conduct in serving all Consumers fairly.
3.1.2 Description
- 3.1.2.1 The Central Bank requires Licensed Financial Institutions to have robust management oversight and responsibility structures in place for their activities including design, development, promotion, sales and distribution of products and/or services; compliance, risk and audit controls; up to date policies, procedures and training; engagement of qualified staff.
- 3.1.2.2 Licensed Financial Institutions’ Board and Senior Management are required to instil a Consumer- focused corporate culture that will treat the Consumer fairly. The Licensed Financial Institution must actively monitor, identify, respond and address misconduct and potential Market Conduct risks.
3.2 Governance of Retail Operations
3.2.1 Introduction
Licensed Financial Institutions’ governance and management oversight structures must establish and maintain the level of integrity in the Market that both Consumers and the Central Bank expect. Governance of retail operations must be appropriate, properly implemented and maintained to ensure Consumer needs, suitability and affordability are properly assessed. Consumers are to be provided the right products and/or services to meet their needs and their ability to accept risk.
Licensed Financial Institutions must ensure Consumer financial assets, information and all Data are secure and protected.3.2.2 Description
- 3.2.2.1 Licensed Financial Institutions must have strong governance and effective management oversight in place over the design, development, promotion, sales and distribution, and the ongoing review and changes of Financial Products and/or Services.
- 3.2.2.2 Licensed Financial Institutions offering or promoting Shari’ah compliant products and/or services must ensure compliance with Shari’ah governance which is set out in more detail by separate Regulation issued by the Central Bank.
- 3.2.2.3 Licensed Financial Institutions must have effective controls, strong security and monitoring of transactions and activities of staff.
- 3.2.2.4 All Licensed Financial Institutions must maintain up to date policies and procedures, systems and controls that fully comply with the requirements specified within this Regulation and its accompanying Standards.
- 3.2.2.5 Licensed Financial Institutions must have and be able to demonstrate a corporate culture of Consumer service, fairness, transparency, ethical business conduct and effective disclosure.
- 3.2.2.6 Licensed Financial Institutions must promote compliance with this Regulation and accompanying Standard in retail activities through policies, procedures, training, systems and controls including and not limited to Complaint handling and Complaint resolution, Consumer education, compensation and practices in sales and advisory services.
- 3.2.2.7 Licensed Financial Institutions must ensure that all Authorized Agents comply with the applicable Articles of this Regulation and the accompanying Standards.
- 3.1.2.1 The Central Bank requires Licensed Financial Institutions to have robust management oversight and responsibility structures in place for their activities including design, development, promotion, sales and distribution of products and/or services; compliance, risk and audit controls; up to date policies, procedures and training; engagement of qualified staff.
Article 4: Market Conduct
4.1 Responsible Market Conduct
4.1.1 Introduction
Licensed Financial Institutions must uphold the integrity of the financial Market through responsible Market activities which contributes to the overall stability of and confidence in the financial system.
Licensed Financial Institutions must sell and provide Consumers with appropriate products and/or services in accordance with the principles of this Regulation.
4.1.2 Description
- 4.1.2.1 Licensed Financial Institutions must monitor and uphold high ethical practices in the Market.
- 4.1.2.2 Licensed Financial Institutions must prohibit and prevent abusive sales, marketing and pricing practices.
- 4.1.2.3 Licensed Financial Institutions must promote disclosure, transparency and a fair and competitive Market without discrimination.
- 4.1.2.4 Licensed Financial Institutions must not create unreasonable barriers that unfairly limits access to Financial Products and/or Services by Consumers.
- 4.1.2.5 Independent control functions within Licensed Financial Institutions must be competent in the application of Market Conduct principles set out in this Regulation and accompanying Standards set out by the Central Bank.
4.2 Promoting Competition
4.2.1 Introduction
The Regulation aims to promote a competitive Market by improving the freedom of choice through transparency, eliminating unreasonable and unfair barriers to competition, and requiring access to comparative information on product and/or services. The consistent application by Licensed Financial Institutions of Market Conduct principles will ensure ethical practices in Advertising and selling appropriate products and/or services and Consumer treatment throughout the lifecycle of engagement with the Licensed Financial Institution.
4.2.2 Description
- 4.2.2.1 Licensed Financial Institutions must provide Consumers with accurate, sufficient and consistent information to easily understand and to be able to compare products and/or services offered by other Licensed Financial Institutions.
- 4.2.2.2 Licensed Financial Institutions must not impose practices or barriers that prevent Consumers from easily switching their relationship(s) between Licensed Financial Institutions at reasonable and disclosed costs.
- 4.2.2.3 Licensed Financial Institutions must not collude to fix features, pricing or terms to the detriment of Consumers and the Market.
- 4.2.2.4 Licensed Financial Institutions must not use misleading or incomplete information to promote an advantage of their Financial Products and/or Services over other competitors.
- 4.1.2.1 Licensed Financial Institutions must monitor and uphold high ethical practices in the Market.
Article 5: Business Conduct
5.1 Responsible Business Conduct
5.1.1 Introduction
Responsible business conduct is based on the internal culture and behaviour of Licensed Financial Institutions. Appropriate Business conduct instils a culture of integrity and ethics in its services and activities including product design, development, promotion, sales, distribution, lending / providing finance practices; minimizing Conflict of Interest and Consumer risks; and from a broader perspective, improving the financial wellbeing of its Consumers.
5.1.2 Description
- 5.1.2.1 Licensed Financial Institutions must act, with due skill, care and diligence, fairly, honestly and professionally in their relationship with Consumers.
- 5.1.2.2 Licensed Financial Institutions must establish and maintain effective policies, procedures, systems and controls to avoid any potential, perceived or actual Conflict of Interest.
- 5.1.2.3 For inherent conflicts of Interest, Licensed Financial Institutions must have controls in place and must provide full and proper disclosure to Consumers prior to any agreements or commitments.
- 5.1.2.4 Licensed Financial Institutions must ensure ethical behaviour of staff towards Consumers by developing an internal code of conduct for the staff, providing regular training, and monitoring Complaints.
- 5.1.2.5 Licensed Financial Institutions must ensure that the staff who directly interact with Consumers will:
- Competently, efficiently and professionally discharge their duties and provide prospective and existing Consumers with the information and services they are entrusted to provide or sell.
- Have sufficient knowledge of products and/or services required to help and educate Consumers.
- Have the professional qualifications at all times necessary to provide Advice and carry out transactions.
- Competently, efficiently and professionally discharge their duties and provide prospective and existing Consumers with the information and services they are entrusted to provide or sell.
- 5.1.2.6 Licensed Financial Institutions must adopt remuneration and staff appraisal policies with the aim of preventing mis-selling, unreasonable risk-taking, Conflict of Interest or other irresponsible conduct. Such policies must not incentivize unethical practices and must reward positive conduct.
- 5.1.2.7 Licensed Financial Institutions are responsible for the actions of their staff. Licensed Financial Institutions’ must maintain appropriate monitoring of staff in relation to its standards of business conduct and ensure full compliance with codes of conduct, laws and regulations.
- 5.1.2.8 Licensed Financial Institutions must not adopt abusive or unreasonable contractual terms.
- 5.1.2.9 Licensed Financial Institutions must monitor for misleading or aggressive sales practices and exploitation of Consumers due to their vulnerabilities, apathy or lack of knowledge.
- 5.1.2.10 Licensed Financial Institutions must monitor and identify Borrowers / Financees facing difficulties in servicing their debt and, upon the Borrower’s / Financee’s request, designate a Credit counsellor to assist the Borrower / Financee in managing their indebtedness. Licensed Financial Institutions must inform Borrowers / Financees who are delinquent as to the availability of qualified Credit counsellors.
5.2 Fair Treatment of Consumers
5.2.1 Introduction
This Regulation aims to address the gap between the level of the public’s financial literacy and the complexity and risks of the Financial Products and/or Services being offered.
5.2.2 Description
- 5.2.2.1 All Consumers must be treated equitably, honestly and fairly at all stages of their relationship with Licensed Financial Institutions. Treating Consumers fairly must be an integral part of the good governance, business conduct and corporate culture of all Licensed Financial Institutions.
- 5.2.2.2 Licensed Financial Institutions must provide clear and understandable information to Consumers to ensure they are explained their rights and responsibilities with respect to the products and/or services, including the right to have their problems or Complaints addressed in an efficient, effective and respectful manner.
- 5.2.2.3 Licensed Financial Institutions must not restrict Consumer’s choices, such as tied selling and bundling of products and/or services.
- 5.2.2.4 Licensed Financial Institutions must not benefit from their Errors. Errors must be rectified without undue delay upon identification. Consumers affected by an Error must be immediately informed in writing of the cause, impact and rectification of Errors.
- 5.2.2.5 Licensed Financial Institutions must establish clear standards and procedures that prohibit undue and coercive pressure on Consumers in collection of repayments/payments or debts due.
- 5.1.2.1 Licensed Financial Institutions must act, with due skill, care and diligence, fairly, honestly and professionally in their relationship with Consumers.
Article 6: Protection of Consumer Data and Assets
6.1 Consumer Data Protection
6.1.1 Introduction
Licensed Financial Institutions are required by the Article 120 of the Decretal Federal Law No. (14) 2018 to protect Consumers’ Data and ensure their confidentiality. This Regulation further requires that Licensed Financial Institutions collect the minimal amount of Consumer Data and information needed in respect of their licensed activities and remain in compliance with all other related laws.
6.1.2 Description
- 6.1.2.1 Licensed Financial Institutions must establish a function in their organization that is responsible for Data Management and Protection including responsibility for maintaining policies, procedures, systems and controls to protect Consumers’ Personal Data and information against misuse, unauthorized access and undue processing and analysis.
- 6.1.2.2 Licensed Financial Institutions must have policies that specify duration of record keeping and Data retention in accordance with the applicable laws, regulations and business.
- 6.1.2.3 Licensed Financial Institutions must have appropriate security and monitoring measures in place to detect and track unauthorized internal access or use of Consumer information. Any breach of access, misuse or unauthorized release must be recorded including any harm done by such breach for future reporting to and review by the Central Bank.
- 6.1.2.4 Licensed Financial Institutions must notify the Central Bank of all significant breaches of Consumer Data and information and notify any Personal Data breach to Consumers where a breach may pose a risk to the financial and personal security of the Consumer without undue delay. Licensed Financial Institutions are liable for reimbursing any direct costs incurred by the consumer for actual harm done as a result of the breach.
- 6.1.2.5 Licensed Financial Institutions must ensure that Consumers are able to make informed choices with respect to providing expressed consent as to their Data being collected, used and shared with third parties and within the Licensed Financial Institution.
- 6.1.2.6 Licensed Financial Institutions must prevent the misuse of Consumer information and Data.
6.2 Protection of Consumer Assets, Information and Data against Financial Crimes, Misappropriation and Misuse
6.2.1 Introduction
Financial Crimes, misappropriation and misuse of Consumer assets, Data and information significantly undermine Consumers’ trust and confidence in Financial Services. Licensed Financial Institutions must have sound and effective management and business practices for security within the first line of defence.
Licensed Financial Institutions must continually make appropriate efforts and investments to stay on top of these risks and make use of the latest technology and solutions to protect Consumer assets and Data.
6.2.2 Description
- 6.2.2.1 Without prejudice to other laws and regulations, Licensed Financial Institutions must treat Consumers’ information relationships and business affairs as private and confidential.
- 6.2.2.2 Licensed Financial Institutions must put in place strict internal controls to effectively protect Consumers’ deposits, savings, funds held by stored value facilities and other assets as well as Consumer information and Data, against internal frauds.
- 6.2.2.3 Licensed Financial Institutions must apply sufficient resources to be able to detect both external and internal frauds quickly and ensure they are fully addressed with future prevention measures.
- 6.2.2.4 Licensed Financial Institutions must compensate Consumers in a timely manner for financial losses and expenses resulting from Financial Crimes, misappropriation, cyber-attacks and misuse of assets and information unless it can be proven that the loss was due to the gross negligence or fraudulent behavior of the Consumers.
- 6.2.2.5 Licensed Financial Institutions must ensure their security and protection systems are updated and have the capacity to develop and adopt new approaches to cyber security as required.
- 6.2.2.6 Licensed Financial Institutions must demonstrate they have carried out sufficient Consumer awareness activities related to educating Consumers of the need to protect themselves from Financial Crime.
- 6.1.2.1 Licensed Financial Institutions must establish a function in their organization that is responsible for Data Management and Protection including responsibility for maintaining policies, procedures, systems and controls to protect Consumers’ Personal Data and information against misuse, unauthorized access and undue processing and analysis.
Article 7: Responsible Financing Practice
7.1 Responsible Financing
7.1.1 Introduction
Financing must be provided in a responsible manner to protect Consumers, prevent over-indebtedness and support economic stability. Licensed Financial Institutions must fully apply this Regulation to each and all parts of the Licensed Financial Institutions’ Credit granting process and ongoing management.
7.1.2 Description
- 7.1.2.1 Licensed Financial Institutions must ensure they have obtained credible and independent information regarding the financial situation of the Consumer requesting financing.
- 7.1.2.2 Licensed Financial Institutions must assess the related financial obligations, dependencies, capabilities and needs of their Consumers before agreeing to provide them with a financing product, Advice or service.
- 7.1.2.3 Licensed Financial Institutions must ensure at the time of granting of Credit, the Credit does not cause over-indebtedness and/or undue financial burden on the Consumer.
- 7.1.2.4 Licensed Financial Institutions must not charge unreasonable fees.
- 7.1.2.5 Licensed Financial Institutions must not provide excessive Credit beyond amounts of Credit that the Consumer requires and / or that is reasonable, affordable and suitable for the Consumer’s needs.
- 7.1.2.6 Licensed Financial Institutions must apply proper criteria in the method for carrying out due diligence and stress testing for the affordability and suitability of a Credit product for the Borrower / Financee. A copy of the testing results must be provided to the Consumer in writing for free.
- 7.1.2.7 Licensed Financial Institutions must not grant or extend any form of Credit without expressed and documented consent by the Consumer.
- 7.1.2.8 Licensed Financial Institutions must adopt a remuneration program for the staff that does not incentivize aggressive and inappropriate levels of Credit granting.
- 7.1.2.9 Licensed Financial Institutions must monitor for inappropriate activities by Credit granting and sales representatives. The monitoring, at minimum, includes monitoring of monthly trend analysis of Credit granted and relevant Consumer Complaints.
- 7.1.2.10 Licensed Financial Institutions must investigate and, where required, take corrective actions on anomalies and inappropriate activities in Credit granting. Such actions must be documented for review by Central Bank.
- 7.1.2.11 Licensed Financial Institutions must ensure that Consumer Credit information provided to external bodies, including the Credit Information Agency is accurate and filed in a timely manner. Where a Licensed Financial Institution is made aware of any Errors in the Consumer information, the Licensed Financial Institution must take corrective measures in a timely manner.
- 7.1.2.1 Licensed Financial Institutions must ensure they have obtained credible and independent information regarding the financial situation of the Consumer requesting financing.
Article 8: Complaint Management and Complaint Resolution
8.1 Complaint Management and Complaint Resolution
8.1.1 Introduction
Licensed Financial Institutions must be transparent with Consumers and operate in a fair, honest and competitive manner. Licensed Financial Institutions must have in place a fair, accessible and transparent process provided without charge for addressing Complaints with Consumers and that are resolved in a timely manner.
8.1.2 Description
- 8.1.2.1 A Licensed Financial Institution must establish an independent Complaint management function in the organisation that directly reports to the Senior Management. The function must be empowered to effectively resolve Complaints and independent of other business operations.
- 8.1.2.2 Licensed Financial Institutions must have an efficient and effective Complaint management system with supporting policies and procedures. The system must enable Consumers to make Complaints easily and free of cost.
- 8.1.2.3 Licensed Financial Institutions must ensure Consumers are aware of their rights and responsibilities when seeking to resolve their problems or Complaints.
- 8.1.2.4 Licensed Financial Institution is responsible for accepting and addressing all Complaints involving the activities of Authorized Agents as well as any product and/or service sold, marketed or advertised by the agent on behalf of the Licensed Financial Institution.
- 8.1.2.5 Licensed Financial Institutions must ensure compliance with all time frames prescribed by the Central Bank including turnaround time for acknowledgments and provided written responses to Complaints that must provide the Consumer an explanation in writing of any delay or any inability of having a resolution to the Complaint or Error.
- 8.1.2.6 Licensed Financial Institutions must ensure their Authorized Agents provide a credible and unbiased process for Complaint resolution in accordance with this Regulation and Standards and the Licensed Financial Institution’s policy and procedures.
- 8.1.2.7 Licensed Financial Institutions must train their staff and Authorized Agents in identification and handling of Complaints.
- 8.1.2.8 Consumers must be informed of the Licensed Financial Institution’s process for the management of Complaints as well as recourse to a Complaint resolution mechanism to ensure fairness, transparency and neutrality in resolving Complaints.
- 8.1.2.9 The Central Bank will supervise the effectiveness and efficiency of the financial Complaint resolution mechanism.
8.2 Complaint and Inquiries Management Data
8.2.1 Introduction
Data collected on Complaints and inquires is a critical source for analysis that can improve a Licensed Financial Institution’s overall conduct as well as problems with its product offering. Prompt analysis of trends help to identify deficiencies in Licensed Financial Institutions’ sales practice, business conduct, and product design and system defects. Therefore, it is critical for a Licensed Financial Institution to establish standards for Complaint and inquiry Data to be gathered, collected, classified, stored, analysed and reported.
8.2.2 Description
- 8.2.2.1 Licensed Financial Institutions must utilise the Data collected to conduct analysis and assess key risks and trends arising out of the Data. The results of the analysis must be used by the Licensed Financial Institution for conducting investigations into thematic trends, conducting root cause analysis of repeat issues and for designing new controls to address issues and improving quality and efficiency of various aspects of Consumer service. The Licensed Financial Institution must document any actions taken for review by the Central Bank.
- 8.2.2.2 The Complaints Data must be provided on a quarterly basis to the Senior Management of the Licensed Financial Institution to enable managerial level monitoring of trends and supportive decision-making.
- 8.2.2.3 Licensed Financial Institutions must ensure that the Data collected and reported to the Senior Management and to the regulator as required, is accurate, timely and complies with the Licensed Financial Institution’s data governance policies and procedures.
- 8.1.2.1 A Licensed Financial Institution must establish an independent Complaint management function in the organisation that directly reports to the Senior Management. The function must be empowered to effectively resolve Complaints and independent of other business operations.
Article 9: Consumer Education and Awareness
9.1 Consumer Education and Awareness
9.1.1 Introduction
Article 121/2 of the Decretal Law states: “The Central Bank and Licensed Financial Institutions shall work together to raise public awareness of the types of banking services and financial products and their inherent risk through all means of communications and media, in accordance with the rules set by the Central Bank in this regard.”
Financial education and awareness must play an important role in the Consumer protection framework. Financial education can help to reduce the risk exposure of Consumers by enabling them to make financial decisions that are in their best interests. The collaboration between the Central Bank and Licensed Financial Institutions to expand efforts to increase awareness will help to mitigate risks to Consumer and aid Consumers in making informed financial decisions.
9.1.2 Description
- 9.1.2.1 Licensed Financial Institutions have responsibility in improving Consumers’ financial education and awareness. Licensed Financial Institutions must undertake on-going initiatives to increase awareness, mitigate Consumer risks and aid Consumers in making informed financial decisions.
- 9.1.2.2 Where products and/or services are offered online or in any other digital form, Licensed Financial Institutions must still comply with the provisions of the Regulation and accompanying Standards by providing Consumers with unbiased educational information and ensure Consumer awareness of any risks before acceptance of the product or services is completed.
- 9.1.2.3 Licensed Financial Institutions must collaborate with the Central Bank and may assist jointly with other stakeholders to promote financial education and awareness.
- 9.1.2.4 Licensed Financial Institutions must assist Consumers to develop knowledge, skills and confidence to sufficiently understand risks, make informed choices, know where to go for Advice / assistance, and to take positive action to improve their own financial wellbeing.
- 9.1.2.1 Licensed Financial Institutions have responsibility in improving Consumers’ financial education and awareness. Licensed Financial Institutions must undertake on-going initiatives to increase awareness, mitigate Consumer risks and aid Consumers in making informed financial decisions.
Article 10: Financial Inclusion
10.1 Inclusion
10.1.1 Introduction
Article 123 of the Decretal Law states: “The Board of Directors shall establish necessary regulations and mechanisms to ensure that every natural Person shall have the right to access all or part of the banking and financial services and products from Licensed Financial Institutions suited to his/her need.”
To be able to fully participate in society and the financial Market, access must be inclusive. Consumers including vulnerable groups and People of Determination must have access to Financial Products and/or Services, e.g. a bank account, credit and the ability to carry out financial transactions in a safe and efficient manner.
10.1.2 Description
- 10.1.2.1 Licensed Financial Institutions must consider the requirements of vulnerable groups and People of Determination in its product and service design.
- 10.1.2.2 Licensed Financial Institutions must provide the option of basic and low-cost financial products and/or services to Consumers.
- 10.1.2.3 The staff of Licensed Financial Institutions must be regularly trained to identify and, where possible, assist vulnerable persons and People of Determination.
- 10.1.2.4 Licensed Financial Institutions must consider a vulnerable person’s or person of Determination’s special financial situation when offering products or services and the cost of any payable fees and instalments.
- 10.1.2.5 Licensed Financial Institutions must ensure that they provide physical locations of their ATMs and branches where there is appropriate access and conveniences for use by People of Determination.
- 10.1.2.6 Licensed Financial Institutions must be able to demonstrate their compliance with Federal Law No. 29 of 2006, in respect of the rights of People of Determination with Special Needs.
10.2 Gender and Racial Equality
10.2.1 Introduction
Minority Groups have differing financial needs. Licensed Financial Institutions have a responsibility of ensuring there is appropriate access to their products and/or services for Minority Groups.
10.2.2 Description
- 10.2.2.1 Licensed Financial Institutions must establish anti-discrimination code of conduct.
- 10.2.2.2 Licensed Financial Institutions should collect, analyse and track Consumer supply and demand Data disaggregated by gender, age and ethnicity to measure access to and usage of Financial Products and/or Services. The research outcome must be used solely for improving equality of the Financial Services provided to minority groups and females.
- 10.2.2.3 Licensed Financial Institutions should consider the particular needs of minority groups in their financial education and awareness programs.
- 10.2.2.4 Licensed Financial Institutions must not make decisions on the sale of product or services including Credit and/or setting of interest/profit rates that discriminate on the grounds of family status, gender of being a member of a Minority Group.
- 10.1.2.1 Licensed Financial Institutions must consider the requirements of vulnerable groups and People of Determination in its product and service design.
Article 11: Shari’ah Compliance for Financial Services
11.1 Shari’ah Compliance for Financial Services
11.1.1 Introduction
Given the critical significance of Shari’ah compliance in the Islamic finance business, Islamic Institutions the State must strive for the best international standards by incorporating Shari’ah principles in all aspects of their business comprised of operational, reporting, business conduct, risk management and oversight functions.
11.1.2 Description
- 11.1.2.1 Islamic Financial Institutions must uphold Shari’ah principles and must be compliant with the Islamic Financial Institution’s Internal Shari’ah Supervision Committees (ISSC).
- 11.1.2.2 Board and Senior Management of the Islamic Financial Institutions must monitor the activities and integrate Shari’ah compliance into the Islamic Financial Institution’s culture, processes, operation, and code of conduct.
- 11.1.2.1 Islamic Financial Institutions must uphold Shari’ah principles and must be compliant with the Islamic Financial Institution’s Internal Shari’ah Supervision Committees (ISSC).
Article 12: Conflict with Other Regulation
This Regulation and the accompanying Standards are in addition to any requirement of any other regulatory authority as applicable to Licensed Financial Institutions. In case of any conflict with such requirement, the provisions of this Regulation and accompanying Standards will prevail.
If there is conflict between the provisions of this Regulation and/or its accompanying Standards with any provisions in the previous regulations, notices, standards, circulars or instructions issued by the Central Bank, the provisions of this Regulation and the accompanying Standards shall prevail.
Article 13: Enforcement and Sanctions
Violation of any provision of this Regulation and the accompanying Standards may be subject to supervisory action, sanctions and penalties as deemed appropriate by the Central Bank.
Without prejudice to the provisions of the Decretal Law, supervisory action and sanctions by the Central Bank may include fines, replacing or restricting the powers of Senior Management or Members of the Board.
Article 14: Interpretation of Regulation
The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
Article 15: Publication and Effective Date
This Regulation and the accompanying Standards shall be published in the Official Gazette and shall be considered effective one month from the date of publication. This Regulation shall apply to all Licensed Financial Institutions, and they have to adjust their provisions in accordance with the Articles of this Regulation during a period not exceeding one year of its publication date.
Consumer Protection Standards
N 1158/2021Introduction
These Regulatory Standards form part of the Consumer Protection Regulation (Circular No. 8 - 2020). All Licensed Financial Institutions must comply with these Standards when the Licensed Financial Institution carries out licensed financial activities. These Standards are mandatory and enforceable in the same manner as the Regulation.
The Standards follow the principles-based structure of the Regulation, with each Article corresponding to the specific Article in the Regulation.
This document must be read in conjunction with other regulations, including Shari’ah compliance regulations and the Standard Re. Shari’ah Governance For Islamic Financial Institutions.
Article 1: Definitions
The Definitions set out in Article 1 of the Consumer Protection Regulation (Circular No. 8 - 2020) apply to these Standards
Article 2: Disclosure and Transparency
2.1 Disclosure
2.1.1 General Provisions for all Financial Products and/or Services
General Requirements
2.1.1.1 Licensed Financial Institutions must apply the Disclosure and Transparency requirements to all Financial Products and/or Services provided through all communication channels of service including branches, telephone banking, mobile applications, internet banking and all other channels.
2.1.1.2 All disclosure information must be available in Arabic and English. Refer to Clause 2.3.1.3.
2.1.1.3 Disclosure information must be easily available in all branches and all other communication and distribution channels.
2.1.1.4 Information must be available in a format accessible and in a manner suitable for People of Determination or a representative nominated by such a Consumer. The Licensed Financial Institutions must assess and provide the information in the format best suitable for the Consumer.
2.1.1.5 Information must be in clear and plain language and presented using user-friendly sized font, color and spacing. It should incorporate appropriate visual graphics and provide examples using text boxes and tables to help educate Consumers about key financial concepts.
2.1.1.6 Licensed Financial Institutions must use official documents for all transactions when dealing with its Consumers. In particular, the name of the Licensed Financial Institution and a regulatory disclosure statement stating that the Licensed Financial Institution is licensed by the Central Bank must be accurately displayed in the documents. Documents must not use any other term that might indicate any out of scope unlicensed activities.
2.1.1.7 Licensed Financial Institutions must clearly and prominently display the full legal/trade name of the Licensed Financial Institution on the main signage of the licensed premises, websites, letterheads, business cards, transaction receipts and all other marketing/branding materials.
2.1.1.8 When Licensed Financial Institutions provide Advice of any kind, they must not make statements that are untrue, misleading or omit information that is necessary to understand the nature, costs, risks, terms and conditions of the Financial Products and/or Services.
2.1.1.9 When Specific Advice is provided to a Consumer by the Licensed Financial Institution, the Specific Advice must be documented. If a Financial Product and/or Service is sold, a copy of the Specific Advice must be provided to the Consumer.
2.1.1.10 Licensed Financial Institutions must continuously monitor and, improve the effectiveness of its disclosures with techniques such as Complaint analysis, Consumer satisfaction surveys, mystery shopping and Call- backs to Consumers.
2.1.1.11 Licensed Financial Institutions must inform Consumers about account services that are included and the account services that are optional and if there is an additional fee.
2.1.1.12 Licensed Financial Institutions must inform Consumers about the terms and conditions related to termination, expiry date, unclaimed balances and Fees for all payment instruments that it offers.
2.1.1.13 Where Licensed Financial Institutions are offering any form of rebate, gift or other incentive on their Financial Products and/or Services, Licensed Financial Institutions must clearly disclose separately the terms and conditions associated with that rebate, gift or incentive and highlight any conditions and/or restrictions. Easy and direct access must be provided to obtain the specific terms and conditions related to the rebate, gift or incentive.
2.1.1.14 Licensed Financial Institutions must include statements in terms and conditions, financial product disclosure documents, Key Facts Statements and application forms that will warn Consumers of consequences in the event of a Consumer’s failure to meet the Licensed Financial Institution’s terms and conditions before and during the Consumer’s relationships with Licensed Financial Institutions.
2.1.1.15 Licensed Financial Institutions must ensure that all warning statements required by these Standards are prominently and clearly displayed in the disclosure document, i.e. they must be in a highlight box and in bold type. Warning statements, as specified in this Standard, are to be provided during all communications with the Consumer regarding a product or service. Additional warning statements must be provided regarding potential negative financial implication on the Consumer.
2.1.1.16 Information on Base Lending / base financing rates or other reference rates including the effective dates of these rates must be made available on the Licensed Financial Institution’s website and mobile application and be displayed at the Licensed Financial Institution’s branch. The posting of the rates must be updated on a regular basis with each change in rates.
2.1.1.17 Where a contract with a Consumer has a provision for annual automatic renewal of the contract, the Licensed Financial Institution must send a written notice to the Consumer at least 30 calendar days in advance from the date of renewal. The notice must also inform the Consumer how and when the automatic renewal can be cancelled.
2.1.1.18 Licensed Financial Institution’s schedule for Fees, including Third Party Fees, must be clearly on display in all branches and on the Licensed Financial Institution’s website.
2.1.1.19 Licensed Financial Institutions must provide Consumers with a Key Facts Statement prior to providing a Financial Product and/or Service or on the Consumer’s request.
2.1.1.20 The Key Facts Statement should be the first document provided to the Consumer during the sales process and must be individually and clearly presented. Prior to signing the contract, the Consumer must sign to acknowledge receipt of a Key Facts Statement for the product or service being purchased.
2.1.1.21 Key Facts Statements specific for a Financial Product and/or Service must be offered to Consumers for any Financial Product and/or Service that is being distributed, advertised, marketed, sold or otherwise provided by Licensed Financial Institutions (including insurance/takaful and structured products).
2.1.1.22 The Key Facts Statement must:
a. Be a stand-alone document;
b. Be concise (preferably within 2 pages) and use plain language which is easy to understand;
c. Provide an accurate description of each Financial Product and/or Service;
d. Specify whether the Licensed Financial Institution reserves the right to change terms and conditions at a later date;
e. Specify the notice period to be provided before implementing any future and Permissible change in terms and conditions;
f. Specify, as applicable, related interest/profit rates, Fees, key terms & conditions, key obligations, limitations and key requirements of the financial product in a legible font size;
g. Use “Warning” boxes to highlight key risks related to the purchase of Financial Products and/or Services. This should include disclosure of any assumptions made that may affect the performance of the Financial Product and/or Service, any risks that would create the potential for monetary losses or the lack of any potential gains/profit and any limitations on potential monetary gains; and
h. For loan/financing products, Licensed Financial Institutions must disclose to Consumers the expected Annual interest/profit rate, any possible fees on the Credit Product and the standard formula of computing interest/profit amount as may be prescribed by the Central Bank. In addition, Licensed Financial Institutions must disclose in a prominent manner in the Key Facts Statement whether the product has a fixed, variable or a combination of fixed and variable interest/profit rate basis.
Section 2.1.2, 2.1.3, 2.1.4 and 2.1.5 of this Article apply to Key Facts Statements.
2.1.1.23 Licensed Financial Institutions must provide appropriate information to the potential and existing Consumer at all stages of the relationship. All information, disclosures and other communications by Licensed Financial Institutions to Consumers must be accurate and comprehensive at each of the following 3 stages of the Consumer relationship:
a. Prior to providing a Financial Product and/or Service to a Consumer: The information gathering stage before the point of sale or at the application stage. Disclosure should be made so that the Consumer has an understanding of the financial product’s features, pricing, benefits, risks, Fees and Consumer’s rights and obligations before making a decision;
b. At point of entering the contract: The stage in which the Consumer is being provided with an offer and is at the stage of accepting the Financial Product and/or Service offer made by the Licensed Financial Institution; and
c. During the term of the contract: The stage after the acceptance of the contract and until the end of the contract.
2.1.1.24 Disclosures relating to the privacy and use of personal information must be made to the Consumer in accordance with Article 6: Protection of Consumer Data and Assets of these Standards.
Prior to Providing a Financial Product and/or Service
2.1.1.25 Licensed Financial Institutions must provide inquiring Consumers with a copy of the terms and conditions of the Financial Product and/or Service that pertains to the inquiry. Licensed Financial Institutions must answer in Writing, any queries of Consumers relating to terms and conditions.
At Point of Entering the Contract
2.1.1.26 In case of rejection of any Consumer’s application for a Financial Product and/or Service by the Licensed Financial Institution, the Licensed Financial Institution must disclose the reason for rejection to the applicant except where the reason of rejection is related to Financial Crime Compliance risks or as may be prohibited by law.
2.1.1.27 Licensed Financial Institutions must provide Consumers with a copy of the contract to read and with appropriate time to review before signing it.
2.1.1.28 Licensed Financial Institutions must provide Consumers with all final documents involved in a transaction including any document that contains the signature or indication of approval of the Consumer. This applies to all documents including but not limited to the offer, contract, terms and conditions, security and guarantee. Documents must be provided free of charge regardless of how they are provided.
2.1.1.29 Where there is a guarantor or more than one Person signing a contract for a Financial Product and/or Service, each Person must be given copies of the documents free of charge.
2.1.1.30 Consumers must be offered a choice of which document format they wish to receive the initial copies of the documents.
2.1.1.31 Where a Cooling-off Period is required to be provided by these Standards or prescribed by the Central Bank, Consumers must be informed of their right to a Cooling-off¬Period at time of signing the contract for the purchase of a Financial Product or Service. Where a longer Cooling-off period is specified by way of other legal or regulatory requirements, the longer period must be applied.
2.1.1.32 Consumers may waive the Central Bank’s required Cooling-off Period of complete 5 business days by signing a written waiver provided by the Licensed Financial Institution containing a warning about agreeing to an immediate commitment.
2.1.1.33 The underlying Shari’ah contracts for Shari’ah-compliant financial products should include a clause granting the Consumer Cooling-off option for a period of 5 complete business days in accordance with the provisions contained in the Civil Transactions Law and the relevant Shari’ah standards.
2.1.1.34 Where a Licensed Financial Institution is required to carry out an assessment of a Consumer regarding the suitability, affordability and/or appropriateness of a Financial Product and/or Service, a copy of the summary of the results of the assessment must be provided to the Consumer without charge except as may be prohibited by law.
2.1.1.35 Licensed Financial Institutions must disclose in a prominent manner to a Consumer whether the interest/profit rate charged on a Credit Product is variable or fixed or a combination of the variable and fixed rate, where applicable, and the method of calculation of the rate.
2.1.1.36 Where a Base Lending / base financing Rate forms part of the final interest/profit rate offered to a Consumer, Licensed Financial Institutions must disclose to the Consumer the separate components of the rate i.e. Base Lending / base financing Rate + X basis points. Licensed Financial Institutions must explain and provide a clear example of the concept of the Base Lending / base financing Rate and the potential frequency at which the rate will be revised as well as where the rates will be publicly posted.
2.1.1.37 Licensed Financial Institutions must disclose all Fees that are applicable to Consumers and provide Consumers with a copy of the Fees specific to the Financial Product and/or Service, at the time of signing a contract or upon a Consumer’s request at any time. Licensed Financial Institutions must explain the amount and calculation methodology of all applicable Fees. The Licensed Financial Institution must disclose to the Consumer that Third Party Fees may apply and disclose the amount. If the amount is not known, the Licensed Financial Institution should endeavor to provide an estimate or range.
2.1.1.38 Licensed Financial Institutions must disclose whether the Fees to be charged to the Consumer are one time or recurring. In cases where Fees are recurring, Licensed Financial Institutions must disclose the frequency of recurrence and the time period over which the amount will continue to be charged to the Consumer.
2.1.1.39 Licensed Financial Institutions must advise Consumers on what they can do to protect their accounts from fraud and misuse and must ensure that Consumers are fully aware of the consequences of granting an unauthorized Person and/or Third Parties access to their bank accounts and any other Financial Product and/or Service. In particular, Licensed Financial Institutions must inform Consumers of the consequences of sharing their personal information, personal identification number (PIN) and other security information.
2.1.1.40 Licensed Financial Institutions must inform Consumers of the process and contact method to follow in reporting a lost or a stolen card and in case of Unauthorized Transactions on their accounts.
2.1.1.41 Licensed Financial Institutions must inform Consumers that they are responsible for:
a. Keeping their banking correspondence secure for future reference;
b. Verifying the accuracy of any account / transaction statements sent to them; and
c. Confirming to the Licensed Financial Institution, their contact information and identification when changes occur or as requested. Requests for subsequent confirmation of information from a Licensed Financial Institution must be executed in a secure manner.
2.1.1.42 Islamic Financial Institutions (IFIs) which offer Shari’ah compliant products must disclose the Shari’ah basis of the Financial Product and/or Service and the approval from the Internal Shari’ah Supervision Committee. The Shari’ah basis should also be included in the Key Facts Statement.
During the Term of the Contract
2.1.1.43 During the term of the contract, Licensed Financial Institutions must provide Consumers with a regular detailed statement including all transactions that occurred in an account for a Financial Product and/or Service:
a. The statement must include key information that fully informs the Consumer as to the amount, type and status of the transactions in the account(s); and
b. No Fees can be charged for original statements provided to the Consumer.
Sections 2.1.2, 2.1.3, 2.1.4 and 2.1.5 of this Article contain further details on statements to be shared during the term of the contract.
2.1.1.44 Licensed Financial Institutions must inform Consumers of all transactions on their accounts as they occur, by sending a free SMS to a mobile phone or, if requested, to the Consumer’s email address. The details of such transactions must be available on the Consumer’s mobile or internet banking platforms.
2.1.1.45 In case of digital transactions, the Licensed Financial Institution must communicate specific information to the Consumer upon receiving transaction requests and upon execution of the transaction as prescribed by the Central Bank.
2.1.1.46 Licensed Financial Institution cannot change terms and conditions of a contract unless this has been clearly, separately, and prominently disclosed and agreed by way of expressed consent by the Consumer.
2.1.1.47 If the Licensed Financial Institution decides to make Permissible changes to the contract, the Licensed Financial Institution must give Consumers a minimum of 60 calendar days’ notice before changes to the terms and conditions of a Financial Product and/or Service, including changes to Fees, can take effect, with exception provided by Clause 2.1.1.36 and 2.1.3.21 regarding lending Rates.
2.1.1.48 In the notification to Consumers of Permissible changes to the terms and conditions of a contract, the Licensed Financial Institutions must provide a plain language summary of the key changes along with a copy of the revised Terms and Conditions.
2.1.1.49 Where there is a Permissible change in the methodology to calculate rates and Fees, the Licensed Financial Institution must disclose the revised methodology to the Consumer by way of written notice that must be provided 60 calendar days in advance of the change taking effect.
2.1.1.50 When a Consumer or the Licensed Financial Institution transfers or closes a Consumer’s account except for credit cards and investment accounts, the Licensed Financial Institution must issue to the Consumer a final closing account statement, identified as such, within 7 complete business days of the Consumer requesting the transfer or closure of the account.
2.1.1.51 When intending to close, merge or move a branch of a Licensed Financial Institution, the Licensed Financial Institution must:
a. Notify the Central Bank immediately in the manner as may be prescribed by the Central Bank;
b. Provide at least 60 calendar days’ written notice to affected Consumers to enable them to make alternative arrangements;
c. Post a notice that is clearly visible to Consumers in the closing branch and stating the date of closing of the branch;
d. Disclose how continuity of service will be provided to the Consumer; and
e. Disclose this information on their website.
2.1.2 General Provisions for Deposit Products
General Requirements
2.1.2.1 Licensed Financial Institutions that offer Deposit Products must comply with the requirements in Section 2.1.1 of this Article as applicable, in addition to complying with the requirements of this Section.
Prior to Providing a Deposit Product and/or Service
2.1.2.2 Where a Licensed Financial Institutions offers low cost savings account and / or current account, they must be transparent and inform the Consumer of the availability of a low cost savings account and / or current account and disclose the key features of such accounts.
2.1.2.3 Licensed Financial Institutions must disclose if the account type requires an initial deposit to open the account and a minimum balance to be maintained in that type of account. The disclosure must warn the Consumer of the consequence of not maintaining a minimum (daily / monthly) balance in the account including the imposition of any Fee.
2.1.2.4 Licensed Financial Institutions must disclose the expected Annual Interest/Profit Rate that will be paid on the deposit, the frequency of interest/profit payments and any circumstances that might affect the amount or frequency of the interest/profit payments.
2.1.2.5 Licensed Financial Institutions must disclose all Fees on both standard and additional/optional services applicable to the deposit account to Consumers.
At Point of Entering the Contract
2.1.2.6 Licensed Financial Institutions must inform Consumers of the implication of redeeming a fixed deposit before maturity. Licensed Financial Institutions must disclose any penalty applied to the interest/profit rate or Permissible Fees applicable to early closure of deposit account within a specified time frame.
2.1.2.7 For accounts with a cheque book facility, Licensed Financial Institutions must inform Consumers in Writing of:
a. Any limit on the number of cheques permitted in their cheque book; and
b. The repercussions of returned cheques including fees, closure of the current account and / or a negative report to the Credit Information Agency.
2.1.2.8 Licensed Financial Institutions must inform Consumers of the communications channel that Consumers can use to obtain periodic transaction account statements on their deposit accounts.
During the Term of the Contract
2.1.2.9 Licensed Financial Institutions must, at minimum on a monthly basis, provide the Consumer with a free transaction account statement (electronic or paper) which must include, where applicable:
a. Account Number/ID;
b. Name(s) on the Account;
c. The time period covered by the statement;
d. The opening balance;
e. Each deposit;
f. Each withdrawal;
g. Breakdown of any interest/profit credited;
h. Breakdown of all Fees by amount and type;
i. The end of statement period closing balance;
j. Term dates on fixed deposits;
k. Early redemption penalties;
l. Explanations of the interest/profit rate applied if fixed, or if variable, the annual rate on the account during the period covered by the statement; and
m. Information on how to file a Complaint with the Licensed Financial Institution which includes, at minimum, the contact details of the Licensed Financial Institution’s Complaint function, channels for lodging Complaints (e.g. by email, phone, fax etc.) and response time to address Complaints.
2.1.2.10 Licensed Financial Institutions must inform Consumers of any Permissible changes in Annual Interest/Profit Rates on their deposit products. Refer to Clause 2.1.3.21.
2.1.2.11 If an account is to become dormant, free reminders must be sent to the Consumer informing them about the impending dormancy, as may be prescribed by the Central Bank.
2.1.2.12 Licensed Financial Institutions must inform Consumers of their decision to close a Consumer's account 60 calendar days in advance of the account being closed and provide in Writing, the reasons for closure. If the Licensed Financial Institution has reasonable grounds to believe there may be financial crime risks and potential fraud, Licensed Financial Institutions can immediately close or block an account without providing the advanced notice or reasons to the Consumer.
Disclosure Requirements for Shari’ah Deposit Products
2.1.2.13 IFIs which offer Shari’ah compliant Deposit Products must comply with the requirements in Section 2.1.2 of this Article as applicable, in addition to complying with the below requirements.
2.1.2.14 IFIs which offer Shari’ah compliant Deposit Products to Consumers must:
a. Explain briefly the Shari’ah concepts applicable to the Deposit Product, including the rights and obligations of the Consumer;
b. Disclose that funds are invested and managed in accordance with Shari’ah requirements;
c. Disclose the profit-sharing ratio, weights and profit distribution method by the Licensed Financial Institution for deposits under the mudarabah concept, including the frequency of profit payment. For Deposit Products with fixed tenor, the Licensed Financial Institution should disclose the historical profit rates to facilitate comparison by the Consumer; and
d. Disclose if a minimum deposit amount is required for the account to be eligible for profit sharing.
2.1.3 General Provisions for Credit / Financing Products
General Requirements
2.1.3.1 Licensed Financial Institutions that offer Credit Products must comply with the requirements in Section 2.1.1 of this Article as applicable, in addition to complying with the requirements of this Section.
Prior to Providing a Credit Product and/or Service
2.1.3.2 Licensed Financial Institutions must provide Consumers with the expected Annual Percentage Rate that will be charged on the offered Credit Product to facilitate comparison between Credit Products and between institutions.
2.1.3.3 Licensed Financial Institutions must disclose whether security, a guarantor, co-signer or collateral is required for a Credit Product before the consumer signs the contract. Licensed Financial Institutions must fully disclose the purpose of these requirements and the conditions placed on the pledging of security and any other collateral including the Licensed Financial Institution’s rights to dispose of them and the manner in which they may be disposed.
At Point of Entering the Contract
2.1.3.4 Licensed Financial Institutions must disclose:
a. How the interest/profit on the Credit Product will be calculated (including the date from which interest/profit is incurred) and provide an example of the calculation to the Consumer; and
b. How the payments are allocated between outstanding balance and interest / profit as per the Reducing Balance Method.
2.1.3.5 Licensed Financial Institutions must disclose that they are not permitted to charge interest/profit on accrued interest/profit of any Credit Product granted to Consumers in accordance with Article (121), Clause 3 in Decretal Federal Law No. (14) of 2018, Regarding the Central Bank & Organization of Financial Institutions and Activities.
2.1.3.6 For variable rate loans/financing, Licensed Financial Institutions must disclose to Consumers the potential impact of an increase in the Annual Interest/Profit Rate on the loan/financing. The disclosure must explain via an illustrative example:
a. The potential consequences of an increase to the rate on the loan/financing payment amounts;
b. The change in the allocation of the payment between interest/profit amount and a reduction in outstanding balance;
c. The impact on the tenor if any; and
d. The consequences of any increase in rates on the amount of a deferred payment or an accumulated balloon payment during or at the end of the loan/financing tenor.
2.1.3.7 Licensed Financial Institutions must disclose whether early settlement is possible and which Permissible Fees are payable if the Credit Product is terminated before the end of the tenor along with, how the Fees will be calculated and when they are payable.
2.1.3.8 The Key Facts Statement on a financing product must set out a detailed example relevant to the product with the calculation and cost of the applicable Early Settlement Fees where applicable.
2.1.3.9 When a Licensed Financial Institution decides to sell a Credit Product to a Consumer, the Licensed Financial Institution must issue a written offer that contains the approved loan/financing amount, all the terms and conditions and for financing with a tenor, the cumulative total of all repayment/payment amounts to be paid by the end of the tenor based on the initial interest / profit rate, and a separate amount that will total the expected amount of interest/profit that would be paid over the tenor.
2.1.3.10 Licensed Financial Institutions must inform Consumers that funds approved on a Credit Product, except for mortgages and credit cards, will be disbursed within 10 complete business days of signing the contract or within such other time frame that is agreed to and specified in the contract. Complying with the period of time for disbursement of funds is subject to the Consumer and / or third party providing the required and properly completed documents and meeting the agreed conditions. If it is not possible to release the funds within the time limit, the Licensed Financial Institution must advise the Consumer in Writing immediately as to the reason for the delay and the date by which the funds will be available. As a consequence of the delay caused by the Licensed Financial Institution, the Consumer retains the option to cancel the contract without cost or penalty before the funds are made available.
2.1.3.11 At the point of entering the contract, except for credit cards, Licensed Financial Institutions must provide Consumers with a complete repayment/payment schedule document including the following but as may be applicable:
a. The initial amount of the loan/financing;
b. The Annual Interest/Profit Rate including whether it is fixed or variable;
c. The expected tenor;
d. The date of the first installment;
e. The number of installments to be paid;
f. The frequency of repayment/payment;
g. The amount to be paid for each installment;
h. The allocation of each installment between the principal and interest/profit payments;
i. The decline in principal amount of the loan/financing with each payment; and
j. The total cost of the loan/financing in terms of the total interest/profit paid by the Consumer.
2.1.3.12 For Shari’ah compliant financing products:
a. Licensed Financial Institutions must inform a Consumer when late payment Fees/commitment for contribution towards charity will be imposed and the amount to be imposed. Licensed Financial Institutions must also disclose to Consumers the manner in which the late payment Fees/commitment for contribution towards charity will be calculated; and
b. Late payment Fees/commitment for contribution towards charity must be based on an administrative cost and must not include any remuneration to the Licensed Financial Institution that could be considered unlawful charging of interest/profit on accrued interest/profit.
2.1.3.13 Where Licensed Financial Institutions offer or market insurance/takaful products and/or services associated with the credit/financing product, Consumers must be informed in Writing that they have the choice to accept or reject the offer of insurance/takaful.
2.1.3.14 In addition to any other UAE regulator’s requirements regarding the sale and marketing of insurance/takaful, Licensed Financial Institutions must at a minimum:
a. Explain the nature, purpose, coverage and limitations of coverage;
b. Disclose its suitability for the Consumer;
c. Disclose termination conditions including any obligations related to future insurance/takaful payments/ premiums; and
d. Disclose the Fees (including associated commissions) paid with the sale of such an insurance/takaful product.
The Licensed Financial Institution must obtain the Consumer’s expressed consent for insurance/takaful independently of signing application forms or the contract for offering insurance/takaful. The appropriate Cooling- off Period will apply. This Section must be read in conjunction with the Section on Cooling-off Period of Article 5: Business Conduct of these Standards. Refer to Clause 2.1.1.31.
2.1.3.15 Where insurance/takaful coverage is a mandatory component of the Credit/Financing Product and/or Service, the Licensed Financial Institutions must disclose the purpose of the insurance/takaful. The Licensed Financial Institution must disclose the costs of the Licensed Financial Institution’s insurance/takaful product in Writing to the Consumer and inform the Consumer that the Consumer has the right to choose an insurance/takaful provider from minimum choice of 3 insurance/takaful providers approved by the Licensed Financial Institution. The Consumer should inform the Licensed Financial Institution of the choice of insurance/takaful provider within a reasonable period of time. If the Consumer does not inform Licensed Financial Institutions of the choice of a provider, the Licensed Financial Institution has the right to choose an insurance/takaful provider from the approved insurance/takaful providers presented to the Consumer.
The Licensed Financial Institution must also disclose to the Consumer if the insurance/takaful provider belongs to the same group of institutions as the Licensed Financial Institution.
2.1.3.16 If the Consumer decides to acquire insurance/takaful through the Licensed Financial Institution, the Consumer must be informed of any additional costs that may be incurred if the insurance/takaful costs are added to the loan/financing principal and thereby incurring the additional interest/profit costs.
2.1.3.17 When a Credit Product that is offered to a Consumer includes a balloon or deferred payment(s), or the option of a balloon or deferred payment, Licensed Financial Institutions must explain to the Consumer verbally and in Writing the concept of a balloon or deferred payment and the risks associated with the credit/financing product. Specifically before entering the contract, Licensed Financial Institutions must provide the Consumer with an explanation of the repayment/payment schedule and clearly outline the scheduling and amount of the balloon or deferred payments. The Consumer must acknowledge in Writing that this has been fully disclosed to him/her by the Licensed Financial Institution.
2.1.3.18 Licensed Financial Institutions must disclose to Consumers that a Credit Product cannot exceed its authorized limit or be allowed to draw on an overdraft facility and that any transaction resulting in the limit being exceeded may be rejected and may incur Fees.
During the Term of the Contract
2.1.3.19 Licensed Financial Institutions must, at minimum, on a quarterly basis for credit/financing facilities and at minimum on a monthly basis for credit / payment instruments, provide Consumers with a free statement of transactions (electronic or paper) which must include:
a. Account Number/ID or Card Number/ID;
b. Name(s) of Consumer(s);
c. The date of the statement and the period covered by the statement;
d. Next payment due date;
e. The opening balance;
f. Each transaction and the date of the transaction;
g. The allocation of each payment between the outstanding balance and interest/profit payments (for loan/financing facilities);
h. All interest/profit charged (for credit cards, Annual Interest/Profit Rate charged must be disclosed separately);
i. All Fees transactions identified and totaled separately;
j. Foreign exchange rate applied to each foreign exchange transaction (applicable to credit / payment card statements);
k. The outstanding balance due;
l. In case of balloon payments, the statement must clearly identify the balloon payment and future date due;
m. In case of deferred payments, the statement must clearly identify the deferred amount and future date due;
n. Details of the Annual Interest/Profit Rate applied during the period covered by the statement; and
o. Information on how to file a Complaint with the Licensed Financial Institution which includes, at minimum, the contact details of the Licensed Financial Institution’s Complaint channels for reporting disputed transactions and lodging Complaints (e.g. by email, phone, fax etc.) and response time to address Complaints.
2.1.3.20 In addition to the above, a Credit Product statement for credit cards must also explain the cost that would be incurred if the Consumer does not make a full payment for the total amount outstanding by the payment due date by disclosing:
a. The length of time it would take to fully settle the cardholder’s actual existing balance outstanding including the costs of total interest/profit if the Consumer only pays the minimum payment and there is no new transaction on the credit card during that period;
b. The minimum payment amount that would be due; and
c. The following warning statement:
Warning: If you make only the minimum repayment/payment each period, you will pay more in interest/profit/fees and it will take you longer to pay off your outstanding balance.
2.1.3.21 Where any change in the Annual Interest/Profit Rate of a Credit Product is permitted, Licensed Financial Institutions must notify Consumers of the change. Where the rate change is an increase to the part of the Consumer’s interest/profit rate that is added to the variable Base Lending Rate/Financing Rate, the Licensed Financial Institution must not increase that part of the interest/profit rate until after the 30 calendar days’ notice period. This notification must include:
a. The date from which the new rate will change;
b. Details of the old and new rate;
c. The details of the impact on the allocation of payments towards principle and interest/profit amount;
d. If applicable, the revised repayment/payment amount; and
e. The contact information for the unit in the Licensed Financial Institution that will respond to Consumers regarding the change and / or where the Consumer anticipates difficulties meeting any resulting higher repayments/payments.
2.1.3.22 Licensed Financial Institutions must ensure that a Consumer is immediately advised in Writing when a payment is missed for more than calendar 30 days past its due date.
2.1.3.23 When the Consumer is 2 payments in Arrears, the Licensed Financial Institution must advise the Consumer in Writing of the possible consequences of the Arrears as deemed appropriate by the Licensed Financial Institution, including:
a. Legal action;
b. Foreclosure;
c. Redemption of security;
d. Demand for payment from the guarantor; and
e. Negative reporting with the Credit Information Agency.
2.1.3.24 Licensed Financial Institutions must disclose to Consumers the amount of late payment Fees and the dates they were incurred.
2.1.3.25 In the event of sale or transfer by a Licensed Financial Institution of a Consumer’s Credit Product to a Third Party, the Licensed Financial Institution must ensure that a Consumer is advised in Writing, 60 calendar days in advance of the sale or transfer and notified of the name of the Third Party unless otherwise instructed by the Central Bank.
Disclosures Requirements for Shari’ah Financing Products
2.1.3.26 IFIs which offer Shari’ah compliant financing products must comply with all the requirements in Section 2.1.3 of this Article, in addition to complying with the below requirements.
2.1.3.27 IFIs which offer Shari’ah compliant financing products to Consumers must:
a. Explain briefly the Shari’ah concepts applicable to the financing product; and
b. Indicate any takaful/insurance that is required as a condition of the financing product.
2.1.3.28 IFIs must comply with the specific early settlement disclosure requirements set by the Central Bank.
2.1.4 General Provisions for Structured Investment Products / Shari’ah Compliant Structured Products
General Requirements
2.1.4.1 Licensed Financial Institutions that offer structured investment products must comply with the requirements in Section 2.1.1 of this Article as applicable, in addition to complying with the requirements of this Section.
Prior to Providing a Structured product
2.1.4.2 Licensed Financial Institutions must disclose to the Consumers the details of the bank or entity issuing the structured product including the name and contact information of the entity.
2.1.4.3 Licensed Financial Institutions must disclose to the Consumers the responsibilities of the Consumer’s Licensed Financial Institution and that of the entity issuing the product regarding the sales, performance and management of the structured product.
2.1.4.4 Licensed Financial Institutions must disclose the name of the regulatory entity who regulates the product. Where a Licensed Financial Institution intends to use a Third Party to develop a structured product on its behalf for its Consumers, it must disclose this fact and whether the Third Party is regulated within the UAE.
At Point of Entering the Contract
2.1.4.5 Licensed Financial Institutions offering any structured product must provide Consumers with disclosure information on the structured product as may be relevant to the Consumer including:
a. Capital security (any guarantee provided on the whole or portion of the principal amount of investment);
b. The level, nature, extent and limitations of any guarantee on the principal and/or returns;
c. The name of the guarantor of any guarantees and the credit worthiness of the guarantor if rated by an accredited credit rating agency;
d. The risk that some or all the investment may be lost;
e. The risk of using leveraging on an investment and an explanation with an example as to the full cumulative effects on losses of initial capital investment, the potential extraordinary losses possible due to leveraging and that it could result in the possible liquidation of the Consumers pledged assets;
f. Any limitations/restrictions on the sale early redemption of the funds invested; or
g. The consequences, including the cost, of exiting the product early;
h. Description of any assumptions or calculations used to determine performance/cost of the investments including detailed, clear examples where the assumptions are met and failed to be met, and the consequences it has on the investment;
i. The risk or likelihood that the estimated or anticipated return on the product will not be achieved;
j. The potential effects of volatility in price and fluctuation in interest/profit rates and/or movements in exchange rates and underlying securities on the value of the investment; and
k. Separate disclosure of each type of fee and amount associated with the management, purchase, sale, set up and administration of the product and investment account.
2.1.4.6 Licensed Financial Institutions must provide a copy of its assessment as to the suitability of the product based on the financial and risk profile of Consumer including the following warning statement with all numerical illustrations of investment performance:
Warning: These figures are estimates only. They are not a reliable guide to the future performance of your investment.
During the Term of the Contract
2.1.4.7 Licensed Financial Institutions must, at minimum, on a quarterly basis, provide to Consumers a statement on their investment which must include, as applicable:
a. The date of the statement and the period covered by the statement;
b. The initial value of the investment at the time the investment was first made;
c. The opening balance or value at the start of the quarter;
d. Each addition to the account including additional amounts invested and the respective dates of the transaction;
e. Each withdrawal and the respective dates of the transaction;
f. The total actual balance at end of the quarter;
g. The number of units held;
h. Disclosure as to the net interest/profit and loss when comparing the cumulative total amount invested at the start against the market value of the investment shown at the end of this quarterly statement;
i. Separate disclosure of each type of Fee and amount associated with the management, administration, sale, set up and ongoing administration of the structured product and investment account; in addition, a cumulative total of these Fees since the investment was initiated must also be disclosed; and
j. Information on how to file a Complaint with the Licensed Financial Institution which includes, at minimum, the contact details of the Licensed Financial Institution’s Complaint function, channels for disputing a transaction or lodging Complaints (e.g. by email, phone, fax etc.) and response time to address Complaints.
Disclosure Requirements for Shari’ah Compliant Structured products
2.1.4.8 IFIs which offer Shari’ah compliant structured products must comply with the requirements in Section 2.1.4 of this Article as applicable, in addition to complying with the below requirements.
2.1.4.9 IFIs which offer Shari’ah compliant structured products to Consumers must:
a. Explain in plain language the Shari’ah concepts applicable to the investment accounts including the rights and obligations of Consumers;
b. Disclose to Consumers that any losses arising from the investment (other than losses caused by misconduct, negligence or breach of terms and conditions by the Licensed Financial Institution) must be borne by the Consumers;
c. Disclose that investment account funds are invested and managed in accordance with Shari’ah requirements; and
d. Disclose the minimum amount required to open an investment account. Consumers should also be warned of the consequences of premature termination of the investment account, including forfeiture of profits.
2.1.4.10 In the case of a Licensed Financial Institution offering Shari’ah compliant profit-sharing investment account to Consumers, Licensed Financial Institutions must provide:
a. The profit-sharing ratio between the Licensed Financial Institution and Consumer;
b. The profit distribution method;
c. How and when the Licensed Financial Institution will pay profit and repay the principal;
d. How funds may be dealt with upon maturity; and
e. Additional Fees or change in profit rate resulting from a withdrawal in advance of maturity.
2.1.5 General Provisions for Remittances, Transfers and Foreign Exchange
General Requirements
2.1.5.1 Licensed Financial Institutions that offer remittance, transfer and foreign exchange products and/or services must comply with the requirements in Section 2.1.1 of this Article as applicable, in addition to complying with the requirements of this Section.
2.1.5.2 Licensed Financial Institutions must provide to Consumers clear information about all applicable Fees imposed on any services and the applicable buy and sell exchange rate. Where available, the Licensed Financial Institution should endeavor to disclose the Fees imposed by the correspondent bank or financial institution or the disbursing remittance service provider. Where Fees are not available, the Licensed Financial Institution should endeavor to provide an estimate or range and provide a disclaimer that states that the transfer may be subject to additional charges.
2.1.5.3 Licensed Financial Institutions must prominently display the following at all public locations where consumers are served, during working hours and in a prominent place of the Licensed Institution’s premises clearly visible to Consumers:
a. Buy and sell rates for money exchanged against the local currency (i.e. AED) for all major foreign currencies that the Licensed Financial Institution deals and posted under the headings “we buy” and “we sell”; and
b. Buy rates for remittances in major foreign currencies that the Licensed Financial Institution deals in against the local currency.
Pre-Transaction
2.1.5.4 Licensed Financial Institutions who carry on money changing and / or other foreign exchange activities must disclose the exchange rate, the difference between the buy and sell rate on a transaction and the Fees imposed by the Licensed Financial Institution for transactions prior to providing the money exchange, remittance, transfer and foreign exchange product and/or service. The exchange rate, the difference between the buy and sell rate on a transaction and Fees must be shown separately to the Consumer.
2.1.5.5 Licensed Financial Institutions who carry on remittance activities, must, where possible, disclose to Consumers the following prior to undertaking any remittance transaction:
a. The information set out in Section 2.1.5.4;
b. The amount in the currency that is expected to be paid to the beneficiary with a warning box that the amount may be subject to additional costs;
c. The Fees imposed by the correspondent bank or financial institution, if known;
d. A clear warning that there may be additional and significant costs charged by the receiving entities should there be Errors / omissions in the remittance information provided by the Consumer causing a rejection of, or delays in the transfer;
e. The estimated time for the funds to be transferred to the beneficiary with a warning box that the time taken to transfer funds can be delayed;
f. The name of the correspondent bank or financial institution, contact information and location where the funds will be available for collection by the beneficiary; and
g. Clear information on procedures for the cancellation of transactions by Consumers which must include the period of time within which the cancellation request can be made by a Consumer, the fact that exchange rate used for the refund of money paid by the Consumer may differ from the original rate used for the transfer, and any costs which could be incurred for the cancellation caused by the Consumer.
Post Transaction
2.1.5.6 Licensed Financial Institutions must include the following information in a receipt issued to its Consumers:
a. Licensed Financial Institutions who carry on money changing or wholesale currency activities:
i. The legal name and contact details (address, phone and email address of the branch) of the Institution;
ii. The date and time of the transaction;
iii. The remittance, transfer and foreign exchange product name;
iv. The serial number for the receipt;
v. The amount paid and the type of currencies tendered by the Consumer;
vi. The amount and the type of currencies issued to the Consumer;
vii. The rate of exchange applied and the buy and sell rate;
viii. The transaction Fees for services rendered to the Consumer including where possible charges that maybe levied by correspondent banks or financial institutions or agents;
ix. Terms and conditions and additional Consumer information as prescribed by the Central Bank; and
x. Information on how to file a Complaint with the Licensed Financial Institution which includes, at minimum, the contact details of the Licensed Financial Institution’s Complaint function, channels for lodging Complaints (e.g. by email, phone, fax etc.) and response time to address Complaints.
b. Licensed Financial Institutions who carry on remittance activities:
i. Requirements outlined in sub-clause a.;
ii. The name of the sender;
iii. The name of the beneficiary;
iv. The beneficiary bank account details (account number and branch name);
v. The destination country;
vi. The amount paid of funds to be remitted in AED and its equivalent in foreign currency to be received by the beneficiary;
vii. Where the correspondent institution is not a bank, the name of the correspondent institution or the name of the instant money transfer service provider through which the remittance is routed, contact information and location, where known; and
viii. Information on how to file a Complaint with the Licensed Financial Institution which includes, at minimum, the contact details of the Licensed Financial Institution’s Complaint function, channels for lodging Complaints (e.g. by email, phone, fax etc.) and response time to address Complaints.
2.2 Transparency
2.2.1 General Provisions for Transparency
2.2.1.1 The Consumer Protection Regulation and the accompanying Standards focus on the best interests of Consumers by ensuring that Licensed Financial Institutions:
a. Provide competent Advice that is sound, constructive and understandable;
b. Advise Consumers of all reasonable options, substitutes and choices available from the Licensed Financial Institution based on Consumer needs;
c. Eliminate the use of fine print and legal jargon;
d. Correspond in clear and plain language;
e. Explain the full impact of any risks, key restrictions and obligations;
f. Explain the possible negative impact of fluctuations in interest/profit rate and exchange rates on remittances, transfers and foreign exchange products and/or services; and
g. Disclose and explain any potential conflicts of interest between the Consumer and the Licensed Financial Institution.
2.2.1.2 Information must be timely, up-to-date and provided at each stage of the contractual process to ensure Consumers have the information required to facilitate informed decision-making.
2.2.2 Providing Comparative Information/Options
2.2.2.1 Before the sale of a Financial Product and/or Service, Licensed Financial Institutions must present all reasonable product comparisons/options for the type of products that are being considered by the Consumer. This will include comparison of benefits, options, pricing, Fees, risks, terminations costs etc. of the various Financial Products and/or Services that the Licensed Financial Institution offers.
2.2.2.2 Licensed Financial Institutions must not deliberately withhold or conceal the existence of reasonable alternative Financial Products and/or Services that may be appropriate to the Consumer including those with lower costs, financing rates and Fees.
2.3 Responsible Advertising
2.3.1 General Provisions for Responsible Advertising
2.3.1.1 This Section must be read in conjunction with Article 5: Business Conduct of these Standards.
2.3.1.2 Licensed Financial Institutions must apply these Standards to any Advertising activity through any and all channels, including branches, websites, mobile applications, ATMs, telephone banking, account statements, social media and public media comprised of any form of audio, visual and print content.
2.3.1.3 All advertisements must be available in both Arabic and English. At the discretion of the Licensed Financial Institution, other languages can be chosen based on the Consumer target market. Where advertisement is targeted to one linguistic market, Licensed Financial Institutions can target and tailor the advertisement for that linguistic market.
2.3.1.4 An advertisement by the Licensed Financial Institution must:
a. Be accurate, honest and understandable and not be misleading or contrary to actual factual information. An advertisement is misleading if, in any way, its presentation deceives or is likely to deceive the Person to whom it reaches;
b. Highlight key information and, display it prominently;
c. Ensure that all information, including footnotes, qualifiers, or disclaimers, is clearly visible, legible and understandable;
d. Ensure any footnotes, qualifiers, or disclaimers in Advertising are prominently and clearly displayed and of a font size that is clearly readable by Consumers;
e. Ensure that all written text and numbers are of a sufficient font size, minimum 10; and
f. Not contain any false statement of fact, or conceal important facts or information that may be deceptive or create a false impression.
2.3.1.5 An advertisement must be designed and presented in a manner that allows Consumers to immediately identify it as promotional material.
2.3.1.6 Where Licensed Financial Institutions advertise or promote any Financial Product and/or Service, they must disclose the name and logo of the Licensed Financial Institution and its contact details in a prominent manner in the advertisement. The advertisement must also provide the means and manner of easily accessing the details of any qualifying criteria the Consumer will need to meet before obtaining the Financial Product and/or Service. Where the full information is provided through a link on a Digital Channel, the link must provide the ability to re-direct Consumers specifically to the qualifying criteria relevant only for that advertisement/financial promotion.
2.3.1.7 Licensed Financial Institutions must ensure that Advertising or promotional material which contains acronyms (e.g. APR) clearly states the full form of the acronym.
2.3.1.8 When contacting or meeting Consumers, Licensed Financial Institutions’ sales and Advertising/marketing Staff must clearly identify themselves and the Licensed Financial Institution being represented.
2.3.1.9 Pursuant to 2.3.1.8 above, Licensed Financial Institutions must ensure that Advertising/marketing Staff explain the key terms, benefits and risks of the financial product being offered to Consumers.
2.3.1.10 Where Licensed Financial Institutions use advertisement or promotional material that:
a. Advertises any kind of bonus, gifts, points or any other incentives, such advertisement must clearly present and convey information that is required by these Standards to be disclosed. For special financial promotions, contests etc., all rules, entry instructions, dates or deadlines and factors likely to influence Consumers’ understanding of the financial promotion must be clearly stated and advertisements must explain these requirements accurately, unambiguously and completely. If it is not practical, for valid reasons, to include all such details in the advertisement, then the means, manner and channel of directly accessing the full information must be included in all material featuring the financial promotion;
b. Offers introductory low/zero cost Fees, interest/profit rates or pricing, Licensed Financial Institutions must clearly state the expiry date or the specific time period of such an offer and what the regular amount of Fees, interest/profit or pricing will revert to on expiry;
c. Advertises offers of interest/profit rates with terms such as “rates as low as” on credit/financing facilities or deposit/investment rates advertised as “rates as high as”, Licensed Financial Institutions must also state in clear and plain language the conditions, assumptions and chances of the Consumer receiving the lowest interest/profit rate on credit/financing or the highest rate for deposits or investments; and
d. Describes a Financial Product and/or Service as ‘free’, the Financial Product and/or Service must in its entirety be free of all Fees and/or interest/profit rates. If the financial product and/or service is ‘free’ for a certain time period, the advertisement must prominently disclose that the Financial Product and/or Service will not be free upon conclusion of the time period. The Consumer will be advised 30 calendar days in advance before being subject to the amount of expected Fees or the application interest/profit rates. The material must disclose if the product and/or service can be cancelled after the offer had been accepted by the Consumer. If cancellation is possible, disclose how to cancel and the Fees or penalties which apply.
2.3.1.11 Where Licensed Financial Institutions advertise or promote any Financial Product and/or Service that will require the payment of Fees, they must disclose the details of the fees in the advertisement. If it is not practical, for valid reasons, to include the fees in the advertisement, Licensed Financial Institutions must include:
a. An explanation of the means and manner of easily accessing the information in that advertisement; and
b. Where the complete information is provided through a link on a Digital Channel, the link must provide the ability to re-direct Consumers specifically to the terms and conditions or fees relevant only for that advertisement/financial promotion and that specific product and/or service. Key information must be prominently displayed. When the Fee is not a set amount, the disclosure must provide the basis on which the Fee is determined.
2.3.1.12 Advertising material must include statements to warn Consumers of the consequences of a Consumer’s failure to meet the conditions and requirements before and during his/her relationships with Licensed Financial Institutions. If it is not practical, for valid reasons, to include this information in the advertisement, Licensed Financial Institutions must apply the condition stated in Clause 2.3.1.11.b.
2.3.1.13 Licensed Financial Institutions must ensure that where advertisement materials include an Annual Percentage Rate, the rate must clearly be labelled as an Annual Percentage Rate and inclusive of all related Fees. It must clearly state if the interest/profit rate is fixed or variable. In the case of a fixed interest/profit rate, the tenor of the fixed interest/profit rate must be displayed. It must state any conditions on which the advertised rate is based upon.
2.3.1.14 Where Licensed Financial Institutions have a relationship with a Third Party provider for a particular Financial Product and/or Service, the Licensed Financial Institutions must disclose this fact in all advertisements for the advertised Financial Product and/or Service.
2.3.1.15 If advertisement material contains a statement, promise or forecast based on assumptions, Licensed Financial Institutions must ensure those assumptions are reasonable, up to date with market trends and clearly disclosed and labelled as assumptions in the advertisement.
2.3.1.16 Advertisements promoting the potential returns of a financial product must state that the forecast is for illustrative purposes only and is not indicative or construed as likely returns. A warning statement must be prominently displayed beside any statement regarding potential returns that states the potential risks of a loss as well. Any statement or forecast must not mislead at the time it is made.
2.3.1.17 Where the Advertising material does not refer to the benefits or returns but only names the Financial Product and/or Service and/or invites a Consumer to discuss the Financial Product and/or Service in more detail, a Licensed Financial Institution need not display the related warning statements required by Section 2.3 of Article 2: Disclosure & Transparency of these Standards.
2.3.1.18 Where the warning statements required by these Standards do not cover the Licensed Financial Institution’s products and services, the Licensed Financial Institution must devise their own with respect to raising awareness of potential risks associated with the product or service.
2.3.2 Advertisement of Deposit Products
2.3.2.1 Licensed Financial Institutions which offer Deposit Products must comply with all the requirements in Section 2.3.1 of this Article as applicable, in addition to complying with all the requirements of this Section.
2.3.2.2 Licensed Financial Institutions must ensure that where the interest/profit rate for a Deposit Product is quoted in advertisement materials, the advertisement materials must include the following:
a. Whether it is fixed or variable and if fixed, for what period of time;
b. Where more than one term (period of time) is advertised, it must disclose the relevant Annual Interest/Profit Rate for each term and each rate must be displayed in equal font size and prominence;
c. The minimum tenor and/or minimum amount required to qualify for a specified rate of interest/profit, if applicable;
d. The frequency in which the accrued interest/profit will be paid to the Consumer;
e. The basis on which the interest/profit calculation will be made (e.g. monthly/quarterly/annual compounding); and
f. Any other conditions that are required to be met in order to obtain the rate.
2.3.3 Advertisement of Credit Products
2.3.3.1 Licensed Financial Institutions which offer Credit Products must comply with the requirements in Section 2.3.1 of this Article as applicable, in addition to complying with the requirements of this Section of this Article.
2.3.3.2 When displaying the Annual Percentage Rate for a term loan/financing in advertisement materials, Licensed Financial Institutions must also display the total interest/profit and Fees to be paid over the term of the loan/financing by means of an example and disclose any conditions that are required to be met in order to obtain the rate. This provision does not apply to the provision of loans/financing for residential mortgages.
2.3.3.3 Licensed Financial Institutions must ensure that advertisement materials for a residential mortgage contain the following warning statement:
Warning: If you do not keep up your repayments/payments, you may lose your property.
2.3.3.4 Licensed Financial Institutions must ensure that advertisement materials for a loan/financing contain the following warning statement:
Warning: You may have to pay penalties if you pay off a loan/financing early.
Warning: If you do not meet the repayments/payments on your loan/financing, your account will go into arrears. This may affect your credit rating, which may limit your ability to access financing in the future.
2.3.3.5 Licensed Financial Institutions must ensure that advertisement materials for a debt consolidation loan/financing contain the following warning statement:
Warning: Refinancing your loans/financing may take longer to pay off than your previous loan/financing and may result in paying more in interest/profit.
2.3.4 Advertisement of Structured Products
2.3.4.1 Licensed Financial Institutions which offer structured products must comply with the requirements in Section 2.3.1 of this Article as applicable, in addition to complying with the requirements of this Section.
2.3.4.2 Licensed Financial Institutions must assess the suitability of the structured product to the targeted Consumer segment prior to launching the product advertisement and limit the Advertising to that appropriate Market segment.
2.3.4.3 Licensed Financial Institutions must disclose the name of the entity issuing the structured product in the advertisement and promotional material and the regulator of the structured product.
2.3.4.4 Licensed Financial Institutions must not advertise a structured product solely based on the projected or expected return of the structured product.
Where a Consumer may not receive 100% of the initial capital invested, Licensed Financial Institutions must ensure that advertisement materials for a structured product, contains the following warning statement:
Warning: If you invest in this product, you may lose some, all or more than the amount of money you invested.
2.3.4.5 Where the invested funds provide for early redemption, Licensed Financial Institutions must ensure that advertisement materials for the structured product contains the following warning statement:
Warning: If you cash in your investment before [specify the particular time], you may lose some or all of the money you invest and incur early redemption fees.
2.3.4.6 Licensed Financial Institutions must ensure that advertisement for a structured product where the funds are locked in i.e. no access to funds for the term of the product contain the following warning statement:
Warning: If you invest in this product, you will not have any access to your money for / until [insert time required before the product matures].
2.3.4.7 Where Licensed Financial Institutions give information about past performance when Advertising a structured product and/or service, this information must:
a. Be based on actual performance;
b. Be based on a structured product similar to that being advertised;
c. Not be selected so as to exaggerate the success or disguise the lack of success of the advertised structured product and/or service;
d. State the source of the information relied on regarding the performance;
e. State clearly the period chosen during which the actual performance occurred and how it relates to the structured product being advertised;
f. Include the actual performance during the most recent period;
g. Indicate, where they arise, details of all transaction costs, Fees and interest/profit that have been taken into account or not taken into account in the calculation of the actual performance; and
h. State, where applicable, the assumptions upon which the actual performance was calculated.
2.3.4.8 Licensed Financial Institutions must ensure that advertisement materials which contain information on past performance, must also contain the following warning statement:
Warning: Past performance is not a reliable guide to future performance.
2.3.4.9 Licensed Financial Institutions must ensure that advertisement materials which contain illustrations or information on simulated performance must also contain the following warning statement:
Warning: These figures are estimates / examples only. They are not a reliable guide to the future performance of this investment.
2.3.4.10 Licensed Financial Institutions must ensure that advertisement materials do not describe a structured product as guaranteed or partially guaranteed unless:
a. There is a legally enforceable contract with a credible Third Party who undertakes to meet, to whatever extent is stated in the advertisement and marketing materials, the Consumer's claim under the guarantee;
b. The Licensed Financial Institution has made and can demonstrate that it has made an assessment of the quality and value of the guarantee;
c. It clearly states the level, nature and extent of limitations of the guarantee and the name of the guarantor; and
d. Where it is the case, the advertisement materials must state that the guarantee is from a Third Party approved by a Licensed Financial Institution.
2.3.5 Advertisement of Remittances, Transfers and Foreign Exchange
2.3.5.1 Licensed Financial Institutions that offer remittance, transfer and foreign exchange products and/or services must comply with the requirements in Section 2.3.1 of this Article as applicable, in addition to complying with the requirements of this Section.
2.3.5.2 Licensed Financial Institutions must ensure that advertisement material contains the following warning statement:
Warning: Additional fees may be levied by the correspondent 0 22/00216121 institution or entity providing financial services to the beneficiary of remittances.
Warning: Penalties and Fees may be applied if there is a customer error or omission in providing correct or incomplete information for remittances.
2.3.5.3 Licensed Financial Institutions must ensure that where an advertised remittance, transfer and foreign exchange product and/or service is denominated or priced in a foreign currency, or where the value of an advertised remittance, transfer and foreign exchange product and/or service may be directly affected by changes in foreign exchange rates, the advertisement contains the following warning statement:
Warning: This product/service may be affected by changes in foreign currency exchange rates.
2.3.5.4 Where Licensed Financial Institutions advertise an attractive promotional foreign exchange rate, Licensed Financial Institutions must specify the period of applicability and any restrictions/conditions/assumptions associated with the offer.
2.3.5.5 Where the estimated time for completing a remittance is advertised, it must include the following statement:
Warning: The actual time to complete a transaction may differ from estimates due to increased scrutiny of transactions by the correspondent bank/financial institution or entity providing financial services to the beneficiary of remittances.
Article 3: Institutional Oversight
3.1 Institutional Oversight and Governance
3.1.1 Monitoring by Central Bank
General
3.1.1.1 Regulatory oversight of Licensed Financial Institutions by the Central Bank is an essential pillar of strengthening Consumer confidence and trust in the financial services. The Central Bank expects Licensed Financial Institutions to be effectively managed by establishing appropriate organizational oversight and structure, a supportive and constructive corporate culture, engaging well-qualified Staff, defining clear policies and procedures and creating proper monitoring and control frameworks supported by proper overall governance oversight.
3.1.2 General Provisions
Effective Institutional Oversight
3.1.2.1 Effective Oversight includes requiring Licensed Financial Institutions to:
a. Integrate into the management of the Licensed Financial Institution, the general principles which the Consumer Protection Regulation and the accompanying Standards are based upon;
b. Maintain effective Board governance and oversight of the management of conduct and compliance risks. With respect to the term Board and any assigned roles or responsibilities required by these Standards, these shall, for the purpose of licensed foreign bank branches, be the same requirements of the foreign bank branch representative or committee that have been designated by Licensed Financial Institution in accordance with the Central Bank Regulation on Corporate Governance;
c. Establish a governance structure that provides assurance and evidence that there is effective oversight of conduct risks. The governance structure must cover the breadth of the Licensed Financial Institution’s financial products, services and related Retail Operations including the use of Third Parties;
d. Develop and implement an effective control framework to manage conduct risks and ensure compliance with the Consumer Protection Regulation and the accompanying Standards. The control framework must be approved by the Board of the Licensed Financial Institution;
e. Develop, document and integrate conduct risk tolerance into the Licensed Financial Institution’s decision-making process and overall strategy;
f. Ensure the Licensed Financial Institution’s key control and assurance functions, Compliance, Risk and Audit, are each mandated appropriately for the identification, prevention, monitoring, detection, verification and mitigation/resolution of conduct and related risks;
g. Ensure all appropriate Staff are qualified at all times to perform their responsibilities and are competent in their understanding and application of the Consumer Protection Regulation and the accompanying Standards;
h. Establish management and Staff remuneration structures that promote responsible business and Market Conduct with the aim of preventing mis-selling practices, unreasonable risk taking, or other irresponsible actions and or behaviors;
i. Apply strict product and/or service approval processes that must be carried out before a new or updated Financial Product and/or Service is released to the Market;
j. Establish effective and efficient Complaint management processes and systems to ensure resolution, analysis and reporting of Complaints;
k. Implement appropriate control framework, security and monitoring measures to protect Consumers’ Data and information against misuse, unauthorized access and undue processing and analysis;
l. Establish a comprehensive Data collection process for Consumer Complaints and inquiries to enable effective trend analysis and the identification of issues regarding Financial Products and/or Services, non¬compliance matters, Staff misconduct and the fair treatment of Consumers. The Central Bank may prescribe templates to Licensed Financial Institutions to standardize Data collection, classification and reporting;
m. Instill a culture in the Licensed Financial Institution that promotes fair dealing, transparency and behavior that protects the interests of Consumers first;
n. Ensure the Licensed Financial Institution’s governance framework encompassing the above components is commensurate with the size, complexity and risk profile of the Licensed Financial Institution; and
o. Ensure that Islamic Financial Institutions comply with Islamic Shari’ah.
3.1.2.2 Licensed Financial Institutions must apply the principles and the requirements of the Consumer Protection Regulation and accompanying Standards to any new product or service, activity, action, change, event or any other situations.
3.1.2.3 Licensed Financial Institutions must file by January 31st each year an annual letter of attestation confirming compliance with Article 98 of the Decretal Law and specifically addressing matters related to Chapter 6 of the Decretal Law and the supporting Regulation and Standards. The letter must be filed by the Licensed Financial Institution’s most senior compliance officer and approved by the Board. The Central Bank may prescribe the form and details as to the content of the letter.
3.2 Governance of Retail Operations
3.2.1 Governance Framework - Roles and Responsibilities
The Board and Senior Management
3.2.1.1 Licensed Financial Institutions must have a Board approved governance framework in place that provides the Board with assurance and evidence that they have effective oversight and control frameworks over Retail Operations. The governance framework must detail the roles and responsibilities for all business, control and assurance functions as well as for the senior management.
3.2.1.2 The Board and Senior Management are responsible for overseeing conduct of the Licensed Financial Institution within the financial marketplace in which it operates. The Board must approve the Market Conduct compliance policy that states how the Licensed Financial Institution will comply with the regulatory principles. An annual report on Consumer Protection & Conduct Risk Management must be submitted to the Board or a Committee of the Board of the Licensed Financial Institution and the Board’s response must be documented.
3.2.1.3 The governance framework must specifically establish and maintain oversight over the design, production, Advertising, marketing, distribution and sales of Financial Products and/or Services with the objectives:
a. To minimize potential harm to Consumers;
b. Avoid potential Conflicts of Interest with Consumers; and
c. Ensure that the best interests and well-being of the Consumers are appropriately addressed.
3.2.1.4 The Board and Senior Management must adopt and promote a culture that will protect the interests of their Consumers by promoting principles of Consumer service, fairness, transparency and disclosure.
3.2.1.5 The Board and Senior Management are accountable for setting the culture and direction of the Licensed Financial Institution to align business practices with the consumer protection regulatory requirements. This requires concerted and wide-ranging measures, in particular:
a. Ensuring legal and regulatory requirements are being complied with;
b. Establishing complete and up-to-date control frameworks;
c. Executing effective monitoring, analysis and regular management reporting;
d. Ensuring competent frontline Staff, independent control and assurance functions and annually evaluating their effectiveness;
e. Establishing a Staff performance evaluation and remuneration system to promote and incentivize treating Consumers fairly;
f. Ensuring that Staff have the required qualifications and training to perform their responsibilities in a fully competent manner;
g. Establishing effective Complaint management, resolution, analysis and reporting;
h. Implementing comprehensive Financial Products and/or Services approval processes;
i. Ensuring accessibility to branches and ATMs by People of Determination;
j. Carrying out effective Consumer education and awareness programs; and
k. Addressing issues related to Conflicts of Interest.
3.2.1.6 As part of the Consumer Protection & Conduct Risk Management annual report required by Clause 3.2.1.2 the Senior Management must assess and report therein of their activities to support positive conduct and risk culture with evidence of support of the Consumer Protection Regulatory Principles. The review should also assess how Board and corporate messages about conduct and risk are permeated within the organization.
3.2.1.7 The Board and Senior Management must ensure independent control and assurance functions of Risk, Compliance and Audit are appropriately resourced to effectively execute at all times the Central Bank’s consumer protection regulatory framework and its supervisory requirements.
Control and Assurance Functions (Risk, Compliance and Audit)
3.2.1.8 Licensed Financial Institutions must have robust and effective controls to prevent inappropriate conduct and risks towards Consumers.
3.2.1.9 The Licensed Financial Institution’s control functions are required to be competent in the interpretation and application of the Consumer Protection Regulation and the accompanying Standards. The Board must clearly define the role and responsibilities of the control functions. They must jointly:
a. Be held accountable for supporting the Retail Operations by providing active oversight and challenge, not just performing an advisory role;
b. Be held accountable for their carrying out their assigned roles in the identification, prevention, monitoring, detection, robust controls and resolution of risks that Retail Operations create; and
c. Promote a corporate culture of protecting the best interests of Consumers first.
3.2.1.10 Licensed Financial Institutions must monitor compliance with the Consumer Protection Regulation and the accompanying Standards. The Licensed Financial Institution’s Compliance function must:
a. Inform and educate operational units of their responsibilities under the Consumer Protection Regulation and the accompanying Standards;
b. Ensure the Licensed Financial Institution’s code of conduct is complied with within the organization;
c. Conduct regular monitoring including mystery shopping, thematic reviews and Complaint Data analysis to monitor adherence to the Consumer Protection Regulation, the accompanying Standards and the Licensed Financial Institution’s code of conduct;
d. Ensure that individual Staff performance includes measurements of non-financial (qualitative) parameters that promote ethical conduct of Staff during their interactions with Consumers;
e. As a part of the Consumer Protection & Conduct Risk Management annual report required by Clause 3.2.1.2, evaluate and report on the state of the organization’s compliance culture and provide recommendations for improvements.; and
f. Escalate material non-compliance matters with the code of conduct and the Consumer Protection Regulation and the accompanying Standards to Senior Management and the Board, together with rectification plans. Such matters must also be reported to the Central Bank in accordance with Article (98), Clause 1.b in Decretal Federal Law No. (14) of 2018, Regarding the Central Bank & Organization of Financial Institutions and Activities.
3.2.1.11 Licensed Financial Institutions must conduct regular conduct audits of this area. The Internal Audit function must:
a. Independently assess the effectiveness and efficiency of the Licensed Financial Institution’s codes of conduct, the Consumer protection governance, systems, procedures and policies;
b. Independently assess the effectiveness of Retail Business line functions, Control functions and Senior Management in fulfilling their responsibility to effectively monitor and oversee conduct and regulatory requirements; and
c. Identify weaknesses in the effective implementation of control framework and regulatory requirements.
Risk Mitigation
3.2.1.12 Licensed Financial Institutions must:
a. Establish an approved conduct risk framework which enables them to identify, assess, monitor, mitigate and control conduct risk;
b. Define and document the risk appetite and risk limits that articulate the level and types of conduct risk the Licensed Financial Institution is willing to assume;
c. Develop mitigation strategies for the conduct risks that are identified; and
d. As part of the Consumer Protection & Conduct Risk Management annual report required by Clause 3.2.1.2, review and report on the type and level of conduct risks to the Board to ensure they are aligned with the Licensed Financial Institution’s risk tolerance and regulatory requirements.
Oversight of Financial Products and/or Services
3.2.1.13 Licensed Financial Institutions must have a comprehensive and effective product approval framework documented in policies and procedures that are approved by the Board of Directors.
3.2.1.14 The product approval framework must cover all new Financial Products and/or Services as well as subsequent amendments to existing products and/or services.
3.2.1.15 Policies must ensure inherent risks are properly assessed.
3.2.1.16 Policies must define all the pertinent procedures with checks and balances that must be complied with before a Licensed Financial Institution launches a Financial Product and/or Service into the financial marketplace. This includes defining the roles and responsibilities of each function involved in the creation, updating and launching a Financial Product and/or Service including the Control functions, the Retail Management, Legal services, marketing, Sales, Information - Technology services, etc.
3.2.1.17 The product approval process must include a documented sign-off by all relevant authorized Staff, Senior Management and Control functions.
3.3 Regulatory Reporting
3.3.1 Fees
3.3.1.1 Licensed Financial Institutions must submit their up to date schedule of fees and amounts annually to the Central Bank by January 31 of each year in a manner as may be prescribed by the Central Bank from time-to- time.
3.3.2 Financial Products and/or Services
3.3.2.1 Licensed Financial Institutions must report to the Central Bank annually by January 31st with the list of Financial Products and/or Services offered to Consumers in the UAE in a manner as may be prescribed by the Central Bank.
3.3.2.2 The Central Bank may require detailed information and Data on all Financial Products and/or Services offered by Licensed Financial Institutions. All Licensed Financial Institutions are required to comply with such requests within the stipulated timeframe.
3.3.2.3 Licensed Financial Institutions must submit an application to request a “No Objection Letter” from the Central Bank for any new or revised Financial Product and/or Service that the Central Bank may prescribe as requiring an application for a “No Objection Letter”. Where there is a requirement for a “No Objection Letter”, the CBUAE will establish appropriate turn-around times / response times.
3.3.2.4 The Central Bank will publish periodically its procedural time frames for the matters required to be submitted and considered by the Central Bank.
3.3.2.5 The application for a “No Objection Letter” by the Licensed Financial Institution must include information as may be prescribed by the Central Bank.
3.3.2.6 The Central Bank or The Higher Shari’ah Authority may issue additional guidance or standards for certain types of Financial Products and/or Services offered by Islamic Financial Institutions.
3.3.3 Undue Delays in Filing
3.3.3.1 Where Licensed Financial Institutions do not comply with the service standards established by the Consumer Protection Regulation and the accompanying Standards, or with any other time requirements for filing or reporting set by the Central Bank, Licensed Financial Institutions may be subject to enforcement measures.
Article 4: Market Conduct
4.1 Responsible Market Conduct
4.1.1 General Provisions for Responsible Market Conduct
Appropriate Market Conduct
4.1.1.1 To encourage Consumers’ trust in the safety and the integrity of the financial marketplace, Licensed Financial Institutions must conduct themselves with integrity and in a fair, honest, competent and transparent manner at all times.
Appropriate location for carrying out Business
4.1.1.2 When meeting Consumers in person on any location/premise for carrying out any business, the Licensed Financial Institution must ensure that the location/premise provides an appropriate physical space and environment that ensures confidentiality of the exchange of personal information and security in carrying out transactions.
Qualified Retail Staff
4.1.1.3 Licensed Financial Institutions must ensure that their Staff do not have any past criminal record for fraud or financial crimes or have been previously terminated for misconduct. Stated qualifications by Staff must also be verified.
4.1.1.4 Licensed Financial Institutions must ensure that Staff are appropriately qualified to fulfil their duties and remain at all times fit & proper.
Disclosure of Employer
4.1.1.5 Licensed Financial Institutions must ensure that their Staff clearly disclose their employee identification and whom they work for to the Consumer.
4.1.1.6 Licensed Financial Institutions must require Authorized Agents to ensure that their representatives disclose and explain to Consumers the relationship between the Licensed Financial Institution and the Authorized Agents.
Sales, Pricing and Financial Promotional Activities
4.1.1.7 Licensed Financial Institutions must act with integrity and in a fair, honest, transparent manner, and must take into account the best interests of Consumers in their sales and financial promotional activities. This Section must be read in conjunction with Article 5: Business Conduct of these Standards.
Monitoring of Market Conduct by Management
4.1.1.8 Licensed Financial Institutions must monitor their marketplace behavior of sales, marketing, financing / lending and advisory services. They must conduct and document, at minimum, monthly call backs on a sample of Consumers to detect any inappropriate conduct by Staff.
4.1.1.9 Licensed Financial Institutions must conduct regular mystery shopping and site visits of locations where the Licensed Financial Institution’s business is carried out in order to monitor and ensure that the Advertising, sales, financing / lending and advisory practices are conducted in line with their internal standards and control framework.
4.1.1.10 Monitoring must include collection and analysis of Consumer Complaints. Trend analysis reports from all monitoring activities must be reported monthly to Senior Management.
4.1.1.11 Licensed Financial Institutions must document their control framework for the monitoring activities described above. The findings and management reporting on monitoring must be documented and available to Central Bank for inspection on a demand basis.
4.2 Promoting Competition
4.2.1 General Provisions for Promoting Competition
Competitive and Level Playing Field
4.2.1.1 Licensed Financial Institutions must not collude to limit competition in any manner including the fixing of prices, fees, or limiting contract terms or financial product features which are not in the best interest of the Consumers. This provision does not include any Fee, tariff or premium/takaful contribution rates or policy/takaful certificate terms that have been approved by the Central Bank or any other lawful authority.
4.2.1.2 Collusion that results in detriment to Consumers must not be undertaken including actions such as:
a. Agreements between Licensed Financial Institutions to restrict the rate of interest/profit offered on Deposit Products for Consumers;
b. Setting lending/financing rates;
c. Setting currency and foreign exchange Fees, spreads and rates; and
d. Coordinated efforts among Licensed Financial Institutions to charge maximum allowable Fees regardless of differences in actual costs between Licensed Financial Institutions.
Promoting Consumer Mobility in the Marketplace
4.2.1.3 This Section must be read in conjunction with the Consumer Mobility Section of Article 5: Business Conduct.
4.2.1.4 Licensed Financial Institutions must not have policies, procedures, requirements, Fees or any other barrier that unfairly limits or delays Consumers in their ability to transfer their financial activities to another Licensed Financial Institution or other financial service provider of their choice.
4.2.1.5 Consumers must be permitted to close or switch accounts (current and saving account) without Fees any time after 6 months of opening the account with the Licensed Financial Institution.
4.2.1.6 Licensed Financial Institutions must facilitate the transfer of the Consumer’s Product and/or Services to another Licensed Financial Institution or other financial service provider by providing the necessary information, letters, certificates, etc. within the specified time frames in these Standards or as may be prescribed by the Central Bank.
Intervention by Central Bank
4.2.1.7 The Central Bank supports a fair and competitive marketplace but may intervene where abuse, unfairness, collusion and/or imbalance occurs. In accordance with the Decretal Law, intervention may include:
a. Setting limits on unfair Fees including Fees for early Financial Product and/or Service terminations;
b. Limitations on bundling of Financial Products and/or Services;
c. Limitations on interest/profit rates;
d. Limitations on specific terms and/or conditions in Consumer contracts;
e. Limitations on Advertising;
f. Limitations on policies and practices by Licensed Financial Institutions which have the impact of unfairly limiting Consumers’ ability to easily switch or close accounts in a reasonable time; and
g. Other matters the Central Bank may determine necessary to promote fair competition and uphold its Regulatory Principles and Standards and the protection of Consumers.
Article 5: Business Conduct
5.1 Responsible Business Conduct
5.1.1 General Provisions for Promoting Competition
General Requirements
5.1.1.1 This Article must be read in conjunction with Article 2: Disclosure and Transparency that sets out the related Disclosure and Transparency requirements applicable to this Section.
5.1.1.2 The Board and Senior Management must serve as positive role models in demonstrating the types of behavior expected by the principles set out in the Regulation. Positive behavior and actions should be aligned to the Consumer Protection Regulation and the accompanying Standards and reinforced by regular communication between Senior Management and Staff.
5.1.1.3 Licensed Financial Institutions must:
a. apply the principles of the Regulation in their business conduct by establishing appropriate standards of organizational behavior, control frameworks and functions, employee training; and
b. develop and provide appropriate Financial Products and/or Services that are focused on serving the best interests of the Consumer.
5.1.1.4 Pursuant to Article (123) in Decretal Federal Law No. (14) of 2018, Regarding the Central Bank & Organization of Financial Institutions and Activities, Licensed Financial Institutions must respect the Consumer’s right to access to all or part of Financial Products and/or Services from Licensed Financial Institutions suited to his/her needs upon presentation of adequate identification and in accordance with UAE laws and Regulations.
5.1.1.5 Licensed Financial Institutions must establish and track service performance standards for activities including time to open accounts, approval and disbursement of credit/financing facilities and funds, closure of accounts, issuance of documents including liability and clearance letters and time to acknowledge, respond to and resolve Consumer Complaints. The Central Bank may prescribe service performance standards with which Licensed Financial Institutions must comply.
5.1.1.6 Licensed Financial Institutions must endeavor to adopt the highest standards of practices to extend quality Consumer service and achieve high levels of Consumer satisfaction.
5.1.1.7 Responsible business conduct requires that the designing, marketing, sales and distribution of Financial Products and/or Services are appropriate for the targeted Consumer segments. There is a duty of care that requires Licensed Financial Institutions to determine the appropriateness and suitability of financial products for their clients and to protect Consumers from mis-selling.
5.1.1.8 All direct contact with Consumers for the purpose of Advertising/marketing communications must be conducted in accordance with any Applicable Laws and with the expressed consent and preferences of Consumers.
5.1.1.9 Unless Consumers have given expressed consent to ‘opt in’, they are regarded as having ‘opted out’ from receiving promotional communication of any kind. Consumers who have ‘opted out’ of receiving promotional communications must not be contacted by the Licensed Financial Institution with regards to future sales, Advertising or financial promotional activities.
5.1.1.10 Licensed Financial Institutions are prohibited from marketing loans/financing and other services offered to individual Consumers through direct contact by telephone.
5.1.1.11 Licensed Financial Institutions must conduct themselves in a professional manner at all times when dealing with Consumers. They must not be unreasonably persistent or place Undue Pressure on Consumers to purchase any Financial Product and/or Service.
5.1.1.12 Licensed Financial Institutions must not send direct Advertising and promotional material to Consumers under the age of 18 years.
5.1.1.13 Licensed Financial Institutions must have in place policies, procedures, controls and trainings that will assist Staff with a consistent approach to assessing the Consumer’s financial needs and objectives as well as carrying out an assessment as to the appropriateness, suitability and affordability of products and / or services. Any assessments conducted for profiling Consumers for the purposes of sales and marketing initiatives must be documented and retained for a minimum of 5 years. Only relevant information must be requested from the Consumer for carrying out such assessments and all information must be treated as confidential. The assessment and/or profile of the Consumer should be updated as appropriate by the Licensed Financial Institutions.
Best Interest of the Consumer
5.1.1.14 Licensed Financial Institutions must have a corporate objective clearly stated in its codes of conduct that it will work in the best interest of their Consumers.
5.1.1.15 Licensed Financial Institutions must, with due skill, care and diligence, act at all times with integrity and in a fair, honest and professional manner in their relationship with Consumers.
5.1.1.16 Acting in the best interest of Consumers starts from the beginning of any relationship with the Consumer and continues for as long as the Consumer remains with the Licensed Financial Institution. It includes assessing the Consumers’ financial needs, current and future financial situation, financial dependencies, attitude towards incurring risk and the Consumers’ level of literacy and understanding of the Financial Product and/or Service being requested or offered.
5.1.1.17 Where Financial Products and/or Services are not suitable or appropriate for certain groups of Consumers, Licensed Financial Institutions must not target those groups and must not carry out the distribution of marketing and sales efforts for such Financial Products and/or Services to those groups. This requirement must be considered in the product approval processes to ensure that the Financial Products and/or Services are fit for the targeted groups.
5.1.1.18 All Licensed Financial Institution Staff that provide Specific Advice on financial or investment matters must have the appropriate experience, current knowledge and qualifications to provide Specific Advice and to assess what is suitable for a Consumer.
Fees
5.1.1.19 Licensed Financial Institutions must comply with the directions issued by the Central Bank regarding the charging of Fees on products and services.
5.1.1.20 Licensed Financial Institution must not exceed the maximum Fee limits as prescribed by the Central Bank from time-to- time.
5.1.1.21 Licensed Financial Institutions must provide Consumers with a copy of the schedule of applicable Fees when providing a Financial Product and/or Service, signing a contract or as requested by a Consumer at any time.
5.1.1.22 Any increase of Fees that are capped by the Central Bank must not exceed the limit imposed by such caps. Please refer to the Maximum Limits for Fees Annexure contained in the Consumer Protection Standards
This paragraph has been amended by Notice No. (2535/2022). To view the previous version, click the version box below.Version 15.1.1.22 Licensed Financial Institutions must apply for and have Fee approval from the Central Bank in relation to any Fees for products and services that are subject to the authorities of the Central Bank. Fees or increases in fees must be appropriate and justified. Approval is required for:
a. Introduction of a new Fee;
b. Increases of any existing Fee greater than .5%
Any increase of Fees that are capped by the Central Bank must not exceed the limit imposed by such caps.
Refer to Maximum Fees Annexure contained in the Consumer Protection Standards.
5.1.1.23
This paragraph has been cancelled by Notice No. (2535/2022). To view the previous version, click the version box below.Version 15.1.1.23 The Fee approval application form and required documentation must be submitted to the Central Bank during the first 5 complete business days of April and October of any given year.
5.1.1.24
This paragraph has been cancelled by Notice No. (2535/2022). To view the previous version, click the version box below.Version 1(effective from 31/10/2018 to 02/01/2021)5.1.1.24 As an exception to Clause 5.1.1.23, the Central Bank will accept a Licensed Financial Institution’s application for approval of new Fees on an ad hoc basis where it is shown to the Central Bank's satisfaction that these relate to new Financial Products and/or Services. This will be assessed on a case-by-case basis.
5.1.1.25 Licensed Financial Institutions cannot impose a transaction or payment Fee on any transfers or payments between a Consumer’s accounts within a Licensed Financial Institution, including credit and payment card accounts issued by that Licensed Financial Institution.
5.1.1.26 Islamic Financial Institutions must comply with the specific Early Settlement Fee requirements prescribed by the Central Bank and comply with disclosure requirements as provided in Article 2: Disclosure and Transparency.
5.1.1.27 Pursuant to Article 2: Disclosure and Transparency, Licensed Financial Institutions must provide a statement to Consumers that includes clear explanation for Fees related to the Financial Products and/or Services held.
Cooling-off Period
5.1.1.28 When an agreement, in principle, has been reached with a Consumer to purchase a credit, insurance/takaful, structured product or any other product regulated by the Central Bank, the Licensed Financial Institution must provide the Consumer with copies of all related documentation and disclosures. Licensed Financial Institutions must inform the Consumer as to the right to a Cooling-off Period of 5 complete business days after the signing of the contract unless a longer Cooling-off Period is required/allowed for that product and/or service by way of other legal or regulatory requirements. The Consumer may be advised of the right to waive the Central Bank’s Cooling-off when permitted. For investment and structured products that may be price sensitive to the time of execution, Licensed Financial Institutions must warn Consumers about the potential change in pricing and costs that may occur when the Consumer requires the Cooling-off Period and that it may be unable to execute the purchase until the expiry of that period. Refer to Clause 2.1.1.31 and 2.1.1.32 of Article 2: Disclosure and Transparency.
5.1.1.29 The Consumer may choose to consult other persons including a lawyer or any advisor in order to make an informed decision. By the 6th business day, the Consumer must decide to choose to reject or negotiate an amendment to the contract or otherwise the contract may be in force in accordance with its terms and conditions.
5.1.1.30 If the Consumer decides not to proceed with the Financial Product and/or Service within the Cooling-off Period, Licensed Financial Institutions must refund any related Fees net of any reasonable and direct costs already incurred. The Licensed Financial Institution must have disclosed to Consumers in advance and in Writing, any details of those costs that could be deducted from the amount of refund.
5.1.1.31 With regard to transactions that require immediate implementation including foreign exchange, the Licensed Financial Institution must disclose such circumstances to the Consumer and that the Consumer will need to waive the Cooling-off option for the transaction to occur. Refer to Article 2.1.1.32 of Article 2: Disclosure and Transparency.
Consumer Mobility
5.1.1.32 Consumer Request for account closure: Upon receiving an account closure request from a Consumer, Licensed Financial Institution must:
a. Acknowledge in Writing within 2 complete business days, the account closure request by the Consumer;
b. Disclose to the Consumer the process for account closure;
c. Not exert Undue Pressure to cancel the request;
d. Not impose a closing fee / penalty if the account has been open for a period of 6 months or more;
e. With the exception of credit card, payment and investment accounts (as defined by the Central Bank from time to time), close all other accounts within the prescribed time limit of 7 complete business days from the date of the Consumer’s request. By the 8th business day, the Licensed Financial Institution must also:
i. Produce and provide the Consumers with all documentation including clearance and liability letters that are required to facilitate the closure and transfer; and
ii. Provide the Consumer with Written confirmation of the closure;
f. With respect to credit card and payment accounts, Licensed Financial Institution must close the account within 45 calendar days and provide the Consumer with Written confirmation of the closure except where there is a negative balance outstanding. The credit card / payment accounts should be frozen or blocked once the Consumer has requested the closure. During this interim period no unauthorized Fees can be charged.
Where an account cannot be closed due to an outstanding balance remaining after 45 calendar days, the Licensed Financial Institution must provide a written notice to the Consumer and may follow normal collection procedures.
5.1.1.33 Licensed Financial Institutions cannot require Consumers to provide information regarding their decision to transfer their financial activities to another Licensed Financial Institution or to require Consumers to provide information regarding the competing offer from the other Licensed Financial Institution. Consumers can be asked to provide this information only when the Licensed Financial Institution has evidence for suspecting a risk of financial crime.
5.1.1.34 Licensed Financial Institutions may communicate with and make offers to retain Consumers who wish to transfer or end their relationship with the Licensed Financial Institution. Any such offers by the Licensed Financial Institution in relation to the retention of the Consumer must be provided to the Consumer in Writing. Unless the Consumer withdraws the request for transfer/closure, the Licensed Financial Institution must complete the transfer/closure formalities within the prescribed time.
Service Interruptions
5.1.1.35 Licensed Financial Institutions must advise their Consumers in advance of any planned interruption to digital services of more than 4 hours, e.g. online banking, ATM system, card payment system. Such interruption includes any foreseen events, such as planned system updates and maintenance and must be properly planned to limit disruption to Consumers.
5.1.1.36 For unforeseen events where the interruption for services is expected to last more than 4 hours, a notice must be posted on the Licensed Financial Institution’s website if available and by way of sending a short message service (SMS)/email if possible. Where possible, Consumers must be provided with or advised of alternative service solutions during the interruption. The Licensed Financial Institution must inform and provide an incident report to the Central Bank when such an event is occurring.
Errors or omissions by Licensed Financial Institutions
5.1.1.37 Licensed Financial Institution must monitor and document the trends in Errors or omissions to identify systemic issues within the Licensed Financial Institution.
5.1.1.38 Where an Error or omission by the Licensed Financial Institution involves one or more Consumers, the Licensed Financial Institution must correct the Error or omission for all affected Consumers. When a Consumer has incurred a deduction from their accounts or incurs costs due directly to the Error or omissions, a refund must be paid to the Consumer immediately.
5.1.1.39 Licensed Financial Institutions must issue a communication to any affected Consumer within 10 complete business days of identifying the Error or omission to advise of the matter and the steps to be taken for corrective action, including the amount of the refund to be provided to the Consumer(s).
5.1.1.40 Licensed Financial Institutions must not benefit from any amounts due to their Error or omission. The full sum must be returned to the affected Consumer’s account or in cash immediately and without requiring an affected Consumer to register a claim with the Licensed Financial Institution or to agree to forgo their right for legal redress.
5.1.1.41 In case of Errors or omissions by the Licensed Financial Institution with respect to making timely foreign exchange transfers, the Licensed Financial Institution must not pass on the cost or differences associated with any change in exchange rates to the Consumers.
5.1.1.42 Licensed Financial Institutions must consider the cause of an Error or omission and ensure appropriate action is taken to mitigate the chance of re-occurrence. In case of a system wide Error or omission, the Licensed Financial Institution must immediately report the incident to the Central Bank with a description and explanation of the incident and corrective actions taken.
Unauthorized Transactions
5.1.1.43 Licensed Financial Institutions must provide appropriate and responsive digital and phone channels to assist Consumers 24 hours and 7 days a week to easily report loss, theft, fraud or misuse of their account and/or credit/payment cards/digital instruments.
5.1.1.44 The Unauthorized Transaction reporting service must have performance standards and tracking of responsiveness so as not to cause undue delay for the Consumer in blocking further Unauthorized Transactions. All calls or reports must be monitored and regular quality control checks must be conducted on these calls including monitoring waiting times and hang ups. Records of the monitoring must be retained for a period of 1 year. Licensed Financial Institutions must also document the action taken on poor service and performance. Response times towards Consumers must also be recorded.
5.1.1.45 All transactions will be considered as authorized if proper and secure validation procedures have been applied by the Licensed Financial Institution, unless prima facie evidence can be provided by the Consumer to establish reasonable doubt that the transaction in dispute was not executed by the Consumer.
5.1.1.46 For reporting Unauthorized Transactions, Consumers must be allowed a minimum of 30 business day to report the transaction to their Licensed Financial Institution after the Consumer has been properly informed of the transaction. When an Unauthorized Transaction is reported to a Licensed Financial Institution or an Authorized Agent, the Licensed Financial Institution must:
a. Document the reported transaction including date and time it is received and any pertinent information provided by the Consumer;
b. Inform the Consumer as to the options of blocking the account / credit/payment card/digital instrument while the matter is being investigated, having the account/card/instrument closed or cancelling and replacing the account /card/instrument; and
c. Take all appropriate actions deemed necessary to protect the Consumer from further Unauthorized Transactions.
5.1.1.47 Unauthorized payments must be reimbursed to the Consumer after the completion of the investigation or within 30 calendar days of the day the matter was first reported by the Consumer or identified by the Licensed Financial Institution, whichever period of time is shorter. This provision does not apply where there is evidence that the Consumer has acted fraudulently or with gross negligence.
5.1.1.48 If no Consumer transaction or payment authorization can be clearly confirmed and documented by the Licensed Financial Institution and there remains a dispute as to the liability and the quality of proof, the complaint shall be immediately referred to a complaint resolution mechanism.
Training, Competency and Ethical Conduct
5.1.1.49 The Board is ultimately responsible for ensuring that the Licensed Financial Institution’s business is conducted with due skill, care and diligence, integrity and in a fair, honest and professional manner towards Consumers.
5.1.1.50 Developing and maintaining the proper level of Staff competence must be integrated into a Licensed Financial Institution’s operational risk and conduct risk policies and be reflective of its corporate values and standards.
5.1.1.51 Where gaps in Staff competencies are identified and/or fail to meet qualification standards, a Licensed Financial Institution must address them immediately through additional education and training.
5.1.1.52 Licensed Financial Institutions must verify and document that their Staff (including Authorized Agents) are properly trained, qualified and fully understand their obligations regarding the Financial Products and/or Services being offered and the standards of assessing Financial Product and/or Service for appropriateness, suitability and affordability.
5.1.1.53 Licensed Financial Institutions must demonstrate compliance with the training requirements set out by other responsible UAE regulators of insourced products and services.
5.1.1.54 Licensed Financial Institutions must provide suitable training to all Staff to raise awareness of the principles and guidelines relating to treating all Consumers fairly including assistance to People of Determination. Specific sensitivity training programs and helpful aids must be designed for Staff that interact with these Consumers.
5.1.1.55 Licensed Financial Institutions must ensure that Staff, especially those who interact directly with Consumers, are required to update and enhance their professional knowledge through programs of professional development on an ongoing basis. The training must enable Staff to acquire and maintain the appropriate level of knowledge and competence.
5.1.1.56 The Central Bank may prescribe appropriate qualifications, training and development programs for the Staff of the Licensed Financial Institutions.
5.1.1.57 Licensed Financial Institutions must ensure Staff involved in the sale or marketing of any products or services from third parties including insurance/takaful products or structured / investment products must demonstrate appropriate and current qualifications and training requirements as set out by the responsible UAE regulator.
5.1.1.58 Licensed Financial Institutions must document and retain a record of an individual Staff person’s training and qualification while that Person is employed by the Licensed Financial Institution including Staff of Authorized Agents.
5.1.1.59 Licensed Financial Institutions must have in place, methods for ensuring all levels of Staff within Licensed Financial Institutions act with integrity, due skill, care and diligence in carrying and in a fair, honest and professional manner while carrying out their role and responsibilities.
Monitoring Performance and Remuneration
5.1.1.60 Licensed Financial Institutions must monitor Staff performance and competence during the course of the Staff’s work and their performance must be reviewed in the regular Staff performance appraisal at least once a year.
5.1.1.61 In response to changing circumstances, including Market developments, financial product innovation and changes in the regulatory requirements, Licensed Financial Institutions must monitor and review regularly the type and levels of competence that Staff are required to have in order to remain fit and proper for their role of serving Consumers.
5.1.1.62 Licensed Financial Institutions must ensure that their remuneration arrangements with Staff in respect of providing, arranging or recommending a Financial Product and/or Service to a Consumer, are not structured in such a way as to potentially impair the Licensed Financial Institution’s responsibilities to Consumers. The remuneration arrangements must provide incentives:
a. To act in the best interests of Consumers;
b. To carry out and apply in a competent manner the assessment of appropriateness, suitability and affordability requirements for all Financial Products and/or Services as set out in the Standards; and
c. To encourage responsible business conduct, fair treatment of Consumers and to avoid conflicts of interest.
5.1.1.63 Licensed Financial Institutions must have adequate policies, procedures and controls in place, so that Staff are not remunerated solely, or in large part, on criteria such as, but not limited to, volume of solicitations, sales, amount of credit financing. Staff performance assessments must include factors such as consumer satisfaction, loan/financing repayment/payment performance, loan/financing delinquency rates, consumer retention, substantiated Complaints, compliance with regulatory requirements/best practices guidelines and codes of conduct.
5.1.1.64 Effective Senior Management oversight is required to detect any biases or inappropriate behavior that may be caused by remuneration & incentive schemes. There must be monitoring of actions or activities that may indicate abusive practices such as the volume and type of Consumer Complaints, abnormal sales variance and trends, results of audit/compliance review, etc. Licensed Financial Institutions must be able to demonstrate that such monitoring is in place and effective. Corrective actions taken must be documented and available for review by the Central Bank.
5.1.1.65 Staff misconduct identified with respect to aggressive sales behavior and unfair or unethical treatment of Consumers must be addressed and taken into account during Staff appraisals/remuneration and promotional considerations. Licensed Financial Institutions must ensure and be able to demonstrate greater emphasis on proper conduct related performance indicators during appraisal/remuneration consideration of the Senior Management.
Sales, Marketing, Advertising and Financial Promotional Activities:
5.1.1.66 This Section must be read in conjunction with Section 2.3 of Article 2: Disclosure and Transparency.
5.1.1.67 Licensed Financial Institutions must not apply Undue Pressure or coercion on Consumers to purchase any Financial Product and/or Service.
5.1.1.68 Licensed Financial Institutions must not engage in marketing and / or sales conduct that is misleading or deceptive. The following actions fall within the prohibitive practices:
a. Making repeated solicitations through any channel of communications to promote Financial Products and/or Services to Consumers who have previously opted out of these communications and/or communicated their disinterest in the Financial Product and/or Service;
b. Conducting one or more personal visits to the Consumer’s home or workplace without the Consumer’s permission;
c. Exploiting a Consumer’s lack of knowledge, apathy or ability to understand the Financial Product and /or Service or the proposed transactions;
d. Falsely stating that the offer regarding Financial Products and/or Services that includes any promotional gifts, incentives, bonuses is only available for a limited time or is in limited supply, to elicit an immediate decision, when in fact there is no such limitation;
e. Misrepresenting conventional products as being Shari’ah-compliant funds or products;
f. Omitting material facts that are relevant for the Consumer to make an informed decision, including the use of small print to obscure such facts; and
g. Soliciting Consumers with incentives or attractive promises, for example financial promotions or gifts, when the Licensed Financial Institution is aware that it is not able to reasonably fulfil the demand for such promises.
5.1.1.69 Where Financial Products and/or Services are promoted or associated with a raffle/draw/lottery/give-away, the Licensed Financial Institution must ensure easy access to clearly disclosed rules, terms and conditions and any cost before registration in the promotional activity by the Consumer. Such an activity must be compliant with the rules and requirements (including prior authorization/approval) of any State law or regulatory authority.
5.1.1.70 Licensed Financial Institutions must not issue or distribute any marketing or sales information on Financial Products and/or Services publicly or to Consumers that:
a. Does not provide the required disclosure information and is not in the format as prescribed in this Regulation and its accompanying Standards;
b. Gives prominence to and/or exaggerates the returns on a Financial Products and/or Services without giving adequate or equal prominence to significant terms and conditions, risk warnings, or that obscures the terms or conditions, as this may mislead Consumers to form unrealistic expectations on the returns that will be earned;
c. Misrepresents the benefits, advantages, conditions or terms of any Financial Products and/or Services;
d. Misrepresents the actual pricing, costs or interest/profit rates for acquiring a Financial Product and/or Service; and
e. Misrepresents any incentives, gifts, bonuses offered to the public or an individual Consumer.
Solicitation
5.1.1.71 When Consumers are presented documentation that requests their approval for solicitations, Consumers must also be informed at the same time of their right to opt out at any time including any previously expressed consent granted to a Licensed Financial Institution regarding the distribution of sales or solicitation material and electronic messages sent to the Consumer.
5.1.1.72 Licensed Financial Institutions must not make unsolicited calls to Consumers by any means for the purpose of marketing their Financial Products and/or Services. Licensed Financial Institutions must obtain expressed consent from the Consumer if the Consumer wishes to be informed about Licensed Financial Institution’s Financial Products and/or Services through promotional contacts.
5.1.1.73 Exchange Houses must not solicit their Consumers or any other party for selling Credit Products on behalf of local or foreign banks or finance companies and must not be involved in or assist its Consumers or any other party to open bank accounts with local or foreign banks unless otherwise permitted by the Central Bank.
Consent for Financial Products and/or Services:
5.1.1.74 When a Licensed Financial Institution offers a Consumer a new Financial Product and/or Service through any channel, the Licensed Financial Institution must not interpret a Consumer's failure to respond or take an affirmative response or action as an affirmative consent to accept the new/modified Financial Product and/or Service, an option, or to be charged any Fee or other cost.
5.1.1.75 Licensed Financial Institutions cannot provide any new or optional Financial Products and/or Services to a Consumer without expressed consent provided by the Consumer.
5.1.1.76 If expressed consent is given verbally, the Licensed Financial Institution must provide the Consumer with immediate confirmation of the Consumer’s expressed consent in Writing and inform the Consumer that he/she retains the right of refusal as well as the 5 complete business days Cooling Off period. The confirmation must include a method of contacting the Licensed Financial Institution, should the Consumer subsequently decide to refuse the Financial Product and/or Service.
5.1.1.77 Where expressed consent is given, this Section must be read in conjunction with the sub-section on Cooling-off Periods in the Section 5.1.1 of Article 5: Business Conduct.
Bundling of Financial Products and/or Services
5.1.1.78 Licensed Financial Institutions must not apply Undue Pressure or coerce Consumers into obtaining a Financial Product and/or Service from them or anyone else as a condition for obtaining another Financial Product and/or Service from them.
5.1.1.79 Licensed Financial Institutions are allowed to offer Consumers, in conjunction with one of their Financial Products and/or Service, another Financial Product and/or Service on more favorable terms than they normally would, provided the more favorable terms are clearly disclosed. The Consumer has the right to acquire separately one of proposed bundled Products and or Services and forgo the favorable terms.
Accountability for Authorized Agents
5.1.1.80 Licensed Financial Institutions must have a fit and proper policy and perform appropriate due diligence and verification before contracting with their potential Authorized Agents or renewing contracts. These policies must be reviewed on a periodic basis. Licensed Financial Institutions must apply the fit and proper policy based on the type of activity being insourced or outsourced and document the process and results.
5.1.1.80 Licensed Financial Institutions are accountable and liable for ensuring that Authorized Agents remain fit and proper and fully understand the Licensed Financial Institutions’ control framework and agree to comply with all Applicable Laws and Regulations applicable to the Licensed Financial Institution.
5.1.1.82 Licensed Financial Institutions must ensure they include provisions in the contract that provides the Licensed Financial Institutions and the Central Bank the ability to access, verify and ensure compliance with all Applicable Laws and Regulations applicable to the Licensed Financial Institution.
5.1.2 General Provisions for Deposit Products
Current and Saving Accounts
5.1.2.1 Opening Accounts:
a. Commercial banks can open all types of accounts for their retail Consumers, but in such cases, they must abide by the Consumer Protection Regulation and the accompanying Standards;
b. Accounts must be opened within 2 complete business days from the date of application except as noted as follows. An exception is provided where the Licensed Financial Institution is acting accordance with UAE’s Financial Crime Compliance requirements. Where other valid circumstances require additional time to allow the account to function, the Licensed Financial Institution must explain the delay to the Consumer and document the reason for the delay. The account may still be opened and the low risk Consumer may be provided with the account number, however, the account may have limited transactions until the circumstances or the lack of certain documentation causing the delay are resolved;
c. Licensed Financial Institutions may refuse to open an account when the Licensed Financial Institution:
i. Has reasonable grounds to believe that the account will be used for transactions categorized as Suspicious Transactions by UAE’s Financial Crime Compliance; or
ii. Any reasonable and justifiable grounds;
d. When a Licensed Financial Institution refuses to open an account, it must provide a written notice to the Consumer immediately stating that the application to open an account has been refused and that the Consumer may file a Complaint with the Central Bank. The Licensed Financial Institution must internally document the specific reason for refusal for review by the Central Bank;
e. Licensed Financial Institutions must develop risk-based policies and procedures for account opening for Consumer accounts and in applying Know Your Customer (KYC) requirements. Such risk based policies and procedures should provide for account opening with limited features and Permissible transactions for low risk Consumers. Limitations may include limits on the number of transactions, the amount and types of transactions, prohibit transfers, remittances, use of cheques, etc. Licensed Financial Institutions must use their internal controls and monitoring to mitigate risks in account openings for Consumers; and
f. Licensed Financial Institutions must inform a Consumer of the requirements and procedures to open and operate a bank account. As part of the process, Licensed Financial Institutions must disclose to the Consumer all Fees that would be applied and ensure that Consumers are fully aware of the consequences of granting third parties access to their bank accounts, cheques or debit cards.
5.1.2.2 Account closure by the Licensed Financial Institution:
a. Licensed Financial Institutions must inform Consumers in Writing of their decision to close a Consumer’s account 60 calendar days in advance of the account being closed;
b. The Licensed Financial Institution must provide in Writing, the reasons for the closure except where the Licensed Financial Institution has suspicion as to the use of the account by the Consumer to carry out financial crimes; and
c. An exception is provided where the Licensed Financial Institution is acting accordance with UAE’s Financial Crime Compliance requirements.
5.1.2.3 Account blockage:
a. A Licensed Financial Institution must not block a Consumer’s account, block debit and/or credit transactions; hold funds or remove certain privileges for reasons other than the following or otherwise prescribed by the Central Bank:
i. The Licensed Financial Institution may block the Consumer’s account privileges and funds when the Licensed Financial Institution is acting in accordance with Central Bank’s request and/or relevant UAE laws and Regulations. (refer to Article 6.2.1.5). Licensed Financial Institutions must maintain detailed records of such events for review by the Central Bank;
ii. The Licensed Financial Institution may block the account, a privilege on an account or a determined amount of funds in a Consumer’s account for a set period of time in the following scenarios:
o A court order served on the Licensed Financial Institution to block the account and/or a defined amount;
o Upon instructions from the Central Bank;
o Recovery of amount of funds owed to the Licensed Financial Institution by the Consumer relating to credit facilities and/or unpaid Fees;
o Evidence that a Consumer has acted dishonestly, fraudulently, or is convicted of a crime; or
o Evidence that the Consumer has died.
b. When a Licensed Financial Institution blocks the use of a Consumer’s account, or blocks all or a defined amount of funds, or suspends certain privileges on an account, the Licensed Financial Institution must provide a written notice to the Consumer within 24 hours to inform the Consumer of the blockage details, the action the Consumer is expected to take and the contact information for the Licensed Financial Institution regarding the blockage. This provision is not applicable in instances when Licensed Financial Institutions have a reasonable basis of considering the transaction is related to risks of financial crime or as may be prohibited by law;
c. The Licensed Financial Institution must not:
i. Apply any account related Fees to a Consumer account that will result in an overdraft in the account while it is being blocked, including returned cheques Fees caused as a result of the blockage by the Licensed Financial Institution. Once the blockage has been removed, such fees may be collected and the Consumer informed;
ii. Block an amount of funds greater than the actual outstanding liability owed to the Licensed Financial Institution by the Consumer at the time of the blockage; and
iii. Block funds from a Consumer’s end of service payment for repayment/payment of a Consumers’ mortgage loan/financing.
Digital Instruments
5.1.2.3 Where there is an expiry date associated with a Digital Instrument product that stores or uses digital money, the Licensed Financial Institution that has issued the product must continue to provide a method of access to those funds and to safeguard any remaining balance of funds on behalf of the Consumer.
Debit Cards
5.1.2.5 Licensed Financial Institutions can issue debit cards in a secure manner that are linked to any type of accounts. They may charge approved Fees for issuance of new cards, replacement of lost cards or renewal of expired cards. However, they must disclose these Fees in the manner specified in Article 2: Disclosure and Transparency.
5.1.2.6 Licensed Financial Institutions cannot issue the Consumer’s initial debit card without expressed consent from the Consumer. Licensed Financial Institutions cannot issue a replacement for a lost or stolen debit card unless authorized by the Consumer. A replacement card can be issued automatically to the Consumer due to the expiry date of the current card or as agreed to by the Consumer. If the Licensed Financial Institution must issue new cards due to its own procedural changes, then the Consumer must be provided with a separate and advanced notice in Writing.
5.1.2.7 Licensed Financial Institutions must ensure that cards are issued and delivered to the Consumer named on the card, or to an authorized Persons as approved by the Consumer.
5.1.2.8 Licensed Financial Institutions must obtain the Consumers approval of the daily transaction limits that apply to the debit card for use with Automated Teller Machine (ATM) and Point of Sale (POS) transactions at time of issuing of the initial card or the reissuing of cards. If the Licensed Financial Institution has decided to reduce the limit of the Permissible daily transactions or the terms and conditions of the card, the Licensed Financial Institution must provide 60 calendar days’ notice in Writing to the Consumer and explain the change and what Consumers can do if they do not agree.
Automated Teller Machines and Point of Sale
5.1.2.9 Licensed Financial Institutions must fully investigate problems, Complaints and claims from Consumers, regarding incorrect transactions or any difficulties encountered when using any ATM or POS and where appropriate take corrective action:
a. In relation to provision of POS products or services, Licensed Financial Institutions must monitor whether the merchant clients impose any additional and unauthorized Fees onto Consumers when they use the Licensed Financial Institutions’ card/digital payment methods for the purchase of goods or services from the merchants; and
b. Licensed Financial Institutions must monitor for evidence of fraudulent use of ATMs and POS Terminals. Proof of the monitoring must be documented for review by the Central Bank. Where there is evidence of tampering with an ATM or POS Terminal, a Licensed Financial Institution must review its records and related Consumer Complaints for possible identification of past transactions previously deemed authorized transactions that need to be reversed due to the evidence of tampering.
5.1.3 General Provisions for Credit Products
5.1.3.1 Refer to Article 2: Disclosure and Transparency for applicable requirements.
5.1.3.2 The criteria for Business Conduct are prescribed by Article 7: Responsible Financing Practice of these Standards.
5.1.3.3 Licensed Financial Institutions must in accordance with Article 7 and without undue delay, allow Consumers to transfer their loan/financing from any bank or finance company operating in the UAE. Licensed Financial Institutions may require payment of an Early Settlement Fee as prescribed by the Central Bank.
5.1.4 General Provisions for Structured products
5.1.4.1 Refer to Article 2: Disclosure and Transparency for applicable requirements.
5.1.4.2 Licensed Financial Institutions are required to submit an application for approval with the relevant details and rationale of the proposed product to the Central Bank for consideration before selling and/or marketing structured products.
5.1.5 General Provisions for Remittances, Transfers and Foreign Exchange
5.1.5.1 Licensed Financial Institutions may impose Fees on Consumers for transferring funds external to the Licensed Financial Institution. These Fees must be a fixed amount and not a percentage of the amount being transferred.
5.1.5.2 Licensed Financial Institutions must inform the Consumer of the amount of their Fees before confirming the transfer of funds. The Consumer must be informed of the potential of Fees being charged by the receiving correspondent bank or financial institution. This Section is to be read in conjunction with Clause 2.1.5.5 of Article 2: Disclosure & Transparency.
5.1.5.3 Licensed Financial Institutions must be transparent and disclose options for low cost services for remittances of funds and avoid excessive Fees that may limit use by low income Consumers.
5.1.5.4 Licensed Financial Institutions must provide an official receipt of the transaction including details of all the Fees. Licensed Financial Institutions must ensure that the Consumers receive an official receipt for all the transactions in a manner that allows the Consumer to retain a record of the transaction details.
5.1.5.5 Licensed Financial Institutions are responsible for validating the accuracy of payment instructions, specifically the International Bank Account Number (IBAN) and Bank Identifier Code (BIC), before completing the transfer of the funds.
5.1.5.6 Licensed Financial Institutions must advise a Consumer within 2 complete business days of the return of funds by a correspondent bank or financial institution. The funds returned must be credited to the Consumer’s account as soon as received from the correspondent bank or financial institution. Where the Consumer does not have an account, the returned funds must be available in cash or by cashier’s cheque within the 2 complete business days. If Licensed Financial Institutions are required to undertake financial crime investigations, Licensed Financial Institutions are exempt from the 2 complete business days refund requirement.
5.2 Fair Treatment of Consumers
5.2.2 General Provisions for Fair Treatment of Consumers
5.2.2.1 The Board of Licensed Financial Institutions, must establish a control framework that articulates and demonstrates clearly its values and culture with respect to treating the Consumer fairly and address such matters as:
a. Good ethics, values and transparency in promoting and selling Financial Products and/or Services to Consumers;
b. Positive Consumers relations, Complaint management and Complaint resolution;
c. Assisting People of Determination;
d. Equal, Fair treatment of all Consumers;
e. Confidentiality and safeguarding of Consumers’ information and assets;
f. Addressing conflicts of interest;
g. Service performance standards that provide timely delivery of Financial Products and/or Services; and
h. Identifying and addressing Errors or omissions including systemic and administrative Errors/omissions expeditiously.
5.2.2.2 Licensed Financial Institutions must ensure Staff are provided with a copy of the Licensed Financial Institution’s Code of Fair Treatment of Consumers that summarizes the Licensed Financial Institution’s policy and procedures. Staff must be trained on the Code. Each year, Senior Management must send a reminder to all Staff of their responsibility to comply with the Code.
5.2.2.3 The Code of Fair Treatment of Consumer should be a basis for evaluating the annual performance of Staff.
5.2.2.4 Licensed Financial Institutions must monitor the performance of Staff regarding the fair treatment of Consumers by undertaking periodic mystery shopping, review of Consumer Complaints and annual Consumer satisfaction surveys.
5.2.3 Conflict of Institution’s Interest with Consumers
5.2.3.1 Licensed Financial Institutions must have in place and operate in accordance with a written Conflict of Interest policy appropriate to the nature, scale and complexity of the Licensed Financial Activities carried out by the Licensed Financial Institution. The conflicts of interest policy must:
a. Identify the circumstances which constitute or may give rise to a Conflict of Interest entailing a risk of harm done to the interests of its Consumers; and
b. Specify procedures to be followed, and measures to be adopted, in order to mitigate such conflicts and to address non-compliance.
5.2.3.2 Where conflicts of interest arise and cannot be reasonably avoided, Licensed Financial Institutions must:
a. Disclose the general nature and/or source of the conflicts of interest to the Consumer. Licensed Financial Institutions must only undertake those businesses with or on behalf of a Consumer where that Consumer has acknowledged in Writing that the Consumer is fully aware of the Conflict of Interest and agrees to proceed; and
b. In case a Conflict of Interest cannot be avoided, Licensed Financial Institutions must put in place proper disclosure and controls to mitigate them.
5.2.3.3 Where Licensed Financial Institutions distribute their Financial Products and/or Services to Consumers through an Authorized Agent and pay commission based on levels of business introduced, Licensed Financial Institutions must be able to demonstrate that these arrangements:
a. Are disclosed to the Consumer;
b. Confirm the agent’s duty to act in the best interests of Consumers;
c. Do not give rise to a Conflict of Interest between the agent and the Consumer and controls are set in place to mitigate any Conflict of Interest which may arise; and
d. Provide for effective monitoring for potential/actual abusive sales and disclosure practices.
5.2.3.4 Licensed Financial Institutions must ensure that there are effective controls in place between the different business lines of the Licensed Financial Institution, and between the Licensed Financial Institution and its connected parties, in relation to access and the use of personal information that could potentially give rise to a Conflict of Interest or abuse of Consumers’ Personal Data.
5.2.3.5 Licensed Financial Institutions must take reasonable steps to ensure that it or any of its Staff do not offer, give, solicit or accept any gifts or rewards (monetary or otherwise) that are likely to be perceived or are a potential conflict with any duties of the recipient in relation to his /her activities involving Consumers or/and the policies of the Licensed Financial Institution.
5.2.3.6 The Board of Licensed Financial Institutions must have in place adequate control framework to ensure that any Outsourcing or insourcing arrangement does not create situations of Conflict of Interest. Any Outsourcing or insourcing arrangement must be subjected to appropriate due diligence, fit and proper approvals and ongoing monitoring in order to identify and mitigate risks of any Conflict of Interest.
5.2.4 Fair Treatment of Financially Distressed Consumers
Debt Counselling
5.2.4.1 Licensed Financial Institutions must provide Consumers with qualified credit counselling services on debt problems and encourage Consumers to feel confident about approaching the Licensed Financial Institutions and openly discussing their financial concerns. When approached by a Consumer, the Licensed Financial Institution must give reasonable consideration to alternative arrangements that could enable Consumers to overcome their repayment/payment difficulties.
5.2.4.2 Licensed Financial Institutions must proactively provide assistance to Consumers when initial irregularities in payments are observed. Licensed Financial Institutions must encourage Consumers to reach out to them to discuss their financial difficulties.
5.2.4.3 Licensed Financial Institutions must ensure their counselling Staff is qualified and adequately trained to handle Consumers facing financial difficulties and treat them with respect and empathy.
Revised Payment Arrangements
5.2.4.4 Where Licensed Financial Institutions reach an agreement on a revised repayment/payment arrangement with a Consumer, the Licensed Financial Institution must, within 10 complete business days, provide the Consumer in Writing, with a clear disclosure and explanation of the revised repayment/payment arrangement. The Licensed Financial Institution will provide the Consumer with a copy of detailed and revised payment schedule, and a breakdown of how payments will be allocated to interest/profit and the outstanding balance owing. The Licensed Financial Institution must disclose to the Consumer that reporting relating to the Consumer’s Arrears must be shared with the Credit Information Agency.
5.2.4.5 Where Arrears arise on an account and a Consumer makes an offer of a revised repayment/payment arrangement that is rejected by the Licensed Financial Institution, the Licensed Financial Institution must internally document its reasons for rejecting the offer and communicate to the Consumer in Writing why the matter was rejected.
5.2.4.6 Licensed Financial Institutions must make the following information available for Consumers, including on a dedicated section of its website for debt management that provides the following:
a. General information to encourage a Consumer to deal with debt issues and problems of Arrears, and stating the benefits of doing so;
b. Licensed Financial Institutions’ contact information for Staff that deal with debt issues and Arrears management including Staff dealing with counselling;
c. Details on the Fees that may be imposed on Consumers in Arrears; and
d. Self-help tools for budgeting and managing money.
5.2.4.7 The information on the website must be easily accessible with a prominent link on the homepage.
5.2.5 Debt Collection Practice
General Requirements
5.2.5.1 Licensed Financial Institutions must have in place written policies and procedures for managing the collection of debts owed to the Licensed Financial Institution by a Consumer. To the extent reasonably possible, Licensed Financial Institutions must discuss financial difficulties with their Consumers before proceeding with collection efforts, redemption of collaterals/guarantees and/or taking legal proceedings. Licensed Financial Institutions must document these discussions.
5.2.5.2 Where an account is in Arrears, Licensed Financial Institutions must approach a Consumer, or through the Consumer’s authorized representative and discuss options that will assist the Consumer in resolving the Arrears.
5.2.5.3 Where an account remains in Arrears 30 calendar days after the date on which the Arrears first arose, Licensed Financial Institutions must immediately communicate with the Consumer to establish why the Arrears have arisen. At the Consumer’s request and with the Consumer’s expressed consent, Licensed Financial Institutions must liaise with the Consumer’s authorized representative who may act on the Consumer’s behalf in relation to addressing the Arrears.
5.2.5.4 Where an account remains in Arrears more than 60 calendar days after the date on which the Arrears first arose, Licensed Financial Institutions must immediately issue a notice in Writing to inform the Consumer, authorized representative and/or any guarantor of the loan/financing of the status of the account.
The information in the notice must include the following, as may be applicable:
a. The date the account fell into Arrears;
b. The number and total amount of repayments/payments (including partial repayments/payments) missed (this information is not required for credit card accounts);
c. The amount of the Arrears as of a specified date;
d. The interest/profit rate;
e. Details of any Fees in relation to the Arrears that may be applied;
f. Request that the Consumer begin engaging with the Licensed Financial Institution in order to address the Arrears;
g. The contact information for the responsible Person / function within the Licensed Financial Institution or where an external collection agent is assigned, the name and contact information of the authorized collection agent representing the Licensed Financial Institution;
h. The consequences of continued non¬ payment, including:
i. Where relevant, sharing of Data relating to the Consumer’s Arrears with the Credit Information Agency;
ii. Any impact the non-payment may have on other accounts held by the Consumer with that Licensed Financial Institution including the potential for off-setting accounts, where it is Permissible under existing agreed terms and conditions;
iii. Potential for the sale of collateral and security;
iv. Demand for payment from guarantors and co-signers;
v. Legal proceedings; and
vi. Continued accumulation of interest charges and related fees.
i. A statement that advises the Consumer to seek assistance from the Licensed Financial Institution for credit counselling and provides the contact details for the responsible Staff to provide the assistance.
5.2.5.5 Where Arrears persist, the Licensed Financial Institution must send the Consumer an updated disclosure notice of Arrears regarding the state of the Arrears. The notice of Arrears is to be sent monthly confirming any payments received by the Licensed Financial Institution or its Authorized Agent and the allocation of those payments between interest/profit, principle and related Fees as well as detailing the balance of accumulated payment Arrears, Fees and interests/profits and the outstanding balance owing on the loan/financing facility.
Communication with the Consumers
5.2.5.6 Licensed Financial Institutions must ensure that the frequency and manner of contact and communications of a Licensed Financial Institution with a Consumer regarding Arrears is proportionate and not excessive. A Licensed Financial Institution must apply a fair and due process when communicating with a Consumer before seeking recourse with competent judicial authorities, while observing the following:
a. A Licensed Financial Institution may communicate with a Consumer or his/her guarantor using the following approved methods:
i. E-mail;
ii. Registered mail;
iii. Courier;
iv. SMS messages;
v. Phone calls; or
vi. Such other method as consented to by the Consumer.
b. The Licensed Financial Institution must not:
i. Visit the Consumer’s place of employment or the Consumer’s home unless expressed consent is given by the Consumer or by permission of a court order;
ii. Visit the Consumer outside the hours of 9 AM to 8 PM; and
iii. Disclose any of the Consumer’s information to any Third Party other than a Credit Information Agency, an authorized debt collection agent, as may be legally required or where expressed consent is given by the Consumer.
c. In its attempts to contact a Consumer by telephone, a Licensed Financial Institution must not make unreasonable and excessive number of communication attempts /actual communications with the Consumer. Such attempts / actual contact must only be made during the hours of 9 AM to 8 PM. Where the Consumer has not been reached, a message should be left by the Licensed Financial Institution and/or authorized debt collection agent, so that the Consumer will have the ability to Call-back the same number used by the Licensed Financial Institution and/or authorized debt collection agent; and
d. During any communication with Consumer the communication message must include, at minimum:
i. The name of the Licensed Financial Institution and its collection department or authorized agent concerned with the collection of defaulted payments;
ii. The contact number of the concerned department / agent;
iii. Working hours of the concerned department; and
iv. Name of the employee / agent who contacts a Consumer through a phone call.
5.2.5.7 All communications with Consumers must be recorded and records maintained within Licensed Financial Institutions for 5 years after the credit amount due has been settled or the debt is written off.
5.2.5.8 A Licensed Financial Institution must inform the concerned Consumer, if it has appointed a Third Party to engage with the Consumer in relation to collection of Arrears and must disclose who the Third Party is, the amount that they are to collect and explain the authority granted to the Third Party to act on behalf of the Licensed Financial Institution including the receiving of payments.
Default on Residential Mortgage Loan/Financing
5.2.5.9 In respect of residential mortgages, where a full or partial repayment/payment is missed and remains outstanding and an alternative repayment/payment arrangement has not been put in place, Licensed Financial Institutions must notify the Consumer, in Writing, of the following:
a. The potential for legal proceedings for collection of payments and proceedings for repossession of the property;
b. The importance of the Consumer seeking independent Advice;
c. That, irrespective of how the property is repossessed and disposed of, the Consumer may remain liable for the outstanding debt after consideration of any proceeds of sale of a property and including accrued interest/profit, Fees, legal, selling and other related costs, as may be the case; and
d. The costs and Fees related to default proceedings charged to the Consumer must be fair, transparent and reasonable.
Licensed Financial Institutions must comply with the above requirements taking into consideration the characteristics of the underlying contracts for such financing.
Article 6: Protection of Consumer Data and Assets
6.1 Consumer Data Protection
6.1.1 Policies, Procedures and Systems
6.1.1.1 Pursuant to Article (120) in Decretal Federal Law No. (14) of 2018, Regarding the Central Bank & Organization of Financial Institutions and Activities, Licensed Financial Institutions must have policies, procedures and control frameworks regarding the collection, protection, confidentiality and authorized use of Consumers’ Data. Consumers must be informed in Writing with respect to how their personal information will be processed, e.g. collected, used, disclosed, Data mined and profiled.
6.1.1.2 Licensed Financial Institutions must protect Consumer Data and maintain the confidentiality of the Data, including when it is held, accessed or used by Authorized Agents.
6.1.1.3 Licensed Financial Institutions are responsible for ensuring Data protection and individual Consumer confidentiality with respect to any profiling, Data mining, marketing and sale of financial services through use of new technologies and social media.
6.1.1.4 Licensed Financial Institution must provide a safe, secure and confidential environment in all of its delivery channels to ensure a high level of confidentiality and privacy of Personal Data.
6.1.1.5 Licensed Financial Institutions have a legal obligation of confidentiality towards a Consumer except:
a. When disclosure of Consumer Data is properly imposed by a legal authority; or
b. When disclosure is made with the expressed consent of the Consumer, or through a representative nominated by the Consumer.
6.1.1.6 Licensed Financial Institutions must have a proper Data Management Control Framework with policies, procedures, system controls, and checks and balances to protect Consumer Data and to identify and resolve any incidents of information security breaches, when they may occur.
6.1.1.7 Where the Consumer’s identity verification is conducted online, the Licensed Financial Institution must apply more than one evidence of identity verification for electronic services. Licensed Financial Institutions must advise Consumers regarding any directed and repeated attempts of online fraud on their accounts for the Consumers to take additional precautions.
6.1.1.8 Licensed Financial Institutions must secure digital transaction processing and controls, implement detailed activity monitoring and enhance Consumer identification methods in accordance with the Central Bank’s requirements for strengthening Digital Channels.
6.1.1.9 Licensed Financial Institutions must provide employee training and awareness programs on their Data control framework for accessing and handling Consumer Data and reporting security and policy breaches. The Licensed Financial Institution must promote the importance of protecting Consumer’s Data as an ongoing responsibility of Staff with reminders sent on an annual basis.
6.1.1.10 Licensed Financial Institutions must ensure that access to personal information and Personal Data of Consumers is limited to authorized business lines and their Staff only. Licensed Financial Institutions must maintain logs for audit and supervisory purposes, recording the names of Staff who have accessed Consumer databases and the timing. Such records must be provided to the Central Bank as and when requested.
6.1.2 Data Management of Data Protection
6.1.2.1 The Board must designate responsibility and accountability for the Data Management and Protection function to a senior position in management who reports directly to Senior Management. The function is responsible for ensuring oversight of and compliance with the Data Management Control Framework and any related requirements for Data protection and privacy laws of the UAE and the Central Bank.
6.1.2.2 The Data Management and Protection function must ensure that:
a. Adequate monitoring and preventive controls are in place to detect any unauthorized or accidental loss, misuse, modification, access, disclosure or destruction of Personal Data;
b. Verifications are regularly carried out on the legitimacy of Data collection, access to Data, Data integrity and the electronic procedures and address any issues identified;
c. Controls are commensurate with the criticality and sensitivity of the relevant systems and Data handled; and
d. Detailed monitoring of records and the actions taken are maintained for 5 years.
6.1.2.3 The Data Management and Protection Function must:
a. Annually review and improve the adequacy of the Data Management Control Framework for the collection, classification, storage, usage, transfer, protection, correction and destruction of Personal Data;
b. Monitor, investigate and report to Senior Management any material incidents of accidental or unauthorized access, loss, alteration, transfer, destruction, use, modification or disclosure of Data; and
c. Participate in the handling and investigation of privacy related Consumer Complaints and must report the conclusion of the investigation to the head of the Complaint Management function, who will then correspond with the Consumer and provide the Institution’s findings in Writing.
6.1.2.4 The Data Management and Protection function must issue reports to the Senior Management and the Board on significant Data management violations and breaches immediately. Senior Management must ensure proactive measures are taken to address the violation / breach and to improve Data management systems and safeguard the confidentiality and privacy of Consumers’ Personal Data.
6.1.2.5 Licensed Financial Institutions must, without delay, inform their Consumers of unauthorized access to, and/or loss, destruction or alteration of Consumers’ Personal Data where it may reasonably pose a risk to the Consumer’s financial and personal security and/or where it may pose reputational harm to a Consumer.
6.1.2.6 Licensed Financial Institutions must notify the Central Bank immediately of all significant breaches of Personal Data.
6.1.3 Expressed Consent by Consumers
6.1.3.1 Licensed Financial Institutions must ensure Personal Data is:
a. Collected for a lawful purpose directly related to the Licensed Financial Activities of the Licensed Financial Institution;
b. Adequate and not excessive in relation to the stated purpose; and
c. Collected with appropriate security and protection measures against unauthorized or unlawful processing and accidental loss, destruction, or damage.
6.1.3.2 Before requesting the consent of a Consumer to share Personal Data, the Licensed Financial Institution must proactively disclose in Writing to a Consumer its intent to use and/or share Personal Data and with whom the Consumer’s Personal Data will be shared.
6.1.3.3 The Consumer must give his/her expressed consent freely and explicitly to a request for the use and/or sharing of Personal Data by the Licensed Financial Institution. The request for consent must be expressed in clear and plain language and inform the Consumer of his/ her right to refuse to provide expressed consent.
6.1.3.4 Licensed Financial Institutions must obtain informed and expressed consent before using and sharing a Consumer’s Personal Data for direct marketing or transferring the Personal Data to Authorized Agents for direct marketing. A copy of the expressed consent must be retained for 5 years after the relationship with the Consumer has terminated.
6.1.3.5 The Consumer shall have the right to withdraw expressed consent for the following at any time:
a. The processing of Personal Data by the Licensed Financial Institution except where Persona Data is required for business operations related to the Consumer’s Products and Services; and
b. Personal Data sharing with Authorized Agents and other third parties for purposes such as but not limited to sales and marketing.
6.1.3.6 Prior to a Consumer entering any contract with a Licensed Financial Institution, the Licensed Financial Institution must provide the following disclosures to the Consumer:
a. That Licensed Financial Institutions will only collect Data / Personal Data for a lawful purpose directly related to a function or activity of the Consumer;
b. Whether the collection is obligatory or voluntary for the Consumer to provide the Data / Personal Data;
c. Where it is obligatory for the Consumer to provide the Data / Personal Data, the consequences for the Consumer for failing to provide the Data / Personal Data as required;
d. A future withdrawal of expressed consent by a Consumer shall not affect the lawfulness of Data processing based on the prior expressed consent. Unless specified otherwise, the withdrawal must take effect within complete 30 calendar days of the Consumer requesting the withdrawal with the Licensed Financial Institution;
e. When Data / Personal Data of the Consumer is being processed by or on behalf of the Licensed Financial Institution, provide a description of the Data / Personal Data being processed;
f. When other external information on the Consumer is collected by the Licensed Financial Institution and the source of that Data / Personal Data; g. The Consumer’s right and means to request access to and to request correction of the Data / Personal Data and how to contact the Licensed Financial Institution with any inquiries or Complaints in respect of the Data / Personal Data; and
h. The choices and means the Licensed Financial Institution offers the Consumer for limiting the processing of Data / Personal Data.
6.1.4 Sharing with Authorized Agents
6.1.4.1 Licensed Financial Institutions must ensure that any Authorized Agent to whom some part or the entire delivery of the Financial Product and/or Service is outsourced meet the fit and proper policy regarding Data management and protection including secure handling procedures and applying proper controls.
6.1.4.2 Licensed Financial Institutions must ensure that access to a Consumer’s Personal Data by Authorized Agents is properly authorized in Writing by the Licensed Financial Institution, regularly monitored, and appropriately restricted in line with the purpose of the access given. All legal contracts with Authorized Agents relating to the Outsourcing of functions and services must include appropriate provisions for safeguarding confidentiality of Personal Data and must prohibit the unauthorized disclosure of confidential Personal Data by Authorized Agents. The Authorized Agents must report to the Licensed Financial Institutions Data Management and Protection function significant breaches of Personal Data. The Licensed Financial Institution’s obligation to protect all Consumer Data extends to the actions of all Authorized Agents.
6.1.4.3 Where Personal Data is shared and retained outside of a Licensed Financial Institution’s own network such as with Authorized Agents, Licensed Financial Institutions and Authorized Agents must use encryption techniques to suitably encrypt Consumer Data and take measures for the secure transfer of Data.
6.1.4.4 Licensed Financial Institutions are responsible for ensuring any outsourced technology using or retaining Personal Data meets the highest standards of security, encryption and protection and are regularly audited and verified for vulnerabilities.
6.1.4.5 In the event of a termination of an Outsourcing contract with a Third Party, Licensed Financial Institutions must ensure and be able to demonstrate that all Personal Data is either retrieved from the Third Party and/ or is destroyed.
6.1.4.6 Where the Consumer provided expressed consent to the Licensed Financial Institution for sharing Data to a Third Party, the Licensed Financial Institution must confirm in any contract with a Third Party that the Third Party has no further right to share the Data or use it for other unauthorized purposes unless required by the laws in UAE.
6.1.5 Sharing With Authorized Credit Information Agencies
6.1.5.1 Licensed Financial Institutions are required to provide Consumer Data to government- authorized Credit Information Agencies as may be prescribed. Consumers must be informed of this requirement and be advised as to the possible limitations of accessing future Financial Products and/or Services based on the Consumer records provided to these agencies.
6.1.5.2 Correction of Reported Credit Information:
a. With respect to any Errors, omissions or inaccuracies of Consumer information and Personal Data provided to the Credit Information Agencies by a Licensed Financial Institution, the Licensed Financial Institution must correct any Errors, omissions and inaccuracies within 7 complete business days of becoming aware of it;
b. For Personal Data unlawfully collected and reported by Licensed Financial Institutions, the Licensed Financial Institution must request the deletion of such Data in order to reduce the permanence of erroneous Personal Data in the Credit Information Agencies; and
c. When Consumers notify and request a Licensed Financial Institution to make updates or corrections to their Data reported to Credit Information Agencies, the Licensed Financial Institution must acknowledge receipt and verify if the request is accurate. If an update or correction is required, the Licensed Financial Institutions must report the update or correction to the Credit Information Agencies within 7 complete business days of the Licensed Financial Institution having been notified by the Consumer.
6.1.6 Standards for Retention of Consumer Records
6.1.6.1 All Personal Data, documents, records and files must be securely retained for a minimum of 5 years. The retention period begins, depending on the circumstances, from the date of the most recent of any of the following events:
a. Termination of the Business Relationship or the closing of a Consumer’s account with the Licensed Financial Institution; and
b. Completion of a casual transaction (in respect of a Consumer with whom no Business Relationship is established).
All Standards related to confidentiality and security must be maintained after the termination of the relationship until the Personal Data is destroyed.
6.1.6.2 Licensed Financial Institutions must not process or use Personal Data for any period longer than is necessary for the fulfillment of the purpose for which that Personal Data is required. After the lapse of the mandatory retention period for retaining Consumer records, Licensed Financial Institutions must take all reasonable steps to ensure that all Data / Personal Data is destroyed or permanently deleted if it is no longer required for the purpose for which it was collected and processed or no longer required by law.
6.1.6.3 All Licensed Financial Institutions must hold and store all Consumer and transaction Data within the UAE as prescribed by the Central Bank.
At a minimum, Licensed Financial Institutions must also establish a safe and secure backup of all the Consumer Data and transactions in a separate location for the required period of retention specified in Section 6.1.6.
6.1.6.4 Licensed Financial Institutions must ensure there is secure retention of Consumer Data that would prevent any unauthorized or accidental loss, misuse, modification, access, disclosure or destruction. Licensed Financial Institutions must review their procedures and methods for retention of Consumer Data on an annual basis.
6.1.7 Notification to the Central Bank
6.1.7.1 Where breaches of the Data Management Control Framework occur regarding the unauthorized access or release of Consumer Personal Data, the Licensed Financial Institution must record any disciplinary actions taken against any Staff, agents or contractors responsible for the breach. The Licensed Financial Institution must maintain records of such events for 5 years after the event being recorded. The records must be made available to Central Bank upon request.
6.1.7.2 Licensed Financial Institutions must notify the Central Bank of any material Data breaches, losses, destruction or alteration when they occur, in a manner, as may be prescribed by the Central Bank.
6.2 Protection of Consumer Assets, Information and Data against Fraud, Misappropriation and Misuse
6.2.1 Protection of Assets
6.2.1.1 Licensed Financial Institutions must ensure that they have clearly assigned responsibility and accountability for security of assets to Senior Management who must ensure internal control structures are in place and monitored including:
a. The proper segregation of duties, roles and responsibilities of management and Staff within the Licensed Financial Institution;
b. Operational risk mitigation;
c. Application of logistical access security;
d. Access rights and security on electronic Data and to assets;
e. Physical security of the Consumer assets and records; and
f. Completeness of documentation relating to business processes, policies, controls, and technical requirements in accordance with UAE’s anti-money laundering and terrorism financing guidelines.
6.2.1.2 Licensed Financial Institutions must implement stringent safeguards and verifications in order to protect unclaimed assets including the assets in the form of Stored Value Facilities, digital money, and dormant accounts and to ensure effective monitoring and reporting of any attempts to access them.
6.2.1.3 Collateral provided by the Consumer / guarantor must be properly secured and protected by the Licensed Financial Institution. The Licensed Financial Institution must act honestly, fairly and professionally and take into account the best interests of Consumer, while managing the collateralized assets.
6.2.1.4 Unclaimed Funds: Exchange Houses must ensure that unclaimed funds are assessed, documented, monitored and disclosed on a monthly basis as prescribed by the Central Bank.
6.2.1.5 Licensed Financial Institutions must have a robust internal risk based policy to update Consumers’ KYC documents, including expired identification documentation. Where Consumers have failed to respond to the Licensed Financial Institution’s written notices requesting the Consumer to provide required identification details to update the Licensed Financial Institution’s records, banks must after a notice period of 90 calendar days or after such period as may be prescribed by the Central Bank, temporarily block Debit & Credit Cards for all types of transactions, including ATM withdrawals. However, all other operations in the accounts of the Consumers are permitted through the branch. Licensed Financial Institutions must not levy any charges on such temporary blockage of the Consumers’ use of their cards.
6.2.1.6 Licensed Financial Institutions must undertake Consumer education initiatives and undertake fraud awareness campaigns every year and more frequently if there is evidence of heightened fraudulent activity.
6.2.1.7 Licensed Financial Institutions have an ongoing duty to educate and advise Consumers in Writing as to the security precautions that need to be taken to access their financial services including:
a. Avoidance of using simple passwords or numbers associated with personal dates;
b. The financial liability on the Consumers if they provide their password or personal identification number (PIN) to anyone or leave them written down and accessible to others to observe;
c. Advising Consumers on how they should and can change passwords and PINs periodically;
d. Cautiously entering the PIN at an ATM or POS Terminal to ensure they are not being observed; and
e. Protecting access to their cheque book.
6.2.1.8 Payment instruments/terminals (such as ATMs) and online banking channels must be progressively upgraded with the latest technology, particularly to prevent the use of counterfeit cards, and inspected regularly in accordance with the Central Bank’s guideline on preventing ATM Card frauds.
6.2.1.9 Licensed Financial Institutions must ensure ATMs are secure. They must:
a. Install and maintain pin pad shields to prevent the recording of Consumer PINs while using ATMs or POS terminals;
b. Install Anti-Skimming devices to prevent the magnetic stripe being read. Operators must immediately withdraw from service any ATM that has been compromised;
c. Install sensors to detect the presence of skimming devices and to send alerts to the operator and/or shutdown the ATM;
d. Ensure digital security cameras are within the ATM;
e. Apply any other advances in security as deemed necessary to protect Consumers; and
f. Monitor and investigate reported ATM issues from Consumers.
6.2.1.10 Licensed Financial Institutions must conduct periodic maintenance of all ATMs including verification of its proper functionality and ensuring security has not been breached (e.g. illegal keypad replicators and cameras). A record of the verifications on each machine must be maintained for a period of one year and made available for inspection by the Central Bank.
6.2.1.11 Licensed Financial Institutions may be liable for any direct losses incurred as a result of any breaches of the Licensed Financial Institutions’ security controls.
6.2.1.12 Licensed Financial Institutions must effectively perform and document their due diligence measures when verifying the background and competence of any Third Party that will represent the Licensed Financial Institution and/or have access to or possession of the Consumer’s assets, information and Data.
6.2.1.13 Licensed Financial Institutions must ensure their Authorized Agents have equivalent level of fraud control, coordination and monitoring for all activities performed by their Staff on behalf of the Licensed Financial Institution.
6.2.1.14 Licensed Financial Institutions must perform due diligence before hiring Staff and ensure verification of all fit and proper requirements are fully commensurate with responsibilities and functions of the positions.
6.2.1.15 Licensed Financial Institutions must provide adequate and up to date Staff training on its control framework to ensure Consumers’ assets are securely handled.
6.2.2 Fraud Detection
6.2.2.1 Licensed Financial Institutions must have adequate systems and processes in place to monitor and respond to external fraud activities commensurate with the type of risk associated with the Financial Product or Service and the frequency of Consumer transactions.
6.2.2.2 Licensed Financial Institutions must inform the Consumer of the procedures for reporting cases of theft, loss and fraud.
6.2.2.3 Licensed Financial Institutions must monitor and document trends on the number and type of incidents for fraud, attempted frauds and Consumer Complaints in order to determine if there is any evidence of weakness in the security and detection measures. Licensed Financial Institutions must report significant fraud events immediately to the Central Bank in a manner as it may be prescribed.
6.2.3 Fraud Investigation and Reporting
6.2.3.1 Licensed Financial Institutions must have a fraud reporting function to investigate Financial Crime Compliance.
6.2.3.2 When a specific pattern of frauds or deception is identified, a Licensed Financial Institution shall issue timely notifications to Consumers to promote awareness and preventative measures. The Licensed Financial Institution’s notice must provide a contact method for Consumers to report fraud incidents or make inquiries.
6.2.3.3 Licensed Financial Institutions must report all Consumer Complaints arising from external, internal and attempted frauds, as well as any apparent vulnerabilities in the security and online systems to the Central Bank on a quarterly basis.
6.2.3.4 Licensed Financial Institutions must file a summary annual report by January 31st to the Central Bank on the trends and significant incidents of fraud and attempted frauds including a description of the preventative measures taken.
Article 7: Responsible Financing Practice
7.1 Responsible Financing
7.1.1 General Provisions for Responsible Financing
7.1.1.1 This Article must be read in conjunction with Article 2: Disclosure and Transparency and Article 5: Business Conduct of these Standards and the Regulation regarding lending/financing and related services offered to Consumers.
7.1.1.2 The provisions of this Article apply to any form of lending/financing/Credit Products granted by Licensed Financial Institutions to Consumers through any channel of distribution (e.g. online, mobile apps, branch walk-in, etc.).
7.1.1.3 Providing lending/financing to Consumers must be subject to the credit risk policies of the Licensed Financial Institution. The Licensed Financial Institution must assess the ability of its Consumers to meet credit obligations and comply with Debt Burden Ratio (DBR) limits prescribed by the Central Bank.
7.1.1.4 The required Consumer assessments in these Standards assists in determining if a Borrower/Financee could meet both current and future repayment/payment obligations, thereby reducing issues of over indebtedness, insolvency and vulnerability to unexpected adverse events and income shocks.
7.1.1.5 Before granting any Credit Product, Licensed Financial Institutions must educate their Consumers by:
a. Explaining in plain language the application and approval process;
b. Explaining and providing a copy of the Licensed Financial Institutions’ offer to provide credit as well as the Key Facts Statement for the type of Credit Product being offered;
c. Clearly informing Consumers of any risks associated with the use of lending/financing, including the variance of interest/profit rates/costs, consequences of violating the terms and conditions, late payment Fees, Early Settlement Fees, for Shari’ah financing any Commitment to Donate to charity, etc.;
d. Explaining to Consumers and guarantors the implications of pledging any collateral, post¬dated payment cheques or other guarantees that are required in obtaining the loan/financing; and
e. Informing Consumers of the potential consequences of late payments or non¬payment of their liabilities. The consequences to be explained may include, but should not be limited to:
i. A negative Credit Information Agency rating and the possible limitations on the ability to borrow/obtain financing in the future;
ii. Collection measures involving collateral, collection Fees and claim on guarantees; and
iii. Legal actions through the courts.
7.1.1.6 Prior to offering, recommending, arranging or providing a Credit Product to Consumers for the purpose of consolidating / refinancing existing loan/financing, Licensed Financial Institutions must provide Consumers, in Writing, a comparison of the total interest/profit charged over the tenor of the loans/financing payable if they continue with the existing facilities versus the total interest/profit payable based on the consolidated facility being offered. Any assumptions used in calculations must be reasonable, justifiable and clearly stated and communicated. The comparison must be retained and a copy is to be provided to the Consumer for review during the Permissible Cooling-off Period.
7.1.1.7 Licensed Financial Institutions may agree to defer installment(s) as they deem appropriate, provided that such deferments do not result in the amount of future deductions from salary being in excess of the DBR percentage as prescribed by the Central Bank.
7.1.1.8 Licensed Financial Institutions must only take from the Consumer the number of post¬dated cheques covering the instalments and of value not exceeding 120% of value of the loan/financing or the debit balance. It is prohibited to take signed blank cheques. When one or more cheques are provided to the Licensed Financial Institution, the Licensed Financial Institution must provide the Consumer with a photocopy of all the properly completed cheques that were provided to the Licensed Financial Institution. The copies are to be stamped as accepted by the Licensed Financial Institution and given to the Consumer as proof of possession. When the lending/financing is paid off early, the remaining postdated cheques must be returned to the Consumer within 7 complete business days of the loan/financing being paid off.
7.1.1.9 Consumers can request a written confirmation at any time from their Licensed Financial Institutions confirming if there are any liabilities owing or not. Licensed Financial Institutions must provide a Consumer with a “letter of no liability” in such cases in accordance with Article 5: Business Conduct of these Standards. If liabilities are owed, the Licensed Financial Institution must instead issue a “letter of liability” stating the details and amounts of the liability still owing. The relevant letter must be issued to the Consumer within 7 complete business days from the date of the Consumer’s request.
7.1.2 Training and Remuneration
7.1.2.1 Representatives of the Licensed Financial Institution involved in providing lending/financing must be properly trained and qualified in assessing and approving the suitability, affordability and appropriateness of applications for credit/financing using established criteria and applying the Licensed Financial Institution’s lending/financing policies and procedures. Training of the Staff must cover the characteristics of the Credit Products sold/extended financing, identification of Consumer risks and procedures for carrying out proper verification of Consumer information.
7.1.2.2 The remuneration structure for Staff of the Licensed Financial Institutions must be designed to encourage responsible business conduct in lending / financing and fair treatment of Consumers and to avoid conflicts of interest. Refer to Article 5, Clause 5.1.1.62.
7.1.2.3 Licensed Financial Institution must monitor their sales representatives’ conduct to ensure they do not apply any unethical measures to profit from volume sales based incentives or commission based lending/financing objectives.
7.1.3 Consumer Assessment for Suitability
7.1.3.1 Staff of Licensed Financial Institutions responsible for assessing suitability and granting credit to Consumers must be qualified for the level of credit granting authority that the Person is authorized to give.
7.1.3.2 Suitability is defined as the degree to which the Financial Product and/or Service offered by the Licensed Financial Institution matches the Consumer’s financial situation, investment objectives, level of risk tolerance, financial need, knowledge and experience.
7.1.3.3 Where a Licensed Financial Institution is required to carry out an assessment of a Consumer regarding the suitability, affordability and/or appropriateness of a Credit Product and/or Service, a summary copy of the assessment must be provided to the Consumer without charge.
7.1.3.4 The Licensed Financial Institutions’ Consumer assessment control framework must include:
a. Methods for assessing the profile and circumstances of the Consumer for which a Credit product would be suitable; and
b. Clear lines of authority for approving the offer of a Credit Product and/or Service to a Consumer and the parameters for allowing exceptions from the assessment policy, procedures and established criteria. The basis for the approval or exceptions should be properly documented and supported with information relevant to the decision. Such approvals or exceptions should be subject to independent reviews by appropriate Control functions of the Licensed Financial Institution to ensure that they do not undermine the Consumer assessment procedures that are in place.
7.1.3.5 When providing a Credit Product, Licensed Financial Institutions must:
a. Assess the purpose of the credit/financing and the appropriate amount required;
b. Verify personal information, employment income and any other sources of regular income and revenue;
c. Assess the status of the Consumer’s credit worthiness including verifying information with the Credit Information Agency;
d. Provide General Advice on the appropriateness of the lending/financing request and provide any other reasonable options that the Consumer may or should consider; and
e. Not issue or bundle a credit card with the Credit Product or automatically increase a credit card limit, except upon expressed consent of the Consumer. Licensed Financial Institutions may offer a Consumer an increase in the limit of an existing credit card but must comply with the following:
i. Must perform a new check with the Al Etihad Credit Bureau for an updated credit history of the Consumer; and
ii. Must obtain expressed consent of the Consumer before applying the increase in credit/financing to the card.
7.1.3.6 Licensed Financial Institutions may decrease the credit limit on a card or close the card due to business reasons; Consumers must be provided a notice and the reason for limit decrease or closure.
7.1.3.7 If a Licensed Financial Institution engages in bundling of products and/or services with a Credit Product of any kind, it must provide the Consumer with the option to refuse the other bundled product(s) and retain the right to obtain the amount of credit based on the original offer from the Licensed Financial Institution. Offering Shari’ah compliant products and/or services must comply with the relevant Shari’ah requirements. The Licensed Financial Institution must disclose, in Writing, and explain the benefits of accepting a bundled product. As an exception, where credit insurance/takaful is a requirement of a proposed Credit Product, the Consumer must be informed in Writing that the Consumer must obtain the insurance/takaful from regulated companies proposed by the Licensed Financial Institution.
7.1.4 Consumer Assessment for Affordability
General Requirements
7.1.4.1 Affordability refers to the ability of a Consumer to reasonably afford the costs of existing and/or additional liabilities given the Consumer’s level of stable income, financial obligations/dependencies and basic personal and life style expenditures.
7.1.4.2 A Financial Product and/or service is considered affordable based on compliance with the DBR prescribed by the Central Bank as well as consideration of the level of basic personal and life style expenditures and other financial obligations and dependencies. Affordability assessment methodologies may be prescribed by the Central Bank.
7.1.4.3 Licensed Financial Institutions must assess the financial stability and needs of their Consumers before offering them a Credit Product. Licensed Financial Institutions must:
a. Assess that the Consumer will be able to make the payments without suffering substantial hardship given the Consumer’s financial, personal commitments and potential to retire in the near term;
b. Apply an appropriate level of stress testing to assess affordability given a scenario of increased interest /profit rates:
i. The results of the testing must be taken into consideration by the Licensed Financial Institution before granting the credit;
ii. If the stress testing results shows that the potential increase of a future interest/profit means the Consumer would exceed DBR set by the Central Bank, the Licensed Financial Institutions must document the reasons why they still provided the Credit Product; and
iii. Licensed Financial Institutions must provide a written summary of the results of the stress testing to the Consumer so that the Consumer is informed of the potential risks of an increase in the interest/profit rate. The Consumer must sign an acknowledgement of receiving the summary.
7.1.4.4 Licensed Financial Institutions must examine the credit record of the Consumer to verify his/her solvency, ability to meet monthly credit obligations and past credit behavior. The information obtained must be documented by the Licensed Financial Institution.
7.1.4.5 The Licensed Financial Institution must determine the level of affordability of a Consumer from the information collected by the Licensed Financial Institution including information provided by the Consumer and the Credit Information Agency.
7.1.4.6 A summary of the completed affordability assessment should be dated and signed by the Consumer and the Licensed Financial Institution credit granting Staff. The Consumer must be given a copy.
Debt Burden Ratio (DBR)
7.1.4.7 Licensed Financial Institutions must comply with the DBR prescribed by the Central Bank for Consumers. Licensed Financial Institutions must take reasonable steps to establish that Consumers are offered financing products that are appropriate to their financial circumstances and ability to repay by observing a prudent level of DBR. Licensed Financial Institutions must not grant excessive credit only on the basis of the Consumer’s affordability criteria (e.g. attempting to lend/finance in excess of what is required or requested by the Consumer).
Assessment of a Consumer’s Debt Repayment/Payment Obligations
7.1.4.8 Licensed Financial Institutions must conduct a comprehensive due diligence on the Consumer’s overall indebtedness by obtaining information on the Consumer’s outstanding debt obligations, including both secured and unsecured financing. Verification with the Credit Information Agency must also be completed.
7.1.4.9 With respect to the assessment of the Consumer’s credit application, the amount of credit to be approved, shall take into consideration the following:
a. The amount of the proposed scheduled repayment/payment of principal and interest/profit (including any Fees as part of the financing amount);
b. For interest/profit-only residential mortgages extended during the construction phase of new housing development projects, Licensed Financial Institutions must include both the principal and interest/profit payment that would apply at the end of the interest/profit- only period;
c. Where discounted interest/profit rates apply in the early part of a financing plan, the highest applicable rate that will apply to the financing at the point of assessment should be used. Should the higher rate result in payments that will exceed the DBR, this type of financing is not permitted;
d. Licensed Financial Institutions cannot use balloon structures/facilities to circumvent any existing or future forecasted DBR, personal loan/financing limits, or loan/financing to value ratio;
e. Where discounted rates and/or lower introductory payments are offered by re¬allocating a portion of the front-end interest/profit and/or principal by scheduling a large re-payment at a future point in time within the tenor (balloon payments), the Licensed Financial Institution must demonstrate and document how the applicable balloon payment will reasonably be within the Consumer’s DBR at that future date when it is due. Where it is not reasonable that the Consumer would be under the DBR when the balloon payment is due, this type of financing is not permitted and Licensed Financial Institutions cannot use balloon structures/facilities to circumvent any existing or future forecasted DBR, personal loan/financing limits, or Loan/financing to Value (LTV) ratio;
f. Where there is evidence of financing granted by the Consumer’s employer, friends, or relatives and any other finance that must be repaid through instalments on a monthly, semi-annual, or other basis, it must be considered in the assessments; and
g. Evidence of financial obligations such as being a guarantor on other debts, having margin and leveraged loans/financing for investments, court order payments, etc. must also be considered in an affordability assessment.
Income Assessment
7.1.4.10 In assessing income for the determination of the DBR, Licensed Financial Institutions must consider:
a. If variable income is taken into account, Licensed Financial Institutions are to evaluate the variability of such income and only include a prudent portion of the average amount as the Consumer’s income while assessing affordability. This flexibility should not be used to manipulate the DBR calculation. Where the Consumer has no permanent employment or is self-employed, Licensed Financial Institutions must evaluate the stability of the primary sources of income by requiring the Consumer to provide reasonable evidence of income;
b. Where a high month-to-month variance is observed for Consumers, a longer period of evidence of variable income than that specified in the previous paragraph must be applied to establish the amount that may be regarded as the Consumer’s stable income; and
c. The Licensed Financial Institution should exclude one-off variable income such as windfall gains in the assessment of income.
7.1.4.11 The Licensed Financial Institutions must obtain a signed confirmation from the Consumer identifying all his/her sources of income and existing liabilities.
7.1.4.12 Licensed Financial Institutions must, where reasonably possible, verify the Consumer’s income against reliable sources and must not rely solely on the Consumer’s self¬declaration of income. If the Licensed Financial Institution finds material discrepancies in the information provided by the Consumer, the Licensed Financial Institution must perform further verification. The Licensed Financial Institution must document its verification findings.
Assessing Life Style Expenditures
7.1.4.13 The concept of affordability considers the DBR calculation based on income but must also assesses the Consumer’s monthly basic personal and life style expenditures and obligations and whether they exceed the level of Disposable Income.
7.1.4.14 Licensed Financial Institutions must calculate the Consumer’s level of affordability by identifying and classifying the Consumer’s basic personal and life style living expenses as well any family and financial dependencies/obligations. The calculation should cover, at a minimum, the following groups of expenses as may be applicable:
a. Monthly food expenses, which are affected by the number of dependents;
b. Housing (rent) and maintenance services’ expenses, which depend on whether the Consumer is the owner or tenant of the house or otherwise;
c. Property taxes;
d. Wages to be paid for domestic workers;
e. Average Education expenses, which are affected by the number of dependents;
f. Average Healthcare expenses, which are affected by the number of dependents;
g. Travel expenses;
h. Insurance/takaful expenses (cars, health, life, property);
i. Utility, internet and mobile costs;
j. Child and spousal maintenance, support for extended family;
k. Costs of maintaining services of other owned properties; and
l. Any other expected costs or expenses.
7.1.4.15 With the calculation of the basic personal and life style expenditures, the Licensed Financial Institution must determine if it exceeds Consumer’s Disposable Income. A copy of the calculation must be given to the Consumer.
7.1.4.16 If the life style expenditures and dependencies exceed Disposable Income, the Licensed Financial Institution must discuss with the Consumer and evaluate whether the Consumer can make reasonable reductions in expenses, to an acceptable level. Such agreed to changes must also be documented and signed by the Consumer with a copy maintained on the Licensed Financial Institution credit file.
7.1.5 Terms of Financing
Financing Decision
7.1.5.1 Licensed Financial Institutions must comply with the DBR and loan to value (LTV) limits prescribed by the Central Bank when advancing loans/financing to the Consumers and must not lend/finance to the Consumer beyond his/her affordable limit. Licensed Financial Institutions must set a prudent level of DBR & LTV in their risk policies for financing decisions that allows sufficient buffers for expenditures and contingencies, having regard to the stress test results and the relevant circumstances of the Consumer. This may include appropriate consideration of the nature and security of employment, number of dependents, location of residence and other relevant factors that have a bearing on the Consumer’s financial obligations and the level of expenditures.
7.1.5.2 Licensed Financial Institutions must establish a control framework and systems that include the required financial assessment tools to measure the Consumer’s ability to meet monthly credit obligations and to what extent such Credit Products are suitable based on the Consumer’s profile, needs and circumstances.
7.1.5.3 Licensed Financial Institutions must ensure both the efficiency and effectiveness of their financial assessment tools that are used to measure the Consumer’s ability to repay the finance being provided.
7.1.5.4 The basis for a financing decision shall be properly documented and backed with information that supports the decision. This should facilitate internal risk management and supervisory reviews of the Licensed Financial Institution’s credit underwriting standards and compliance with these guidelines. The consideration of collateral alone should not lead the Licensed Financial Institution to extend financing to a Consumer who has otherwise been assessed by the Licensed Financial Institution to be unable to afford the financing.
Tenor of Financing
7.1.5.5 Licensed Financial Institutions must abide by the lending/financing tenor as prescribed by the Central Bank.
7.1.5.6 Licensed Financial Institutions must not increase the tenor of the loan/financing to decrease the DBR, with an intention to lend/finance further to the Consumer. For compliance purposes, the Central Bank will supervise loans/financing that have extended the tenor and increased the amount borrowed.
7.1.5.7 Licensed Financial Institutions must not purposely avoid the prescribed DBR by closing off a loan/financing as paid only to open another with an extended tenor and amount greater than the closed loan/financing. Licensed Financial Institutions must document from where the funds for the payment to close out the loan/financing came from.
7.1.5.8 Licensed Financial Institutions must provide borrowers / financees the funds approved on a Credit Product, except for mortgages and credit cards, within 10 complete business days of Consumer signing the contract or within such other time frame that is agreed to by the Consumer and specified in the financing contract. Complying with the period of time for making funds available by the Licensed Financial Institution is subject to the Consumer and / or third party providing the required and properly completed documents and meeting agreed to conditions. If it is not possible to release the funds in the agreed time limit, the Licensed Financial Institution must advise the Consumer in Writing immediately as to the reason for the delay and the date by which the funds will be available. As a consequence of any delay caused by the Licensed Financial Institution, the Consumer retains the option to cancel the contract without cost or penalty before the funds are to be made available.
Interest/Profit Rate
7.1.5.9 This Section should be read in conjunction with Article 2: Disclosure and Transparency of these Standards.
7.1.5.10 The Annual Percentage Rate (APR) which includes the total amount of the interest/profit payable and the cost of other Fees compounded over a year must be disclosed.
7.1.5.11 Licensed Financial Institution must not charge excessive margins or interest/profit rates.
7.1.5.12 Pursuant to Article (121) in Decretal Federal Law No. (14) of 2018, Regarding the Central Bank & Organization of Financial Institutions and Activities, Licensed Financial Institutions are not permitted to charge interest/profit on accrued interest/profit on any Credit Products granted to Consumers. In addition, Licensed Financial Institutions are not permitted to charge future unearned interest from the date of full early settlement of the credit facility. In the event of a partial early settlement, the interest must be proportionately adjusted based on the principal remaining.
7.1.5.13 Licensed Financial Institutions must calculate the APR/profit amount charged for the loans/financing and overdraft facilities as well as unpaid credit card balances using the Reducing Balance Method.
7.1.5.14 Licensed Financial Institutions, in case of credit cards, must not levy interest/finance Fees on the outstanding balance (excluding cash advance transactions) when the new balance outstanding shown in the statement is paid in full by the payment due date. In the event of part payment of the balance on or before the maturity date (excluding cash advance transactions), interest/finance fees are to be calculated on the outstanding balance from the period from the contractual due date to the date on which payment of the outstanding amount is made.
Fees on Financing Facilities
7.1.5.15 Refer to the Annexure on Maximum Limits for Fees and Commission Charged on Retail Customer Service of the Consumer Protection Regulations for the application of approved Fees.
7.1.5.16 Also refer to Article 2: Disclosure and Transparency and Article 5: Business Conduct of these Standards.
Article 8: Complaint Management and Complaint Resolution
8.1 Complaint Management and Complaint Resolution
8.1.1 Complaints Management Function
8.1.1.1 Licensed Financial Institutions must have in place a Consumer Complaint Management function situated in the UAE. A Licensed Financial Institution may combine this function with another suitable function within its organization depending on the nature, size, potential for Conflict of Interests, and complexity of the business.
8.1.1.2 The Complaint Management function must be independent of management of Retail Operations and able to carry out independent review of the escalated Complaints and make its recommendations to resolve a Complaint including provision of redress.
8.1.1.3 This Complaint Management function is responsible for:
a. Defining the Licensed Financial Institution’s Complaint handling principles;
b. Monitoring all channels for reporting Complaints;
c. Defining roles and responsibilities of units involved in the Complaint process including Retail Operations, Risk, Compliance, Audit, etc.;
d. Adhering to service standards for turnaround times (TAT) for each step of the Complaint process;
e. Providing governance, oversight and regulatory reporting;
f. Monitoring, analysis, reporting of all Complaints;
g. Promoting Complaint resolution and recommending appropriate redress by the Licensed Financial Institution for harm done; and
h. Escalation of Complaints to the separate Complaint Resolution Mechanism.
8.1.1.4 The Complaint Management function must ensure:
a. The Licensed Financial Institution’s written Complaint process and procedures are publicly available in branches and given to new Consumers with contact information including an email address and phone number for Consumers to file a Complaint. The email address and phone number must also be printed on all receipts handed over to Consumer, be present on the Licensed Financial Institution’s website and be displayed at a prominent location in the Licensed Financial Institution’s premises;
b. Easy and convenient access for Consumers to file a Complaint;
c. Proper processes for the registration all the Complaints received from the various channels, the classification and tracking of Complaints and the monitoring of TAT;
d. Acknowledgement of the Complaints with a unique service request (SR) number. The SR number shall be used for tracking and escalating the Complaints;
e. A written response is provided to the Consumer on the decision of the Licensed Financial Institution regarding the Complaint and include full and complete reasons for the decision, subject to lawful obligations;
f. The Consumer is informed in Writing if there is a violation of the TAT for issuing a final decision and provide the reasons;
g. The timed performance standards of the Licensed Financial Institution’s Complaint process are monitored and reported quarterly on the adequacy of the actual performance to Senior Management;
h. Potential breaches of the law are reported to the Licensed Financial Institution’s Compliance function without delay; and
i. The tracking and analysis of Complaint trends and issues and reporting to Senior Management on a monthly basis.
8.1.2 Filing of a Complaint
8.1.2.1 When the Consumer has verbally expressed dissatisfaction with a Financial Product and/or Service and the matter cannot be resolved by frontline Staff to the Consumer’s satisfaction, Licensed Financial Institutions must inform the Consumer of his/her right to file a written Complaint through the Licensed Financial Institutions’ Complaint management process.
8.1.2.2 When a Consumer’s dissatisfaction with a Financial Product and/or Service is verbally expressed but the Consumer does not wish to pursue it as a formal Complaint, Licensed Financial Institutions must maintain a log of the Consumer’s expression of dissatisfaction. The log will detail the date, issue and outcome and should form part of the analysis of the Licensed Financial Institution.
8.1.2.3 A Consumer may file a Complaint through various communication channels that the Licensed Financial Institution may have including, but not limited to, emails, calls or on-line portals.
8.1.2.4 When a Consumer wants to pursue a Complaint, the Complaint must be submitted to the Licensed Financial Institution. A Consumer may designate a person who is authorized by the Consumer to present a Complaint on the Consumer’s behalf.
8.1.2.5 A written acknowledgment of the Complaint filed with the Licensed Financial Institution must be given to the Consumer within 2 complete business days.
8.1.2.6 If for any reason the Complaint cannot be filed through the official channels provided, the Licensed Financial Institution must assist and document the Complaint on behalf of the complainant and register it under its Complaint management process.
8.1.3 Complaint Management Process
8.1.3.1 The Complaint Management Process and Staff training must take into consideration and apply the Licensed Financial Institution’s Code of Fair Treatment of Consumers.
8.1.3.2 Licensed Financial Institutions must have an efficient, well-resourced and dedicated phone line for Consumer Complaints and offer services on their secure web based portal system for receiving and communicating with consumers on the Complaints process.
8.1.3.3 Licensed Financial Institutions must have Senior Management approval of the Complaint management policies and procedures that:
a. Establish the role, responsibilities and authorities of the Complaint Management function;
b. Are clear, complete and accessible for retail Staff;
c. Establish the Licensed Financial Institution’s Consumer Complaint process that is simplified and Consumer friendly;
d. Address the confidentiality of Consumer Complaint information;
e. Require proper record keeping of Consumer Complaints including secure retention for 5 years;
f. Require ongoing training programs for retail management and Staff;
g. Centralize the monitoring, oversight and supervision of the Complaint management in the Complaints Management function;
h. Require reporting to Senior Management on the progress of Complaints and on noticeable trends; and
i. Establish performance time frames for each step of the Complaint process including those prescribed by the Central Bank.
8.1.3.4 Licensed Financial Institutions must set up effective procedures to monitor Complaints as specified in Section 8.2 of this Article and to make regular reports to their Senior Management for review (refer to Clause 8.1.1.4 g. and i). Information to be reported must include:
a. Statistics on the volume and type of Complaints;
b. An analysis on how well the internal Complaint management system meets prescribed performance standards;
c. The results of any survey, root cause analysis and verifications conducted to gauge the level of Consumer satisfaction on Complaints handling; and
d. Whether repetitive Consumer related problems are being effectively identified and corrected.
8.1.3.5 Licensed Financial Institutions must take appropriate steps to handle anonymous Complaints. Any problems alleged by the complainant and substantiated by investigation must be rectified as soon as possible.
8.1.3.6 Ensure that Complaints received are acknowledged as received within 2 complete business days and Consumers are advised of the Complaint process.
8.1.3.7 Within 30 complete business days of receiving a Complaint, or such other time limit as may be prescribed by the Central Bank, Licensed Financial Institutions must send the complainant in Writing, its final response with detailed reasons.
8.1.3.8 A final response from the Licensed Financial Institution must:
a. Clearly accept or reject the validity of the Complaint in whole or in part (and where appropriate state offers of redress);
b. Provide detailed reasons for the rejection except where the reason of rejection is related to obligations with respect to Financial Crime Compliance or as may be prohibited by law; and
c. Inform Consumers of the process for escalation of unresolved Complaints to the Licensed Financial Institution’s Complaint Resolution Mechanism.
8.1.3.9 Licensed Financial Institutions must have in place a verification process to monitor the fairness and adequacy of the Complaint management process and the decisions issued.
8.1.4 Resources and Training
8.1.4.1 Licensed Financial Institutions must make available the resources needed to ensure the efficiency and effectiveness of a Complaint management system.
8.1.4.2 Licensed Financial Institutions must take reasonable steps to ensure that all relevant Staff are aware of the internal Complaint handling procedures and that they act in accordance with them. In particular, the front line Staff must be provided with training on how to handle and process Complaints.
8.1.4.3 Licensed Financial Institutions must monitor the quality of how the Staff handles Complaints. The knowledge level and the service level standards for relevant Staff must be monitored on an ongoing basis and the standards set as Key Performance Indicators of the Complaint handling Staff.
8.1.5 General Provisions for Complaint Resolution
8.1.5.1 Recourse to a fair and efficient Complaint Resolution Mechanism must be made available by the Licensed Financial Institution free of cost to the Consumer to address Complaints that are not resolved. The Central Bank will supervise the fairness, effectiveness and efficiency of the Complaint Resolution Mechanism.
8.2 Complaint and Inquiries Management Data
8.2.1 Monitoring & Analysis of Data by Licensed Financial Institutions
8.2.1.1 Licensed Financial Institutions must carry out Complaint Data monitoring that includes information and related statistics on the following:
a. Complaints received, closed and pending on a quarterly basis;
b. Complaints substantiated;
c. Complaints acknowledged outside target time;
d. Complaints resolved and closed outside target time;
e. Overdue Complaints;
f. Complaints before the courts;
g. Complaints referred to the Licensed Financial Institution’s Complaint Resolution Mechanism;
h. Complainants who remain dissatisfied with the results of investigation of the Complaint;
i. The nature and the value of redress provided;
j. Suggestions from Consumers arising from Complaints; and
k. Errors / omissions identified as either Systemic or non-systemic Errors.
8.2.1.2 Details of all unresolved Complaints pending for each month must be reported to the Senior Management within 5 complete business days from the end of every month.
8.2.1.3 Licensed Financial Institutions must undertake root cause analysis to identify the source of Complaint, e.g. Staff conduct issue, financial product issue, system issues, systematic issues etc. The Licensed Financial Institution must take corrective measures expeditiously and without delays.
8.2.1.4 Complaints Data analysis must be augmented with thematic reviews, surveys and mystery shopping to develop a holistic understanding of Complaint trends.
8.2.1.5 In addition to Complaints being monitored, the Consumer inquiries received should also be analyzed as this type of Data provides information on common issues which may indicate poor disclosure material, a misunderstood Financial Product and/or Service or other common issues that raise Consumer inquiries.
8.2.1.6 The information gathered from the Data analysis, thematic reviews, mystery shopping or surveys must be utilized to improve the Licensed Financial Institution’s control framework and conduct.
8.2.2 Reporting of Data
8.2.2.1 Licensed Financial Institutions must submit semi-annual reports to the Board and the response from the Board must be recorded.
8.2.2.2 Senior Management must decide on the course of action that may be required based on the reports and information received and record all actions undertaken.
8.2.2.3 Licensed Financial Institutions must submit through the Central Bank’s Complaints Data Management System monthly reports on Complaint data by the 15th day of the month. Reporting must be in a manner and format prescribed by the Central Bank.
8.2.2.4 The Central Bank will hold periodic meetings with managers of the Licensed Financial Institution’s Complaints Management function to discuss the main trends and challenges and ways to address them.
8.2.3 Data Retention & Coverage
8.2.3.1 Licensed Financial Institutions must record and retain details of registered Complaints for a minimum period of 5 years from the date of resolution or closure, whichever is latest.
8.2.3.2 The details to be retained must include where applicable:
a. The complainant's name;
b. The substance of the Complaint;
c. The root cause of the Complaint; and
d. How the Complaint was resolved, and details of any redress offered by the Institution.
8.2.3.3 Such Data maybe requested by the Central Bank at its discretion.
Article 9: Consumer Education and Awareness
9.1 Consumer Education and Awareness
9.1.1 General Provisions for Consumer Education and Awareness
9.1.1.1 In support of Article (121), Clause 2 in Decretal Federal Law No. (14) of 2018, Regarding the Central Bank & Organization of Financial Institutions and Activities, Licensed Financial Institutions must establish a Consumer Education and Awareness (CEA) function responsible for educational and awareness programs for Consumers and the general public. All educational and awareness programs should limit the amount of promotion of the Licensed Financial Institution’s Financial Products and/or Services and refer to choices as to the types and characteristics of Financial Products and/or Services in a generic manner.
9.1.1.2 Licensed Financial Institutions may collaborate and / or coordinate programs with other organizations but must ensure their respective consumer base have full access to programs. A CEA function responsible for such programs must be designated within the Licensed Financial Institution.
9.1.1.3 By January 31st of every year, a Licensed Financial Institution must file a summary report with the Central Bank setting out its past year’s educational and awareness activities. The report must also contain its proposed program for the coming year.
9.1.1.4 The CEA function should, when feasible, test the content and delivery of all initiatives before customer / public release on a broadly representative sample of audience to ensure each initiative is suitable for its target audience and achieves its objectives.
9.1.1.5 The CEA function must conduct an annual review of its educational initiatives. The initiatives are to be assessed on their impact and reach. Based on the assessment of initiatives, the function should make adjustments as necessary.
9.1.1.6 The Central Bank may issue guidance recommending the focus, content or approach of the educational and awareness programs to be provided by Licensed Financial Institutions.
Article 10: Financial Inclusion
10.1 Inclusion
10.1.1 General Provisions for Inclusion
10.1.1.1 Vulnerable Consumers are Consumers who, due to their personal circumstances, are particularly susceptible to abuse, discrimination and harm, especially when Licensed Financial Institutions do not act with appropriate levels of fairness and due care. Vulnerable Consumers normally encompass low-income, Minority Groups, People of Determination or any other disadvantaged groups.
10.1.1.2 Licensed Financial Institutions must demonstrate to the Central Bank their compliance with the provisions of Federal Law No. (29) of 2006, In Respect of the Rights of People with Special Needs and any subsequent amendments or relevant laws.
10.1.1.3 Licensed Financial Institutions must ensure vulnerable Consumers have access to services provided by Licensed Financial Institutions on equivalent terms with others Consumer.
10.1.1.4 Licensed Financial Institutions must incorporate anti-discrimination principles into their internal code of conduct in accordance with Article 3: Institutional Oversight. The anti-discrimination principles are to ensure that Licensed Financial Institutions must, with due skill, care and diligence, act fairly, honestly and professionally in their relationship with all Consumers, regardless of their religion, gender, age, income level, and marital status.
10.1.1.5 Licensed Financial Institutions must ensure their public information is available in written, verbal and/or digital formats that are suitable to Consumers from vulnerable groups. The use of plain language content and method of delivery of information to such Consumers should be focus tested before distribution.
10.1.1.6 The Board and the Senior Management of Licensed Financial Institutions must ensure financial product and service design, business operations, premises and processes are made suitable and accessible to Consumers across different vulnerable groups.
10.1.1.7 Licensed Financial Institutions must review its Retail Operations annually for the purpose of identifying and eliminating any unreasonable barriers to the use of the Financial Products and/or Services that may be faced by Consumers who are People of Determination.
10.1.1.8 Relevant Staff of Licensed Financial Institutions must be trained on an annual basis to identify, assist and serve Consumers in vulnerable groups. Staff are expected to adhere to the Institution’s service standard for Consumers in vulnerable groups.
10.1.2 Inclusion of Vulnerable Groups
10.1.2.1 This Section must be read in conjunction with Fair Treatment of Financially Distressed Consumers of Article 5: Business Conduct of these Standards.
10.1.2.2 Pursuant to Clause 5.1.2.1 of Article 5: Business Conduct, Licensed Financial Institutions must be transparent and always disclose the lowest cost option of its Financial Products and/or Services to Consumers. Such Financial Products and/or Services include, but are not limited to, current, savings and/or call accounts. Licensed Financial Institutions should provide products and services that have minimum requirements such as minimum salary, minimum balance and can offer low fees.
10.1.2.3 Licensed Financial Institutions should respect the intended Consumer rights set out in Article (123) on Inclusion, Decretal Federal Law No. (14) of 2018, Regarding the Central Bank & Organization of Financial Institutions and Activities.
10.1.2.4 Licensed Financial Institutions should ensure branches and points of services used for public access and ATMs can accommodate the needs of vulnerable Consumers. The Central Bank may carry out periodic verification in line with the international standards of public access.
10.1.2.5 Licensed Financial Institutions must undertake regular reviews of all publicly available information and contracts to ensure that the content and delivery of information is suitable to People of Determination. All information regarding financial product features, risks, terms and conditions must be suitable for and comprehensible to vulnerable Consumers.
10.1.2.6 Licensed Financial Institutions must consider the provision of Financial Products and/or Services for residents in remote regions. Licensed Financial Institutions must assess when locating and relocating Consumer service location, the distance Consumers’ in remote locations must travel to access financial product and/or services and consider options to service those needs.
10.1.2.7 Licensed Financial Institutions must serve elderly and technologically illiterate Consumers with trained Staff and interactive guides to help them use mobile applications and online services. Service must include awareness of ways to protect Consumers from fraud and cyber-attacks.
10.1.2.8 Provision of services for Consumers who are illiterate and do not have a nominated representative must include, but not be limited to, audio information about financial products and contracts that do not exclude or distort any information to ensure that such Consumers make informed decisions.
10.1.2.9 Licensed Financial Institutions should inform illiterate Consumers that they may choose to conduct interactions with their Licensed Financial Institution in the presence of their trusted Person such as an advisor, family member or friend.
10.2 Gender and Racial Equality
10.2.1 General Provisions for Gender and Racial Equality
10.2.1.1 Licensed Financial Institutions, without prejudice to Data privacy and confidentiality, must regularly collect, analyze, and track Data aggregated by gender, income level, age and marital status in order to assess the differences in access to services and quality of services provided based on this Data. The analysis will identify any possible issues of inequality on the grounds of gender, income level, age and marital status. Licensed Financial Institutions must document its evaluations and findings for review by the Central Bank.
10.2.1.2 Licensed Financial Institutions must establish and implement a procedure to annually train Staff to provide service equally regardless of family status, gender, Minority Group status or age of Consumer.
Article 11: Shari’ah Compliance for Financial Services
11.1 Regulation on Shari’ah Compliance for Financial Services
11.1.1 General Provisions for Inclusion
11.1.1.1 Where IFIs offer Islamic Financial Products and/or Services, the Board and Senior Management must monitor and ensure that they are fully compliant with Shari’ah principles and governance. Shari’ah governance rules are set out in separate Regulation issued by the Central Bank.
11.1.1.2 ISSC is responsible for the Shari’ah compliance and the fairness of the Financial Products and/or Services offered by IFIs in accordance with the Shari’ah Governance Standard for IFIs.
11.1.1.3 IFIs must establish an effective and fair distribution of profit between the IFIs (shareholders) and investment accountholders (profit distribution mechanisms) in accordance with the applicable, relevant standards. IFIs and their respective ISSC should have effective oversight over profit distribution.
11.1.1.4 IFIs must integrate Shari’ah compliance into their culture, processes, operations and code of conduct.
11.1.1.5 IFIs must establish effective and independent oversight to ensure Shari’ah compliance throughout the organization.
11.1.1.6 IFIs must educate Consumers on the differences between conventional and Islamic financial products as well as the principles and the contracts that their Financial Products and/or Services are based on.
11.1.1.7 IFIs must disclose to Consumers the legal consequences of the contracts used in the financing provided to the Consumer.
11.1.1.8 IFIs must disclose to Consumers the legal consequences of their choices.
11.1.1.9 IFIs must ensure that the Consumers are presented with adequate information in regards to the Financial Products and/or Services they offer, including Shari’ah Certificates and grant access to the internal Shari’ah functions in case the Consumers have doubts about the Shari’ah compliance of the Financial Products and/or Services.
11.1.1.10 ISSC must ensure that obligation to pay charity in case of a Consumer's default is not abused by the IFIs and the relevant departments.
11.1.1.11 ISSC must ensure that the obligation set out above is not exercised if the Consumer is insolvent or bankrupt (not Mumatil).
11.1.2 Early Settlement Fee
11.1.2.1 IFIs must adhere to the Early Settlement Fee requirements set by the Central Bank and disclose this fact to their Consumers.
11.1.2.2 In the event that the Central Bank mandates the IFI to waive a part of the outstanding debt in case of early settlement, the IFI must comply with the Permissible limits of debt/liability IFIs are allowed to retain prescribed by the Central Bank in accordance with the relevant HSA resolutions.
11.1.2.3 Licensed Financial Institutions must not impose Early Settlement Fees except in relation to the actual costs incurred by the Licensed Financial Institutions as a result of the early settlement process and in accordance with the HSA resolution on early settlement No. (76/3/2019), and these principles should be considered in the product disclosure statements while ascertaining transparency and truthfulness of the information.
Annexure
Maximum Limits for Fees and Commissions Charged on Retail Customer Service
No. Product Fee Cap (AED) 1 Personal Accounts Account closure fee 100 2 Personal Accounts Account balance letter 50 3 Personal Accounts No liability certificate 60 4 Personal Accounts Release letter 50 5 Personal Accounts Liability letter issued to Gov't Departments/embassies 60 6 Personal Accounts Liability letter issued to financial institutions 60 7 Debit Card Issuing supplementary ATM Card 25 8 Debit Card Replacing Secret Pin Code 25 9 Debit Card Replacing lost or stolen ATM card 25 10 Debit Card Own ATM fees 0 11 Debit Card Fees for using other bank's ATM 2 12 Debit Card Copy of sales slip 25 13 Consumer Loans/Financing Delayed payment penal interest charges Max 200 14 Consumer Loans/Financing Early settlement from other bank loans 1% Max 10,000 15 Consumer Loans/Financing Final settlement from other sources/EOSB 1% Max 10,000 16 Consumer Loans/Financing Partial payment 1% Max 10,000 17 Consumer Loans/Financing Revolving overdraft fees 200 18 Consumer Loans/Financing Loan Cancellation Fee 100 19 Consumer Loans/Financing Other (loan copy, issuing redemption statements, audit confirmation 25 20 Car Loans/Financing Early settlement 1% outstanding 21 Car Loans/Financing NOC to Traffic Department 0 22 Car Loans/Financing Advance payment of instalment 1% of instalment 23 Car Loans/Financing Late payment penal charges Max 500 24 Car Loans/Financing Issuance of liability letter to other banks 60 25 Car Loans/Financing Cancellation fee 100 26 Remittance Swift copy charges 15 27 Remittance Demand draft/pay order issuance/cancellation 75 28 Customer Term Deposits Account closure fees-terms deposits Cost (max 2%) 29 Credit Cards Card replacement fee 75 30 Credit Cards Liability/no liability letter 50 31 Credit Cards Duplicate statement 45 32 Credit Cards Copy of sales voucher 65 33 Credit Cards Late payment fees Max 230 34 Home Loans/Financing Late payment fees Max 700 35 Home Loans/Financing Early settlement fees Max 1% of outstanding balance or 10,000, whichever is less 36 Home Loans/Financing Issuance of liability letter 85 37 Home Loans/Financing Other certificate 75 38 Home Loans/Financing Non-standard statement production/copy of original documentation 100 39 Home Loans/Financing Property swaps administration fee Max 1320 (valuation included) 40 Home Loans/Financing Issuance of NOC 150 41 Home Loans/Financing Partial Settlement Charges Max 1% of outstanding balance or 10,000, whichever is less 42 Home Loans/Financing Clearance letter 95 43 Home Loans/Financing Request of other letters 90 Small to Medium Sized Enterprises (SME) Market Conduct Regulation
C 1/2021 Effective from 26/2/2021Introduction
For achieving the Central Bank of the UAE’s objectives, the Decretal Federal Law No. 14 of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities permits the Central Bank to establish policies, and issue regulations and, as required, standards and guidelines relating to Licensed Financial Institutions.
In issuing this Regulation, the Central Bank is seeking to enhance access to Financial Products or Services for small and medium-sized enterprises (SMEs) in the UAE, through promoting appropriate market conduct by Licensed Financial Institutions when dealing with SME Customers.
This Regulation is issued pursuant to the powers vested in the Central Bank by the Decretal Federal Law No (14) of 2018 regarding the Central Bank and Organization of Financial Institutions and Activities.
Objective
The Regulation seeks to promote a culture within Licensed Financial Institutions of dealing with SMEs by defining the obligations of Licensed Financial Institutions when dealing with SME Customers that include:
- Setting standards of business and market conduct by Licensed Financial Institutions;
- Strengthening the governance and oversight over the design, promotion and sale of Financial Products and/or Services;
- Promoting responsible financing practices;
- Ensuring the quality and timing of effective disclosure to SME Customers by Licensed Financial Institutions regarding matters and/or risks that may affect an SME Customer’s decision to purchase a Financial Product and/or Service;
- Providing SME Customers with the access to the right information at the right time to make informed decisions;
- Promoting access to banking facilities for SMEs;
- Implementing clear and reasonable mechanisms by Licensed Financial Institutions for redress of SME Customer Complaints;
- Implementing appropriate debt counselling for SME Customers.
- Setting standards of business and market conduct by Licensed Financial Institutions;
Scope
This Regulation applies to all Banks and Finance Companies licensed by the Central Bank in relation to their activities specified in Article 65 of the Decretal Law No. 14 of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities in provision of Financial Products and/or Services to SMEs.
Where this Regulation includes a requirement to provide information or take certain measures or to address certain items listed as a minimum, the Central Bank may impose requirements that are additional to the listing provided in the relevant Articles.
The Central Bank may issue further requirements relating to this Regulation.
Article (1): Definitions
Authorised Agent: a commercial representative of a Licensed Financial Institution, which undertakes to enter into transaction in the name and for the account of, the Licensed Financial Institution. The Licensed Financial Institution shall be liable for any actions, transactions and contracts entered into by the authorised agent.
Bank: a juridical person licensed in accordance with the provisions of the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities, to primarily carry out the activity of taking deposits, and any other Licensed Financial Activities.
Bank Account: for the purposes of this Regulation, a Bank Account is a transactional basic business bank account that allows the making of payment, deposit and withdrawal of funds.
Board: a Licensed Financial Institution’s Board of Directors (Owners/Partners in the absence of a Board of Directors).
Borrower/Financee: a Customer to which a Licensed Financial Institution provides Credit as a Service and/or Product.
Central Bank: the Central Bank of the United Arab Emirates.
Central Bank Law: Decretal Federal Law No. (14) Of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities and its amendments
Complaint: an expression of dissatisfaction by a Small to Medium sized Enterprise with a product, service, policy procedure or action by the Licensed Financial Institution that is presented to the Licensed Financial Institution in writing or verbally.
Compliance of an IFI with Islamic Shari’ah refers to compliance with Shari’ah in accordance with:
- resolutions, fatwas, regulations, and standards issued by the Higher Shari’ah Authority (“HSA”) in relation to licensed activities and businesses of IFIs (“HSA’s Resolutions”); and
- resolutions and fatwas issued by Internal Shari’ah Supervision Committee (“ISSC”) of the respective IFI, in relation to licensed activities and businesses of such institutions (“the Committee’s Resolutions”), provided they do not contradict HSA’s Resolutions.
Customer: for the purpose of this Regulation, a Customer is a Small to Medium Sized Enterprise as herein defined who obtains or may prospectively obtain Financial Services and/or Products, with or without charge.
Credit Information Agency: Al Etihad Credit Bureau and any credit information agency established for the purpose of credit reporting requirements.
Credit products: products that provide funding including any advance, loan/financing or other facility in whatever form, including the giving of a guarantee or undertaking of any surety obligation for a Customer.
Fee: any fees, charges, penalties and commissions incurred on a Product and/or Service.
Finance Company: any juridical person licensed in accordance with the Finance Companies Regulation issued via Circular No. 112/2018 on 24/04/2018.
Financial Crime Compliance: includes compliance with, but not limited to, all applicable fraud, anti-money laundering, counter-terrorism financing, sanctions, bribery and corruption laws, rules and regulations.
This Regulation does not impose, reduce or modify any requirements pertaining to the compliance with all laws, rules and regulations relating to Financial Crime Compliance.
Financial Products and/or Services: Products and/or Services (including stored value facilities) provided by Licensed Financial Institutions, with or without charges, through their financial activities. It will be referenced to as Products and/or Services in this Regulation.
Higher Shari’ah Authority (HSA): The Central Bank’s Higher Shari’ah Authority for financial and banking activities, formed by virtue of the Cabinet’s Resolution No. (1/و5/102) of 2016 and referred to in article 17 of the Central Bank Law
Internal Shari’ah Supervision Committee (ISSC): An independent committee established within each Licensed Financial Institution that carries on all or part of its activities and businesses in accordance with the provisions of Islamic Shari’ah. Membership of this committee shall consist of experienced specialists in Islamic financial and banking transactions jurisprudence. The said committee shall undertake Shari’ah supervision of all businesses, activities, products, services, contracts, documents and conduct of business charters of the concerned institution and shall approve them and establish their respective Shari’ah requirements, within the framework of the rules, principles and standards set by the Higher Shari’ah Authority, in order to ensure compliance thereof with Shari’ah Fatwas or opinions issued by the Committee shall be binding.
Islamic Financial Institution (IFI): the Licensed Financial Institution that carries on all or part of its activities and businesses in accordance with the provisions of Islamic Shari’ah.
Licensed Financial Activities: The financial activities subject to Central Bank licensing and supervision as specified in Article (65) of the Central Bank Law.
Licensed Financial Institutions: Banks and Finance Companies licensed in accordance with the provisions of the Central Bank Law to carry on a Licensed Financial Activity or more, including those which carry on the whole or a part of their business in compliance with the provisions of Islamic Shari’ah, and are either incorporated inside the State, or have branches, subsidiaries or representative offices inside the State.
Market: the financial Market where Licensed Financial Institutions promote and/or sell Financial Products and/or Services and compete for Customers who are SMEs.
Market Conduct: Market Conduct is the focus on Licensed Financial Institutions' Market place actions, behavior and practices that are applied in providing Financial Products and/or Services to the market.
Permissible: any action that is specifically permitted by regulation or standards, or any actions which the Consumer is allowed by laws, rules and regulations to agree to and is confirmed by expressed consent.
Regulation: any resolution, legislation, circular, rule, instruction, standard or notice issued by the Central Bank.
Senior Management: the executive management of the Licensed Financial Institution responsible and accountable to the Board (or Owner/Partners where there is no Board of Directors) for the sound and prudent day-to-day management of the Licensed Financial Institution, generally including, but not limited to, the chief executive officer, chief financial officer, chief risk officer and heads of the compliance and internal audit functions.
Small to Medium Sized Enterprises: For the purposes of this Regulation, the words and acronym SME includes small, micro and medium businesses, provided that the businesses meet the thresholds of employee headcount and turnover, as defined by the Federal Cabinet Resolution No. 22 of 2016 which sets out the Small to Medium sized Enterprise definition for the purposes of Federal Law No. 2 of 2014 or any subsequent amendments to the Federal laws defining a SME:
a. Medium Enterprise:
Trading Sector 51 – 200 employees; or < AED 250 million annual revenues; Manufacturing Sector 101 – 250 employees; or < AED 250 million annual revenues; Service Sector 51 – 200 employees; or < AED 200 million annual revenues.
b. Micro Enterprise:
Trading Sector < 5 employees; or < AED 3 million annual revenues; Manufacturing Sector < 9 employees; or < AED 3 million annual revenues; Service Sector < 5 employees; or < AED 2 million annual revenues.
c. Small Enterprise:
Trading Sector 6 – 50 employees; or < AED 50 million annual revenues; Manufacturing Sector 10 – 100 employees; or < AED 50 million annual revenues; Service Sector 6 - 50 employees; or < AED 20 million annual revenues.Staff: one or more employee(s) of the Licensed Financial Institution or third parties acting in any capacity for or on behalf of the Licensed Financial Institution.
- resolutions, fatwas, regulations, and standards issued by the Higher Shari’ah Authority (“HSA”) in relation to licensed activities and businesses of IFIs (“HSA’s Resolutions”); and
Article 2: Disclosure and Transparency
- 2.1 Licensed Financial Institutions must provide information in a proactive and transparent manner to allow a Customer sufficient time to understand the information, including the terms and conditions.
- 2.2 All information on products and services aimed at and for Customers must have clear, transparent and consistent disclosures and comply with all applicable documentation requirements.
- 2.3 Licensed Financial Institutions must use plain language, information that is accessible and communicated in terms that are easily understandable. Licensed Financial Institutions must also use specific disclosure mechanisms, including warnings, to inform Customers of the key characteristics of and limitations on, accounts and other Financial Products or Services, including and not limited to risks, costs, fees, interest or profit rates, penalties, commitments to donate, tenure and locked terms relating to any Financial Product or Service.
- 2.4 Licensed Financial Institutions must provide effective disclosures at all stages of the relationship with the Customer. Customers must be made aware in advance of any permissible change in terms and conditions through all stages of the relationship.
- 2.5 In case of rejection of a Customer’s application for a Financial Product and/or Service by the Licensed Financial Institution, the Licensed Financial Institution must disclose the reason for rejection to the applicant except where the reason of rejection is related to Financial Crime risks or as may be prohibited by law.
- 2.6 Licensed Financial Institutions must not provide only partial or biased disclosure to entice a Customer by limiting the initial disclosure material that only presents the positive aspects of the product and/or service and only then disclosing the full characteristics of the product at the point of sale or post-sale, a point at which the Customer may feel obligated to complete the transaction(s) or do not have a recourse to exit the Product and/or Service post-sale.
- 2.7 Licensed Financial Institutions must regularly monitor and improve the effectiveness of their disclosures with techniques including and not limited to SME Complaint analysis and Customer satisfaction surveys.
- 2.8 Information must be available in both English and Arabic.
- 2.9 Licensed Financial Institutions should provide Customers with the signed documentations and contracts within a reasonable time.
- 2.10 Licensed Financial Institutions must ensure the accuracy of all disclosures made including the verification and correctness of statements made in such disclosures and any related calculation, assumption or reference.
- 2.11 Licensed Financial Institutions must promote, sell, distribute and manage Financial Products and/or Services in a responsible manner. Licensed Financial Institutions must take necessary steps to ensure that Customers are made aware of and understand the proposed terms and conditions prior to the final stage of the sales process or the time of signing of the agreement.
- 2.12 Licensed Financial Institutions must be transparent in their pricing and product structure.
- 2.13 A Licensed Financial Institution’s Board and Senior Management are responsible for providing direction and oversight to ensure that good disclosure practices for Financial Products and/or Services relating to SMEs are adopted throughout the institution.
- 2.1 Licensed Financial Institutions must provide information in a proactive and transparent manner to allow a Customer sufficient time to understand the information, including the terms and conditions.
Article 3: Responsible Conduct
- 3.1 Licensed Financial Institutions must monitor and uphold high ethical standards and practices when dealing with Customers.
- 3.2 Licensed Financial Institutions must prohibit and prevent abusive sales, marketing and pricing practices.
- 3.3 Licensed Financial Institutions must ensure disclosure, transparency and avoid anti-competitive and discriminatory practices and at all times have the controls in place to identify and manage conflicts of interest.
- 3.4 Licensed Financial Institutions must provide Customers with accurate, sufficient and consistent information for Customers to easily understand and to be able to compare products and/or services with those offered by other Licensed Financial Institutions.
- 3.5 Licensed Financial Institutions must not impose practices or barriers that prevent Customers from easily switching their relationship(s) between Licensed Financial Institutions at reasonable and disclosed costs and within a reasonable timeframe.
- 3.6 Licensed Financial Institutions are encouraged to engage with and put in place appropriate interface mechanisms with all available SME support schemes (such as credit guarantee schemes, movable collateral registry system or SME credit scoring services) provided by any Federal or Emirate-level government agencies and development banks.
- 3.7 Licensed Financial Institutions must ensure that all Authorised Agents comply with the applicable Articles of this Regulation.
- 3.8 Licensed Financial Institutions must, with due skill, care and diligence, act fairly, honestly and professionally in their relationship with Customers.
- 3.9 Licensed Financial Institutions must establish and maintain effective policies, procedures, systems and controls to avoid any potential, perceived or actual Conflict of Interest.
- 3.10 For inherent conflicts of interest, Licensed Financial Institutions must have controls in place and must provide full and proper disclosure to Customers prior to any agreements or commitments.
- 3.11 Licensed Financial Institutions must ensure ethical behavior of staff towards Customers by developing an internal code of conduct for the staff, providing regular relevant training and monitoring Complaints.
- 3.12 Licensed Financial Institutions must ensure that the staff who directly interact with Customers will competently, efficiently and professionally discharge their duties and provide prospective and existing Customers with the information and services they are entrusted to provide or sell.
- 3.13 Licensed Financial Institutions staff dealing with Customers must have sufficient knowledge of the products and/or services being offered.
- 3.14 Licensed Financial Institutions must ensure that staff dealing with Customers are suitably qualified to provide advice and carry out transactions.
- 3.15 Licensed Financial Institutions are responsible for the actions of their staff. Licensed Financial Institutions’ must maintain appropriate monitoring of staff in relation to their standards for business conduct and to ensure full compliance with codes of conduct, laws and regulations.
- 3.16 Licensed Financial Institutions must not adopt abusive or unreasonable contractual terms.
- 3.17 Licensed Financial Institutions must monitor for misleading or aggressive sales practices and exploitation of Customers due to their vulnerabilities, apathy or lack of knowledge.
- 3.18 Licensed Financial Institutions must provide impartial credit counselling services to their borrowers/financees who face difficulties with servicing their debt.
- 3.19 Licensed Financial Institutions must establish clear standards and procedures that prohibit excessive pressure on Customers in collection of repayments or debts due.
- 3.1 Licensed Financial Institutions must monitor and uphold high ethical standards and practices when dealing with Customers.
Account Opening
- 3.20 Licensed Financial Institutions should seek to have appropriate systems in place to ensure the opening of a Customer Bank Account can be completed within 3 business days in instances where the Licensed Financial Institution has assessed the profile of the applicant to present low money laundering and terrorist financing risks, and can demonstrate that it is satisfied with standard customer due diligence documentation.
- 3.21 Licensed Financial Institutions must have clear, transparent and consistent disclosure regarding the documentary requirements for the opening of a Customer Bank Account.
- 3.22 The requirement to open a Customer Bank Account does not constitute the requirement to permit any type of transaction until the Licensed Financial Institution has undertaken all appropriate due diligence including those required for Financial Crime Compliance including the risk based approach and sanctions screening required by the Decree Federal Law No. 20 of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations and the Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Law No. (20) of 2018 On Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations (as amended from time to time ).
- 3.23 Licensed Financial Institutions may receive funds for opening a Bank Account, but the funds are to be blocked until the requirements for opening Bank Accounts are fulfilled, including those relating to Financial Crime Compliance. Customer consent must be obtained in such cases.
- 3.24 Licensed Financial Institutions should record SME account-opening requests registered through all channels (branches, phone banking, automatic teller machines etc.) The register should have details of requests received, accounts opened, rejected, pending less or greater than 30 days. ). The report must be regularly shared with Senior Management and available for regulatory examination on request.
- 3.20 Licensed Financial Institutions should seek to have appropriate systems in place to ensure the opening of a Customer Bank Account can be completed within 3 business days in instances where the Licensed Financial Institution has assessed the profile of the applicant to present low money laundering and terrorist financing risks, and can demonstrate that it is satisfied with standard customer due diligence documentation.
Article 4: Responsible Financing Practice
- 4.1 Licensed Financial Institutions must not charge unreasonable fees for the SME products or services.
- 4.2 Licensed Financial Institutions must not provide credit beyond amounts that the Customer is capable to service.
- 4.3 Licensed Financial Institutions must not grant or extend any form of credit without expressed and documented prior request by the Customer.
- 4-4 Licensed Financial Institutions must monitor for inappropriate activities by credit granting and sales representatives. The monitoring, at a minimum, includes monitoring of monthly trend analysis of credit granted, relevant customer complaints and credit counselling.
- 4.5 Licensed Financial Institutions should only provide credit after obtaining the relevant details from the Credit Information Agency.
- 4.1 Licensed Financial Institutions must not charge unreasonable fees for the SME products or services.
Article 5: Complaint Management and Resolution
- 5.1 Licensed Financial Institutions must have in place a fair, accessible and transparent process provided without charge for addressing Customer Complaints, with a view to resolving Complaints in a timely manner.
- 5.2 A Licensed Financial Institution must establish an independent Complaints management function in the organization that directly reports to the Senior Management. The function must be empowered to effectively resolve Complaints independently of other business operations.
- 5.3 Licensed Financial Institutions must have an efficient and effective Complaint management system with supporting policies and procedures. The system must enable Customers to make Complaints easily and free of cost.
- 5.4 Licensed Financial Institutions must take the necessary steps to ensure that Customers are made aware of their rights and responsibilities when seeking to resolve their Complaints.
- 5.5 A Licensed Financial Institution is responsible for accepting and investigating all Complaints involving the activities of Authorised Agents towards Customers as well as any product and/or service sold, marketed or advertised by the Authorised Agent on behalf of the Licensed Financial Institution.
- 5.6 Licensed Financial Institutions must train their Staff and Authorized Agents in handling of Complaints.
- 5.7 Customers must be informed of the Licensed Financial Institution’s process for the management of SME Complaints as well as recourse to a Complaint resolution mechanism to ensure fairness, transparency and neutrality in resolving Complaints.
- 5.8 Licensed Financial Institutions must utilize the data collected to conduct analysis and assess key risks and trends based on collected data. The results of the analysis must be used by the Licensed Financial Institution for conducting investigations into thematic trends, conducting root cause analysis of repeat issues and for designing new controls to address issues and improving quality and efficiency of various aspects of Customer service.
- 5.9 The SME Complaints Data must be provided on a quarterly basis to the Senior Management of the Licensed Financial Institution to enable managerial level monitoring of trends and supportive decision-making and document any decisions or actions taken.
- 5.10 Licensed Financial Institutions must participate in, fully co-operate with and inform customers of, any external financial Complaints resolution function (e.g. ombudsman) as established by the appropriate authorities or industry bodies.
Article 6: Shari’ah Compliance
- 6.1 IFIs must incorporate and uphold Shari’ah principles in all aspects of their business comprised of reporting, business conduct, risk management and oversight functions.
- 6.2 IFIs’ staff dealing with Customers must have sufficient knowledge of the Shari’ah aspects of the Shari’ah compliant products and/or services being offered.
- 6.3 IFIs must provide customers with accurate information regarding their investment accounts including, but not limited to, the profit-sharing ratio between the IFIs and Customer and the profit distribution method.
- 6.4 IFIs must be compliant with the resolutions and fatwas issued by the IFI’s ISSC in relation to licensed activities and businesses of such institution, provided they do not contradict the HSA’s Resolutions.
- 6.5 Board and Senior Management of the IFIs must monitor the activities and integrate Shari’ah compliance into the IFI’s culture, processes, operation, and code of conduct.
- 6.1 IFIs must incorporate and uphold Shari’ah principles in all aspects of their business comprised of reporting, business conduct, risk management and oversight functions.
Article 7: Interpretation of Regulation
The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
Article 8: Publication and Effective Date
This Regulation shall be published in the Official Gazette and shall come into effect 30 days from the date of publication.
Acceptance of Public Subscription
With refer to our Circular No. 444 dated 15/6/1987 regarding the conditions banks are required to fulfil in the matter of acceptance of public subscription to the capital of new companies or to an increase in the capital of existing companies, whether such companies are established in the U.A.E. or abroad.
We wish to inform you that in respect of companies established abroad, banks operating in the U.A.E., in addition to the conditions laid down in our above mentioned circular, are further required to submit the following :-
- A copy of the approval given by the appropriate official authority in the country of origin authorising the concerned company to offer shares abroad. This approval should be translated into Arabic and duly authenticated in case the letter of approval is issued in a language other than Arabic or English.
Total number of share allocated to U.A.E. subscribers, compared to total number of shares applied for, as soon as the allocation procedures are finalised.
Furthermore, all applications and other required documents, seeking approval of Central Bank, should be submitted at least two weeks before the issue is opened to the public.
Approval for IPO Participation by Banks
In view of enquiries made by some banks operating in the country regarding the acceptance of public subscription to the capital of new companies or to an increase in the capital of existing companies, we would like to advise that we have decided to make some amendments and additions to our circulars Nos. 40 and 429 dated 14.5.81 and 22.3.87 respectively, and to consolidate them into one circular which would read as follows:-
- 1) All licenced banks (including Representative Offices) operating in the UAE must obtain prior approval of the Central Bank (Banking Supervision Department) before accepting any public subscription to the capital of new companies or to any increase in the capital of existing companies, whether these companies are established in the UAE or abroad.
- 2) Approval must be requested whether banks act as underwriters or intermediaries to the issue. Banks are regarded as intermediaries if they advertise in any way for share issue and/or collect customers’ application forms. They are not regarded as intermediaries and have not to ask for any authorisation if they are only involved in transferring money at the request of customers, without advertising in any way for the issue and without collecting application forms.
- 3) Applications submitted to the Central Bank must include the following:-
- (a) Banks must certify that the share issue in question is made in compliance with the rules and regulations of the country where the company is incorporated and that they are entitled to collect funds in this regard.
- (b) Banks must provide the Central Bank with a copy of all terms and conditions of the share issue: share value, period of issue, date of allotment, date of delivery of share certificates, deadlines for refund in case shares are over-subscribed, etc.
- (c) Banks must confirm in writing that they will be responsible to protect the interest of subscribers and are prepared to take the necessary steps, in due time, to enable their customers to fully obtain what they are entited to:
- — refund, in case payment is made in advance and shares are over-subscribed;
- — confirmation from the issuing company stating the number of shares allotted to the customer, in case payment is made in instalment;
- — delivery of the share certificate, in due time.
- — refund, in case payment is made in advance and shares are over-subscribed;
- (a) Banks must certify that the share issue in question is made in compliance with the rules and regulations of the country where the company is incorporated and that they are entitled to collect funds in this regard.
4) Banks should bring to the knowledge of customers any information that may be useful for making a decision upon the offer, especially the following:-
- (a) In case the offer is advertised in the press, summary of latest audited accounts of the issuing company should be published.
- (b) Date when allotment of shares is to be made and deadline for refund, in case subscription is paid in advance and shares are over-subscribed, must be clearly indicated to the applicant.
- (c) It must also be stated whether interest is to be paid or not to the applicant in case refund is not made by the above mentioned deadline.
- (d) Applicant must also be clearly informed in case loss or gain on foreign exchange is to be borne by him.
Banks should make sure that applicants have acknowledged that they are aware and have accepted the terms and conditions of such subscription.
- (a) In case the offer is advertised in the press, summary of latest audited accounts of the issuing company should be published.
- 5) Banks should issue acknowledgement to the subscribers for the application ledged with them, stating the name and address of the issuing company, the number of shares subscribed, amounts paid in advance, date of delivery of share certificates, date of delivery of receipt from the issuing company in case payment is made in instalments, and deadline for refund in case shares are over-subscribed.
- 6) In case of locally incorporated companies banks are required to verify that founder members have already paid for their shares in one of the banks operating in the country before they accept public subscriptions.
- 7) where relevant, banks are required to open special account(s) for the collection of subscriptions after receiving Central Bank approval. The amounts deposited in such account(s) are subject to reserve requirement in case they are kept for a period of more than one month.
- 1) All licenced banks (including Representative Offices) operating in the UAE must obtain prior approval of the Central Bank (Banking Supervision Department) before accepting any public subscription to the capital of new companies or to any increase in the capital of existing companies, whether these companies are established in the UAE or abroad.
Establishment of an Ombudsman Unit for The United Arab Emirates Regulation
N 1659/2023 Effective from 15/3/2023Introduction
One of Central Bank’s objectives, as mandated by the Decretal Federal Law No. 14 of 2018 Regarding the Central Bank & Organization of Licensed Financial Institutions and Activities and its amendments, is to establish Regulations for the protection of Consumers of Licensed Financial Institutions.
The Central Bank has the right to establish a unit with an independent legal personality to receive and to handle Complaints from Consumers of Licensed Financial Institutions.
This Regulation is issued pursuant to the powers vested in the Central Bank according to Article (121) of the aforementioned Decretal Federal Law and to Article (110) of the Federal Law No. 6/2007 concerning the Organization of Insurance Operations and its amendments.
Post replacement of the Insurance Authority with the Central Bank in all competencies and legislation, pursuant to Article (2) of the Decretal Federal Law No. 24/2020 concerning Amending Certain Provisions of the Federal Law No. (6) of 2007 concerning the Establishment of Insurance Authority and Regulation of Insurance Operations and its amendments, the Central Bank is now the regulator of insurance operations according to the Federal Decree Law No. 24/2020 on the Establishment of Insurance Authority and Regulation of Insurance Operations.
Therefore, this Regulation covers Insurance Companies as defined in the Federal Law No. 6/2007 on the Organization of Insurance Operations and its amendments in addition to Licensed Financial Institutions governed by the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities and its amendments.
This Regulation is to provide for the establishment of an independent Ombudsman Unit that enjoys independent legal personality, and to confer its powers and functions; to provide for a complaint process and resolutions mechanism; to provide for an appeal mechanism in relation to determinations made by the Ombudsman Unit; to set out the Ombudsman Unit’s funding and to provide for the appointment of the Board of Directors and engage Persons to the Ombudsman Unit.
This Regulation also establishes the overarching Regulatory framework for the Ombudsman Unit and its interactions with Licensed Financial Institutions and Insurance Companies in relation to Consumer Complaint resolution in the State.
Objectives
The primary objective of this Regulation is to establish an independent Ombudsman Unit that enjoys legal personality, which shall be known as “Sanadak”. The Ombudsman Unit will provide a Complaint resolution mechanism to the consumers of Licensed Financial Institutions and Insurance Companies. Consumers can access an independent and fair Complaint resolution mechanism that will serve to strengthen Consumer trust and confidence in their relations with Licensed Financial Institutions and Insurance Companies.
This Regulation sets out the Complaint resolution mechanism framework for the establishment and functioning of the Ombudsman Unit designed to be consistent with the International Ombudsman Association’s Code of Ethics and Standards of Practice.
This Regulation seeks to enhance a culture within Licensed Financial Institutions and Insurance Companies that will respect and act in the best interest of Consumers by:
- Establishing an independent Complaint resolution mechanism for the fair, efficient and timely resolution of Complaints by the Consumers in the regulated banking and insurance services industry ;
- Setting consistent standards for the resolution of Consumer Complaints by Licensed Financial Institutions and Insurance Companies;
- Providing Consumers with access to relevant Information, as required, to ensure Consumers have the opportunity to make informed decisions;
- Strengthen Consumer knowledge, awareness and ability to address their concerns and / or complaints involving their relations with Licensed Financial Institutions and Insurance Companies.
- Establishing an independent Complaint resolution mechanism for the fair, efficient and timely resolution of Complaints by the Consumers in the regulated banking and insurance services industry ;
Scope of Application
This Regulation is issued under the authority of Decretal Federal Law No. 14 of 2018 Regarding the Central Bank & Organization of Licensed Financial Institutions and Activities, as amended and the Federal Law No. 6 of 2007 concerning the Organization of Insurance Operations, as amended (“Insurance Law”).
The Scope of this Regulation applies to all Licensed Financial Institutions and Insurance Companies as defined by Article 1 of this Regulation and their obligations and responsibilities regarding their relationship with the Ombudsman Unit and its operations. Furthermore, this Regulation sets out the definition as to those consumers and persons that are given a right of free access to the Complaint resolution mechanism of the Ombudsman Unit.
This Regulation is in addition to any requirement of any other regulatory authority as applicable to all Licensed Financial Institutions and Insurance companies. In case of any conflict with such requirement, the provisions of this Regulation will prevail, unless otherwise specified in this Regulation.
Where this Regulation includes requirements to provide information, to take certain measures or to address certain items listed as a minimum, the Central Bank may impose requirements that are additional to the listing provided in the relevant Articles.
The Central Bank may issue further guidance relating to this Regulation.
Article 1: Definitions
For the purposes of this Regulation, words and expressions shall have the meaning assigned to, unless the context requires otherwise, as mentioned below and/or defined in other Laws and Regulations:
- Annual Levy: Fee levied by the Ombudsman Unit on Licensed Financial Institutions and Insurance Companies on an annual basis.
- Appeals Committee: A committee formed by the Ombudsman Unit for the final resolution of Complaints by the Ombudsman Unit, against the Licensed Financial Institutions.
- Appeals Fee: Fee levied by the Ombudsman Unit on the appellant of a Complaint to the Appeals Committee which may, at the discretion of the Ombudsman Unit, be refunded when the Determination of the Complaint is in favor of the appellant.
- Case Fee: Fee levied by the Ombudsman Unit on the Licensed Financial Institution or the Insurance Company for each Complaint closed by the Ombudsman Unit during a Financial Year (regardless of when the Complaint was referred to the Ombudsman Unit).
- Central Bank: The Central Bank of the United Arab Emirates.
- Central Bank Regulations: Any resolution, legislation, circular, rule, instruction, standard or notice issued by the Central Bank.
- Complainant: A Complainant filing a Complaint shall include:
- A Consumer
- An actual or potential beneficiary
- A Person acting on behalf of the Consumer or beneficiary such as personal or legal representative, counselor, guardian, trustee, or executor.
- A Consumer
- Complaint: For the purpose of this Regulation, a Complaint shall be defined as:
- An expression of dissatisfaction by a Consumer with a product, service, policy, procedure or actions by the Licensed Financial Institution that is presented to an Employee of the Licensed Financial Institution in Writing, verbally or through other electronic means.
- An expression of dissatisfaction by a Consumer with a product, service, policy, procedure or actions by the Insurance Company that is presented to an Employee of the Insurance Company in Writing, verbally or through other electronic means.
- An expression of dissatisfaction referred to an Employee of the Ombudsman Unit in Writing, verbally or any other electronic means, by a Consumer against the response provided by a Licensed Financial Institution or an Insurance Company to a Complaint in accordance with (a) and (b) above.
- An expression of dissatisfaction by a Consumer with a product, service, policy, procedure or actions by the Licensed Financial Institution that is presented to an Employee of the Licensed Financial Institution in Writing, verbally or through other electronic means.
- Consumer: Consumer is a customer for the purpose of this Regulation. A customer:
- is any Natural Person, Sole Proprietor or Small to Medium Sized Enterprise who obtains or may prospectively obtain services and/or products from a Licensed Financial Institution, with or without charge, to satisfy his/her personal need or others’ needs.
- is any Natural Person, Sole Proprietor, Small to Medium Sized Enterprise who obtains or may prospectively obtain services and/or products from an Insurance Company, with or without charge, to satisfy his/her personal need or others’ needs.
- is any Natural Person, Sole Proprietor or Small to Medium Sized Enterprise who obtains or may prospectively obtain services and/or products from a Licensed Financial Institution, with or without charge, to satisfy his/her personal need or others’ needs.
- Court: The Federal and Local Courts System of the United Arab Emirates .
- Decretal Law: Decretal Federal Law No. (14) Of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities and its amendments.
- Determination: A decision made by the Ombudsman Unit or the Appeals Committee or the Insurance Dispute Resolution Committee on a specific Complaint.
- Financial Crime Compliance: Financial Crime Compliance is the requirement to comply with, including and not limited to, all applicable fraud, anti-money laundering, counter-terrorism financing, sanctions, bribery and corruption laws, rules and regulations.
- Financial Year: Financial Year represents a period of 12 months in which a full accounting cycle takes place .
- Information: Any form of data, documents and/or electronic records .
- Insurance Company: The Insurance Company incorporated in the State and the foreign Insurance Company licensed to carry out insurance activities in the State either through a branch, or through an insurance agent including Takaful insurance companies.
- Licensed Financial Institutions: Banks and other Financial Institutions licensed in accordance with the provisions of the Decretal Federal Law No. (14) of 2018, to carry on a licensed financial activity or more, including those which carry on the whole or a part of their business in compliance with the provisions of Islamic Shari’ah, and are either incorporated inside the State, or have branches, subsidiaries or representative offices inside the State .
- Minority Group: A category of people who experience relative disadvantage as compared to members of a dominant social group. Minority Group membership is typically based on differences in observable characteristics or practices, such as ethnicity, race, religion or determination.
- Ombudsman Unit: An independent Ombudsman Unit that enjoys independent legal personality, and to confer its powers and functions; to provide for a complaint process and resolutions mechanism.
- Chief Ombudsman: The Person appointed by the Board of Directors of the Central Bank to be the Chief Ombudsman, to manage and direct the day-to-day operations and affairs of the Ombudsman Unit.
- People of Determination: A person suffering from a temporary or permanent, full or partial deficiency or infirmity in his physical, sensory, mental, communicational, educational or psychological abilities to an extent that limits his possibility of performing the ordinary requirements.
- Person: A natural or juridical Person, as the case may be .
- Small to Medium Sized Enterprises: For the purposes of this Regulation, the words and acronym SME includes small, micro and medium businesses, provided that the businesses meet the thresholds of employee headcount and turnover, as defined by the Federal Cabinet Resolution No. 22 of 2016 which sets out the Small to Medium sized Enterprise definition for the purposes of Federal Law No. 2 of 2014 or any subsequent amendments to the Federal laws defining a SME:
- Medium Enterprise: Trading Sector 51 – 200 employees; or < AED 250 million annual revenues; Manufacturing Sector 101 – 250 employees; or < AED 250 million annual revenues; Service Sector 51 – 200 employees; or < AED 200 million annual revenues.
- Micro Enterprise: Trading Sector < 5 employees; or < AED 3 million annual revenues; Manufacturing Sector < 9 employees; or < AED 3 million annual revenues; Service Sector < 5 employees; or < AED 2 million annual revenues.
- Small Enterprise: Trading Sector 6 – 50 employees; or < AED 50 million annual revenues; Manufacturing Sector 10 – 100 employees; or < AED 50 million annual revenues; Service Sector 6 - 50 employees; or < AED 20 million annual revenues.
- Medium Enterprise: Trading Sector 51 – 200 employees; or < AED 250 million annual revenues; Manufacturing Sector 101 – 250 employees; or < AED 250 million annual revenues; Service Sector 51 – 200 employees; or < AED 200 million annual revenues.
- Staff of the Ombudsman Unit: One or more employee(s) of the Ombudsman Unit acting in any official capacity for or on behalf of the Ombudsman Unit.
- Standards: Any Standards adopted from time to time, including performance Standards, rules, codes of behavior and conflict of interests, and procedural guidelines for the handling and resolution of Complaints / disputes.
- State: The United Arab Emirates.
- Supplementary Levy: Fee levied by the Ombudsman Unit on Licensed Financial Institutions and Insurance Companies to supplement the costs of establishing and the continued operation of Ombudsman Unit in the event the Annual Levy and Case Fee are insufficient to meet the objectives of Ombudsman Unit .
- Terms of Reference: A document prepared by the Ombudsman Unit and approved by the Board of the Ombudsman Unit, that shall provide the governance structure of the Ombudsman Unit, the roles and responsibilities of different departments, the Complaints management framework that shall be followed by the Ombudsman Unit and the principal powers and duties of the Ombudsman Unit.
- Third Party: Any Person, group of Persons or organization external to, and not a related party to, the Ombudsman Unit.
- Writing: For any requirement of communications and signatories, declarations, consents, agreements or other instruments/requirements in Writing, for the sake of clarity, these terms apply to electronic, digital and paper based insofar an Electronic Document or Record satisfies the requirement of the provision of Federal Decree Law No. (46) of 2021 regarding the Electronic Transactions and Trust Services .
- Year: The Gregorian calendar Year.
- Annual Levy: Fee levied by the Ombudsman Unit on Licensed Financial Institutions and Insurance Companies on an annual basis.
Article 2: Establishment of the Ombudsman Unit
2.1 Establishment
2.1.1. Pursuant to this Regulation, the Central Bank establishes an independent legal personality, which shall be known as the “Sanadak”, to perform the functions conferred on it by this Regulation. The principal mandate of the Ombudsman Unit shall be to receive, handle, review and resolve Complaints in a thorough, timely, transparent, fair and legally sound manner. The Ombudsman Unit shall be financially and administratively independent, insofar as provided by this Regulation.
2.1.2. The Ombudsman Unit shall be accountable to the Central Bank based on the provisions under Article 5 of this Regulation .
2.2 Mandate
2.2.1. The Ombudsman Unit shall abide by the principles of fairness, equity, objectivity, legality and integrity .
2.2.2. The Ombudsman Unit shall:
- be accessible to the Consumers for filing Complaints and inquiries related to status of Complaints;
- ensure that Complaints regarding the conduct of Licensed Financial Institutions and Insurance Companies are processed and dealt with in a fair, efficient, effective and legally sound manner ;
- promote Consumer awareness and understanding of the role and functions of the Ombudsman Unit as well as the types of issues related to Complaints that are considered .
2.2.3. The Ombudsman Unit may:
- assist Complainants with understanding the Complaint process but shall not advocate on their behalf;
- make appropriate observations and recommendations for the improvement of the Complaint procedures / processes of the Licensed Financial Institutions and Insurance Companies.
2.3 Delegation of functions of Central Bank relating to Insurance Dispute Resolution Committee
2.3.1. All functions, powers and authorities vested with the Central Bank with respect to the Insurance Dispute Resolution Committee, are being delegated to the Ombudsman Unit by virtue of this Regulation .
- be accessible to the Consumers for filing Complaints and inquiries related to status of Complaints;
Article 3: Governance and Organizational Structure
3.1 Appointment of the Board of the Ombudsman Unit and the Chief Ombudsman
3.1.1. The Board of the Ombudsman Unit must be comprised of seven (7) members including a Chairperson:
- The Chairperson of the Board of the Ombudsman Unit who shall have knowledge and experience of the financial services industry and Consumer Protection issues, to lead the Board of the Ombudsman Unit;
- Board Members of the including:
- at least 3 Persons who have knowledge or experience of Customer relations management, Consumer protection, Complaints resolution and other Consumer issues relating to the Licensed Financial Institutions;
- at least 3 Persons who have knowledge or experience of Customer relations management, Consumer protection, Complaints resolution and other Consumer issues relating to the Insurance operations;
- at least 3 Persons who have knowledge or experience of Customer relations management, Consumer protection, Complaints resolution and other Consumer issues relating to the Licensed Financial Institutions;
3.1.2. A member of the Board of the Ombudsman Unit shall hold office for such period as determined by the Board of Directors of the Central Bank but cannot exceed a 3 Year term from the date of the appointment.
3.1.3. The Chairperson of the Board of the Ombudsman Unit, the Chief Ombudsman and members of the Board of the Ombudsman Unit shall be appointed by a resolution of the Board of Directors of the Central Bank, upon a recommendation by the Governor of the Central Bank, and renewable for a similar period(s), for a maximum of two terms, by the same appointment mechanism. The Board of the Ombudsman Unit may be reconstituted before or after expiry of its term by a resolution of the Board of Directors of the Central Bank.
3.1.4. In the event that the position of any member of the Board of the Ombudsman Unit or the office of the Chief Ombudsman becomes vacant for any reason before the expiry of the membership term, a successor shall be appointed, within a period not exceeding 3 months, in the same manner in which the previous member was appointed.
3.1.5. The Chairperson of the Board of the Ombudsman Unit, the Ombudsman and members of the Board of the Ombudsman Unit shall be independent of Licensed Financial Institutions and Insurance Companies, for at least two years prior to the date of appointment and during the full term of the appointment. In terms of previous and existing employment, directorship and shall be void of any other apparent conflicts of interest.
3.1.6. The Chief Ombudsman shall, at the request of the Chairperson of the Ombudsman Unit, designate a member of the Staff of the Ombudsman Unit to be Secretary to the Board of the Ombudsman Unit.
3.1.7. Every decision at a meeting of the Board of the Ombudsman Unit shall be determined by a majority of the votes of the members of the Board of the Ombudsman Unit in attendance (in person and/or online) when voting on any matter tabled for the Board to decide. Records of all meetings along with decisions shall be maintained for a period of at least 5 years from the date of each Board meeting of the Ombudsman Unit.
3.1.8. Quorum to hold a Board meeting of the Ombudsman Unit and vote on matters requires majority members including the Chairperson of the Board of the Ombudsman Unit to be in attendance.
3.1.9. Subject to this Article, the Board of the Ombudsman Unit shall develop rules for its internal procedures. The Central Bank may provide direction or recommendation for any necessary changes to these rules.
3.2 Responsibilities of the Chairperson of the Board of the Ombudsman Unit
3.2.1. The Chairperson of the Board of the Ombudsman Unit shall be accountable for and charged with the responsibility for:
- managing the business of the Board of the Ombudsman Unit and that of any relevant Board subcommittees;
- setting agendas and meeting times for the Board of the Ombudsman Unit;
- ensuring follow-up to decisions of the Board of the Ombudsman Unit and any recommendations from independent reviews and /or audit findings;
- official liaisons between the Board of the Ombudsman Unit, Board of Directors of the Central Bank and the Governor of the Central Bank;
- advising the Governor of the Central Bank with a list of qualified candidates for re-appointment or replacement when a member of the Board of the Ombudsman Unit’s appointment is expiring or a vacancy has occurred;
- liaison between the Board of the Ombudsman Unit and the Chief Ombudsman.
3.3 Functions of the Board of the Ombudsman Unit
3.3.1. The Board of the Ombudsman Unit have the ultimate responsibility for the functioning of the Ombudsman Unit. The Board of the Ombudsman Unit shall be delegated by the Board of the Central Bank to have all such powers / authorities as are necessary for the performance of its functions.
3.3.2. The Board of the Ombudsman Unit shall delegate to the Chief Ombudsman the duties and responsibilities for day-to-day operations of the Ombudsman Unit.
3.3.3. The functions of the Board of the Ombudsman Unit shall be to:
- determine and prescribe the methodology for setting the Annual Levy, Case Fee, Supplementary Levy and any other fee or charge deemed necessary for the efficient functioning of the Unit;
- monitor the standards of performance and review the efficiency and effectiveness of the Ombudsman Unit;
- provide oversight of the functioning of the Ombudsman Unit to ensure that the Ombudsman Unit is operating in accordance with its regulatory mandate;
- make recommendations to the Central Bank on any matter relevant to the mandate, operations and performance of the Ombudsman Unit;
- subject to the provisions under Article 3.3.5, make recommendations to the Chief Ombudsman, the Chairperson of the Appeals Committee or Insurance Dispute Resolution Committee on any matter relevant to the Ombudsman Unit, for which recommendation is requested from the Board of the Ombudsman Unit;
- approve the strategies and objectives proposed for the Chief Ombudsman and management team of the Ombudsman Unit;
- set out and approve appropriate governing rules and policies related to the administration and operations for the Ombudsman Unit including budgeting and revenue allocation, expenditure / contract management, human resources, performance standards, management reporting to the Board of the Ombudsman Unit and any other policies as deemed necessary for effective oversight, and;
- carry out such other functions as are conferred on it by this Regulation.
3.3.4. The Board of the Ombudsman Unit must approve the Terms of Reference, which shall be prepared by the Ombudsman Unit to provide clarity on its governance, funding and operations. The Board of the Ombudsman Unit shall also approve the policies and procedures that govern the Complaint resolution process.
3.3.5. The Board of the Ombudsman Unit shall establish appropriate human resources policy to ensure that the Staff of the Ombudsman Unit are fit and proper and have appropriate level of qualifications and experience.
3.3.6. The Board of the Ombudsman Unit shall have no direct or indirect capacity to influence or affect the review process or the outcome of individual Complaints.
3.4 Powers and Duties of the Chief Ombudsman
3.4.1. The Chief Ombudsman may, or on the request of the Board of the Ombudsman Unit shall:
- make recommendations to the Central Bank, in relation to any proposals for regulatory change, or any other policy matters in relation to Complaints, concerning Complaint resolution and the functions of the Ombudsman Unit, and;
- submit any proposals they consider appropriate for amendment of this Regulation, or for new Central Bank Regulations concerning Licensed Financial Institutions and Insurance Companies in relation to the functions of the Ombudsman Unit.
3.4.2. All such recommendations and proposals, under Article 3.4.1, may be approved and submitted to the Central Bank for consideration by the Board of the Ombudsman Unit.
3.4.3. Subject to this Regulation, the Chief Ombudsman shall be independent in the performance of the assigned functions.
a. The Chief Ombudsman shall have such powers as are necessary for the performance of the functions as conferred on the Chief Ombudsman by this Regulation including:
- acceptance of Complaints ;
- rejection of Complaints that are deemed frivolous or vexatious or unfounded and / or without merit;
- determining the need for a review of a Complaint and with the view of resolving them ;
- assignment of qualified Staff of the Ombudsman Unit to carry out the review and resolution of Complaints;
- determining the validity of the complaint and applying appropriate redress;
- raising concerns with the Central Bank, about the Complaints management process of Licensed Financial Institutions and Insurance Companies, for review and further action if required ;
- hiring and terminating Staff of the Ombudsman Unit in accordance with Board of the Ombudsman Unit’s policies;
- management and evaluation of performance by the Staff of the Ombudsman Unit, consultants, contractors and agents ;
- approving expenditures of the Ombudsman Unit in accordance with approved budgets, financial delegations and policies; and
- other powers as may be assigned by the Board of the Ombudsman Unit.
3.4.4. The Chief Ombudsman may:
a. delegate responsibilities to any member of the Staff of the Ombudsman Unit that are conferred on the Chief Ombudsman by this Regulation or by the Board of the Ombudsman Unit.
b. authorize and direct any member of the Staff of the Ombudsman Unit to perform any of the functions including giving of directions under Article 4 to Article 5 conferred on the Chief Ombudsman by this Regulation.
3.4.5. The Chief Ombudsman shall establish and maintain efficient and effective systems and procedures that are carried out in a fair and timely manner for the acceptance, handling, review and resolution of Complaints.
3.4.6. The Chief Ombudsman duties include ensuring that the Staff of the Ombudsman Unit, contractors, agents and consultants act in compliance with the Ombudsman Unit’s policies and procedures, Terms of Reference, code of conduct, conflict of interest and all applicable Central Bank Regulations and the Decretal Law.
3.4.7. As may be delegated by the Board of the Ombudsman Unit, the Chief Ombudsman may appoint individuals as Staff of the Ombudsman Unit and may determine their duties. The Chief Ombudsman shall have regard to the human resources policy, resource allocation and any directions that the Board of the Ombudsman Unit may give from time to time for the purpose of giving effect to those policies.
3.5 Staff of the Ombudsman Unit
3.5.1. Persons engaged by the Ombudsman Unit may be appointed:
a. as Staff of the Ombudsman Unit on a permanent basis;
b. as Staff of the Ombudsman Unit on a temporary or part-time basis;
c. on a contract for services including as consultants or advisors.
3.5.2. The members of Staff of the Ombudsman Unit shall perform their functions under the direction and control of the Chief Ombudsman or an authorized staff supervisor, as designated by the Chief Ombudsman.
3.5.3. A member of the Staff of the Ombudsman Unit is free to perform their functions, without inappropriate interference from any Person. The member shall:
a. comply with the directions given by the authorized staff supervisor designated by the Chief Ombudsman, and
b. ensure the authorized staff supervisor/ Chief Ombudsman remain informed about the performance of functions and activities by the Staff of the Ombudsman Unit as well as the status of assigned work including time delays or any material issues or developments.
3.6 Appointment of the Appeals Committee
3.6.1. There shall be a Committee known as the Appeals Committee for the settlement and resolution of Complaints against Licensed Financial Institutions. The Appeals Committee shall act as the final level of Complaints resolution within the Ombudsman Unit for Licensed Financial Institutions.
3.6.2. The Appeals Committee may accept the appeal where there is reason to believe that the Ombudsman Unit :
a. may have overlooked material Information ;
b. may have failed to assess material issues previously raised by the appellant;
c. may have incorrectly or unfairly applied its operational policies and procedures; or
d. new material Information is available that was not previously considered by the Ombudsman Unit.
3.6.3. The Appeals Committee shall consist of a Chairperson of the Appeals Committee and two or more qualified members from the Staff of the Ombudsman Unit who will be independent of the case management and appointed by the Board of the Ombudsman Unit.
3.6.4. The Appeals Committee shall proceed in an expedited but fair manner based on values of natural justice, neutrality and objectivity regarding the Complaints being appealed.
3.6.5. The Appeals Committee is not bound by the rules of evidence expected in a normal Court of law or arbitration process.
3.6.6. The Appeals Committee shall take into consideration the Central Bank's Laws and Regulations, resolutions and instructions related to matters that may be a factor in the Complaint.
3.6.7. In fulfilling its duties, the Appeals Committee shall be entitled to obtain and review papers, documents, records and all pertinent evidence and take all actions as it deems appropriate.
3.6.8. The Appeals Committee shall hold its hearings in the presence of the Chairperson of the Appeals Committee and majority of members to consider the Complaints referred to it. The Appeals Committee may hear the statements and arguments of the parties and issue its decisions by majority. The Appeals Committee shall reject an appeal referred to it if the requirements for lodging a Complaint are not met under Article 4.
3.6.9. The Appeals Committee shall be competent to settle and resolve Complaints of all admissible types and classes arising from the Complaints of the Consumers.
3.6.10. The Chief Ombudsman shall, at the request of the Chairperson of the Appeals Committee, designate a member of the Staff of the Ombudsman Unit to be the Secretary to the Appeals Committee.
3.6.11. The Committee Secretary shall assume the following duties and powers :
a. Maintain records management of Committee documents and files;
b. Prepare the meeting agendas and required files and documentation for the Committee ;
c. Contact the parties, related to a Complaint as per the Committee's directives ;
d. Record the minutes of the Committee meetings and the outgoing correspondences and decisions ;
e. Implement the decision of the Committee by inviting the parties related to a Complaint and experts to appear before the Committee ;
f. Notify the parties, on the Determination of the Committee ;
g. Any other tasks assigned to them by the Committee.
- The Chairperson of the Board of the Ombudsman Unit who shall have knowledge and experience of the financial services industry and Consumer Protection issues, to lead the Board of the Ombudsman Unit;
Article 4: Complaint Resolution
4.1 Eligible Complaints
4.1.1. The Ombudsman Unit may accept Complaints in relation to the conduct of a Licensed Financial Institution or an Insurance Company, involving:
- the provision of a service or product or an offer to provide a service or product by the Licensed Financial Institution or Insurance Company;
- a failure by the Licensed Financial Institution or Insurance Company to provide a particular service or product requested by the Complainant, due to reasons that discriminate on the grounds of family or socio-economic status, gender or being a member of a Minority Group;
- an alleged financial loss or harm to a Complainant through any deceptive, misleading, fraudulent or unfair conduct by or on behalf of the Licensed Financial Institution or Insurance Company.
4.1.2. The Ombudsman Unit can reject a Complaint, where:
- the conduct giving rise to the Complaint is or has been the subject of legal proceedings before a Court in the State ;
- the Complaint has not been raised or properly communicated to the Licensed Financial Institution or Insurance Company concerned ;
- the Complainant has not provided at least 30 complete business days’ response time, or such other time limit as may be prescribed by the Central Bank for the Licensed Financial Institution or Insurance Company, to provide a final response in Writing to the Complaint ;
- the Complaint relates to a matter that occurred outside the time limits as specified in Article 4.4 ;
- the Complaint materially relates to a Licensed Financial Institution or Insurance Company's risk management, internal pricing policy or AntiMoney Laundering policies and practices; or
- the Complaint has already been settled between the Complainant and the Licensed Financial Institution or Insurance Company.
4.1.3. The Complaint may be made by any Complainants having an interest in the subject matter of the Complaint. The Ombudsman Unit may consider the subject matter of a Complaint without the participation of one or more Complainants that may be affected by the subject matter of the Complaint.
4.1.4. The Ombudsman Unit shall publish the acceptable format for filing Complaints on its website or by way of other communications generally available to the public.
4.1.5. The Complainant may withdraw the Complaint at any time by giving a formal notice of withdrawal, in Writing, to the Ombudsman Unit. The Ombudsman Unit shall, within 5 business days, notify the Licensed Financial Institution or Insurance Company about the withdrawal of the Complaint by the Complainant.
4.1.6. The Ombudsman Unit may refuse to accept or may discontinue a review of a Complaint, where in the opinion of the Ombudsman Unit:
- the Complaint is frivolous or vexatious or was not made in good faith;
- the Complainant has no vested interest or an insufficient interest in the conduct complained of ;
- the Complaint is or was subject to Court proceedings or the subject matter of the Complaint is of such a degree of complexity or is about the legitimate exercise of commercial judgment that the Courts are a more appropriate forum;
- the Complaint was previously considered by the Ombudsman Unit, unless material new evidence has since become available and the Ombudsman Unit is satisfied that the new Information warrants treating it as a new Complaint;
- the Licensed Financial Institution or Insurance Company are offering a reasonable amount for the actual loss / harm suffered by the Complainant.
4.1.7. The decision of the Ombudsman Unit will be final with respect to the Ombudsman Unit’s jurisdiction and acceptance of Complaints.
4.1.8. The Ombudsman Unit may make preliminary inquiries before deciding whether a Complaint should be reviewed. It may request either party to the Complaint to provide further particulars of the Complaint in Writing, within a period not exceeding 10 business days.
4.1.9. Within 5 business days after deciding not to review or to discontinue a review of a Complaint, the Ombudsman Unit shall inform the Complainant, Licensed Financial Institution and Insurance Company in Writing of the decision and the reasons for it.
4.1.10. The Ombudsman Unit shall keep the parties to the Complaint informed, as to the progress of the review.
4.1.11. The Ombudsman Unit shall have the capability to communicate with the Complainants in English or/and Arabic language, as preferred by the Complainant.
4.1.12. The Ombudsman Unit shall allocate the jurisdiction of the Complaint to Licensed Financial Institution or Insurance Company, as the case may be, at the beginning of the Complaint resolution process.
4.1.13. The Ombudsman Unit shall obtain from Complainants, appropriate consent concerning the release and treatment of confidential Information related to the Complainants.
4.2 Financial Inclusion
4.2.1. The Ombudsman Unit shall have provisions in place to handle Complaints from vulnerable groups and People of Determination in its Complaints resolution process.
4.2.2. The Chief Ombudsman shall have the power to waive all Fees in cases where the Complainants have little or no means of their own.
4.3 Undertaking to Comply
4.3.1. The Licensed Financial Institutions and Insurance companies shall comply with and be bound by this Regulation.
4.3.2. The Ombudsman Unit shall ensure that all parties to a Complaint shall :
- fully cooperate with the Ombudsman Unit and assist in its review of a Complaint;
- shall comply with a requirement or request made by the Ombudsman Unit, the Appeals Committee or the Insurance Dispute Resolution Committee.
4.3.3. The Licensed Financial Institutions and Insurance companies shall not:
- obstruct or hinder or cause delay in providing requested Information to the Ombudsman Unit, the Appeals Committee or the Insurance Dispute Resolution Committee in the performance of its functions conferred by this Regulation;
- fail to comply with a requirement or request made by the Ombudsman Unit, the Appeals Committee or the Insurance Dispute Resolution Committee under this Regulation ;
- provide false, incomplete and misleading information;
- fail to disclose Information relevant to a review that had not been specifically requested by the Ombudsman Unit while knowingly withholding this Information from the Ombudsman Unit, or;
- attempt to recover from the Complainant, any related costs incurred in the Complaint resolution process at the Ombudsman Unit.
4.3.4. The Complainant shall agree to be bound by Article 4.3.2, at the time of submitting the Complaint to the Ombudsman Unit.
4.3.5. Where the Licensed Financial Institution or the Insurance Company fails to fully cooperate in the review, the Ombudsman Unit shall escalate the matter to the Central Bank for enforcement action.
4.3.6. Where the Complainant fails to fully cooperate in the review, the Ombudsman Unit may in its discretion, terminate the Complaint.
4.3.7. Licensed Financial Institutions and Insurance companies shall inform the Consumers in Writing of their legal right to go to the Ombudsman Unit with their Complaint. Licensed Financial Institutions and Insurance companies shall also provide the Consumers with a copy of the detailed contact information of the Ombudsman Unit.
4.3.8. Licensed Financial Institutions and Insurance Companies may appoint an individual who shall be responsible for representing the Licensed Financial Institution or Insurance Company and furnishing information on their behalf in respect of Complaints.
4.4 Time limits
4.4.1. A Complaint shall be made to the Ombudsman Unit within whichever of the following periods is the last to expire:
- 3 years from the date of the conduct giving rise to the Complaint;
- 2 years from the date on which the Person making the Complaint became aware of the conduct giving rise to the Complaint.
4.4.2. For the purposes of Article 4.4.1:
- conduct that is of a continuing nature is taken to have occurred at the time when it stopped and conduct that consists of a series of acts or omissions is taken to have occurred when the last of those acts or omissions occurred; and
- conduct that consists of a single act or omission is taken to have occurred on the date of that act or omission.
4.4.3. If the Ombudsman Unit considers it fair to do so, it may review a Complaint it receives later than the timelines mentioned under Article 4.1.1. In assessing the fairness of doing so, the Ombudsman Unit will consider, among other things :
- whether, and in what manner, the Licensed Financial Institution or the Insurance Company notified the Complainant of the right to bring a Complaint to the Ombudsman Unit, including whether any written notice provided by the Licensed Financial Institution or the Insurance Company sufficiently specified the timelines within which the Complainant has the right to bring a Complaint to the Ombudsman Unit and whether the Licensed Financial Institution or the Insurance Company adhered to any Complaint handling requirements that may apply ;
- the extent to which the Complainant and the Licensed Financial Institution or the Insurance Company were occupied with negotiations for the resolution of the Complaint during the timelines stipulated in Article 4.1.1; and
- whether the Complainant was subject to extraordinary circumstances.
4.4.4. Within 12 months from the date of implementation of the Ombudsman Unit or as otherwise provided for by the Central Bank, the Ombudsman Unit shall publish performance standards related to:
- Turnaround time by Ombudsman Unit with respect to acknowledgement of receipt of Complaint to the Complainant ;
- Time limit by which parties to a Complaint shall appeal the Determination to the Appeals Committee or Insurance Dispute Resolution Committee;
- Time limit by which the Ombudsman Unit shall provide a report, after the Ombudsman Unit , Appeals Committee or Insurance Dispute Resolution Committee has provided a Determination;
- Time limit for the Licensed Financial Institutions and Insurance companies to settle the Complaint.
4.5 Review of Complaints
4.5.1. Subject to Article 4.1, the Ombudsman Unit may decide to conduct a review of a Complaint referred to them.
4.5.2. The Ombudsman Unit shall give written notice of its decision to carry out a review to the Licensed Financial Institution, Insurance Company, Complainant and any other parties, as deemed relevant by the Ombudsman Unit. The notice will specify:
- summary description of the Complaint and the scope of the review;
- the name and contact Information of the appointed staff reviewer ;
- the Information or document(s) required;
- the date by which the Information or document is required to be filed; and
- the place at which attendance, if any, is required.
4.5.3. The scope and conduct of review shall be determined by the Ombudsman Unit as appropriate in the circumstances of the case.
4.5.4. When reviewing a Complaint about the conduct of a Licensed Financial Institution or Insurance Company, the appointed staff reviewer may, at any time :
- request additional Information be provided by the Licensed Financial Institution or Insurance Company. If a document is not legible, the Ombudsman Unit may request it be reproduced in a legible form or to provide reasonable Information, in relation to that document, to the Ombudsman Unit.
- request and carry out interviews with key persons that may have knowledge of the circumstances being reviewed.
4.5.5. Where the Ombudsman Unit has given a notice of a review of a Complaint, the Ombudsman Unit shall provide the Licensed Financial Institution, Insurance Company and Complainant, an opportunity to make an initial submission, in Writing, within a period not exceeding 10 business days, regarding:
- the scope of the review ;
- the alleged conduct that is the subject of the Complaint, and;
- a rebuttal of any allegations contained in the Complaint or reference.
4.6 Application to the Central Bank for Interpretation/Information, Recommendation and Guidance
4.6.1. When dealing with a Complaint that may involve an issue as to the application of or compliance with a Central Bank Regulation, the Ombudsman Unit may request the Regulatory Development Division of the Central Bank for an interpretation of the Central Bank Regulation.
4.6.2. Where any clarification of Central Bank Regulation in connection with the Complaint concerned has been referred to the Regulatory Development Division of the Central Bank under this Article, the Ombudsman Unit may not:
- make a Determination to which the clarification is relevant while the reference is pending or;
- proceed in a manner, or make a Determination, that is inconsistent with the interpretation of the Regulatory Development Division of the Central Bank on the clarification.
4.7 Determination by the Ombudsman Unit
4.7.1. On completing a review of a Complaint relating to a Licensed Financial Institution or Insurance Company, the Ombudsman Unit shall review the reports, the submissions of the parties and any other evidence that has been gathered and appropriately disclose to the parties subject to compliance with all laws, rules and regulations relating to Financial Crime Compliance. The Ombudsman Unit may then make a Determination, in Writing, that the Complaint:
- is upheld;
- is partially upheld, or;
- is rejected.
4.7.2. A Complaint may be found to be upheld, or partially upheld on one or more of the following grounds where the conduct complained of, under Article 4.1:
- was contrary to applicable Central Bank Regulations ;
- was deceptive, misleading, fraudulent or unfair, in its application to the Complainant;
- was based wholly or partly on an improper motive, an irrelevant ground or an irrelevant consideration;
- was not provided with satisfactory explanation by the Licensed Financial Institution or Insurance Company;
- was previously found to be unlawful by a court or authorized regulatory body;
- was otherwise contrary to the principles of the Consumer Protection Regulation.
4.7.3. A Determination of the Ombudsman Unit under this Article shall be communicated in Writing to the parties by the Ombudsman Unit and such Determination shall include the following:
- the Determination;
- the grounds for the Determination; and
- any direction or recommendation.
4.8. Conduct of review by the Appeals Committee and Insurance Dispute Resolution Committee
4.8.1. Any party to the Complaint may refer the Determination made by the Ombudsman Unit to the Appeals Committee for Complaints against Licensed Financial Institutions or to the Insurance Dispute Resolution Committee for Complaints against Insurance Companies, for further analysis and review.
4.8.2. The request for an appeal by either party shall be made within 30 complete business days from the issue of Determination by the Ombudsman Unit, failing which the Determination shall be considered final and enforceable.
4.8.3. The Ombudsman Unit shall refer the Complaint file to the Appeals Committee or the Insurance Dispute Resolution Committee within a reasonable timeframe
4.8.4. Parties to the Complaint shall be notified of the status of referring the Complaint to the Appeals Committee or the Insurance Dispute Resolution Committee.
4.9 Determination by the Appeals Committee
4.9.1. On completing a review of a Complaint relating to a Licensed Financial Institution, the Appeals Committee shall make a Determination, in Writing, that the Complaint:
- is upheld;
- is partially upheld, or;
- is rejected.
4.9.2. A Complaint may be found to be upheld, or partially upheld on one or more of the following grounds where the conduct complained of, under Article 4.1:
- was contrary to applicable Central Bank Regulations;
- was deceptive, misleading, fraudulent or unfair, in its application to the Complainant;
- was previously found to be unlawful by a court or authorized regulatory body;
- was based wholly or partly on an improper motive, an irrelevant ground or an irrelevant consideration;
- was not provided with satisfactory explanation by the Licensed Financial Institution.
- was otherwise contrary to the principles of the Consumer Protection Regulation, and its accompanying Standards.
4.9.3. A Determination of the Appeals Committee under this Article shall be communicated in Writing to the parties by the Appeals Committee and such Determination shall include the following:
- the Determination;
- the grounds for the Determination; and
- any direction or recommendation.
4.10 Finalization of Determinations
4.10.1. Where a Complaint is upheld or partially upheld, the Ombudsman Unit, or in the case of an Appeal, the Appeals Committee or the Insurance Dispute Resolution Committee, may direct the Licensed Financial Institution or Insurance Company to do one or more of the following:
- review, rectify, mitigate and / or change the conduct complained of or its consequences;
- provide reasons or explanations for that conduct;
- change a practice relating to that conduct;
- recommend to pay a reasonable amount for any actual loss / harm that occurred as a result of the conduct complained of.
4.10.2. The Ombudsman Unit, or in the case of an Appeal, the Appeals Committee or the Insurance Dispute Resolution Committee shall give a copy of the Determination under this Article to:
- the Complainant, and
- the Licensed Financial Institution or Insurance Company to which the Complaint relates
4.10.3. Where the Determination under this Article contains a direction or recommendation, the Licensed Financial Institution or Insurance Company concerned:
- shall comply with the direction or recommendation within such period as is specified in the direction or recommendation, or within such extended period as determined by the Ombudsman Unit, the Appeals Committee or the Insurance Dispute Resolution Committee, and;
- shall not later than 14 business days after the end of that period or extended period, notify in Writing to the Ombudsman Unit, the Appeals Committee or the Insurance Dispute Resolution Committee of action taken to be in compliance with the direction or recommendation.
4.11 Enforceability of Requests / Determination by the Ombudsman Unit or/and Appeals Committee
4.11.1. Where a Licensed Financial Institution or Insurance Company fails or refuses to comply with any request by or the Determination by the Ombudsman Unit or the Appeals Committee within the period stipulated under Article 4.10.3, the Ombudsman Unit or the Appeals Committee, as applicable, will report the case to the Central Bank for inquiry into the case and necessary enforcement action, as deemed appropriate.
- the provision of a service or product or an offer to provide a service or product by the Licensed Financial Institution or Insurance Company;
Article 5: Oversight and Reporting
5.1 Reporting of Patterns and Trends
5.1.1. The Ombudsman Unit shall have controls and detailed procedures in place to identify patterns and trends of issues, including conducting a detailed study, maintaining a record of key themes, and root causes of the Complaints. There shall be a strong governance and oversight mechanism within the Ombudsman Unit to ensure there is early identification and reporting of such patterns and trends.
5.1.2. If the Ombudsman Unit identifies a pattern or trend, it shall within a reasonable timeframe, no later than 1 month after the Ombudsman Unit first became aware, notify the Central Bank in Writing of the issue and supporting details.
5.2 Annual Budget
5.2.1. The Ombudsman Unit shall, not later than 3 months, before the beginning of each Financial Year, or within such extended period as set by the Board of the Ombudsman Unit:
- arrange for the preparation of an annual budget setting out estimates of the income and expenditure of the Ombudsman Unit for the following Year; and
- submit the annual budget to the Board of the Ombudsman Unit for approval.
5.2.2. The annual budget for the following year shall specify:
- the forecasted revenue amounts expected to be collected during the Financial Year concerned from the imposition of the Annual Levy, Case Fee, Supplementary Levy and Appeals Fee, as applicable;
- the proposed level of the Annual Levy, Case Fee, Supplementary Levy and Appeals Fee ;
- any other sources of revenue from which funds are expected to be obtained during the Year to finance the functions of the Ombudsman Unit and the amounts expected to be raised from those sources and;
- proposed breakdown of planned expenditures for.A the Year.
5.2.3. The Ombudsman Unit shall, not later than 3 months into the following Financial Year, publish the annual budget on its website.
5.2.4. The Ombudsman Unit shall incorporate any directions set out by the Central Bank that may be issued for the purpose ofensuring proper and sufficient level of funding for the operations of the Ombudsman Unit
5.3 Strategic plan
5.3.1. The Chief Ombudsman shall prepare and submit a strategic plan for a period of three years, or such period as required by the Central Bank, to the Board of the Ombudsman Unit. The strategic plan and updates shall be approved by the Board of the Ombudsman Unit and submitted to the Central Bank, on an annual basis or as requested by the Central Bank.
5.3.2. The strategic plan shall specify the following:
- objectives of the Ombudsman Unit;
- nature and scope of the activities to be undertaken by the Ombudsman;
- strategic plans and policies for achieving the objectives of the Ombudsman
- targets and criteria for assessing the performance of the Ombudsman;
- allocation of the resources of the Ombudsman Unit;
- estimated budget for the three-year period considering the above factors.
5.4 Annual Financial Reporting
5.4.1. The Ombudsman Unit shall, in respect of each Financial Year, keep in such form as may be approved by the Board of the Central Bank, all proper accounts and receipts of all moneys received or expended in performing the Unit’s functions in accordance with this Regulation.
5.4.2. The Chief Ombudsman shall submit the accounts required to be kept under this Article to the external auditor that shall be appointed by the Board of the Ombudsman Unit. The Board of the Central Bank shall, at its discretion, provide direction to the external auditor regarding its mandate for review of the Ombudsman Unit. Such direction would include a mandate beyond the minimum standard required by the International Financial Reporting Standards for audit of accounts by an external auditor.
5.4.3. Immediately following an external audit, the Board of the Ombudsman Unit shall approve and present to the Central Bank:
- copies of the audited accounts, including the income and expenditure account, the balance sheet and such other accounts (if any) kept under this Article as the Central Bank may direct, and
- the external auditor’s report on the audited accounts ;
- the Ombudsman Unit’s management’s response and action plan for any recommendations or observations made in the external auditor’s report.
5.5 Annual report of the Ombudsman Unit
5.5.1. The Chief Ombudsman shall, not later than 3 months from the end of the Financial Year prepare and submit to the Board of the Ombudsman Unit, an annual report on the activities and performance of the functions of the Ombudsman Unit during that Year.
5.5.2. The annual report shall be first approved by the Board of Directors of the Ombudsman Unit and then presented to the Board of Directors of the Central Bank for approval.
5.5.3. The annual report shall cover the following:
- Information in such form and regarding such matters as the Central Bank may direct;
- Copy of the audited accounts of the Ombudsman Unit for the Financial Year concerned;
- Summary of complaint handling data by the Ombudsman Unit in the Year concerned, including the type of Licensed Financial Institutions and Insurance Companies with Complaints, the type of products, volume and nature of Complaints, turnaround and resolution time, etc. and;
- Summary of patterns, trends and issues submitted to the Central Bank for review and consideration.
- Summary of service complaints against the Ombudsman Unit.
5.5.4. Nothing in this Article shall be construed as requiring the Chief Ombudsman to disclose Information, which, in the opinion of the Chief Ombudsman, would potentially prejudice the performance of the Ombudsman Unit functions or violate any privacy or confidentiality requirements.
5.5.5. The Chief Ombudsman shall arrange for the annual report, that has been approved by the Central Bank, to be published on the website of the Ombudsman Unit, within a reasonable timeframe.
5.6 Other Reporting Requirements
5.6.1. Not later than 3 months after the end of each Financial Year, the Chief Ombudsman shall publish the following on the website of the Ombudsman Unit:
- data of all Complaints made to the Ombudsman Unit during the Financial Year (e.g. received, pending, withdrawn and closed by the Year end) ;
- a review of trends and patterns in the Complaints received by the Ombudsman Unit;
- a breakdown as to the method of disposition of all Complaints made to the Ombudsman Unit during the preceding Financial Year ;
- a summary of the key outcomes of Complaints concluded or terminated, including analysis of Complaints that were settled during the preceding Financial Year; and
- statistics on the cases that have been filed for an appeal.
5.6.2. The detailed reporting template of the above may be specified by the Central Bank.
5.6.3. The Chief Ombudsman may publish statistics of Complaints against all Licensed Financial Institutions or Insurance Companies, without disclosing any names or other details about the Licensed Financial Institutions or Insurance Companies, subject to Central Bank’s approval.
5.6.4. In circumstances where the Chief Ombudsman is of the opinion that there is need for public disclosure of the name of a Licensed Financial Institution or Insurance Company, the Ombudsman shall seek explicit approval from the Central Bank.
5.6.5. A report under this Article shall not divulge the identity of any Complainant nor shall anything be published in the report that may lead to the identification of any Complainant.
5.6.6. The Chief Ombudsman may, from time to time, prepare and submit to the Central Bank such other reports in relation to the performance of the functions under this Regulation as the Chief Ombudsman considers appropriate.
5.6.7. The Chief Ombudsman may, after consultation and approval from the Central Bank, publish reports on other matters related to Complaints resolution if the Chief Ombudsman considers that it would be in the public interest to do so.
5.7 Quality Assurance Review
5.7.1. The Ombudsman Unit shall:
- Submit every three Years to an independent quality assurance review regarding the proper discharge of its functions and the performance of its activities. The review shall be conducted by a Third Party appointed by the Central Bank;
- Conduct a stakeholder survey once a Year covering all Licensed Financial Institutions and Insurance Companies, and with recent Complainants since the previous consultation, with respect to the discharge of its functions and performance of its activities.
5.7.2. The Board of the Ombudsman Unit shall provide the Central Bank with an action plan for any recommendations or observations made in the quality assurance reviewer’s report and / or concluded from the analysis of the stakeholder survey.
5.8 Accountability to Central Bank
5.8.1. The Chairperson of the Board of the Ombudsman Unit shall, whenever required to do so by the Central Bank, provide confirmation in Writing, in relation to:
- the regularity and propriety of the transactions recorded or required to be recorded under this Regulation, subject to financial audit by the External Auditor;
- the economy and efficiency of the Ombudsman Unit in the use of resources;
- the account of the general administration of the Ombudsman Unit;
- the systems, procedures and practices employed by the Ombudsman Unit for the purposes of evaluating the effectiveness of its operations; and
- any matter affecting the Ombudsman Unit referred to in the report of the External Auditor that is submitted to the Central Bank.
5.8.2. The Chairperson of the Board of the Ombudsman Unit shall, at the request of the Governor of the Central Bank, along with designated Central Bank officials, give account for the general administration and functions of the Ombudsman Unit.
5.8.3. The Chief Ombudsman and the Chairperson of the Board of the Ombudsman Unit shall report material issues or developments related to the Ombudsman Unit, to the Board of the Central Bank that may be required by the Decretal Law, Central Bank Regulations and Central Bank’s internal controls framework.
5.8.4. If the Chief Ombudsman and the Chairperson of the Board of the Ombudsman Unit consider that they have information, which in their opinion, would or might be of assistance to the Central Bank in advancing one or more of the Central Bank's operational objectives, they shall disclose that information to the Central Bank.
- arrange for the preparation of an annual budget setting out estimates of the income and expenditure of the Ombudsman Unit for the following Year; and
Article 6: Funding
6.1 Scope
6.1.1. The Licensed Financial Institutions and Insurance Companies shall pay an Annual Levy and Case Fee to the Ombudsman Unit. The amount of the Annual Levy shall not exceed those sums necessary to fund the operation of the Ombudsman Unit, having regard to the income and expenditure mentioned in Article 5.2. The Board of the Ombudsman Unit shall have the authority to determine and revise the Annual Levy and Case Fee.
6.1.2. The Licensed Financial Institutions and Insurance Companies may be required to pay a Supplementary Levy to supplement the costs of establishing and the continued operation of Ombudsman Unit in the event the Annual Levy and Case Fee are insufficient to meet the objectives of Ombudsman Unit. The Supplementary Levy shall be determined by the Board of the Ombudsman Unit and approved by the Central Bank.
6.1.3. For the manner of calculating the funding requirements, as well as the manner and times of payment, the following criteria shall be taken into consideration:
- the Ombudsman Unit’s need for stability of funding;
- the overall administrative costs of the Ombudsman Unit’s operations, including those costs arising from services provided to those Licensed Financial Institutions or Insurance Companies that have ceased to pay fees to the Ombudsman Unit;
- fairness to all Licensed Financial Institutions or Insurance Companies;
- the desirability of accurately allocating expenses to the volume of Complaints received and the various Complaint resolution activities; and
- administrative efficiency and ease.
6.1.4. Any party to a Complaint who seeks an appeal of the Ombudsman Unit Determination may also be required to deposit an Appeals Fee with the Ombudsman Unit which may be refundable in case of a Determination in the favor of the appellant. The Chief Ombudsman shall have the power to waive the Appeals Fee if necessary, given the circumstances for the Complainant.
6.1.5. A Licensed Financial Institution or Insurance Company may be exempted from paying the full quantum of the Annual Levy or may pay a lower Annual Levy upon approval by the Ombudsman Unit where a Licensed Financial Institution or Insurance Company submits an undertaking to the Central Bank that it currently does not serve and does not intend to serve Consumers defined within the scope of this Regulation. In the event that the Ombudsman Unit revokes its approval of the Annual Levy exemption, the Licensed Financial Institution or Insurance Company shall pay the Annual Levy on a pro-rata basis for the Financial Year in which the approval was revoked, and resume paying the full Annual Levy going forward.
6.1.6. Licensed Financial Institutions or Insurance Companies that come under the jurisdiction of the Ombudsman Unit part way through the Financial Year will be required to pay the Annual Levy on a pro-rata basis.
6.1.7. All Licensed Financial Institutions and Insurance Companies that cease to be under the jurisdiction of the Ombudsman Unit shall continue to remain liable for full Annual Levy and Case Fee incurred on Complaints brought to the Ombudsman Unit until all related Complaints are withdrawn or settled.
6.2 Collection by the Ombudsman Unit
6.2.1 All Licensed Financial Institutions and Insurance companies shall be required to pay the Annual Levy, Supplementary Levy (if any) and Case Fee to the Ombudsman Unit. The payment shall not be later than 30 calendar days after the date of assessment of payment by the Ombudsman Unit.
6.2.2 A Licensed Financial Institution or Insurance Company which fails to make payment of the Annual Levy or Supplementary Levy (if any) or Case Fee in full on or before the scheduled payment due date will be charged an administrative late payment charge as may be determined by the Ombudsman Unit. The Chief Ombudsman may refer the matter to the Central Bank to take any necessary action.
6.3 Annual Revenue Request
6.3.1 The Ombudsman Unit shall, when submitting the annual budget, also request from the Central Bank an approval of the following:
- Annual Levy;
- Supplementary Levy;
- Case Fee;
- Payment schedule;
- Appeal fee;
- Administrative charges for late payments;
- A record of Licensed Financial Institutions and Insurance Companies who are liable to pay the Annual Levy;
- A record of any general or special exemptions approved regarding the payment of the Annual Levy or Case Fees (wholly or partly).
- the Ombudsman Unit’s need for stability of funding;
Article 7: Information, Data and Confidentiality
7.1 Exchange of Information and co-operation
7.1.1 The Ombudsman Unit shall co-operate with the Central Bank with a view to ensuring that this Regulation operates in a way that contributes to promoting the best interests and protection of Consumers.
7.1.2 The Chief Ombudsman shall, whenever requested in writing to do so by the Central Bank, provide records or copies of records, or information, dealing with specified matters, or matters of a specified kind, relevant to the performance of the functions of the Central Bank.
7.2 Confidentiality
7.2.1 No Person, including a member of the Board of the Ombudsman Unit, the Chief Ombudsman, a member of the Staff of the Ombudsman Unit or a consultant or adviser to the Ombudsman Unit, shall disclose any confidential Information obtained by them while performing their duties or afterwards, unless disclosure of such Information is required by any applicable law, regulatory or judicial authority in the State.
7.2.2 Nonetheless, the above shall not operate to prevent the disclosure of Information by or on behalf of the Chief Ombudsman or the Board of the Ombudsman Unit to the Central Bank.
Article 8: Complaints against Ombudsman Unit
8.1 A party to a Complaint who is dissatisfied with the Standard of service provided by the Ombudsman Unit when dealing with a Complaint may lodge a service complaint against the Ombudsman Unit.
8.2 The Ombudsman Unit shall acknowledge receipt of the Complaint within 3 business days and provide a response to the party within 14 business days.
8.3 The Ombudsman Unit shall provide a report to the Central Bank, on an annual basis, of all service complaints received and/or addressed, in the format as determined by the Central Bank.
Article 9: Changes to Complaints Resolution Process
9.1 If the Board of the Ombudsman Unit proposes to make changes to the Complaints resolution process under this Regulation, it must ensure that a draft of the proposed amendment(s) to the Regulation is published on the website of the Central Bank for stakeholder consultation, which shall be accompanied by:
- an explanation of the proposed changes to the process within the Regulation; and
- a statement that representations about the proposals may be made to the Board of the Ombudsman Unit within a specified time
9.2 Any proposed amendments to the Regulation must be approved by the Board of Directors of the Central Bank, based on a recommendation of the Board of the Ombudsman Unit.
9.3 Immediately after approval of the amendments to the Regulation under 9.2, the Board of the Ombudsman Unit must arrange for them to be made available to the public.
- an explanation of the proposed changes to the process within the Regulation; and
Article 10: Conflict with Other Regulations
This Regulation is in addition to any requirement of any other regulatory authority as applicable to Licensed Financial Institutions and Insurance Companies. In case of any conflict with such requirement, the provisions of this Regulation will prevail.
Article 11: Enforcement and Sanctions
Noncompliance with any provision of this Regulation by the Licensed Financial Institutions or Insurance Companies is a regulatory violation and may be subject to supervisory action, sanctions and penalties as deemed appropriate by the Central Bank.
Article 12: Interpretation of this Regulation
The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation or any related Central Bank Regulations.
Article 13: Publication and Effective Date
This Regulation shall be published in the Official Gazette and shall be considered effective one month from the date of publication. This Regulation shall apply to the Ombudsman Unit, all Licensed Financial Institutions and Insurance Companies. The Ombudsman Unit will be operational as of one Year from the date of publication of this Regulation.
Regulated Products
Crowdfunding
Dormant accounts
Loan-Based Crowdfunding Activities Regulation
C 7/2020 Effective from 14/11/2020Dormant Accounts Regulation
C 1/2020 Effective from 15/2/2020Introduction
The Central Bank shall regulate and license Loan-based Crowdfunding Activities (“LCAs”) in the United Arab Emirates (“UAE”). By issuing this Regulation, the Central Bank aims to set out the minimum standards required of LCAs. Companies providing LCAs are encouraged to strive to meet higher standards than the minimum requirements set out in this Regulation.
Introduction:
Following consultations with Banks operating in the United Arab Emirates (U.A.E), and having conducted comparisons with regulatory requirements in this area, the Central Bank of the U.A.E. is issuing this Regulation to regulate the handling of dormant accounts and unclaimed balances.
This Regulation has been issued pursuant the powers of the Central Bank of the United Arab Emirates in accordance with the Decretal Federal Law no.14 of 2018 Regarding the Central Bank & Organization of Financial Institutions and ActivitiesObjective
The objective of introducing this Regulation is to put in place a framework for licensing, regulating and monitoring LCAs and to set out the standards that the Central Bank expects in this regard. The purpose of both the framework and the requirements is to:
- Safeguard the financial system from the risks posed by LCAs; and
- Safeguard the interests of consumers in the UAE.
- Safeguard the financial system from the risks posed by LCAs; and
Scope:
All Banks must comply with the provisions of this Regulation at all times
Application
This Regulation is issued pursuant to the powers vested in the Central Bank by the Decretal Federal Law No (14) of 2018 regarding the Central Bank and Organization of Financial Institutions and Activities.
Objective:
The purpose of this Regulation is to establish a general framework for the control and protection of dormant accounts in Banks and seek to enable customers (or legal owners) to receive the available balances on these accounts.
Scope
This Regulation shall apply to crowdfunding companies, wherever their platforms hosted, engaging in LCAs in the UAE, except in the Financial Free Zones.
A company is considered to be engaging in LCAs in the UAE if it meets one of the following conditions:
- If the company carrying out LCAs is incorporated in, or the crowdfunding platform is hosted in the UAE; or
- The crowdfunding platform uses a company’s address situated in the UAE for correspondence; or
- It provides LCAs to clients residing in the UAE.
Article (1): Definitions
- Bank/Banks: Any juridical person licensed in accordance with the provisions of the Central Bank Law, to primarily carry on the activity of taking deposits, and any other licensed financial activities;
- Board: The Bank’s board of directors;
- Central Bank: The Central Bank of the United Arab Emirates;
- Central Bank Law: Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities;
- Customer Communication: Any communication by the customer whether written or electronic in response to contact attempts initiated by Banks;
- Demand Deposit Accounts: All customer deposit accounts, payable on demand, including but not limited to current, call, savings, asset based liability accounts or any account with similar balance sheet treatment;
- Dividend: Dividends declared by the Bank to its shareholders and held in trust in Bank’s books for shareholders to claim;
- Dormant Customer: A customer (individual or corporate) who holds account(s) with a Bank, where all held accounts are individually eligible for dormancy and who holds no outstanding facilities with the same Bank in accordance with Article 2 of this Regulation
- Fixed Term Deposit Accounts: All customer deposits placed with a Bank for a fixed term period, with or without an early repayment option or any account with similar balance sheet treatment;
- Investment Accounts: An Investment Account is a portfolio account where a Bank invests the funds in assets (equity, mutual funds, bonds, structured products etc.) on behalf of a Customer;
- Joint Account: A jointly held account which has a distinct identity as a customer, separate from its individual joint owners;
- Outstanding Facilities: Any financing facilities due from customers, including but not limited to Credit Card balances, loan products, overdrafts etc. and off balance sheet products, also due from customers, such as Bank Guarantees, etc.;
- Safe Deposit Boxes: An individually secured container, in a Bank’s vaults, hired out to Bank’s customers for the safekeeping of their belongings;
- Senior Management: The executive management of the Bank responsible and accountable to the Board for the sound and prudent day-to-day management of the Bank, generally including, but not limited to, the Chief Executive Officer, chief financial officer, chief risk officer, and heads of the compliance and internal audit functions.
- Bank/Banks: Any juridical person licensed in accordance with the provisions of the Central Bank Law, to primarily carry on the activity of taking deposits, and any other licensed financial activities;
Article (1): Definitions
- Borrower: A UAE registered company (including sole proprietors) seeking a loan from one or more persons.
- Central Bank: Shall mean the Central Bank of the UAE.
- Client: Either a Borrower or a Lender on the Crowdfunding Platform (“CFP”).
- Client money: Money belonging to either the Borrower or the Lender of a CFP that is controlled by the CFP relating to loan-based crowdfunding activity.
- Pricing Platform: A type of Crowdfunding model whereby the platform is responsible for pricing borrower loans and administering the loans. The platform may not give any form of advice or place Lenders funds at its own discretion.
- Commitment period: the period specified by the CFP during which Lenders may commit to lending money to a particular Borrower.
- Controlling interest: The holding, directly or indirectly, of voting rights in another entity, or of the power to direct or cause the direction of the management of another entity.
- “Cooling-off” period: The period of at least two full business days starting at the end of the commitment period1
- Crowdfunding platform (‘CFP’): A web-based platform, social networking site or similar means used for the purpose of Crowdfunding activities.
- Crowdfunding: Crowdfunding is solicitation of funds from persons through a platform for a specific purpose.
- Funding goal: The amount that a borrower aims to raise on the CFP within a set time limit.
- Lender: A person for whom a CFP conducts / provides or intends to conduct / provide Regulated Activities under this Regulation. There are two types of clients who may participate in a CFP:
- Retail Lender: a Client that is not a Market Counterparty; and
- Market Counterparty: a Client that can evidence net assets of over AED 2,000,000 outside of their primary residence and self-attests to being treated as a Market Counterparty. Such self-attestation appropriately reviewed and verified by the CFP.
- Retail Lender: a Client that is not a Market Counterparty; and
- Loan: any funds provided to borrowers under a loan-based crowdfunding agreement through a CFP.
- Loan-based Crowdfunding Company: Whereby a company duly incorporated under the Federal Law No. 2 of 2015 Concerning Commercial Companies and its amendments (excluding Partnership and Limited Partnership companies), with the business objectives including E-Finance or similar activities, conducts its activity through a platform intermediating between lenders and borrowers engaging in loan-based crowdfunding activities which operates using only the pricing business model whereby lenders pick investment opportunities and the pricing of the loan is decided by the CFP.
- On-Boarding: the process of evaluating new clients, ensuring understanding and agreement of legal terms and opening of a new account.
- Person: natural or juridical person.
- Personal loan: a loan that is given to individual borrowers, where repayments are made from a verifiable regular income from a well-defined source, as defined under the Central Bank Regulations No. (29/2011) – Regulations Regarding Bank Loans & Other Services Offered to Individual Customers (as amended), or subsequent regulations issued in this regard.
- Regulated activities: Any activity that requires licensing by the Central Bank in order to be conducted legally in the UAE.
1 The CFP may choose to provide a longer period
- Borrower: A UAE registered company (including sole proprietors) seeking a loan from one or more persons.
Article (2): Criteria for Determining Dormant Accounts and Unclaimed Balances
First: Dormant Accounts
Dormancy is defined at customer level. For dormancy to apply, the customer should not have another active liability account with the same Bank, the current address of the customer is not known and the account does not have any litigations or requirements from other regulatory authorities.
Any correspondence from the customer or activity in relation to other accounts held with the same Bank shall be considered as evidence that the customer is still active and does not meet the definition of “dormant customer”.
Customers with asset accounts will be excluded from the purview of dormancy definition.
Joint accounts should be treated distinctly from individual accounts of their holders (individual/entities). Any activity in joint accounts does not impact dormancy classification in individual accounts held by the joint account holders and vice versa.
- An Individual/Corporate savings or call or current account where there has been no transactions (withdrawals or deposits) or non-financial actions (service requests, due diligence, particulars update, etc.) for a period of 3 years from the date of the last transaction on the account, other than transactions initiated by the Bank (such as interest and charges posted by the system or manually), and there has been no communication from the customer (whether written or electronic).
- A Fixed Term Deposit Account where there is no automatic renewable clause and where the deposit has matured, but neither renewal nor claim request has been made in the past 3 years since the deposit matured (or) where there is an automatic renewable clause, but there is no communication (whether written, electronic or verbal) from the customer within a period of 3 years from the date of first maturity.
- A closed ended Investment Account or a redeemable Investment Account where there is no communication from the customer for a period of 3 years from final maturity or redemption date, whichever is earlier. An open-ended Investment Account will be treated as Dormant, when the customer’s other accounts have been classified as dormant in accordance with this Regulation. However, the Bank shall liquidate or dispose of assets in the open-ended Investment Account only as per stated terms & conditions of the account.
- An Individual/Corporate savings or call or current account where there has been no transactions (withdrawals or deposits) or non-financial actions (service requests, due diligence, particulars update, etc.) for a period of 3 years from the date of the last transaction on the account, other than transactions initiated by the Bank (such as interest and charges posted by the system or manually), and there has been no communication from the customer (whether written or electronic).
Second: Unclaimed Balances
Unclaimed Bankers Cheques, Bank Drafts or Cashiers Orders
- Bankers cheques, bank drafts, or cashiers orders, which have been issued at the request of a customer by debit to his/her account, that have not been claimed by the beneficiary and remain unclaimed by the beneficiary or the customer for a period of 1 year (despite the efforts of the Bank to contact the customer).
Unclaimed Dividends
- Wherever, unclaimed dividend balances are held, the market regulator’s guidelines will govern the unclaimed dividend maintenance and re-claim process.
Unclaimed Contents of Safe Deposit Boxes
- Notwithstanding the provision of Article 474 of Federal Law No. 18 of 1993 on Commercial Transactions, the dormancy definition shall apply as follows:
Where charges for a safe deposit box remain outstanding for a period of more than 3 years and the Bank has not received a reply from the Safe Deposit Box tenant, or the tenant has not made alternative arrangements in relation to the Safe Deposit Box.
- To comply with the above, the customer does not have another active account with the same Bank (liability or assets). Safe Deposit Box operations by nominees is not sufficient for maintaining them as active in status.
- Notwithstanding the provision of Article 474 of Federal Law No. 18 of 1993 on Commercial Transactions, the dormancy definition shall apply as follows:
Article 2: Categories
- LCAs are categorised according to lending volume:
- Category 1 (Large): Cumulative loans facilitated in a calendar year AED 5,000,000 and above; or
- Category 2 (Small): Cumulative loans facilitated in a calendar year below AED 5,000,000.
- Category 1 (Large): Cumulative loans facilitated in a calendar year AED 5,000,000 and above; or
- For the purpose of the above, the references to lending volume shall mean either:
- Cumulative loans in the preceding year(s); or
- In the case of new applicants, the projected / forecasted volume for the current year(s).
- Cumulative loans in the preceding year(s); or
- The company wishing to undertake LCAs must apply to the Central Bank for an LCAs license. Such a license will be issued either as a Category 1 or Category 2 as per the definitions in Article 2 (1).
- A crowdfunding company that is licensed to operate as Category 2 and wishes to upgrade its license to Category 1 status, must evidence that it meets all regulatory requirements for a Category 1 license before any application to upgrade can be considered.
- Once a crowdfunding company is deemed to be Category 1 it cannot be deemed Category 2 again without prior written approval from the Central Bank.
- LCAs are categorised according to lending volume:
Article (3): Required Action when an Account Becomes Dormant
- The Bank must attempt to contact the Dormant Customer through written, electronic or verbal (recorded) channels for re-activation of the account
- A communication must be initiated to issuers of unclaimed bankers cheques, bank drafts, or cashier orders; notifying them of non-encashment of the issued instruments
- A final notice must be sent to the dormant Safe Deposit Box tenant’s last known address.
- The Bank must wait for a period of 3 months for a response, from the Dormant Customers, beneficiaries of unclaimed bankers cheques, bank drafts, cashier orders Unclaimed Balances”, and Safe Deposit Box tenants.
- After expiry of the 3 months period mentioned above, the Bank must transfer the money in the dormant account to the “dormant accounts ledger”.
- The balances in unclaimed bankers cheques, bank drafts and cashier orders must be transferred to the “unclaimed balances account” within the Bank.
- For Safe Deposit Boxes, if there is no response, the Bank should apply to the Court to appoint a person to supervise the opening of the box and provide direction regarding disposal of contents found in the box or the appointment of a Court receiver.
- Non-interest bearing dormant accounts may be closed at the discretion of the Bank and balances preserved in the “unclaimed balances account”.
- Access to the Dormant Customer’s documents, including specimen signatures, should be controlled and monitored with a display message clearly denoting “Dormant Account” whenever accessed, to prevent unauthorized operations in these accounts. Wherever Banks continue to maintain physical copies of documents, they must be segregated physically and placed under dual control until the account balances are transferred to the Central Bank. Post transfer of balances to the Central Bank. Banks, may maintain, for perpetuity, only digital/scanned copies of customer documents.
- The Bank must attempt to contact the Dormant Customer through written, electronic or verbal (recorded) channels for re-activation of the account
Communication to the Central Bank
- The report of all transferred accounts/amounts in a quarter must be provided to the Central Bank through the banking return forms (BRF) filed for that quarter, with a copy each to the Banking Operations Department and the Banking Supervision Department at the Central Bank.
- Banks must report Dormant Accounts separately in local and foreign currency under appropriate fields in the BRF reporting system.
- The detailed list of contents of all opened Safe Deposit Boxes in the quarter must be provided to the Central Bank through the BRF filed for that quarter.
- The report of all transferred accounts/amounts in a quarter must be provided to the Central Bank through the banking return forms (BRF) filed for that quarter, with a copy each to the Banking Operations Department and the Banking Supervision Department at the Central Bank.
Article 3: Licensing Requirements
Application for License:
- A crowdfunding company shall apply to the Central Bank for a licence in the form prescribed by the Central Bank’s licensing manual.
- The application and all supporting documents shall be in either Arabic or English. Documents in any other language shall be accompanied by a certified English or Arabic translation. Any financial figures should be presented in UAE Dirham (AED).
Category:
- The crowdfunding company shall stipulate which Category of license it is applying for and provide reasoning for such a decision, which includes how that Category fits into its wider strategy.
- The crowdfunding company shall provide details of any plans it may have to move to a different Category license over time.
Core Information:
- The core information required as part of an initial application for an LCAs license is set out in further detail in Appendix 1 and in the Central Bank’s Licensing manual which will be provided to the applicant on request.
- A CFP that is regulated in another jurisdiction and is applying for a license to set-up a subsidiary in the UAE shall obtain a No-Objection Letter from its home-jurisdiction regulator that is addressed to the Central Bank by its home regulator.
- The Central Bank as a condition of the license may require the crowdfunding company to appoint a skilled person(s) to carry out a 3rd party assessment of any aspect of the company’s proposed business model/systems. The findings and reports of the 3rd party assessment will form part of the core licensing information required to be submitted by an applicant to the Central Bank.
- The Central Bank shall communicate its decision considering the merits of the application and:
- Grant the licence with or without conditions and limitations; or
- Reject the application, stating the reasons for rejecting the application
- Grant the licence with or without conditions and limitations; or
- Drafts may be accepted for certain documents required for the application but their content may not be changed substantially once pre-approval is provided.
Validity of License:
- The licence shall be valid for a period of twelve (12) months and shall renew subject to Central Bank’s approval.
- A crowdfunding company shall pay the relevant application fee at the time of submitting its application to the Central Bank and shall also annually pay a license fee to the Central Bank when it renews its licence.
Cancellation and Modification of License:
- The Central Bank may cancel or modify a licence if the crowdfunding company:
- Has not commenced to operate the business within one (1) year of the date Central Bank granting the LCAs licence;
- Ceases to operate for a period exceeding six (6) months;
- Failed to fulfil its obligations under this regulation; or
- Posed undue risk to consumers or the financial system.
- Has not commenced to operate the business within one (1) year of the date Central Bank granting the LCAs licence;
- The Central Bank will give a notice, including its reasons, to a crowdfunding company within twenty (20) days of implementing the action.
- Where a crowdfunding company voluntarily submits a request to surrender its licence, the Central Bank will evaluate and consider such a request, including the adequacy of arrangements made by the crowdfunding company for an orderly wind down and/or otherwise impose such conditions as it deems fit to ensure that continuing obligations are satisfactorily addressed.
Ongoing Obligations:
- A crowdfunding company shall ensure criteria set out in this Article are met on an ongoing basis and comply with any conditions or limitations set forth on an ongoing basis.
- The Central Bank may undertake site inspections or instruct crowdfunding companies to conduct independent assessments at periodic intervals confirming that the criteria and conditions under this Article are being satisfied on an ongoing basis.
Bank Guarantee:
- Should the application be approved, crowdfunding companies must undertake to provide a bank guarantee drawn in favour of the Central Bank and issued by a locally incorporated UAE bank of value equal to the required paid-up capital as per Article 4.
Further Information:
- The Central Bank may seek any additional information from a crowdfunding company as it deems necessary throughout the application process.
- A crowdfunding company shall apply to the Central Bank for a licence in the form prescribed by the Central Bank’s licensing manual.
Article (4): Claim of Funds from a Dormant Account
- If a customer has reason to believe that he/she has funds in a dormant account, he/she should personally, or through a legal representative, approach the Bank concerned and submit a claim with all relevant documentation to prove his/her identity.
- If the customer wants to reactivate a dormant account, the Bank may allow it after taking a photocopy of his/her current ID, verifying them with the originals and updating other details of his/her profile. Banks may also utilize alternate channels of authentication for Dormant Accounts re-activation.
- The Bank, after verifying with the original ID and being satisfied with all other details received, should pay the amount with accrued interest, where applicable (before transfer to the Central Bank), to the customer and maintain a record with following details:
Payments Made Against a Dormant Account
Date of Payment of Amount Final Amount Paid Amount (as in Register/
ledger)Account No & Type of Account Full name of the customer (as recorded) (In any case the Bank should settle claims within a period of one month unless there are valid reasons for delay)
- The accounts of such customers should be monitored closely to ensure such accounts have not and are not being used for the purposes of money laundering or fraudulent purposes.
- Unclaimed bankers cheques, bank drafts and cashier orders’ claims are to be settled in accordance with the applicable UAE legal framework and Banks’ policies and procedures in relation to these instruments.
- If a customer has reason to believe that he/she has funds in a dormant account, he/she should personally, or through a legal representative, approach the Bank concerned and submit a claim with all relevant documentation to prove his/her identity.
Article 4: Prudential Requirements
Capital Requirement:
- The minimum capital for a crowdfunding company shall be:
- Category 1: AED 1,000,000; or
- Category 2: AED 300,000.
- Category 1: AED 1,000,000; or
- The crowdfunding company must hold the higher of:
- The capital as stated under Article 4.1; or
- Capital equivalent to 5% of the outstanding lending volume
- The capital as stated under Article 4.1; or
- The minimum capital for a crowdfunding company shall be:
Article (5): Responsibilities of Banks
- Banks must ensure that customers’ profiles are always updated, as instructed via the UAE’s Anti-Money Laundering framework; Decree Federal Law No. 20 of 2018 on AML/CFT and Illegal Organizations, Cabinet Resolution No. 10 of 2019 regarding the implementing Regulation of the Decree Federal Law No. 20 of 2018 on AML/CFT and Illegal Organizations, Notice 74/2019 regarding Procedures for AML/CFT and Illicit Organizations and Notice 79/2019 regarding Guidelines on AML/CFT and Illegal Organizations. Banks must also periodically advise their customers through letters, emails and SMS alerts to update their IDs, address and telephone numbers. Banks may introduce “inactive” status for accounts, with transaction restrictions as necessary before the account becomes dormant for their enhanced monitoring.
- In order to reduce the number of dormant accounts, Banks must carry out an annual review of such accounts and contact the customers through letters, telephone calls, SMS alerts and emails as feasible, and advise them of the dormancy and the need to activate the account.
- Banks must evolve suitable systems so that the customers do not face difficulty in closing a dormant account or re-activating it for normal operations. No fee or charges should be levied for re-activation or closing such accounts.
- All dormant accounts and unclaimed balances accounts must be fully reconciled on a monthly basis (at least) and be subject to review by the external auditor annually.
- Banks must ensure that customers’ profiles are always updated, as instructed via the UAE’s Anti-Money Laundering framework; Decree Federal Law No. 20 of 2018 on AML/CFT and Illegal Organizations, Cabinet Resolution No. 10 of 2019 regarding the implementing Regulation of the Decree Federal Law No. 20 of 2018 on AML/CFT and Illegal Organizations, Notice 74/2019 regarding Procedures for AML/CFT and Illicit Organizations and Notice 79/2019 regarding Guidelines on AML/CFT and Illegal Organizations. Banks must also periodically advise their customers through letters, emails and SMS alerts to update their IDs, address and telephone numbers. Banks may introduce “inactive” status for accounts, with transaction restrictions as necessary before the account becomes dormant for their enhanced monitoring.
Article 5: Governance
- A crowdfunding company shall have adequate staff who possess the requisite qualifications, competencies and skills to individually and collectively provide the range of skills and experience to manage its affairs in a sound and prudent manner.
- A crowdfunding company shall ensure that the following relevant functions/persons are ‘fit and proper’:
- Members of the Board of Directors;
- Chief Executive Officer or General Manager;
- Chief Financial Officer or equivalent;
- Chief Risk Officer or equivalent;
- Head of Compliance or equivalent;
- Money Laundering Reporting Officer; and
- Sharia advisor, as appropriate when offering Islamic products.
- Members of the Board of Directors;
- To be considered ‘fit and proper’, the relevant person shall demonstrate personal integrity, honesty and good reputation, shall be competent to undertake the role assigned and shall be financially sound. The relevant person must not have:
- Served as an auditor of a crowdfunding company while concurrently serving in the board of directors of the same crowdfunding company.
- Been terminated from any senior executive position in a company engaged in financial activities on the basis of disciplinary matters or on the basis of a disciplinary action based on a court judgement.
- Been found guilty of any crime that violates honour or ethics, or that involves violence.
- Failed to honour financial liabilities to any bank or creditor.
- Declared bankruptcy or failed to reach a settlement agreement with creditors.
- Had properties confiscated; or
- Been placed under court receivership, unless he had been rehabilitated or pardoned by the relevant authorities.
- Served as an auditor of a crowdfunding company while concurrently serving in the board of directors of the same crowdfunding company.
- All licensed crowdfunding companies must comply with applicable Emiratization requirements issued by the National Human Resources Development and Employment Authority, or any other UAE government ministry and subsequent Central Bank requirements.
- A crowdfunding company shall have adequate staff who possess the requisite qualifications, competencies and skills to individually and collectively provide the range of skills and experience to manage its affairs in a sound and prudent manner.
Article (6): Responsibilities of the Bank to the Customer
- Banks must inform customers of their following responsibilities:
- If the customer changes his/her address or contact numbers, he/she should inform the Bank through relevant channels.
- The customer should keep all correspondence relating to the account between themselves and the Bank in a secure place for future reference.
- The customer should check the statements sent to him/her and acknowledge receipt where required by the Bank to do so.
- If the customer changes his/her address or contact numbers, he/she should inform the Bank through relevant channels.
- Banks must inform customers of their following responsibilities:
Article 6: Risk Governance Framework
- The crowdfunding company must have an appropriate risk governance framework in place that identifies all material risks. This includes policies, processes, procedures, systems and controls to identify, measure, evaluate, monitor, report and control or mitigate material sources of risk on a timely basis.
- A crowdfunding company’s definition and assessment of material risks must take into account its risk profile, nature, size and complexity of its business and structure.
- The crowdfunding company must have in place mitigating action plans for key material risks and monitor these on an ongoing basis.
- The risk governance framework shall address, amongst other key risks, the following areas:
- Operational risk;
- Conduct risk;
- Fraud by employees;
- Cybercrime and attacks;
- Money laundering;
- Managing defaults;
- Miss-selling risk;2 and
- Terrorist financing
- The board of the crowdfunding company is ultimately accountable for the risk governance framework.
- The crowdfunding company shall have appropriate governance arrangements in place that include a sufficient focus on risk management and ensure that the Chief Risk Officer, or equivalent, reports directly to the Board with an appropriate reporting line to the Chief Executive Officer or General Manager.
- The crowdfunding company must have a detailed exit plan to provide for the orderly wind down of the crowdfunding company business. The exit plan must also assume that in the event of failure of the crowdfunding company, loans will continue to be administered and lender funds protected.
2 e.g. how the CFP advertises and how it sells to clients and the appropriateness of messages, among others.
- The crowdfunding company must have an appropriate risk governance framework in place that identifies all material risks. This includes policies, processes, procedures, systems and controls to identify, measure, evaluate, monitor, report and control or mitigate material sources of risk on a timely basis.
Article (7): Consumer Protection
- It must be clearly understood that the money in a dormant account will remain the property of the account holder, or his/her legal heirs, if the account holder has died.
- Where it is an interest bearing account, interest will continue to accrue at prevailing rates depending on the terms of the contract between the Bank and the customer until the time the balance is transferred to the Central Bank. No fees other than those agreed, during the lifecycle of account activity, should be levied on such dormant accounts.
- Once an account has been classified as dormant, physical and electronic statement generation should be suppressed. However, the account/customer should not be precluded from other routine Bank communication lists on account of dormancy.
- No debits or system based charges must be levied on dormant accounts. However, credits received, if any, are allowed to be deposited in the account. Such credits will not however interfere with the criteria for dormant accounts as set out in Article 2.
- Banks must ensure that important terms relating to dormant accounts are included in the terms and conditions for account opening and hiring of Safe Deposit Boxes to ensure transparency for the customer, including the condition that the Central Bank is not taking any responsibility as a result of transferring the amounts available in the Dormant Accounts or Unclaimed Balances to the Central Bank in accordance with this regulation.
- It must be clearly understood that the money in a dormant account will remain the property of the account holder, or his/her legal heirs, if the account holder has died.
Article 7: Internal Controls
Systems & controls
- A crowdfunding company shall ensure that it has instituted adequate internal controls, ensured proper segregation of duties within the organisational structure and that its operations are undertaken within the boundaries of clearly documented policies, authorities and procedures
Outsourcing
- A crowdfunding company shall seek prior approval from the Central Bank wherever it proposes to enter into a material outsourcing arrangement with other parties. The systems and controls established in relation to the crowdfunding company’s operation shall at the minimum meet the standards set by this regulation. All outsourcing arrangements shall meet the Central Bank requirements.
- For the purpose of the above, an outsourcing contract is material if its failure would pose significant risk of disruption, or insolvency or detrimental impact on its ability to provide services to clients.
External Audit
- A crowdfunding company shall appoint external auditors.
- A crowdfunding company shall seek approval from the Central Bank before appointing or re-appointing its external auditors.
- A crowdfunding company shall ensure that the external audit firm responsible for their audit does not undertake that function for more than six (6) successive years and that the Partner in charge of the audit is rotated every three (3) years.
- A crowdfunding company shall ensure that it has instituted adequate internal controls, ensured proper segregation of duties within the organisational structure and that its operations are undertaken within the boundaries of clearly documented policies, authorities and procedures
Article (8): Transfer of Funds in Dormant Accounts or Unclaimed Balances to the Central Bank and Reclaim Procedures
- If an account remains dormant for a period of 5 years from the date of the last transaction on the account, the Bank must transfer the net amount to “Unclaimed Balances Account - Dormant Accounts” at the Central Bank. This is provided the customer has no other active accounts with the same Bank and provided the current address of the owner of the account is unknown.
- If a bankers cheque, bank draft or cashier order remains unclaimed for a period of 5 years from date of issue, the Bank must transfer net amounts pertaining to these instruments to “Unclaimed Balances Account - Dormant Accounts” at the Central Bank.
- Banks must close dormant accounts after transfer to Central Bank, however account related documents must be preserved in accordance with Article (3) of this Regulation.
- If receivables of a dormant Safe Deposit Box remain unclaimed for a period of 5 years from the date of the last transaction on the account, the Bank must transfer the net amount (after deducting charges, if any, in accordance with Article 3) to “Unclaimed Balances Account - Dormant Accounts” at the Central Bank.
- Any unclaimed balances in foreign currencies must be converted as of date of transfer at the Bank’s published customer rates, before transfer to the Central Bank. Customers will be reimbursed this AED equivalent amount on reclaim.
- Banks must transfer all dormant account funds balances to the Central Bank in accordance with this article, irrespective of the size of the residual fund balance.
- Banks should use the following form titled “Movement in Dormant Accounts - Deposits and Withdrawals” to record fund movements to and from “Unclaimed Balances Account – Dormant Accounts”. Banks should use the formats provided in guidelines from the Central Bank for withdrawing funds from the said account at the Central Bank, if the customer approaches the Bank for withdrawal/re-activation of the account.
Movement in Dormant Accounts – Deposits and Withdrawals
Balance Withdrawals Deposits Account Number Name of Customer and his ID Details Name of the Bank & Branch Date Amount Date Amount Ref. No Date Amount Ref No. - The settlement of customer claims on dormant accounts shall be carried out post receipt of relevant funds from Central Bank.
- Direct debits, manager’s cheques and cashier orders transferred to the Central Bank, when presented for clearing must be put on hold, pending receipt of such funds from the Central Bank. The process of verification of such instruments must be in accordance with the UAE legal framework and Banks’ policies and processes in relation to these instruments.
- If an account remains dormant for a period of 5 years from the date of the last transaction on the account, the Bank must transfer the net amount to “Unclaimed Balances Account - Dormant Accounts” at the Central Bank. This is provided the customer has no other active accounts with the same Bank and provided the current address of the owner of the account is unknown.
Article 8: Conduct of Business
Lender selection and suitability
- A crowdfunding company must take reasonable care in on-boarding Lenders, assessing the suitability of the Lender and ensuring the Lender has a clear understanding of the risks they are undertaking. This process shall be documented and relevant employees shall have appropriate training.
- In addition to other checks (e.g. for money laundering), a crowdfunding company shall verify and document the identity of a Lender and confirm their address. Such measures include (but are not limited to) the following:
- Call the client on their home or business contact numbers;
- Contact an employer to confirm employment, after gaining the client’s consent;
- Review bank statements for details of salary and other income; or
- Requesting documents confirming their identity
- Call the client on their home or business contact numbers;
- A crowdfunding company shall obtain sufficient information from Lenders about their financial circumstances and objectives through self-declared assessment questionnaire forms, or by any other equivalent means.
- Based on the information provided and independently reviewed by the crowdfunding company, the CFP shall classify all Lenders as a Retail or Market Counterparty. The classification shall be shared with the Lender.
Lending structure
- A crowdfunding company shall structure its activities in a clear, transparent format using plain language that shall be stipulated within an enforceable (lending) contract, taking into account Appendix 2 of this Regulation.
- A crowdfunding company must ensure that, when a loan is made using its platform, there is a written loan agreement in place between the Borrower and Lender that is legally enforceable and sets out sufficient details of the loan, the terms of repayment and the rights and obligations of the Borrower and Lender.
Borrower Risk Scoring, Loan Pricing and Due Diligence
A crowdfunding company shall be responsible to:
- Ensure there is a sufficient and transparent risk scoring and loan pricing system in place. The basis and methodology of risk scoring, loan pricing and due diligence shall be made publically available.
- Obtain self-declared risk assessment questionnaire forms from their Borrowers.
- Take reasonable steps to confirm the information provided in the risk assessment questionnaire.
- Take adequate measures to prevent Borrowers from seeking loans for personal use.
- Requiring a range of information, including Al-Etihad Credit Bureau reports, to enable the risk scoring and loan pricing, including cash flow forecasts.
- Carry out a risk assessment on prospective Borrowers based on the information required.
- Taking reasonable care to undertake thorough anti-money laundering (AML) checks and establishing the ultimate beneficial owner of the Borrower.
- Ensure what is treated as a default is in accordance with the Central Bank definition and methodology. Default rates on projects/borrowers listed on the platform must be made publically available.
- Implement policies to manage disputes / conflicts of interest.
- Ensure there is a sufficient and transparent risk scoring and loan pricing system in place. The basis and methodology of risk scoring, loan pricing and due diligence shall be made publically available.
- A crowdfunding company shall conduct reasonable due diligence and risk assessment on a Borrower and communicate the result of the due diligence to the Lenders within the risk scoring process.
- A crowdfunding company shall review the financial situation of Borrowers at least annually and in the event of any material change, communicate its assessment to clients.
- In the event that a crowdfunding company identifies any issues with the Borrower that increase the risk score of that Borrower, the crowdfunding company shall communicate its findings with the relevant Lenders and develop an action plan for how outstanding balances on any loans related to that borrower will be managed.
- A crowdfunding company shall require Borrowers to declare its current and intended borrowing from other CFPs and other sources in a calendar year. A crowdfunding company should take reasonable steps to monitor whether Borrowers are accessing loans through any other sources, including regularly checking with Al Etihad Credit Bureau.
Ceilings on lending
- A crowdfunding company shall impose a limit on lending per person per project (per calendar year) to:
- Retail Client: AED 20,000; and
- Market counterparty: AED 50,000
- Retail Client: AED 20,000; and
- A crowdfunding company shall impose a limit on total lending per person (per calendar year) to:
- Retail Client: AED 200,000; and
- Market counterparty: AED 500,000
- Retail Client: AED 200,000; and
Ceilings on borrowing
- The borrowing limit for Borrowers in any calendar year is AED 10,000,000.
- Borrowers may only list themselves on one CFP per project. The crowdfunding company and its management shall be responsible for ensuring, as part of the due diligence of Borrowers, that the borrower is not listed on any other CFP for the same project.
Loan release
- Crowdfunding companies shall prevent borrowers from gaining access to:
- Any amounts raised unless the borrowers raised 100% of its funding goal.
- Any amount exceeding the funding goal.
- Any amounts raised unless the borrowers raised 100% of its funding goal.
Client information confidentiality
- A crowdfunding company shall maintain the strictest standards of client information confidentiality including implementing the necessary systems and controls to ensure such standards are met.
Client money
- A crowdfunding company shall not accept, take, or receive the transfer of full ownership of money from clients.
- A crowdfunding company shall ensure adequate protection of Client Money.
- Where a crowdfunding company makes arrangements on behalf of a client to receive and disburse funds, such monies shall be maintained in segregated/ escrow accounts in the name of the client as per the agreed arrangements.
- The segregated/escrow accounts holding clients’ money must be externally audited:
- on a monthly basis for Category 1 CFPs; and
- on a quarterly basis for Category 2 CFPs
- on a monthly basis for Category 1 CFPs; and
- Client funds shall only be held with local retail banks who are licensed and regulated by the Central Bank.
Information disclosures
- All crowdfunding companies shall disclose the terms and conditions of their business to their Clients and any subsequent updates to these terms and conditions.
- All crowdfunding companies shall provide necessary (written) warnings of material risks to Clients.
- A crowdfunding company shall collaborate and coordinate with Al Etihad Credit Bureau and share information concerning both its Lender(s) and Borrower(s).
- Further to the above, all crowdfunding companies shall also make Clients aware of the relevant information as set out in Appendix 3.
Disclosures to Lender
- For the purposes of the above, a crowdfunding company shall disclose comprehensive information about the Borrowers linked to a specific project directly to Lenders. The information expected shall include (at a minimum) the following:
- Information on the business model or operation of the Borrower, both historical and projected.
- Critical success factors and important dependencies.
- Information on the financial condition of the Borrower.
- Risks relevant to the Borrower based on due diligence undertaken by the CFP including expected default rates.
- Other borrowing and repayment terms.
- CFP’s fees and charges on the specific project.
- Terms of repayment and controls and precautionary measures taken, and
- Right of cancellation of contracts and lawful jurisdiction applicable for any disputes.
- Information on the business model or operation of the Borrower, both historical and projected.
Conflicts of interest
- A crowdfunding company and the key personnel shall take steps to identify/disclose and prevent or manage conflicts of interest. Examples of conflicts of interest include (but not limited to) the following:
- A crowdfunding company lists a Borrower who is a related party to a CFP (or its significant shareholders / directors / employees);
- A crowdfunding company has an interest in the outcome of a service provided to the Client, which is distinct from the Client's interest in that outcome;
- A crowdfunding company has a financial or other incentive to favour the interest of another Client or group of Clients over the interests of the Client;
- A crowdfunding company receives or will receive from a person other than the Client an inducement in relation to a service provided to the Client, in the form of money, goods or services, or
- A crowdfunding company (or its significant shareholders / directors / employees) has financial interest in a Borrower.
- A crowdfunding company lists a Borrower who is a related party to a CFP (or its significant shareholders / directors / employees);
- A crowdfunding company shall not allow any of its shareholders, directors or employees to borrow on the platform.
- A crowdfunding company shall not provide advice to Clients relating to any crowdfunding available through its CFP.
- A crowdfunding company may not directly market any offer, Borrower or project available on the CFP to any current or prospective Client.
Dispute management
- A crowdfunding company shall:
- Establish dispute handling and grievance redress mechanisms to deal with complaints from clients or other parties and include in client agreements the details of these mechanisms.
- Develop an adequate collections policy and procedures, setting out actions to be taken against borrowers who fail to make timely payments.
- Maintain records demonstrating to the Central Bank that it has control mechanisms in place to address complaints and grievances.
- Establish dispute handling and grievance redress mechanisms to deal with complaints from clients or other parties and include in client agreements the details of these mechanisms.
Contingency Portfolio Administration Arrangements
- In the event that a crowdfunding company fails or is wound up (either voluntarily or involuntarily), the crowdfunding company must have in place documented arrangements to ensure that the loan portfolio continues to be administered.
- The board of the crowdfunding company bears ultimate responsibility for ensuring that contingency portfolio administration arrangements are in place.
- The Central Bank will periodically review the contingency portfolio administration arrangements and may take supervisory or enforcement actions if such plans are found to be inadequate.
- A crowdfunding company must take reasonable care in on-boarding Lenders, assessing the suitability of the Lender and ensuring the Lender has a clear understanding of the risks they are undertaking. This process shall be documented and relevant employees shall have appropriate training.
Article (9): Retention of Dormant Account Balances with the Central Bank
- Funds transferred to the “Unclaimed Balances Account - Dormant Accounts” will be retained by the Central Bank from the date of transfer to the said account until claimed by the beneficiary.
- Funds transferred to the Central Bank will no longer generate interest payments by the Bank.
For avoidance of doubt, the Central Bank shall not be liable for any interest payments on the transferred funds.
- Furthermore, the Central Bank is not legally responsible or obligated in any manner, with any claim whatsoever, related to interest, returns, and/or profits, or other, on funds transferred to the Central Bank.
- Funds transferred to the “Unclaimed Balances Account - Dormant Accounts” will be retained by the Central Bank from the date of transfer to the said account until claimed by the beneficiary.
Article 9: Reporting and Record Keeping
Reporting to the Central Bank
- A crowdfunding company shall submit reports to the Central Bank in the prescribed form within thirty (30) days of the period specified below:
- Category 1: Quarterly (as of the end of 31 March, 30 June, 30 September and 31 December);
- Category 2: Semi-annually (as of the end of 30 June and 31 December); and
- A crowdfunding company shall file its annual audited financial statements with the Central Bank.
- Category 1: Quarterly (as of the end of 31 March, 30 June, 30 September and 31 December);
- The crowdfunding company shall report the following (at a minimum) to the Central Bank:
- Financial position;
- Client money held;
- Description of complaints received and resolution status of these complaints;
- Details of loans arranged each quarter; and
- Defaults and near-defaults.
- Financial position;
Record keeping
- A crowdfunding company shall maintain adequate books and records at all times.
- All records and materials must be made available for inspection by the Central Bank from time to time.
- Records of Client Money and completed transactions shall be kept for a minimum period of ten (10) years.
- The records maintained shall include:
- Historical records of information displayed online (websites / social media / any other media) and any print copies, if applicable, displaying the crowdfunding company’s promotional communication, advertisements or online banners and tag lines;
- Internal policies, procedures and operating documents;
- Corporate and financial records and general ledger and sub-ledgers;
- Reports and statements issued to Clients and regulators;
- Any communications related to Clients, including confirmations related to risk understanding, classification documents and confirmation related to classification, amongst others;
- All suitability assessments of Clients, including any clients (both Lenders and Borrowers) that were deemed not suitable by the crowdfunding company.
- Management information, accounts and communications.
- HR records; and
- IT architecture and security related documents.
- Historical records of information displayed online (websites / social media / any other media) and any print copies, if applicable, displaying the crowdfunding company’s promotional communication, advertisements or online banners and tag lines;
- The board of the crowdfunding company is directly responsible to the Central Bank in relation to reporting breaches.
- A crowdfunding company shall submit reports to the Central Bank in the prescribed form within thirty (30) days of the period specified below:
Article (10): Cancellation of Previous Circulars
This Regulation repeals and replaces the Dormant Accounts Regulation, issued under Circular No. 106/2018 in April 2018.
Article 10: Interpretation
- The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
- The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
Article (11): Interpretation of this Regulation
The Regulatory Development Division of the Central Bank is the sole interpreter to the provisions of this Regulation, and its interpretations shall be considered final.
Article 11: Publication and Application
- This Regulation shall be published in the Official Gazette in both Arabic and English and shall come into effect one (1) month from the date of its publication.
- This Regulation shall be published in the Official Gazette in both Arabic and English and shall come into effect one (1) month from the date of its publication.
Article (12): Enforcement and Sanctions
Violation of any provision of this Regulation may be subject to supervisory action and sanctions as deemed appropriate by the Central Bank.
Appendix 1: Detailed Licensing Requirements
- When applying for a crowdfunding company license, the application must include the following information/documents. The Central Bank may request further information as part of the process.
- Completed application form
- Strategy overview
- Business plan, including;
- Background to the business and history
- Corporate governance system and organization structure, including:
- Background to the business and history
- Committee structures and responsibilities;
- Conflict of interest policy; and
- Reporting lines
- Group structure, if applicable;
- Financial position (if applicable) and projected income and expenditure operation for the next three (3) years, including;
- Group structure, if applicable;
- Opening balance sheet
- Monthly forecasts of profit and loss
- Cash flow forecast
- Targeted clients, products and services, including:
- Opportunities identified in the UAE and expected volume of clients
- International opportunities and expected volume of customers
- Client segments to be served
- Fees structure payable by clients and borrower
- Opportunities identified in the UAE and expected volume of clients
- Marketing approach and delivery channels;
- Information and cyber security arrangements;
- Technology infrastructure, outsourcing arrangements, data warehousing arrangements, webhosting;
- Constitutional documents (such as board resolution) or draft (if available);
- Ownership details;
- Shareholder or partners’ details;
- Proof of identity for shareholders who are natural persons (a minimum of two separate documents); and
- Details and proof of identity (as above) for the ultimate beneficial owner
- Shareholder or partners’ details;
- The background and experience of senior management, including CVs of senior management1;
- An assessment of key risks and mitigants, including risks relating to;
- Client asset handling arrangements;
- Inadequate systems and controls;
- Economic factors; and
- Competitors
- Client asset handling arrangements;
- Audited financial statements (for the past three years, if available);
- Exit strategy and plan which includes, at a minimum;
- Identification of key risks and business disruptors
- Effects of key risks on CFP including reverse stress test and contingency planning arrangements
- Identification of key risks and business disruptors
- Identification of key risks and business disruptors
- Application fee (if applicable)
- Completed application form
1 Senior management is understood to mean Chief Executive Officer (CEO), Chief Financial Officer (CFO), Chief Risk Officer (CRO), Head of Compliance and Head of Internal Audit (or their equivalents) at a minimum
- When applying for a crowdfunding company license, the application must include the following information/documents. The Central Bank may request further information as part of the process.
Article (13): Application and Publication
This Regulation shall be published in the Official Gazette in both Arabic and English and shall come into effect one month from the date of publication.
Appendix 2: Additional Terms for Crowdfunding Platforms
2. The following terms must be included in a Client Agreement between a crowdfunding company and a Lender:
a. the crowdfunding company’s obligations to administer the loan, including:
i. how payments made by the Borrower will be transferred to the Lender.
ii. steps that will be taken if payments by a Borrower are overdue or the Borrower is in default; and
iii. Clear guidelines on what is considered to be a default
b. if the Lender is a Market Counterparty, the steps that will be taken by the CFP and Lender to ensure that the Lender complies with any applicable limits relating to the amounts of loans that may be made using the platform;
c. the contingency arrangements that the crowdfunding company will put in place to deal with a platform failure or if the CFP ceases to carry on its business.
3. The following terms must be included in a Client Agreement between a crowdfunding company and a Borrower:
a. a restriction on the Borrower using any other Crowdfunding service to raise funds during the commitment period;
b. a restriction on the Borrower or any Person that is connected to the Borrower, lending or financing, or arranging lending or finance for a Lender using the service;
c. a restriction on the Borrower advertising its proposal, or soliciting potential lenders or investors, outside the platform during the commitment period;
d. a requirement on the Borrower to give reasonable advance notice to the operator of any material change affecting the Borrower, its business or the carrying out of its proposal;
e. the obligations of the Borrower to disclose if there is any material change after funds have been provided; and
f. An obligation on the Borrower to produce financial statements, including bank statements at least annually.
Appendix 3: Required Crowdfunding Company Disclosures
- A crowdfunding company must prominently disclose on its website key information about how its service operates, including:
- Details of how the CFP functions;
- Details of how and by whom the crowdfunding company is remunerated for the service it provides, including fees and charges it imposes;
- Any financial interest of the crowdfunding company or significant shareholders, directors or employees of the crowdfunding company, that may create a conflict of interest;
- The eligibility criteria for Borrowers that use the CFP;
- The minimum and maximum amounts of loans that may be sought by a Borrower;
- What, if any, security is usually sought from Borrowers, when it might be exercised and any limitations on its use;
- The eligibility criteria for Lenders that use the service;
- Any limits on the amounts a Lender may lend using the CFP, including limits for individual loans and limits that apply over any twelve (12) month period;
- When a Lender may withdraw a commitment to provide funding (‘cooling–off period’) and the procedure for exercising such a right;
- What will happen to funds raised if Loans sought by a Borrower either fail to meet, or exceed, the target level;
- Steps the crowdfunding company will take if there is a material change in a Borrower’s circumstances and the rights of the Lender and Borrower in that situation;
- How the crowdfunding company will deal with overdue payments or a default by a Borrower;
- Which jurisdiction’s laws will govern the loan agreement between the lender and borrower;
- Arrangements and safeguards for Client Money held or controlled by the crowdfunding company, including details of any legal arrangements that may be used to hold Client Money;
- Any facility it provides to facilitate the transfer of Loans, the conditions for using the facility and any risks relating to the use of that facility;
- Measures it has in place to ensure the CFP is not used for money-laundering or other unlawful activities;
- Measures it has in place for the security of information technology systems and data protection; and
- Contingency portfolio administration arrangements the crowdfunding company has in place to ensure the orderly administration of Loans if the CFP ceases to carry on business.
- Details of how the CFP functions;
- Additional risks that the crowdfunding company must prominently disclose on its website include:
- By participating in the CFP, Clients are exposing themselves to material risks pertaining to the business model of the CFP;
- Listing the specific material risks for Borrowers and for Lenders separately and clearly;
- Lenders are not placing deposits and are not protected by any insurance or guarantee scheme; and
- Lenders may face material risks, including the loss of some or all of their money, should the Borrower fail or default on loan repayments
- By participating in the CFP, Clients are exposing themselves to material risks pertaining to the business model of the CFP;
- A crowdfunding company shall post the disclosures (in this Part) on promotional material whether in electronic medium or otherwise.
- A crowdfunding company shall also disclose additional information including (but not limited to) the following:
- Lack of full visibility of use of funds and means to monitor Borrowers closely similar to methods adopted by conventional financing channels such as banking channels;
- Risk of misleading or insufficient information disclosure by the borrower; and
- Dispute resolution and redress mechanisms
- Lack of full visibility of use of funds and means to monitor Borrowers closely similar to methods adopted by conventional financing channels such as banking channels;
A crowdfunding company must
- Attach key disclosure clauses in agreement which must be initialled by the borrower;
- Issue statement of transactions (monthly);
- Provide 30-day notice of any changes to fees, interests etc.
- Attach key disclosure clauses in agreement which must be initialled by the borrower;
- A crowdfunding company must prominently disclose on its website key information about how its service operates, including:
Stored-value facilities
Stored Value Facilities (SVF) Regulation
C 6/2020 Effective from 30/10/2020Introduction
The ‘Regulatory Framework for Stored Values and Electronic Payment Systems’ has been providing the framework and basis for the Central Bank to license and regulate Stored Value Facilities (SVF) issued in the UAE on 13/12/2016. Due to technological advancements, the rapid developments of stored value products and services, and the enacted Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities, which grants the Central Bank more and specific supervisory powers, therefore, the existing regulatory framework for SVF has been reviewed and is being amended.
The relevant Articles of the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities include: (a) Article (65) that requires providing SVF services to be subject to a licensing regime administered by the Central Bank; and (b) the Articles (67) - (71) that provide the statutory basis for the powers of the Central Bank in relation to the licensing and on-going supervision of SVF activities.
Scope and Objectives
The scope of this Regulation includes the licensing and the ongoing supervisory and enforcement requirements on the licensed companies for providing SVF in the UAE, excluding the Financial Free Zones. Financial institutions regulated by Financial Free Zone Authorities may conduct SVF business in the State after obtaining a License from the Central Bank. Under the framework, the Central Bank is empowered to (a) decide whether an SVF License should be granted; (b) conduct ongoing supervision of Licensees; and (c) conduct examination and impose sanctions and measures on Licensees when required.
Transition Period
A one-year transitional period will commence on the date the Regulation comes into force. Licensees already holding an SVF License granted under the previous regulatory framework may continue operating without contravening this Regulation. Nevertheless, they are required to complete the implementation of the relevant measures set out in this Regulation by the end of the transition period.
The existing Licensees are required to submit an independent assessment report as prescribed in paragraphs 5 and 6 of Article (3) before the end of the transition period to ensure that they are in full compliance with this Regulation.
Article (1): Definitions
- AML/CFT: Anti-Money Laundering and Combating the Financing of Terrorism and financing of illegal organizations.
- Applicant: a company duly incorporated in the United Arab Emirates in accordance with the Federal Law No. (2) of 2015 on Commercial Companies, except Joint Liability Company, Simple Commandite Company, which files an Application for the issuance of an SVF License.
- Application: a request submitted by an Applicant in the form and with the documents and information set out in the Annex for providing an SVF Services.
- Central Bank: The Central Bank of the United Arab Emirates.
- Central Bank Law: Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities and its amendments.
- Closed Loop Payment Scheme: a payment scheme, which is limited in terms of where it can be used to purchase goods and services from an issuing retailer or entity.
- Controlling Shareholder: a shareholder who has the ability to directly or indirectly influence or control the appointment of the majority of the board of directors, or the decisions made by the board of directors, or has the power to direct or cause the direction of the management or policies of an entity, whether by the general assembly of the entity, through the ownership of a percentage of the shares or stocks or under an agreement or other arrangement providing for such influence or control.
- Crypto-Assets: cryptographically secured digital representations of value or contractual rights that use a form of distributed ledger technology and can be transferred, stored or traded electronically.
- Customer: a natural or legal person who contracts with a Licensee in order to establish and use an SVF in accordance with this Regulation.
- Customer Due Diligence (CDD): includes measures and processes to be taken for: (a) identifying the Customer and verifying that Customer’s identity using reliable, independent source documents, data or information, and (b) on-going due diligence on the Customer or business relationship and scrutiny of transactions undertaken throughout the course of that relationship.
- Device-based Stored Value Facility: an SVF which has the value stored in an electronic chip on a card or physical device such as pre-paid cards, watches and ornaments.
- Financial Action Task Force (FATF): an inter-government body which sets international standards that aim to prevent global money laundering and terrorist financing activities.
- Financing of Terrorism: any of the acts mentioned in Articles (29) and (30) of the Federal Law no. (7) of 2014 On Combating Terrorism Offences.
- Float: the Customers’ funds / money / Money’s Worth paid to the Licensee in exchange for the value of the money/Money’s Worth (including Money’s Worth such as values, points, Crypto-Assets or Virtual Assets) on the facility.
- Information Technology (IT): the use of any computers, smart devices, storage, networking and other physical devices, infrastructure and processes to create, process, store, secure and exchange all forms of electronic data.
- IT Controls: a set of policies and procedures that aims to provide a reasonable assurance that the technologies and computer systems used by an organization operates as intended and in a secure and reliable manner, that data security, integrity and reliability can be ensured, and that the organization is able to comply with applicable laws and regulations.
- License: a License issued by the Central Bank to an Applicant for the issuance and operation of SVF business in the State. The License is valid, unless it is withdrawn, suspended or revoked by the Central Bank.
- Licensee: an Applicant who has been granted an SVF License by the Central Bank.
- Licensed Financial Activity: The financial activities subject to the Central Bank’s licensing and supervision, which are specified in article (65) of the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities.
- Money Laundering: any of the acts mentioned in Clause (1) of the Article (2) of the Federal Decree-law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Financing of Illegal Organizations.
- Money’s Worth: value added onto an SVF by the Customer; value received on the Customer’s SVF account; and value redeemed by the Customer include not only “money” in the primary sense but also other forms of monetary consideration or assets such as values, reward points, Crypto-Assets, or Virtual Assets. For example, a value top-up of an SVF account may take the form of values, reward points, Crypto-Assets, or Virtual Assets earned by the SVF Customer from making purchases of goods and services. Similarly, value received on the account of the SVF Customer may take the form of an online transfer of value, reward points, Crypto-Assets, or Virtual Assets between fellow SVF Customers.
- Non-device Based Stored Value Facility: is a facility which has the value stored on a network-based account and can be accessed through the internet, a computer network or mobile network. Examples include internet-based payment platforms or mobile e-wallets which provide “network-based accounts” with which Customers can store value for making payments for online and off-line purchases, or for person-to-person funds transfers.
- Operating Rules: are rules set up by a Licensee to cover the complete chain of an SVF’s operation including but not limited to Customer account opening and maintenance, merchant acquisition and contractual relationships with business partners, pre-transaction, payment authorization and post-transaction processes.
- Senior Management: a team of individuals at the highest level of management of the Licensee who have the day-to-day tasks of managing the Licensee’s business.
- Single-purpose Stored Value Facility: a facility that in respect of which the issuer gives an undertaking that, if the facility is used as a means of making payments for goods or services (not being money or Money’s Worth) provided by the issuer, the issuer will provide the goods or services under the rules of the facility. A Closed Loop Payment Scheme is a typical Single-purpose Stored Value Facility.
- State: the United Arab Emirates, excluding the Financial Free Zones.
- Stored Value Facility (SVF): A facility (other than cash) for or in relation to which a Customer, or another person on the Customer’s behalf, pays a sum of money (including Money’s Worth such as values, reward points, Crypto-Assets or Virtual Assets) to the issuer, whether directly or indirectly, in exchange for: (a) the storage of the value of that money (including Money’s Worth such as values, reward points, Crypto-Assets or Virtual Assets), whether in whole or in part, on the facility; and (b) the “Relevant Undertaking”. SVF includes Device-based Stored Value Facility and Non-device based Stored Value Facility.
- SVF Issuer: a company which carries out the business of the provision of SVF and is responsible and accountable for the safekeeping of the Float.
- Relevant Undertaking: In relation to an SVF, Relevant Undertaking means an undertaking by the Licensee that, upon the use of SVF by the Customer as a means for payment for goods and services (which may be or include money or Money’s Worth) or payment to another person, and whether or not some other action is also required, the Licensee, or a third party that the SVF Issuer has procured to do so, will, in accordance with the Operating Rules: (a) supply the goods or services; (b) make payment for the goods or services; or (c) make payment to the other person, or as the case requires.
- Virtual Assets: Virtual assets include digital tokens (such as digital currencies, utility tokens or asset-backed tokens) and any other virtual commodities, Crypto Assets and other assets of essentially the same nature.
- Virtual Asset Service Provider: is a business which conducts Virtual Assets-related activities or operations for or on behalf of another natural or legal person. The activities or operation may include exchange between Virtual Assets and fiat currencies; exchange between one or more forms of Virtual Assets; transfer of Virtual Assets; safekeeping and/or administration of Virtual Assets or instruments enabling control over Virtual Assets; and participation in and provision of financial services related to an issuer’s offer and/or sale of a Virtual Asset.
- AML/CFT: Anti-Money Laundering and Combating the Financing of Terrorism and financing of illegal organizations.
Part I – Licensing Requirements
Article (2): Scope of Application
- This Regulation applies to all SVF as defined in Article (1) Definition.
License required for issuing SVF
- Issuing and operating SVF in the State requires a prior License from the Central Bank. It is prohibited to carry on the activity of issuing or operating SVF without prior License except if the issued SVF is a Single-purpose Stored Value Facility.
Exclusion of certain types of SVF
- On application by an Issuer, the Central Bank may exempt an SVF from the licensing requirements and will do so based on the risk the SVF poses to its (potential) Customers, Customer funds and the financial system.
- The types of SVF that may be exempted from the licensing requirements by the Central Bank include:
- 4.1. SVF used for certain cash reward schemes. Such SVF may be used for storing only a sum of money paid by (i) the issuer; or (ii) a person who agrees to pay a sum of money for storage in the facility under an agreement with the issuer and the sum of money stored may only be used for making payments for goods or services provided by the issuer or person under very specific terms and conditions of the facility. Examples include loyalty schemes provided by shops and supermarkets which offer cash rewards for customer loyalty;
- 4.2. SVF used for purchasing certain digital products. Such SVF may only be used as a means of making payments for goods or services that are delivered to, and are to be used through, a telecommunication, digital or technology device; the payments are executed through such a device; and the telecommunication, digital or technology operator acts as an intermediary between the Customer of the facility and the provider of the goods or services. Examples include purchase of digital contents such as ringtones, music, videos, electronic books, games and applications that can be used on smartphones, computers or other information technology devices;
- 4.3. SVF used for certain bonus point schemes. Such SVF may be used only for storing points or units (by whatever name called) that are Money’s Worth provided by (i) the issuer; or (ii) a person who agrees to provide goods or services to the Customer under an agreement with the issuer. The Customer may use the points or units for making payments for the goods or services provided by the issuer or person either by (i) using only the points or units; or (ii) using the points or units together with a sum of money (in any currency) that is stored on the facility temporarily for the sole purpose of executing the payments; and the sum of money so stored is not redeemable for cash. Examples are airline mileage programs and customer loyalty schemes that provide non-cash points to customers to reward their patronage, and whereby such points and value stored, if any, is not redeemable for cash;
- 4.4. SVF that can only be used within a limited group of goods or services providers. Such SVF may be used as a means of making payments only for goods or services provided by (i) the issuer; or (ii) a person who provides the goods or services under an agreement with the issuer; and
- 4.5. whereby (i) the aggregate amount of the Float of the facilities does not exceed half a million Dirham (500,000 AED) or its equivalent and the aggregate number of Customers is not more than 100. If a potential SVF Issuer wishes to apply for this particular exemption, the SVF is required to test out its product before making a full launch of SVF. In this regard, the relevant issuer is required to participate in the Central Bank’s FinTech Office sandboxing arrangement for a possible trial run.
- 4.1. SVF used for certain cash reward schemes. Such SVF may be used for storing only a sum of money paid by (i) the issuer; or (ii) a person who agrees to pay a sum of money for storage in the facility under an agreement with the issuer and the sum of money stored may only be used for making payments for goods or services provided by the issuer or person under very specific terms and conditions of the facility. Examples include loyalty schemes provided by shops and supermarkets which offer cash rewards for customer loyalty;
- The Central Bank may request any information from an exempted SVF Issuer when the Central Bank considers it necessary to determine its eligibility for exemption and continued exemption. The Central Bank may declare an SVF not exempt from the licensing requirement and require the issuer of the SVF to apply for a License.
Overseas SVF schemes
- It is prohibited for an SVF without a prior License to publish in the State or elsewhere, an advertisement, invitation or document which is, or contains, an invitation or a solicitation to the public of the State relating (whether in whole or in part) to the issuance of SVF.
Relevant factors to be considered
- The Central Bank will take into account the factors to determine whether an overseas SVF is issued in the State or a person publishes an advertisement, invitation or document which is, or contains, an invitation or solicitation to the State public relating to the issuance of SVF.
- In determining whether an SVF scheme is presented or provided in such a manner that it appears to be issued in the State, the Central Bank will consider all relevant factors including, in particular, the following:
- 8.1. whether the location for the delivery of the facility and the provision of the subsequent customer service to facility users is in the State;
- 8.2. whether the location for and the manner to top-up the SVF is through channels in the State (e.g. banks in the State);
- 8.3. whether the promotional material is targeted, via “push” techniques, at a group or groups of people whom the issuer knows, or should reasonably know, reside in the State. “Push” techniques include spamming, broadcasting or directing information to a particular person or group of people through, for instance, e-mails, SMS messages and any social media channels;
- 8.4. whether any news group, bulletin board, chat room or similar facility associated with the site has been used to promote the SVF service in the State; and
- 8.5. in the case of services details and promotional material hosted on a site, the Central Bank will assess whether the website's existence has been included in a State search engine or the State section of a search engine; and whether the SVF advertisements, in print or online forms, are easily accessible in the State and whether the website has been advertised in the State through advertising agencies, in periodicals (e.g. newspapers, journals or electronic publications) or by broadcasting (e.g. television or radio).
- 8.1. whether the location for the delivery of the facility and the provision of the subsequent customer service to facility users is in the State;
- In determining whether the content of the issuer’s website and the relevant promotional materials are written in a manner which gives an impression that the SVF is issued in the State, the Central Bank will take a holistic approach and consider a host of factors including but not limited to the following:
- 9.1. whether representations made in any promotional materials and advertisements regarding the location of the issue of the SVF and the usage of that facility is in the State; and
- 9.2. whether the website and its functions are designed in a manner that may imply or give the impression that the SVF is issued in the State, such as the languages used in the SVF website (e.g. the Arabic language), the use of particular domain name such as a State domain name, the currencies accepted for the services (e.g. AED), contact details in the State.
- 9.1. whether representations made in any promotional materials and advertisements regarding the location of the issue of the SVF and the usage of that facility is in the State; and
- The Central Bank will consider all relevant factors including, in particular, whether reasonable precautions are in place to avoid the promotional materials being made available or accessible to persons in the State and whether the issuer has systems in place to avoid providing services to persons residing in the State.
- The Central Bank may also consider matters such as whether the SVF Issuer has established a physical presence in the State; and whether it has established business relationships with banks or financial institutions in the State for payment or other banking support services in the State.
- The above factors and criteria are neither exhaustive nor conclusive. The Central Bank will use a holistic approach to judge each case on its merits and take into account the particular circumstances and all relevant facts.
Article (3): Licensing Requirements
- In accordance with Article (65) of the Central Bank Law, the provision of Stored Value Facilities is considered a Licensed Financial Activity and subject to the Central Bank’s licensing and supervision in accordance with the provisions of the Central Bank Law. In this connection, an Applicant must satisfy the licensing requirements set by the Central Bank for SVF issuance, and continue to do so on an ongoing basis as a Licensee.
- The Applicant must be a company incorporated in the State, including free zones but excluding Financial Free Zones.
- Applicants must meet, or demonstrate that they will meet upon License issuance, the ongoing requirements set out in Articles (7) to (14) of this Regulation applicable to Licensees, in particular:
- 3.1. The requirements regarding financial resources as set out in Article (7) of this Regulation. The Central Bank may add additional requirements regarding financial resources or increase the existing ones as a condition for License issuance, where it considers such additional requirements necessary;
- 3.2. The requirements regarding their principal business, as set out in Article (7) of this Regulation. The Application must disclose to the Central Bank any activities and secondary or ancillary businesses that the Applicant conducts or plans to conduct that may not be directly related to the issuance of SVF;
- 3.3. The requirements regarding corporate governance, general risk management and internal control, and accounting system as set out in Articles (8) to (10) of this Regulation. In particular, board of directors, the Senior Management, and the Controlling Shareholder must have been approved by the Central Bank as fit and proper in the context of the Application before the License is granted;
- 3.4. The requirements regarding risk management policies and procedures for the management and protection of the Float, as set out in Article (11) of this Regulation;
- 3.5. The requirements regarding technology and specific risk management policies and procedures for managing the risks arising from the operation of the SVF business, as set out in Article (12) of this Regulation;
- 3.6. The requirements regarding business conduct and Customer protection as set out in Article (13) of this Regulation;
- 3.7. The requirements regarding anti-money laundering and countering the financing of terrorism, as set out in Article (14) of this Regulation.
- 3.1. The requirements regarding financial resources as set out in Article (7) of this Regulation. The Central Bank may add additional requirements regarding financial resources or increase the existing ones as a condition for License issuance, where it considers such additional requirements necessary;
- As part of the licensing process, separate face-to-face meetings between Central Bank staff and the Applicant’s board of directors and the Senior Management may be conducted.
Independent assessments
- The Applicant is required to submit a report of independent assessments on seven key areas based on the scope set out in paragraphs 3.3 to 3.7 above: (a) corporate governance and risk management; (b) Float management; (c) technology risk management; (d) payment security management; (e) business continuity management; (f) business conduct and Customer protection; and (g) AML/CFT control systems.
- The Central Bank expects the Applicant to appoint one or more competent and qualified assessor(s), which are independent from the business units of the Applicant, to carry out the independent assessments. The assessors should not be involved in the operations to be reviewed or in selecting or implementing the relevant control measures to be reviewed, have relevant knowledge and experience, and should be able to report their findings independently. They should also confirm to the Central Bank that there is no conflict of interest in the conduct of independent assessments.
- Bank that are deemed to be licensed for providing of SVF, are exempted from the assessment report mentioned in paragraphs 5 and 6 above, unless the Central Bank explicitly requires the report from them.
- In accordance with Article (65) of the Central Bank Law, the provision of Stored Value Facilities is considered a Licensed Financial Activity and subject to the Central Bank’s licensing and supervision in accordance with the provisions of the Central Bank Law. In this connection, an Applicant must satisfy the licensing requirements set by the Central Bank for SVF issuance, and continue to do so on an ongoing basis as a Licensee.
Article (4): Application Procedure
Licensed bank to issue SVF
- Although licensed banks are deemed to be authorized for the issuance of SVF, they are nevertheless required to notify the Central Bank in writing if they plan to issue an SVF and carry out the SVF business. A “No Objection” letter is required from the Central Bank before the licensed bank concerned can commence the SVF business.
Preliminary meeting with the Central Bank
- Any company that is interested in obtaining a License may obtain the Application form from the Licensing Division of the Central Bank.
- The Senior Management of the company is strongly encouraged to meet and discuss the SVF business plan with the Central Bank before submitting a formal Application.
Consultation with home regulator
- Where the Controlling Shareholder of the Applicant is regulated by another authority, including by authorities in other jurisdictions, the Central Bank may contact the relevant authority about the Applicant. The Central Bank may take into account the relevant authority’s views in respect of matters such as the financial soundness and the overall internal control environment of the Controlling Shareholder, and whether the relevant home regulator has any concern about that Controlling Shareholding extending its SVF business to the State.
Completing and submitting the Application
- The Application must be lodged with the Central Bank with the completed form and the required documents as set out in the Annex.
Processing of Application
- The Central Bank may seek additional information from the Applicant to reach a decision on the Application. The circumstances of each particular Application will dictate the additional information required. Specifically, the applicant is required to submit a report of independent assessments as set out in paragraphs 5 and 6 of Article (3) of this Regulation. The validity of the assessment report should not exceed six months after the report’s sign-off date.
- Incomplete information may result in delays. Applicants should, therefore, pay attention to the following points:
- 7.1. All Applications must be submitted with documents and information listed in the Annex. The Applicant will be informed in writing that the Application is complete and the processing of the Application will begin;
- 7.2. Where an Application received is incomplete or supporting documents or information is lacking, the Applicant will be informed in writing that the Application will be treated as “draft” and will be asked to complete the Application or provide the missing information by a date specified by the Central Bank. Once a properly completed Application with all necessary supporting documents and information is received, the Applicant will be notified in writing that Application is complete and the processing of the Application will begin;
- 7.3. Where information requested is not received by the specified date or a revised date agreed in writing by the Central Bank at the request of the Applicant, the Application may be treated as “suspended” and the Applicant will be notified of this in writing;
- 7.4. Where an Application is “suspended”, the Applicant will be informed in writing that the processing of the Application will cease temporarily. Suspended Applications will be reactivated only when the outstanding information is submitted; and
- 7.5. Where an Application is “suspended” for 6 months or more for any reasons, a new Application will generally be required if the Applicant wishes to pursue the matter further.
- 7.1. All Applications must be submitted with documents and information listed in the Annex. The Applicant will be informed in writing that the Application is complete and the processing of the Application will begin;
Approval of Application
- The Central Bank may approve an Application for the License made by the Applicant provided that all the licensing criteria can be met by the Applicant.
- The Central Bank may grant the License without conditions or subject to any conditions attached. Conditions attached to a License may include, among others, imposing a higher level of capital requirement, restrictions on the SVF business or any secondary or ancillary businesses, requirements relating to protection of the Float, and restrictions as to the maximum amount of value that may be stored on an SVF, etc.
- If the Central Bank grants a License to the Applicant, the Central Bank will:
- 10.1. assign a unique reference number to the License; and
- 10.2. specify in the License the date on which the License is to take effect.
- 10.1. assign a unique reference number to the License; and
- Specifically, a Licensee must ensure that the License reference number of the License is clearly displayed in the Licensee’s website and promotional materials.
Article (5): Suspension, Withdrawal and Revocation of License
- The Central Bank may suspend, withdraw or revoke a License as stipulated in the Central Bank Law.
- In considering whether to exercise such power, the Central Bank would have primary regard to the need to maintain the stability of the payment system in the State, reputation of the UAE and to protect the interests of the Customer or potential Customer of the Licensee in question.
- Where a Licensee is suspended, withdrawn or revoked, the Licensee must immediately cease to take any further sum of money from Customers.
- The Central Bank may suspend, withdraw or revoke a License as stipulated in the Central Bank Law.
Article (6): Authority over Licensees
- The Central Bank may take all measures and actions it deems appropriate for achieving its objectives and discharging its functions, and may particularly take the following actions, if it was found that a material violation to the provisions of this Regulation has occurred:
- 1.1. The Central Bank may require the concerned Licensee to take necessary actions to rectify the situation immediately;
- 1.2. Appoint a specialized expert, or a Central Bank employee, to advise or guide the concerned Licensee, or oversee some of its operations, for a period specified by the Central Bank. The concerned Licensee shall pay remunerations of such appointee if he is an expert from outside the Central Bank; or
- 1.3. The Central Bank may appoint a manager where the Central Bank is of the view that the management of the Licensee cannot be relied upon to take appropriate steps to rectify a situation. The main objectives of appointing a manager to take control of the management of a Licensee are:
- 1.3.1. to provide for the control of the affairs, business and property of a troubled Licensee so that it can be nursed back to health or else be run down in an orderly fashion; or
- 1.3.2. to safeguard the assets and maintain the business of the Licensee until a liquidator can be appointed
- 1.3.1. to provide for the control of the affairs, business and property of a troubled Licensee so that it can be nursed back to health or else be run down in an orderly fashion; or
- 1.4. Take any other action or measure, or impose any penalties it deems appropriate.
- 1.1. The Central Bank may require the concerned Licensee to take necessary actions to rectify the situation immediately;
- The Central Bank may take all measures and actions it deems appropriate for achieving its objectives and discharging its functions, and may particularly take the following actions, if it was found that a material violation to the provisions of this Regulation has occurred:
Part II – Ongoing Regulatory Requirements
Article (7): Principal Business and Financial Resources Requirements
- The principal business of a licensee must be the issuance of SVF under a License.
- The principal business and financial resources requirements set out in this Article do not apply to licensed banks that carry out the SVF business in the State.
Principal business requirement
- For the avoidance of doubt, a Licensee is not permitted to carry on any other Licensed Financial Activity without obtaining a License from the relevant authority. If the Licensee wishes to conduct any secondary or ancillary businesses, the Licensee must seek approval from the Central Bank before undertaking such activity.
Financial resources requirements
- A Licensee must maintain the following:
- 4.1. paid-up capital of at least 15 million Dirham (15,000,000 AED) or an equivalent amount in any other currency approved by the Central Bank;
- 4.2. Aggregate Capital Funds must be at least 5% of the total Float received from the Customers.
- 4.1. paid-up capital of at least 15 million Dirham (15,000,000 AED) or an equivalent amount in any other currency approved by the Central Bank;
- The Aggregate Capital Funds consist of the following items:
- 5.1. Paid-up capital;
- 5.2. Reserves, excluding revaluation reserves; and
- 5.3. Retained earnings.
- 5.1. Paid-up capital;
- The following items must be deducted from Aggregate Capital Funds:
- 6.1. Accumulated losses; and
- 6.2. Goodwill.
- 6.1. Accumulated losses; and
- A Licensee must be able to demonstrate that its financial resources are sufficient for implementing its business model in a safe, efficient and sustainable manner, without compromising the interests of Customers.
- A Licensee must provide adequate details to the Central Bank on the source of funds that will be used to support the proposed business activities.
- A Licensee must demonstrate that it will be able to maintain sufficient financial resources to facilitate an orderly wind-down of its SVF business, including a smooth refunding process.
- The Central Bank may impose a higher financial resources requirement if, taking into account the scale and complexity of a Licensee’s business, it considers such a requirement important in ensuring that the Licensee concerned has the ability to fulfil its regulatory obligations under this Regulation. An unconditional irrevocable bank guarantee for the full paid up capital amount in favor of the Central Bank paid upon first demand shall also be submitted to the Central Bank with the application of the License. Such a guarantee should be renewable before expiry or based on the Central Bank’s demand.
- The principal business of a licensee must be the issuance of SVF under a License.
Article (8) Corporate Governance Requirements
- A Licensee must have in place appropriate risk management policies and procedures for managing the risks arising from the operation of its SVF business that are commensurate with the scale and complexity of the scheme.
- The corporate governance requirements set out in this Article do not apply to licensed banks that carry out the SVF business. Banks are required to adhere to the Central Bank regulation and standards for corporate governance at banks.
Responsibilities of the board of directors
- A Licensee is required to have in place sound governance arrangements for the purpose of effective decision-making and proper management and control of the risks of its business and operations. Such arrangements should include a clear organizational structure with well-defined, transparent and consistent lines of responsibility. There should also be clear documentation on decision-making procedures, reporting lines, internal reporting and communication process.
- As part of a sound governance arrangement, a Licensee should put in place a code of conduct which lays down the standards of integrity and probity expected of its management and employees. The Licensee should also have adequate systems for enforcing the code of conduct, including regular assessments of the relevancy and effectiveness of the code.
- The board of directors is responsible for the sound and prudent management of the Licensee’s SVF business operations.
- The board of directors should have an adequate number and appropriate composition of members to ensure sufficient checks and balances and collective expertise for effective and objective decision-making. The size and composition of the board of directors will vary from institution to institution depending on the size of the Licensee and the nature and scope of its activities.
- The board of directors should document and clearly define appropriate internal governance practices and procedures for the conduct of its own work and have in place the means to ensure that such practices are followed and periodically reviewed with a view to ongoing improvement.
- Effective arrangements should be put in place such that the board of directors can assess the performance of the Senior Management and hold them accountable for their performance.
Fitness and propriety of officers and Controlling Shareholder
- A person must not become a chief executive or director of a Licensee except with the Central Bank’s approval. The Central Bank’s approval must be obtained for a person to become Controlling Shareholder of a Licensee. In considering the fitness and propriety of the chief executive, directors and Controlling Shareholder of a Licensee, the Central Bank will take into account factors including, among others, the integrity, willingness to uphold professional ethics and industry good practices, and competence of the person concerned. Set out below are the Central Bank’s general expectations in relation to the fitness and propriety of chief executives, directors and the Controlling Shareholders of licensees.
Directors and chief executives
- Given the leadership role of directors and chief executives, fitness and propriety will be assessed taking into consideration their integrity and competence, which will generally be assessed in terms of relevant knowledge, experience, judgement as well as leadership. Their commitment and ability to devote sufficient time and attention to the SVF business will also be assessed. The standards required from persons in these respects will vary, depending on the scale and complexity of a Licensee’s operations.
Controlling Shareholder
- In assessing the fitness and propriety of the Controlling Shareholder, a key consideration is the influence that the Controlling Shareholder could potentially have on the interests of the Customers and potential Customers of the scheme concerned. This has to be assessed in the context of the circumstances of individual cases. The general presumption is that the greater the influence on the Licensee, the higher the standard will be for the Controlling Shareholder to fulfil the criterion.
Outsourcing
- A Licensee may outsource activities and processes to service providers, including independent third parties, or companies within the Licensee’s group. Such outsourcing must be approved by the Central Bank.
- A Licensee is ultimately responsible for the adequacy, service levels, quality and security of the outsourced activities and processes, including the reliability, robustness, stability and availability, of the outsourced activities and processes as well as the integrity and protection of the information held by the service providers.
- Prior to outsourcing an activity or process, a Licensee must:
- 14.1. Conduct a comprehensive independent risk assessment, identifying all risks involved, and ensuring that all material risks, including business interruption risk, and controls over Customer data protection, are adequately managed. The assessment should identify any additional risks or increases in risks caused by the outsourcing;
- 14.2. Perform an appropriate due diligence regarding not just the cost and quality of the services offered, but also on the provider’s financial soundness, reputation, managerial skills, technical and operational capacity to meet the Licensee’s requirements in the longer run, ability to meet the regulatory requirements with regard to the services offered, familiarity with the payment industry, and capacity to keep pace with innovation in the market.
- 14.3. Prior to outsourcing any process or activity: (a) perform an appropriate due diligence to ensure that the services to be rendered fully meet the performance and relevant regulatory requirements, (b) executing appropriate outsourcing agreements with the service providers to set out clearly the outsourcing arrangements and the related rights and obligations, and (c) carrying out proper transfer of the related operations or functions to ensure smooth transition; and
- 14.4. Properly manage the outsourcing arrangements on an ongoing basis by performing appropriate regular audits and/or quality reviews of the outsourced operations or services.
- 14.1. Conduct a comprehensive independent risk assessment, identifying all risks involved, and ensuring that all material risks, including business interruption risk, and controls over Customer data protection, are adequately managed. The assessment should identify any additional risks or increases in risks caused by the outsourcing;
- The outsourcing agreement must set out clearly:
- 15.1. The type and level of services to be provided and the related performance standards of the service provider, including its contingency arrangements in respect of daily operational and systems problems;
- 15.2. The contractual obligations and liabilities of the service provider;
- 15.3. The rights and obligations of the Licensee including the relevant fees and charges payable by the Licensee and the rights of the Licensee to access, retrieve and retain on a timely basis accurate and up-to-date records and make those records available for inspection by the relevant authorities including the Central Bank or an independent assessor appointed by the Licensee or the Central Bank, if required; and
- 15.4. Data handling controls and arrangements relating to the storage, backup, protection and confidentiality, and data removal and transfer arrangements upon termination or expiry of the contract. The right for the Licensee, the Central Bank and/or an independent assessor appointed by the Licensee or Central Bank to conduct an on-site inspection and off-site review of the operations and controls of the service provider. This includes access by the Central Bank or an appointed independent assessor to the premises, systems, record and documents relevant to the outsourced activity or process.
- 15.1. The type and level of services to be provided and the related performance standards of the service provider, including its contingency arrangements in respect of daily operational and systems problems;
- A Licensee should ensure that it has an adequate understanding of its service provider’s contingency plan and consider the implications for its own business continuity planning in the event that an outsourced service is disrupted due to failure of the service provider’s system. Such contingency plans should be tested by the licensee and its service providers regularly.
- A Licensee should ensure that its outsourcing arrangements comply with the relevant personal data privacy/protection requirements and any relevant codes of practice, guidelines and best practices issued by the Central bank and relevant authorities.
Location of Senior Management
- The chief executive and the alternate chief executive should be individuals who are ordinarily resident in the State. Licensees must ensure that this requirement is being complied with on an ongoing basis. Furthermore, the Senior Management team and the key personnel responsible for scheme operation, system support, risk management and compliance of the Licensee must be based in the State. Depending on the nature, scale, complexity of business, and the organization structure of the Licensee, the Central Bank may approve different arrangements.
- A Licensee must have in place appropriate risk management policies and procedures for managing the risks arising from the operation of its SVF business that are commensurate with the scale and complexity of the scheme.
Article (9): General Risk Management & Internal Control Systems
- The Licensee must have in place appropriate risk management policies and procedures for managing the risks arising from the operation of its SVF scheme that are commensurate with the scale and complexity of the scheme.
- The general risk management and internal control systems requirements set out in this Article also apply to licensed banks that carry out the SVF business in the State.
Risk management
- A Licensee must have in place effective risk management framework, which is approved by the board of directors. Dedicated human resources should be equipped with sufficient professional knowledge and experience to oversee the risk management and internal control processes.
Liquidity risk management
- A Licensee must establish and implement an effective process for managing liquidity risk that is appropriate for the size and complexity of its operations. The objective is to ensure that the Licensee will have sufficient liquidity to meet different financial obligations arising from its day-to-day operations as well as redemption requests under all plausible circumstances.
Internal controls
- A robust internal control system must be put in place to promote effective and efficient operation, safeguard assets, provide reliable financial and management information, enable prevention or early detection of irregularities, fraud and errors, and ensure compliance with relevant statutory and regulatory requirements and internal policies.
- A Licensee should put in place a comprehensive business strategy and plan, including details on the strategic goals and roadmap. A business plan should normally cover proposed business in terms of geographical scope of operations, target markets and Customer breakdown, client types and base size, product and services offering, delivery channels, pricing strategy, and promotion and marketing activities.
Compliance and internal audit functions
- A Licensee must maintain an effective (i) compliance function; and (ii) internal audit function to ensure compliance with all applicable legal and regulatory requirements as well as its own policies, procedures and controls. Among other factors, the quality of a Licensee’s compliance and internal audit functions will be assessed by the Central Bank based on its:
- 7.1. clear governance framework with board level support to ensure effective policies and sufficient authorities to perform the functions;
- 7.2. relevant professional knowledge and experience;
- 7.3. independence from business units;
- 7.4. direct and unfettered access to the board;
- 7.5. coverage, comprehensiveness and effectiveness of compliance and internal audit programs; and
- 7.6. ability to take timely and proactive rectifying actions upon identifying non-compliance or other control deficiencies.
- 7.1. clear governance framework with board level support to ensure effective policies and sufficient authorities to perform the functions;
- The compliance function must not be combined with the internal audit function.
Reporting to the Central Bank
- A Licensee must have effective procedures to ensure submission of data and information requested by the Central Bank in a timely and accurate manner, including: (a) incidents having a material adverse impact on its business, operation, assets, risks or reputation; and (b) breach of any statutory or regulatory requirements by the Licensee or its officers or employees.
- A Licensee should at least annually perform a risk assessment by its own risk management or audit function. If the results of the risk assessment suggest that a detailed independent assessment is necessary, the Licensee should conduct such assessment and cover the following seven key areas: (a) corporate governance and risk management; (b) Float management; (c) technology risk management; (d) payment security management; (e) business continuity management; (f) business conduct and consumer protection; and (g) AML/CFT controls systems. If the Licensee has an independent function elsewhere in its group, with the relevant knowledge and experience, the independent assessment can be conducted by its internal function. Otherwise the assessment must be carried out by an independent third party.
- The report mentioned in paragraph 10 above must be submitted to the Central Bank after being approved by the board of directors. These reports must include an executive summary highlighting the key risks, most important findings and the actions for rectifying the issues.
- Arising from the findings of the annual risk assessment, a Licensee that is unable to meet its obligations must immediately report this to the Central Bank.
- A Licensee must also immediately notify the Central Bank of any breach or potential breach of major regulatory requirements in this Regulation.
- The Licensee must have in place appropriate risk management policies and procedures for managing the risks arising from the operation of its SVF scheme that are commensurate with the scale and complexity of the scheme.
Article (10): Information and Accounting Systems
- The information and accounting systems, risk management and internal control systems set out in this Article do not apply to licensed banks that carry out the SVF business in the State. Banks must comply with the relevant regulations in these areas issued by the Central Bank for banks.
Information and accounting systems
- A Licensee must have in place robust information and accounting systems to (a) record all business activities in a timely and accurate manner; (b) provide quality management information to enable effective and efficient management of business and operations; and (c) maintain appropriate audit trail to demonstrate effectiveness of controls.
- A Licensee must properly maintain books and accounts and prepare financial statements and returns in compliance with all applicable regulatory reporting requirements and accounting standards in the State.
Record keeping
- A Licensee must have in place adequate record keeping policies and systems for maintaining accurate and sufficient records of its books, accounts, management decisions and business activities, including transactions of Customers.
Data protection
- A Licensee must have in place adequate policies, measures and procedures to protect its information and accounting systems, databases, books and accounts, and other records and documents from unauthorized access, unauthorized retrieval, tampering and misuse.
- A Licensee must also adequately protect the Customer data (including Customer identification and transaction records) which are required to be stored and maintained in the State. Such data can only be made available to the corresponding Customer, the Central Bank, other regulatory authorities following prior approval of the Central Bank, or by a UAE court order. A Licensee must store and retain all Customer and transaction data for a period of five years from the date of the creation of the Customer data, or longer if required by other laws.
Article (11): Management and Safekeeping of the Float
- A Licensee must have in place an effective and robust system to protect and manage the Float to ensure that: (a) all funds are deployed for the prescribed usage only; (b) funds belonging to Customers are protected against claims by other creditors of the Licensee in all circumstances; and (c) funds are protected from operational and other relevant risks.
- A Licensee may need to seek an external legal opinion on the protection arrangement of the Float to ensure the legal soundness of the arrangements and to commission an independent review to ensure the operational soundness.
- Licensed banks are required to comply with the requirements set out in paragraphs 7 to 16 in this Article, and are exempt from the other paragraphs.
Protection of the Float
- A Licensee must put in place an effective contractual arrangement to ensure the legal right and priority claim of the Float by Customers in the event of insolvency of a Licensee. With respect to the contractual arrangement, a Licensee should ensure that the assets of the Float must be adequately protected from any possible claims and in segregated accounts with licensed banks or a foreign bank recognized by the Central Bank.
- Alternatively, an effective bank guarantee and/or insurance coverage may be used. For the avoidance of doubt, any funds received by the Licensee that are not yet credited to the Customers’ accounts, or funds that are still held by the Licensee but have already been deducted from the Customer’ account are treated as the Float received from the Customer and must be accorded the same level of protection.
- Where circumstances warrant a trigger to redeem the Float to Customers, the contractual arrangement should operate to the effect that proper legal positions and authorizations are in place to ensure a smooth and efficient redemption process. Detailed procedures to ensure a smooth and efficient redemption process must be put in place. In assessing the efficiency of the redemption process, the Central Bank will consider factors including but not limited to notification to relevant Customers, the duration in which a Customer is expected to receive the redemption, and the steps that a Customer needs to take to seek redemption.
- A Licensee must ensure that there are sufficient funds for the redemption of the Float to all Customers at all times and there are sufficient additional funds to pay for the costs of distributing the Float to all Customers in case of need.
- An adequate process must be put in place to ensure timely and accurate records of funds paid into and out of a Licensee’s Float, with appropriately regular reconciliation between system records and the actual Float (e.g. balances of the dedicated bank account holding the Float). Such reconciliation should be done at least on a daily basis.
- A Licensee must ensure that all Customer accounts in the SVF scheme Customer ledger are maintained in an accurate and timely manner and that the aggregate balance of all Customer accounts in the ledger accurately reflects the total amount of the Float of the SVF scheme at all times.
- The assets, including cash and bank deposits, in which the Float of an SVF scheme are held must be segregated from the Licensee’s own funds as well as funds received for the Licensee’s other business activities.
- A Licensee must put in place effective internal control measures and procedures, which constitute an integral part of the Licensee’s overall robust internal control system, to protect the Float from all operational risks, including the risk of theft, fraud and misappropriation.
Management of the Float
- The Float of an SVF scheme must be managed mainly for the purpose of liquidity management to ensure that there will always be sufficient funds for redemption. A Licensee must put in place effective liquidity management policies, guidelines and control measures commensurate with the mode of operation of the SVF scheme in respect of the assets in which the Float are held.
- A Licensee must not adopt a business model that takes investment returns from the Float management as a significant source of income. A Licensee who proposes to hold a proportion of the Float in low risk financial assets other than cash or bank deposits must obtain the Central Bank’s prior written consent by demonstrating to the Central Bank that the Float will be adequately protected from all relevant risks, including investment risk, market risk, concentration risk and liquidity risk. The Licensee seeking the Central Bank’s prior consent must put in place adequate investment policies and guidelines and effective control measures to protect the Float from all relevant risks.
- Unless effective currency risk management policies, guidelines and control measures are put in place, mismatch between the currency denomination of the Float and that of the assets in which the Float are held is not allowed except for the mismatch between AED and US dollar positions.
- If there are legitimate reasons that render it inevitable for a Licensee to run a currency mismatch as described in paragraph 14 above, the licensee must obtain an exemption from the Central Bank. Licensees exempted from this provision, will be expected to put in place appropriate policies and procedures to monitor or manage the foreign exchange risk arising therefrom and to ensure the sufficiency of the Float.
Reporting to the Central Bank
- In respect of the protection and management of the Float, any material non-compliance with any regulatory requirements or internal policies, procedures and controls as well as any material unresolved discrepancies identified in any reconciliation must be reported to the Central Bank together with adequate rectification measures immediately through the established communication channels.
- A Licensee must have in place an effective and robust system to protect and manage the Float to ensure that: (a) all funds are deployed for the prescribed usage only; (b) funds belonging to Customers are protected against claims by other creditors of the Licensee in all circumstances; and (c) funds are protected from operational and other relevant risks.
Article (12): Technology and Specific Risk Management
- A Licensee is expected to take into account international best practices and standards when designing and implementing the technology and specific risk management systems and processes.
- All technology and specific risk management requirements set out in this Article also apply to licensed banks that carry out the SVF business in the State.
Technology risk management
- A Licensee must establish an effective technology and cyber security risk management framework to ensure (a) the adequacy of IT controls, (b) cyber resilience, (c) the quality and security, including the reliability, robustness, stability and availability, of its computer and payment systems, and (d) the safety and efficiency of the operations of the SVF scheme. The framework must be “fit for purpose” and commensurate with the risks associated with the nature, size, complexity and types of business and operations, the technologies adopted and the overall risk management system of the Licensee. Consideration should be given to adopting recognized international standards and practices when formulating such risk management framework.
- A Licensee must establish an incident management framework with sufficient management oversight to ensure effective incident response and management capability to deal with significant incidents properly. This includes: (a) timely reporting to the Central Bank of any confirmed technology-related fraud cases or major security breaches, including cyber-attacks, cases of prolonged disruption of service and systemic incidents where Customers suffer from monetary loss or Customers’ interests are being affected (e.g. data leakage) and (b) a communication strategy to address the concerns any stakeholders may have arising from the incidents, and restore the reputational damage that the incidents may cause.
- An effective technology risk management framework should comprise proper IT governance, a continuous technology risk management process and implementation of sound IT control practices.
IT governance
- A Licensee must establish a proper IT governance framework. IT governance covers various aspects, including a clear structure of IT functions and the establishment of IT control policies. While there could be different constructs, the major functions should include an effective IT function, a robust technology risk management function, and an independent technology audit function.
- A set of IT control policies that fits the Licensee’s business model and technology applications, must be put in place. The IT control policies which establish the ground rules for IT controls must be formally approved by Senior Management and properly implemented among IT functions and business units. Processes used to verify compliance with IT control policies and the process for seeking appropriate approval by Senior Management for dispensation from IT control policies must also be clearly specified, and consequences associated with any failure to adhere to these processes are in place.
Technology risk management process
- A Licensee must put in place an effective risk management system that fits its specific business model and risk profile.
- A robust process must be established to manage all changes (e.g. changes arising from new products, services, processes, contract terms, or any changes of external factors such as law and regulations) that might change a Licensee’s technology risk exposures. All identified risks must be critically evaluated, monitored and controlled on an ongoing basis.
- A general framework for management of major technology-related projects, such as in-house software development and acquisition of information systems must be established. This framework should specify, among other things, the project management methodology to be adopted and applied to these projects.
Project life cycle
- A full project life cycle methodology governing the process of developing, implementing and maintaining major computer and payment systems should be adopted and implemented.
- Where a Licensee acquires a software package from vendors, a formal software package acquisition process should be established to manage risks associated with acquisitions, such as breach of software license agreement or patent infringement.
- Quality assurance review of major technology-related projects by an independent party, with the assistance of the legal and compliance functions should be conducted if necessary.
Security requirements
- Security requirements should be defined clearly in the early stage of system development or acquisition as part of business requirements and adequately built during the program development stage.
Coding practice
- Guidelines and standards for software development with reference to industry generally accepted practice on secure development should be developed. Source code reviews (e.g. peer review and automated analysis review), which could be risk-based, as part of software quality assurance process should be conducted.
System testing, acceptance and deployment
- A formal testing and acceptance process should be established to ensure that only properly tested and approved systems are promoted to the production environment. The scope of tests should cover business logic, security controls and system performance under various stress-load scenarios and recovery conditions.
- Segregated environments for development, testing and production purposes should be maintained. System testing and user acceptance testing (UAT) should be properly carried out in the testing environment. Production data should not be used in development or acceptance testing unless the data has been desensitized and prior approval from the information owner has been obtained.
Segregation of duties
- Segregation of duties among IT teams should be properly maintained. Developers should not be able to get access to production libraries and promote programming code into the production environment. If automated tools are used for the promotion of programming code, adequate monitoring, reviews and checks by independent teams should be done. Vendor accesses to the UAT environment, if necessary, should be closely monitored.
End-user computing
- An inventory of end-user developed applications should be maintained and where necessary, control practices and responsibilities with respect to end-user computing to cover areas such as ownership, development standard, data security, documentation, data/file storage and backup, system recovery, audit responsibilities and training should be established.
IT service support - Problem management
- A problem management process to identify, classify, prioritize and address all IT problems in a timely manner should be established. A trend analysis of past incidents should be performed regularly to facilitate the identification and prevention of similar problems.
Change management
- A formal change management process should be developed to ensure the integrity and reliability of the production environment and that the changes to application systems, system software (e.g. operating systems and utilities), hardware, network systems and other IT facilities and equipment, are proper and do not have any undesirable impact on the production environment. Formal procedures for managing emergency changes (including the record keeping and endorsement arrangement) should also be established to enable unforeseen problems to be addressed in a timely and controlled manner.
Security baseline standards
- Control procedures and baseline security requirements, including all configurations and settings of operating systems, system software, databases, servers and network devices should be adequately and accurately documented. Periodic reviews on the compliance of the security settings with the baseline standards should be performed.
IT operation - Job scheduling
- The initial schedules and changes to scheduled jobs should be appropriately authorized. Procedures should be in place to identify, investigate and approve departures from standard job schedules.
Vulnerability and patch management
- A combination of automated tools and manual techniques should be deployed to regularly perform comprehensive vulnerability assessments. For web-based external facing systems, the scope of vulnerability assessment should include common web vulnerabilities.
- Patch management procedures should be formulated to include the identification, categorization, prioritization and installation of security patches. To implement security patches in a timely manner, the implementation timeframe for each category of security patches should be defined based on severity and impact on systems.
- Security monitoring tools should be implemented to retain system, application and network device logs to facilitate examination when necessary in accordance with the Licensee’s defined log retention policy. The tools should also monitor and report, on a real-time basis if possible, critical configurations and security settings to identify unauthorized changes to these settings and block anomalies on IT assets, e.g. abnormal user behaviors, unusual system processes and memory access and malicious callbacks to devices.
IT facilities and equipment maintenance
- IT facilities and equipment should be maintained in accordance with the industry practice, and suppliers’ recommended service intervals and specifications to ensure the facilities and equipment are well supported.
Mobile computing
- Where a Licensee provides mobile devices for its employees, policies and procedures covering, among others, requisition, authentication, hardening, encryption, data backup and retention should be established.
Network and infrastructure management
- Overall responsibility for network management should be clearly assigned to individuals who are equipped with expertise to fulfil their duties. Network standards, design, diagrams and operating procedures should be formally documented, kept up-to-date, communicated to all relevant network staff and reviewed periodically.
- A Licensee should have in place adequate measures to maintain appropriate segregation of databases for different purposes to prevent unauthorized or unintended access or retrieval and robust access controls should be enforced to ensure the confidentiality and integrity of the databases. In respect of any personal data of Customers, including merchants, a Licensee should at all times comply with this Regulation, the relevant data protection laws as well as any relevant codes of practice, guidelines or best practice issued by the relevant authorities from time to time.
- Access to the information and application systems should be restricted by an adequate authentication mechanism associated with access control rules. A role-based access control framework should be adopted and access rights should only be granted on a need-to-have basis.
- A security administration function and a set of formal procedures should be established for administering the allocation of access rights to system resources and application systems, and monitoring the use of system resources to detect any unusual or unauthorized activities.
- Due care should be exercised by Licensees when controlling the use of and access to privileged and emergency IDs. The necessary control procedures include: (a) changing the default password; (b) restricting the number of privileged users; (c) implementing strong controls over remote access by privileged users; (d) granting of authorities that are strictly necessary to privileged and emergency IDs; (e) formal approval by appropriate senior personnel prior to being released for usage; (f) logging, preserving and monitoring of the activities performed by privileged and emergency IDs (e.g. peer reviews of activity logs); (f) prohibiting sharing of privileged accounts; (g) proper safeguard of privileged and emergency IDs and passwords (e.g. kept in a sealed envelope and locked up inside the data center); and; (h) changing of privileged and emergency IDs’ passwords immediately upon return by the requesters.
Cyber resilience
Cyber security risk assessment process
- Where a Licensee is heavily reliant on Internet and mobile technologies to deliver its services, cyber security risks must be adequately managed through the Licensee’s technology risk management process. The Licensee should also commit adequate resources to ensure its capabilities to identify the risk, protect its critical services against the attack, contain the impact of cyber security incidents and restore the services.
Cyber threat intelligence
- A Licensee must keep pace with the trends in cyber threats. It may consider subscribing to quality cyber threat intelligence services, which are relevant to its business, to enhance its ability to precisely respond to new type of threats in a timely manner. The Licensee may also seek opportunities to collaborate with other organizations to share and gather cyber threat intelligence with the aim of facilitating the SVF industry to better prepare and manage cyber security risks.
Penetration and cyber-attack simulation testing
- A Licensee must regularly assess the necessity to perform penetration and cyber-attack simulation testing. Coverage and scope of testing should be based on the cyber security risk profile, cyber intelligence information available, covering not only networks (both external and internal) and application systems but also social engineering and emerging cyber threats. A Licensee should also take appropriate actions to mitigate the issues, threats and vulnerabilities identified in penetration and cyber-attack simulation testing in a timely manner, based on the impact and risk exposure analysis.
Internet connected device
- As Internet evolves, more devices or appliances are embedded with Internet connectivity. These devices with “always on” network connectivity may create more end-points which allow intruders to get access to a Licensee’s critical IT infrastructure. The Licensee should pay attention to related risks and take appropriate measures accordingly.
Payment security management
- A Licensee must put in place a robust payment security management framework that is commensurate with the scale and nature of payment security risks associated with its SVF schemes to effectively monitor, identify, evaluate, respond and mitigate the payment security risks arising from the operation of the SVF schemes.
- A Licensee must have adequate policies and procedures on the ownership, classification, storage, transmission, processing and retention of information collected from Customers through registration of SVF service and execution of payment transactions to ensure confidentiality and integrity of the information.
Information ownership
- An information owner should be assigned to the specific information being collected, processed, created, and maintained. The information owner should be accountable for classification, usage authorization and protection of information processed by and stored in systems.
Information classification
- Information should be classified into different categories according to the degree of sensitivity to indicate the extent of protection required. To aid the classification process, a Licensee should develop guidelines and definitions for each classification and define an appropriate set of procedures for information protection in accordance with the classification scheme.
Information in storage
- Sensitive data stored in end-user devices as well as the backend systems of Licensees, such as payment data, personal identifiable information and authentication data must be appropriately secured against theft and unauthorized access or modification. Sensitive data should be encrypted and stored in a secure storage environment, using strong and widely recognized encryption techniques.
Information in transmission
- A Licensee must ensure that when transmitting sensitive data, e.g. from a Customer’s device to a Licensee’s server, a strong and secure end-to-end encryption is adopted and maintained in order to safeguard the confidentiality and integrity of the data, using strong and widely recognized cryptographic techniques.
- Where applicable, communication channels for data exchange should only be open on a need-to-use basis. For example, where it is practical to do so, communications via contactless channels should only be allowed after activation by the Customer and within a limited time window.
Information in processing
- If a Licensee offers merchant acquiring services, it should require its merchants to have necessary measures in place to protect sensitive data related to payments and should refrain from providing services to merchants which cannot ensure such protection. The Licensee should also implement sufficient controls to maintain and verify the integrity of the information processed by its systems.
Information retention and disposal
- A Licensee must implement an information retention and disposal policy to limit the data storage amount and retention time, having regard to applicable legal, regulatory, and business requirements.
Information minimization
- In designing, developing and maintaining payment services, a Licensee should ensure that information minimization is an essential principle of the core functionality: gathering, routing, processing, storing and/or archiving.
- A Licensee must implement adequate security measures to protect each payment channel (including cards and user devices) provided to Customers for using its SVF against all material vulnerabilities and attacks. A Licensee providing payment card services should implement adequate safeguards to protect sensitive payment card data.
Customer device
- A Licensee should assume that Customer devices are exposed to security vulnerabilities and take appropriate measures when designing, developing and maintaining payment services. Security measures should be in place to guard against different situations, including unauthorized device access, malware or virus attack, compromised or unsecure status of mobile device and unauthorized mobile applications.
Mobile device for payment acceptance
- If mobile devices are used by merchants to accept a Licensee’s payment solutions, additional security measures should be implemented to safeguard the mobile payment acceptance solution, including the detection of abnormal activities and logging them in reports, and the provision of merchant identification for Customers to validate its identity.
Customer authentication
- A Licensee should select reliable and effective authentication techniques to validate the identity and authority of its Customers. Two-factor authentication is normally expected for high-risk transactions. Customer authentication is stronger when two-factor authentication is adopted by combining any two of the following three factors: (a) something a Customer knows (e.g. user IDs and passwords); (b) something a Customer has or possesses (e.g. one-time passwords generated by a security token or a Licensee’s security systems); and (c) something a Customer is (e.g. retina, fingerprint or voice recognition).
- If a password (including a personal identification number) is used as one factor of authentication, a Licensee must put in place adequate controls related to the strength of the password (e.g. minimum password length).
Login attempts and session management
- Effective controls include limiting the number of login or authentication attempts (e.g. wrong password entries), implementing time-out controls and setting time limits for the validity of authentication. If one-time password is used for authentication purpose, a Licensee should ensure that the validity period of such passwords is limited to the strict minimum necessary.
Activities logging
- A Licensee should have processes in place ensuring that all transactions are logged with an appropriate audit trail.
- A Licensee should have robust log files allowing retrieval of historical data including a full audit trail of additions, modifications or deletions of transactions. Access to such tools, including privileged responsibilities, should only be available to authorized personnel and should be appropriately logged.
- Channels should be provided for Customers to check their past transactions.
Fraud detection systems
- A Licensee must operate transaction monitoring mechanisms designed to prevent, detect and block fraudulent payment transactions. Suspicious or high-risk transactions should be subject to a specific screening, filtration and evaluation procedure.
- Where an SVF enables a Customer to bind a credit/debit/prepaid card as a funding source for his/her SVF account, the Licensee should implement appropriate verification arrangements, to be conducted by the card issuer with the cardholder (e.g. SMS one-time password or other effective measures), to confirm that cardholder gives consent to the card binding. Such verification arrangement should be triggered at least during the binding process or when the card is initially used by the relevant SVF account. Licensees should disallow binding a card if the relevant card issuer does not support the verification arrangement required by the Licensee or fails to perform the required verification with the relevant cardholder.
- Where an SVF enables a Customer to set up a direct debit from a bank account, the Licensee should implement appropriate measures to ensure that the setting up of such a direct debit has been authorized by the relevant bank account owner.
Administration of Customer accounts
- If a Licensee allows a Customer to open an account through online channel, a reliable method should be adopted to authenticate the identity of the Customer. In general, the electronic know your customer (eKYC) process currently adopted by licensed banks is acceptable for SVF account opening.
- A Licensee should perform adequate identity checks when any Customer requests a change to the Customer’s account information or contact details that are useful for the Customer to receive important information or monitor the activities of the Customer’s accounts.
Controls over higher-risk transactions
- A Licensee should implement effective controls, such as two-factor authentication, to re-authenticate the Customer before effecting each high-risk transaction. High-risk transactions should, at least, include: (a) transactions that exceeded the predefined transaction limit(s); (b) change of personal contact details; and (c) unless it is not practicable to implement in the SVF concerned, transactions that exceeded the aggregate rolling limit(s) (i.e. total value of transactions over a period of time).
- A Licensee should define the per transaction limit(s) and the aggregate rolling limit(s), having regard to factors such as its fraud monitoring capability, maximum stored value per SVF (if applicable), maximum daily top up limit (if applicable) and other fraud protection mechanism implemented. Such limits should be clearly communicated to Customers.
Business continuity management
- A Licensee must have in place an adequate business continuity management program to ensure continuation, timely recovery, or in extreme situations orderly scale-down of critical operations in the event of major disruptions caused by different contingent scenarios. An adequate business continuity management program comprises business impact analysis, recovery strategies, a business continuity plan and alternative sites for business and IT recovery. These components are elaborated further below.
Business impact analysis
- A business impact analysis normally comprises two stages. The first stage is to (a) identify potential scenarios that may interrupt a Licensee’s services over varying periods of time, and (b) identify the minimum level of critical business and payment services that must be maintained in the event of a prolonged service interruption.
- The second stage of a business impact analysis is a recovery time-frame assessment. It aims to develop key realistic, measurable and achievable recovery time objectives: (a) maximum tolerable downtime to recover and resume the minimum service levels of critical business and payment services; (b) recovery time objective to recover critical IT resources and critical business and payment services; and (c) recovery point objective to recover data in a secure, timely manner and full integrity.
Recovery strategies
- A set of recovery strategies should be put in place to ensure that all critical business functions identified in business impact analysis can be recovered in accordance with the recovery timeframe defined. These recovery strategies should be clearly documented, thoroughly tested and regularly drilled to ensure achievement of recovery targets.
- A crucial element of service recovery is robust record management. A Licensee must put in place effective measures to ensure that all business records, in particular Customer records, can be timely restored in case they are lost, damaged, or destroyed. It is also crucial for a Licensee to allow Customers to access their own records in a timely manner.
- In determining a Licensee’s levels of minimal services and the recovery objectives, it should take into account a host of relevant factors, including but not limited to interdependency among critical services/systems, expectations of Customers and other stakeholders in terms of speed, stability, and reliability of its services, legal and reputational risk implications.
Business continuity plan
- A business continuity plan must be developed based on the business impact analysis and related recovery strategies. A business continuity plan should comprise, at a minimum, (a) detailed recovery procedures to ensure full accomplishment of the service recovery strategies, (b) escalation procedures and crisis management protocol (e.g. set up of a command center, timely reporting to the Central Bank, etc.) in case of severe or prolonged service disruptions, (c) proactive communication strategies (e.g. Customer notification, media response, etc.), (d) updated contact details of key personnel involved in the business continuity plan; and (d) assignment of primary and alternate personnel responsible for recovery of critical systems.
Alternate sites for business and IT recovery
- A Licensee should examine the extent to which key business functions are concentrated in the same or adjacent locations and the proximity of the alternate sites to primary sites. Alternate sites should be sufficiently distanced to avoid any shared risk and being affected by the same disaster.
- A Licensee’s alternate site should be readily accessible, installed with appropriate facilities and available for occupancy within the time requirement specified in its business continuity plan. Appropriate physical access controls should be implemented. If certain recovery staff are required to work from home in the event of a disaster, adequate computer and systems facilities should be made available in advance.
- Alternate sites for IT recovery should have sufficient technical equipment, including communication facilities, of appropriate model and capacity to meet recovery requirements.
- A Licensee must avoid placing excessive reliance on external vendors in providing business continuity management support, including the provision of the disaster recovery site and back-up equipment and facilities. A Licensee should satisfy itself that such vendors do have the capacity to provide the services when needed and the contractual responsibilities of the vendors, including the lead-time, types of support and capacity, are clearly specified.
- If a Licensee is reliant on shared computing services provided by external providers, such as cloud computing, to support its disaster recovery, it should manage the risk associated with these services.
Senior Management oversight
- Senior Management of the Licensee must establish clearly, which function has the responsibility for the entire process of business continuity management, and ensure that it has sufficient resources and expertise.
- Given the importance of business continuity management, the chief executive of a Licensee should prepare and sign-off a formal annual statement submitted to the board of directors on whether the recovery strategies adopted are still valid and whether the documented business continuity plan is properly tested and maintained.
Implementation of business continuity plan
- A Licensee is expected to conduct testing of its business continuity plan at least annually. Senior Management, primary and alternate relevant personnel should participate in the annual testing to familiarize themselves with their recovery responsibilities.
- All business continuity planning related risks and assumptions must be reviewed for relevancy and appropriateness as part of the annual planning of testing. Formal testing documentation (including test plan, scenarios, procedures and results) should be produced. A post mortem review report should be prepared for formal sign-off by Senior Management.
Reputation risk management
- A Licensee must establish and implement an effective process for managing reputation risk that is appropriate for the size and complexity of its operations. A Licensee should integrate into its business processes proper due diligence work to (a) critically assess the potential reputational implications of its plans and activities for itself and for the industry; (b) take proactive actions to avoid or contain the identified risks; and (c) respond swiftly to mitigate the potential impact should such risks materialize.
- A Licensee must also devote appropriate resources to conduct surveillance work with a view to identifying any issues with reputational implications for its operations. The objective is to protect the Licensee from potential threats to its reputation and, should there be a reputation event, minimize the effects of such an event.
- A Licensee must ensure that the relevant process is capable of detecting and responding swiftly to new and emerging threats to reputation, monitoring the changing status of risks, providing early warning of potential problems to enable remedial actions to be taken, and providing assurance that the risks affecting reputation are under control.
- A Licensee is expected to take into account international best practices and standards when designing and implementing the technology and specific risk management systems and processes.
Article (13): Business Conduct and Customer Protection
- The SVF schemes must be operated prudently and with competence in a manner that will not adversely affect the interests of the Customer or potential Customer of the Licensee. All Licensees must also comply with the existing regulatory requirements for consumer protection of the Central Bank.
- The business conduct and Customer protection requirements set out in this Article also apply to licensed banks that carry out the SVF business in the State.
Standard of conduct and business practices
- A Licensee must ensure that its business is operated in a responsible, honest and professional manner. A Licensee must treat all Customers, as well as merchants, equitably, honestly and fairly at all stages of their relationship with the Licensee. A Licensee must also act in a manner that will not adversely affect the interests of the Customer or potential Customer or the stability of any payment system in the State.
- A Licensee must be responsible for the acts or omissions of its employees, service providers and agents in respect of the conduct of its business. Employees and agents of a Licensee must be properly trained and qualified.
- A Licensee must ensure that it adopts and if needed, develops good business practices that can demonstrate its standard of conduct, including:
- 5.1. Due diligence must be performed by a Licensee to ensure that all promotional materials it issues are accurate and not misleading;
- 5.2. A Licensee may use its websites and mobile apps to provide links to e-commerce portals and other online merchants. When providing such links, the Licensee must carry out due-diligence on the e-commerce portals and merchants acquired to ascertain they are bona fide companies conducting legitimate business so as to manage reputation risk; and
- 5.3. Websites or apps of a Licensee may only provide hyper-links to other websites which offer advisory and/or sale of financial products and services provided that the Licensee has sought external legal opinion to ensure that the arrangements comply with all relevant legal and regulatory requirements.
- 5.1. Due diligence must be performed by a Licensee to ensure that all promotional materials it issues are accurate and not misleading;
Schemes and Operating Rules
- The Operating Rules of an SVF scheme must be fair to all parties concerned. A Licensee must operate its SVF scheme in strict accordance with the relevant Operating Rules.
- If a Licensee intends to engage business partners (e.g. merchant acquirers to procure merchants), it must ensure that the arrangement with business partners will not compromise its obligations under this Regulation in respect of ensuring safe and efficient operation of the SVF scheme, in particular:
- 7.1. The Licensee must conduct due diligence on business partners to carefully assess the risks involved before engaging the business relationship, and to put in place adequate control mechanism to mitigate the risks identified;
- 7.2. The Licensee must be satisfied that the contractual relationship between itself and business partners (e.g. merchants) is clearly constructed and enforceable with well-defined division of duties and liabilities supported by well-documented service level agreements, and that there are necessary safeguards in its contractual relationship with the business partners to ensure the operational safety and efficiency of the SVF scheme;
- 7.3. The Licensee must impose appropriate controls and oversight over the business arrangements with its business partners (e.g. in case of merchant acquirers), to ensure that they have proper systems in place for settlement of funds with the merchants and for mitigation of any potential money laundering and terrorist financing risks; and
- 7.4. The Licensee must ensure that the arrangement of engaging business partners is compliant with relevant personal data privacy/protection requirements and also observes this Regulation and the relevant supervisory guidelines on data protection in order to safeguard the interest of its Customers.
- 7.1. The Licensee must conduct due diligence on business partners to carefully assess the risks involved before engaging the business relationship, and to put in place adequate control mechanism to mitigate the risks identified;
- The Operating Rules of an SVF scheme must provide that the amount of funds received by a Licensee or its agent from a Customer will be credited to the account of the Customer and made available for use by the Customer in a timely manner according to the Operating Rules.
- Whilst the Central Bank will not establish a hard limit on the maximum amount of the value stored in each type of Customer accounts under an SVF scheme, a reasonable limit, supported by business justifications and control measures, must be set for the maximum amount that can be stored in each type of Customer accounts under an SVF scheme. Different storage limits can be set for different types of Customer accounts according to their respective features. All limits must be set out in the Operating Rules. The Central Bank may request a Licensee to change the limits on a case-by-case basis if the Central Bank considers it appropriate to apply such limits or the business justifications and control measures put up by the Licensee are considered unsatisfactory.
- 10. A Licensee must set out and explain clearly the key features, risks, terms and conditions, and applicable fees, charges and commissions of its schemes, facilities, services and products. Such details must be effectively communicated and made available to the relevant Customers, as well as merchants. Additional disclosures, including appropriate warnings, must be developed to provide information commensurate with the nature, complexity and risks of the schemes, facilities, services and products.
- A Licensee is solely responsible for the robustness of its SVF scheme and as such it must bear the full loss of the value stored in a Customer account where there is no fault on the part of the Customer. In general, a Customer of the Licensee must not be responsible for any direct loss suffered by him/her as a result of unauthorized transactions conducted through his/her account.
Anti-fraud framework
- A Licensee must implement an anti-fraud framework. Such framework must include duties and obligations of chief executive officer, Compliance Committee, and fraud reporting and follow-up mechanism. Appropriate and documented anti-fraud training must be provided to all employees.
Security advice for Customers
- The Licensee should provide easy-to-understand, prominent and regularly reviewed advice from time to time via effective methods and multiple channels to its Customers on security precautionary measures.
- A Licensee must manage the risk associated with fraudulent emails, websites and mobile applications, which are designed to trick customers into revealing sensitive user information such as login identifiers, passwords and one-time passwords.
Business exit plan
- With a view to minimizing the potential impact that a failure, disruption, or exit of a Licensee would have on Customers and the payment systems in the State, a Licensee is required to maintain viable plans for an orderly exit of its business and operations should other options be proven not possible.
- Among other things, a business exit plan should (a) identify a range of remote but plausible scenarios which may render it necessary for a Licensee to consider an exit; (b) develop risk indicators to gauge the plausibility of the identified scenarios; (c) set out detailed, concrete, and feasible action steps to be taken upon triggering the exit plan; (d) assess the time and cost required to implement the exit plan in an orderly manner; and (e) set out clear procedures to ensure that sufficient time and financial resources are available to implement the exit plan. The plan should be reviewed on an annual basis to ensure its relevancy and workability.
Systems interoperability
- A Licensee should ensure that its SVF systems are interoperable with other major payment systems in the State to allow connectivity of all key payment services. This is important for building a cost effective and efficient digital payment ecosystem in the State.
- The Central Bank expects Licensees to adopt a risk-based approach and refrain from adopting practices that would result in financial exclusion, particularly in respect of the need for bona fide businesses and individuals to have access to SVF products and services.
- The risk assessment processes should be able to differentiate the risks of individual Customers within a particular segment or grouping through the application of a range of factors, including country risk, business risk, product/service risk and delivery/distribution channel risk. It is inappropriate for Licensees to adopt a one-size-fits-all approach.
- The SVF schemes must be operated prudently and with competence in a manner that will not adversely affect the interests of the Customer or potential Customer of the Licensee. All Licensees must also comply with the existing regulatory requirements for consumer protection of the Central Bank.
Article (14): Anti-Money Laundering and Countering the Financing of Terrorism Procedures
- All Licensees must comply with the existing legal obligations and regulatory requirements for AML/CFT of the Central Bank and address money laundering and terrorist financing risks through appropriate preventive measures to deter abuse of the sector as a conduit for illicit funds, and detect money laundering and terrorist financing activities and report any suspicious transactions to the Financial Intelligence Unit at the Central Bank.
- The Central Bank requires the Licensees to undertake periodic risk profiling and assessment based on the AML/CFT requirements.
Risk factors
- The risk of an SVF product will to a significant degree, depend on its design, its functions and the mitigating measures applied. In assessing the risk of an SVF product, a Licensee should take into account the following risk factors:
- 3.1. maximum stored value or transaction amount of the SVF – SVF products with higher transaction value or higher maximum stored value may increase the money laundering and terrorist financing risk;
- 3.2. methods of funding – SVF products that allow funding by cash offer with little or no audit trail present a higher money laundering and terrorist financing risk. On the other hand, funding by unverified parties or via other payment methods without Customer identification can also create an anonymous funding mechanism and hence present higher money laundering and terrorist financing risks;
- 3.3. cross-border usage – in general, SVF products with cross-border usage may increase the risk as transactions may be subject to different AML/CFT requirements and oversight in other jurisdictions and also give rise to difficulties with information sharing;
- 3.4. person-to-person fund transfer function – an SVF product that allows person-to-person fund transfers may give rise to higher money laundering and terrorist financing risks;
- 3.5. cash withdrawal function – an SVF product that allows access to cash for instance through automated teller machine networks may increase the level of money laundering and terrorist financing risk;
- 3.6. holding of multiple accounts/cards – SVF products that allow a Customer to hold more than one account or card may also increase the money laundering and terrorist financing risk as it may be utilized by a third-party user other than the Customer;
- 3.7. multiple cards linked to the same account – SVF products that permit this functionality may present higher money laundering and terrorist financing risks, especially where the linked card is anonymous; and
- 3.8. payment for high-risk activities – some merchant activities, for example, gaming, present higher money laundering and terrorist financing risks.
- 3.1. maximum stored value or transaction amount of the SVF – SVF products with higher transaction value or higher maximum stored value may increase the money laundering and terrorist financing risk;
- The money laundering and terrorist financing risks of an SVF product can be reduced by implementing risk mitigating measures, which may include: (a) the application of limits on the maximum storage values, cumulative turnover or transaction amounts; (b) disallowing higher risk funding sources; (c) restricting the SVF product being used for higher risk activities; (d) restricting higher risk functions such as cash access; and (e) implementing measures to detect multiple SVF accounts/cards held by the same Customer or group of Customers.
- The level of money laundering and terrorist financing risks posed by a particular SVF product will depend on a consideration of all risk factors, the existence and effectiveness of risk mitigating measures and their functionality.
- A Licensee should assess whether a business relationship presents a higher money laundering and terrorist financing risk and assign a related risk rating. Generally, the Customer risk assessment will be based on the information collected during the identification stage. The Licensee should ensure that their CDD models are designed to address the specific risks associated to its Customer profile and SVF product features.
Compliance management arrangements and independent audit function
- A Licensee must have appropriate compliance management arrangements that facilitate the SVF’s implementation of AML/CFT systems to comply with relevant legal and regulatory obligations and to manage money laundering and terrorist financing risks effectively. Compliance management arrangements should at a minimum include oversight by the Licensee’s Senior Management and appointment of a Compliance Officer and a Money Laundering Reporting Officer.
- In addition, a Licensee should put in place comprehensive AML/CFT policies and procedures in accordance with the AML/CFT law and regulations.
Use of technology
- The Central Bank supports innovative means by which Licensees implement AML/CFT Systems effectively as well as exploring the greater use of technology and analytical tools. The Central Bank expects Licensees, before introducing any new product, service or technology, to conduct adequate risk assessments and ensure that any identified risks are effectively managed or mitigated.
- In general, the eKYC process currently adopted by licensed banks for digital onboarding of Customers is acceptable for SVF account opening. No physical face-to-face meetings with the Customer or physical documents verification are required so long as the digital authentication of the Customer and digital verification of all required documents can be done in accordance with the existing requirements of the Central Bank.
- Depending on the nature of relationship, Licensees may undertake additional CDD measures, including the collection of sufficient information to adequately understand the nature of the Virtual Asset Service Providers’ business; determining from publicly available information whether the Virtual Asset Service Providers are licensed or registered, and subject to AML/CFT supervision; and assessing the AML/CFT controls of the Virtual Asset Service Providers as appropriate. The extent of Customer due diligence measure should be commensurate with the assessed money laundering and terrorist financing risks of the Virtual Asset Service Providers.
- Globally there is an emerging range of new products and services involving Virtual Asset. In line with the FATF standards, before a Licensee offers any new products relating to Virtual Assets, it should undertake money laundering and terrorist financing risk assessment and take appropriate measures to manage and mitigate the identified risks in accordance with applicable legal and regulatory requirements. Licensees are encouraged to refer to the suggestions provided by FATF in relation to the guidance for a risk-based approach to Virtual Assets and Virtual Assets Service Providers.
- All Licensees must comply with the existing legal obligations and regulatory requirements for AML/CFT of the Central Bank and address money laundering and terrorist financing risks through appropriate preventive measures to deter abuse of the sector as a conduit for illicit funds, and detect money laundering and terrorist financing activities and report any suspicious transactions to the Financial Intelligence Unit at the Central Bank.
Part III – Enforcement
Article (15): Enforcement and Sanctions
- Violation of any provision of this Regulation may be subject to supervisory action and administrative & financial sanctions measures as deemed appropriate by the Central Bank.
- Supervisory action and administrative & financial sanctions by the Central Bank may include replacing or restricting the powers of Senior Management or board of directors, providing for the interim management of the Licensee, imposition of fines or barring individuals from the UAE financial sector.
- Violation of any provision of this Regulation may be subject to supervisory action and administrative & financial sanctions measures as deemed appropriate by the Central Bank.
Article (16): Interpretation of Regulation
The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
Article (17): Cancellation of Previous Regulation
This Regulation repeals and replaces the “Regulatory Framework for Stored Value and Electronic Payment Systems” Regulation issued in the UAE on 13/12/2016.
Article (18): Publication & Application
This Regulation shall be published in the Official Gazette in both Arabic and English and shall come into effect one month from the date of publication. In case of any discrepancy between the Arabic and the English, the Arabic version will prevail.
Annex
List of documents to be submitted in an application
- Completed application form for License
- A report on paid-up capital certified by external auditor
- A copy of the ownership structure
- The latest audited financial statements for each Controlling Shareholder
- Completed application form(s) for each Controlling Shareholder
- Outline of the Senior Management and staff structure
- Completed application forms for chief executive, alternate chief executive and director
- Independent assessment report(s) on seven areas as set out in paragraph 5 of Article (3).
- Copies of risk management policies and procedures on AML/CFT systems
- Copies of policies and procedures for managing the Float
- A copy of the investment policy for managing the investment of Float
- A copy of contract, and terms & conditions between the Applicant and the Customer
- A copy of Operating Rules for the SVF scheme
- A copy of contractual agreements which describe the rights and obligations of the related parties involved in the SVF scheme
- Business plan that covers a three-year time horizon
- Board of director’s resolution in support of the Application
- A copy of the articles of association (or equivalent) of the Applicant company in English and Arabic
- A copy of the Applicant's audited annual reports and / or audited financial statements for the past three financial years immediately prior to application.
- Each of the following:
- a). A copy of the notarized Memorandum and Articles of Association
- b). A copy of the Licensee Commercial License
- c). Auditors certification that the paid-up capital has been injected into the business
- a). A copy of the notarized Memorandum and Articles of Association
- Completed application form for License
Retail Payment Systems Regulation
C 10/2020 Effective from 10/2/2021Introduction
The Central Bank is responsible for licensing, designating and overseeing systemically important Retail Payment Systems (RPS) pursuant to the Central Bank Law. The Central Bank Law stipulates criteria and relevant factors based on which the Central Bank will determine whether or not a licensed RPS should be designated and subject to the ongoing oversight of the Central Bank. The policy objective is to ensure that operations of designated RPS are safe, sound, efficient and in compliance with relevant international standards (e.g. the PFMI), and also, would contribute to the financial and payment system stability of the State.
The Central Bank Law expressly sets out the powers of the Central Bank in relation to the licensing, designation and oversight of Financial Infrastructure Systems that are systemically important such as the RPS.
Objective and Scope of Application
The objective of this Regulation is to ensure safety and efficiency of Financial Infrastructure Systems and promote efficient and smooth operations thereof. The Regulation sets out the licensing, designation and oversight framework that the Central Bank intends to follow with respect to the licensing and designation of RPS, and the ongoing oversight of such systems. This Regulation also outlines the major obligations and ongoing requirements of a designated RPS, the powers of the Central Bank in respect thereof, the licensing, designation and ongoing oversight of an RPS.
The scope of this Regulation will cover the systematically important RPS which meet one of the following conditions: (a) the concerned system is operated in the State; or (b) the concerned system has the capacity to provide transfer, clearing or settlement of payment obligations relating to retail activities denominated in the Currency, any currency or any Regulated Medium of Exchange.
This Regulation explains the relevant policies and procedures adopted by the Central Bank with respect to the licensing and designation of RPS. It sets out: (a) the types of RPS which are likely to be covered by the Regulation; (b) the Central Bank’s intended interpretation of the key criteria for designating an RPS; (c) the licensing and designation process; (d) the ongoing requirements of the designated RPS; and (e) the appeal mechanism in respect of the licensing, designation, suspension and revocation of licensing and/or designation.
The provisions of this Regulation shall not apply to Financial Free Zones and to RPS operating therein unless when expressly provided hereunder.
Article (1): Definitions
- Central Bank: means the Central Bank of the United Arab Emirates.
- Central Bank Law: means Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities and its amendments from time to time.
- Clearing: means the process of transmitting, reconciling and, in some cases, confirming transactions prior to settlement, potentially including the Netting of transactions and the establishment of final positions for settlement.
- Clearing and Settlement System: means a system established for (a) the clearing or settlement of payment obligations; or (b) the clearing or settlement of obligations for the transfer of book-entry securities, or the transfer of such securities.
- Currency: means the State’s official national currency notes and coins, which its unit is referred as the “Dirham”.
- Default Arrangements: in respect of a Financial Infrastructure System, means the arrangements in place within the system for limiting systemic and other types of risk in the event of a Participant Person appearing to be, or likely to become, unable to meet his obligations in respect of a Transfer Order; and would include any arrangements that have been enforced by the System Operator or Settlement Institution for the following: (1) the Netting of obligations owed to or by a Participant Person; (2) the closing out of open financial position of a Participant Person; or (3) the realization of collateral securities to secure payment of obligations owed by the Participant Person.
- Designated System: means any Financial Infrastructure System designated by the Central Bank as systemically important, in accordance with the provisions of the Central Bank Law and the Regulation.
- Financial Free Zones (FFZ): means free zones subject to the provisions of Federal Law No 8 of 2004, regarding Financial Free Zones, and amending laws.
- Financial Infrastructure System: means either (1) a Clearing and Settlement System or (2) a Retail Payment System, established, operated, licensed, or overseen by any of the Regulatory Authorities in the State.
- Grievances & Appeals Committee: means the Committee referred to in Article (136) of the Central Bank Law.
- License: means a License issued by the Central Bank to an SO and/or SI to operate an RPS in the State. The License shall be valid for a period of five years, unless it is suspended or revoked by the Central Bank.
- Licensee: means an SO and/or SI that holds a valid License to operate an RPS from the Central Bank.
- Money’s Worth: value added onto an SVF by the customer; value received on the customer’s SVF account; and value redeemed by the customer including not only “money” in the primary sense but also other forms of monetary consideration or assets such as values, reward points, Crypto-Assets, or Virtual Assets. For example, a value top-up of an SVF account may take the form of values, reward points, Crypto-Assets, or Virtual Assets earned by the SVF customer from making purchases of goods and services. Similarly, value received on the account of the SVF customer may take the form of an on-line transfer of value, reward points, Crypto-Assets, or Virtual Assets between fellow SVF customers.
- Netting: in respect of a Clearing and Settlement System, means the conversion of the various obligations owed to or by a Participant Person towards all the other Participant Persons in the system, into one net obligation owed to or by the Participant Person.
- Operating Rules: means rules set up by the System Operator to cover the operation of a Financial Infrastructure System, including but not limited to, Participant Person account opening and maintenance, contractual relationships with and among Participant Persons, Default Arrangements, payment and settlement processing, Netting and collateral arrangements, authorization and post-transaction processes.
- Payment System: a Financial Infrastructure System which consists of a set of instruments, procedures, and rules for the transfer of funds between or among Participant Persons.
- Participant Person: in respect of a Financial Infrastructure System shall mean a Person who is party to or participant of the arrangements for which the system has been established.
- Person: means a natural or juridical person, as the case may be.
- Principles of Financial Market Infrastructures (PFMI): means the international standards for financial market infrastructures (i.e. Payment Systems, central securities depositories, securities settlement systems, central counterparties and trade repositories) issued by the Committee on Payments and Market Infrastructures (CPMI) and the International Organization of Securities Commissions (IOSCO). The PFMI are part of a set of 12 key standards that international community considers essential to strengthening and preserving financial stability.
- Regulated Medium of Exchange: means an instrument or a token that is widely used and accepted in the State as a means of payment for goods and services and regulated by the Central Bank to be a medium of exchange.
- Regulation: means the Retail Payment Systems Regulation.
- Regulatory Authorities: means the Central Bank and the Securities & Commodities Authority.
- Relevant Undertaking: In relation to an SVF, Relevant Undertaking means an undertaking by the Licensee that, upon the use of SVF by the customer as a means for payment for goods and services (which may be or include money or Money’s Worth) or payment to another person, and whether or not some other action is also required, the Licensee, or a third party that the SVF issuer has procured to do so, will, in accordance with the Operating Rules: (a) supply the goods or services; (b) make payment for the goods or services; or (c) make payment to the other person, or as the case requires.
- Retail Payment System (RPS): means any fund transfer system and related instruments, mechanism, and arrangements that typically handles a large volume of relatively low-value payments in such forms as cheques, credit transfers, direct debit, card payment transactions or a Regulated Medium of Exchange.
- Settlement Institution (SI): means an institution that provides settlement services to a Financial Infrastructure System, settlement accounts in one currency or multi-currency in the Financial Infrastructure System and in certain cases grants access to intraday liquidity to Participant Persons.
- State: means the United Arab Emirates.
- Stored Value Facilities (SVF): A facility (other than cash) for or in relation to which a customer, or another person on the customer’s behalf, pays a sum of money (including Money’s Worth such as values, reward points, Crypto-Assets or Virtual Assets) to the issuer, whether directly or indirectly, in exchange for: (a) the storage of the value of that money (including Money’s Worth such as values, reward points, Crypto-Assets or Virtual Assets), whether in whole or in part, on the facility; and (b) the “Relevant Undertaking”. SVF includes device-based Stored Value Facility and non-device based Stored Value Facility.
- System Operator (SO): means a Person responsible for the operation of a Financial Infrastructure System, including the comprehensive management of all risks in the Financial Infrastructure System and ensuring that the operation of the system is in accordance with this Regulation and other relevant regulations issued by the Central Bank.
- Systemically Important Payment System: means a Financial Infrastructure System which has the potential to trigger or transmit systemic disruptions to the State’s monetary and financial stability; this includes, among other things, systems that are the sole Financial Infrastructure System in a jurisdiction or the principal system in terms of the aggregate value of payments, and systems that mainly handle time-critical, high-value payments or settle payments used to effect settlement in other Financial Infrastructure Systems.
- Transfer: means operationally, the sending (or movement) of funds or securities or of a right relating to funds and securities from one party to another party by (i) conveyance of physical instruments/money; (ii) accounting entries on the books of a financial intermediary; or (iii) accounting entries processed through a funds and/or securities transfer system.
- Transfer Order: in respect of a Financial Infrastructure System shall mean any of the following instructions: (1) instructions by a Participant Person to make funds available to another Participant Person to be transferred, on a book-entry basis, in the accounts of the Settlement institution for a Clearing and Settlement System; or (2) instructions for discharge from obligation to pay, for the purposes of the Operating Rules of a Clearing and Settlement Systems; or (3) instructions by a Participant Person to either settle an obligation by transferring a book-entry security, or transferring those securities; or (4) instructions by a Participant Person that result in liability or discharge of retail operations payment obligation.
- Central Bank: means the Central Bank of the United Arab Emirates.
Article (2): Licensing Requirements
- As stipulated in Article (129) (1) (a) of the Central Bank Law, operating an RPS in the State requires a prior License from the Central Bank.
- The SO and/or SI of the RPS must apply and submit the required information and documents set out in Annex A to the Central Bank for a License if the RPS is in operation in the State.
- As stipulated in Article (129) (1) (a) of the Central Bank Law, operating an RPS in the State requires a prior License from the Central Bank.
Article (3): Eligibility and Criteria for Designation as Systemically Important Financial Infrastructure System
- As stipulated in Article (126) (2) of the Central Bank Law, if a licensed RPS falls within the eligibility for designation as set out in the aforementioned Article, the Central Bank may designate such RPS as systemically important.
- Financial Infrastructure Systems which may be covered by the definition of RPS include, but are not limited to, the following systems:
- 2.1. Electronic funds transfer system: a system that handles transfer of funds which is initiated through a computer system, for the purpose of ordering, instructing, or authorizing a financial institution to debit or credit a customer’s account. The Central Bank will not license or designate RPS owned and/or operated by licensed banks (e.g. Internet or mobile banking systems, electronic fund transfer systems, etc.) for serving their own customers because such RPS are already subject to the Central Bank’s prudential supervision of the licensed bank as a whole. However, if a licensed bank provides RPS services to other payment service providers or financial institutions, such RPS may be subject to designation if the RPS falls within the designation criteria.
- 2.2. Payment card system: a set of functions, procedures, arrangements, rules, and most importantly, a Clearing and Settlement System and network infrastructure that enable a holder of a payment card to effect a payment and/or cash withdrawal transaction with a third party other than the card issuer.
- 2.3. Clearing and Settlement System for SVF1: a Payment System used to support the SVF business and scheme. An SVF scheme normally requires a Payment System to support their operation. Such a system normally falls within the RPS definition. To avoid regulatory overlap and inducing excess regulatory burden on SVF Licensees, the Central Bank does not intend to designate a Payment System run by a SVF Licensee to support its own SVF business and scheme. It is because the entire SVF business scheme and the related Payment System are already subject to the SVF Regulation, which ensures the safety and soundness of the Payment System including the transfer, clearing and settlement of payment obligations. Nonetheless, if the RPS operated by the SVF Licensee also supports SVF schemes run by other issuers or if a third party operates a Payment System to support other SVF schemes operating in the State, the Central Bank may designate such RPS if it meets the designation criteria.
- 2.4. Payment gateway: a system that processes, accepts or declines payment transactions on behalf of the merchant secure network connections.
- 2.1. Electronic funds transfer system: a system that handles transfer of funds which is initiated through a computer system, for the purpose of ordering, instructing, or authorizing a financial institution to debit or credit a customer’s account. The Central Bank will not license or designate RPS owned and/or operated by licensed banks (e.g. Internet or mobile banking systems, electronic fund transfer systems, etc.) for serving their own customers because such RPS are already subject to the Central Bank’s prudential supervision of the licensed bank as a whole. However, if a licensed bank provides RPS services to other payment service providers or financial institutions, such RPS may be subject to designation if the RPS falls within the designation criteria.
- In forming an opinion as to whether an RPS satisfies the designation criteria, the Central Bank may consider one or more of the following factors in order to determine whether or not the RPS is a Systemically Important Payment System: -
- 3.1. The estimated aggregate value of Transfer Orders transferred, cleared or settled through the RPS in a normal business day. The foregoing refers to the total value of individual instructions cleared or settled in the RPS. For established RPS during the transitional period, the estimated value can be worked out with reference to historical data and business plan.
- 3.2. The estimated average value of Transfer Orders transferred, cleared or settled through the RPS in a normal business day. The foregoing refers to the aggregate value of instructions transferred, cleared or settled through the RPS in a normal business day, divided by the number of instructions processed.
- 3.3. The estimated number of Transfer Orders transferred, cleared or settled through the RPS in a normal business day.
- 3.4. Whether those transactions or the equivalent payment services could be immediately and effectively handled by another Payment System in the State.
- 3.5. Whether any cross-border activities are involved, including the number of involved countries and the total volume of processed Transfer Orders.
- 3.6. The estimated number of Participant Persons of the RPS.
- 3.7. Whether such RPS is linked to any Designated Systems or any Payment System that is licensed or regulated by other Regulatory Authorities in the State.
- 3.1. The estimated aggregate value of Transfer Orders transferred, cleared or settled through the RPS in a normal business day. The foregoing refers to the total value of individual instructions cleared or settled in the RPS. For established RPS during the transitional period, the estimated value can be worked out with reference to historical data and business plan.
- In general, the higher the estimated aggregate value or number of Transfer Orders, the more likely an RPS is material to the financial system of the State and of significant public interest. The number of linkages of an RPS to another Designated System is an important factor that the Central Bank will consider when making a designation decision given the contagion risk to the financial system such linkage could bring.
- Apart from the above factors, the Central Bank will also consider other factors, for example, in the case of a card payment system, among others, the number of cards issued, the number of card acceptance points. The Central Bank will take a holistic approach in considering these factors, as they complement each other in providing different criteria for assessing the significance of an RPS.
- The above-mentioned factors are intended to identify an RPS whose proper functioning is material to the monetary or financial stability of the State, or that should be designated, having regard to matters of significant public interest or public order. During the designation process, should the need arise, the Central Bank will discuss with the SO and/or SI of the relevant RPS so as to understand the design and features of the system and assess whether it fulfills the criteria of a Systemically Important Financial Infrastructure System.
1 Detailed regulatory requirements of SVF are set out in the SVF Regulation
- As stipulated in Article (126) (2) of the Central Bank Law, if a licensed RPS falls within the eligibility for designation as set out in the aforementioned Article, the Central Bank may designate such RPS as systemically important.
Article (4): Designation Process
- The Central Bank will initiate the designation process under the designation framework as stipulated in Article (126) (3) of the Central Bank Law if it considers an RPS is meeting, or is likely to meet the criteria for designation. It is important to note that designation of an RPS does not in any way represent or imply that the Central Bank endorses such system. Designation of an RPS is to provide for such system to be subject to oversight by the Central Bank, with a view to maintaining and promoting the general safety and efficiency of such system.
- For the Central Bank to determine whether an RPS is eligible to be designated and whether it satisfies the designation criteria for the purposes of this Regulation, the Central Bank will request information or documents regarding the RPS from any Person who is holding, or whom the Central Bank reasonably believes holds such information or documents or is a SO and/or SI of the RPS or a Participant Person in the RPS. This power to request information or documents applies to RPS, individuals or corporations established, located or incorporated in the State and/or outside the State. The Central Bank will coordinate with any competent Regulatory Authority in the State or other competent authorities in other jurisdictions for the purpose of requesting and securing such information and documents.
- Generally speaking, the Central Bank will seek to request information or documents as set out in the Annexes of this Regulation and may, where necessary, seek additional information as is required in order to assist the Central Bank in making such determination. The types of information or documents that the Central Bank will require might vary from RPS to RPS.
- During the designation process, the Central Bank may discuss with the SO and/or SI of such system where necessary to understand the features and the design of the system and determine the RPS’s eligibility for designation.
- The time for the designation process may vary depending on the particular situation of each case, including the nature and complexity of the prospective designated RPS, the completeness of information and documents submitted to the Central Bank.
- The SO and/or SI of the designated RPS may submit a grievance against the designation decision by applying to the Grievances & Appeal Committee. Details on the appeal mechanism as set out in Article (11) of this Regulation.
- If the Central Bank intends to designate any of the RPS licensed by a competent Regulatory Authority in the State or competent regulatory authorities in other jurisdictions as systemically important RPS, the Central Bank shall implement the process provided for under Article (126) (6) of the Central Bank Law.
RPS deemed to have been licensed and designated
- As stipulated in Article (126) (5) of the Central Bank Law, the RPS established, developed, and/or operated by the Central Bank are deemed to have been licensed and designated.
- The RPSs that are deemed to have been designated are required to observe all the obligations and requirements imposed on designated RPSs under this Regulation in the same manner as other designated RPSs.
- The Central Bank will initiate the designation process under the designation framework as stipulated in Article (126) (3) of the Central Bank Law if it considers an RPS is meeting, or is likely to meet the criteria for designation. It is important to note that designation of an RPS does not in any way represent or imply that the Central Bank endorses such system. Designation of an RPS is to provide for such system to be subject to oversight by the Central Bank, with a view to maintaining and promoting the general safety and efficiency of such system.
Article (5): Cooperation with Relevant Regulatory Authorities
- As part of the designation process for RPS established and/or licensed by another Regulatory Authority in the State or by relevant regulatory authorities in other jurisdictions, the Central Bank may agree with the relevant regulatory authority which parts of this Regulation, where relevant, may not apply to concerned designated RPS to avoid additional regulatory burden on the SO and SI of the RPS.
- The Central Bank will rely on co-operative oversight with the relevant regulatory authority of a designated RPS operating in the State or in other jurisdictions, in accordance with articles (28) and (127) (2) of the Central Bank Law and the cooperative framework set out in the PFMI.
- As part of the designation process for RPS established and/or licensed by another Regulatory Authority in the State or by relevant regulatory authorities in other jurisdictions, the Central Bank may agree with the relevant regulatory authority which parts of this Regulation, where relevant, may not apply to concerned designated RPS to avoid additional regulatory burden on the SO and SI of the RPS.
Article (6): Revocation of License and Designation
Grounds for revocation
- As stipulated in Article (128) of the Central Bank Law, the Central Bank may revoke the License of an RPS if the RPS is unable to carry out its operations in compliance with the provisions of the Central Bank Law or this Regulations.
- As stipulated in Article (126) (7) of the Central Bank Law, the Central Bank may revoke the designation of an RPS if the RPS has ceased to be, or is likely to cease being a Systemically Important Financial Infrastructure System or an RPS whose proper functioning is material to the monetary or financial stability of the State.
Revocation process
- The Central Bank will prepare a review report on whether a licensed and/or designated RPS satisfies the revocation criteria under this Regulation. If the Central Bank intends to revoke the License and/or the designation of a RPS, the Central Bank will notify in writing the SO and/or SI of the RPS or the regulatory authority where the RPS is licensed so that such authority can notify the SO and/or SI of the system of the intention of the Central Bank to revoke the License and/or the designation. The notice needs to state the grounds on which the revocation is to be made and specify in the notice a period of not less than twenty (20) working days from the date of notification, during which the SO and/or SI of the system may be heard, or may make written justifications, as to why the grounds for revocation stated in the notice are not valid.
- If any SO and/or SI of the licensed and/or designated RPS wish to be heard or to make written justifications, it should make such a request to the Central Bank in writing before the revocation takes effect, giving reasons as to why the grounds for revocation specified in the notice have not been established. After reviewing the reasons given by the SO and/or SI, the Central Bank will determine whether the Licensee and/or designation should be revoked. In the course of reviewing the matter, the Central Bank may meet with the SO and/or SI of the License and/or designated RPS should such need arise.
- If the Central Bank decides to proceed to revoke the License and/or designation of the RPS, the Central Bank will notify the SO and/or SI of the RPS of the Central Bank’s decision in writing.
- The SO and/or SI may object to the Central Bank’s decision to revoke the License and/or the designation of the RPS and provide justifications for such objection by applying to the Grievances & Appeals Committee as provided by the Central Bank Law.
- The Central Bank, if it considers that any of the RPS licensed by another Regulatory Authority in the State or the relevant regulatory authorities in other jurisdictions is no longer meeting the designation criteria, may request the concerned regulatory authority, via an official notice, to revoke the License and/or designation of the RPS.
- In all cases, the revocation of the License and/or designation of the RPS shall not affect any transaction cleared and settled in the concerned RPS prior to the effective date of revocation.
- As stipulated in Article (128) of the Central Bank Law, the Central Bank may revoke the License of an RPS if the RPS is unable to carry out its operations in compliance with the provisions of the Central Bank Law or this Regulations.
Article (7): Settlement Finality
- In accordance with Article (131) of the Central Bank Law settlement finality is “the discharge of an obligation by a transfer of funds that has become irrevocable and unconditional”. Specifically, “settlement finality” refers to the abrogation of all rights otherwise existing at law that would allow the reversal of a Transfer Order effected through, or proceeding within, an RPS.
- Article (131) (1) of the Central Bank Law grants finality to all transactions conducted through a Financial Infrastructure System, therefore rendering the same final, irrevocable and irreversible, in any of the cases provided for thereunder. Besides finality in respect of Transfer Orders, the Central Bank Law also provides legal certainty on the Netting arrangements in a designated RPS.
- If Netting has been effected in an RPS that meets any of the designation conditions refers to in Article (126) (2) of the Central Bank Law, the SO and/or SI needs to take into consideration the Netting of obligations of insolvent or bankrupt parties in Article (133) of the Central Bank Law.
- In addition, the preservation of rights in underlying transactions and obligation of Participant Person to notify of insolvency are set out in Article (134) and Article (135) of the Central Bank Law respectively.
- In accordance with Article (131) of the Central Bank Law settlement finality is “the discharge of an obligation by a transfer of funds that has become irrevocable and unconditional”. Specifically, “settlement finality” refers to the abrogation of all rights otherwise existing at law that would allow the reversal of a Transfer Order effected through, or proceeding within, an RPS.
Article (8): Ongoing Requirements of Designated Retail Payment Systems
Principal Requirements
- The SO and/or SI of a designated RPS, are required to ensure compliance with the following:
- 1.1. RPS must comply with any instructions issued by the Central Bank and any relevant international standards (e.g. PFMI), and ensure proper and continued functioning of the designated RPS; and
- 1.2. RPS must provide the information required by the Central Bank or where SO and/or SI consider it appropriate for achievement of the Central Bank objectives.
- 1.1. RPS must comply with any instructions issued by the Central Bank and any relevant international standards (e.g. PFMI), and ensure proper and continued functioning of the designated RPS; and
- The Central Bank may exempt the SO and/or SI or a Participant Person of a designated RPS in a general or specific manner, from the provisions of this Regulation.
- The Central Bank may appoint experts and advisors specialized in Financial Infrastructure Systems to assist the Central Bank in performing its duties and functions in accordance with this Regulation.
Detailed requirements
Principal requirements
- Upon designation, a designated RPS is required to comply with the ongoing requirements imposed under this Regulation and the relevant provisions of PFMI (see Article (9) for detail). Failure to comply with any of those requirements would expose the concerned party to possible sanctions provided for under the Central Bank Law. The principal requirements include: -
- 4.1. Submission of particulars – the Central Bank requires any SO and/or SI of a newly designated RPS to inform the Central Bank in writing of the designation particulars within fourteen (14) working days after the notification of designation, including the name, place of business, postal address and electronic mail address, as well as the aspects of the management or operations of the system. For any SO and/or SI which is a corporation, the names and personal particulars of the directors, chief executive (if any) and shareholders of the corporation are similarly required to be submitted to the Central Bank. Details of any subsequent change in any of those particulars are to be notified to the Central Bank in writing within fourteen (14) days of the change taking effect.
- 4.2. Compliance with safety and efficiency requirements - the general requirements include safe and efficient operation of the RPS, the establishment of appropriate Operating Rules, the existence of adequate compliance arrangements, and the availability of appropriate financial resources.
- 4.3. Submission of information or documents - the Central Bank may request information or documents relating to a designated RPS from the SO and/or SI of, or the Participant Person in, the RPS when performing the oversight functions under this Regulation. The SO and/or SI of, or the Participant Person in the designated RPS to whom a request is made is required to submit the information or documents within the period specified in the request.
- 4.4. The Central Bank may, at any time, with a short prior notice to the SO and/SI concerned, examine any books, accounts or transactions of the SO and/or SI of a designated RPS when performing the oversight functions.
- 4.5. The Central Bank may require the SO and/or SI of, or the Participant Person in, a designated RPS to submit to the Central Bank a report prepared by one or more auditors on matters that the Central Bank requires for discharging or exercising its duties and powers under this Regulation.
- 4.6. The Central Bank may direct the SO and/or SI of a designated RPS to take any action necessary to bring the RPS into compliance with any of the requirements under this Regulation. Such a direction will specify the Central Bank’s concerns and the action(s) to be taken, include a statement of the respect in which the Central Bank considers the designated RPS not be in compliance with a requirement under this Regulation and specify the period within which the direction is to be complied with.
- 4.7. The Central Bank may, by notice in writing, direct the SO and/or SI of a designated RPS to take any action the Central Bank considers necessary to bring the RPS into compliance with any of the requirements under this Regulation.
- 4.1. Submission of particulars – the Central Bank requires any SO and/or SI of a newly designated RPS to inform the Central Bank in writing of the designation particulars within fourteen (14) working days after the notification of designation, including the name, place of business, postal address and electronic mail address, as well as the aspects of the management or operations of the system. For any SO and/or SI which is a corporation, the names and personal particulars of the directors, chief executive (if any) and shareholders of the corporation are similarly required to be submitted to the Central Bank. Details of any subsequent change in any of those particulars are to be notified to the Central Bank in writing within fourteen (14) days of the change taking effect.
Obligation of SO and SI to notify the Central Bank of certain events
- The SO and/or SI of a designated RPS must notify the Central Bank of the occurrence of any of the following events as soon as practicable after that occurrence:
- 5.1. An event or irregularity that impedes or prevents access to, or impairs the usual operations of, the designated RPS or its settlement operations.
- 5.2. Any material function of the SO and/or SI that is outsourced.
- 5.3. Any civil or criminal proceeding instituted against the SO and/or SI, whether in the State or elsewhere.
- 5.4. The SO and/or SI being unable to meet any of the financial, statutory, contractual or other obligations of the SO and/or SI.
- 5.5. Any disciplinary action taken against the SO and/or SI by any regulatory authority, whether in the State or elsewhere.
- 5.6. Any change of the chief executive officer or senior management of the SO and/or SI.
- 5.1. An event or irregularity that impedes or prevents access to, or impairs the usual operations of, the designated RPS or its settlement operations.
Governance arrangements
- The SO and/or SI of the designated RPS must have clearly defined and documented organizational arrangements, such as ownership and management structure. Each should operate with appropriate segregation of duties and internal control arrangements so as to reduce the risk of mismanagement and fraud.
- The SO and/or SI of the designated RPS must have effective measures and controls to ensure compliance with this Regulation. Appropriate processes must be in place to ensure that rules and procedures as well as the contractual relationships with its Participant Persons are valid and enforceable. These include clear rules and procedures to govern transfer, clearing and settlement for both domestic and cross-border transactions (if applicable).
Compliance
- The SO and/or SI of the designated RPS are required to perform a periodic self-assessment or independent assessment of its compliance with this Regulation and the relevant principles of the PFMI set out in Article (9) of this Regulation. Such assessment must be done at least every 24 months. Its internal auditors, internal compliance officer or appointed independent assessor should perform such assessment as part of their on-going duties and provide the Central Bank with a copy of their compliance report. Assessment reports submitted to the Central Bank by the SO and/or SI of the designated RPS are confidential and shall not be disclosed to any third party unless the approval of the Central Bank is obtained.
Financial requirement
- The financial condition of the SO and/or SI of the designated RPS must be sound and viable, and subject to ongoing review and monitoring by the senior management of the SO and/or SI.
Participation criteria
- The SO and/or SI of the designated RPS must have an established process for considering applications to become its Participant Person. The SO and/or SI of the designated RPS must have procedures in place to allow prospective Participant Persons to access or obtain the information necessary to determine whether to apply to become a Participant Person.
- The general eligibility and participation criteria should be disclosed to genuine applicants upon request.
Transparency, interoperability and competition
- The SO and/or SI of the designated RPS shall not establish or impose any operational policies, procedures and arrangements that will prevent operational transparency or interoperability among Payment Systems, and competition among market players. The SO and/or SI of the designated RPS must observe and comply with all relevant laws, codes of practice and guidelines applicable to their payment activities and services in the State.
- If the Central Bank considers the interoperability between the RPS and other Payment System(s) would be in the interest of the public or the Participant Persons of systems involved, it may direct the SO and/or SI of the RPS involved to enter into arrangements to enable the interoperability among the systems involved or to adopt any common standards.
- The relevant fees and charges must be documented and communicated clearly to the Participant Persons.
- The SO and/or SI of the designated RPS must inform affected Participant Persons of changes to its operational procedures and arrangements that materially affect such parties’ financial risk, operational risk, data security risk and legal risk in the State.
Rules and procedures
- The SO and/or SI of the designated RPS must have proper Operating Rules to enable its Participant Persons to obtain sufficient information regarding their respective rights and obligations associated with their participation in the RPS. Such rights and obligations must be clearly defined and disclosed to the Participant Persons.
- Operating Rules of the RPS must be complete, up-to-date and readily available to all Participant Persons. Participant Persons must also be duly informed of any relevant changes in the Operating Rules.
- The SI must establish rules and procedures to enable final settlement to take place no later than the end of the intended settlement date. The related rules and procedures must also ensure certainty in terms of circumstances under which Transfer Orders effected through the RPS are to be regarded as settled for the purposes of the RPS.
- The liabilities of Participant Persons for any loss arising from unauthorized use of the RPS and the arrangements to handle any disputes over Participant Persons’ liability with respect to unauthorized transactions must be clearly set out in the rules and procedures.
Operational efficiency
- The SO and/or SI of the designated RPS should provide convenient and efficient payment services to its Participant Persons, and ensure that the RPS can process transactions at a speed which is efficient and complies with the RPS’ committed service level.
Operational reliability and business continuity
- The SO and/or SI of the designated RPS must have sound and prudent management, administrative, accounting and control procedures managing the financial and non-financial risks to which it reasonably considers it may be exposed.
- The SO and/or SI of the designated RPS must conduct risk analysis on new payment activity or service. In addition, where it reasonably believes that there has been a change of relevant circumstances, the SO and/or SI of the designated RPS should perform a review on the risk profile of existing activities and services to assess risks relating to security and business continuity.
- The SO and/or SI of the designated RPS must seek to ensure that it has an adequate number of properly trained and competent personnel to operate its system at a level it considers appropriate in all situations that it considers are reasonably foreseeable.
- The SO and/or SI of the designated RPS should provide its Participant Persons with information it reasonably considers relevant to fraud awareness in the context of the operation of its payment activities and services. The SO and/or SI of the designated RPS should provide Participant Persons with education it reasonably considers relevant to fraud awareness and the proper use or processing of the RPS to reduce the risk of fraud so that the Participant Persons can educate and promote the awareness of their customers accordingly.
- The SO and/or SI of the designated RPS must have comprehensive, rigorous and well-documented operational and technical procedures to address reasonable operational reliability, the integrity of its network and the timeliness of transactions in the face of malfunctions, system interruption and transmission failures or delays. The SO and/or SI of the designated RPS must also have in place a reasonable, effective, well-documented and regularly-tested business contingency plan addressing system functionality in the event of unforeseen interruption.
- The SO and/or SI of the designated RPS must have a thorough due diligence and management oversight process for managing its outsourcing relationships, if any, that it considers may impact the operation of its payment activities and services. The liabilities and responsibilities between the SO and/or SI of the designated RPS and its outsourcing service providers must be clearly defined.
- The SO and/or SI of the designated RPS must design its technical system for payment activities and services with sufficient capacity to enable its ongoing operations, which should be monitored periodically and upgraded on a periodic basis.
- The SO and/or SI of the designated RPS must have sufficient clearing and settlement arrangements to enable efficient, reliable and secure operation of the RPS.
- The SO and/or SI of the designated RPS must review periodically its security objectives, policies and operational services.
- The SO and/or SI of the designated RPS must develop well-defined procedures to respond to payment activity or service security-related incidents. The procedures should encompass a consistent and systematic approach in handling an incident.
- As a follow-up to each security-related incident materially affecting the Participant Persons, the SO and/or SI of the designated RPS should initiate a confidential post-incident assessment of the situation by the parties it considers appropriate having regard to the nature and the root cause of the incident, weaknesses leading to the incident and other potentially vulnerabilities underlying the incident.
Safety
- The SO and/or SI of the designated RPS must adopt appropriate and commercially reasonable technical security measures and procedural safeguards to protect the security of its system. The SO and/or SI of the designated RPS should also consider adopting international technical security standards where appropriate.
- The required measures must include the building and maintenance of a secure network, including conditions to install and maintain firewalls to protect data, and a change of vendor-supplied default system passwords and other security passwords.
- The implemented measures must protect data through the entire life cycle of a transaction, particularly on control measures to access data, procedures for storing Participant Persons’ transaction data, and disposal of Participant Persons’ transaction information after use.
- The designated RPS must use and regularly update anti-virus software to maintain secure systems and applications, and take proper measures to manage cyber security risk effectively, including the capability to keep pace with the trends of cyber attacks.
- In addition, the SO and/or SI of the designated RPS must have mechanisms which enable them to monitor on an ongoing basis attempted security breaches that may compromise its systems and data. There should be measures to control access and to regularly monitor and test the operation networks. There must be a policy that addresses information security for all related parties, such as employees and contractors.
- The SO and/or SI of the designated RPS must conduct periodic security reviews of its system. Such reviews could be performed either by the SO and/or SI of the designated RPS or, at its (or the Central Bank’s) discretion, by an independent party appointed by it.
Data Security and Integrity
- The SO and/or SI of the designated RPS are responsible for the security and integrity of all payment data and records maintained or controlled by it. The SO and/or SI of the designated RPS should ensure that the Participant Persons have, rules and procedures to safeguard the necessary confidentiality of all data and records in its control, including customer and transaction information. The SO and/or SI of the designated RPS should adopt generally accepted industry and international data security standards that it considers to be applicable to its operations.
- The SO and/or SI of the designated RPS must establish and maintain policies and procedures for the recovery of transaction data that is necessary for its daily operation in the event of system failure.
Incident Reporting
- The SO and/or SI of the designated RPS must report to the Central Bank of any incident (such as data security breaches) that may have a material and adverse impact on its operation or other Systematically Important Payment Systems in the State.
- Where action has been taken under Default Arrangements of a designated RPS by the SO and/or SI in respect of a Participant Person in the RPS, the Central Bank may direct the SO and/or SI of a designated RPS to give information relating to the default to any official nominated by the Central Bank. The nominated official is responsible for assessing and examining any matter arising out of or connected with the default of the Participant Person in that RPS. The liabilities of Participant Persons for any loss arising from the default of the Participant Person and the arrangements to handle any disputes over Participant Persons’ liability with respect to default transactions should be clearly set out in the rules and procedures.
- The SO and/or SI of a designated RPS, are required to ensure compliance with the following:
Article (9): Compliance with Principles of Financial Market Infrastructures Requirements
- The Committee on Payment and Market Infrastructures (CPMI) and the Technical Committee of the International Organization of Securities Commissions (IOSCO) have set forth a set of PFMI. PFMI aims to assist central banks, market regulators, and other relevant authorities in enhancing safety and efficiency in payment, clearing, settlement, and recording arrangements, and more broadly, limiting systemic risk and fostering transparency and financial stability. (details of PFMI are available in the two websites: www.bis.org and www.iosco.org).
- Another objective of PFMI is to harmonize and, where appropriate, strengthen the existing international standards and risk management practice for Financial Infrastructure Systems such as RPS that are systemically important.
- A poorly designed and operated systemically important RPS can contribute to and exacerbate systemic crises if the risks of the RPS are not adequately managed. The financial shocks, as a result, could be passed from one Participant Person to another Participant Person as well as a separate Systematically Important Payment System. The effects of such a disruption could extend well beyond the RPS and their Participant Persons, threatening the stability of domestic financial markets and the broader economy.
- Against this backdrop, the SI and/or SO should robustly manage the risks of their systematically important RPS to ensure its safety and promote financial stability. In addition, a systemically important RPS should not only be safe, but also efficient. Efficiency refers generally to the use of resources by SO and/or SI and their Participant Persons in performing their functions. Safe and efficient systemically important RPS contributes to well-functioning financial markets and economy.
- The Central Bank requires any designated RPS to observe and comply with the relevant principles in the PFMI, in addition to the compliance with the ongoing requirements set out in Article (8) of this Regulation. Moreover, the Central Bank may consider imposing higher requirements than PFMI for the designated RPS either on the basis of specific risks posed by the RPS or as a general policy.
- The SO and/or SI must apply the relevant principles on an ongoing basis in the operation of their RPS and business, including when reviewing their own performance, assessing or proposing new services, or proposing changes to risk controls.
- In aligning this regulation with leading international practice, RPS must comply with the relevant principles set out in the following paragraphs.
- Principle 1: Legal basis – a systemically important RPS must have a well-founded, clear, transparent, with a high degree of legal certainty, and an enforceable legal framework for each material aspect of its activities.
- Principle 2: Governance – a systemically important RPS must have governance arrangements that are clear and transparent, promote the safety and efficiency of the RPS, and support the stability of the broader financial system, other relevant public interest considerations, and the objectives of relevant stakeholders.
- Principle 3: Framework for the comprehensive management of risks – a systemically important RPS must have a sound risk management framework for comprehensively managing legal, credit, liquidity, operational, and other risks.
- Principle 4: Credit risk – a systemically important RPS must effectively measure, monitor, and manage its credit exposures to Participant Persons and those arising from its payment, clearing and settlement processes. The systematically important RPS must maintain sufficient financial resources to cover its credit exposures to each Participant Person fully with a high degree of confidence.
- Principle 5: Collateral – a systemically important RPS that requires collateral to manage its or its Participant Persons’ credit exposure should accept collateral with low credit, liquidity, and market risks. A systematically important RPS should also set and enforce appropriately conservative haircuts and concentration limits.
- Principle 6: Liquidity risk – a systemically important RPS must effectively measure, monitor, and manage its liquidity risk. A systemically important RPS should maintain sufficient liquid resources in all relevant currencies to effect same-day and, where appropriate, intraday and multiday settlement of payment obligations with a high degree of confidence under a wide range of potential stress scenarios that should include, but not be limited to, the default of the Participant Person and its affiliates that would generate the largest aggregate liquidity obligation for the systemically important RPS in extreme but plausible market conditions.
- Principle 7: Money settlement – a systemically important RPS should conduct its money settlements in central bank money where practical and available. If central bank money is not used, a systemically important RPS should minimize and strictly control the credit and liquidity risk arising from the use of commercial bank money.
- Principle 8: Participant-default rules and procedures – a systemically important RPS must have effective and clearly defined rules and procedures to manage a Participant Person default. These rules and procedures should be designed to ensure that the systemically important RPS can take timely action to contain losses and liquidity pressures and continue to meet its obligations.
- Principle 9: General business risk – a systemically important RPS must identify, monitor, and manage its general business risk and hold sufficient liquid net assets funded by equity to cover potential general business losses so that it can continue operations and services as a going concern if those losses materialize. Further, liquid net assets should at all times be sufficient to ensure a recovery or orderly wind-down of critical operations and services.
- Principle 10: Operational risk – a systemically important RPS must identify the plausible sources of operational risk, both internal and external, and mitigate their impact through the use of appropriate systems, policies, procedures, and controls. Systemically important RPS should be designed to ensure a high degree of security and operational reliability and should have adequate, scalable capacity. Business continuity management should aim for timely recovery of operations and fulfilment of the systemically important RPS’s obligations, including in the event of a wide-scale or major disruption.
- Principle 11: Access and participation requirements – a systemically important RPS should have objective, risk-based, and publicly disclosed criteria for participation, which permit fair and open access.
- Principle 12: Tiered participation arrangements – a systemically important RPS should identify, monitor, and manage the material risks to the systemically important RPS arising from tiered participation arrangements.
- Principle 13: Financial market infrastructure links – a systemically important RPS that establishes a link with one or more FMIs should identify, monitor, and manage link-related risks.
- Principle 14: Efficiency and effectiveness – a systemically important RPS should be efficient and effective in meeting the requirements of its Participant Persons and the markets it serves.
- Principle 15: Communication procedures and standards – a systemically important RPS should use, or at a minimum accommodate, relevant internationally accepted communication procedures and standards in order to facilitate efficient payment, clearing, settlement, and recording.
- Principle 16: Disclosure of rules, key procedures, and market data – a systemically important RPS must have clear and comprehensive rules and procedures and must provide sufficient information to enable Participant Persons to have an accurate understanding of the risks, fees, and other material costs they incur by participating in the systemically important RPS. All relevant rules and key procedures should be adequately disclosed.
- The Committee on Payment and Market Infrastructures (CPMI) and the Technical Committee of the International Organization of Securities Commissions (IOSCO) have set forth a set of PFMI. PFMI aims to assist central banks, market regulators, and other relevant authorities in enhancing safety and efficiency in payment, clearing, settlement, and recording arrangements, and more broadly, limiting systemic risk and fostering transparency and financial stability. (details of PFMI are available in the two websites: www.bis.org and www.iosco.org).
Article (10): Enforcement and Sanctions
1. Violation of any provision of this Regulation or committing any of the violations provided for under the Central Bank Law may subject SI and/or SO to administrative and financial sanctions and penalties as deemed appropriate by the Central Bank.
Article (11): Appeal Mechanism
- For the purposes of this Regulation, the relevant Central Bank’s decisions that may be subject to appeal before the Grievances & Appeals Committee include: -
- 1.1. licensing and designation of RPS;
- 1.2. revocation of License and designation of RPS; and
- 1.3. any Central Bank’s actions undertaken against a violating Person.
- 1.1. licensing and designation of RPS;
- Under the Regulation, any Person aggrieved by any of the decisions set out in paragraph 1 of this Article may refer the decision to the Grievances & Appeals Committee in writing for review.
- Any person who intends to refer any of the relevant decisions of the Central Bank to the Grievances & Appeals Committee is required to do so in writing to the Central Bank stating the grounds on which the review is sought.
- For the purposes of this Regulation, the relevant Central Bank’s decisions that may be subject to appeal before the Grievances & Appeals Committee include: -
Article (12): Transition Period
1. A one-year transitional period will commence on the date the Regulation comes into force. System Operators and Settlement Institutions of existing RPS operating in the State may continue operating throughout the transitional period without being regarded as contravening this Regulation. Nevertheless, they are required to obtain a license from the Central Bank to operate their RPS before the expiration of the transition period.
2. If the Central Bank considers that a Financial Infrastructure System fulfills the criteria for designation as provided for under the Central Bank Law, the Central Bank shall have the power to require any such system to obtain a license within a reasonable period to be determined by the Central Bank prior to the expiration of the transition period.
Article (13): Interpretation of Regulation
1. The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
Article (14): Publication & Application
1. This Regulation shall be published in the Official Gazette in both Arabic and English and shall come into effect one month from the date of publication. In case of any discrepancy between the Arabic and the English, the Arabic version will prevail.
Annex A
Information or documents that may be requested for licensing of RPS operating in the State under this Regulation
- Name of clearing and settlement system to which the designated RPS relates.
- Name of SO / SI.
- Legal form (body corporate, partnership, etc.).
- Country of incorporation or formation.
- Date of incorporation or formation.
- Registered office.
- Principal place of business.
- Contact details (names, physical and email addresses).
- Aspects of the management or operations of the system for which the entity is responsible.
- Organization chart of your company.
- A copy of the Operating Rules of the Payment System.
- Details of the type of activities and/or services offered by the RPS.
- Details of the constitution, structure, nature of business, ownership and management of the RPS, the SO and the SI.
- Details of the design and function and external system interfaces of the RPS, including details specifying the point at which a Transfer Order takes effect as having been entered into the RPS and of the point after which a Transfer Order may not be revoked by a Participant Person or any other party.
- A copy of the last three annual reports, if any, and the financial statements (with any auditor’s reports) for the current financial year of the RPS, the SO and/or the SI.
- The basis for membership of or participation in the RPS System (i.e. admission criteria) and a list of the current members of or Participant Persons in the RPS.
- Tariff information and schedule.
- Names of the SO and/or SI, if any, of the RPS and whether the SO and/or SI are also Participant Persons in the RPS under the Operating Rules of the System. Legal contracts or documents between the SO and/or the SI in relation to the RPS (for instance, documents which show the co-operation between the SO and/or SI, such as MoUs between them on data security, and the functional specifications of the linkages between the computer systems and networks between them that makes the system works.).
- Name and contact details of the Person to whom questions relating to the designation of the RPS should be directed.
- Name of clearing and settlement system to which the designated RPS relates.
Annex B
Information or documents that may be requested under this Regulation
- A copy of the Operating Rules of the Payment System.
- Details of the type of activities and/or services offered by the RPS.
- Details of the constitution, structure, nature of business, ownership and management of the RPS, the SO and the SI.
- Details of the design and function and external system interfaces of the RPS, including details specifying the point at which a Transfer Order takes effect as having been entered into the RPS and of the point after which a Transfer Order may not be revoked by a Participant Person or any other party.
- A copy of the last three annual reports, if any, and the financial statements (with any auditor’s reports) for the current financial year of the RPS, the SO and/or the SI.
- The basis for membership of or participation in the RPS System (i.e. admission criteria) and a list of the current members of or Participant Persons in the RPS.
- Tariff information and schedule.
- Names of the SO and/or SI, if any, of the RPS and whether the SO and/or SI are also Participant Persons in the RPS under the Operating Rules of the System. Legal contracts or documents between the SO and/or the SI in relation to the RPS (for instance, documents which show the co-operation between the SO and/or SI, such as MoUs between them on data security, and the functional specifications of the linkages between the computer systems and networks between them that makes the system works.).
- Details of the types, volume and values of Transfer Orders processed by the RPS.
- Detailed business contingency plan.
- Name and contact details of the Person to whom questions relating to the designation of the RPS should be directed.
For overseas systems, the following additional information may be required: -
- Name of each of the relevant regulators where the RPS is regulated by one or more regulatory authorities not within the State jurisdiction.
- An outline of any laws and other regulatory requirements relating to the operations of the RPS, if regulated by a regulatory authority not within the State jurisdiction.
- Evidence of the RPS’ compliance with any applicable laws and regulatory requirements of a jurisdiction outside State, which may include comments from home supervisory authority on the RPS’s compliance with any applicable laws and regulatory requirements of a jurisdiction outside State.
- A copy of the Operating Rules of the Payment System.
Retail Payment Services and Card Schemes Regulation
C 15/2021 Effective from 6/6/2021Large Value Payment Systems Regulation
C 9/2020 Effective from 10/2/2021Introduction
The Regulation (‘RPSCS Regulation’) lays down the rules and conditions established by the Central Bank for granting a License for the provision of Retail Payment Services. The Retail Payment Services are digital payment services in the State and comprise nine categories, namely Payment Account Issuance Services, Payment Instrument Issuance Services, Merchant Acquiring Services, Payment Aggregation Services, Domestic and Cross-border Fund Transfer Services, Payment Token Services, Payment Initiation Services and Payment Account Information Services. It also requires Card Schemes to obtain a License from the Central Bank and sets out the conditions for granting such License as well as the ongoing obligations of Card Schemes. The Central Bank has furthermore been given the right to receive information on the fees and charges of Card Schemes, and regulate such fees and charges if the Central Bank considers it appropriate. In addition, proper contractual arrangements are required between Banks or other Payment Service Providers providing Payment Account Issuance Services, on one hand, and Payment Service Providers providing Payment Initiation and Payment Account Information Services, on the other hand. Payment Service Providers wishing to participate in wages distribution and be given access to the Wages Protection System are subject to a set of on-going requirements.
The Central Bank Law requires providing money transfer services, electronic retail payments, and digital money services to be subject to a licensing regime administered by the Central Bank and provides the statutory basis for the powers of the Central Bank in relation to the licensing and ongoing supervision of Payment Service Providers and Card Schemes.
Introduction
Robust Financial Infrastructure Systems are essential to monetary and financial stability, the smooth and efficient operation of the financial system, and the effectiveness of international financial centers. Against this backdrop, the policy objective of the Central Bank is to promote and ensure the safety and efficiency of Financial Infrastructure Systems in the UAE. For the purpose of this Regulation, the regulatory focus is on Large-value Payment Systems (LVPS) which are Financial Infrastructure Systems that support the financial and wholesale activities in the State.
The Regulation covers the licensing requirements in relation to LVPS as well as the obligations and ongoing requirements in relation to a designated LVPS.
The Central Bank Law expressly sets out the powers of the Central Bank in relation to the licensing, designation, oversight and enforcement of Financial Infrastructure Systems that are systemically important, including LVPS.
The Central Bank Law also considers finality of payment and settlement to all transactions conducted through Financial Infrastructure Systems, that meet one of the designation conditions provided for in Article (126) (2) of the Central Bank Law.
Scope and Objectives
This Regulation sets out the requirements concerning:
- conditions for granting and maintaining a License for the provision of Retail Payment Services;
- rights and obligations of Retail Payment Service Users and Payment Service Providers;
- proper contractual arrangements allowing Payment Service Providers providing Payment Initiation and Payment Account Information Services to access Payment Accounts held with Banks and other Payment Service Providers providing Payment Account Issuance Services;
- conditions for granting a License to Card Schemes;
- conditions for participating and obtaining an access to the Wages Protection System;
- powers of the Central Bank with regard to the supervision of Payment Service Providers and the on-going reporting requirements for Card Schemes.
In exercising its powers and functions under this Regulation, the Central Bank has regard to the following objectives:
- ensuring the safety, soundness and efficiency of Retail Payment Services;
- adoption of effective and risk-based licensing requirements for Payment Service Providers;
- promoting the reliability and efficiency of Card Schemes as well as public confidence in Card-based Payment Transactions;
- promoting innovation and creating a level playing field for market participants; and
- reinforcing the UAE’s status as a leading payment hub in the region.
- conditions for granting and maintaining a License for the provision of Retail Payment Services;
Objectives and Scope
The objective of this Regulation is to ensure safety and efficiency of Financial Infrastructure Systems in the UAE and promote efficient and smooth operations thereof.
This Regulation applies to LVPS that are operated in the State, or accept the clearing or settlement of Transfer Orders denominated in the Currency both in the State or outside the State, in compliance with the provisions of the Central Bank Law, including Article 28 thereof. With respect to designated LVPS, this Regulation also requires compliance with the relevant provisions of the PFMI relating to the obligations of central banks, market regulators and relevant authorities for financial market infrastructures to cooperate with each other, domestically and internationally, as appropriate, in order to promote the safety and efficiency of financial market infrastructures.
The provisions of this Regulation shall not apply to Financial Free Zones and to LVPS operating therein unless when expressly provided hereunder
Exclusions
This Regulation shall not apply to the following:
- Payment Transactions involving Stored Value Facilities;
- Transactions involving Commodity or Security Tokens;
- Transactions involving Virtual Asset Tokens;
- Payment Transactions involving Remittances;
- Currency exchange operations where the funds are not held on a Payment Account;
- Any service other than Payment Initiation and Payment Account Information Service, including (but not limited to) any of the following:
- 6.1. services, provided by any technical service provider that supports the provision of any payment service, but does not at any time enter into possession of any money under that payment service;
- 6.2. the service of processing or storing data;
- 6.3. any information technology security, trust or privacy protection service;
- 6.4. any data or entity authentication service;
- 6.5. any information technology service;
- 6.6. the service of providing a communication network; and
- 6.7. the service of providing and maintaining any terminal or device used for any payment service.
- 6.1. services, provided by any technical service provider that supports the provision of any payment service, but does not at any time enter into possession of any money under that payment service;
- Payment Transactions carried out within a payment system or securities settlement system between Payment Service Providers and settlement agents, central counterparties, clearing houses, central banks or other participants in such system including central securities depositories;
- Payment Transactions and related services between a parent undertaking and its subsidiary or between subsidiaries of the same parent undertaking, without any intermediary intervention by a Payment Service Provider other than an undertaking belonging to the same group; and
- Any other relevant activity that may be designated by the Central Bank.
- Payment Transactions involving Stored Value Facilities;
Article (1): Definitions
- Central Bank: means the Central Bank of the United Arab Emirates.
- Central Bank Law: means Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities and its amendments from time to time.
- Clearing: means the process of transmitting, reconciling and, in some cases, confirming transactions prior to settlement, potentially including the Netting of transactions and the establishment of final positions for settlement.
- Clearing and Settlement System: means a system established for (a) the clearing or settlement of payment obligations; or (b) the clearing or settlement of obligations for the transfer of book-entry securities, or the transfer of such securities.
- Currency: means the State’s official national currency notes and coins, which unit is referred to as the “Dirham”.
- Default Arrangements: in respect of a Financial Infrastructure System, means the arrangements in place within the system for limiting systemic and other types of risk in the event of a Participant Person appearing to be, or likely to become, unable to meet his obligations in respect of a Transfer Order; and would include any arrangements that have been enforced by the System Operator or Settlement Institution for the following: (1) the Netting of obligations owed to or by a Participant Person; (2) the closing out of open financial position of a Participant Person; or (3) the realization of collateral securities to secure payment of obligations owed by the Participant Person.
- Designated System: means any Financial Infrastructure System designated by the Central Bank as systemically important, in accordance with the provisions of the Central Bank Law and this Regulation.
- Financial Free Zones (FFZ): means free zones subject to the provisions of Federal Law No 8 of 2004, regarding Financial Free Zones, and amending laws.
- Financial Infrastructure System: means either (1) a Clearing and Settlement System or (2) a Retail Payment System, established, operated, licensed, or overseen by any of the Regulatory Authorities in the State.
- Grievances & Appeals Committee: means the Committee referred to in Article (136) of the Central Bank Law.
- Large-value Payment System (LVPS): means a Clearing and Settlement System that is designed primarily to process large-value and/or wholesale payments typically among financial market participants (so-called wholesale payments) or involving money market, foreign exchange or many commercial transactions, excluding bilateral clearing and settlement arrangements and relationships which do not constitute a “system”.
- License: means a License issued by the Central Bank to an SO and/or SI to operate an LVPS in the State. The License shall be valid for a period of five years, unless it is suspended or revoked by the Central Bank.
- Netting: in respect of a Clearing and Settlement System, means the conversion of the various obligations owed to or by a Participant Person towards all the other Participant Persons in the system, into one net obligation owed to or by the Participant Person.
- Operating Rules: means rules set up by the System Operator to cover the operation of a Financial Infrastructure System including, but not limited to, Participant Person account opening and maintenance, contractual relationships with and among Participant Persons, Default Arrangements, payment and settlement processing, Netting and collateral arrangements, authorization and post-transaction processes.
- Participant Person: in respect of a Financial Infrastructure System, means a Person who is party to or participant of the arrangements for which the system has been established.
- Person: means a natural or juridical person, as the case may be.
- Principles of Financial Market Infrastructures (PFMI): means the international standards for financial market infrastructures (i.e. payment systems, central securities depositories, securities settlement systems, central counterparties and trade repositories) issued by the Committee on Payments and Market Infrastructures (CPMI) and the International Organization of Securities Commissions (IOSCO). The PFMI are part of a set of 12 key standards that the international community considers essential to strengthening and preserving financial stability.
- Regulation: means the Large-value Payment Systems Regulation.
- Regulatory Authorities: means the Central Bank and the Securities & Commodities Authority.
- Retail Payment System: means any fund transfer system and related instruments, mechanism, and arrangements that typically handles a large volume of relatively low-value payments in such forms as cheques, credit transfers, direct debit, or card payment transactions.
- Settlement Institution (SI): means an institution that provides settlement services to a Financial Infrastructure System, settlement accounts in one currency or multi-currency in the Financial Infrastructure System and in certain cases, grants access to intraday liquidity to Participant Persons.
- State: means the United Arab Emirates.
- System Operator (SO): means a Person responsible for the operation of a Financial Infrastructure System including the comprehensive management of all risks in the Financial Infrastructure System, and ensuring that the operation of the system is in accordance with this Regulation and other relevant regulations issued by the Central Bank.
- Systemically Important Financial Infrastructure System: a Financial Infrastructure System which has the potential to trigger or transmit systemic disruptions to the State’s monetary and financial stability; this includes, among other things, systems that are the sole Financial Infrastructure System in a jurisdiction or the principal system in terms of the aggregate value of payments, and systems that mainly handle time-critical, high-value payments or settle payments used to effect settlement in other Financial Infrastructure Systems.
- Transfer Order: in respect of a Financial Infrastructure System, means any of the following instructions: (1) instructions by a Participant Person to make funds available to another Participant Person to be transferred, on a book-entry basis, in the accounts of the SI for a Clearing and Settlement System; or (2) instructions for discharge from obligation to pay, for the purposes of the Operating Rules of a Clearing and Settlement Systems; or (3) instructions by a Participant Person to either settle an obligation by transferring a book-entry security, or transferring those securities; or (4) instructions by a Participant Person that result in liability or discharge of retail operations payment obligation.
- Central Bank: means the Central Bank of the United Arab Emirates.
Article (1): Definitions
- Agent: means a juridical Person providing Retail Payment Services on behalf of a Payment Service Provider.
- AML/CFT: means Anti-Money Laundering and Combating the Financing of Terrorism.
- AML Law: means Decree Federal Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations and Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Federal Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations, as may be amended from time to time, and any instructions, guidelines and notices issued by the Central Bank relating to their implementation or issued in this regard.
- Annex I: means the list of Retail Payment Services that a Payment Service Provider may provide subject to the requirements of this Regulation.
- Annex II: means the Guidance on the best practices for technology risk and information security.
- Annex III: means the minimum level of information to be reported by Card Schemes to the Central Bank.
- Applicant: means a juridical Person duly incorporated in the State in accordance with Federal Law No. 2 of 2015 on Commercial Companies and as provided for under Article (74) of the Central Bank Law, which files an Application with the Central Bank for the granting of a License for the provision of one or more Retail Payment Services, operation of a Card Scheme or the modification of the scope of a granted License.
- Application: means a written request for obtaining a License for the provision of one or more Retail Payment Services submitted by an Applicant which contains the information and documents specified in this Regulation or by the Central Bank, and is in the form specified by the Central Bank’s Licensing Division, including a written request for obtaining a modification to the scope of a granted License.
- Auditor: means an independent juridical Person that has been appointed to audit the accounts and financial statements of a Payment Service Provider in accordance with Article (10) (7).
- Bank: any juridical person licensed in accordance with the provisions of the Central Bank Law, to primarily carry on the activity of taking deposits, and any other Licensed Financial Activities.
- Beneficial Owner: means the natural person who owns or exercises effective ultimate control, directly or indirectly, over a Retail Payment Service User (client) or the natural person on whose behalf a transaction is being conducted or, the natural person who exercises effective ultimate control over a legal person or legal arrangement.
- Branded: means having any digital name, term, sign, logo, symbol or combination thereof that is capable of differentiating the Card Scheme under which Payment Transactions are executed.
- Board: means the board of directors of an Applicant, Payment Service Provider or a Card Scheme in accordance with applicable corporate law.
- Business Day: means a day other than Friday, Saturday, public holiday or other non-working holiday or day in the State.
- Card-based Payment Transactions: means a service based on a Card Scheme's infrastructure and business rules to make Payment Transactions by means of any card, telecommunication, digital or IT device or software if this results in a debit or a credit card transaction.
- Card Issuer: means a category of Payment Service Provider providing a Payer with a Payment Instrument to initiate and process the Payer’s Card-based Payment Transactions.
- Cardholder: means a Person who holds a Payment Instrument, physical or otherwise, issued by a Card Issuer based on a contract for the provision of an electronic payment instrument.
- Card Scheme: means a single set of rules, practices and standards that enable a holder of a Payment Instrument to effect the execution of Card-based Payment Transactions within the State which is separated from any infrastructure of payment system that supports its operation, and includes the Card Scheme Governing Body. For the avoidance of doubt, a Card Scheme may be operated by a private or Public Sector Entity.
- Card Scheme License: means a License for operating as a Card Scheme, as referred to in Article (18).
- Card Scheme Governing Body: means the juridical Person responsible and/or accountable for the functioning and operation of a Card Scheme.
- Category I License: means a License for the provision of the Retail Payment Services referred to in Article (3) (2).
- Category II License means a License for the provision of the Retail Payment Services referred to in Article (3) (3).
- Category III License means a License for the provision of the Retail Payment Services referred to in Article (3) (4).
- Category IV License means a License for the provision of the Retail Payment Services referred to in Article (3) (5).
- Central Bank: means the Central Bank of the United Arab Emirates.
- Central Bank Law: means the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank and Organization of Financial Institutions and Services, as may be amended or substituted from time to time.
- Co-Branded: means having the inclusion of at least one payment brand and one non-payment brand on the same Payment Instrument.
- Controller: means a natural or juridical Person that alone or together with the Person’s associates has an interest in at least 20% of the shares in a Payment Service Providers or is in a position to control at least 20% of the votes in a Payment Service Provider.
- Commodity Token: means a type of Crypto-Asset that grants its holder an access to a current or prospective product or service, and is only accepted by the issuer of that token. Commodity token can also be referred to as utility token
- Complaint: Means an expression of dissatisfaction by a consumer with a product, service, policy, procedure or actions by the licensed financial institution that is presented to an Employee of the licensed financial institution in writing or verbally.
- Cross-Border Fund Transfer Service: means a Retail Payment Service for the transfer of funds in which the Payment Service Providers of the Payer and the Payee are located in different jurisdictions/countries.
- Crypto-Assets: means cryptographically secured digital representations of value or contractual rights that use a form of Distributed Ledger Technology and can be transferred, stored or traded electronically.
- Customer Due Diligence or CDD: means the process of identifying or verifying the information of a Retail Payment Service User or Beneficial Owner, whether a natural or legal person or a legal arrangement, and the nature of its activity and the purpose of the business relationship and the ownership structure and control over it.
- Custodian Services: means the safekeeping or controlling, on behalf of third parties, of Payment Tokens, the means of access to such tokens, where applicable in the form of private cryptographic keys.
- Data Breach: means an intrusion into an IT system where unauthorized disclosure or theft, modification or destruction of Cardholder or Retail Payment Service User data is suspected and such is likely to result in a loss for the Cardholder or Retail Payment Service User.
- Data Subject: means an identified or identifiable natural Person who is the subject of Personal Data.
- Digital Money Services: means, for the purposes of this Regulation, the business activity related to the provision of Payment Token Services.
- Distributed Ledger Technology: means a class of technologies that supports the distributed recording of encrypted data across a network and which is a type of decentralized database of which there are multiple identical copies distributed among multiple participants and accessible across different sites and locations, and which are updated in a synchronized manner by consensus of the participants, eliminating the need for a central authority or intermediary to process, validate or authenticate transactions or other types of data exchanges.
- Domestic Fund Transfer Service: means the Retail Payment Service of accepting money for the purpose of executing, or arranging for the execution of Payment Transactions between a Payer in the State and a Payee in the State.
- Electronic Payment Service: means any and each of the Retail Payment Services listed in points (1) to (4) and (8) to (9) of Annex I.
- Employer: means a Person using the Wages Protection System for the payment of wages.
- Exchange House: means an exchange business that has been licensed under the Regulations re Licensing and Monitoring of Exchange Business.
- Exempted Person: means any Person who is exempted from the requirement to hold a License as per Article (2) of this Regulation.
- Facilitating the Exchange of Payment Tokens: means a Retail Payment Service related to establishing or operating a Payment Token exchange, in a case where the person that establishes or operates that exchange, for the purposes of an offer or invitation made or to be made on that Payment Token exchange, to buy or sell any Payment Token in exchange for Fiat Currency or Payment Token, whether of the same or a different type, comes into possession of any Fiat Currency or Payment Token, whether at the time that offer or invitation is made or otherwise.
- FATF: an inter-government body which sets international standards that aim to prevent global money laundering and terrorist financing activities.
- Fiat Currency: means a currency that is controlled by the respective central bank, has the status of legal tender and is required to be accepted within a given jurisdiction.
- Financial Free Zones: means free zones subject to the provisions of Federal Law No (8) of 2004, regarding Financial Free Zones, as may be amended or supplemented from time to time.
- Four Party Card Scheme: means a Card Scheme in which Card-based Payment Transactions are made from the payment account of a Payer to the payment account of a payee through the intermediation of the scheme, an issuer (on the payer’s side) and an acquirer (on the Payee’s side).
- Framework Agreement: means a payment service agreement for the provision of Retail Payment Services which governs the future execution of individual and successive Payment Transactions and which may contain the terms and conditions for opening a Payment Account.
- Group: means a corporate group which consists of a parent entity and its subsidiaries, and the entities in which the parent entity or its subsidiaries hold, directly or indirectly, 5% or more of the shares, or are otherwise linked by a joint venture relationship.
- Legal Form: means the legal form of Applicants established in accordance with Article (74) of the Central Bank Law.
- Level 2 Acts: means any written act that may be adopted or issued by the Central Bank complementing the implementation of this Regulation, such as, without being limited to, rules, directives, decisions, instructions, notices, circulars, standards, and rulebooks.
- License: means a License issued by the Central Bank to an Applicant to provide Retail Payment Services or operate a Card Scheme in the State. The License is valid unless it is withdrawn, suspended or revoked by the Central Bank.
- Licensed Financial Activities: means the financial activities subject to Central Bank licensing and supervision, which are specified in Article (65) of the Central Bank Law.
- Major Regulatory Requirement: means any requirement of this Regulation or Level 2 Acts the violation of which is capable of compromising and/or negatively affecting the attainment of the Central Bank’s objectives pursued under this Regulation, as determined at the discretion of the Central Bank.
- Management: means the Applicant, Payment Service Provider, Agent and Card Scheme’s senior officers that are involved in the daily management, supervision and control of the business services of the entity, typically including the chief executive officer, his or her alternate(s) and each person directly reporting to that officer. The chief executive officer and his or her alternate(s) shall be a natural person who are ordinarily residing in the State whereas the remaining members of Management shall be based in the State unless the Central Bank allows otherwise.
- Means of Distance Communication: means a method which may be used for the conclusion of a payment services agreement without the simultaneous physical presence of the Payment Service Provider and the Retail Payment Service User.
- Merchant: means a Person who accepts Payment Instruments as a mode of payment for the purchase and sale of goods and services.
- Merchant Acquirer: means a category of Payment Service Provider providing Merchant Acquiring Services.
- Merchant Acquiring Service: means a Retail Payment Service provided by a Payment Service Provider contracting with a Payee to accept and process Payment Transactions, which results in a transfer of funds to the Payee.
- Money Transfer Services: means the Domestic and Cross-border Fund Transfers Services, excluding Remittances.
- Money’s Worth: means value added onto an SVF by the customer; value received on the customer’s SVF account; and value redeemed by the customer including not only “money” in the primary sense but also other forms of monetary consideration or assets such as values, reward points, Crypto-Assets, or Virtual Assets. For example, a value top-up of an SVF account may take the form of values, reward points, Crypto-Assets, or Virtual Assets earned by the SVF customer from making purchases of goods and services. Similarly, value received on the account of the SVF customer may take the form of an on-line transfer of value, reward points, Crypto-Assets, or Virtual Assets between fellow SVF customers.
- Payment Account: means an account with a Payment Service Provider held in the name of at least one Retail Payment Service User which is used for the execution of Payment Transactions.
- Payment Account Information Service: means a Retail Payment Service to provide consolidated information on one or more Payment Accounts held by a Retail Payment Service User with either another Payment Service Provider or with more than one Payment Service Providers. For the avoidance of doubt, the Payment Account Information Service does not involve the holding of Retail Payment Service User’s funds at any time.
- Payment Account Issuance Service: means a Retail Payment Service, other than Domestic and Cross-border Fund Transfer Services, enabling (i) the opening of a Payment Account; (ii) cash to be placed on a Payment Account; (iii) cash to be withdrawn from a Payment Account; and (iv) all necessary operations for operating a Payment Account. The Payment Account is only used for holding fund/cash in transit and not allowed to store and maintain fund/cash.
- Payment Aggregation Service: means a Retail Payment Service facilitating e-commerce websites and Merchants to accept various Payment Instruments from the Retail Payment Service Users for completion of their payment obligations without the need for Merchants to create a separate payment integration system of their own. Payment aggregation facilitates Merchants to connect with Merchant acquirers; in the process, they receive payments from Retail Payment Service Users, pool and transfer them on to the Merchants after a time period.
- Payment Data: means any information related to a Retail Payment Service User, including financial data and excluding Personal Data.
- Payment Initiation Service: means a Retail Payment Service to initiate a Payment Order at the request of the Retail Payment Service User with respect to a Payment Account held at another Payment Service Provider. For the avoidance of doubt, the Payment Initiation Service does not involve the holding and maintenance of Payer’s funds at any time.
- Payment Instrument: means a personalized device(s), a payment card and/or set of procedures agreed between the Retail Payment Service User and the Payment Service Provider, and used in order to initiate a Payment Order.
- Payment Instrument Issuance Service: means a Retail Payment Service related to the provision of a Payment Instrument to a Retail Payment Service User which enables it to initiate Payment Orders as well as the Processing of the Retail Payment Service User’s Payment Transactions.
- Payment Service Provider: means a legal Person that has been licensed in accordance with this Regulation to provide one or more Retail Payment Services and has been included in the Register as per Article (73) of the Central Bank Law.
- Payment Token Issuing: means a Retail Payment Service related to the issuing of Payment Tokens by a Payment Service Provider. For the avoidance of doubt, Payment Tokens may not be offered to the public or segments thereof unless the Payment Service Provider issuing the Payment Tokens has obtained a Category I License, drafted a White Paper in respect of those Payment Tokens and received an approval by the Central Bank prior to offering such tokens to the public.
- Payment Token: means a type of Crypto-Asset that is backed by one or more Fiat Currencies, can be digitally traded and functions as (i) a medium of exchange; and/or (ii) a unit of account; and/or (iii) a store of value, but does not have legal tender status in any jurisdiction. A Payment Token is neither issued nor guaranteed by any jurisdiction, and fulfils the above functions only by agreement within the community of users of the Payment Token. For the avoidance of doubt, a Payment Token does not represent any equity or debt claim.
- Payment Token Buying: means the buying of Payment Tokens in exchange for any Fiat Currency or Payment Token.
- Payment Token Selling: means the selling of Payment Tokens in exchange for any Fiat Currency or Payment Token.
- Payment Token Services: means the Retail Payment Services consisting of any of the following activities related to Payment Tokens: (i) Payment Token Issuing; (ii) Payment Token Buying; (iii) Payment Token Selling; (iv) Facilitating the Exchange of Payment Tokens; (v) enabling payments to Merchants and/or enabling peer-to-peer payments; and (vi) Custodian Services. For the avoidance of doubt, a Payment Service Provider may provide only one of the Retail Payment Services referred to in points (v) and (vi); if it wishes to provide both and allows Retail Payment Service Users to redeem the Payment Tokens with any Fiat Currency under a contractual arrangement, it must comply with the respective SVF requirements.
- Payment Transaction: means an act initiated by the Payer or on his behalf or by the Payee of placing, transferring or withdrawing funds, irrespective of any underlying obligations between the Payer and the Payee.
- Payee: means a Person who is the intended recipient of funds which have been the subject of a Payment Transaction.
- Payer: means a Person who holds a Payment Account and allows a Payment Order from that Payment Account, or, where there is no Payment Account, a Person who gives a Payment Order.
- Person means any natural or legal Person.
- Personal Data: means any information which are related to an identified or identifiable natural Person.
- Processing: means Payment Transaction processing necessary for the handling of an instruction, including clearing and settlement, between the Merchant Acquirer and the Card Issuer.
- Promotion: means any form of communication, by any means, aimed at inviting or offering to enter into an agreement related to any Retail Payment Service. For the avoidance of doubt, any Person that has been mandated to provide or engage in Promotion activities by a Person providing Retail Payment Services without holding a License shall not be held liable under this Regulation.
- Public Sector Entity: means the Federal Government, Governments of the Union’s member Emirates, public institutions and organizations.
- Register: means the Register referred to in Article (73) of the Central Bank Law.
- Regulation: means the Retail Payment Services and Card Schemes Regulation.
- Remittance: means the receipt of funds from a Payer without any Payment Accounts being created in the name of the Payer or the Payee.
- Reserve of Assets: means the pool of Fiat Currencies that are legal tender backing the value of a Payment Token.
- Retail Payment Service: means any business activity set out in Annex I.
- Retail Payment Service User: means a Person who intends to make use of or makes use of a Retail Payment Service in the capacity of a Payer, Payee or both.
- Sensitive Payment Data: means data, including personalized security credentials which can be used to carry out unauthorized activities. For the purposes of Payment Initiation and Payment Account Information Services, the name of the Payment Account owner and Payment Account number shall not constitute Sensitive Payment Data.
- Single Retail Payment Agreement: means an agreement which governs the execution of an individual Payment Transaction.
- State: means the United Arab Emirates.
- Security Token: means a type of Crypto-Asset that provides its holder with rights and obligations that represent a debt or equity claim against the issuer of that token.
- Stored Value Facility or SVF: means a facility (other than cash) for or in relation to which a Customer, or another person on the Customer’s behalf, pays a sum of money (including Money’s Worth such as values, reward points, Crypto-Assets or Virtual Assets) to the issuer, whether directly or indirectly, in exchange for: (a) the storage of the value of that money (including Money’s Worth such as values, reward points, Crypto-Assets or Virtual Assets), whether in whole or in part, on the facility; and (b) the “Relevant Undertaking”. SVF includes Device based Stored Value Facility and Non-device based Stored Value Facility.
- Third country: means a country other than the UAE.
- Three Party Card Scheme: means a Card Scheme in which the scheme itself provides Merchant Acquiring and Payment Instrument Issuing Services and Card-based Payment Transactions are made from the Payment Account of a Payer to the Payment Account of a Payee within the Card Scheme. When a Three Party Card Scheme licenses other Payment Service Providers for the issuance of Card-based Payment Instruments or the Merchant Acquiring of Card-based Payment Transactions, or both, or issues Card-based Payment Instruments with a co-branding partner or through an agent, it is considered to be a Four Party Card Scheme.
- UAE: means the United Arab Emirates.
- Unauthorized Payment Transaction: means a Payment Transaction for the execution of which the Payer has not given consent. Consent to execute a Payment Transaction or a series of Payment Transactions shall be given in the form agreed between the Payer and the Payment Service Provider. Consent to execute a Payment Transaction may also be given via the Payee or the Payment Initiation Service Provider.
- Virtual Assets: A Virtual Asset is a digital representation of value that can be digitally traded, or transferred, and can be used for payment or investment purposes. Virtual Assets do not include digital representations of Fiat Currencies, securities and other financial assets that are already covered elsewhere in the FATF Recommendations.
- Virtual Assets Service Providers: Virtual Asset Service Provider means any natural or legal person who is not covered elsewhere under the FATF Recommendations, and as a business conducts one or more of the following activities or operations for or on behalf of another natural or legal person: (i) exchange between Virtual Assets and Fiat Currencies; (ii) exchange between one or more forms of Virtual Assets; (iii) transfer of Virtual Assets; (iv.) safekeeping and/or administration of Virtual Assets or instruments enabling control over Virtual Assets; and (v) participation in and provision of financial services related to an issuer’s offer and/or sale of a Virtual Asset.
- Virtual Asset Token: means a type of Crypto-Asset that can be digitally traded and functions as (i) a unit of account; and/or (ii) a store of value. Although some Virtual Asset Tokens may be accepted as a means of payment, they are generally not accepted as a medium of exchange, may not have an issuer and do not have legal tender status in any jurisdiction. A Virtual Asset Token is neither issued nor guaranteed by any jurisdiction, and fulfils the above functions only by agreement within the community of users of the Virtual Asset Token. For the avoidance of doubt, a Virtual Asset Token does not represent any equity or debt claim, and it is not backed by any Fiat Currency.
- Virtual Asset Token Services: means any of the following services: (i) enabling peer-to-peer Virtual Asset Token transfers, and (ii) custodian services of Virtual Asset Tokens.
- Wages Protection System or WPS: means a reconciliation system implemented at the Central Bank aimed at providing a safe, secure, efficient and robust mechanism for streamlining the timely and efficient payment of wages.
- Wire Transfer: means any transaction carried out on behalf of an originator through a financial institution by electronic means with a view to making an amount of funds available to a beneficiary person at a beneficiary financial institution, irrespective of whether the originator and the beneficiary are the same person
- WPS Payment Account: means a WPS account opened in the infrastructure of the Central Bank and held for the purposes of holding and payment of wages.
- WPS Payment Account Holder: means a holder of a Payment Account held with a Payment Service Provider who has been given access to the Wages Protection System for the purpose of executing transfers of wages.
- White Paper: means a detailed description in Arabic and English of: (i) the Payment Service Provider issuing a Payment Token and a presentation of the main participants involved in the project’s design and development; (ii) a detailed description of the project and the type of Payment Token that will be offered to the public; (iii) the number of Payment Tokens that will be issued and the issue price; (iv) a detailed description of the rights and obligations attached to the Payment Token and the procedures and conditions for exercising those rights; (v) information on the underlying technology and standards applied by the Payment Service Provider issuing the Payment Token allowing for the holding, storing and transfer of those Payment Tokens; (vi) a detailed description of the risks relating to the Payment Service Provider issuing Payment Tokens, the Payment Tokens, the offer to the public and the implementation of the project, and other disclosures that the Central Bank may specify; (vii) detailed description of the Payment Service Provider’s governance arrangements, including a description of the role, responsibilities and accountability of the third-parties responsible for operating, investment and custody of the Reserve of Assets, and, where applicable, the distribution of the Payment Tokens; (viii) a detailed description of the Reserve of Assets; (ix) a detailed description of the custody arrangements for the Reserve of Assets, including the segregation of the assets; (x) in case of an investment of the Reserve of Assets, a detailed description of the investment policy; and (xi) information on the nature and enforceability of rights, including any direct redemption right or any claims that holders of Payment Tokens may have on the Reserve of Assets or against the Payment Service Provider issuing the Payment Tokens, including how such rights may be treated in insolvency procedures. For the avoidance of doubt, the White Paper shall be written in a simple, easy to understand and non-misleading language, and shall be dated. The White Paper shall be endorsed by the Payment Service Provider’s Management and published on the Payment Service Provider’s website after receipt of an approval by the Central Bank.
- Agent: means a juridical Person providing Retail Payment Services on behalf of a Payment Service Provider.
Article (2): Licensing Requirements
- As stipulated in Article (129) (1) (a) of the Central Bank Law, operating an LVPS in the State requires a prior License from the Central Bank.
- The SO and/or SI of the LVPS must apply and submit the required information and documents set out in Annex A of this Regulation to the Central Bank to obtain a License if the LVPS is in operation in the State.
- As stipulated in Article (129) (1) (a) of the Central Bank Law, operating an LVPS in the State requires a prior License from the Central Bank.
Article (2): Licensing
- No Person shall provide or engage in the Promotion within the State of any of the Retail Payment Services set out in Annex I without obtaining a prior License from the Central Bank unless this Person is an exempted Person.
Exempted Persons
- Banks licensed in accordance with the Central Bank Law shall be deemed licensed to provide Retail Payment Services and shall therefore be exempt from the prohibition laid down in paragraph (1). Nevertheless, Banks shall be required to notify the Central Bank in writing if they intend to provide the Retail Payment Services referred to in points (3) to (4) and (7) to (9) of Annex I and obtain a No Objection Letter prior to commencing the provision of such services. Banks are exempted from the No Objection Letter requirement and any licensing requirements for providing the Retail Payment Services referred to in points (1), (2), (5) and (6) of Annex I.
- For the avoidance of doubt, Banks providing Retail Payment Services other than the Retail Payment Services referred to in points (1), (2), (5) and (6) of Annex I, shall be required to comply only with the requirements set out in Article (11) on Payment Token Services, Article (12) on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations, Article (13) on Technology Risk and Information Security, and Article (14) on Obligations Towards Retail Payment Service Users.
- Finance companies licensed in accordance with the finance companies Regulation shall be exempt from the prohibition laid down in paragraph (1) for the service of issuance of credit cards. For the avoidance of doubt, except issuance of credit cards, finance companies that intend to provide Retail Payment Services shall be required to obtain a prior License from the Central Bank.
- The Central Bank may request from a Person or Exempted Person the provision of any information or documentation that it considers necessary to determine the eligibility for exemption or continued exemption, respectively.
- The Central Bank reserves the right to withdraw an exemption granted under this Article 2.
- No Person shall provide or engage in the Promotion within the State of any of the Retail Payment Services set out in Annex I without obtaining a prior License from the Central Bank unless this Person is an exempted Person.
Article (3): Eligibility and Criteria for Designation as Systemically Important Financial Infrastructure System
- As stipulated in Article (126) (2) of the Central Bank Law, if a licensed LVPS falls within the eligibility for designation as set out in the aforementioned Article, the Central Bank may designate such LVPS as systemically important.
- In forming an opinion as to whether an LVPS satisfies the designation criteria, the Central Bank may consider one or more of the following factors in order to determine whether or not the LVPS is a Systemically Important Financial Infrastructure System: -
- 2.1. The estimated aggregate value of Transfer Orders transferred, cleared or settled through the LVPS in a normal business day. This refers to the total value of individual instructions transferred, cleared or settled in the LVPS. It also represents the sum of total debits (or credits) to all accounts maintained by the system prior to or in the absence of any Netting of transactions in a normal business day. For established systems during the transition period, the estimated value can be worked out with reference to historical data and business plan.
- 2.2. The estimated average value of Transfer Orders transferred, cleared or settled through the LVPS in a normal business day. This refers to the aggregate value of instructions transferred, cleared or settled through the system in a normal business day, divided by the number of instructions processed.
- 2.3. The estimated number of Transfer Orders transferred, cleared or settled through the LVPS in a normal business day.
- 2.4. The estimated number and the type of Participant Persons of the LVPS.
- 2.5. Whether the LVPS is linked to any Designated Systems that are licensed or regulated by other Regulatory Authorities in the State.
- 2.1. The estimated aggregate value of Transfer Orders transferred, cleared or settled through the LVPS in a normal business day. This refers to the total value of individual instructions transferred, cleared or settled in the LVPS. It also represents the sum of total debits (or credits) to all accounts maintained by the system prior to or in the absence of any Netting of transactions in a normal business day. For established systems during the transition period, the estimated value can be worked out with reference to historical data and business plan.
- The above factors are intended to identify an LVPS whose proper functioning is material to the monetary or financial stability of the State or that should be designated, having regard to matters of significant public interest or public order. During the designation process, should the need arise, the Central Bank will discuss with the SO and/or SI of the relevant LVPS so as to understand the design and features of the system and assess whether it fulfills the criteria of a Systemically Important Financial Infrastructure System.
- As stipulated in Article (126) (2) of the Central Bank Law, if a licensed LVPS falls within the eligibility for designation as set out in the aforementioned Article, the Central Bank may designate such LVPS as systemically important.
Article (3): License Categories
- A Person that intends to provide Retail Payment Services shall apply for one of the following categories of License:
- 1.1. Category I License;
- 1.2. Category II License;
- 1.3. Category III License; and
- 1.4. Category IV License
- 1.1. Category I License;
- An Applicant shall apply for a Category I License where it intends to provide one or more of the following Retail Payment Services:
- 2.1. Payment Account Issuance Services;
- 2.2. Payment Instrument Issuance Services;
- 2.3. Merchant Acquiring Services;
- 2.4. Payment Aggregation Services;
- 2.5. Domestic Fund Transfer Services;
- 2.6. Cross-border Fund Transfer Services; and
- 2.7. Payment Token Services.
- 2.1. Payment Account Issuance Services;
- An Applicant shall apply for a Category II License where it intends to provide one or more of the following Retail Payment Services:
- 3.1. Payment Account Issuance Services;
- 3.2. Payment Instrument Issuance Services;
- 3.3. Merchant Acquiring Services;
- 3.4. Payment Aggregation Services;
- 3.5. Domestic Fund Transfer Services; and
- 3.6. Cross-border Fund Transfer Services.
- 3.1. Payment Account Issuance Services;
- An Applicant shall apply for a Category III License where it intends to provide one or more of the following Retail Payment Services:
- 4.1. Payment Account Issuance Services;
- 4.2. Payment Instrument Issuance Services;
- 4.3. Merchant Acquiring Services;
- 4.4. Payment Aggregation Services; and
- 4.5. Domestic Fund Transfer Services.
- 4.1. Payment Account Issuance Services;
- An Applicant shall apply for a Category IV License where it intends to provide one or all of the following Retail Payment Services:
- 5.1. Payment Initiation Services; and
- 5.2. Payment Account Information Services.
- 5.1. Payment Initiation Services; and
- A Person that intends to provide Retail Payment Services shall apply for one of the following categories of License:
Article (4): Designation Process
- The Central Bank will initiate the designation process under the designation framework as stipulated in Article (126) (3) of the Central Bank Law, if it considers an LVPS is meeting or is likely to meet the criteria for designation.
- For the Central Bank to determine whether an LVPS is eligible to be designated and whether it satisfies the designation criteria for the purposes of this Regulation, the Central Bank will request information or documents regarding the LVPS from any Person who is holding, or whom the Central Bank reasonably believes holds such information or documents, or from the SO or SI of the LVPS. This power to request for information or documents applies to LVPS, individuals or corporations established, located or incorporated in the State and/or outside the State. The Central Bank will coordinate with any competent Regulatory Authority or other competent authorities in other jurisdictions for the purpose of requesting and securing such information and documents.
- The nature of information or documents that the Central Bank may require might vary from LVPS to LVPS. Generally speaking, the Central Bank will seek to request information or documents as set out in the Annexes of this Regulation and may, where necessary, seek additional information as is required in order to assist the Central Bank in making such determination.
- During the designation process, the Central Bank may discuss with the SO and/or SI of such system where necessary to understand the features and the design of the system and determine the LVPS’s eligibility for designation.
- The time for the designation process may vary depending on the particular circumstances of each case, including the nature and complexity of the prospective designated LVPS and the completeness of the information and documents submitted to the Central Bank.
- The SO and/or SI of a Designated System licensed by the Central Bank may submit a grievance against the designation decision, issued by the Central Bank in accordance with Article (126) (3) of the Central Bank Law, by applying to the Grievances & Appeals Committee as set out in Article (11) of this Regulation.
- If the Central Bank intends to designate any of the LVPS licensed by any Regulatory Authority in the State or the competent regulatory authorities in other jurisdictions as systemically important, the Central Bank shall implement the process for designation as provided for under Article (126) (6) of the Central Bank Law.
LVPS deemed to have been licensed and designated
- As stipulated in Article (126) (5) of the Central Bank Law, the LVPS established, developed, and/or operated by the Central Bank are deemed to have been licensed and designated.
- The LVPS that are deemed to have been designated are required to observe all the obligations and oversight requirements imposed on designated LVPS under this Regulation in the same manner as other designated LVPS.
- The Central Bank will initiate the designation process under the designation framework as stipulated in Article (126) (3) of the Central Bank Law, if it considers an LVPS is meeting or is likely to meet the criteria for designation.
Article (4): License Conditions
- To be granted a License, an Applicant shall, at the time of submitting an Application:
- 1.1. fulfil the Legal Form;
- 1.2. meet the respective initial capital requirements per License Category specified in Article (6); and
- 1.3. provide the necessary documents and information specified in the Central Bank application form as provided by the Licensing Division.
- 1.1. fulfil the Legal Form;
- In addition to the requirements set out in paragraph (1) to be granted a Category I License, an Applicant shall, at the time of submitting an Application, provide a list of all Payment Tokens that it intends to issue and obtain a legal opinion on the assessment for all Payment Tokens.
- In addition to the requirements set out in paragraph (1), to be granted a Category IV License, an Applicant shall, at the time of submitting an Application, hold a professional indemnity insurance as per Article (10) paragraphs (14) to (16).
- To be granted a License, an Applicant shall, at the time of submitting an Application:
Article (5): Cooperation with Relevant Regulatory Authorities
- As part of the designation process for LVPS established and/or licensed by another Regulatory Authority in the State or by relevant regulatory authorities in other jurisdictions, the Central Bank may agree with the relevant regulatory authority which parts of this Regulation, where relevant, may not apply to concerned designated LVPS to avoid additional regulatory burden on the SO and SI of the LVPS.
- The Central Bank will rely on co-operative oversight with the relevant regulatory authority of a designated LVPS operating in the State or in other jurisdictions, in accordance with articles (28) and (127) (2) of the Central Bank Law and the cooperative framework set out in the PFMI.
- As part of the designation process for LVPS established and/or licensed by another Regulatory Authority in the State or by relevant regulatory authorities in other jurisdictions, the Central Bank may agree with the relevant regulatory authority which parts of this Regulation, where relevant, may not apply to concerned designated LVPS to avoid additional regulatory burden on the SO and SI of the LVPS.
Article (5): Licensing Procedure
- The licensing of Applicants shall be subject to the procedure envisaged in the Central Bank’s Licensing Guidelines.
- The Management of an Applicant is encouraged to meet with the Central Bank’s Licensing Division before submitting a formal Application.
- The licensing of Applicants shall be subject to the procedure envisaged in the Central Bank’s Licensing Guidelines.
Article (6): Revocation of License and Designation
Grounds for revocation
- As stipulated in Article (128) of the Central Bank Law, the Central Bank may revoke the License it has given to an LVPS if the LVPS is unable to carry out its operations in compliance with the provisions of the Central Bank Law or this Regulation.
- As stipulated in Article (126) (7) of the Central Bank Law, the Central Bank may revoke the designation of an LVPS it licenses if the LVPS has ceased or is likely to cease being a Systemically Important Financial Infrastructure System or an LVPS whose proper functioning is material to the monetary or financial stability of the State.
Revocation process
- The Central Bank will prepare a review report on whether a licensed and/or designated LVPS satisfies the ground of revocation under this Regulation. If the Central Bank intends to revoke the License and/or designation of an LVPS, the Central Bank will notify in writing the SO and/or the SI of the LVPS or the regulatory authority where the LVPS is licensed so that such authority can notify the SO and/or SI of the system the intention of the Central Bank to revoke the License and/or designation. The notice will state the grounds on which the revocation is to be made and specify in the notice a period of not less than twenty (20) working days from the date of notification, during which the SO and/or SI of the system may be heard, or may make written justifications, as to why the grounds for revocation stated in the notice are not valid.
- If any SO and/or SI of the licensed and/or designated LVPS wish to be heard or to make written justifications, it should make such a request to the Central Bank in writing before the revocation takes effect, giving reasons as to why the grounds for revocation specified in the notice have not been established. After reviewing the reasons given by the SO and/or SI, the Central Bank will determine whether the License and/or designation should be revoked. In the course of reviewing the matter, the Central Bank may meet with the SO and/or SI of the licensed and/or designated LVPS should such need arise.
- If the Central Bank decides to proceed to revoke the License and/or designation of the LVPS, the Central Bank will notify the SO and/or SI of the LVPS of the Central Bank’s decision in writing.
- The SO and/or SI may object to the Central Bank’s decision to revoke the License and/or designation of the LVPS and provide justifications for such objection by applying to the Grievances & Appeals Committee as provided by the Central Bank Law.
- If the Central Bank considers that any designated LVPS licensed by another Regulatory Authority in the State or the concerned regulatory authorities in other jurisdictions is no longer meeting the designation criteria, the Central Bank may request the concerned regulatory authority, via an official notice, to revoke the designation of the LVPS.
- In all cases, the revocation of the License and/or designation of the LVPS shall not affect any transaction cleared and settled in the concerned LVPS prior to the effective date of revocation.
- As stipulated in Article (128) of the Central Bank Law, the Central Bank may revoke the License it has given to an LVPS if the LVPS is unable to carry out its operations in compliance with the provisions of the Central Bank Law or this Regulation.
Article (6): Initial Capital
- An Applicant shall hold, upon being granted a License by the Central Bank, initial capital as per the below:
- 1.1. for obtaining a Category I License:
- 1.1.1. initial capital of at least three (3) million Dirhams where the monthly average value of Payment Transactions amounts to ten (10) million Dirhams or above; or
- 1.1.2. initial capital of at least one and a half (1.5) million Dirhams where the monthly average value of Payment Transactions amounts to less than ten (10) million Dirhams.
- 1.1.1. initial capital of at least three (3) million Dirhams where the monthly average value of Payment Transactions amounts to ten (10) million Dirhams or above; or
- 1.2. for obtaining a Category II License:
- 1.2.1. initial capital of at least two (2) million Dirhams where the monthly average value of Payment Transactions amounts to ten (10) million Dirhams or above; or
- 1.2.2. initial capital of at least one (1) million Dirhams where the monthly average value of Payment Transactions amounts to less than ten (10) million Dirhams.
- 1.2.1. initial capital of at least two (2) million Dirhams where the monthly average value of Payment Transactions amounts to ten (10) million Dirhams or above; or
- 1.3. for obtaining a Category III License:
- 1.3.1. initial capital of at least one (1) million Dirhams where the monthly average value of Payment Transactions amounts to ten (10) million Dirhams or above; or
- 1.3.2. initial capital of at least five hundred thousand (500,000) Dirhams where the monthly average value of Payment Transactions amounts to less than ten (10) million Dirhams.
- 1.3.1. initial capital of at least one (1) million Dirhams where the monthly average value of Payment Transactions amounts to ten (10) million Dirhams or above; or
- 1.4. for obtaining a Category IV License: initial capital of at least one hundred thousand (100,000) Dirhams regardless of the monthly average value of Payment Transactions.
- 1.1. for obtaining a Category I License:
- An Applicant shall provide information to the Central Bank on the source(s) of funds that constitute the initial capital as per paragraph (1).
Calculation Method
- The monthly average value of Payment Transactions referred to in paragraph (1) shall be calculated on the basis of the moving average of the preceding (3) months or, where such data does not exist at the time of being granted a License by the Central Bank, on the basis of the business plan and financial projections provided.
- An Applicant shall hold, upon being granted a License by the Central Bank, initial capital as per the below:
Article (7) Settlement Finality
- In accordance with Article (131) of the Central Bank Law settlement finality is “the discharge of an obligation by a transfer of funds that has become irrevocable and unconditional”. Specifically, “settlement finality” refers to the abrogation of all rights otherwise existing at law that would allow the reversal of a Transfer Order effected through, or proceedings within, an LVPS.
- Article (131) (1) of the Central Bank Law grants finality to all transactions conducted through a Financial Infrastructure System, therefore rendering the same final, irrevocable and irreversible, in any of the cases provided for thereunder. Besides finality in respect of Transfer Orders, the Central Bank Law also provides legal certainty on the Netting arrangements in a designated LVPS.
- If Netting has been effected in an LVPS that meets any of the designation conditions refers to in Article (126) (2) of the Central Bank Law, the SO and/or SI needs to take into consideration the Netting of obligations of insolvent or bankrupt parties to all obligations owed to or by a participant person in the system, as per Article (133) of the Central Bank Law.
- In addition, this Regulation shall not limit, restrict or otherwise effect, the preservation of rights in underlying transactions and obligation of Participant Person to notify of insolvency are set out in Article (134) and Article (135) of the Central Bank Law respectively.
- In accordance with Article (131) of the Central Bank Law settlement finality is “the discharge of an obligation by a transfer of funds that has become irrevocable and unconditional”. Specifically, “settlement finality” refers to the abrogation of all rights otherwise existing at law that would allow the reversal of a Transfer Order effected through, or proceedings within, an LVPS.
Article (7): Aggregate Capital Funds
- A Payment Service Provider shall hold and maintain at all times aggregate capital funds that do not fall below the initial capital requirements laid down in Article (6), taking into consideration the applicable License category.
- The Central Bank may impose aggregate capital funds requirements higher than the ones referred to in paragraph (1) if, taking into consideration the scale and complexity of the Payment Service Provider’s business, it considers such higher requirements essential to ensuring that the Payment Service Provider has the ability to fulfil its obligations under this Regulation.
- Where the monthly average value of Payment Transactions calculated in accordance with Article (6) (3) exceeds the Payment Transaction threshold of ten (10) million Dirhams in (3) consecutive months, Payment Service Providers shall report this fact to the Central Bank and become automatically subject to the higher aggregate capital funds requirements determined by the Central Bank under paragraph (2).
- The aggregate capital funds referred to in paragraph (1) shall be comprised of one or more of the capital items provided for in paragraphs (5) and (6).
Capital Items
- A Payment Service Provider’s aggregate capital funds shall consist of:
- 5.1. Paid-up capital;
- 5.2. Reserves, excluding revaluation reserves; and
- 5.3. Retained earnings.
- 5.1. Paid-up capital;
- The following items shall be deducted from the aggregate capital funds:
- 6.1. Accumulated losses; and
- 6.2. Goodwill.
- 6.1. Accumulated losses; and
- A Payment Service Provider shall hold and maintain at all times aggregate capital funds that do not fall below the initial capital requirements laid down in Article (6), taking into consideration the applicable License category.
Article (8): Ongoing Requirements of Designated Large-Value Payment Systems
Principal Requirements
- The SO and/or SI of a designated LVPS, are required to ensure compliance with the following:
- 1.1. LVPS must comply with any instructions issued by the Central Bank and any relevant international standards (e.g. PFMI), and ensure proper and continued functioning of the designated LVPS; and
- 1.2. LVPS must provide the information required by the Central Bank and where it deems appropriate for achievement of its objectives.
- 1.1. LVPS must comply with any instructions issued by the Central Bank and any relevant international standards (e.g. PFMI), and ensure proper and continued functioning of the designated LVPS; and
- The Central Bank may exempt the SO, SI or a Participant Person of a designated LVPS in a general or specific manner, from the provisions of this Regulation, instructions, rules, directives, rules, and controls issued by it.
- The Central Bank may appoint experts and advisors specialised in Financial Infrastructure Systems to assist the Central Bank in performing its duties and functions in accordance with this Regulation.
Detailed requirements
- Upon designation, an LVPS must comply with the oversight requirements imposed under this Regulation and the relevant provisions of PFMI (see Article (9) for detail). Failure to comply with any of those requirements may expose the concerned party to possible sanctions as provided for under the Central Bank Law. The principal requirements, in addition to the relevant provisions of the PFMI, include: -
- 4.1. Submission of particulars – the Central Bank requires any SO and/or SI of a newly designated LVPS to inform the Central Bank in writing of the designation particulars within fourteen (14) working days after the notification of designation, including the name, place of business, postal address and electronic mail address, as well as the aspects of the management or operations of the system. For any SO and/or SI which are a corporation, the names and personal particulars of the directors, chief executive (if any) and shareholders of the corporation are similarly required to be submitted to the Central Bank. Details of any subsequent change in any of those particulars are to be notified to the Central Bank in writing within fourteen (14) days of the change taking effect.
- 4.2. Compliance with safety and efficiency requirements – the general requirements include safe and efficient operation of the LVPS, the establishment of appropriate Operating Rules, the existence of adequate compliance arrangements, and the availability of appropriate financial resources. Any major change to a designated LVPS’s Operating Rules requires prior approval of the Central Bank.
- 4.3. Submission of information or documents - the Central Bank may request information or documents relating to a designated LVPS from the SO and/or SI of, or the Participant Person in, the LVPS when performing the oversight functions under this Regulation. The SO and/or SI of, or the Participant Person in, the designated LVPS to whom a request is made is required to submit the information or documents within the period specified in the request.
- 4.4. The Central Bank may, at any time, with a short prior notice to the concerned SO and/or SI, examine any books, accounts or transactions of the SO and/or SI of a designated LVPS when performing its functions.
- 4.5. The Central Bank may require the SO and/or SI of, or the Participant Person in, a designated LVPS to submit to the Central Bank a report prepared by one or more auditors on matters that the Central Bank requires for discharging or exercising its duties and powers under this Regulation. The SO and/or SI of, or the Participant Person in, a designated LVPS may only appoint an auditor approved by the Central Bank or an auditor amongst auditors approved by the Central Bank for preparing a report required by the Central Bank.
- 4.6. The Central Bank may direct the SO and/or SI of a designated LVPS to take any action necessary to bring the LVPS into compliance with any of the requirements of this Regulation. Such a direction will specify the Central Bank’s concerns and the action(s) to be taken, include a statement of the respect in which the Central Bank considers the designated LVPS not to be in compliance with a requirement of this Regulation and specify the period within which the direction is to be complied with.
- 4.7. The SO and/or SI of the designated LVPS must have proper Operating Rules to enable its Participant Persons to obtain sufficient information regarding their respective rights and obligations associated with their participation in the LVPS, especially the Default Arrangements and the related procedures. Such rights and obligations must be clearly defined and disclosed to the Participant Persons.
- 4.8. The SI must establish rules and procedures as part of the Operating Rules to enable final settlement to take place no later than the end of the intended settlement time and date. The related rules and procedures must also ensure certainty in terms of circumstances under which Transfer Orders effected through the LVPS are to be regarded as final as well as settled for the purposes of the LVPS.
- 4.9. Where action has been taken under Default Arrangements of a designated LVPS by the SO and/or SI in respect of a Participant Person in the LVPS, the Central Bank may direct the SO and/or SI of a designated LVPS to give information relating to the default to any official nominated by the Central Bank. The nominated official is responsible for assessing and examining any matter arising out of or connected with the default of the Participant Person in that LVPS. The liabilities of Participant Persons for any loss arising from the default of the Participant Person and the arrangements to handle any disputes over Participant Persons’ liability with respect to default transactions should be clearly set out in the rules and procedures.
- 4.1. Submission of particulars – the Central Bank requires any SO and/or SI of a newly designated LVPS to inform the Central Bank in writing of the designation particulars within fourteen (14) working days after the notification of designation, including the name, place of business, postal address and electronic mail address, as well as the aspects of the management or operations of the system. For any SO and/or SI which are a corporation, the names and personal particulars of the directors, chief executive (if any) and shareholders of the corporation are similarly required to be submitted to the Central Bank. Details of any subsequent change in any of those particulars are to be notified to the Central Bank in writing within fourteen (14) days of the change taking effect.
- The SO and/or SI of a designated LVPS, are required to ensure compliance with the following:
Article (8): Control of Controllers
- A Person shall not become a Controller in a Payment Service Provider without obtaining a prior approval from the Central Bank.
- The Central Bank shall grant an approval under paragraph (1) if it considers that:
- 2.1. having regard to the likely influence of the Controller, the Payment Service Provider will remain compliant with the requirements of this Regulation and Level 2 Acts; and
- 2.2. the Controller meets the fit and proper requirements specified by the Central Bank.
- 2.1. having regard to the likely influence of the Controller, the Payment Service Provider will remain compliant with the requirements of this Regulation and Level 2 Acts; and
- The approval under paragraph (2) may be granted subject to any conditions that the Central Bank may impose on the Person, including but not limited to:
- 3.1. conditions restricting the Person’s disposal or further acquisition of shares or voting powers in the Payment Service Provider; and
- 3.2. conditions restricting the Person’s exercise of voting power in the Payment Service Provider.
- 3.1. conditions restricting the Person’s disposal or further acquisition of shares or voting powers in the Payment Service Provider; and
- A Person shall not become a Controller in a Payment Service Provider without obtaining a prior approval from the Central Bank.
Article (9): Compliance with Principles of Financial Market Infrastructures Requirements
- The Committee on Payment and Market Infrastructures (CPMI) and the Technical Committee of the International Organization of Securities Commissions (IOSCO) have set forth a set of PFMI (details of PFMI are available in the two websites: www.bis.org and www.iosco.org).
- PFMI aims to assist central banks, market regulators, and other relevant authorities in enhancing safety and efficiency in payment, clearing, settlement, and recording arrangements, and more broadly, limiting systemic risk and fostering transparency and financial stability.
- Another objective of PFMI is to harmonize and, where appropriate, strengthen the existing international standards and risk management practice for Financial Infrastructure Systems such as LVPS that are systemically important. In general, these standards are expressed as broad principles in recognition of the differing organizations, functions, and designs of the SO and/or SI, and the different ways to achieve a particular result. The principles have also incorporated a range of specific minimum requirements (such as in the credit, liquidity, the general business risk principles) to ensure a common base level of risk management across Systemically Important Financial Infrastructure Systems and jurisdictions.
- The SI and SO must robustly manage the risks of their systemically important LVPS to ensure their safety and promote financial stability. In addition, a systemically important LVPS should not only be safe, but also efficient. Efficiency refers generally to the use of resources by SO, SI and their Participant Persons in performing their functions. Safe and efficient systemically important LVPS contributes to well-functioning financial markets.
- PFMI, as global standards, are broadly designed to apply to all Systemically Important Financial Infrastructure Systems across jurisdictions. The Central Bank therefore requires any designated LVPS to observe and comply with the relevant principles in PFMI, in addition to the compliance with the oversight requirements set out in Article (8) of this Regulation. Moreover, the Central Bank may impose higher requirements than PFMI for the LVPS either on the basis of specific risks posed by a LVPS or as a general policy.
- The requirements set out in the following paragraphs are applicable to the systemically important LVPS operated by the Central Bank, a related entity/subsidiary of the Central Bank and those operated by the private sector. The SO and/or SI should apply these requirements on an ongoing basis in the operation of their LVPS and business, including when reviewing their own performance, assessing or proposing new services, or proposing changes to risk controls.
- In aligning this regulation with leading international practice, LVPS must comply with the relevant principles set out in the following paragraphs.
- Principle 1: Legal basis – a systemically important LVPS must have a well-founded, clear, transparent, with a high degree of legal certainty and an enforceable legal framework for each material aspect of its activities.
- Principle 2: Governance – a systemically important LVPS must have governance arrangements that are clear and transparent, promote the safety and efficiency of the LVPS, and support the stability of the broader financial system, other relevant public interest considerations, and the objectives of relevant stakeholders.
- Principle 3: Framework for the comprehensive management of risks – a systemically important LVPS must have a sound risk management framework for comprehensively managing legal, credit, liquidity, operational, and other risks.
- Principle 4: Credit risk – a systemically important LVPS must effectively measure, monitor, and manage its credit exposures to Participant Person and those arising from its payment, clearing and settlement processes. The systemically important LVPS must maintain sufficient financial resources to cover its credit exposures to each Participant Person fully with a high degree of confidence.
- Principle 5: Collateral – a systemically important LVPS that requires collateral to manage its or its participants’ credit exposure must accept collateral with low credit, liquidity, and market risks. A systemically important LVPS must also set and enforce appropriately conservative haircuts and concentration limits.
- Principle 6: Liquidity risk – a systemically important LVPS must effectively measure, monitor, and manage its liquidity risk. A systemically important LVPS must maintain sufficient liquid resources in all relevant currencies to effect same-day and, where appropriate, intraday and multiday settlement of payment obligations with a high degree of confidence under a wide range of potential stress scenarios that should include, but not be limited to, the default of the participant and its affiliates that would generate the largest aggregate liquidity obligation for the systemically important LVPS in extreme but plausible market conditions.
- Principle 7: Settlement finality – a systemically important LVPS must provide clear and certain final settlement, at a minimum by the end of the value date. Where necessary or preferable, a systemically important LVPS should provide final settlement intraday or in real-time.
- Principle 8: Money settlement – a systemically important LVPS must conduct its money settlements in central bank money where practical and available. If central bank money is not used, a systemically important LVPS should minimize and strictly control the credit and liquidity risk arising from the use of commercial bank money.
- Principle 9: Exchange-of-value settlement systems – if a systemically important LVPS settles transactions that involve the settlement of two linked obligations such as securities or foreign exchange transactions, it must eliminate principle risk by conditioning the final settlement of one obligation upon the final settlement of the other.
- Principle 10: Participant-default rules and procedures – a systemically important LVPS must have effective and clearly defined rules and procedures to manage a Participant Person default. These rules and procedures should be designed to ensure that the systemically important LVPS can take timely action to contain losses and liquidity pressures and continue to meet its obligations.
- Principle 11: General business risk – a systemically important LVPS must identify, monitor, and manage its general business risk and hold sufficient liquid net assets funded by equity to cover potential general business losses so that it can continue operations and services as a going concern if those losses materialize. Further, liquid net assets should at all times be sufficient to ensure a recovery or orderly wind-down of critical operations and services.
- Principle 12: Custody and investment risks – a systemically important LVPS must safeguard its own and its Participant Persons’ assets and minimize the risk of loss on and delay in access to these assets. A systemically important LVPS’s investments should be in instruments with minimal credit, market, and liquidity risks.
- Principle 13: Operational risk – a systemically important LVPS must identify the plausible sources of operational risk, both internal and external, and mitigate their impact through the use of appropriate systems, policies, procedures, and controls. LVPS should be designed to ensure a high degree of security and operational reliability and should have adequate, scalable capacity. Business continuity management should aim for timely recovery of operations and fulfilment of the systemically important LVPS’s obligations, including in the event of a wide-scale or major disruption.
- Principle 14: Access and participation requirements – a systemically important LVPS must have objective, risk-based, and publicly disclosed criteria for participation, which permit fair and open access.
- Principle 15 – Tiered participation arrangements – a systemically important LVPS must identify, monitor, and manage the material risks to the systemically important LVPS arising from tiered participation arrangements.
- Principle 16: Financial market infrastructure links – a systemically important LVPS that establishes a link with one or more FMIs must identify, monitor, and manage link-related risks.
- Principle 17: Efficiency and effectiveness – a systemically important LVPS must be efficient and effective in meeting the requirements of its Participant Persons and the markets it serves.
- Principle 18: Communication procedures and standards – a systemically important LVPS must use, or at a minimum accommodate, relevant internationally accepted communication procedures and standards in order to facilitate efficient payment, clearing, settlement, and recording.
- Principle 19: Disclosure of rules, key procedures, and market data – a systemically important LVPS must have clear and comprehensive rules and procedures and should provide sufficient information to enable Participant Persons to have an accurate understanding of the risks, fees, and other material costs they incur by participating in the systemically important LVPS. All relevant rules and key procedures should be adequately disclosed.
- In addition, CPMI issued a strategy, “Reducing the risk of wholesale payments fraud related to endpoint security”, on 8th May 2018, to encourage industry efforts to reduce the risk of wholesale payments fraud and help market participants stay focused. The strategy is designed to help SO, SI and Participant Persons of Financial Infrastructure Systems and messaging networks as well as their respective supervisors, regulators and overseers. The strategy sets out seven elements, which cover all areas relevant to preventing, detecting, responding to and communicating about fraud and will work holistically.
- The Central Bank requires the SO and/or SI of the designated LVPS to take into account this CPMI strategy and any amendments thereto, when implementing the security measures over the LVPS.
- The Committee on Payment and Market Infrastructures (CPMI) and the Technical Committee of the International Organization of Securities Commissions (IOSCO) have set forth a set of PFMI (details of PFMI are available in the two websites: www.bis.org and www.iosco.org).
Article (9): Principal Business
- The principal business of a Payment Service Provider shall be the provision of the Retail Payment Service(s) for which it has been granted a License.
- Where a Payment Service Provider intends to provide ancillary service(s) falling outside the scope of its License, it shall obtain the approval of the Central Bank prior to commencing the provision of such service(s).
- The Central Bank requires prior approval for the provision of any ancillary service(s) by a Payment Service Provider, and may require a Payment Service Provider that intends to provide ancillary service(s), to create a separate entity for the provision of such services, if it believes that the conduct of the ancillary activities may have a negative impact on the Payment Service Provider’s ability to comply with the requirements of this Regulation and Level 2 Acts.
- The principal business of a Payment Service Provider shall be the provision of the Retail Payment Service(s) for which it has been granted a License.
Article (10): Enforcement and Sanctions
Violation of any provision of this Regulation or committing any of the violations provided for under the Central Bank Law may subject SI and/or SO to administrative and financial sanctions and penalties as deemed appropriate by the Central Bank.
Article (10): On-Going Requirements
Corporate Governance
- Payment Service Providers must comply with the below requirements on corporate governance.
- Payment Service Providers must have and maintain effective, robust and well-documented corporate governance arrangements, including a clear organizational structure with well-defined, transparent and consistent lines of responsibility.
- The corporate governance arrangements referred to in paragraph (2) must be comprehensive and proportionate to the nature, scale and complexity of the Retail Payment Services provided, and shall contain, at a minimum:
- 3.1. an organization chart showing each division, department or unit, indicating the name of each responsible individual accompanied by a description of the respective function and responsibilities;
- 3.2. controls on conflicts of interest;
- 3.3. controls on integrity and transparency of the Payment Service Provider’s operations;
- 3.4. controls to ensure compliance with applicable laws and regulations;
- 3.5. methods for maintaining confidentiality of information; and
- 3.6. procedures for regular monitoring and auditing of all corporate governance arrangements.
- 3.1. an organization chart showing each division, department or unit, indicating the name of each responsible individual accompanied by a description of the respective function and responsibilities;
Risk Management
- Payment Service Providers must have and maintain robust and comprehensive policies and procedures to identify, manage, monitor and report the risks arising from the provision of Retail Payment Services to which they are or might become exposed, and adequate internal control mechanisms, including sound administrative and accounting procedures.
- Payment Service Providers’ risk management policies and procedures shall be:
- 5.1. kept up-to-date;
- 5.2. reviewed annually; and
- 5.3. proportionate to the nature, scale and complexity of the Retail Payment Services provided.
- 5.1. kept up-to-date;
- Payment Service Providers must establish a risk management function, an internal audit function and a compliance function.
Accounting and Audit
- Payment Service Providers must appoint an Auditor to audit on an annual basis:
- 7.1. the financial statements or consolidated financial statements of the Payment Service Provider prepared in accordance with the accepted accounting standards and practices; and
- 7.2. the systems and controls of the Retail Payment Services provided by the Payment Service Provider, separately from any audit on non-Retail Payment Services.
- 7.1. the financial statements or consolidated financial statements of the Payment Service Provider prepared in accordance with the accepted accounting standards and practices; and
- Upon request by the Central Bank, the appointed Auditor shall submit, directly or through the Payment Service Provider, a report of the audit in a form and within a timeframe acceptable to the Central Bank.
- In addition to the report of audit, the Central Bank may request from the Auditor to:
- 9.1. submit any additional information in relation to the audit, if the Central Bank considers it necessary;
- 9.2. enlarge or extend the scope of the audit;
- 9.3. carry out any other examination.
- 9.1. submit any additional information in relation to the audit, if the Central Bank considers it necessary;
Record Keeping
- Payment Service Providers shall keep all necessary records on Personal and Payment Data for a period of (5) years from the date of receipt of such data, unless otherwise required by other applicable laws or the Central Bank.
Notification Requirements
- Where any material change affects the accuracy and completeness of information provided in an Application, the Applicant or Payment Service Provider, as the case may be, shall immediately notify the Central Bank of such change and provide all necessary information and documents.
- A Payment Service Provider shall immediately notify the Central Bank of any violation or potential violation of a Major Regulatory Requirement of this Regulation or Level 2 Acts.
- A Payment Service Provider shall immediately notify the Central Bank if it becomes aware that any of the following events have occurred or are likely to occur:
- 13.1. any event that prevents access to or disrupts the operations of the Payment Service Provider;
- 13.2. any legal action taken against the Payment Service Provider either in the State or in a Third Country;
- 13.3. the commencement of any insolvency, winding up, liquidation or equivalent proceedings, or the appointment of any receiver, administrator or provisional liquidator under the laws of any country;
- 13.4. any disciplinary measure or sanction taken against the Payment Service Provider or imposed on it by a regulatory body other than the Central Bank, whether in the State or in a Third Country;
- 13.5. any change in regulatory requirements to which it is subject beyond those of the Central Bank, whether in the State or in a Third Country; and
- 13.6. any other event specified by the Central Bank.
- 13.1. any event that prevents access to or disrupts the operations of the Payment Service Provider;
Professional Indemnity Insurance
- Payment Service Providers providing Payment Initiation and Payment Account Information Services shall hold a professional indemnity insurance whose amount shall be decided upon by the Central Bank.
- The professional indemnity insurance of Payment Service Providers providing Payment Initiation Services referred to in paragraph (14) shall cover these Payment Service Providers’ liabilities for Unauthorized Payment Transactions and non-execution, defective or late execution of Payment Transactions.
- The professional indemnity insurance of Payment Service Providers providing Payment Account Information Services referred to in paragraph (14) shall cover these Payment Service Providers’ liability vis-à-vis the Payment Service Provider providing Account Issuance Services or the Retail Payment Service User resulting from non-authorized or fraudulent access to or non-authorized or fraudulent use of Payment Account information.
- Payment Service Providers must comply with the below requirements on corporate governance.
Article (11): Appeal Mechanism
- For the purposes of this Regulation, the relevant Central Bank’s decisions that may be subject to appeal before the Grievances & Appeals Committee include: -
- 1.1. licensing and designation of LVPS;
- 1.2. revocation or cancellation or suspension of a License and designation of LVPS; and
- 1.3. any Central Bank’s actions undertaken against a violating Person.
- 1.1. licensing and designation of LVPS;
- Under the Regulation, any Person aggrieved by any of the decisions set out in paragraph 1 of this Article may refer the decision to the Grievances & Appeals Committee in writing for review.
- Any Person who intends to refer any of the relevant decisions of the Central Bank to the Grievances & Appeals Committee is required to do so in writing to the Central Bank stating the grounds on which the review is sought, as per the committee charter.
- For the purposes of this Regulation, the relevant Central Bank’s decisions that may be subject to appeal before the Grievances & Appeals Committee include: -
Article (11) Payment Token Services
- This Article (11) is without prejudice to other provisions of this Regulation that are relevant to Payment Service Providers providing Payment Token Services.
- For the avoidance of doubt, Payment Token Services do not include Security Token, Commodity Token and Virtual Asset Token and the provision of services associated with the same.
- Security Token and Commodity Token fall within the jurisdiction of the Securities and Commodities Authority and as such are regulated by the Securities and Commodities Authority.
- Virtual Asset Tokens, although may be accepted as a means of payment, are not generally accepted as a medium of exchange due to the lack of stability and high volatility in their market value. As a result, any services associated with Virtual Asset Tokens, including Virtual Asset Token Services, fall outside the scope of this Regulation.
Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations
- Payment Token Services shall be considered to carry high money laundering and terrorist financing risk due to their speed, anonymity and cross-border nature. In line with the FATF standards, Payment Services Providers providing Payment Token Services shall undertake risk assessment and take appropriate measures to manage and mitigate the identified risks in accordance with applicable legal and regulatory requirements. Payment Service Providers providing Payment Token Services shall comply with the FATF Guidance for a Risk-based Approach to Virtual Assets and Virtual Assets Service Providers, as may be supplemented from time to time, or any related standards or guidance in assessing and managing risks in Payment Token Services.
Technology Risk and Information Security
Security Requirements
- A Payment Service Provider providing Payment Token Services shall have a good understanding of the security risks and vulnerabilities of each Payment Token provided. It shall carry out a security risk assessment for each Payment Token.
Cyber Security Risk
- Payment Service Providers providing Payment Token Services whose monthly average value of Payment Transactions amounts to ten (10) million Dirhams or above shall regularly assess the necessity to perform penetration and cyber-attack simulation testing. Coverage and scope of testing shall be based on the cyber security risk profile, cyber intelligence information available, covering not only networks (both external and internal) and application systems but also social engineering and emerging cyber threats. A Payment Service Provider shall also take appropriate actions to mitigate the issues, threats and vulnerabilities identified in penetration and cyber-attack simulation testing in a timely manner, based on the impact and risk exposure analysis.
Specific Obligations for Providing Retail Payment Service on Payment Tokens
Reserve of Assets
- Payment Service Providers issuing Payment Tokens shall keep and maintain at all times a Reserve of Assets per category of Payment Token issued.
- Payment Service Providers issuing Payment Tokens shall ensure effective and prudent management of the Reserve of Assets. They shall ensure that the creation and destruction of Payment Tokens is matched by a corresponding increase or decrease in the Reserve of Assets and that such increase or decrease is adequately managed to avoid any adverse impacts on the market of the Reserve Assets.
Stabilisation Mechanism
- Payment Service Providers issuing Payment Tokens shall have and maintain a clear and detailed policy on the selected stabilisation mechanism. That policy and procedure shall in particular:
- 10.1. describe the type, allocation and composition of the reference assets the value of which aims at stabilising the value of the Payment Tokens;
- 10.2. contain a detailed assessment of the risks, including credit risk, counterparty risk, market risk and liquidity risk, resulting from the Reserve of Assets;
- 10.3. describe the procedure for the creation and destruction of Payment Tokens and the consequence of such creation or destruction on the increase and decrease of the Reserve of Assets;
- 10.4. provide information on whether the Reserve of Assets is invested, and where part of the Reserve of Assets is invested, describe in detail the investment policy and contain an assessment of how that investment policy can affect the value of the Reserve of Assets; and
- 10.5. describe the procedure to purchase and redeem Payment Tokens against the Reserve of Assets, and list the persons who are entitled to such redemption.
- 10.1. describe the type, allocation and composition of the reference assets the value of which aims at stabilising the value of the Payment Tokens;
- Payment Service Providers issuing Payment Tokens shall ensure an independent audit of the Reserve of Assets on a bi-annual basis as from the receipt of the Central Bank’s approval of the White Paper with respect of the Payment Tokens.
Custody
- Payment Service Providers issuing Payment Tokens shall establish, maintain and implement custody policies, procedures and contractual arrangements for each category of issued Payment Tokens that ensure at all times that:
- 12.1. the Reserve of Assets is segregated from the Payment Service Provider’s own assets;
- 12.2. the Reserve of Assets is not encumbered or pledged;
- 12.3. the Reserve of Assets is held in custody in accordance with paragraph (14); and
- 12.4. the Payment Service Providers have prompt access to the Reserve of Assets to meet any redemption requests from the holders of Payment Token.
- 12.1. the Reserve of Assets is segregated from the Payment Service Provider’s own assets;
- The assets received in exchange for the Payment Tokens shall be held in custody by no later than (5) Business Days after the issuance of the Payment Tokens by:
- 13.1. Bank; or
- 13.2. Payment Service Provider providing Payment Token Custody.
- 13.1. Bank; or
Investment of the Reserve of Assets
- Payment Service Providers issuing Payment Tokens that invest a portion of the Reserve of Assets shall invest those assets only in highly liquid financial instruments with minimal market and credit risk. The investments shall be capable of being liquidated rapidly with minimal adverse price effect.
- All profits or losses, including fluctuations in the value of the financial instruments referred to in paragraph (14), and any counterparty or operational risks that result from the investment of the assets shall be borne by Payment Service Providers issuing the Payment Tokens.
Pre-Trade Transparency
- Payment Service Providers that engage in Facilitating the Exchange of Payment Tokens shall disclose to its Retail Payment Service Users and the public as appropriate, on a continuous basis during normal trading, the following information relating to trading of each accepted Payment Tokens on their platform:
- 16.1. the current bid, offer prices and volume;
- 16.2. the depth of trading interest shown at the prices and volumes advertised through their systems for the accepted Payment Tokens; and
- 16.3. any other information relating to accepted Payment Tokens which would promote transparency relating to trading.
- 16.1. the current bid, offer prices and volume;
- Payment Service Providers that engage in Facilitating the Exchange of Payment Tokens shall use appropriate mechanisms to enable pre-trade information to be made available to the public in an easy to access and uninterrupted manner.
Post-Trade Transparency
- Payment Service Providers that engage in Facilitating the Exchange of Payment Tokens shall disclose the price, volume and time of the Payment Transactions executed in respect of accepted Payment Tokens to the public as close to real-time as is technically possible on a nondiscretionary basis. They shall use adequate mechanisms to enable post-trade information to be made available to the public in an easy to access and uninterrupted manner, at least during business hours.
- This Article (11) is without prejudice to other provisions of this Regulation that are relevant to Payment Service Providers providing Payment Token Services.
Article (12): Transition Period
- A one-year transitional period will commence on the date the Regulation comes into force. System Operators and Settlement Institutions of existing LVPS operating in the State may continue operating throughout the transitional period without being regarded as contravening this Regulation. Nevertheless, they are required to obtain a license from the Central Bank to operate their LVPS before the expiration of the transition period.
- If the Central Bank considers that a Financial Infrastructure System fulfills the criteria for designation as provided for under the Central Bank Law, the Central Bank shall have the power to require any such system to obtain a license within a reasonable period to be determined by the Central Bank prior to the expiration of the transition period.
- A one-year transitional period will commence on the date the Regulation comes into force. System Operators and Settlement Institutions of existing LVPS operating in the State may continue operating throughout the transitional period without being regarded as contravening this Regulation. Nevertheless, they are required to obtain a license from the Central Bank to operate their LVPS before the expiration of the transition period.
Article (12) Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations
- Payment Service Providers must comply with the relevant UAE AML Laws and Regulations and address money laundering and terrorist financing risks through appropriate preventive measures to deter abuse of the sector as a conduit for illicit funds, and detect money laundering and terrorist financing activities and report any suspicious transactions to the Financial Intelligence Department at the Central Bank.
- Payment Service Providers must have comprehensive and effective internal AML/CFT policies, procedures and controls in place. Payment Service Providers shall be prohibited from invoking banking, professional or contractual secrecy as a pretext for refusing to perform their statutory reporting obligation in regard to suspicious activity.
- Payment Service Providers must identify, assess, and understand the ML/FT risks to which they are exposed and conduct enterprise-level and business relationship-specific risk assessments. Accordingly, all AML/CFT CDD, monitoring and controls must be risk-based and aligned to the risk assessments.
- Payment Service Providers shall undertake periodic risk profiling of Retail Payment Service Users and assessment based on the AML/CFT requirements.
- Payment Service Providers shall assess whether a business relationship presents a higher money laundering and terrorist financing risk and assign a related risk rating. Payment Service Providers shall be prohibited from dealing in any way with shell banks or other shell financial institutions and from establishing or maintaining any business relationship or conducting any Payment Transaction under an anonymous or fictitious name or by pseudonym or number.
- Payment Service Providers shall ensure that their CDD models are designed to address the specific risks posed by a Retail Payment Service User profile and Payment Instrument features. Payment Service Providers shall be prohibited from establishing or maintaining any business relationship or executing any Payment Transaction in the event that they are unable to complete adequate risk-based CDD measures for any reason.
- Payment Service Providers providing Retail Payment Services must undertake certain CDD measures concerning Wire Transfers as stipulated in the relevant provisions of the AML Law if Wire Transfer services are provided by Payment Service Providers. Payment Service Providers should introduce appropriate systems for screening, as part of the CDD process, on all parties involved in a transaction against all applicable sanction lists (i.e. the UN sanction lists and the names contained in the ‘search notices’/’search and freeze notices’ issued by the Central Bank).
- If Payment Service Providers provide the service of Wire Transfers, they should take freezing action and prohibit conducting transactions with designated persons and entities, as per the obligations set out in the Central Bank’s Notice 103/2020 on the Implementation of United Nations Security Council (UNSC) and the UAE Cabinet Resolutions regarding UNSC and Local Lists, as amended from time to time.
- Payment Service Providers should also be guided by the Financial Action Task Force (FATF) Standards on anti-money laundering and countering the financing of terrorism and proliferation. Payment Service Providers should incorporate the regular review of ML/FT trends and typologies into their compliance training programmes as well as into their risk identification and assessment procedures.
- Payment Service Providers must comply with the relevant UAE AML Laws and Regulations and address money laundering and terrorist financing risks through appropriate preventive measures to deter abuse of the sector as a conduit for illicit funds, and detect money laundering and terrorist financing activities and report any suspicious transactions to the Financial Intelligence Department at the Central Bank.
Article (13): Interpretation of this Regulation
- The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
Article (13) Technology Risk and Information Security
- Payment Service Providers shall comply with this Article (13) and are encouraged to consult Annex II for the Guidance on the best practices for technology risk and information security.
Technology Risk
- Payment Service Providers are expected to take into account international best practices and standards when designing and implementing the technology and specific risk management systems and processes.
- A Payment Service Provider shall establish an effective technology and cyber security risk management framework to ensure the adequacy of IT controls, cyber resilience, the quality and security, including the reliability, robustness, stability and availability, of its computer systems, and the safety and efficiency of the operations of Retail Payment Services. The framework shall be “fit for purpose” and commensurate with the risks associated with the nature, size, complexity and types of business and operations, the technologies adopted and the overall risk management system of the Payment Service Provider. Consideration shall be given to adopting recognized international standards and practices when formulating such risk management framework.
- A Payment Service Provider’s effective technology risk management framework shall comprise proper IT governance, a continuous technology risk management process and implementation of sound IT control practices.
- A Payment Service Provider shall establish a general framework for management of major technology-related projects, such as in-house software development and acquisition of information systems. This framework shall specify, among other things, the project management methodology to be adopted and applied to these projects.
- Payment Service Provider shall apply and meet at a minimum the UAE Information Assurance Standards, as may be amended from time to time.
IT Governance
- A Payment Service Provider shall establish a proper IT governance framework. IT governance shall cover various aspects, including a clear structure of IT functions and the establishment of IT control policies. While there could be different constructs, the major functions shall include an effective IT function, a robust technology risk management function, and an independent technology audit function.
- The Board, or a committee designated by the Board shall be responsible for ensuring that a sound and robust risk management framework is established and maintained to manage technology risks in a manner that is commensurate with the risks posed by the Payment Service Provider’s Retail Payment Activities.
Security Requirements
- A Payment Service Provider must define clearly its security requirements in the early stage of system development or acquisition as part of business requirements and adequately built during the system development stage.
- A Payment Service Provider using the Agile methods to accelerate software development must incorporate adequate security practices to ensure the software is not compromised at any stage in its development process.
- A Payment Service Provider that develops an Application Programming Interface (API) or provides an API shall establish safeguards to manage the development and provision of the APIs to secure the interaction and exchange of data between various software applications.
Network and Infrastructure Management
- A Payment Service Provider whose monthly average value of Payment Transactions amounts to ten (10) million Dirhams or above shall clearly assign overall responsibility for network management to individuals who are equipped with expertise to fulfil their duties. Network standards, design, diagrams and operating procedures shall be formally documented, kept up-to-date, communicated to all relevant network staff and reviewed periodically.
- A Payment Service Provider shall establish a security administration function and a set of formal procedures for administering the allocation of access rights to system resources and application systems, and monitoring the use of system resources to detect any unusual or unauthorized activities.
- Payment Service Providers shall exercise due care when controlling the use of and access to privileged and emergency IDs. The necessary control procedures include:
- 14.1. changing the default password;
- 14.2. implement strong password control, with minimum password length and history, password complexity as well as maximum validity period;
- 14.3. restricting the number of privileged users;
- 14.4. implementing strong controls over remote access by privileged users;
- 14.5. granting of authorities that are strictly necessary to privileged and emergency IDs;
- 14.6. formal approval by appropriate senior personnel prior to being released for usage;
- 14.7. logging, preserving and monitoring of the activities performed by privileged and emergency IDs (e.g. peer reviews of activity logs);
- 14.8. prohibiting sharing of privileged accounts;
- 14.9. proper safeguard of privileged and emergency IDs and passwords (e.g. kept in a sealed envelope and locked up inside the data center); and
- 14.10.changing of privileged and emergency IDs’ passwords immediately upon return by the requesters.
- 14.1. changing the default password;
Cyber Security Risk
- Where a Payment Service Provider is heavily reliant on Internet and mobile technologies to deliver the Retail Payment Services it provides, cyber security risks shall be adequately managed through the Payment Service Provider’s technology risk management process. The Payment Service Provider shall also commit adequate skilled resources to ensure its capability to identify the risk, protect its critical services against the attack, contain the impact of cyber security incidents and restore the services.
- A Payment Service Provider shall establish a cyber incident response and management plan to swiftly isolate and neutralize a cyber threat and to resume affected services as soon as possible. The plan shall describe procedures to respond to plausible cyber threat scenarios
- Payment Service Providers whose monthly average value of Payment Transactions amounts to ten (10) million Dirhams or above shall regularly assess the necessity to perform penetration and cyber-attack simulation testing. Coverage and scope of testing shall be based on the cyber security risk profile, cyber intelligence information available, covering not only networks (both external and internal) and application systems but also social engineering and emerging cyber threats. A Payment Service Provider shall also take appropriate actions to mitigate the issues, threats and vulnerabilities identified in penetration and cyber-attack simulation testing in a timely manner, based on the impact and risk exposure analysis.
Retail Payment Service User Authentication
- A Payment Service Provider shall select and implement reliable and effective authentication techniques to validate the identity and authority of its Retail Payment Service Users. Multi-factor authentication shall be required for high-risk transactions.
- End-to-end encryption shall be implemented for the transmission of Retail Payment Service User passwords so that they are not exposed at any intermediate nodes between the Retail Payment Service User mobile application or browser and the system where passwords are verified.
Login Attempts and Session Management
- A Payment Service Provider shall implement effective controls to limit the number of login or authentication attempts (e.g. wrong password entries), implementing time-out controls and setting time limits for the validity of authentication. If one-time password is used for authentication purpose, a Payment Service Provider shall ensure that the validity period of such passwords is limited to the strict minimum necessary.
- A Payment Service Provider shall have processes in place ensuring that all Payment Transactions are logged with an appropriate audit trail.
Administration of Retail Payment Service User Accounts
- Where a Payment Service Provider providing Payment Account Issuance Services allows a Retail Payment Service User to open a Payment Account through an online channel, a reliable method shall be adopted to authenticate the identity of that Retail Payment Service User. In general, the electronic know your customer (i.e. Retail Payment Service User) (eKYC) processes accepted by the Central Bank for Banks is acceptable for the customer verification and validation processes of Payment Account Issuance Services.
- A Payment Service Provider shall perform adequate identity checks when any Retail Payment Service User requests a change to the Retail Payment Service User’s Payment Account information or contact details that are useful for the Retail Payment Service User to receive important information or monitor the activities of the Retail Payment Service User’s Payment Accounts.
- A Payment Service Provider shall implement effective controls such as two-factor authentication, to re-authenticate the Retail Payment Service User before effecting each high-risk transaction. High-risk transactions shall, at least, include:
- 24.1. Payment Transactions that exceeded the predefined transaction limit(s);
- 24.2. Change of personal contact details; and
- 24.3. Unless it is not practicable to implement, Payment Transactions that exceeded the aggregate rolling limit(s) (i.e. total value of Payment Transactions over a period of time).
- 24.1. Payment Transactions that exceeded the predefined transaction limit(s);
Business Continuity
- A Payment Service Provider shall have in place an adequate business continuity management program to ensure continuation, timely recovery, or in extreme situations orderly scaledown of critical operations in the event of major disruptions caused by different contingent scenarios. An adequate business continuity management program comprises business impact analysis, recovery strategies, a business continuity plan and alternative sites for business and IT recovery.
- A Payment Service Provider shall put in place a set of recovery strategies to ensure that all critical business functions identified in a business impact analysis can be recovered in accordance with the predefined recovery timeframe. These recovery strategies shall be clearly documented, thoroughly tested and regularly reviewed to ensure achievement of recovery targets.
- A Payment Service Provider shall put in place effective measures to ensure that all business records, in particular Retail Payment Service User records, can be timely restored in case they are lost, damaged, or destroyed. A Payment Service Provider shall also allow Retail Payment Service Users to access their own records in a timely manner. A Payment Service Provider shall notify Retail Payment Service Users of any loss in their records through an operational failure or through theft, and make reasonable effort to ensure that personal records so lost are not used wrongfully.
- A Payment Service Provider shall develop a business continuity plan based on the business impact analysis and related recovery strategies. A business continuity plan shall comprise, at a minimum:
- 28.1. detailed recovery procedures to ensure full accomplishment of the service recovery strategies;
- 28.2. escalation procedures and crisis management protocol (e.g. set up of a command center, timely reporting to the Central Bank, etc.) in case of severe or prolonged service disruptions;
- 28.3. proactive communication strategies (e.g. Retail Payment Service User notification, media response, etc.);
- 28.4. updated contact details of key personnel involved in the business continuity plan; and
- 28.5. assignment of primary and alternate personnel responsible for recovery of critical systems.
- 28.1. detailed recovery procedures to ensure full accomplishment of the service recovery strategies;
- A Payment Service Provider shall conduct testing of its business continuity plan at least annually. Its Management, primary and alternate relevant personnel shall participate in the annual testing to familiarize themselves with their recovery responsibilities.
- A Payment Service Provider shall review all business continuity planning-related risks and assumptions for relevancy and appropriateness as part of the annual planning of testing. Formal testing documentation, including a test plan, scenarios, procedures and results, shall be produced. A post mortem review report shall be prepared for formal sign-off by Management
Alternate Sites for Business and IT Recovery
- A Payment Service Provider shall examine the extent to which key business functions are concentrated in the same or adjacent locations and the proximity of the alternate sites to primary sites. Alternate sites shall be sufficiently distanced to avoid any shared risk and being affected by the same disaster.
- A Payment Service Provider’s alternate site shall be readily accessible, installed with appropriate facilities and available for occupancy within the time requirement specified in its business continuity plan. Appropriate physical access controls shall be implemented. If certain recovery staff are required to work from home in the event of a disaster, adequate computer systems and communication facilities shall be made available in advance.
- Alternate sites for IT recovery shall have sufficient technical equipment, including communication facilities, of an appropriate standard and capacity to meet recovery requirements.
- A Payment Service Provider shall avoid placing excessive reliance on external vendors in providing business continuity management support, including the provision of the disaster recovery site and back-up equipment and facilities. A Payment Service Provider shall satisfy itself that each vendor has the capacity to provide the services when needed, and that the contractual responsibilities of the vendors, including the lead-time to provide necessary emergency services, types of support and capacity, are clearly specified.
- Where a Payment Service Provider is reliant on shared computing services provided by external providers, such as cloud computing, to support its disaster recovery, it shall manage the risk associated with these services.
Reputation Risk Management
- A Payment Service Provider shall establish and implement an effective process for managing reputational risk that is appropriate for the size and complexity of its operations.
- Payment Service Providers shall comply with this Article (13) and are encouraged to consult Annex II for the Guidance on the best practices for technology risk and information security.
Article (14): Publication & Application
- This Regulation shall be published in the Official Gazette in both Arabic and English and shall come into effect one month from the date of publication. In case of any discrepancy between the Arabic and the English, the Arabic version will prevail.
Article (14): Obligations Towards Retail Payment Service Users
- Payment Service Providers must be operated prudently and with competence in a manner that will not adversely affect the interests of the Retail Payment Service Users or potential Retail Payment Service Users. In addition, they must also observe and comply with the relevant regulatory requirements and standards on consumer protection of the Central Bank. For the avoidance of doubt, in case of discrepancies between this Regulation and the Central Bank’s requirements and standards on consumer protection, the respective provisions of this Regulation shall prevail.
Safeguarding of Funds In-Transit
- At no time shall Payment Service Providers hold funds of Retail Payment Service Users unless these are funds in transit.
- Payment Service Providers that settle Payment Transactions within twenty four (24) hours shall segregate Retail Payment Service Users’ funds in the following ways:
- 3.1. funds shall not be commingled at any time with the funds of any Person other than the Retail Payment Service Users on whose behalf the funds are held; and/or
- 3.2. funds shall be insulated in the interest of the Retail Payment Service Users against the claims of other creditors of the Payment Service Provider, in particular in the event of insolvency.
- 3.1. funds shall not be commingled at any time with the funds of any Person other than the Retail Payment Service Users on whose behalf the funds are held; and/or
- Payment Service Providers that settle Payment Transactions after twenty-four (24) hours shall segregate Retail Payment Service Users’ funds in the following ways:
- 4.1. open a separate escrow account with a Bank and restrict any operations and transactions on this account save for the transfer of the deposited Retail Payment Service Users’ funds to the end beneficiary; and/or
- 4.2. funds shall be covered by an insurance policy or by a bank guarantee from a regulated insurance company or Bank which does not belong to the same Group as the Payment Service Provider.
- 4.3. While Banks, acting as Retail Payment Service Provider, are not required to establish a separate escrow account, an insurance policy or a bank guarantee to safeguard Retail Payment Service Users’ funds, a separate bank account under the name of the concerned Retail Payment Service Users must be set up for protecting the funds.
- 4.1. open a separate escrow account with a Bank and restrict any operations and transactions on this account save for the transfer of the deposited Retail Payment Service Users’ funds to the end beneficiary; and/or
Transparency of Contractual Terms
- Payment Service Providers shall provide the terms and conditions governing their contractual relationship with:
- 5.1. each new Retail Payment Service User, sufficiently in advance of entering into the contractual relationship as to allow the Retail Payment Service User to make an informed decision; and
- 5.2. each existing Retail Payment Service User, at their request in writing and delivered as per the Retail Payment Service User’s preference, including through an e-mail, mobile application or any other electronic manner.
- 5.1. each new Retail Payment Service User, sufficiently in advance of entering into the contractual relationship as to allow the Retail Payment Service User to make an informed decision; and
- The terms and conditions referred to in paragraph (5) shall be written in a clear, plain and understandable language, in a manner that is not misleading and shall be provided to the Retail Payment Service User in both Arabic and English, as may be requested by the Retail Payment Service User.
- Any changes to the terms and conditions referred to in paragraph (5) shall be communicated to the Retail Payment Service User by the Payment Service Provider sufficiently in advance and at least 30 calendar days prior to any such change becoming effective.
- A Retail Payment Service User shall be entitled to terminate its contractual relationship with a Payment Service Provider at no charge where it does not agree with the revised terms and conditions referred to in paragraph (7).
Single Retail Payment Service Agreements
- For transactions that are to be concluded under a Single Retail Payment Service Agreement, Payment Service Providers shall provide Retail Payment Service Users with the following information before the entry into a contractual relationship:
- 9.1. schedule of fees, charges and commissions, including conversion rates and withdrawal charges, where applicable;
- 9.2. contact details of the Payment Service Provider, including legal name and registered address, including the address of the agent or branch, where applicable;
- 9.3. the form and procedure for giving consent to the initiation of a Payment Order or execution of a Payment Transaction and for the withdrawal of consent;
- 9.4. the communication channel between the Payment Service Provider and the Retail Payment Service User;
- 9.5. the manner in safeguarding of funds as per Article 14(3) and (4) and Reserve of Assets as per Article 11(9);
- 9.6. the manner and timeline for notification by the Retail Payment Service User to the Payment Service Provider in case of Unauthorized or incorrectly initiated or executed Payment Transaction;
- 9.7. information on Payment Service Provider’s and Retail Payment Service User’s liability for Unauthorized Payment Transactions;
- 9.8. the service level for the provision of the Retail Payment Service;
- 9.9. information on the Payment Service Provider’s complaint procedure; and
- 9.10. the Payment Service Provider’s procedure for reporting of Unauthorized Payment Transactions.
- 9.1. schedule of fees, charges and commissions, including conversion rates and withdrawal charges, where applicable;
- The information required in paragraph (9) shall be provided immediately after the execution of the Payment Transaction where it is concluded at a Payment Service User’s request using a Means of Distance Communication which does not allow for the provision of such information before the entry into a contractual relationship.
Framework Agreements
- For transactions that are concluded under a Framework Agreement, Payment Service Providers shall provide to Retail Payment Service Users the following information before the Retail Payment Service User consents to the entry into a Payment Transaction as well as at any other time the Retail Payment Service User requests this information, and within (5) Business Days of such request:
- 11.1. schedule of fees, charges and commissions, including conversion rates and withdrawal charges, where applicable;
- 11.2. contact details of the Payment Service Provider, including legal name and registered address, including address of the agent or branch, where applicable;
- 11.3. the form and procedure for giving consent to the initiation of a Payment Order or execution of a Payment Transaction and for the withdrawal of consent;
- 11.4. the communication channel between the Payment Service Provider and the Retail Payment Service User;
- 11.5. the manner in safeguarding of funds as per Article 14(3) and (4) and Reserve of Assets as per Article 11(9);
- 11.6. the manner and timeline for notification by the Retail Payment Service User to the Payment Service Provider in case of Unauthorized or incorrectly initiated or executed Payment Transaction;
- 11.7. information on Payment Service Provider’s and Retail Payment Service User’s liability for Unauthorized Payment Transactions;
- 11.8. information relating to terms under which a Payment Service User may be deemed to have accepted changes to the terms and conditions, the duration of the contract and the rights of the parties to terminate the Framework Agreement;
- 11.9. the service level for the execution of the Retail Payment Service;
- 11.10.information on the Payment Service Provider’s complaint procedure; and
- 11.11.the Payment Service Provider’s procedure for reporting of Unauthorized Payment Transactions.
- 11.1. schedule of fees, charges and commissions, including conversion rates and withdrawal charges, where applicable;
- The information required in paragraph (11) shall be provided immediately after the execution of the Payment Transaction where it is concluded at a Payment Service User’s request using a Means of Distance Communication which does not allow for the provision of such information before the entry into a contractual relationship.
- Payment Service Providers shall provide Retail Payment Service Users with a written statement of the Payment Transactions under a Framework Agreement at least once per month free of charge, including details of the amounts, fees, charges and commissions, the dates and times of execution and the reference numbers for each Payment Transaction.
Information Requirements
- Immediately after the receipt of an order for a Payment Transaction, the Payment Service Provider of the Payer shall provide a receipt for Retail Payment Service Users with:
- 14.1. confirmation of the successful or unsuccessful initiation and execution of the Payment Transaction;
- 14.2. acknowledgement and reference number to track the status of the Payment Transaction, including:
- 14.2.1. the date and amount of the Payment Transaction; and
- 14.2.2. information relating to the Payee;
- 14.2.1. the date and amount of the Payment Transaction; and
- 14.3. the amount of the Payment Transaction, any related fees or charges, including the actual currency and conversion rates used, and withdrawal charges, where applicable; and
- 14.4. the date on which the Payment Service Provider received the Payment Order.
- 14.1. confirmation of the successful or unsuccessful initiation and execution of the Payment Transaction;
- The Payee’s Payment Service Provider shall, immediately after the execution of the Payment Transaction, provide to the Payee with a statement with the following information:
- 15.1. reference enabling the Payee to identify the Payment Transaction and, where appropriate, the Payer and any information transferred with the Payment Transaction;
- 15.2. the amount of the Payment Transaction in the currency in which the funds are to be dispersed disbursed to the Payee;
- 15.3. the amount of any fees or charges for the Payment Transaction payable by the Payee;
- 15.4. where applicable, the currency exchange rate used in the Payment Transaction by the Payee’s Payment Service Provider; and
- 15.5. the date on which the amount of a Payment Transaction is credited to a Payee’s Payment Account.
- 15.1. reference enabling the Payee to identify the Payment Transaction and, where appropriate, the Payer and any information transferred with the Payment Transaction;
- The Payer’s Payment Service Provider shall ensure that Payment Orders are accompanied by the necessary information so that they can be processed accurately and completely, and also, be easily identified, verified, reviewed, audited and for any subsequent investigation if needed.
- The Payee’s Payment Service Provider shall implement procedures to detect when any necessary information is missing or inaccurate for a Payment Transaction.
Protection of Payment and Personal Data
- Payment Service Providers shall have in place and maintain adequate policies and procedures to protect:
- 18.1. Payment Data and identify, prevent and resolve any data security breaches; and
- 18.2. Personal Data.
- 18.1. Payment Data and identify, prevent and resolve any data security breaches; and
- Payment Service Providers may disclose Payment and Personal Data to:
- 19.1. a third party where the disclosure is made with the prior written consent of the Retail Payment Service User or is required pursuant to applicable laws;
- 19.2. to the Central Bank;
- 19.3. other regulatory authorities upon request/following prior approval of the Central Bank;
- 19.4. a court of law; and
- 19.5. other government bodies who have lawfully authorized rights of access.
- 19.1. a third party where the disclosure is made with the prior written consent of the Retail Payment Service User or is required pursuant to applicable laws;
- In addition to the envisaged in paragraph (19), Payment Service Providers may also disclose Personal Data to its corresponding Data Subject.
- Payment Service Providers shall have in place and maintain Payment and Personal Data protection controls.
- Personal and Payment Data shall be stored and maintained in the State. Payment Service Providers must also establish a safe and secure backup of all Personal and Payment Data in a separate location for the required period of retention of (5) years.
- Payment Service Providers shall comply with applicable regulatory requirements and standards on data protection. They shall control, process and retain only Personal Data that is necessary for the provision of Retail Payment Services and upon obtaining the explicit consent of the Retail Payment Service User.
Liability for Unauthorized Payment Transactions and Refunds
- Payment Service Providers shall be fully liable for any fraudulent or Unauthorized Payment Transaction, whether before or after the Payer informs the Payment Service Provider of any potential or suspected fraud, except where there is evidence that:
- 24.1. the Payer acts fraudulently; or
- 24.2. the Payer acted with gross negligence and did not take reasonable steps to keep its personalized security credentials safe.
- 24.1. the Payer acts fraudulently; or
Refunds
- The Payment Service Provider shall refund the amount of the Unauthorized Payment Transaction to the Payer and, where applicable, restore the debited Payment Account to the state it would have been in had the Unauthorized Payment Transaction not taken place.
- The Payment Service Provider shall provide a refund under paragraph (25) as soon as practicable and in any event no later than the end of the Business Day following the day on which it becomes aware of the Unauthorized Payment Transaction.
- Paragraphs (25), (26) and (30) do not apply where the Payment Service Provider has reasonable grounds to suspect fraudulent behavior by the Retail Payment Service User and notifies the Central Bank of those grounds in writing.
- When crediting a Payment Account under paragraph (30), a Payment Service Provider shall ensure that the date on which the amount of a Payment Transaction is credited to a Payee’s Payment Account is no later than the date on which the amount of the Unauthorized Payment Transaction was debited.
- Where an Unauthorized Payment Transaction was initiated through a Payment Initiation Service Provider, the Payment Service Provider providing Payment Account Issuance Services shall comply with paragraph (30). In addition, if the Payment Initiation Service Provider is liable for the Unauthorized Payment Transaction, it shall, on the request of the Payment Service Provider providing Payment Account Issuing Services, compensate the Payment Service Provider providing Payment Account Issuing Services immediately for the losses incurred or sums paid as a result of complying with paragraph (30), including the amount of the Unauthorized Payment Transaction.
- Other than in relation to the circumstances contemplated in paragraphs (25) to (29), on conclusion of an investigation by a Payment Service Provider into an error or Complaint, a Payment Service Provider shall pay any refund or monetary compensation due to a customer within (7) calendar days of such conclusion or instruction. In case of a delay in payment of any refund or compensation, the Payment Service Provider shall update the customer with the expected time for crediting the amount due, along with a justification for the delay.
- Payment Service Providers must be operated prudently and with competence in a manner that will not adversely affect the interests of the Retail Payment Service Users or potential Retail Payment Service Users. In addition, they must also observe and comply with the relevant regulatory requirements and standards on consumer protection of the Central Bank. For the avoidance of doubt, in case of discrepancies between this Regulation and the Central Bank’s requirements and standards on consumer protection, the respective provisions of this Regulation shall prevail.
Annex A
Information or documents that may be requested under this Regulation
- A copy of the Operating Rules of the LVPS.
- Details of the type of services offered by the LVPS.
- Details of the constitution, structure, nature of business, ownership and management of the LVPS, the SO and the SI.
- Details of the design and function and external system interfaces of the LVPS, including details specifying the point at which a Transfer Order takes effect as having been entered into the LVPS and of the point after which a Transfer Order may not be revoked by a Participant Person or any other party.
- A copy of the last three annual reports, if any, and the financial statements (with any auditor’s reports) for the current financial year of the LVPS, the SO and the SI.
- The basis for membership of or participation in the LVPS (i.e. admission criteria) and a list of the current members of or Participant Persons in the LVPS.
- Tariff information and schedule.
- Names of the SO and/or SI, if any, of the LVPS and whether the SO and/or SI are also Participant Persons in the LVPS under the Operating Rules of the system. Legal contracts or documents between the SO and the SI in relation to the LVPS.
- Details of the types, volume and values of Transfer Orders processed by the LVPS.
- Detailed business contingency plan.
- Name and contact details of the Person to whom questions relating to the designation of the LVPS should be directed.
For overseas systems, the following additional information may be required: -
- Name of each of the relevant regulators where the LVPS is regulated by one or more regulatory authorities not within the State jurisdiction.
- An outline of any laws and other regulatory requirements relating to the operations of the LVPS, if regulated by a regulatory authority not within the State jurisdiction.
- Evidence of the LVPS’ compliance with any applicable laws and regulatory requirements of a jurisdiction outside State, which may include comments from home supervisory authority on the LVPS’ compliance with any applicable laws and regulatory requirements of a jurisdiction outside State.
- A copy of the Operating Rules of the LVPS.
Article (15): Use of Agents and Branches
- Where a Payment Service Provider intends to provide Retail Payment Services through an Agent or branch, it must conduct an assessment of such arrangement and provide a report on an annual basis to the Central Bank of the following:
- 1.1. name and address of the Agent or branch;
- 1.2. assessment of the adequacy of the internal control mechanisms that will be used by the Agent in order to comply with AML/CTF requirements;
- 1.3. assessment of the Persons responsible for the Management of the Agent or branch, and evidence that they fulfil the fit and proper requirements specified by the Central Bank; and
- 1.4. the scope of Retail Payment Services for which the Agent or branch is mandated.
- 1.1. name and address of the Agent or branch;
- Payment Service Providers shall contractually ensure that Agents acting on their behalf disclose this fact to the Retail Payment Service Users.
- Payment Service Providers shall immediately notify the Central Bank of any change regarding the use of Agents or branches.
- Where a Payment Service Provider intends to provide Retail Payment Services through an Agent or branch, it must conduct an assessment of such arrangement and provide a report on an annual basis to the Central Bank of the following:
Annex B
Information on System Operator (SO) / Settlement Institution (SI)
- Name of clearing and settlement system to which the designated LVPS relates.
- Name of SO / SI.
- Legal form (body corporate, partnership, etc.).
- Country of incorporation or formation.
- Date of incorporation or formation.
- Registered office.
- Principal place of business.
- Contact details (names, physical and email addresses).
- Aspects of the management or operations of the system for which the entity is responsible.
- Organization chart of your company.
- Name of clearing and settlement system to which the designated LVPS relates.
Article (16): Outsourcing
- Payment Service Providers outsourcing services and processes to service providers, Agents or Group entities shall be obliged to contractually ensure that such third parties comply with the requirements of this Regulation, Level 2 Acts and other relevant laws.
- The outsourcing under paragraph (1) shall be subject to the prior approval of the Central Bank. Furthermore, Payment Service Providers shall provide details on all outsourcing under paragraph (1) in a report on an annual basis to the Central Bank.
- Payment Service Providers shall remain fully liable for any acts of any Agent, branch or service provider to which a Retail Payment Service has been outsourced.
- Payment Service Providers shall be responsible for ensuring and maintaining appropriate training and qualifications of their Agents.
- Payment Service Providers outsourcing services and processes to service providers, Agents or Group entities shall be obliged to contractually ensure that such third parties comply with the requirements of this Regulation, Level 2 Acts and other relevant laws.
Annex C
LVPS Turnover Information
- Aggregate value of Transfer Orders transferred, cleared or settled through the LVPS in a normal business day (in billions of the original currency transferred, cleared or settled).
- Average value of Transfer Orders transferred, cleared or settled through the LVPS in a normal business day (in thousands of the original currency transferred, cleared or settled).
- Number of Transfer Orders transferred, cleared or settled through the LVPS in a normal business day.
- Aggregate value of Transfer Orders transferred, cleared or settled through the LVPS in a normal business day (in billions of the original currency transferred, cleared or settled).
Article (17): Contractual Arrangements
Access to Payment Accounts
- Payment Service Providers providing Payment Account Issuance Services and/or Banks may agree to contract with Payment Service Providers providing Payment Initiation and Payment Account Information Services for the provision of access, direct or indirect, to the Payment Accounts held with them in order to allow such Payment Service Providers to provide Payment Initiation and Payment Account Information Services in an unhindered and efficient manner.
- The contractual arrangements under paragraph (1) shall:
- 2.1. have a sound legal basis and be legally enforceable;
- 2.2. clearly describe the rights and obligations of the counterparties;
- 2.3. clearly define the allocation of liability between the counterparties, including in cases of fraud, unauthorized access or Data Breach, in a manner that each counterparty takes responsibility for the respective parts of the Payment Transaction under its control;
- 2.4. specify the reasons for denying access to Payment Accounts related to unauthorized or fraudulent access by Payment Service Providers providing Payment Initiation and Payment Account Information Services; and
- 2.5. explicitly oblige the counterparties to comply with Article (13) on Technology Risk and Information Security.
- 2.1. have a sound legal basis and be legally enforceable;
- The choice of Payment Service Providers providing Payment Initiation and Payment Account Information Services shall be at the sole discretion of the Payment Service Providers providing Payment Account Issuance Services and/or Banks.
- Payment Service Providers providing Payment Initiation and Payment Account Information Services shall:
- 4.1. provide services only where based on the Retail Payment Service User’s explicit consent;
- 4.2. ensure that the personalized security credentials of the Retail Payment Service User are not, with the exception of the Retail Payment Service User and the issuer of the personalized security credentials, accessible to other parties and that they are transmitted through safe and efficient channels;
- 4.3. not request or store Sensitive Payment Data of the Retail Payment Service User;
- 4.4. not use, access or store any data for purposes other than for the provision of the Payment Initiation or Payment Account Information Services, as explicitly requested by the Retail Payment Service User; and
- 4.5. comply with the requirements of Article (13) on Technology Risk and Information Security where the Payer initiates an electronic Payment Transaction or carries out any action through a remote channel which may imply a risk of payment fraud or other abuses.
- 4.1. provide services only where based on the Retail Payment Service User’s explicit consent;
- In addition to the requirements set out in paragraph (4), Payment Service Providers providing Payment Account Information Services shall access only the information from designated Payment Accounts and associated Payment Transactions.
- In addition to the requirements set out in paragraph (4), Payment Service Providers providing Payment Initiation Services shall not modify the amount, the Payee or any other feature of the Payment Transaction.
- Payment Service Providers providing Payment Account Issuance Services and/or Banks may agree to contract with Payment Service Providers providing Payment Initiation and Payment Account Information Services for the provision of access, direct or indirect, to the Payment Accounts held with them in order to allow such Payment Service Providers to provide Payment Initiation and Payment Account Information Services in an unhindered and efficient manner.
Annex D
Information to be collected from SO/SI by the Central Bank
To be submitted before the end of the first year of designation
- Liquidity commitment or other financial commitment by SI for daily operation of LVPS.
- Current credit rating(s) of SI.
- Throughput guidelines (if changed) from SO/SI.
- Results of stress testing, if any (once the results are available) from SO.
- Fees and cost from SO, including: -
- Joining cost (breakdown into (i) entry/admission fee, (ii) basic system set-up costs (limit to those costs known to SO) and membership fee).
- Calculation basis of (i) admission fee and (ii) membership fee.
- Transaction tariff (breakdown by types) and how the tariff is determined (e.g. whether determined on a cost-recovery basis).
- Other fees of participating in the LVPS, if any.
- Joining cost (breakdown into (i) entry/admission fee, (ii) basic system set-up costs (limit to those costs known to SO) and membership fee).
- Outsourcing plan (if any) (for any outsourcing plan not yet implemented) from SO.
- Internal and/or external auditor’s report on various risk areas (if any) from SO and/or SI.
To be submitted if and when available by SO and/or SI
- Development plan and business forecast for the designated LVPS for the coming year, if available.
- Budgetary plan highlighting the resources devoted to system maintenance and development for the coming year, if available.
To be submitted within two weeks when available by SO and/or SI
- Audited financial statements and accounts of SO and/or SI, such as balance sheet, cash flow statement, profit and loss account for the latest financial year.
- Results of stress testing, if any (once the results are available).
- Internal and/or external auditor’s report on various risk areas (if any) if initiated by SO/SI.
To be submitted within two weeks when changes are made, highlighting the changes
- Current credit rating(s) by SI.
- Throughput guidelines (if changed) by SI.
- Fees and Cost by SO.
- Outsourcing plan (if any) (when new plan is available) by SO.
- Business continuity plan (if any, during the year).
- Organization chart and structure (if changed) Throughput guidelines (if changed) by SO and/or SI.
- Business continuity plan (if any, during the year) by SO and/or SI.
- LVPS specifications by SO and/or SI.
To be submitted as and when required by the Central Bank
- Internal and/or external auditor’s report on various risk areas as and when required by the Central Bank.
To be submitted on a yearly basis
- Liquidity commitment or other financial commitment by SI for daily operation of LVPS.
- Development plan and business forecast for the designated LVPS for the coming year, if available by SO and/or SI.
- Budgetary plan highlighting the resources devoted to system maintenance and development for the coming year, if available by SO and/or SI.
- Liquidity commitment or other financial commitment by SI for daily operation of LVPS.
Article (18): Card Schemes
Card Scheme License
- Card Schemes operating within the State shall obtain a License by the Central Bank prior to commencing operations.
- Applicants shall be subject to the procedure envisaged in the Central Bank’s Licensing Guidelines.
- The Central Bank shall determine whether to grant or refuse to grant a License to a Card Scheme Applicant and indicate this in writing to the Applicant within (90) calendar days from the receipt of the full set of documents and information requested under the Application.
- The Central Bank may grant a License under paragraph (1) with or without conditions or restrictions attached to it, or refuse to grant a License at its discretion.
- The Central Bank shall notify the Card Scheme of the decision taken under paragraph (3). In case of a refusal to grant a License, the Central Bank shall indicate the reasons for such refusal.
- The Central Bank reserves the sole right to issue Card Issuer (Bank) Identification Numbers (BIN) in accordance with ISO/IEC 7812, as may be amended or supplemented from time to time.
License Conditions
- The Central Bank shall grant a License to a Card Scheme under this Article (18) upon the fulfilment of the following conditions:
- 7.1. the Central Bank has been provided with all necessary documents and information as it may request, in the form and within the timeframe specified by it, to allow it to assess the adequacy, efficiency and soundness of a Card Scheme, including:
- 7.1.1. the business model and business strategy;
- 7.1.2. the corporate governance structure;
- 7.1.3. the Management contact details;
- 7.1.4. the ownership and Group structure;
- 7.1.5. the financial and operational resources; and
- 7.1.6. the description of key risks, including conduct of business and money laundering and terrorist financing risks;
- 7.1.1. the business model and business strategy;
- 7.2. the Management of the Card Scheme fulfil the fit and proper requirements specified by the Central Bank, including that each member of Management:
- 7.2.1. possesses the necessary knowledge, skills, and experience;
- 7.2.2. has a record of integrity and good repute;
- 7.2.3. has sufficient time to fully discharge the responsibilities under this Regulation and Level 2 Acts; and
- 7.2.4. has a record of financial soundness.
- 7.2.1. possesses the necessary knowledge, skills, and experience;
- 7.1. the Central Bank has been provided with all necessary documents and information as it may request, in the form and within the timeframe specified by it, to allow it to assess the adequacy, efficiency and soundness of a Card Scheme, including:
Reporting Requirements
- A Card Scheme that has been granted a License shall:
- 8.1. report to the Central Bank the information contained in Annex III on a quarterly basis;
- 8.2. provide additional information or become subject to more frequent reporting, as deemed necessary by the Central Bank; and
- 8.3. report immediately any changes that affect or are likely to affect its business model or financial viability, or which may otherwise be deemed to be material in nature such as significant increase or decrease in transaction volumes.
- 8.1. report to the Central Bank the information contained in Annex III on a quarterly basis;
Ongoing Requirements
Governance
- The Board and Management of a Card Scheme shall be responsible for ensuring that a licensed Card Scheme has an internal control framework that is adequate to establish a properly controlled operating environment for the conduct of its business, taking into account its risk profile.
- Management shall be responsible for developing an internal control framework that identifies, measures, monitors and controls all risks faced by the Card Scheme.
- Licensed Card Schemes shall have organizational structures that incorporate a “three lines of defense” approach comprising the business lines, the support and control functions and an independent internal audit function.
Compliance Function
- The Board shall be responsible for ensuring that a Card Scheme has an independent, permanent and effective compliance function to monitor and report on observance of all applicable laws, regulations and standards and on adherence by staff and members of the Board to legal requirements, proper codes of conduct and policy on conflicts of interest.
- The Card Payment Scheme shall have a Boardapproved compliance policy that is communicated to all staff specifying the purpose, standing and authority of the compliance function within the Card Scheme.
- Card Schemes shall establish appropriate policies, procedures and controls pertaining to the internal reporting by their Management and staff of suspicious transactions, including the provision of the necessary records and data, to the designated Anti-Money Laundering and Combating the Financing of Terrorism compliance officer for further analysis and reporting decisions. Card Schemes shall report transactions to the competent authority when there are suspicions, or reasonable grounds to suspect, that the proceeds are related to a crime, or to the attempt or intention to use funds or proceeds for the purpose of committing, concealing or benefitting from a crime.
Internal Audit Function
- The Board shall be responsible for ensuring that the Card Scheme has an independent, permanent and effective internal audit function commensurate with the size, nature of operations and complexity of its organization.
- The internal audit function shall provide independent assurance to the Board and Management on the quality and effectiveness of the Card Scheme’s internal controls, risk management, compliance, corporate governance, and the systems and processes created by the business units, support and control functions.
- The Card Scheme shall have an internal audit charter approved by the Board audit committee that articulates the purpose, standing and authority of the internal audit function within the Card Scheme.
Risk Management
- Card Schemes shall have an adequately resourced risk management function headed by a chief risk officer or equivalent. The function shall be independent of the management and decision-making of the Card Scheme’s risktaking functions. The risk management function shall include policies, procedures, systems and controls for monitoring and reporting risks, and to ensure that risk exposures are aligned with the entity’s strategy and business plan.
Risk Strategy
- Card Schemes shall have a clearly defined business strategy, risk appetite and defined corporate culture that has been approved by the Board and reviewed at least annually. Management shall ensure full compliance of this articulated strategy across all business lines and the Board will be ultimately responsible for such compliance.
Information Security
- A Card Scheme shall apply and meet at a minimum the Payment Card Industry Data Security Standard (‘PCI DSS’) and UAE Information Assurance Standards, as may be amended from time to time.
- A compliance report regarding the Card Scheme’s adherence to the standards referred to in paragraph (20) shall be presented to the Board at least annually as well as transmitted to the Central Bank.
- In the case of a Data Breach, the Card Scheme shall notify the Central Bank without undue delay and not later than (72) hours after having become aware of such Data Breach.
Disaster Recovery and Business Continuity Management
- Card Schemes shall have disaster recovery and business continuity plans in place to ensure their ability to operate on an ongoing basis and limit losses in the event of a severe business disruption. Such plans must be commensurate with the risk profile, nature, size and complexity of the Card Scheme’s business and structure and take into account different scenarios to which the Card Scheme may be vulnerable.
- Disaster recovery and business continuity plans shall ensure that critical business functions of the Card Scheme can be maintained and recovered in a timely manner to minimize the financial, legal, regulatory, reputational and other risks that may arise from a disruption.
- The Board shall ensure there is a periodic independent review of the Card Scheme’s disaster recovery and business continuity plans to ensure adequacy and consistency with current operations, risks and threats, recovery levels and priorities.
Risk Assessment
- Card Schemes shall regularly assess risks through the identification of new risks, measurement of known risks and prioritization of risks through thorough understanding of the business and the market.
Risk Mitigation
- Card Schemes shall mitigate risks through the implementation of:
- 27.1. risk mitigation programs and technologies;
- 27.2. the effective management of risk principles; operation with risk management in mind; and
- 27.3. outsourcing of risk functions that cannot be performed in-house.
- 27.1. risk mitigation programs and technologies;
Monitoring
- Card Schemes shall perform regular monitoring of all risks and mitigation programs on at least an annual basis to ensure the robustness of the risk management procedures and programs. Continuous monitoring reports, including dashboards, shall be presented to the Management and the Board to ensure that all levels of management are aware of the current risk situation, including potential fraud, in the Card Scheme.
Assurance
- Card Schemes shall give assurance to all stakeholders through external and internal audits.
Winding Down
- Where a Card Scheme intends to terminate its operation in the State, it shall obtain an approval from the Central Bank to this effect.
- A Card Scheme shall notify the Central Bank in advance of (3) months from the intended termination of its operations, and provide an orderly wind-down plan.
Supervisory Examinations
- The Central Bank may conduct periodic examinations of the operation of Card Schemes to ensure their financial soundness and compliance with the requirements of this Regulation and Level 2 Acts.
- Card Schemes shall provide the Central Bank with full and unrestricted access to their accounts, records and documents, and shall supply such information and facilities as may be required to conduct the examination referred to in paragraph (32).
Fees and Charges
- The Central Bank has the right to receive information on any fees and charges of Card Schemes and regulate such fees and charges as it considers appropriate.
- The Central Bank may publicly disclose the fees and charges of Card Schemes referred to in paragraph (34).
- Card Schemes operating within the State shall obtain a License by the Central Bank prior to commencing operations.
Article (19): Access to the Wages Protection System
Eligibility and Conditions
- Payment Service Providers are eligible to apply to the Central Bank to participate in and, be given access to the Wages Protection System. They shall be given access to the Wages Protection System subject to an approval granted by the Central Bank.
- To allow wages to be credited to an account that can store and maintain the funds, Payment Service Providers may engage with an SVF scheme or a Bank for the provision of such account. Payment Service Providers that apply for participation in and access to the Wages Protection System shall demonstrate, among other things, that they have stringent security measures put in place so as to minimize the risks to the Wages Protection System.
- Upon being given access to the Wages Protection System, Payment Service Providers shall be entitled to open WPS Payment Accounts.
- The requirements in this Article (19) are without prejudice to other requirements of this Regulation to which Payment Service Providers are subject.
Obligations
- Payment Service Providers that have been given access to the Wages Protection System under paragraph (1) shall:
- 5.1. organize marketing campaigns targeting the unbanked and underbanked segments with the objective of educating WPS Payment Account Holders on the benefits and risks associated with the services provided by the Payment Service Providers;
- 5.2. conduct workshops with the objective of raising awareness of Employers on the salary information file (SIF) format to be submitted, penalties and related procedures and regulatory requirements;
- 5.3. ensure that they provide WPS Payment Account Holders with a transaction statement in a timely manner;
- 5.4. execute the payments to WPS Payment Account Holders in a timely manner and acknowledge such execution in accordance with the WPS Rulebook;
- 5.5. not hold WPS Payment Account Holders liable for any fraudulent or Unauthorized Payment Transactions, and shall guarantee the full amount of funds; and
- 5.6. provide a dedicated Retail Payment Service User service and complaints team for WPS Payment Account Holders that are separate from the equivalent teams servicing other Retail Payment Services that may be provided by the Payment Service Providers.
- 5.1. organize marketing campaigns targeting the unbanked and underbanked segments with the objective of educating WPS Payment Account Holders on the benefits and risks associated with the services provided by the Payment Service Providers;
- Payment Service Providers that fail to comply with the requirements of paragraph (5.4) shall be subject to the penalties specified in the WPS Rulebook.
- The Central Bank may request from the Payment Service Providers that have been given access to the Wages Protection System under paragraph (1) to:
- 7.1. prepare and provide quarterly reports on the average Payment Transactions value per WPS Payment Account Holder; and
- 7.2. prepare and provide quarterly reports on the number of WPS Payment Account Holders being serviced.
- 7.1. prepare and provide quarterly reports on the average Payment Transactions value per WPS Payment Account Holder; and
- Payment Service Providers are eligible to apply to the Central Bank to participate in and, be given access to the Wages Protection System. They shall be given access to the Wages Protection System subject to an approval granted by the Central Bank.
Article (20): Enforcement and Sanctions
Violation of any provision of this Regulation or committing any of the violations provided for under the Central Bank Law may subject the Payment Service Provider or Card Scheme to administrative and financial sanctions and penalties as deemed appropriate by the Central Bank.
Article (21): Transition Period
A one-year transitional period will commence on the date this Regulation comes into force. The Central Bank may order the cessation of provision of the Retail Payment Services or the operations of the Card Scheme if the Payment Service Provider or the Card Scheme concerned has not obtained the relevant License from the Central Bank before the end of the transition period. The Central Bank may extend the transition period for the Applicant at its own discretion.
Article (22): Interpretation of Regulation
The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
Article (23): Publication & Application
1. This Regulation shall be published in the Official Gazette in both Arabic and English and shall come into effect one month from the date of publication. In case of any discrepancy between the Arabic and the English, the Arabic version will prevail.
Annex I: Retail Payment Services
- Payment Account Issuance Service
- Payment Instrument Issuance Service
- Merchant Acquiring Service
- Payment Aggregation Service
- Domestic Fund Transfer Service
- Cross-border Fund Transfer Service
- Payment Token Service
- Payment Initiation Service
- Payment Account Information Service
- Payment Account Issuance Service
Annex II: Guidance on the Best Practices for Technology Risk and Information Security
The following best practices will enable Payment Service Providers to operate adaptive and responsive cyber resilience processes. Payment Service Providers are encouraged to discuss and consider their application to improve their technology risk, information security and cyber resilience preparedness.
Technology Risk
An incident management framework with sufficient management oversight to ensure effective incident response and management capability to deal with significant incidents properly should include:
- (i) timely reporting to the Central Bank of any confirmed technology-related fraud cases or major security breaches, including cyberattacks, cases of prolonged disruption of service and systemic incidents where Retail Payment Service Users suffer from monetary loss or Retail Payment Service Users’ interests are being affected (e.g. data leakage); and
- (ii) a communication strategy to address the concerns any stakeholders may have arising from the incidents and restore the reputational damage that the incidents may cause.
Change Management
Payment Service Providers whose monthly average value of Payment Transactions amounts to (10) million Dirham or above are encouraged to:
- (i) develop a formal change management process to ensure the integrity and reliability of the production environment and that the changes to application systems, system software (e.g. operating systems and utilities), hardware, network systems and other IT facilities and equipment, are proper and do not have any undesirable impact on the production environment. Formal procedures for managing emergency changes (including the record keeping and endorsement arrangement) should also be established to enable unforeseen problems to be addressed in a timely and controlled manner; and
- (ii) adequately and accurately document control procedures and baseline security requirements, including all configurations and settings of operating systems, system software, databases, servers and network devices. They are also expected to perform periodic reviews on the compliance of the security settings with the baseline standards.
Project Life Cycle
A full project life cycle methodology governing the process of developing, implementing and maintaining major computer should be established.
Where a software package is acquired from vendors, a formal software package acquisition process should be established to manage risks associated with acquisitions, such as breach of software license agreement or patent infringement.
Quality assurance reviews of major technology-related projects by an independent party, with the assistance of the legal and compliance functions should be conducted.
IT Governance
A set of IT control policies that fits the business model and technology applications should be implemented. The IT control policies which establish the ground rules for IT controls should be formally approved by Management and properly implemented among IT functions and business units. Processes used to verify compliance with IT control policies and the process for seeking appropriate approval by Management for dispensation from IT control policies are also be clearly specified, and consequences associated with any failure to adhere to these processes should be effected.
Security Requirements
Guidelines and standards for software development are adopted with reference to industry generally accepted practices on secure development. Source code reviews (e.g. peer review and automated analysis review), which could be risk-based, as part of a software quality assurance process should be conducted.
Formal testing and acceptance processes should be conducted to ensure that only properly tested and approved systems are promoted to the production environment. The scope of tests covers business logic, security controls and system performance under various stress-load scenarios and recovery conditions.
Segregated environments for development, testing and production purposes should be maintained. System testing and user acceptance testing (UAT) should be properly carried out in the testing environment. Production data should not be used in development or acceptance testing unless the data has been desensitized and prior approval from the information owner has been obtained.
A segregation of duties among IT teams should be introduced. Developers should not be permitted to access to production libraries and promote programming code into the production environment. If automated tools are used for the promotion of programming code, adequate monitoring, reviews and checks by independent teams should be done. Vendor accesses to the UAT environment, if necessary, should be closely monitored.
An inventory of end-user developed applications and where necessary, control practices and responsibilities with respect to end-user computing to cover areas such as ownership, development standards, data security, documentation, data/file storage and backup, system recovery, audit responsibilities and training should be established.
A problem management process to identify, classify, prioritize and address all IT problems in a timely manner should be established. It should perform a trend analysis of past incidents regularly to facilitate the identification and prevention of similar problems.
Network and Infrastructure Management
Network security devices such as firewalls at critical junctures of its IT infrastructure should be installed to secure the connection to untrusted external networks, such as the Internet and connections with third parties.
Where mobile devices are provided to employees, policies and procedures covering, among others, requisition, authentication, hardening, encryption, data backup and retention should be established.
Adequate measures to maintain appropriate segregation of databases for different purposes to prevent unauthorized or unintended access or retrieval and robust access controls should be enforced to ensure the confidentiality and integrity of the databases. In respect of any Personal Data of Retail Payment Service Users, including Merchants, the relevant data protection laws as well as any relevant codes of practice, guidelines or best practice issued by the Central Bank or any other relevant authorities should be assessed from time to time.
Access to the information and application systems should be restricted by an adequate authentication mechanism associated with access control rules. A role-based access control framework should be adopted and access rights should be granted on a need-to-have basis.
Cyber Security Risk
The trends in cyber threats should be considered, including subscribing to quality cyber threat intelligence services, which are relevant to the provision of Retail Payment Services to enhance ability to precisely respond to new type of threats in a timely manner. The Payment Service Provider may also seek opportunities to collaborate with other organizations to share and gather cyber threat intelligence with the aim of facilitating the Retail Payment Services industry to better prepare and manage cyber security risks.
Monitoring or surveillance systems to ensure being alerted to any suspicious or malicious system activities such as multiple sessions of same account from different geographic locations should be carried out. Real-time monitoring of cyber events for critical systems should be performed to facilitate the prompt detection of anomalous activities.
Close attention should be paid to evolving risks related to accessing critical IT infrastructure and appropriate measures are accordingly taken.
Payment Acceptance Devices
Retail Payment Service User devices should be assumed to be exposed to security vulnerabilities and appropriate measures when designing, developing and maintaining Retail Payment Services should be taken. Security measures to guard against different compromising situations, including unauthorized device access, malware or virus attack, compromised or unsecure status of mobile device and unauthorized mobile applications should be taken.
Where Merchants use mobile devices to accept a Payment Service Provider’s Retail Payment Services, additional security measures should be implemented to safeguard the mobile payment acceptance solution, including the detection of abnormal activities and logging them in reports, and the provision of Merchant identification for Retail Payment Service Users to validate identity.
Retail Payment Service User Authentication
Retail Payment Service User authentication based on a multi-factor authentication by combining any two or more of the following three factors is adopted:
- (i) verification information specified by Retail Payment Service User knows (e.g. user IDs and passwords);
- (ii) verification information a Retail Payment Service User has provided or possesses (e.g. one-time passwords generated by a security token or a Payment Service Provider’s security systems); and
- (iii) physical verification information belonging to a Retail Payment Service User (e.g. retina, fingerprint or voice recognition).
If a password (including a personal identification number) is used as one factor of authentication, adequate controls related to the strength of the password (e.g. minimum password length) should be put in place.
Login attempts and session management
Robust log files allowing retrieval of historical data including a full audit trail of additions, modifications or deletions of transactions are provided. Access to such tools, including privileged responsibilities, should only be available to authorized personnel and is appropriately logged.
Retail Payment Service Users should be provided with channels to check their Past Payment Transactions.
Fraud Detection Systems
Payment Transaction monitoring mechanisms designed to prevent, detect and block fraudulent Payment Transactions should be operated by Payment Service Providers providing Payment Token Services and Payment Service Providers whose monthly average value of Payment Transactions amounts to ten (10) million Dirhams or above. Suspicious or high-risk transactions are subject to a specific screening, filtration and evaluation procedure.
- (i) timely reporting to the Central Bank of any confirmed technology-related fraud cases or major security breaches, including cyberattacks, cases of prolonged disruption of service and systemic incidents where Retail Payment Service Users suffer from monetary loss or Retail Payment Service Users’ interests are being affected (e.g. data leakage); and
Annex III: Information to be Reported by Card Schemes in English and Arabic
I. ATM data:
Field Name Max Size Type Field Details Primary Account Number (PAN) 16-19 Numeric PAN is a series of digits used to identify a Retail Payment Service User account or relationship
Transaction Code 2 Numeric Transaction Code - 31 (Balance Enquiry), 01 (Cash Withdrawal).
Transaction Amount 12 Numeric Transaction amount gives the value of the funds requested by the cardholder in the local currency of the acquirer or source location of the transaction.
Transaction Currency Code 3 Alphabet (or) Numeric Identifies the local currency of the acquirer or source location of the transaction. See ISO 4217.
Transmission Date and Time 10 Numeric MM/DD/hh/mm/ss format
The date used is the current calendar day in Greenwich Mean Time (GMT) that the transaction occurred (not Business Day)
Systems Trace Audit Number 6 Numeric Contains a number assigned by the transaction acquirer to identify uniquely a transaction. The trace number remains unchanged for all messages throughout the life of the transaction.
Merchant’s Type 4 Numeric Contains the classification of the merchant's type (ATM/web/etc) of business product or service.
Acquiring Institution Country Code 3 Numeric Contains the code of the country where the acquiring institution is located (see ISO 3166)
Point of Service Entry Mode 3 Numeric Contains two numeric to indicate the method by which the primary account number was entered into the system and one numeric to indicate the PIN entry capabilities.
Acquiring Institution Identification Component 11 Numeric Contains a code identifying the acquiring institution (e.g. merchant bank) or its agent.
Card Acceptor Name/Location 40 Alpha Numeric Special Char Contains the name and location of the card acceptor (i.e. the merchant or ATM).
Card Acceptor Terminal Identification 15 Alpha Numeric Special Char Contains a unique code identifying a terminal at the card acceptor location.
Authorization Identification Response 6 Alpha Numeric Contains the response identification assigned by the authorizing institution.
This field is often referred to as "auth-code".
Response Code 2 Alpha Numeric Contains a code, which defines the disposition of a message.
II. PoS data:
Field Name Max Size Type Field Details Primary Account Number (PAN) 16-19 Numeric PAN is a series of digits used to identify a Retail Payment Service User account or relationship
Transaction Code 2 Numeric Transaction Code - 00 (Purchase/Sale), 20 (Refund), 31 (Balance Enquiry).
Transaction Amount 12 Numeric Amount of funds requested by the cardholder.
Transaction Currency Code 3 Numeric Code that indicates the local currency of the acquirer or source location of the transaction. This defines the currency that applies to the transaction amount.
Transmission Date and Time 10 Numeric MMDDhhmmss format
Generated and sent by the message initiator. It is expressed in GMT.
Systems Trace Audit Number 6 Numeric Unique identifier assigned to the transaction by the message sender. It remains unchanged for all messages within a transaction between the two parties. This is used to provide an audit trail for every message sent by the acquirer for a given business date.
Merchant Category Code 4 Numeric Contains the classification of the merchant's type of business product or service.
Acquiring Institution Country Code 3 Numeric Contains the code of the country where the acquiring institution is located (see ISO 3166)
Point of Service Entry Mode 3 Numeric Contains two numeric to indicate the method by which the primary account number was entered into the system and one numeric to indicate the PIN entry capabilities.
POS Condition Code 2 Numeric Contains an identification of the condition under which the transaction takes place at the point of service.
00 - Normal Presentment
59 - eCommerce
Authorization Identification Response 6 Alpha Numeric Contains the response identification assigned by the authorizing institution.
This field is often referred to as "auth-code".
Card Acceptor Terminal ID 16 Alpha Numeric Special Char Unique code identifying the terminals at the acquirer location
Card Acceptor Identification Code 15 Alpha Numeric Special Char Unique code identifying the card acceptor
Card Acceptor Name and Location 40 Alpha Numeric Special Char Used to hold the name and location of the card acceptor as known to the cardholder.
Response Code 2 Alpha Numeric Contains a code, which defines the disposition of a message.
III. Fraud data:
Field Name Max Size Type Field Details Primary Account Number (PAN) 16-19 Numeric PAN is a series of digits used to identify a Retail Payment Service User account or relationship
Transaction Code 2 Numeric Transaction Code - 00 (Purchase/Sale), 20 (Refund), 31 (Balance Enquiry).
Transaction Amount 12 Numeric Amount of funds requested by the cardholder.
Transaction Currency Code 3 Numeric Code that indicates the local currency of the acquirer or source location of the transaction. This defines the currency that applies to the transaction amount.
Transmission Date and Time 10 Numeric MMDDhhmmss format
Generated and sent by the message initiator. It is expressed in GMT.
Systems Trace Audit Number 6 Numeric Unique identifier assigned to the transaction by the message sender. It remains unchanged for all messages within a transaction between the two parties. This is used to provide an audit trail for every message sent by the acquirer for a given business date.
Merchant Category Code 4 Numeric Contains the classification of the merchant's type of business product or service.
Acquiring Institution Country Code 3 Numeric Contains the code of the country where the acquiring institution is located (see ISO 3166)
Point of Service Entry Mode 3 Numeric Contains two numeric to indicate the method by which the primary account number was entered into the system and one numeric to indicate the PIN entry capabilities.
POS Condition Code 2 Numeric Contains an identification of the condition under which the transaction takes place at the point of service.
00 - Normal Presentment
59 - eCommerce
Authorization Identification Response 6 Alpha Numeric Contains the response identification assigned by the authorizing institution.
This field is often referred to as "auth-code".
Card Acceptor Terminal ID 16 Alpha Numeric Special Char Unique code identifying the terminals at the acquirer location
Card Acceptor Identification Code 15 Alpha Numeric Special Char Unique code identifying the card acceptor
Card Acceptor Name and Location 40 Alpha Numeric Special Char Used to hold the name and location of the card acceptor as known to the cardholder.
Response Code 2 Alpha Numeric Contains a code, which defines the disposition of a message.
Mortgage loans & Personal loans
Bank Loans & Other Services Offered to Individual Customers
Regulation No. 29/2011 Regarding Bank Loans & Other Services Offered to Individual Customers
C 29/2011 Effective from 23/3/2011This regulation has been amended and clarified by the following notices respectively (E 28/02/2011), (N 2705/2012), (N 4501/2011), (N 13/1187/2013), (N 22/2017), (N 193/2018), (N 3986/2019), (N 5060/2019) and (N 2535/2022). You are viewing the latest version. Please find the PDF of the previous version on the table below.version 2 (consolidated as of 24/06/2022) pdf download version 1 (effective from 23/03/2011) pdf download Introduction
Following review of reports on loans and other services offered to individual customers, and banks' responses to the questionnaire previously sent, titled "Personal Consumer Loans", and pursuant to provisions of article nos. (5), (18), (94) and (96) of Union Law No (10) of 1980, Regarding the Central Bank, the Monetary System & Organization of Banking, the Central Bank has decided that all banks must abide by the provisions of these regulations, at all times.
Objective
The objective of these regulations is to determine the relationship between banks (conventional and Islamic) and finance companies on the one hand, and their individual customers on the other, in a more transparent manner, so as to boost confidence in banks and finance companies and enhance credibility of the banking system.
Article (1) Definitions
a) Bank Transfer: Transferring funds electronically from one account to another, whether inside the UAE or to an account abroad.
b) Bank's Cheque: A manager's cheque, or a cheque where the bank is the drawer and the beneficiary is an individual, an establishment, a commercial company or a government institution, inside or outside the UAE.
c) Bank Guarantees: Guarantees issued by banks on behalf of their customers (including retail customers), which are usually payable upon first demand by the beneficiary.
d) Debit Cards: Cards similar to credit cards, except that purchases and withdrawals charged to it are immediately deductible from the account.
e) Prepaid Cards: Cards filled with value, where purchases and withdrawals are deducted from the stored value until depleted (or fully exhausted).
f) Top-Up Loan: An additional loan obtained by the borrower from the lending bank or finance company, prior to full repayment of the outstanding loan.
g) Commissions: Rates charged against particular banking services rendered by banks.
h) Fees: Rates charged against particular banking services, commitments or obligations.
i) Deductions: deductions or debits to bank accounts against banking services.
j) Deductible Charges: Charges to accounts against banking services.
Article (2) Personal Loan
a) Personal Loan: Is "a loan that is given to individual customers, where repayments are made out of salary and end of service indemnity and/or any other verifiable regular income from a well-defined source".
b) Personal Loan's Limit: Amount of the personal consumer loan has been set at (20) twenty times the salary or the total income of the borrower, and banks and finance companies must make sure that this limit is not exceeded.
c) Repayment Period: The repayment period for this loan must not exceed (48) months.
d) In order to ensure that the monthly installments deducted for repayment of this loan and resulting interest are kept in a reasonable proportion to the customer’s income, the deductions from his salary and/or regular income must not exceed the limits specified under Article (7) of these Regulations.
e) Loans extended to sole proprietorship firms and companies, secured by salary of the owner or salaries of the partners shall be treated the same way this loan is treated, and shall be subject to the same terms and conditions.
f) This loan shall be extended as per an application by the customer to be approved by the bank or the finance company, and it should be drafted in the manner set out in Article (12) hereof.
Clarifications and Guidelines (Notice No. 2901/2011)- These regulations apply to personal facilities viz. loans, overdrafts, car loans and credit cards extended to individuals which are repayable from salary, end of service indemnity and/ or other verifiable regular income from a well defined source.
- It should be ensured that the borrowers’ salary and end of service benefits are properly ascertained from the employer. If the facility is partly or fully given against other income, it should be from a well defined source and its full details should be obtained.
- In case of borrowers with heavy personal commitments and lower disposable income or uncertain employment/ job prospects, banks may not allow facilities up to the upper limit of 20 times salary and/ or the total income, repayable within 48 months despite meeting the specified criteria.
- .For sound loan decisions, banks should have clear policy guidelines on issues which have direct bearing on the quality of risk and repayment of the loan.
- If a customer avails for a lower amount than his eligibility or there is significant increase in his income level in subsequent months due to promotion etc, banks may reassess his eligibility after proper verification. In such a case, either existing loan is enhanced or a new loan is set up (without disturbing the existing loan).
- If other income is main or supplementary source of repayment, it should be ensured that such income is from a known regular source, the borrower has produced documentary evidence of such income.
- Besides personal facilities against salary and other income as above, banks may extend loans and overdrafts against lien over fixed deposits held with them.
Article (3) Car Loan
a) Car Loan: Is a loan extended by the bank or the finance company to its customer for the purpose of purchasing a private car.
b) Car loan shall be treated as separate from the personal consumer loan, and should not exceed (80%) eighty percent of the value of the financed vehicle.
c) Repayment Period: The maximum period for repayment of the loan shall be (60) months.
d) Security: This loan should be secured by a mortgage over the car.
e) Car loans extended to sole proprietorship firms and companies, secured by salary of the owner or salaries of the partners shall be treated the same way this loan is treated, and shall be subject to the same terms and conditions.
f) This loan shall be extended as per an application by the customer and approved by the bank or the finance company, and it should be drafted in the manner set out in Article (12) of these Regulations.
Clarifications and Guidelines (Notice No. 2901/2011)- Banks may finance passenger new and used cars to the extent of 80% of their value. Financing of commercial vehicles is outside the purview of these regulations unless repayment of the loan is from the salary of the customer and other laid down criteria are satisfied.
- Financing of operating leases to individuals would not be considered as car finance and would not fall within these regulations.
- Car loans may be allowed in addition to the personal loan as above but within the 50% of gross salary and any regular income as explained in Article (7).
Article (4) Overdraft Facilities
a) Overdrafts: Are "facilities linked to customers accounts, and are provided by banks for payment on their behalf, in advance. This usually results in a negative balance in the customers' accounts, which would require deposit of funds to cover that balance plus resulting interest and deductions".
b) Overdraft facilities extended to sole proprietorship firms and companies, secured by salary of the owner or salaries of the partners shall be treated the same way these facilities are treated, and shall be subject to the same terms and conditions
c) To obtain such facilities, there should be pre-arrangements between the customer and the bank. The customer must submit his application, which shows the purpose of the facilities, the expected repayment period and the sources of repayment, in accordance with the form set out in Article (12) of these Regulations.
Clarifications and Guidelines (Notice No. 2901/2011)- Overdrafts limits will be counted within 20 times salary as specified for the personal loans under Article (2) above
- Islamic banks may allow overdraft facilities by whatever name described in accordance with Shariaah principles, without violating the upper limits and other requirements of these regulations.
Article (5) Credit Cards
a) Credit Cards: Are "Plastic cards linked to an electronic network, containing details and credit limit of the card holder. Value of a customer's purchases and cash withdrawals are paid on his behalf by the issuing bank or the finance company, and the customer pays the value at the beginning of the month following the transactions' month, or by installments as per agreement with the issuing bank or finance company, after end of the period allowed for full payment of the balance.
b) Credit cards shall be issued to customers of the bank or the finance company, and may be issued to non-customers, in which case customer statistical data, as residents or non-residents, must be recorded separately.
c) Banks and finance companies issuing such cards must abide by the following:
1. Provide these cards to persons whose annual income equal or exceeds AED 60,000.
2. These cards may be provided against a pledged deposit of value not less than AED 60,000.
d) Banks or finance companies should provide their credit card customers with a monthly statement of expenses, showing values of purchases and cash withdrawals, and they should immediately investigate if a customer challenges any expense item.
e) Credit card facilities for the unpaid balances of these cards provided to sole proprietorship firms and companies and secured by salary of the owner or salaries of the partners shall be treated the same way these facilities are treated, and shall be subject to the same terms and conditions.
f) Provisions of the agreement for providing credit cards, signed by the customer, should be in accordance with the form set forth in Article (12) of these Regulations.
Clarifications and Guidelines (Notice No. 2901/2011)- In order to ensure that credit cards are issued to creditworthy individuals, a mandatory minimum income level of AED 60,000 per annum has been stipulated. Banks may fix the limits within the policy as stated in this regulation.
- Those not meeting the above income criteria are required to place a pledged deposit of not less than AED 60,000 with the bank for issuance of credit card. However such persons may be permitted credit facility besides credit card provided aggregate of credit facility and credit card limit do not exceed 50% of the pledged deposit.
- Credit card limit is allowed as additional facility but repayment of outstandings must remain within 50% of gross salary and any regular income as explained in Article (7).
- Banks may encourage greater use of debit cards for the customers who are not found to be eligible for issuance of credit card.
- If the cards have been issued to non-customers, banks should compile statistical data separately for residents and non-residents and review them from time to time.
- Banks will take particular care in respect of credit cards issued to non-residents.
Article (6) Interest
Computation of Interest
a) Each bank or finance company must calculate the interest rate charged for the loans mentioned under article nos. (2) and (3) and overdraft facilities (Article- 4 in case of banks only) as well as unpaid credit card balances (Article -5), in accordance with the following formula:
b) All banks and finance companies must declare their respective interest rates on loans, overdraft balances (In case of banks only), and balances due for credit cards within the table. The rate shall be determined on basis of the reducing balance of the loan on annual basis and included in the display board mentioned in Article (11) of these Regulations.
c) "Interest Amount" on loans and overdraft balances shall be determined on basis of the formula mentioned under (a) above.
d) Deduction of a ratio of the loan in advance, as the payable interest amount is prohibited, the formula mentioned under (a) above should be used to calculate the first interest amount, and then interest amount shall be calculated on the reducing balance of the loan by using the following simple equation:
e) Banks and finance companies must arrive at the "Interest Amount" and deduct it from the agreed monthly installment, then use the net amount to reduce the loan balance and reach "the new balance of the loan at the beginning of the month" which would, in turn, be used in the calculation process at the end of the following month.
f) With regard to calculation of interest amount on credit cards due balances, these shall only be calculated for the outstanding balance after the maturity date for its full payment; i.e., in the month following the month on which the purchases and withdrawals have occurred. Interest amount must then be calculated as per the equation mentioned under (a) above and in accordance with the rates declared on the display board mentioned under Article (11) of these Regulations.
g) A Bank or a finance company shall determine the penalty rate in the event of full or partial prepayment before maturity date, or in case of a top- up loan, however, a top- up loan, should not be granted unless the original loan was repaid, without default, for a period not less than one year, and in this case the rate shall be declared in the table mentioned in Annex-2
Clarifications and Guidelines (Notice No. 2901/2011)- Method of interest calculation has not been changed from the earlier Circular No 12/93. Banks should continue to follow reducing balance method, by taking a year of 365 days. However they must ensure that effective interest rate on per annum basis is disclosed to the customer, displayed on the Board, it is used for calculation and specified in the loan documentation.
- .While reducing balance method of interest calculation will be followed on personal and car loans, average daily outstanding balances will form the basis for interest calculation in all cases.
- In case of credit cards, the banks may continue to follow the global practice where no interest/ finance charges are levied on the outstanding balance (excluding cash advance transactions) when the new balance outstanding shown in the statement is paid in full by the Payment Due Date. Finance/ interest charges on cash advance may be applied from the transaction date till final repayment.
- Within the above broad framework, Islamic banks may vary display of interest rates or use appropriate terminology as permitted under the Shariaah.
- Any bank advertising or propagating ‘Flat’ interest rate must invariably state the equivalent effective rate side by side.
Article (7) Repayment Installments
a) Deductions from salary or regular income of any borrower, for all types of loans extended by banks and finance companies together, including, but not necessarily restricted to, car and private housing loans, overdraft facilities, and credit cards facilities, must not exceed 50% fifty percent of his gross salary, and any regular income from a defined and specific source at any time.
b) Should a loan or a banking facility's repayment period extends to the retirement age, banks and finance companies must schedule reduction of these loans or facilities in such way as to allow deduction of only 30% of the income (or pension salary).
c) Banks and finance companies may only take from the customer the number of postdated cheques covering the installments, and of value not exceeding 120% of value of the loan or the debit balance.
Clarifications and Guidelines (Notice No. 2901/2011)- All the lenders are obliged to carry out proper due diligence to ascertain the applicants’ liabilities and income sources so that total installments including payments on account of credit card do not exceed 50% of their gross salary and other regular income.
- Personal loans will be setup for a maximum tenor of 48 months. However if a borrower retires before full repayment, his loan will be restructured from the date of retirement so that his total repayments do not exceed 30% of income (or pension salary).
- Existing loans will continue in accordance with the present arrangement and documentation. However no top ups, deferrals or rescheduling will be permitted beyond eligibility in terms of salary multiplier, tenor and repayment percentage.
- Banks should formulate specific policy on top ups and rescheduling in order to restrict their frequency. It should be ensured that there is no ‘ever greening’ of loans to disguise problem or delinquent loans.
- In case of Islamic banks, they have to ensure that in case of prepayment, adequate rebate is allowed to a customer so that final charge to him does not exceed the level given in Annexure 2 to the Circular.
Banks are permitted to defer up to two instalments in a year at their discretion. (NOTICE NO. 4501/2011)
Article (8) Armed Forces Staff Loans
In the case of army personnel, the conditions detailed in our Notice No. 1850/2004 dated 14/06/2004 shall continue to apply, but with the following amendments:
a) The value of installments deducted by the bank (or the finance company) for all types of loans and facilities (personal- commercial- housing – car loan- credit cards and any other loans or facilities) shall not exceed 50% of the borrower's gross salary.
b) Military ID cards should not be taken, nor photocopied. A certificate issued by the Armed Forces stating gross salary, period of service and that the applicant is still holding his job should suffice.
c) In case a lending bank or finance company fails to abide with the above, the Armed Forces shall transfer the salary of the concerned Armed Forces staff to any other bank (or finance company) without referring to the bank that extended the loans or facilities.
Article (9) Bank Accounts & Related Commissions, Fees and Charges
a) Bank Accounts are: current accounts, savings accounts, call accounts and the like, as well as accounts set-up for specific purposes.
b) Commercial banks may open all types of accounts for their retail customers, but in such cases, they must abide by the standard agreement mentioned under Article (12) of these Regulations. In case a customer requested closing of the account and termination of the business relationship with the bank, the bank should do that without imposing a penalty if the account opening date goes back to more than one year. In all cases, an account must be closed and an appropriate certificate must be issued within, maximum, seven days (7) from date of submission of the application.
c) Banks may set a minimum credit balance for each account, and impose charges if such minimum was not maintained, as specified in Article (11) of this regulation.
d) None of the opened accounts can be considered "dormant" if the customer's address is known or if the customer is present and has other active accounts with the bank. Accounts are classified as dormant only in accordance with the provisions of these regulations issued by the Central Bank in this regard.
e) Banks may issue ATM cards, or debit cards linked to any type of these accounts. They may also charge fees for issuance of new cards, replacement of lost cards or renewal of expired cards. However, they must declare these fees in the manner specified in Article (11) of these Regulations.
Clarifications and Guidelines (Notice No. 2901/2011)- Banks may continue with their present practices and internal guidelines to control and monitor dormant accounts. However in no case they should transfer the balance of such accounts to their profit and loss account.
- Central Bank is in the process of issuing suitable guidelines in respect of dormant accounts. In the interim, banks may continue to comply with Notice No 24/2000 in respect of dormant accounts and take necessary precautions for operating such accounts.
Article (10) Personal Banking Services & the Fees and Commissions Charged on them
a) Personal Banking Services: are bank transfers, issuance of bank cheques (or manager's cheques) issuance of bank guarantees, opening of documentary credit, discount of cheques of local and foreign banks, issuance of balance certificates, issuance of indebtedness certificates and the like.
b) All banks and finance companies (finance companies are not permitted to open current, savings or call accounts to retail customers or provide services and facilities relating to such accounts) may provide the personal banking services mentioned in (a) above and collect related commissions and fees, or deduct such fees from the account, however they should declare them in the manner specified in Article (11) of these Regulations.
Clarifications and Guidelines (Notice No. 2901/2011)- Relevant fees, charges and commissions applicable to personal customers have been specified in the Appendices to the Circular. Banks are not allowed to levy any other commissions, fees, charges or fines without Central Bank’s written approval. Banks are however free to reduce or exempt their customers from payment of certain fees and charges at their discretion.
- Loans and insurance are separate products. Hence it should be a customer’s choice to select either to pay them together over the period of loan or to pay upfront. Banks should however explain to the customer properly and obtain his concurrence before charging him for the insurance.
- List of charges and commissions apply to personal loans, car loans and personal overdrafts. Banks may continue to levy charges and commissions on credit cards as hitherto as no change has been proposed in the regulations.
- If there are other important fees and charges applicable to certain segment of customers but left out in the Appendices, these may be submitted for consideration of the Central Bank.
Article (11) Interest Rates, Commissions and Banking Service Charges
a) Each bank or finance company shall determine the interest rates pertaining to personal loans and car loans (must include insurance and expressed in one figure) along with overdraft balances and unpaid credit cards balances and include them in the table shown in Annex-1 of these Regulations. Copy of this table must be sent for publication by the Central Bank.
b) Fees, commissions, deductions and charges on loans, overdraft balances and unpaid credit card balances and those charged on retail banking services, shall be in accordance with the limits prescribed in the table shown in Annex-2 of these Regulations. Banks and finance companies may not impose any commissions, fees, charges or fines other than those mentioned in the said table without Central Bank's written approval.
c) Any Fees/commissions on purchase/sale of currency notes, Travelers Cheques, Demand Drafts, and Telegraphic Transfers for major countries must also be clearly written in Arabic and English on a board of an appropriate size to be fixed next to the Foreign Exchange Counter in the banking hall at banks’ branches, as shown in Annex-3 of these Regulations.
d) The Central Bank shall annually review fees, commissions and charges imposed as per table No-(2) attached to these regulations.
Clarifications and Guidelines (Notice No. 2901/2011)- Relevant fees, charges and commissions applicable to personal customers have been specified in the Appendices to the Circular. Banks are not allowed to levy any other commissions, fees, charges or fines without Central Bank’s written approval. Banks are however free to reduce or exempt their customers from payment of certain fees and charges at their discretion.
- Loans and insurance are separate products. Hence it should be a customer’s choice to select either to pay them together over the period of loan or to pay upfront. Banks should however explain to the customer properly and obtain his concurrence before charging him for the insurance.
- List of charges and commissions apply to personal loans, car loans and personal overdrafts. Banks may continue to levy charges and commissions on credit cards as hitherto as no change has been proposed in the regulations.
- If there are other important fees and charges applicable to certain segment of customers but left out in the Appendices, these may be submitted for consideration of the Central Bank.
Article (12) Conditions for Opening of Accounts, Providing of Credit Cards and Granting Loans & Bank Facilities
a) Conditions for opening of accounts of all types as well as conditions for obtaining credits cards must be included in a standard agreement, drafted in both English and Arabic and written in an easily readable font, and in accordance with texts drafted and approved by the Emirates Banks Association.
b) Conditions for granting personal loans, car loans, overdraft facilities and facilities for covering unpaid credit card balances must be included in standard applications, drafted in both Arabic and English and written in an easily readable font, and in accordance with texts drafted and approved by the Emirates Banks Association.
Clarifications and Guidelines (Notice No. 2901/2011)- Emirates Banks Association will be providing the banks with standard account opening forms including general terms and conditions and other loan documentation which will be beneficial to various user groups. Pending finalization and introduction of new forms, the banks may continue to use the existing forms as hitherto.
- In addition to the above, each bank will also be allowed to define specific terms and conditions which do not require prior approval from the Emirates Banks Association or Central Bank provided these are signed by the customer and do not contravene or contradict any other requirement. These terms will be shown in a separate section along with general terms and conditions.
Article (13) Shariaah Compliant Banking Services
The provisions of these Regulations shall apply to Shariaah compliant banking services, except in the matter of computing interest and determining its amount, which would be done in accordance with Shariaah principles.
In such case, clarity, transparent disclosure, accuracy and documentation at all times, must all be observed, and copy of the established rates should be sent to the Central Bank for publication.
Clarifications and Guidelines (Notice No. 2901/2011)Islamic banks will be allowed to use certain special terms applicable only to such banks, viz profit, finance, etc. However scheduled rates under different names or descriptions should be in accordance with these regulations and sent to Central Bank for information and publication.
Article (14) Violations to the Provisions of These Regulations
Should suspicions arise as to the violation of provisions of these Regulations by any bank, the matter shall be referred to the Legal Development Unit of the Central Bank to decide whether such violation has occurred. If the violation is established, the fine referred to in Article (107) of Union Law No-(10) of 1980 Regarding the Central Bank, the Monetary System and Organization of Banking, shall be imposed, and shall apply to each violation, and be charged on daily basis to the violating bank, until rectified.
Article (15) General Provisions
a) Banks or finance companies are not allowed to alter or vary terms and conditions for granting the loan or the facility during the tenor of the loan or the facility, unless agreed to in writing by the borrower. In case of changes to the commissions or fees, customers must be notified, at least, two months prior to implementation of such changes.
b) Banks and finance companies are prohibited from taking blank cheques for granting loans or overdraft facilities, or for issuing credit cards.
Clarifications and Guidelines (Notice No. 2901/2011)- If a bank uses additional pages to the forms prescribed by the Emirates Banks Association, such sheets containing terms and conditions should be accepted by the borrower under his signature.
- Banks are not expected to upgrade a customer’s status whether for his credit card or other similar facility unless his prior concurrence has been obtained. Besides written concurrence, banks would be allowed to use SMS or email facility to communicate with the customers and obtain their concurrence.
- Effective 1 May, 2011 all new personal accounts will be subject to the revised fee structure. Existing customers will however be given two months notice from that date through letters or via electronic means. Further the revised fee and charges will not be applied retrospectively.
- Banks should continue to pay greater emphasis on cash flow/ repaying capacity of the borrower and less on security or guarantee.
- 5.As hitherto, banks are prohibited to take private houses as security for personal loans or take personal guarantees as security when these loans are given to non-UAE nationals.
- No fees and charges have been mentioned for credit cards and banks may maintain status quo.
- Banks may levy relationship based fee on personal accounts and offer incentives to high value customers provided a specific fee or charge does not exceed the maximum permissible rate specified in the rate structure.
Article (16) The Provisions of These Regulations are not Applicable to Merchant and Investment Banks
The provisions of these Regulations are not applicable to investment banks or merchant banks, nor to finance or investment companies, since these institutions are not authorized to provide personal loans or retail banking services. Moneychangers, however, shall only be subject to the provisions regarding bank transfers and exchange of currency.
Article (17) Responsibilities of the Banking Supervision & Examination Department
a) The Banking Supervision & Examination Department will issue a guide to clarify how banks should comply with the provisions of these Regulations and submit the required statistical data to the Central Bank.
b) The Banking Supervision & Examination Department will also issue a guide to its examiners to explain the regulatory procedures relevant to these Regulations.
Article (18) Cancellation of the Previous Circular on the Subject
Upon enforcement of this Regulation, Circular No- 12/93 dated 23/2/1993, and Central Bank's clarifications ref. DMM/1263/93 dated 6/7/1993, and any notices or directives relating thereto shall be cancelled, except for Notice No- 1850/2004, dated 14/6/2004, regarding Armed Forces Personnel.
Article (19) Interpretation of These Regulations
The Legal Development Unit of the Central Bank shall be the reference for interpretation of the provisions these Regulations.
Article (20) Currently Outstanding Loans
a- The provisions of these Regulations shall apply to all banks and finance companies including Islamic banks and Islamic finance companies in relation to personal consumer loans and car loans granted by these entities currently existing, except for commissions, fees or any fines charged on them prior to the date on which these regulations come into force, which is considered finalized.
b- Any borrower may transfer his/her loan/financing from any bank or finance company operating in the UAE against paying of an early payment fee not exceeding 1% of the outstanding balance of the loan, or AED 10,000, whichever is less. Another bank or a finance company operating in the UAE may accept the transfer under the following conditions:
- For loans granted after the issuance of this Regulation, the requirements of the Regulation must be fully complied with, in particular those relating to the loan or financing amount, the repayment period and monthly deduction.
- For loans granted prior to the issuance of this Regulation, the profit/interest rate should be reduced and the repayment period or loan/financing balance should not be increased by granting an additional loan or financing to the borrower.
Clarifications and Guidelines (as per Notice No. 2901/2011)- Existing loans and overdrafts will continue to be governed by the terms and conditions agreed between the parties. However early settlement charges, other charges, fees and commissions levied after 1st May, 2011 will be in accordance with the new structure.
- New loans extended after 1st May, 2011 or rescheduled after that date will be subject to the new regulations.
- In exceptional circumstances such as rescheduling due to retirement of the borrower or loss of his income for any other reason, a longer repayment period beyond 48 months could be permitted.
- For loans granted after the issuance of this Regulation, the requirements of the Regulation must be fully complied with, in particular those relating to the loan or financing amount, the repayment period and monthly deduction.
Article (21) Publication
These regulations shall be published in the Official Gazette in both Arabic and English, and shall come into effect one month after date of its publication.
Appendix No. (1)
Interest rates charge on Loans
Interest Rate Range Interest/profit on a personal loan (p.a.)
- from AED 0 – AED 50 k
- from AED 51 k – AED 100 k
- from AED 101 k – AED 200 k
- above AED 200 k
--------------
--------------
--------------
--------------
Interest/profit on a car loan (p.a.)
- from AED 0 – AED 50 k
- from AED 51 k – AED 100 k
- from AED 101 k – AED 200 k
- above AED 200 k
--------------
--------------
--------------
--------------
Interest/profit on overdrafts (p.a.)
- from AED 0 – AED 30 k
- from AED 31 k – AED 50 k
- from AED 51 k – AED 100 k
- above AED 100 k
--------------
--------------
--------------
--------------
Interest/profit on unpaid balance on credit card (p.m.)
- from AED 0 – AED 30 k
- from AED 31 k – AED 50 k
- from AED 51 k – AED 100 k
- above AED 100 k
--------------
--------------
--------------
--------------
Appendix No. (2)
Introduction:
- This Amendment applies to and forms part of the Regulations Regarding Bank Loans & Services Offered to Individual Customers (29/2011) (the “Regulations”). It applies specifically to Appendix 2 of those Regulations, which set out the “Maximum Limits for Fees and Commissions Charged on Retail Customer Service”. Upon coming into force, this Amendment replaces the previous version of Appendix 2 and is mandatory and enforceable in the same manner as the Regulations. This Amendment also replaces any other fee caps set out by the Central Bank at this time but not future caps set outside of the scope of this document.
- All fees set out in this Amendment are exclusive of UAE VAT charges.
- Article 11 of 29/2011 remains in force and banks and finance companies must comply accordingly.
- Banks and finance companies will need to notify and seek approval from the CBUAE ex-ante for any planned introduction of a new fee or a change in existing fee levels (which are larger than 5%) not capped by this amendment. Such notifications can be submitted to the CBUAE during the first 5 business days of April and October of any given year.
- The Central Bank will accept ad hoc notifications for exempt fees on an ad hoc basis where it is shown to the Central Bank’s satisfaction that these relate to new products. This will be assessed on a case-by-case basis.
- The fee caps set out in this Amendment represent the maximum permissible charges. Banks and finance companies must have appropriate product approval processes in place for all products, which include an examination of the basis and appropriateness of a fee calculation and, if applicable, must charge lower fees than those prescribed in these caps.
- The Central Bank will supervise regulated entities to ensure that rates are applied in a fair and appropriate manner. This will include ensuring that regulated entities do not automatically default to using maximum caps where actual costs may be lower.
- Regulated entities to which the Regulations apply are required to provide the Central Bank with a full list of the fees they charge no later than 30 days after this Amendment comes into force. Up to date fees should also be made publicly available and should be easily accessible for consumers (e.g. online and in branches).
- These fee caps will be reviewed on an annual basis for continued suitability.
Maximum Limits for Fees and Commissions Charged on Retail Customer Service
No. Product Fee Cap (AED) 1 Personal Accounts Account closure fee 100 2 Personal Accounts Account balance letter 50 3 Personal Accounts No liability certificate 60 4 Personal Accounts Release letter 50 5 Personal Accounts Liability letter issued to Govt Departments/embassies 60 6 Personal Accounts Liability letter issued to financial institutions 60 7 Debit Card Issuing supplementary ATM Card 25 8 Debit Card Replacing Secret Pin Code 25 9 Debit Card Replacing lost or stolen ATM card 25 10 Debit Card Own ATM fees 0 11 Debit Card Fees for using other bank’s ATM 2 12 Debit Card Copy of sales slip 25 13 Consumer Loans Delayed payment penal interest charges Max 200 14 Consumer Loans Early settlement from other bank loans 1% Max 10,000 15 Consumer Loans Final settlement from other sources/EOSB 1% Max 10,000 16 Consumer Loans Partial payment 1% Max 10,000 17 Consumer Loans Revolving overdraft fees 200 18 Consumer Loans Loan Cancellation Fee 100 19 Consumer Loans Other (loan copy, issuing redemption statements, audit confirmation etc) 25 20 Car Loans Early settlement 1% outstanding 21 Car Loans NOC to Traffic Department 0 22 Car Loans Advance payment of installment 1% of installment 23 Car Loans Late payment penal charges Max 500 24 Car Loans Issuance of liability letter to other banks 60 25 Car Loans Cancellation fee 100 26 Remittance Swift copy charges 15 27 Remittance Demand draft/pay order issuance/cancellation 75 28 Customer Term Deposits Account closure fees-terms deposits Cost (max 2%) 29 Credit Cards Card replacement fee 75 30 Credit Cards Liability/no liability letter 50 31 Credit Cards Duplicate statement 45 32 Credit Cards Copy of sales voucher 65 33 Credit Cards Late Payment fees Max 230 34 Home Loans Late payment fees Max 700 35 Home Loans Early settlement fees Max 1% of outstanding balance or 10,000, whichever is less 36 Home Loans Issuance of liability letter 85 37 Home Loans Other certificate 75 38 Home Loans Non-standard statement production/copy of original documentation 100 Home Loans Property swaps administration fee Max 1320
(valuation included)40 Home Loans Issuance of NOC 150 41 Home Loans Partial settlement charges Max 1% of outstanding balance or 10,000, whichever is less 42 Home Loans Clearance letter 95 43 Home Loans Request of other letters 90 - This Amendment applies to and forms part of the Regulations Regarding Bank Loans & Services Offered to Individual Customers (29/2011) (the “Regulations”). It applies specifically to Appendix 2 of those Regulations, which set out the “Maximum Limits for Fees and Commissions Charged on Retail Customer Service”. Upon coming into force, this Amendment replaces the previous version of Appendix 2 and is mandatory and enforceable in the same manner as the Regulations. This Amendment also replaces any other fee caps set out by the Central Bank at this time but not future caps set outside of the scope of this document.
Appendix (3)
Foreign Exchange
Related fees/commissions
Fees for purchase/Sale of currency notes & TC’s (Over & above posted Exchange rates).
Fees on sale of TCs:
- ----------------------.
- ----------------------.
- ----------------------
Fees on issuing Demand Drafts:
Fees on Telegraphic Transfers to:
- India
- Pakistan
- Egypt
- --------
- --------
- -------- etc.
Clarifications and Guidelines Manual for Regulations No 29/2011 Regarding Bank Loans & Services Offered to Individual Customers
N 2901/2011 Effective from 28/4/2011Introduction:
Central Bank of the United Arab Emirates has issued Circular No 29/2011 dated 23.02.2011 titled Loans and Services Offered to Individual Customers. In compliance with Article 17 of the Circular and based on feed-back received from Emirates Bankers Association/ various banks, this Manual is being issued to clarify certain relevant provisions and requirements.
Banks and finance companies (hereafter referred to as bank or banks) extending personal facilities in accordance with the underlying regulations must ensure that they have adequate risk management systems to approve and monitor such facilities. Banks should also ensure that they have trained staff to market the relative products with proper guidance being given to the borrowing customers
Article (2)- Personal Loan:
- 1.These regulations apply to personal facilities viz. loans, overdrafts, car loans and credit cards extended to individuals which are repayable from salary, end of service indemnity and/ or other verifiable regular income from a well defined source.
- 2.It should be ensured that the borrowers’ salary and end of service benefits are properly ascertained from the employer. If the facility is partly or fully given against other income, it should be from a well defined source and its full details should be obtained.
- 3.In case of borrowers with heavy personal commitments and lower disposable income or uncertain employment/ job prospects, banks may not allow facilities upto the upper limit of 20 times salary and/ or the total income, repayable within 48 months despite meeting the specified criteria.
- 4.For sound loan decisions, banks should have clear policy guidelines on issues which have direct bearing on the quality of risk and repayment of the loan.
- 5.If a customer avails for a lower amount than his eligibility or there is significant increase in his income level in subsequent months due to promotion etc, banks may reassess his eligibility after proper verification. In such a case, either existing loan is enhanced or a new loan is set up (without disturbing the existing loan).
- 6.If other income is main or supplementary source of repayment, it should be ensured that such income is from a known regular source, the borrower has produced documentary evidence of such income.
- 7.Besides personal facilities against salary and other income as above, banks may extend loans and overdrafts against lien over fixed deposits held with them.
Article (3)- Car Loan:
- 1.Banks may finance passenger new and used cars to the extent of 80% of their value. Financing of commercial vehicles is outside the purview of these regulations unless repayment of the loan is from the salary of the customer and other laid down criteria are satisfied.
- 2.Financing of operating leases to individuals would not be considered as car finance and would not fall within these regulations.
- 3.Car loans may be allowed in addition to the personal loan as above but within the 50% of gross salary and any regular income as explained in Article (7).
Article (4)- Overdraft Facilities:
- 1.Overdrafts limits will be counted within 20 times salary as specified for the personal loans under Article (2) above
- 3.Islamic banks may allow overdraft facilities by whatever name described in accordance with Shariaah principles, without violating the upper limits and other requirements of these regulations.
Article (5)- Credit Cards:
- 1.In order to ensure that credit cards are issued to creditworthy individuals, a mandatory minimum income level of AED 60,000 per annum has been stipulated. Banks may fix the limits within the policy as stated in this regulation.
- 2.Those not meeting the above income criteria are required to place a pledged deposit of not less than AED 60,000 with the bank for issuance of credit card. However such persons may be permitted credit facility besides credit card provided aggregate of credit facility and credit card limit do not exceed 50% of the pledged deposit.
- 3.Credit card limit is allowed as additional facility but repayment of outstandings must remain within 50% of gross salary and any regular income as explained in Article (7).
- 4.Banks may encourage greater use of debit cards for the customers who are not found to be eligible for issuance of credit card.
- 5.If the cards have been issued to non-customers, banks should compile statistical data separately for residents and non-residents and review them from time to time.
- 6.Banks will take particular care in respect of credit cards issued to non-residents.
Article (6)- Computation of Interest:
- 1.Method of interest calculation has not been changed from the earlier Circular No 12/93. Banks should continue to follow reducing balance method, by taking a year of 365 days. However they must ensure that effective interest rate on per annum basis is disclosed to the customer, displayed on the Board, it is used for calculation and specified in the loan documentation.
- 2.While reducing balance method of interest calculation will be followed on personal and car loans, average daily outstanding balances will form the basis for interest calculation in all cases.
- 3.In case of credit cards, the banks may continue to follow the global practice where no interest/ finance charges are levied on the outstanding balance (excluding cash advance transactions) when the new balance outstanding shown in the statement is paid in full by the Payment Due Date. Finance/ interest charges on cash advance may be applied from the transaction date till final repayment.
- 4.Within the above broad framework, Islamic banks may vary display of interest rates or use appropriate terminology as permitted under the Shariaah.
- 5.Any bank advertising or propagating ‘Flat’ interest rate must invariably state the equivalent effective rate side by side.
Article (7)- Repayment Installments:
- 1.All the lenders are obliged to carry out proper due diligence to ascertain the applicants’ liabilities and income sources so that total installments including payments on account of credit card do not exceed 50% of their gross salary and other regular income.
- 2.Personal loans will be setup for a maximum tenor of 48 months. However if a borrower retires before full repayment, his loan will be restructured from the date of retirement so that his total repayments do not exceed 30% of income (or pension salary).
- 3.Existing loans will continue in accordance with the present arrangement and documentation. However no top ups, deferrals or rescheduling will be permitted beyond eligibility in terms of salary multiplier, tenor and repayment percentage.
- 4.Banks should formulate specific policy on top ups and rescheduling in order to restrict their frequency. It should be ensured that there is no ‘ever greening’ of loans to disguise problem or delinquent loans.
- 5.In case of Islamic banks, they have to ensure that in case of prepayment, adequate rebate is allowed to a customer so that final charge to him does not exceed the level given in Annexure 2 to the Circular.
Article (9)- Bank Accounts & Related Commissions and Charges:
- 1.Banks may continue with their present practices and internal guidelines to control and monitor dormant accounts. However in no case they should transfer the balance of such accounts to their profit and loss account.
- 2.Central Bank is in the process of issuing suitable guidelines in respect of dormant accounts. In the interim, banks may continue to comply with Notice No 24/2000 in respect of dormant accounts and take necessary precautions for operating such accounts.
Articles (10) and (11)- Personal Banking Services & Fees and Commissions Charged on them:
- 1.Relevant fees, charges and commissions applicable to personal customers have been specified in the Appendices to the Circular. Banks are not allowed to levy any other commissions, fees, charges or fines without Central Bank’s written approval. Banks are however free to reduce or exempt their customers from payment of certain fees and charges at their discretion.
- 2.Loans and insurance are separate products. Hence it should be a customer’s choice to select either to pay them together over the period of loan or to pay upfront. Banks should however explain to the customer properly and obtain his concurrence before charging him for the insurance.
- 3.List of charges and commissions apply to personal loans, car loans and personal overdrafts. Banks may continue to levy charges and commissions on credit cards as hitherto as no change has been proposed in the regulations.
- 4.If there are other important fees and charges applicable to certain segment of customers but left out in the Appendices, these may be submitted for consideration of the Central Bank.
Article (12)- Conditions for Opening of Accounts, Providing of Credit Cards and Granting Loans & Bank Facilities:
- 1.Emirates Banks Association will be providing the banks with standard account opening forms including general terms and conditions and other loan documentation which will be beneficial to various user groups. Pending finalization and introduction of new forms, the banks may continue to use the existing forms as hitherto.
- 2.In addition to the above, each bank will also be allowed to define specific terms and conditions which do not require prior approval from the Emirates Banks Association or Central Bank provided these are signed by the customer and do not contravene or contradict any other requirement. These terms will be shown in a separate section alongwith general terms and conditions.
Article (13)- Shariaah Compliant Banking Services:
Islamic banks will be allowed to use certain special terms applicable only to such banks, viz profit, finance, etc. However scheduled rates under different names or descriptions should be in accordance with these regulations and sent to Central Bank for information and publication.
Article (15)- General Provisions:
- 1.If a bank uses additional pages to the forms prescribed by the Emirates Banks Association, such sheets containing terms and conditions should be accepted by the borrower under his signature.
- 2.Banks are not expected to upgrade a customer’s status whether for his credit card or other similar facility unless his prior concurrence has been obtained. Besides written concurrence, banks would be allowed to use SMS or email facility to communicate with the customers and obtain their concurrence.
- 3.Effective 1 May, 2011 all new personal accounts will be subject to the revised fee structure. Existing customers will however be given two months notice from that date through letters or via electronic means. Further the revised fee and charges will not be applied retrospectively.
- 4.Banks should continue to pay greater emphasis on cash flow/ repaying capacity of the borrower and less on security or guarantee.
- 5.As hitherto, banks are prohibited to take private houses as security for personal loans or take personal guarantees as security when these loans are given to non-UAE nationals.
- 6.No fees and charges have been mentioned for credit cards and banks may maintain status quo.
- 7.Banks may levy relationship based fee on personal accounts and offer incentives to high value customers provided a specific fee or charge does not exceed the maximum permissible rate specified in the rate structure.
Article (20)- Currently Outstanding Loans:
- 1.Existing loans and overdrafts will continue to be governed by the terms and conditions agreed between the parties. However early settlement charges, other charges, fees and commissions levied after 1st May, 2011 will be in accordance with the new structure.
- 2.New loans extended after 1st May, 2011 or rescheduled after that date will be subject to the new regulations.
- 3.In exceptional circumstances such as rescheduling due to retirement of the borrower or loss of his income for any other reason, a longer repayment period beyond 48 months could be permitted.
Regulations Regarding Mortgage Loans
C 31/2013 Effective from 28/12/2013This regulation has been amended by the Central Bank Board of Directors Resolution No. 96/2019 and Central Bank Board of Directors Resolution No. 31/2/2020 respectively. You are viewing the latest version. Please find the PDFs of previous versions on the table below.version 2 (consolidated as of 08/04/2020) pdf download version 1 (effective from 28/11/2013) pdf download Introduction
The Central Bank is seeking to promote the proper development, organization and regulation of the mortgage loans market in the United Arab Emirates (UAE).
In introducing these Regulations the Central bank wishes to ensure that banks, finance companies and other financial institutions providing mortgage loans to UAE nationals, GCC nationals and expatriates do so in accordance with best practice.
The Central Bank is also seeking to ensure that financial institutions have and maintain effective business standards and control frameworks in place for the granting of mortgage loans
These Regulations make a distinction between loans to owner occupiers of residential property and investors in residential property since the risk profile and due diligence required is distinctly different for each type of borrower
Objective
The objective of these Regulations is to set minimum acceptable standards for granting mortgage loans with a view to:
i. protecting the financial sector;
ii. fostering consumer protection; and
iii. enhancing financial stability.These Regulations are issued pursuant to the powers vested in the Central Bank under Articles (5), (18), (94) and (96) of Union Law No (10) of 1980 concerning the Central Bank, the Monetary System and Organization of Banking.
Application
These Regulations apply to:
a. Banks
b. Finance companies
c. Other financial institutions providing mortgage loansFor the purpose of these Regulations banks, finance companies and other financial institutions that provide mortgage loans are collectively referred to as ‘mortgage loan providers’.
These Regulations set minimum standards and regulated financial institutions are encouraged to apply higher standards in order to protect the financial soundness of their business. Nothing in these Regulations prevent mortgage loan providers from adopting more conservative limits in relation to granting mortgage loans where deemed appropriate.
Article (1): Definitions
- Mortgage loan: A loan that is collateralized against a residential property granted for the purpose of constructing, purchasing or renovating a house for owner occupier or investment purposes. It also includes loans granted for the purchase or the development of land for these purposes.
- Collateral: Property upon which the residential real estate loan is secured.
- Collateral Management: All tasks and processes within granting of mortgage loans where collateral is involved, e.g. appraisal and constitution of collateral; confirmation of its legal existence and enforceability.
- Debt Burden Ratio: Ratio of debt burden to income.
- Down payment: Up-front payment from the buyer for a portion of the purchase price, which reduces the value of the loan against the property.
- Equity: Difference between the appraised value of the property and the total claims held against the property.
- Loan-to-Value (LTV): The ratio of the amount of the loan outstanding to the appraised value of the residential property.
- Property appraisal: a comprehensive assessment of the property characteristics including the determination of the collateral’s value.
- Mortgage loan providers: All banks, finance companies and other financial institutions that provide mortgage loans.
- Tenor: The initial term length of a mortgage loan.
- Mortgage loan: A loan that is collateralized against a residential property granted for the purpose of constructing, purchasing or renovating a house for owner occupier or investment purposes. It also includes loans granted for the purchase or the development of land for these purposes.
Article (2): Risk Management Requirements
- 1. Lending Policy
All mortgage loan providers must have a separate mortgage lending policy in place which has been approved by the board of directors of the concerned institution.
Mortgage loan providers should set a limit for this type of lending in relation to (a) exposure to property lending and (b) the overall loan book.
The lending policy for mortgage loans must make a clear distinction between financing for owner occupiers and financing for investors and take account of the different risks involved.
Lending policy must include, inter alia, detailed requirements in relation to verification of income and assessment of the borrower’s ability to repay, the maximum loan-to-value and tenor allowable for each type of loan, effective collateral management procedures for taking security against the loan and the application of the risk management framework in relation to this area of business.
Mortgage loan providers are required to have robust procedures and processes in place to monitor completion schedules for the financing of properties being constructed. Where stage payments are to be made as part of the financing agreement, the mortgage loan provider must first use owner’s equity portion of the construction price to pay the developer/contractor before the mortgage loan provider provides any of the loan monies.
Payments to the developer/contractor should be based upon prescribed completion milestones that must be physically confirmed either by the mortgage loan provider or by a suitably qualified professional agent who is independent from both the borrower and the developer/contractor.
Lending policies must be reviewed and signed off by the board of directors of the mortgage loan provider, at least annually, and updated or amended as and when appropriate.
- 2. Effective Verification of Income and Other Financial Information
A key input to effective management of mortgage loans granting process is properly verifying the borrower’s ability to service the loan. Accordingly mortgage loan providers must have in place proper processes and procedures to ensure effective and accurate verification of income and other financial information which the lender will rely on to determine the borrower’s capacity to repay.
Loan documentation should be designed to collect a full income and liabilities history for each applicant. A detailed record of the steps taken to verify income capacity along with full documentary evidence to support the decision (including a formal sign off by the appropriate approval authority) should be maintained on file and be available for inspection by the Central Bank’s examiners if required.
- 3. Reasonable Debt Service Coverage
Prudent granting of mortgage loans requires an accurate assessment of the borrower’s ability to repay the loan. This is an important factor in the context of:
- a. minimizing defaults and losses to the mortgage loan provider.
- b. limiting the possibility of consumer over-indebtedness; and
- c. maintaining stability in the financial system.
In making this assessment the mortgage loan providers must take into account all relevant factors that could impact on the ability of the borrower to repay the loan, including, for example, other debt servicing obligations (including credit card debt), security of employment and the individual’s particular ‘lifestyle’ expenditure. Only reliable and sustainable income should be included when making the assessment. Bonuses and other non-standard or temporary income should be suitably discounted or if not guaranteed excluded from the assessment of repayment.
Mortgage loan providers should develop standard Debt Burden Ratio (DBR) calculation templates that enable lenders to gain a full understanding of the borrower’s financial capacity in order to make an informed decision on the borrower’s ability to service the new loan. The DBR assessment should include an appropriate amount calculated to cover normal recurring household expenditure commitments in addition to other liabilities.
Where the loan extends beyond normal retirement age, lenders must take account of the adequacy of the borrower’s retirement income to repay the loan in making the assessment.
Also, the prevailing interest rate environment shall be taken into account, as such a stress test should be carried out to determine whether the borrower could continue to repay the loan should interest rates rise.
In the case of mortgage loans with deferred repayment of the principal in the first stage and interest only is paid, lenders must be satisfied that the borrower will be able to meet principal and interest payments arising at the end of that period, when assessing the borrower’s ability to repay the loan.
The assessment of the borrower’s ability to repay should not be based on future property price appreciation or an expected increase in the borrower’s earning capacity.
- a. minimizing defaults and losses to the mortgage loan provider.
- 4. Appropriate Loan to Value Ratio (LTV)
The taking of collateral is an important element in the lending decision. Accordingly, the Central Bank expects mortgage loan providers to adopt prudent LTV ratios when granting loans.
Lenders must ensure that all loans granted are subject to an appropriate LTV that takes into account current, latent, or emerging risk factors that may impact on the value of the collateral and the lenders’ ability to realize it. The value of collateral should be suitably discounted to take account of these risk factors.
The level of down payment required from the borrower should be drawn from the borrower’s own resources and not from other sources of borrowing (including personal loans or credit cards). The Central Bank expects mortgage loan providers lending policy to be explicit in this regard to ensure the borrower has an appropriate level of financial interest in the collateral.
It is also important to note that the LTV ratios set out in these Regulations are the maximum allowable. Ultimately mortgage loan providers are responsible for ensuring their institutions remain financially sound. Accordingly, mortgage loan providers should adopt more conservative LTV ratios where the underlying risks in lending markets or segments of the lending markets are higher.
Lending decisions should not be based solely on the security available and it is important that lenders do not rely on the LTV as an alternative to assessing repayment capacity. Mortgage loan providers must ensure that appropriate processes and procedures are in place to capture this risk.
- 5. Effective Collateral Management
Mortgage loan providers are required to have adequate internal risk management and collateral management processes in places that ensure property appraisals are realistic and substantiated. Property appraisal reports should not reflect expected future house price appreciation.
Prior to any irrevocable commitment to lend an independent on-site valuation of the property must be undertaken by a professional third party who is suitably qualified and independent of the borrower, seller, developer/contractor and the loan decision process.
Based on clear evaluation criteria, each bank and finance company should have in place a board approved list of independent Valuers.
All legal titles must be free from encumbrances and contain no impediments for the registration of security interests. In the case of land gifted to UAE Nationals confirmation of the gift from either The relevant Diwan, or Housing Program, as well as confirmation from the land department is required.
- 6. Due Diligence
In order to limit and mitigate the risk arising from mortgage loans business, mortgage loan providers must have in place a clear written program of due diligence (legal and other) to be followed during all stages of the application process to ensure lending policies are being implemented correctly. Procedures must also be in place to ensure that, prior to drawdown, all conditions attaching to the loan have been (or are being) complied with.
- 1. Lending Policy
Article (3): Important Ratios
- 1. Debt Burden Ratio (DBR)
The maximum DBR allowed is set out in “Regulations Regarding Bank Loans and Other Services Offered to Individual Customers”- i.e. 50 percent of gross salary and any regular income from a defined and specific source at any time’. It is important however that when making an assessment of the borrower’s ability to repay, financial institutions do not automatically apply the maximum DBR and take into account the specific circumstances of the borrower and the exposure to the institution.
In arriving at the DBR, mortgage loan providers are required to stress test the loan at (2 to 4) percentage points above the current rate of interest on the loan, depending upon what level interest rates are at in the cycle. Where an introductory interest rate applies the stress test should be carried with reference to the rate that will apply on cessation of the introductory rate.
Where the property is for investment purposes mortgage loan providers are required to make a deduction of at least two months’ rental income from the DBR calculation to assess the borrower’s ability to repay taking account of non-rental periods.
Where the loan repayment schedule extends beyond the expected retirement age, mortgage loan providers are required to ensure that the balance outstanding at that time can continue to be serviced at a DBR of 50 percent of the borrower’s post retirement income.
- 2. Loan to Value Ratio (LTV)
The maximum Loan to Value (LTV) ratio are as follows: -
A. UAE Nationals
• First House/Owner OccupierEach borrower can only claim one property under this category.
- a. Value of Property less or equal to AED 5 million - maximum 85% of the value of the property.
- b. Value of Property more than AED 5 million - maximum 75% of the value of the property.
- • Second and Subsequent House or Investment Property
65% of the value of the property, regardless of value.
- B. Expatriates
• First House/Owner Occupier
Each borrower can only claim one property under this category.
- a. Value of Property less than AED 5 million - maximum 80% of the value of the property.
- b. Value of Property more than AED 5 million – maximum 70% of the value of the property.
Second and Subsequent House or Investment Property
60% of the value of the property, regardless of value.
- C. All Categories - Property purchased off plans
Given the long term nature of the development process and the higher level of risk to completion, the maximum LTV for mortgages on property being purchased off plans is 50% regardless of purpose, value, or category of purchaser.
- 3. Maximum Term of Loan
The maximum tenor of the mortgage loan is 25 years. - The maximum age at the time of the last repayment should be determined by the mortgage loan providers in accordance with their risk management and lending policies.
- 4. Maximum Financing Amount
As per Article 3.1, the DBR cannot exceed 50%.
In addition, the maximum financing amount allowed is as follows:
- • UAE Nationals: up to 8 years annual income.
- • Expatriates: up to 7 years annual income.
- • UAE Nationals: up to 8 years annual income.
- 5. Source and Frequency of Repayment
Repayment should be made from salary or verifiable business or rental income. The use of ‘End of Service Benefit’ is not allowed.
Principal and interest repayments should be made on a reducing balance basis (except for mortgage loans with differed repayment of principal – treated as per 6 below).
Repayments should be at a frequency not less than quarterly. The Central Bank would expect there to be minimum exceptions to this policy.
- 6. Interest Only Period
Mortgage loans with deferred principal repayment should only apply to investment loans. These loans should not allow for non-repayment of principal for longer than 5 years from date of first drawdown of the loan.
- 7. Acceptable Collateral
A first class mortgage in the name of the mortgage loan provider must be taken on all financed properties.
In cases where the property being financed falls under the various Government Housing Schemes and a first charge cannot be created, mortgage loan providers should have other means in place to protect the loan collateral including the taking of a second charge on the mortgaged property where possible.
- 1. Debt Burden Ratio (DBR)
Article (4): Disclosure and Transparency
Lenders should provide the borrower with sufficient and transparent information, including costs and risks associated with the loan, to enable the borrower to make an informed assessment of the suitability of the loan to their needs and financial circumstances.
There should be transparency in preparing and publishing all fees, charges and interest rates (or profits) including the method of calculating interest/profit.
Loan documentation should include, inter alia, the details of the property or the development, the borrower’s contribution, the amount of the loan, the repayment period, the periodic installment, the interest/profit rate, insurance requirement, mode and method of disbursement, the milestones required for progress payments in case of properties under construction with a clear pre-payment policy. For fees and charges it should be detailed in a separate schedule to be attached to the loan contract.
Borrowers should be provided with information setting out the total cost of the loan during its lifetime. The borrower must sign each page of the loan documentation and be given a copy signed by both the mortgage loan provider and the borrower.
The maximum charges to refinance with other banks or financial institutions or for early repayments are the actual cost (to break fixed loans) to the lender and/or fees and charges as set out in Regulations No. 29/2011. There should also be no impediment for borrowers to refinance with other institutions.
Financial institutions should also follow the transparency and disclosure requirements for real-estate lending in accordance with Regulations No. 29/2011.
Mortgage loan providers are not allowed to alter or vary terms and conditions of the loan or the facility during the tenor of the loan or the facility, unless agreed to in writing by the borrower. In case of changes to the commissions or fees, customers must be notified, at least, two months prior to implementation of such changes.
Article (5): Housing Programs
The Central Bank wishes to support specific Government housing programs that are established for the purpose of serving society for the betterment of communities and individuals.
The Central Bank will engage with such programs directly and seek to agree a more preferential regulatory treatment where loans under such programs are guaranteed by the Government.
Where the loan amount advanced to a UAE National to construct or purchase a property for ‘owner occupation purposes’ under a local housing program is guaranteed, the maximum DBR allowable is increased to 60 percent.
The maximum LTV allowable may be increased to 85 percent when the value of the property is AED 5 million or less.
Article 6: Shari’ah Compliant Finance
Certain mortgage loan providers will be providing mortgage finance in accordance with Shari’ah principles.
While it is recognized that Islamic finance has specific features, an institution offering Islamic financial services is generally exposed to the same types of risks as a conventional mortgage loan provider.
In addition to observing the specific requirements set out by the Shari’ah advisory committees given under each mode of financing separately, the requirements laid down in these Regulations should also be complied with while granting mortgage loans under Shari’ah principles.
Article (7): Reporting
Reporting requirements will be as set out in the Central Bank’s online periodic Banking Return Forms system.
Article (8): Monitoring and Supervision
The Central Bank will monitor and supervise the implementation of these Regulations and take appropriate regulatory action where breaches occur.
In implementing these Regulations the Central Bank expects mortgage loan providers to apply ‘substance over form’ in making lending decisions and have appropriate policies and procedures in place to ensure that requirements of these Regulations are not circumvented. The Central Bank will be mindful of schemes or vehicles some mortgage loan providers may establish to circumvent these Regulations and shall take appropriate action as necessary.
The Central Bank reserves the right to alter any of the “Important Ratios” contained in these Regulations either globally, or for an individual mortgage loan provider, where it so deems appropriate
Article (9): Interpretation of Regulations
The Legal Development Unit of the Central Bank shall be the reference for interpretation of the provisions of these Regulations.
Article (10): Cancellation of Previous Notices
Notice number 3871/2012 is withdrawn from the date these Regulations become effective.
Article (11): Publication and Application
These Regulations shall be published in the Official Gazette in both Arabic and English and shall come into effect one month from the date of publication.
Loans Extended to Finance Purchase of Company Shares
This Circular has been amended by the Notice No. 2418/2006. You are viewing the latest version. Please find the PDF of the previous version on the table below.version 2 (consolidated as of 28/05/2006) pdf download version 1 (effective from 28/04/2006 pdf download In order to organize lending against pledge of company shares, for the benefit of the banking and financial system in the UAE, the Board of Directors of the Central Bank has resolved to establish the following rules:
- No loans should be extended to purchase shares except against tangible securities, among which shares of joint stock public companies, newly established or those under establishment.
- Loans extended to the founders of companies against the pledge of their allotted shares should not exceed 50% of the nominal value of those shares. This position continues until the expiry of the legal period required to maintain ownership of these shares as per companies law, thereafter, they will be treated as in (4) below.
- Loans extended to subscribers in the public subscription of companies under establishment against an undertaking to pledge their allotted shares should not exceed 10% of the nominal value of the subscribed shares, except in case where the issuing company or the bank receiving the subscription funds (subscription bank) undertakes to refund excess funds directly to the lending bank (or lending party). In this case, lending may be extended to maximum fivefolds the amount contributed by the subscriber for the purchase of IPO shares
- Loans extended against pledge of allotted shares in the public subscription of newly established companies should not exceed 70% of the book value of these shares. This limitation shall remain valid until these companies have been in operation for five years.
- Loans extended against pledge of shares of companies which have been in operation for more than five years should not exceed 80% of the market value of these shares.
- Banks and other financial institutions operating in the UAE may extend loans to purchase shares of companies established in the other AGCC countries, as per paragraphs (2), (3), (4) and (5) above, but with a maximum, in all cases, of 40% (the 10% in (3) above remains as it is in similar cases), and on condition that they must comply with all local laws prevailing in the country of origin of the company.
- In case borrowers pledged other assets (such as deposits, shares of other companies, property, bonds) or their application included submitting various securities, priority should be given to securities according to quality and degree of liquidity.
It should be noted that in case any of the banks (lending parties) violated the monetary policy by undertaking book-lending in order to lend subscribers to shares (or other securities), whether directly or indirectly, the Central Bank shall deprive such banks from the entire amount of the resulting interest, by debiting their accounts with it. Please note that book-lending means loans which have no corresponding customer deposits, capital and reserves of the lending party.
Please withdraw and cancel our Notice No. 311/96 of 4/6/1996, and our Circular No. 19/97 of 4/11/1997.
- No loans should be extended to purchase shares except against tangible securities, among which shares of joint stock public companies, newly established or those under establishment.
Payment Token Services Regulation
C 2/2024 Effective from 21/8/2024Introduction
This Regulation (the ‘Payment Token Services Regulation’) lays down the rules and conditions established by the Central Bank for granting a License or Registration for the provision of Payment Token Services and related matters. Payment Token Services are digital payment services in the UAE and comprise three categories, namely Payment Token Issuance, Payment Token Conversion and Payment Token Custody and Transfer.
Providing digital money services is a financial activity subject to Central Bank licensing and supervision in accordance with the provisions of the Central Bank Law. Accordingly, the Central Bank Law provides the statutory basis for the powers of the Central Bank in relation to the licensing and ongoing supervision of Licensed Payment Token Service Providers, and related matters.
Part 1
Scope and Objectives
This Regulation sets out:
conditions for the grant and maintenance of a License or Registration for the provision of Payment Token Services;
rights and obligations of Customers, Licensed Payment Token Service Providers, Registered Foreign Payment Token Issuers, Registered Foreign Payment Token Custodians and
Transferors and Registered Payment Token Conversion Providers; and
powers of the Central Bank including with regard to the licensing, registration and supervision of Licensed Payment Token Service Providers, Registered Foreign Payment Token Issuers, Registered Foreign Payment Token Custodians and Transferors and Registered Payment Token Conversion Providers, and on-going reporting requirements;
limitations on certain services and the promotion of services relating to Foreign Payment Tokens, and on acceptance of such Foreign Payment Tokens as a Means of Payment; and
a prohibition of the issuance, promotion and performance of certain services in relation to Algorithmic Stablecoins, Privacy Tokens or other Means of Payment which are not Dirham Payment Tokens or Foreign Payment Tokens.
In exercising its powers and functions under this Regulation, the Central Bank has regard to the following objectives:
ensuring the safety, soundness and efficiency of Payment Token Services;
ensuring adequate protection and avoidance of misappropriation of the Reserve of Assets held by Payment Token Issuers;
adoption of effective and risk-based licensing and registration requirements for Licensed Payment Token Service Providers, Registered Foreign Payment Token Issuers, Registered Foreign Payment Token Custodians and Transferors and Registered Payment Token Conversion Providers; and
promoting consumer protection and innovation. Exclusions
This Regulation shall not apply to the following:
1. Any activity for which the service provider is licensed by (or requires a license from) the Central Bank under the Retail Payment Services and Card Schemes Regulation or the Stored Value Facilities (SVF) Regulation;
2. Any information technology security, operation of technology infrastructure, trust or privacy protection service not of itself constituting a Payment Token Service;
3. Any service of providing or maintaining a communication network or Distributed Ledger Technology;
4. Any service of providing and maintaining any terminal or device used for any Payment Token Service;
5. Any Payment Token Transfers carried out within a payment system or securities settlement system between Licensed Payment Token Service Providers and settlement agents, central counterparties, clearing houses, central banks or other participants in such system including central securities depositories; or
6. Payment Token Transfers and related services between a parent undertaking and its subsidiary or between subsidiaries of the same parent undertaking, without any intermediary intervention by a Licensed Payment Token Service Provider, Registered Foreign Payment Token Issuer, Registered Foreign Payment Token Custodian and Transferor or Registered Payment Token Conversion Provider other than an undertaking belonging to the same group.
Part 2
Article (1): Definitions
Except where an alternative definition is expressly stated in this Regulation, the following terms are defined as set out in this Article (1).
1. Agent: means a juridical person performing Payment Token Services on behalf of a Licensed Payment Token Service Provider. 2. Algorithmic Stable coins: means a virtual Asset which purports to maintain a stable value by reference to a Fiat Currency or other asset as a result of interventions (either automated or manual) by its issuer or another Person to alter the supply of or demand for the Virtual Asset from time to time, and which is used or may be used as a Means of Payment. 3. AML/CFT: means Anti-Money Laundering and Combating the Financing of Terrorism. 4. AML Law: means Decree Federal Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations and Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Federal Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations, as amended, and any regulations issued hereunder and any instructions, guidelines and notices issued by the Central Bank relating to their implementation or issued in this regard. 5. AML Obligor: means a Licensee or Registree. 6. Applicant: means a juridical person:
a) duly incorporated in the UAE in accordance with Federal Law No. 2 of 2015 on Commercial Companies, as may be amended or substituted from time to time and as provided for under Article (74) of the Central Bank Law (or other analogous commercial regulation applying in a free zone), which files an Application with the Central Bank for the granting of a License for the provision of one or more Payment Token Services or the modification of the scope of a granted License; b) incorporated and located outside of the UAE (which for the purposes of this Regulation would include a juridical person incorporated and located in a Financial Free Zone), which files an Application with the Central Bank for the granting of a Foreign Payment Token Issuer Registration or the modification of the scope of a granted Registration; or c) that is a Virtual Assets Exchange Platform Operator, Bank or Exchange House which files an Application with the Central Bank for the granting of a Non-Objection Registration or the modification of the scope of a granted Non-Objection Registration. 7. Application: means a written request for obtaining a License for the provision of one or more Payment Token Services, for obtaining a Foreign Payment Token Issuer Registration, or for obtaining a Non-Objection Registration, submitted by an Applicant which contains the information and documents specified in this Regulation or by the Central Bank, and is in the form specified by the Central Bank’s Licensing Division, including a written request for obtaining a modification to the scope of a granted License or Registration. 8. Bank: any juridical person licensed in accordance with the provisions of the Central Bank Law, to carry on the activity of taking deposits of all types, including Shari`ah-compliant deposits. 9. Beneficial Owner: means the natural person who owns or exercises effective ultimate control over the Customer or the natural person on whose behalf a transaction is being conducted, or the natural person who exercises effective ultimate control over a legal person or legal arrangement, whether directly or through a chain of ownership, control or other indirect means. 10. Board: means the board of directors of an Applicant, a Controller of an Applicant, a Licensed Payment Token Service Provider or a Registree in accordance with applicable corporate law. 11. Business Day: means a day other than Saturday, Sunday, public holiday or other non-working holiday or day in the UAE. 12. CBUAE Regulation: means any written act that may be adopted or issued by the Central Bank complementing the implementation of this Regulation, such as, without being limited to, rules, directives, decisions, instructions, notices, circulars, standards, and rulebooks. 13. Central Bank: means the Central Bank of the United Arab Emirates. 14. Central Bank Digital Currency: means a digital version of a Fiat Currency that is issued by the Central Bank or another central bank. 15. Central Bank Law: means the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities, as amended. 16. Consumer Protection Regulation: means Consumer Protection Regulation (Circular No. 8 – 2020) dated 25 November 2020, as amended, and Consumer Protection Standards, as amended. 17. Controller: means a Person that alone or together with the Person’s associates has an interest in at least 10% of the shares in an Applicant or Licensed Payment Token Service Provider or Registree or is in a position to control at least 10% of the votes in an Applicant or Licensed Payment Token Service Provider or Registree. 18. Customer: means a Person receiving or potentially receiving a Payment Token Service and includes a Token holder. 19. Customer Agreement: means a Framework Agreement or a Single Payment Token Service Agreement. 20. Customer Due Diligence or CDD: means the process of identifying and verifying the identity of a Customer and its Beneficial Owners, whether a natural or legal person or a legal arrangement, and of collecting information as to the nature of the Customer's activity and the purpose of any business relationship between the Customer and the Payment Token Services provider and the ownership structure and control over it. 21. Data Breach: means an intrusion into an IT system where unauthorized disclosure or theft, modification or destruction of Customer data is suspected and such is likely to result in a loss for the Customer. 22. Data Subject: means an identified or identifiable natural person who is the subject of Personal Data. 23. Designated Payment Token: mean a Virtual Asset that the Central Bank has designated as a Payment Token in accordance with Article (12)6. 24. Dirham Payment Token: means a Payment Token whose value is denominated in Dirham (AED), or denominated by reference to the value of another Payment Token whose value is denominated in Dirham (AED), and which is issued by a Dirham Payment Token Issuer. 25. Dirham Payment Token Issuer: means a Payment Token Issuer that is Licensed to perform Payment Token Issuing for Dirham Payment Tokens pursuant to Article (5)1(a). 26. Distributed Ledger Technology: means a class of technologies that supports the distributed recording of encrypted data across a network and which is a type of decentralized database of which there are multiple identical copies distributed among multiple participants and accessible across different sites and locations, and which are updated in a synchronized manner by consensus of the participants, without involving a central authority or intermediary using a system other than the network or another distributed ledger. 27. Dormant Accounts Regulation: means Dormant Accounts Regulation (C 1/2020) dated 15 January 2020, as amended. 28. Exchange House: means an exchange business that has been licensed under the Regulations re Licensing and Monitoring of Exchange Business. 29. Exempted Person: means any Person who is exempted from the requirement to hold a License under Article (4). 30. External Auditor: means an independent juridical Person that has been appointed to audit the accounts and financial statements of a Licensed Payment Token Service Provider in accordance with Article (34)9, to audit the Reserve of Assets of a Licensed Payment Token Issuer in accordance with Article (22)8(b) or to audit the White Paper of a Licensed Payment Token Issuer in accordance with Article (26)4. 31. FATF: means the Financial Action Task Force, being an inter-government body which sets international standards that aim to prevent global money laundering and terrorist financing activities. 32. Fiat Currency: means a currency that is controlled by a central bank, has the status of legal tender and is required to be accepted within a given jurisdiction. 33. Financial Free Zones: means free zones subject to the provisions of Federal Law No. (8) of 2004, regarding Financial Free Zones, as amended. 34. Foreign Currency: means a Fiat Currency which is not the Dirham (AED). 35. Foreign Payment Token: means a Payment Token whose value is denominated in a Foreign Currency, or denominated by reference to the value of another Payment Token whose value is denominated in a Foreign Currency. 36. Foreign Payment Token Custodian and Transferor: means a Person who, by way of business, performs Payment Token Custody and Transfer of Foreign Payment Tokens, pursuant to Article (5)2. 37. Foreign Payment Token Issuer: means a Payment Token Issuer that is Registered pursuant to Article (5)2. 38. Foreign Payment Token Registration: means a registration granted by the Central Bank to an Applicant registered and located outside of the UAE (which for the purposes of this Regulation would include a juridical person incorporated and located in a Financial Free Zone) to perform Payment Token Issuing with respect to Foreign Payment Tokens, pursuant to Article (5)2, and Foreign Payment Token Registree refers to a Foreign Payment Token Issuer holding a valid Foreign Payment Token Registration. 39. Framework Agreement: means an agreement between a Licensed Payment Token Service Provider and a Customer for the provision of a Payment Token Service, other than a Single Payment Token Service Agreement, which governs the rights and obligations as between the Licensed Payment Token Service Provider and the Customer (and their assignees, transferees or successors). 40. Group: means a corporate group which consists of a parent entity and its subsidiaries, and the entities in which the parent entity or its subsidiaries hold, directly or indirectly, 5% or more of the shares, or are otherwise linked by a joint venture relationship. 41. License: means a License issued by the Central Bank provide a Payment Token Service, pursuant to Article (5)1. Licensed refers to having been granted such a License, where such License remains valid, and Licensee refers to a Licensed Payment Token Service Provider holding a valid License. 42. Licensed Payment Token Issuer: means a juridical person that has been Licensed in accordance with this Regulation to perform Payment Token Issuing. 43. Licensed Payment Token Service Provider: means a juridical person that has been Licensed in accordance with this Regulation to provide one or more Payment Token Services. For the avoidance of doubt, a Registree is not included within the definition of Licensed Payment Token Service Provider. 44. Local Licensing Authority: means any authority competent to regulate Virtual Assets in the concerned Emirate in accordance with Cabinet Resolution No. (111) of 2022 Concerning the Regulation of Virtual Assets and their Service Providers, as amended. 45. Means of Payment: means a Virtual Asset:
a) which is, or which is able to be used as, or is purported or promoted to be, a store of value, medium of exchange and unit of account; or b) which the Central Bank designates, pursuant to Article (3)1, as being a Means of Payment. 46. Merchant: means a Person who accepts Payment Tokens as a Means of Payment for the sale or provision of goods or services. 47. Non-Objection Registration: means a registration by the Central Bank of an Applicant based on a decision by the Central Bank to permit the Applicant to perform Payment Token Conversion or Foreign Payment Token Custody and Transfer, pursuant to Article (8)1, and Non-Objection Registree refers to a Payment Token Conversion Provider or Foreign Payment Token Custodian and Transferor holding a valid Non-Objection Registration. 48. Outsourcing Regulation means the Outsourcing Regulation for Banks (Circular No. 14/2021) dated 31 May 2021, as amended. 49. Payee: means a Person who is the intended recipient of a Payment Token Transfer. 50. Payer: means a Person who performs a Payment Token Transfer of a Payment Token for which it is the Tokenholder, or instructs a Licensee or Registree to perform such Payment Token Transfer on its behalf (by having the Licensee or Registree initiate, facilitate, effect or direct such transfer). 51. Payment Token: means a Virtual Asset which purports to maintain a stable value by referencing the value of:
a) the same Fiat Currency as the Payment Token is denominated in; or b) another Payment Token also denominated in the same Fiat Currency. A Designated Payment Token shall be deemed to be a Payment Token. 52. Payment Token Conversion: means a service, other than Payment Token Issuing, which is performed by way of business, of selling or buying Payment Tokens in return for any form of remuneration by spot conversion as principal or agent or enabling other counterparties to place and accept offers for sale of Payment Tokens. 53. Payment Token Conversion Provider: means a Person who, by way of business, performs Payment Token Conversion, other than a Person acting as a Payment Token Issuer. 54. Payment Token Custody and Transfer: means a service, performed by way of business, to:
a) safeguard, or to safeguard and administer:
(i) Payment Tokens on behalf of Customers, or (ii) private cryptographic keys on behalf of Customers in order to hold, store and transfer Payment Tokens; or b) receive, hold and transfer Payment Tokens on behalf of Customers. For the avoidance of doubt, Payment Token Custody and Transfer excludes provision of technology (including provision of updates to the technology, and support to address any technical issues with the technology) to another Person which enables the other Person to safeguard or safeguard and administer their own Payment Tokens or the cryptographic keys for such Payment Tokens or the Wallet in which they are held, or to transfer such Payment Tokens on their own behalf.
For the avoidance of doubt, Payment Token Custody and Transfer may be a service performed to facilitate or enable a Merchant to receive payments by Payment Token in exchange for the supply of goods or services under a merchant acquiring-style arrangement.
55. Payment Token Custodian and Transferor: means a Person who, by way of business, performs Payment Token Custody and Transfer. 56. Payment Token Data: means any information related to a Customer, including financial data and excluding Personal Data. 57. Payment Token Issuer: means a Person who, by way of business, performs Payment Token Issuing. 58. Payment Token Issuing: means a sale or transfer, performed by way of business, of a Payment Token, where it is the first occasion on which that Payment Token is sold or transferred.
a) This can include (without limitation) where such first sale or transfer is undertaken through an exchange or trading venue. b) If the first occasion on which a Payment Token is transferred is when one Person (an ‘issuer’) generates a Payment Token (or arranges for its generation) for transfer to a distributor with a view to the distributor selling the Payment Token, or otherwise transferring the Payment Token to the public, the Payment Token Issuing is performed by the distributor rather than by the issuer. 59. Payment Token Service: means the performance by way of business of any of the following activities:
a) Payment Token Issuing; b) Payment Token Custody and Transfer; and c) Payment Token Conversion. 60. Payment Token Transfer: means an act initiated by the Payer or Payee or on either of their behalves, or by the Payment Token Issuer, of transferring a Payment Token(s) or an interest in a Payment Token(s), whether or not such transfer is performed using Distributed Ledger Technology and irrespective of any underlying obligations between the Payer and the Payee. 61. Person: means any natural or juridical person. 62. Personal Data: means any information which is related to an identified or identifiable natural person. 63. Privacy Token: means a Virtual Asset which, by design, disguises or otherwise obfuscates, or purports to hide or obfuscate, details of its Tokenholder or transaction history which would otherwise be visible to third parties through the Distributed Ledger Technology on which the Virtual Asset is hosted, and which is used or may be used as a Means of Payment. 64. Promotion: means any form of communication, by any means, aimed at inviting or offering to enter into an agreement for provision of services. 65. Registered Foreign Payment Token Issuer: means a Foreign Payment Token Issuer which is registered pursuant to Article 5(2). 66. Registered Foreign Payment Token Custodian and Transferor: means a juridical person that has received a Non-Objection Registration in accordance with this Regulation to perform Payment Token Custody and Transfer of Foreign Payment Token. 67. Registered Payment Token Conversion Provider: means a juridical person that has received a Non-Objection Registration in accordance with this Regulation to perform Payment Token Conversion. 68. Registration: means a Foreign Payment Token Issuer Registration or a Non-Objection Registration, and Registered refers to having been granted such a Registration, where such Registration remains valid, and Registree refers to a Foreign Payment Token Issuer or Payment Token Conversion Provider or Foreign Payment Token Custodian and Transferor holding a valid Registration. 69. Regulation: means this Payment Token Services Regulation. 70. Reserve of Assets: means the assets held in accordance with Article (22). 71. Retail Payment Services and Card Schemes Regulation: means Retail Payment Services and Card Schemes Regulation (Circular No. 15/2021) dated 6 June 2021, as amended. 72. SCA: means the UAE Securities & Commodities Authority. 73. Senior Management: means a team of individuals at the highest level of management of the Licensee or Registeree who have the day-to-day tasks of managing the Licensee’s business. 74. Single Payment Token Service Agreement: means an agreement which governs the rights and obligations as between a Licensed Payment Token Service Provider and a Customer (and their assignees, transferees or successors) and which is limited to:
a) governing a single sale, transfer and redemption of Payment Tokens; or b) provision of a Payment Token Custody and Transfer Service for a single Payment Token Transfer. 75. Stored Value Facilities (SVF) Regulation: means Stored Value Facilities (SVF) Regulation (Circular No. 6/2020) dated 30 September 2020, as amended. 76. Third Country: means any Financial Free Zone or any country other than the UAE. 77. Tokenholder: means the person who has the lawful power of disposal over a Payment Token. 78. Transition Period: has the meaning given in Article (40). 79. UAE: means the United Arab Emirates. 80. Unauthorized Payment Token Transfer: means a Payment Token Transfer:
a) initiated, facilitated, effected or directed by a Licensed Payment Token Service Provider as part of its Payment Token Service; and b) where such transfer has not been consented to by the Tokenholder or (in the case of the Licensed Payment Token Service Provider selling a Payment Token) the purchaser of the Payment Token. 81. Virtual Asset: means a digital representation of value or of a right that can be transferred and stored electronically using Distributed Ledger Technology. Excluding, for the purposes of this regulation, Central Bank Digital Currencies. 82. Virtual Assets Exchange Platform Operator: means a Person licensed by SCA as a virtual assets platform operator and regulated by SCA or any Local Licensing Authority. 83. Wallet: means a Distributed Ledger Technology address or account to which a Virtual Asset is attributed from time to time and in relation to which a Payment Token Transfer is performed. 84. Wire Transfer: means any Payment Token Transfer carried out on behalf of a Payer through a Licensed Payment Token Service Provider with a view to making an amount of Payment Tokens available to a Payee at the beneficiary’s Licensed Payment Token Service Provider, irrespective of whether the Payer and the Payee are the same Person. 85. White Paper: means a document setting out the information stipulated in Article (26) and published or otherwise made available in accordance with the provisions of that Article. Part 3
Article 2: Prohibitions on Activities and Promotions
Restrictions on activities
1. No Person shall perform any Payment Token Service within the UAE or directed to Persons in the UAE, unless such Person is Licensed or Registered by the Central Bank to perform such Payment Token Service. 2. No Person shall perform any service, within the UAE or directed to Persons in the UAE, where that service:
a) is performed with respect to any Means of Payment that is not a Payment Token; and b) is a service that is similar or equivalent to a Payment Token Service. This prohibition shall apply to all Persons, including any Person acting in the course of performing Virtual Asset activities for which it is licensed or regulated by SCA or a Local Licensing Authority.
3. No Person shall, within the UAE or directed to Persons in the UAE, issue Algorithmic Stablecoins or Privacy Tokens or perform services relating to Algorithmic Stablecoins or Privacy Tokens. This prohibition shall apply to all Persons, including any Person acting in the course of performing Virtual Asset activities for which it is licensed or regulated by SCA or a Local Licensing Authority. 4. A Licensee or Registree must not knowingly initiate, facilitate, effect or direct a Payment Token Transfer as part of its Payment Token Service unless the transfer is of a:
a) Dirham Payment Token issued by a Licensed Payment Token Issuer being used for any lawful purpose; or b) Foreign Payment Token issued by a Registered Foreign Payment Token Issuer being lawfully used (or sold for use) as a Means of Payment for purchase of Virtual Assets or derivatives of Virtual Assets. 5. A Foreign Payment Token Registree may only initiate, facilitate, effect or direct a Payment Token Transfer as part of its Payment Token Service in the UAE if the transfer is of a Foreign Payment Token being used (or sold for use) as a Means of Payment for purchase of Virtual Assets or derivatives of Virtual Assets. 6. A Licensed Payment Token Issuer may only issue Dirham Payment Tokens to Persons resident in the UAE. For the avoidance of doubt, aside from this Article (2)6 there shall be no restriction under this Regulation as to the territory in which a Payment Token may be used or to or from which it may be transferred. 7. No Merchant or other Person in the UAE selling goods or services during the course of business may accept a Virtual Asset towards payment for that sale unless that Virtual Asset is:
a) a Dirham Payment Token issued by a Licensed Payment Token Issuer being used as a Means of Payment ; or b) a Foreign Payment Token issued by a Registered Foreign Payment Token Issuer being used as a Means of Payment for purchase of a Virtual Asset or Virtual Asset derivative. 8. A Bank may not act as a Payment Token Issuer, but may, subject to the licensing and other requirements of this regulation, set up a subsidiary, affiliate or other related entity to perform this activity. Restrictions on promotions
9. No Person shall engage in any Promotion, within the UAE or directed to Persons in the UAE, where such Promotion relates to Payment Token Services unless such Person:
a) has a License or Registration to perform the activities which are the subject matter of the Promotion; or b) is appointed by such a Licensee to engage in the Promotion on the Licensee’s behalf. 10. No Person shall engage in any Promotion, within the UAE or directed to Persons in the UAE, where such Promotion is for services relating to any Means of Payment unless the Promotion solely relates to:
a) Dirham Payment Tokens issued by Licensed Payment Token Issuers being used for any lawful purpose; or b) Foreign Payment Tokens issued by Registered Foreign Payment Token Issuers being lawfully used as a Means of Payment for purchase of a Virtual Asset or Virtual Asset derivative. This prohibition shall apply to all Persons, including any Person engaging in Promotions relating to Virtual Asset activities for which it is licensed or regulated by SCA or a Local Licensing Authority.
11. No Person shall engage in a Promotion, within the UAE or directed to Persons in the UAE, where such Promotion is for the issuance of Algorithmic Stablecoins or Privacy Tokens or services relating to Algorithmic Stablecoins or Privacy Tokens. This prohibition shall apply to all Persons, including any Person engaging in Promotions relating to Virtual Asset activities for which it is licensed or regulated by SCA or a Local Licensing Authority. 12. The Central Bank may require any Person to provide a reasonable level of evidence to demonstrate that such Person is not performing an activity in breach of this Article (2). The Central Bank may request such evidence on a single occasion or may require regular reporting (in such form as the Central Bank may specify from time to time) of such evidence by any Person. 13. For the avoidance of doubt, reference to ‘the UAE’ in this Article (2) excludes the jurisdiction of the Financial Free Zones. Article (3): Designation of Means of Payment
1.
The Central Bank may designate a type of Virtual Asset as constituting a Means of Payment.
2.
The Central Bank may require any Person which, within the UAE or directed at Persons in the UAE, issues Virtual Assets or performs services relating to Virtual Assets, to provide the Central Bank with such information as the Central Bank requires in order to determine whether to designate the Virtual Asset as a Means of Payment.
3.
For the avoidance of doubt, reference to ‘the UAE’ in this Article (2) excludes the jurisdiction of the Financial Free Zones.
Article (4): Exemptions
1.
Payment Token Services limited to the following types of Payment Tokens and posing a low level of risk to Customers and the financial system are exempt from this Regulation:
a)
Payment Tokens used for certain reward schemes. Such Payment Tokens may only be:
(i)
issued in return for a sum of money paid by (A) the Payment Token Issuer; or (B) a Merchant under an agreement with the Payment Token Issuer; and
(ii)
used for making payments for goods or services provided by the Payment Token Issuer or Merchant under specific terms and conditions of the Payment Token Service.
Examples may include loyalty schemes provided by shops and supermarkets that offer Payment Token rewards for customer loyalty;
b)
Payment Tokens used for certain bonus point schemes:
(i)
Such Payment Tokens may be used as points or units (by whatever name called) provided by (A) the Payment Token Issuer; or (B) a Merchant who agrees to provide goods or services to the Customer under an agreement with the Payment Token Issuer.
(ii)
The Customer may only use the Payment Token for making payments for goods or services provided by the Payment Token Issuer or a Merchant.
Examples are airline mileage programmes and customer loyalty schemes that provide Payment Tokens to customers to reward their patronage, and whereby such Payment Tokens are not redeemable for cash;
c)
Payment Tokens that can only be used as a Means of Payments for non-financial goods or services provided by the Payment Token Issuer; or
d)
Payment Tokens falling within Article (4)2.
2.
The Central Bank may exempt a Payment Token Issuer from licensing and other requirements under this Regulation with respect to its Payment Tokens, and specify the conditions for such exemption, where:
a)
if the Payment Token Issuer had to hold a Reserve of Assets in accordance with Article (22), the aggregate amount of the Reserve of Assets would not exceed half a million Dirham (500,000 AED) or its equivalent; and
b)
the aggregate number of Tokenholders is not more than 100.
3.
The Central Bank may determine that a Payment Token Service is not exempt or is no longer exempt and require the Person performing the service to apply for a License.
Part 4
Article (5): License Categories
1. A Person that intends to provide Payment Token Services shall as appropriate apply for one or more of the following categories of License:
a) Dirham Payment Token Issuer; b) Payment Token Custodian and Transferor; and c) Payment Token Conversion. 2. A Person not incorporated and located in the UAE may apply for a Foreign Payment Token Issuer Registration. For the avoidance of doubt, this includes a Person located in a Financial Free Zone. Article (6): License Conditions
1.
To be granted a License, an Applicant shall, at the time of submitting an Application:
a)
fulfil the legal form requirement as set out in Article (74) of the Central Bank Law;
b)
meet the respective initial capital requirements specified in Article (13) to (15); and
c)
provide the necessary documents and information specified in the Central Bank application form as provided by the Licensing Division.
2.
The Applicant must be a company incorporated in the UAE, including free zones but excluding Financial Free Zones
3.
An Applicant must meet, or demonstrate that it will meet upon License issuance, the ongoing requirements set out in Article (12) to Article (36), to the extent applicable to the License category for which it has applied, in particular:
a)
The requirements regarding regulatory capital as set out in Article (13) to Article (15). The Central Bank may add additional requirements regarding regulatory capital or increase the existing ones as a condition for License issuance, where it considers such additional requirements necessary;
b)
The requirements regarding corporate governance, general risk management and internal control, and accounting system as set out in Article (34). In particular, the Board, the Senior Management, and the Controller(s) must have been approved by the Central Bank as fit and proper in the context of the Application before the License is granted;
c)
The requirements regarding risk management policies and procedures for the management and protection of the Reserve of Assets, as set out in Article (22);
d)
The requirements regarding technology and specific risk management policies and procedures for managing the risks arising from the operation of the Payment Token business, as set out in Article (34) and Article (35);
e)
The requirements regarding business conduct and Customer protection as set out in Article (25) to Article (32); and
f)
The requirements regarding anti-money laundering and countering the financing of terrorism, as set out in Article (24).
4.
As part of the licensing process, separate face-to-face meetings between Central Bank staff and the Applicant’s and the Applicant’s Controllers’ Boards and the Senior Management may be conducted.
Independent assessments
5.
The Applicant is required to submit an independent assessment report not older than six (6) months assessing how it will comply with Article (6)3, covering at least the following key areas:
a)
capital requirements;
b)
corporate governance and risk management;
c)
Reserve of Assets management;
d)
technology risk management;
e)
payment security management;
f)
business continuity management;
g)
business conduct and Customer protection; and
h)
AML/CFT control systems.
6.
The Applicant must appoint one or more competent and qualified assessor(s), which are independent from the business units of the Applicant, to carry out the independent assessments. The assessors must not be involved in the operations to be reviewed or in selecting or implementing the relevant control measures to be reviewed, must have relevant knowledge and experience, and must be able to report their findings independently. They must also confirm to the Central Bank that there is no conflict of interest in the conduct of independent assessments.
7.
An Applicant for Payment Token Issuing shall, at the time of submitting an Application, provide a list of all Payment Tokens that it intends to issue. The Central Bank may require that the Applicant obtain a legal opinion for all Payment Tokens assessing whether the Payment Tokens and the operations of the Payment Token Issuer comply with Central Bank regulations including but not limited to whether the White Paper is accurate and the Reserve of Assets is properly held.
Article (7): Licensing Procedure
1. The licensing of Applicants shall be subject to the procedure envisaged in the Central Bank’s licensing manual.
Preliminary meeting with the Central Bank
2. Any Person that is interested in obtaining a License may obtain the Application form from the Licensing Division of the Central Bank.
3. The Senior Management of the Applicant is strongly encouraged to meet and discuss the Applicant’s Payment Token business plan with the Central Bank before submitting a formal Application.
Consultation with home regulator
4. Where a Controller of the Applicant is regulated by another authority, including by authorities in other jurisdictions, the Central Bank may contact the relevant authority about the Applicant to elicit the relevant authority’s views.
Completing and submitting the Application
5. An Application must be lodged with the Central Bank with the completed form and the required documents and information set out in the Annex to this Regulation.
Processing of Application
6. The Central Bank may seek any additional information it deems necessary from the Applicant to reach a decision on the Application.
7. Incomplete information may result in delays. Applicants should, therefore, pay attention to the following points:
a) All Applications must be submitted with documents and information listed in the Annex to this Regulation.;
b) Where an Application received is incomplete or supporting documents or information is lacking, the Applicant will be informed in writing that the Application will be treated as “draft” and will be asked to complete the Application or provide the missing information by a date specified by the Central Bank.;
c) Where information requested is not received by the specified date or a revised date agreed in writing by the Central Bank at the request of the Applicant, the Application may be treated as “suspended” and the Applicant will be notified of this in writing;
d) Where an Application is “suspended”, the Applicant will be informed in writing that the processing of the Application will cease temporarily. Suspended Applications will be reactivated only when the outstanding information is submitted; and
e) Where an Application is “suspended” for six (6) months or more for any reason, a new Application will be required if the Applicant wishes to pursue the matter further.
Approval of Application
8. The Central Bank may approve an Application for a License made by an Applicant provided that all the licensing criteria are met by the Applicant.
9. The Central Bank may grant the License without conditions or subject to any conditions attached. Conditions attached to a License may include, among others:
a) imposing a higher capital or liquidity requirement;
b) additional requirements relating to protection of the Reserve of Assets; and
c) restrictions on the Payment Token business or any secondary or ancillary businesses, or as to the maximum volume or value of Payment Tokens which may be issued.
10. After the Central Bank has granted a License to an Applicant, the Central Bank will:
a) assign a unique reference number to the License;
b) specify in the License the date on which the License has taken effect; and
c) list the details in (a) and (b) in a publicly available register on its website.
11. A Licensee must ensure that the License reference number of the License assigned to it by the Central Bank is clearly displayed on the Licensee’s website and promotional materials. Article (8): Application for a Non-Objection to perform Payment Token Conversion or Foreign Payment Token Custody and Transfer
1. A Virtual Assets Exchange Platform Operator may apply for a Non-Objection Registration in order to perform Payment Token Conversion.
2. A Bank or Exchange House may apply for a Non-Objection Registration in order to perform Dirham Payment Token Conversion.
3. A Person who is licensed by SCA or any Local Licensing Authority as a Virtual Assets Service Provider to provide custody services for Virtual Assets, may apply for a Non-Objection Registration to perform Payment Token Custody and Transfer of Foreign Payment Tokens. For the avoidance of doubt, any other Person seeking to perform Payment Token Custody and Transfer shall be required to obtain a Payment Token Custodian and Transferor license from the Central Bank.
4. To be granted a Non-Objection Registration, an Applicant must provide details in its Application of its SCA or Local Licensing Authority licensing status, where applicable, and the nature and extent of its SCA-licensed or Local Licensing Authority licensed business.
5. To be granted a Non-Objection Registration, an Applicant must demonstrate, in such manner as the Licensing Division may direct, that it will meet any conditions imposed by the Central Bank and the requirements listed in Article (8)10 or Article 8(11)
Non-Objection Registration process
6. To be granted a Registration as a Payment Token Conversion Provider or Foreign Payment Token Custodian and Transferor, an Applicant shall, at the time of submitting an Application, provide the necessary documents and information specified in the Central Bank application form as provided by the Licensing Division.
7. As part of the licensing process, separate face-to-face meetings between Central Bank staff and the Applicant’s and its Controllers’ Boards and Senior Management may be conducted.
8. Article (7) shall apply to Applicants and Applications for Registration as a Payment Token Conversion Provider or Foreign Payment Token Custodian and Transferor, for which purposes:
a) references to License, Licensee and licensing in that Article shall be construed as references to Non-Objection Registration, Registered Payment Token Conversion Provider and registration or Registered Foreign Payment Token Custodian and Transferor; and
b) the Applicant shall only be required to provide such information and documents listed in the Annex as the Central Bank may specify.
9. The Central Bank may contact SCA and any relevant Local Licensing Authority to obtain such information as the Central Bank considers relevant in relation to the Applicant, including in order to take into account:
a) the relevant authority’s views in respect of matters such as the financial soundness and the overall internal control environment of the Applicant, and whether SCA or any relevant Local Licensing Authority has any concern about that Applicant extending its business to include Payment Token Conversion; and
b) the relevant authority’s scope of and approach to regulation and supervision of the Applicant, in order to assist the Central Bank with determining which if any conditions or requirements of this Regulation (in addition to those listed in Article (7)9(c), Article (8)10 and Article (8)11, as applicable) the Central Bank will impose on the Applicant.
Application of this Regulation to Registered Payment Token Conversion Providers
10. Without prejudice to the other provisions of this Article (8), a Registered Payment Token Conversion Provider which is a Virtual Assets Exchange Platform Operator shall comply with the following Articles of this Regulation:
(i) Article (10);
(ii) Article (11);
(iii) Article (12);
(iv) Article (17)2;
(v) Article (18);
(vi) Article (24);
(vii) Article (25);
(viii) Article (33);
(ix) Article (34);
(x) Article (35);
(xi) Article (36);
(xii) Article (37); and
(xiii) Article (38),
to the extent provided for in those Articles.
11. Without prejudice to the other provisions of this Article (8) and without prejudice to the application of other laws and regulations, a Registered Payment Token Conversion Provider which is a Bank or Exchange House shall comply with the following Articles of this Regulation:
(i) Article (10);
(ii) Article (11);
(iii) Article (12);
(iv) Article (17)2;
(v) Article (18);
(vi) Article (23);
(vii) Article (24);
(viii) Article (25);
(ix) Article (27);
(x) Article (28);
(xi) Article (29);
(xii) Article (33);
(xiii) Article (34);
(xiv) Article (35);
(xv) Article (36);
(xvi) Article (37); and
(xvii) Article (38),
to the extent provided for in those Articles.
12. The Central Bank may apply any other provision or requirement under this Regulation, not already applicable, to a Registered Payment Token Conversion Provider or Registered Foreign Payment Token Custodian and Transferor if the Central Bank determines it necessary to do so to achieve its statutory objectives. Article (9): Foreign Payment Token Issuer Registration
1. A Person incorporated outside the UAE (which for the purposes of this Regulation would include a Person incorporated in a Financial Free Zone) may apply for a Registration as a Foreign Payment Token Issuer.
Registration process
2. To be granted a Registration as a Registered Foreign Payment Token Issuer, an Applicant shall, at the time of submitting an Application:
a) provide the necessary documents and information specified in the Central Bank application form as provided by the Licensing Division;
b) obtain written evidence of the non-objection from SCA or a Local Licensing Authority for the Registration based on a joint framework between the relevant authorities; and
c) demonstrate, in such a manner as the Licensing Division may direct, that it will meet any conditions which may be imposed by the Central Bank pursuant to Article (7)9(c) and the requirements listed in Article (9)7.
3. As part of the registration process, separate face-to-face meetings between Central Bank staff and the Applicant’s and its Controllers’ Boards and Senior Management may be conducted.
4. An Applicant for a Foreign Payment Token Issuer Registration shall, at the time of submitting an Application, provide a list of all Foreign Payment Tokens that it intends to issue and obtain a legal opinion on the assessment for all Foreign Payment Tokens. The legal opinion must assess whether the Foreign Payment Tokens and the operations of the Payment Token Issuer comply with this Regulation including but not limited to whether the White Paper is complete and accurate.
5. Article (7) shall apply to Applicants and Applications for Registration as a Foreign Payment Token Issuer, for which purposes:
a) references to License, Licensee and licensing in that Article shall be construed as references to Registration, Registered Foreign Payment Token Issuer and registration;
b) Article (7)3, Article (7)4, and Article (7)9(a) shall not apply; and
c) the Applicant shall only be required to provide such information and documents listed in the Annex as the Central Bank may specify.
6. Where the Applicant is regulated by another authority, including by authorities in other jurisdictions, the Central Bank may contact the relevant authority about the Applicant. The Central Bank may take into account the relevant authority’s views in respect of matters such as the financial soundness and the overall internal control environment of the Applicant, and whether the relevant authority has any concern about that Applicant extending its Payment Token business to the UAE.
Application of this Regulation to Registered Foreign Payment Token Issuers
7. Without prejudice to the remainder of this Article (9), a Registered Foreign Payment Token Issuer shall comply with the following Articles of this Regulation:
a) Article (10);
b) Article (11);
c) Article (12);
d) Article (17);
e) Article (18);
f) Article (21)1 to Article (21)5;
g) Article (24);
h) Article (25)1 and Article (25)3;
i) Article (26); and
j) to the extent provided for in those Articles.
8. A Registered Foreign Payment Token Issuer shall:
a) hold a reserve of the same value as the total value of Foreign Payment Tokens which that Foreign Payment Token Registree has issued, and denominated in the same currency as that of the Foreign Payment Tokens which that Foreign Payment Token Registree has issued;
b) procure and publish regular audits of the reserve referred to in (a) by an External Auditor;
c) at any time requested by the Central Bank, demonstrate that it holds Fiat Currency received from Customers for the issuance of Payment Tokens to equivalent standards of proper management and safekeeping as are set out in Article (22); and
d) comply with all laws, regulations and guidance which apply to it in the jurisdiction of its incorporation and in any other jurisdiction in which it operates, including but not limited to AML/CFT laws and regulations.
Article (10): Suspension, Withdrawal and Revocation of License or Registration
1. The Central Bank may suspend, withdraw or revoke a License or Registration as stipulated in the Central Bank Law. 2. Where a License or Registration is suspended, withdrawn or revoked, the Licensee or Registree must immediately cease to perform Payment Token Services. Part 5
Article (11): Authority Over Licensees and Registrees
1.
The Central Bank may take all measures and actions it deems appropriate in relation to a Licensee or Registree for achieving its objectives and discharging its functions, and may particularly take one or more of the following actions, if a material violation to the provisions of this Regulation has occurred:
a)
The Central Bank may require the concerned Licensee or Registree to take necessary actions to rectify the situation immediately;
b)
The Central Bank may appoint a specialized expert, or a Central Bank employee, to advise or guide the concerned Licensee or Registree or oversee some of its operations, for a period specified by the Central Bank. The concerned Licensee or Registree shall pay remuneration for such appointee if he is an expert from outside the Central Bank;
c)
The Central Bank may appoint a manager where the Central Bank is of the view that the management of a Licensee cannot be relied upon to take appropriate steps to rectify a situation. The main objectives of appointing a manager to take control of the management of a Licensee are:
(i)
to provide for the control of the affairs, business and property of a Licensee until such time as the Central Bank is satisfied that its concerns in relation to that Licensee have been addressed; or
(ii)
to safeguard the assets and maintain the business of the Licensee until a liquidator can be appointed;
d)
The Central Bank may take any other action or measure, or impose any penalties it deems appropriate, in relation to a Licensee or Registree.
2.
Where the Central Bank provides a Non-Objection Registration to a Virtual Assets Exchange Platform Operator, the Central Bank will coordinate with the relevant Local Licensing Authorities before and when taking any measures or actions under Article (11)1.
Article (12): Restrictions on Payment Tokens
1. All Payment Tokens issued by a Dirham Payment Token Issuer shall be denominated only in Dirham. 2. All Payment Tokens issued by a Foreign Payment Token Issuer shall be denominated only in a Foreign Currency. 3. A Payment Token Issuer may not (and may not arrange that another person shall) pay to or for the benefit of a Customer:
a) interest related to the length of time during which the Customer holds a Payment Token; or b) any other benefit related to the length of time during which the Customer holds a Payment Token, with respect to Payment Tokens for which the Payment Token Issuer performs Payment Token Issuing.
4. The Central Bank may place a limit(s) on:
a) the total volume or value of Payment Tokens which a Dirham Payment Token Issuer may sell or transfer, or restrict the sale or transfer of further Payment Tokens by that Payment Token Issuer; b) the total volume or value of Payment Tokens which a Foreign Payment Token Issuer may sell or transfer to Persons in the UAE, or restrict the sale or transfer of further Payment Tokens by that Payment Token Issuer to Persons in the UAE; c) the total number of Customers, or restrict the onboarding of new Customers, to which a Dirham Payment Token Issuer may sell or transfer its Payment Tokens; d) the total number of Customers in the UAE, or restrict the on-boarding of new Customers in the UAE, to which a Foreign Payment Token Issuer may sell or transfer its Payment Tokens; e) the total volume or value of Payment Tokens which a Payment Token Conversion Provider may buy, sell or admit to trading on its platform; and f) the total number of Customers to which a Payment Token Conversion Provider or Payment Token Custodian and Transferor may provide services, or the on-boarding of new Customers by that Payment Token Conversion Provider or Payment Token Custodian and Transferor. 5. If the Central Bank determines that to do so is necessary to achieve its statutory objectives, the Central Bank may impose any other restrictions on a specific Licensee or Registree, or across Licensees and Registrees. 6. If the Central Bank determines that to do so is necessary to achieve its statutory objectives, the Central Bank may designate any Virtual Asset to be a Payment Token whether or not it is sold or transferred by a Payment Token Issuer, and may impose any one or more of the restrictions set out in Article (12)4 in relation to such Designated Payment Token. 7. If the Central Bank imposes any restriction set out in Article (12)4, the Licensed Payment Token Service Provider, Registered Foreign Payment Token Issuer, Registered Foreign Payment Token Custodian and Transferor or Registered Payment Token Conversion Provider must:
a) provide the Central Bank with daily reporting evidence verifying its compliance with such restriction(s); and b) maintain policies and procedures to ensure that any breach of such a restriction is rectified promptly. Article (13): Regulatory Capital Requirement for Licensed Payment Token Issuers
1. A Licensed Payment Token Issuer must maintain at least:
a) Initial and ongoing capital of fifteen (15) million Dirhams; plus b) additional ongoing capital of at least 0.5% of the Fiat Currency face value of outstanding Payment Tokens. 2. A Payment Token Issuer subject to the alternative requirement for the Reserve of Assets as set out in Article (22)3 must, instead of the requirement in Article (13)1 above, maintain at least:
a) initial and ongoing capital of fifteen (15) million Dirhams; plus b) additional ongoing capital of at least 2% of the Fiat Currency face value of outstanding Payment Tokens. Article (14): Regulatory Capital Requirement for Licensed Payment Token Custodians and Transferors and Licensed Payment Token Conversion Providers
1. A Licensed Payment Token Service Provider performing Payment Token Custody and Transfer or Payment Token Conversion shall:
a) where the monthly average value of Payment Token Transfers initiated, facilitated, effected, directed or received by that Licensed Payment Token Service Provider as part of those Payment Token Services amounts to ten (10) million Dirhams or above, hold regulatory capital of at least three (3) million Dirhams; and
b) where the monthly average value of Payment Token Transfers initiated, facilitated, effected, directed or received by that Licensed Payment Token Service Provider as part of those Payment Token Services amounts to less than ten (10) million Dirhams, hold regulatory capital of at least one and a half (1.5) million Dirhams.
2. For a Licensed Payment Token Service Provider falling within Article (14)1(b) whose monthly average value of Payment Token Transfers referred to in Article (14)1 rises above ten (10) million Dirhams in three (3) consecutive months, the Licensee shall report this fact to the Central Bank and become subject to the higher regulatory capital requirement in Article (14)1(a).
3. The monthly average value of Payment Token Transfers referred to in Article (14)1 shall:
a) be calculated on the basis of the moving average of the preceding three (3) months or, where such data does not exist at the time of being granted a License by the Central Bank, on the basis of the business plan and financial projections provided; and
b) take into account both Payment Token Transfers initiated, facilitated, effected or directed by a Licensed Payment Token Service Provider and those received by the provider.
Article (15): Regulatory Capital Supplementary Requirements (for all Licensed Payment Token Service Providers)
1.
The Central Bank may impose aggregate regulatory capital requirements higher than that provided for in Article (13) and Article (14) if, taking into consideration the scale and complexity of the Licensee’s business, it considers such higher requirements essential to ensuring that the Licensee has the ability to fulfil its obligations under this Regulation.
2.
An Applicant shall provide information to the Central Bank on the source(s) of funds that constitute the regulatory capital held under Article (13) or Article (14).
Capital Items
3. A Licensed Payment Token Service Provider’s aggregate regulatory capital shall consist of:
a) Paid-up capital;
b) Reserves, excluding revaluation reserves; and
c) Retained earnings.
4. In addition to the capital requirement, an unconditional irrevocable bank guarantee equal to the full paid-up capital amount in favour of the Central Bank paid upon first demand, shall be submitted to the Central Bank with the application of the License. Such a guarantee must remain in place at all times.
5. Licensee must demonstrate that its regulatory capital and other financial resources are sufficient for implementing its business model in a safe, efficient and sustainable manner, without compromising the interests of Customers.
6. A Licensee must provide adequate details to the Central Bank on the source of funds that will be used to support the proposed business activities.
7. A Licensee must demonstrate that it will be able to maintain sufficient regulatory capital and other financial resources to facilitate an orderly wind-down of its Payment Token business, including a smooth refunding process. Deductions
8.
The following items shall be deducted from the aggregate regulatory capital:
a)
Accumulated losses;
b)
Anticipated losses in the first year of operation;
c)
Goodwill;
d)
Any assets encumbered to secure the unconditional irrevocable bank guarantee; and
e)
Any other items which the Central Bank may direct from time to time.
9.
If a Licensed Payment Token Service Provider is both:
a)
Licensed as a Payment Token Conversion Provider or Payment Token Custodian and Transferor; and
b)
licensed or regulated for any Virtual Asset activities by SCA or any Local Licensing Authority,
any regulatory capital it holds pursuant to requirements imposed by SCA or any Local Licensing Authority shall not contribute towards satisfying the regulatory capital requirements in this Article (15).
Article (16) Assessment of Controllers and Senior Management
1. A Person shall not become a Controller or member of Senior Management of a Licensed Payment Token Service Provider without obtaining prior approval from the Central Bank.
2. The Central Bank shall grant an approval under Article (16)1 if it considers that the proposed Controller or member of Senior Management meets all fit and proper requirements specified by the Central Bank.
3. The Central Bank may attach conditions to its approval under Article (16)1 of a Controller, including but not limited to:
a) conditions restricting or preventing the Person’s disposal or further acquisition of shares or voting powers in the Licensed Payment Token Service Provider; and
b) conditions restricting or preventing the Person’s exercise of voting power in the Licensed Payment Token Service Provider.
Article (17): Principal Business
1. The exclusive business of a Payment Token Issuer shall be the performance of the Payment Token Issuing for which it has been granted a License.
a) In addition to performing the sale or transfer of Payment Tokens that forms part of its Payment Token Issuing, a Payment Token Issuer shall be responsible for the generation of Payment Tokens, development and maintenance of associated technology required for Payment Tokens to operate in accordance with their White Paper and Customer Terms, and burning of Payment Tokens. If any of those activities are performed by another Person, they must be performed on behalf of the Payment Token Issuer and in accordance with the outsourcing requirements under Article (20).
2. The exclusive business of a Payment Token Conversion Provider or Payment Token Custodian and Transferor which is a Virtual Assets Exchange Platform Operator shall be the performance of:
a) any Payment Token Conversion and Payment Token Custody and Transfer activities for which it has been granted a License or Non-Objection Registration; and
b) any Virtual Asset activities for which it is licensed or regulated by SCA or any Local Licensing Authority prior to receipt of its License or Non-Objection Registration under this Regulation.
3. The exclusive business of a Payment Token Conversion Provider or Payment Token Custodian and Transferor which is an Exchange House shall be the performance of:
a) Any Payment Token Conversion and Payment Token Custody and Transfer activities for which it has been granted a License or Non-Objection Registration; and
b) any activities for which it is licensed or regulated by the CBUAE under the Regulations re Licensing and Monitoring of Exchange Business.
4. The exclusive business of a Payment Token Conversion Provider or Payment Token Custodian and Transferor which is licensed under the Retail Payment Services and Card Schemes Regulation or the Stored Value Facilities (SVF) Regulation shall be the performance of:
a) any Payment Token Conversion and Payment Token Custody and Transfer activities for which it has been granted a License; and
b) any activities for which it is licensed, regulated or otherwise approved by the CBUAE under the Retail Payment Services and Card Schemes Regulation or the Stored Value Facilities (SVF) Regulation
5. Except where one of Article (17)2 to Article (17)4 apply or the Payment Token Conversion Provider or Payment Token Custodian and Transferor is a Bank, the exclusive business of a Payment Token Conversion Provider or Payment Token Custodian and Transferor shall be the performance of any Payment Token Conversion and Payment Token Custody and Transfer activities for which it has been granted a License. Article (18): Notification and Reporting Requirements
1.
Where any material change affects the accuracy and completeness of information provided in an Application, the Applicant, Licensee or Registree, as the case may be, shall immediately notify the Central Bank of such change and provide all necessary information and documents.
2.
A Licensee or Registree shall immediately notify the Central Bank of any violation or potential violation of any provision of this Regulation or CBUAE Regulations. Such notification must be accompanied by details of adequate measures which the Licensee or Registree will implement to rectify the violation.
3.
A Licensee or Registree shall immediately notify the Central Bank if it becomes aware that any of the following events have occurred or are likely to occur:
a)
any event that prevents access to or disrupts the operations of the Licensee or Registree;
b)
any legal action taken against the Licensee or Registree either in the UAE or in a Third Country;
c)
the commencement of any insolvency, winding up, liquidation or equivalent proceedings in relation to the Licensee or Registree, or the appointment of any receiver, administrator or provisional liquidator under the laws of any country;
d)
any disciplinary measure or sanction taken against the Licensee or Registree or imposed on it by a regulatory body other than the Central Bank, whether in the UAE or in a Third Country;
e)
any change in regulatory requirements to which a Licensee or Registree is subject beyond those of the Central Bank, whether in the UAE or in a Third Country;
f)
any repeated occurrence of sales of a Payment Token at below its nominal/Fiat Currency face value where the sale is by or facilitated by the Licensee or Registree; or
g)
any other event specified by the Central Bank from time to time.
4.
Payment Token Conversion Providers and Payment Token Custodian and Transferors shall report to the Central Bank on the volume and value of business that they conduct in relation to Virtual Assets which are not Payment Tokens, in accordance with such reporting requirements as the Central Bank may determine from time to time.
5.
Licensees shall report to the Central Bank on their complaints management programme, including reporting on the number of complaints received, the topics of complaints, the number of open and closed complaints, and the amount of time complaints have been open or took to close, in accordance with such reporting requirements as the Central Bank may determine from time to time.
6.
Licensees and Registrees must comply with any further regular or ad-hoc reporting as determined by the Central Bank.
7.
Notwithstanding the paragraphs above, Licensees and Registrees shall, as appropriate and applicable, comply with their notification requirements as further specified in this Regulation, including but not limited to under:
a)
b)
c)
d)
e)
Article (19): Use of Agents
1. Where a Licensee intends to perform Payment Token Services through an Agent, it must conduct an assessment of such arrangement and provide a report to the Central Bank of the following:
a) name and address of each Agent;
b) assessment of the adequacy of the internal control mechanisms that will be used by the Agent in order to comply with the requirements of Article (33) and any CBUAE Regulations produced under it;
c) assessment of the Persons responsible for the management of the Agent, and evidence that they fulfil any fit and proper requirements specified by the Central Bank;
d) the scope of Payment Token Services for which the Agent is mandated; and
e) evidence of the Licensed Payment Token Service Provider’s adherence, in its contractual arrangements with the Agent, to Article (20).
2. The Central Bank shall assess the suitability of a proposed Agent and Agent arrangements based on the report submitted under Article (19)1, and may require the Licensee to supply additional information for its assessment.
a) Following its assessment, the Central Bank shall make a decision whether to approve or decline to approve the Agent.
b) The Licensee shall not engage an Agent to perform Payment Token Services before having received such approval.
3. Licensees shall contractually ensure that Agents acting on their behalf disclose this fact to Customers.
4. Licensees shall:
a) immediately notify the Central Bank of any change regarding their use of Agents; and
b) on an annual basis conduct an additional assessment and provide an additional report to the Central Bank of the matters listed in Article (19)1.
5. The Central Bank may suspend, withdraw or revoke its approval of an Agent. Where the approval of an Agent is suspended, withdrawn or revoked, the Licensee must ensure that the Agent immediately ceases to perform Payment Token Services on the Licensee’s behalf.
6. Licensees shall be responsible for ensuring and maintaining appropriate training and qualifications for their Agents.
7. A Payment Token Service performed by an Agent shall be treated as performed by its principal Licensees. Article (20): Outsourcing
All Licensees shall comply with the Outsourcing Regulation as if they were a “Bank” as defined in the Outsourcing Regulation.
Part 6
Article (21): Issuance and Redemption of Payment Tokens
1. A Payment Token Issuer must:
a) on receipt of payment for a Payment Token, without delay transfer the Payment Token to the Wallet nominated by the purchaser; and
b) at the request of the Tokenholder, without delay (and in any case by the same time on the next Business Day after the day on which the request was made, unless the Central Bank permits otherwise) redeem (or, in the case of a Foreign Payment Token, initiate redemption) in Fiat Currency at par value the Dirham (AED) or Foreign Currency denominated face value of the Payment Token presented by the Tokenholder to the Payment Token Issuer for redemption.
2. A Tokenholder may request redemption of a Payment Token without any limitation in time. The Central Bank may extend the Dormant Accounts Regulation, or any provision thereof to Payment Token Issuers.
3. A Tokenholder shall not be entitled to a Payment Token once it is redeemed.
4. A Payment Token Issuer must provide a Customer with a Customer Agreement that clearly and prominently states the conditions of redemption, including any fees relating to redemption, in good time before the parties enter into the Customer Agreement.
5. Redemption may be subject to a fee only where the fee is proportionate and commensurate with the costs actually incurred by the Payment Token Issuer.
6. A Licensed Payment Token Issuer must:
a) maintain a copy of the Distributed Ledger Technology on which its Payment Tokens are issued;
b) put in place a process to enable Customers to redeem their Payment Tokens in the event of a failure or other disruption of the Distributed Ledger Technology on which the Payment Token is issued, which does not rely on the normal operation of that Distributed Ledger Technology; and
c) in the event that a ‘fork’ or similar event which results in the creation of one or more versions of a Payment Token, redeem any one version of each Payment Token as if it were the version of the Payment Token that the Payment Token Issuer originally sold or transferred.
Article (22): Management and Safekeeping of the Reserve of Assets
Requirement for a Reserve of Assets
1. A Licensed Payment Token Issuer must have in place an effective and robust system to protect and manage the Reserve of Assets to ensure that the constituent assets:
a) are deployed for the prescribed usage only;
b) are protected against claims by other creditors of the Licensee in all circumstances; and
c) are protected from operational and other relevant risks.
Composition of the Reserve of Assets
2. A Licensed Payment Token Issuer must hold the Reserve of Assets as cash in a separate escrow account that:
a) is wholly denominated in the same currency as the Payment Tokens in relation to which it is held;
b) it holds in its name with another Person not in its Group which is a Bank licensed in the UAE;
c) is designated in such a way as to show that it is an account which is held for the purpose of safeguarding the Reserve of Assets in accordance with this Regulation; and
d) is used only for holding that Payment Token Issuer’s Reserve of Assets.
3. Where a Licensed Dirham Payment Token Issuer is a wholly-owned subsidiary of a Bank, it may choose, as an alternative to holding 100% of the Reserve of Assets in accordance with Article (22)2, to hold at least 50% of the Reserve of Assets as cash in accordance with Article (22)2 and invest the remaining portion of the Reserve of Assets in UAE government bonds and Central Bank of the UAE Monetary Bills (M-bills) that have an average duration of 6 months or less. If the Dirham Payment Token Issuer makes such a choice, it must hold regulatory capital in accordance with Article (13)2.
4. The Central Bank may require a Licensed Payment Token Issuer to hold the Reserve of Assets as cash in an account held with the Central Bank, rather than on one of the other bases permitted under this Article (22).
Protection of the Reserve of Assets
5. A Licensed Payment Token Issuer must put in place an effective contractual arrangement to ensure that, in the event of its insolvency, its Customers have a legal right and claim to payment of all amounts owed on the redemption of their Payment Tokens from the Reserve of Assets. A Licensed Payment Token Issuer shall, at the request of the Central Bank, seek an external legal opinion on the protection arrangement of the Reserve of Assets to ensure the legal soundness of the arrangements, and commission an independent review to ensure the operational soundness.
6. A Licensed Payment Token Issuer must ensure that no other Person has any claim on or interest in the Reserve of Assets.
7. The Reserve of Assets held in relation to one type of Payment Token must be segregated (including being held in a different account or Wallet) from that held in relation to any other type of Payment Token.
Management of the Reserve of Assets
8. A Licensed Payment Token Issuer must ensure that the value of its Reserve of Assets amounts at least to the total Fiat Currency face value of Payment Tokens in circulation, including without limitation by putting in place:
a) an adequate process to ensure timely and accurate records of cash or Payment Tokens paid into and out of a Reserve of Assets, with appropriately regular reconciliation between system records and the actual Reserve of Assets (e.g. balances of the account or Wallet holding the Reserve of Assets). Such reconciliation must be done at least on a daily basis and reported to the Central Bank daily;
b) a monthly audit by an External Auditor, who is not an officer or employee of the Payment Token Issuer or an officer or employee of another company or undertaking in its Group, to confirm that, during the course of the preceding month, the value of its Reserve of Assets amounted at all times at least to the total Fiat Currency face value of Payment Tokens in circulation; and
c) effective internal control measures and procedures, which constitute an integral part of the Licensee’s or Registree’s overall robust internal control system, to protect the Reserve of Assets from possible misappropriation and all operational risks, including the risk of theft, fraud and misappropriation.
Article (23) Safeguarding of Payment Tokens Held in Relation to the Performance of Payment Token Custody and Transfer
1. Payment Token Custodians and Transferors must keep Customer Payment Tokens in a separate Wallet from any Wallet that it uses to hold any other Virtual Assets.
2. A Wallet in which Customer Payment Tokens are placed under Article (23)1 must:
a) be designated as a Wallet held for the purpose of safeguarding or holding Customer Payment Tokens in accordance with this Regulation; and
b) be used only for holding those Customer Payment Tokens.
3. No person other than the Customer may have any interest in or right over the Customer Payment Tokens placed in a Wallet in accordance with Article (23)1.
4. The Payment Token Custodian and Transferor must keep a record of any Customer Payment Tokens segregated in accordance with Article (23)1.
Part 7
Article (24): Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organizations
1. This Article (24) applies to an AML Obligor in addition to, and without prejudice to, that AML Obligor’s obligations under other applicable UAE AML/CFT laws and regulations, including but not limited to the AML Law.
2. AML Obligors must comply with relevant and applicable UAE AML/CFT laws and regulations, address money laundering and terrorist financing risks through appropriate preventive measures to deter abuse of the sector as a conduit for illicit funds, detect money laundering and terrorist financing activities and report any suspicious transactions to the Financial Intelligence Unit at the Central Bank.
3. AML Obligors must have comprehensive and effective internal AML/CFT policies, procedures and controls in place.
4. AML Obligors shall be prohibited from invoking banking, professional or contractual secrecy as a pretext for refusing to perform their statutory reporting obligation in regard to suspicious activity.
5. Payment Token Services shall be considered to carry high money laundering and terrorist financing risk due to their speed, anonymity and cross-border nature.
6. AML Obligors must identify, assess, and understand the AML/CFT risks to which they are exposed and conduct enterprise-level and business relationship-specific risk assessments. Accordingly, all AML/CFT CDD, monitoring and controls must be risk-based and aligned to the risk assessments.
7. AML Obligors shall undertake an AML/CFT risk assessment and take appropriate measures to manage and mitigate the identified risks in accordance with applicable legal and regulatory requirements. AML Obligors shall comply with the FATF Guidance for a Risk-based Approach to Virtual Assets and Virtual Assets Service Providers, as may be supplemented from time to time, or any related standards or guidance in assessing and managing risks in Payment Token Services.
8. AML Obligors shall undertake periodic risk profiling of Customers and assessment based on the AML/CFT requirements.
9. AML Obligors shall assess whether a business relationship presents a higher money laundering and terrorist financing risk and assign a related risk rating. AML Obligors shall be prohibited from dealing in any way with shell banks or other shell financial institutions and from establishing or maintaining any business relationship or conducting any Payment Token Services under an anonymous or fictitious name or by pseudonym or number.
10. AML Obligors shall ensure that their CDD models are designed to address the specific risks posed by a Customer profile and Payment Token or Payment Token Service features. AML Obligors shall be prohibited from establishing or maintaining any business relationship with a Customer or performing any Payment Token Services for a Customer in the event that they are unable to complete adequate risk-based CDD measures for any reason for that Customer.
11. AML Obligors must undertake CDD measures concerning Wire Transfers as stipulated in the relevant provisions of the AML Law if Wire Transfer services are provided by the AML Obligor. AML Obligors must introduce appropriate systems for screening, as part of the CDD process, on all parties involved in a transaction against all applicable sanction lists (including the UN sanction lists and the names contained in the ‘search notices’/’search and freeze notices’ issued by the Central Bank).
12. If AML Obligors conduct Wire Transfers, they must take freezing action and prohibit conducting transactions with designated persons and entities, as per the obligations set out in the Central Bank’s Notice 103/2020 on the Implementation of United Nations Security Council (UNSC) and the UAE Cabinet Resolutions regarding UNSC and Local Lists, as amended from time to time.
13. AML Obligors must also be guided by FATF Standards on anti-money laundering and countering the financing of terrorism and proliferation. AML Obligors must incorporate the regular review of AML/CFT trends and typologies into their compliance training programmes as well as into their risk identification and assessment procedures.
Risk Factors
14. In assessing the risk associated with a Payment Token or Payment Token Service for the purposes of Article (24)6, 7, 10 and 13, AML Obligors must take into account the following risk factors:
a) maximum stored value or transaction amount of the Payment Token Service or Wallet – Payment Token Services or Wallets which enable higher transaction values or higher maximum stored value may increase the money laundering and terrorist financing risk;
b) methods of funding – Payment Token Services or Wallets that can be funded by cash or with little or no audit trail present a higher money laundering and terrorist financing risk. Funding from unverified sources or via other payment methods without Customer identification can also create an anonymous funding mechanism and hence present higher money laundering and terrorist financing risks;
c) cross-border usage – in general, Payments Tokens and Payment Token Services providing for cross-border usage may increase the risk as transactions may be subject to different AML/CFT requirements and oversight in other jurisdictions and also give rise to difficulties with information sharing;
d) person-to-person fund transfer function – Payments Tokens and Payment Token Services that allow person-to-person fund transfers may give rise to higher money laundering and terrorist financing risks;
e) cash withdrawal function – Payments Tokens and Payment Token Services that enable access to cash for instance through automated teller machine networks may increase the level of money laundering and terrorist financing risk;
f) holding of multiple Wallets – Payment Token Services that allow a Customer to hold more than one Wallet may also increase the money laundering and terrorist financing risk as it may be utilized by a third-party user other than the Customer;
g) payment for high-risk activities – some Merchant activities, for example, gaming, present higher money laundering and terrorist financing risks.
15. The money laundering and terrorist financing risks of a Payment Token or Payment Token Service can be reduced by implementing risk mitigating measures, which may include:
a) the application of limits on the maximum storage values, cumulative turnover or transaction amounts;
b) disallowing higher risk funding sources;
c) restricting the Payment Token Services from being used for higher risk activities;
d) restricting higher risk functions such as cash access; and
(e) implementing measures to detect multiple Wallets held by the same Customer or group of Customers.
16. The level of money laundering and terrorist financing risks posed by a particular Payment Token or Payment Token Service will depend on a consideration of all risk factors, the existence and effectiveness of risk mitigating measures and their functionality.
17. AML Obligors must assess whether a business relationship with a Customer presents a higher money laundering and terrorist financing risk and assign a related risk rating. Generally, the Customer risk assessment will be based on the information collected during the identification stage and subsequently updated as new information becomes available through ongoing due diligence and transaction monitoring. AML Obligors must ensure that their CDD models are designed to address the specific risks associated to its Customer profile and Payment Token or Payment Token Service features.
Compliance management arrangements
18. AML Obligors must have appropriate compliance management arrangements that facilitate their implementation of AML/CFT systems to comply with relevant legal and regulatory obligations and to manage money laundering and terrorist financing risks effectively. Compliance management arrangements must at a minimum include oversight by the AML Obligor’s Senior Management and appointment of a compliance officer and a money laundering reporting officer.
19. In addition, AML Obligors must put in place comprehensive AML/CFT policies and procedures in accordance with the AML/CFT laws and regulations.
Use of technology
20. The Central Bank supports innovative means by which AML Obligors implement AML/CFT systems effectively as well as exploring the greater use of technology and analytical tools. The Central Bank expects AML Obligors, before introducing any new product, service or technology, to conduct adequate risk assessments and ensure that any identified risks are effectively managed or mitigated.
21. In general, the electronic Know Your Customer process currently adopted by licensed banks for digital onboarding of Customers is acceptable for Wallet opening and provision of Payment Token Services. No physical face-to-face meetings with the Customer or physical documents verification are required so long as the digital authentication of the Customer and digital verification of all required documents can be done in accordance with the existing requirements of the Central Bank.
22. Depending on the nature of relationship, AML Obligors may undertake additional CDD measures, including the collection of sufficient information to adequately understand the nature of the Customer’s business. The extent of CDD measure should be commensurate with the assessed money laundering and terrorist financing risks of the Customer.
23. Globally there is an emerging range of new products and services involving Virtual Assets. In line with the FATF standards, before an AML Obligor offers any new products relating to Virtual Assets, it must undertake money laundering and terrorist financing risk assessment and take appropriate measures to manage and mitigate the identified risks in accordance with applicable legal and regulatory requirements. AML Obligors are encouraged to refer to the suggestions provided by the FATF Guidance for a risk-based approach to Virtual Assets.
Part 8
Article (25): Obligations Towards Customers
1. Licensees and Registrees must be operated prudently and with competence in a manner that will not adversely affect the interests of their Customers.
a) In addition, Licensees and Registrees must also observe and comply with the relevant regulatory requirements and standards on consumer protection of the Central Bank, including all relevant provisions of the Consumer Protection Regulation.
b) For the avoidance of doubt, in case of discrepancies between this Regulation and the Consumer Protection Regulation, the respective provisions of the Consumer Protection Regulation shall prevail.
2. Licensees and Registered Payment Token Conversion Providers must:
a) maintain a copy of each Distributed Ledger Technology on which it provides Payment Token Services; and
b) in the event that a ‘fork’ or similar event results in the creation of two or more versions of a Payment Token, treat any one version of each Payment Token presented by a Customer as being equal to any other version of the same type of Payment Token and as if it were the version of the Payment Token to which its Payment Token Service applies.
3. Licensees and Registrees must ensure that their business is operated in a responsible, honest and professional manner. Licensees and Registrees must treat all Customers, as well as merchants, equitably, honestly and fairly at all stages of their relationship with the Licensee or Registree. Licensees and Registrees must also act in a manner that will not adversely affect the interests of their Customer.
4. Licensees and Registered Payment Token Conversion Providers must be responsible for the acts or omissions of their Senior Management, employees, service providers and Agents in respect of the conduct of its business. Senior Management, employees and Agents of Licensees and Registered Payment Token Conversion Providers must be properly trained and qualified.
5. Licensees and Registered Payment Token Conversion Providers must ensure that they adopt and, if needed, develop good business practices that can demonstrate their standard of conduct, including as follows:
a) Due diligence must be performed by Licensees and Registered Payment Token Conversion Providers to ensure that all promotional materials it issues are accurate and not misleading;
b) Licensees and Registered Payment Token Conversion Providers may use their websites and mobile apps to provide links to other online merchants. Before providing such links, the Licensee or Registered Payment Token Conversion Provider must carry out due diligence on the merchants to ascertain they are bona fide companies conducting legitimate business so as to manage reputational risk;
c) Websites or apps of Licensees and Registered Payment Token Conversion Providers may only provide hyper-links to other websites that offer advisory and/or sale of Payment Token Services, or financial products and services, if the arrangements comply with all relevant legal and regulatory requirements. The Central Bank may require that the Licensee or Registered Payment Token Conversion Provider obtain a legal opinion assessing whether such arrangements comply with all relevant legal and regulatory requirements; and
d) Licensees and Registered Payment Token Conversion Providers shall adhere to such other disclosure or customer communications requirements as the Central Bank may direct in CBUAE Regulations from time to time or otherwise require.
Article (26): Payment Token White Papers
1. Obligation to publish a White Paper
a) No Payment Token Issuer shall perform Payment Token Issuing with respect to a Payment Token unless that Payment Token Issuer has:
(1) produced a White Paper in respect of that Payment Token;
(2) submitted the White Paper to the Central Bank;
(3) received the Central Bank’s acceptance of the White Paper; and
(4) published the White Paper,
in accordance with this Article (26).
b) The Central Bank may publish a White Paper with respect to a particular Payment Token on its website, in which case any Payment Token Issuer which publishes a web-link to the White Paper on the Central Bank website shall be deemed to have complied with Article (26)1(a).
2. Content and form of the White Paper
a) A White Paper shall contain, insofar as it is relevant to each Licensee or Registered Foreign Payment Token Issuer, a detailed description of all of the following: I. the Payment Token Issuer;
II. the type of Payment Token that will be offered to the public;
III. the number of Payment Tokens that will be issued and the issue price;
IV. the rights and obligations attached to the Payment Token and the procedures and conditions for exercising those rights;
V. information on the underlying technology and standards applied by the Payment Token Issuer when allowing for the holding, storing and transfer of those Payment Tokens;
VI. the risks relating to the Payment Token Issuer issuing Payment Tokens, the Payment Tokens, the offer to the public, and other disclosures that the Central Bank may specify;
VII. the Payment Token Issuer’s governance arrangements, including a description of the role, responsibilities and accountability of the third-parties responsible for operating, investment and custody of the Reserve of Assets, and, where applicable, the distribution of the Payment Tokens;
VIII. the constituent parts of the Reserve of Assets held by the Licensed Payment Token Issuer or similar reserve held by a Registered Foreign Payment Token Issuer;
IX. the custody arrangements for the Reserve of Assets or similar reserve held by a Registered Foreign Payment Token Issuer, including but not limited to the relevant segregation and safeguarding measures;
X. information on the nature and enforceability of rights, including any direct redemption right or any claims that holders of Payment Tokens may have on the Reserve of Assets (or other reserve held by a Registered Foreign Payment Token Issuer) or against the Payment Token Issuer issuing the Payment Tokens, including how such rights may be treated in insolvency procedures;
XI. information on the permitted use of a Payment Token and any restrictions on its use including having regard to Article (2) and Article (12); and
XII. any such other matters as the Central Bank may direct from time to time.
b) The White Paper shall be fair, clear and not misleading, and shall be presented in a concise and comprehensible form.
c) The White Paper shall be drafted in both Arabic and English.
d) The White Paper shall contain an attestation by the Board of the Payment Token Issuer of the White Paper’s completeness and accuracy.
e) The White Paper shall prominently contain the following statement:
“The Central Bank of the UAE is not responsible for determining the accuracy or completeness of this White Paper. The Central Bank of the UAE’s review and acceptance of this White Paper does not constitute an endorsement of the Payment Token or Payment Token Issuer to which it relates, or of the accuracy or completeness of any information or statements in this White Paper.”
f) The White Paper shall be dated, including with the date of the application of any update to the White Paper.
g) In good time before a Licensed Payment Token Issuer enters into a Customer Agreement, or a Registree enters into an agreement with a Customer relating to a Payment Token, it must (subject to Article (26)5) provide a copy of or web-link to the White Papers of all Payment Tokens to which the Customer has access pursuant to the Customer Agreement.
3. Updates
A Payment Token Issuer must (subject to Article (26)5) without delay update any White Paper it has previously produced to reflect:
a) any material change to the information in the White Paper; or
b) any material addition that it would be appropriate to make to the White Paper in order to reflect any changes in the arrangements or circumstances relating to its Payment Tokens or Payment Token Issuing.
4. Audit
A Payment Token Issuer must procure an audit of a White Paper by an External Auditor, who is not an officer or employee of the Payment Token Issuer or an officer or employee of another company or undertaking in its Group, to confirm that the form and content of the White Paper complies with all applicable requirements of Article (26)2(a) to (f).
5. Notification of the White Paper
a) A Payment Token Issuer must submit a White Paper to the Central Bank for review and acceptance before it sells or transfers the Payment Token to any Person in the UAE (excluding a Person in a Financial Free Zone).
1. The Payment Token Issuer must, at the time when it submits a White Paper to the Central Bank, also submit the audit report of that White Paper, referred to in Article (26)4, to the Central Bank for review.
2. If the Central Bank accepts the White Paper, the Payment Token Issuer must publish the White Paper on a publicly and freely accessible website at least 7 days in advance of the Payment Token becoming available for sale or transfer to Persons in the UAE (excluding a Person in a Financial Free Zone).
3. If the Central Bank declines to accept the White Paper the Payment Token issuer may resubmit an updated White Paper for approval under this Article (26)5(a).
b) If a Payment Token Issuer desires to amend (including, for the avoidance of doubt, making additions), or is required to amend, the White Paper previously submitted in accordance with Article (26)5(a), it must submit the amendments to the White Paper, and an audit report of the amended White Paper conducted in accordance with Article (26)4 to the Central Bank for review and acceptance before making the amendments. If the amendments are urgent, the Payment Token Issuer shall prominently bring the urgency to the attention of the Central Bank.
(1) If the Central Bank accepts the amendments, the Payment Token Issuer must publish the White Paper on a publicly and freely accessible website at least 14 days in advance of such amendment taking effect unless the Central Bank requires or agrees to a shorter period.
(2) If the Central Bank declines to accept the amendments the Payment Token issuer may resubmit an updated White Paper for approval under this Article (26)5(b).
c) The Central Bank shall not be responsible for determining the accuracy or completeness of a White Paper. The Central Bank’s review and acceptance of the White Paper shall not constitute an endorsement of the Payment Token or Payment Token Issuer to which it relates, or of the accuracy or completeness of any information or statements in the White Paper.
6. Liability for White Papers
a) A Payment Token Issuer shall be liable for and shall compensate a Customer within at least 28 calendar days for any and all loss or damage caused to a Customer arising from a material misstatement in a White Paper which it has published, except to the extent that any UAE law or regulation prevents the payment or provision of compensation to that Customer by the Payment Token Issuer. Any contractual exclusion or limitation of civil liability as referred to in this paragraph shall be deprived of legal effect.
b) In addition, the Central Bank may consider conducting an investigation and taking enforcement action against any misstatement in the White Paper.
c) The Central Bank shall not be liable to Customers or other Persons for the contents of any White Paper that it has accepted.
7. Exemptions The Central Bank may, at its discretion, exempt a Payment Token Issuer from one or more of the requirements in this Article (26) if equivalent documentation has been published, or obligations complied with, pursuant to regulation issued by SCA or any Local Licensing Authority.
Article (27): Customer Agreement
1. In this Article (27), “Payment Token Service Provider” refers to a Licensee or a Registree, with the exception of Registered Foreign Payment Token Issuers.
2. A Payment Token Service Provider shall:
a) set out in the Customer Agreement the terms and conditions governing their contractual relationship with each Customer, including the terms required under Article (28), sufficiently in advance of entering into the contractual relationship as to allow the Customer to make an informed decision; and
b) provide each Customer and Tokenholder with a copy of the Customer Agreement, at their request at any time in writing and delivered as per the Customer’s or Tokenholder’s preference, including through an e-mail, mobile application or any other electronic manner.
3. The Customer Agreement (and any changes to it) referred to in Article (27)2 shall be written in a clear, plain and understandable language, in a manner that is not misleading and shall be provided to the Customer in both Arabic and English, as may be requested by the Customer.
4. Any changes to the Customer Agreement referred to in Article (27)2 shall be communicated to the Customer and Tokenholder by the Payment Token Service Provider sufficiently in advance and at least 30 calendar days prior to any such change becoming effective.
5. A Customer or Tokenholder shall be entitled to terminate its Customer Agreement with a Payment Token Service Provider at no charge where it does not agree with the revised terms and conditions referred to in Article (27)4.
6. The rights and obligations set out in a Customer Agreement shall apply as between a Payment Token Issuer and each Tokenholder, whether or not the Payment Token Issuer is aware of the identity of the Tokenholder or has made any arrangements with the Tokenholder, subject to any UAE laws which would prevent the Payment Token Issuer from performing its obligations under a Customer Agreement for that Tokenholder. Article (28): Required Terms and Pre-Contractual Information
1. In this Article (28), “Payment Token Service Provider” refers to a Licensee or a Registree, with the exception of Registered Foreign Payment Token Issuers.
2. A Payment Token Service Provider shall include the following terms in, and information with, its Customer Agreement, and must provide them to the Customer before the provision of any services:
a) schedule of fees, charges and commissions, including redemption fees, conversion rates and withdrawal charges, where applicable;
b) contact details of the Payment Token Service Provider, including legal name and registered address, and including the name and address of any Agent where applicable;
c) the form and procedure for giving consent to the initiation, facilitation, effecting or directing by a Payment Token Service Provider as part of its Payment Token Service; of a Payment Token Transfer and for the withdrawal of such consent;
d) the communication channel between the Payment Token Service Provider and the Customer;
e) the manner of safeguarding of Payment Tokens as per Article (23);
f) the manner and timeline for notification by the Customer to the Payment Token Service Provider in case of Unauthorized Payment Token Transfers or incorrectly initiated, facilitated, effected or directed Payment Token Transfers;
g) the Payment Token Service Provider’s and Customer’s or Tokenholder’s liability for Unauthorized Payment Token Transfers;
h) information relating to terms under which a Customer may be deemed to have accepted changes to the Customer Agreement, the duration of the Customer Agreement and the rights of the parties to terminate the Customer Agreement;
i) the service level for the provision of the Payment Token Service; and
j) information on the Payment Token Service Provider’s complaint procedure.
Article (29): Transactional Information
1. In this Article (29), “Payment Token Service Provider” refers to a Licensee or a Registree, with the exception of Registered Foreign Payment Token Issuers.
2. Payment Token Service Providers shall provide Customers with a written or an electronic statement of the Payment Token Transfers initiated, facilitated, effected, directed or received by a Payment Token Service Provider under a Customer Agreement at least once per month free of charge. The statement shall include details of (insofar as relevant) the amounts, fees, charges and commissions, the dates and times of performance and the reference numbers for each Payment Token Transfer.
3. Immediately after the receipt of an instruction for initiation, facilitation, effecting or directing of a Payment Token Transfer, the Payment Token Service Provider of the Payer shall provide a receipt for the Payer with the following information insofar as relevant:
a) confirmation of the successful or unsuccessful performance of the Payment Token Transfer;
b) acknowledgement and reference number to track the status of the Payment Token Transfer, including:
(i) the date, time and amount of the Payment Token Transfer; and
(ii) information relating to the Payee;
c) the amount of the Payment Token Transfer, any related fees or charges, including any actual currency and conversion rates used, and withdrawal charges, where applicable; and
d) the date and time on which the Payment Token Service Provider received the instruction for the Payment Token Transfer.
4. The Payee’s Payment Token Service Provider shall, immediately after receipt of a Payment Token Transfer, provide to the Payee with a statement with the following information insofar as relevant:
a) reference enabling the Payee to identify the Payment Token Transfer and, where appropriate, the Payer and any information transferred with the Payment Token Transfer;
b) the amount of the Payment Token Transfer in the currency in which the Payment Token is denominated;
c) the amount of any fees or charges for the Payment Token Transfer payable by the Payee;
d) where applicable, the currency exchange rate used in the Payment Token Transfer by the Payee’s Licensed Payment Token Service Provider; and
e) the date and time on which the amount of a Payment Token Transfer is received into the Payee’s Wallet.
5. The Payer’s Payment Token Service Provider shall ensure that instructions for a Payment Token Transfer are accompanied by the necessary information so that they can be processed accurately and completely, and also, be easily identified, verified, reviewed, audited and for any subsequent investigation if needed.
6. The Payee’s Payment Token Service Provider shall implement procedures to detect when any necessary information is missing or inaccurate for a Payment Token Transfer. Article (30): Protection of Payment and Personal Data
1. A Licensed Payment Token Service Provider shall have in place and maintain adequate policies and procedures to protect Personal Data received or held by the provider and identify, prevent and resolve any data security breaches.
2. Licensed Payment Token Service Providers may disclose such Personal Data to:
a) a third party where the disclosure is made with the prior written consent of the Customer or is required pursuant to applicable laws;
b) the Central Bank;
c) other regulatory authorities upon request/following prior approval of the Central Bank;
d) a court of law; or
e) other government bodies who have lawfully authorized rights of access.
3. In addition to the disclosures envisaged in Article (30)2, Licensed Payment Token Service Providers may also disclose Personal Data to the corresponding Data Subject.
4. Licensed Payment Token Service Providers shall have in place and maintain Personal Data protection controls.
5. Personal Data shall be stored and maintained in the UAE unless otherwise approved by the Central Bank. Licensed Payment Token Service Providers must also establish a safe and secure backup of all Personal Data in a separate location for the required period of retention of five (5) years.
6. Licensed Payment Token Service Providers shall comply with applicable legal and regulatory requirements and standards on data protection, including as set out in or pursuant to the Consumer Protection Regulation. They shall control, process and retain only Personal Data that is necessary for the provision of Payment Token Services and upon obtaining the explicit consent of the Customer.
Article (31): Liability for Unauthorized Payment Token Transfers and Refunds
1. A Payment Token Custodian and Transferor shall be fully liable for any fraudulent or Unauthorized Payment Token Transfer initiated, facilitated, effected or directed by the Payment Token Custodian and Transferor or otherwise made from a Wallet maintained by the Payment Token Custodian and Transferor, whether before or after the Customer as Payer informs the Payment Token Custodian and Transferor of any potential or suspected fraud, except where there is evidence that:
a) the Customer acted fraudulently; or
b) the Customer acted with gross negligence and did not take reasonable steps to keep their Wallet safe.
2. The Payment Token Custodian and Transferor shall refund the amount of the Unauthorized Payment Token Transfer for which it is liable to its Customer and, where applicable, restore the debited Wallet to the state it would have been in had the Unauthorized Payment Token Transfer not taken place.
3. The Payment Token Custodian and Transferor shall provide a refund under Article (31)2 as soon as practicable and in any event no later than the end of the Business Day following the day on which it becomes aware of the Unauthorized Payment Token Transfer.
4. Article (31)2 and Article (31)3 do not apply where the Payment Token Custodian and Transferor has reasonable grounds to suspect that fraud or gross negligence as referred to in Article (31)1 applies, and notifies the Central Bank of those grounds in writing.
5. Other than in relation to the circumstances contemplated in paragraphs Article (31)2 to Article (31)4, on conclusion of an investigation by a Payment Token Custodian and Transferor into an error or Complaint, a Payment Token Custodian and Transferor shall pay any refund or monetary compensation due to a Customer within (7) calendar days of such conclusion or instruction. In case of a delay in payment of any refund or compensation, the Payment Token Custodian and Transferor shall update the Customer with the expected time for crediting the amount due, along with a justification for the delay.
Article (32): Certainty of Transfers of Payment Tokens
1. Licensed Payment Token Issuers must exercise prudence and due diligence in their choice of Distributed Ledger Technology for their Payment Tokens, to ensure that the Distributed Ledger Technology is technologically resilient, secure and has a clear operating procedure in which Customers can identify and understand the point at which a Payment Token passes from one Wallet to another. A copy of this due diligence must be provided to the Central Bank as part of the Licensed Payment Token Issuer’s Application.
2. Licensed Payment Token Issuers must specify, in their White Paper and Customer Agreement, the point at which the lawful power of disposal over a Payment Token transfers from a sending Tokenholder to a receiving Tokenholder in a Payment Token Transfer. This must be specific to the Distributed Ledger Technology of the Payment Token.
3. A Person may provide evidence to a Licensed Payment Token Issuer demonstrating that, but for a ‘fork’, error or similar failure in the operation of the Distributed Ledger Technology of a Payment Token, they would be the Tokenholder of that Token, in which case the Licensed Payment Token Issuer shall give them the same rights of redemption as are given to a Tokenholder pursuant to Article (21).
4. A Licensed Payment Token Issuer must include a warning in the White Paper and Customer Agreement for each Payment Token that they issue, that:
a) there is always a risk that a Payment Token Transfer may fail or be reversed or unwound as a result of the operation of the Distributed Ledger Technology, and that anyone who believes they are the victim of a failed or unwound transfer must contact the Payment Token Issuer which issued that Payment Token to ensure that they are compensated in accordance with Article (32)3; and
b) the Licensed Payment Token Issuer has no control over the time that a Payment Token Transfer may take to complete on the Distributed Ledger Technology, and that (aside from their obligation to submit a Payment Token Transfer to the Distributed Ledger Technology for execution) they are not responsible for ensuring that a Payment Token Transfer completes within a specific time-period. Nevertheless a comprehensive audit trail must be made available to the Customer.
Part 9
Article (33): Corporate Governance
1. In this Article (33), “Payment Token Service Provider” refers to a Licensee or a Registree, with the exception of Registered Foreign Payment Token Issuers.
2. A Payment Token Service Provider must have and maintain effective, robust and well-documented corporate governance arrangements, including a clear organizational structure with well-defined, transparent and consistent lines of responsibility.
3. The corporate governance arrangements referred to in Article (33)2 must be comprehensive and proportionate to the nature, scale and complexity of the Payment Token Services provided, and shall contain, at a minimum:
a) an organization chart showing each division, department or unit, indicating the name of each responsible individual accompanied by a description of the respective function and responsibilities;
b) controls on conflicts of interest;
c) controls on integrity and transparency of the Licensed Payment Token Service Provider’s operations;
d) controls to ensure compliance with applicable laws and regulations;
e) methods for maintaining confidentiality of information; and
f) procedures for regular monitoring and auditing of all corporate governance arrangements.
Article (34): General Risk Management & Internal Control Systems
1. In this Article (34), “Payment Token Service Provider” refers to a Licensee or a Registree, with the exception of Registered Foreign Payment Token Issuers.
2. A Payment Token Service Provider must have and maintain robust and comprehensive policies and procedures to identify, manage, monitor and report the risks arising from the provision of Payment Token Services to which it is or might become exposed, and adequate internal control mechanisms, including sound administrative and accounting procedures.
3. A Payment Token Service Provider’s risk management policies and procedures shall be:
a) kept up-to-date;
b) reviewed annually; and
c) proportionate to the nature, scale and complexity of the Payment Token Services provided.
4. A Payment Token Service Provider must establish a risk management function, an internal audit function and a compliance function.
Capital adequacy and capital planning
5. A Payment Token Service Provider must implement an effective process for managing its capital adequacy. This process must monitor capital adequacy over time and include forward-estimations of the level of capital and the capital requirement, and ensure that the Payment Token Service Provider at a minimum complies at all times with the capital requirements set out in this regulation.
Liquidity risk management
6. A Payment Token Service Provider must establish and implement an effective process for managing liquidity risk that is appropriate for the size and complexity of its operations. The objective is to ensure that the Payment Token Service Provider will have sufficient liquidity to meet different financial obligations arising from its day-to-day operations as well as redemption requests under all plausible circumstances.
Internal controls
7. A Payment Token Service Provider must put in place a robust internal control system to promote effective and efficient operation, safeguard assets, provide reliable financial and management information, enable prevention or early detection of irregularities, fraud and errors, and ensure compliance with relevant statutory and regulatory requirements and internal policies.
8. A Payment Token Service Provider must put in place a comprehensive business strategy and plan, including details on the strategic goals and roadmap. A business plan must normally cover proposed business in terms of geographical scope of operations, target markets and Customer breakdown, client types and base size, product and services offering, delivery channels, pricing strategy, and promotion and marketing activities.
Accounting and External Audit
9. A Payment Token Service Provider must appoint one or more External Auditor(s) to audit, on an annual basis:
a) the financial statements or consolidated financial statements of the Payment Token Service Provider prepared in accordance with the accepted accounting standards and practices; and
b) the systems, controls and technology (including any ‘smart contracts’) of the Payment Token Services provided by the Payment Token Service Provider, including the results of any penetration or cyber-attack simulation testing performed pursuant to Article (35)17, separately from any audit of non-Payment Token Services.
10. Upon request by the Central Bank, the appointed External Auditor shall submit, directly or through the Payment Token Service Provider, a report of the audit in a form and within a timeframe acceptable to the Central Bank.
11. In addition to the report of audit, the Central Bank may request the External Auditor to:
a) submit any additional information in relation to the audit, if the Central Bank considers it necessary;
b) enlarge or extend the scope of the audit;
c) carry out any other examination.
Compliance and internal audit functions
12. A Payment Token Service Provider must maintain effective compliance and internal audit functions; to ensure compliance with all applicable legal and regulatory requirements as well as its own policies, procedures and controls. Among other factors, the quality of a Payment Token Service Provider’s compliance and internal audit functions will be assessed by the Central Bank based on its:
a) clear governance framework with Board level accountability to ensure effective policies and sufficient authorities to perform the functions;
b) relevant professional knowledge and experience;
c) independence from business units;
d) direct and unfettered access to the Board;
e) coverage, comprehensiveness and effectiveness of compliance and internal audit programs; and
f) ability to take timely and pro- active rectifying actions upon identifying non-compliance or other control deficiencies.
13. A Payment Token Service Provider must at least annually perform a risk assessment by its own risk management.
a) If the results of the risk assessment suggest that a detailed independent assessment is necessary, the Payment Token Service Provider must conduct such assessment and cover the following key areas:
(i) business model assessment;
(ii) corporate governance and risk management;
(iii) Reserve of Assets management;
(iv) technology risk management;
(v) security management;
(vi) business continuity management;
(vii) business conduct and consumer protection;
(viii) business exit plan; and
(ix) AML/CFT controls systems.
b) If the Payment Token Service Provider has an independent function elsewhere in its Group, with the relevant knowledge and experience, an independent assessment can be conducted by its internal function. Otherwise the assessment must be carried out by an independent third party.
14. A Payment Token Service Provider must submit any assessment under Article (34)13 to the Central Bank after it has been approved by the Board, accompanied by an executive summary highlighting the key risks, most important findings and the actions for rectifying the issues.
15. Arising from the findings of the annual risk assessment, a Payment Token Service Provider that is unable to meet its obligations must immediately report this to the Central Bank.
Reputation Risk Management
16. A Payment Token Service Provider shall establish and implement an effective process for managing reputational risk that is appropriate for the size and complexity of its operations.
Record Keeping
17. Payment Token Service Providers shall keep all necessary records of Personal Data and Payment Data for a period of five (5) years from the date of receipt of such data, unless otherwise required by other applicable laws or the Central Bank.
Article (35): Technology Risk and Information Security
1. In this Article (35), “Payment Token Service Provider” refers to a Licensee or a Registree, with the exception of Registered Foreign Payment Token Issuers.
2. Payment Token Service Providers are expected to take into account international best practices and standards when designing and implementing the technology and specific risk management systems and processes.
3. A Payment Token Service Provider shall establish an effective technology and cyber security risk management framework to ensure the adequacy of IT controls, cyber resilience, the quality and security, including the reliability, robustness, stability and availability, of its computer systems, and the safety and efficiency of the operations of Payment Token Services. The framework shall be fit for purpose and commensurate with the risks associated with the nature, size, complexity and types of business and operations, the technologies adopted and the overall risk management system of the Payment Token Service Provider. Consideration shall be given to adopting recognized international standards and practices when formulating such risk management framework.
4. A Payment Token Service Provider’s effective technology risk management framework shall comprise proper IT governance, a continuous technology risk management process and implementation of sound IT control practices.
5. Payment Token Service Provider shall apply and meet at a minimum the UAE Information Assurance Standards, as amended.
6. Licensed Payment Token Issuers must maintain policies and procedures on how to respond to ‘forking’ events or adverse governance actions affecting the Distributed Ledger Technology in which their Payment Tokens are issued, including by establishing a process to ensure that redemption rights are afforded in accordance with Article (21)6(c), and to prevent redemption by Persons who are not Tokenholders. Such policies and procedures must address each blockchain in which a Payment Token is issued.
7. Licensed Payment Token Issuers which hold any Payment Tokens which they have issued (on their own behalf) must maintain a safeguarding and security policy setting out the manner in which the security of those Payment Tokens shall be ensured.
IT Governance
8. A Payment Token Service Provider shall establish a proper IT governance framework. IT governance shall cover various aspects, including a clear structure of IT functions and the establishment of IT control policies. While there could be different constructs, the major functions shall include an effective IT function, a robust technology risk management function, and an independent technology audit function.
9. The Board, or a committee designated by the Board shall be responsible for ensuring that a sound and robust risk management framework is established and maintained to manage technology risks in a manner that is commensurate with the risks posed by the Payment Token Service Provider’s Payment Token Services.
Security Requirements
10. A Payment Token Service Provider must clearly define its security requirements in the early stage of system development or acquisition as part of the business requirements and these must be adequately built-in during the system development stage.
11. A Payment Token Service Provider that develops or provides an application programming interface (API) shall establish safeguards to manage the development and provision of the API to secure the interaction and exchange of data between various software applications.
Network and Infrastructure Management
12. A Payment Token Service Provider shall clearly assign overall responsibility for network management to individuals who are equipped with expertise to fulfil their duties. Network standards, design, diagrams and operating procedures shall be formally documented, kept up-to-date, communicated to all relevant network staff and reviewed periodically.
13. A Payment Token Service Provider shall establish a security administration function and a set of formal procedures for administering the allocation of access rights to system resources and application systems, and monitoring the use of system resources to detect any unusual or unauthorized activities.
14. A Payment Token Service Provider shall exercise due care when controlling the use of and access to privileged and emergency IDs. The necessary control procedures include:
a) changing the default password;
b) implement strong password control, with minimum password length and history, password complexity as well as maximum validity period;
c) restricting the number of privileged users;
d) implementing strong controls over remote access by privileged users;
e) granting of authorities that are strictly necessary to privileged and emergency IDs;
f) formal approval by appropriate senior personnel prior to being released for usage;
g) logging, preserving and monitoring of the activities performed by privileged and emergency IDs (e.g. peer reviews of activity logs);
h) prohibiting sharing of privileged accounts;
i) proper safeguard of privileged and emergency IDs and passwords (e.g. kept in a sealed envelope and locked up inside the data centre); and
j) changing of privileged and emergency IDs’ passwords immediately upon return by the requesters.
Cyber Security Risk
15. A Payment Token Service Provider shall ensure that its cyber security risks are adequately managed through its technology risk management process. The Payment Token Service Provider shall also commit adequate skilled resources to ensure its capability to identify the risk, protect its critical services against the attack, contain the impact of cyber security incidents and restore the services.
16. A Payment Token Service Provider shall establish a cyber incident response and management plan to swiftly isolate and neutralize a cyber threat and to resume affected services as soon as possible. The plan shall describe procedures to respond to plausible cyber threat scenarios.
17. A Payment Token Service Provider shall regularly assess the necessity to perform penetration and cyber-attack simulation testing, based on a risk-based assessment of the likelihood of a cyber-attack and its impact (considering amongst other things the size and nature of its business). Coverage and scope of testing shall be based on the cyber security risk profile, cyber intelligence information available, covering not only networks (both external and internal) and application systems but also social engineering and emerging cyber threats. A Payment Token Service Provider shall also take appropriate actions to mitigate the issues, threats and vulnerabilities identified in penetration and cyber-attack simulation testing in a timely manner, based on the impact and risk exposure analysis. The Central Bank may request evidence of the risk-based assessment referred to in this paragraph, and may direct that further or alternative penetration and cyber-attack simulation testing measures be adopted.
Customer Authentication
18. A Payment Token Service Provider shall select and implement reliable and effective authentication techniques to validate the identity and authority of its Customers or Tokenholders. Multi-factor authentication shall be required.
19. End-to-end encryption shall be implemented for the transmission of Customer passwords so that they are not exposed at any intermediate nodes between the Customer mobile application or browser and the system where passwords are verified.
Login Attempts and Session Management
20. A Payment Token Service Provider shall implement effective controls to limit the number of login or authentication attempts (e.g. wrong password entries), implementing time-out controls and setting time limits for the validity of authentication. If one-time passwords are used for authentication purposes, a Payment Token Service Provider shall ensure that the validity period of such passwords is limited to the strict minimum necessary.
21. A Payment Token Service Provider shall have processes in place ensuring that all Payment Token Transfers occurring in the context of its Payment Token Services are logged with an appropriate audit trail.
Fraud Detection Systems
22. Payment Transaction monitoring mechanisms designed to prevent, detect and block fraudulent Payment Transactions must be operated by a Payment Token Service Provider, in a manner which is proportionate based on a risk-based assessment of the likelihood of fraudulent Payment Transactions and their impact (considering amongst other things the size and nature of its business). Suspicious or high-risk transactions must be subject to a specific screening, filtration and evaluation procedure. The Central Bank may request evidence of such risk-based assessment, and may direct that further or alternative monitoring mechanisms be adopted.
Security advice for Customers
23. A Payment Token Service Provider must provide easy-to-understand, prominent and regularly reviewed advice from time to time via effective methods and multiple channels to its Customers and Tokenholders on security precautionary measures.
24. A Payment Token Service Provider must manage the risk associated with fraudulent emails, websites and mobile applications, which are designed to trick customers into revealing sensitive user information such as login identifiers, passwords and one-time passwords.
Security incident reporting
25. Payment Token Service Providers shall report major security and operational incidents including downtimes to the Central Bank, either immediately or in such form and on such basis as the Central Bank may direct from time to time, or as set out in CBUAE Regulations.
Article (36): Business Continuity
1. In this Article (36), “Payment Token Service Provider” refers to a Licensee or a Registree, with the exception of Registered Foreign Payment Token Issuers.
2. A Payment Token Service Provider shall have in place an adequate business continuity management program to ensure continuation, timely recovery, or in extreme situations orderly scale-down of critical operations in the event of major disruptions caused by different contingent scenarios. An adequate business continuity management program comprises business impact analysis, recovery strategies, a business continuity plan and alternative sites for business and IT recovery.
3. A Payment Token Service Provider shall put in place a set of recovery strategies to ensure that all critical business functions identified in a business impact analysis can be recovered in accordance with the predefined recovery timeframe. These recovery strategies shall be clearly documented, thoroughly tested and regularly reviewed to ensure achievement of recovery targets.
4. A Payment Token Service Provider shall put in place effective measures to ensure that all business records, in particular Customer records, can be timely restored in case they are lost, damaged, or destroyed. A Payment Token Service Provider shall also allow Customers to access their own records in a timely manner. A Payment Token Service Provider shall notify Customers of any loss in their records through an operational failure or through theft, and make reasonable effort to ensure that personal records so lost are not used wrongfully.
5. A Payment Token Service Provider shall develop a business continuity plan based on the business impact analysis and related recovery strategies. A business continuity plan shall comprise, at a minimum:
a) detailed recovery procedures to ensure full accomplishment of the service recovery strategies;
b) escalation procedures and crisis management protocol (e.g. set up of a command centre, timely reporting to the Central Bank, etc.) in case of severe or prolonged service disruptions;
c) proactive communication strategies (e.g. Customer notification, media response, etc.);
d) updated contact details of key personnel involved in the business continuity plan; and
e) assignment of primary and alternate personnel responsible for recovery of critical systems.
6. A Payment Token Service Provider shall conduct testing of its business continuity plan at least annually. Its Senior Management, primary and alternate relevant personnel shall participate in the annual testing to familiarize themselves with their recovery responsibilities.
7. A Payment Token Service Provider shall review all business continuity planning-related risks and assumptions for relevance and appropriateness as part of the annual planning of testing. Formal testing documentation, including a test plan, scenarios, procedures and results, shall be produced. A post mortem review report shall be prepared for formal sign-off by Senior Management.
Business exit plan
8. With a view to minimizing the potential impact that a failure, disruption, or exit of a Payment Token Service Provider would have on Customers and the payment systems in the UAE, a Payment Token Service Provider is required to maintain viable plans for an orderly exit of its business and operations should other options be proven not possible.
9. Among other things, a business exit plan must:
a) identify a range of remote but plausible scenarios which may render it necessary for a Payment Token Service Provider to consider an exit;
b) develop risk indicators to gauge the plausibility of the identified scenarios;
c) set out detailed, concrete, and feasible action steps to be taken upon triggering the exit plan;
d) assess the time and cost required to implement the exit plan in an orderly manner; and
e) set out clear procedures to ensure that sufficient time and regulatory capital and other financial resources are available to implement the exit plan.
10. A Payment Token Service Provider must review the plan on an annual basis to ensure its relevance and workability.
Part 10
Article (37): Enforcement and Sanctions
Violation of any provision of this Regulation or committing any of the violations provided for under the Central Bank Law may subject the Licensee or Registree to administrative and financial sanctions and penalties as deemed appropriate by the Central Bank.
Article (38): Additional Information Gathering Powers
1. The Central Bank may require the following persons to provide it with such information as the Central Bank considers necessary:
a) Licensees and Registrees;
b) providers of Virtual Asset services who are not Licensed or Registered by the Central Bank or licensed or regulated by SCA or any Local Licensing Authority with respect to those activities.
2. The Central Bank may enter into information-sharing agreements or other memoranda of understanding with, or otherwise request the following persons to provide it with such information as the Central Bank considers helpful in order to exercise its powers or meet its objectives under this Regulation:
a) SCA;
b) any Local Licensing Authority;
c) other regulators.
Article (39): Amendment to Retail Payment Services and Card Schemes Regulation and Stored Value Facilities (SVF) Regulation
1. A Person licensed under the Retail Payment Services and Card Schemes Regulation or Stored Value Facilities (SVF) Regulation with respect to Crypto-Asset, Virtual Asset Token or Virtual Asset activities shall cease to be licensed with respect to those activities under either Regulation following the end of the Transition Period. 2. The Retail Payment Services and Card Schemes Regulation shall not apply with respect to Crypto-Assets, Virtual Asset Tokens, Virtual Assets Service Providers or Virtual Asset Token Services (each as defined in the Retail Payment Services and Card Schemes Regulation), with effect from the end of the Transition Period. 3. The Stored Value Facilities (SVF) Regulation shall not apply with respect to Crypto-Assets, Virtual Assets or Virtual Asset Service Providers (each as defined in the Stored Value Facilities (SVF) Regulation), with effect from the end of the Transition Period. Article (40): Transition Period
1. There shall be a one calendar year period following the commencement of this Regulation during which Article (2) shall not apply (the “Transition Period”).
2. The Central Bank may extend the Transition Period at its discretion.
3. Notwithstanding Article (40)1, if the Central Bank determines that a service provider is unlikely to be able to comply with any provision of Article (2) following the Transition Period, it may order the cessation of any aspect of that service provider’s business which is within scope of this Regulation.
Article (41): Interpretation of Regulation
The Regulatory Development Department of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
Article (42): Publication & Application
This Regulation shall be published in the Official Gazette in both Arabic and English and shall come into effect one month from the date of publication.
Annex
List of documents to be submitted in an application
1.
Completed application form for License
2.
A report on paid-up capital certified by External Auditor
3.
A copy of the ownership structure
4.
The latest audited financial statements for each Controller
5.
Completed application form(s) for each Controller
6.
Outline of the Senior Management and staff structure
7.
Completed application forms for members of the Board and Senior Management
8.
Independent assessment report(s) on the key areas as set out in Article (6)5
9.
Documentation on the sources of funds (Article (15)2 and Article (15)6)
10.
A copy of the cyber-security policy
11.
Risk management policies and procedures
12.
Policies and procedures regarding AML/CFT risk
13.
A copy of the risk appetite framework
14.
Copies of policies and procedures for managing the Reserve of Assets
15.
A copy of the investment policy for managing the investment of Reserve of Assets
16.
A copy of any Customer Agreements to be used
17.
Business plan that covers a three-year time horizon
18.
A copy of the business exit plan
19.
Board resolution in support of the Application
20.
A copy of the articles of association (or equivalent) of the Applicant company in English and Arabic
21.
A copy of the Applicant's audited annual reports and / or audited financial statements for the past three financial years immediately prior to application
22.
Each of the following:
(a)
A copy of the notarized Memorandum and Articles of Association
(b)
A copy of the Licensee Commercial License
(c)
External Auditor's certification that the paid-up capital has been injected into the business
Sustainable Finance
Shari’ah Supervision
Guidance Note Re Annual Shari'ah Report of Internal Shari'ah Supervision Committee*
N 5330/2020 Effective from 10/12/2020The Central Bank is pleased to attach herewith the Guidance Note Re Annual Shari’ah Report of Internal Shari’ah Supervision Committee, which applies to licensed financial institutions that conduct all or part of their activities and businesses in accordance with the provisions of Islamic Shari’ah (Islamic Financial Institutions).
This Guidance Note must be read in conjunction with the regulations, standards and resolutions issued by the Central Bank and the Higher Shari’ah Authority.
This Guidance Note is mandatory and effective from the date of this notice.
Please bring this Guidance Note to the attention of the board of directors of your institution at the next board meeting.
*This document was drafted in Arabic and translated to English. In case of any differences in interpretation, the Arabic version shall prevail.
Article (1) Introduction
1.1. This Guidance Note Re Annual Shari’ah Report of Internal Shari’ah Supervision Committee (“Guidance Note” or “Note”) complements the requirements outlined in:
- Decretal Federal Law No. (14) of 2018 Regarding the Central Bank and Organization of Financial Institutions and Activities; and
- Standard Re Shari’ah Governance for Islamic Financial Institutions issued by the Central Bank.
with the aim to promote development of the banking system and to ensure its effectiveness and efficiency.
- 1.2. Islamic Financial Institutions (“IFIs”) are required to have Shari’ah governance policies and mechanisms to ascertain that Annual Shari’ah Report that is issued by the Internal Shari’ah Supervision Committee (“Annual Shari’ah Report”) is compliant with requirements outlined in this Guidance Note, and applicable standards and regulations.
- 1.3. Where the Guidance Note contains a stipulation (in an article) to provide information, or undertake certain measures, or address particular terms, as a minimum requirement, the Central Bank may impose (new) requirements additional to those specified in the relevant article (of the Guidance Note).
Article (2) Objectives
- 2.1. The Guidance Note contains guidance aimed at facilitating implementation of the requirements related to the issuance of Annual Shari’ah Report.
- 2.2. The Guidance Note provides clarity on the supervisory expectations with respect to Annual Shari’ah Report.
- 2.1. The Guidance Note contains guidance aimed at facilitating implementation of the requirements related to the issuance of Annual Shari’ah Report.
Article (3) Scope of Application
- 3.1. The Guidance Note applies to all IFIs.
- 3.2. The Guidance Note must be read in conjunction with the standards and resolutions issued by Higher Shari’ah Authority (HSA) and notified to IFIs.
- 3.1. The Guidance Note applies to all IFIs.
Article (4) General Requirements for Issuing the Annual Shari'ah Report
- 4.1. The Annual Shari’ah Report represents annual disclosure of the Internal Shari’ah Supervision Committee (ISSC) on the level of IFI’s compliance with Islamic Shari’ah. Accordingly, responsibility for preparing the annual Shari’ah report rests with the ISSC of IFI within the mechanisms and requirements stipulated in the Guidance Note.
- 4.2. The Annual Shari’ah Report should be presented at the general assembly in accordance with the applicable regulatory requirements.
- 4.3. The Annual Shari’ah Report shall be submitted to HSA for review and approval prior to its submission at the general assembly.
- 4.4. The Annual Shari’ah Report must be submitted to the HSA, no later than two (2) months from end of the financial year.
- 4.5. The ISSC must verify accuracy and validity of all information in the Annual Shari’ah Report before its submission to the HSA.
- 4.6. The Board must ensure that the Annual Shari’ah Report is submitted to HSA for review and approval prior for its submission at the general assembly.
- 4.7. The ISSC must ascertain that all information required to be stated in the Annual Shari’ah Report (as stipulated in the template in article No. 5.3) are included in the designated places of the report before submitting it to HSA.
- 4.8. The ISSC must ensure that all duties fulfilled by the ISSC, as outlined in the Annual Shari’ah Report, are well documented for audit purposes.
- 4.9. IFI shall publish the Annual Shari’ah Report in the IFI’s disclosures of the financial statement and other available means.
- 4.1. The Annual Shari’ah Report represents annual disclosure of the Internal Shari’ah Supervision Committee (ISSC) on the level of IFI’s compliance with Islamic Shari’ah. Accordingly, responsibility for preparing the annual Shari’ah report rests with the ISSC of IFI within the mechanisms and requirements stipulated in the Guidance Note.
Article (5) Template for the Annual Shari'ah Report
- 5.1. Template of the Annual Shari’ah Report (as per below) represents the principal information and disclosures, and minimum requirements for information that should be included in the report.
- 5.2. The ISSC may add other information to the Annual Shari’ah Report, if necessary, according to the template in the Guidance Note.
- 5.1. Template of the Annual Shari’ah Report (as per below) represents the principal information and disclosures, and minimum requirements for information that should be included in the report.
(5/3) Template for the Annual Shari'ah Report (English)
Annual Report of the Internal Shari'ah Supervision Committee of (name of the financial institution)
Issued on: (issue date)
To: Shareholders of (name of the Financial Institution) (“the Institution”)
After greetings,
Pursuant to requirements stipulated in the relevant laws, regulations and standards (“the Regulatory Requirements”), the Internal Shari’ah Supervision Committee of the Institution (“ISSC”) presents to you the ISSC’s Annual Report (in case of Islamic windows add: (regarding Shari’ah compliant businesses and operations of the Institution)) for the financial year ending on 31 December --------- (“Financial Year”).
- Responsibility of the ISSC
In accordance with the Regulatory Requirements and the ISSC’s charter, the ISSC’s responsibility is stipulated as to:- undertake Shari’ah supervision of all businesses, activities, products, services, contracts, documents and business charters of the Institution; and the Institution’s policies, accounting standards, operations and activities in general, memorandum of association, charter, financial statements, allocation of expenditures and costs, and distribution of profits between holders of investment accounts and shareholders (“Institution’s Activities”) and issue Shari’ah resolutions in this regard, and
- determine Shari’ah parameters necessary for the Institution’s Activities, and the Institution’s compliance with Islamic Shari’ah within the framework of the rules, principles, and standards set by the Higher Shari’ah Authority (“HSA”) to ascertain compliance of the Institution with Islamic Shari’ah.
The senior management is responsible for compliance of the Institution with Islamic Shari’ah in accordance with the HSA’s resolutions, fatwas, and opinions, and the ISSC’s resolutions within the framework of the rules, principles, and standards set by the HSA (“Compliance with Islamic Shari’ah”) in all Institution’s Activities, and the Board bears the ultimate responsibility in this regard.
- undertake Shari’ah supervision of all businesses, activities, products, services, contracts, documents and business charters of the Institution; and the Institution’s policies, accounting standards, operations and activities in general, memorandum of association, charter, financial statements, allocation of expenditures and costs, and distribution of profits between holders of investment accounts and shareholders (“Institution’s Activities”) and issue Shari’ah resolutions in this regard, and
- Shari’ah Standards
In accordance with the HSA’s resolution (No. 18/3/2018), and with effect from 01/09/2018, the ISSC has abided by the Shari’ah standards issued by the Accounting and Auditing Organization for Islamic Financial Institutions (AAOIFI) as minimum Shari’ah requirements, in all fatwas, approvals, endorsements and recommendations, relating to the Institution’s Activities without exception. - Duties Fulfilled by the ISSC During the Financial Year
The ISSC conducted Shari’ah supervision of the Institution’s Activities by reviewing those Activities, and monitoring them through the internal Shari’ah control division or section, internal Shari’ah audit, and (if applicable) external Shari’ah audit, in accordance with the ISSC’s authorities and responsibilities, and pursuant to the Regulatory Requirements in this regard. The ISSC’s activities included the following:- Convening (number) meetings during the year.
- Issuing fatwas, resolutions and opinions on matters presented to the ISSC in relation to the Institution’s Activities.
- Monitoring compliance of policies, procedures, accounting standards, product structures, contracts, documentation, business charters, and other documentation submitted by the Institution to the ISSC for approval.
- Ascertaining the level of compliance of allocation of expenditures and costs, and distribution of profits between investment accounts holders and shareholders with parameters set by the ISSC.
- Supervision through the internal Shari’ah control division or section, internal Shari’ah audit, and (if applicable) external Shari’ah audit, of the Institution’s Activities including supervision of executed transactions and adopted procedures on the basis of samples selected from executed transactions, and reviewing reports submitted in this regard.
- Providing guidance to relevant parties in the Institution — to rectify (where possible) incidents cited in the reports prepared by internal Shari’ah control division or section, internal Shari’ah audit, and/or (if applicable) external Shari’ah audit — and issuing of resolutions to set aside revenue derived from transactions in which non-compliances were identified for such revenue to be disposed towards charitable purposes.
- Approving corrective and preventive measures related to identified incidents to preclude their reoccurrence in the future.
- Specifying the amount of Zakat due on each share of the Institution (if applicable).
- Communicating with the Board and its subcommittees, and the senior management of the Institution (as needed) concerning the Institution’s compliance with Islamic Shari’ah.
- (add other works that the ISSC wants to mention in this report)
The ISSC sought to obtain all information and interpretations deemed necessary in order to reach a reasonable degree of certainty that the Institution is compliant with Islamic Shari’ah. (the phrase “External Shari’ah audit” is included in the report if applicable, otherwise it should be deleted.)
- Independence of the ISSC
The ISSC acknowledges that it has carried out all of its duties independently and with the support and cooperation of the senior management and the Board of the Institution. The ISSC received the required assistance to access all documents and data, and to discuss all amendments and Shari’ah requirements. (Factors that have affected independence, if any, should be mentioned).
- The ISSC’s Opinion on the Shari’ah Compliance Status of the Institution
Premised on information and explanations that were provided to us with the aim of ascertaining compliance with Islamic Shari’ah, the ISSC has concluded with a reasonable level of confidence, that the Institution’s Activities are in compliance with Islamic Shari’ah, except for the incidents of non-compliance observed, as highlighted in the relevant reports. The ISSC also provided directions to take appropriate measure in this regard.
(Add a statement on any other breaches to the Shari’ah provisions, resolutions and controls established by the Higher Shari’ah authority, if applicable)
The ISSC formed its opinion, as outlined above, exclusively on the basis of information perused by the ISSC during the financial year.
Signatures of members of the Internal Shari’ah Supervision Committee of the Institution
Member’s Name Type of Membership Signature Member’s Name Type of Membership Signature Member’s Name Type of Membership Signature Member’s Name Type of Membership Signature Member’s Name Type of Membership Signature (End of the Template) - Responsibility of the ISSC
Guidance Note Re Charter of Internal Shari'ah Supervision Committee
N 5325/2020 Effective from 10/12/2020The Central Bank is pleased to attach herewith the Guidance Note Re Charter of Internal Shari’ah Supervision Committee, which applies to licensed financial institutions that conduct all or part of their activities and businesses in accordance with the provisions of Islamic Shari’ah (Islamic Financial Institutions).
This Guidance Note must be read in conjunction with the regulations, standards and resolutions issued by the Central Bank and the Higher Shari’ah Authority.
This Guidance Note is mandatory and effective from the date of this notice, taking into account what is stated in Article No. (4.2) of the Guidance Note.
Please bring this Guidance Note to the attention of the board of directors of your institution at the next board meeting.
Article (1) Introduction
- 1.1 This Guidance Note Re Charter of Internal Shari’ah Supervision Committee (“Guidance Note” or “Note”) complements the Standard Re Shari’ah Governance for licensed financial institutions that conduct all or part of their activities and businesses in accordance with the provisions of Islamic Shari’ah (“Islamic Financial Institutions” or “IFIs”) that was issued by the Central Bank (“Shari’ah Governance Standard” or “SGS”) with the aim to promote development of the banking system and to ensure its effectiveness and efficiency.
- 1.2. IFIs must establish Shari’ah governance policies and governance mechanisms to ascertain that the adopted Charter of Internal Shari’ah Supervision Committee (“Charter”) is compliant with requirements outlined in the Guidance Note and requirements outlined in the regulations, standards and resolutions issued by the Central Bank and the Higher Shari’ah Authority (“Regulations, Standards and Resolutions”).
- 1.3. Where the Guidance Note contains a stipulation (in an article) to provide information, or undertake certain measures, or address particular terms, as a minimum requirement, the Central Bank may impose (new) requirements additional to those specified in the relevant article (of the Guidance Note).
- 1.1 This Guidance Note Re Charter of Internal Shari’ah Supervision Committee (“Guidance Note” or “Note”) complements the Standard Re Shari’ah Governance for licensed financial institutions that conduct all or part of their activities and businesses in accordance with the provisions of Islamic Shari’ah (“Islamic Financial Institutions” or “IFIs”) that was issued by the Central Bank (“Shari’ah Governance Standard” or “SGS”) with the aim to promote development of the banking system and to ensure its effectiveness and efficiency.
Article (2) Objectives
- 2.1. The Guidance Note contains guidance aimed at facilitating implementation of requirements specified in the SGS related to establishment of the Charter.
- 2.2. The Guidance Note provides clarity on the supervisory expectations with respect to the Charter.
- 2.1. The Guidance Note contains guidance aimed at facilitating implementation of requirements specified in the SGS related to establishment of the Charter.
Article (3) Scope of Application
- 3.1. The Guidance Note applies to all IFIs.
- 3.2. The Guidance Note must be read in conjunction with the SGS and the standards and resolutions issued by HSA and notified to IFIs.
- 3.1. The Guidance Note applies to all IFIs.
Article (4) Compliance and Charter Template
- 4.1. Template of the Charter in Article No. 5 represents minimum requirement, and IFI may add additional paragraphs to its Charter provided such addition does not contradict requirements specified in the Regulations, Standards, and Resolutions.
- 4.2. The IFIs should comply with the Charter’s Template from 21 April 2021.
- 4.1. Template of the Charter in Article No. 5 represents minimum requirement, and IFI may add additional paragraphs to its Charter provided such addition does not contradict requirements specified in the Regulations, Standards, and Resolutions.
Article (5) Charter's Template
(template)
Charter for Internal Shari’ah Supervision Committee in (insert the name of the Islamic Financial Institution)
1. Introduction
- 1.1. This charter specifies the functional controls of Internal Shari’ah Supervision Committee of (insert the name of the Islamic Financial Institution) (“IFI”), and its meetings management, decision-making process, and other organizational matters (“Charter”).
2. Definition of Internal Shari'ah Supervision Committee
- 2.1. Internal Shari’ah Supervision Committee (“ISSC”) is a body, appointed by the IFI, comprised of scholars specialized in Islamic financial transactions, with the mandate to independently supervise transactions, activities, and products of the IFI and ensures they are compliant with Islamic Shari’ah in all its objectives, activities, operations, and code of conduct and other mandates stated in the relevant laws and standards.
3. Qualification of Members of ISSC
- 3.1. A member of the ISSC must meet the eligibility and competency requirements stipulated in the regulations, standards and resolutions issued by the Central Bank and the Higher Shar’ah Authority (“Regulations, Standards and Resolutions”).
4.Independence of the ISSC
- 4.1. It is mandatory to comply with the controls and guidelines specified in the Regulations, Standards and Resolutions to ascertain independence of the ISSC members.
5 Appointment of ISSC, Membership Period, Dismissal and Resignation of the Members
- 5.1. It is mandatory to adhere to the relevant standards regarding:
- appointment and formation of the ISSC,
- duration of the membership,
- dismissal or resignation of its members,
as specified in the Regulations, Standards and Resolutions. The ISSC should select from among its members a chairperson and a deputy chairperson in its first meeting.
- 5.1. It is mandatory to adhere to the relevant standards regarding:
6 Responsibilities and Authorities of the ISSC
- 6.1. It is mandatory to adhere to the standards regarding responsibilities of the ISSC stipulated in the Regulations, Standards and Resolutions.
7 The ISSC's Meetings and Issuance of Resolutions
- 7.1. The ISSC must meet regularly, at least four times in the fiscal year, and the period between two meetings should not exceed 120 days.
- 7.2. Quorum for ISSC meeting is constituted by presence of majority of its members. The ISSC resolutions are issued by the majority of its attending members, and in case of tied votes, the side with the chairperson prevails. The opinion of the member who is not in favour of the ISSC’s resolution must be recorded in the minutes of meeting with its reasoning.
- 7.3. Attendance of an ISSC member must not be less than 75% of the total meetings held during a year. An ISSC member may attend or convene the meeting in full through video or audio means of communication, if necessary, provided that this is recorded in the minutes of the meeting and approved by the ISSC members.
- 7.4. The ISSC may invite to its meeting the IFI’s directors, employees, experts, advisors, and other parties that ISSC decides in order to obtain clarification regarding data and information needed by ISSC in relation to the issues under their review. For the avoidance of doubt, the invitees are not entitled to vote on the ISSC’s resolutions.
- 7.5. The ISSC may issue resolutions by circulation in urgent cases, provided unanimity is reached. Resolution issued by circulation must be recorded in the minutes of the first meeting held after the issuance. In case of a disagreement, the ISSC should hold a meeting as soon as possible.
- 7.6. Resolutions of the ISSC must be:
- written in a clear form, and
- accompanied by procedures necessary for implementation of the provisions contained therein in a manner that ensures adequate execution. The ISSC specifies the details that must be accompanied with the resolution in relation to its implementation.
- 7.1. The ISSC must meet regularly, at least four times in the fiscal year, and the period between two meetings should not exceed 120 days.
8 Methodology of ISSC's Functions
- 8.1.a.The ISSC must thoroughly investigate matters on its agenda to establish adequate (fact-based) understanding related to nature of the presented matter. If a matter does not become clear to the ISSC, it may postpone issuance of the resolution or request additional information or supporting studies, and accordingly (in this case) the subject matter shall be presented again after the request is addressed.
- b.The IFIs must provide the ISSC with adequate time to:
- i.investigate the matters submitted to the ISSC, and
- ii.review any contracts and documents that may relate to the presented matters.
- b.The IFIs must provide the ISSC with adequate time to:
- 8.2.The ISSC should trace the Shari’ah ruling on the matter it is examining by:
- a.leveraging the legal opinions of Shari’ah jurists in the credible schools of law, and
- b.ensuring that the Shari’ah ruling does not contradict the Shari’ah standards or resolutions adopted by the HSA, even if such ruling differs from rulings issued by the ISSC in the past.
- 8.3.Fatwas issued by ISSCs of other institutions (i) are not binding on the IFI’s ISSC, and (ii) existence of those fatwas do not obviate the need for a resolution from the IFI’s ISSC, even if the members are same.
- 8.4.The resolutions of the ISSC are binding on its respective IFI in accordance with the applicable laws and standards.
- 8.5.The IFI must comply with interpretations of the ISSC regarding the HSA’s resolutions and standards or their implementation.
- 8.1.a.The ISSC must thoroughly investigate matters on its agenda to establish adequate (fact-based) understanding related to nature of the presented matter. If a matter does not become clear to the ISSC, it may postpone issuance of the resolution or request additional information or supporting studies, and accordingly (in this case) the subject matter shall be presented again after the request is addressed.
9 Subcommittees of the ISSC
- 9.1 To facilitate decision making process in urgent matters, the ISSC may choose to authorize:
- an executive member or
- an executive sub-committee,
from among its members, and determine their responsibilities.
Resolutions of the executive member or the executive sub-committee should be presented to the ISSC at its first meeting. Neither the executive member nor the executive committee has the right to issue a resolution on:- important transactions that contain new structures, mechanisms, or documentation that have not previously been endorsed by the ISSC (such as new structures, mechanisms and documentation in Sukuk issuances, syndicated financings or products), or
- to adopt plan of internal Shari’ah audit or endorsing reports submitted by the internal audit.
- 9.1 To facilitate decision making process in urgent matters, the ISSC may choose to authorize:
10 Internal Shari'ah Controls Functions
- 10.1 The IFIs must comply with the requirements related to Internal Shari’ah Control functions as stipulated in the Regulations, Standards and Resolutions.
11 Engagement (Appointment) Letter
- 11.1 An IFI must ensure that:
- the engagement letter by which a candidate is appointed to the ISSC conforms to the requirements specified in the Regulations, Standards and Resolutions,
- the candidate, whom the IFI wants to appoint to its ISSC, must have accepted content of the engagement letter before his/her name is submitted to the HSA and the General Assembly for approval, and
- the engagement letter must be available in Arabic.
- 11.1 An IFI must ensure that:
12 Approval, Effectiveness, Amendment and Review of the Charter
- 12.1 The Charter may be amended based on a request by the ISSC and approved by the board of directors, and the amendment will be effective from the date of its approval. The ISSC reviews the Charter at least once every two years or sooner if needed.
Approval of the Charter
Shaikh: Mr/Ms: Chairman of the ISSC Chairman of the Board ............................... ............................... Date of Signing: Date of Signing: Date of Approval: (Date of the latest signature above)
(end of the template)
Standard Re. Regulatory Requirements for Financial Institutions Housing an Islamic Window
N 4743/2020 STA Effective from 26/10/2020The Central Bank of UAE is pleased to attach herewith the Standard Re. Regulatory Requirements for Financial Institutions Housing an Islamic Window, which applies to licensed financial institutions that conduct part of their activities and businesses in accordance with the provisions of Islamic Shari’ah (Financial Institutions Housing an Islamic Window).
This Standard must be read in conjunction with the regulations, standards and resolutions issued by the Central Bank and the Higher Shari’ah Authority.
This Standard is mandatory and effective from the date of this notice, taking into account what is stated in Article No. (8) of the Standard.
Please bring this Standard to the attention of the board of directors of your institution at the next board meeting.
Article (1) Introduction
- 1.1 The Central Bank seeks to promote the development of banking activities to ensure their effectiveness and efficiency. To achieve this, licensed financial institutions that conduct part of their activities and businesses in accordance with the provisions of Islamic Shari’ah (“Institution housing an Islamic Window”) must establish a framework to ensure that the Shari’ah compliant activities and businesses are conducted in a manner that complies with the requirements set in this Standard and other Regulations and Standards issued by the Central Bank.
- 1.2 This Standard articulates the minimum requirements that Institutions housing an Islamic Window are required to comply with.
- 1.3 This Standard is issued pursuant to the powers vested in the Central Bank under the provisions of the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities (the Central Bank Law).
- 1.4 Where this Standard specifies requirements to provide information, undertake certain measures, or address certain terms listed as a minimum, the Central Bank may impose requirements which are additional to those outlined in the relevant article.
- 1.1 The Central Bank seeks to promote the development of banking activities to ensure their effectiveness and efficiency. To achieve this, licensed financial institutions that conduct part of their activities and businesses in accordance with the provisions of Islamic Shari’ah (“Institution housing an Islamic Window”) must establish a framework to ensure that the Shari’ah compliant activities and businesses are conducted in a manner that complies with the requirements set in this Standard and other Regulations and Standards issued by the Central Bank.
Article (2) Objective
- 2.1 The objective of this Standard is to establish minimum requirements for the Shari’ah compliant activities and businesses of Institutions housing an Islamic Window, with a view to:
- Ensuring robust governance towards activities and businesses that comply with Islamic Shari’ah, and
- Contributing to financial stability and consumer protection.
- 2.2 This Standard elaborates on the supervisory expectations of the Central Bank with respect to Institutions housing an Islamic Window.
- 2.1 The objective of this Standard is to establish minimum requirements for the Shari’ah compliant activities and businesses of Institutions housing an Islamic Window, with a view to:
Article (3) Scope of Application
- 3.1 This Standard applies to all Institutions housing an Islamic Window. Institutions housing an Islamic Window established in the UAE with Group relationships, including Subsidiaries, Affiliates, or international branches, must ensure that the Standard is adhered to on a solo and Group-wide basis.
- 3.2 This Standard must be read in conjunction with the Standards and Resolutions issued by HSA and notified to Institutions housing an Islamic Window.
- 3.1 This Standard applies to all Institutions housing an Islamic Window. Institutions housing an Islamic Window established in the UAE with Group relationships, including Subsidiaries, Affiliates, or international branches, must ensure that the Standard is adhered to on a solo and Group-wide basis.
Article (4) Definitions
For the purposes of this Standard, the following words and phrases shall have the meanings stated below.
- a. Senior Management: The executive management of the Institution housing an Islamic Window responsible and accountable to the Board for the sound and prudent day-to-day management of the financial institution, generally including, but not limited to, the chief executive officer, chief financial officer, chief risk officer, and heads of the compliance and internal audit functions. The term Senior Management includes the head of Islamic banking at the Institutions housing an Islamic Window.
- b. Independence: Ensuring that the ISSC is not subject to any form of undue influence when issuing resolutions and fatwas in accordance with the Shari’ah parameters, and ensuring that the Internal Shari’ah Control Division or Section and Shari’ah Audit Division or Section are also not subject to any form of undue influence. This should be carried out to strengthen the confidence of both shareholders and stakeholders in the Institution housing an Islamic Window compliance with Islamic Shari’ah.
- c. Internal Shari’ah Audit: regular process to inspect and assess Institution housing an Islamic Window’s compliance with Islamic Shari’ah and the level of adequacy and effectiveness of the Institutions housing an Islamic Window’s Shari’ah governance systems.
- d. Compliance with Islamic Shari’ah refers to compliance with Islamic Shari’ah in accordance with:
a. resolutions, fatwas, regulations, and standards issued by the HSA in relation to licensed activities and businesses of Institutions housing an Islamic Window (“HSA’s Resolutions”), andb. resolutions and fatwas issued by ISSC (“ISSC”) of respective Institution housing an Islamic Window, in relation to licensed activities and businesses of such institution (“the Committee’s Resolutions”), provided they do not contradict HSA’s Resolutions.
- e. Shari’ah Supervision: monitoring of Institution housing an Islamic Window’s compliance with Islamic Shari’ah in all its objectives, activities, operations, and code of conduct.
- f. Subsidiary: An entity, owned by another entity by more than 50% of its capital, or under full control of that entity regarding the appointment of its board of directors.
- g. Affiliate: An entity owned by another entity by more than 25% and less than 50% of its capital.
- h. Fatwas: juristic opinions on any matter pertaining to Shari’ah issues in Islamic finance, issued by HSA or ISSC.
- i. Internal Shari’ah Supervision Division (or Section): a technical division (or section) in the Institution housing an Islamic Window with a mandate to support the ISSC in its mandate.
- j. Internal Shari’ah Supervisory Committee (“ISSC”): a body appointed by the Institution housing an Islamic Window, comprised of scholars specialized in Islamic financial transactions, which independently supervises transactions, activities, and products of the Institution housing an Islamic Window and ensures they are compliant with Islamic Shari’ah in all its relevant objectives, activities, operations, and code of conduct.
- k. Board: Institution housing an Islamic Window’s board of directors.
- l. Group: A group of entities which includes an entity (the ‘first entity’) and:
a. any Controlling Shareholder of the first entity;
b. any Subsidiary of the first entity or of any Controlling Shareholder of the first entity; and
c. any Affiliate, joint venture, sister company and other member of the Group. - m. Shari’ah Non-Compliance Risks: probability of financial loss or reputational risk that an Institution housing an Islamic Window might incur or suffer for not complying with Islamic Shari’ah.
- n. Confidential Information: information that is publicly unavailable and where its disclosure is not allowed as per Article 120 of Decretal Federal Law No. (14) of 2018.
- o. Higher Shari’ah Authority (HSA): is the Central Bank’s Higher Shari’ah Authority for Islamic banking and financial activities.
- p. Islamic Window: refers to the licensed activities that are carried on in accordance with the Islamic Shari’ah that are carried on by financial institutions whether for their account or for the account of or in partnership with third parties which comply with the regulatory requirements stated in this standard and other regulations issued by the central bank.
- q. High Quality Liquid Assets (HQLA): Assets unencumbered by liens and other restrictions on transfer which can be converted into cash easily and immediately, with little or no loss of value, including under the stress scenario.
- a. Senior Management: The executive management of the Institution housing an Islamic Window responsible and accountable to the Board for the sound and prudent day-to-day management of the financial institution, generally including, but not limited to, the chief executive officer, chief financial officer, chief risk officer, and heads of the compliance and internal audit functions. The term Senior Management includes the head of Islamic banking at the Institutions housing an Islamic Window.
Article (5) Governance Requirements
- 5.1 The Institution housing an Islamic Window must comply with Islamic Shari’ah in all of its goals, activities, operations and code of conduct in all matters related to Islamic window at all times.
- 5.2 Branches of foreign licensed financial institutions housing an Islamic Window must adhere to this standard or establish equivalent arrangements to ensure regulatory comparability and consistency. The equivalent arrangement, if applicable, should include the matters related to general assembly, the Board and its Committees without contradicting the prevailing laws in the UAE. The equivalent arrangements shall be submitted to the Central Bank for approval.
- 5.3 Each Institution with an Islamic Window is required to comply with the Shari’ah Governance Standard for Islamic Financial Institutions and other Regulations and Standards issued by the Central Bank, including but not limited to:
- a. The organizational structure of the Islamic window should ensure that the Shari’ah control divisions or sections are independent and are not subject to any influence that may affect their independence;
b. Alignment of the divisions or sections stated in the clause (a) with the three lines of defense approach as set out in the Central Bank’s Corporate Governance Standard and Shari’ah Governance Standard for Islamic financial institutions.
5.4 The Board is in ultimate control of the Institution housing an Islamic Window and accordingly responsible for the Islamic Window’s compliance with Islamic Shari’ah and the requirements set in this Standard.
5.5 Senior Management of the Institution with an Islamic Window is responsible and accountable to the Board for the sound and prudent day-to-day management of the Institution including executing and managing the Shari’ah compliant activities and businesses. All the Shari’ah compliant activities and business of the Institution must be offered through the Islamic window.
5.6 The Institution housing an Islamic Window should appoint a Head of Islamic Window who must be dedicated to the operations of the Islamic Window and must not perform any tasks that are not within the scope of the Islamic Window.
5.7 The appointment of the Head of Islamic Window must be approved by the Central Bank. The Central Bank must be informed regarding the organizational structure of the Islamic Window at least 20 working days before the same is implemented.
5.8 The Head of Islamic Window should report directly to the Executive Management Committee of the Institution or the CEO. The Head of Islamic Window is responsible and accountable to the Executive Management Committee of the Institution or the CEO for the operations of Shari’ah compliant activities and businesses. The Head of the Islamic Window is responsible to coordinate with the relevant departments concerning activities and businesses that comply with Islamic Shari’ah and shall be regarded part of the business line.
5.9 The Head of Islamic Window should:- have a bachelor degree or masters in banking and finance or other relevant fields,
- demonstrate adequate knowledge, and experience (not less than 10 years) in Islamic banking and finance that will allow him/her to lead Shari’ah compliant business, and
- have held relevant senior positions in the banking sector or other relevant sectors.
9.5 The Institution housing an Islamic Window must adopt an approach with regard to conducting the Shari’ah compliant businesses and activities within the institution. Such approach should take into consideration staffing and physical premises in accordance with the size and the complexity of the Shari’ah compliant business and activities. The approach may take one of the following forms:- -Stand-alone separate branches and offices to service the Islamic Banking clientele as well as designated staff;
- -Embedding of designated and/or dedicated Islamic Window personnel within the existing branch network and premises.
- -Any other form subject to the Central Bank approval.
Such approach must be approved by the ISSC and the approach submitted to the Central Bank for review and approval every 5 years unless the HSA or the Central Bank requires a shorter period.
- 5.10 The Institution Housing an Islamic Window may leverage on its existing infrastructure to source Shari’ah compliant activities, including the offering of Shari’ah compliant products and services through the existing business lines. The institution housing an Islamic Window must develop an approach to internal services (between different departments) with respect to Islamic Window in order to ensure the compliance with Islamic Shari’ah at all times.
- 5.11 The approach to internal services must include the following:
- a. A minimum of one designated function to manage Shari’ah compliant Asset and Liability Management (ALM), Treasury and Investment operations.
- b. A dedicated sales function with appropriate Shari’ah qualification to market and sell Shari’ah compliant products and services, and employees at this function are not allowed to market or sell conventional products. Other sales personnel may sell Shari’ah compliant financial products and services to customers provided that they have been given adequate and appropriate training and they are supported by the dedicated Islamic Window sales function.
- c. Development and delivery of a comprehensive and specific training plan to cover all staff engaged in Shari’ah compliant operations, including staff assuming positions in the front line, middle and back offices and control functions, to ensure adequate management of the Shari’ah compliant products and services within the institution. The training program should take into account:
- specifics of the functions (roles) performed by the staff, and equip the staff with information and skills, depending on the nature of work of each employee, to ascertain compliance with Islamic Shari’ah, and
- the general banking and business risks associated and encountered with that function as well as any Shari’ah non-compliance risks.
- d. The approach towards internal services should be approved by the ISSC and submitted to the Central Bank for review and approval. Any material changes thereafter must be submitted to the Central Bank for approval.
- 5.1 The Institution housing an Islamic Window must comply with Islamic Shari’ah in all of its goals, activities, operations and code of conduct in all matters related to Islamic window at all times.
Article (6) Asset and Liability Management
- 6.1 The institution housing an Islamic Window must establish an ALM Framework for the management of Shari’ah compliant assets and liabilities to ensure their sound and prudent management, including ring-fencing of Shari’ah compliant assets and liabilities.
- 6.2 The framework should demonstrate the segregation between Shari’ah compliant assets and liabilities and other assets and liabilities of the Institution.
- 6.3 The segregation must include having separate product codes for Shari’ah compliant products mapped with specific General Ledger accounts. Institution housing an Islamic Window may apply alternative methods, subject to the approval of the Central Bank.
- 6.4 The Institution housing an Islamic Window is required to report a separate Liquidity Coverage Ratio (LCR)/Net Stable Funding Ratio (NSFR)/Eligible Liquid Assets Ratio (ELAR) (as applicable) for the Islamic Window. These reports are to be submitted along with periodic reports submitted to the Central Bank.
- 6.5 If the Institution housing an Islamic Window is maintaining separate liquidity levels for the Islamic Window, an appropriate stock of Shari’ah compliant High Quality Liquid Assets must be held against 30 days net outflow and documented accordingly for Central Bank supervision and examination review. Documentation must be retained for two years from any point in time that the information is documented
- 6.6 The formula of calculating LCR, specific to the Islamic Window operation is as follows:
6.7 Any surplus or deficit in Shari’ah compliant assets and liabilities in the Islamic Window must be managed in a Shari’ah compliant manner. Institutions must develop an approach to the mechanism of financing and funding between the Islamic window and the institution. The approach developed must be reviewed and approved by the ISSC and the Central Bank.
- 6.8 The management and treatment of non-Shari’ah compliant income shall be carried out in accordance with the directives of the ISSC.
- 6.9 Non-Shari’ah compliant income, if any, must be treated in accordance with the Shari’ah requirements in this regard.
- 6.10 There should be no internal procedure or a policy that encourages converting Shari’ah compliant assets to conventional assets. Similarly, the institution housing an Islamic Window must not transfer Shari’ah compliant assets (which are in the Islamic Window) to its conventional side in order to deal with it as a conventional asset. The Senior Management should ensure the independence of the Shari’ah compliance businesses and activities, and Islamic Window’s customers from the conventional businesses and activities.
- 6.11 All marketing and promotional material of Shari’ah compliant activities of the Bank must be formulated under a separate brand (e.g. different logo and different commercial name) and must be approved by the ISSC.
- 6.1 The institution housing an Islamic Window must establish an ALM Framework for the management of Shari’ah compliant assets and liabilities to ensure their sound and prudent management, including ring-fencing of Shari’ah compliant assets and liabilities.
Article (7) Regulatory and Financial Reporting, IT Systems and Infrastructure
- 7.1 The Institutions housing an Islamic Window are mandated to report a separate Islamic Bank Return Form “iBRF” as per the template set out by the Central Bank.
- 7.2 The Institutions housing an Islamic Window are required to separately report the results and activities of their Islamic Window to Executive Management and the Board. Such internal reporting shall include among other items an appropriate allocation of the costs of internal services to accurately reflect the cost of offering Shari’ah compliant financial services.
- 7.3 The reports produced by the Shari’ah control department or division and by the Shari’ah Audit department or division should be submitted in accordance with the requirements stated in the Shari’ah Governance Standard for Islamic Financial Institution.
- 7.4 The institution housing an Islamic Window are encouraged to separately report the results and activities of their Islamic Window operations within the annual report to promote market disclosure, transparency and customer confidence.
- 7.5The institution housing an Islamic Window may use a single or dual core banking system to record, manage and report Shari’ah compliant activities and other activities.
- 7.6 Where a single core banking system is used, it must be adjusted to account for the unique features of Shari’ah compliant products. Such adjustments for Shari’ah compliance purposes must be approved by the ISSC.
- 7.1 The Institutions housing an Islamic Window are mandated to report a separate Islamic Bank Return Form “iBRF” as per the template set out by the Central Bank.
Article (8) Compliance with the Standard
- 8.1 The Institutions housing an Islamic Window must set a Shari’ah governance framework in accordance with this Standard within 180 days from issuing this standard. The same must be submitted to the Central Bank for approval.
- 8.2 The Institutions housing an Islamic Window should comply fully with these standard requirements within one year from publishing this standard.
- 8.3 The Regulatory Development Division of the Central bank shall be the reference for interpretation of the provisions of this Standard.
- 8.1 The Institutions housing an Islamic Window must set a Shari’ah governance framework in accordance with this Standard within 180 days from issuing this standard. The same must be submitted to the Central Bank for approval.
Standard Re Shari’ah Compliance Function At Islamic Financial Institutions
Effective from 3/4/2025Article (1) Introduction
1.1 This Standard Re Shari’ah Compliance Function at Islamic Financial Institutions (“the Standard”)complements the Standard re Shari’ah Governance for Islamic Financial Institutions(“the Shari’ah Governance Standard” or “SGS”) with the aim to promote the development of the banking system and to ensure its effectiveness and efficiency.
1.2 The licensed financial institutions that conduct all or part of their activities and businesses in accordance with the provisions of Islamic Shari’ah (“Islamic Financial Institutions” or “IFIs”) must establish Shari’ah governance policies and governance mechanisms to ascertain compliance with requirements outlined in the Standard and requirements outlined in the relevant regulations, standards, resolutions and other notices issued by the Central Bank and by the Higher Shari’ah Authority (“HSA”) in relation to compliance with Islamic Shari’ah (“Regulatory Requirements”).
1.3 Where the Standard contains a requirement to provide information, or undertake certain measures, or address particular terms stated as a minimum requirement, the Central Bank may impose additional requirements to those specified in the relevant article in the Standard.
Article (2) Objective
The Standard sets supervisory expectations to implement the requirements specified in the SGS in relation to Shari’ah Compliance Function as part of the second line of defense.
Article (3) Scope of Application
3.1 The Standard applies to all Islamic Financial Institutions licensed by the Central Bank.
3.2 The Standard must be read in conjunction with the SGS and the standards and resolutions issued by HSA and notified to IFIs.
Article (4) Shari’ah Compliance Function
4.1 In accordance to Article No. (10.6) of the Shari’ah Governance Standard, the internal Shari’ah control division or section shall perform various functions, including Shari’ah Compliance Function (“SCF”). The SCF is responsible to continuously monitor compliance of an IFI’s businesses and activities with resolutions, fatwas, regulations, and standards, which are issued by the HSA.
4.2 The SCF is different from Shari’ah audit in terms of reporting line, frequency of the review, as well as the fact that SCF conducts reviews before and during the execution, while Shari’ah audit conducts review post execution.
4.3 The responsibility regarding managing Shari’ah Non-Compliance Risk lies with the IFI’s risk management department, not with the SCF. However, the two departments should provide each other with information in order to achieve compliance with Islamic Shari’ah and manage Shari’ah Non-Compliance Risk in a prudent manner.
Article (5) Stages of the Review Process in Shari’ah Compliance Function
5.1 The SCF shall conduct reviews and evaluate the Shari’ah Non-Compliance controls and their applications, issue reports on the same and monitor remedial actions to ensure that Shari’ah compliance controls are adequate and operate as intended.
5.2 The IFI must develop internal procedures and policies regarding SCF review exercises that should include, at least, the following stages: a. Develop an Annual Plan,
b. Planning and Scoping of the review,
c. Conduct a Field Review,
d. Documenting Issues & Actions,
e. Draft Reports, and
f. Monitor Progress.
The IFI may refer to the review stages that are stated in the Guidance Note of this Standard.
Article (6) Development of Annual Plan
The SCF shall be responsible for developing the annual review plan (“Annual Plan”) which must be approved by the Internal Shari’ah Supervision Committee (“ISSC”) and the Board.
Article (7) Planning and Scoping of the Review
The SCF shall set a planning and scoping of the review process (“Planning”), and it involves gathering information from the business or function under review, allowing development of the scope, objectives and approach to the review, and determining the planned review procedures.
Article (8) Field Review
The IFI’s SCF shall conduct a field review for the IFI that consists of procedures built on robust methodology basis. The details regarding field review may be referred to in the Guidance Note of this Standard.
Article (9) Issues and Actions
The SCF shall record each identified finding/incident in the report that follows every field review. The identified issues must be factual, accurate, precise, objective, clear, concise, complete and supported with:
a. Adequate evidence that demonstrates the accuracy and factuality of the identified finding.
b. Determination of the Shari’ah or governance or other documents and the relevant paragraphs from which deviation has occurred, if applicable, such as, but not limited to specific Regulatory Requirements, ISSC’s Resolutions, or the Products Manual.
c. Specification of the root cause that has triggered the identified finding.
d. Establishment of a clear action plan that adequately addresses the root cause and closes the gap, and specification of the party responsible for the action plan.
e. Specification of risk rating of the identified incident according to the approved risk matrix of the IFI which is prepared by risk management department.
Article (10) Reports
10.1 The SCF shall record the issues of the field review in a report that shall be developed through robust procedures before dissemination, as follows:
a. Preliminary Issues Report
b. Response from Respective Parties
c. Closing Meeting
d. Final Report
e. Final Report Approval
f. Final Report Dissemination
The IFI may refer to the detailed guidance in the Guidance Note of this Standard.
10.2 The final report shall be disseminated to the CEO and the relevant parties within five working days after being approved by the ISSC. This is to ensure the implementation of its contents within the period specified by the ISSC in the final report.
Article (11) Progress Status Monitoring
The SCF shall monitor progress updates provided by the relevant parties, and monitor the implementation of the action plan. The IFI may refer to the Guidance Note of this Standard for further guidance regarding the procedures that should adopted at this stage.
Article (12) Compliance with the standard
The IFI must comply fully with the requirements of this Standard within one year from its date of issuance.
Guidance Note Re Shari’Ah Compliance Function At Islamic Financial Institutions
Effective from 3/4/2025Article (1) Introduction
This Guidance Note Re Shari’ah Compliance Function at Islamic Financial Institutions (“Guidance Note” or “Note”) complements the Standard Re Shari’ah Compliance Function at Islamic Financial Institutions (“the Standard”) with the aim to promote the development of the banking system and to ensure its effectiveness and efficiency.
Article (2) Objective
The Guidance Note contains guidance aimed at facilitating implementation of the requirements related to Shari’ah Compliance at licensed financial institutions that conduct all or part of their activities and businesses in accordance with the provisions of Islamic Shari’ah (“Islamic Financial Institutions” or “IFIs”).
Article (3) Scope of Application
3.1 The Guidance Note applies to all IFIs. IFIs may comply with the guidance stated in this Guidance Note or apply equivalent criteria in order to comply with the requirements stated in the Standard. 3.2 The Guidance Note should be read in conjunction with the Standard and the standards and resolutions issued by Higher Shari’ah Authority (“HSA”) and notified to IFIs. Article (4) Development of Annual Plan
4.1 The Board and the senior management approve the Annual Plan that relate to Shari’ah Compliance Function (“SCF”) review exercises and ascertain smooth realization and implementation of the approved Annual Plan, including but not limited to, full cooperation and support from the relevant department heads at the IFI. 4.2 The IFI should prioritize what needs to be included in the Annual Plan, and develop a prioritization matrix that takes into account the relevant parameters, including: a. frequency of reviews, b. historical incidents, and c. size and complexity of products. Appendix (A) contains generic guidance on developing the prioritization matrix that aims to assist IFIs in identifying segments of operations and activities that should undergo review in a financial year. Article (5) Planning and Scoping of the Review
In the planning stage, the SCF should understand the regulatory requirements, the resolutions of Internal Shari’ah Supervision Committee(“ISSC Resolutions”) that relates to SCF, Shari’ah Non-Compliance (“SNC”) risks, compliance obligations, processes, policies and procedures, and related internal controls, including identifying and documenting known and self-identified issues. Subsequently, the SCF should send a memo outlining the reason for the review, scope, planned timeline and other terms of the scheduled review exercise to the relevant parties, including those departments or sections directly impacted by the review, prior to the commencement of the field review.
Article (6) Field Review
6.1 The Field Review May Include The Following
a. Opening Meeting, b. Sampling Methodology, c. Development of Internal Checklists, d. Walkthrough, e. Internal Controls Assessment, and f. Staff Awareness. 6.2 Opening Meeting
The SCF should start the field review with an opening meeting that involves representatives from the relevant departments and sections.
6.3 Sampling Methodology
a. The SCF should develop a sampling methodology that will be followed during the review exercise. The sample size and the sampling procedure should be objective and robust to ascertain with a high level of confidence that the selected sample fairly represents transactions executed during the period that is covered by the review exercise. b. The SCF should determine the sampling methodology which provides clarity related to the minimum quantity of samples that may be reviewed (such as 10% sample size) of the total number of transactions subject to the review exercise. Appendix (B) contains generic guidance for developing the sampling methodology. c. The SCF may need to select a larger or additional sample size than what was initially planned if the circumstances arise, such as in cases where there is reasonable uncertainty on whether an identified SNC incident/s is a random or systemic failure of the IFI to comply with the regulatory requirements and ISSC Resolutions. These instances should be specified in the IFI’s sampling methodology. 6.4 Development of Internal Checklists
a. SCF should develop checklists needed to undertake an adequate and effective review of the subject that is being reviewed. b. In developing checklists, the SCF should ascertain that it has mapped all requirements and expectations of the regulatory requirements and the ISSC’s Resolutions applicable to the subject planned to be reviewed, and that all relevant requirements are adequately transferred into the checklists. Appendix (C) outlines generic guidance for developing the respective checklists. 6.5 Walkthrough
a. SCF should conduct a walkthrough test of real-life deals to gauge the reliability of internal procedures, manuals and policies in relation to day-to-day activities of the IFI. b. The walkthrough should be accompanied by an assessment of the controls, their adequacy and effectiveness in real-life deals. Preparation for the walkthrough should include interviewing the relevant staff regarding the applicable processes and procedures, and questions or queries that would need to be asked during the walkthrough. The questions should cover exceptional and unusual situations that occur in day-to-day work. 6.6 Internal Controls Assessment
The SCF should assess internal controls related to SNC risk to ascertain their design and operational effectiveness. The assessment should, among others, cover the following aspects:
a. scope and adequacy of the control design in relation to addressing the SNC risk, b. operational reliability of the control and its effectiveness in identifying exceptions across all possible scenarios that could arise, c. probability of avoiding or circumventing the control, and d. comprehensiveness of the existing controls to address all relevant SNC risk. 6.7 Staff Awareness
a. The SCF should assess the staff awareness in relation to knowledge and skills that they need to possess to adequately fulfil their job duties, as per the responsibilities specified in the employee’s job description, without violating the provisions of Islamic Shari’ah. b. Determination of the type of knowledge and skills each employee needs to possess should depend on the nature of the employee’s responsibilities. For example, personnel with responsibility to execute the exchange of currency should be equipped with knowledge and skills specifically related to: 1. execution of all necessary steps or processes in currency exchange, which the employee is responsible for executing in line with parameters of Islamic Shari’ah. 2. reasonable understanding of SNC risks that may arise from this type of transaction, their potential consequences and steps or actions required to adequately manage the risks in order to prevent potential incidents from occurring. c. The IFI should develop proper training and staff awareness programme. Article (7) Issues and Actions
Article (9) of the Standard emphasizes that each identified finding/incident is included in the report. The SCF should analyze and identify the root cause and assess the following:
a. existence of reliable and efficient controls that should have prevented the identified incident from occurring, b. comprehensiveness and clarity of the internal policy’s requirement in relation to the incident, c. Whether the relevant employees are notified of, and have access to, the relevant internal policy, d. adequacy of staff awareness and the existing training programmes in relation to the identified finding, and e. staff conduct and adherence to the established policies, and potential conflict of interest. Article (8) Reports
8.1 Preliminary Issues Report
The SCF should send a report of preliminary issues (“Preliminary Issues Report”) to the relevant parties at least five (5) working days before the closing meeting.
8.2 Response from Respective Parties
After receiving the report, the respective parties should respond on the Preliminary Issues Report within a specific number of days. All responses should undergo an assessment by the SCF in light of the existing evidence related to the issue raised.
8.3 Closing Meeting
The SCF should conduct a closing meeting after completing the assessment of the responses. The relevant parties should be made aware of all the findings and supporting evidence. The meeting should be documented in the form of minutes of the meeting for audit purposes.
8.4 Final Report
a. The SCF when preparing the final review report (“Final Report”) should consider that the report is to assist the IFI in establishing effective and adequate procedures at the institutional level, making corrections and improvements where needed, and rectifying and closing identified gaps, if any. The Final Report should include: - adequacy of control status and adequacy of management action, - an executive summary that will briefly explain the scope and methodology used in preparing the report (such as specifying the total number of customers or transactions, sample size, list of issues and their risk grading, etc.), and - details of issues and actions as per the Standard and the Note. b. The Final Report may include a statement of the level of cooperation and support extended by the relevant departments to the SCF during the review exercise. 8.5 Final Report Approval
The SCF presents the Final Report, upon its completion, to the ISSC for assessment and approval. The ISSC should conduct a comprehensive assessment of the report regarding its compliance with the Standard, including but not limited to, assessment of the following aspects:
- validity of the identified issues, - accuracy of root cause/s of the issues and suitability of action plan, - adequacy and effectiveness of the controls, and - clarity of the report. The ISSC should maintain records of the same for audit purposes.
8.6 Final Report Dissemination
The SCF should conduct the following procedures regarding the Final Report Dissemination:
a. Circulating the final report to the relevant parties within five (5) working days after being approved by the ISSC. b. All findings of the report should be incorporated in the tracker for progress status monitoring (“Status Tracker”). c. Each party responsible for an action plan may confirm to SCF within the agreed timeline, or periodically if needed, that all the actions specified in the Final Report have been addressed, and substantiate such confirmation with adequate evidence for each finding. d. If any action from the Final Report is not closed/addressed within the timeline, the party responsible for the action plan should provide reasoning and evidences for not closing/addressing the issue, and its target completion date. e. The progress update on addressing the findings and implementing recommendations should be monitored. Article (9) Progress Status Monitoring
The SCF may consider the following procedures in the progress status monitoring, including but not limited to:
a. Monitoring progress updates provided by the relevant parties regarding how the findings are addressed and whether the action plan has been implemented. b. All responses should be supported with adequate evidence. The evidence should be kept for audit purposes. c. All responses received from the respective parties should be read in the context of existing evidence related to the highlighted issue. d. The Status Tracker should be updated based on the results of the monitoring. e. An update on the outstanding issues to be provided to the ISSC and risk management committee (or equivalent committee) in each meeting, and if needed, to the CEO of the IFI on a monthly basis for onward escalation in the relevant meetings. The update should be provided in a suitable format such as a dashboard that includes timeline analysis and is suitable for, and understandable by, each respective committee. f. Each party responsible for an action plan should seek approval from the ISSC, via SCF, for any extension to close the outstanding issue. Appendix (A): An Example in Prioritization Parameters for Selection of Subjects in the Annual Plan
1 Frequency of Reviews a. All products should be reviewed by the SCF at least once every three (3) years. b. All branches or distribution channels should be reviewed by the SC at least once every two (2) years. c. All new products should be reviewed within the first 3 months from the date when the product was launched. d. Products that have not been reviewed in the past are prioritized over those that have been reviewed. 2 Historical Incidents a. Products based on underlying contracts or concepts similar to those in which systemic or major incidents were identified in the past are prioritized over those in which no such incidents were identified. b. Distribution channels in which systemic or major incidents were identified in the past are prioritized over those in which no such incidents were identified. 3 Level of Complexity of the Products Products with higher level of complexity that negatively impact SNC risk are given priority over other products. Appendix (B): Generic Guidance for Developing Sampling Methodology
The selection methodology of the sample size should cover, among others, the following aspects: a. transactions of different sizes such as, small, medium and large transactions, b. transactions executed via different distribution channels and in different geographical areas, c. transactions executed with different customers, d. transactions executed in different currencies (if applicable), The selected transactions should be distributed throughout the period covered by the review exercise in accordance with the adopted methodology, such as equal distribution of samples across the period covered by the review exercise, or uneven distribution whereby transactions executed in certain periods may be deemed more vulnerable to the SNC risk and for that reason larger sample will be collected to ensure fair representation of the executed transactions in it during the time covered by the review. Appendix(C):Generic Guidance for Developing Product CheckList
Scope
Checklist for product review should cover all the relevant areas of a product that should be checked and their compliance with Islamic Shari’ah ascertained, including assessment of the following items: a. underlying structure of the product, b. templates of agreements, contracts, documentations, terms and conditions, (“Documentation Templates”) c. product related operational manuals, workflows, policies, guidelines, etc., (“Product Manuals”), d. relevant aspects of accounting entries/treatment, e. fees and charges, (if applicable), and f. compatibility of the IT system with Islamic Shari’ah in relation to operationalization of the product. The products should be reviewed by the SCF in accordance with a standard that considers the risks associated with the products. The SCF should review each product at least once every five (5) years. Aspects
Items specified in the Scope should be assessed from the below listed aspects (as applicable): a. Existence of well-maintained and complete record of all relevant and adequate ISSC’s approvals (and where applicable no objection letters from HSA or Central Bank) regarding Shari’ah compliance of the product prior to its launch, including approval of any amendments to the products before they are offered to the customers. b. Consistency of ISSC’s Resolutions with the regulatory requirements, which requires mapping details of the ISSC’s Resolutions regarding the product and their comparison with the regulatory requirements. c. Compliance of all items specified in the Scope with the regulatory requirements and ISSC’s Resolutions. This would include an assessment of the product details against the regulatory requirements and the ISSC’s Resolutions. d. Compliance of executed transactions with the regulatory requirements and the ISSC’s Resolutions. Standard Re External Shari’ah Audit for Islamic Financial Institutions
N 5785/2024 STA Effective from 29/11/2024Article (1) Introduction
The Central Bank seeks to promote development of the banking activities to ensure their effectiveness and efficiency. To achieve this, financial institutions that conduct all or part of their activities and businesses in accordance with the provisions of Islamic Shari`ah (“Islamic Financial Institutions” or “IFIs”) must comply with the requirements stated in this Standard when appointing a specialized external firm to conduct External Shari’ah Audit.
Article (2) Objective
The objective of this Standard is to set the minimum requirements that must be adhered for conducting an External Shari’ah Audit for the purpose of reassuring shareholders, depositors, and all stakeholders regarding the IFI’s compliance with Islamic Shari’ah Provisions.
Article (3) Scope of Application
3.1 This Standard applies to the IFIs in the case where:
- the IFI appoints an External Shari’ah Auditor on a voluntary basis, or - there is a regulatory requirement to appoint an External Shari’ah Auditor.
3.2 This Standard applies to all incorporated IFIs. IFIs established in the UAE with Group relationships, including Subsidiaries, Affiliates, or international branches, must ensure that the Standard is adhered to on a solo and Group-wide basis. 3.3 This Standard must be read in conjunction with the standards and resolutions issued by the Central Bank and the Higher Shari’ah Authority (“HSA”) and notified to IFIs. Article (4) Definitions
For the purposes of this Standard, the following words and phrases shall have the meanings stated below.
a. Senior Management: The executive management of the IFI responsible and accountable to the Board for the sound and prudent day-to-day management of the IFI, generally including, but not limited to, the chief executive officer, chief financial officer, chief risk officer, and heads of the compliance and internal audit functions. b. Internal Shari’ah Control Division (or Section): A technical division (or section) in the IFI that supports the ISSC in its mandate. c. Compliance with Islamic Shari’ah Provisions: It refers to compliance with Islamic Shari’ah in according with:
a. The provisions stated in Section Six of Book Three of the Commercial Transactions Law, b. The provisions contained in the bylaws issued implementing Section Six of Book Three of the Commercial Transactions Law, c. The resolutions, Fatwas, regulations and standards issued or adopted by the Higher Shari’ah Authority in relation to businesses and activities of the IFI ("HSA’s Resolutions"), d. The resolutions and Fatwas issued or approved by the Internal Shari’ah Supervision Committee of the respective IFI, in relation to businesses and activities of such IFI ("ISSC’s Resolutions"), provided that they do not contradict HSA’s Resolutions.
d. External Shari’ah Audit: An independent process to inspect and assess the IFI’s compliance with Islamic Shari’ah Provisions, and the level of adequacy and effectiveness of its Shari’ah governance systems for the relevant fiscal year, conducted by an external party. e. Internal Shari’ah Audit: The regular process to inspect and assess the IFI’s compliance with Islamic Shari’ah Provisions and the level of adequacy and effectiveness of IFI’s Shari’ah governance systems conducted by the Internal Shari’ah Audit division or department. f. Commercial Transactions Law: Federal Decree Law No. (50) of 2022 regarding the Commercial Transactions Law. g. Internal Shari’ah Supervision Committee (“ISSC”): A body appointed by an IFI, comprised of scholars specialized in Islamic financial transactions, which independently supervises transactions, activities, and products of the IFI and ensure its compliance with Islamic Shari’ah Provisions in all its objectives, activities, operations, and code of conduct. h. Board: Islamic Financial Institution’s board of directors. i. Shari’ah Non-Compliance Risks: Probability of financial loss or reputational risk that IFI might incur for not complying with Islamic Shari’ah Provisions. j. External Shari’ah Auditor: The Shari’ah audit firm and the individual audit engagement team members conducting the audit. Where relevant, specific references are made to the external Shari’ah audit firm only in certain paragraphs. k. Central Bank: The Central Bank of the United Arab Emirates. l. Islamic Financial Institutions (“Institutions/IFIs”): The Central Bank licensed financial Institutions that conduct all or part of their activities and businesses in accordance with the provisions of Islamic Shari’ah. m. Higher Shari’ah Authority: The authority established in accordance with the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities, as amends. It exercises the mandates and responsibilities stipulated in the above mentioned decretal law. Article (5) Purpose of the External Shari’ah Audit
The purpose of the External Shari’ah Audit is to reach reasonable and independent assurance regarding the IFI’s Compliance with Islamic Shari’ah Provisions through an expression of an opinion thereon from the External Shari’ah Auditor.
Article (6) Basis of the External Shari’ah Audit
6.1 The External Shari’ah Auditor’s opinion must rely on the Shari’ah basis as per the order stated in Article (4/c). 6.2 If the External Shari’ah Auditor comes across an issue for which no provision is found in the list stated in Article (6.1), the External Shari’ah Auditor must refer to the IFI’s Internal Shari’ah Supervision Committee (ISSC) to obtain a Shari’ah resolution for the same. Article (7) Fit and Proper
7.1 To conduct External Shari’ah Audit for IFIs, the external Shari’ah audit firm must be approved by the Central Bank. The firm will be granted the Central Bank approval after fulfilling certain criteria, including that the firm must have:
a. a license issued by competent authorities to perform its business in the UAE, b. at least three years of experience in Shari’ah audit. As for new firms, the approval may be granted to such external Shari’ah audit firms under special conditions that enable them to gain experience in External Shari’ah Audit, c. adequate resources to conduct the duties of External Shari’ah Audit and disclose the names of personnel specialized in Shari’ah audit engaged by the firm, d. an External Shari’ah Audit team that meets the competencies required to carry out External Shari’ah Audit duties. These include Shari’ah proficiency, accounting and legal experience, and other competencies according to the nature of the IFI’s business. In all cases, the personnel specialized in Shari’ah audit who meet the conditions stipulated in Article (7.3) must not be less than two-thirds of the team members, e. formal manual that states its methodology in conducting External Shari’ah Audit’s duties. The manual should be in line with the best practices in this field.
7.2 Firms that conduct external audit and are not specialized in External Shari’ah Audit may perform External Shari’ah Audit as long as they meet the criteria stipulated in this Standard and they must be approved by the Central Bank. 7.3 Personnel specialized in Shari’ah audit must fulfil the following conditions:
a. Should have a university degree in Islamic Shari’ah or relevant specializations, b. Should have a professional certificate in Shari’ah Auditing such as certificates issued by the Accounting and Auditing Organization for Islamic Financial Institutions (AAOIFI) or the General Council for Islamic Banks and Financial Institutions (CIBAFI), c. Should have sufficient expertise of at least seven years in Shari’ah Audit, d. Proficiency in Arabic and English, e. Should not be sentenced by a final decision in crimes related to honor or honesty, or convicted of offences and sentenced by imprisonment. Article (8) Appointment of External Shari’ah Auditor
8.1 The Board or its audit committee, in coordination with the ISSC, must recommend to the general assembly the appointment, re-appointment, dismissal, or the remuneration of the firm after ensuring that the firm has been pre-approved by the Central Bank. 8.2 The general assembly of the Islamic Financial Institution appoints, reappoints or dismisses the firm, and sets its remuneration, on an annual basis, in order for the firm to carry out its duties as specified in this Standard or as determined by the Central Bank and the HSA. 8.3 The audit committee must ensure that the External Shari’ah Audit team members as a whole have the expertise stated in Article (7.1/d) and that at least two-thirds of the team members are qualified personnel in Shari’ah audit who meet the conditions stated in Article (7.3) before submitting the appointment recommendation. 8.4 The IFI, any of its Board members, any ISSC member, or their relatives including their second-degree must not be shareholders in the appointed external Shari’ah audit firm. This is also applicable to the External Shari’ah Audit team. 8.5 The IFI must determine the External Shari’ah Auditor’s terms of engagement in written contract, which at a minimum, provides that:
a. the External Shari’ah Auditor must meet with the Central Bank as deemed necessary for supervisory purposes. The Central Bank will determine whether the IFI will participate in such meetings; b. the External Shari’ah Auditor bears no duty of confidentiality to the IFI with respect to any notification of meeting with the Central Bank required by this Standard, or the provision of any document or information required to be submitted to, or requested by, the Central Bank for supervisory purposes; and c. the External Shari’ah Auditor must provide, upon the request of the Central Bank, access to any documents that support conclusions made in the external Shari’ah audit opinion.
8.6 The External Shari’ah Auditor or any of its Subsidiaries or Affiliates companies must not provide any consulting services or services other than External Shari’ah Audit scope that would jeopardize its objectivity or independence during the years of the assignment as an External Shari’ah Auditor. 8.7 The External Shari’ah Auditor must not obtain any financial or in-kind consideration or benefits other than the contractual compensation/consideration for the External Shari’ah Audit work. 8.8 The IFI must terminate the contract or dismiss the external Shari’ah audit firm if it is proven to be not in adherence to the relevant professional standards, lacks sufficient experience or independence, or there are supervisory observations regarding the firm from the Central Bank. In any case, the approval of the Central Bank must be obtained before terminating or dismissing the services of the firm. 8.9 The IFI must rotate their external Shari’ah audit firm at least every 6 years, subject to the conduct of a procurement procedure. In addition, the IFI must rotate their external Shari’ah audit firm’s partner in charge of the audit every 3 years. Article (9) Responsibility of the Islamic Financial Institution
9.1 The IFI must comply with the requirements stated in this Standard and the relevant Shari’ah governance standards. The Board has the ultimate responsibility in this regard and it may delegate some relevant duties to the audit committee. 9.2 The audit committee should follow up on the work of the External Shari’ah Audit in accordance with this Standard and the relevant Shari’ah governance standards. Article (10) Scope of External Shari’ah Audit
10.1 The scope of work of the External Shari’ah Auditor includes any aspect that is deemed necessary to express an opinion on the extent of the IFI’s compliance with provisions of Islamic Shari’ah in accordance with the approved Shari’ah basis, and this may include:
a. The IFI and its branches, departments, and Subsidiaries and Affiliates. b. Any existing activity, product and service. c. Forms, contracts, agreements, and operation processes/procedures. d. Bylaws, instructions, work procedures, and product programs. e. Basis for calculating and distributing the profit and ensuring the expenses are well allocated between shareholders’ account and investment accounts. f. Accounting systems and Information Technology systems. g. The IFI’s Shari’ah governance systems and framework, the evaluation of the independence of the internal Shari’ah control departments and their effectiveness, and verification of the IFI’s adherence to its policies and procedures in this regard, including its commitment to its responsibilities stipulated in ISSC’s charter. h. Internal Shari’ah audit manual and plan to ensure that they have been approved by the ISSC, as decided by HSA. i. Any other aspects that the External Shari’ah Auditor needs to examine for the purpose of forming its opinion.
10.2 The External Shari’ah Auditor is not responsible to ensure the competency of the members of the ISSC or to evaluate their resolutions. 10.3 The External Shari’ah Auditor may determine the extent of reliance on the work of the internal Shari’ah auditor after examining four elements:
a. Organizational structure including administrative reporting and submission reports, b. Scope of work, c. Professional competency, d. Professional performance. Article (11) External Shari’ah Audit Frequency
In case there is no regulatory requirement to appoint an external Shari’ah audit firm to conduct the External Shari’ah Audit for the IFI, it is recommended to conduct External Shari’ah Audit at least once every three years.
Article (12) External Shari’ah Auditor Report
12.1 The External Shari’ah Auditor must submit its report to the general assembly, after the report is approved by the Central Bank. A copy of the report shall be sent to the Board and to the ISSC. If the IFI does not have a general assembly, the report shall be submitted to the Board. 12.2 A copy of the External Shari’ah Auditor report shall be sent to the ISSC before the ISSC issues the annual Shari’ah report. 12.3 A copy of the External Shari’ah Auditor report shall be published in the IFI’s annual financial statements, and if there are reservations in the report, these must be stated without prejudice to the confidentiality of the related transactions. 12.4 The External Shari’ah Auditor report must contain at least the following points:
a. Report title; b. The party to whom the report is submitted; c. Scope of audit engagement; d. An introductory paragraph about the details of the work during the audit, such as the number and dates of field visits, etc.; e. The responsibility of the Board and the IFI's Senior Management for compliance with the provisions of Islamic Shari’ah; f. Responsibility of the External Shari’ah Auditor; g. Expression of opinion paragraph; and h. Date, address, and signature of the External Shari’ah Auditor.
12.5 The External Shari’ah Auditor must report the observed weaknesses in the IFI’s internal Shari’ah control system, or any other weaknesses observed during the audit. It should be submitted to the IFI’s audit committee and to the ISSC, with a special detailed report addressed to them only. 12.6 If the External Shari’ah Auditor finds, during the audit, a mismatch between any resolution of the IFI’s ISSC and the resolutions of the HSA; a special report on this matter must be sent to the ISSC for information. If the ISSC approves the observations, it must take appropriate measures in this regard, and its secretariat will retain the report for regulatory purposes. 12.7 In the event of a conflict of opinion between the ISSC and the External Shari’ah Auditor regarding Shari’ah aspects, the opinion of the ISSC shall prevail. Article (13) Duty to Report to the Central Bank
13.1 External Shari’ah Auditors must promptly report to the Central Bank, regarding any violations of the relevant laws, regulations, instructions and any matters of significance arising from their audit of the IFI. External Shari’ah Auditors making such reports in good faith shall not be considered to have breached any of their obligations. 13.2 The IFI must promptly notify the Central Bank in case of resignation of their External Shari’ah Auditor and the reasons thereof, as well as obtain the no-objection from the Central Bank in case of their dismissal or change. Divergence of opinions between the IFI and its External Shari’ah Auditor cannot be ground for dismissal. Article (14) Interpretation of Standard
The Regulatory Development Department of the Central Bank shall be the reference for interpretation of the provisions of this Standard.
Article (15) Compliance with the Standard
Appointing an External Shari’ah Auditor is not mandatory unless it required by the Central Bank or the HSA. However, if an IFI appoints an External Shari’ah Auditor, it must fully comply with the requirements stated in this Standard. This Standard becomes effective one financial year after its date of issuance.
Principles for the effective management of climate-related financial risks
A. Introduction
1. The UAE Sustainable Finance Working Group (SFWG) was established in 2019 to enable the UAE’s economic transition and encourage the adoption of sustainable finance at the national level. This is in line with the Paris Agreement ratified by the UAE in 2016 and domestic acts and initiatives, such as the UAE Green Agenda 2015-2030, the National Climate Change Plan of the UAE 2017-2050 and the UAE Net Zero by 2050 Strategic Initiative.
2. The members of the SFWG include ministries (Ministry of Finance, Ministry of Economy, Ministry of Climate Change and Environment, the Office of the UAE's Special Envoy for Climate Change), financial services regulators (the Central Bank of the UAE, the Securities and Commodities Authority, the Financial Services Regulatory Authority of Abu Dhabi Global Market and the Dubai Financial Services Authority), and UAE exchanges (Abu Dhabi Securities Exchange, Dubai Financial Market and Nasdaq Dubai).
3. In 2020, in its Guiding Principles on Sustainable Finance in the UAE2, the SFWG committed to developing standards for the financial sector to integrate ESG factors into corporate governance, strategy and risk management. In its First Public Statement published in November 2021, the SFWG set out its roadmap and refined its focus setting out three interlinked work areas including on ESG reporting, corporate governance and risk management, and taxonomy. In November 2022, in its Second Public Statement, the SFWG reported on the progress of its three workstreams. In particular, the Workstream Two on Sustainability-focused Corporate Governance announced it would start working on developing enhanced standards to help embed and address climate-related risks in corporate governance and risk management in financial services entities in the UAE.
4. This document is the result of the efforts of Workstream Two and contains Principles for the effective management of climate-related financial risks (the Principles) which are issued in accordance with the relevant laws in each jurisdiction. The Principles have been developed in consideration of a number of standards on this topic published by international standard-setters. The key standards used for the purpose of the Principles include the Principles for the effective management and supervision of climate-related financial risks from the Basel Committee on Banking Supervision (BCBS) and the Guide for Supervisors Integrating climate-related and environmental risks into prudential supervision by the Network for Greening the Financial System (NGFS). A more complete list of international standards covering, for example, risk scenarios or details of the insurance sector is included in the Annex.
2 Principle One of the Guiding Principles, available here.
B. Application
5. The Principles constitute a declaration of common understanding among the SFWG members on the minimum standards that they expect to implement in their respective jurisdictions and in line with their legal frameworks in the area of climate risk management.
6. While the Principles are endorsed by the entire SFWG, it is understood that they are primarily relevant for those members who are financial services regulators. The ministries and exchanges may consider them in the context of their activities, where relevant.
7. For the purposes of the Principles, financial sector entities are referred to collectively as ‘financial firms’ without drawing distinctions between the various financial service activities offered by these entities. While it is recognised that the BCBS and the NGFS standards are primarily designed for the banking and insurance sectors, the Principles are drafted to cater for a wider spectrum of financial firms and taking into account differences in business models.
8. It remains in the discretion of each of the financial services regulators to determine the financial firms in scope of the Principles, how to apply each of them and the timeframe to do so in their jurisdictions. However, the relevant financial services regulators intend to commence application of these Principles in respect of their firms not later than from November 2023. The financial services regulators may also introduce additional details relevant for specific types of financial firms, in particular based on the standards cited in the Annex.
9. It is recognised that several standards in this area are still evolving at international level. This fact has been reflected in the drafting of the Principles allowing for the necessary flexibility and adaptations to future developments.
C. General Considerations
10. Transitioning to a low-carbon, and subsequently zero-carbon, economy entails both risks and opportunities for the financial sector. Strong corporate governance can drive and enable financial firms to identify and take the strategic steps necessary to develop and deploy new and more sustainable approaches and technologies, to strengthen business models and to improve both business and sustainability metrics. Importantly, enhanced risk management is critical for financial firms to identify and manage these risks better and to be able to demonstrate this to their clients and supervisors.
11. Climate-related financial risk refers to the financial risks arising from climate change, including physical, transition and liability risks. Such risks could impact the viability and soundness of individual financial firms and have broader implications for financial stability.
12. Physical risk refers to potential economic and financial losses from climate and weather-related events and the long-term progressive impact of climate change.
13. Transition risk refers to the financial risk related to the process of adjustment towards a lower-carbon economy, which can be prompted by, for example, changes in climate policy, technological changes or change in market and social sentiments.
14. Liability risk refers to climate-related compensatory claims and/or direct legal actions against financial firms. Liability risk can be considered as a separate risk but can also be treated as a subset of physical and transition risks.
15. Climate-related financial risks are not bound by timelines and can emerge within the short, medium, and long-term. They can materialize through transmission channels in the balance sheets of financial firms and within the traditional categories of financial risks, including credit, market, operational, underwriting, reputational and liquidity risks.
16. The reference to the board and senior management throughout the Principles is to be understood in accordance with their respective roles and responsibilities and is meant to include the members of the board of directors (or equivalent) and senior management. The Principles do not presume or endorse a specific board or senior management structure, nor do they advocate for a specific approach to assigning climate-related financial risk responsibilities within a financial firm.
D. The Principles
Principle 1 – Oversight and responsibility of climate-related financial risk exposures
1. The board and senior management of financial firms should have an appropriate understanding of the organization’s climate-related financial risk exposures and their potential impact to facilitate effective oversight.
1.1 The financial firm should ensure that the board and senior management have an adequate understanding of climate-related financial risks and that senior management is equipped with the appropriate skills and experience to manage and oversee these risks.
1.2 Financial firms should have in place a sound climate-related financial risk management framework as part of their overall business strategy, including considering the risk appetite specific to climate-related financial risks. The risk appetite should be defined, approved and overseen by the board. The board should be able to provide evidence of its ongoing oversight of these risks, particularly when they are deemed to be material.
1.3 Certain functions related to the management of climate-related financial risks may be delegated, but, as with other risks, the board is ultimately responsible and accountable for monitoring, managing and overseeing climate-related risks for the financial firm.
1.4 Where required, financial firms should ensure that the board and senior management actively keep up to date to develop and maintain sufficient knowledge and skills to understand and assess the impact of climate-related financial risks on the financial firm and the broader financial sector, including by providing training. In addition, financial firms should also provide capacity building and training to relevant personnel to enhance management of climate-related financial risks.
Principle 2 - Incorporation of climate-related financial risk exposures into overall business strategy
2. The board and senior management of a financial firm should consider material climate-related financial risk exposures when setting the organization’s overall business strategy.
2.1 In developing and executing the financial firm’s overall strategic plan, the board and senior management should ensure that all risks including material climate-related financial risks and the ensuing opportunities are considered. Please refer to Principle 4 for considerations on materiality.
2.2 Any climate-related strategies or objectives should align with and support the financial firm’s broader strategy, risk appetite, and risk management framework.
2.3 It is recognised that the incorporation of material climate-related financial risks into various planning processes is evolving as measurement methodologies, models, and data for analysing these risks mature over time. The board and senior management should ensure that climate-related financial risks are documented and periodically reviewed. Any climate-related strategies or objectives should be continuously improved based on the lessons drawn from measuring, analysing and monitoring of these risks.
Principle 3 – Assigning climate-related financial risk management responsibilities within the organization
3. The financial firm’s board should assign climate-related financial risk management responsibilities throughout the organization.
3.1 Responsibilities for identifying and managing climate-related financial risks should be clearly assigned to either board committees or appropriate senior management to ensure climate-related financial risks are appropriately considered as part of the financial firm’s business strategy and risk management framework.
3.2 As outlined in Principle 1, while the financial firm’s board remains ultimately responsible and accountable for the oversight of the management of climate-related financial risks, the assignment of responsibilities in line with Principle 3 should be formally documented.
3.3 Such roles and responsibilities should be clearly defined to ensure there is clarity over functions, accountability, governance structure, escalation processes and reporting procedures across the financial firm in relation to climate-related financial risk management.
3.4 Where dedicated climate-related roles or departments are established, their responsibilities and interaction with existing governance structures should be clearly defined and documented.
3.5 Roles and responsibilities for identifying and managing climate-related financial risks should be regularly reviewed to ensure it continues to be relevant to the nature and complexity of the business model and activities of the financial firm as well as the evolution of climate-related financial risks management approaches and methodologies.
Principle 4 – Incorporation of climate-related financial risks into risk management framework
4. The financial firm’s board and senior management should oversee the incorporation of climate-related financial risks into the organization’s internal risk management framework and oversee the development and implementation of policies and procedures to identify, assess, measure, mitigate, monitor and report on climate-related financial risk exposures.
4.1 Climate-related financial risks affecting financial firms should be identified. Identification of these risks should involve a comprehensive assessment of how the risks posed by climate-related matters may affect the financial firm, which should include an assessment of climate-related financial risks across a range of plausible scenarios and under various time horizons.
4.2 An appropriate framework for managing climate-related financial risks should be based on a comprehensive assessment of how and to what extent such risks would affect the financial firm’s business, operations and/or portfolios. The assessment of climate-related financial risks should take into account strategic, financial, operational and reputational risk implications.
4.3 Financial firms should conduct a materiality assessment with clear definitions and thresholds for climate-related financial risks, which will help them decide how to embed climate-related financial risks into their existing risk management frameworks.
4.4 A financial firm should, in a materiality assessment, consider its exposure to physical and transition risks.
4.5 Depending on the type of exposure and risk drivers, financial firms should deploy qualitative and/or quantitative approaches to assess the materiality of the risks. To form a final judgement on materiality, financial firms should develop a threshold, or a combination of thresholds, against which the outcome of the materiality assessment is determined. These thresholds can be quantitative or qualitative, depending on whether a quantitative assessment of materiality is feasible or whether a qualitative threshold is more suitable.
4.6 Based on the materiality and potential impacts identified, financial firms should update their existing risk management framework to embed climate-related financial risk considerations.
4.7 Financial firms should also regularly review relevant policies and processes to assess their effectiveness, and adjust them based on the outcomes of ongoing risk monitoring. Any ensuing updates to these policies and procedures should be documented.
4.8 Where material climate-related financial risks are identified, financial firms should establish and implement plans to mitigate these risks and manage their exposures. Examples of such mitigation measures include establishing and enforcing sectoral or client-specific risk and relationship limits, including financial and durational; adjusting client engagement criteria; or applying haircuts to asset values, among others.
4.9 Relevant financial firms should consider climate-related financial risk within established traditional risk categories (for example, credit, market, liquidity, operational, underwriting and reputational risk profiles) or, depending on the materiality of the perceived risk, as a stand-alone risk category.
4.10 In line with their usual risk governance arrangements, relevant financial firms should consider how best to allocate the responsibilities for managing climate-related financial risks, such as by allocating them across the “three lines of defence” (core business, risk function and internal audit) to ensure comprehensive and effective identification, measurement monitoring and mitigation of climate-related financial risk.
4.11 A financial firm that has significant relationships with other entities in its group, including subsidiaries, affiliates or international branches, should develop and maintain methods and processes to coordinate the identification, assessment, measurement, mitigation, monitoring and reporting of material climate-related financial risks across the group.
Principle 5 – Monitoring and reporting of climate-related financial risks
5. The financial firm should ensure that internal reporting systems are capable of monitoring material climate-related financial risks and producing relevant, accurate and timely information to inform effective board and senior management decision-making. Such information should be reported to the board, senior management and relevant stakeholders, where required to do so. The financial firm should address identified information and data gaps.
5.1 The board and senior management should ensure that the financial firm has systems and resources in place to collect, analyse and aggregate climate-related financial risk data. Senior management should incorporate climate-related financial risk information in internal reporting, monitoring, and escalation processes, where relevant. This will facilitate timely and sound decision-making across the firm.
5.2 The financial firm should establish procedures to provide the board and senior management with relevant information on its material climate-related financial risk exposures, including monitoring and mitigation actions. The extent, form and frequency of internal reporting should be based on the nature and scale of the risks to which the financial firm is exposed.
5.3 Financial firms should develop metrics to monitor and report climate-related financial risks appropriate to their size, complexity, risk profile and activities. Like all risks, climate-related financial risks should be closely monitored; the higher the impact, the higher the review frequency.
5.4 Financial firms should ensure that risk monitoring captures the potential impact of climate-related risk drivers on the financial firm’s third-party arrangements and business continuity planning.
5.5 Given the evolving nature of climate-related financial risks, financial firms should monitor developments and seek to understand and, where possible, manage the impact of climate-related financial risk drivers on other material risks where additional transmission channels are identified. This should feed into the risk identification, assessment, measurement, mitigation and monitoring processes of these material risks.
5.6 Where appropriate, financial firms should consider building capabilities to address any information and data gaps. For example, data collection processes may need to be enhanced, such as strengthening the engagement with clients to develop a better understanding of the impact of climate-related financial risks on clients’ businesses, obtaining more climate-related or environmental information from clients, and using appropriate data proxies where necessary.
5.7 Financial firms should develop an adequate data governance framework that covers the nature and level of the risks to which they are or might be exposed and which allows them to use sufficiently forward-looking and granular climate-related risk information in their risk management and governance strategy.
Principle 6 – Incorporation of climate-related financial risks into capital and liquidity adequacy processes
6. Relevant financial firms should incorporate material climate-related financial risks in their internal capital and liquidity adequacy assessment processes.
6.1 Relevant financial firms should develop processes to evaluate the liquidity, capital and solvency impact of climate-related financial risks that may manifest within specified time horizons.
6.2 As part of their internal capital and liquidity adequacy assessment processes, relevant financial firms should consider climate-related financial risks that may impact their capital and liquidity positions over relevant time horizons (e.g., through their impact on traditional risk categories).
6.3 For those financial firms required to complete an Internal Capital Adequacy Assessment Process (ICAAP), an Internal Liquidity Adequacy Assessment Process (ILAAP), an Own Risk and Solvency Assessment (ORSA), or a similar process, climate-related financial risks should be incorporated into these frameworks to consider and record any material impact on capital and liquidity adequacy.
Principle 7 – Scenario analysis of climate-related financial risks
7. Where appropriate, relevant financial firms should develop and implement climate-related scenario analysis frameworks, including stress testing, in a manner commensurate with their size, complexity, risk profile and nature of activities.
7.1 Relevant financial firms should build sufficient capacity and expertise to develop and implement climate-related scenario analysis and stress testing programmes suited to their size, complexity, risk profile and nature of activities. These frameworks should include clearly defined objectives that reflect the firm’s overall climate-related financial risk management strategies and objectives. While working to build adequate internal capabilities in climate scenario development and analysis, financial firms may utilise relevant existing or emerging climate scenarios, whether global or regional, general or purpose-built.
7.2 The objectives of scenario analysis could include, for example, exploring the impacts of climate-related financial risks on the financial firm’s strategy and business model, identifying and measuring vulnerabilities to relevant climate-related financial risk factors including physical and transition risks, and estimating climate-related exposures and potential losses across a range of plausible scenarios.
7.3 Financial firms should identify appropriate data inputs and suitable metrics to assess climate-related financial risks.
7.4 Scenarios should include a spectrum of plausible, relevant and severe climate pathways, and should cover the types of climate-related financial risks (physical, transition and/or liability risks) to which financial firms are exposed and that affect their businesses and risk profiles.
7.5 Financial firms should conduct scenario analysis over a range of time horizons and assumptions while considering the benefits and limitations of such assumptions and the models. Short-term analysis is typically used to assess the impact on the firm’s risk profile and business operations, while longer-term analysis facilitates assessment of business models in light of shifts in economic and financial system structures.
7.6 Financial firms should use the results of scenario analysis as an input to analysing the adequacy of their existing risk management framework, including designing and implementing actions that mitigate the impact of identified climate-related financial risks. Results of the stress tests should also be considered as part of the internal capital and liquidity adequacy assessment processes, as detailed under Principle 6.
7.7 Climate-related financial risk scenario analysis is a developing area and approaches are expected to evolve and mature over time. Nevertheless, a climate-related scenario analysis framework could, in the near term, assist financial firms in identifying data and methodological limitations and uncertainties in climate-related financial risk management, as well as helping inform the firm about the adequacy of its climate-related financial risk management framework.
Annex
1. BCBS – Principles for the effective management and supervision of climate-related financial risks (June 2022).
2. BCBS – Climate-related financial risks: a survey on current initiatives (April 2020).
3. BCBS – Climate-related financial risks – measurement methodologies (April 2021).
4. BCBS – Climate-related risk drivers and their transmission channels (April 2021).
5. BCBS – Frequently asked questions on climate-related financial risks (December 2022).
6. Financial Stability Board (FSB) – Supervisory and Regulatory Approaches to Climate-related risks (October 2022).
7. FSB and NGFS – Climate Scenario Analysis by Jurisdictions (November 2022).
8. International Association of Insurance Supervisors – Application Paper on the Supervision of Climate-related Risks in the Insurance Sector (May 2021).
9. NGFS – Climate Scenarios (2022).
10. NGFS – Guide for Supervisors: Integrating climate-related and environmental risks into prudential supervision (May 2020).
Principles for Sustainability-Related Disclosures
Issued on 14/6/2024A. Introduction
- The UAE Sustainable Finance Working Group (SFWG) was established in 2019 to enable the UAE’s economic transition and encourage the adoption of sustainable finance at the national level. The members of the SFWG (the UAE Authorities) include ministries (Ministry of Finance, Ministry of Economy, Ministry of Climate Change and Environment, the Office of the UAE's Special Envoy for Climate Change), financial services regulators (the Central Bank of the UAE, the Securities and Commodities Authority, the Financial Services Regulatory Authority of Abu Dhabi Global Market and the Dubai Financial Services Authority), and UAE exchanges (Abu Dhabi Securities Exchange, Dubai Financial Market and Nasdaq Dubai).
- In the UAE’s first set of Guiding Principles on Sustainable Finance published in January 2020, the SFWG committed to promoting appropriate Environmental, Social and Corporate Governance (ESG)-related reporting and disclosures. The SFWG also recommended that ESG reporting be consistent with national disclosure obligations and take into account internationally recognised reporting standards on ESG matters.
- This document is the result of the work of the SFWG and contains Principles for Sustainability-related Disclosures (the Disclosure Principles) for the domestic entities or branches and subsidiaries of foreign entities falling under the purview of the UAE Authorities (the Reporting Entities). The SFWG members recognise that adequate transparency in relation to the actual or potential impact of climate change and other environmental, social and governance factors is essential to inform investors and protect consumers, foster efficient functioning of financial markets and promote financial stability, while driving the values of sustainability and social responsibility.
- Transparency allows investors to make more informed decisions and evaluate investment risks and opportunities. Measurement and high-quality sustainability-related disclosures allow organisations and their relevant stakeholders to understand better both risk-adjusted returns and the progress being made in managing and adapting to sustainability matters. It can also act as a market discipline mechanism through which investors, shareholders and other stakeholders can exert influence on companies and the investment industry to act in the best interests of society, by directing capital to companies that positively contribute to sustainability.
The members of the SFWG consider it important to encourage transparency on sustainability-related matters.
Accordingly, in issuing these Principles, the SFWG members undertake to:
- Consider implementation of recognised regulatory disclosure frameworks by relevant entities under our respective remits in our respective jurisdictions;
- Consider progressing towards full implementation of a prevailing disclosure framework or frameworks to help support the UAE’s Net Zero Strategic Initiative in the context of stable economic development; and
- Engage in capacity building activity and industry outreach with the relevant entities in our respective jurisdictions in order to facilitate and prepare any such implementation.
B. Objectives of the Principles
- The objective of these Disclosure Principles is to pave the way and help prepare relevant entities in the UAE to achieve high-quality and relevant ESG disclosures.
- The SFWG members recognise the existence and widespread use of numerous reporting initiatives and frameworks, which have developed over time around the globe and are being currently used in the UAE. Some of these are industry-based, regionally or globally recognized frameworks and standards, operating on a voluntary basis, including those issued by the Global Reporting Initiative (GRI), the Sustainability Accounting Standards Board (SASB), the International Integrated Reporting Council (IIRC), the Task Force on Climate-related Financial Disclosures (TCFD), the Climate Disclosure Standards Board (CDSB) and the International Sustainability Standards Board (ISSB). The SFWG members acknowledge that these frameworks may have different objectives and provide varying perspectives on ESG-related matters.
- The SFWG members also recognise that there exists an international movement towards greater uniformity, such as the issuance of the ISSB disclosure standards and the ongoing development of Pillar 3 disclosure requirements for banks by the Basel Committee on Banking Supervision, which may pave the way for a global baseline framework in the future that complements and works alongside other general disclosure frameworks.
C. Application of the Principles
- The Disclosure Principles constitute a declaration of common understanding among the SFWG members on their minimum expectations in this area in their respective jurisdictions. Members of the SFWG will consider the development and implementation of disclosures frameworks in line with the Principles, if they have not already done so. Reporting Entities should also be aware of the Principles as they relate to current and future efforts undertaken by Reporting Entities in the area of ESG disclosures.
- While the Disclosure Principles are endorsed by the entire SFWG, it remains at the discretion of each of the Authorities to determine how the Disclosure Principles may be translated into their respective regulatory frameworks. This means that the relevant Authority, when implementing disclosure requirements based on these Disclosure Principles, may decide on matters including but not limited to:
- which Reporting Entities the requirements apply to;
- the Reporting Entity’s type, profile or size threshold (if any) that must be crossed before disclosure is applicable;
- the respective disclosure requirements to be followed;
- the reporting frequency for each disclosure requirement;
- whether to use voluntary, ‘comply or explain’ or mandatory avenues for given Reporting Entities;
- whether additional requirements or modalities relevant for specific types of Reporting Entities are necessary to improve transparency; and
- the timeline to implement disclosure requirements in its jurisdiction.
D. Implementation
- The SFWG members will communicate to the Reporting Entities their expectations in relation to the publication of the sustainability-related information relevant to their investors, markets and customers as well as to regulators. It is understood that the term “sustainability-related information” may encompass both ESG and climate related considerations. The timing, frequency, scope of application (including recognition of reporting at the group level), materiality and level of granularity required for the reported information will need to be considered carefully for the purpose of providing meaningful and adequate information. Unless otherwise determined by the relevant authority, branches or subsidiaries of foreign entities may implement these Principles or equivalent standards at the group level if applicable to avoid duplication of disclosures.
- To ensure that adequate progress is being made, the SFWG members would expect to track the respective Reporting Entities’ use and implementation of the applicable ESG disclosures frameworks, including through the use of relevant regulatory tools.
- In some instances, the SFWG may work in cooperation with the relevant stock exchanges who may have a role to play in promoting and supporting this process. In some instances, exchanges may wish to issue additional guidance in line with standards set by the relevant Regulator(s).
E. The Principles
Principle 1
1- Reporting Entities should put in place adequate policies, procedures and systems allowing them to report on sustainability- related matters. 1-1 Systems: Reporting Entities should put in place the internal reporting systems for monitoring, and reporting on, material sustainability-related risks, and the processes to ensure that data gaps are addressed within their data governance framework.1 1-2 Internal communication: Reporting Entities should ensure timely reports of data, information and analysis to the board of directors and senior management to enable and underpin robust decision-making internally. 1-3 Reporting: Reporting Entities should provide timely reports of data and sustainability-related information to the public. __________________________________
1 The details related to the application of this Principle 1 are also cross-referred to in the UAE SFWG’s “Principles for the effective management of climate-related financial risks”, in particular in Principle 5 on Monitoring and reporting of climate- related financial risks.
Principle 2
2- In disclosing information about their sustainability-related risks and opportunities, Reporting Entities should consider including the following factors. 2-1 Transparency: Reporting Entities should disclose relevant information about their sustainability policies, practices, and performance to the public, including investors, customers, and stakeholders. 2-2 Materiality: Reporting Entities should focus on disclosing all material sustainability risks and opportunities that are relevant to their business and that have or could have a significant impact on their financial performance. Information is deemed as material if omitting, misstating or obscuring it could reasonably be expected to influence decisions that investors or other stakeholders make. 2-3 Relevance: Reporting Entities should ensure that their sustainability disclosures are relevant and useful to stakeholders, including investors, customers, and regulators, by providing context, analysis, and insights that help them understand the risks and opportunities associated with sustainability issues. 2-4 Comprehensiveness: The disclosure should facilitate comprehensive insight into Reporting Entities exposures to potential sustainability-related impacts; the potential nature and size of such impacts; the organisation’s governance, strategy, and processes for managing such risks, and its performance with respect to managing the related risks and opportunities. 2-5 Consistency and comparability: Reporting Entities should use consistent and comparable sustainability metrics and reporting standards. The disclosures should be presented using consistent formats, language, and metrics from period to period to allow for assessment over time. 2-6 Clarity: the information and data presented should be easy to read and understand by the relevant audience. Necessary definitions, explanations and illustrations should be used to facilitate the comprehension of the data and information presented. 2-7 Frequency and timeliness: Reporting Entities should provide timely and regular updates on their sustainability performance, so that stakeholders can track their progress over time and make informed decisions. When appropriate, the Reporting Entities should be prompt in their issuance of interim reports and statements of interest and relevance to their stakeholders. 2-8 Stakeholder engagement: Reporting Entities should, where relevant, engage with stakeholders, to understand their sustainability concerns and priorities, and use this feedback to improve their sustainability disclosures and performance. 2-9 Verification and assurance: Reporting Entities should aim to use independent, third-party verification and assurance to confirm the accuracy and reliability of their sustainability disclosures, particularly for key performance indicators, metrics and targets. 2-10 Integration: Reporting Entities should integrate their sustainability disclosures into their overall corporate reporting and governance frameworks, including their board discussions and annual reports, financial statements, to ensure that sustainability is adequately embedded in their business strategies and decision-making processes. 2-11 Continual review and improvement: Reporting Entities should strive for continual improvement in their sustainability disclosures and performance, by setting adequate sustainability targets and regularly reviewing and updating their sustainability policies, practices, and reporting. Principle 3
3- Sustainability-related disclosures should reflect the way in which an entity operates, including in the areas of governance, strategy and risk management, and incorporate relevant metrics and targets. While additional, specific disclosure requirements may apply depending on the type of Reporting Entity, the following minimum disclosures would be expected from the Reporting Entities. 3-1 Governance: Information about the governance processes, controls, and procedures in place to manage sustainability-related risks and opportunities. Disclosures should include information on how the board of directors determines whether sufficient knowledge and skills are available to understand and assess the impact of sustainability-related risks on the Reporting Entity, and how sustainability-related risks and opportunities are taken into account in the board’s oversight, decisions and actions. Disclosures should also cover the role of the senior management in the governance processes for sustainability-related risks and opportunities. 3-2 Strategy: Information about how the Reporting Entity’s strategy incorporates sustainability-related considerations, including risks and opportunities, as well as any relevant transition plans. Information disclosed should include a description of how identified sustainability risks and opportunities are expected to affect the Reporting Entity’s business model and financial results over the short-, medium- and longterm, and the measures the Reporting Entity has undertaken or plans to undertake to manage such risks and take advantage of the potential opportunities. 3-3 Risk management: Information about sustainability-related risks and opportunities and how they are being managed. Information disclosed should include the processes and policies the Reporting Entity uses to identify, assess, measure, mitigate, monitor and report on sustainability-related risk exposures, how those processes are integrated into the overall risk management framework of the Reporting Entity, including capital and liquidity monitoring and, if applicable, how scenario analysis is used to identify sustainability-related risks. 3-4 Metrics and targets: Information about the metrics and targets used to measure, manage and monitor sustainability-related performance. Principle 4
4- To improve transparency and quality of sustainability-related, product-level disclosures, market participants should consider the following elements when dealing with and offering sustainability-related products. 4-1 Naming: Naming of sustainability-related products should ensure that the name of the product accurately reflects the nature and extent of the product’s sustainability focus, including promoting consistency with the product’s objectives, characteristics and strategies. 4-2 Labelling and classification: Labelling and classification systems used for the purpose of sustainability-related products should be clearly and correctly explained and inconsistent application should be avoided. 4-3 Objectives disclosure: Sustainability- related products should contain clear disclosures in a form appropriate for the product about sustainability-related objectives. 4-4 Strategies disclosure: Disclosures should be made in product offering documents about the strategies of the sustainability-related products to achieve their sustainability goals. 4-5 Risk disclosure: Sustainability-related products should contain disclosures of material risks unique to the product profile and arising from a product’s focus on sustainability. 4-6 Marketing materials: Marketing materials relating to sustainability-related products should be fair, clear and not misleading. 4-7 Monitoring and reporting: Monitoring of compliance and reporting to customers in respect of the sustainability-related product’s compliance with its objectives and characteristics, containing as appropriate and available qualitative and quantitative information, should be put in place. Enabling Technologies
Guidelines for Financial Institutions Adopting Enabling Technologies
Open Finance Regulation
C 7/2023 Effective from 15/4/2024Introduction
The Central Bank of the UAE (CBUAE), together with the Securities and Commodities Authority (SCA), the Dubai Financial Services Authority (DFSA) of the Dubai International Financial Centre and the Financial Services Regulatory Authority (FSRA) of Abu Dhabi Global Market, collectively referred to as “Supervisory Authorities”, have issued the “Guidelines for Financial Institutions adopting Enabling Technologies” (“the Guidelines”).
The Guidelines are issued pursuant to the powers vested in the respective law of the individual Supervisory Authorities, including:
- •The Central Bank of the UAE under the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities (“Central Bank Law”);
- •The Securities and Commodities Authority under Federal Law No. (4) of 2000 concerning the Emirates Securities and Commodities Authority and Market;
- •The Dubai Financial Services Authority pursuant to the Regulatory Law - DIFC Law No. (1) of 2004 concerning Dubai International Financial Centre; and
- •The Financial Services Regulatory Authority pursuant to Law No. (4) of 2013 concerning Abu Dhabi Global Market.
The increasing adoption of technology-enabled business models presents both opportunities and challenges to those carrying out Innovative Activities.
The purpose of the Guidelines is to provide a set of principles when using Enabling Technologies in financial services and accompanying guidance. The key principles are broad enough to cater to the different business models, operating models and financial services offered by existing organisations operating in, and new entrants to, the financial services sector. The key principles are accompanied by more detailed guidance for Institutions to consider when using Enabling Technologies.
The Supervisory Authorities may issue further guidance relating to the Guidelines.
Introduction and Scope
This Open Finance Regulation (this Regulation) establishes a framework for the licensing, supervision and operation of an Open Finance Framework in the United Arab Emirates. The Open Finance Framework consists of a Trust Framework, an API Hub and Common Infrastructural Services, which provide Open Finance access for the cross-sectoral sharing of data and the initiation of Transactions, on behalf of Users.
Mandated Entities
Participation in the Open Finance Framework is mandatory for all Licensees with respect to the Products and Services within its scope. Licensees (as Data Holders and Service Owners) are required under this Regulation to provide participants in the Open Finance Framework (as data recipients and service initiators) with access to customer data and the ability to Initiate Transactions on customer Accounts and Products.
Data Sharing and Service Initiation of Transactions is in all cases subject to the express consent of Users, the application of appropriate authentication processes and the use of secure communication. This Regulation and the rights of access to data and Accounts established hereunder, do not apply with respect to activities that are not regulated by the Central Bank.
Licensees mandated by this Regulation to provide Open Finance access include the following entities:
a. Banks incorporated in the UAE. b. branches of foreign Banks/representative offices of foreign Banks. c. specialized Banks. d. restricted license Banks. e. Islamic Banks and Islamic windows. f. Finance Companies. g. payment service providers (category 1/2/3/4). h. retail payment systems providers. i. stored value facility providers. j. exchange houses. k. loan-based crowdfunding companies. l. Insurance Brokers. m. Insurance Companies (national companies and foreign branches). n. any other entity deemed to be a relevant Licensee by the Central Bank. The Licensees which are mandated to provide Open Finance access, pursuant to this Regulation, will be onboarded in phases. The first phase will include all Banks, including branches of foreign banks, and Insurance Companies (national companies and foreign branches) only. Later phases of the onboarding will be announced by the Central Bank through official channels.
Open Finance Providers and their Licensing
In order to facilitate the adoption of Open Finance and the participation of businesses as licensed Data Sharing Providers and/or Service Initiation Providers, this Regulation establishes a new category of regulatory license for providers of Open Finance Services. Open Finance Providers will be the holders of such a license, which enables them to undertake Data Sharing and/or Service Initiation.
Providers of Open Finance Services can opt for either one or both of the options to undertake Data Sharing or Service Initiation under an Open Finance License.
Without prejudice to other regulatory licenses that they hold, an Open Finance License will not permit license holders to perform any other category of licensed activity and, in particular, will not entitle license holders to provide any form of Advice or to arrange or mediate Transactions in licensed activities, or hold customer funds in any form. Open Finance Providers must separately obtain or hold the additional regulatory licenses required to undertake any other licensed activity or activities.
Persons Deemed Licensed
Certain categories of Licensees, as specified in Article 3 of this Regulation, are treated as Persons Deemed Licensed. A Person Deemed Licensed must notify the Central Bank in writing of the intention to provide any Open Finance Service, setting out full details of its intended activities, and obtain the approval of the Central Bank prior to commencing such activities.
Articles Applicable to Licensees
All Licensees, whether or not they are engaged in the provision of Open Finance Services, must comply with the requirements of this Regulation with regard to Data Sharing and Service Initiation by Users through Open Finance Providers and specifically the requirements in Articles 18 to 22 of this Regulation.
Objectives
The objectives of the Guidelines are:
- •To provide Institutions with best practices on risk management in respect to Enabling Technologies;
- •To encourage the safety and soundness of Institutions so that relevant risks arising from innovative business models and services are adequately managed and mitigated;
- •To limit the systemic risks that could arise from the use of innovative technology, thus fostering transparency and financial stability;
- •To provide guidance on how to manage the risks when adopting Enabling Technologies to deliver more efficient, secure and robust solutions to Customers thereby improving organisational efficiency and financial inclusion; and
- •To promote the growth and advancement of the UAE financial services sector and encourage adoption of Innovative Activities in the UAE whilst managing risks in a proportionate manner.
Objectives
In exercising its powers and functions under this Regulation, the Central Bank has regard to the following objectives:
a. Ensuring the safety and soundness of Open Finance Services; b. Adoption of effective and risk- based licensing requirements for Data Sharing and Service Initiation; c. Promoting the reliability and efficiency of Open Finance Services as well as public confidence; d. Encouraging innovation to promote competition and to benefit consumers through. enhanced transparency across all financial products and services; and e. Reinforcing the UAE's status as a leading financial technology hub in the region. Where this Regulation, or its accompanying Regulations, includes a requirement to provide information or to take certain measures, or to address certain items listed at a minimum, the Central Bank may impose requirements that are additional to those provided in the relevant article. Structure of the Guidelines
The Guidelines are divided into the following sections:
- •Section 1: Provides definitions of the key terms used throughout the Guidelines;
- •Section 2: Sets out the key principles relating to the adoption and use of different types of Enabling Technologies; and
- •Section 3: Provides guidance on the application of the key principles covering the use of Application Programming Interface (API), Cloud Computing, Biometrics, Big Data Analytics and Artificial Intelligence (AI), and Distributed Ledger Technology (DLT).
Article (1) Definitions
The following terms shall have the meaning assigned to them below for the purposes of this Regulation:
- Account: an account held by a User with a Licensee relating to one or more of the Products specified in Article 5 of this Regulation.
- Advice: advice on Products or Accounts and includes any method of communication that provides an opinion, evaluation, recommendation, and/or biased information / comparisons to a User or when acting as a User’s agent, provided that it could reasonably be regarded as having the intent to influence a User’s choice or decision to select, buy, sell, hold or subscribe to a particular Product or Account, related options or an interest in a particular Product or Account.
- AML Laws: Decree Federal Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations and Cabinet Decision No. (10) of 2019 Concerning the Implementing Regulation of Decree Federal Law No. (20) of 2018 on Anti-Money Laundering and Combating the Financing of Terrorism and Illegal Organizations, as amended, and any instructions, guidelines and notices issued relating to their implementation.
- API Hub: the centralized Application Programming Interface Hub established by the Central Bank, through which parties will be able to access the Open Finance Framework.
- Applicant: any juridical person duly incorporated in the State which submits an Application.
- Application: a written request for obtaining an Open Finance License.
- Bank: any juridical person licensed in accordance with the provisions of the Central Bank Law to primarily carry on the activity of taking deposits and any other Licensed Financial Activities.
- Board: the board of directors of an Applicant or Open Finance Provider in accordance with applicable State law.
- Central Bank: the Central Bank of the United Arab Emirates.
- Central Bank Law: the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank and Organization of Financial Institutions and Services, as amended.
- Chief Executive Officer: the most senior executive appointed by the Board.
- Common Infrastructural Services: the services specified in Schedule 1 of this Regulation.
- Confidential Data: data relating to a User, who is or can be identified, either from the confidential data, or from the confidential data in conjunction with other information that is in, or is likely to come into, the possession of a Person or entity that is granted access to the confidential data.
- Controller: a Person that alone or together with the Person’s associates has an interest in at least 20% of the shares in an Open Finance Provider or is in a position to control at least 20% of the votes in an Open Finance Provider.
- Data Holder: a Licensee holding User Data.
- Data Sharing: an on-line service to provide a User with consolidated User Data relating to one or more Accounts and/or Products held with a Data Holder.
- Data Sharing Provider: a juridical person who is licensed by the Central Bank to carry on Data Sharing activities.
- Finance Company: the juridical person who is licensed as a Finance Company under the Finance Companies Regulation.
- Finance Companies Regulation: Central Bank Circular No. 3/2023, as amended.
- Initiate: (1) an electronic instruction to a Service Owner to effect a transfer, credit, debit, placement, withdrawal, redemption, sale, order or cancellation; or (2) communicating a User’s agreement to open, effect, enter into or take any other action in relation to an Account or Product. Initiate does not include the execution of any Transaction.
- Insurance Broker: a juridical person licensed to practice insurance brokerage activity in the State, under the Insurance Law.
- Insurance Company: any juridical person licensed to engage in insurance business in the State, under the Insurance Law.
Insurance Intermediation: the activity of soliciting, negotiating or selling insurance contracts through any medium where:
(a) “solicit” means attempting to sell insurance or asking a Person to apply for a particular kind of insurance from a particular insurer for compensation;
(b) “negotiate” means the act of conferring directly with, or offering Advice directly to, a purchaser or prospective purchaser of a particular contract of insurance concerning any of the substantive benefits, terms or conditions of the contract, provided that the person engaged in that act either sells insurance or obtains insurance from insurers for purchasers;
(c) “sell” means to exchange a contract of insurance by any means for money or its equivalent on behalf of an Insurance Company.
- Insurance Law: the Federal Decree-Law No. (48) of 2023 Regulating Insurance Activities and its Executive Regulations, and any amendments thereof.
- Insurance Underwriting: evaluating the risk and establishing the price of insurance.
- Licensed Financial Activities: the financial activities subject to Central Bank licensing and supervision, which are specified in Article (65) of the Central Bank Law.
- Licensed Financial Institution: Banks and Other Financial Institutions licensed in accordance with the provisions of the Central Bank Law to carry on a Licensed Financial Activity, including those which carry on the whole or a part of their business in compliance with the provisions of Islamic Shari`ah, and are either incorporated inside the State or have branch offices inside the State.
- Licensees: Banks, Insurance Companies, Insurance Brokers and Other Financial Institutions.
- Master System of Record: the collection of all data, including Confidential Data, required to conduct all core activities of a Licensee, including the provision of services to clients, managing all risks, and complying with all legal and regulatory requirements.
- Open Finance Framework: the framework for Open Finance Services established and operated under this Regulation.
- Open Finance License: the license granted under this Regulation to provide Data Sharing and/or Service Initiation.
- Open Finance Provider: a juridical person who is licensed by the Central Bank to carry on Open Finance Services.
- Open Finance Service: Data Sharing and/or Service Initiation.
- Other Financial Institutions: any juridical person, other than Banks, licensed, in accordance with the provisions of the Central Bank Law, to carry on a financial activity or more, of the Licensed Financial Activities.
- Outsourcing: an agreement with another party either within or outside the UAE, including a party related to the Open Finance Provider, to perform on a continuing basis an activity which currently is, or could be, undertaken by the Open Finance Provider itself.
- Payee: a Person who is the intended recipient of funds, which have been the subject of a Transaction.
- Payer: a Person who holds a Payment Account and gives a payment order from that Payment Account, or, where there is no Payment Account, a Person who gives a payment order.
- Payment Account: an account with a Payment Service Provider held in the name of at least one user of a Retail Payment Service which is used for the execution of payment Transactions.
- Payment Service Provider: a juridical person that has been licensed in accordance with the Retail Payment Services and Card Schemes Regulation to provide one or more Retail Payment Services and has been included in the register of Licensed Financial Institutions as per Article (73) of the Central Bank Law.
- Person: a natural or juridical person, as the case may be.
- Personal Data: any information, which is related to an identified or identifiable natural person.
- Person Deemed Licensed: a Person specified in Article 3 of this Regulation as deemed licensed under this Regulation.
- Processing: in relation to Personal Data and for the purposes of Article 22 of this Regulation, any operation or set of operations which is performed on Personal Data or on sets of Personal Data, whether or not by automated means, such as collection, recording, organisation, structuring, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, restriction, erasure or destruction.
- Product: a product specified in Article 5 of this Regulation.
- Regulations: any resolution, regulation, circular, rule, standard or notice issued by the Central Bank.
- Retail Payment Service: any business activity set out in Annex I of the Retail Payment Services and Card Schemes Regulation, as amended.
- Retail Payment Services and Card Schemes Regulation: Central Bank Circular No. 15/2021, as amended.
- Senior Management: the executive management of the Open Finance Provider responsible and accountable to the Board for the sound and prudent day-to-day management of the Open Finance Provider, generally including, but not limited to, the Chief Executive Officer, chief financial officer, chief risk officer, and heads of the compliance and internal audit functions.
- Sensitive Data: any Personal Data related to the health of a person, such as his/her physical, psychological, mental, genetic or sexual condition, including information related to healthcare services provided thereto that reveals his/her health status.
- Service Initiation: the service of initiating by electronic means a Transaction relating to an Account or Product.
- Service Initiation Provider: a juridical person who is licensed by the Central Bank to carry on Service Initiation activities.
- Service Owner: a Licensee that holds an Account or Product for a User.
- State: the United Arab Emirates (UAE).
- Stored Value Facilities Regulation: Central Bank Circular No. 6/2020, as amended.
- Technical Service Provider: a Person who provides technical support to third parties for the provision of Open Finance Services, including information technology services, communication network provision, the processing and storage of data, the obtaining and processing of Account and Product information and trust and privacy protection services.
- Transaction: an act Initiated by a User through the Service Initiation Provider to effect a transfer, credit, debit, placement, withdrawal, redemption, sale, order or cancellation in relation to an Account or a Product.
- Trust Framework: the trust framework established and operated pursuant to Article 2 and Schedule 1 of this Regulation.
- Unauthorized Transaction: a transaction, the execution or initiation of which, the User has not given consent for.
- User: a Person who uses Data Sharing or Service Initiation.
- User Data: information relating to a User that is: (1) in relation to Accounts and Products as specified in Article 5 of this Regulation; and (2) data more particularly described in the relevant Regulations issued by the Central Bank for that purpose.
- Account: an account held by a User with a Licensee relating to one or more of the Products specified in Article 5 of this Regulation.
Scope of Application
The Guidelines are applicable to all Institutions licensed and supervised by the Supervisory Authorities that are using, or intend to use, Enabling Technologies. Institutions are expected to consider the application of the Guidelines to their business activities in a manner that reflects the size and complexity of the Institution and the nature, scope, risk level, complexity and materiality of their Institution’s Innovative Activities. They are in addition to any binding regulations, standards, guidance, and other instructions issued by the relevant Supervisory Authorities, which shall take precedence over the Guidelines.
The Open Finance Framework
Requirements to be Licensed
Article (2) Licensing and Licensing Procedures
- No juridical person may engage in providing an Open Finance Service within the State unless it obtains an Open Finance License from the Central Bank or is specified as a Person Deemed Licensed.
- An Applicant for an Open Finance License must submit an Application (together with the required supporting documents and information) to the Central Bank in accordance with the procedure specified by the Central Bank’s Licensing Division and according to its licensing guidelines.
- An Applicant must submit an Application which includes the options for which it would like to apply in respect of Data Sharing or Service Initiation. If the Licensee later seeks to change the options selected under their license, they must re-apply and obtain approval from the Central Bank.
- An Applicant must at the time of submitting its Application satisfy all requirements as to legal form, minimum capital and fit and proper requirements and any other requirements set by the Central Bank.
- The Central Bank will issue its decision of approval or dismissal of the Application within a period not exceeding sixty (60) working days from the date of the Applicant meeting all conditions and requirements for licensing. The lapse of this period without decision on the Application shall be considered an implicit rejection thereof.
- The granting by the Central Bank of an Open Finance License permits the holder of that license to provide an Open Finance Service (Data Sharing and/or Service Initiation) but no other Licensed Financial Activities or services.
- A Technical Service Provider does not require an Open Finance License provided that its services are limited to the provision of support services to Open Finance Providers and/or Persons Deemed Licensed and it does not directly engage in any activities regulated under this Regulation.
- In the event of use of a Technical Service Provider by an Open Finance Provider or a Person Deemed Licensed, the responsibility, regulatory requirements, legal basis and liability as a result of operation within the Open Finance Framework cannot be transferred to the Technical Service Provider or any other third party.
- No juridical person may engage in providing an Open Finance Service within the State unless it obtains an Open Finance License from the Central Bank or is specified as a Person Deemed Licensed.
Article (3) Persons Deemed Licensed
The following are Persons Deemed Licensed:
1.1. Banks licensed in accordance with the Central Bank Law;
1.2. Finance Companies licensed in accordance with the Finance Companies Regulation;
1.3. Persons licensed by the Central Bank to provide Retail Payment Services under the Retail Payment Services and Card Schemes Regulation;
1.4. Insurance Brokers licensed in accordance with the Insurance Law;
1.5. Insurance Companies licensed in accordance with the Insurance Law; and
1.6. Stored value facility providers licensed in accordance with the Stored Value Facilities Regulation.
- A Person Deemed Licensed must provide prior written notice to the Central Bank of its intention to provide an Open Finance Service. The notice must be in the form prescribed by the Central Bank from time to time and must provide a description of the Open Finance Service that the Person intends to provide, the resources that will be utilised in the provision of the Open Finance Service and the governance arrangements relating to them. The Central Bank’s approval must be obtained prior to the commencement of the provision of the Open Finance Service. The Central Bank will issue its decision of approval or rejection within a period not exceeding sixty (60) working days from the date of the notice. The lapse of this period without decision on the request shall be considered an implicit rejection thereof.
- All articles of this Regulation apply to Persons Deemed Licensed, when their approval to provide the Open Finance Service is granted by the Central Bank.
Article (4) Limitations
An Open Finance Provider must not:
1.1. receive, hold or transfer any funds for or on behalf of a User;
1.2. provide Advice to a User in relation to a particular Account or Product;
1.3. provide any personal and specific recommendation to a User in relation to a particular Account or Product;
1.4. receive any fee, commission, payment or other benefit from the provider of an Account or Product;
1.5. process any User Data that is Sensitive Data for the provision of any Open Finance Service, even with the explicit consent of the User;
1.6. negotiate, mediate, effect or enter into any agreement or Transaction on behalf of a User in relation to an Account or Product; or
1.7. engage in any form of Insurance Intermediation or Insurance Underwriting.
- The limitations specified in Article 4(1) of this Regulation, do not prevent an Open Finance Provider from providing Users with information, including information based on analyses, relating to commercially available but nonspecific Accounts and/or Products. This can be communicated by displaying the information on-line or otherwise, but must not involve the provision of Advice.
- The limitations specified in Article 4(1) of this Regulation do not apply to an Open Finance Provider who holds any required additional license to perform the relevant activities from the Central Bank.
Section 1: Definitions
In the Guidelines, words and expressions have the meanings set out below.:
Accounts and Products in Scope of Open Finance
Article (5) Accounts and Products
An Account or a Product is within the scope of this Regulation where it relates to any of the following offered or issued by a Licensee:
1.1 deposits;
1.2 payment accounts and services;
1.3 savings accounts and term deposits;
1.4 credit, debit and charge card accounts and products (including acquiring and processing card transactions);
1.5 standing orders;
1.6 direct debits;
1.7 stored value facilities and prepaid payment accounts;
1.8 post-paid payment accounts;
1.9 foreign exchange accounts and products;
1.10 credit, loans and any other personal finance accounts and products;
1.11 mortgages and other loans secured on property or other assets;
1.12 virtual accounts or products providing for the items specified in 1.1 – 1.11 above; and
1.13 insurance products, including life and general insurance.
- The Central Bank may, from time to time, amend or supplement the list in Article 5(1) of this Regulation.
- The list in Article 5(1) of this Regulation shall not include accounts or products regulated by the Securities and Commodities Authority, unless approved by the Securities and Commodities Authority.
Section 2: Key Principles for Adopting Enabling Technologies
Initial and Ongoing Requirements
Key Principles for All Enabling Technologies
- 2.1Data Protection: Institutions are required to cpmply with all applicable legislation and regulations in relation to Data protection when handling the use, transmission, and storage of Data.
- 2.2Control Functions: Institutions should have effective audit, compliance and risk management functions that are equipped with the relevant expertise for reviewing and assessing the adequacy of the internal control environment for implementing the Enabling Technologies.
- 2.3Independent Review: Institutions should ensure that formal, independent reviews/audits of Enabling Technologies are carried out periodically, the regularity of which will depend on the nature, scope, complexity and materiality of the Institution’s technology framework. These reviews should be conducted by the internal audit function and/or third party/external auditors that can provide independent, timely assurance in respect of an Institution’s Enabling Technologies, including compliance with relevant internal policies. While Institutions may co-source or outsource the audit activities surrounding their innovative technology, they are expected to ensure that the OSP has a solid understanding of their operations, an appreciation of the existing and potential risks and knowledge of the controls required to remain in compliance with all applicable laws and regulations.
- 2.4Skills, Knowledge and Expertise: Institutions should ensure that their adoption of Enabling Technologies is supported by resources with the necessary skills, knowledge, and expertise specific to their roles and functions. Staff responsible for the operations, management and oversight of innovative technologies should possess the required expertise to ensure ongoing effectiveness and that the technologies continue to meet intended outcomes. Institutions should ensure that they continue to develop specialist expertise relative to the technologies adopted.
- 2.5Training: Given the rapid developments in respect of Enabling Technologies, Institutions should ensure that adequate training is provided to the relevant staff for handling Enabling Technologies.
Article (6) Minimum Capital
- For the purpose of being granted a license by the Central Bank to perform an Open Finance Service, an Open Finance Provider will be required to hold a minimum capital amount of one million Dirham (AED 1,000,000).
- Additional capital requirements may be imposed by the Central Bank, at its sole discretion and notified to the Open Finance Provider, with the Central Bank taking into account factors such as the risk, size and/or complexity associated with the activities conducted by the Open Finance Provider.
- For the purpose of being granted a license by the Central Bank to perform an Open Finance Service, an Open Finance Provider will be required to hold a minimum capital amount of one million Dirham (AED 1,000,000).
Application Programming Interfaces (APIs)
- 2.6Governance: Institutions should establish an approved and documented governance framework for effective decision-making and the proper management and control of risks arising from the use of APIs.
- 2.7Design: Institutions should ensure that APIs, whether designed in-house or by a Third Party, are designed such that the APIs can flexibly evolve and have robust controls to support cybersecurity, cyber resilience, and data protection.
- 2.8Management and Monitoring: Institutions should establish an approved and documented API monitoring framework that addresses infrastructure, technology and security-related incidents and events in a timely and effective manner.
- 2.9Outsourcing: Where an Institution outsources API development to an Outsourcing Service Provider, the Institution must follow the outsourcing requirements of the relevant Supervisory Authority. Institutions should ensure that the contract governing the arrangement between the Institution and Outsourcing Service Provider contains at a minimum information on the roles and obligations of all parties, liability, dispute management, access to relevant information by the relevant Supervisory Authority, and minimum control measures to be employed by the OSP that are acceptable to the Institution.
- 2.10Business Continuity: Institutions should sufficiently cover APIs and the related security controls in their business continuity plans. Institutions should also assess the criticality of different types of APIs being used and ensure that the business continuity planning scenarios reflects them.
Article (7) Aggregate Capital Funds
- An Open Finance Provider must hold, at all times, aggregate capital funds that do not fall below the minimum capital requirements set in Article 6 of this Regulation.
- The minimum capital held as aggregate capital funds must be the higher of the figure stated in Article 6 of this Regulation and the Central Bank’s estimate of the wind down costs for the Open Finance Provider.
- The Central Bank may at its sole discretion impose aggregate capital funds requirements higher than the requirements referred to in Article 7(1) of this Regulation, if, taking into consideration the risk, scale and complexity of the Open Finance Provider’s business, it considers such higher requirements are necessary for ensuring that the Open Finance Provider has the ability to fulfil its obligations under this Regulation.
- An Open Finance Provider must hold, at all times, aggregate capital funds that do not fall below the minimum capital requirements set in Article 6 of this Regulation.
Cloud Computing
- 2.11Material Arrangements: Institutions should assess the materiality and the associated risks of their Cloud Computing arrangements and address any concerns and expectations that the relevant Supervisory Authority may have prior to implementing any material Cloud Computing arrangement.
- 2.12Governance: Institutions should establish an approved and documented governance framework for effective decision-making and proper management and control of risks arising from the use of Cloud Computing and Outsourcing to Outsourcing Service Providers.
- 2.13Auditability: Institutions should ensure that the Cloud Computing arrangement is auditable by maintaining appropriate evidence and records to enable the Institution’s internal control functions, external auditors, regulators, and other authorities to conduct their audits and reviews.
- 2.14Outsourcing: Institutions should establish an approved and documented governance framework for Outsourcing their Cloud Computing arrangements to appropriately select and monitor vendors as well as mitigate risks arising from Cloud Computing Outsourcing arrangements.
- 2.15Design: Institutions should implement adequate measures that are commensurate with the materiality of the arrangement to ensure that Cloud Computing arrangements are resilient, secure, recoverable, and meet the capacity and other needs of the Institution.
- 2.16Management and Monitoring: Institutions should regularly monitor their Cloud Computing arrangements, to evaluate performance, detect technology and security related incidents, and promptly take any remedial action.
- 2.17Data Protection: Institutions should ensure that the use, transmission and storage of Data in a Cloud Computing arrangement complies with applicable laws and regulations and is secured from unauthorised access, use or modification to the extent commensurate with the importance of the Data.
- 2.18Business Continuity: Institutions should put in place a robust and regularly tested business continuity plan for each material Cloud Computing arrangement and ensure that the plan complies with the relevant Supervisory Authority’s requirements.
- 2.19Exit and Resolution Planning: Institutions should define and maintain specific exit plans for their material outsourced Cloud Computing arrangements and account for these arrangements when developing recovery and resolution plans.
Article (8) Capital Instruments
An Open Finance Provider’s aggregate capital funds consist of:
1.1. paid-up capital;
1.2. reserves, excluding revaluation reserves; and
1.3. retained earnings.
- An Open Finance Provider’s aggregate capital funds cannot be met by any capital held within their entity which is otherwise allocated as any other regulatory capital for Licensed Financial Activities.
The following items must be deducted from the aggregate capital funds:
3.1 accumulated losses;
3.2 goodwill; and
3.3 any other items as determined by the Central Bank.
Biometrics
- 2.20Governance: Institutions should establish an approved and documented governance framework to control and manage the broad range of risks which may arise from the use of Biometrics.
- 2.21Identity Proofing and Enrolment Management: Institutions should establish appropriate identity verification and proofing mechanisms as part of the Biometrics Application’s identity enrolment process.
- 2.22Ongoing Authentication: Institutions should establish controls and processes to protect the customers and their credentials against vulnerabilities and unauthorised access, disclosure or use in the authentication process and throughout the Identity Lifecycle.
- 2.23Management and Monitoring: Institutions should regularly monitor their Biometrics Applications throughout the Identity Lifecycle to evaluate performance, detect security-related events, ensure the adequacy of controls, and promptly take any remedial action.
- 2.24Data Management: Institutions should ensure the security, confidentiality, authenticity, and integrity of Data throughout all phases of authentication and whether the Data is in use, storage, or transmission.
Article (9) Professional Indemnity Insurance
An Open Finance Provider must hold professional indemnity insurance of an amount and scope suitable and proportionate to the risks arising from the Open Finance Service it provides, as determined by the Central Bank on a case-by-case basis. Subject to this, the minimum limits of indemnity per year are:
1.1. for a single claim, five million Dirham (AED 5,000,000); and
1.2. in aggregate the higher of five million Dirham (AED 5,000,000) or an amount equivalent to 50% of annual income from the Open Finance Provider’s Open Finance Services.
The Central Bank may determine that an Open Finance Provider must hold minimum limits of indemnity in excess of these amounts.
- The professional indemnity insurance must at a minimum cover liabilities of the Open Finance Provider and its employees in respect of, inter alia, Unauthorized Transactions, data loss and breaches, cyber security risks and delayed or incorrectly Initiated Transactions.
Big Data Analytics and Artificial Intelligence (AI)
- 2.25Governance: Institutions should establish an approved and documented governance framework for effective decision-making and proper management and control of risks arising from the use of Big Data Analytics and AI.
- 2.26Accountability: The Governing Body and Senior Management of the Institution should remain accountable for the outcomes and decisions of their Big Data Analytics and AI Applications including those Applications that make decisions on behalf of the Institutions.
- 2.27Design: Institutions should ensure that the models for their material Big Data Analytics and AI Applications are reliable, transparent, and explainable, commensurate with the materiality of those Applications.
- 2.28Management and Monitoring: Institutions should establish an approved and documented framework to review the reliability, fairness, accuracy and relevance of the algorithms, models and Data used prior to deployment of a material Big Data Analytics and AI Application and on a periodic basis after deployment, to verify that the models are behaving as designed and intended.
- 2.29Ethics: Institutions should ensure that their Big Data Analytics and AI Applications promote fair treatment, produce objective, consistent, ethical, and fair outcomes and are aligned with the Institutions’ ethical standards, values and codes of conduct.
- 2.30Customer protection: Institutions should be transparent with Customers about their use of Big Data Analytics and AI through their conduct and through accurate, understandable, and accessible plain language disclosure.
Article (10) Control of Controllers
- A Person must not become a Controller of an Open Finance Provider without obtaining prior authorisation from the Central Bank.
The Central Bank may grant authorisation under Article 10(1) of this Regulation if it considers that:
2.1 having regard to the likely influence of the Controller, the Open Finance Provider will remain compliant with the requirements of this Regulation and any other relevant Regulations, including Regulations issued in accordance with this Regulation and any relevant law; and
2.2 the Controller meets the fit and proper and suitability requirements specified by the Central Bank.
The approval under Article 10(2) of this Regulation may be granted subject to any conditions that the Central Bank may impose on the Person, including, but not limited to:
3.1 conditions restricting the Person’s disposal or further acquisition of shares and/or voting powers in the Open Finance Provider; and
3.2 conditions restricting the Person’s exercise of voting power in the Open Finance Provider.
- A Person must not become a Controller of an Open Finance Provider without obtaining prior authorisation from the Central Bank.
Distributed Ledger Technology (DLT)
- 2.31Governance: Institutions should establish an approved and documented governance framework for effective decision-making and proper management and control of the risks arising from the use of DLT.
- 2.32Auditability: Institutions should ensure that the DLT Application is auditable by maintaining appropriate evidence and records to enable the Institution’s internal control functions, external auditors, regulators, and other authorities to conduct their audits and reviews.
- 2.33Design: Institutions should design their DLT Applications to be efficient and effectively secure IT Assets and any Customer assets.
- 2.34Anonymity and Pseudonymity: Institutions developing Permissionless DLT Applications should ensure that users are not anonymous or pseudonymous.
- 2.35Management and Monitoring: Institutions should ensure that their DLT Application are reviewed and monitored on a periodic basis to evaluate performance, detect technology and security related incidents, ensure the adequacy of controls, and promptly take any remedial action.
- 2.36Business Continuity: Institutions should establish an effective business continuity plan to ensure and periodically test arrangements to maintain the continuity of the service/process performed by the DLT Application in the event of an incident that adversely affects the availability of the Application.
Article (11) Corporate Governance
- Open Finance Providers must have and maintain effective, robust and well-documented corporate governance arrangements, including a clear organisational structure with well-defined, transparent and consistent lines of responsibility.
The corporate governance arrangements referred to in Article 11(1) of this Regulation must be comprehensive and proportionate to the nature, scale and complexity of the Open Finance Provider’s business, and must contain, at a minimum:
2.1 a Board approved organisation structure which records in writing each division, department or unit, indicating the name of each responsible individual accompanied by a description of the respective function and responsibilities;
2.2 controls on conflicts of interest;
2.3 controls on integrity and transparency of the Open Finance Provider’s operations;
2.4 controls to ensure compliance with applicable laws and Regulations;
2.5 methods for maintaining confidentiality of information and complying with data privacy requirements; and
2.6 procedures for regular monitoring and auditing of all corporate governance arrangements.
The Senior Management of an Open Finance Provider must fulfil fit and proper and suitability requirements specified by the Central Bank from time to time, including that each member of Senior Management:
3.1 is competent and possesses the necessary knowledge, skills, qualifications and experience;
3.2 has a record of acting honestly, ethically, with integrity and is of good repute;
3.3 has a good record of financial conduct;
3.4 is able to make his/her own decisions in a reasoned, objective and independent manner; and does not have any conflict of interest that could affect their conduct;
3.5 has sufficient time to devote to fully performing his/her duties/responsibilities under this Regulation;
3.6 contributes to the collective suitability of the Senior Management; and
3.7 meets any additional requirements specified in applicable Regulations.
- Open Finance Providers must have and maintain effective, robust and well-documented corporate governance arrangements, including a clear organisational structure with well-defined, transparent and consistent lines of responsibility.
Article (12) Risk Management, Compliance and Internal Audit
- Open Finance Providers must establish a framework with appropriate mitigation measures and control mechanisms to manage the operational, security and other risks to which they are or might become, exposed.
The framework established under Article 12(1) of this Regulation must be proportionate to the nature, scale and complexity of the Open Finance Provider’s business, and must contain, at a minimum:
2.1 incident management procedures, including for the detection and classification of major operational and security incidents;
2.2 business continuity and disaster recovery plans, which include: (i) an adequate business continuity management programme to ensure continuation, timely recovery, or in extreme situations, orderly scale-down of critical operations in the event of major disruptions. The programme must comprise business impact analysis, recovery strategies, a business continuity plan and alternative sites for business and information technology recovery; and (ii) appropriate software development life cycle practices to ensure operational resilience and minimise application failures that may pose risks to users; and
2.3 sound administrative and accounting procedures.
- Open Finance Providers must establish a risk management function, an internal audit function and a compliance function and ensure that they are adequately resourced.
- Open Finance Providers must establish and maintain on an ongoing basis a wind down plan that is acceptable to the Central Bank.
- The risk management function must be independent, permanent, have a reporting line directly to the Board and effectively monitor, report on and mitigate the operational, market, credit, legal and other risks to which the Open Finance Provider is exposed.
- The compliance function must be independent, permanent, have a reporting line directly to the Board and must monitor and report on observance of all applicable laws, regulations and standards and on adherence by staff and Senior Management to legal requirements, proper code of conduct and the requirements of this Regulation and other Regulations, where applicable.
- The internal audit function must be independent, permanent, report directly to the Board, employ best practice in internal audit, and be effective. It must provide independent assurance to Senior Management on the quality of the Open Finance Provider’s internal controls, risk management, compliance, systems, and controls.
- Open Finance Providers must not Outsource any material activity, including to any related party without the prior receipt of notification of non-objection from the Central Bank. Open Finance Providers will retain full responsibility for the services provided by any Outsourced service provider. Although all requests for non-objection will be considered on their individual merits, the Central Bank will, in general, not permit the Outsourcing of core activities, and key management and control functions.
- Regulatory requirements for specific functions including risk management, internal audit and compliance, may be established in separate Regulations.
- Open Finance Providers must establish a framework with appropriate mitigation measures and control mechanisms to manage the operational, security and other risks to which they are or might become, exposed.
Article (13) Record Keeping
Open Finance Providers must maintain records relating to the provision of their Open Finance Services, which must at a minimum include records of the following matters:
1.1. User consent to access User Data and/or Initiate Transactions as required under Article 22 of this Regulation;
1.2. Evidence of all User Data provided to the Open Finance Provider by Licensees who are Data Holders on behalf of Users;
1.3. All Transactions Initiated by the Open Finance Provider on the instruction of Users; and
1.4. Evidence of all User Data related to a Transaction which was destroyed or otherwise disposed of.
- All records maintained pursuant to Article 13 of this Regulation must be kept securely, in a durable medium and must be capable of being made available to the Central Bank promptly upon request.
- Open Finance Providers must retain the records referred to in Article 13 of this Regulation for a period of at least five (5) years from the date of creation of such records, unless otherwise required by applicable laws or the Central Bank.
Article (14) Notification and Reporting Requirements
- An Open Finance Provider must be open and cooperative with the Central Bank and notify the Central Bank of all matters that the Central Bank might reasonably require notice of, including to support the performance of the Central Bank’s supervisory functions.
- An Open Finance Provider must comply with all regulatory reporting requirements, including ongoing requirements specified by the Central Bank from time to time.
- Where any material change affects the accuracy and completeness of information provided in an Application, the Applicant or Open Finance Provider, as the case may be, must immediately notify the Central Bank of such change and provide all necessary information and documents.
- An Open Finance Provider must immediately notify the Central Bank of any violation or potential violation of a material requirement under this Regulation or other applicable legal or regulatory requirement.
An Open Finance Provider must immediately notify the Central Bank if it becomes aware that any of the following events have occurred or are likely to occur:
5.1 if a Data Holder or Service Owner unjustifiably refuses access to an Account or Product and/or information relating to them;
5.2 any event that prevents access to or disrupts the operational or security status of the Open Finance Provider;
5.3 any legal action taken against the Open Finance Provider or any member of its Senior Management or director of the Board either in the State or outside the State;
5.4 the commencement against the Open Finance Provider or any member of its Senior Management or director of the Board of any insolvency, winding up, liquidation or equivalent proceedings, or the appointment of any receiver, administrator or provisional liquidator in any jurisdiction;
5.5 any disciplinary measure or sanction taken against the Open Finance Provider or any member of its Senior Management or director of the Board or any measure or sanction imposed on any of them by a body other than the Central Bank, whether in the State or outside the State;
5.6 any material change in regulatory requirements to which the Open Finance Provider is subject beyond those of the Central Bank, whether in the State or outside the State; or
5.7 any other event specified by the Central Bank.
- An Open Finance Provider must be open and cooperative with the Central Bank and notify the Central Bank of all matters that the Central Bank might reasonably require notice of, including to support the performance of the Central Bank’s supervisory functions.
Section 3: Guidelines for Adopting Enabling Technologies
Requirements Relating to the Sharing of Data and Initiation of Transactions
Application Programming Interfaces (APIs)
Article (15) Obligations of licensees
Licensees who are Data Holders and Service Owners must:
1.1. establish and maintain a dedicated interface to provide secure on-line access to Accounts and Products by Open Finance Providers through the API Hub and other relevant components of the Open Finance Framework;
1.2. within fourteen (14) days of receipt of approval from the Central Bank to perform Open Finance Services, register and maintain their registration as a participant under the Trust Framework; and
1.3. co-operate openly and in a timely manner, as specified in this Regulation and any accompanying Regulations, with an Open Finance Provider with regard to the sharing of User Data of the Users who are customers of the Licensee and/or the initiation of Transactions, subject to the User’s consent. A Licensee must not share any User Data in its possession where that User is not a customer of the Licensee, or where the Licensee receives the User Data from a Service Owner.
- No Person shall engage in data scraping, or any other similar data extraction activity, whether or not in conjunction with automated data entry, in order to undertake any activities subject to this Regulation except as permitted under applicable laws. No Person shall engage in the interception of digital connections, including but not limited to the application programming interface, between the public interfaces and other systems of a Licensee’s online or mobile applications by way of reverse engineering or any other similar activity, except as permitted under applicable State laws.
Governance
- 3.1Institutions should establish a documented governance framework for effective decision-making and proper management and control of risks arising from the use of APIs. The governance framework should:
- a.Define the roles and responsibilities of the Institution, API Provider and API developer (where different), including the division of duties;
- b.Establish appropriate policies, procedures, standards and controls to govern the API Lifecycle within the Institution;
- c.Employ tools and technologies that enable communication, change management and performance monitoring across the API Lifecycle;
- d.Establish appropriate testing strategies prior to publication and on an ongoing basis for optimal performance of APIs, for example:
- i.A load testing strategy which can be used to assess how the API performs against service-level agreements and to determine what response is normal for the API. Target API test case problems that would prevent longer load tests from running correctly should be developed;
- ii.Stress testing of the APIs that can be undertaken by simulating a heavy load on the API or by conducting crash point testing to identify the maximum number of users the API can handle; and
- iii.A monitoring framework that can ensure critical interfaces and functions to be appropriately tested and verified for conformance to expected behavior;
- e.Establish a framework to assess, monitor, report and mitigate risks associated with the APIs including developing mechanisms to ensure regular testing and implementation of coding controls, production monitoring and support post deployment, process control mapping and development of a risk control matrix; and
- f.Be approved by the appropriate Governing Body.
- 3.2When Outsourcing to an Outsourcing Service Provider, Institutions should ensure that access to information is adequately controlled, monitored, reviewed and audited by the Institution’s internal control functions, and regulators, including the appropriate Supervisory Authority;
- 3.3Business continuity plans of an Institution should cover APIs and the security controls associated with APIs. Institutions should assess criticality of the different types of APIs used and ensure that the business continuity planning scenarios cover the various types of APIs being used. The business continuity strategy and arrangements should be updated when changes are made to the operating environment, and most importantly, be tested periodically.
- 3.1Institutions should establish a documented governance framework for effective decision-making and proper management and control of risks arising from the use of APIs. The governance framework should:
Architecture
- 3.4Institutions should ensure that the systems and technology architecture for the APIs are designed such that the APIs can flexibly evolve. This could be done by making the architecture independent from the applications using the APIs (i.e. such that it is not over tailored to the most common use cases). The evolution of APIs should not hinder existing applications, which should be able to function without interruption.
- 3.5Institutions should establish controls so that the architecture supporting the API and the API itself is secure and protected against misuse or security attacks.
Design
- 3.6When determining the design of an API, Institutions may consider the following elements to deliver innovation and flexibility:
- a.Accessibility: Ensure all relevant parties can access the API;
- b.Interoperability: Enable exchange of Data across Institutions without any dependencies on underlying technologies;
- c.Reuse: Leverage existing standards and taxonomies to avoid duplication of effort;
- d.Independence: Avoid dependency on any vendors or technologies and retain various options for delivery models and implementation technologies;
- e.Extensibility: Establish flexibility to extend APIs to new stakeholders and business channels and offer new functionality in existing APIs;
- f.Stability: Ensure consistency in functionality and accessibility when modifying the API through appropriate governance;
- g.Privacy by design: All APIs should be designed in a way to only expose relevant Data elements to any party in order to fulfil the purpose of the API;
- h.Transparency: Promote transparency and clarity on the API, including environments supported, changes implemented, and standards followed; and
- i.Loosely coupled: Provide flexibility and minimise impact of changes to operations of other APIs or API applications.
- 3.7Institutions should have proper engagement with API Providers before API Providers can expose any Personal Data through the APIs. This engagement should cover the onboarding of and due diligence processes on the API Provider.
- 3.8Institutions should undertake the following steps when designing APIs:
- a.Decide on in-house vs outsourced API development;
- b.Prioritise and sequence APIs to publish;
- c.Consider guiding principles such as openness, usability and interoperability;
- d.Ensure that adequate security and Data protection mechanisms are in place to protect Personal Data; and
- e.Identify and define requirements and technical guidelines.
- 3.9During the development of APIs, Institutions and API Providers should ensure that they:
- a.Adopt the appropriate API design model based on the type of the API and the protocol used;
- b.Develop requirements and technical specification that define the output to be achieved by the APIs and how the APIs should perform their expected functionality from a technical perspective; and
- c.Document these requirements and technical specifications so that the behavior of the API is well understood and can be measured against expected behavior.
- 3.10Institutions should ensure that Personal Data being transmitted or stored is encrypted to enable privacy and integrity of Data. Institutions can consider utilizing secure public/private key based encryption methods and protocols, which should comply with internationally recognised and applicable security standards.
- 3.11Institutions should ensure that access management and authentication processes are used so that only authorised and authenticated individuals and organisations have controlled access to the appropriate API resources.
- 3.12Institutions should ensure that authentication mechanisms are implemented effectively and securely, preventing attackers from compromising authentication tokens, or exploiting implementation flaws to assume other user identities temporarily or permanently.
- 3.13Institutions should develop an appropriate infrastructure to manage and securely store access credentials.
- 3.14Institutions should use Multi-Factor Authentication when a Customer initially accesses an online service that uses APIs, to provide secure access to the account.
- 3.15Institutions should consider using Multi-Factor Authentication when a customer uses an API to access, process or transmit Personal Data. Multi-Factor Authentication may also be considered for the initiation or processing of transactions.
- 3.16Institutions should ensure that they create clear access control policies that separate administrators and regular users and that accurately reflect the hierarchies, groups, and roles within the organisation. Institutions should review their internal hierarchies, groups, and roles to ensure that there are no gaps in the roles that could lead to unauthorized access to the APIs.
- 3.17Institutions should ensure that APIs are designed to impose restrictions on the size or number of resources that can be requested by the user to prevent Denial of Service (DoS) attacks.
- 3.18An independent function or external expert with adequate skills and knowledge should conduct vulnerability assessments and penetration tests on the Institution’s and the API Provider’s systems and infrastructure to identify weaknesses or flaws in the security processes at least on an annual basis.
- 3.6When determining the design of an API, Institutions may consider the following elements to deliver innovation and flexibility:
Standardisation
- 3.19Institutions should consider the adoption of standardised APIs that are issued either by Supervisory Authorities or the industry. Standardised APIs can, among other matters, include the following:
- a.API design standards: Adopting a uniform API design model and language across the relevant financial services industry based on a broad range of design considerations;
- b.Data standards: Adopting international Data standards that define the semantics and syntax of Data being transmitted using APIs, based on the type of Data being transacted and the use case, to promote interoperability; and
- c.Information security standards: Adopting international information security standards to ensure information is securely transmitted through APIs.
- 3.19Institutions should consider the adoption of standardised APIs that are issued either by Supervisory Authorities or the industry. Standardised APIs can, among other matters, include the following:
Management
- 3.20Institutions should consider establishing an API monitoring framework that addresses infrastructure, technology and security related incidents and events in a timely and effective manner. The monitoring framework should:
- a.Define what constitutes an incident/event, such as unusual activity or unauthorised changes;
- b.Monitor the use of APIs to rapidly and accurately detect incidents and events;
- c.Report incidents and events to decision makers in a timely manner commensurate with their severity; and
- d.Remediate the impact of the incidents and events in an effective manner.
- 3.21Larger Institutions with important API adoption should consider establishing a security operations centre dedicated to monitoring, assessing and defending IT systems and assets such as APIs, web sites, applications, Data servers, networks, hardware and software.
- 3.22Institutions should maintain an audit trail that records the appropriate metrics and security-related behavior of each API and records any breaches of security that occur. The audit trail should capture the metrics and behavior before and after such breaches to support future detection of breaches of security.
- 3.23Institutions should establish incident handling procedures to swiftly detect, review, report and rectify any incidents. Institutions should only provide the necessary details of any incident when reporting incidents to the public to avoid providing attack vectors for bad actors.
- 3.20Institutions should consider establishing an API monitoring framework that addresses infrastructure, technology and security related incidents and events in a timely and effective manner. The monitoring framework should:
Cloud Computing
Article (16) Obligations relating to Data Sharing
- The Data Sharing obligations under Article 16 of this Regulation apply only in relation to User Data.
- Subject to provision of the User’s consent in accordance with Article 22 of this Regulation, where a User uses Data Sharing provided by a Data Service Provider to consolidate information relating to the User Data of that User, the Data Holder must:
2.1 communicate the information relating to the User Data in accordance with the request received;
2.2 treat a request for information relating to the User Data in the same way as a request solely received directly from the User; and
2.3 communicate securely with the Data Sharing Provider in accordance with this Regulation and other applicable Regulations and requirements of the Open Finance Framework.
- A Data Sharing Provider must:
3.1 only provide Data Sharing in accordance with the User's explicit consent and instructions;
3.2 not Process any User Data that is Sensitive Data for the provision of Data Sharing, even with the explicit consent of the User;
3.3 ensure that the User's personalised security credentials, such as Personal Identification Numbers (PIN) and/or passwords, are:
3.3.1 not accessible to other parties, with the exception of the issuer of the credentials; and
3.3.2 transmitted through secure and efficient channels.
- The Data Sharing Provider must identify itself to and communicate securely with the Data Holder and the User.
- The Data Sharing Provider must not use, access or store any information for any purpose except for the provision of the Data Sharing services explicitly requested by the User, except where necessary to comply with any applicable law of the State.
- The Data Sharing obligations under Article 16 of this Regulation apply only in relation to User Data.
Materiality
- 3.24A Cloud Computing arrangement is considered material when a disruption in service or breach of security or confidentiality of systems and/or Data may have the potential to materially impact:
- a.The Institution’s business operations;
- b.The Institution’s ability to manage risks;
- c.The Institution’s ability to comply with applicable laws and regulations; or
- d.The confidentiality or integrity of an Institution’s or Customer’s Personal Data (i.e. if the arrangement may lead to unauthorized access, disclosure, loss or theft of Personal Data).
- 3.25Institutions should conduct an assessment to determine the materiality and the associated risks of a Cloud Computing arrangement. When conducting such an assessment, Institutions should consider:
- a.The criticality and inherent risk profile of the Cloud Computing arrangement i.e. activities that are critical to the business continuity/viability of the Institution and its obligations to Customers;
- b.The impact and likelihood of a service failure, security breach or other event on an Institution’s business operations or reputation;
- c.The impact and likelihood of a confidentiality breach, loss or theft of Customer Data or breach of Data integrity of the Institution and its Customers; and
- d.The cost and other resources to support a Cloud Computing arrangement.
- 3.26Institutions should engage the relevant Supervisory Authority of any material Cloud Computing plans in order to address any concerns and expectations early in the design process before implementing any material Cloud Computing arrangement. This approach must comply with existing outsourcing requirements set by the relevant Supervisory Authority, including, where appropriate, the need to seek approval for material Cloud Computing plans.
- 3.24A Cloud Computing arrangement is considered material when a disruption in service or breach of security or confidentiality of systems and/or Data may have the potential to materially impact:
Governance
- 3.27Institutions considering the use of Cloud Computing should define a clear strategy and architectural roadmap which covers the target IT environment, the transition from the current environment to the target and the operating model, including any organisational change or additional skillsets that maybe necessary.
- 3.28Institutions should establish an approved and documented governance framework for effective decision-making and proper management and control of risks arising from the use of Cloud Computing and Outsourcing of Cloud Computing to Outsourcing Service Providers. The governance framework should:
- a.Define the roles and responsibilities for the operation and management of the Cloud Computing arrangement, security controls and risk management controls. Where an Outsourcing Service Provider is involved, the division of roles and responsibility between the Institution and the Outsourcing Service Provider should be clearly defined;
- b.Define the process to conduct a risk-based analysis to identify and classify the IT Assets involved in or deployed by the Cloud Computing arrangement based on criticality and confidentiality;
- c.Require the maintenance and updating of the log of IT Assets in the cloud environment including their ownership;
- d.Establish appropriate policies, procedures, and controls to govern the use of Cloud Computing covering risk management, due diligence on the Outsourcing Service Providers and access, confidentiality, integrity, and recoverability of IT Assets outsourced; and
- e.Set out the steps for management and review of the contract between the Institution and the Outsourcing Service Provider, where Cloud Computing services are outsourced.
- 3.29Senior Management of the Institution should be responsible for the assessment, understanding and monitoring of the Institution’s reliance on Outsourcing Service Providers for material Cloud Computing services.
- 3.30Institutions should maintain up-to-date and accurate documentation pertaining to the Cloud Computing arrangement for review, audit, supervision, and other purposes, including but not limited to:
- a.Rationale and an appropriate strategy for implementing the Cloud Computing arrangement;
- b.Materiality and risk assessment and conclusion;
- c.Outsourcing risk assessment, other initial security-related risk assessments and their conclusions (further guidance on assessments provided in subsection “Outsourcing”);
- d.Due diligence or suitability assessments conducted on the Outsourcing Service Provider and conclusions;
- e.Description of the Cloud Computing arrangement including but not limited to:
- i.Name of Outsourcing Service Provider and any sub-contractors;
- ii.Level of reliance on Outsourcing Service Providers;
- iii.Type of Cloud Computing service models (i.e. Software as a service - SaaS, Infrastructure as a service - IaaS etc.) and deployment models used (i.e. private, public etc.);
- iv.IT Assets in scope including their criticality and ownership;
- v.Services/products selected;
- vi.Parties involved; and
- vii.Delivery locations.
- f.Contract and other legal documentation pertaining to the arrangement with the Outsourcing Service Provider (further guidance provided in subsection “Outsourcing”).
Outsourcing
- 3.31Prior to engaging an Outsourcing Service Provider to provide Cloud Computing services, Institutions should perform a comprehensive Outsourcing risk assessment covering:
- a.The role and materiality of the service to be outsourced in the Institution’s business operations;
- b.Due diligence on prospective Outsourcing Service Providers (further guidance on the due diligence process provided in Clause Institutions should verify the maturity, adequacy and appropriateness of the prospective Outsourcing Service Provider and services selected, taking into account the intended usage of the Cloud Computing service. Institutions should consider the following specific factors when conducting due diligence on Outsourcing Service Providers providing Cloud Computing services, including but not limited to:); and
- c.Assessing the benefits of the Outsourcing arrangement against the risks.
- 3.32Institutions should verify the maturity, adequacy and appropriateness of the prospective Outsourcing Service Provider and services selected, taking into account the intended usage of the Cloud Computing service. Institutions should consider the following specific factors when conducting due diligence on Outsourcing Service Providers providing Cloud Computing services, including but not limited to:
- a.Materiality: The results of the materiality assessment. The depth of the due diligence undertaken and risk mitigating controls established should be commensurate with the materiality of the Cloud Computing arrangement and the level of reliance the Institution places on the provider to maintain effective security controls;
- b.Due diligence scope: The scope of the due diligence assessment should be appropriate and cover an adequate set of controls and individual assessments of all locations expected to be relevant in the arrangement. In particular, the Institution should consider the track record of the Outsourcing Service Provider in achieving acceptable outcomes in areas such as information security policies and awareness, due diligence and risk assessment of practices related to sub-contracting, system vulnerability assessments, penetration testing, and technology refresh management;
- c.Data centers: Evaluation of whether the data centers are located in countries that the Institution deems suitable and acceptable to store and process Data (further guidance outlined in the subsection “Design”);
- d.Controls: Institutions should ensure that Outsourcing Service Providers implement strong authentication, access controls, Data encryption and other security and technical controls (further guidance outlined in the subsections “Design” and “Management and monitoring”) to meet the Institutions’ requirements. Controls implemented by Outsourcing Service Providers should be at least as strong as those which the Institutions would have implemented had the operations been performed in-house;
- e.Security risk assessments: Prior to implementing Cloud Computing services and undertaking an Outsourcing arrangement, Institutions should conduct an initial security and risk assessment of the service to identify any information security, cybersecurity and other IT control weaknesses. The risk assessment will identify security threats including information security threats and operational weaknesses and develop safeguards to mitigate those threats and weaknesses. The factors considered during the risk assessment should include but not be limited to:
- i.Nature of the service (including specific underlying arrangements);
- ii.Provider and the location of the service;
- iii.Criticality and confidentiality of the IT Assets involved;
- iv.Transition process including handover from the Institution and/or other service providers to the potential Outsourcing Service Provider;
- v.Target operating model; and
- vi.Adherence to recognised technical security standards.
- vii.Compliance with standards and external assurance: The Outsourcing Service Provider’s adherence to international standards as relevant to the provision of services (for e.g. ISO/EIC etc.). Institutions may take into consideration any external assurance that has already been provided by independent auditors when conducting their own due diligence.
- 3.33When conducting risk assessments of Cloud Computing services, Institutions should consider key risks including but not limited to:
- a.Cybersecurity risk;
- b.Operational risks, specifically information security, Outsourcing and business continuity risk. In particular, Institutions in an outsourced Cloud Computing arrangement should consider the impact of the Outsourcing arrangement on the Institution’s risk profile i.e. the potential heightened operational, legal, compliance, reputational, concentration and other risks associated with the arrangement;
- c.Reputational risk; and
- d.Specific risks arising from the design and operating model of the Cloud Computing arrangement.
- 3.34Institutions should ensure that the written contract governing the Cloud Computing arrangement between the Institution and Outsourcing Service Provider covers the following issues including, but not limited to:
- a.The roles, relationships, obligations and responsibilities of all contracting parties;
- b.Location of the data centres;
- c.Ownership and control over IT Assets, if the Outsourcing Service Provider is expected to be given some level of control over IT Assets;
- d.Liability in the event of losses or breaches in security or confidentiality;
- e.Measures to protect the Institution’s Data and confidential information and limits to disclosure of such information;
- f.Data recovery and access to Data used for daily operational purposes as well as for contingency, disaster recovery or backups;
- g.Advance notice to the Institutions regarding any changes to data centre locations;
- h.Access to information held by the Institution;
- i.The right to monitor, review and audit Cloud Computing arrangements by the Institution’s internal control functions, and regulators, or persons employed by them, including for the purposes of supervisory reviews by the respective Supervisory Authority;
- j.With respect to Outsourcing Service Providers use of sub-contracting arrangements:
- i.Disclosure of all material and service-related sub-contracting arrangements;
- ii.Advance notification of any new sub-contracting arrangements or changes to existing arrangements by the Outsourcing Service Provider;
- iii.Outsourcing Service Provider’s accountability to the Institution for the provision of service and effectiveness of agreed controls;
- iv.Outsourcing Service Provider’s contractual liability for the performance and risk management of any sub-contractor(s) it employs and, where this is the case, the full compliance of the sub-contractor(s) with the obligations existing between the Institution and Outsourcing Service Provider.
- k.Scenarios or events in which Institutions have the right to terminate the contractual agreement, such as where new or modifications to existing sub-contracting arrangements have an adverse effect on the Institution’s security or risk assessment of the Cloud Computing arrangement; and
- l.The exit plan and process to be followed in the event of termination of the Cloud Computing arrangement including, but not limited to:
- i.A reasonable transition period;
- ii.Procedures for returning Data to the Institution;
- iii.Permanent Data deletion by the Outsourcing Service Provider; and
- iv.Any arrangements to transfer the outsourced service to another Outsourcing Service Provider or reincorporate it into the Institution with sufficient handover and support from the previous Outsourcing Service Provider.
- 3.35Institutions should understand their roles and those of the Outsourcing Service Provider providing Cloud Computing services. Roles and owners should be defined and agreed upon as part of the shared responsibility model which should specifically cover roles with respect to cybersecurity, information security and related controls.
- 3.36Where a material Outsourcing arrangement involves the transfer of Data, Institutions should:
- 3.31Prior to engaging an Outsourcing Service Provider to provide Cloud Computing services, Institutions should perform a comprehensive Outsourcing risk assessment covering:
Design
- 3.37Institutions should ensure that the design and architectural aspects of the Cloud Computing services, or arrangement are optimised to cater to the needs of the Institution, adhere to the Institution’s internal policies and procedures and minimise risks.
- 3.38Institutions and Outsourcing Service Providers should consider the following principles when developing the design and architecture of the Cloud Computing arrangement:
- a.Availability: To reduce the likelihood of IT Assets becoming unavailable in the event of failure of individual components and improve the ability for users to request and use IT Assets;
- b.Resilience: To improve resilience through implementation of security controls, implementation of regular testing and checks to detect security and service issues, and use of multiple data centres distributed across multiple locations, or where appropriate, use of multiple Outsourcing Service Providers to provide Cloud Computing services;
- c.Recoverability: To allow for swift and effective recovery and restoration of IT Assets to a specified level of service in the event of a compromise of integrity or availability;
- d.Capacity: To ensure the Cloud Computing arrangement’s capacity is commensurate with the Institution’s needs; and
- e.Encapsulation: To ensure re-usability of network and system components.
- 3.39Institutions should carefully determine and choose the type of cloud(s) deployed based on an assessment of the business operations performed on the cloud(s) and the risks associated with each type of cloud.
- 3.40Institutions should evaluate and assess the location of data centres while determining the design of the Cloud Computing arrangement to select data centres appropriate to the Institution’s needs. The assessment should address the location’s:
- a.Potential risks, including information security, legal and compliance risks;
- b.Wider political and security issues; and
- c.Legislation and legal framework including law enforcement and insolvency law provisions that would apply in the event of an Outsourcing Service Provider’s failure.
- 3.41Institutions should implement appropriate and effective network access and security controls such as firewalls, Intrusion Prevention System, advanced threat protection and web proxy so that other on-premise environments are not exposed to unauthorized access from the cloud.
- 3.42Institutions should define a standard set of tools and processes to manage containers, images and release management and ensure consideration of any risks posed by shared virtual environments or Data co-mingling.
- 3.43Institutions should implement preventative and detective Data controls to keep Data secure and prevent Data loss. Institutions should ensure that the Data controls including those outlined in this section cover all Data, whether it is Data in storage, Data in transmission (i.e. Data that is actively moving from one location to another) or Data in use.
- 3.44Institutions should ensure that Data processed or stored through the Cloud Computing arrangement are recoverable within a pre-defined timeframe and appropriate and secure backups of Data are maintained.
- 3.45Where the Cloud Computing arrangement is using a multi-tenancy environment or Data comingling arrangement, Institutions should ensure its Data and information is segregated and the Outsourcing Service Provider is able to protect the confidentiality and integrity of the Data and information.
- 3.46Institutions should introduce controls to prevent unauthorised access to Data and permit access to IT Assets only when appropriate.
- 3.47Institutions should establish security controls to protect against attacks (e.g. network intrusion attempts, DoS attacks) including cloud specific attacks.
- 3.48Institutions should introduce cryptographic key management to control access to, segregate and secure Customer’s Data.
- 3.49Institutions should utilise encryption or tokenisation to protect confidentiality of Personal Data, such as authentication credentials and emails etc., being processed, or in transit including Data in Data back-ups.
- 3.50Institutions should introduce user identity and access management and authentication (including Multi-Factor Authentication) to provide controlled access to information systems allowing Staff and Outsourcing Service Providers to perform their business activities, while protecting Data and systems from unauthorised access.
- 3.51Institutions should ensure that user access and activities are logged and reviewed on an “as needed” basis.
- 3.52Institutions should develop controls to ensure confidentiality and integrity of source codes and prevent alteration of source codes and system configurations (particularly when the Institution uses models such as DevOps).
- 3.53Institutions should conduct vulnerability assessments and penetration tests specific to the Cloud Computing arrangement to identify weaknesses or flaws in the security processes.
Management and Monitoring
- 3.54Institutions should establish change management processes to ensure any changes in the Cloud Computing arrangement by the Institution or the Outsourcing Service Provider are appropriately governed and implemented.
- 3.55Institutions should ensure that they define the conditions and scenarios in which automated testing and releases can take place for changes to their Cloud Computing arrangements, and that there is a full audit trail, record of the changes and evidence of pre-approval.
- 3.56Institutions should develop a mechanism by which they are notified of material changes to the Cloud Computing arrangement in a timely manner.
- 3.57Institutions should develop a configuration management process which includes regular monitoring to detect unauthorised changes to the cloud environment and ensure such changes can be appropriately remediated.
- 3.58Institutions should ensure that the Cloud Computing arrangement has the capacity to run the Institution’s workloads. Institutions should regularly monitor utilisation and proactively plan for upgrades or enhancements based on anticipated spikes in workloads or resulting from strategic business initiatives.
- 3.59Institutions should establish a monitoring framework to define, monitor, report and remediate key infrastructure, technology and security related incidents and events in the cloud environment in a timely and effective manner to minimise detriment. The framework should:
- a.Cover incidents and events that may impact the stability or availability of the Institution’s applications, networks and systems or the confidentiality or integrity of cloud environments;
- b.Be centralised to promote clarity of process and enable consolidation and analysis of threat intelligence, incident and event related Data;
- c.Manage incidents and events according to their frequency, criticality and assigned ownership;
- d.Identify, monitor and manage systemic issues;
- e.Monitor and identify vulnerabilities, incidents, and events on an on-going basis by:
- i.Defining a standard set of health and performance metrics;
- ii.Utilising analytics and Data from previous security incidents and events to enable retrospective detection;
- f.Categorise and record Data associated with incidents and events;
- g.Report and escalate incidents and events to relevant stakeholders for notification or action; and
- h.Ensure that incidents and events are properly reviewed and identified gaps are remediated to prevent a reoccurrence.
- 3.60Institutions should be able to swiftly and safely:
- a.Detect vulnerabilities in the software used in the cloud environment; and
- b.Deploy security and operating system patches.
- 3.61After implementation of the Cloud Computing arrangement, Institutions should re-assess the risks associated with the Cloud Computing arrangement when there is a material change to existing arrangements and on a regular basis through ongoing:
- a.Outsourcing risk assessments to assess adequacy of controls in managing the risks arising from the Outsourcing arrangement; and
- b.Security and risk assessments to assess the adequacy of the security and risk controls in managing the risks arising from Cloud Computing. These should include conducting vulnerability assessments and penetration tests specific to the Cloud Computing arrangement on at least an annual basis.
- 3.62Institutions should establish risk mitigation controls to address any shortcomings of the Cloud Computing arrangement. The degree of risk should inform the stringency of controls and mitigation procedures implemented.
Business Continuity
- 3.63Institutions’ business continuity management functions and crisis management teams should develop and implement a business continuity plan for material Cloud Computing arrangements. If Cloud Computing arrangements are outsourced, the Outsourcing Service Provider should have a business continuity plan in place that is acceptable to the Institution.
- 3.64Institutions should define key risk indicators, performance metrics and adverse conditions that can trigger the business continuity plan for the Cloud Computing arrangement during its on-going monitoring and oversight of any services provided by the Outsourcing Service Provider.
- 3.65As part of an Institution’s own business continuity planning for Cloud Computing services, it should tailor the plan to:
- a.Account for any dependency on one Outsourcing Service Provider;
- b.Define the division of roles and responsibilities;
- c.Define recovery objectives;
- d.Identify alternative solutions/develop transition plans; and
- e.Test their business continuity plans for their Cloud Computing arrangement (jointly with the Outsourcing Service Provider if the Cloud Computing arrangement is outsourced) on at least an annual basis.
Exit and Resolution Planning
- 3.66Institutions should consider the possibility of a stressed exit wherein an event of disruption cannot be managed through business continuity measures.
- 3.67Institutions should define and maintain specific exit plans for their outsourced Cloud Computing arrangements, taking into account, developments (such as new technology) that may change the feasibility of an exit in stressed and non-stressed scenarios.
- 3.68Institutions should account for outsourced Cloud Computing arrangements when developing resolution plans or strategies to identify and address any impediments to its resolvability and to prepare for its possible resolution.
- 3.69Institutions should establish procedures for Data recovery by the Institution and permanent Data deletion by the Outsourcing Service Provider in the event of a termination of services.
Biometrics
Article (17) Obligations relating to Service Initiation
1. The obligations under Article 17 of this Regulation relating to Service Initiation apply only in relation to relevant Accounts and Products. 2. Where a User gives explicit consent for a Transaction to be Initiated through a Service Initiation Provider, the Service Owner must: 2.1 communicate securely with the Service Initiation Provider in accordance with the Regulations and requirements of the Open Finance Framework; 2.2 immediately after receipt of the instruction to Initiate a Transaction for the User, provide or make available to the Service Initiation Provider all information required for the initiation of the Transaction, and subsequently display the status of the Transaction to the User, until its completion; and 2.3 treat the instruction to Initiate the Transaction in the same way as an instruction solely received directly from the User. 3. A Service Initiation Provider must: 3.1 only provide Service Initiation in accordance with the User's explicit consent and instructions; 3.2 ensure that the User's personalised security credentials, such as PIN and/or passwords, are: 3.2.1 not accessible to other parties, with the exception of the issuer of the credentials; and 3.2.2 transmitted through secure and efficient channels. 4. Each time it Initiates a Transaction, the Service Initiation Provider must identify itself to the Service Owner and communicate securely with the Service Owner. 5. In providing its services the Service Initiation Provider must not use, access or store any information for any purpose except for the provision of the services explicitly requested by the User, except where necessary to comply with any applicable law of the State. Governance
- 3.70Institutions should ensure compliance with the relevant legislation and regulations in relation to Data protection.
- 3.71When Outsourcing to an Outsourcing Service Provider, Institutions should ensure that access to information is adequately controlled, monitored, reviewed, and audited by the Institution’s internal control functions, and regulators, or persons employed by them, including supervisory reviews by the respective Supervisory Authority.
Identity Proofing and Enrolment Management
- 3.72Institutions using Biometric Applications should ensure effective proofing of identities, including validation and verification of identities. Validation involves determining that the documentary evidence for the Biometric identity is genuine, reliable, and independent. Verification involves confirming the validated identity relates to the individual being proofed.
- 3.73Institutions should obtain and store evidence of any digital identity verification (e.g., via chip or wireless technologies) performed by integrated scanners, sensors and other devices.
Ongoing Authentication and Identity Lifecycle Management
- 3.74Institutions should establish controls and processes to protect Customers and their credentials against vulnerabilities and unauthorized access, disclosure or use in the authentication process and throughout the Identity Lifecycle.
- 3.75Institutions deploying Multi-Factor Authentication at login that includes a Biometric factor should consider employing phishing-resistant authenticators where at least one factor relies on public key encryption to secure the Customer authentication process.
- 3.76Institutions should implement risk-based or adaptive authentication measures that present Customers with authentication options commensurate with the risk level of the transaction and sensitivity of the information.
- 3.77Institutions should implement Multi-Factor Authentication using a Biometric factor, where possible, to authorize high risk activities and protect the integrity of Customer account Data and transaction details. High-risk activities include changes to Personal Data (e.g. Customer office and home address, email and telephone contact details), registration of Third-Party payee details, high value funds transfers and revision of funds transfer limits.
- 3.78For Biometric authentication of transactions, Institutions should adopt security measures to ensure the confidentiality, authenticity and integrity of authentication codes, Personal Data and transaction specific information.
Management and Monitoring
- 3.79Institutions should periodically monitor their Biometric Applications throughout the Identity Lifecycle to assess performance, detect security-related events, evaluate the adequacy of controls, and take any remedial action.
- 3.80Institutions should ensure that all communications with individuals involving Biometric Data across the Identity Lifecycle occur over a mutually authenticated and protected channel.
- 3.81Institutions should ensure the employment of physical tamper detection and resistance features appropriate for the environment in which the identity-proofing session occurs.
- 3.82Across the Identity Lifecycle, Institutions should introduce processes and controls to safeguard against Data tampering, cyberattacks, security breaches and other fraudulent activities which may lead to identity theft, compromise or misuse of Data and errors.
- 3.83Institutions should monitor and evaluate all the processes involved in the Identity Lifecycle including identity proofing, authentication etc. to ensure that they are secure and efficient.
- 3.84As a Credential Service Provider may be an independent Third Party or may issue credentials for its own use, Institutions should ensure that they perform the requisite due diligence checks and protocols on the Credential Service Provider on a regular basis.
- 3.85Institutions should monitor the performance of the Biometrics Application for inherent risks such as false acceptance rates and false rejection rates. Poorly executed algorithms may result in higher false acceptance rates and these inherent risks should be calibrated to be commensurate with the risks associated with the Biometric Application.
Data Management
- 3.86Institutions should ensure the security, confidentiality, authenticity and integrity of Data across all phases of authentication, whether the Data is in use, storage or transmission.
- 3.87Institutions should maintain a clear trail and record of the Biometric Application’s Data obtained from the Credential Service Providers.
- 3.88Institutions should consider the principles of portability and interoperability when planning and implementing systems and databases for the Biometric Application.
- 3.89Where Biometric Applications are used for Biometric authentication, Institutions should ensure Biometric Data and authentication credentials, whether in use, storage or transmission, are encrypted.
Outsourcing
- 3.90If Biometric activities are outsourced, Institutions should ensure that:
- a.They obtain the necessary Data concerning Biometric identification/verification from the Outsourcing Service Providers and take adequate steps to satisfy themselves that copies of identification Data and other relevant documentation will be made available from the Outsourcing Service Providers upon request and without delay; and
- b.The Outsourcing Service Provider complies with the Institution’s Customer due diligence and record-keeping requirements.
- 3.90If Biometric activities are outsourced, Institutions should ensure that:
Big Data Analytics and Artificial Intelligence (AI)
Materiality
- 3.92Institutions should assess their Big Data Analytics and AI Applications to determine the materiality and associated risks of each Application.
- 3.93When conducting a materiality assessment of a Big Data Analytics and AI Application, Institutions should consider:
- a.The purpose of the Big Data Analytics and AI Application (i.e. use case) and its role in the Institution’s decision-making process;
- b.The criticality and inherent risk profile of the activities (i.e. are they activities that are critical to the business continuity/viability of the Institution and its obligations to Customers); and
- c.The likelihood that the activity may be disrupted and the impact of any such disruption.
Governance
- 3.94Institutions should establish an approved and documented governance framework for effective decision-making and proper management and control of risks arising from the use of Big Data Analytics and AI. The governance framework should:
- a.Establish a mechanism to ensure that Institutions are required to assess whether the Application is suitable for Big Data Analytics and AI implementation and define specific parameters and criteria to enable the Institution in its decision-making;
- b.Establish appropriate policies, procedures and controls to govern the design, development, monitoring, review and use of Big Data Analytics and AI Applications within the Institution;
- c.Ensure proper validation of Big Data Analytics and AI Applications prior to their launch, and thereafter implement on-going training, calibration and review to ensure the reliability, fairness, accuracy and relevance of the algorithms, models and Data used and the results;
- d.Maintain a transparent, enterprise-wide record of Big Data Analytics and AI Applications and their underlying mechanics;
- e.Establish processes to assess, monitor, report and mitigate risks associated with the Big Data Analytics and AI Application;
- f.Ensure that material decisions regarding Big Data Analytics and AI Applications and their underlying models and Data are documented and sufficiently justified; and
- g.Cover every stage of the model lifecycle including design, development, deployment, review, update and discontinuation.
- 3.95The Governing Body and Senior Management of the Institution should be accountable for the outcomes and decisions arising from the use of Big Data Analytics and AI Applications, including those Applications that make decisions on behalf of the Institution. They should:
- a.Ensure that all Staff working on or using Big Data Analytics and AI Applications are assigned appropriate accountability for their involvement with Big Data Analytics and AI Applications and understand what they should to do meet this accountability; and
- b.Ensure that technical specialists with appropriate technology skillsets (e.g. Big Data analysts, Artificial Intelligence engineers and specialists) and Application specific skillsets (e.g. credit risk modelling specialists if the Application is a credit scoring model) form part of the team actively involved in developing and implementing Big Data Analytics and AI Applications.
- 3.96When Outsourcing to an Outsourcing Service Provider, Institutions should ensure that access to information is adequately controlled, monitored, reviewed, and audited by the Institution’s internal control functions, and regulators, or persons employed by them, including supervisory reviews by the respective Supervisory Authority.
- 3.97Big Data Analytics and AI Applications, including when the model is developed by an Outsourcing Service Provider, should be auditable and, accordingly, Institutions, where relevant and considering the type of application used, should maintain on-going and up-to-date information through:
- a.Establishing audit logs and maintaining traceability of decisions and outcomes of the Big Data Analytics and AI Application;
- b.Developing and maintaining design documentation (further guidance provided in Clause Institutions should maintain documentation outlining the design of the material Big Data Analytics and AI model including but not limited to, where applicable:);
- c.Maintaining records of the various versions of the model including its code (further guidance provided in Clause Institutions should establish a robust system for versioning and maintain record of each version of the material Big Data Analytics and AI model including but not limited to, where applicable:);
- d.Archiving original Datasets used to develop, re-train or calibrate models;
- e.Tracking outcomes and performance of the Big Data Analytics and AI Application; and
- f.Retaining above information for a minimum period of five (5) years, or as otherwise prescribed by applicable laws and regulations.
- 3.94Institutions should establish an approved and documented governance framework for effective decision-making and proper management and control of risks arising from the use of Big Data Analytics and AI. The governance framework should:
Design
- 3.98Institutions should ensure that the models for their Big Data Analytics and AI Applications are reliable, transparent, and explainable, commensurate with the materiality of those Applications. Accordingly, Institutions, where appropriate, should consider:
- a.Reliability: Implementing measures to ensure material Big Data Analytics and AI Applications are reliable and accurate, behave predictably, and operate within the boundaries of applicable rules and regulations, including any laws on data protection or cyber security;
- b.Transparency: Institutions should be transparent in how they use Big Data Analytics and AI in their business processes, and (where reasonably appropriate) how the Big Data Analytics and AI Applications function; and
- c.Technical Clarity: Implementing measures to ensure the technical processes and decisions of a Big Data Analytics and AI model can be easily interpreted and explained to avoid the threat of “black-box” models. The level of technical clarity should be appropriate and commensurate with the purpose and materiality of the Big Data Analytics and AI Application (e.g. where the model results have significant implications on decision making).
- 3.99Institutions should adopt an effective Data governance framework to ensure that Data used by the material Big Data Analytics and AI model is accurate, complete, consistent, secure, and provided in a timely manner for the Big Data Analytics and AI Application to function as designed. The framework should document the extent to which the Data meets the Institution’s requirements for data quality, gaps in data quality that may exist and steps the Institution will take, where possible, to resolve these gaps over time.
- 3.100Institutions should make regular efforts to ensure data used to train the material Big Data Analytics and AI model is representative (i.e. how relevant the Data and inferences drawn from the Data are to the Big Data Analytics and AI Application) and produces predictable, reliable outcomes that meet objectives.
- 3.101Institutions should be able to promptly suspend material Big Data Analytics and AI Applications upon the Institution’s discretion such as in the event of a high cyber threat, information security breach or malfunctioning of the model.
- 3.102Institutions should, where relevant, conduct rigorous, independent validation and testing of material trained Big Data Analytics and AI models to ensure the accuracy, appropriateness, and reliability of the models prior to deployment. Institutions should ensure the model is reviewed to identify any unintuitive or false causal relationships. The validation may be carried out by an independent function within the Institution or by an external organisation.
- 3.103Institutions should maintain documentation outlining the design of the material Big Data Analytics and AI model including but not limited to, where applicable:
- a.The input Data source and Data description (types and use of Data);
- b.The Data quality checks and Data transformations conducted;
- c.Reasons and justifications for specific model design and development choices;
- d.Methodology or numerical analyses and calculations conducted;
- e.Results and expected outcomes;
- f.Quantitative evaluation and testing metrics used to determine soundness of the model and its results;
- g.Model usage and implementation;
- h.Form and frequency of model validation, monitoring and review; and
- i.Assumptions or limitations of the model with justifications.
- 3.104Institutions should introduce controls to ensure confidentiality and integrity of the codes used in the material Big Data Analytics and AI Application so that the code is only accessed and altered by authorized persons.
- 3.105Institutions should identify and monitor the unique risks arising from use of the material Big Data Analytics and AI Application and establish appropriate controls to mitigate those risks.
- 3.98Institutions should ensure that the models for their Big Data Analytics and AI Applications are reliable, transparent, and explainable, commensurate with the materiality of those Applications. Accordingly, Institutions, where appropriate, should consider:
Management and Monitoring
- 3.106Institutions should establish an approved and documented framework to review the reliability, fairness, accuracy and relevance of the algorithms, models and Data used prior to deployment of a material Big Data Analytics and AI Application and on a periodic basis after deployment, to verify that the models are behaving as designed and intended. The framework should cover, where relevant:
- a.The various types and frequencies of reviews including continuous monitoring, re-training, calibration and validation;
- b)Scenarios and criteria that would trigger a re-training, calibration, re-development or discontinuation of the model such as a significant change in input Data or external/economic changes;
- a.Review of material Big Data Analytics and AI model outcomes for fairness or unintentional bias (e.g. through monitoring and analysis of false positive and/or false negative rates); and
- b.Review of continuity or contingency measures such as human intervention or the use of conventional processes (i.e. that do not use Big Data Analytics and AI).
- 3.107When the use of a material Big Data Analytics and AI model results in a technical or model-related error or failure, Institutions should:
- a.Be able to swiftly detect the error;
- b.Establish a process to review the error and rectify it in a timely manner, which may include notifying another function; and
- c.Report the error to relevant stakeholders if material.
- 3.108Institutions should establish a robust system for versioning and maintain record of each version of the material Big Data Analytics and AI model including but not limited to, where applicable:
- a.New Data used;
- b.Revisions to the documentation;
- c.Revisions to the algorithm;
- d.Change in the way variables are picked and used in the model or, where possible, the names of variables; and
- e.The expected outcome of the newly calibrated, re-trained or re-developed model.
- 3.106Institutions should establish an approved and documented framework to review the reliability, fairness, accuracy and relevance of the algorithms, models and Data used prior to deployment of a material Big Data Analytics and AI Application and on a periodic basis after deployment, to verify that the models are behaving as designed and intended. The framework should cover, where relevant:
Ethics
- 3.109Institutions should ensure that their Big Data Analytics and AI Applications promote fair treatment, produce objective, consistent, ethical, and fair outcomes, and also, are aligned with Institutions’ ethical standards, value and codes of conduct. Accordingly, they should:
- a.Comply with laws against discrimination and other applicable laws;
- b.Be produced using representative inputs and Data which have been tested for selection bias (further guidance provided in Clause 3.100);
- c.Consider whether a human-in-the-loop mechanism is needed to detect and mitigate biases;
- d.Retain the possibility of manual intervention to mitigate or reverse irresponsible and erroneous decisions;
- e.Retain the possibility of modification by the Institution; and
- f.Be explainable.
- 3.110Institutions should consider the fairness of a Big Data Analytics and AI model through understanding the biases and noise affecting Big Data Analytics and AI decisions. Institutions should define what it means for a Big Data Analytics and AI model to be fair.
- 3.111Institutions should consider and assess the impact that Big Data Analytics and AI models may have on individuals or groups of individuals to ensure that such individuals or groups are not systematically disadvantaged unless the decisions suggested by the models have a clearly documented justification. Institutions should take steps to minimize unintentional or undeclared bias.
- 3.109Institutions should ensure that their Big Data Analytics and AI Applications promote fair treatment, produce objective, consistent, ethical, and fair outcomes, and also, are aligned with Institutions’ ethical standards, value and codes of conduct. Accordingly, they should:
Customer Protection
- 3.112Institutions should be transparent with Customers about their use of Big Data Analytics and AI through their conduct and through accurate, understandable, and accessible plain language disclosure. Institutions should:
- a.Ensure that Customers are informed of products and/or services that utilise Big Data Analytics and AI and the associated risks and limitations of the technology, prior to providing the service or each time Customers interact with the service (e.g. in the case of a Customer-facing service);
- b.Explain how to use the Big Data Analytics and AI Application to Customers and ensure Customers always have easy access to the instructions; and
- c.Provide clear explanations of the types of Data, types of variables and decision-making process used by Big Data Analytics and AI Applications upon Customers’ requests. To avoid doubt, clear explanations do not require exposure of Institutions intellectual property, publishing of proprietary source code or details on firms’ internal processes.
- 3.113Institutions should obtain each Customer’s acceptance of the risks associated with the use of Big Data Analytics and AI prior to providing the service.
- 3.114Institutions should put in place a mechanism for Customers to raise inquiries about Big Data Analytics and AI Applications and request reviews of decisions made by Big Data Analytics and AI Applications.
- 3.112Institutions should be transparent with Customers about their use of Big Data Analytics and AI through their conduct and through accurate, understandable, and accessible plain language disclosure. Institutions should:
Distributed Ledger Technology (DLT)
Governance
- 3.115Institutions should establish an approved and documented governance framework for effective decision-making and proper management and control of risks arising from the use of DLT. The governance framework should include the following, as may be relevant depending on the type of DLT:
- a.Cover the following elements integral to the functioning of a DLT Application:
- b.Ownership model of the DLT platform and the Nodes running on it;
- c.The model used to operate and manage the distributed ledger (e.g. a consortium, a single Institution);
- d.Rules to govern the ledger(s) including participant and validator rules and restrictions;
- e.Approval processes and procedures to grant access to create, read, update or deactivate Data stored on the distributed ledger(s);
- f.Managing public and private keys;
- g.Consensus protocol; and
- h.Off-chain procedures (if any) including parameters for the validity of an off-chain activity and any standards or requirements for off-chains systems are defined and complied with.
- i.Define the roles and responsibilities of the key groups involved with respect to the design, development, and operation of the distributed ledger(s). Key groups may include:
- i.Core group who will design, govern and operate the distributed ledger(s);
- ii.Qualified users of the distributed ledger(s), such as other Institutions and miners;
- iii.Participants involved in the distributed ledger(s), such as owners of cryptocurrency etc.; and
- iv.Third Parties including Outsourcing Service Providers such as custodians or software developers involved in delivering the service.
- 3.116Reviews of the DLT Application should be conducted with oversight from Senior Management, prior to launch and thereafter on an on-going basis to ensure its reliability and security.
- 3.117Institutions should establish clear and unambiguous governing rules for participants of the distributed ledger(s) for onboarding, on-going operations and dispute resolution.
- 3.118When Outsourcing to an Outsourcing Service Provider, Institutions should ensure that access to information is adequately controlled, monitored, reviewed, and audited by the Institution’s internal control functions, and regulators, or persons employed by them, including supervisory reviews by the respective Supervisory Authority.
- 3.119Institutions should ensure that their DLT Applications maintain appropriate evidence and records to enable the Institution’s internal control functions, external auditors, regulators, and other authorities to conduct their audits and reviews. Accordingly, Institutions should:
- a.Record and store the additional evidence and information to provide auditors with a complete representation of processes, internal controls, financial statements, etc., and for proper accounting treatment of the transaction;
- b.Ensure that a log of records of the DLT Application is fully available and accessible to the relevant parties to audit and review;
- c.In the event that the DLT is in the form of a blockchain, ensure that off-chain activities, rules and protocols associated with and any link to on-chain activities are recorded and stored; and
- d.Ensure that the DLT code and subsequent updates are recorded and stored.
- 3.115Institutions should establish an approved and documented governance framework for effective decision-making and proper management and control of risks arising from the use of DLT. The governance framework should include the following, as may be relevant depending on the type of DLT:
Design
- 3.120Institutions should design their DLT Applications to be efficient and effectively secure IT assets and any customer assets. Institutions should, where possible, ensure the design and architectural aspects of the DLT are optimised to cater to the specific use of the technology and the needs of the Institution.
- 3.121Institutions should consider the following principles when developing the design of a DLT Application that manages financial assets:
- a.Flexibility: To define the DLT Application narrowly, which is easier to optimise, or flexibly, which may incur higher costs (more difficult protocol, less predictability, larger target for attacks, etc.);
- b.Traceability: To ensure that the distributed log of records and any off-chain records are traceable and anonymity is avoided;
- c.Capacity: To ensure that the DLT Application’s computing and Data capacity is commensurate with the Institution’s needs and is scalable depending on the intended use;
- d.Security: To ensure that the activities and records on the distributed ledger(s) are secure;
- e.Confidentiality: To maintain confidentiality of Data and implement adequate controls over the set-up and number of Nodes; and
- f.Resilience: To ensure that the system is resistant to Data loss, loss of integrity, unavailability, or manipulation.
- 3.122Institutions should define rules relating to Data and technological architecture of the DLT Application during the design phase to ensure that internal control functions, external auditors and Supervisory Authorities can effectively access the application (when applicable) and monitor compliance.
- 3.123Institutions should appropriately determine the type of access, whether permissioned or permissionless, granted to participants based on an assessment of the operations performed, level of security and Data stored using DLT. For instance, Applications involving any of the following elements should use permissioned systems:
- 3.124Institutions should establish controls to ensure the integrity and security of the network and DLT Application. These controls may include, but are not limited to:
- a.Implementing processes to limit Node processing ability and limit the potential for a Node to process an excessive number of transactions;
- b.Designing the Application to allow blocking of IPs/Nodes that generate too many new transactions; and
- c.Developing permissioned DLT Applications with individual Nodes that comply with security standards and requirements to guard against attacks.
- 3.125Institutions should establish appropriate consensus protocols or platforms to accept and validate new records. The consensus methodology should be based on the Institution’s requirements with respect to performance, scalability, consistency, Data capacity, governance, security and failure redundancy.
- 3.126Institutions should avoid storing clear-text Personal Data on a blockchain and instead use sidechains or other private storage options.
- 3.127Institutions should introduce cryptographic key management to control access to confidential information and Personal Data. Institutions should institute controls with respect to key generation and management and ensure an appropriate and secure storage and transmission mechanism for private keys. The key management controls should cover offline root keys (split amongst multiple owners) and online root keys (stored on hardware security modules).
- 3.128With respect to the issuance of keys to Staff and other personnel:
- a.Institutions should issue individual keys to Staff and other persons working on behalf of the Institution for audit, supervision and review purposes;
- b.Institutions should embed internal checks and verifications on the transactions and activities executed through the distributed ledger such as Staff sign-off on requests or transactions; and
- c.Institutions should ensure they can internally identify the Staff signing-off messages or requests on the distributed ledger.
- 3.129Institutions should, if possible, ensure that the design of the DLT Application allows for change i.e. add new functionality or remove unwanted or incorrectly functioning features within the DLT Application.
- 3.130Institutions should, if possible, introduce mechanisms to manage forks (i.e. conflicts arising from incompatible versions of the DLT that are broadcast within a short time period) and ensure that the situation is resolved quickly and the integrity of the DLT is maintained.
- 3.131Institutions should, if possible, introduce user access management and authentication to provide controlled access to the DLT Application. Staff and Outsourcing Service Providers should be provided access to only those parts of the system they need to perform their responsible business or operational activities. Institutions may consider if, in certain cases, it might be feasible to accept transactions only from selected, authorised IP addresses.
- 3.132Institutions should develop controls to ensure confidentiality and integrity of code(s) and prevent alteration of code(s).
Anonymity and Pseudonymity
- 3.133Institutions developing Permissionless DLT Applications should ensure that users are not anonymous or pseudonymous, as allowing anonymity and pseudonymity can facilitate criminal purposes like tax evasion, bribery, money laundering or terrorism financing.
- 3.134Further, Institutions should consider using mechanisms such as chain analytics to follow and monitor transactions on pseudonymous blockchains.
Management and Monitoring
- 3.135Institutions should ensure that their DLT Applications are reviewed and monitored on a periodic basis to evaluate performance, detect technology and security related incidents, ensure the adequacy of controls, and promptly take any remedial action.
- 3.136Institutions should ensure that code is reviewed and validated on an ongoing basis at regular, predetermined intervals to identify any weaknesses. Institutions should ensure code is performing its expected functions and is secure.
- 3.137Institutions should conduct vulnerability assessments and penetration tests specific to the DLT Application to identify weaknesses or flaws in the security processes.
- 3.138Institutions should manage and monitor information integrity, privacy and confidentiality in the implementation of the DLT throughout its lifecycle (e.g. by conducting privacy threshold analysis, privacy impact assessment, and Data protection impact assessment). Institutions may adopt processes such as sharding and pruning during the design of the Application to further manage privacy and confidentiality mechanisms.
- 3.139Institutions should further ensure adequate control and monitoring of the DLT through an even stringent focus on encryption than traditional controls with a particular focus on key management. A related control to consider is encrypting the ledger(s) with more than one key and applying on-chain encryption.
- 3.140Institutions should review the distributed log of records and transactions within the ledger(s) to identify suspicious patterns and connections to monitor any anomalous behavior using analytics and testing.
- 3.141Institutions should adopt operations security controls including standard infrastructure controls such as virus checking schedules, zero-day exploit remediation, maintenance schedules, capacity, and backup management.
- 3.142Institutions should adopt security incident management controls that describe the processes around reporting, escalation, and response to any breaches. Institutions should monitor if one of the Nodes increases processing power and is executing a significantly higher number of transactions.
- 3.143Institutions should ensure that adequate human resources are put in place for implementing security controls to monitor access to the DLT Application and system. Institutions should ensure that these controls are updated when Staff leave or change roles.
- 3.144Institutions should maintain and monitor physical and environmental security through use of hardware security modules, physical security measures such as CCTVs, physical barriers, traditional key security, and access controls.
Data Standardisation and Interoperability
- 3.145Institutions should not maintain Personal Data on the ledger(s) and such Data should be maintained off-chain.
- 3.146Data retention will need to be factored into the underlying design of the network for Nodes to purge ledger information after certain defined time periods. Where Data retention rules apply to individual Data sets, destruction of keys used to encrypt the on-chain Data should be implemented.
- 3.147Depending on the Application, Institutions should consider the principle of interoperability when planning the design of the distributed ledger(s). Institutions should establish processes to prune the distributed ledger(s) and remove records older than a specific time period or enable processes that allow Data stored on the ledger to be forgotten (i.e. destruction of keys used to encrypt Data).
Business Continuity
- 3.148Institutions should ensure appropriate business continuity planning with respect to DLT, as it covers the potential loss of Data and processing capability due to loss of servers or connectivity, and risks such as cyber-crime.
- 3.149Institutions should plan, establish, and periodically test arrangements to maintain the continuity of the service/process performed by the DLT Application in the event of an incident that affects the availability of the Application
- 3.150Institutions should ensure that their business continuity plan encompasses all the complex technical areas of DLT, from key storage and key regeneration in the event of catastrophic Data loss to creating new keys when a cyber-crime incident compromises Data security.
- 3.151Institutions should consider DLT specific scenarios such as network malfunction or compromise of Data integrity in their business continuity plans.
- 3.152The Institution’s business continuity plan team should include specialists in DLT and should monitor cryptographic advances and vulnerabilities such that proactive responses can be developed to avoid system outages.
- 3.153In solutions involving public key infrastructure, Institutions should ensure that the business continuity plan covers the technical integrity of the key generation mechanisms (certificate authorities, hardware security modules etc.), the business processes involved in the secure transportation of the private keys and the authorisation layer around these mechanisms.
Customer Protection
- 3.154Institutions should disclose the relevant governing rules to Customers participating in the distributed ledger(s).
- 3.155Institutions should disclose any Fees associated with the on-going operation and management of the distributed ledger(s) including providing notice that Fees may be charged by Third Parties, where applicable.
- 3.156Institutions should advise Customers on what they should do to protect their keys from misuse. In particular, Institutions should inform Customers of the consequences of sharing their private keys and other security information.
Section 4: Interpretation
Any clarification or interpretation of the provisions of the Guidelines may be sought from the respective Supervisory Authority:
- •FinTech Office of the Central Bank of the UAE (fintechoffice@cbuae.gov.ae);
- •FinTech Team of the Securities and Commodities Authority (fintech@sca.gov.ae);
- •Innovation Team at the Dubai Financial Services Authority (innovation@dfsa.ae); and
- •Financial Technology and Innovation Unit of the Financial Services Regulatory Authority (fintech@adgm.com).
Authentication and Secure Communication
Article (18) Authentication
Licensees who are Data Holders and Service Owners must apply authentication procedures in accordance with Article 18(2) of this Regulation, where a User:
1.1. accesses Account or Product information through a Data Sharing Provider conducting Data Sharing activities; or
1.2. initiates a Transaction through a Service Initiation Provider conducting Service Initiation activities.
- Licensees who are Data Holders and/or Service Owners must select and implement a reliable and effective authentication procedure to verify the identity and validate the authority of the User. At a minimum, the procedure must require two factor authentication, including elements of knowledge, possession or inherence. Additional procedures must be applied in higher risk circumstances. Licensees who are Data Holders and/or Service Owners must also comply with any additional requirements specified from time to time by the Central Bank.
- Providers of Data Sharing and/or Service Initiation may rely on authentication procedures performed by the Data Holder or Service Owner, as appropriate.
Article (19) Secure Communication
- All participants in Open Finance must use common and secure open standards of communication for the purpose of identification, authentication, notification and information, as well as for the implementation of security measures, between Licensees who are Data Holders and/or Service Owners in addition to Data Sharing Providers, Service Initiation Providers, Users, Payers, Payees and other relevant parties.
- All communications must be conducted in accordance with the Regulations, as prescribed from time to time by the Central Bank, pursuant to the Open Finance Framework.
Licensees offering Accounts or Products that are accessible online must have in place at least one interface which meets each of the following requirements:
3.1 Data Sharing Providers and Service Initiation Providers can identify themselves to the Licensees;
3.2 Data Sharing Providers can communicate securely to request and receive information on one or more Products and/or Accounts; and
3.3 Service Initiation Providers can communicate securely to provide Service Initiation and receive information on Service Initiation and the associated Transaction.
- Licensees must establish the interface referred to in Article 19(3) of this Regulation by means of a dedicated interface or by allowing use by the Open Finance Providers, of the interface used for authentication and communication with the Licensee’s User.
- Licensees must also ensure that any dedicated interface referred to in Article 19(3) of this Regulation uses ISO 20022 elements, components or approved message definitions, for financial messaging, as amended/updated from time to time.
- Information held by the Data Holder or Service Owner must only be accessed for the purposes of providing Open Finance Services and any relevant ancillary activities in compliance with the requirements of this Regulation.
- All participants in Open Finance must use common and secure open standards of communication for the purpose of identification, authentication, notification and information, as well as for the implementation of security measures, between Licensees who are Data Holders and/or Service Owners in addition to Data Sharing Providers, Service Initiation Providers, Users, Payers, Payees and other relevant parties.
Article (20) Obligation Toward Users
- Open Finance Providers must operate prudently and ethically and with competence, in a manner that will not adversely affect the interests of a User or potential User.
- Open Finance Providers must provide a User with written terms and conditions governing their contractual relationship with the User in advance of entering into a relationship with a User for the provision of Open Finance Services.
- The terms and conditions referred to in Article 20(2) of this Regulation must be written in clear, plain and understandable language, in a manner that is not misleading, and must, at a minimum, be available in Arabic and in English. To the extent that the Open Finance Provider is contractually entitled to make changes to its terms and conditions, the Open Finance Provider must provide at least sixty (60) calendar days’ notice to the User of such changes.
- A User is entitled to terminate its relationship with an Open Finance Provider, at no charge (direct or indirect), if the User does not accept the change(s) to the Open Finance Provider’s terms and conditions notified to the User under Article 20(3) of this Regulation.
An Open Finance Provider’s terms and conditions with Users must at a minimum set out the following:
5.1 schedule of fees and charges;
5.2 contact details of the Open Finance Provider, including legal name and registered address, and the address of the agent, where applicable;
5.3 the communication channel(s) between the Open Finance Provider and the User;
5.4 the manner and timeline for notification by the User to the Open Finance Provider in case of unauthorised, delayed or incorrect Service Initiation;
5.5 information on the Open Finance Provider’s and the User’s respective liability for Unauthorized Transactions;
5.6 information on the Open Finance Provider’s complaints procedure;
5.7 information on the manner in which disputes between the Open Finance Provider and the User are to be resolved; and
5.8 the Open Finance Provider’s procedure for reporting of Unauthorized Transactions.
- Open Finance Providers must operate prudently and ethically and with competence, in a manner that will not adversely affect the interests of a User or potential User.
Liability
Article (21) Liability for Unauthorised Transactions, Defective Transactions and Data Breaches
- An Open Finance Provider is liable to a User for loss or damage suffered by the User where there has been unauthorized access to or loss of the User Data of that User held by the Open Finance Provider.
- In relation to Initiation Services, a Service Initiation Provider is liable to a User for loss or damage suffered by the User in relation to the non- execution or late or defective execution of a Transaction (arising from the late initiation and/or late processing of the initiation of Transactions), including where there has been a failure by the Service Initiation Provider to ensure that the Transaction was appropriately authorised, authenticated, accurately recorded or failure to use appropriate secure methods of communication.
- In the case of a dispute between the Service Initiation Provider and the User as to the Service Initiation Provider’s liability under Article 21(2) of this Regulation, it is for the Service Initiation Provider to prove that the Transaction was correctly processed, with supporting evidence.
- In relation to Initiation services, a Service Owner is liable to a User for loss or damage suffered by the User in relation to the non-execution or late or defective execution of a Transaction, unless such loss or damage occurred as a result of any act or omission of the Service Initiation Provider as provided for in Article 21(2) of this Regulation.
- Any breach of security or other action that leads to the illegal, unauthorised, or accidental access, alteration, destruction, disclosure or loss of User Data that is a User’s Personal Data during storage, transmission or otherwise that is caused directly or indirectly, in whole or in part, by an Open Finance Provider may subject the Open Finance Provider to administrative and financial sanctions and penalties as deemed appropriate by the Central Bank, without prejudice to any other sanctions or penalties set out under applicable laws.
- An Open Finance Provider is liable to a User for loss or damage suffered by the User where there has been unauthorized access to or loss of the User Data of that User held by the Open Finance Provider.
Data Privacy and Users’ Consent
Article (22) Data Privacy and Consent for the Use of Personal Data
- An Open Finance Provider must not Process any Personal Data for the provision of its services unless it has the explicit consent of the User to do so. Article 22 of this Regulation is subject to the prohibitions on Processing Sensitive Data set out in Article 4(1)(5) and in Article 16(3)(2) of this Regulation.
A User’s consent must:
2.1 be specific to the purpose for which it is provided, informed, unambiguous, and freely given;
2.2 be given using a clear, objective and affirmative statement or action to signify agreement to the Processing of Personal Data of that User;
2.3 if the Processing is intended to cover multiple purposes, be obtained for each purpose in a manner that is clearly distinguishable;
2.4 in case of a recurring Transaction, specify the period for which the consent is valid, up to a maximum period of twelve (12) months; and
2.5 be able to be withdrawn by the User at any time and for any reason, upon notice to the Open Finance Provider.
- An Open Finance Provider must inform the User of this right to withdraw consent and how to exercise that right at the time the consent is obtained. Withdrawing consent should not require undue effort on the part of the User and should be at least as simple, quick and easy as the process of giving consent. Withdrawal of consent does not affect the lawfulness of Processing carried out before the date of withdrawal and shall not prevent the Open Finance Provider from retaining Personal Data required for compliance with Article 13 of this Regulation or applicable laws.
In the case of Service Initiation, a User’s consent must be obtained in relation to each Transaction to be Initiated by the Service Initiation Provider or, in the case of a recurring Transaction, a User’s consent must be obtained at the time that the User first establishes the recurring Transaction, and its parameters. A User’s consent in the case of Service Initiation must include details, as relevant, of:
4.1 The relevant Account(s) or Product(s) to which the Transaction(s) relates;
4.2 The nature of the relevant Transaction(s) to be Initiated (including whether it is a recurring Transaction);
4.3 The value(s) of the relevant Transaction(s);
4.4 The beneficiary(ies) of the relevant Transaction(s); and
4.5 The value date(s) of the relevant Transaction(s).
- A User’s consent will not be considered valid in circumstances where the Open Finance Provider has obtained that User’s consent to Process Personal Data which includes Personal Data that is not relevant or not limited to what is necessary for the relevant purpose for which it is provided.
- If User Data contains Personal Data of natural persons other than the User, Open Finance Providers must anonymise such Personal Data of these other natural persons, or ensure that the consent of such natural persons to whom the Personal Data relates, is obtained prior to Processing such Personal Data in accordance with this Regulation (unless the Processing of that Personal Data is otherwise permissible under applicable laws concerning the protection of Personal Data).
- Nothing in this Regulation derogates from the obligations of a Licensee under all other applicable laws and regulations relating to protection of Personal Data including other Regulations.
- Open Finance Providers must comply with all other applicable laws and regulations relating to the protection of Personal Data.
Without prejudice to Articles 22(7) and (8) of this Regulation, Personal Data Processed by a Licensee or an Open Finance Provider relating to Open Finance Services must be:
9.1 Processed lawfully, fairly and in a transparent manner;
9.2 collected for specified, explicit and legitimate purposes and not Processed at any time, in a manner that is incompatible with those purposes;
9.3 adequate, relevant and limited to what is necessary in relation to the purposes for which it is Processed;
9.4 accurate and, where necessary, kept up to date; every reasonable step must be taken to ensure that Personal Data that is inaccurate, having regard to the purposes for which it is Processed, is erased or rectified without delay; and
9.5 Processed in a manner that ensures appropriate security of the Personal Data, including protection against unauthorised or unlawful Processing and against accidental loss, destruction or damage, using appropriate technical or organisational measures.
- Open Finance Providers must destroy User Data that is Personal Data which allows for the identification of the User, after the purpose of its provision to the Open Finance Provider has been completed, subject to the record retention requirements in Article 13 of this Regulation and any mandatory data retention requirements under applicable laws, including AML Laws.
Open Finance Providers must store all data relating to Open Finance Services within the State and are not permitted to maintain copies of the data they obtain through Open Finance Services outside of the State, unless the Open Finance Provider has obtained:
11.1 approval from the Central Bank and additional approvals from any other relevant competent authority, as necessary;
11.2 prior written consent from the User. For the purpose of obtaining such consent from a User, the User must be informed of the following, prior to or at the time of being asked to give consent:
11.2.1 where the User Data will be stored;
11.2.2 why it will be stored outside the State; and
11.2.3 that consent is sought only for the purpose which has been approved by the Central Bank; and
11.3 written acknowledgement from the User that his/her User Data may be accessed under legal proceedings outside the State in such circumstances.
- Subject to Central Bank approval, and in accordance with relevant laws and Regulations, licensed branches of foreign banks may store data relating to Open Finance Services outside of the State, provided a copy of the Master System of Record, updated on at least a daily basis, is stored in the State.
- An Open Finance Provider must not Process any Personal Data for the provision of its services unless it has the explicit consent of the User to do so. Article 22 of this Regulation is subject to the prohibitions on Processing Sensitive Data set out in Article 4(1)(5) and in Article 16(3)(2) of this Regulation.
Anti-Money Laundering, Terrorist Financing and Security
Article (23) Anti-Money Laundering and Combating the Financing of Terrorism and Illicit Organisations
- Open Finance Providers must have comprehensive and effective internal Anti-Money Laundering and Combating the Financing of Terrorism policies, procedures and controls in place to ensure compliance with the AML Laws and Regulations, as amended from time to time.
- Open Finance Providers must have robust fraud control policies and systems in place, which should address identification and access controls requirements, to comply with the requirements of this Regulation.
- Open Finance Providers must have comprehensive and effective internal Anti-Money Laundering and Combating the Financing of Terrorism policies, procedures and controls in place to ensure compliance with the AML Laws and Regulations, as amended from time to time.
Article (24) Technology Risk and Information Security
- Open Finance Providers must establish an appropriate information technology (IT) governance framework. IT governance must cover various aspects, including a clear structure of IT functions and the establishment of IT control and risk management policies, and at a minimum, must include an effective IT function, a robust technology risk management function, and an independent technology audit function.
- The Board, or a committee designated by the Board, shall be responsible for ensuring that a sound and robust risk management framework is established and maintained to manage technology risks in a manner that is proportionate to all risks that the Open Finance Provider is exposed to.
- Open Finance Providers must adhere to the security and other standards set by the operator to ensure that the software used by the Open Finance Provider is not compromised at any stage in its development process.
- Open Finance Providers must adopt and implement industry standards and best practices in relation to security risk management as directed by the Central Bank from time to time.
- Open Finance Providers must identify, manage and adequately address all cybersecurity risks through the implementation of a technology risk management framework. Open Finance Providers must commit adequate skilled resources to ensure its capability to identify the risk and protect its critical infrastructure and services against any attack and contain the impact of cybersecurity incidents and restore its services.
- Open Finance Providers must establish a cybersecurity incident response and management plan to swiftly isolate and neutralise a cybersecurity threat and to resume affected services as soon as possible. The plan must, inter alia, describe the procedures to respond to plausible cyber threat scenarios.
- Open Finance Providers must establish an appropriate information technology (IT) governance framework. IT governance must cover various aspects, including a clear structure of IT functions and the establishment of IT control and risk management policies, and at a minimum, must include an effective IT function, a robust technology risk management function, and an independent technology audit function.
Supervisory Examinations
Article (25) Supervision
- The Central Bank may conduct periodic examinations of the operation of Open Finance Providers to ensure their financial soundness and compliance with the requirements of this Regulation and all applicable laws and Regulations.
- Open Finance Providers must provide the Central Bank with full and unrestricted access to their premises, Senior Management and employees, accounts, records and documents, and must promptly supply such information and facilities as may be required by the Central Bank to conduct the monitoring and examination referred to in Article 25(1) of this Regulation.
- The Central Bank may conduct periodic examinations of the operation of Open Finance Providers to ensure their financial soundness and compliance with the requirements of this Regulation and all applicable laws and Regulations.
Supporting Regulatory Technical Standards
Article (26) Supervision
The Central Bank may, from time to time, and, in cooperation with relevant government bodies and consultation with relevant stakeholders, develop and issue regulatory technical standards addressed to Open Finance Providers with the aim of establishing additional requirements and/or providing additional details, controls and guidance on areas relating to the provision of Open Finance Services within the scope of Open Finance activities, including, but not limited to:
1.1. digital access specification;
1.2. cyber security;
1.3. overall customer journey design;
1.4. management and journeys of centralised consent including consent; app-to-app
1.5. right to implement capped charging or to inhibit charging to third party providers; and
1.6. any other area as may be required.
Enforcement and Sanctions
Article (27) Enforcement and Sanctions
- Violation of any provision of this Regulation or committing any of the violations provided for under the Central Bank Law or other applicable laws may subject the Open Finance Provider and/or Licensee to administrative and financial sanctions and penalties as deemed appropriate by the Central Bank.
- Violation of any provision of this Regulation or committing any of the violations provided for under the Central Bank Law or other applicable laws may subject the Open Finance Provider and/or Licensee to administrative and financial sanctions and penalties as deemed appropriate by the Central Bank.
Article (28) Consumer Protection
- Open Finance Providers will be subject to applicable consumer protection laws and their implementing regulations as well as any Regulations issued.
- Open Finance Providers will be subject to applicable consumer protection laws and their implementing regulations as well as any Regulations issued.
Article (29) Interpretation
- The Regulatory Development Department of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
- The Regulatory Development Department of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
Article (30) Publication and Application
- This Regulation shall be published in the Official Gazette in both Arabic and English and shall come into effect in phases as notified by the Central Bank.
Schedule 1 – Details of the Open Finance Framework
The Introduction to this Regulation specifies that the Open Finance Framework consists of the Trust Framework, the API Hub, the Common Infrastructural Services and such other matters as might be determined from time to time by the Central Bank.
The Trust Framework, the API Hub and the Common Infrastructural Services shall at a minimum include the following:
Trust Framework
The Trust Framework shall include:
The Participant Directory
1.1. to facilitate the validation of participants in the Open Finance Framework and the secure exchange of information.
1.2. to provide identity and access management services to enrolled market participants providing secure access to use Open Finance Services, contact and enrolment management, digital certificate validation and Application registration and validation services.
- Digital Certificates: to facilitate secure communication between participants with respect to the provision of Open Finance Services. The operator of the Trust Framework will mint, revoke and validate digital certificates used to access Open Finance Services.
- API Portal: to hold all documentation on standards, technical specification, requirements and business rules for all participants.
- Sandbox: to facilitate participants’ ongoing testing and official conformance certifications.
API Hub
The API Hub shall include an API Manager. The API Manager will provide an API Aggregator to aggregate participant API’s and provide a single point of implementation. The API aggregator will provide a harmonised and standardised API for participants in the Open Finance Framework for all of the underlying APIs included in this Regulation with which it integrates.
A Participant Integration Layer used to receive and manage information related to Accounts, Transaction Initiation Services and all other data exposed to the Open Finance Framework.
Common Infrastructural Services
The Common Infrastructural Services shall include:
- A Consent and Authorization Manager: a standalone App for Users or a set of APIs for participants that supports the creation, management, enforcement and revocation of consumer, organisational and jurisdictional privacy directives.
- Service Assurance: a platform for managing all service level enquiries relating to onboarding and registration requests as well as technical enquiries relating to all key components covering data and Transaction flow enablement.
- Reporting and Analytics: a platform used to analyse and report operational data and KPIs across participants including service performance, service availability and service adoption.
- Administration Tools: a platform used to facilitate the management, tracking, adjudication and resolution of cases and disputes among participant (whether between participants or in relation to end Users).
- Value added enablers as appropriate.
Recovery and Resolution
Recovery Planning Regulation
C 4/2023 Effective from 29/12/2023Introduction
The purpose of the recovery plan is to prepare a Financial Institution to be more resilient to periods of severe financial stress and guide it to stabilize itself and restore its financial position and overall viability.
The recovery plan is an important crisis preparedness and management resource. It must be designed with a view to its implementation in distressed situations and must not be treated as a compliance exercise.
This Regulation is issued pursuant to the powers vested in the Central Bank under the provisions of the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organisation of Financial Institutions and Activities, as amended and Federal Law No. (6) of 2007 Concerning Organizing of Insurance Operations, as amended.
Scope of Application
This regulation applies to Financial Institutions, which includes the following for the purpose of this regulation:
1) Banks.
2) Insurance Companies.
3) Branches of foreign Banks and branches of foreign Insurance Companies.
4) Any other Licensed Financial Institution designated by the Central Bank, at its discretion, as being required to implement recovery planning. Article (1): Definitions
1.1 Bank: Any juridical person licensed in accordance with the provisions of the Central Bank Law, to primarily carry on the activity of taking deposits, and any other licensed financial activities, as defined in the Central Bank Law.
1.2 Central Bank: The Central Bank of the United Arab Emirates.
1.3 Central Bank Law: Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organisation of Financial Institutions and Activities, as amended.
1.4 Control Function: Function (whether in the form of a person, unit or department) that has a responsibility in a Financial Institution to provide objective assessment, reporting and/or assurance; this includes the risk management, compliance, internal audit and, where applicable, actuarial, Shari’ah control and Shari’ah audit functions.
1.5 Core Business Lines: Business lines and associated services that represent material sources of revenue, profit or franchise value for a Financial Institution.
1.6 Critical Functions: Activities, services or operations the discontinuance of which is likely to lead to the disruption of financial stability, or of services that are essential to the economy due to the size, market share, external and internal interconnectedness, complexity, cross-border activities of a Financial Institution, with particular regard to the substitutability of those activities, services, or operations.
1.7 Enterprise Risk Management (ERM): The strategies, policies and processes of identifying, assessing, measuring, monitoring, controlling, reporting and mitigating risks in respect of an Insurance Company’s enterprise as a whole.
1.8 Financial Institution: a Bank or Insurance Company, or branch in the UAE of a foreign bank or insurance company, or any other Licensed Financial Institution designated by the Central Bank.
1.9 Financial Market Infrastructure: multilateral system among participating institutions, including the operator of the system, used for the purposes of clearing, settling, or recording payments, securities, derivatives, or other financial transactions.
1.10 Idiosyncratic Stress Scenario: a stress scenario that affects only the Financial Institution’s group or part of that group, but not the broader market or sector; as opposed to a System-Wide Stress Scenario.
1.11 Insurance Company: The insurance company incorporated in the State, or a foreign branch of an insurance company, that is licensed to underwrite primary insurance and reinsurance, including Takaful Insurance Companies.
1.12 Insurance Law: The Federal Law No. 6 of 2007 Concerning the Organization of Insurance Operations, as amended.
1.13 Internal Shari’ah Supervisory Committee: A body appointed by an Islamic Financial Institution (“IFI”) or a Takaful Insurance Company, comprised of scholars specialized in Islamic financial transactions, which independently supervises transactions, activities, and products of the IFI or the Takaful Insurance Company to ensure compliance with Islamic Shari’ah in all its objectives, activities, operations, and code of conduct.
1.14 Islamic Financial Institutions: The Central Bank licensed Financial Institutions that conduct all or part of their activities and businesses in accordance with Islamic Shari’ah Provisions.
1.15 Islamic Shari’ah Provisions:
a. The resolutions, Fatwas, regulations and standards issued by the Higher Shari’ah Authority in relation to activities and businesses of the IFIs and the Takaful Insurance Companies ("HSA’s Resolutions"),
b. The resolutions and Fatwas issued by the Internal Shari’ah Supervision Committee of the respective IFIs and the Takaful Insurance Companies, in relation to their activities and businesses ("ISSC’s Resolutions"), provided that they do not contradict the HSA’s Resolutions.
1.16 Own Risk and Solvency Assessment (ORSA): an internal process undertaken by an Insurance Company/ Group to assess the adequacy of its Risk Management and current and prospective solvency positions under normal and severe stress scenarios. It requires an Insurance Company to analyze all reasonably foreseeable and relevant material risks. It covers current and future risks and requires company-specific judgment about risk management and the adequacy of their capital position that could have an impact on its ability to meet both its business objectives as well as its policyholder obligations. This encourages management to anticipate potential business challenges, capital needs and to take proactive steps to reduce risks. The ORSA is not a one-off exercise; it is a continuously evolving process and must be a component of an Insurance Company’s Enterprise Risk Management (ERM) framework. Whilst there is not one specific way of conducting an ORSA, the output is expected to be a set of documents that demonstrate the results of management's proactive approach to its own self-assessment.
1.17 Senior Management: The individuals or body responsible for managing the Financial Institution on a day-to-day basis in accordance with strategies, policies and procedures set out by the board, generally including, but not limited to, the chief executive officer, chief financial officer, chief risk officer, and heads of the compliance and internal audit functions.
1.18 Staff: All the persons working for a Financial Institution including the members of Senior Management, except for the members of its Board.
1.19 Standing Facilities: Monetary Policy tools made available to Licensed Financial Institutions, to enable management of their liquidity in accordance with the controls and instructions issued by the Central Bank, in accordance with the provisions of the Central Bank Law.
1.20 System-Wide Stress Scenario: a stress scenario that affects not only the Financial Institution’s group or part of that group, but also the broader market or sector in which it operates; as opposed to an Idiosyncratic Stress Scenario.
1.21 Takaful Insurance: A collective contractual arrangement aiming at achieving mutuality and cooperation among a group of participants against certain risks, whereby each participant pays certain contribution to form an account called the participants’ account. This account is used for paying the entitled compensations and/or benefits when risk is realized, in accordance with the terms and conditions. The Takaful Insurance Company manages this account and invests its funds.
All transactions of the Takaful Insurance Company should be in accordance with the Islamic Shari’ah Provisions. Article (2): Requirement for a Recovery Plan
Financial Institutions must have in place a recovery plan in line with the requirements stated in this Regulation, which must include, at a minimum, the following:
2.1 An executive summary setting out the key elements of the plan and a summary assessment of the overall recovery capacity;
2.2 A summary of the material changes to the Financial Institution and to the recovery plan since the most recent recovery plan;
2.3 Description of the Financial Institution that outlines its legal structure, Core Business Lines, main risks, business model, Critical Functions, and key financial operations and characteristics;
2.4 The governance aspects of the Recovery Plan and how it is integrated into the broader corporate governance, policies and processes of the Financial Institution;
2.5 A framework of recovery indicators, trigger thresholds, and the associated governance and escalation procedures;
2.6 A range of recovery options that can be implemented to restore the viability of the Financial Institution;
2.7 A range of stress scenarios, stressing the Financial Institution in various manners, and setting out the management actions to restore its viability, in particular by implementing recovery options;
2.8 The recovery capacity of the Financial Institution in general and applied to various scenarios;
2.9 The central bank liquidity facilities that the Bank may have access to and the process to obtain access, including the collateral available for this purpose;
2.10 An overview of the preparatory arrangements the Financial Institution has taken or intends to take to improve their access to recovery options;
2.11 Business continuity arrangements;
2.12 A communication plan catered to all relevant stakeholders, internal and external, to deploy when implementing recovery options; and
2.13 The Annex as set out in Article 13 below. Article (3): Scope of Recovery Plan and Proportionality
3.1 The recovery plan must be commensurate with the Financial Institution’s complexity, size, group and organizational structure, risk profile and interconnectedness.
3.2 Financial Institutions must assess whether they provide Critical Functions to the financial systems in which they operate and take this into account for all aspects of their recovery plan, including, in particular, the definition of stress scenarios, the calibration of recovery thresholds and the impact recovery options may have on the provision of these Critical Functions.
Examples of Critical Functions include payments, custody, certain lending and deposit-taking activities in the commercial or retail sector, clearing and settling, limited segments of wholesale markets, market making in certain securities and highly concentrated specialist lending sectors. Article (4): Group Recovery Plans
4.1 Groups must draw up recovery plans that cover all of the Financial Institutions within the group, and must consider in their plan the scenarios, recovery options, indicators and thresholds relevant for each Financial Institution in the group.
4.2 The aim of the group recovery plan is to achieve the recovery of the group as a whole, or of one or more Financial Institutions within that group while considering the impact on the group as a whole.
4.3 Group recovery plans must include an overview of the arrangements in place to enable intra-group financial support, where applicable.
4.4 The group recovery plan should provide an overview of any material links between group entities, including for example back-to-back transactions and guarantees.
4.5 Group recovery plans must identify and set out any possible practical, legal or other impediments that may prevent the implementation of recovery options that involve multiple entities in the group, and in particular when the options involve transfers between group entities.
4.6 Group recovery plans must be assessed and approved by the parent entity of the group’s board of directors.
4.7 For a Financial Institution whose head office is in the UAE, the recovery plan must cover the entire group.
4.8 For a Financial Institution that is a UAE subsidiary of an institution whose parent entity is outside the UAE, the recovery plan must cover the UAE subsidiary. The recovery plan must be consistent with and complement the group’s recovery plan and clearly set out the interactions and interdependencies between the local and group recovery plans.
4.9 For a Financial Institution that is a UAE branch of a foreign institution, the recovery plan must be tailored to its local operations. The Central Bank may require the branch to disclose fully or partially the recovery plans prepared by the foreign institution at the level of its group and may at its discretion determine that such recovery plan suffices to meet the requirements under this Regulation or recommend changes thereto for this purpose. In making this determination, the Central Bank will consider whether the local operations have been sufficiently considered in the group recovery plan.
4.10 For a group recovery plan to be deemed to sufficiently cover the local operations, the group recovery plan must at a minimum:
4.10.1 describe whether and how, the major recovery options in the group recovery plan, if deployed, would impact the UAE operations either directly or indirectly;
4.10.2 demonstrate how recovery plan actions at the group level may be triggered by the occurrence of severe stress events in the UAE;
4.10.3 describe the process for activating the group recovery plan, specifying the local UAE management’s role and involvement in the recovery planning process and outlining the conditions for execution of recovery options (such as the necessary steps, estimated implementation time and cross-border considerations); and
4.10.4 illustrate how the recovery options are expected to restore the financial position and overall viability of the operations in the UAE.
4.11 The Central Bank may require Financial Institutions in a group to have recovery plans of their own, in addition to the group recovery plan. Article (5): Governance
5.1 Financial Institutions must ensure effective governance arrangements are in place for the production, review and approval of the recovery plan, as well as the monitoring of its recovery indicators and its implementation.
5.2 Production, review and approval of the recovery plan:
5.2.1 The Financial Institution’s board of directors must assess and approve the recovery plan prior to its submission to the Central Bank.
5.2.2 For branches of foreign Financial Institutions, the recovery plan must be assessed and approved by the branch’s Senior Management committee.
5.2.3 For branches of foreign Financial Institutions, the Central Bank may require that, in addition to Article 5.2.2 above, the recovery plan is approved by the Board of Directors of the head office.
5.2.4 The chief risk officer is responsible for leading the development of the recovery plan along with the Senior Management.
5.2.5 The Financial Institution must ensure all relevant Senior Management including key persons in Control Functions have been involved in the production, review and approval of the recovery plan, including senior individuals from relevant business areas related to recovery plan options and those responsible for stress testing. In this context key persons in Control Functions refers to persons responsible for heading control functions.
5.2.6 The recovery plan must undergo a self-assessment and review by the Financial Institution’s internal audit function, before its submission for approval to the board of directors.
5.2.7 For governance arrangements to be effective, the Financial Institution must be prepared to demonstrate that the credibility and executability of the recovery plan in a severe stress has been sufficiently challenged to justify its approval. This includes the establishment of a development and approval process with an appropriate segregation of duties and controls between those accountable for the development of the plan and those who review and/or approve the plan.
5.2.8 An Islamic Financial Institution must, in addition, obtain approval from its Internal Shari’ah Supervisory Committee that the recovery plan is compliant with the Islamic Shari’ah Provisions.
5.3 Implementation of the recovery plan:
5.3.1 The recovery plan must include a clear escalation and decision-making process to determine its timely implementation, which should take into account the recovery indicators.
5.3.2 Decisions and actions must be associated to clearly defined roles and responsibilities assigned to key individuals.
5.3.3 Governance procedures for the communication plan must be included in the recovery plan and be consistent with governance procedures to implement the recovery plan.
5.4 Financial Institutions must have adequate systems in place to generate, on a timely basis, all relevant and up-to-date information required to support the recovery plan.
5.5 A Bank must ensure that the recovery plan is consistent with its liquidity contingency funding plan, and vice versa.
5.6 For an Insurance Company, the existing tools of its ERM framework may serve as a source of input when drafting and developing the recovery plan; these may include, but are not limited to, the ORSA, contingency plans and capital and liquidity risk management plans. Article (6): Recovery Plan Indicators
6.1 The recovery plan must include a series of recovery indicators with recovery plan triggers calibrated in a manner that will warn with sufficient notice of an upcoming stress and allow the Financial Institution to take prompt corrective action through its recovery plan.
6.2 The breach of a recovery plan trigger does not necessitate the automatic or immediate implementation of recovery options. However upon a breach:
6.2.1 The Senior Management must be notified immediately and must assess the nature of the breach, and determine whether the recovery plan needs to be activated;
6.2.2 The board of directors must be notified within 1 business day of the breach of the recovery plan indicator or immediately upon activation of the recovery plan; and
6.2.3 The Central Bank must be notified within 2 business days of the breach of the recovery plan indicator or immediately upon activation of the recovery plan.
For the purpose of the above, activation of the recovery plan means that the breach of the recovery plan trigger was confirmed and that the implementation of recovery options must be considered.
6.3 The recovery indicator framework must be integrated into the Financial Institution’s risk management and management information system. Financial Institutions must calibrate their recovery triggers to enable the timely implementation of recovery options and reduce the risk that its risk tolerance will be breached. The recovery plan must contain the expected implementation timeframes of the recovery options.
6.4 The recovery plan must include a range of quantitative and qualitative recovery indicators.
6.5 Quantitative indicators shall at a minimum include capital indicators, liquidity indicators, profitability indicators, and asset quality indicators. Quantitative recovery indicators are specified in the corresponding Annex to this Regulation.
6.6 Qualitative recovery indicators could include, for example, difficulties in issuing liabilities at current market rates, unexpected loss of Senior Management, adverse court rulings, negative market press and significant reputational damage to the franchise.
6.7 The choice of recovery indicators and the calibration of their corresponding triggers must be justified in the recovery plan. Capital and liquidity recovery indicators must be calibrated in respect of the Financial Institution’s corresponding buffers.
6.8 The recovery plan must include a detailed description of the governance arrangements surrounding the monitoring of the recovery indicators and the associated escalation procedures when they are triggered. Article (7): Recovery options
7.1 Recovery options are capital, liquidity, restructuring and other measures a Financial Institution can implement in response to stress or expected stress to restore or maintain its viability or financial position.
7.2 With respect to recovery options, the recovery plan must contain:
7.2.1 a broad range of recovery options to ensure the sufficient availability of implementable options in a variety of stress situations;
7.2.2 an approach to determine which recovery options to implement and in what sequence depending on the circumstances of each stress;
7.2.3 a description of the processes for determining the value and marketability of the Core Business Lines, operations and assets in the respective recovery options;
7.2.4 an assessment of the viability of any business lines and legal entities subject to separation in a recovery option and the impact on the remaining group structure and its viability;
7.2.5 details of the Financial Institution’s available collateral and the processes to identify it; and
7.2.6 an assessment of the possibility to transfer liquidity across group entities, where relevant.
7.3 For Banks, the range of recovery options must also include:
7.3.1 actions to strengthen capital and capital conservation measures such as suspension of dividends and payments of variable remuneration;
7.3.2 measures to secure sufficient funding while ensuring sufficient diversification of funding sources and adequate availability of collateral in terms of volume, location and quality. Proper consideration must be given to possible transfers of liquidity and assets within the Bank’s group; and
7.3.3 sales of subsidiaries and spin-off of business units, and voluntary restructuring of liabilities through debt-to-equity conversion, where possible.
7.4 For Insurance Companies, the recovery plan must also include or justify the non-inclusion of the following range of recovery options:
7.4.1 actions to strengthen capital, for example recapitalization after extraordinary losses and capital conservation measures such as suspension of dividends and payments of variable remuneration;
7.4.2 triggering of contingent capital instruments;
7.4.3 possible sales of subsidiaries, portfolios of insurance contracts, or spin-off of business units;
7.4.4 changes to the reinsurance programme;
7.4.5 changes to the investment strategy and hedging programme;
7.4.6 changes to business mix, sales volumes and product designs, including options to close books of business to new sales or business;
7.4.7 changes to underwriting and claims handling practices; and
7.4.8 modifications to contract terms and conditions, the level of charges, fees and surrender payments, the amount and timing of any discretionary benefits and the operation of discretionary incentives to renew contracts (such as “no-claims discounts” or contract renewals without new underwriting).
7.5 Each recovery option must at a minimum include the following details:
7.5.1 a description of the recovery option;
7.5.2 detailed preparatory arrangements to ensure it is implementable in a timely manner;
7.5.3 clearly allocated roles and responsibilities for its implementation;
7.5.4 the capital and liquidity impact of its implementation, measured in both monetary terms and relevant regulatory metrics; and
7.5.5 for Islamic Financial Institutions, the preparatory arrangements referred to in Article 7.5.2 above may include the requirement for obtaining pre-approval for the documentation associated with the sales and transfers of debt-based assets.
An assessment of:
7.5.6 the credibility of its successful implementation and realization of benefits;
7.5.7 the timeline for its implementation;
7.5.8 the timeline for the impact of its capital and liquidity benefits;
7.5.9 the potential impact of its implementation on the Financial Institution’s franchise, ranging between low, medium and high;
7.5.10 the potential impact of its implementation on customers or policyholders, counterparties, the financial sector and market confidence ranging between low, medium and high;
7.5.11 the impact of its implementation on the Financial Institution’s Critical Functions;
7.5.12 the potential impediments to its implementation, including those of a legal and regulatory nature, and how they could be mitigated;
7.5.13 the particularities of Islamic contracts including Takaful Insurance products, to ensure Shari’ah compliance of its implementation, for example in respect of the transferability of assets and liabilities, contract-specific requirements and terms and conditions, among others; and
7.5.14 identification of mutually exclusive recovery options and financial and operational dependencies between recovery options whose combined implementation would likely result in a lower benefit than the aggregate impact of implementing them in isolation of each other.
7.6 Recovery options that consist of asset sales or disposals must at a minimum detail potential purchasers by type and the realistic discount required to achieve a sale, taking into account different market conditions.
7.7 For Banks, the timeline for the implementation of a recovery option and the impact of its benefits must generally not exceed six months, except in rare cases where a longer timeframe is robustly justified in the recovery option’s assessment. It is expected that such cases would primarily relate to certain disposals and capital market transactions.
7.8 The recovery plan and the options it contains must be reasonably likely to be implemented quickly and effectively in situations of financial stress, and must be likely to restore the viability of the Financial Institution.
7.9 Financial Institutions must provide an overview of the preparatory measures they have taken or intend to take to improve their access to recovery options, including also new recovery options not yet included in the plan.
7.10 Islamic Financial Institutions must monitor on an ongoing basis the portion of their debt-based assets in portfolios designated for sale as part of their recovery options, and ensure that such portions remain within the permissible limits that allow the sale of these portfolios. Article (8): Scenario Testing
8.1 The purpose of scenario testing is to demonstrate the effectiveness of the recovery plan in a range of different types of stress. In particular, scenario testing should help evaluate the adequacy of arrangements in respect of recovery plan indicators, governance and recovery options.
8.2 The recovery plan must include at least:
8.2.1 An Idiosyncratic Stress Scenario;
8.2.2 A System-Wide Stress Scenario; and
8.2.3 A combined scenario, combining elements of an Idiosyncratic Stress Scenario with elements of a System-Wide Stress Scenario.
8.3 Financial Institutions must take into account how the scenario, including actions of other Financial Institutions within that scenario, may impact the effectiveness and feasibility of certain recovery options, and provide an adjusted estimate of the recovery option impact specific to the scenario, in addition to the non-adjusted impact referred to in Article 7-5-4 of this regulation.
8.4 Scenario testing for recovery planning should be aligned with other stress tests conducted by Financial Institutions as part of their capital and liquidity planning.
8.5 The recovery plan must identify a point of near failure for the Financial Institution and each scenario must be sufficiently severe to cause the Financial Institution to reach it. Financial Institutions are encouraged to use reverse stress testing as a starting point for the design of the recovery plan scenarios.
6-8 Each scenario must show the evolution of recovery indicators, including the points at which triggers are breached, across the whole scenario period, both in the absence of implementing the recovery plan and with the impact of implementing the chosen recovery options necessary to restore the Financial Institution’s financial position.
8.7 The scenario impact of the chosen recovery plan options must be set at a conservative point estimate instead of a range.
8.8 Each scenario must include an explanation of the choice of recovery plan options, sequencing and point of implementation during the recovery timeline. Article (9): Recovery Capacity
9.1 The recovery capacity is the maximum financial benefits that could be achieved by implementing the most effective and sufficiently credible combination of recovery options under different types of stress scenarios.
9.2 The combination of recovery options must consider the dependencies between them and the viability of the post-recovery business model.
9.3 Actual recovery capacity is based on the Financial Institution’s currently available recovery options. Potential recovery capacity is based on planned improvements to the effectiveness of existing recovery options, or the creation of new options whereconcrete steps have already been taken for their development.
9.4 The recovery plan must describe planned improvements to recovery options with details of the expected timeline and concrete steps that have already been taken for their development.
9.5 With respect to a Financial Institution’s recovery capacity, the recovery plan must include an assessment of:
9.5.1 the actual recovery capacity, and its potential recovery capacity where relevant, measured in both monetary terms and relevant regulatory metrics;
9.5.2 the contribution of each recovery option;
9.5.3 the timeline for implementation of each recovery option; and
9.5.4 the timeline for the impact of the capital and liquidity benefits of each recovery option.
9.6 For Banks, the minimum regulatory metrics to measure recovery capacity must comprise the common equity tier 1 ratio, leverage ratio, liquidity coverage ratio and net stable funding ratio, or eligible liquid asset ratio and loans and advances to stable resources ratio where relevant.
9.7 For Insurance Companies, the minimum regulatory metrics to measure recovery capacity must comprise the solvency ratios, the liquidity ratios and earnings ratios.
9.8 The Financial Institution may present a range of recovery capacities on the basis of a range of potential impacts and timelines for each recovery option of its recovery capacity assessment. Article (10): Central Bank Liquidity Facilities
10.1 Banks’ recovery plans must include an operational plan for accessing the Central Bank's Standing Facilities, including foreign central bank standing liquidity facilities where relevant.
10.2 In respect of these standing facilities, the operational plan must include the following information:
10.2.1 Identification of the facilities, including a description of their purpose and their suitability at different stages of implementation of the recovery plan;
10.2.2 An assessment of how the Financial Institution would meet their eligibility criteria;
10.2.3 An assessment of the Financial Institution’s eligible assets and the drawing capacity against them;
10.2.4 Processes and steps necessary to access the facilities with clearly allocated roles and responsibilities; and
10.2.5 An identification of the recovery options that would allow the Financial Institution, over time, to repay any central bank liquidity support received.
10.3 The recovery plan must be prepared without including the availability of discretionary extraordinary central bank liquidity facilities or public support.
10.4 Banks that specify standing liquidity facilities as part of their recovery options shall regularly test the operational aspects of accessing such facilities, including through test transactions. Banks shall notify the Central Bank, or any other authorityproviding the facility, that these are test transactions. Article (11): Business Continuity arrangements
11.1 The recovery plan must include:
11.1.1 An assessment of the additional requirements to which the Financial Institution may potentially become subject during crisis situations to maintain its membership of Financial Market Infrastructures, such as, for example, the prefunding or collateralising of positions, and measures to address them such as plans for the sourcing of additional collateral and the impact this in turn may have on the Financial Institution; and
11.1.2 Appropriate contingency arrangements to enable the Financial Institution to continue operating during the implementation of its recovery options. At a minimum, these arrangements must cover infrastructure and IT systems, key suppliers and key Staff, and be consistent with the Financial Institution’s other business continuity arrangements.
11.2 Financial Institutions must ensure that key service level agreements are not terminated as a result of recovery events and that contracts allow for their transfer to third parties. Article (12): Communication Plan
12.1 Financial Institutions must develop an adequate communication strategy to communicate with the public, financial markets, their Staff and other stakeholders to use in the event of deploying the recovery plan.
12.2 To this end, Financial Institutions must have in place prepared statements and a step by step plan setting out the target audience, the timing, and the approvals required to issue them. Article (13): Annex to the Recovery Plan
13 The recovery plan Annex must at a minimum include:
13.1 The recovery plan template, as determined by the Central Bank;
13.2 an overview of crisis-management roles and responsibilities and relevant contact information;
13.3 supporting documentation for the operational preparedness of the recovery options; and
13.4 supporting documentation for the assessments and analyses in the recovery plan. Article (14): Update and Submission Frequency
14.1 Financial Institutions must carry out a comprehensive review of all aspects of the recovery plan, in particular of the recovery capacity, the recovery indicators and their thresholds, the scenarios and scenario testing:
14.1.1 At least annually, for domestic systemically important Financial Institutions;
14.1.2 At least every two years, for other Financial Institutions, except where required annually by the Central Bank; and
14.1.3 Upon a change to the Financial Institution’s legal or organizational structure, business model or financial situation that would have a material effect on the recovery plan.
14.2 The recovery plan must be submitted annually to the Central Bank. Where the recovery plan has not undergone a comprehensive review in accordance with Article 14.1 above, the outline of changes referred to in Article 2.2 must demonstrate that this was not required in accordance with Article 14.1.3 above by providing an assessment of the most important relevant events.
14.3 The Central Bank may require a Financial Institution to revise its recovery plan in accordance with the instructions and timeframes determined by the Central Bank.
14.4 Where the Central Bank judges a recovery plan to not meet the objectives of this regulation due to a lack of viable or effective recovery options or due to the presence of material impediments to their implementation, the Central Bank may require the Financial Institution to take specific measures that address these deficiencies. Article (15): Enforcement & Sanctions
15.1 Violation of any provision of this Regulation and any accompanying Standards may be subject to supervisory action and administrative & financial sanctions as deemed appropriate by the Central Bank.
15.2 Supervisory action and administrative & financial sanctions by the Central Bank may include withdrawing, replacing or restricting the powers of Senior Management or members of the board of directors, providing for the interim management of the Bank, imposition of fines or barring individuals from the UAE banking sector. Article (16): Interpretation of Regulation
16.1 The Regulatory Development Division of the Central Bank shall be the reference for interpretation of the provisions of this Regulation. Article (17): Publication & Effective Date
17.1 This Regulation shall be published in the Official Gazette in both Arabic and English and shall come into effect immediately upon its publication.
17.2 Financial Institutions must have a recovery plan in place by 30 June 2024. Recovery Planning Regulation: Annex
Recovery Planning Regulation: Annex
Indicators to be included in every recovery plan (Banks)(Banks may justify replacing an indicator that is not sufficiently relevant to them with a suitable alternative indicator)
1. Capital indicators
a) Common Equity Tier 1 ratio (CET 1)
b) Total Capital ratio
c) Leverage ratio
2. Liquidity indicators
a) Liquidity Coverage Ratio (LCR) or Eligible Liquid Asset Ratio (ELAR)
b) Net Stable Funding Ratio (NSFR) or Loans to Stable Resources Ratio (LSRR)
c) Available central-bank eligible unencumbered assets
d) Liquidity position
e) Loan/financing-to-deposit ratio (LDR, FDR)
f) Asset encumbrance
3. Profitability indicators
a) Return on assets
b) Return on equity
c) Significant operational losses
4. Asset quality indicators
a) Growth rate of gross non-performing loans/financing
b) Coverage ratio [provisions ÷ (total non-performing loans/financing)]
5. Market-based indicators
a) Rating under negative review or rating downgrade
b) Credit Default Swaps spread
c) Stock price variation
6. Macroeconomic indicators
a) GDP variations
b) Credit Default Swap spreads of sovereigns
Additional indicators to be included in the recovery plan as appropriate (Banks)
Additional indicators to be included in the recovery plan as appropriate (Banks)
(non-exhaustive list provided for illustration purposes only)
1. Capital indicators
a) (Retained earnings and reserves) ÷ total equity
b) Adverse information on the financial position of significant counterparties
2. Liquidity indicators
a) Concentration of liquidity and funding sources
b) Cost of total funding (retail and wholesale funding)
c) Average tenure of wholesale funding
d) Contractual maturity mismatch
e) Cost of wholesale funding
f) Increased collateral demands
g) Deposit withdrawal
3. Profitability indicators
a) Cost-income ratio (operating costs ÷ operating income)
b) Net interest/profit margin
4. Asset quality indicators
a) Off-balance-sheet exposures
b) Net non-performing loans/financing ÷ equity
c) (Gross non-performing loans/financing) ÷ total loans/financing
d) Growth rate of impairments on financial assets
e) Non-performing loans/financing by significant geographic or sector concentration
f) Forborne exposures ÷ total exposures
5. Market-based indicators
a) Price to book ratio
b) Reputational threat to the institution or significant reputational damage
6. Macroeconomic indicators
a) Rating under negative review or rating downgrade of sovereigns
Indicators to be included in every recovery plan (Insurance Companies)
Indicators to be included in every recovery plan (Insurance Companies)
(Insurance Companies may justify not including an indicator that is not sufficiently relevant to them)
1. Capital indicators
a) Admissible assets less liabilities
b) Own funds eligible to meet the minimum capital requirement (MCR)
c) MCR surplus/ deficit
d) Own funds to meet solvency capital requirement (SCR)
e) SCR surplus/ deficit
f) Own funds eligible to meet the MGF
g) SCR ratio - groups
h) SCR ratio - non-life/general
i) SCR ratio - life/family
j) SCR underwriting
k) SCR market
l) SCR counterparty default
m) SCR operational
2. Liquidity indicators
a) Liquid assets ratio
3. Profitability indicators
a) Net combined ratio - non-life
b) Investment return - non-life/general (considering the segregation of accounts for takaful)
b) Investment return - life/family (considering the segregation of accounts for takaful)
c) Assets over liabilities
d) Return on excess of assets over liabilities
e) Return on assets
f) Return to premiums/contributions (both Gross and Net)
g) Underwriting surplus
4. Market-based indicators
a) Concentration of assets
b) Duration mismatch (years)
5. Credit Risk indicators
a) Average rating of investments (credit quality step)
b) Share of below investment grade assets (credit quality step > 3)
6. Reserving indicators
The Insurer or Re-insurer/Takaful insurance or Re-takaful insurance companies must consider including reserving indicators that measure and monitor the development of its technical provisions. Reserving indicators may include key reserving assumptions such as relevant yield curve, lapse rates or changes to the value of options and guarantees or expected profits included in future premiums/contributions.
Risk Management
Credit Risk Management Regulation
C 3/2024 Effective from 30/11/2024Introduction
The Central Bank of the UAE (“CBUAE”) seeks to promote the continuous development of an effective and efficient financial system. This regulation and the accompanying standards are issued pursuant to the powers vested under the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities and its amendments.
Each LFI is required to implement a comprehensive framework to manage the credit risk it acquires to ensure its financial resilience. In this context, this regulation establishes the minimum acceptable practices for credit risk management and provisioning for LFIs.
Where this regulation or the accompanying standards include requirements to provide specific information, to take specific measures or to address a specific list of items ‘at a minimum’, the CBUAE reserves the right to impose additional requirements to those articulated in this regulation and the accompanying standards.
This regulation supersedes and replaces the circulars and notices as set out in Article 17 of this regulation.
The accompanying ‘Credit Risk Standards’ supplement the regulation and are mandatory and enforceable in the same manner as the regulation.
Scope
This regulation applies to all LFIs in the UAE that provide Credit Facilities. In addition, LFIs incorporated in the UAE with foreign subsidiaries, affiliates, or international branches, must comply with this regulation on a consolidated basis. UAE branches or subsidiaries of foreign institutions must apply this regulation to their activities in the UAE and their reporting to the Central Bank.
Objective
The objective of this regulation is to establish minimum requirements for LFIs with regard to effective credit risk management.
Article (1): Definitions
1.1Bank: Any juridical person licensed in accordance with the provisions of the Central Bank Law, to primarily carry on the activity of taking deposits, and any other Licensed Financial Activities.
1.2Board: The LFI's board of directors.
1.3CCO: The Chief Credit Officer of an LFI, this includes the Head of Credit, or any similar designation which denotes the highest level of authority for this role within the LFI.
1.4Central Bank: The Central Bank of the United Arab Emirates.
1.51.6CEO: The Chief Executive Officer of an LFI.
1.7Counterparty Credit Risk: Transactions that give rise to counterparty credit risk include: OTC derivatives, exchange-traded derivatives, long settlement transactions and securities financing transactions that are bilaterally or centrally cleared. Counterparty credit risk may result from (but is not limited to) transactions with LFIs and corporate entities.
1.8Country Risk: The risk of loss caused by geopolitical, economic or natural events in a foreign country. The concept is broader than sovereign risk because it covers exposures to all types of obligors in the country, including individuals, corporates, banks and government entities. Country risk can have direct and indirect impacts on credit risk, market risk, operational risk, reputational risk and several other risk types. Country risk also covers transfer risk, i.e. the risk that an obligor is not able to convert local currency into a foreign currency, thereby reducing its ability to repay its debt in foreign currency. Such risk arises from foreign exchange restrictions imposed by the government in the country of the obligor.
1.9Credit Facility (“Facility”): Any legal agreement that gives rise to financial obligations or commitments that are legally binding or perceived to be legally binding on one of the parties in a transaction. In the context of this regulation, credit facilities should be understood in the broad sense as credit exposure via any financial instrument, including amongst others, on-balance sheet credit facilities, capital market instruments, receivables, off-balance sheet contracts including but not limited to guarantees/letters of credit, as well as Counterparty Credit Risk arising from over-the-counter derivatives contracts and securities financing transactions including Shari’ah compliant facilities.
1.10Credit Risk: The potential loss arising from the likelihood that a borrower or counterparty fails to meet its obligations in accordance with agreed terms of a lending agreement.
1.11Credit Risk Mitigation (“CRM”): Cash flows derived from liquidation of collateral and other sources that may be utilised to mitigate against financial loss as described in this regulation and the accompanying standards.
1.12CRO: The Chief Risk Officer of an LFI this includes the Head of Risk, or any similar designation which denotes the highest level of authority for this role within the LFI.
1.13Days-Past-Due (“DPD”): A payment is considered past due if it has not been made by its contractual due date. The days-past-due is the number of calendar days that a payment is due, i.e. the number of days for which a payment is late.
1.14Default: As defined in Article 6 of this regulation and the accompanying standards.
1.15Deferrals: A payment is considered deferred if it has not been made on or by its contractual due date with the formal agreement of the LFI to delay the single instalment.
1.16Group of Connected Counterparties: as defined in the Central Bank’s Large Exposures Regulation.
1.17Interest: For the purpose of this regulation and the accompanying standards, the treatment of ‘interest’ used for conventional finance applies to ‘profit’ used for Islamic finance unless an exception from the Central Bank and the Higher Shari’ah Authority is obtained for Shari’ah compliance purposes.
1.18Islamic Financial Services: Shari'ah compliant financial services offered by Licensed Financial Institutions that conduct all or part of their activities and businesses in accordance with the Islamic Shari’ah (“Islamic Financial Institutions” or “IFIs”).
1.19Lending: For the purpose of this regulation, the treatment of ‘lending’ used for conventional finance also apply to ‘financing’ used for Islamic finance.
1.20Licensed Financial Institutions (“LFI”): as defined under the Central Bank Law.
1.21Obligor: Individual or entity or group of entities that have a Credit Facility with the LFI.
1.22Parent and Subsidiary: An entity (the 'first entity') is a parent of another entity (the 'second entity') if any of the below requirements are met:
1.22.1The first entity holds more than 50% shareholding in the second entity;
1.22.2The first entity holds more than 50% of the voting rights in the second entity;
1.22.3The first entity is a shareholder of the second entity and has the right to appoint or remove a majority of the Board of directors or managers of the second entity;
1.22.4The first entity is a shareholder of the second entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the second entity; or
1.22.5The second entity is a subsidiary of another entity which is itself a subsidiary of the first entity.
1.23Past Due: A financial asset is past due when an Obligor has failed to make a payment when that payment was contractually due, that is if any part of the contractual Interest and/or principal payment (or the debt due in case of IFIs’ debt-based structures) is not met on time. The number of days past due is non-cumulative, where the most recent payment cures the earliest contractual breach.
1.24Purchased or Originated Credit Impaired (“POCI”): Credit Facility that is already impaired at the time when it is purchased or originated.
1.25Related Parties: The Group and its controlling shareholders, members of the Board and Senior Management (and their Relatives) and persons with control, joint control or significant influence over the LFI (and their Relatives).
1.26Relatives: The individual's parents, siblings and children.
1.27Repayment: For the purpose of this regulation, the requirements applied to “repayment” in the context of conventional finance also apply to “payment” in Islamic finance context. The timing of such repayment is called the repayment structure. In many cases Interest and/or a charge to the principal balance is added in exchange for lending/financing services and/or to cover the time value of money/compensation for the exchange.
1.28Restructured Credit Facility: As defined in Article 8 of this regulation.
1.29Retail Obligor: For the purpose of this regulation, retail obligors refer to individuals to whom Credit Facilities are granted to satisfy that individual’s personal needs. It also includes SME, small business Credit Facilities for which Credit Risk is managed by the LFI using similar methods as applied for personal Credit Facilities. If this is not the case, then SME will be classified as wholesale.
1.30Risk Appetite: The aggregate level and types of risk an LFI is willing to assume, decided in advance and within its risk capacity, to achieve its strategic objectives and business plan.
1.31Risk Governance Framework: As part of the overall approach to corporate governance, the framework through which the Board and management establish and make decisions about the LFI's strategy and risk approach; articulate and monitor adherence to the Risk Appetite and Risk Limits relative to the LFI's strategy; and identify, measure, manage and control risks.
1.32Risk Limits: Specific quantitative measures that must not be exceeded based on, for example, forward-looking assumptions that allocate the LFI's aggregate Risk Appetite to business lines, legal entities or management units within the LFI or group in the form of specific risk categories, concentrations or other measures as appropriate.
1.33Risk Management Function: Collectively, the systems, structures, policies, procedures and people that measure, monitor and report risk on an LFI-wide and, if applicable, group-wide basis.
1.34Risk Profile: Point in time assessment of the LFI's risk exposures aggregated within and across each relevant risk segment based on current or forward-looking assumptions.
1.35Senior Management: The executive management of the LFI responsible and accountable to the Board for the sound and prudent day-to-day management of the LFI, generally including, but not limited to, the chief executive officer, chief financial officer, chief risk officer, chief credit officer and heads of the compliance and internal audit functions.
1.36Significant Increase in Credit Risk (“SICR”): Material deterioration in credit-worthiness of a Credit Facility since its initial recognition as articulated in Article 7 of this regulation.
1.37Small to Medium sized Enterprise (SME): includes small, micro and medium businesses, provided that the businesses meet the thresholds of employee headcount and turnover, as defined by the Federal Cabinet Resolution No. 22 of 2016 which sets out the Small to Medium sized Enterprise definition for the purposes of Federal Law No. 2 of 2014 or any subsequent amendments to the Federal laws defining an SME.
1.38Stages: Stages are employed to classify Credit Facilities according to their current and expected credit worthiness.
1.39Wholesale: Any Obligor that is not considered a Retail Obligor as defined in this regulation.
Article (2): Credit Risk Governance
2.1The Board must approve and regularly review the LFI’s Credit Risk management strategy and significant policies and processes for the identification, measurement, evaluation, monitoring, reporting, control and mitigation of Credit Risk, including Counterparty Credit Risk, in a manner that is consistent with the Board-approved Risk Appetite.
2.2Branches of foreign banks must comply with this regulation. Where this regulation refers to the Board of the LFI, branches of foreign banks may apply the requirement either with respect to the Board of their head office or with respect to the Senior Management of their head office, which has the oversight of the foreign branch. The Central Bank may, at its discretion, require that all or some of the requirements are met with respect to the Board of the head office.
2.3The Board must ensure that the Risk Governance Framework is appropriate to the Risk Profile, nature, size and complexity of the LFI's business and structure. This includes a proactive and forward-looking oversight of the management of people, policies, processes, procedures and systems to identify, measure, monitor, report, control and mitigate Credit Risk on a timely basis, covering all exposures.
2.4The Board must oversee management to ensure that the Credit Risk management strategy and governance is effectively implemented and fully integrated into the LFI’s overall risk management process.
2.5The Board must ensure that the Risk Governance Framework includes a delegation matrix that articulates the roles and responsibilities for the approval of Credit Facilities, whereby facilities that are material, particularly risky or not aligned with the LFI’s core activities must be approved by the Board.
2.6The Board must ensure that the LFI has policies for the classification of exposures, the determination of provisions and for the management of problem exposures and write-offs. These policies must be approved and regularly reviewed by the Board, and the Board must oversee management to ensure that these policies are effectively implemented.
2.7The Board must ensure that it obtains information and reporting with sufficient detail on the LFI’s Credit Risk at an appropriate frequency throughout the year.
2.8The Board must ensure that credit decisions are made free of conflicts of interest and on an arm’s length basis.
2.9The Board remains ultimately accountable for the appropriate management of Credit Risk, notwithstanding specific responsibilities delegated to Senior Management.
Article (3): Credit Risk Management Framework
3.1LFIs must implement an adequate, well-documented and effective Credit Risk management framework consisting of policies, processes and controls that comprehensively cover the acquisition and management of Credit Risk. This framework must be consistent with the Board-approved Risk Appetite of the LFI and the Risk Profile, systemic importance and capital strength of the LFI.
3.2The framework must cover all the key steps of the Credit Risk lifecycle, including, but not limited to, origination, underwriting, approval, monitoring, portfolio management, recovery and provisioning.
3.3The Credit Risk management framework must include a robust methodology for the early identification and appropriate measurement of credit losses that meets the minimum requirements as set out in the accompanying standards to this regulation.
3.4The Credit Risk management framework must ensure the effective data aggregation, identification, measurement, monitoring, reporting, control and mitigation of Credit Risk.
3.5The framework must ensure that significant sources of concentration risk and exposures with low levels of credit-worthiness are specifically addressed, and that proper risk management and risk mitigating processes are in place.
3.6The framework must be supported by documented policies and procedures and clearly defined roles and responsibilities.
3.7The Credit Risk framework must ensure an effective credit administration process supported by comprehensive and robust information systems for the accurate and timely identification, aggregation and reporting of Credit Risk exposures to the Board and Senior Management on a regular basis is in place.
3.8The framework must also ensure that the LFI implements policies to identify, manage and report on exceptions to policies governing Credit Risk management. Such policies must specify the process to grant exceptions and ensure the involvement of Senior Management or the Board when necessary.
3.9The framework must also be designed to identify and monitor the risk factors that could lead to a deterioration in creditworthiness or Default of their Obligors.
Article (4): Credit Risk Oversight Functions and Roles
4.1Each LFI must have a credit review function headed by the CCO that is responsible for the prudent acquisition of Credit Risk arising from all products types across the LFI.
For Wholesale Obligors, the function must review individual transactions in order to assess the specific Credit Risk of facilities, in accordance with Article 5 of this regulation focusing on credit underwriting.
For Retail Obligors, the acquisition of Credit Risk must be controlled and governed at minimum at portfolio level.
4.2Each LFI must have an independent Credit Risk Management Function within the risk management function headed by the CRO to conduct adequate and continuous oversight of the acquisition and management of Credit Risk. This function must safeguard the LFI from acquiring Credit Risk that is not within the LFI’s Risk Appetite, is not in accordance with the LFI’s policies, or may otherwise present a threat to the LFI.
4.3While the Credit Risk Management Function must not have any decision-making role in the acquisition of Credit Risk, the Credit Risk Management Function must nevertheless have the power and responsibility to veto credit proposals where necessary, including but not limited to instances where the Risk Limits are or risk being breached.
4.4The internal audit function, compliance function and external audit function must have an active role in the control and oversight of Credit Risk throughout the LFI.
Article (5): Credit Underwriting
5.1LFIs must implement a comprehensive underwriting process for the acquisition of Credit Risk, consistent with the strategy of the LFI. This process must ensure a thorough understanding of the risk profile of Obligors.
5.2The underwriting process must be supported by adequate policies and procedures covering the key components of the decision process, including, but not limited to, (i) governance of credit approval, (ii) credit limits, (iii) due diligence and financial information from the Obligor, (iv) methodology for Credit Risk analysis, (v) collateral and risk mitigation, (vi) credit file documentation, and (vii) legal documentation.
5.3The credit underwriting policy must incorporate risk-return discipline consistent with the LFI’s Risk Appetite and strategy. Appropriate Risk Limits must be defined at an adequate level of granularity.
5.4LFIs must limit their reliance on external credit assessment. Where external ratings or external credit analysis are employed for a credit decision, LFIs must nevertheless develop their own independent view of the Credit Risk associated with their exposures.
5.5Credit underwriting policies must cover the approval of (i) new exposures, (ii) renewal and (iii) refinancing of existing exposures. The policy must ensure a thorough understanding of the risk profile and characteristics of the borrowers and counterparties driving the performance of these exposures. In the case of securitisations, this includes a thorough understanding of the risk profile of both the underlying assets and the structured investmentvehicle.
Article (6): Definition of Default
6.1A Default is considered to have occurred with regard to a particular Obligor when at least one of the following events have taken place: (a) non-payment and/or (b) unlikeliness to pay.
Non-payment
6.2Non-payment is considered to have occurred when a material credit obligation to the LFI is Past Due for a period greater than 90 days.
6.3Overdrafts are considered Past Due once the Obligor has breached a contractual or internal limit, or has been advised of a limit smaller than the current outstanding.
Unlikeliness to pay
6.4Unlikeliness to pay is considered to have occurred when it is unlikely that the Obligor will pay its credit obligations to the LFI in full.
6.5For the purpose of the evaluation of the unlikeliness to pay, LFIs must establish and document a set of criteria and early warning signals. The early identification of decline in creditworthiness must be based on both financial and non-financial indicators.
Article (7): Significant Increase in Credit Risk
7.1The LFI must assess and document regularly whether the Credit Risk of a financial instrument has increased significantly since its initial recognition. The identification of Significant Increase in Credit Risk (“SICR”) must be done in accordance with accounting standards and the LFI’s internal policy on SICR -and must incorporate the requirements set outin this regulation and the accompanyingstandards.
7.2The presence of SICR must be used by the LFI to determine the classification of facilities and their associated provisioning.
7.3LFIs must implement a process and develop a methodology to determine if an SICR has occurred, for all types of Obligors. The process and criteria for the identification of SICR must be linked to and consistent with the identification of unlikeliness to pay.
Article (8): Restructuring
8.1LFIs must develop and implement a process supported by policies and procedures to appropriately identify, implement and manage Restructured Credit Facilities. The Obligor/Credit Facility must be correctly classified in accordance with the criteria articulated in Article 9 on classification and provisioning.
8.2The requirements on the classification of exposures continue to apply throughout and after the restructuring process, including the related provisioning requirements set out in Article 9 of this regulation.
8.3The restructuring process must be subject to robust internal oversight and be reviewed by internal audit on a regular basis.
8.4Branches of foreign banks may have processes for the oversight of the restructuring process at head office level. Therefore, they may adopt alternative equivalent measures of oversight of the restructuring process which will be subject to supervisory review and approval by the Central Bank.
8.5For the purpose of this regulation, restructuring events are categorised into two distinct groups:
8.5.1Distressed restructuring: where any of the terms of a Credit Facility are amended in a context of financial difficulty of the Obligor.
8.5.2Non-distressed restructuring: where any of the terms of a Credit Facility are amended in the absence of current financial distress of the Obligor.
Article (9): Classification and Provisioning
Classification principles
9.1Each LFI must establish a process to assess, monitor and classify each Credit Facility or each portfolio of facilities according to its current and expected credit-worthiness. This classification must form the basis for proactive Credit Risk management, risk mitigation and provisioning.
9.2LFIs must adhere to the classification Stages as set out in the accompanying standards, or maintain a classification system that is mapped to the categories required under the accompanying standards.
9.3The classification process must be documented based on the provisioning policy approved and regularly reviewed by the Board or, in the case of branches of foreign institutions, the Board of the head office or the senior management committee of the branch.
Provisioning
9.4All LFIs must implement a process to estimate and document provisions associated with each Credit Facility in all Stages and in all credit portfolios, supported by sufficient organisational resources, in compliance with this regulation and the accompanying standards.
9.5The provisioning process must be documented, organised and approved by Senior Management and the Board, and fully integrated into the LFI’s overall risk management process.
9.6The policies and processes related to provisioning must ensure that provisions and write-offs are timely and reflect realistic repayment and recovery expectations, including appropriate expectations about future credit losses.
9.7The methodologies and levels of provisions and write-offs must be subject to an effective review and validation process by a function independent from the relevant risk-taking function.
Restructured Credit Facilities
9.8LFIs must pay particular attention to the classification of Restructured Credit Facilities as per the additional requirements articulated in the accompanying standards.
Article (10): Credit Risk Mitigation
10.1LFIs may account for the presence of CRM when determining the appropriate level of provisions, but only to the extent permitted as per the accompanying standards.
10.2LFIs must have appropriate mechanisms in place to regularly assess the value of Credit Risk mitigation, such as guarantees, credit derivatives and collateral, and adjust the level of provisions where necessary.
10.3The valuation of collateral must reflect the net realisable value, taking into account prevailing market conditions and the time and cost required for realisation.
Article (11): Portfolio Management and Internal Reporting
11.1LFIs must ensure that Credit Risk acquired through underwriting, refinancing and other mechanisms is fully monitored, reported and managed.
11.2The processes for portfolio management, underwriting and restructuring must be organized such that information from each process informs the other processes.
11.3The monitoring process must include processes to ensure that funds are used in accordance with the facility legal agreement of each Obligor.
Article (12): Non-Performing Assets and Write-Off
12.1LFIs must establish a strategy to manage non-performing assets and avoid maintaining elevated stocks of non-performing assets. This strategy must be approved and regularly reviewed by the Board, and be achieved by maximising recoveries and implementing timely write-offs. The strategy must be fully embedded into the management process of the LFIs and be the subject of regular reviews.
12.2When the LFI has no reasonable expectation to recover the full or part of a facility exposure as per the terms of the legal agreement, it should undertake a full or partial write-off of that exposure.
12.3The LFI must ensure that write-offs are timely and reflect realistic payment and recovery expectations.
Article (13): Credit Risk Models
13.1LFIs must have methodologies and analytical solutions to measure, analyse and categorise Credit Risk and compute the associated provisions. LFIs must be able to analyse Credit Risk at several granularity levels including Credit Facility level, Obligor level, segment level and portfolio level in order to identify credit concentration risk.
13.2Where an LFI makes use of models for decision making, it must comply with separate modelling standards and guidance issued by CBUAE. Each LFI must demonstrate that its models are fit for purpose and adequately calibrated to effectively support the associated risk and business decisions.
Article (14): Counterparty Liability
This regulation and the accompanying standards, including the requirement to apply haircuts or to not account for certain CRM for the purposes of calculating provisions, or to partly or fully write off exposures, do not reduce or extinguish the liability outstanding of the counterparty, and are without prejudice to the counterparty’s liability and the ability of LFIs to fully exercise and enforce their rights with regard to any form of CRM (including collateral).
Article (15): Enforcement and Sanctions
15.1Violation of any provision of this Regulation and any accompanying Standards may be subject to supervisory action and administrative & financial sanctions as deemed appropriate by the Central Bank.
15.2Supervisory action and administrative & financial sanctions by the Central Bank may include withdrawing, replacing or restricting the powers of Senior Management or members of the Board, providing for the interim management of the Bank, imposition of fines or barring individuals from the UAE banking sector.
Article (16): Interpretation of Regulation
The Regulatory Development Department of the Central Bank shall be the reference for interpretation of the provisions of this Regulation.
Article (17): Cancellation of Previous Circulars and Notices
This regulation repeals and replaces the following Central Bank regulations, circulars and notices:
17.117.217.3Notice No. 130/2016 dated 28/04/2016 regarding “Write-off of Fully Provisioned Non-Performing Loans”;
17.4Notice No. 458/2018 dated 30/04/2018 regarding “Final Guidance Note on IFRS 9”;
and any related guidance and amendments.Article (18): Publication and Effective Date
This Regulation shall be published in the Official Gazette in both Arabic and English and shall come into effect one month from the date of publication.
Credit Risk Management Standards
C 3/2024 STA Effective from 30/11/2024Introduction and Scope
1.These standards form part of the Credit Risk Regulation and both documents must be read together. All LFIs must comply with these standards, which expand on the regulation. These standards are mandatory and enforceable in the same manner as the regulation.
2.The standards follow the structure of the regulation, with each article corresponding to the specific article in the regulation.
Article 1: Definitions
These standards follow the definitions as set out in the Credit Risk Regulation.
Article 2: Credit Risk Governance
Board of Directors2.1The Board must regularly review, and approve, the Credit Risk management strategy, framework, significant policies, tolerances/limits and processes for identifying, measuring, evaluating, monitoring, reporting and controlling or mitigating Credit Risk. The Board must also ensure these are consistent with the Risk Appetite and capital strength and other relevant parameters that they set. At a minimum, it must approve the organisation of the LFI’s Credit Risk Management Functions, including the credit underwriting process, the independent review of such underwriting, the portfolio management of credit exposures and the management of distressed assets.
2.2The Board must oversee and ensure that Senior Management is fully capable of managing the Credit Risk bearing activities conducted by the LFI and that such activities are within the Risk Appetite, strategy, policies and tolerances reviewed and approved by the Board. In addition, the Board must oversee and ensure that policies and processes are implemented effectively and fully integrated into the LFI’s overall risk management process.
2.3The Board must ensure the comprehensive inclusion of Credit Risk and credit concentration risk in the stress testing programme for risk management purposes of the LFI.
2.4For LFIs incorporated in the UAE, the aforementioned includes policies and processes that provide a comprehensive group-wide view of significant sources of Credit Risk and concentration risk with appropriate consideration of the LFI’s Risk Profile, nature, and size as well as the complexity of its business and structure.
2.5The Board is responsible for ensuring that the LFI has appropriate processes, methods and systems to identify problem assets and to determine adequate provisions and reserves in accordance with the LFI’s stated policies and procedures, with the applicable accounting framework and in compliance with relevant supervisory regulations and standards.
2.6The Board, not a Board sub-committee, must approve material Facilities including any subsequent write offs. Material Credit Facilities must be approved by the Board at least every three years. The materiality thresholds must be defined by each LFI based on its Risk Appetite and the size and creditworthiness of the facility. At a minimum, material Facilities must include the following:
a.Any Facility leading to an exposure greater than 10% of the LFI’s Tier 1 Capital, and
b.Any Facility granted towards a Related Party, a Related Party’s spouse, and their Group of Connected Counterparties. Board members or other members of staff must be excluded from the approval process of granting and managing transactions for which they have a conflict of interest.
2.7For Credit Facilities below the materiality threshold defined in Article 2.6.a, the Board may assume the approval authority as outlined below or alternatively, delegate to a Board Credit Committee, which must be distinct and independent from a Board Risk Committee and Board Audit Committee. Such a committee must set appropriate thresholds and criteria for the purpose of identifying and reviewing significant Facilities that may generate a higher level of risk and may not be consistent with the Risk Appetite of the LFI. At a minimum, the approval authority for this committee must include any Credit Facility computed as the lower of the following:
a.Any Credit Facility resulting in an exposure to an Obligor greater than 5% of the LFI’s Tier 1 Capital, or
b.Any Credit Facility resulting in an exposure to an Obligor greater than AED 1 billion.
2.8For branches of foreign LFIs operating in the UAE, the requirements in 2.6 and 2.7 must be fulfilled with formal approval from Senior Management or the Board outside of UAE to which the UAE based Senior Management have a formal reporting responsibility.
2.9For Credit Facilities that do not require Board approval, the Board must define and approve a formal delegation matrix that articulates the roles and responsibilities of Senior Management for the approval of these Facilities.
2.10In order to fulfil its oversight role, the Board and Board credit committee, if any, must regularly receive timely and appropriate information on:
a.The credit worthiness of the LFI’s asset portfolio, material concentrations, the restructured portfolio, as well as significant individual credits, including classification of assets,
b.The level of provisions and reserves and major problem assets.
c.The classification of Credit Facilities, their associated provision level, the expected trend of credit quality and potential losses.
d.The key drivers and the actions taken by the management to mitigate Credit Risk.
2.11The information must include, at a minimum, summary results of the latest asset review process, trends related to problem assets, and measurements of existing or anticipated deterioration in asset quality and expected losses.
Senior Management
2.12The business line heads and their direct reports are responsible to ensure robust credit underwriting consistent with the Risk Appetite of the LFI. They must act as the first line of defence against Credit Risk, which requires appropriate identification, allocation and pricing of Credit Risk.
2.13The LFI must ensure that Credit Risk is adequately mitigated by robust underwriting, provisions, reserves and, when possible, by collateral. LFIs must have appropriate policies and processes to ensure that provisions and write-offs are timely and reflect realistic Repayment and recovery expectations, taking into account market and macroeconomic conditions and computed in compliance with the regulations, standards and generally accepted accounting principles. The CRO must form an independent opinion on the appropriateness of provisions and regularly report their view to the Board.
2.14The Senior Management team is responsible and accountable for the implementation of the Board approved strategy and Risk Appetite and is also responsible for the day-to-day management of the LFI. Regarding Credit Risk, this includes:
a.The robust implementation and communication of the strategic direction and principles set by the Board regarding the management of Credit Risk throughout the LFI and documented in the Credit Risk framework.
b.The robust implementation of the Risk Appetite of the LFI within the Credit Risk framework.
c.The acquisition, administration, underwriting and mitigation of Credit Risk within the Credit Risk framework.
2.15The Senior Management, including the CEO, the CCO and the CRO are collectively responsible for:
a.The development and implementation of sound and effective processes, policies, procedures and systems designed to manage Credit Risk in accordance with the Credit Risk framework approved by the Board, across the LFI’s portfolios and geographies.
b.Ensuring that credit exposures are within levels consistent with prudential standards and internal limits.
c.The establishment and enforcement of internal controls to ensure that exceptions to policies, procedures and limits are reported in a timely manner to the appropriate level of management for action.
d.Additional responsibilities and roles as included in Article 4.
Control and Oversight2.16Internal Audit: The internal audit function is responsible to review and report on the suitability and efficiency of the implementation of the Credit Risk framework across the entire LFI, in accordance with the strategic direction set by the Board. At a minimum the scope must include the following:
a.Material Credit Facilities (based on thresholds as formally determined by each LFI).
b.All Wholesale Restructured Credit Facilities.
c.The Credit Facilities for which it has been determined that no SICR has occurred, as per Article 7 of these standards. Evidence supporting the decision must be reviewed in light of relevant regulations and policies/Risk Appetite of the LFI.
d.Material Credit Facilities classified in Stage 3, as defined in Article 9 on classification and provisioning.
e.Any breach of this regulation and these standards.
2.17Compliance: The compliance function must ensure that this regulation and these standards are understood, communicated and correctly followed for Credit Risk underwriting and management throughout the LFI. For this purpose, it must implement a process to review the compliance of all the internal parties involved in Credit Risk acquisition and management.
2.18External Audit: External auditors are responsible to review and verify that classifications and provisions are accurate and comply with accounting and regulatory standards.
2.19The LFI must at all times provide full access to all information in the credit and investment portfolios to the LFI officers involved in assuming, managing, controlling and reporting on Credit Risk.
Article 3: Credit Risk Management Framework
3.1The Credit Risk management framework must be designed to support effectively the acquisition and mitigation of Credit Risk. It must be consistent with the Risk Appetite, Risk Profile, systemic importance and capital strength of the LFI. It must take into consideration the current and forward-looking market factors and macroeconomic environment, with the objective to ensure prudent standards of underwriting, evaluation, administration, monitoring, measurement and control of Credit Risk.
3.2The framework must include key components to be effective including, but not be limited to: the scope of instruments and geographies, Risk Appetite, controls, limits, underwriting process, credit administration process, monitoring, management of Past Due Facilities, remediation, provisioning methods, collateral management, system, models and exception management.
3.3The Credit Risk management framework must enable the LFI to obtain a comprehensive group-wide view of Credit Risk exposures. and significant sources of concentration risk, it must cover the entire organisation and must be comprehensive in terms of products, activities and geographies, as well as including a robust methodology for the early identification and appropriate measurement of credit losses.
3.4Scope: The Credit Risk management framework must enable the LFI to obtain a comprehensive group-wide view of Credit Risk exposures and significant sources of concentration risk, it must cover the entire organisation and must be comprehensive in terms of products, activities and geographies. The Credit Risk management framework must cover all financial instruments generating Credit Risk, including on- and off- balance sheet Facilities, receivables, capital market instruments and derivatives. LFIs must ensure that the risks arising from products or activities new to them are subject to adequate controls before being undertaken, and approved in advance by the Board of directors or its appropriate committee.
3.5Risk Appetite: The Credit Risk management framework must be consistent with the Risk Appetite, Risk Profile, and systemic importance of the LFI. It must take into account market and macroeconomic conditions and result in prudent standards of credit underwriting, evaluation, administration and monitoring. This includes risk management policies and processes that establish thresholds for acceptable concentrations of risk and requirements related to Credit Facility structuring, legal due diligence, product-specific controls and underwriting standards.
3.6Climate-related Credit Risk: The Credit Risk management framework must include prudent policies and processes to identify, measure, monitor, report and mitigate the impacts of material climate- related risk drivers on their Credit Risk exposures (including Counterparty Credit Risk) on a timely basis. LFIs should consider a range of risk mitigation options to control or minimise material climate-related Credit Risks. These options may include adjusting credit underwriting criteria, deploying targeted client engagement, or imposing limitations or restrictions such as shorter-tenor Lending, lower loan-to-value limits or discounted asset valuations. LFIs could also consider setting limits on or applying appropriate alternative risk mitigation techniques to their exposures to companies, economic sectors, geographical regions, or segments of products and services that do not align with their business strategy or Risk Appetite.
3.7Country Risk: LFIs that provide Credit Facilities susceptible to Country Risk must implement adequate policies and processes for the appropriate identification, measurement, evaluation, monitoring, reporting and mitigation of Country Risk, comprehensively addressing the implications on Credit Risk. Exposures to Country Risk must be consistent with the Risk Appetite and risk profile of the LFI. The management and control of Country Risk must be incorporated into the key steps of Credit Risk management, covering the origination, underwriting, monitoring and provisioning processes. Relative to the magnitude of foreign Lending, an LFI must review and establish additional provisioning percentage ranges for each country, considering prevailing conditions that may be applicable to its individual exposures.
3.8At a minimum, the Credit Risk management framework must include the following components: Risk Limits, underwriting process, credit administration, monitoring, measurement of Past Due Facilities including problem assets, remediation process, Counterparty Credit Risk, provisioning methodology, collateral management, information systems, analytical tools, provisioning methodologies as well as exception management. The corresponding minimum requirements are articulated below.
Risk Acquisition
3.9Risk Limits: LFIs must implement prudent and appropriate credit limits based on adequate metrics and at a suitable level of segmentation granularity. These limits must be consistent with the Board-approved Risk Appetite statement, Risk Profile and capital strength. Risk Limits should be understood by, and regularly communicated to, relevant staff.
3.10Underwriting process: LFIs must implement a clear credit underwriting framework commensurate with their Risk Appetite and Lending strategy. LFIs must follow the minimum requirements presented in the dedicated section of these standards.
Risk Management
3.11Credit administration: LFIs must establish effective credit administration policies and processes to address the operational requirements of Credit Facilities throughout their lifetime. These must support the monitoring process of Credit Risk and mitigate operational risks linked to Credit Risk management and must include at a minimum: continued and forward-looking analysis of a Obligor’s (and potentially, a wider borrowing group’s) ability and willingness to repay under the terms of the financial obligation including but not limited to evaluation of underlying assets, robust data gathering, monitoring of documentation, financing covenants, contractual requirements, collateral and other forms of CRM and an archiving mechanism.
3.12Monitoring: LFIs must have policies and processes to continuously monitor the total indebtedness of Obligors, their financial performance and any risk factors that may result in the increased risk of Default, including significant unhedged foreign exchange risk. The above must incorporate the continuous and forward-looking analysis of each portfolio/Obligor’s ability and willingness to meet its obligations under the terms of its contracts, while taking into account the current and future economic environment. This should include regular reviews of credit exposures (at an individual level or at a portfolio level for credit exposures with homogeneous characteristics) to ensure appropriate classification, detection of deteriorating exposures and early identification of problem exposures. This process must be established at several levels of granularity.
a.For each level, suitable metrics and early warning indicators must be put in place. At a minimum, for Wholesale Obligors the monitoring process must be implemented at the following levels of granularity (a) Credit Facility level and Obligor level, (b) consolidated group level for large conglomerate, and (c) segment, portfolio level.
b.The monitoring process must analyse, understand and document the links between Obligors. This must include economic connectivity and correlated factors such as suppliers and/or customers of the Obligor. This must also capture the common sensitivity to the business cycle, the industry risk and any other systemic risks.
c.For Retail Obligors, monitoring should be performed at portfolio levels or at a more granular level, determined by the LFI.
d.The monitoring process must include a regular review and assessment of the impact of Country Risk. In the case of exceptional Country Risk events, dedicated analysis must be performed and reported to Senior Management and the Board. Pro-active mitigating actions must be identified to respond promptly to such events.
3.13Days-Past-Due: Each LFI must have a clearly documented policy compliant with these standards, addressing the method to count Days-Past-Due. Particular attention must be given to the re-ageing of Facilities, whereby the Days-Past-Due counter is reset at zero. This applies only to non-distressed restructuring as defined in these standards. At a minimum, the re- ageing policy must include:
a.The internal approval process and subsequent reporting requirements;
b.Eligibility criteria including minimum performance and a minimum age of a Facility to be eligible for re-ageing;
c.A maximum number of re-ageing occurrence per Facility; and
d.A process to reassess the Obligor’s capacity meet the new terms of its Credit Facility.
3.14Remediation: Any Obligor that has triggered the definition of Default must be managed by individuals not involved in the origination of that Credit Facility, including both relationship management and credit approver for that Credit Facility. The provisions related to distressed assets must be decided independently from the underwriting process. Consequently, each LFI must be in a position to demonstrate that (i) it complies with such independence, irrespective of its specific organization circumstances and (ii) management of provisions on distressed assets are determined according to the LFIs delegated authorities with the oversight of the appropriate committee, or for branches of foreign banks the delegated authority from the head office.
3.15Counterparty Credit Risk: The Credit Risk framework must be adequately designed to manage Counterparty Credit Risk (“CCR”) arising from all derivative transactions. At a minimum the following requirements apply.
a.Each LFI must have a centralised management and Risk Appetite pertaining to CCR across the entire LFI in order to manage the identification, measurement, monitoring, reporting and mitigation of such risk. At a minimum, limits must be established at Obligor level against potential future exposures arising from derivatives.
b.Reporting should include a consolidated view at Obligor level of exposures arising from derivatives and from other financial instruments such as Credit Facilities, bonds and/or Sukuks.
c.The framework must capture all the key drivers of CCR including, but not limited to: (i) current and future exposures, (ii) market risk drivers, (iii) client ratings, (iv) potential netting and collateral agreement, and (v) potential wrong-way risk. All these drivers should be included in the reporting framework.
d.The CCR framework must ensure that adequate legal documentation is place to manage and mitigate derivative exposures. Such documentation should be reviewed and approved by qualified internal or external legal teams.
e.The management of CCR must be supported by adequate documented methodology and analytical tools. Each LFI should identify, analyse and report the market risk factors driving the potential exposure and hence responsible for potential limit breach in the case of market volatility.
f.Finally, as CCR is driven by both Credit Risk and market risk factors, it is essential that the CCR management framework relies on appropriate collaboration and allocation of responsibilities between the Market Risk function, the Credit Risk function and the business lines.
Risk Mitigation3.16Provisioning methodologies: LFIs must establish robust governance and control framework for the estimation and reporting of provisions, consistent with actual recovery of collateral if any, and must be able to substantiate the recoveries with documented evidence. This framework must include the minimum requirements of these standards and ensure that the LFI can demonstrate prudent and effective estimation and reporting of provisions.
3.17Collateral management: Policies must be in place to determine the preferred type of collateral (at a level of specification relevant to the nature of the collateral) and legal charge.
a.There must be robust processes and procedures relating to collateral management, which should be managed by a specialist team. These policies and procedure should include, where relevant, but not be limited to, filing of legal charges, ensuring legal enforceability in a timely manner, collateral valuation methodology and value monitoring, collateral insurance, possible assignment of income derived from any collateral and the ability to inspect the asset. For Wholesale exposures, the credit review function must approve changes in collateral valuation or legal enforceability.
b.The process must also include regular reviews of the performance of underlying assets in the case of securitization and asset-backed Lending/financing.
Risk Analytics
3.18Information systems: LFIs must implement effective information systems for the accurate and timely identification, aggregation, data storage and reporting of Credit Risk exposures to Senior Management and the Board on an ongoing basis. Such systems must cover exception tracking, limit breaches and early warning measures to ensure prompt action at the appropriate level of the organisation, when necessary. Processes must be in place to ensure the collection of adequate information on the composition of the credit portfolio, including key financial information, financing metrics and the Repayment history of each Credit Facility and facilitate active management of exposures creating risk concentrations and large exposures to single counterparties or groups of connected counterparties. Credit management systems must be of appropriate sophistication in order to facilitate this data collection and enable appropriate portfolio-level analysis across key risk drivers.
3.19Analytical tools: LFIs must implement analytical tools commensurate with the size and complexity of the organisation to support the measurement and reporting of Credit Risk and provisions. The design, management and validation of these tools must comply with Article 13 on Credit Risk models.
Exceptions3.20Exceptions management: LFIs must implement a clear process to adequately identify and manage exceptions from credit policies and underwriting standards. All exceptions must be reviewed and documented by the CRO. Conclusions and analyses must be supported by clear rationales, prior to submission for approval by the appropriate level of authority within the LFI. Such review and approval must be achieved at Credit Facility level for Wholesale Obligors and at portfolio level for Retail Obligors.
a.LFIs must define materiality criteria for each level of approval of exceptions to credit related policies. Depending on these criteria, exceptions must be approved by either Senior Management, the Credit Risk committee and/or the Board Risk Committee. These criteria must be documented and substantiated by a thorough analysis. Exceptions must represent only a small portion of the credit portfolio.
b.Any Credit Facility granted with deviations from either the credit policy, underwriting standards or Risk Appetite, must be subject to active monitoring and consolidated reporting to Senior Management and the Board on a regular basis. The CRO is responsible for the review, identification and escalation of exceptions to credit policy.
c.Any issuance or the acquisition of credit exposures in breach of the LFI’s Board approved Risk Appetite must always be formally approved by the Board and each approval must contain the written signature of every Board member involved in the approval process.
Article 4: Credit Risk Oversight Functions and Roles
4.1The corresponding Article of the regulation outlines the main principles. Detailed requirements are presented below.
Credit Review Function4.2Each LFI must have a CCO supported by a Credit Review function or equivalent to fulfil the duties as defined below.
4.3The CCO is required to review Obligors and associated exposures every year. For Wholesale Obligors, this review must take place at Obligor level. For Retail Obligors, this review must take place at portfolio level. This must include an updated risk rating of the Obligor(s) based on recent financials, at a minimum annually. LFIs must set the conditions triggering more frequent risk rating, and the conditions triggering technical amendments to a Facility.
4.4The CCO’s key responsibilities are as follows:
a.Heading the credit review function which will review all credit proposals.
b.Ensure that all credit proposals are:
i.Comprehensive and suitable to make a view on Credit Risk,
ii.In compliance with the underwriting principles in these standards, and
iii.In accordance with the Risk Appetite and underwriting standards of the LFI.
c.For approvals up to the authority level of the CCO, to review and approve each individual transaction either directly or in accordance with the LFIs approved delegation matrix.
d.For approvals required above the authority level of the CCO as per the delegation matrix, the CCO must submit credit proposals to the Credit Committee or its alternative.
e.Ensure that exceptions and their justifications are referred to the CRO for review.
f.The function responsible for underwriting Credit Risk must be independent of the business. Therefore, the CCO must not report to the head of a business line.
Credit Risk Management Function4.5In the context of credit acquisition, each LFI must have an independent Credit Risk Management Function within the Risk Management Function headed by the CRO.
4.6The Credit Risk Management Function, must not have a decision-making role in the acquisition of Credit Risk.
4.7The Credit Risk Management Function is responsible to safeguard the LFI from acquiring Credit Risk not consistent with the LFI’s Risk Appetite and/or policies, that may cause a threat to the LFI, in which case he must raise his concerns at the appropriate level.
4.8The Credit Risk Management Function has the responsibility and authority to protect the LFI from Credit Risk, while maintaining an arms-length and independent oversight of Credit Risk acquisition. To perform this duty, the Credit Risk Management Function must have the following powers and responsibilities:
a.To own the LFI’s Credit Risk policies. The Credit Risk Management Function must define policies, procedures, systems and controls to monitor and report Credit Risk upon commencement of any Credit Facility, and throughout the Credit Risk life-cycle.
b.To ensure that the Credit Risk management framework, and/or any subsequent change is adequate to meet the aforementioned objectives.
c.To ensure that Credit Risk is identified, measured, reported, mitigated, and remains within the LFI’s Risk Appetite. To ensure that, for material Facilities, the metrics pertaining to Credit Risk provision and capital are accurately reflecting the Risk Profile of these Facilities.
d.To review material defaulted Credit Facilities and the associated rationale for provisioning based on appropriate discounted future cash flows and eligible collateral, in compliance with relevant regulations. For this purpose, materiality is defined by each LFI.
e.To ensure that regular updates are provided to Senior Management and the Board or to a Board Committee as per a pre-established schedule, or more frequently when required. Such reporting must cover the portfolio Risk Profile, exceptions and early warning signals.
f.The authority to attend credit committee meetings as a non-voting member. The right to be fully informed of all proposals, renewals, amendments to acquire or renew Credit Facilities.
4.9The CRO has the following powers and responsibilities with regard to Credit Risk:
a.To ensure that the LFI has adequate resources and skilled employees dedicated to Credit Risk management.
b.To ensure that the approved Credit Facilities conform to the Board approved Risk Appetite of the LFI. For this purpose, the CRO must undertake prior reviews of all material credit applications and renewals in order to express and document independent views on their Risk Profile in the context of the LFI’s Risk Appetite and policies, and communicate these views to Senior Management and the Board.
c.The Board of the LFI must establish formal materiality thresholds (based on the total exposure amount) above which the CRO review must take place.
d.At a minimum, the materiality threshold must include the following principles.
i.The CRO must review all Credit Facilities requiring approval from the Senior Management credit committee or equivalent, and above.
ii.For Credit Facilities considered as higher risk (this must include at a minimum all Credit Facilities rated non-investment grade or equivalent) by the LFI, the materiality threshold for the CRO review must be set at 20% below the delegated authority of the Senior Management committee or equivalent, i.e. a delegated authority of AED 100 million means a threshold of AED 80 million and above for high-risk Facilities to be reviewed by the CRO.
iii.For Wholesale Obligors, the review must take place at the Obligor level.
iv.For Retail and SME Obligors, the review can be performed at portfolio level or individual level, provided that the LFI outlines its approach in its policy.
e.The power and the responsibility to veto credit proposals when necessary in accordance with his responsibilities. In the case of veto:
i.If the observations are fully addressed and formally agreed to by the CRO, the transaction may be re-submitted to the relevant approvers.
ii.If CRO’s concerns are not fully addressed, the proposal must not proceed without escalation to the Board for approval. The proposal should contain the reasons to support the transaction and include the rationale for the veto from the CRO.
4.10In the case of LFIs offering Islamic Financial Services, the Credit Risk Management Function must discharge its responsibilities in compliance with the Shari’ah rules and principles.
Article 5: Credit Underwriting
5.1In order to comprehensively address the Risk Profiles of its portfolios, each LFI must operate with a sound and granular credit underwriting policy based on its Lending strategy in accordance with its Board approved Risk Appetite. The Risk Appetite and the credit underwriting policy must incorporate sufficient risk-return discipline, consistent with the LFI’s business model.
5.2The underwriting process must ensure a thorough understanding of the Risk Profile and characteristics of the Obligors and the drivers of their credit performance. For that purpose, the LFI must establish well defined criteria within its policies and processes for approving new Facilities, renewing and refinancing existing Facilities. This decision process must be supported by a clearly defined approval authority based on the size and complexity of the Facilities.
5.3Materiality thresholds must be established to govern decisions surrounding the issuance of each Credit Facility. All financing to existing and new Obligors must be assessed against risk acceptance criteria during the initial credit evaluation process and during the continuous Obligor/portfolio monitoring phase, as per Article 3.12.
5.4LFIs must ensure that the underwriting framework and respective criteria, policies and procedures are implemented effectively and are subject to regular audit reviews.
Decision-making process
The decision-making process must include the following key elements:
5.5Credit Committee: Decisions to issue Credit Facilities are expected to be governed by a management credit committee or individual(s) with the appropriate sanctioning authority where appropriate. The credit committee is expected to be a forum to analyse and discuss in detail the risk drivers, the pricing and the structure of Credit Facilities or, pools of Credit Facilities. Robust documented evidence must be retained to demonstrate that underwriting decisions are sufficiently challenged. Underwriting decisions must clearly document an appropriate balance between risk and commercial considerations.
5.6Depending on their materiality, their rating and other criteria, some Facilities may be delegated for approval at levels of authority that report to the CCO and are below that of the credit committee. However, those delegations must be clearly documented and approved.
5.7As an alternative to a credit committee, LFIs may structure underwriting approvals through individual delegations, however they must have in place a clearly documented and approved delegation matrix setting out delegations from Board level down to Senior Management (excluding control functions), CCO and individual credit officers.
5.8LFIs must ensure that the approval of Credit Facilities is achieved through a continuous accountability framework for each step of the underwriting process. LFIs must define the roles of executive committees and senior executives involved in the process of underwriting of Credit Facilities.
The following principles apply:
a.The Board and/or Senior Management must be directly involved in the approval of Credit Facilities with the following characteristics: (i) materially large Facilities relative to the LFI’s capital and (ii) Facilities with a high Risk Profile as explicitly defined in the policy.
b.The authority to approve Credit Facilities must flow through a mandate from the Board of directors or a designated body in the Board. The delegation must be vested with the highest executive committee/individual in the LFI that oversees the underwriting of Credit Facilities.
c.The delegation process must consider, at a minimum, the Obligor risk captured by Obligor rating, Facility amount and structure, the experience and qualifications of staff, the business segment of the Credit Facility to be approved, and the ranking of the financial obligation.
d.The staff delegated to make credit decisions have the adequate level of experience, qualifications and abilities.
e.The individuals responsible for underwriting must remain accountable for their decisions and should be subject to performance indicators reflecting the quality of their underwriting decisions.
5.9LFIs must establish a performance assessment mechanism for all stakeholders involved in the acquisition and the management of Credit Risk which is aligned with the long term sustainability of the LFI. The mechanism must be articulated differently for the business lines and the control functions, based on the following principles:
a.The mechanism must enforce accountability amongst employees who make decisions that commit the LFI over several years and/or that result in material risk taking activities.
b.All internal employees involved in the acquisition and the management of Credit Risk including employees from the business lines must be subject to key performance indicators reflecting the quality of their underwriting decisions i.e. demonstrated by the credit worthiness of the Obligors after the underwriting process.
c.Each LFI should put in place deferred compensation mechanisms that align with the risk outcomes for the employees who benefit from the completion of large transactions that expose LFIs to long term risks.
d.Staff in the control functions involved in Credit Risk management must be compensated in a way that makes their incentives independent of the performance of the business. Their performance incentives must be based on achievements assessed against the objectives of the control functions, so as not to compromise their independence.
5.10Independence: All credit decisions must be made free of conflicts of interest and on an arm’s length basis. In particular, Related Party transactions must be governed by internal policies, to prevent potential conflicts of interests. They must be authorised by the Board of the LFI, and regularly monitored. The policies and processes must be articulated so as to prevent persons benefiting from the transaction and/or persons related to such a person from being part of the process of granting and managing the transaction. All Credit Facilities to Related Parties must be formally approved and signed-off by each Board member.
Key components of underwriting5.11The underwriting process must be structured to adequately support the decision-making process for the issuance and the acquisition of Credit Facilities, consistent with the LFI’s Risk Appetite and strategic objectives. The underwriting process must enable the LFI to form a view on the suitability of the Risk Profile of each Credit Facility in light of the associated risk-adjusted return objective of the LFI. Consequently, this process must be clear and comprehensive, fully documented, and enforced in accordance with its internal policy.
5.12In addition, the underwriting process is expected to include the following at a minimum:
a.Limits: The underwriting process must be controlled adequately with Risk Limits established at a suitable level of granularity. LFIs must establish overall credit limits at the level of individual Obligors and counterparties, and groups of connected counterparties that aggregate different types of Credit Facilities in a comparable and meaningful manner. The limits must be structured around the drivers of Credit Risk, including but not limited to Obligor rating, industry type, product type, geography, Credit Facility tenor and Credit Facility structure. LFIs must define acceptable terms in accordance with the limits, (for example: Credit Facility covenants, legal requirements, leverage, tenor, amortization, pricing and/or minimum security).
b.Due diligence: LFIs must ensure that they implement a robust and comprehensive credit due diligence process (including legal aspects as appropriate) in order to fully capture all the relevant information necessary to assess the Obligors’ credit worthiness. They must demonstrate a robust documented understanding of the purpose of the Credit Facility and the associated risk measured by key financial parameters such as leverage, debt service coverage ratio, liquidity, net worth and operating cash flows. This process must include quantitative and qualitative information over a period of time suitable to make informed credit decisions. It must also cover the assessment of the ownership structure of the Obligor and related group and the identification of the ultimate beneficial owner. Finally, LFIs must define a set of criteria triggering an enhanced due-diligence process with a larger and deeper scope of investigation.
c.Risk drivers: The underwriting process must incorporate a comprehensive identification and analysis of the key drivers of Credit Risk, typically separated into systemic risks and specific risk (or ‘idiosyncratic’ risk). Systemic risks should include Country Risk and industry risk. Specific risk should include business risk, financial risk and management risk.
d.Financial information: LFIs must collect comprehensive financial information and cash flow projections from their Obligors, contingent Obligors and guarantors. They must ensure that the due diligence process captures all financial obligations of their Obligors (including other LFIs and Related Parties). LFIs must refrain from making underwriting decisions mostly based on subjective information.
In addition, for Wholesale Obligors:
i.Credit analysis must be forward-looking incorporating macro-economic forecasts considering business cycle effects, the sector in which the Obligor operates, the Obligor’s relative position and expertise within that sector and associated downside scenarios.
ii.Affordability analysis throughout the Credit Facility should include a sensitivity analysis based on stressed market benchmark rates and profitability.
iii.For Credit Facilities that are not fully amortising, an assessment of the LFI’s exposure to re-finance risk, including possible exit options for the LFI, should be undertaken.
iv.The LFI should have a formal documented process to ensure that the financial analysis of an Obligor is based on financial statements that have been audited by reputable auditing firms.
5.13Documentation: The credit files must be well documented and include all information necessary to ascertain the current financial condition of the Obligor, including but not limited to the rationale and computations upon which classification and provisioning has been determined. In addition, files must contain sufficient information to track the decisions made and the history of the credit. For example, the credit files should include current financial statements, financial analyses and internal rating documentation, internal memoranda, reference letters, appraisals and forward-looking financial projections. The credit review function must determine that the credit files are complete and that all Credit Facility approvals and other necessary documents have been obtained. Documents must include the evidence of the perfection of the LFI’s legal interest as well as evidence of the ability to collect / exercise their creditor interest in collateral taken in support of the Credit Facility.
5.14Collateral: LFIs must ensure that the collateral used as risk mitigant in the underwriting process is appropriately identified and valued. In addition, LFIs must monitor, control and assess the implications of multiple Lending against the same collateral. For that purpose, the following actions must be undertaken, at a minimum:
a.When appropriate, LFIs must ensure that collateral used as mitigation are registered with the relevant official body: (i) the land department for real estate collateral and (ii) the Emirates Integrated Registries Company LLC for other collateral.
b.The types of collateral covered in the registers are likely to evolve through time. Therefore LFIs must verify all collateral types.
c.Prior to the disbursement of any secured Lending, LFIs must verify the registration of collateral and ensure that the priority of their claim is reflected in underwriting and provisioning.
5.15Facility structure: LFIs must ensure that amortization schedules and Facility tenors are suitably designed to meet the needs of Obligors and their Repayment abilities. The amortization structure should include the following principles:
a.The depth and breadth of credit analysis should increase with the Facility tenor, i.e. additional justifications and business rationale should be provided to support Facilities with long tenors.
b.The Repayment schedule should match the business cyclicality.
c.Tenors and amortization profiles should be within acceptable Risk Appetite and risk-reward relationship.
d.In the case of project finance, the Repayment schedule should match the expected development schedule of the project.
5.16Legal due diligence: The LFI must ensure that the legal documentation of the Credit Facility is adequate to support the right of the LFI over the recoverability of the debt, including but not limited to, the liquidation of collateral, enforceability of guarantees, access of overseas assets. In addition, the LFI should review and evaluate the right to use Credit Facilities as collateral to raise liquidity, and ensure the conclusions of such evaluation are reflected in the legal documentation.
Article 6: Definition of Default
6.1LFIs must employ the criteria presented herein to identify an event of Default. These are applicable to all Credit Facilities and all Obligors, including Retail Obligors and Wholesale Obligors. For Islamic Financial Services, the definition must also comply with Shari’ah requirements including the Shari’ah contract terms and conditions.
6.2In the case of Default measurement, each LFI must monitor and assess the Defaults of Obligors by considering the obligation of a given Obligor across all the legal entities of a banking group incorporated in the UAE and abroad, including the Parent company, its branches and Subsidiaries.
6.3A Default is considered to have occurred with regard to a particular Obligor when either or both of the following events have taken place: non-payment and/or unlikeliness to pay.
Non-payment
6.4The Obligor is Past Due for a period greater than 90 days on any material credit obligation to the LFI. In this context, materiality must be measured with respect to the total exposure of the individual Obligor. A Facility or a group of Facilities with an Obligor is considered material if their combined exposure is greater than 5% of the total funded exposure of that Obligor to the LFI. In the case of multiple Credit Facilities, for Wholesale Obligors, the Days-Past-Due (“DPD”) counter must start from date of the first Credit Facility becoming Past Due. In other words, the DPD counter must be computed across Credit Facilities with a consecutive day count.
6.5Overdrafts will be considered Past Due once the Obligor has breached a contracted or internal limit, or been advised of a limit smaller than the current outstanding. In addition, Default must be considered when the outstanding balance is consistently in excess of the agreed upon limit. ‘Consistently’ is defined as a period that exceeds 90 continuous days, in addition, for Wholesale Obligors only, a total of more than 90 days in any 6 months period.
Unlikeliness to pay6.6The LFI considers that the Obligor is unlikely to pay its credit obligations in full. This evaluation should be based on a holistic evaluation of creditworthiness supported by factual evidence, whereby the LFI must forms a balanced view on the current and future overall performance of the Obligor. The classification of an Obligor as ‘defaulted’, due to a perceived unlikeliness to pay, is not automatic.
6.7For the purpose of the evaluation of the unlikeliness to pay, LFIs must establish a set of criteria, including the requirements provided herein. These criteria would be most applicable to Wholesale Obligors with high Credit Risk, such as Obligors involved in Facilities with Interest only obligations, Obligors that are routinely Past Due with Repayments and/or Obligors with a bullet Repayment at maturity.
6.8Indicators of unlikeliness to pay may include, but are not limited to, the indicators listed below. LFIs must clearly evaluate and document whether any of these situations apply (or others specific to the LFI) prior to forming an overall conclusion on the likeliness to pay of the Obligor:
a.The LFI makes an account-specific provision due to a significant decline in credit worthiness of the Obligor, subsequent to the origination of the Credit Facility.
b.The Interest and/or fee relating to the Credit Facility is Past Due more than 90 days.
c.The LFI sells part of a Credit Facility at an economic loss exceeding 30% of the amount which is the greater of the current outstanding balance and the net present value of the Credit Facility.
d.The LFI has filed for the Obligor’s bankruptcy or a similar order with respect to the Obligor’s obligation to the LFI. Alternatively, the Obligor has become insolvent, has sought voluntary liquidation, or has been placed into bankruptcy by any other party.
e.The Obligor is classified as defaulted by another LFI.
f.There is evidence that the Obligor is capable but unwilling to meet its contractual credit obligations.
g.The LFI has to liquidate collateral due to a decline in the Obligor’s credit worthiness.
h.The Obligor is classified in the default grade by approved credit rating agencies included in the Capital Adequacy Regulations.
i.Material concessions to the Credit Facility’s original contractual obligations have been granted formally in writing, or informally, in the context of a restructuring, including but not limited to a bullet Repayment, significant grace periods, payment holidays or low Repayment at the beginning of the Repayment schedule.
j.For Wholesale Obligors based in the UAE, one of the owners of the company has left the UAE without a clear rationale, for a period greater than 6 months.
6.9For Wholesale Obligors in particular, unlikeliness to pay can be indicated by a clear material decline in credit worthiness evidenced by the following circumstances:
a.A significant deterioration in financial performance of the Obligor leading to financial difficulty,
b.A high likelihood that the Obligor will enter bankruptcy or other material financial reorganisation,
c.Crisis in the Obligor’s sector,
d.A breach of a material covenant included in the Credit Facility structure.
e.Repeated restructurings granted to the Obligor due to financial difficulties faced by the Obligor,
f.The Obligor’s sources of income to repay the Obligor’s Credit Facility are no longer existent or are distressed,
g.A significant deterioration in the quality of Obligor’s operating assets leading to an inability to operate these assets efficiently. For asset-based Lending, this should include the ability of the assets to generate sufficient cash flows,
h.A significant deterioration in the value of collateral,
i.Pending litigations or regulatory changes resulting in material negative consequences,
j.The Default of a Subsidiary for which the Obligor provides a guarantee,
k.A loss of key staff to the Obligor’s organisation,
l.Breach of major terms and conditions of the Facility and/or practice of non-payment on due dates,
m.For Wholesale Obligors, maintaining a material overdraft constantly up to or above limits with limited and irregular inflows, or
n.Other circumstances and external factor that would affect the Obligor’s ability to repay.
6.10For Retail Obligors in particular, the LFI should introduce a process to identify and evaluate Obligors that may be unlikely to pay based on specific circumstances of the Obligor, including, but not limited to, the following:
a.The Obligor’s sources of income to repay the Credit Facility are no longer existent or are distressed,
b.The regulatory Debt Burden Ratio (“DBR”) and/or internal DBR limits if more stringent is breached or likely to be breached when undertaking appropriate stress tests,
c.For Obligors/Obligors based in the UAE, the Obligor/Obligor has been absent from the UAE and not contactable for a period greater than 3 months, with an outstanding balance on a Credit Facility,
d.There is a significant deterioration of collateral whereby the value of the collateral falls below a predetermined minimum level, for example a significant fall in residential real estate values that brings the loan/financing-to-value (“LTV”) of mortgage loans/financing above regulatory and/or internal limits.
Cross Default
6.11Retail Obligors: The definitions of Default must only apply at Credit Facility level, therefore cross-Default does not apply automatically. The Default of a Credit Facility must neither trigger the Default of the individual Obligor nor the Default of other Credit Facilities granted to the same Obligor unless warranted due to actual Default on each Credit Facility.
6.12Wholesale Obligors: The Default of a material Credit Facility must also trigger the Default of the Obligor. In the context of an economic group composed of multiple legal entities, and in the absence of explicit consideration of cross-Default in the legal documentation of the Facility, then the following principles must apply.
a.LFIs must establish appropriate Credit Facility materiality thresholds and/or criteria, above which cross-Default should be considered and analysed.
b.Cross-Default must not automatically apply between an Obligor and its Parent entity or other entities of the group, if the Repayment of the Obligor Facility has no legal or economic dependency towards the Parent entity or any other entity of the group, or where the Repayment of the Credit Facility is only linked to the cash-flow of a specific, clearly defined project of the Obligor.
c.Cross-Default must apply if the Repayment of the Credit Facility is economically dependent on the performance and cash-flows generated from the consolidated economic group. In this case, Default on a material Credit Facility under the economic group must trigger the Default of all Credit Facilities and entities within the economic group.
d.If the Obligor is benefiting from a guarantee from its Parent company, then the Default of the Parent company must not automatically trigger the cross-Default of the entity benefitting from the guarantee. Consideration should be given to assess whether the Obligor can continue to operate without this guarantee under the terms of its financial obligations. However, the rating of the Obligor must be immediately reassessed without the presence of the guarantee and amended if necessary.
Article 7: Significant Increase in Credit Risk
7.1The LFI must assess and document regularly whether the Credit Risk of a financial instrument has increased significantly since its initial recognition. The identification of Significant Increase in Credit Risk (“SICR”) must be done in accordance with accounting standards, the LFI’s internal policy on SICR and must incorporate the requirements presented in these standards. It must be based on all available, reasonable and supportable information; including forward-looking information. The identification of SICR must be employed by LFIs to determine the staging of Obligors and Facilities as explained in Article 9 below on classification and provisioning.
7.2The indicators employed for the identification of a SICR must be regarded as early warning indicators to the identification of the Obligor’s unlikeliness to pay, articulated earlier in this regulation and the these standards. Consequently, for Obligors subject to a SICR, the identification process must also consider the possibility of a further deterioration in credit worthiness leading to unlikeliness to pay. Such analysis must be fully documented. Wholesale Obligors must be considered individually not as a portfolio.
7.3Each LFI must review forward-looking information and determine appropriate indicator to determine if an SICR has occurred. Those indicators must include, but not be limited to, the number of Deferrals granted to the Obligor and the Days-Past-Due.
7.4For each Obligor, LFIs must implement a rigorous process to regularly assess whether a SICR has occurred. This process can be based on information at the level of each Credit Facility or at pool or portfolio level. If an LFI decides to set its SICR criteria threshold at the level of a group of Credit Facilities, the Facilities within that group must have similar Credit Risk drivers.
7.5LFIs must ensure that the assessment of SICR is applied at different levels of granularity for connected financial instruments, e.g. Credit Facility level, Obligor level and/or group level. Such assessment must be documented.
7.6As a precursor to SICR, LFIs should implement a watch list mechanism, employed for forward-looking Credit Risk management, appropriate to the size and complexity of the LFI.
7.7Deferral indicator:
a.Any individual Credit Facility of a Wholesale Obligor, subject to 3 or more Deferrals of instalments due in a rolling 24-month period, must be identified as a deteriorating asset and therefore subject to SICR, unless there is supportable and documented evidence that no SICR has occurred. This requirement applies to Credit Facilities that are material to the LFI for a given Obligor, i.e. Credit Facilities representing more than 5% of the total Obligor’s financial obligations to the LFI.
b.If the Obligor has 3 or more Deferrals of consecutive instalments then the days-past-due counter commences from the original due date of the first deferred instalment. Relevant classifications and required provisions must be applied on the basis of this day count.
7.8DPD indicator: Credit Facilities with Repayments more than 30 Days-Past-Due must be identified as deteriorating assets and therefore subject to SICR. If the 30 Days-Past-Due presumption is rebutted, this must be fully documented with reasonable and supportable information evidencing that no SICR has occurred.
7.9Other indicators: For all Obligor types, in addition to the Deferral indicator and the DPD indicator, LFIs must review forward-looking information to determine if a SICR has occurred. Such a review must include a comprehensive assessment of quantitative and qualitative drivers of Credit Risk associated with each Obligor. This assessment must be fully documented and retained as evidence. During this assessment, it may not be possible to identify a single discrete event. Instead, the combined effect of several events can cause a SICR.
7.10Exceptions: For a Credit Facility where it has been determined that no SICR has occurred despite being triggered by the indicators above, such evidence must be formally evaluated and agreed upon by the CCO and CRO before being formally approved at the most Senior Management committee.
7.11For Wholesale Obligors, relevant indicators of a SICR may include, but are not limited to those outlined below. LFIs must be in a position to demonstrate that they have analysed these elements:
a.Deterioration of financial performance, including but not limited to, actual or expected decline in revenues or margins, increase in operating risks, deficiencies in working capital, breaching/deterioration of quantitative Credit Facility covenants and/or rising liquidity risks.
b.Deterioration in the value, quality or income-producing ability of the Obligor’s assets, increase in balance sheet leverage and/or negative equity. Deterioration in the ability of the Obligor to utilise its assets, for instance caused by the loss or damage of these assets.
c.Deterioration in the competitive position of the Obligor. Disruption in the position of the Obligor vis-a-vis its clients and/or suppliers. Disruption in the business and/or economic conditions, in particular, bankruptcy of a counterparty, economic difficulty in the sector in which the Obligor operates, particularly when taking into account the Obligor’s position in that sector.
d.Ineffective governance, sudden management changes, sudden change in the scope of business or organizational structure (such as the discontinuance of a segment of the business) that can result in a significant change in the Obligor’s ability to meet its obligations.
e.Downgrade of the Credit Facility in publicly available information from external parties, such as rating agencies and/or a credit bureau.
f.Any other contributor to deterioration in credit worthiness, such as the following:
i.Unavailable/inadequate financial information and/or financial statements,
ii.Qualified report by external auditors,
iii.Significant contingent liabilities,
iv.Pending litigation resulting in a detrimental impact,
v.Loss of key staff critical to the organization,
vi.Increase in operational risk and higher occurrence of fraudulent activities which are material to impact Repayment of Facilities,
vii.Continued delay and non-cooperation by the Obligor in providing key relevant documentation to the LFI.
g.Any other evidence that full Repayment of Interest and principal without realization of collateral is unlikely.
h.For Wholesale Obligors, where the majority owning Parent is showing stress such as SICR or worse, then there is a risk of diversion of funds from the Obligor, who should also be considered as subject to SICR.
7.12Economic environment: LFIs must analyse and document the relationship between macroeconomic conditions and Obligors’ Credit Risk drivers for the purpose of SICR assessment. This requirement applies to all types of portfolios. Such analysis can be performed at the level of individual Obligors or pools of Obligors, provided that jointly assessed Obligors share similar risk drivers. LFIs must also demonstrate that adequate economic analysis is performed to support this process. In addition to macroeconomic analysis, the SICR assessment must be supported by industry-level analysis, both current and forward-looking, including implications of any geopolitical, environmental and operating risks.
Article 8: Restructuring
8.1Article 8 of the Credit Risk Management Regulation requires LFIs to implement an appropriate process to identify, execute and manage Restructured Credit Facilities.
8.2For the purpose of this regulation and these standards, restructuring events are categorised into two distinct groups:
a.Distressed restructuring, and
b.Non-distress restructuring.
8.3Distressed restructuring: A Credit Facility must be regarded as a distressed restructuring if any of its terms are amended in a context of financial difficulty of the Obligor. This includes restructuring that commences or concludes after a Credit Facility becomes Past Due more than 90 days or falls within the unlikeliness to pay status. The assessment of financial difficulty must incorporate at a minimum the same criteria as outlined in this regulation and these standards for the assessment of SICR, and in particular the number of Deferrals as required by Article 9 on classification and provisioning.
8.4Non-distressed restructuring: A Credit Facility must be regarded as a non-distressed restructuring if any of its terms are formally amended for commercial or regulatory reasons, including the intention to mitigate future financial difficulties, but excluding situations of financial distress at the time of restructuring. Such type of restructuring includes Credit Facilities for which the contractual obligations and Repayments have been made, without any history of Past Dues on the Credit Facility.
8.5Examples of non-distressed restructuring are as follows:
a.A change in the contractual Interest rate to better reflect the credit worthiness of the Obligor and/or the market pricing,
b.A change in the contractual tenor and/or the Repayment schedule to better align such Repayments with the Obligor’s future cash flows. This includes restructuring for which early identification of a lower Repayment capacity from the Obligor is observed because inadequate terms for Repayment were originally approved, as long as there is no Default at any time during the restructuring process.
c.A change in the contractual tenor and/or the Repayment schedule to take into account a modification of the sources of income of a Retail Obligor in order to meet a debt burden ratio requirement. For instance, this may apply in the case of change in employment or voluntary early retirement.
d.Rescheduling prior to an event of Default, provided as a concession with a modification in the Repayment dates of the principal amount. However, when a Facility is rescheduled after a Default event as defined in Article 6, the Obligor falls into the distressed restructuring category described above.
8.6Restructured accounts also include cases where a Credit Facility is fully settled by a simultaneous or subsequent disbursement of a new Credit Facility.
8.7Standstill: In some circumstances, the restructuring process may take time to reach its completion. Such a situation is sometimes referred by LFIs as ‘standstill’. Any type of restructuring that is in standstill for more than 90 days, during which the Obligor is not meeting its financial obligations as per the terms of the original Facility, falls within the definition of Default defined above and, therefore, must be considered a Default event.
Restructuring Process
8.8The restructuring process must be defined by LFIs for Retail Obligors and Wholesale Obligors separately. All distressed restructuring must follow the principles described for remediation in Article 3.14. It must follow a rigorous governance with clear accountability and must be subject to annual internal audit review. The approving authorities (whether a committee or individual) of a restructuring must be accountable for ensuring compliance with the LFI’s internal policies and procedures.
8.9Approval process: LFIs must define a clear process to approve Credit Facility restructuring, including a clear delegation of authority to allow terms and conditions beyond the normal course of business. This process must mirror the process employed for issuing new Credit Facilities as articulated in Article 5 on underwriting principles.
8.10Eligibility of restructuring: LFIs must design and document minimum conditions to evaluate the viability of a proposed restructuring taking into consideration the following:
a.Criteria outlining the number of times a Credit Facility may be restructured. Robust underwriting practices suggest that the number of restructuring has a practical limit as eventually the LFI must suitably forecast the Obligor’s activity. The LFIs policy must deter restructurings that are poorly designed and not workable from the outset where the LFI can reasonably determine that the Obligor will not perform. LFIs must implement a documented framework to restructure Facilities to control such practice.
b.The economic rationale for not meeting the original Repayment schedule.
c.The viability of future Repayment plan.
d.In addition, certain causes of the Obligor’s financial distress requires a more in- depth assessment for the eligibility for restructuring. LFIs must identify these causes, including but not limited to,
i.Any occurrence of fraud by the Obligor in relation to past or present business or financial activities, and
ii.Any occurrence of fund diversion or inappropriate usage of funds by the Obligor.
8.11Credit Facility structure: The structure of a new Credit Facility must be designed to (a) maximise the Repayment likelihood from the Obligor while (b) minimizing the losses and expenses incurred by the LFI. LFIs must design and enforce a policy to govern restructuring principles, focusing on the amortization schedule and with adequate controls over unfunded Facilities. In the case of a deterioration in the Obligor’s credit worthiness, the extension of overdraft limits or other similar Facilities for the Obligor to repay existing Facilities should be treated as a strong indicator of distress restructuring.
8.12Viability analysis: For Wholesale Obligors in particular, LFIs must assess the viability of the Obligor upon restructuring by conducting a rigorous forward-looking analysis, based upon both quantitative and qualitative assessments. This must involve a transparent assessment of the economic environment, the state and prospects of the sector in which the Obligor operates, the Obligor’s position in that sector and the business conditions and the specific circumstances of the Obligor. The analysis must also include forecasted cash flows under several economic and business assumptions both baseline and stressed. The results must be presented to the credit committee as part of the decision-making process. The LFI must maintain and perform analysis on the Repayment history of the Credit Facility from inception of the original Facility.
8.13LFIs performing Islamic Financial Services must carry out the structuring process in accordance with Shari’ah rules and principles and take into considerations the controls imposed in doing so.
Article 9: Classification and Provisioning
Classification Principles9.1Each LFI must establish a process to assess, monitor and determine a classification to reflect the current and expected credit worthiness of each Credit Facility and/or each portfolio of Facilities, except for those measured at fair value. Upon this classification, LFIs must determine provisions based on the application of this regulation and these standards. This process must be proactive, forward-looking and supported by adequate policies, systems, data, analytical tools and by adequately trained employees.
9.2The classification process must be fully documented based on the provisioning policy approved by the Board, or in the case of foreign entities, the Board of the head office or the Senior Management committee of the branch.
9.3The classification process must be based on the assignment of internal risk ratings. LFIs must develop and utilize internal risk rating systems to manage Credit Risk. Where external credit assessments are used, the LFI must exercise appropriate due diligence to ascertain that the rating reflects the Risk Profile of the Obligor and the Facility. Particular attention must be paid to Credit Facilities that have been restructured and/or for which the outstanding Interest is capitalized. LFIs must be in a position to present evidence of undertaking this classification process to the CBUAE upon request.
9.4At a minimum, this classification process must incorporate the following elements:
a.The principles presented in these standards.
b.The regular review of exposure creditworthiness performed at Facility level, Obligor level and/or portfolio level, depending on the nature of the Obligor and the product type.
c.The regular update of internal ratings, at a minimum every 12 months. Such a review should take place more frequently in the case of credit related events. For Wholesale Obligors, such rating update must be performed at Facility level or Obligor level.
d.The early identification of deteriorating credit worthiness of a Credit Facility and the continuous oversight of such Credit Facilities.
e.The timely record of past-due information for all Facilities.
9.5LFIs must classify each Facility according to the three Stages and sub-Stages outlined below, inferred from accounting principles, whereby the likelihood of Default increases through the Stages. The classification described in these standards does not preclude LFIs from developing their own more granular and robust grading system, which must be clearly mapped to the categories outlined herein. The onus will be on the LFI to justify their assessment.
a.Stage 3: Defaulted Credit Facilities as per the definition of Default included in Article 6. In addition, this Stage is further split into three sub-categories as defined below, where each Obligor must be allocated based on his number of Days-Past-Due. Such a split is required for CBUAE reporting purposes.
Table 1: Stage 3 sub-categories, based on Days-Past-Due (DPD)
StageWholesale ObligorsRetail Obligors3.aNot Past Due but unlikely to payNot Past Due but unlikely to pay91 to 180 DPD91 to 120 DPD3.b181 to 365 DPD121 to 180 DPD3.c365+ DPD180+ DPDb.Stage 2: Credit Facilities subject to deterioration in credit worthiness as explained in the section on the SICR, included in these standards.
c.Stage 1: Any financial instrument not allocated to Stage 2 or Stage 3, that is currently fully performing and with robust expectation regarding the Obligor’s future credit worthiness.
9.6LFIs must establish a policy governing the criteria to allow migration between Stages. These must follow accounting principles, the principles articulated in Article 7 dedicated to SICR, and the rules as set out in this Article.
9.7Stage 3 to Stage 2: Credit Facilities must remain in Stage 3 until all arrears are settled. In addition, for Wholesale Obligors, at least 3 instalments must have been made for monthly Repayment schedule, and at least 1 instalment for any other Repayment schedule of longer intervals. Instalments must be composed of principal and/or Interest as per the original applicable Facility agreement, and must not be funded via a new Facility provided by the LFI or other means than the Obligor’s own cash flows.
9.8Stage 2 to Stage 1: For Wholesale Obligors, Credit Facilities must remain in Stage 2 until SICR criteria, as defined in Article 7, are no longer observed. In addition, each financial instrument subject to migration to Stage 2 must be monitored closely and remain in Stage 2 until the following Repayments of principal and/or Interest as per the original applicable Facility agreement have been met. This is referred to as the probation period. After completion of this period, the Facility can return to Stage 1. Interest-only payments are sufficient to migrate back to Stage 1 only if the original Facility agreement provided for a period allowing service of Interest only. The following minimum Repayment frequencies must be applied as from the date of last overdue instalment payment:
a.6 instalments in the case of monthly Repayment (i.e. 6 months),
b.2 instalments in the case of quarterly Repayment (i.e. 6 months),
c.2 instalments in the case of half yearly Repayment (i.e. 12 months),
d.2 instalments in the case of yearly Repayment (i.e. 2 years),
e.12 months minimum in the case of any other frequency.
9.9For step-up Repayment structures and working capital lines, the LFI must apply the above principles to formulate relevant staging criteria, including at a minimum: (i) longer periods may be considered for step Repayments, and (ii) a revolving working capital line would need to remain as Stage 2 until the renewals have been successfully completed during a minimum period of 12 months. However, in all cases, the LFI must re-evaluate the presence of SICR based on the criteria outlined in Article 7 and determine the staging accordingly.
9.10Where an Obligor or Facility was migrated from Stage 1 to Stage 2 for other reasons than missed instalments, then the minimum Repayment frequencies defined in Article 9.8 above do not apply for a migration from Stage 2 back to Stage 1. Instead, the LFI must methodically re-evaluate the presence of SICR based on the criteria outlined in Article 7 and determine the staging accordingly.
9.11Stage 3 to Stage 1: For Wholesale Obligors, financial instruments subject to SICR and allocated to Stage 3 must not be upgraded from Stage 3 to Stage 1 directly. Instead, the Obligor must be upgraded to Stage 2 initially and be subject to continuous monitoring for a minimum period corresponding to the Repayment intervals defined in Article 9.8.
9.12For Retail Obligors, LFIs must define minimum periods to govern the migrations between Stages for cases where their credit worthiness improves: (a) Stage 3 to Stage 2 (all arrears must be settled), (b) Stage 3 to Stage 1 and (c) Stage 2 to Stage 1. These minimum periods must be documented and justified based on the LFI’s business model.
9.13While the Stage 1, 2 and 3 defined above do not apply to derivatives transactions, LFIs must review and classify derivative transactions according to their associated Counterparty Credit Risk. LFIs must create their own appropriate classification based on counterparties’ credit worthiness and potential exposure. Such classification must enable the LFI to manage CCR in a proactive manner, with adequate early warning to manage credit deterioration.
Provisioning9.14All LFIs must implement a process to estimate and document provisions associated with each Credit Facility in all Stages and in all credit portfolios, in compliance with CBUAE regulations, standards and/or guidance. Such provision must be estimated during the life of the Credit Facility and assessed annually or more frequently in light of new information and the evolution of the economic and business environment. LFIs are required to book provisions in line with these standards and deduct them from the profit and loss account, at least by the end of each quarter and not delay them till the end of the financial year.
9.15Determining provisions in the context of Islamic Financial Services may impact the Investment Account holders’ profit as provisions are deducted from profit. Consequently, LFIs performing Islamic Financial Services must ensure that the Internal Shari’ah Supervision Committee approves the provisioning policies. In addition, the determination of provisions must be approved by the committee responsible for profit and loss allocation in accordance with the Central Bank’s standard regarding profit equalization for Islamic Banks.
9.16The provisioning process must be documented, organised and approved by Senior Management and the Board. At a minimum, it must incorporate the following components:
a.The history of classifications of existing Facilities and/or Obligors,
b.Robust methodologies and rating systems for the continuous assessment of Credit Risk arising from all financial instruments,
c.A process for the appropriate estimation of provisions supported by robust analytical solutions and systems commensurate with the size and complexity of the LFI,
d.A process to manage the quality of data used as inputs to the assessment of Credit Risk and provisions.
e.The regular estimation and reporting of key performance indicators (KPIs) relating to provisions and expected credit loss (ECL).
f.Regular back testing of expected credit loss (ECL) against historical losses.
9.17Retail Obligors: A provision of 100% of the Credit Facility net of collateral is required if the Obligor has permanently left the country where the Credit Facility was issued, without leaving sufficient funds with the LFI available to ensure the Repayment of the total outstanding. The above may not apply automatically and the LFI must evaluate the need for a provision for an Obligor who continues to service the Credit Facility from overseas and is not Past Due.
9.18Off-balance sheet items: For Wholesale Obligors, the LFI must undertake the following process, at a minimum.
a.Each LFI must estimate the likelihood that unfunded Facilities become on-balance sheet funded Facilities. For the purpose of provision estimations, it must then convert off-balance sheet Credit Facilities to on-balance sheet Credit Facilities. This process should be achieved by using credit conversion factors (“CCF”) at a minimum as prescribed in the CBUAE Capital Adequacy standards. Deviations are permitted once fully documented and approved by the appropriate governance level for each LFI. For Stage 3, if the LFI has determined that an unfunded Facility will not become an on- balance sheet Facility, then the LFI must document robust evidence supported by legal opinion to confirm such treatment.
b.Each LFI must identify and estimate its exposure to off-balance sheet Credit Facilities in the form of derivative contracts. Thereafter, the LFI must assess the net marked-to- market exposure to the Obligor, considering any enforceable netting arrangements in place and cash collateral received. The Counterparty Credit Risk arising from derivative transactions should be captured through the estimation of a fair value Credit Value Adjustment (CVA) reserve, in compliance with accounting principles. LFI must ensure that CVA is included in their Risk Appetite framework and CCR management process.
9.19Interest and fees in arrears: For all Credit Facilities with any instalments (including principal, Interest and other fees) more than 90 Days-Past-Due, the LFI must immediately set aside full provision at 100% of any Interest and fees not received. The provision must be deducted from current year income and the Interest and fees must not be included in income eligible for distribution. The income not received must be separately tracked and identifiable as a component of the gross outstanding along with the related provisions.
9.20Minimum provision for Stage 1 and 2: LFIs are permitted to estimate expected credit loss (ECL) and provisions via the quantification of probability of Default (PD) and loss given Default (LGD) incorporating CRM as determined by the LFI, but limited to the collateral and associated haircuts listed in the column labelled ‘up to 24 months’ of table 2 in Article 10. The quantification of PD and LGD must reflect the Risk Profile of each Credit Facility and/or portfolio and the experience of the LFI in terms of Default, collateral management and recovery collections. If the LFI incorporates risk mitigation as described in Article 10 for provision estimation, such mitigation must be based on robust and documented methodologies supported by data.
9.21LFIs must ensure that the total provision corresponding to all Stage 1 and Stage 2 Credit Facilities is not less than 1.50% of the LFI’s Credit Risk weighted assets as computed under the CBUAE capital regulations.
a.If the provision computed under 9.20 above is less than the aforementioned floor, the shortfall in provision must be deducted from current year income, similarly to all other provision requirements in this standard.
b.Alternatively, the shortfall amount in provision compared to the above-mentioned floor in this Article may instead be held in a dedicated non-distributable balance sheet reserve called the ‘impairment reserve-general’. The amount held in the impairment reserve-general must be deducted from the capital base (Tier 1 capital for Banks) when computing the regulatory capital.
9.22The CBUAE may impose a floor higher than that of 1.50% of Credit Risk weighted assets mentioned above at its discretion, for reasons including but not limited to:
a.Open high-risk observations from CBUAE regarding the models used in the estimation of expected credit loss (ECL); or
b.Insufficient assurance regarding the reliability or accuracy of relevant expected credit loss (ECL) models, such as due to shortcomings in compliance with the CBUAE Model Management standards or accounting standards.
9.23Minimum provision for Stage 3 (Wholesale Obligors): LFIs must implement a dedicated process and a methodology for the computation of provisions associated to Facilities allocated in Stage 3. The approach must incorporate the following elements.
a.The LFI must compute provisions after deducting, from the principal amount outstanding, the following items:
i.Eligible collateral as detailed in Article 10 after applying the relevant haircuts, and
ii.Any recoveries derived from expected cash flows supported by robust documentation and legal agreements as detailed in Article 10.
b.The provision computation must be based on the recovery and loss specific to each non-performing Credit Facility. For this purpose, the LFI is not permitted to use LGD derived from statistical models based on the LFIs generic recovery rates.
c.The calculation process, the methodology and the results must be reviewed and approved by the committee responsible for the oversight of provisions. This requires a formal review and support of the CRO at that committee. Ultimately, such provisions should be presented to the Board or delegated body of the Board, in accordance with the internal escalation policy of the LFI.
d.In addition, the LFI must ensure that minimum provision levels computed above are maintained against the principal of each defaulted Credit Facility and cannot be lower than the floors discussed below. (This excludes the income not yet received, which requires 100% specific provision). The application of the floors is defined separately for unsecured and secured exposures. These floors apply irrespective of the haircuts applied on collateral.
i.An unsecured exposure refers to an unsecured Facility or the unsecured portion of a secured Facility. A secured exposure refers to the portion of a Facility that is covered by an eligible collateral after haircut, as defined in Article 10 on CRM. The secured portion also means the part of the Facility equal to the value of the collateral after haircut.
ii.The application of the minimum provision is organised as shown in the table below. The unsecured portion is split in two sub-portions: (1) one part covered by expected cash flows (ECF), and (2) one part not covered by ECF. For the unsecured portion, the minimum provision floor is the higher of the minimum provision floor calculated based on the sub-portions and the minimum provision floor calculated for the unsecured portion as a whole1.
Table 2: Stage 3 minimum provision for Wholesale Obligors
Exposure portionsExposure sub-portionPortionsMin provision floorSub-portionsMin provision floorUnsecured portion25% for 4 years and 100% thereafterCovered by expected cash flowsNo floorNot covered by expected cash-flows100%Secured portionNo floor for 4 years and 25% thereafteriii.First, the LFI must apply a minimum provision of 100% corresponding to the unsecured portion that is not covered by expected cash-flows. Second, the LFI must apply minimum provision on the unsecured portion and secured portion respectively, as defined below.
iv.For each unsecured exposure, the provision must not be less than 25% of the unsecured exposure up to 4 years of becoming Stage 3, or from the date of issuance of these standards if it is already in Stage 3. After that date, any unsecured exposure must be fully provisioned at 100%.
v.For each secured exposure, the provision must not be less than 25% of the secured exposure after 4 years of becoming Stage 3. In this context, secured means mitigated by collateral as detailed in Article 10 on CRM.
e.The LFI must book provisions from the profit and loss account, at least by the end of each quarter and not delay them till the end of the financial year.
f.Provisions already held for Stage 3 accounts classified prior to the issuance of these standards may not be reduced, if the provision computed based on the requirements of these standards is lower.
9.24Minimum provision for Stage 3 (Retail Obligor): For Retail Obligors as defined in the standards, each LFIs must put in place a dedicated process and a methodology for the estimation of provisions for Facilities allocated in Stage 3. Each LFI must ensure that minimum provision levels are maintained against the principal of each defaulted Facility.
Table 3: Stage 3 minimum provision for Retail Obligors net of collateral, as per Article 10
Days-Past-Due / ClassificationUnlikely to pay and not Past Due91 to 120121 to 180180 +Sub-Stage3.a3.b3.cMinimum provision25% or higher25% or higher50% or higher100%Stage 3 provisions and accounting standards9.25If Stage 3 provisions computed under this standard exceed the provision computed under accounting standards, this shortfall in provision is required to be taken against current year income similarly to all other provision requirements in this standard.
9.26Prior to the issuance of this regulation, differences between the CBUAE regulatory provisions and accounting provisions were held in a dedicated reserve (‘impairment reserve – specific’). This methodology is now removed and not permissible. An LFI that has an amount in this reserve upon this regulation coming into force, must recalculate the provisions as per the requirements of this regulation and document for each of the exposures the changes relating to this regulation coming into force. The provisions calculated as per this regulation must then be charged fully through current year income, while simultaneously transferring the full balance of the aforementioned reserve back to retained earnings.
Restructured Credit Facilities9.27LFIs must pay particular attention to the classification of Restructured Credit Facilities as per the additional requirements articulated in the subsequent articles.
Classification of distressed restructuring9.28All distressed Restructured Credit Facilities for which the unlikely to pay criteria have been met, or that are Past Due more than 90 days at the conclusion of the restructuring process must be classified as Stage 3. Subsequently, staging transition rules must be applied as for any other Facilities.
9.29Any Credit Facility that has been restructured 3 times or more in a context of financial difficulty as defined under the SICR section of these standards must be migrated to Stage 3.
9.30All other distressed Restructured Credit Facilities not captured above must be allocated to Stage 2 or Stage 3. These also include Facilities where the restructuring has permitted payment of Interest only, whereby the requirement of principal Repayment has been removed; such Facilities remain as Stage 2 until such time that principal Repayment is resumed.
Classification of non-distressed restructuring
9.31All non-distressed Restructured Credit Facilities with a Repayment moratorium exceeding 6 months must be classified as Stage 2, unless the LFI can demonstrate that no SICR has occurred, in which case the same process as outlined under Article 7.10 must be followed. These Facilities must be reviewed annually by the CRO and any necessary action must be documented.
9.32All non-distressed Restructured Credit Facilities greater than 3 years in tenor after the restructuring and with a bullet Repayment, must be classified as Stage 2 at the start of the restructuring period, if any of these features are met:
a.For the purpose of these standards, a Repayment structure should be considered as bullet (balloon) Repayment if a material proportion of the principal Repayment is allocated at the end of the maturity of the Facility, in such a way that the ability of the Obligor to meet these annuity Repayments with its current cash flows is uncertain.
b.The bullet Repayment (or balloon Repayment) exceeds 40% of the outstanding. For the purposes of this limit, the bullet/balloon must be computed by combining any of the 3 largest Repayment amounts throughout the tenor. This does not apply to Facilities with formal UAE Local/Federal government guarantee or a UAE local Bank or bank guarantee rated AA or above.
c.Any non-distressed restructuring, without a bullet Repayment and without any Repayment moratorium can be allocated to Stage 1.
Applicable to all restructuring
9.33Subsequent to all distressed and non-distressed restructuring, the Facility/Obligor must be classified as Stage 3 if the definition of Default explain in these standards is met, at any time until the end of the restructured Facility.
Staging transitions for restructured Facilities9.34Stage 2 to Stage 1: Restructured Credit Facilities are subject to the same rules applicable to any other Credit Facilities for migration from Stage 2 to Stage 1.
9.35Stage 3 to Stage 2: For Restructured Credit Facilities classified in Stage 3, a return to Stage 2 is dependent on the proportion of the bullet Repayment:
a.Where a bullet Repayment (or balloon Repayment) represents 40% or less of the outstanding, the Facility will remain in Stage 3 until 3 instalments have been made and all arrears are settled. Instalments must be composed of principal and Interest. For the purposes of this limit, the bullet/balloon must be computed by combining the 3 largest Repayment amounts throughout the tenor.
b.Where a bullet Repayment (or balloon Repayment) represents more than 40% of the outstanding, under no circumstances may such a Credit Facility be migrated to Stage 1 even after being migrated to Stage 2. The Stage 3 classification will remain until the following Repayment of principal and Interest have been fully met by the Obligor (from its own funds without borrowing or financing from the LFI) and may then be reclassified as Stage 2.
i.6 instalments in the case of monthly Repayment (i.e. 6 months),
ii.2 instalments in the case of quarterly Repayment (i.e. 6 months),
iii.2 instalments in the case of half yearly Repayment (i.e. 12 months),
iv.2 instalments in the case of yearly Repayment (i.e. two years),
v.12 instalments in the case of any other frequency.
9.36The above criteria will apply to every subsequent restructuring.
9.37Particular attention should be paid to Facilities that are “Purchased or Originated Credit Impaired” or “POCI”. This process involves the de-recognition of the original Credit Facility and the recognition of a new Credit Facility, that is now credit-impaired. The new Credit Facility is recognised in the LFI’s financial statements at reduced fair value and routinely monitored for further deterioration in value with appropriate provisions made accordingly.
9.38For any of the cases outlined above, LFIs that extend further Lending/financing to a defaulted restructured Obligor must retain the Stage 3 classification for an additional 12 months to the timeframes outlined above.
1 For instance, assume a facility of 100, with a collateral of 60 after haircut, and 35 additional expected cash flows (ECF). For the first year, the secured portion is 60 and the unsecured portion is 100 – 60 = 40. The unsecured sub-portion not covered by ECF is 40 – 35 = 5, attracting a min provision of 5 (100%). Separately, the minimum provision for the entire unsecured portion is 40 x 25% = 10, which will be retained because it is greater than 5, i.e. the min provision on the unsecured sub-portion. Overall, the floor will be 10, for the first year. This estimation must be conducted again the following year with new collateral haircuts according to Article 10.
Article 10: Credit Risk Mitigation
10.1LFIs may account for the presence of CRM when determining the appropriate level of provisions, but only to the extent permitted as per these standards. The haircuts applied to collateral are only for the purpose of computing the provision amount; these haircuts have no impact on the legal rights of the LFI with respect to any collateral.
10.2The measurement of CRM must be based on realistic and documented assumptions supported by robust data, in particular for collateral valuation and discounted cash flows. The approach must include at a minimum the eligibility of collateral, recovery cash flows, time to recovery, the cost of recovery and the discounting method. The Credit Risk Management Function must review and form an opinion on the adequacy of the associated provisions from a risk perspective and escalate as appropriate.
Discounted future cash flows10.3Where LFIs take into account discounted future cash flows, these must be measured in a conservative manner. For Facilities to Wholesale Obligors in Stage 3 this must be done on a case-by-case basis and only to the extent as set out in the below Articles 10.4 to 10.6.
10.4Future cash flows of high certainty can be considered as forms of risk mitigation provided they meet the requirements herein. All cash flows used for risk mitigation must be discounted to the present and formally validated by external auditors, and hold a formal independent legal opinion to confirm the right of enforcement and ability to obtain those cash flows.
10.5Future rental income under a formal lease agreement, and with the rental income assigned to the LFI from commercial real estate under lien is permitted to be used as risk mitigation when computing the required provision. Other cash flows from defined and distinct sources may be considered within the principles articulated in Article 9.23.
10.6To be eligible for CRM, the future cash flows must not be from the same source as the cash flows expected when the Obligor failed to fulfil its Repayment obligation, unless legal certainty can be established regarding the recovery of such cash flows.
Collateral
10.7Collateral is eligible for risk mitigation if the LFI holds the first right of legally enforceable lien and if the collateral meets the minimum requirements presented herein. LFIs must implement processes and systems to identify, store, measure and monitor all collateral and guarantees linked to each financial instrument generating Credit Risk. LFIs must implement rigorous collateral management and valuation policies to ensure a fair assessment of CRM. They must also analyse and report concentration in some types of collateral and their associated Credit Risk, to Senior Management and the Board, as necessary.
10.8The value of the eligible collateral must be based on the net realizable value, market conditions and haircuts reflective of all material uncertainties, including but not limited to liquidation uncertainty, legal uncertainty, valuation uncertainty, costs associated with the liquidation of collateral and time value of money. At a minimum, LFIs must employ the haircuts in the table below for Stage 3 accounts. All items labelled as N/A in the table must be evaluated, documented and concluded upon on a case-by-case basis. This evaluation must rely on the principles above and specific provisions must be computed accordingly. The column labelled ‘up to 24 months’ also applies to Stage 1 and 2 as per Article 9.20.
10.9For Stage 3 classifications made prior to the issuance of these standards, the months should be counted from the date of issuance of these standards and not the original date of Stage 3 classification. In addition, collateral haircuts already applied by the LFI must be retained if they are higher than those specified in the table below. In other words, the LFI may not reduce the haircuts it has already applied prior to issuance of these standards. If the haircuts are lower than those specified below, they must be adjusted to meet these values.
Table 4: Minimum collateral haircuts
Eligible CollateralMinimum Haircut (months since becoming Stage 3)Up to 24 months*From 25 to 36 monthsFrom 37 to 48 monthsFrom 49 to 60 monthsAfter 60 months **Cash (or cash equivalent) in AED, currencies pegged to USD and cases where there is no currency mismatch between the Facility and the collateralN/AN/AN/AN/AN/AFederal Government (security or guarantee)N/AN/AN/AN/AN/ALocal Government (security or guarantee)N/AN/AN/AN/AN/AUAE licensed Bank (security or guarantee)N/AN/AN/AN/AN/ACash (or cash equivalent) Foreign Currency20%30%60%80%100%Foreign sovereign government bonds/Sukuk rated [BBB-] or above0%20%40%80%100%Foreign bank rated [AA-] or above (security or guarantee)0%20%40%80%100%Foreign bank rated [BBB-] or above but below [AA-] (security or guarantee)20%40%60%80%100%Listed shares on a recognized stock exchange20%40%60%80%100%Bonds or guarantees from corporations rated [BBB-] or above20%40%60%80%100%Aircraft, motor vehicles and boats/vessels20%40%60%80%100%Real estate20%40%60%80%100* For Stage 1 and 2, LFIs are expected to have a framework to compute adequate haircuts based on the Risk Profile of their portfolios. The haircuts in the column labelled ‘up to 24 months’ must be applied as minimum floor.
** In some circumstances, the haircut can be capped at the values corresponding to ‘from 49 to 60 months’, as per the table above, if the LFI has (i) a formal legal claim with respect to the liquidation of the specific collateral registered with the court, and (ii) an internal legal opinion confirming that the outcome of the legal process is likely to be in the favour of the LFI (i.e. greater chance of recovery than not).
10.10For Islamic LFIs, the collateral must be compliant with Shari’ah rules and principles.
10.11For some collateral types, the valuation method is subject to the following conditions:
a.Cash collateral is eligible only if it is held under a legally enforceable lien/pledge.
b.Listed shares, bonds and Sukuk are eligible if they are traded on a deep and liquid market. In this case, the average daily closing price over the previous one month must be used.
c.Real estate collateral criteria:
i.Real estate includes land and/or buildings.
ii.Incomplete properties must not be included as part of the valuation.
iii.For Wholesale Obligors, real estate assets are eligible if an independent third-party valuation has been performed. For Stage 3 Facilities, this valuation must have been performed within the last 12 months of the reporting date. The LFI must set materiality thresholds above which the use of desktop valuations is inadequate and a more comprehensive on-site evaluation is required.
iv.For Retail Obligors with residential mortgages LFIs must rely on at least one third- party valuation. For Stage 3 Facilities, a valuation must have been performed within the last 12 months of the reporting date. This may be supplemented with a framework to base valuations on appropriate house price indices.
v.For residential properties constructed by the borrower, LFIs may formulate a framework to value properties individually based on expert estimates of internal professional engineers and supported by municipality approvals.
d.Aircraft, motor vehicles and boats/vessels are eligible if an independent third-party valuation has been performed and the LFI must have a legal and enforceable charge over the item. For Stage 3 Facilities, the valuation must have been performed within the last 6 months of the reporting date. For motor vehicles, the original valuation with a formal depreciation methodology is an acceptable alternative.
10.12Any collateral held in foreign jurisdictions and booked in UAE is also subject to all the above requirements. In addition, to be eligible the following is required:
a.A formal legal opinion, obtained from a third party in that jurisdiction regarding the enforceability and validity of the legal charge by the LFI over the asset,
b.A formal legal opinion from the internal legal team of the LFI regarding the relevance and acceptability of the opinion formulated by the third party, and
c.A formal third-party independent valuation of the asset validated by the LFI’s external auditor.
Article 11: Portfolio Management and Internal Reporting
11.1LFIs must ensure that Credit Risk acquired through underwriting, refinancing and other mechanisms is fully monitored, reported and mitigated when necessary. For that purpose, LFIs must develop and implement comprehensive procedures, methodologies and systems to monitor the credit worthiness of each financial instrument, each Obligor, and relevant segments and portfolios. Such monitoring must cover all financial instruments and portfolios generating Credit Risk.
11.2Portfolio management must be integrated with the underwriting process so that information flows back and forth between the two processes. LFIs must demonstrate that the conclusions of portfolio management are used in the processes of risk acquisition.
11.3LFIs must review the performance of individual Wholesale Credit Facilities at least annually. The rating of all Credit Facilities and Obligors must be reviewed at least on a yearly cycle. More frequent reviews can be necessary depending on the individual circumstances of Obligors and on the economic environment.
11.4The monitoring process must incorporate steps to ensure that funds are used in accordance with the Facility legal agreement of each Obligor. The LFI must track the usage of the borrowed funds/financing proceeds and methodically identify their sources of Repayment. In the case of syndicated Facilities, it is the responsibility of each syndicate Lender/financier to understand the usage of funds via a monitoring process coordinated by the lead arranger.
11.5One of the key objectives of the monitoring process is to identify occurrences of fund diversion; that is situations where the disbursed funds are not used for the purpose originally intended. The monitoring process must incorporate steps to ensure that funds are used in accordance with the Facility legal agreement of each Obligor.
11.6Aggregation: The monitoring process must be performed at several levels of portfolio aggregation, so that segmentation leads to homogeneous pools of Credit Facilities with common risk drivers. LFIs incorporated in the UAE, which have branches and/or Subsidiaries, must capture and consolidate a group-wide view of Credit Risk. LFIs must implement robust systems and methods to aggregate Credit Facilities across the key risk drivers relevant to each LFI’s portfolio, including but not limited to, Obligor segments, rating grades, product types, collateral type, geographies, industries, Credit Facility maturity and Obligor metrics (e.g. LTV, DSCR, gearing, leverage).
11.7Data gathering: LFI must implement reliable and timely data processes to support appropriately portfolio management. At a minimum, LFIs must implement the following:
a.Robust systems and processes to collect and aggregate internal data in order to convey an accurate representation of Credit Facilities arising from all instruments across the organisation.
b.Robust systems and processes to collect, aggregate and process external data to support the accurate measurement of Credit Risk, including but not limited to, up-to-date financial information (including sector-specific financial performance), collateral data (including indices relevant to the collateral type) and Obligors’ performance against legal covenants, where applicable. The system should be able to present the portfolio’s Credit Risk Profile across a variety of underlying risk drivers, including those referenced in Article 11.6.
c.Historical Default rates and recovery rates must be collected for all material segments in order to support the accurate and prudent estimation of provisions.
11.8Analytics: LFI must implement adequate methodologies, models and analytical tools to identify and measure Credit Risk regularly at several levels of aggregation and segmentation. This assessment must rely on Obligors’ probability of Default, loss given Default, the size of their Credit Facility upon Default and the estimation of collateral values.
11.9Reporting: A robust reporting mechanism must be put in place to analyse the characteristics of credit portfolios and to communicate the observations and conclusion of credit reviews and analysis. Management information must be provided on a frequent and timely basis to the Board and Senior Management, in formats suitable for their use and understanding. As part of this the Board must be informed on: the Credit Risk Profile’s trend compared to the previous reporting period; and the change in underwriting standards, either through policy changes or actual practice, over time.
11.10Risk mitigation: Upon the review of the performance of individual credit instruments and portfolios, LFIs must have a robust process to discuss observations, escalate concerns and implement risk mitigating actions and corrective actions, such as an additional collateral request, a rating downgrade, Credit Facility restructuring, liquidation, sell-off, hedging, portfolio rebalancing, or any other action. Such process must be rigorously documented.
11.11Monitoring: LFIs must ensure the monitoring of the performance of each Credit Facility and Obligor upon restructuring. This process must be based on pre-defined indicators and limits specific to each Restructured Credit Facility. All distressed Restructured Credit Facilities must be subject to close monitoring as long as they remain distressed but not less than a minimum period of 12 months, supported by regular analysis and reporting. For Retail Obligors, LFIs can implement such enhanced monitoring of restructured Facilities at portfolio levels.
Article 12: Non-Performing Assets and Write-Off
Management of Non-Performing Assets12.1The Board and Senior Management of an LFI hold responsibility for the asset quality of the LFIs’ credit portfolios and the timely action to address credit-quality deteriorations. The Board must ensure that the LFI, at an early Stage, understands the underlying drivers of rising levels of non-performing assets and takes appropriate management actions in response.
Non-performing assets must be managed by individuals not involved in the origination of that Credit Facility in accordance with the requirements of article 3.14 of these standards.
12.2At a minimum, the strategy should be based on the following principles:
a.It should be integrated into the Credit Risk management policy of the LFIs and be reflected into its Risk Appetite.
b.It should include a plan to manage non-performing assets over the short, medium and long terms, based on the expected flow of new asset migration to Stage 3. The plan should be forward-looking based on future expectations about asset credit worthiness and recoveries.
c.It should define the conditions and expectations of forbearance.
d.It should have appropriate methodology and systems to monitor and value collateral in a timely fashion.
e.It should have appropriate legal expertise to support the recovery process.
12.3LFIs with elevated Stage 3 exposures will be subject to greater supervisory oversight. When at any time the total amount of Stage 3 exposures as a proportion of the total credit exposure of the LFI exceeds 5%, the Board must:
a.Formally explain to the CBUAE the underlying causes for the high stock of Stage 3 exposure, and
b.Approve and implement a comprehensive strategy to reduce the excess within a reasonable timeframe. Such a plan should include a detailed breakdown of Stage 3 exposures and be communicated to the CBUAE semi-annually.
Write-offs and Partial Write-offs of Non-Performing Assets
12.4When the LFI has no reasonable expectation to recover the full or part of a Credit Facility exposure as per the terms of the legal agreement, then the LFI should undertake a full or partial write-off of the exposure. A write-off constitutes a de-recognition event with the following financial implications: (a) any amounts written-off from the balance sheet must have an equivalent amount of provisions passed through the income statement; and (b) any amounts collected after the write-off must be recognised in the statement of profit and loss.
12.5Timing: LFIs must ensure that write-offs are timely and reflect realistic Repayment and recovery expectations. For that purpose:
a.LFI must define the maximum expected recovery time for collateralised and uncollateralised exposures. Beyond such time, write-offs must be implemented. The internally determined write-off period cannot exceed the maximum permissible period set by the CBUAE.
b.The LFI must not hold a Stage 3 exposure on the balance sheet for more than 5 years since the date of migration to Stage 3. After this time, such exposures must be subject to a full write-off in the accounts. Any exceptions to this should be subject to Board or appropriate Board Committee sign-off and oversight, based upon robust legal or accounting justification at the level of the Credit Facility, and supported by appropriate documentation available for review by the CBUAE. For the avoidance of doubt, such a write-off does not impede or limit the LFI from fully collecting the amounts due.
12.6Process: LFI must clearly define policies and processes to support write-off actions and the periodic review of Credit Facilities subject to partial write-offs. A write-off decision must include an assessment of legal and accounting consequences. For Islamic financial institutions, it must comply with Shari’ah principles. The ultimate authority for approval of write-offs rests with the Board or an appropriate Board Committee. At a minimum, the following drivers must be included in the LFI’s write-off policy, for the assessment of recoverability and write-offs:
a.Exposures with prolonged arrears: if the Obligor has been in arrears for a prolonged period of time, full or partial write-off should be performed based on realistic expectation of little recovery.
b.Exposures under an insolvency procedure: Write-off should be performed if the legal expenses are expected to consume the majority of the recovered amount.
c.Partial write-off: this may be justified when there is evidence that the Obligor is unable to repay the amount of the exposure in full and there is a reasonable expectation of recovering a part of the exposure.
12.7Insolvency process: Where a court appoints an administrator/expert to control the business, the LFI must assist in facilitating the recovery of any profitable business component, where applicable. This component may be ring-fenced as a viable business into a new entity to facilitate the recovery of the debt. Such matters must be handled by the function responsible for account remediation and recovery within the LFI.
Recovery of Non-Performing Exposures Post Write-off
12.8A write-off may take place before legal actions taken against the Obligor to recover the debt have been concluded in full. After any write-off, the LFI in all cases retains the legal right to recover the debt. An LFI’s decision to forfeit the legal claim on the debt is a separate consideration and requires approval from the Board or the relevant authority formally designated by the Board.
12.9An individual memorandum account must be maintained for every Credit Facility subject to write-off. This must also include accounts written-off on a portfolio-level basis. All recoveries made from the accounts subject to earlier write-off must be recognised in the statement of profit or loss. The summarized records must be maintained for the review of the CBUAE and to support claims in the courts. However, the LFI should close those memorandum accounts in the event of collecting the required amount or following a formal decision to discontinue the claims against these Obligors. The reporting of such accounts to CBUAE and other relevant bodies must be consistent with these requirements
Article 13: Credit Risk Models
13.1LFIs must have methodologies and analytical solutions to measure, analyse and categorise Credit Risk, and compute the associated provisions. LFIs must be able to analyse Credit Risk at several granularity levels including Credit Facility level, Obligor level, segment level and portfolio level in order to identify credit concentration risk.
13.2Each LFI must operate analytical tools with sophistication appropriate to the complexity of its portfolio, products, industries and other predominant factors. If an LFI does not use models for a given portfolio, then it must document and provide a rationale for such a decision.
13.3Where models are used for decision-making, LFIs must articulate clearly the roles of models for the support of Credit Risk underwriting, monitoring and provisioning. They must define the modelling strategies, the limits and conditions of model usage. Particular attention must be given to any overriding of model outputs. Such practice must be justified, fully documented and reported. High frequency of overrides of model outputs should be remedied by model recalibration or development.
13.4LFIs must establish an appropriate asset grading or classification system for the measurement of Credit Risk. All acquired and existing Credit Facilities must be assigned a rating grade based on robust justification and supported by historical analysis and analytical tools.
13.5When an LFI makes use of models for decision-making for credit purposes, it must also comply with the modelling standards and Guidance issued by CBUAE. In addition, LFIs must ensure the establishment of effective controls (including in respect of the quality, reliability and relevance of data and in respect of validation procedures) around the use of models to identify and measure Credit Risk and set limits. Each LFI must demonstrate that its models are fit for purpose and adequately calibrated to effectively support the associated risk and business decisions.
Other Topics
Regulation to Impose Financial Sanctions for Strict Liability Violations
CBUAE/BSD/N/2022/1452 Effective from 5/4/2022The Central Bank of the UAE (CBUAE) is pleased to announce the issuance of the ‘Regulation to Impose Financial Sanctions For Strict Liability Violations’ (the Regulation) (Circular No. 22/2021) under which financial sanctions are to be imposed on specific regulatory obligations.
The objective of the Regulation is to establish a regime for imposing financial sanctions on strict liability violations.
Once a violation has been committed, the appropriate financial sanction will be applied to the Licensed Financial Institution (LFI). No further enquiry, review, representations, or appeal process will be applicable.
The Regulation is annexed to this Notice and was published on 28th February 2022 in the Official Gazette and comes into effect one month after its publication.
All LFIs must on-board themselves onto the Licensing Automation Portal to ensure that they can gain access to the Strict Liability Regulation (UAESLR) portal.
All LFIs must create an internal email distribution list as follows. “UAESLR@<DOMAINNAME>”
The LFIs must include the names of the individuals responsible to be included on the distribution list. This email address must be created and communicated to the CBUAE no later than 13th April 2022. All further communication with regard to the UAESLR will be sent to the specified email address.
Introduction
The effective implementation of administrative and financial sanctions is necessary for the proper functioning of the enforcement of the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities as amended (the Central Bank Law).
The Central Bank Law set out the administrative and financial sanctions to be applied to Licensed Financial tostitutions. Those sanctions apply to all violations under the Central Bank Law and require a reasoned assessment of the appropriate sanction and the level at which it is to be applied٠ However, some violations, by their very nature, do not require such an assessment, as the responsibility on the Licensed Financial Institution to comply with the legal requirement does not necessitate any excuse or explanation, except in case of an event of force majeure. Such violations are strict liability violations.
Strict liability is imposed on elements of a variety of regulatory obligations. Typically, such obligations relate to routine, administrative activities that have to be performed often, if not at appointed periods of time. The repetitive nature of the activity does not however belie its importance on the regulatory obligation of the Licensed Financial Iostitutions.
Objective
The objective of this Regulation is to establish a regime for imposing financial sanctions for strict liability violations.
Once a violation has been committed, the appropriate financial sanction will be applied immediately and the Licensed Financial Institution will be informed accordingly. No further investigation, review, representations or appeal process will be applied.Scope of Application
This Regulation applies to all Licensed Financial institutions. It is issued in accordance with Article (137) of the Central Bank Law.
This following are referred to in this Regulation:
- Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities dated 30 September 2018, as amended;
- Regulation No. 29/2011 Regarding Bank Loans & Other Services Offered to Individual Customers dated 23 February 2011;
- The Standards for the Regulations Regarding Licensing and Monitoring of Exchange Business, dated February 2018 (The Standards);
- The Central Bank Notice No. CBUAE/BSD/N/2018/759 dated 23 May 2018;
- The Central Bank Document Code -UAEFTS-AUX804- Version 2017-001;
- The Central Bank Notice No. CBUAE/BSD/N/2018/758 dated 23 May 2018;
- The Central Bank Document Code - U.TS-AUX700- 2018-001-01 dated November 2018;
- The Central Bank Notice No. CBUAE/BSD/N/2019/2900 dated 18 July 2019;
- The Central Bank Notice No. 157/2013 dated 11 April 2013;
- The Central Bank Circular No. 13/189/2013 dated 2 December 2013;
- The Central Bank Notice No. CBUAEESD/2018/3004 dated 15 October 2018.
- Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities dated 30 September 2018, as amended;
Article (1): Definitions
The following terms and phrases shall have the definitions assigned to them for the purpose of this Regulation:
- UAE: The United Arab Emirates.
- Central Bank: The Central Bank of the UAE.
- Central Bank Law: Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organization of Financial Institutions and Activities, as amended).
- Licensed Financial Institution: as defined in the Central Bank Law.
- Working day/s: Monday to Friday excluding public holidays.
- The weekends: Saturday and Sunday.
- The Integrated Regulatory Reporting System: (https://131.5.15.15/cbuaeirr/) is a unified data collection & reporting framework to collect & analyse data submitted by all the Licensed Financial Institutions.
- Card Transactions: All cashless payment modes including but not limited to virtual wallets, digital cards, plastic cards e.g. debit cards, credit cards, store cards, prepaid cards and all other such card payments.
- ATM: Automated Teller Machine.
- CDM: Cash Dispensing Machine, Cash Deposit Machine, and/or Cheque Deposit Machine.
- CARD BINS: Bank Identification Number (“BIN”)
The terms mentioned in the Central Bank Law shall bear the same meanings ascribed thereto in the said Law when used in this Regulation, unless a definition otherwise is stated herein.
- UAE: The United Arab Emirates.
Article (2): Circulation of Counterfeit/Forged) UAE Currency
- The official currency of the UAE is the Dirham and the issuance of the currency shall be the exclusive right of the UAE.
- That right is exercised exclusively and solely by the Central Bank.
- Article 55 (2) of the Central Bank Law states that “No person shall issue or put into circulation Currency Notes, Currency Coins, or any instrument or token payable to bearer on demand having the appearance of, or purporting to be, or are likely to pass as, or be confused with legal tender in the State or in any other country.”
- Accordingly, all Licensed Financial Institutions are required to ensure that they do not circulate counterfeit and/or forged notes, at the point of collection or at the point of transaction or by delivery to its account at the Central Bank.
- If counterfeit and/or forged notes are circulated by the Licensed Financial Institution, whatever the circumstances, whether deliberately, recklessly or negligently, the Licensed Financial Institution will be in violation of Article 55(2) aforementioned.
- Currency notes or currency coins which are legally in circulation in the UAE but are subsequently withdrawn or replaced, are not counterfeit notes or counterfeit currency coins.
- Failure to prevent the circulation of counterfeit and/or forged currency will result in a fine of AED 10,000 for counterfeited note and/or currency plus the face value of the currency and/or currency coin.
- The official currency of the UAE is the Dirham and the issuance of the currency shall be the exclusive right of the UAE.
Article (3): The Court Cases Management System
- On 18 March 2018, the Central Bank introduced the Court Cases Management System, an automated process to facilitate the monitoring of the processing of court orders by stakeholders issued against all Licensed Financial Institutions operating in the UAE. The stakeholders are the courts under the Ministry of Justice, the Dubai Courts, the Ras Al Khaimah Courts and Prosecution and the Rental Disputes Centrel of Dubai.
- Despite the introduction of the Court Cases Management System, numerous orders, issued by different courts were not being processed in a timely manner.
- To address this matter, on 15 October 2018, the Central Bank issued Notice No. CBUAE/BSD/2018/3004, to inform the banks of their obligations to process court orders within the time limits set out in the Notice.
- The Notice also informed the banks that the Central Bank would send reminders about the court orders that become due and would take appropriate measures if no action is taken to comply with the Notice.
- Accordingly, failure to comply with the Notice will result in the Central Bank imposing a fine of AED 1,000 per violation against the concerned bank.
- A daily rate of AED 1,000 will be applied for the delay of each working day that continues after the violation, with a maximum threshold of AED 50,000 for each violation.
- On 18 March 2018, the Central Bank introduced the Court Cases Management System, an automated process to facilitate the monitoring of the processing of court orders by stakeholders issued against all Licensed Financial Institutions operating in the UAE. The stakeholders are the courts under the Ministry of Justice, the Dubai Courts, the Ras Al Khaimah Courts and Prosecution and the Rental Disputes Centrel of Dubai.
Article (4): Data Reporting on Cross Border Transactions (SWIFT Cross-Border Payment Transactions)
- The Central Bank has the mandate to prepare and publish the statistics of the balance of payments and the international investment position for the UAE in line with international standards.
- To enhance the quality of the data for cross-border transactions and ensure better control of the relevant flows, instituting a purpose of payment is critical. To that end, the Central Bank has established a mandatory requirement in its reporting process to capture the purpose of the payment for all cross-border transactions in a reliable and accurate way. This facilitates the collection of the required information directly from the customers of the Licensed Financial Institutions and facilitates the collection of information to account for all transactions in and out of UAE borders by residents of the UAE.
The Licensed Financial Institutions are required to provide customers with the full list of purpose codes as published by the Central Bank without merging or amending the list and to comply with the following requirements:
a) To provide purpose codes when initiating SWIFT cross-border payment transactions under Central Bank Notice No. CBUAE/BSD/N/2018/759 dated 23 May 2018; that is: “to assist the Central Bank in the compilation of the balance of payments, all SWIFT transfers messages need to include a payment purpose code according to the list of codes that are published on the Central Bank’s website under the balance of payments guidelines, along with a description, explanation by code and examples”;
b) To register for the Fin-toform services as required, enabling the Central Bank to collect information from the SWIFT messages initiated by the Licensed Financial Institutions as required, under Central Bank Notice No. CBUAE/BSD/N/2018/759 dated 23 May 2018, that is: “the Licensed Financial Institutions need to report to the Central Bank on a transaction by transaction basis:
i. Swift messages: All customer transfer messages between Licensed Financial Institutions from the UAE to overseas institutions in all currencies (Outflows) or from overseas institutions to the UAE (Inflows)
ii. Non-Swift messages: All customer transfer messages between Financial Institutions in the UAE from resident accounts to non-resident accounts within the UAE banking system in all currencies and from nonresident and resident accounts; And/or cross border transactions between their own branches, residents in the UAE and outside the UAE”
c) To provide the required information by using the required purpose codes as specified in the official list of SWIFT Scope purpose codes.
d) Licensed Financial Institutions can provide the required purpose codes by using any of the following options:
i. Option 01: using TAG 77B
ii. Option 02: using TAG 72
iii. Option 03: using TAG 70
iv. Option 04: using TAG 26T
“TAG” in this Article refers to a specific place holder in a SWIFT message that contains specific data.
e) Technical notes on transaction codes for the compilation of the balance of payments is published on the Central Bank website: Document Code - UAEFTS- AUX700 - 2018-001-01 dated November 2018.
f) The exchange houses that send transfer messages from the UAE, to institutions outside the UAE, in all currencies or receive transfer messages from institutions outside the UAE, in all currencies, must report to the Central Bank, transaction by transaction including the purpose code.
- Failure to provide the required information and to use the designated TAG with the correct purpose codes is a violation of the aforementioned Notice and will result in a fine of AED 1,000 for each violation.
- The Central Bank has the mandate to prepare and publish the statistics of the balance of payments and the international investment position for the UAE in line with international standards.
Article (5): Data Reporting on Card Transactions
- The Central Bank has the mandate to prepare and publish the statistics of the balance of payments for the UAE in line with international standards. To assist the Central Bank in the compilation of the balance of payments and enhance the quality of the information of all Card Transactions, particularly in relation to travel services, the information must be reported on a transaction by transaction basis.
- Under Notice No. CBUAE/BSD/- N/2018/758 dated 23 May 2018, the Licensed Financial Institutions are required to notify the Central Bank of all Card Transactions conducted at:
a. ATM/CDM/KIOSKs
- i. where the transaction is for the customer of the bank owning the terminal and/or
ii.the transaction is not routed to the issuer via the UAE SWITCH to the issuer for authorization
b. Point of Sale terminals:
- i. where the transaction is for the customer of the bank owning the terminal and/or
ii. the transaction is routed to the issuer via the schemes to the issuer for authorization
- i. where the transaction is for the customer of the bank owning the terminal and/or
- Licensed Financial tostitutions are required to upload the files of NON-UAE SWITCH and point of sale transactions on a daily basis even if there are no transactions to report.
- Licensed Financial Institutions are required to use format and variables for each of the files at paragraph 2 (a & b) of this Article following technical details provided in the Document Code U.FS-AUX884- Version 2017-001 UAE Funds Transfer System NON-UAE SWITCH Transaction Details Upload.
- In addition to allowing the Central Bank to identify the issuing countries and the usage countries on Card Transactions, the Central Bank issued Notice No. CBUAE/BSD/N/2019/2900 dated 18 July 2019, requiring Licensed Financial Institutions to:
a. provide CARD BINS information to the Central Bank of all Card Transactions issued in the UAE;
b. provide Customer Account Details for all Card Transactions issued by banks in the UAE; and
c. report data on Card Transactions conducted through e-commerce (online transactions).
- Failure to provide the required information aforementioned in accordance with the Central Bank’s Notices and the Document Code mentioned in this Article, is a violation and will result in a fine of AED 1,000 for each violation.
- The Central Bank has the mandate to prepare and publish the statistics of the balance of payments for the UAE in line with international standards. To assist the Central Bank in the compilation of the balance of payments and enhance the quality of the information of all Card Transactions, particularly in relation to travel services, the information must be reported on a transaction by transaction basis.
Article (6) Sale and Purchase Currency Notes Reporting
- Licensed Financial Institutions must report to the Central Bank the following:
a. Currency notes (cash); and
b. Sales and purchases of foreign currency classified by currency.
- The above report shall be sent to the Central Bank by the end of the working day every Friday. Failure to submit the report/reports as required will result in a fine of AED 1,000 for each violation.
- Licensed Financial Institutions must report to the Central Bank the following:
Article (7): Issuing Certificates to Customers Within 7 Working Days
- A routine function of all banks in the UAE is to provide their customers with liability statements and clearance letters, otherwise known as a certificate, within 7 working days of the customer’s application.
- The purpose of the certificate is to provide confirmation of the customer’s financial position with the bank to enable the customer to rely on the confirmation for personal reasons or to terminate their financial relationship with the bank and to move their account to another bank.
- Article 9 (b) of Regulation No. 29/2011 states that “Commercial banks may open all types of accounts for their customers, but in such cases, they must abide by the standard agreement mentioned under Article (12) [Conditions for Opening of Accounts, Providing Credit Cards and Granting Loans & Bank Facilities] of these Regulations. In case a customer requested closing of the account and termination of the business relationship with the bank, the bank should do that without imposing a penalty if the account opening date goes back to more than one year. In all cases, an account must be closed and an appropriate certificate must be issued within, maximum, seven days (7) from date of submission of the application”
- In addition, Central Bank Circular No. 13/189/2013 dated 2 December 2013 states that “As a normal banking practice, issuance and delivery of certificates and letters should not take more than 7 working days”.
- Accordingly, banks are required to provide certificates to their customers within 7 working days of the customer’s request. For the purposes of this Article, customers are retail customers, not corporate customers.
- Failure by the bank to issue the certificate within the requisite period is a violation and will result in a fine of AED 10,000 for each violation.
- A daily rate of AED 10,000 will be applied for the delay of each working day that continues after the initial violation with a maximum threshold of AED 100,000 for each violation.
- A routine function of all banks in the UAE is to provide their customers with liability statements and clearance letters, otherwise known as a certificate, within 7 working days of the customer’s application.
Article (8): Reporting Requirements
- An important function of the Central Bank is to receive data from Licensed Financial Institutions on various aspects of the Licensed Financial Institution’s activities by way of the Licensed Financial Institution’s reporting requirements. The reporting requirements relate to a broad range of the Licensed Financial Institutions’ business activities and it is critical to receive complete and accurate information in a timely manner to enable the Central Bank to maintain effective supervision of regulated entities.
- The obligation to file regulatory returns or reports to the Central Bank is set out in Central Bank Notice No. 157/2013 dated 11 April 2013.
- All Licensed Financial Institutions are under an obligation to file regulatory returns or reports under the Central Bank’s Integrated Regulatory Reporting System as per the required frequency and format.
- The reporting obligations stated in this Article are subject to change as notified by the Central Bank to Licensed Financial Institutions. Such changes will be informed to all Licensed Financial Institutions via https://13L5.15.15/cbuaeirr/ under “Alerts”.
- It is mandatory for Licensed Financial Institutions to monitor the “Alerts” during the working day to ensure that the reporting obligations are met.
- Licensed Financial Institutions must have a formal process to ensure they are able to comply with the reporting requirements. Failure to meet the filing requirements is a violation of the Licensed Financial Institutions’ obligations.
Licensed Financial institutions reporting requirements are as follow:
a. The Bank’s Reporting Requirements are as follows :
- i. Monthly Reports - The first batch of monthly reports must be filed within 7 working days (excluding weekends and public holidays) after the month end;
ii. Monthly Reports - The second batch of monthly reports must be filed within 11 working days (excluding weekends and public holidays) after the month end;
iii. Monthly Reports - The third batch of monthly reports must be filed by the 25th following each month end or the following working day if the 25th is a holiday;
iv. Quarterly Reports - The first batch of quarterly reports must be filed by the 25th following each calendar quarter end or the following working day if the 25th is a holiday;
v. Quarterly Reports - The second batch of quarterly reports must be filed by the 30th/31st following each quarter end or the following working day if the 30th or 31st is a holiday;
vi. Half Year Reports - The first batch of half-yearly reports must be filed by 31st July and 31st January or the following working day if the 31st is a holiday;
vii. Half Year Reports - The Second batch of half-yearly reports must be filed by 31st July and 31st January or the following working day if the 31st is a holiday;
viii. Yearly Reports- Must be filed by 31st January following the year end or the following working day if the 31st is a holiday;
ix. Quarterly Islamic Returns - Must be filed by 30th or 31st of the month end following the quarter end; or the following working day if the 30th or 31st is a holiday;
X. To submit any additional daily, weekly, fortnightly and other reports as required in the Integrated Regulatory Reporting System, or by law as applicable;
xi. Failure of the bank to comply with its reporting obligations will result in a fine of AED 1,000for each violation.
xii. A daily rate of AED 1,000 will be applied for the delay of each working day that continues after the initial violation with a maximum threshold of AED for each violation; and
xiii Submitting erroneous data in any of its reporting requirements will result in a fine of AED 50,000for each violation.
b. The Exchange House’s Reporting Requirements are as follows:
- i. Monthly reports: The first batch of monthly reports must be filed within 15 working days (excluding weekends and public holidays) after the month end;
ii. Monthly reports: The second batch of monthly reports must be filed within 15 working days after the month end;
iii. Monthly reports: The third batch of monthly reports must be filed within 15 working days after the month end;
iv. Quarterly reports: Must be filed within 15 working days after the quarter end;
v. To submit a Certificate of Remittance Value issued by the External Auditor, within two (2) months from the end of every financial year;
vi. To submit any additional daily, weekly, fortnightly and other reports as required in the Integrated Regulatory Reporting System or by law as applicable;
vii. Failure of the Exchange House to comply with its obligations to submit their reporting requirements in a timely manner as required is a violation of the Standards and will result in a fine of AED 250 for each violation;
viii A daily rate of AED 250 will be applied for the delay of each working day that continues after the initial violation with a maximum threshold of AED 25,000 for each violation; and
ix. Submitting erroneous data in any of its reporting requirements will result in a fine of AED 12,500 for each violation.
c. The Finance Company’s Reporting Requirements are as follows:
- i. Monthly reports: The first batch of monthly reports must be filed within 14 working days (excluding weekends and public holidays) after the month end;
ii. Monthly reports: The second batch of monthly reports must be filed within 20 working days (excluding Saturdays and public holidays) after the month end;
iii. Quarterly reports: Must be filed by the 25th following each quarter or the following working day if the 25th is a holiday;
iv. Half-yearly reports: Must be filed by the 25th following each half year-end or the following working day if 25th is a holiday;
v. Yearly reports: Must be filed by the 25th of the following month or the following working day if the 25th is the holiday;
vi. To submit any additional daily, weekly, fortnightly and other reports as required in the Integrated Regulatory Reporting System or by law as applicable;
vii. Failure of the finance company to comply with its obligations to submit their reports in a timely manner as required is a violation, and will result in a fine of AED 500 for each violation;
viii. A daily rate of AED 500 will be applied for the delay of each working day that continues after the initial violation with a maximum threshold of AED 50,000 for each violation; and
ix. Submitting erroneous data in any of its reporting requirements will result in a fine of AED 25,000 for each violation.
d. Other Licensed Financial Institution’s reporting requirements are as follows:
- i. To submit any reporting requirements for daily, weekly, fortnightly reporting and other reports as required in the Integrated Regulatory Reporting System or by Law as applicable;
ii. Failure of other Licensed Financial Institutions to comply with its obligations to submit their reporting requirements in a timely manner as required is a violation, and will result in a fine of AED 500 for each violation;
iii. A daily rate of AED 500 will be applied for the delay of each working day that continues after the initial violation with a maximum threshold of AED 50,000 for each violation; and
iv. Submitting erroneous data in any of its reporting requirements will result in a fine of AED 25,000 for each violation.
- i. Monthly Reports - The first batch of monthly reports must be filed within 7 working days (excluding weekends and public holidays) after the month end;
- An important function of the Central Bank is to receive data from Licensed Financial Institutions on various aspects of the Licensed Financial Institution’s activities by way of the Licensed Financial Institution’s reporting requirements. The reporting requirements relate to a broad range of the Licensed Financial Institutions’ business activities and it is critical to receive complete and accurate information in a timely manner to enable the Central Bank to maintain effective supervision of regulated entities.
Article (9): The Higher Shari’ah Authority
- Licensed Financial tostitutions that conduct all or part of their activities and businesses in accordance with Islamic Shari’ah Law are required to provide the Higher Shari’ah Authority with an annual Shari’ah report that is prepared by the Internal Shari’ah Supervision Committee.
- According to Article 80 of the Central Bank Law, the annual Shari’ah report is required to be provided to the Higher Shari’ah Authority before the end of February every year. The toternal Shari’ah Supervision Committee shall provide the Higher Shari’ah Authority with a copy of its report, no later than 2 months from the end of the financial year, in order for the Authority to express its remarks prior to the meeting of the general assembly of the concerned institution.
- Failure of the Licensed Financial Institutions to comply with its obligation to submit the annual Shari’ah report is a violation and will result in a fine of AED 5,000.
- A daily rate of AED 5,000 will be applied for the delay of each working day that continues after the initial violation with a maximum threshold of AED 500,000 for each violation.
- A fine of AED 50,000 will be applied if the Licensed Financial Institution submits erroneous data in any of the regulatory returns.
- Licensed Financial tostitutions that conduct all or part of their activities and businesses in accordance with Islamic Shari’ah Law are required to provide the Higher Shari’ah Authority with an annual Shari’ah report that is prepared by the Internal Shari’ah Supervision Committee.
Article (10): Enforcement and Sanctions
- Financial sanctions imposed on Licensed Financial Institutions under this Regulation will accrue as a debt of the Licensed Financial Institutions. The Central Bank will notify the Licensed Financial Institution of the debt, as relates to the period of default deemed appropriate by the Central Bank. The debt will be automatically debited from the Licensed Financial Institution’s account at the Central Bank 28 days after the notification or such alternative means of settlement of the debt as advised to the Licensed Financial Institutions.
- Each obligation is considered separately and the appropriate fine will be applied for violating the specific regulatory obligation. A summary of the financial sanctions is attached at Appendix 1. Continued regulatory violations may result in further enforcement action under the Central Bank Law.
- In the event the Central Bank introduces new reporting requirements or alters the obligations set out in this Regulation, by legislation, decree, notice, circular, or other notification and as amended in the Integrated Regulatory Reporting System, Licensed Financial Institutions are required to comply with those reporting requirements and obligations. Such reporting requirements and obligations shall fall within the scope of this Regulation.
- Financial sanctions imposed on Licensed Financial Institutions under this Regulation will accrue as a debt of the Licensed Financial Institutions. The Central Bank will notify the Licensed Financial Institution of the debt, as relates to the period of default deemed appropriate by the Central Bank. The debt will be automatically debited from the Licensed Financial Institution’s account at the Central Bank 28 days after the notification or such alternative means of settlement of the debt as advised to the Licensed Financial Institutions.
Article (11): Force Majeure
1. In case of extraordinary events or circumstances beyond the Licensed Financial Institution’s control that prevent the timely submission of the required information, such as contingencies regarding the Licensed Financial Institutions information technology system/s or the Central Bank’s inability to receive the same, the Licensed Financial Institutions must immediately notify the Central Bank and seek the Central Bank’s approval for the delay.
Article (12): Interpretation of Regulation
- The Regulatory Development Division of the Central Bank shall be the reference for the interpretation of the provisions of this Regulation.
Article (13): Publication of Regulation
- The Regulation shall be published in the Official Gazette in both Arabic and English and shall come into effect one month from the date of publication.
Appendix 1
Summary of Financial Sanctions
Article Violation Fines Article (2) Failure to prevent the circulation of counterfeit/forged UAE Currency AED 10,000 for each counterfeited note plus the face value of the currency note and/or currency coin.
Article (3) Failure to comply with the Central Bank Court Cases Management System. AED 1,000 per violation and a daily rate of AED 1,000 for the delay of each working day that continues after the initial violation, with a maximum threshold of AED 50,000 for each violation.
Article (4) Failure to comply with the requirements of data reporting on cross border transactions (SWIFT Cross-Border Payment Transactions) AED 1,000 per violation
Article (5) Failure to comply with the requirements of data reporting on Card Transactions AED 1,000 per violation
Article (6) Failure to comply with the requirements of sale and purchase currency notes reporting AED 1,000 per violation
Article (7) Failure to issue liability statements and clearance letters to customers within 7 working days of the customer’s application. AED 10,000 per violation and a daily rate of AED 10,000 for the delay of each working day that continues after the initial violation with a maximum threshold of AED 100,000 for each violation.
Article (8)7.a. Failure of the bank to comply with its reporting obligations on time per the required frequency. AED 1,000 per violation and a daily rate of AED 1,000 for the delay of each working day that continues after the initial violation with a maximum threshold of AED 100,000 for each violation.
Article (8)7.a. Failure of the bank to submit correct data in any of its reporting obligations AED 50,000 per violation.
Article (8)7.b. Failure of the exchange house to comply with its reporting obligations on time per the required frequency AED 250 per violation and a daily rate of AED 250 for the delay of each working day that continues after the initial violation with a maximum threshold of AED 25,000 for each violation.
Article (8)7.b. Failure of the exchange house to submit correct data in any of its reporting obligations AED 12,500 per violation.
Article (8)7.c. Failure of the finance company to comply with its reporting obligations on time per the required frequency AED 500 per violation and a daily rate of AED 500 for the delay of each working day that continues after the initial violation with a maximum threshold of AED 50,000 for each violation.
Article (8)7.c. Failure of the finance company to submit correct data in any of its reporting obligations AED 25,000 per violation
Article (8)7.d. Failure of other Licensed Financial Institutions to comply with its reporting obligations on time per the required frequency AED 500 per violation and a daily rate of AED 500 for the delay of each working day that continues after the initial violation with a maximum threshold of AED 50,000 for each violation.
Article (8)7.d. Failure of other Licensed Financial Institutions to submit correct data in any of its reporting AED 25,000 per violation
Article (9) Failure to file the annual Shari’ah report by the end of February every year AED 5,000 per violation and a daily rate of AED 5,000 for the delay of each working day that continues after the initial violation with a maximum threshold of AED 500,000 for each violation.
Article (9) Failure of the Licensed Financial Institution to submit correct data in the annual Shari’ah report AED 50,000 per violation
Governance and Designated Functions
Fitness and Propriety Regulation
C 4/2024 Effective from 31/10/2024Introduction
The Central Bank is seeking to establish the framework for assessing fitness and propriety of Applicants, Authorized Individuals and Material Risk Takers and other Persons designated by the Central Bank. The Fitness and Propriety Regulation (this Regulation), and the accompanying Fitness and Propriety Standards (the Standards) set out the Central Bank’s minimum requirements for fitness and propriety to ensure that Persons who hold Designated Functions and other key positions within Licensees meet established criteria which support good governance and thereby the protection of depositors, policy holders, other customers and key stakeholders. This Regulation and accompanying Standards must be read in conjunction with the Central Bank Laws and Regulations, including the following, at a minimum:
- Central Bank Circular No. 83/2019 - Corporate Governance Regulation for Banks and accompanying Standards; - Central Bank Circular No. 24/2022 - Corporate Governance Regulation for Insurance Companies and accompanying Standards; - Central Bank Circular No. 3/2023 – Finance Companies Regulation; - Central Bank Circular No. 15/2021 – Retail Payment Services and Card Schemes Regulation; - Central Bank Circular No. 6/2020 – Stored Value Facilities Regulation; - Central Bank Notice No. CBUAE/BSD/N/2020/2123 - Standard Re. Shari’ah Governance for Islamic Financial Institutions; - Central Bank Notice No. CBUAE/BIS/2023/4496 Standard re Shari’ah Governance for Takaful Insurance Companies; - Central Bank Notice No. 35/2018 - The Standards for the Regulations Regarding Licensing and Monitoring of Exchange Business; - Central Bank of the UAE’s Board of Directors’ Resolution published in the Official Gazette issue No. (740) on 30 November 2022 - Regulation Regarding Takaful Insurance; - Insurance Authority Board of Directors Resolution No. 15 of 2013 Concerning Insurance Brokerage Regulations; - Insurance Authority Board of Directors Resolution No. 6 of 2010 Concerning Surveyors and Loss Adjusters’ Regulations; - Insurance Authority Board Resolution No. 08 of 2011 - Instructions Concerning the Regulation of Insurance Agents Business; - Insurance Authority Board Resolution No. 9 of 2011 Concerning the Instructions for Licensing Health Insurance Third Party Administrators and Regulation and Control of their Business; - Insurance Authority Board of Directors’ Resolution No. (27) of 2020 Concerning the Instructions for Licensing Insurance Producers; - Insurance Authority Board of Directors Decision No. (9) of 2017 Concerning the Regulations on Licensing and Registration of Actuaries and Regulation of their Operations; - Board of Directors' Decision No. (12) of 2018 Concerning the Regulation on Licensing and Registration of Insurance Consultants and Organization of their Operations; and - Insurance Authority Board of Directors Decision No. (13) of 2018 Instructions Concerning Marketing Insurance Policies through Banks.
In the event of any conflicts between requirements in this Regulation and the aforementioned Regulations or any other Regulations, the requirements herein take precedence.
The Central Bank will use this Regulation and its accompanying Standards as the benchmark for its evaluation of Authorized Individuals, to ensure that their appointment facilitates the sound and prudent management of Licensees. Licensees hold primary responsibility for assuring themselves and the Central Bank, that Authorized Individuals and Material Risk Takers are fit and proper and suitable by, at a minimum, meeting the criteria established herein on the following (where applicable):
- Honesty, integrity and reputation; - Competence and capability; - Financial conduct; - Independence of mind; and - Time commitment.
This Regulation and the accompanying Standards are issued pursuant to the powers vested in the Central Bank under the Central Bank Laws and set the minimum principles of fitness and propriety, as far as common elements apply across regulated sectors. The Central Bank may issue additional Regulations in respect of ensuring the suitability of Authorized Individuals, Material Risk Takers and other Persons, as may be required within specific Licensees.
Where this Regulation, or its accompanying Standards, include a requirement to provide information or to take certain measures, or to address certain items listed, the Central Bank may impose requirements, which are additional to those provided for in the relevant Article.
Objective
The objective of this Regulation is to implement a framework for ensuring that Authorized Individuals and Material Risk Takers are fit and proper, and suitable to perform their functions within a Licensee. The accompanying Standards supplement this Regulation and elaborate on the framework by setting the minimum criteria and process for assessing the fitness and propriety of Persons prior to appointment and on an ongoing basis, which is expected to ensure the safety and soundness of Licensees and overall stability of the UAE financial sector.
This Regulation and the accompanying Standards establish the functions and Persons who require Authorisation by the Central Bank prior to their appointment or reappointment to positions within a Licensee. Additionally, all functions, which are required to undergo the Fit and Proper Process, are also established.
With the implementation of this Regulation and accompanying Standards, the expectation is that Licensees must be able to assure the Central Bank, on a continuous basis, that they are in full compliance with fit and proper requirements.
Scope
This Regulation and the accompanying Standards apply to all Licensed Financial Institutions, Insurance Companies, Takaful Insurance Companies and Insurance-Related Professions (collectively, Licensees). The fit and proper and suitability requirements apply to the Licensee as a whole and the individuals involved in the management and control, as well as those who exercise significant power or discharge significant responsibilities in relation to the activities carried on by the Licensee.
Licensees established in the UAE with Group relationships, including Subsidiaries, Affiliates, or international branches, must ensure that this Regulation and the accompanying Standards are adhered to on a solo and Group-wide basis. The requirements within this Regulation and the accompanying Standards shall also apply to Persons engaged by a Licensee in cases where a function is outsourced, where applicable.
Article (1): Definitions
The following terms shall have the meaning assigned to them below for the purposes of this Regulation and its accompanying Standards:
1.1 Actuary: a Person licensed or authorized by the CBUAE to determine the value and price of the insurance policies, and to assess the technical provisions, accounts and all matters related thereto. 1.2 Affiliate: an entity that, directly or indirectly, controls, is controlled by, or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity, or of the power to direct or cause the direction of the management of another entity. 1.3 Applicant: a nominee for appointment or reappointment to a Designated Function in a Licensee. The term ‘Applicant’ is captured by Authorized Individual, where relevant. 1.4 Authorisation: the Central Bank’s formal approval or non-objection to the appointment or reappointment of a Person to a function within a Licensee, as determined by the Central Bank. 1.5 Authorized Individual: any natural Person authorized in accordance with the provisions of the Central Bank Laws, to carry on any of the Designated Functions. In the case of Insurance Companies and Insurance-Related Professionals, the term Authorized Individual includes Senior Employees. 1.6 Authorized Manager: a natural Person appointed by a foreign Insurance Company to manage its Branch in the State. 1.7 Bank: any Juridical Person licensed in accordance with the provisions of the Central Bank Law, to primarily carry on the activity of taking deposits, and any other Licensed Financial Activities. 1.8 Board: the board of directors of the Licensee. In the case of branches of foreign Licensees, Board refers to the highest decision making body of the Licensee within the State, for example, the Senior Management committee. 1.9 Branch: a branch of the Insurance Company that carries out insurance activities in the name of the Insurance Company. 1.10 Central Bank: the Central Bank of the United Arab Emirates (CBUAE). 1.11 Central Bank Law: the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organisation of Financial Institutions and Activities, as amended. 1.12 Central Bank Laws: the Central Bank Law and the Insurance Law. 1.13 Chief Executive Officer: the most senior executive appointed by the Board, and in the case of a Branch, this refers to the Authorized Manager. 1.14 Collective Suitability: the structure and composition of a Licensees’ Board which allows for full appreciation of the Licensees’ risk profile and business strategy to enable it to exercise effective challenge and oversight of decisions. The assessment of Collective Suitability takes into consideration, inter alia, size and structure, degree of independence and interaction, degree of diversity, and collective, relevant knowledge, skills and experience. 1.15 Compliance with Islamic Shari’ah Provisions: refers to compliance with Islamic Shari’ah in accordance with:
a. The provisions stated in Section Six of Book Three of the Commercial Transactions Law, b. The provisions contained in the bylaws issued implementing Section Six of Book Three of the Commercial Transactions Law, c. The resolutions, Fatwas, regulations and standards issued or approved by the Higher Shari’ah Authority in relation to businesses and activities of the Licensee ("HSA’s Resolutions"), d. The resolutions and Fatwas issued or approved by the Internal Shari’ah Supervision Committee of the respective Licensee, in relation to businesses and activities of such Licensee ("ISSC’s Resolutions"), provided that they do not contradict the HSA’s resolutions.
1.16 Conflict of Interest: a situation of actual or perceived conflict between the duty and private interests of a Person, which could improperly influence the performance of his/her duties and responsibilities. 1.17 Continuous Professional Development (CPD): any type of training or learning undertaken by a Person which increases relevant knowledge, understanding and experiences of a subject area or role. 1.18 Control Functions: the Licensee’s functions that have a responsibility independent from management to provide objective assessment, reporting and/or assurance; this includes the risk management function, the compliance function and the internal audit function. 1.19 Designated Functions: functions of the Authorized Individual at, or for the benefit of, a Licensee of influential nature on the institution's activities. 1.20 Fit and Proper Process: the evaluation of a Licensee’s proposed and existing members of the Board and Senior Management, Material Risk Takers and other Persons, as determined by the Central Bank. 1.21 Group: a group of entities that includes an entity (the ‘first entity’) and:
a. any Parent of the first entity; b. any Subsidiary of the first entity or of any Parent of the first entity; and c. any Affiliate
1.22 Health Insurance Claims Management Company: a Juridical Person licensed by the CBUAE to carry out health insurance claims management business. 1.23 Higher Sha’riah Authority: an authority that exercises the mandates and authorities stipulated in Regulations regarding Takaful Insurance and the notices issued by the Central Bank. 1.24 Insurance Agent: a Person licensed or authorized by the CBUAE, and is approved by the Insurance Company and authorized to carry out insurance activities on its own behalf or on behalf of a Branch thereof. 1.25 Insurance Broker: a Juridical Person licensed by the CBUAE and acts as independent intermediary in insurance and reinsurance operations between an insurance or re-insurance applicant on the one side and any Insurance Company on the other side, and receives, in consideration of its efforts, a commission from the Insurance Company with which insurance or reinsurance is concluded. 1.26 Insurance Company: an insurance company established in the State as well as a foreign insurance company licensed to carry out insurance business in the State, either through a Branch or through an Insurance Agent; and a Re-Insurance Company licensed to engage in re-insurance business either in the State or abroad. 1.27 Insurance Consultant: a Person licensed or authorized by the CBUAE to examine insurance requirements for their clients and give advice in respect of the suitable insurance coverage, assistance in preparing insurance requirements and receives their remuneration from their clients. 1.28 Insurance Law: the Federal Decree-Law No. (48) of 2023 Regulating Insurance Activities and its Executive Regulations, and any amendments thereof. 1.29 Insurance-Related Professions: any Person licensed or authorized by the CBUAE to operate as an Insurance Agent, Insurance Broker, Surveyor and Loss Adjuster, Insurance Consultant, Actuary or Health Insurance Claim Manager, or any other profession related to insurance as determined and regulated by a resolution of the Board of Directors of the Central Bank. 1.30 Internal Shari’ah Supervision Committee (ISSC): a body appointed by an Islamic financial institution/ a Takaful Insurance Company, comprised of scholars specialized in Islamic financial transactions, which independently supervises transactions, activities, and products of the Islamic financial institution / the Insurance Company and ensure its Compliance with Islamic Shari’ah Provisions in all its objectives, activities, operations, and code of conduct. 1.31 Islamic Financial Institutions: the Licensed Financial Institutions that conduct all or part of their activities and businesses in accordance with the provisions of Islamic Shari'ah. 1.32 Juridical Person: any person who is not a natural Person. 1.33 Licence: authorisation issued by the Central Bank to conduct the business of a Licensee. 1.34 Licensed Financial Activities: the financial activities subject to Central Bank licensing and supervision, which are specified in Article (65) of the Central Bank Law. 1.35 Licensed Financial Institutions: Banks and Other Financial Institutions licensed in accordance with the provisions of the Central Bank Law, to carry on a Licensed Financial Activity or more, including those which carry on the whole or a part of their business in Compliance with Islamic Shari`ah Provisions, and are either incorporated inside the State or in other jurisdictions, or have branches, Subsidiaries or Representative Offices inside the State. 1.36 Licensee: a Licensed Financial Institution, an Insurance Company, Takaful Insurance Company or an Insurance-Related Profession, which is subject to the provisions of this Regulation and its accompanying Standards. 1.37 Material Risk Takers: Staff whose work is deemed to have a significant impact on the overall risk profile of the Licensee or the Group. 1.38 Other Financial Institutions: any Juridical Person, other than Banks, licensed, in accordance with the provisions of the Central Bank Law, to carry on a financial activity or more, of the Licensed Financial Activities. 1.39 Parent: an entity (the ‘first entity’) which:
a. holds a majority of the voting rights in another entity (the ‘second entity’); b. is a shareholder of the second entity and has the right to appoint or remove a majority of the board of directors or managers of the second entity; or c. is a shareholder of the second entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the second entity. Or; d. if the second entity is a subsidiary of another entity which is itself a subsidiary of the first entity
1.40 Person: a natural Person. 1.41 Regulations: any resolution, regulation, circular, rule, standard or notice issued by the Central Bank or any resolution issued by the Higher Sha’riah Authority. 1.42 Representative Offices: an office licensed in accordance with the provisions of the Central Bank Law, to carry on representation of a financial institution incorporated in other jurisdictions. 1.43 Senior Employee: any Person who occupies an executive position equivalent to the duties of a Director-General, Authorized Manager or the deputy or assistant of either one, or any department director, internal audit director or Branch manager. 1.44 Senior Management: the executive management of the Licensee responsible and accountable to the Board for the sound and prudent day-to-day management of the Licensee, generally including, but not limited to, the Chief Executive Officer, chief financial officer, chief risk officer, heads of the compliance and internal audit functions. 1.45 Staff: all the Persons working for a Licensee including the members of Senior Management, except for the members of its Board. 1.46 State: the United Arab Emirates (UAE). 1.47 Subsidiary: an entity (the ‘first entity’) is a subsidiary of another entity (the ‘second entity’) if the second entity:
a. holds a majority of the voting rights in the first entity; b. is a shareholder of the first entity and has the right to appoint or remove a majority of the board of directors or managers of the first entity; c. is a shareholder of the first entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the first entity Or d. if the first entity is a subsidiary of another entity which is itself a subsidiary of the second entity.
1.48 Surveyor and Loss Adjuster: a Person licensed or authorized by the CBUAE to inspect and assess the damage incurred in the subject of insurance. 1.49 Takaful Insurance: A collective contractual scheme intended to achieve solidarity and cooperation among a group of contributors to address certain risks, where each one pays an amount of money called “contribution” to be deposited in a Takaful insurance fund, through which compensation is to be paid to eligible persons when a risk is sustained. 1.50 Takaful Insurance Company: an Insurance Company, which is incorporated and practices its business in accordance with the provisions of the Central Bank Laws and Regulations, and whose carried out businesses and activities are in Compliance with the Islamic Shari’ah Provisions.
Article (2): Fit and Proper Conditions
2.1 Persons being proposed to hold or who hold certain specified positions in Licensees must be authorised by the Central Bank to hold those positions and must demonstrate that they are fit and proper. The list of positions subject to the Central Bank’s Authorisation regime varies according to the Licence/s held by the Licensee, but generally cover members of the Board and Senior Management, including the heads of Control Functions. The current, non-exhaustive list of positions subject to Central Bank Authorisation is presented in Attachment 1 to the accompanying Standards. 2.2 Licensees must ensure that Authorized Individuals and Material Risk Takers meet fit and proper criteria established in this Regulation and the accompanying Standards and continue to do so for the duration of their tenure in a Designated Function or as a Material Risk Taker in a Licensee. 2.3 Authorised Individuals and Material Risk Takers must undergo the Fit and Proper Process. In the case of Authorized Individuals, Licensees must obtain Authorisation from the Central Bank prior to their appointment or reappointment to Designated Functions. 2.4 The Fit and Proper Process must take into account the role that the Person is expected to undertake within the Licensee. Therefore, a Person assessed as suitable for a particular position within a Licensee may not automatically and solely on that basis, be considered suitable for another position with different responsibilities, or for a similar role within a different Licensee. 2.5 Applicants must not participate in any decision-making or policy-making activities related to the proposed Designated Function prior to receiving the Authorisation of the Central Bank for their appointment. 2.6 There must be full and accurate disclosure by Authorized Individuals and Licensees when communicating information to the Central Bank in relation to the Fit and Proper Process
Article (3): Central Bank Powers
3.1 Prior to providing its Authorisation for the appointment of a Person to a Designated Function, the Central Bank may conduct its own assessments, interviews and background, security and other detailed checks, to confirm the accuracy, completeness and relevance of the information and documentation provided by the Person and/or the Licensee. 3.2 The Central Bank may request information about a Person from other Persons, Juridical Persons or authorities within or outside of the State to inform its decision on Authorisation. 3.3 The Central Bank may prescribe the forms which need to be completed and the supporting documentation to be provided in support of an application for Authorisation. 3.4 Where the Central Bank provides Authorisation for the appointment of an Authorised Individual, the Central Bank may impose specific conditions and/or restrictions to the Authorisation. 3.5 The Central Bank may require, at its sole discretion and on a case by case basis that the shareholders, directors and/or senior management of the Parent, Subsidiaries or Affiliates of a Licensee, be subject to the Fit and Proper Process. 3.6 The Central Bank may, in certain circumstances, modify specific requirements set within this Regulation and its accompanying Standards, with regard to a particular case. 3.7 The Central Bank may, at any time, remove or revoke the appointment of any Person, if that Person is found to be not fit and proper or does not fulfil the requirements of suitability for the position which they hold; or where the Central Bank, determines that the Person’s appointment poses significant risk to the safety and soundness of the Licensee.
Article (4): Responsibilities of the Licensee
4.1 Branches of foreign Licensees must establish local governance structures, such as a Senior Management committee or equivalent, that fulfil the responsibilities of a Board required by this Regulation and the accompanying Standards. The local management structure of the branch must take steps as are necessary to help the branch meet its own fitness and propriety responsibilities in line with this Regulation and its accompanying Standards. It is the responsibility of the local management structures to ensure that local legal and regulatory requirements are implemented and, where appropriate, make adjustments where the Group requirements conflict with a provision of this Regulation or the accompanying Standards. 4.2 Licensees must ensure that all Staff are suitable for the positions that they occupy, including Staff who provide advice and/or make recommendations to customers, who must be suitably qualified and competent in undertaking their roles. The Central Bank may issue additional Regulations on suitability, in this regard. 4.3 Licensees must take responsibility for assessing the fitness and propriety of Persons who hold positions which are subject to these assessments. Licensees must inform the Central Bank of the outcome of all assessments related to fitness and propriety of Authorized Individuals, including the assessment of Collective Suitability of the Board and collective skills, competence and experience of the Senior Management team and other decision-making bodies necessary to operate the business in a prudent and effective manner. 4.4 Licensees must ensure that the Senior Management team is collectively competent, giving due regard to the risk profile, business strategy and internal control framework. Collective competence refers to the need for a range of educational qualifications and experience. Licensees that conduct all or part of their activities and businesses in Compliance with Islamic Shari’ah Provisions, must take into consideration the collective competence of the ISSC members particularly in terms of relevant experience and skills related to the business and activities of the Licensee, including inter alia, the legal and regulatory framework and risk management and technological requirements. 4.5 No applications for the appointment of Authorized Individuals should be submitted for the Central Bank’s Authorisation until the Licensee is assured that the Person has been assessed as fit and proper and has been found suitable for the proposed function. 4.6 The Licensee must submit the results of the Fit and Proper Process of Applicants along with all supporting documentation to the Central Bank for Authorisation no later than sixty (60) business days prior to the planned appointment date of the Applicant. 4.7 Licensees must ensure that information submitted to the Central Bank in support of an application for Authorisation, including responses in the prescribed forms, is complete, accurate, not misleading or erroneous and is presented in Arabic and/or English (as stipulated), free of errors and signed off on by a Person, authorised to do so by the Board, where applicable. The Person/s signing the form on behalf of the Licensee must have the appropriate authority to do so and must not be the Person for whom Authorisation is being sought, or the Person who will be the direct manager of that Person. 4.8 In all cases, Licensees must obtain the Central Bank’s Authorisation prior to reappointing or renewing the contract of any Authorized Individual. In cases where a contract or appointment instrument of an Authorized Individual is being amended, at a minimum, Authorisation must be sought from the Central Bank where the amendment relates to the tenure of the contract or period of appointment. 4.9 Licensees and Applicants must not make external, public announcements about proposed appointments prior to obtaining the Central Bank’s Authorisation. 4.10 If an Authorized Individual is deemed to be not fit and proper following the completion of an assessment by either the Licensee or the Central Bank, the Authorized Individual must be removed from the Designated Function. The Person must be replaced within the period specified by applicable law or Regulations; and where not specified, within ninety (90) days, subject to the fit and proper and suitability requirements. The Licensee may apply for an extension to the ninety (90) days and provide the Central Bank with adequate justification for the request. 4.11 In all cases, a Licensee must obtain the non-objection of the Central Bank prior to the termination, dismissal or removal of an Authorized Individual. The request for non-objection to the Central Bank must include all pertinent details, including the planned termination date, reasons for the planned termination, dismissal/ or removal and relevant signed decisions. In the case of ISSC members and heads of internal Shari’ah control and internal Shari’ah audit departments, the Licensee must also obtain a non-objection from the Higher Shari’ah Authority, before the termination, dismissal or removal of the Person. 4.12 In cases where termination, dismissal or removal of an Authorized Individual is required for actions which can severely impact the safety or soundness of the Licensee or where the Person’s actions could amount to criminal misconduct, including fraud, significant legal or regulatory breaches, or gross negligence, the Licensee must immediately notify the Central Bank prior to pursuing the termination, dismissal or removal action. In such cases, the Central Bank may waive the requirement for seeking prior-non-objection.
Article (5): Material Risk Takers
5.1 Licensees must designate Material Risk Takers following an assessment of the functions and duties of its Staff to identify which roles will therefore be subject to the Fit and Proper Process at appointment and on an ongoing basis, in line with this Regulation and the accompanying Standards. 5.2 Material Risk Takers must be assessed by the Licensee as fit and proper and suitable for their roles, in the sense that they are sufficiently skilled, knowledgeable and capable of performing the specific function; and possess the relevant minimum qualifications and experience requirements for the post.
Article (6): The Fit and Proper Process
6.1 The Fit and Proper Process must be applied to all Applicants and Material Risk Takers. 6.2 The Central Bank may require any Person employed within or engaged by a Licensee to be subject to the Fit and Proper Process, at its sole discretion. 6.3 In cases where a Licensee established in the UAE, is a member of a Group, the Fit and Proper Process must be undertaken on the board and senior managers of other entities in the Group, if they exercise a material or controlling influence on the Licensee. In such cases, the Licensee must ensure that an assessment is completed, highlighting any material differences between the requirements herein and those in the jurisdiction of the Parent and submit to the Central Bank, a compliance plan which ensures full compliance in the host jurisdiction while considering the regulatory requirements in the State. In all cases, where there is no clear conflict between the requirements, the stricter and/or more prudent requirements must be complied with. Where the Licensee is not established within the UAE, the Central Bank, may, at its sole discretion, require that the Fit and Proper Process be undertaken for the board and senior managers of other entities in the Group, on a case by case basis. The Central Bank may exempt a Licensee from the requirements herein, if the Licensee demonstrates to the satisfaction of the Central Bank, that the fit and proper requirements of another jurisdiction are satisfactory and are being met by the Licensee. 6.4 If the Fit and Proper Process results in adverse findings, that is, finds that the Person concerned is not fit and proper or not suitable for the position they hold and therefore demonstrate the need to remove the Person from that function, the Central Bank’s non-objection must be sought, where required, in line with this Regulation and the accompanying Standards. 6.5 The Central Bank recommends that Authorised Individuals undergo the Fit and Proper Process on an annual basis. All Authorized Individuals and Material Risk Takers must be subject to the Fit and Proper Process:
a. Prior to appointing the Person to a Designated Function or as a Material Risk Taker; b. Regularly, and at a minimum, every three (3)years or prior to the renewal of the contract or reappointment of the Person, whichever is earlier; c. If there is reason to believe that the Person may no longer be fit and proper either due to a trigger event (as set out in Article 6.11 of the accompanying Standards) or any other reason; and d. Any other time, as determined by the Central Bank.
Article (7): Fit and Proper Criteria
7.1 The criteria for the assessment of fitness and propriety and suitability takes consideration of all relevant information, whether obtained within the State or another jurisdiction, and relies on establishing whether a Person, where applicable:
a. Possesses the necessary knowledge, skills, expertise and experience; b. Has a record of acting honestly, ethically, with integrity and is of good repute; c. Has a good record of financial conduct; d. Is able to make his/her own decisions in a reasoned, objective and independent manner; and does not have any Conflict of Interest that could affect his/her conduct; e. Has sufficient time to devote to fully performing his/her duties and responsibilities; e. Contributes to the Collective Suitability of the Board or the collective competence of the Senior Management team, where applicable; and f. Meets any additional requirements specified in applicable Regulations.
Article (8): Collective Suitability
8.1 The Board must have the collective experience, knowledge and skills to understand all the areas of the Licensee’s activities including the main risks and the management thereof; set the strategy and provide effective leadership, direction and oversight; and facilitate independent opinions and constructive challenge in the decision-making process. 8.2 Diversity of skills and knowledge must be taken into account when selecting Authorized Individuals. Diversity of the Board must be considered in relation to skills, knowledge, qualifications, professional background, age and gender. 8.3 The Fit and Proper Process must therefore be supported by a comprehensive suitability assessment, where applicable, to ensure that the appointment of Authorized Individuals supports a broader objective of ensuring that the Board meets the requirement of Collective Suitability. 8.4 In the event that the results of the assessment reveal a deficiency in the Collective Suitability of the Board, the Licensee must submit to the Central Bank an action plan for achieving Collective Suitability. The Central Bank may consider this action plan in assessing any applications for approval of Applicants for appointment or reappointment to the Board.
Article (9): Continuous Professional Development (CPD) Requirements
9.1 Authorized Individuals and Material Risk Takers must have current, relevant and sufficient knowledge, skills and experience; and remain competent for the positions they hold. 9.2 Licensees must provide opportunities for and/or facilitate access to CPD for Authorized Individuals and Material Risk Takers to maintain and enhance their competencies and stay up to date on developments relevant to their areas of responsibility. 9.3 Unless otherwise specified by applicable Regulations, the minimum number of CPD hours to be completed by Authorized Individuals and Material Risk Takers is ten (10) hours per calendar year. The Central Bank may set minimum requirements for specified functions, including requiring the completion of specific programmes, as approved by the Central Bank. 9.4 The Central Bank may set more specific competency requirements for specified functions including inter alia recognised qualifications, minimum CPD requirements and the programmes, training, or qualifications which are considered as adequate to meet the requirements of CPD. 9.5 Licensees must maintain detailed records of CPD participation by Authorized Individuals and Material Risk Takers along with supporting documentation including inter alia attendance or completion certificates and course receipts. These records must be submitted to the Central Bank, where required and be made available to the Central Bank, upon request.
Article (10): Reporting and Record Keeping
10.1 Licensees must document the results of the Fit and Proper Process for all Persons; and all information and results of the process must be kept confidential. The consent of the Person must be obtained prior to sharing any information or documents, except in cases where required under UAE law. 10.2 Upon completion of the Fit and Proper Process for Authorized Individuals or Collective Suitability assessments for the Board, whether conducted as part of the Licensee’s ongoing programme of reassessments or triggered by an event, the results of these assessments must be submitted to the Central Bank immediately upon finalisation. If the Person is found to be not fit and proper and/or suitable for the Designated Function, the action taken or proposed plan of action for remediation of the breach must also be reported to the Central Bank. 10.3 Where a Licensee becomes aware of circumstances or information that may materially, adversely affect the fitness and propriety of an Authorized Individual, or the Collective Suitability of the Board the Licensee must immediately notify the Central Bank in writing and provide all necessary details, supporting documentation and the results of the reassessment, where applicable. The Licensee must provide an indication of whether the information led or will lead to a reassessment of fitness and propriety of the Person or the Collective Suitability, and if not, the Licensee must provide appropriate justification for not conducting the reassessment. 10.4 A Licensee must formally notify the Central Bank in a form specified by the Central Bank, of the resignation or retirement of any Authorized Individual immediately, but no later than five (5) business days of the Licensee’s receipt of the retirement or resignation notice, as the case may be. In the case of members of the ISSC, and heads of internal Shari’ah control and internal Shari’ah audit departments, in addition to the Central Bank, the Licensee must also notify the Higher Shari’ah Authority. The notifications to the Central Bank and Higher Shari’ah Authority must include all pertinent details, including the effective date of the retirement or resignation and in the case of resignation, the reasons cited by the Person for the resignation, where applicable. 10.5 A Licensee must conduct an exit interview with an Authorised Person who has resigned from their post. The proceedings of the exit interview must be documented and made available to the Central Bank, upon request. 10.6 Licensees must report any other matter that the Central Bank reasonably expects to be aware of, including breaches of any of the provisions of this Regulation and accompanying Standards.
Article (11): Enforcement and Sanctions
11.1 Violation of any provision of this Regulation and the accompanying Standards may subject the Licensee to supervisory action, administrative action and/or financial sanctions as deemed appropriate by the Central Bank. 11.2 Without prejudice to the provisions of the Central Bank Law, supervisory action and sanctions by the Central Bank may include withdrawing, replacing or restricting the powers of Senior Management or Members of the Board, providing for the interim management of a Licensee, or barring individuals from the UAE financial sector.
Article (12): Interpretation of Regulation
12.1 The Regulatory Development Department of the Central Bank shall be the reference for interpretation of the provisions of this Regulation and the accompanying Standards.
Article (13): Publication and Application
13.1 This Regulation and the accompanying Standards shall be published in the Official Gazette and shall come into effect on the date of its publication.
Article (14): Transitional Arrangements
14.1 Any Person who has been approved by the Central Bank to hold a Designated Function on the effective date of this Regulation and the accompanying Standards, is deemed Authorised by the Central Bank to hold the Designated Function, until a reassessment is required, based on the requirements herein. 14.2 In line with the requirements set in this Regulation and accompanying Standards, within nine (9) months of the effective date of this Regulation and the accompanying Standards, Licensees must complete the Fit and Proper Process for any Person who holds a Designated Function and has not been Authorised by the Central Bank; and for any Material Risk Taker, where an assessment has not been conducted within the three (3) years prior to the effective date of this Regulation and the accompanying Standards. 14.3 The Licensee must submit to the Central Bank a report of the exercise conducted in Article (14.2), including the records of assessments conducted and details of any related actions.
Fitness and Propriety Standards
C 4/2024 STA Effective from 31/10/2024Introduction
These Fitness and Propriety Standards (the Standards) form part of the Fitness and Propriety Regulation (the Regulation) (Circular No. 4/2024). All Licensees must comply with these Standards, which expand on the Regulation. These Standards are mandatory and enforceable in the same manner as the Regulation.
The Standards follow the structure of the Regulation, with each article corresponding to the specific article in the Regulation.
Article (1): Definitions
The following terms shall have the meaning assigned to them below for the purposes of these Standards:
1.1 Actuary: a Person licensed or authorized by the CBUAE to determine the value and price of the insurance policies, and to assess the technical provisions, accounts and all matters related thereto. 1.2 Affiliate: an entity that, directly or indirectly, controls, is controlled by, or is under common control with another entity. The term control as used herein shall mean the holding, directly or indirectly, of voting rights in another entity, or of the power to direct or cause the direction of the management of another entity. 1.3 Applicant: a nominee for appointment or reappointment to a Designated Function in a Licensee. The term ‘Applicant’ is captured by Authorised Individual, where relevant. 1.4 Authorisation: the Central Bank’s formal approval or non-objection to the appointment or reappointment of a Person to a Designated Function or any other function within a Licensee, as determined by the Central Bank. 1.5 Authorized Individual: any natural Person authorized in accordance with the provisions of the Central Bank Laws, to carry on any of the Designated Functions. In the case of Insurance Companies, and Insurance-Related Professionals, the term Authorized Individual includes Senior Employees. 1.6 Authorized Manager: a natural Person appointed by a foreign Insurance Company to manage its Branch in the State. 1.7 Bank: any Juridical Person licensed in accordance with the provisions of the Central Bank Law, to primarily carry on the activity of taking deposits, and any other Licensed Financial Activities. 1.8 Board: the board of directors of the Licensee. In the case of branches of foreign Licensees, Board refers to the highest decision making body of the Licensee within the State, for example, the Senior Management committee. 1.9 Branch: a branch of the Insurance Company that carries out insurance activities in the name of the Insurance Company. 1.10 Central Bank: the Central Bank of the United Arab Emirates (CBUAE). 1.11 Central Bank Law: the Decretal Federal Law No. (14) of 2018 Regarding the Central Bank & Organisation of Financial Institutions and Activities, as amended. 1.12 Central Bank Laws: the Central Bank Law and the Insurance Law. 1.13 Chief Executive Officer: the most senior executive appointed by the Board, and in the case of a Branch, this refers to the Authorized Manager. 1.14 Collective Suitability: the structure and composition of a Licensees’ Board, which allows for full appreciation of the Licensees’ risk profile and business strategy to enable it to exercise effective challenge and oversight of decisions. The assessment of Collective Suitability takes into consideration, inter alia, size and structure, degree of independence and interaction, degree of diversity, and collective, relevant knowledge, skills and experience. 1.15 Compliance with Islamic Shari’ah Provisions: refers to compliance with Islamic Shari’ah in accordance with:
a. The provisions stated in Section Six of Book Three of the Commercial Transactions Law, b. The provisions contained in the bylaws issued implementing Section Six of Book Three of the Commercial Transactions Law, c. The resolutions, Fatwas, regulations and standards issued or approved by the Higher Shari’ah Authority in relation to businesses and activities of the Licensee ("HSA’s Resolutions"), d. The resolutions and Fatwas issued or approved by the Internal Shari’ah Supervision Committee of the respective Licensee, in relation to businesses and activities of such Licensee ("ISSC’s Resolutions"), provided that they do not contradict the HSA’s resolutions.
1.16 Conflict of Interest: a situation of actual or perceived conflict between the duty and private interests of a Person, which could improperly influence the performance of his/her duties and responsibilities. 1.17 Continuous Professional Development (CPD): any type of training or learning undertaken by a Person, which increases relevant knowledge, understanding and experiences of a subject area or role. 1.18 Control Functions: The Licensee’s functions that have a responsibility independent from management to provide objective assessment, reporting and/or assurance; this includes the risk management function, the compliance function and the internal audit function. 1.19 Designated Functions: functions of the Authorized Individual at, or for the benefit of, a Licensee of influential nature on the institution's activities. 1.20 Fit and Proper Process: the evaluation of a Licensee’s proposed and existing members of the Board and Senior Management, Material Risk Takers and other Persons, as determined by the Central Bank. 1.21 Group: a group of entities that includes an entity (the ‘first entity’) and:
a. any Parent of the first entity; b. any Subsidiary of the first entity or of any Parent of the first entity; and c. any Affiliate.
1.22 Health Insurance Claims Management Company: a Juridical Person licensed by the CBUAE to carry out health insurance claims management business. 1.23 Higher Sha’riah Authority: an authority that exercises the mandates and authorities stipulated in Regulations regarding Takaful Insurance and the notices issued by the Central Bank. 1.24 Insurance Agent: a Person licensed or authorized by the CBUAE, and is approved by the Insurance Company and authorized to carry out insurance activities on its own behalf or on behalf of a Branch thereof. 1.25 Insurance Broker: a Juridical Person licensed by the CBUAE and acts as independent intermediary in insurance and reinsurance operations between an insurance or re-insurance applicant on the one side and any Insurance Company on the other side, and receives, in consideration of its efforts, a commission from the Insurance Company with which insurance or reinsurance is concluded. 1.26 Insurance Company: an insurance company established in the State as well as a foreign insurance company licensed to carry out insurance business in the State, either through a Branch or through an Insurance Agent; and a Re-Insurance Company licensed to engage in re-insurance business either in the State or abroad. 1.27 Insurance Consultant: a Person licensed or authorized by the CBUAE to examine insurance requirements for their clients and give advice in respect of the suitable insurance coverage, assistance in preparing insurance requirements and receives their remuneration from their clients. 1.28 Insurance Law: the Federal Decree-Law No. (48) of 2023 Regulating Insurance Activities and its Executive Regulations, and any amendments thereof. 1.29 Insurance-Related Professions: any Person licensed or authorized by the CBUAE to operate as an Insurance Agent, Insurance Broker, Surveyor and Loss Adjuster, Insurance Consultant, Actuary or Health Insurance Claim Manager, or any other profession related to insurance as determined and regulated by a resolution of the Board of Directors of the Central Bank. 1.30 Internal Shari’ah Supervision Committee (ISSC): a body appointed by an Islamic financial institution/ a Takaful Insurance Company, comprised of scholars specialized in Islamic financial transactions, which independently supervises transactions, activities, and products of the Islamic financial institution / the Insurance Company and ensure its Compliance with Islamic Shari’ah Provisions in all its objectives, activities, operations, and code of conduct. 1.31 Islamic Financial Institutions: the Licensed Financial Institutions that conduct all or part of their activities and businesses in accordance with the provisions of Islamic Shari'ah. 1.32 Juridical Person: any person who is not a natural Person. 1.33 Licence: authorisation issued by the Central Bank to conduct the business of a Licensee. 1.34 Licensed Financial Activities: the financial activities subject to Central Bank licensing and supervision, which are specified in Article (65) of the Central Bank Law. 1.35 Licensed Financial Institutions: Banks and Other Financial Institutions licensed in accordance with the provisions of the Central Bank Law, to carry on a Licensed Financial Activity or more, including those which carry on the whole or a part of their business in Compliance with the Islamic Shari`ah Provisions, and are either incorporated inside the State or in other jurisdictions, or have branches, Subsidiaries or Representative Offices inside the State. 1.36 Licensee: a Licensed Financial Institution, an Insurance Company, Takaful Insurance Company or an Insurance-Related Profession, which is subject to the provisions of the Regulation and its accompanying Standards. 1.37 Material Risk Takers: Staff whose work is deemed to have a significant impact on the overall risk profile of the Licensee or the Group. 1.38 Other Financial Institutions: any Juridical Person, other than Banks, licensed, in accordance with the provisions of the Central Bank Law, to carry on a financial activity or more, of the Licensed Financial Activities. 1.39 Parent: an entity (the ‘first entity’) which:
a. holds a majority of the voting rights in another entity (the ‘second entity’); b. is a shareholder of the second entity and has the right to appoint or remove a majority of the board of directors or managers of the second entity; or c. is a shareholder of the second entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the second entity. Or; d. if the second entity is a subsidiary of another entity which is itself a subsidiary of the first entity.
1.40 Person: a natural Person. 1.41 Regulations: any resolution, regulation, circular, rule, standard or notice issued by the Central Bank or any resolution issued by the Higher Sha’riah Authority 1.42 Representative Offices: an office licensed in accordance with the provisions of the Central Bank Law, to carry on representation of a financial institution incorporated in other jurisdictions. 1.43 Senior Employee: any Person who occupies an executive position equivalent to the duties of a Director-General, Authorized Manager or the deputy or assistant of either one, or any department director, internal audit director or Branch manager. 1.44 Senior Management: the executive management of the Licensee responsible and accountable to the Board for the sound and prudent day-to-day management of the Licensee, generally including, but not limited to, the Chief Executive Officer, chief financial officer, chief risk officer, heads of the compliance and internal audit functions. 1.45 Staff: all the Persons working for a Licensee including the members of Senior Management, except for the members of its Board. 1.46 State: the United Arab Emirates (UAE). 1.47 Subsidiary: an entity (the ‘first entity’) is a subsidiary of another entity (the ‘second entity’) if the second entity:
a. holds a majority of the voting rights in the first entity; b. is a shareholder of the first entity and has the right to appoint or remove a majority of the board of directors or managers of the first entity; or c. is a shareholder of the first entity and controls alone, pursuant to an agreement with other shareholders, a majority of the voting rights in the first entity. Or; d. if the first entity is a subsidiary of another entity which is itself a subsidiary of the second entity.
1.48 Surveyor and Loss Adjuster: a Person licensed or authorized by the CBUAE to inspect and assess the damage incurred in the subject of insurance. 1.49 Takaful Insurance: a collective contractual scheme intended to achieve solidarity and cooperation among a group of contributors to address certain risks, where each one pays an amount of money called “contribution” to be deposited in a Takaful insurance fund, through which compensation is to be paid to eligible persons when a risk is sustained. 1.50 Takaful Insurance Company: an Insurance Company, which is incorporated and practices its business in accordance with the provisions of the Central Bank Laws and Regulations, and whose carried out businesses and activities are in Compliance with the Islamic Shari’ah Provisions.
Article (2): Fit and Proper Conditions
2.1 An Authorized Individual must not be considered fit and proper for any role other than the position that the Central Bank has authorised the Person to hold. 2.2 Where an Authorized Individual has undergone the Fit and Proper Process and been Authorised by the Central Bank to be appointed to a Designated Function, and is being considered to take on another or additional Designated Functions within a Licensee, where permitted, the Person must be reassessed and an application for Authorisation must be submitted to the Central Bank prior to the Person being assigned to any Designated Function, other than what has been authorised by the Central Bank. 2.3 In the event that a Designated Function becomes vacant unexpectedly or temporarily, with limited notice, a Licensee must immediately notify the Central Bank; and may submit an urgent request to the Central Bank to assign an Authorized Individual to the vacant function on an interim basis. The Central Bank, at its sole discretion and on a case by case basis, will determine the conditions and requirements for granting its Authorisation for an interim appointment, including timeframes and required assessments and reporting, where not specified in applicable Regulations. 2.4 The Central Bank will usually approve an interim appointment for a maximum period of six (6) months, following which an extension may be granted, if requested by the Licensee and supported by adequate justification. 2.5 Fitness and propriety and suitability, including Collective Suitability, must be monitored by Licensees on an ongoing basis, outside of the annual appraisal process, and particularly where material concerns emerge. 2.6 The Fit and Proper Process must consider the proportionality principle, in that, the competency and capability requirements for each function being assessed must be tailored to inter alia, the nature and scale of the activities, size, business model, complexity of the operations and risk profile of the Licensee. The proportionality principle must never be applied in the assessment of honesty, integrity and reputation or independence of mind.
Article (3): Central Bank Powers
3.1 consideration. The list of Designated Functions is presented in Attachment 1 to the Standards, and may be amended by the Central Bank from time to time. 3.2 The Central Bank will not grant Authorisation for the appointment of a Person to a Designated Function until all required information and documentation is provided and all requirements in relation to the fit and proper Authorisation application are fully met. 3.3 The Central Bank may request the participation of an Authorized Individual or any other Person in an interview/s to inform a decision on Authorisation. The decision on whether to conduct an interview is at the sole discretion of the Central Bank. 3.4 The Central Bank may require the participation of a Licensee in meeting/s with the Central Bank to inform a decision on Authorisation of an Authorized Individual. 3.5 Upon the resignation or termination of employment or engagement of an Authorized Individual or any other Person employed or engaged by a Licensee, the Central Bank may conduct an exit interview with that Person. 3.6 The Central Bank, at its sole discretion, may impose a ban on a Person whose request for Authorisation has not been successful, from employment within Licensees, for a specified period or indefinitely.
Article (4): Responsibilities of the Licensee
4.1 The Board must ensure the fitness and propriety of Persons holding Designated Functions in accordance with Central Bank Regulations and the Licensee’s policies, procedures and requirements. The Board must therefore establish a Fit and Proper Process for the selection, continued assessment and monitoring of the Board, Senior Management, Material Risk Takers and other Persons. 4.2 The Fit and Proper Process must be inextricably linked to the Licensee’s determination of a Person’s suitability for a particular function. Therefore, Applicants and proposed Material Risk Takers must be assessed as fit and proper and suitable for the proposed function by a Licensee prior to their appointment. In the case of an Applicant, the appointment of that Person must not take place prior to the Licensee receiving formal Central Bank Authorisation. 4.3 A Licensee must satisfy itself that the information and documentation provided by a Person in the course of the Fit and Proper Process is truthful, complete, fair, accurate and not misleading. 4.4 The Board must ensure that processes are implemented, maintained and monitored to ensure that members of the Board and Senior Management meet the fit and proper requirements on an ongoing basis and are under constant review. 4.5 Licensees must adopt and implement comprehensive fit and proper and suitability assessment frameworks which establish the Fit and Proper Process and clearly identify the procedures to be followed in the selection and assessment of Authorized Individuals, Material Risk Takers and other Persons; and include, at a minimum, clear and detailed policies and adequate resources to ensure that fit and proper and suitability assessments are conducted in a comprehensive and regulatory compliant manner. 4.6 A Licensee’s policies and procedures must, at a minimum:
a. Establish the minimum fit and proper criteria for all Persons subject to fit and proper/suitability requirements; b. Detail the Licensee’s Fit and Proper Process including timing, regularity, processes and accountabilities; c. Document criteria which will trigger a fit and proper reassessment, including, inter alia, negative press, changes in the Licensee’s risk profile, enforcement or supervisory action or performance deficiencies; d. Establish and define the steps to be taken if a Person is found to be not fit and proper, including options for remedial action and communication with the Central Bank; e. Include the list of documents, information, and/or data required to conduct the Fit and Proper Process and reassessments; f. Identify who holds responsibility for establishing and reviewing the fit and proper/suitability assessment framework and for conducting the Fit and Proper Process; g. Designate appropriate responsibilities with timeframes for the submission of reports, applications for Authorisation, and any other communication with the Central Bank related to the Fit and Proper Process; h. The ongoing training requirements and resources for Persons conducting assessments; i. Set the steps and activities involved in the Fit and Proper Process; j. Establish how the information, records and documents related to the Fit and Proper Process are verified, authenticated and stored securely; k. Set the procedures for managing Conflicts of Interest in the Fit and Proper Process; and l. Document the role of internal audit in the Fit and Proper Process, including reviews to ensure effectiveness.
4.7 Policies and procedures related to the Fit and Proper Process must be reviewed regularly and revised in line with inter alia, updates to the legal and regulatory framework and industry best practice. 4.8 Where a Person being assessed has been subject to authorisation or approval by a financial services regulator(s) in another jurisdiction(s), the Central Bank may require that the Licensee contacts the relevant regulator/s to ascertain the status of the authorisation or approval and share all relevant information, to the extent legally permissible, with the Central Bank. 4.9 Following the formal Authorisation by the Central Bank for the appointment of an Authorized Individual, a Licensee must officially notify the Central Bank of the appointment of the Person within seven (7) business days, providing confirmation of the appointment date, tenure of the contract and any additional pertinent details not previously provided to the Central Bank. 4.10 Unless otherwise specified by applicable law or Regulations, where a Designated Function becomes vacant, for whatever reason, a Licensee must ensure that it appoints a Person to the position within thirty (30) days of the vacancy date, either on an interim or permanent basis, and subject to the Authorisation requirements in the Regulation and the Standards. 4.11 With the exception of criteria relevant to the assessment of honesty, integrity and reputation, if a Licensee’s assessment or re-assessment identifies easily remediable shortcomings in a Person’s knowledge, skills or experience, the Licensee should take appropriate corrective measures to overcome those shortcomings in a timely manner. The Licensee must prepare a training plan for the Person which must be submitted to the Central Bank as part of the application for Authorisation.
Article (5): Material Risk Takers
5.1 Licensees must subject Material Risk Takers to the Fit and Proper Process and ensure that they have obtained the appropriate competence, skills, experience and training required to perform the relevant function. 5.2 The Licensee’s assessment of Material Risk Takers’ fitness and propriety must be based on the relevant criteria established in Article (7) of the Standards. When assessing qualifications, knowledge, skills and experience, the role and duties of the specific position must be considered. 5.3 The Licensee must establish and implement approved policies and procedures to ensure that Material Risk Takers meet and continue to meet the fitness and propriety criteria throughout their tenure. The policies and procedures must, at a minimum, cover the applicable criteria established in Article (7) of the Standards. These policies and procedures must be reviewed on a regular basis and must be kept aligned with CBUAE requirements, as they evolve. 5.4 The Central Bank must be notified of the appointment of Material Risk Takers within thirty (30) days of the appointment. 5.5 The Licensee must provide the Central Bank with access to the information collected or procedures conducted in the context of the nomination and appointment of Material Risk Takers, when requested. 5.6 Material Risk Takers must undergo a comprehensive training programme at the commencement of their engagement with the Licensee, which is relevant to their function, where required. Specific training programmes may need to be completed for certain functions and these may be set by the Central Bank in separate Regulations. 5.7 Licensees must ensure that the knowledge of Material Risk Takers is up to date and that Material Risk Takers undergo training on an ongoing basis, relevant to their particular functions. 5.8 Licensees must conduct ongoing assessments of Material Risk Takers to ensure that they remain suitable for their posts over the entire period of their engagement. In addition to the criteria established in Article (7) of the Standards, the assessments must take into account the following, where applicable:
a. the nature of the functions undertaken by the Person; b. the quality of advice or information provided to consumers; c. the quality of the decisions taken by the Material Risk Taker; d. the Person’s knowledge of and compliance with legal and regulatory requirements relevant to the role; e. the results of performance reviews or assessments of the Person; f. any complaints that have been lodged in relation to the Person; and g. the verified number of hours of CPD completed or scheduled to be completed.
Article (6): The Fit and Proper Process
6.1 Authorized Individuals and Material Risk Takers must undergo the Fit and Proper Process prior to their appointment, reappointment or contract renewal, as the case may be. The non-exhaustive list of Designated Functions is presented in Attachment 1 to the Standards. The list of positions should be reviewed in the context of the operations of the Licensee, in that, equivalent positions which may be titled differently within individual Licensees, need to be considered for Authorisation. The list is consistently under review and Licensees must keep abreast of updates to ensure compliance with the Regulation and Standards. 6.2 In applying the Regulation and Standards to Persons who hold or intend to hold Designated Functions, Licensees must consider the job description and requirements of the function and therefore not rely on the precise naming of the functions in Attachment 1.The Regulation and the Standards do not impose a requirement for a Licensee to havein place all functions listed in the List of Designated Functions.
Approach
6.3 Licensees must incorporate the following into their processes for selecting Persons for Designated Functions or as Material Risk Takers:
a. Consideration of the duties and responsibilities of the position; b. A selection process that allows for the assessment of the qualifications and experience of the Person in relation to the requirements of the position; c. Verification of qualifications, experience, references and professional memberships; d. Propriety checks, including personal, financial and professional; and e. An assessment of how the Person contributes to the Collective Suitability of the Board, where applicable.
6.4 The Person must be made responsible for completing the prescribed forms and providing all supporting documentation and information to the Licensee, as far as possible. 6.5 The Licensee’s verification and authentication of information and documents must be comprehensively undertaken and include detailed checks to confirm accuracy. 6.6 The Licensee must sign the prescribed forms including the declarations, confirming that all required assessments and checks have been completed and that the Licensee has verified, as far as is reasonably possible, the information in the forms. 6.7 An application to the Central Bank for Authorisation must be submitted through designated CBUAE portals, where available, or official electronic mail accounts from Persons authorised by the Licensee to do so and must not be submitted from personal accounts. 6.8 Any false or misleading replies to questions in the forms or deliberate withholding of material information must be considered by the Licensee during the Fit and Proper Process as a strong indication that the Person lacks integrity. 6.9 Licensees must assess all necessary information to ensure that fit and proper assessments are comprehensive and accurate and provide confirmation that the Person has been found by the Licensee to meet the required criteria to fulfil the function. 6.10 The Fit and Proper Process for the heads of the internal Shari’ah audit and internal Shari’ah control departments shall be carried out in consultation with the ISSC. 6.11 Notwithstanding the requirement to conduct reassessments prior to the reappointment or renewal of contracts of Authorized Individuals, reassessments may be required where a need for one is triggered. Reassessments must be conducted by the Licensee in the following cases:
a. Where there are concerns regarding the fitness and propriety or suitability of the Person; b. In the case of any event that may materially affect the fitness and propriety or suitability of the Person; c. Where the Licensee is proposing to significantly change the responsibilities of the Designated Function; d. As part of the review of the internal governance arrangements by the Board and/or Senior Management; e. When the Licensee becomes aware that any information, documents, or responses to any of the questions in the prescribed forms or otherwise provided by the Person as part of the Fit and Proper Process may be inaccurate, erroneous or there are questions about their authenticity; or f. Where there is evidence that the Person may have acted in a manner considered detrimental to the interests of the Licensee, its depositors, policyholders or participants or other creditors.
6.12 Additionally, the Central Bank may request a reassessment/s based on additional triggers including, when the Central Bank has cause to question the management and direction of the Licensee’s business or where the Licensee has breached any of its legal, regulatory and/or other compliance obligations. 6.13 The CBUAE requires Licensees to assess all necessary information to ensure that reassessments are comprehensive and accurate. All fit and proper reassessments must take consideration of the following, at a minimum:
a. Information collected in the prescribed form; b. Annual and other appraisals; c. Internal records, including disciplinary actions; and d. Annual and other Board and Senior Management collective assessments.
Documentation
6.14 Licensees must explain the Central Bank’s documentation requirements to the Authorized Individual. 6.15 The Licensee must collect sufficient and appropriate information and documentation to assess whether a Person meets the fit and proper requirements. The information to be collected and its assessment may differ depending on the role of the Person being assessed. 6.16 Licensees must ensure that the prescribed forms are filled completely and accurately and sign off on the forms to indicate that all required reviews, assessments and verifications have been completed. 6.17 The Central Bank may request any information or documentation from a Licensee and/or Authorized Individual, it deems necessary to support an application for Authorisation. 6.18 The Central Bank will not commence its review of an application for Authorisation for any Person until all required information and documents have been received. If the complete set of documents is not received within the period specified by the Central Bank, the application request may be closed off and a new request for Authorisation may need to be submitted, where applicable. 6.19 Where the Central Bank requests the submission of additional information and/or documents, the timeframe set by the Central Bank for submission must be met by the Licensee. Failure to provide the information and/or documents within the timeframe may result in the application request being closed off and the need for the Licensee to submit a new request for Authorisation, where applicable. 6.20 Licensees must immediately notify the Central Bank of any material change to documents and/or information provided to the Central Bank as part of application for Authorisation. 6.21 Licensees must validate, authenticate, verify and/or review all relevant documentation, where applicable, as part of the Fit and Proper Process. Unless otherwise established in separate Regulations, the following documents, where applicable, should be assessed and provided to the Central Bank as part of the application for Authorisation of an Applicant. The Central Bank may prescribe the documentation required for assessments within individual Licensees or holders of specific Licences.
a. Fully completed and signed form/questionnaire, as prescribed by the Central Bank;
Applicant Information:
b. Copy of passport; c. Copy of second form of national photo identification (for example, national ID or driver’s license); d. Copies of any other passports held; e. Evidence of previous nationality or Marsoom letter; f. Copy of Emirates ID; g. UAE residence visa; h. Coloured photograph (passport size and with white background); i. Complete Family Book; j. No objection/National Service Letter from the UAE Ministry of Defense for UAE Citizens under the age of forty (40); k. Comprehensive, current resume or curriculum vitae of the Applicant which includes detailed information on qualifications and work experience of the Person; l. Offer letter and employment contract and/or card; m. Proof of previous employment including UAE experience certificates; n. Attested academic certificates; o. Qualification and training certificates; p. Any other professional certificates; q. Valid certificate of good conduct (police clearance) addressed to the Central Bank; r. Recent, original stamped banker’s or other financial reference; s. Recent professional references (including from previous employers which are Licensees) and/or character references; and t. Proof of relevant anti-money laundering/combatting the financing of terrorism and sanctions screening.
Licensee Information:
u. Approved job description for the proposed function; v. A list of all of the other roles that the Person currently holds and the expected time commitment for each role (where permitted); w. The report documenting the results of the Fit and Proper Process for the Person; x. Self-declaration by the Person that they have sufficient time to dedicate to all the mandates confirmed, by the Licensee; y. Updated trade licence of the main branch of the Licensee; z. Appointment approval request letter addressed to the Central Bank; aa. Board approved authorisation instrument for the Person signing on behalf of the Licensee; bb. Resignation letter of the former employee; cc. The Licensee must confirm that it has assessed the Collective Suitability of the Board and provide justification on how it has determined that the appointment of the Person would be a strategic and effective fit with the other members of the Board and contribute to maintaining or improving the Collective Suitability; and dd. Any other information or documents requested by the Central Bank.
6.22 The Central Bank may amend the information requirements for an Authorisation request, at its sole discretion, on a case-by-case basis. 6.23 Where the Licensee has found the Person deficient in any of the fit and proper assessment factors, a detailed explanation of the mitigating or compensating factors must be submitted to the Central Bank. If the Person does not fully meet the qualification or experience requirements, the Licensee is required to submit the written justification for wishing to proceed with the appointment, including compensating factors or plans for timely remediation, in the case of qualification requirements.
Article (7): Fit and Proper Criteria
7.1 In order to meet fit and proper requirements, an Authorized Individual or Material Risk Taker must have and demonstrate the necessary qualities that will allow him/her to perform the duties and carry out the responsibilities of his/her function within the Licensee. These qualities relate at a minimum to: honesty, integrity and reputation; competence and capability; good financial conduct; independence of mind and time commitment.
Honesty, Integrity and Reputation
7.2 Authorized Individuals and Material Risk Takers must be honest, diligent, of good reputation and independent-minded, and act ethically and with integrity and fairness. The Person must, at all times, act in full compliance with their contract of employment, including adherence to the Licensee’s code of conduct and/or ethics. 7.3 The conduct and actions of the Person who is subject to the Fit and Proper Process must be such that his/her integrity is beyond reasonable doubt. Indicators of integrity include criminal, financial, supervisory and other aspects. 7.4 Supervisory indicators include information collected by supervisors, including the Central Bank in the performance of their duties. Negative indicators could include the withholding of information from competent authorities, submission of incorrect financial or other statements, prior refusal of regulatory approval, other corrective actions or interventions by a competent authority. 7.5 A Person must not be considered of good repute if their personal or business conduct gives rise to any material doubt about their ability to ensure the sound and prudent management of or participation in the Licensee. 7.6 In determining the honesty, integrity and reputation of a Person, consideration must be given to whether the Person:
a. has a record or evidence of previous conduct and activities where he/she has been convicted for a criminal offence under any legislation designed to protect members of the public from financial loss, due to dishonesty, incompetence, malpractice, misappropriation of assets, embezzlement and other fraud. b. is or has been the subject of any adverse finding or any settlement in civil proceedings of an offence related to misconduct, misrepresentation, breach of trust, dishonesty, fraud, money laundering, theft, or other financial crime within the prior ten year period. c. has at any time shown a strong objection or lack of willingness to cooperate with competent authorities resulting in a failure or potential failure to comply with legal obligations, regulatory or professional requirements and standards, including compliance with tax requirements and obligations, or has been obstructive, misleading or untruthful in dealing with competent authorities or a court. d. has not been fair, truthful and forthcoming in dealings with customers, auditors and/or competent authorities. e. has had any judgements or decisions issued against them by the courts, dispute resolution committees or other judicial or semi-judicial bodies; or has ever been disqualified or restricted from acting as a director or serving in a managerial capacity. f. has been convicted or found guilty in any proceedings of a disciplinary, regulatory or criminal nature, including the practice of any unauthorised or unlicensed activity. g. any entity in which the Person holds or has held any position of responsibility or influence or is or has been a significant shareholder, is or has been, subject to any disciplinary proceedings, civil penalty, enforcement action, has been suspended, or has been issued a censure, warning, reprimand or other administrative sanction or its equivalent, by the Central Bank, clearing house or exchange, or by any other competent authority, considering also the level of direct or personal involvement of the Person. h. has contravened any of the material requirements of the Central Bank Laws or any of its Regulations or any equivalent requirements of another competent authority. i. is or has been associated, in ownership, directorship or management capacity, with a company, partnership or other business association which is being or has been wound up by a court or other competent authority; that has been refused registration, authorisation, membership or a licence to conduct trade, business or profession; has been prohibited, restricted or suspended from the right to carry on any trade, business or profession for which a licence, registration or other authorisation is required by the law in that jurisdiction; or has had that registration, authorisation, membership or licence revoked, with drawn or terminated, or struck off the register of companies (or its equivalent) on an involuntary basis; and/or has been found to have contributed significantly to the failure of an organisation or a business unit, considering also the level of direct or personal involvement of the Person. j. has been the subject of any complaint made to the Central Bank, the financial services ombudsman or any equivalent body, relating to activities regulated by the Central Bank or regulated by an equivalent competent authority. In considering whether the complaint adversely affects the Person’s ability to carry out a relevant function, consideration shall be given to the outcome of any inquiry or investigation or any similar process into that complaint if same has been concluded. k. without prejudice to the presumption of innocence, has been the subject of any proceedings of a criminal or disciplinary nature or has been notified of any such potential proceedings or any investigation which may lead to such a proceeding. l. has been untruthful or provided false or misleading information to the Central Bank or has been uncooperative in any dealings with the Central Bank; m. has at any time shown strong objection or a lack of willingness to maintain effective internal control systems and risk management practices. n. has engaged in any business or professional practices which are deceitful, negligent, oppressive or otherwise improper (whether unlawful or not), or which otherwise reflect discredit on his/her professional conduct. o. has been dismissed, asked to resign or has resigned from any profession, vocation, office or employment or from any position of trust or fiduciary appointment, whether or not remunerated because of questions about his/her honesty and integrity, or has breached a fiduciary obligation.
Competence and Capability
7.7 An Authorized Individual or Material Risk Taker must have the necessary academic qualification, competence, capacity, theoretical knowledge, adequate experience and skills to perform his/her role effectively, as well as the ability to understand the technical requirements of the business of the Licensee, the legal and regulatory framework, the risks and the management process. Additionally, the Person must meet all requirements set by the Central Bank, which may include specific qualification, academic, or training requirements related to the specific function the Person holds or is being proposed to assume. 7.8 In determining the competence and capability of a Person, a Licensee must consider and assess whether the Person:
a. has the appropriate professional or other qualifications, training and capability to demonstrate their capacity to undertake the responsibilities of the positions and more generally, their suitability for the relevant function. b. has the competence, proficiency and an appropriate range of skills and experience to understand, operate and manage the affairs of the Licensee and to effectively and efficiently fulfil the role and responsibilities of the function. c. meets minimum qualification and training requirements established by the Central Bank, where applicable. d. has an adequate number of years of relevant, practical experience. e. has the technical knowledge and ability to perform prescribed duties for which they are engaged, specifically professional qualifications and membership in relevant professional bodies. The Licensee must take consideration of any specific, required experiences, skills and/or qualifications for key functions. f. has a sound knowledge of the business of the Licensee as a whole, and the specific responsibilities that are to be undertaken in the relevant function. g. has satisfactory past performance or expertise in the nature of the business being conducted and history of compliance with the law and Regulations. h. has a clear and comprehensive understanding of the legal and regulatory environment relevant to the function. i. is of sound mind. j. has been dismissed or suspended from employment.
7.9 Additionally, Authorized Individuals and Material Risk Takers should demonstrate theoretical knowledge and understanding in some of the following areas:
a. the financial sector and financial markets; b. the legal and regulatory framework, including Shari’ah requirements, where Shari’ah is applicable; c. financial sector risks, risk management and internal controls; d. climate and environmental risks; e. environmental, social and governance (ESG) and sustainability factors; f. corporate governance; g. strategic planning; h. accounting, auditing and financial statement analysis; and i. the business, financial and economic environment.
Financial Conduct
7.10 In assessing the financial conduct of Persons, the Licensee must assess whether the Person can maintain solvency and prudent financial control, including but not limited to, meeting liabilities as they become due. 7.11 A Person's financial conduct is relevant to an assessment of his/her professional integrity as it may have an impact on his/her reputation. 7.12 In assessing the financial conduct of a Person, the Licensee must give due consideration to whether the Person:
a. has the experience needed to manage their financial obligations and affairs prudently and properly. b. can be reasonably expected to meet debts as they fall due. c. has been subject to any judgment, debt or award that they have defaulted on, remains outstanding or has not been satisfied within a reasonable period of time. d. has sought relief for any debt or made arrangements with creditors or made an assignment for the benefit of creditors, filed for bankruptcy or been adjudged bankrupt or had assets sequestered or confiscated or been in any proceedings related to any of the aforementioned. e. has been able to provide the Licensee with satisfactory credit reference/s, where applicable. f. is or has been unable to fulfil their financial obligations as they fall due; g. has seriously or persistently failed to manage personal debts or financial affairs in a satisfactory manner that has caused detriment or loss to others. h. has held in the past year or currently holds a loan or other credit facility with the Licensee which has been or is in arrears for a period of greater than ninety (90) days. i. was able to manage any previous business dealings in a sound and prudent manner. j. has been an owner, director, partner, senior manager or otherwise involved in the management of an entity that has gone into receivership, insolvency, or compulsory liquidation while the Person was connected with that entity or within a reasonably short period (for example, one year) after the Person’s departure from the institution.
Independence of Mind
7.13 Authorized Individuals and Material Risk Takers must demonstrate the capacity to employ independent judgement and make sound, objective and independent decisions, without being unduly, externally influenced. The assessment of independence of mind must consider whether the Person has the ability to express divergent opinions and resist groupthink. The Person should show a record of being able to question and challenge members of Senior Management and the Board. 7.14 Authorized Individuals and Material Risk Takers must be assessed as independent from influence in performing their duties to the Licensee, giving due consideration to any other employment interests, obligations or situations which may give rise to a Conflict of Interest or which could, in any way, impair the Person’s ability to independently perform the duties.. 7.15 Licensees must assess whether the Person’s membership in other boards of directors or similar positions has the potential to conflict with the interests of the Licensee. 7.16 The Licensee must not allow for Persons to conduct concurrent responsibilities which have the potential to impair their ability to discharge the duties of the Designated Function. Where not already set in existing Regulations, the Licensee must set reasonable limits on the number of memberships held by members of the Board in other boards of directors or similar positions. 7.17 Licensees must conduct thorough assessments of whether a Person is involved in any business or other relationship which could materially pose a Conflict of Interest or interfere with the exercise of his/her judgement and has the potential to be disadvantageous to the interests of the Licensee. 7.18 The Licensee must not allow for a Person to simultaneously hold two or more positions within the Licensee where the appointments could result in a material conflict. 7.19 All financial and non-financial interests that could create potential or perceived Conflicts of Interest should be disclosed by the Licensee to the Central Bank as part of the application for Authorisation. The Licensee should notify the Central Bank about any material Conflicts of Interest, when they arise along with details of the proposed resolution plan.
Time Commitment
7.20 Licensees must ensure that a Person has adequately demonstrated their ability to commit time to perform their role and meet the responsibilities associated with their function in the Licensee, by assessing the following, at a minimum:
a. whether the Person is in full time employment and assessing the number of hours or days dedicated to each role; b. whether any of the roles have any additional responsibilities such as membership and/or chair of committees; c. whether the nature, type and size of the other entity/entities will demand more time from the Person (e.g. the entity is regulated, listed etc.); and d. whether the experience of the Person, either generally or with respect to the Licensee, is such that the Person could carry out their duties with greater familiarity and therefore efficiency.
7.21 In order to ensure that time commitment is met by a Person, the Licensee must, at a minimum, request, review and submit to the Central Bank as part of its application for Authorisation, where applicable, the following:
a. a list of all of the other formal roles that the Person currently holds and the expected time commitment for each role; and b. a declaration by the Person that they have sufficient time to dedicate to all the roles confirmed by the Licensee.
Article (8): Collective Suitability
8.1 A Licensee must establish target representation to ensure diversity on the Board. 8.2 A Licensee must undertake an assessment of the Collective Suitability when proposing appointees to its Board. The results of this assessment must be submitted to the Central Bank as part of the package for approval of the appointment of an Applicant. 8.3 In assessing and determining the Collective Suitability of its Board, a Licensee must consider the nature, size and scope of its business operations; the business model, objectives and strategy, and the risk appetite, risk tolerance and risk profile. 8.4 Licensees must establish and implement a policy for the induction and training of members of the Board which should be tailored and aligned with the entity’s goals related to achieving Collective Suitability. The resources allocated by the Licensee for induction and training must be sufficient to achieve the objectives of Collective Suitability and to ensure members’ ongoing fitness and propriety and suitability. Licensees must have a process in place to identify the areas in which training is required, both for the Board as a collective body and for individual directors. 8.5 A Licensee’s assessment of Collective Suitability must take into consideration the Board members’ collective knowledge and understanding of the following, at a minimum:
a. Financial institution governance and management; b. Islamic finance and Shari’ah requirements, where applicable. c. The business of the Licensee, including, inter alia, products, services and markets; d. Risk management, compliance and internal and external audit; e. Main business risks including financial, information technology, information and cyber security, climate, environmental and other industry specific risks and their management; f. Money laundering and terrorist financing risks; g. Strategic planning, operational resilience and digital transformation; h. The legal and regulatory environment and related prudential and other compliance requirements; i. Relevant international and other sectoral standards; j. The financial sector and business environment; k. Outsourcing arrangements; l. Financial and management accounting and reporting; and m. Group risks and management, where applicable.
Article (9): Continuous Professional Development (CPD) Requirements
9.1 At the start of each financial year, Licensees must submit to the Central Bank, a Board approved training plan detailing the areas of training, and Authorized Individuals and Material Risk Takers identified for these training opportunities. The Licensee must be able to demonstrate that the training plan contributes to the suitability of Persons in addition to the Collective Suitability of the Board. 9.2 An Authorized Individual’s or Material Risk Taker’s failure to maintain appropriate qualifications or memberships, where they are relevant, must trigger a reassessment of that Person’s fitness and propriety. 9.3 The Central Bank may exempt an Authorized Individual or Material Risk Taker from the minimum CPD requirement generally, or in a particular year, in exceptional circumstances including cases of serious illness. 9.4 Authorized Individuals and Material Risk Takers must complete the minimum required CPD hours set by the Licensee or the Central Bank, as the case may be. CPD hours completed in one year must not be carried over to another year. 9.5 The content of the CPD hours used to meet the requirements herein must be directly relevant to the specific function of the Person. 9.6 Relevant CPD hours may be comprised of participation at conferences, lectures, workshops, seminars, formal training courses and/or appropriate electronic learning platforms. 9.7 Licensees must document and inform the Central Bank of any breaches of CPD requirements.
Article (10): Reporting and Record Keeping
10.1 A Licensee must keep detailed records of the following, where applicable, in relation to the conduct of the Fit and Proper Process for all applicable Persons and submit, where required or provide access to the Central Bank immediately upon request:
a. Prescribed forms and all supporting documents as stipulated in the Standards; b. Sources of all information, verifications and authentications; c. Character, professional and regulatory references and evidence of criminal and other checks conducted; d. Any information that may affect the Central Bank’s review of the application and or decision to issue Authorisation for the Person; e. The reports and decisions resulting from the Fit and Proper Process including clear rationale for all decisions; and f. The reports and all related records from assessments conducted by any third party.
10.2 Licensees must, at least on an annual basis, provide a report to the Central Bank with information on the following:
a. Vacant Designated Functions; and b. CPD undertaken by Persons, where required.
10.3 The Central Bank will prescribe any additional information required to be submitted and/or to be presented in the Licensee’s annual report.
ATTACHMENT 1: LIST OF DESIGNATED FUNCTIONS
Banks Insurance and/or Reinsurance Companies Finance Companies Exchange Houses Insurance Brokers/Third Party Administrators All Other Licensees 1. Members of the Board of Directors;2. Chief Executive Officer (CEO);3. Deputy Chief Executive Officer;4. Chief Financial Officer (CFO);5. Chief Risk Officer (CRO);6. Chief Internal Auditor (CIA);7. Chief Compliance Officer (CCO);8. AML Compliance Officer and/or Money Laundering Reporting Officer (MLRO);9. General Counsel;10. Advisorto Board or Senior Leadership;11. Chief Representative Officer;12. Chief Credit Officer (CCO);13. Chief Operating Officer (COO);14. Chief Information Security Officer - CISO (InfoSec);15. Chief of Business;16. Members of Internal Shari'ahSupervision Committee (ISSC) – Islamic Financial Institution (IFI);17. Head of Internal Shari'ah ControlDivision or Section - IFI;18. Head of Internal Shari'ah AuditDivision or Section – IFI; and19. Any other executive positions reporting directly to the CEO and/or the Board, as designated by the CBUAE.1. Members of the Board of Directors;2. Board Secretary;3. Chief Executive Officer;4. Deputy Chief Executive Officer;5. Chief Financial Officer;6. Chief Risk Officer;7. Chief Internal Auditor;8. Chief Compliance Officer;9. AML Compliance Officer and/or Money Laundering Reporting Officer;10. General Counsel;11. Advisor to Board or Senior Leadership;12. Chief Actuary13. Chief Operating Officer;14. Director of Legal Affairs;15. Chief of Claims;16. Chief of Underwriting;17. Chief of Reinsurance;18. Chief Information Security Officer - CISO (InfoSec);19. Chief of Business;20. Members of the Internal Shari'ah Supervision Committee - IFI;21. Head of Internal Shari'ah Control Division or Section - IFI;22. Head of Internal Shari'ah Audit Division or Section – IFI; and23. Any other executive positions reporting directly to the CEO and/or the Board, as designated by the CBUAE.1. Members of the Board of Directors;2. Chief Executive Officer;3. Deputy Chief Executive Officer;4. Chief Financial Officer;5. Chief Risk Officer;6. Chief Compliance Officer;7. Chief Internal Auditor;8. AML Compliance Officer and/or Money Laundering Reporting Officer;9. Chief Credit Officer;10. Chief Operating Officer;11. Chief of Business; and12. Any other executive positions reporting directly to the CEO and/or the Board, as designated by the CBUAE.1. Members of the Board of Directors;2. Chief Executive Officer;3. Deputy Chief Executive Officer;4. Chief Financial Officer;5. Chief Risk Officer;6. Chief Compliance Officer;7. Chief Internal Auditor;8. AML Compliance Officer and/or Money Laundering Reporting Officer;9. Chief of Business; and10. Any other executive positions reporting directly to the CEO and/or the Board, as designated by the CBUAE.1. Managing Partners or Members of the Board of Directors, as the case may be;2. Chief Executive Officer;3. Chief Risk Officer;4. Director of Internal Audit;5. Chief Compliance Officer;6. AML Compliance Officer and/or Money Laundering Reporting Officer;7. Chief of Business; and8. Any other executive positions reporting directly to the CEO and/or the Board, as designated by the CBUAE.1. Members of the Board of Directors;2. Chief Executive Officer;3. Chief Financial Officer;4. Chief Risk Officer;5. Chief Compliance Officer;6. Chief of Internal Audit;7. Chief Information Security Officer - CISO (InfoSec);8. AML Compliance Officer and/or Money Laundering Reporting Officer;9. Chief Operating Officer;10. Chief of Business; and11. Any other executive positions reporting directly to the CEO and/or the Board, as designated by the CBUAE.